Quantum resource limited semi-quantum secret sharing method
A quantum secret and resource-constrained technology, applied in the field of semi-quantum secret sharing, can solve problems such as threats to people's privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] 1. Preparation stage:
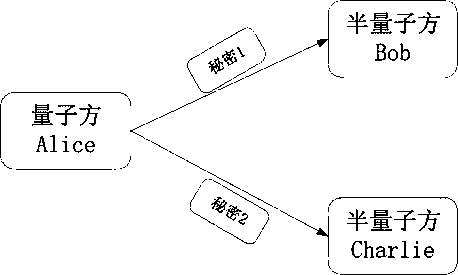
[0022] (1a) Alice randomly generates a string of binary numbers S, performs a specific operation on S and the secret string K she wants to share (for example, XORing the two strings), and obtains a string R;
[0023] (1b) Alice prepares 2N state, send N to Bob and the other N to Charlie.
[0024] 2. Sharing stage:
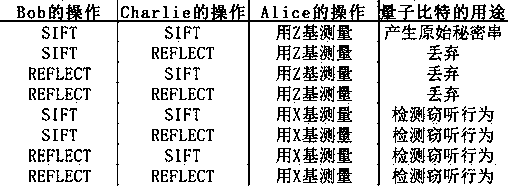
[0025] (2a) Bob receives the message sent by Alice After the state, randomly choose to execute the REFLECT operation or execute
[0026] SIFT operation. Charlie's operation is similar to Bob;
[0027] (2b) After receiving the qubits sent back by Bob and Charlie, Alice randomly chooses to use X-based or Z-based
[0028] Take measurements and record the results of the measurements and the measurement basis used for the corresponding location;
[0029] (2c) After Alice has measured all 2N qubits, she discloses the
[0030] base of measurement. Bob and Charlie disclose what they do to each qubit.
[0031] 3. Detection stage:...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com