Patents
Literature
70 results about "Workaround" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A workaround is a bypass of a recognized problem or limitation in a system. A workaround is typically a temporary fix that implies that a genuine solution to the problem is needed. But workarounds are frequently as creative as true solutions, involving outside the box thinking in their creation.
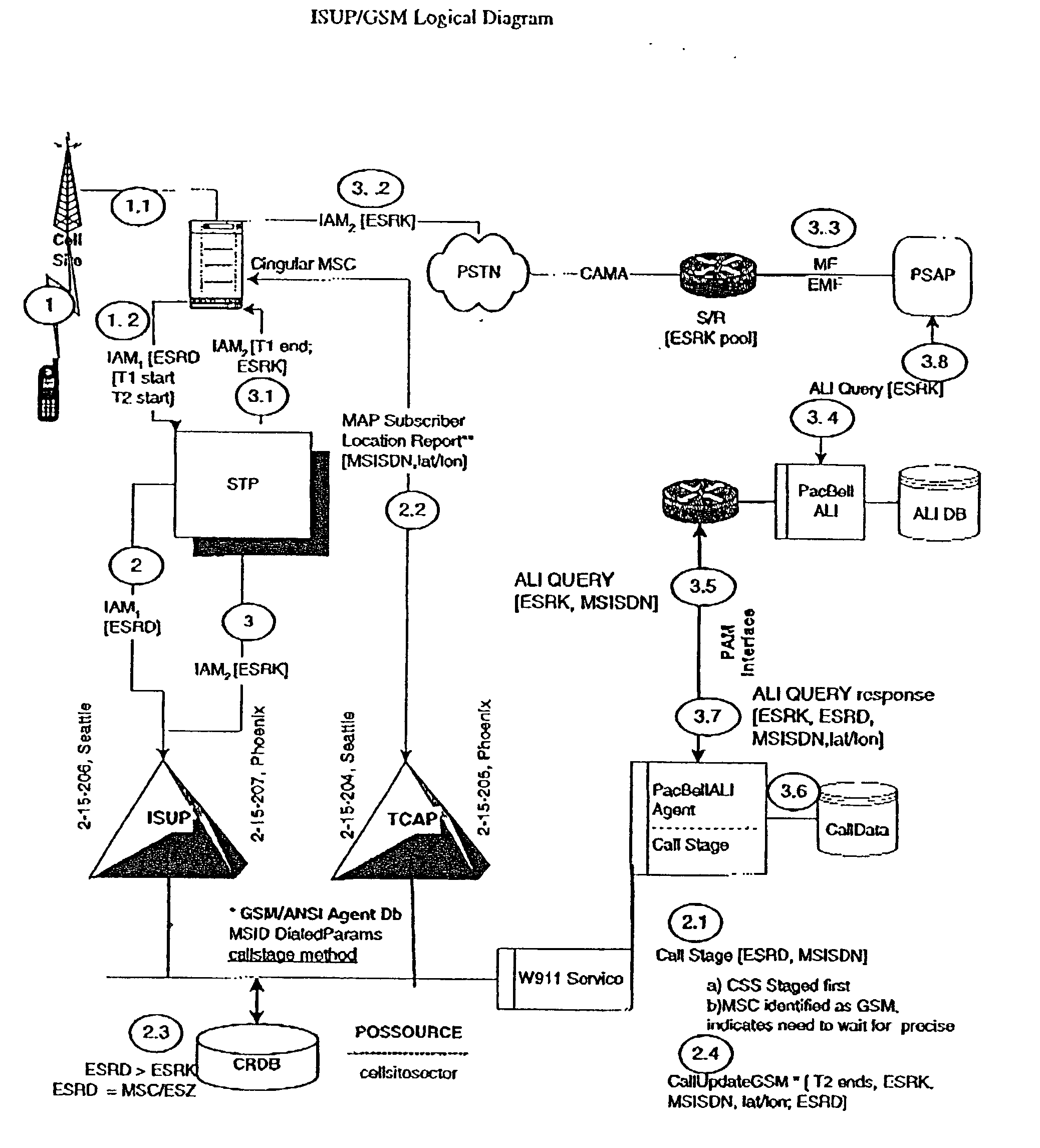
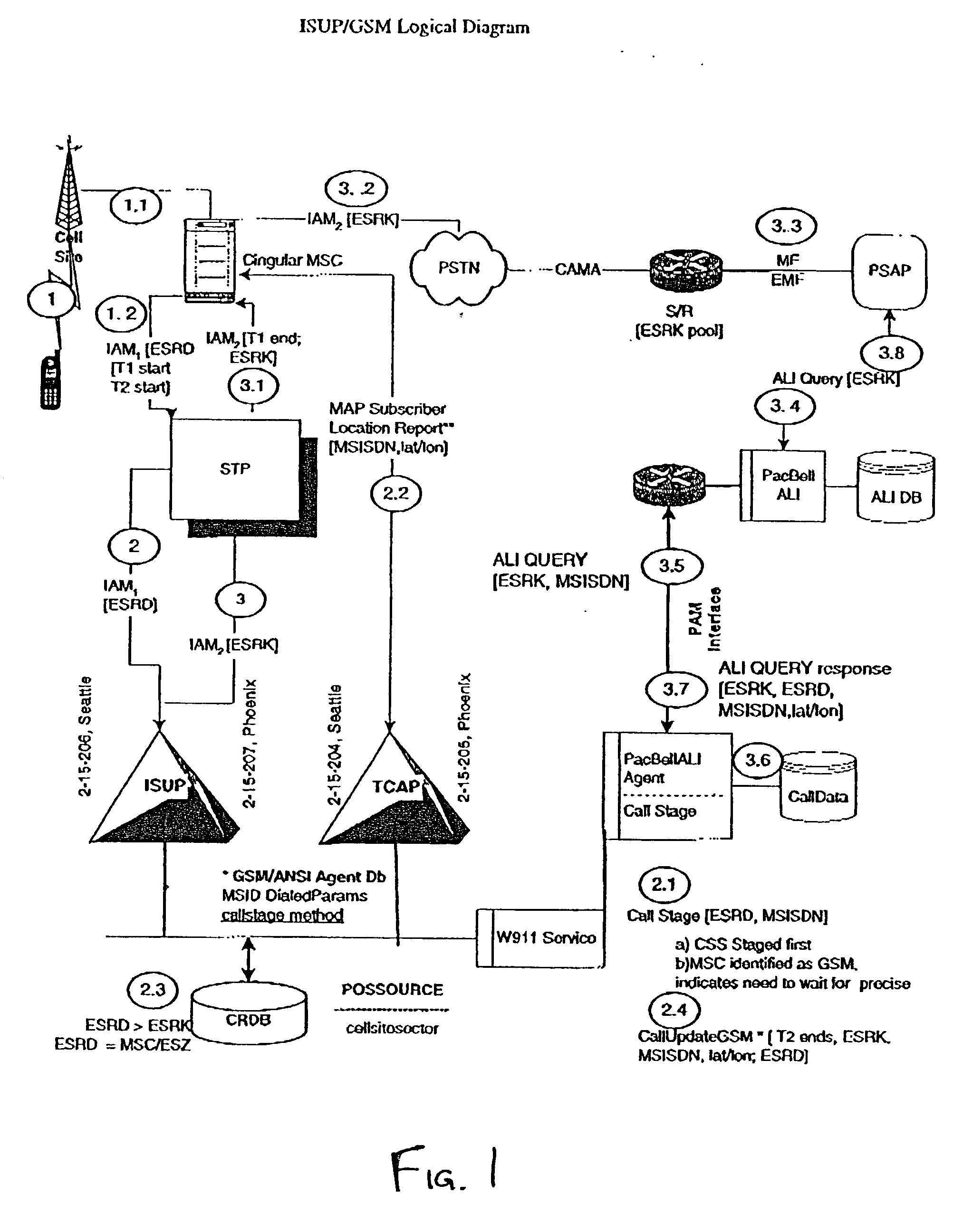
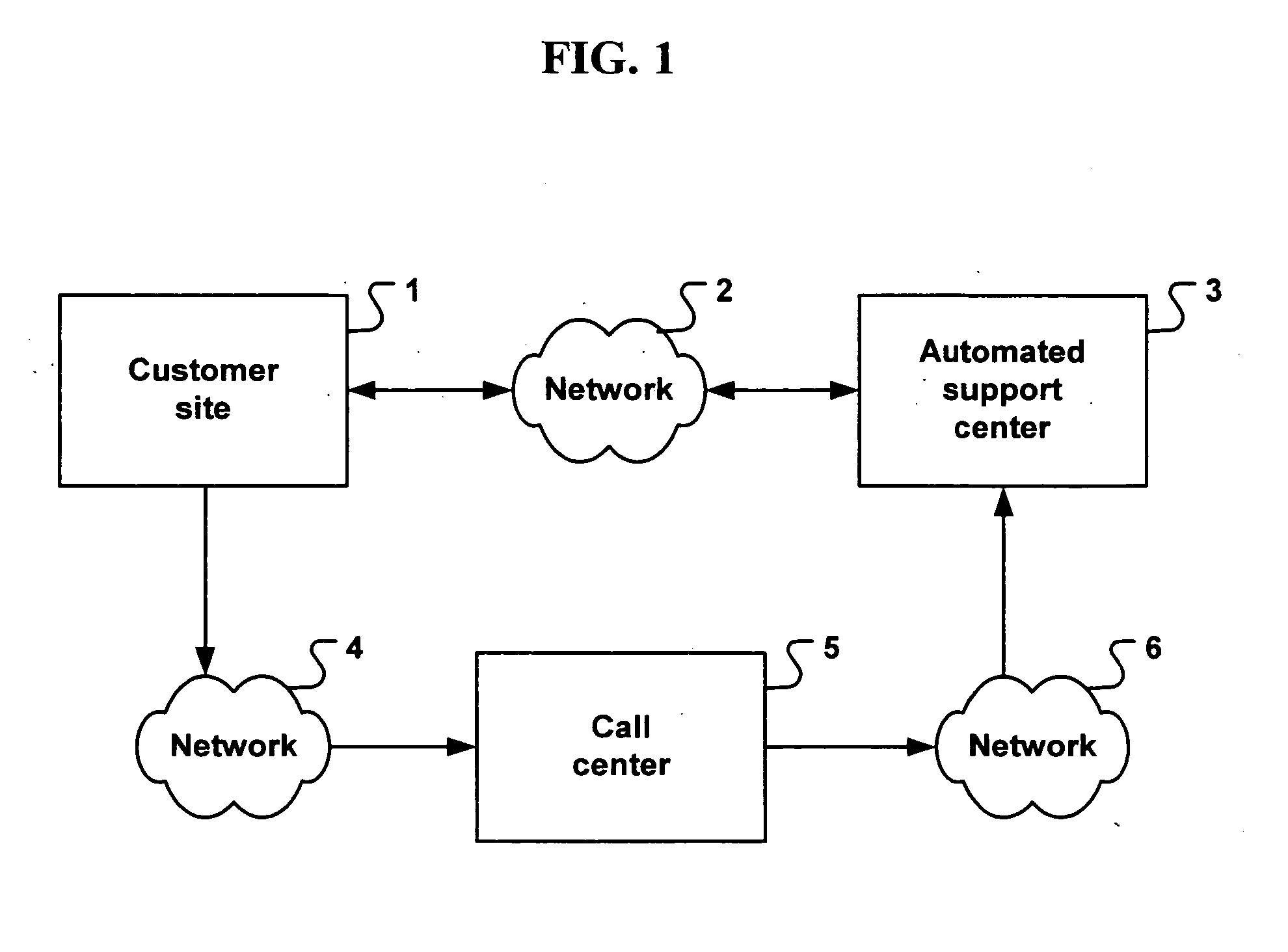
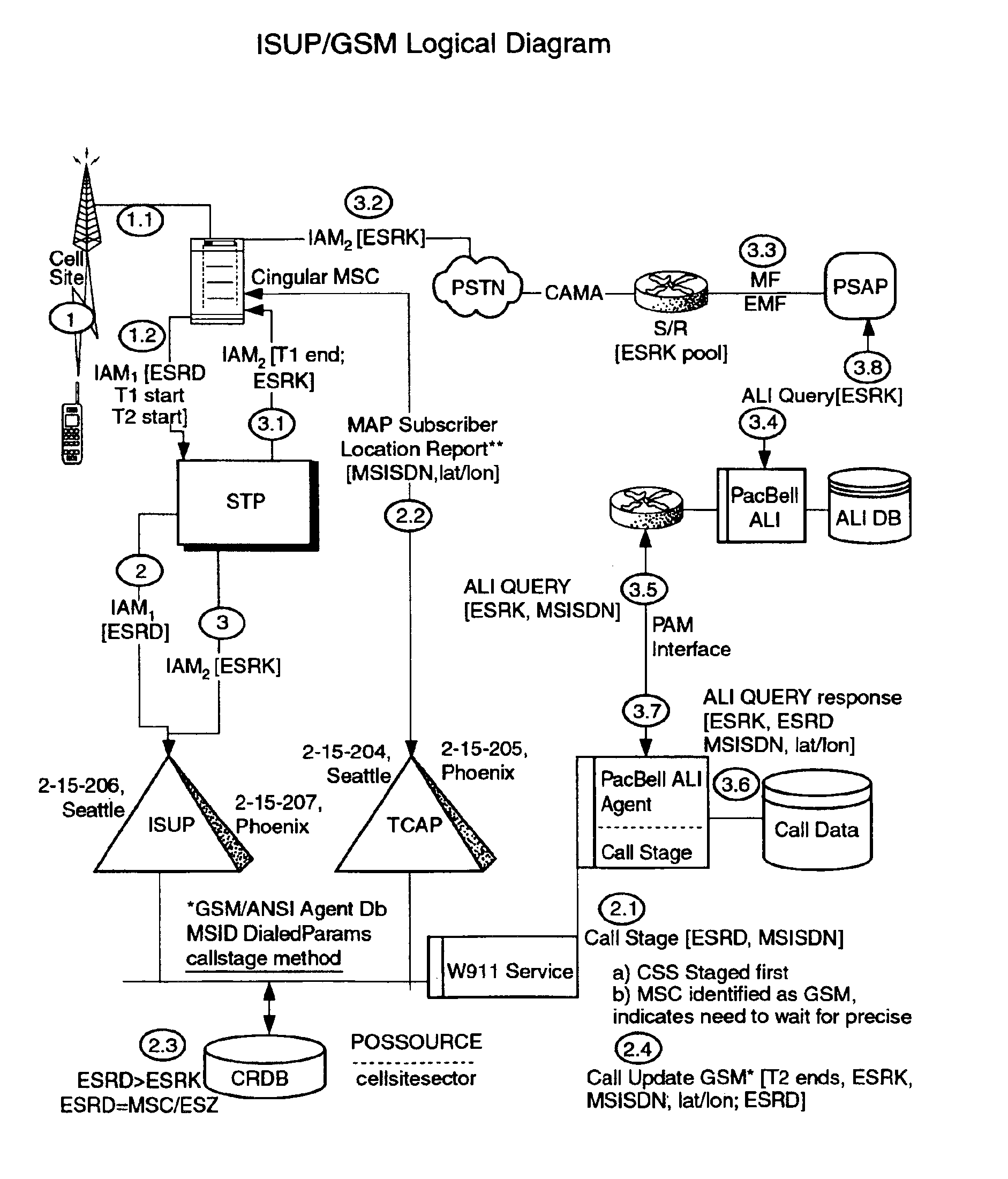
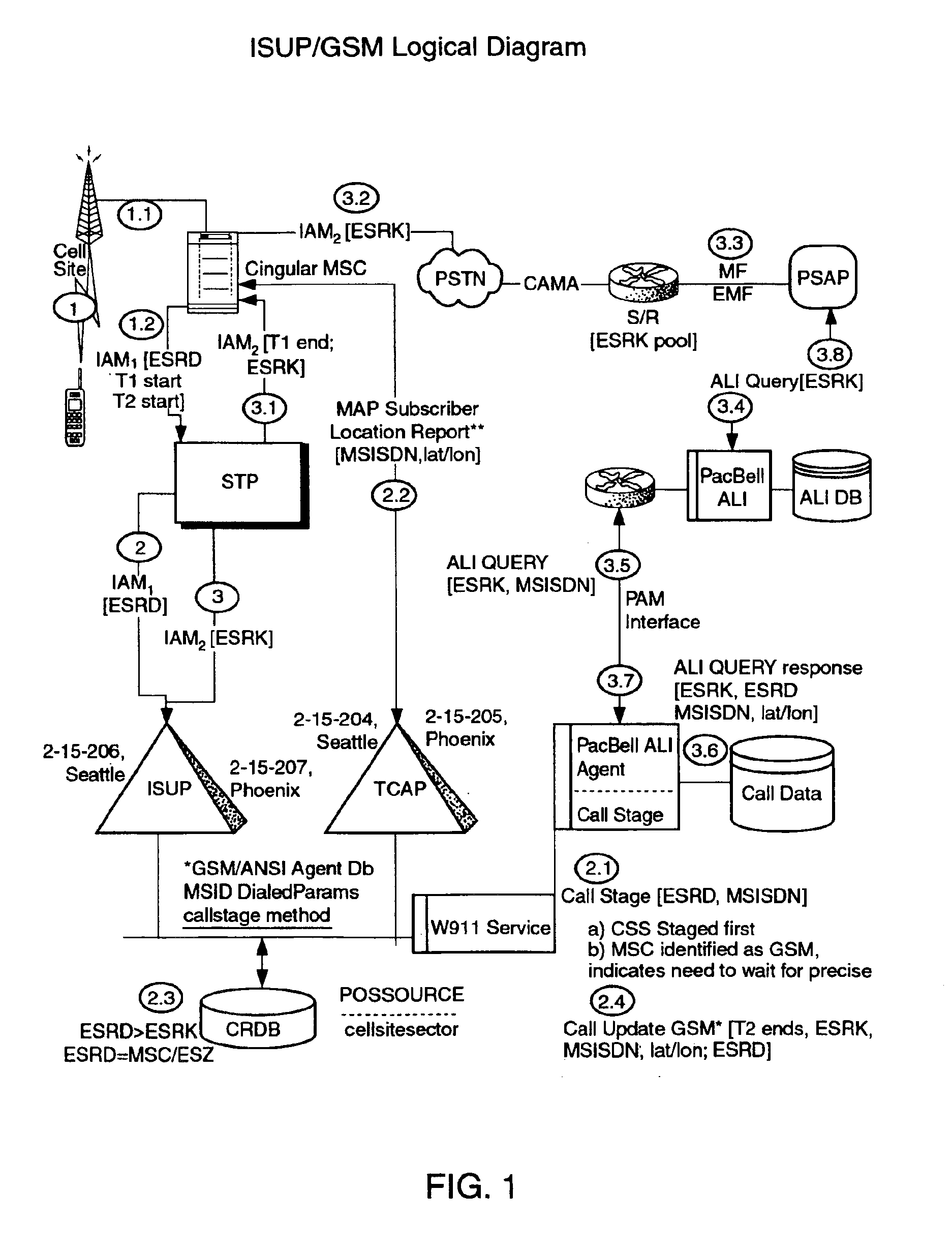
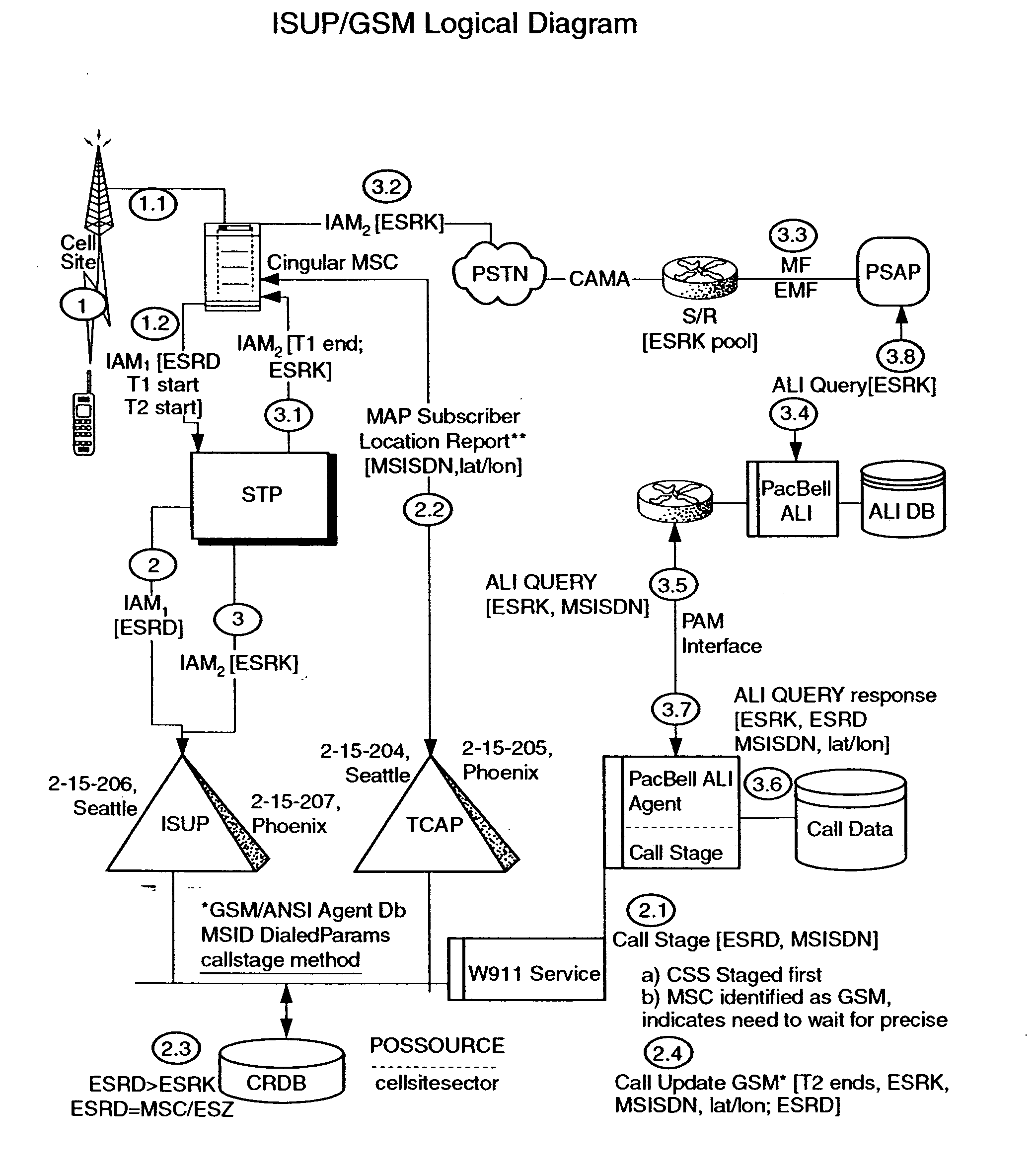
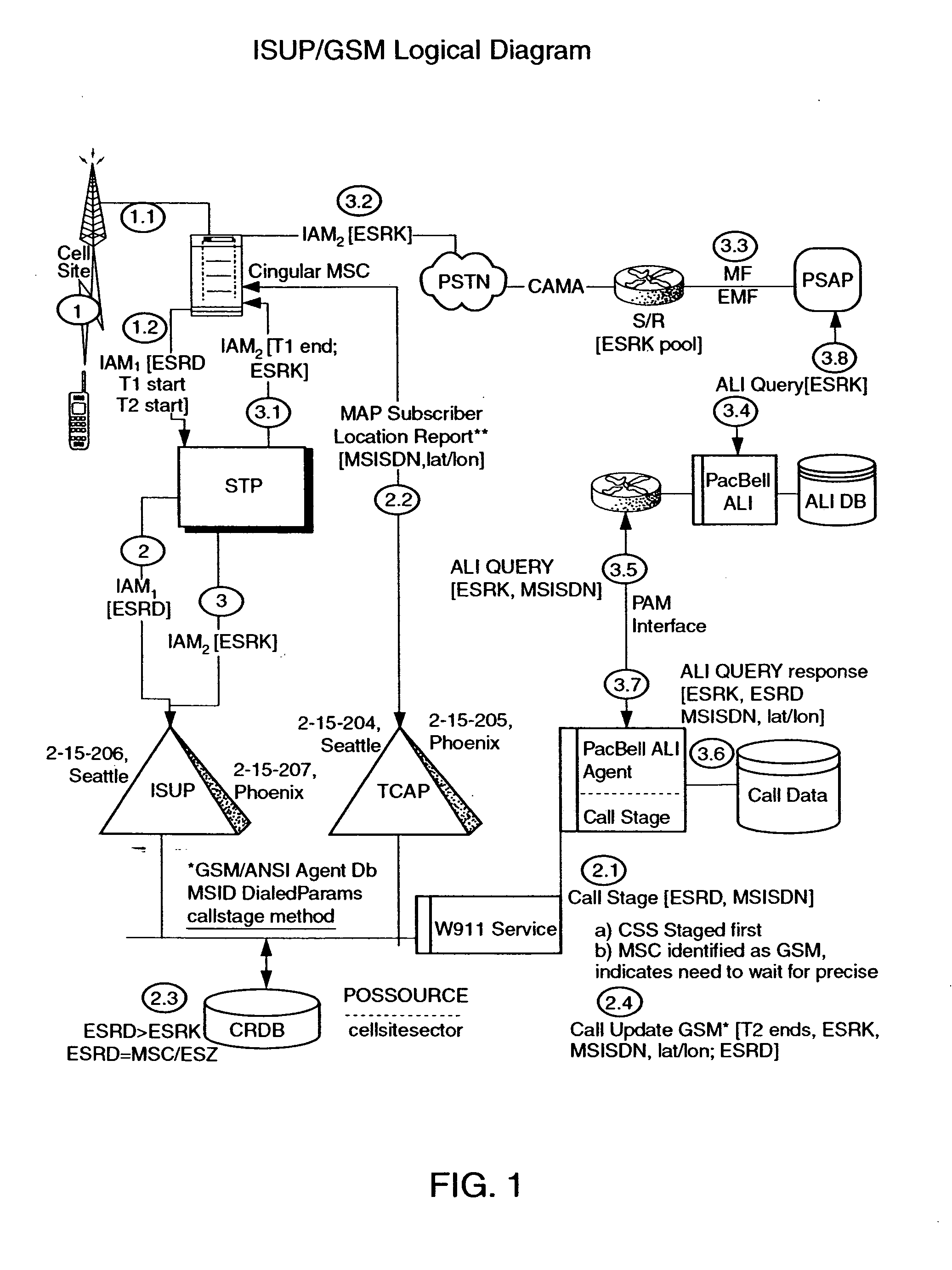
Public safety access point (PSAP) selection for E911 wireless callers in a GSM type system
Public safety access points are selected in a wireless network for E911 calls based on ESRD substitution when ESRKs are not being used. The present invention was conceived as an ESRK workaround solution to implement Phase II of the E911 rules from the starting point of a Phase I implementation. ESRKs, ESRDs or ESRVs are initially obtained and managed for each PSAP in a particular carrier's area. Then, Phase I processes are modified to wait to see if Phase II GSM location information will be reported in a timely manner (e.g., within a second or two or so) before committing to a default selection of a particular PSAP based on information available (e.g., based on the location of a serving cell site).
