Distributed multi-authorization-party ciphertext policy attribute-based encryption method for medium confusion
A technology of attribute-based encryption and ciphertext strategy, applied in the field of cloud computing security, which can solve problems such as collusion attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
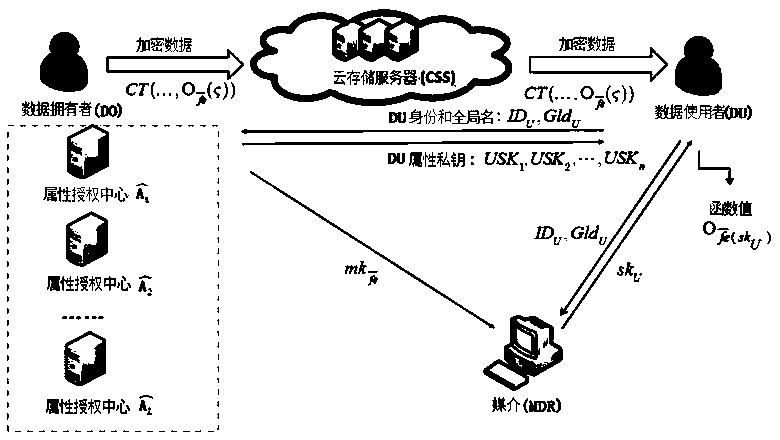
[0037] Please refer to figure 1, the present invention provides a distributed multi-authorized party ciphertext policy attribute-based encryption method for media confusion, and provides a system including a public parameter setting server, a data owner Do, a cloud storage server Css, a data user DU, and a media MDR, including The following steps:
[0038] Step S1: Input security parameter 1 in the public parameter setting server λ , get the public parameter PP and the pseudo-random function PRF(·); establish L attribute authorization centers Per property authority Manage the corresponding property set And establish a trusted medium between the data owner and the data user, generate a pseudo-random function PRF( ) and send it secretly to all attribute authorization centers (AAs) and the medium;
[0039] Step S2: The attribute authorization cente...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com