Quantum secret sharing method and system based on differential phase shift
A quantum secret and differential phase shift technology, which is applied in transmission systems, digital transmission systems, and key distribution, can solve problems such as short transmission distance, poor security, and low coding rate, and achieve improved key coding rate and transmission distance , resist independent attacks, and highly operable
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
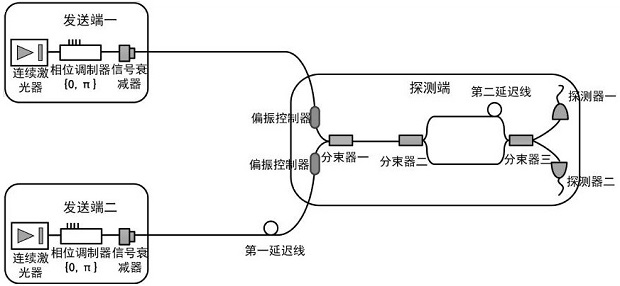
[0057] The three parties are Alice, Bob and Charlie. Wherein Alice and Bob have the same equipment, but the optical fiber distance from Alice to the beam splitter 1 used for beam combining is longer, so as to delay time. Both of them use CW lasers to generate phase-stabilized time-continuous pulsed optical signals. Phase encoding is performed by a phase modulator, phase modulation 0 corresponds to logic bit 0, and phase modulation Corresponds to logic bit 1. Both of them send quantum states with a period of 2 nanoseconds (ns). The moment when Alice arrives at beam splitter 1 is longer than the relaxation time of Bob’s signal T. They are respectively adjusted to two beams with the same polarization direction by polarization controller 1 and polarization controller 2. After the light pulses are combined by a beam splitter, the beams are sent to the detection end Charlie.
[0058] Charlie's beam splitter 2 and beam splitter 3 constitute an unbalanced Mach-Zehnder interferomet...
Embodiment 2
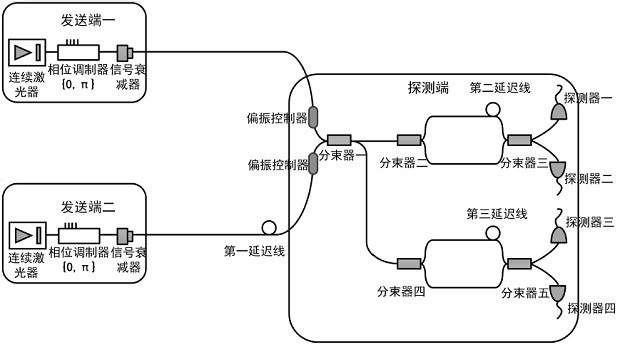
[0066] In Embodiment 1, beam splitter 1 is used to combine beams, and only pulses from one port are used, which wastes half of the photons that can be used for coding.
[0067] combine figure 2 , compared with Embodiment 1, this embodiment also adds a set of detection units that are the same as the detection end in Embodiment 1 at the other port of beam splitter 1. The probability of two sets of detection units responding at the same time is very small and can be ignored. The specific operation is the same as that in Embodiment 1. In this way, the number of photons is effectively utilized, and the efficiency is nearly doubled compared with the first embodiment.
Embodiment 3
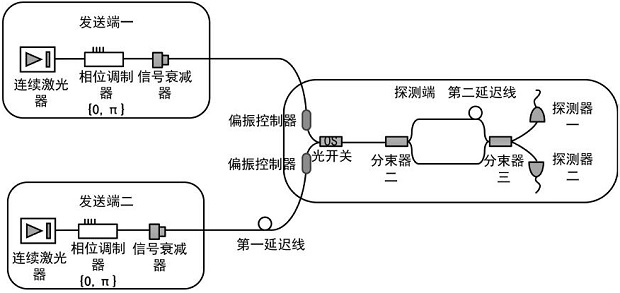
[0069] In the second embodiment, too many devices are used and the operation is relatively complicated. In this embodiment, the beam splitter 1 used for beam combining is replaced with an optical switch. An optical switch combines two optical pulses into a single-mode fiber.
[0070] combine image 3 , Alice and Bob send weakly coherent states with the same polarization direction. Since the pulses sent by Alice and Bob are one after the other in one cycle, when an optical pulse reaches the optical switch, the optical switch will let it pass, so that the two A beam of light pulses is combined into a single-mode fiber. The rest of the operations are the same as in the first embodiment, and the coding rate in the third embodiment is the highest compared with the first and second embodiments.
[0071] To sum up, quantum secret sharing is performed according to the image in Embodiment 3, and the final coding rate is calculated according to the following formula:
[0072]
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com