Owner:TELECOMM SYST INC
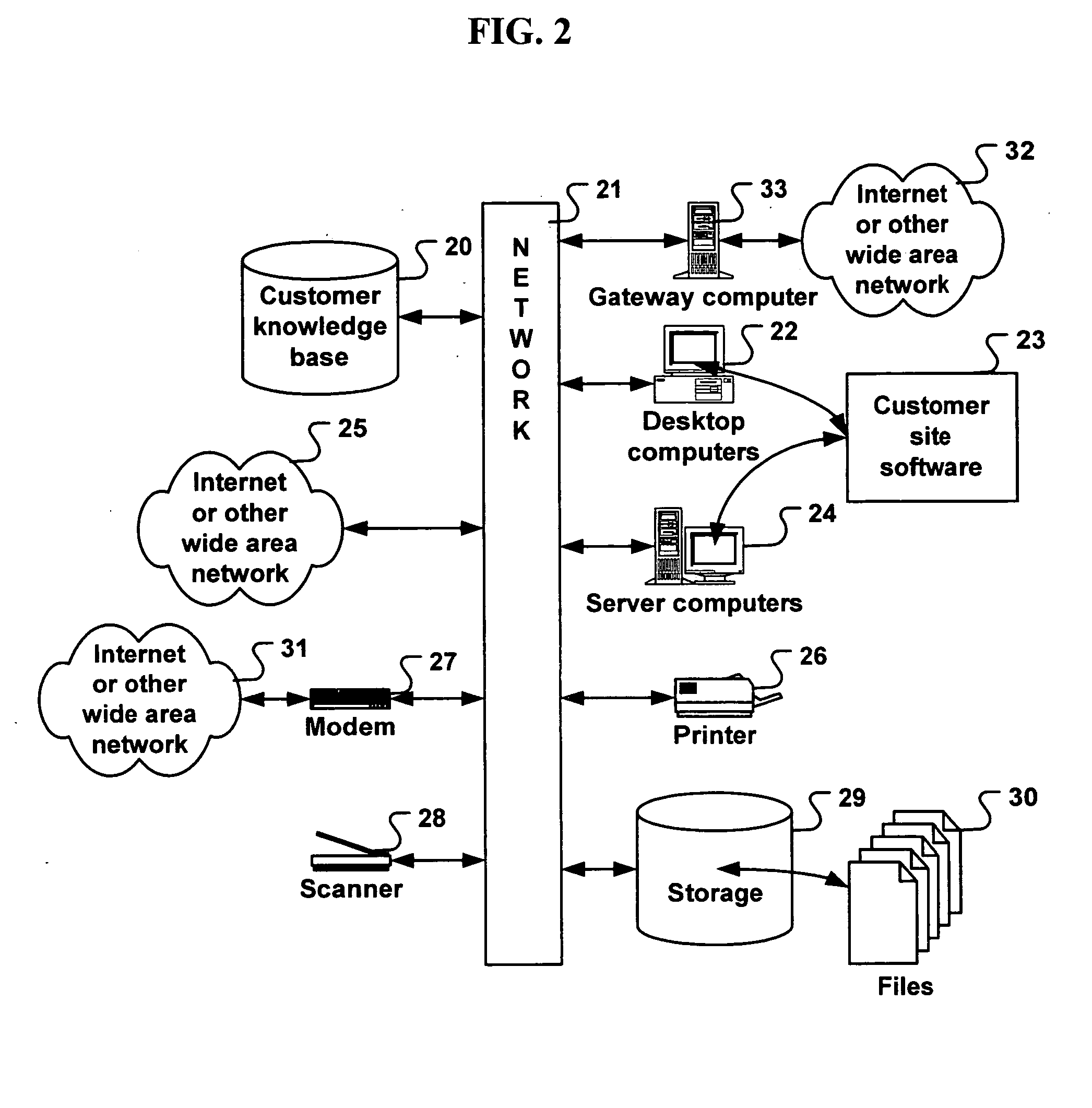
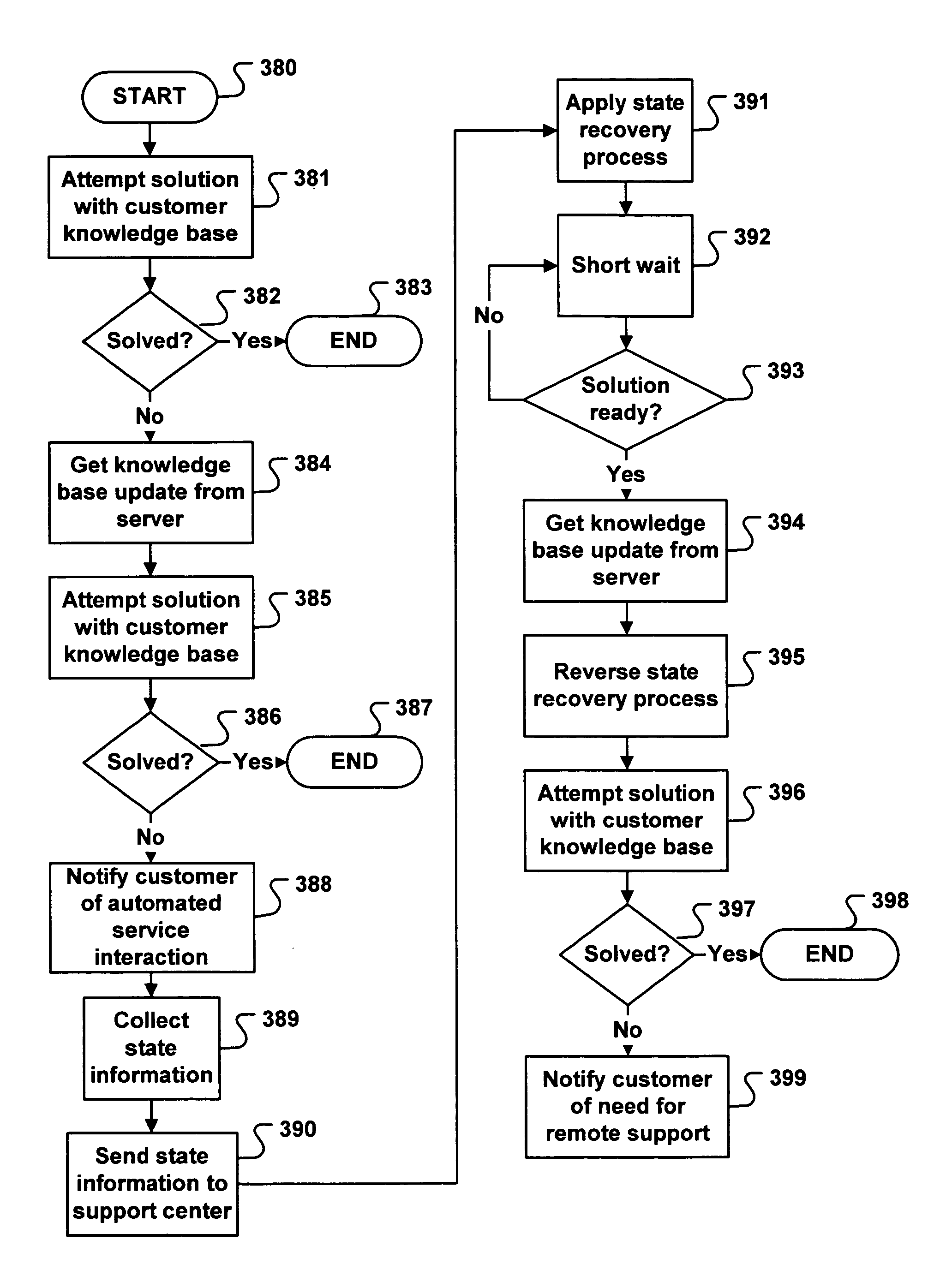
System for automated problem detection, diagnosis, and resolution in a software driven system
InactiveUS20050015678A1Guaranteed uptimeEasy to understandFault responseDetecting faulty hardware by remote testTheoretical computer scienceInstability
In many systems, computer software is a common source of failure or instability. The proliferation of multiple interacting applications from several different software vendors leads to “emergent” problems that are difficult or impossible to predict or prevent. The problems are compounded by the use of networks, which introduce the added complexity of applications on multiple machines interacting in complex scenarios. As a result, many business and home users are hindered from using software-based systems to their fullest potential. More effective use of these systems can be aided by an application which can provide services for monitoring, diagnosing, and solving problems that occur in the operation of the machines at a customer facility. In the system described herein, a database contains entries with executable code that can make use of these services in order to monitor, diagnose, and solve specific problems. Each entry in the database addresses a specific problem. The executable code is designed to isolate and recognize the problem, and then implement a fix or workaround for that problem. The executable code is designed to completely automate the entire process of detection and resolution of the problem. Further, manual intervention may be employed to complete the diagnosis or solution.
Owner:HFN LLC
Public safety access point (PSAP) selection for E911 wireless callers in a GSM type system
Public safety access points are selected in a wireless network for E911 calls based on ESRD substitution when ESRKs are not being used. The present invention was conceived as an ESRK workaround solution to implement Phase II of the E911 rules from the starting point of a Phase I implementation. ESRKs, ESRDs or ESRVs are initially obtained and managed for each PSAP in a particular carrier's area. Then, Phase I processes are modified to wait to see if Phase II GSM location information will be reported in a timely manner (e.g., within a second or two or so) before committing to a default selection of a particular PSAP based on information available (e.g., based on the location of a serving cell site).
Owner:TELECOMM SYST INC
System for automated problem detection, diagnosis, and resolution in a software driven system
InactiveUS7100085B2Simple interfaceEffortless and reliable and affordable supportFault responseDetecting faulty hardware by remote testInstabilityTheoretical computer science
In many systems, computer software is a common source of failure or instability. The proliferation of multiple interacting applications from several different software vendors leads to “emergent” problems that are difficult or impossible to predict or prevent. The problems are compounded by the use of networks, which introduce the added complexity of applications on multiple machines interacting in complex scenarios. As a result, many business and home users are hindered from using software-based systems to their fullest potential. More effective use of these systems can be aided by an application which can provide services for monitoring, diagnosing, and solving problems that occur in the operation of the machines at a customer facility. In the system described herein, a database contains entries with executable code that can make use of these services in order to monitor, diagnose, and solve specific problems. Each entry in the database addresses a specific problem. The executable code is designed to isolate and recognize the problem, and then implement a fix or workaround for that problem. The executable code is designed to completely automate the entire process of detection and resolution of the problem. Further, manual intervention may be employed to complete the diagnosis or solution.
Owner:HFN LLC
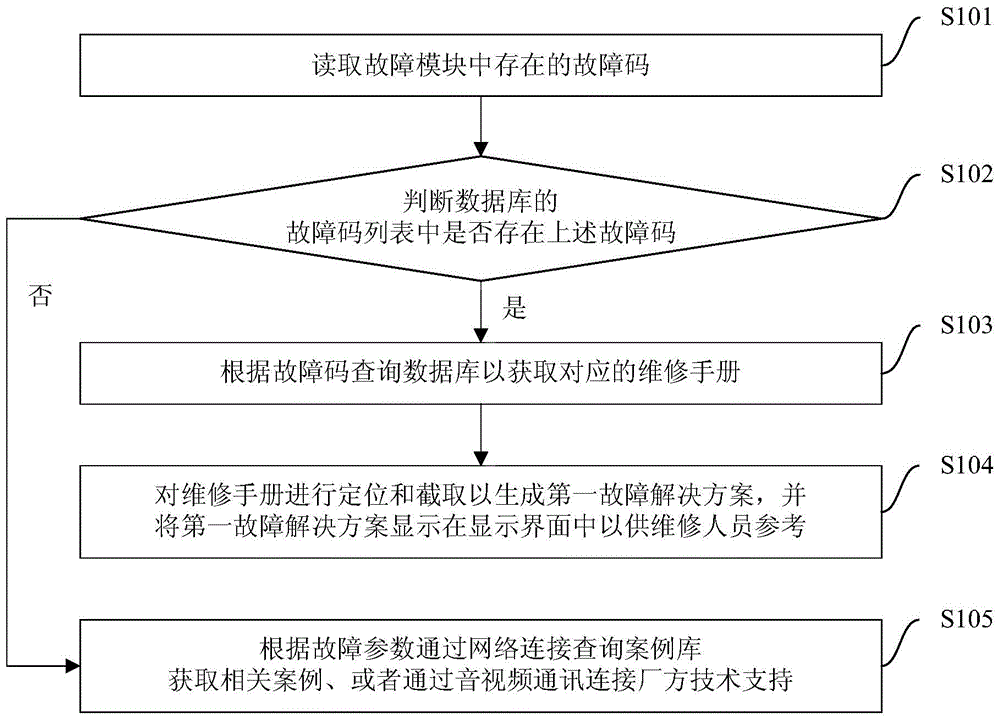
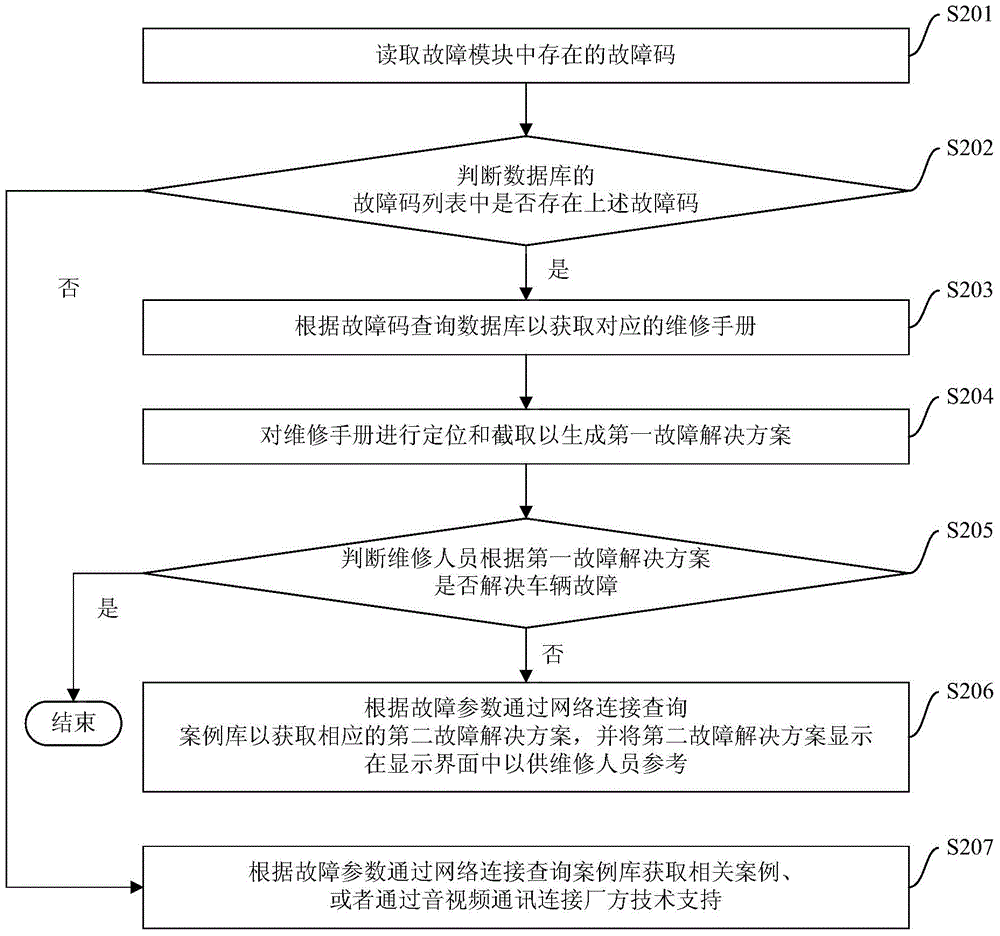
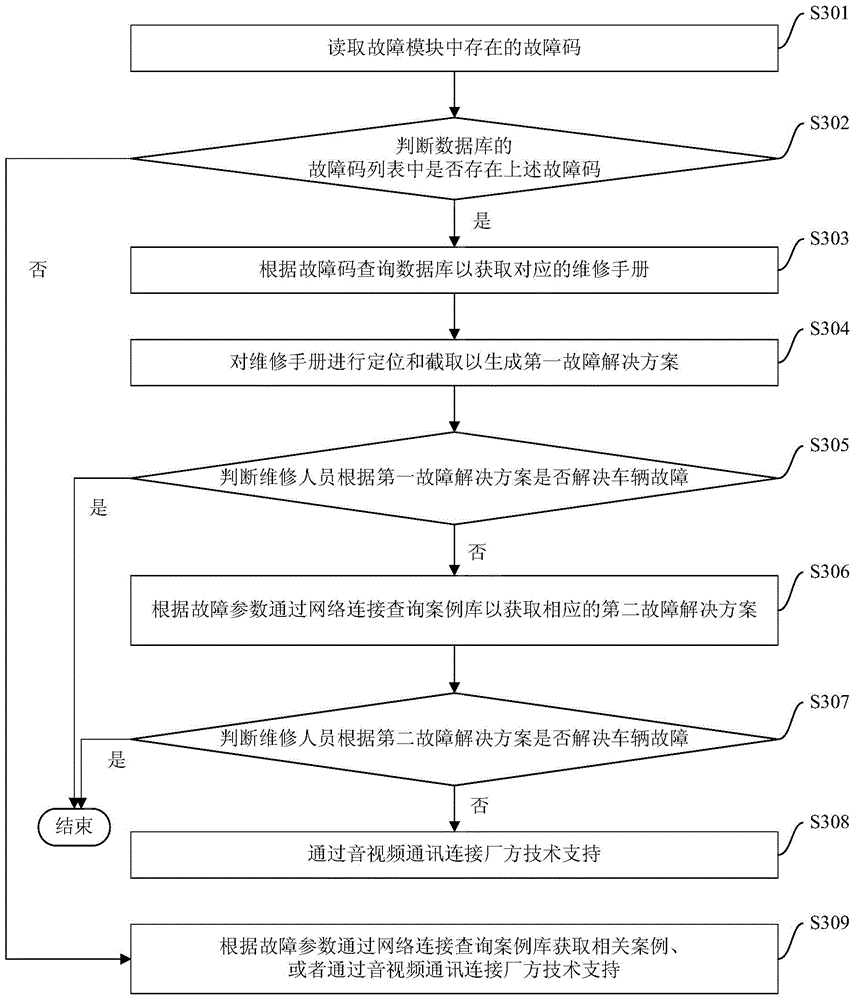
Vehicle fault solution method and device
InactiveCN104460644AReduce manual laborImprove maintenance efficiencyElectric testing/monitoringUsabilityWorkaround
The invention provides a vehicle fault solution method and device. The vehicle fault solution method comprises the steps of reading a fault code existing in a fault module, judging whether the fault code exists in a fault code list of a database or not, querying the fault code in the database to obtain a corresponding service manual if the fault code exists in the fault code list, positioning and intercepting the service manual to generate a first fault solution and displaying the first fault solution on a display interface for reference of a maintainer. According to the vehicle fault solution method, automatic obtaining of the fault solutions is achieved, maintenance efficiency is improved, sharing of the fault solutions is achieved, obtaining approaches of the solutions for difficult faults are increased, and usability is improved.
Owner:BYD CO LTD
Public safety access point (PSAP) selection for E911 wireless callers in a GSM type system
Owner:TELECOMM SYST INC
Mini-refresh processor recovery as bug workaround method using existing recovery hardware
InactiveUS20060184771A1Plurality of obstructionOptimize performance impactDigital computer detailsMemory systemsData processing systemData treatment
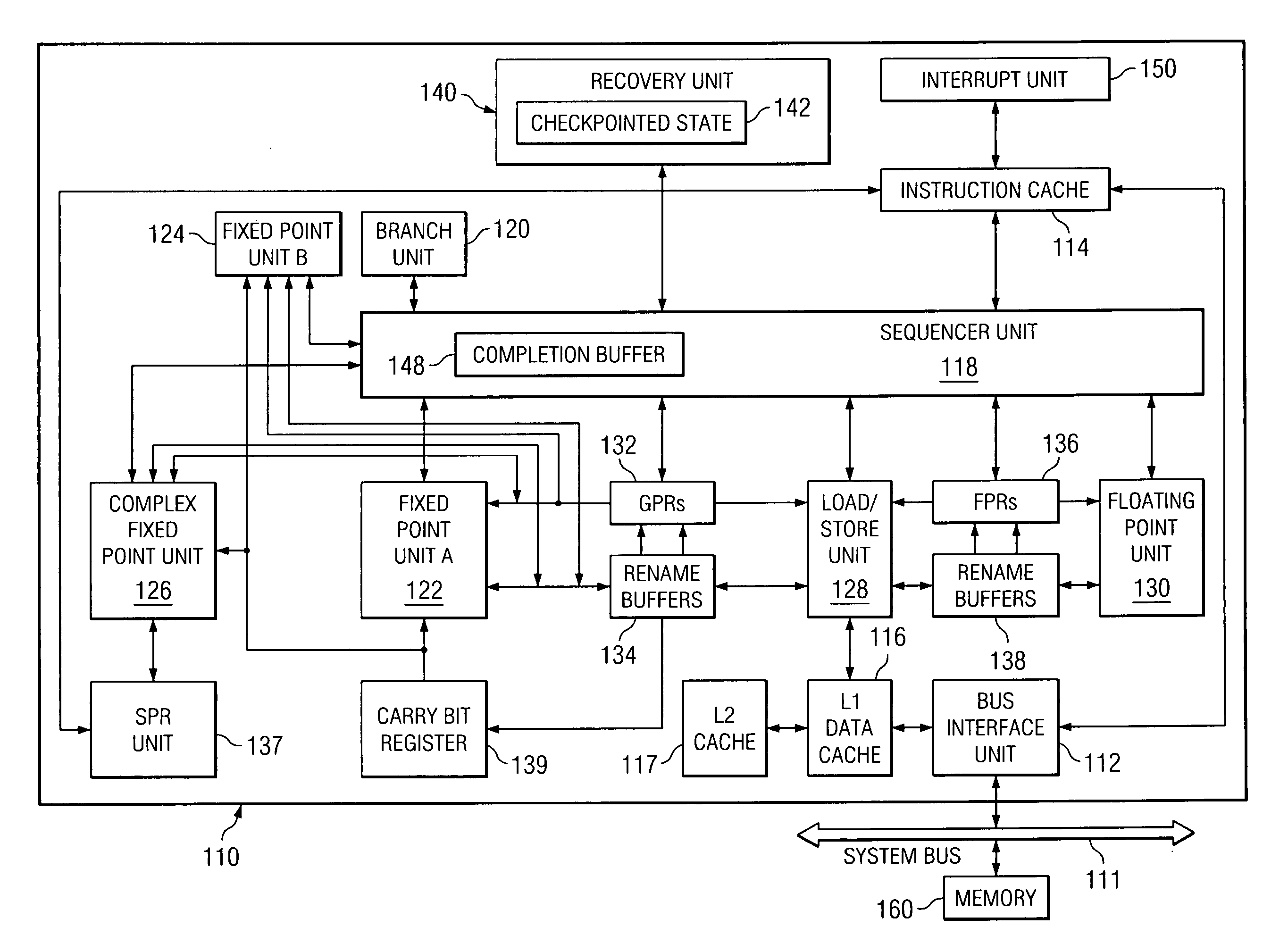
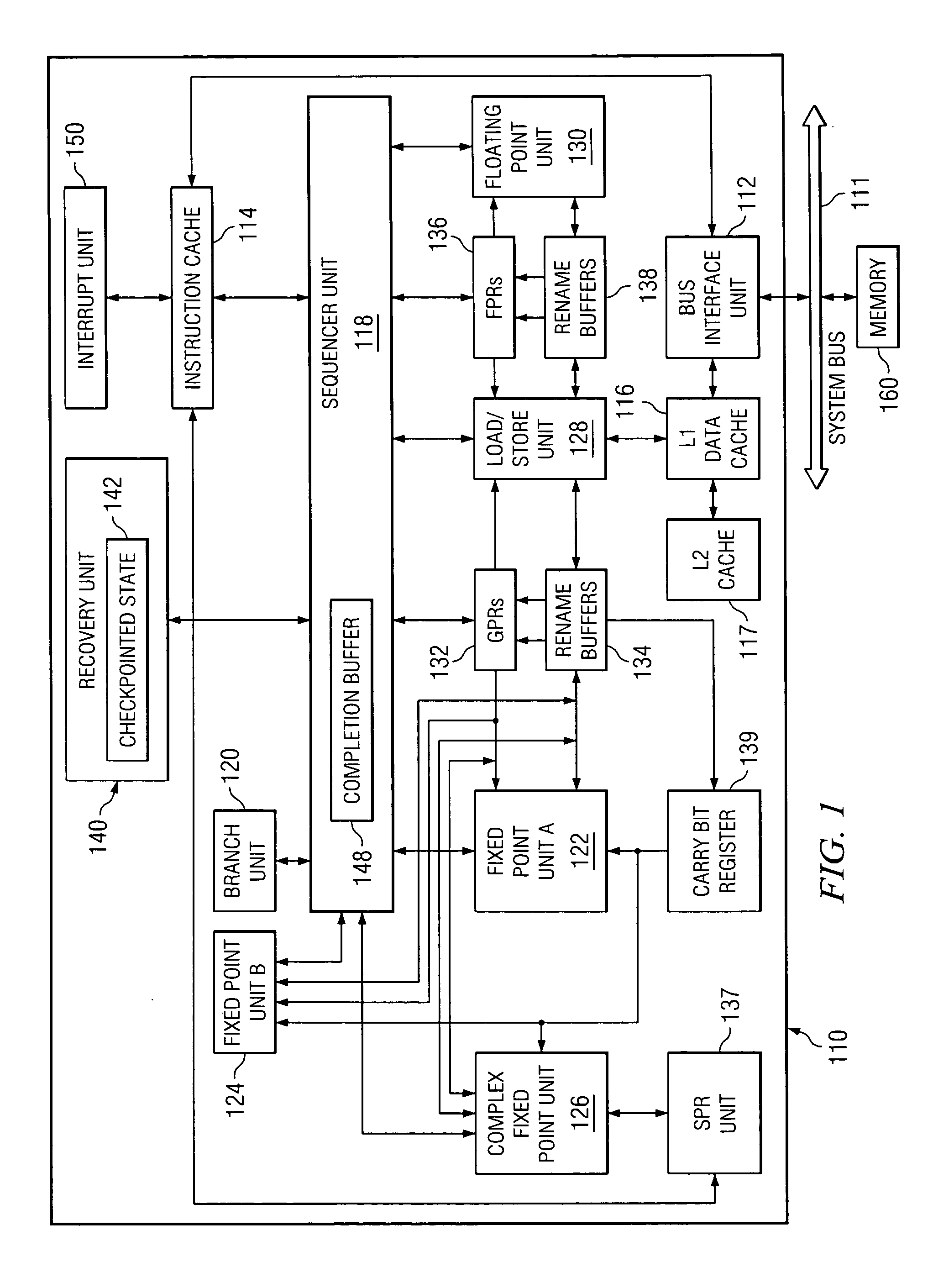
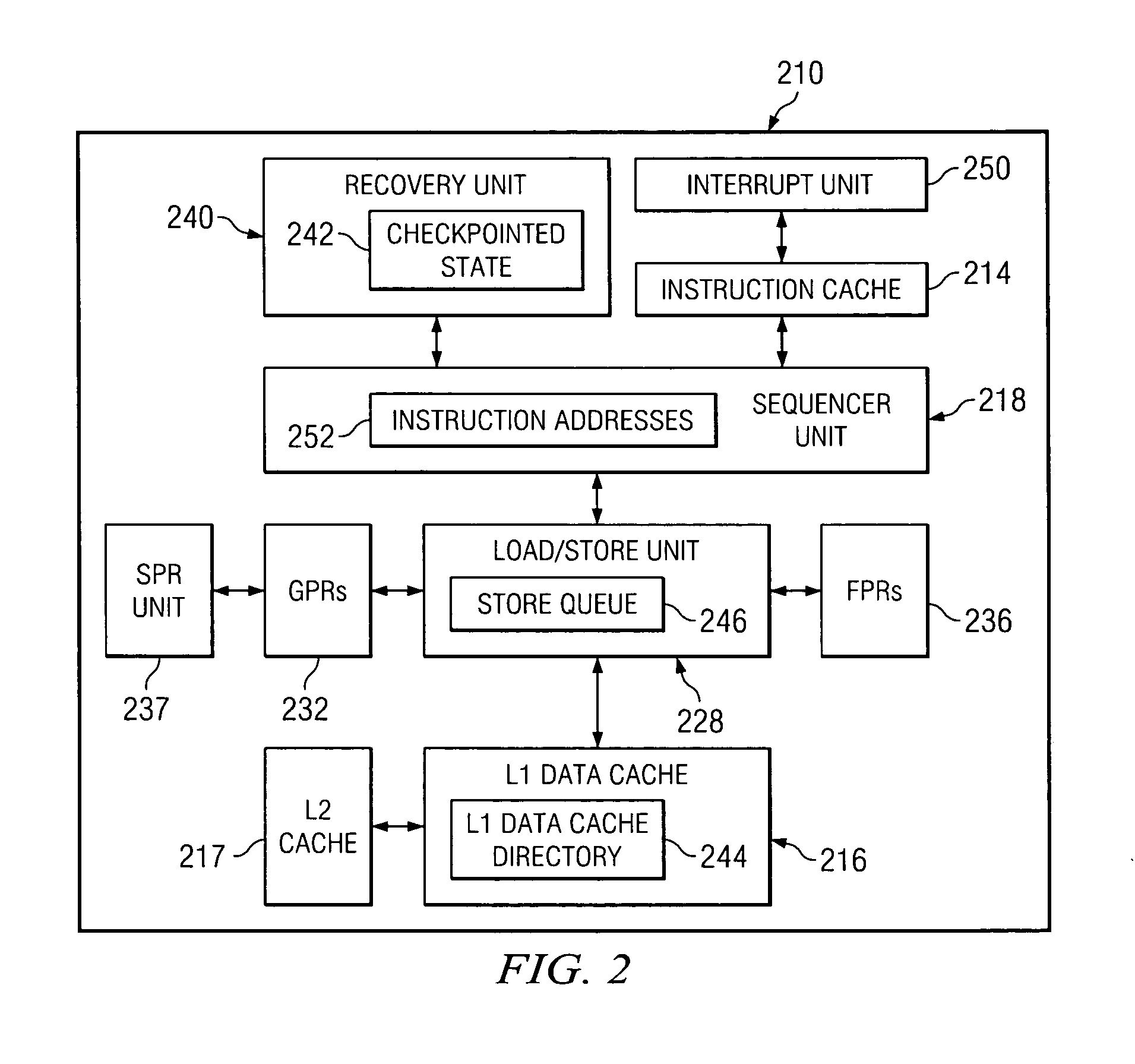
A method in a data processing system for avoiding a microprocessor's design defects and recovering a microprocessor from failing due to design defects, the method comprised of the following steps: The method detects and reports of events which warn of an error. Then the method locks a current checkpointed state and prevents instructions not checkpointed from checkpointing. After that, the method releases checkpointed state stores to a L2 cache, and drops stores not checkpointed. Next, the method blocks interrupts until recovery is completed. Then the method disables the power savings states throughout the processor. After that, the method disables an instruction fetch and an instruction dispatch. Next, the method sends a hardware reset signal. Then the method restores selected registers from the current checkpointed state. Next, the method fetches instructions from restored instruction addresses. Then the method resumes a normal execution after a programmable number of instructions.
