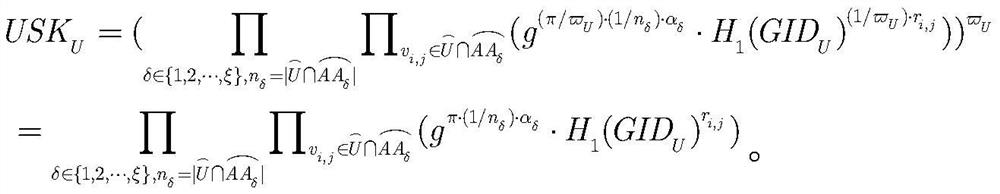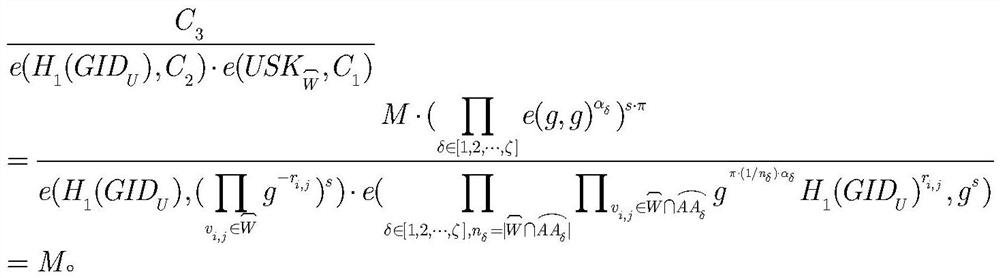Multi-authorization attribute-based encryption method and system without key escrow
An authorization attribute and key escrow technology, which is applied in the field of cloud computing security, can solve the problems of key escrow, data owners cannot manage cloud server data access, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] In order to make the purpose, technical solutions and advantages of the embodiments of the present application clearer, the technical solutions in the embodiments of the present application will be clearly and completely described below in conjunction with the drawings in the embodiments of the present application.
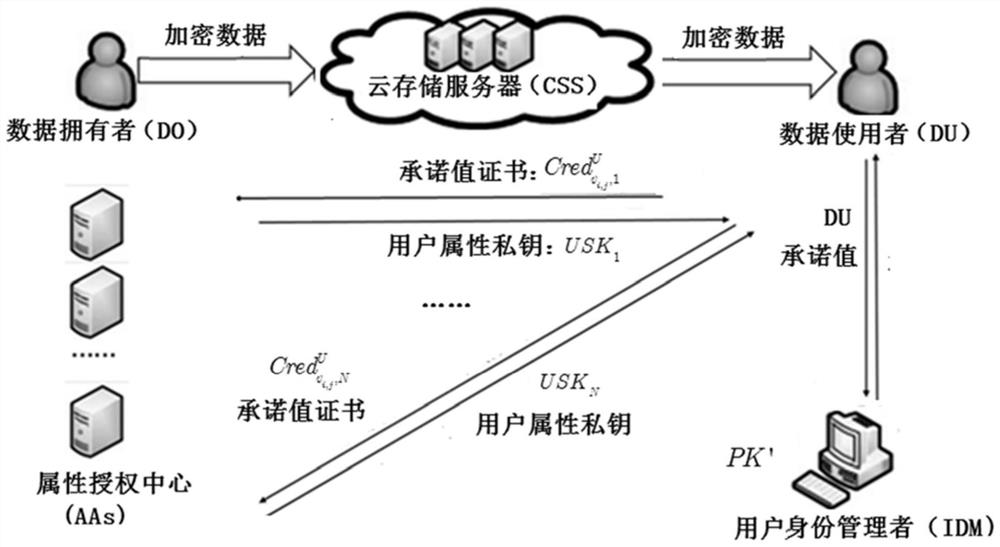
[0052] Such as figure 1 As shown, the present invention discloses a multi-authorization attribute-based encryption system without key escrow, which includes five roles: user identity manager (IDM), attribute authorization center (AAs), data owner (DO), data User (DU) and Cloud Storage Server (CSS). Data user DU submits its legal identity information and commitment value to IDM. After the IDM successfully detects the identity of the DU, the IDM generates and returns the corresponding certificate containing the DU commitment value. When DU applies for a decryption key from AAs, it also submits the corresponding commitment value. After AAs successfully veri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com