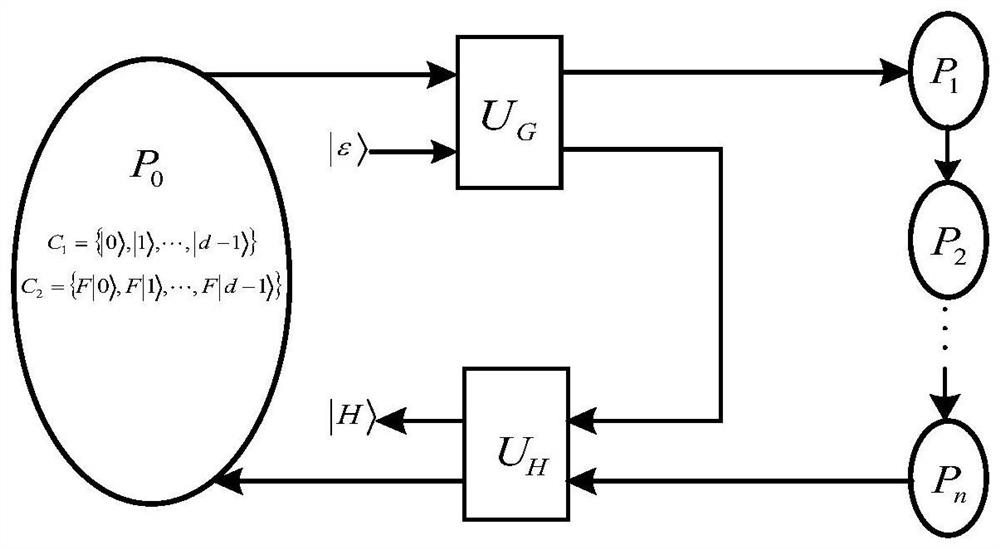
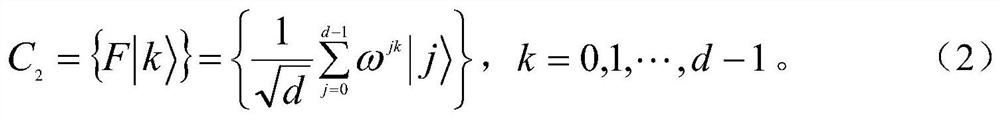A tree-type multi-party semi-quantum secret sharing method based on d-level single-particle states
A quantum secret, single-particle technology, applied in the field of quantum cryptography
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0157] 1. Application example of multi-party semi-quantum secret sharing method
[0158] Without loss of generality, after ignoring the particle transmission process and eavesdropping detection process, the secret m 1 Take as an example to illustrate the correctness of the method of the present invention.
[0159] in S j After the particles used for safe detection in (j=1,2,...,n) are discarded, S j There are only L particles left in . P 0 calculate
[0160]
[0161] Then, P 0 will her secret m 1 encrypted into and calculate Finally, P 0 to P 1 ,P 2 ,...,P n Publish M 1 and V 1 . P 1 ,P 2 ,...,P n Computing together
[0162]
[0163] According to M 1 , V 1 and H 1 , P 1 ,P 2 ,...,P n Through formula (24), the secret m can be recovered together 1 .
[0164]
[0165] It can now be concluded that the multi-party semi-quantum secret sharing method proposed by the present invention is correct. 2. Discussion and conclusion
[0166] In the meth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com