Owner:IBM CORP
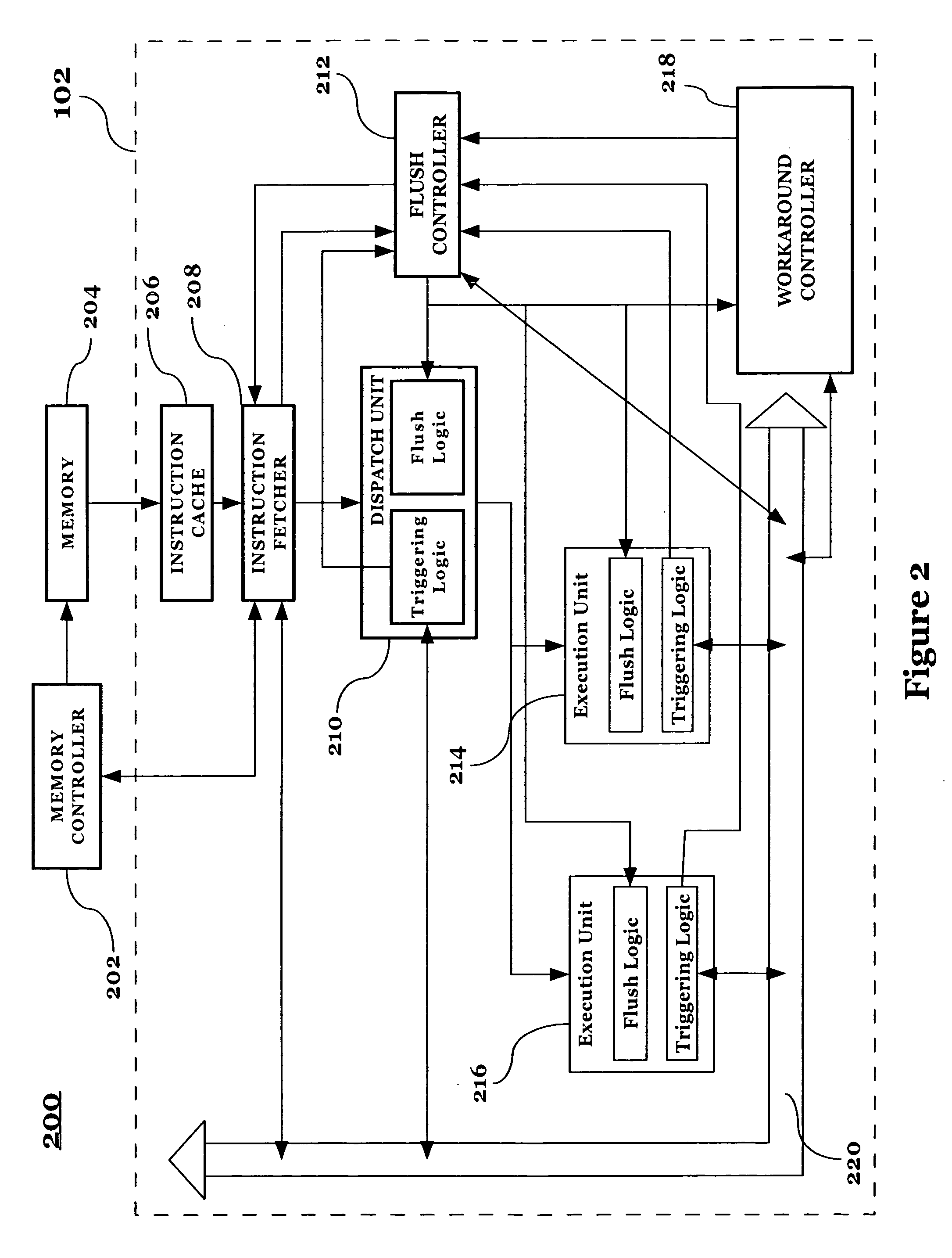
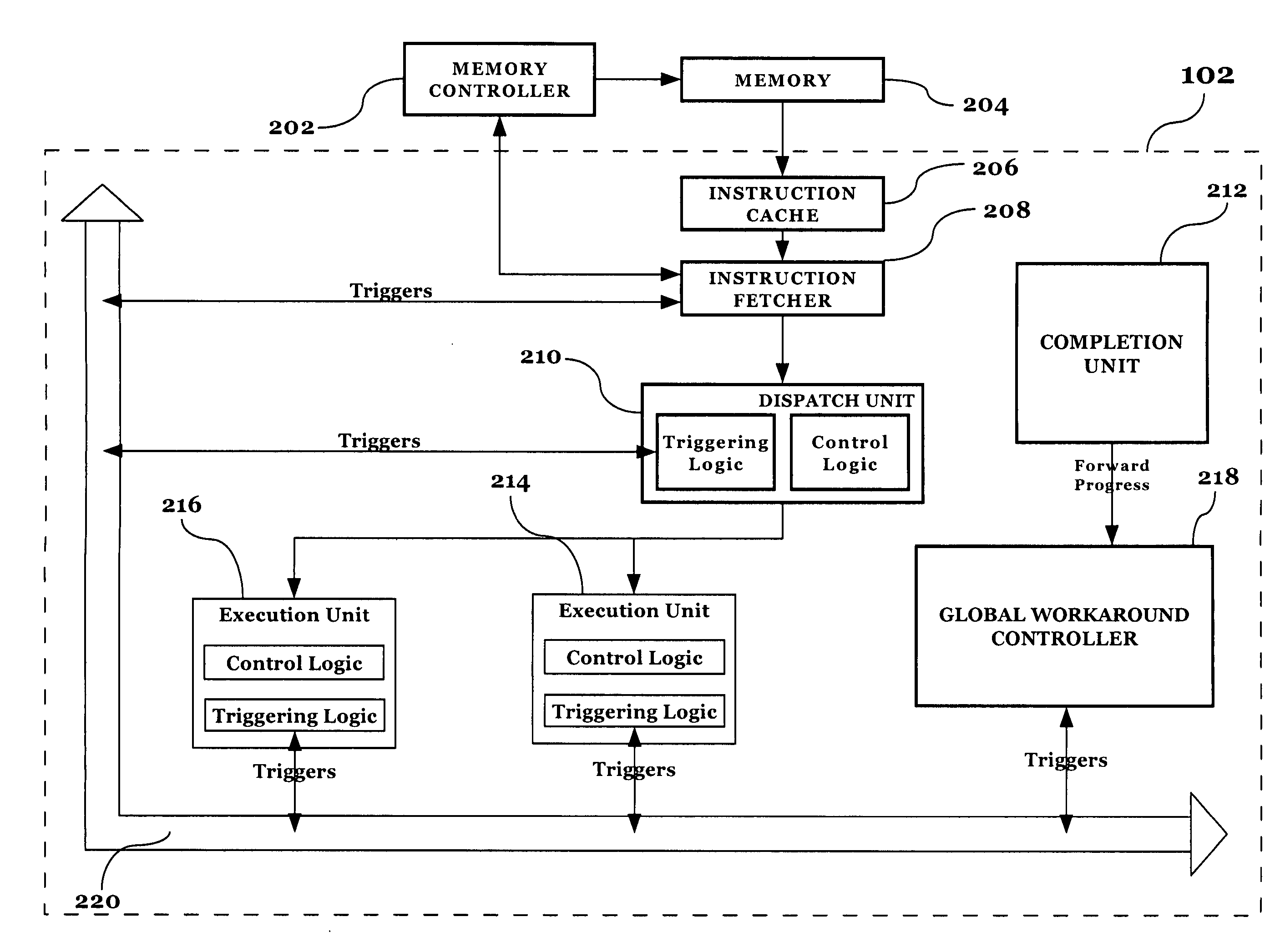
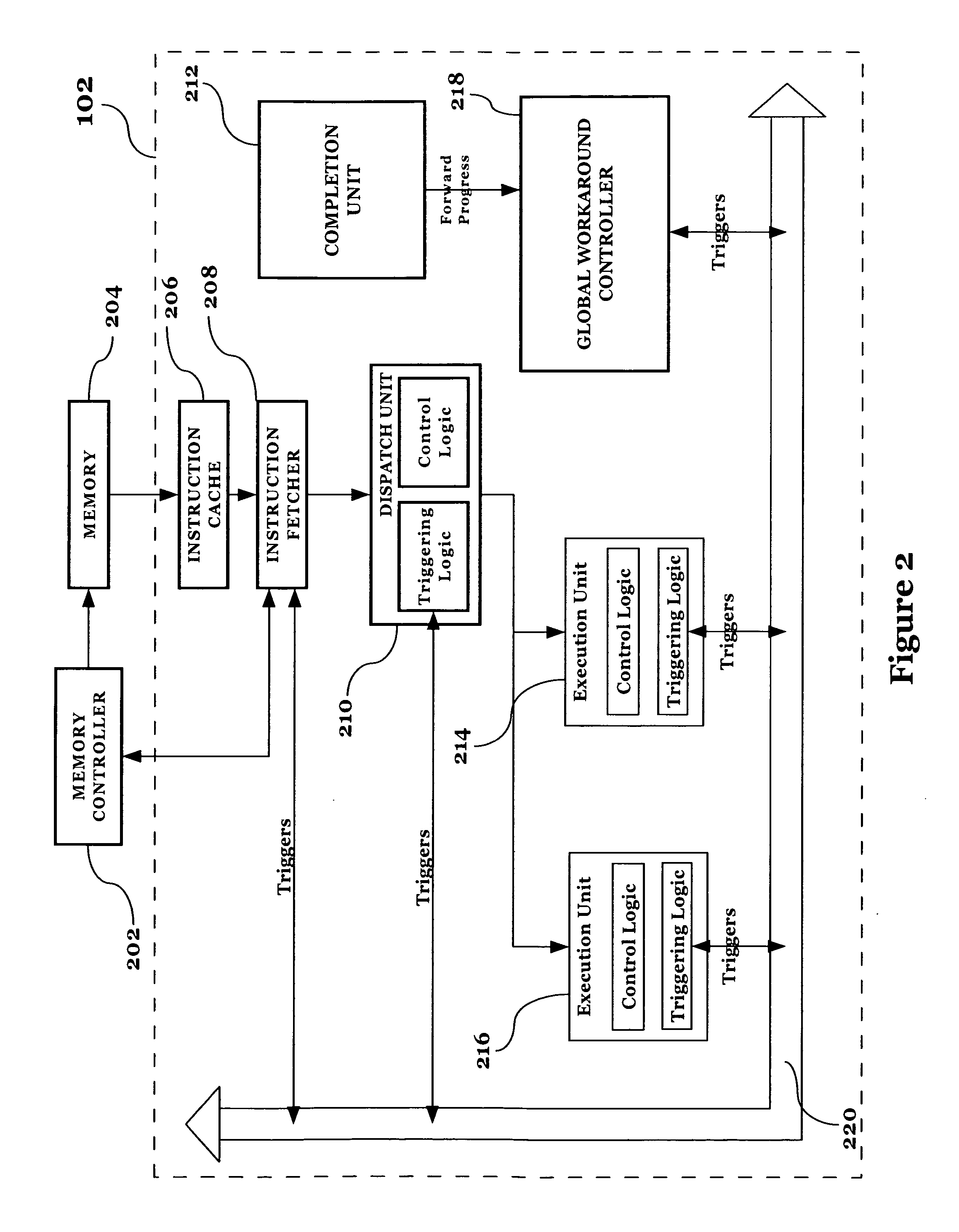
Localized generation of global flush requests while guaranteeing forward progress of a processor
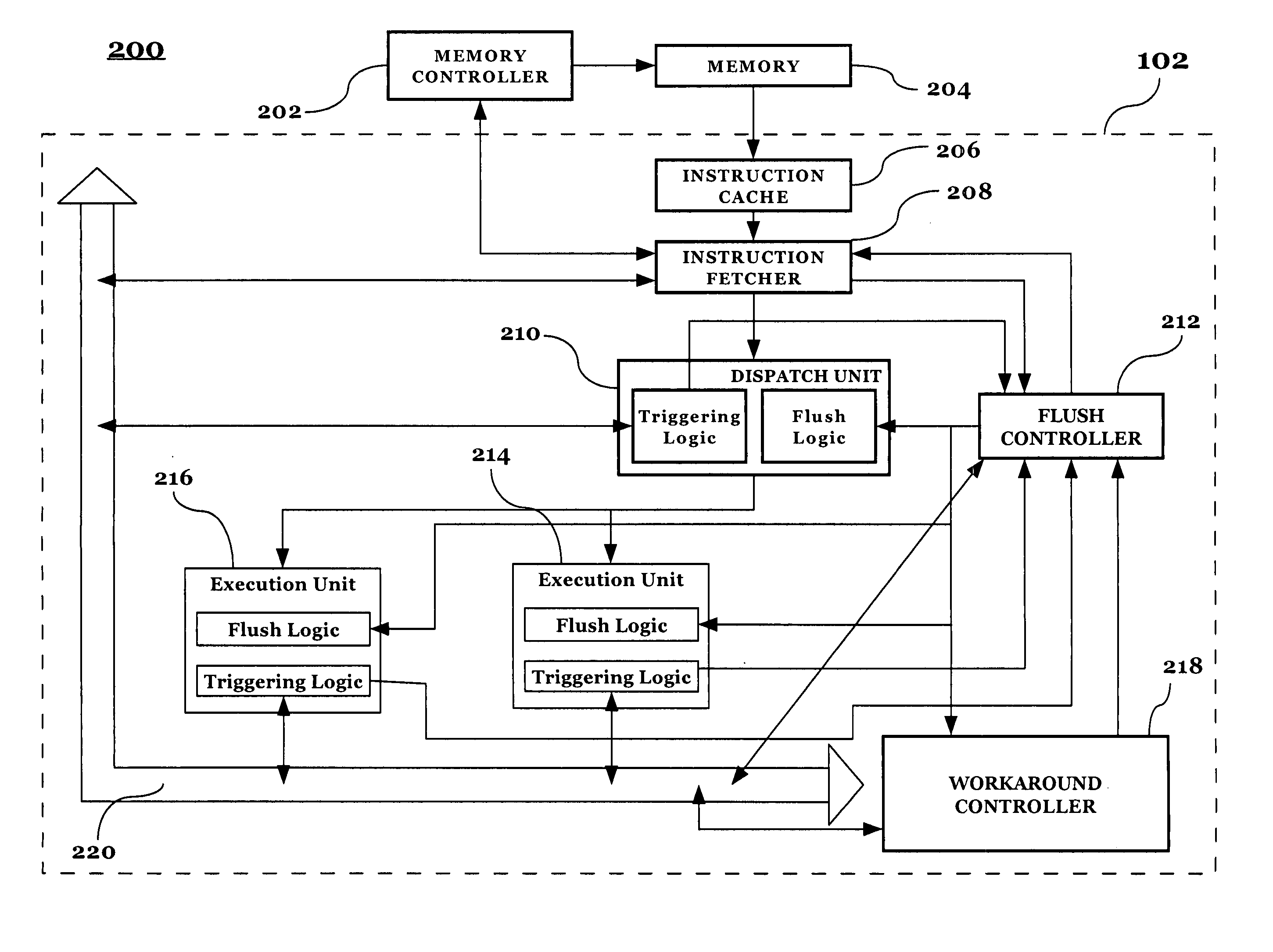
InactiveUS20060184769A1Increasing likely hood of forward progressDigital computer detailsMemory systemsWorkaroundReal-time computing
Localized generation of global flush requests while providing a means for increasing the likelihood of forward progress in a controlled fashion. Local hazard (error) detection is accomplished with a trigger network situated between execution units and configurable state machines that track trigger events. Once a hazardous state is detected, a local detection mechanism requests a workaround flush from the flush control logic. The processor is flushed and a centralized workaround control is informed of the workaround flush. The centralized control blocks subsequent workaround flushes until forward progress has been made. The centralized control can also optionally send out a control to activate a set of localized workarounds or reduced performance modes to avoid the hazardous condition once instructions are re-executed after the flush until a configurable amount of forward progress has been made.
