A Certificateless Key Agreement Method Based on Mobile Ad Hoc Network
A key agreement, certificate-free technology, applied in the field of network communication security, can solve problems such as single point of failure, key escrow, network failure, etc., to achieve the effect of solving single point of failure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0109] The preferred embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
[0110] In this embodiment, the system consists of one TTP and multiple movable free nodes, such as figure 1 shown. TTP is responsible for the generation and distribution of necessary parameters, and decides whether to allow a node to join the network.
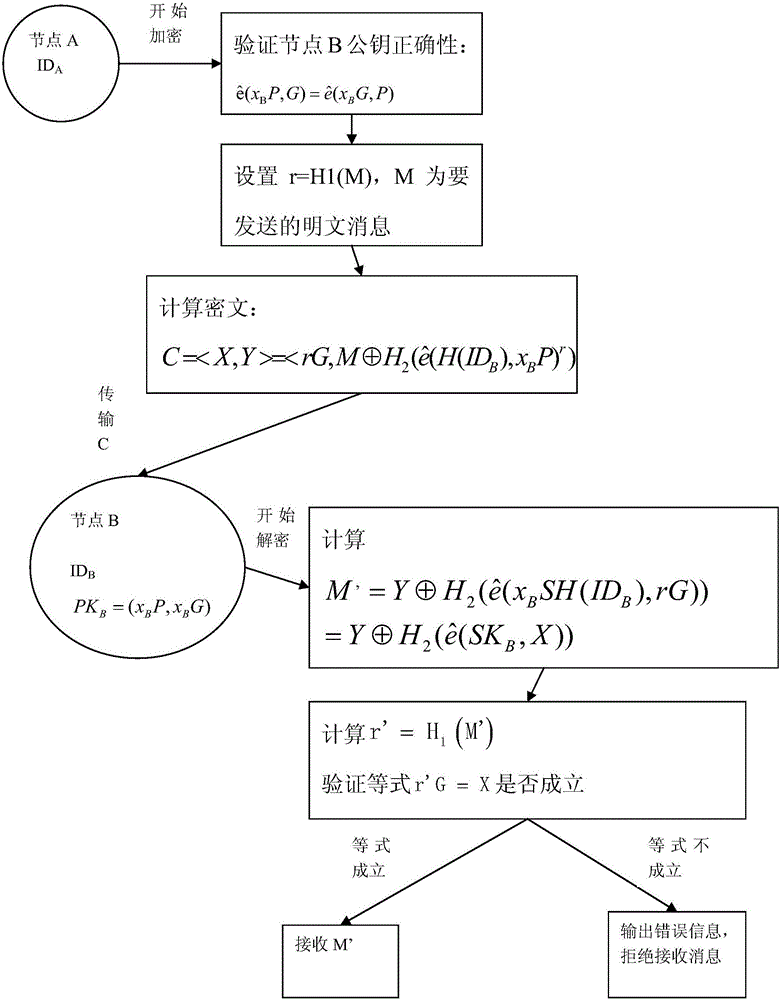
[0111] like figure 2 As shown, this embodiment implements key negotiation according to the following steps:
[0112] 1. Initialize the system network:
[0113] A reliable third-party TTP generates the necessary parameters in the network and informs all nodes in the network. The network initialization includes 5 steps:
[0114] 1) TTP selects a cyclic addition group G1 and a cyclic multiplication group G2, they have the same prime order q, through G1 and G2, construct a bilinear map: : G1×G1→G2;
[0115] 2) TTP arbitrarily selects a generator G of group G1;
[0116] 3) TTP selects th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com