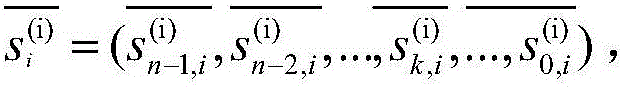Homomorphic encryption-based virtual asset anonymous ranking method
A virtual asset, homomorphic encryption technology, applied in the field of cryptography, can solve the problems of vulnerable storage servers, unfavorable promotion and use, and narrow application scope.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] The present invention will be described in further detail below in conjunction with the accompanying drawings.
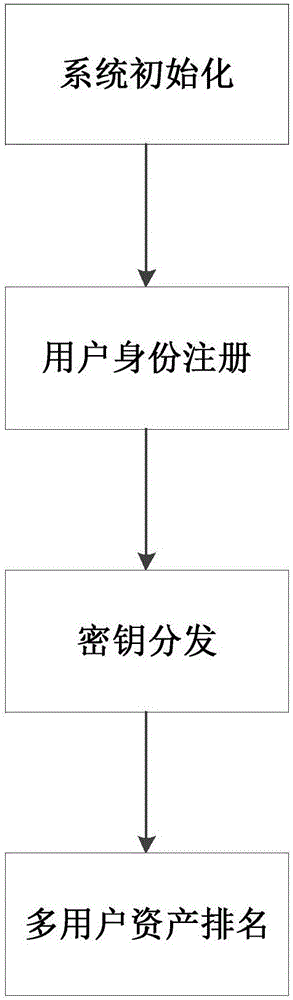
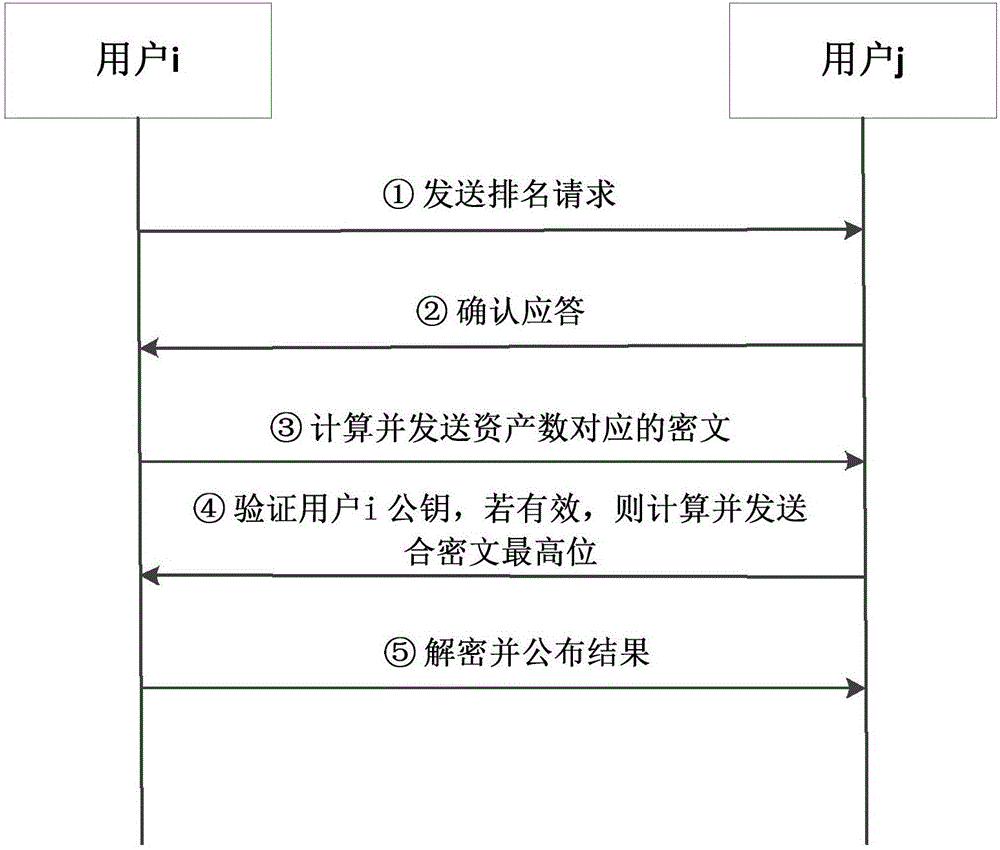
[0052] refer to figure 1 , the realization steps of the present invention are as follows.
[0053] Step 1, system initialization.
[0054] (1a) Authorization center CA runs Sig_Gen CA () algorithm, that is, first select two prime numbers P and Q with different values satisfying the formula ed=1mod((P-1)·(Q-1)), and two positive integers e and d with different values, and then calculate Modulus N=PQ, generate the authentication public key (N, e) and signature private key d of the authorization center itself, and keep the signature private key d secretly;
[0055] (1b) The authorization center CA selects an odd number t and a set of integers that satisfy security Define user public and private key selection set And select the set of user public and private keys Limited to the range of (-t / 2,t / 2];
[0056] (1c) The authorization center CA selects a c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com