Owner:IBM CORP
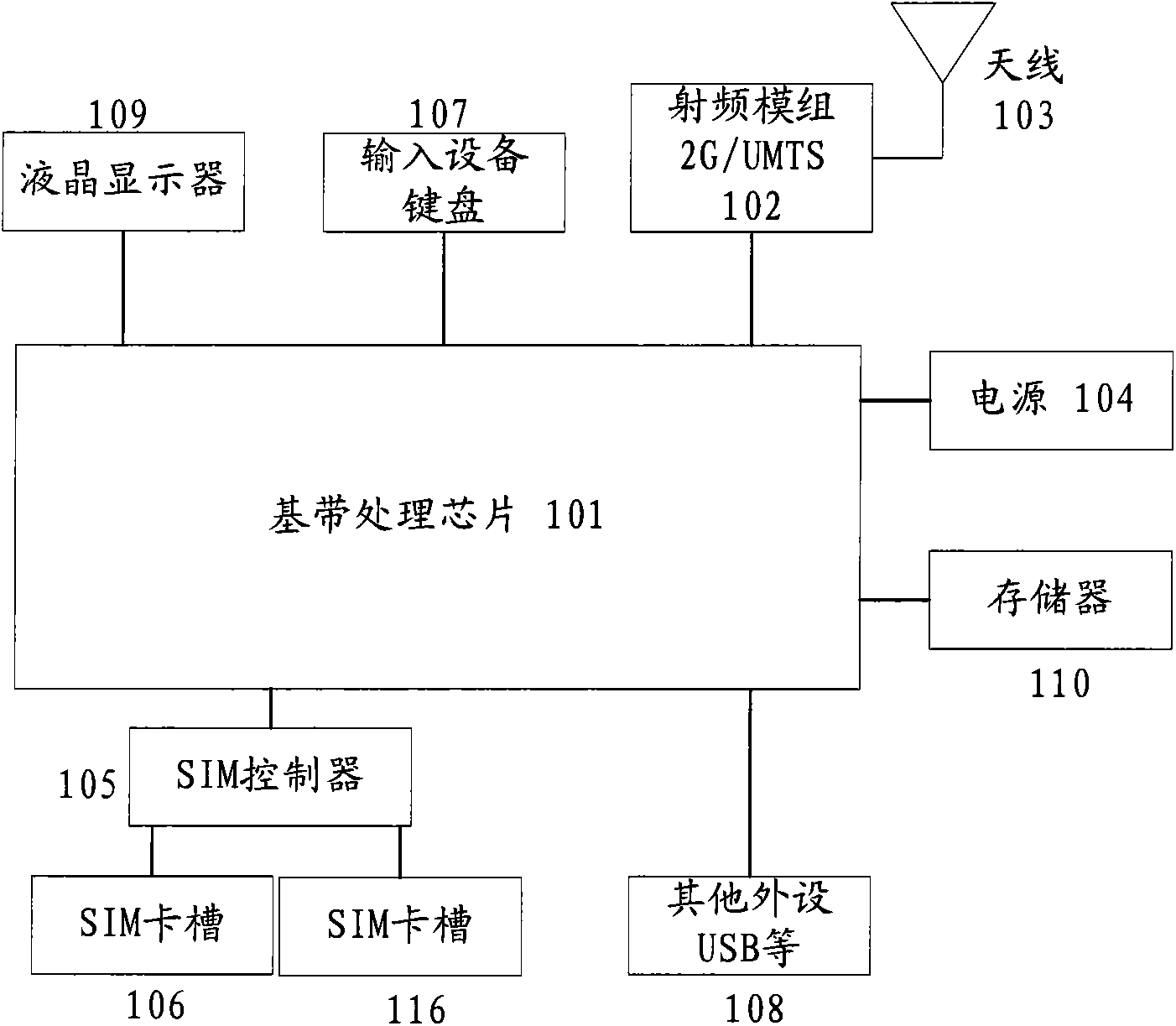
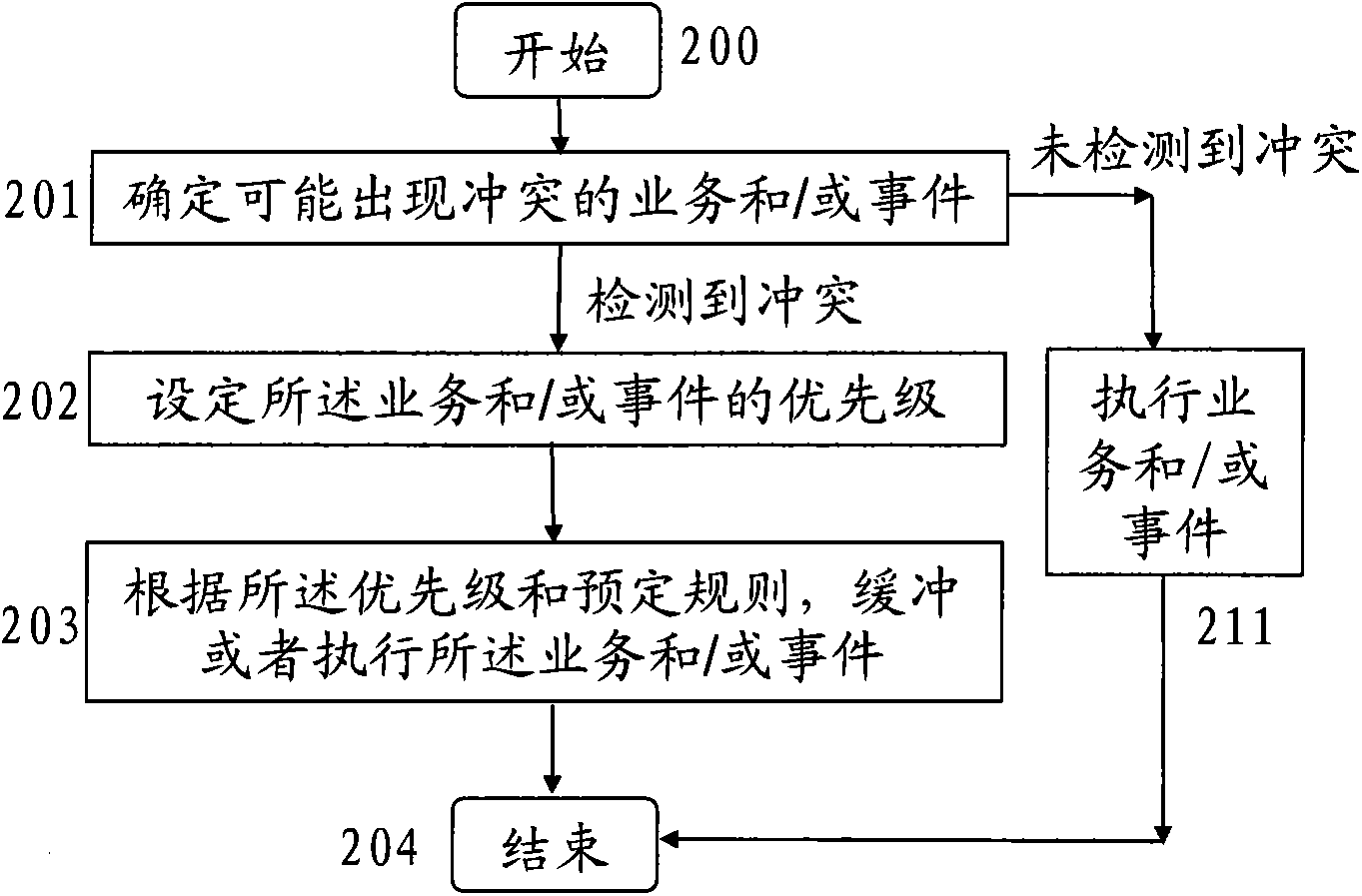
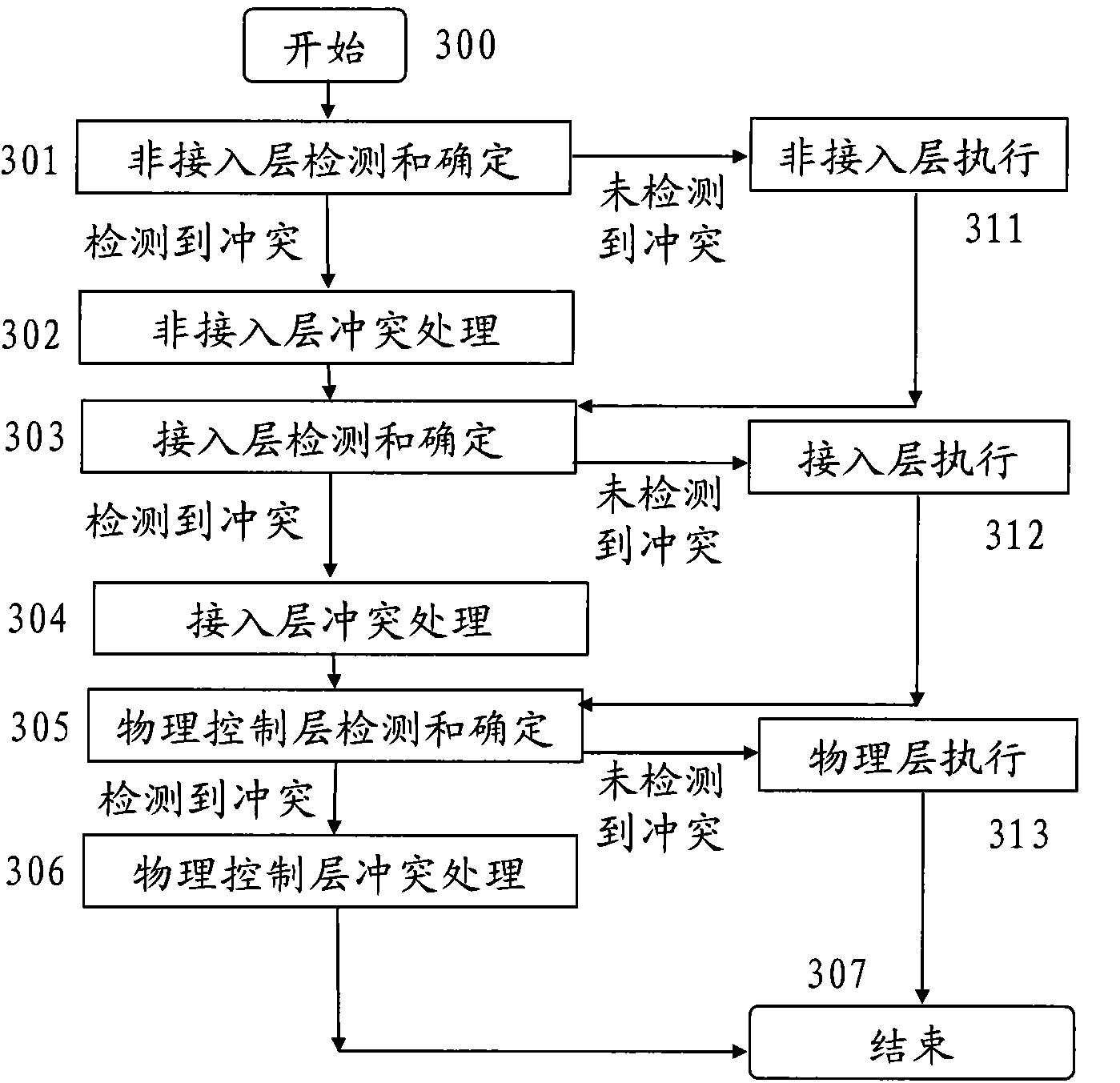
Multi-mode multi-card mobile terminal and business conflict solution method and apparatus thereof
The invention provides a solution method and apparatus for business conflict of a multi-mode multi-card mobile terminal, comprising: adding a detection arbitration module for business conflict in at least one layer of a non-access layer, an access layer and a physical layer of each card, which is used for detecting a business and / or event with possible conflict; setting a priority of the business and / or event; and caching or executing the business and / or event with possible conflict according to the priority and a predetermined rule so as to ensure the multi-mode multi-card mobile terminal to access shared resources without conflict.
Owner:MARVELL INT LTD
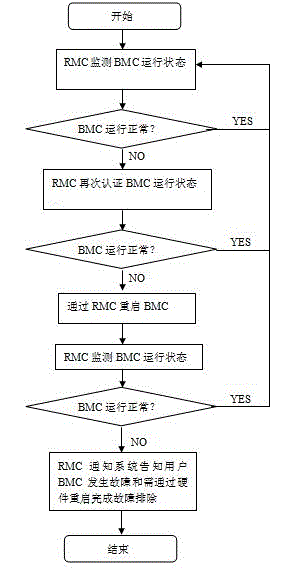
Automatic BMC (baseboard management controller) fault solution method based on RMC (rack server management center) management
InactiveCN104598329AImprove securityTroubleshoot technical issuesFault responseBaseboardComputer performance
The invention discloses an automatic BMC (baseboard management controller) fault solution method based on RMC (rack server management center) management, and belongs to the field of computer performance management. The method comprises the following specific steps: (1) monitoring a running state of a BMC by an RMC, if monitoring a BMC fault, re-authenticating whether the fault occurs in the BMC state or not, and if confirming that the fault occurs in the BMC, actively finishing a BMC restarting action by the RMC, wherein a server system comprises the RMC, an IPMB (intelligent platform management bus), an intermediate node plate and the BMC; (2) after actively finishing BMC restarting by the RMC, if monitoring that the BMC runs normally by the RMC, continuously keeping a monitoring state, or otherwise, notifying the BMC fault to users and prompting that the BMC fault is solved through a hardware restarting mode by a notification system. The method is used for an RACK server, automatic judgment of a BMC fault situation and fault removal and recovery by the system are realized through the RMC, the manual operation is not required, and the demands of BMC fault judgment, removal and recovery required to be performed by the server in time are effectively met.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
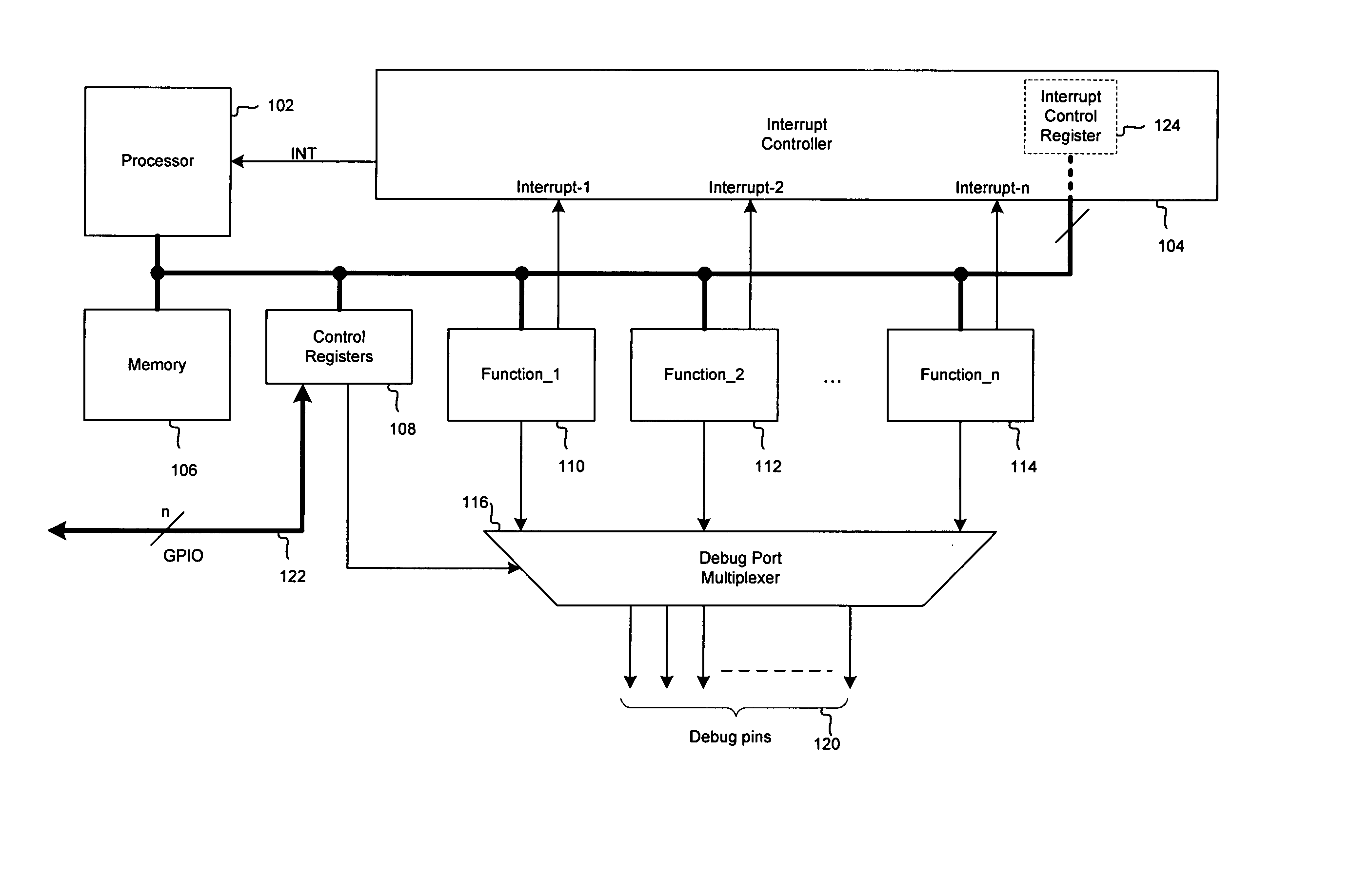
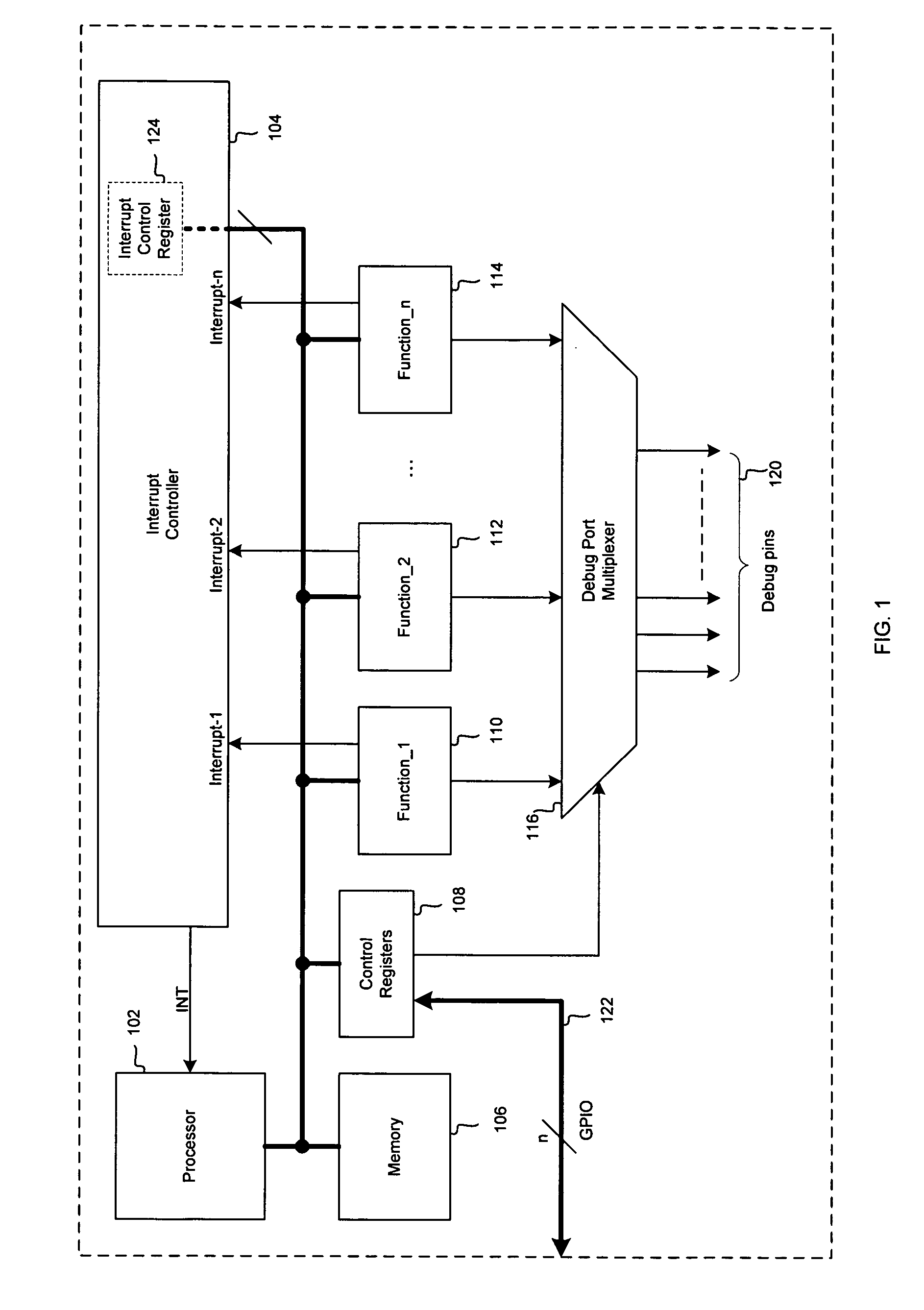
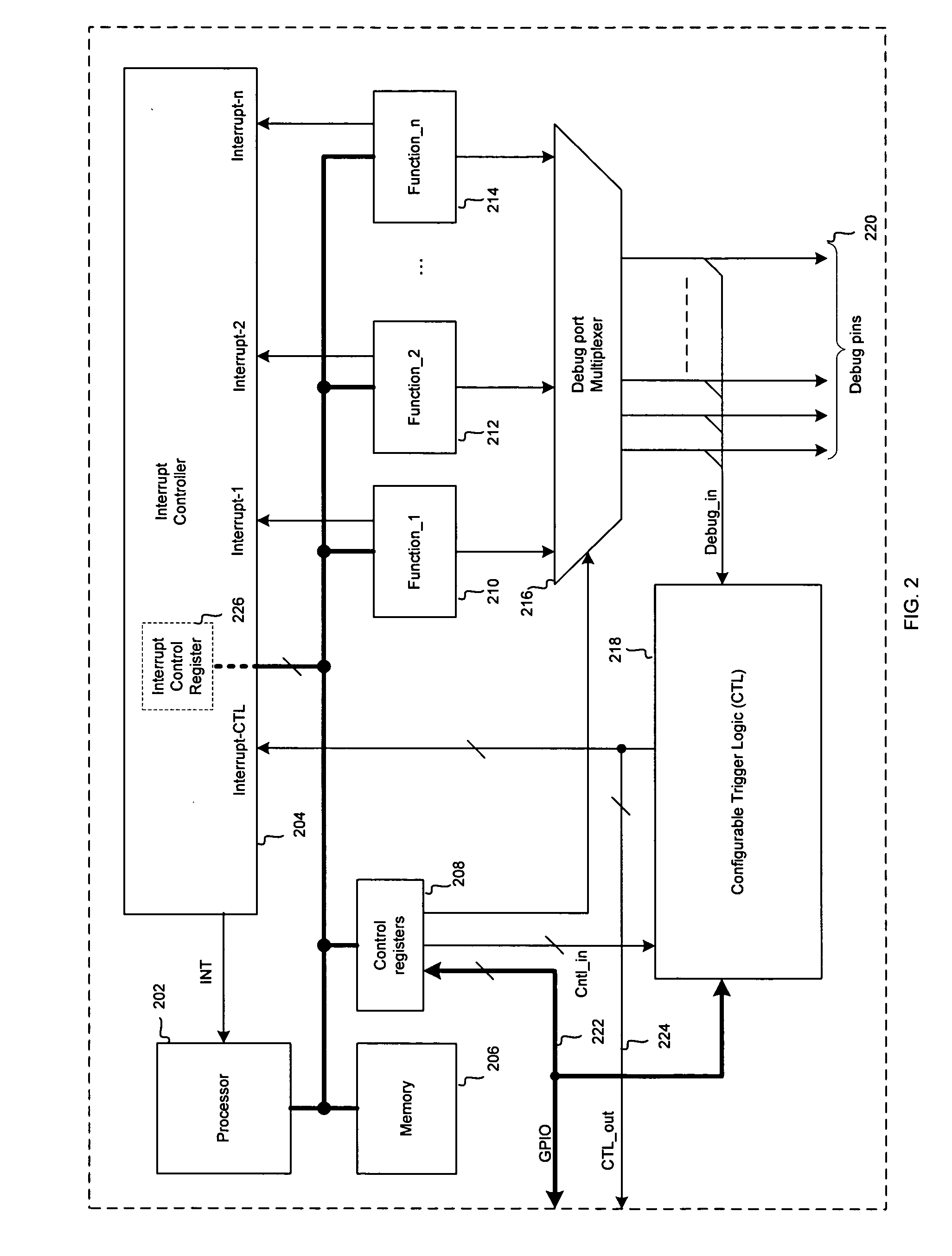
Method and system for configurable trigger logic for hardware bug workaround in integrated circuits
InactiveUS20060053343A1Avoid it happening againError detection/correctionIntegrated circuit layoutWorkaround
Aspects of configurable logic for hardware bug workaround in integrated circuits may comprise detecting within a chip at least one condition that would likely result in an occurrence of a hardware bug prior to the hardware bug occurring. Upon the detection of the condition, at least one trigger event may be generated within the chip via at least one debug signal, and the trigger event may be utilized to execute workaround code that may prevent the occurrence of the hardware bug. The debug signal may be generated inside the chip and / or outside the chip. The trigger event may be generated by combining a plurality of debug signals within the chip with at least one input or output signal of the chip.
Owner:AVAGO TECH INT SALES PTE LTD
Processor and method for workaround trigger activated exceptions
InactiveUS20090210659A1Avoid processing defectsRuntime instruction translationDigital computer detailsWorkaroundMicroarchitecture
A processor includes a microarchitecture for working around a processing flaw, the microarchitecture including: at least one detector adapted for detecting a predetermined state associated with the processing flaw; and at least one mechanism to modify default processor processing behavior; and upon modification of processing behavior, the processing of an instruction involving the processing flaw can be completed by avoiding the processing flaw.
Owner:IBM CORP
Method of implementing precise, localized hardware-error workarounds under centralized control
InactiveUS20060184770A1Minimal impactImpact processor performanceDigital computer detailsNon-redundant fault processingEngineeringWorkaround
In a processor, a localized workaround is activated upon the sensing of a problematic condition occurring on said processor, and then control of the deactivation of the localized workaround is superseded by a centralized controller. In a preferred embodiment, the centralized controller monitors forward progress of the processor and maintains the workaround in an active condition until a threshold level of forward progress has occurred. Optionally, the localized workaround may be re-activated while under centralized control, resetting the notion of forward progress. Using the present invention, localized workarounds perform effectively while having a minimal impact on processor performance.
Owner:IBM CORP
Coordination-centric framework for software design in a distributed environment
InactiveUS20020059558A1Interprogram communicationDigital computer detailsDistributed Computing EnvironmentReusable software
The present invention relates to a coordination-centric framework for implementing a software system in a distributed computing environment. In a presently preferred embodiment the software system is a software design environment having authoring, synthesis, and debugging tools. The coordination-centric framework is flexible enough to interconnect tools and robust enough that tool designers can use it for all aspects of tool interconnection without requiring costly workarounds. The coordination-centric framework uses modular and reusable software elements and standardized interfaces to connect the software elements.
Owner:INTEL CORP
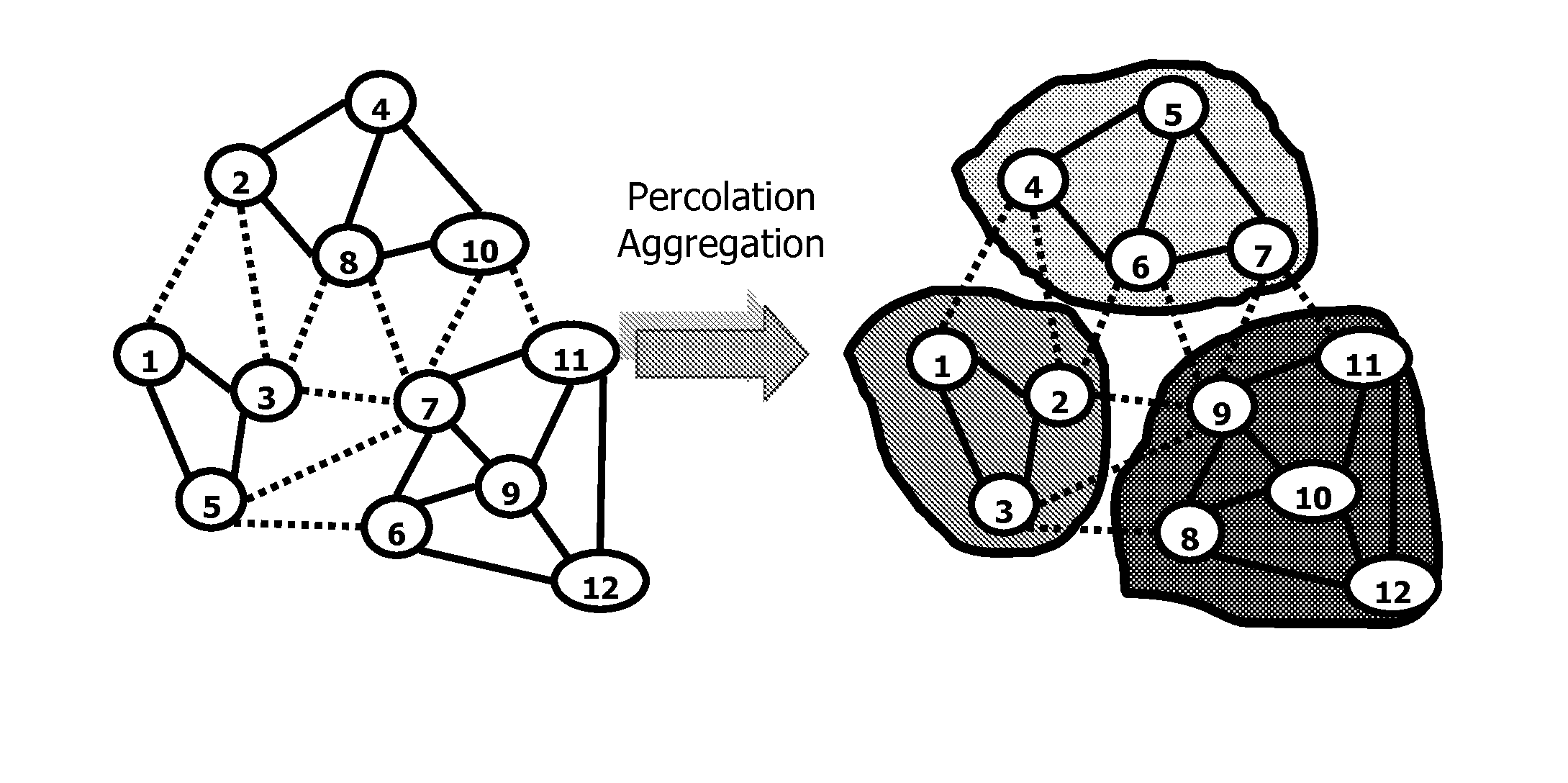
Multilevel percolation aggregation solver for petroleum reservoir simulations
InactiveUS8718993B2Computation using non-denominational number representationCAD numerical modellingPetroleum reservoirWorkaround
An efficient percolation aggregation solver methodology captures media connectivity and continuity to reliably incorporate relevant flow solution trends in subterranean formation models. The approach allows introduction of meaningful physical information that is generally overlooked by state-of-the-art algebraic algorithms in the solution process. Percolation aggregation extends the efficiency and robustness of solution methods used to solve scientific and engineering problems.
Owner:CONOCOPHILLIPS CO
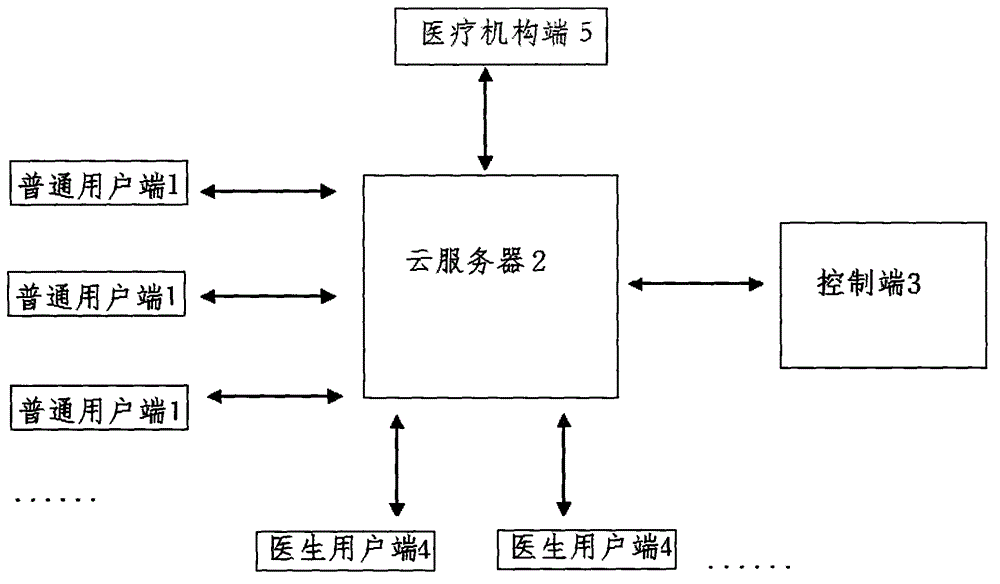
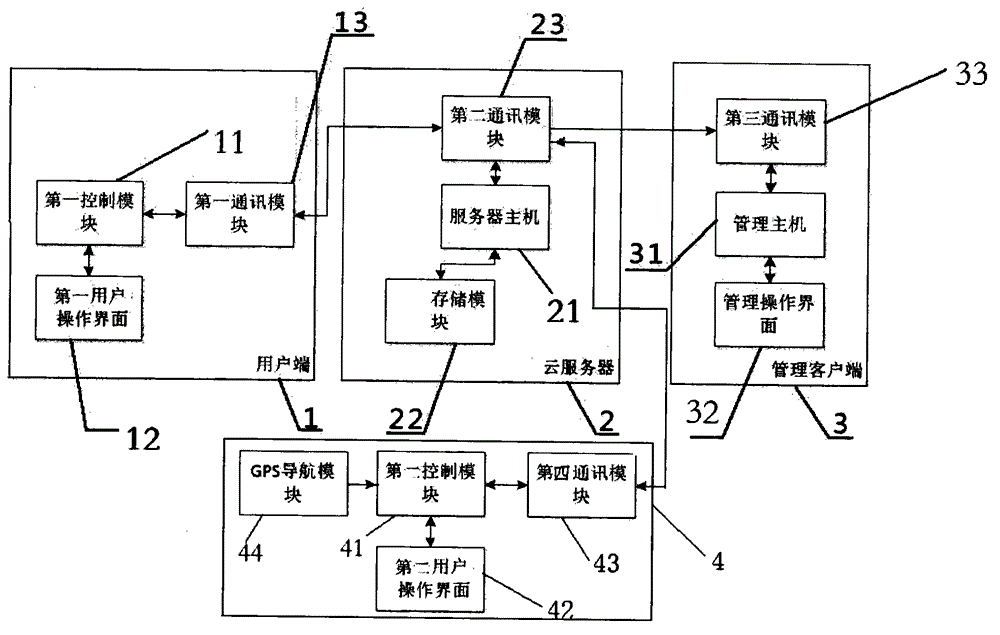
Medical system and method based on network
The invention provides a medical system based on network. The medical system comprises a common user end, a doctor user end, a cloud server, a control end and a medical institution end. A user raises a question according to his own disease at the common user end and describes his own disease, and uploads the information to the cloud server; the cloud server is used for uploading the question to the control end after storing the question; a doctor performs real-time conversation with the common user via an operation interface, and provides a solution for the question of the user, and guides the user to treat at a nearby hospital. According to the GPS navigation provided by the invention, the doctor could recommend a medical institution for the common user to diagnose by locating the consulting place of the common user, and the common user could select whether to invite the doctor to diagnosis and treat at the recommended medical institution based on the policy of a doctor multi-sited license. The medical system of the invention could perform favorable persuasion for medical patients so as to avoid the phenomenon that some medical institutions are overcrowded while some medical institutions are unfrequented, thereby achieving full utilization of the medical resource.
Owner:HENGJIKANGBAO WUHAN NETWORK TECH CO LTD
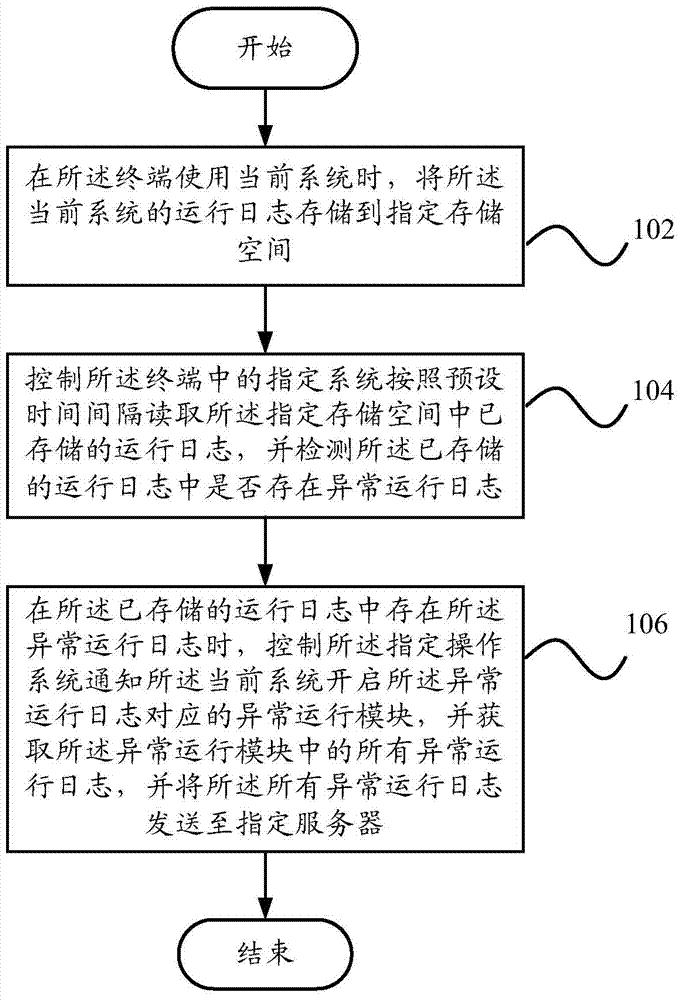
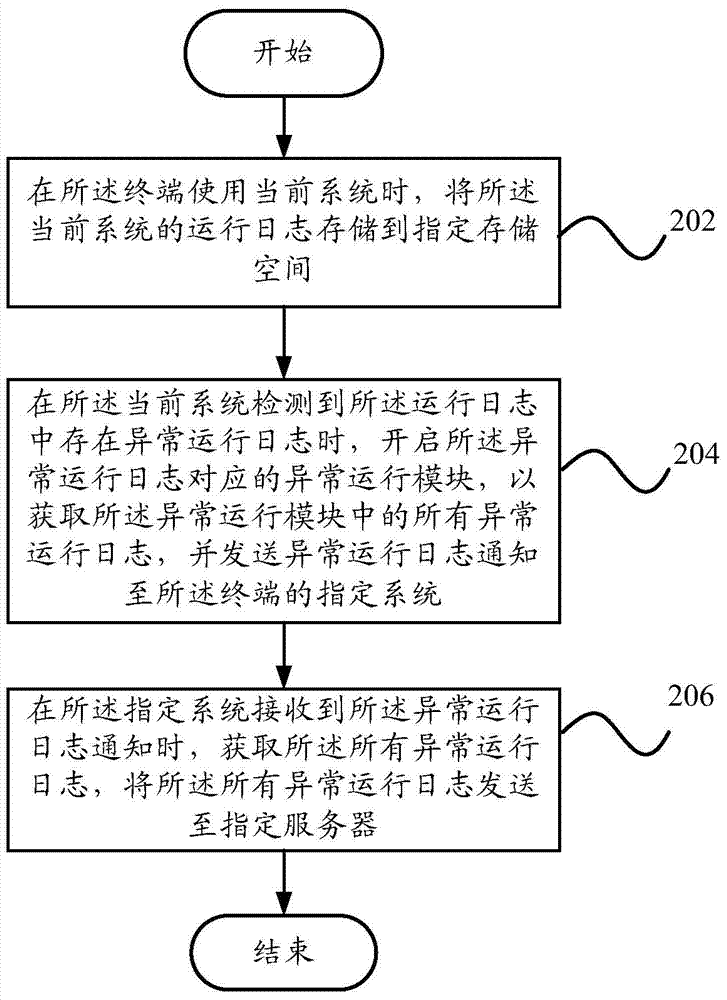
Terminal exception processing method and device and terminal
The invention provides a terminal exception processing method which includes that when a terminal uses a current system, running logs of the current system is stored in an appointed storage space; an appointed system in the terminal is controlled to read the running logs stored in the appointed storage space and detect whether abnormal running logs exist in the stored running logs; when there are abnormal running logs, an appointed operation system is controlled to inform the current system to operate an abnormal running module corresponding to the abnormal running logs, to obtain all the abnormal running logs in the abnormal running module and to send all the abnormal running logs to an appointed server. Correspondingly, the invention further provides a terminal exception processing device and the terminal. By adopting the terminal exception processing method and device and the terminal, problems occurred in the terminal can be fed back to manufacturers timely so that the manufacturers can find the solutions quickly according to the problems, further small problems which have not caused serious impacts can be solved timely, and the use experience of users can be improved.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Main interface locking and content displaying technical method
InactiveCN104184896ASave time and costAccurate acquisitionSubstation equipmentInput/output processes for data processingTime costApplication software
Owner:SHENZHEN INVENO TECH
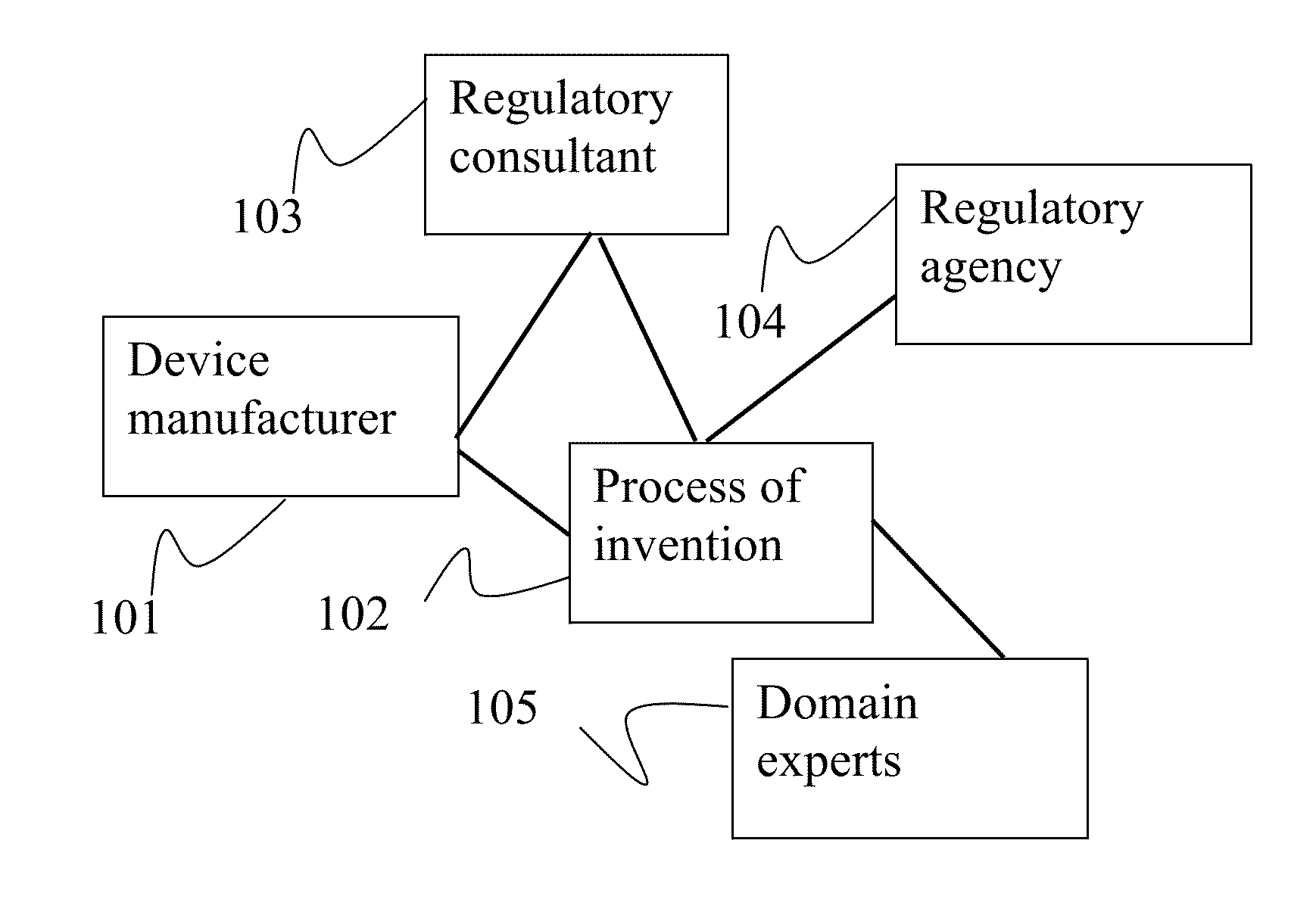
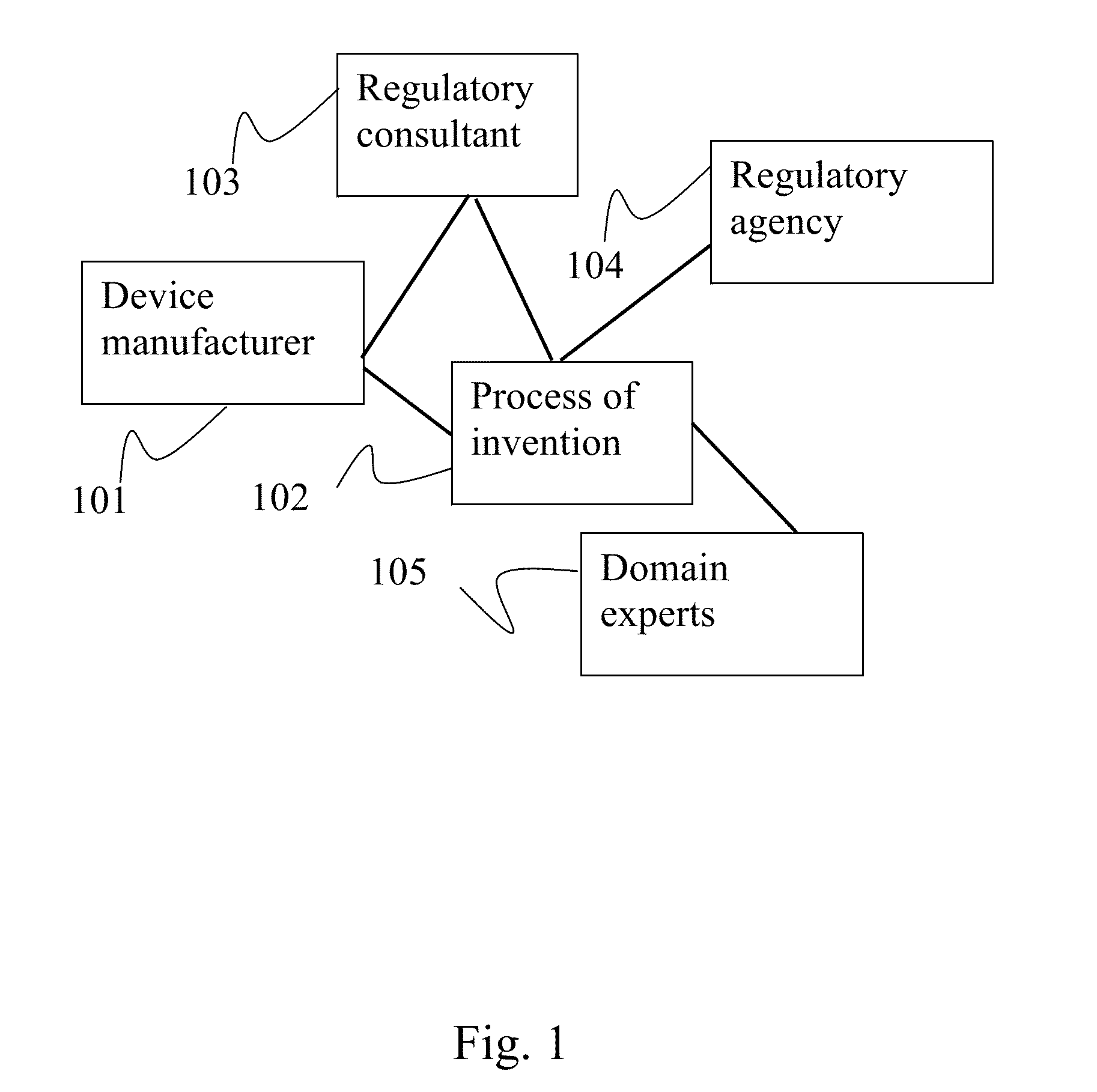
System and method for regulation compliance
The system and method herein disclosed is an online tool for reaching regulatory compliance. It uses a database of requirements by device, country, and agency necessary for licensing and marketing. Further databases include the compliance documents themselves, provided by given users concerning given devices. Still further databases include lists of domain experts, who may be called upon to review and edit these compliance documents. Expert systems running on a server associated with the system and method herein disclosed guide the user along the route to reaching compliance by means of aiding classification, prompting for missing documents, suggesting workarounds, submitting documents and payments automatically, and the like. Regulatory agencies may be given access to parts of the databases of the system and method herein disclosed to allow them to peruse and evaluate the compliance documents.
Owner:ARAZY BENNY
Method and apparatus for managing traffic flow of forwarding entries through a virtual forwarding database of a network node
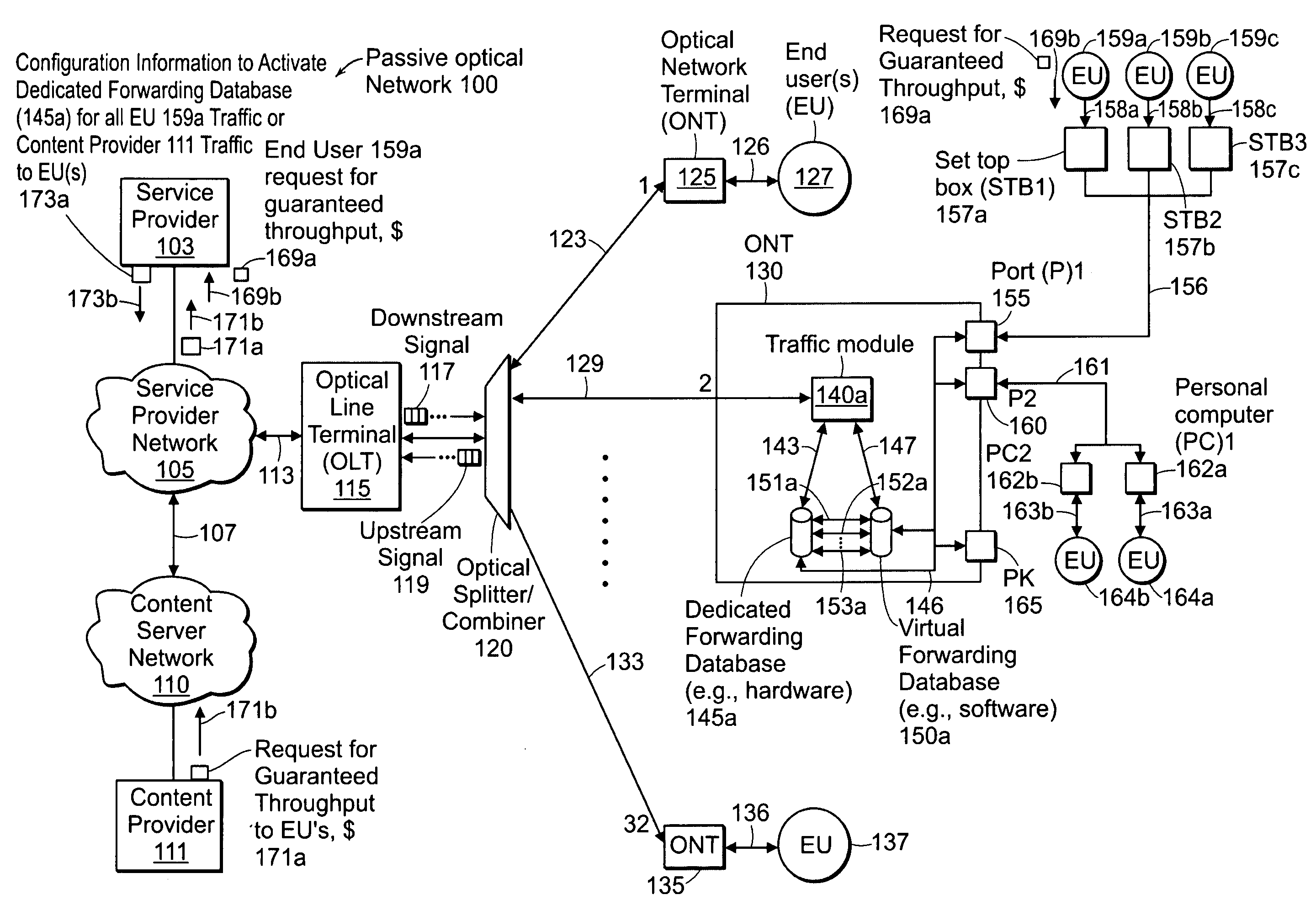
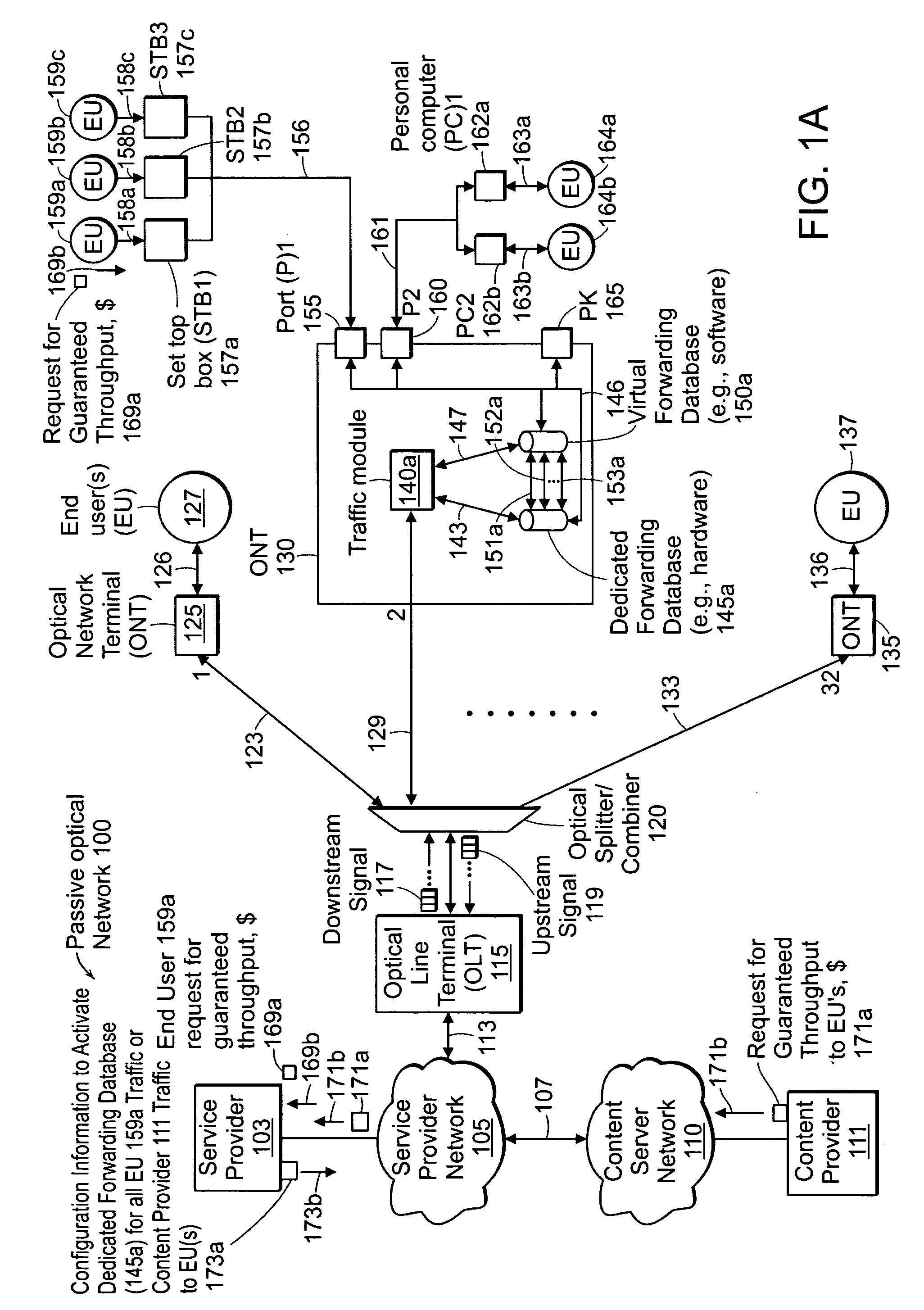
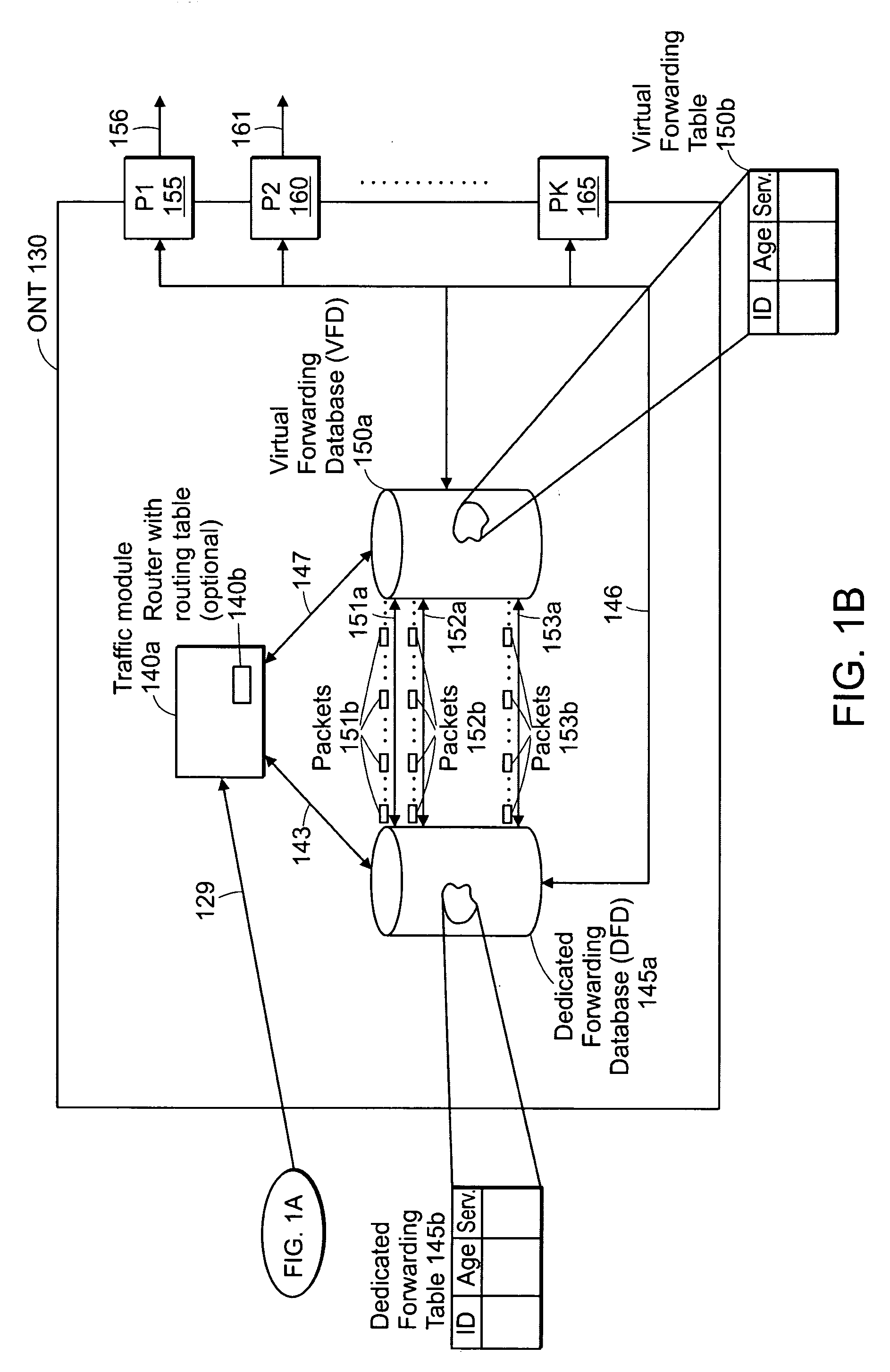
InactiveUS20090154349A1Multiplex system selection arrangementsError preventionTraffic flowWorkaround
Disclosed herein is a method and apparatus for supporting a virtual forwarding database in response to telecommunications network service demands and standard Media Access Control learning processes to support an overall forwarding database greater than the size supported in hardware. An example embodiment of the present invention provides a possible solution or workaround for certain hardware platforms that limit the total number of forwarding entries that are currently available. This is done by creating a virtual forwarding database that may be maintained in local random access memory and not in the switch(es) / network processors' forwarding database. As such, a traffic module (e.g., application code / processor or central processing unit) may continuously update a virtual forwarding database along with a dedicated forwarding database based on the reception of external data, which includes, but is not limited to, any combination of the following: IPTV joins / leaves, new / unknown packets, and known packets.
Owner:TELLABS VIENNA
Look-ahead built-in self tests
InactiveUS7877657B1Avoiding system downtimeElectronic circuit testingPower supply testingDowntimeWorkaround
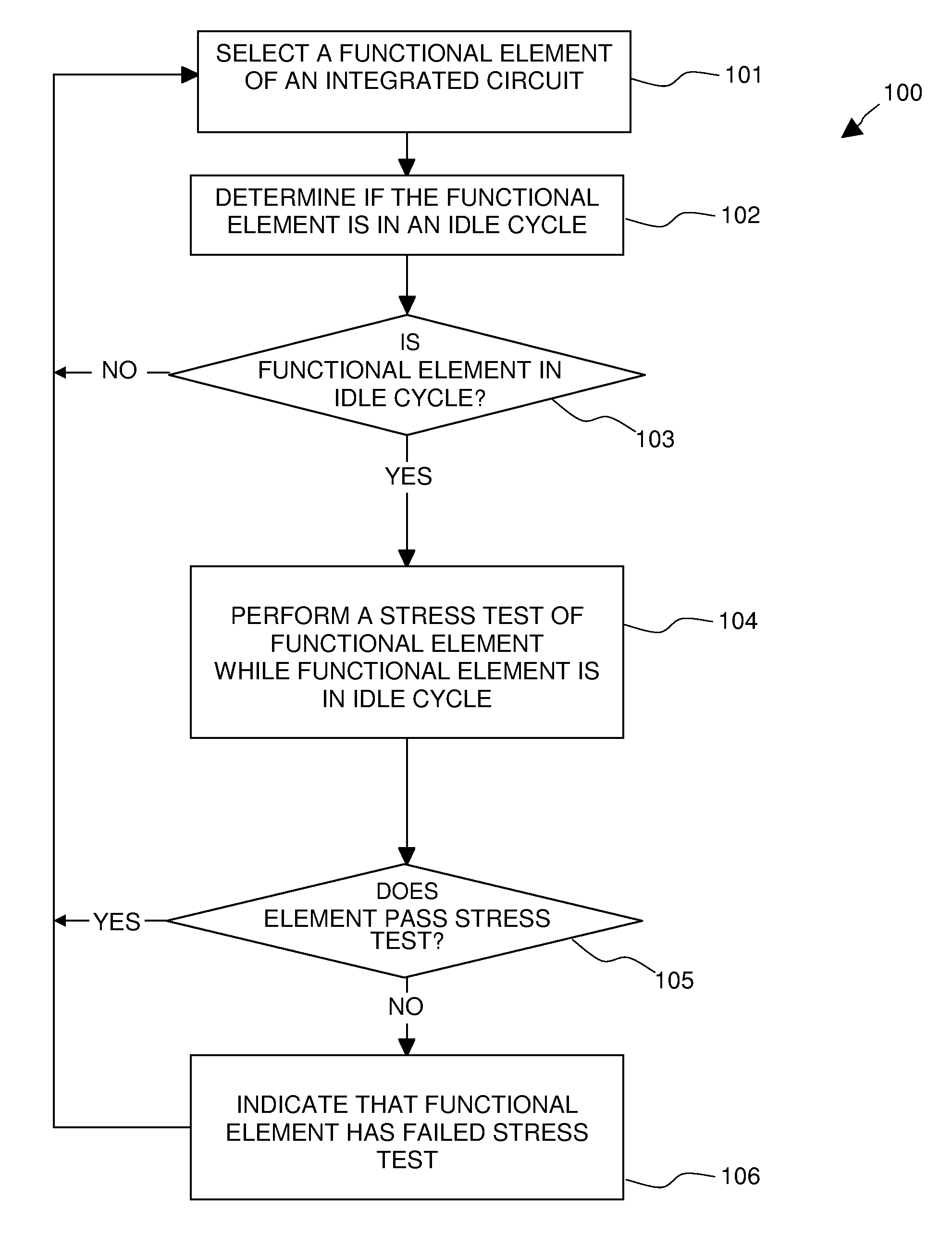
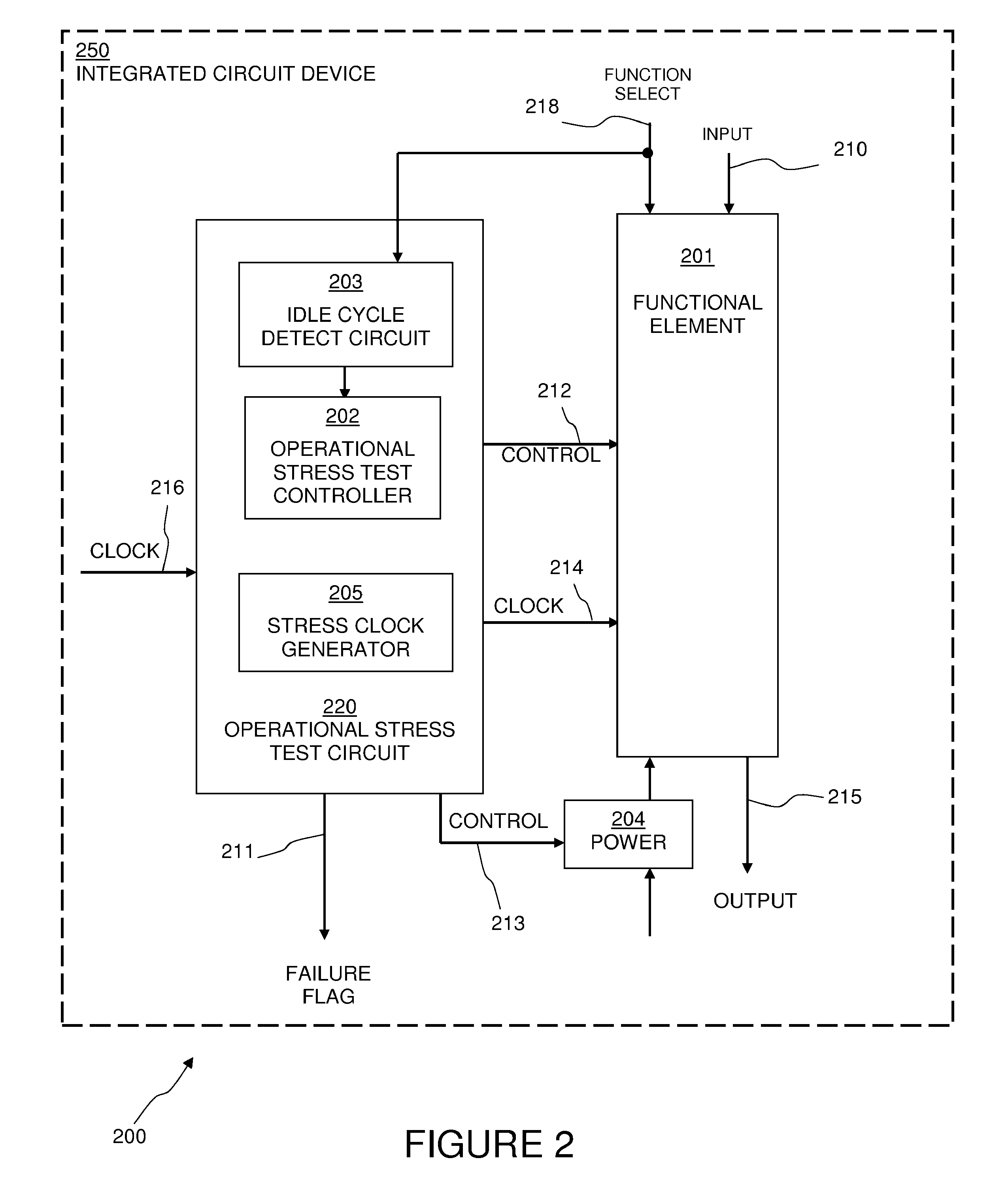
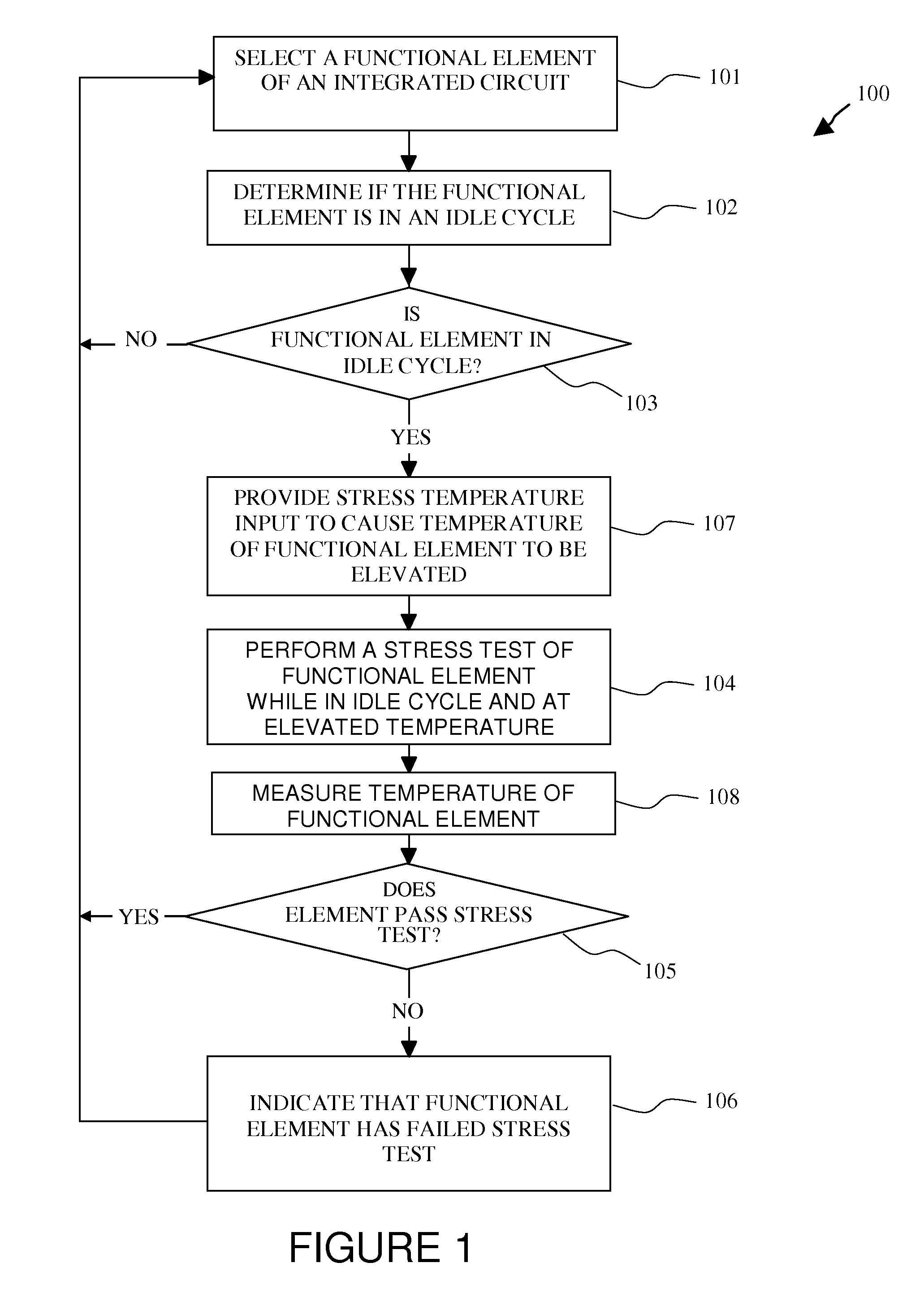
A method and apparatus are disclosed for predicting the failure of a functional element of an integrated circuit during operation. The method includes determining whether the functional element of the integrated circuit device is in an idle cycle, performing a stress test of the functional element while the functional element is in the idle cycle, and indicating that the functional element, if it fails the stress test, is a potential future failing element. The stress test can include simultaneously providing a margining test voltage and a stress clock signal to the functional element. The stress test is performed in the background, during continuous operation of the integrated circuit device, such that normal operation of the integrated circuit device is not interrupted. Thereby, the method and apparatus of the present invention allows for failure prediction in a device before it happens, allowing for planned outages or workarounds and avoiding system downtime for unplanned repairs.
Owner:INTEGRATED DEVICE TECH INC
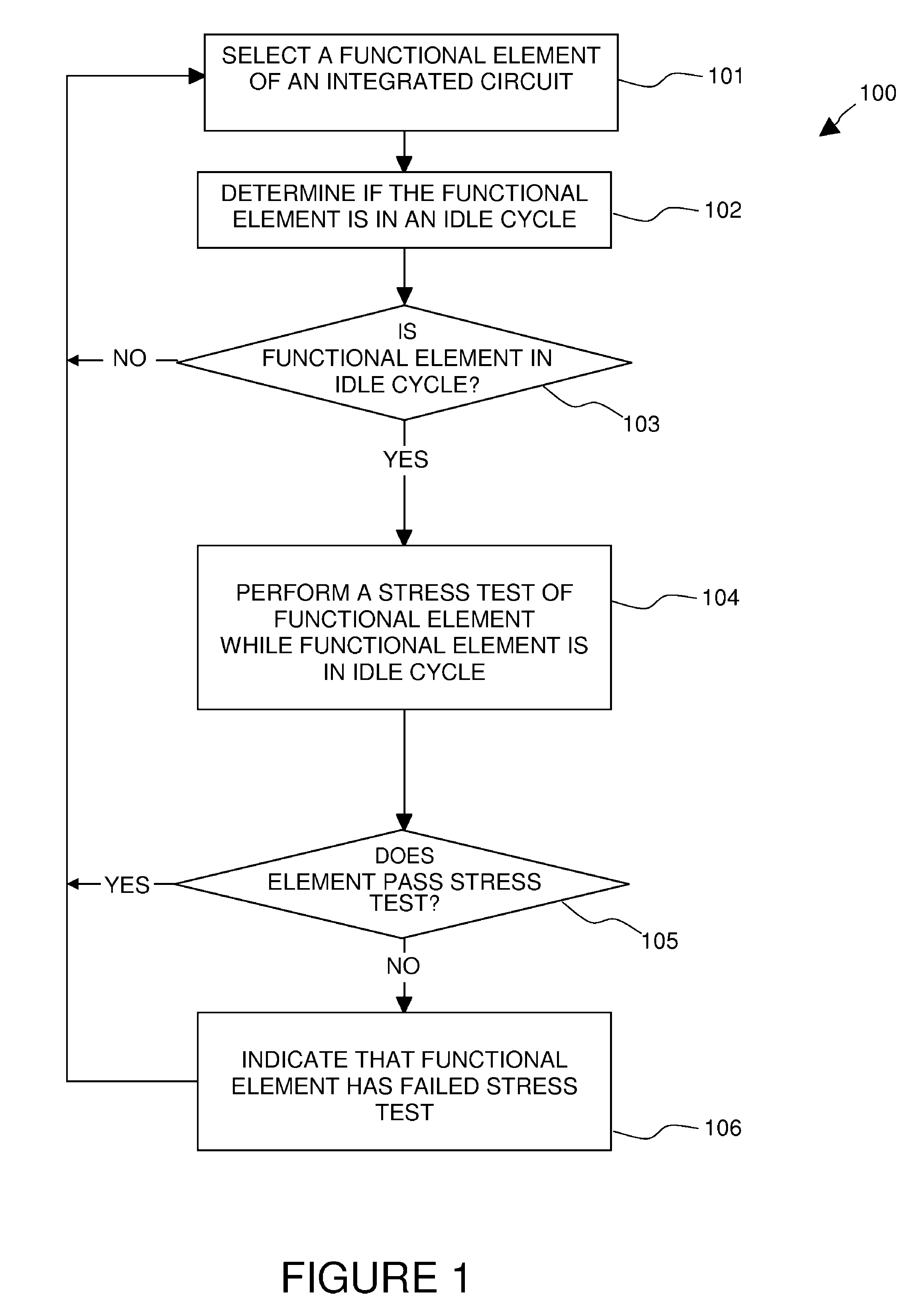
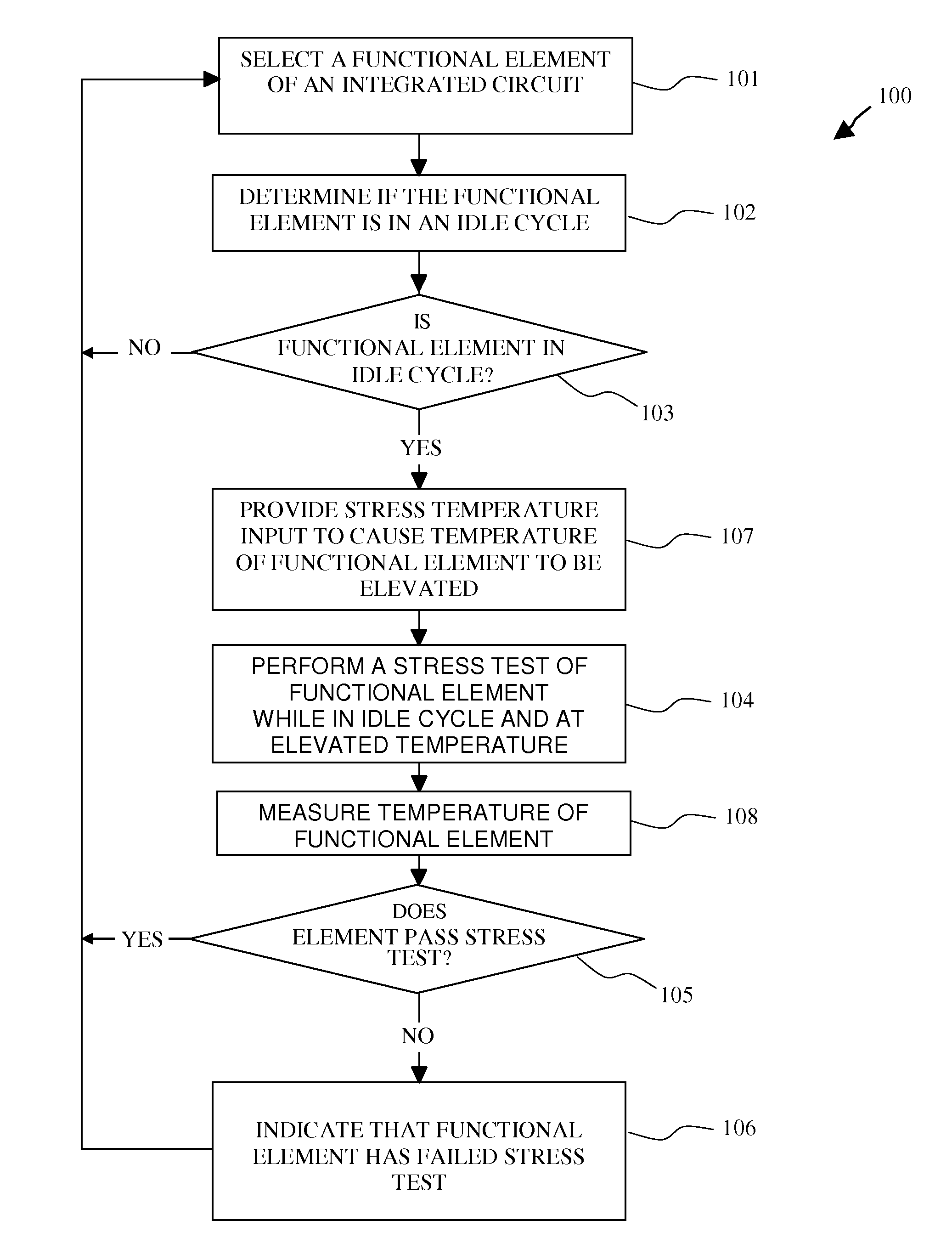
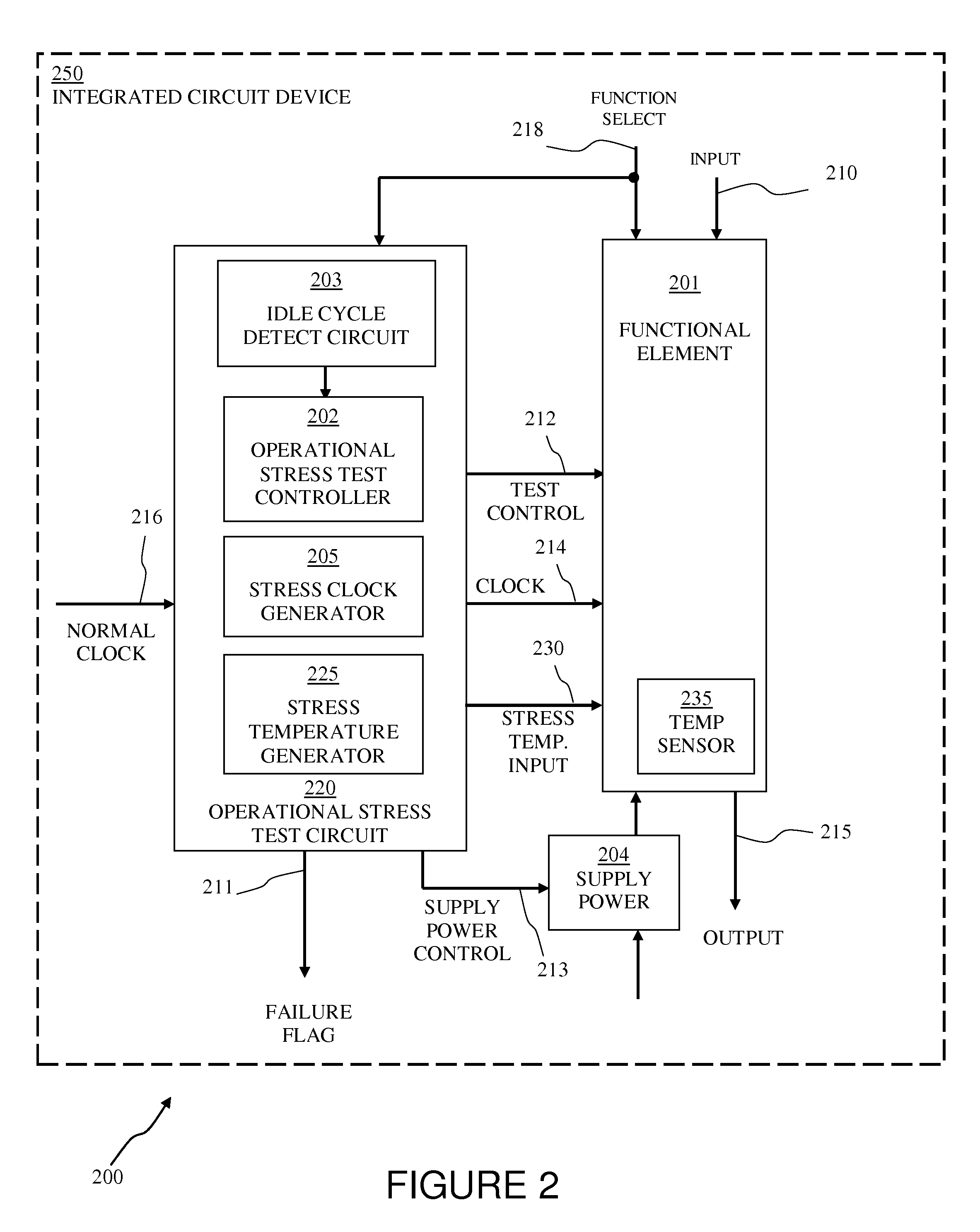
Look-ahead built-in self tests with temperature elevation of functional elements
ActiveUS8028211B1Avoiding system downtimeDoes not impact the performance of the functional element during normal operationElectronic circuit testingPower supply testingDowntimeWorkaround
A method and apparatus are disclosed for predicting the failure of a functional element of an integrated circuit during operation. The method includes determining whether the functional element of the integrated circuit device is in an idle cycle, elevating the temperature of the functional element above a normal operating temperature, performing a stress test of the functional element while the functional element is in the idle cycle, and indicating that the functional element, if it fails the stress test, is a potential future failing element. The stress test can include simultaneously providing a margining test voltage and a stress clock signal to the functional element while the temperature is elevated or at a normal operating temperature. The stress test is performed in the background, during continuous operation of the integrated circuit device, such that normal operation of the integrated circuit device is not interrupted. Thereby, the method and apparatus of the present invention allows for failure prediction in a device before it happens, allowing for planned outages or workarounds and avoiding system downtime for unplanned repairs.
Owner:INTEGRATED DEVICE TECH INC
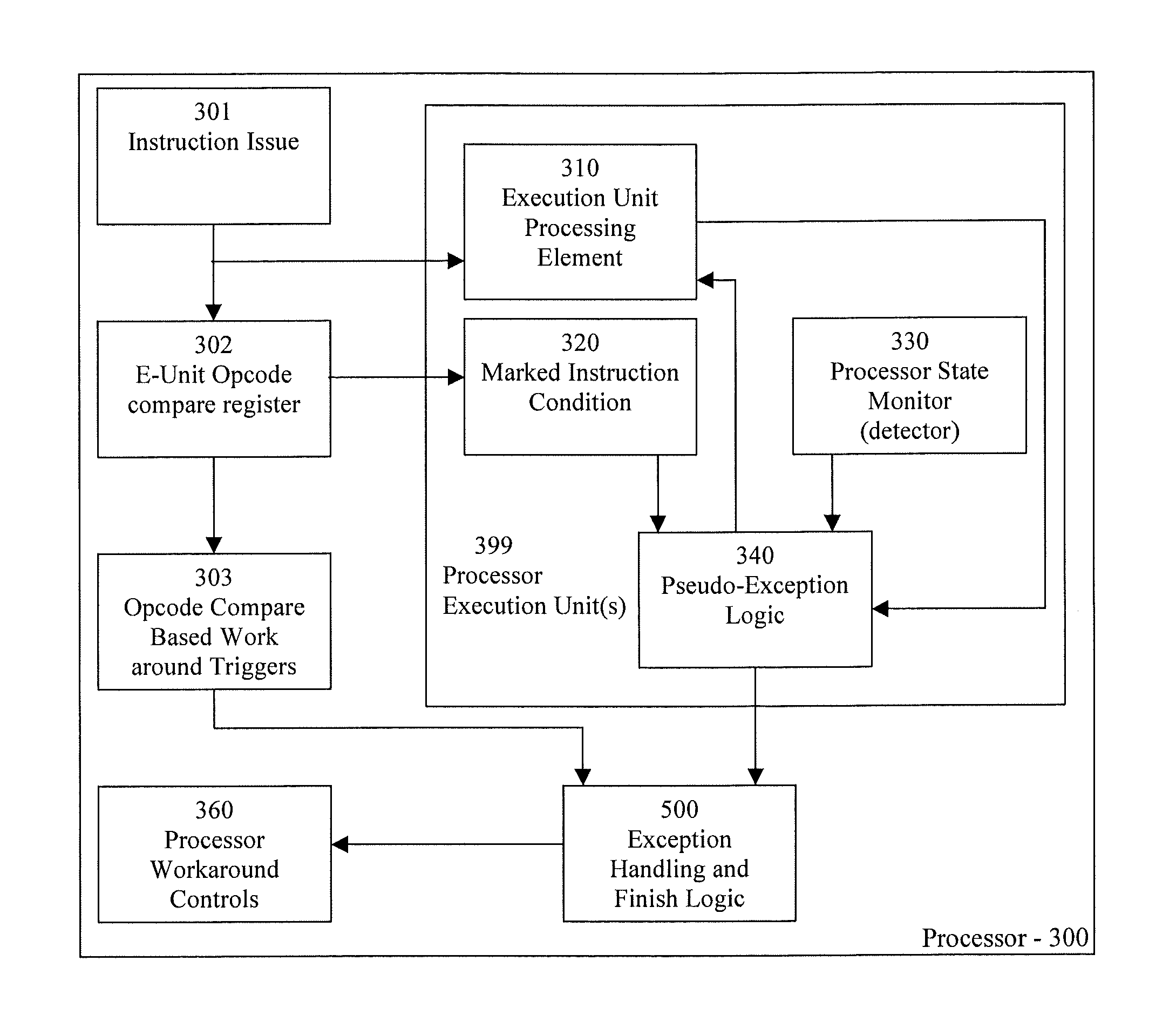
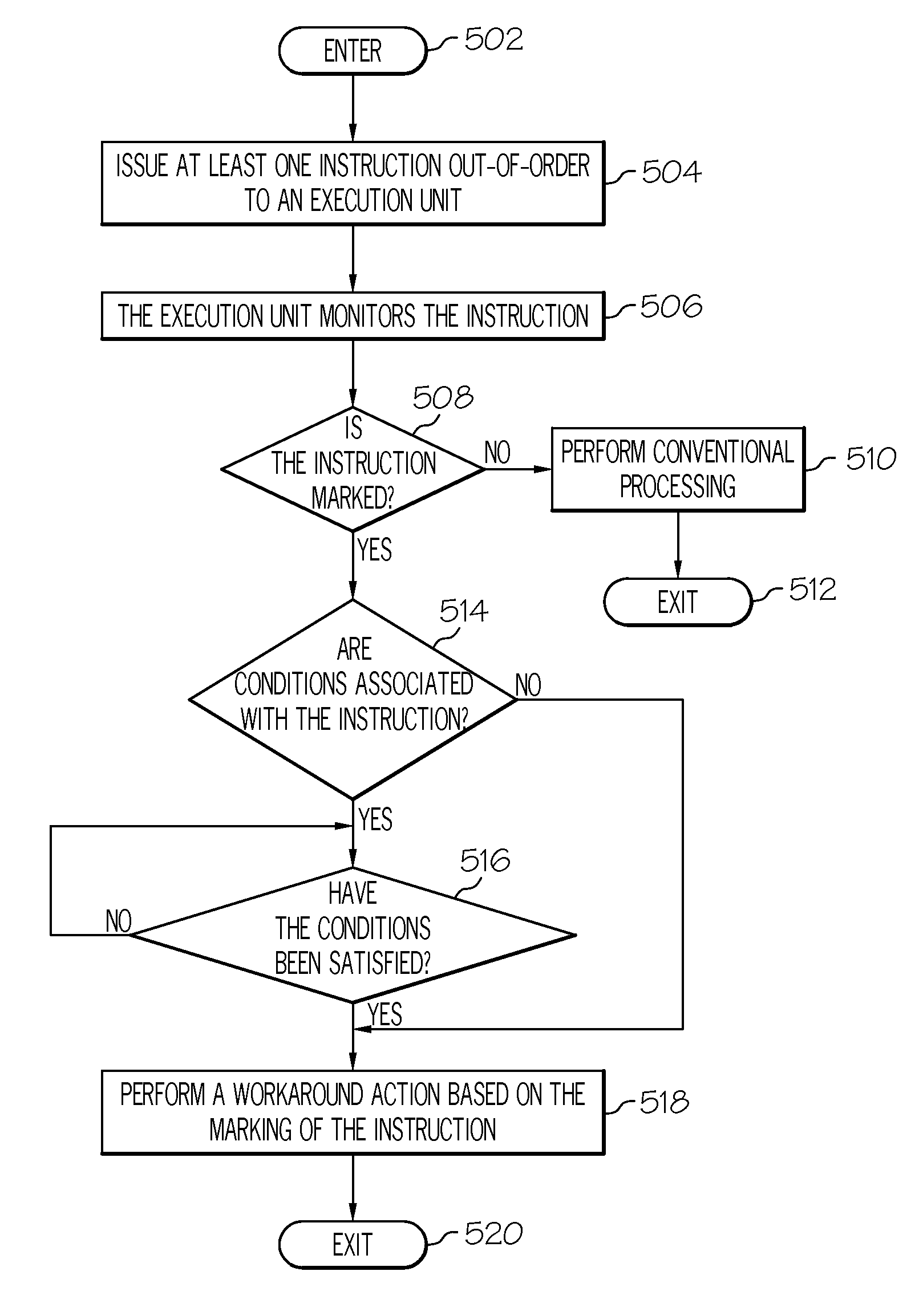
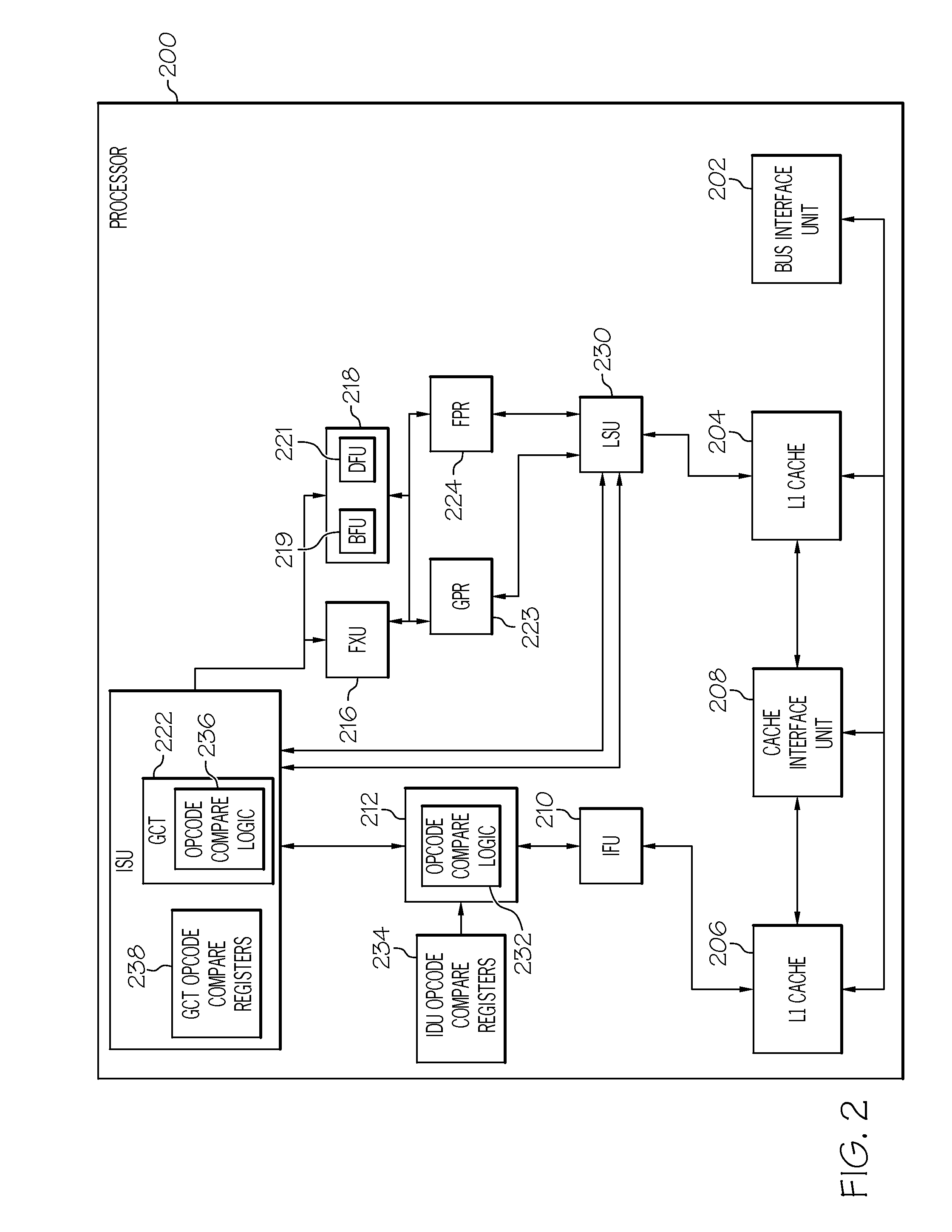
Triggering workaround capabilities based on events active in a processor pipeline
ActiveUS20110154107A1Instruction analysisDigital computer detailsInformation processingProcessor register
A method, information processing system, and processor work around a processing flaw in a processor. At least one instruction is fetched from a memory location. The at least one instruction is decoded. An opcode compare operation is compared with the at least one instruction and a set of values within at least one opcode compare register in response to the decoding. The instruction is marked with a pattern based on the opcode compare operation. The pattern indicates that the instruction is associated with a processing flaw.
Owner:IBM CORP
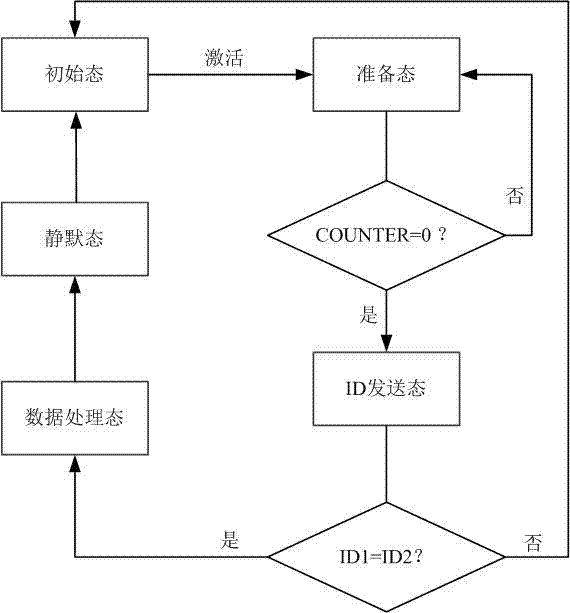
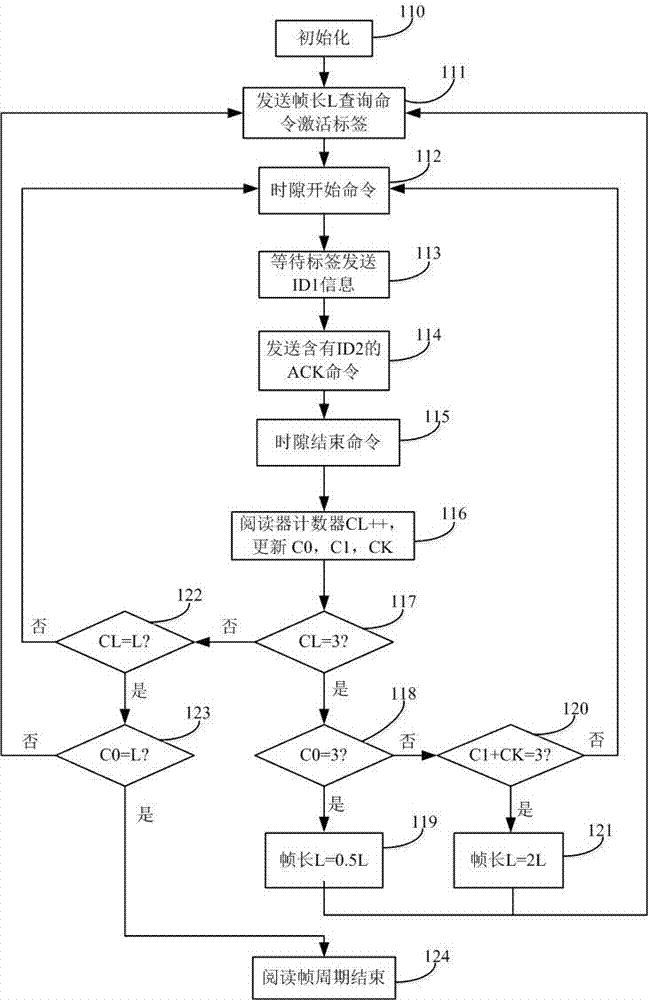
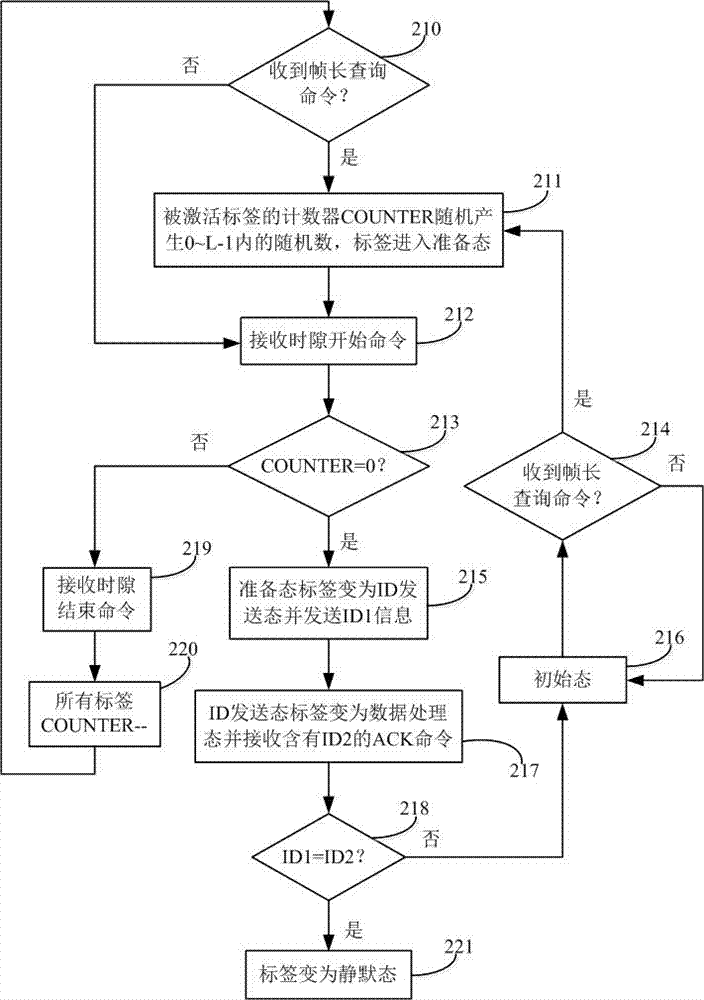
Posterior probability tag collision solution for RFID system
InactiveCN107153802AImprove recognition efficiencyAvoid wastingSensing by electromagnetic radiationCommunications systemFrame time
The invention discloses a posterior probability tag collision solution for an RFID system. The RFID system of the method consists of one reader and a plurality of tags in the coverage of the reader. The reader sends a frame length querying command, and then executes the corresponding operation when the tags receive the command. The label has five states: an initial state, a preparation state, an ID transmission state, a data processing state and a silent state. The state change of the tags is executed through a counter according to a current time slot state, and the reader adjusts the frame length according to the states of the former three time slots in each frame, thereby avoiding the excessive time slots and collision time slots in the frame time slot, avoiding the collision between the large-scale tags, and reducing the impact on the recognition efficiency from a capturing effect. The method can effectively solve a problem of multi-tag collision in the RFID communication system when being used for the collision between a plurality of RFID tags, and improves the recognition rate of a system for the tags.
Owner:YUNNAN MINZU UNIV
Method for solving phishing attack of Android platform
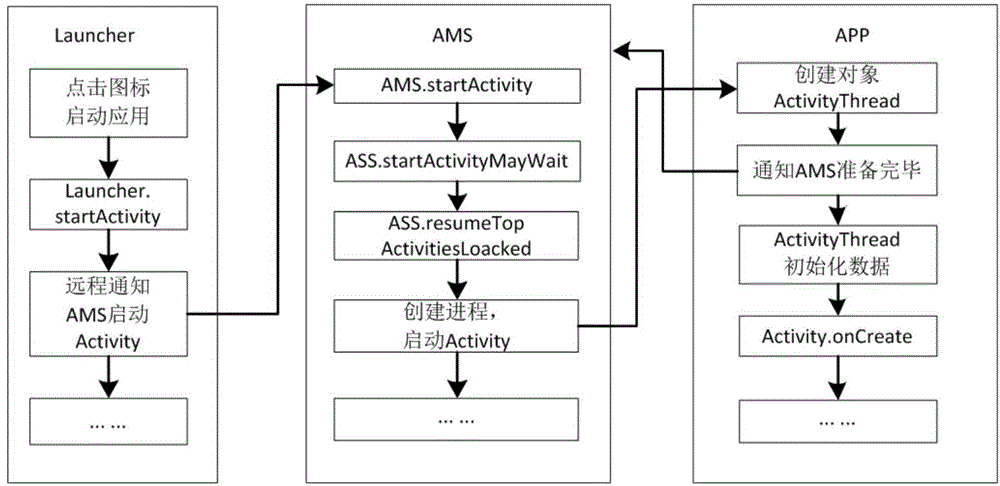
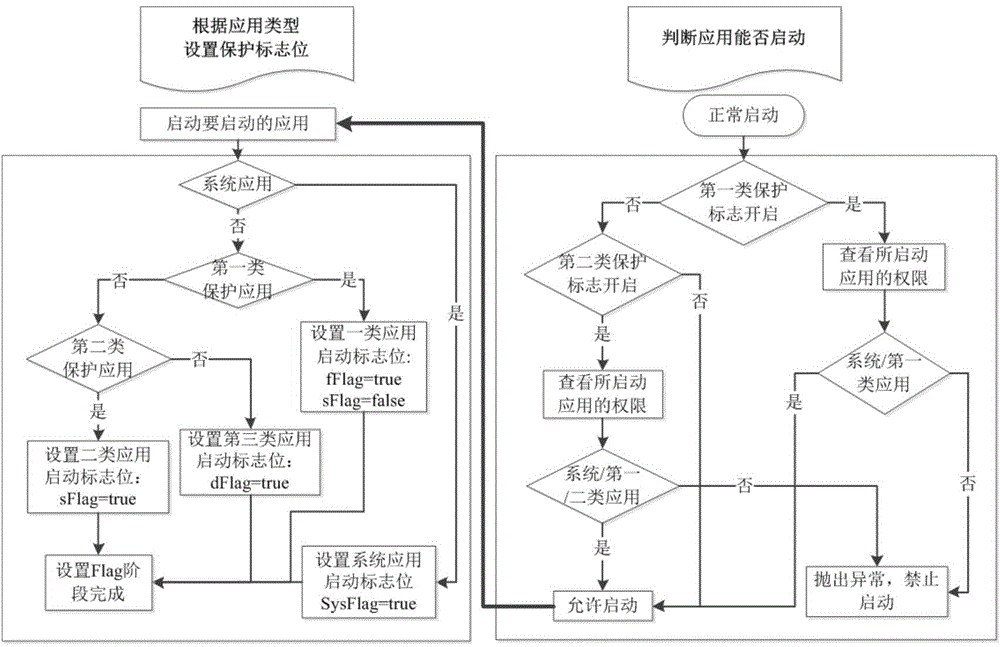
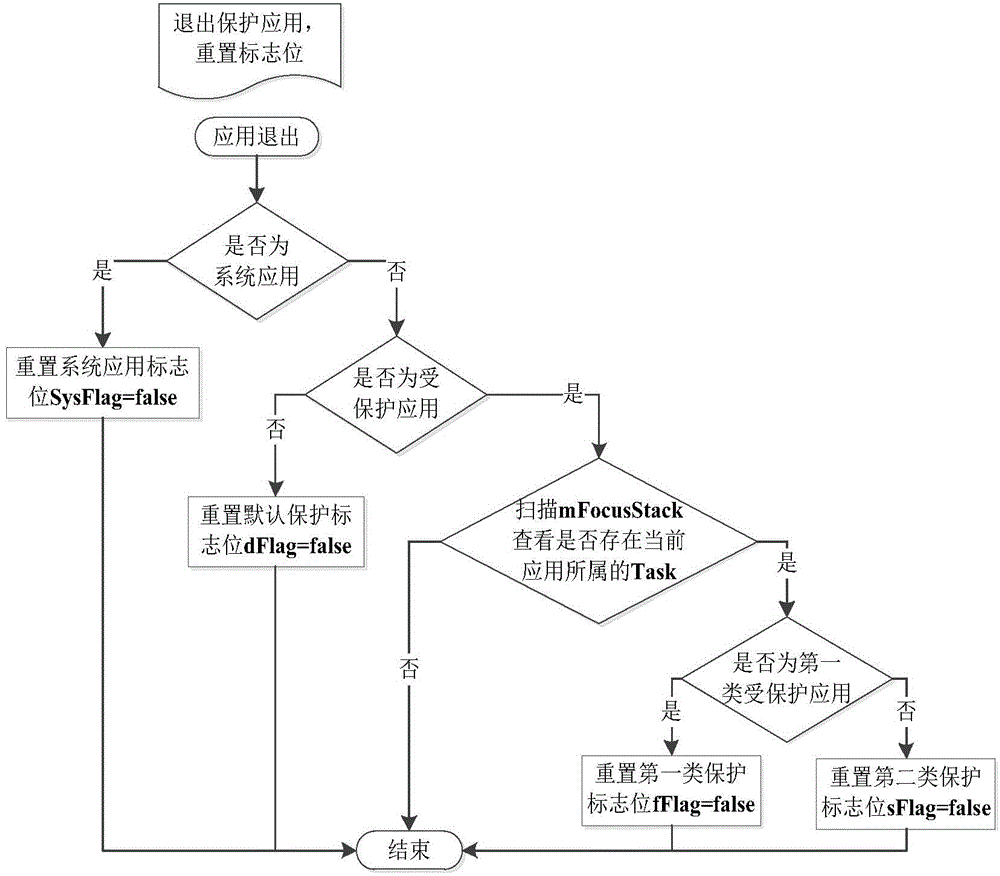
ActiveCN104361281ASolve the problem that phishing apps cannot be blockedEnsure safetyPlatform integrity maintainanceIdentity recognitionWorkaround
The invention discloses a method for solving a phishing attack of an Android platform. The method comprises the steps of classifying a mobile phone application except for a system application into a plurality types of protection applications by a user according to the safe and sensitive degree; when the user starts one application, firstly judging whether one protected application is started by the system, starting a recognition and interception module according to the judgment result and the category of a to-be-started application and determining whether the application is permitted to be started, if so, carrying out identity recognition on the application, arranging a protective flag bit according to the category of the application, and determining whether the application is protected by the system according to the protective flag bit. According to the method, the recognition and interception module is additionally arranged to an application management system (AMS) of a system framework layer, so that the problem that as the application layer cannot intervene with the AMS flow, the phishing application cannot be intercepted is solved; meanwhile, a multi-level protection scheme is provided for the user to customize; the safety of the mobile phone during use of the user is effectively ensured.
Owner:XIDIAN UNIV
Least recently used replacment method with protection
An LRU with protection method is provided that offers substantial performance benefits over traditional LRU replacement methods by providing solutions to common problems with traditional LRU replacement. By dividing a cache entry list into a filter sublist and a reuse list, population and protection processes can be implemented to reduce associativity and capacity displacement. New cache entries are initially stored in the filter list, and the reuse list is populated with entries promoted from the cache list. Eviction from the filter list and reuse list is done by a protection process that evicts a data entry from the filter, reuse, or global cache list. Many variations of protection and eviction processes are discussed herein, along with the benefits each provides in reducing the effect of unwanted displacement problems present in traditional LRU replacement.
Owner:INTEL CORP
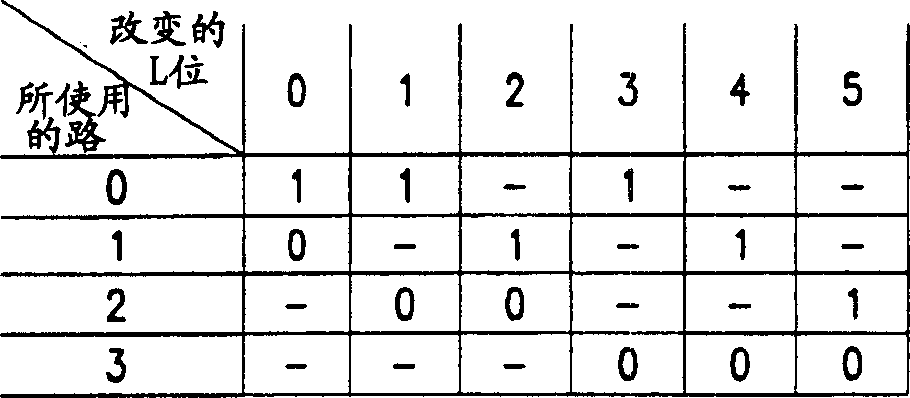
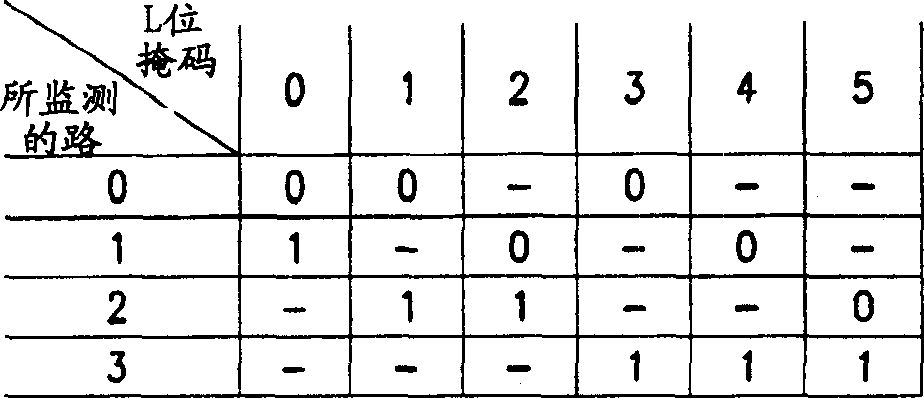
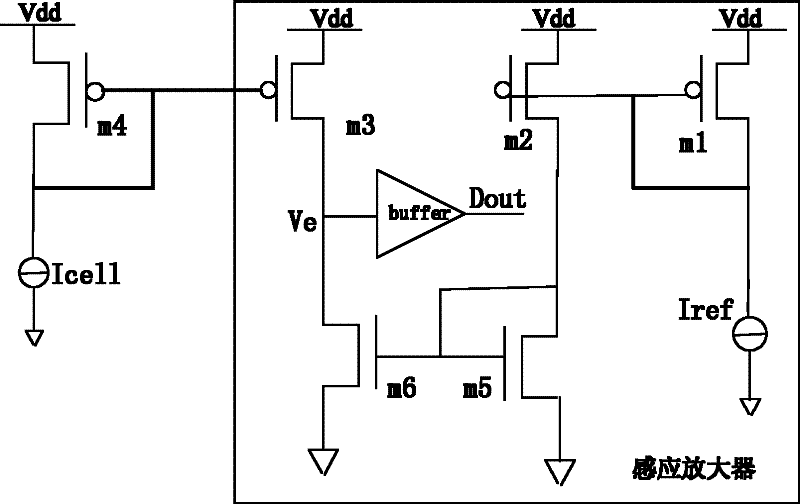
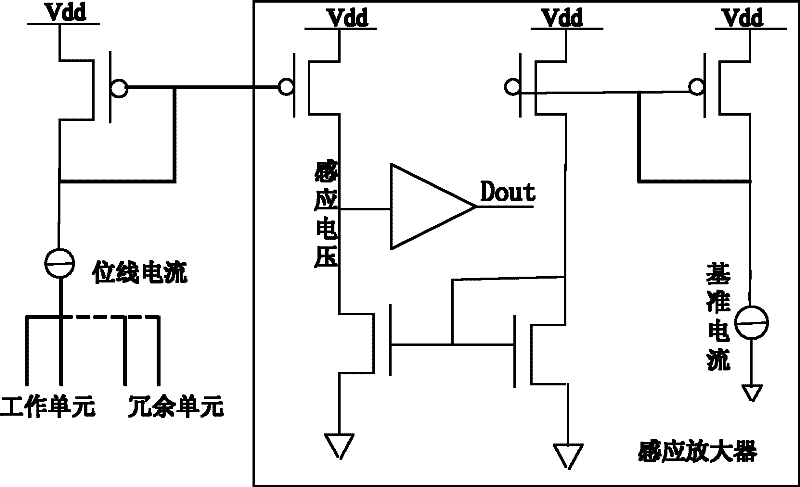
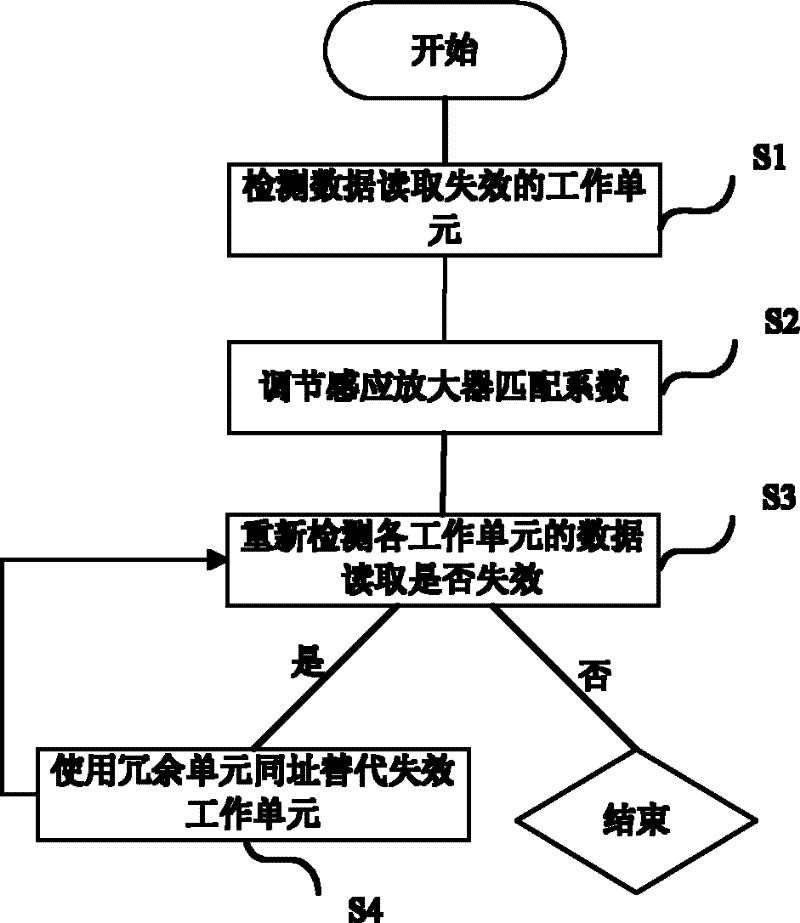
Memory and its redundant alternatives
The present invention provides a memory and a redundancy replacement method thereof. The redundancy replacement method includes: detecting a working unit that fails to read data; adjusting the matching coefficient of the sense amplifier according to the average output bit line current of each working unit; Re-detect whether the data reading of each working unit is invalid; when the data reading of the working unit is still invalid, use the redundant unit to replace the failed working unit at the same location. The invention can self-adaptively adjust the matching coefficient of the sense amplifier according to different output bit line currents of the memory cells, and replace the failed memory cells by means of redundant replacement, thereby prolonging the service life of the memory.
Owner:SHANGHAI HUAHONG GRACE SEMICON MFG CORP
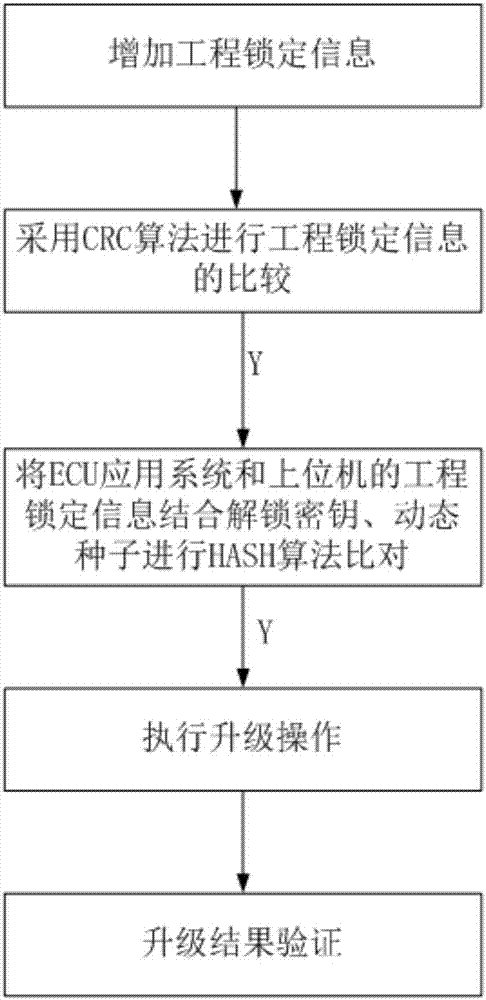
Solution for preventing ECU software of systems from being mistakenly upgraded
InactiveCN107273152AProcess safetyAvoid sending directlyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesSoftware engineeringWorkaround
The invention belongs to the technical field of software, and specifically discloses a solution for preventing ECU software of systems from being mistakenly upgraded. The solution comprises the following steps of: adding engineering locking information, and respectively putting the engineering locking information in an application code area of ECU software in a flash and a generated S19 file; before upgrading an application code of the ECU software, analyzing the engineering locking information from the S19 file by an upper computer, and carrying out algorithm comparison on the analyzed engineering locking information with engineering locking information stored in the Flash; if the algorithm comparison result is consistency, allowing the application code to be upgraded, and other wise, not carrying out any change; and after the upgrading, carrying out algorithm comparison on upgrading file data received by the ECU and S19 file data of the upper computer to determine whether the upgrading is effective or not. According to the method, the effectiveness and safety of the code are protected through adding the engineering locking information; and through the algorithm comparison, the engineering information content is prevented from being directly sent, and the unlocking is completed through combining an unlocking secret key and a random number to generate unlocking information, so that the process is safer.
Owner:ANHUI GVB RENEWABLE ENERGY TECH
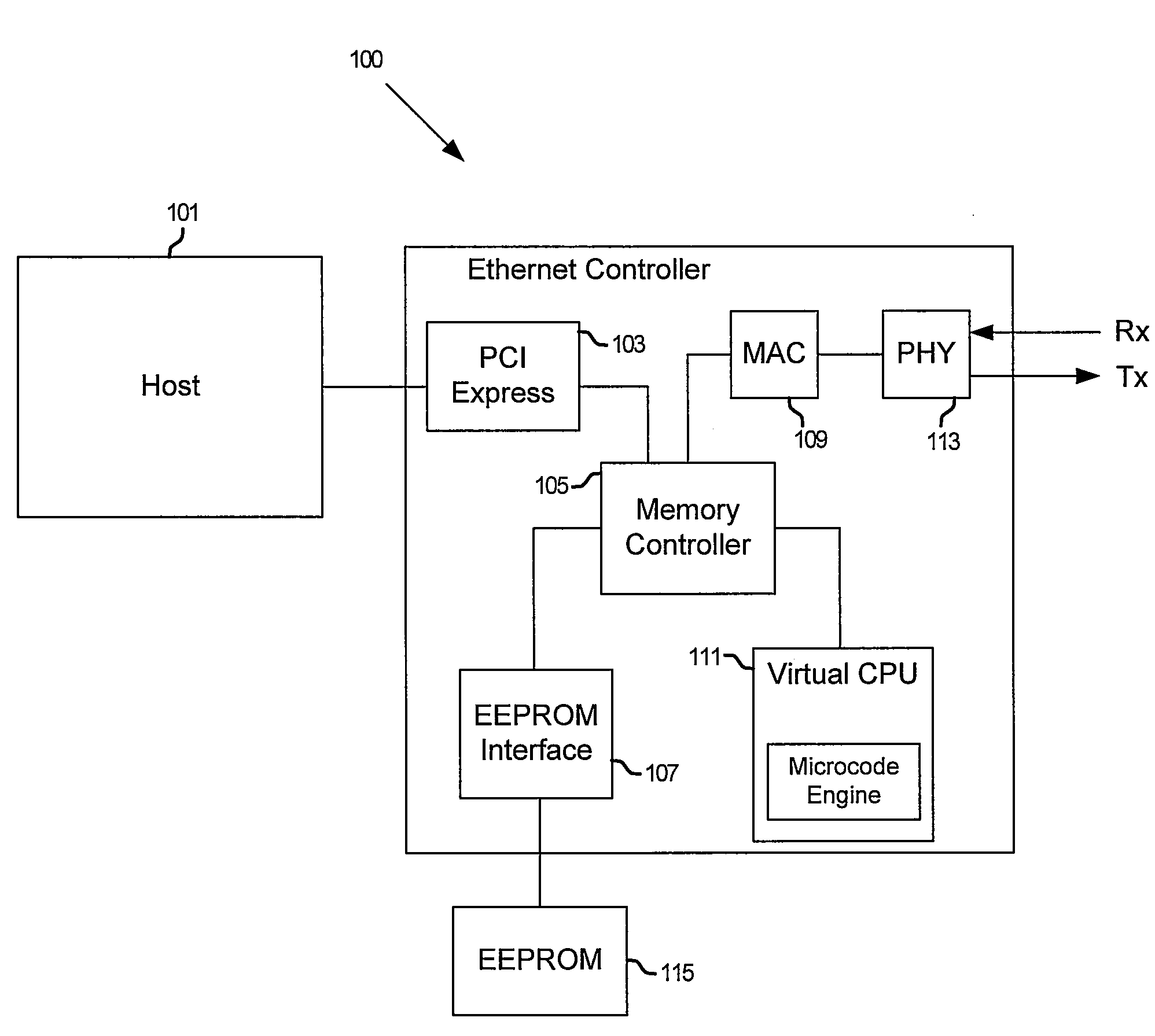
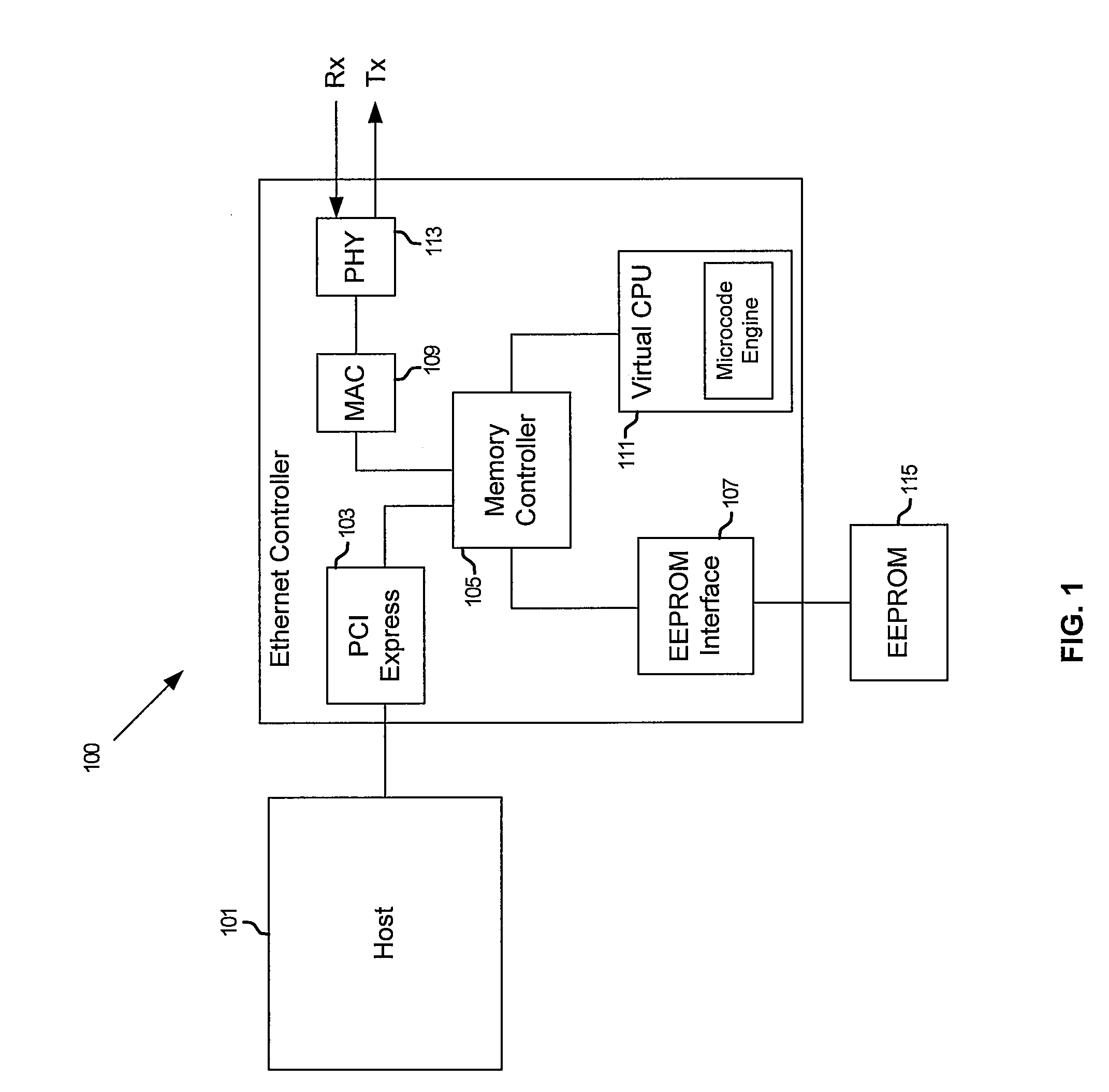
Method and system for fast ethernet controller operation using a virtual CPU
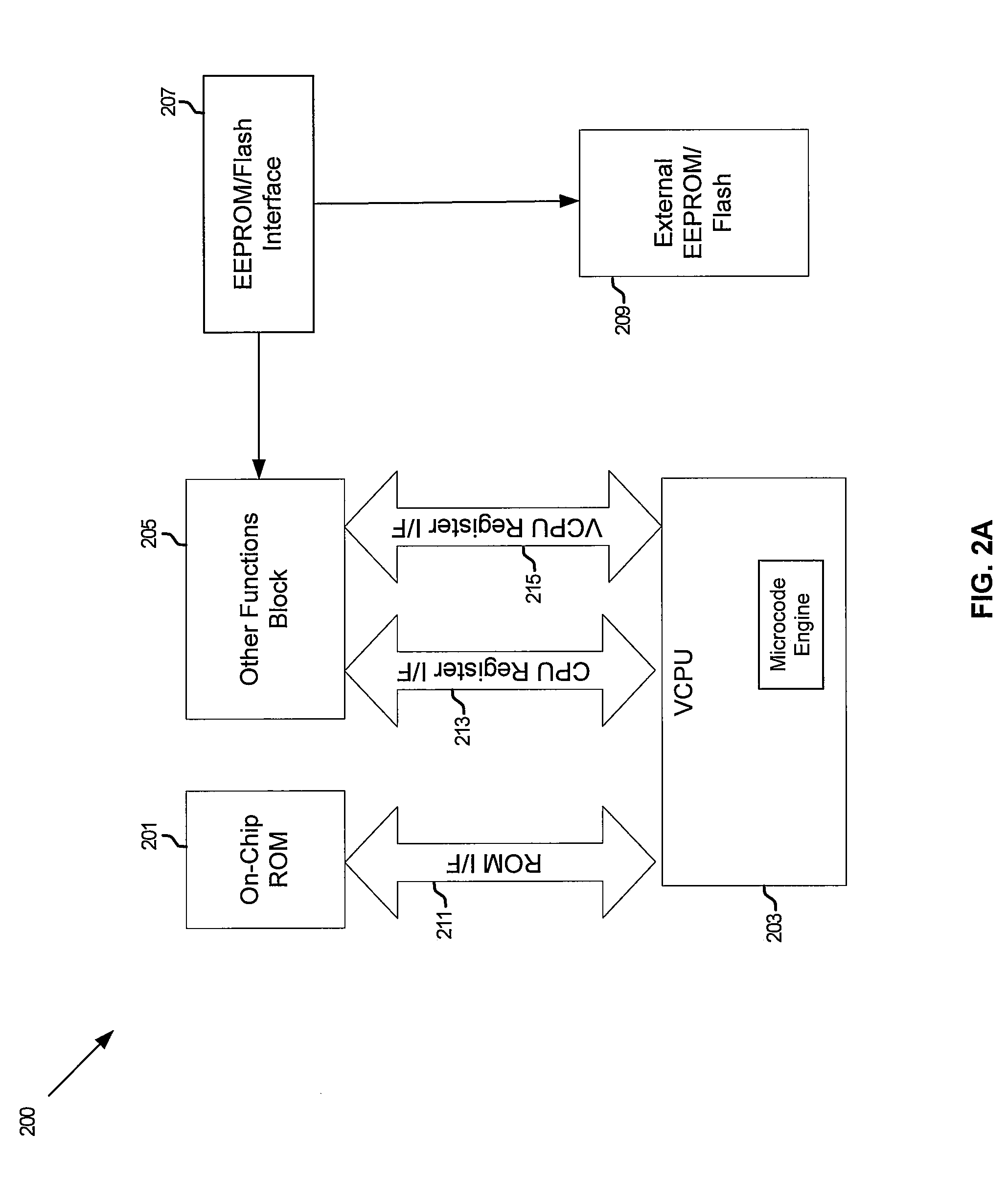
InactiveUS20080209076A1Multiple digital computer combinationsData switching current supplyManufacturing dataWorkaround
Methods and systems for fast Ethernet controller operation using a virtual CPU are disclosed and may comprise controlling an on-chip Ethernet controller utilizing a virtual CPU comprising a microcode engine that loads a single instruction and executes the instruction prior to loading or executing a subsequent instruction. The instructions may be fetched by the virtual CPU from an external non-volatile memory or on-chip ROM. The virtual CPU may initialize the Ethernet controller and provide patches for supporting hardware workarounds, wake on LAN service, and vital production data such as serial number, product name, manufacturer and related manufacturing data. The virtual CPU may power down the Ethernet controller and may be halted via a particular command and procedure.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
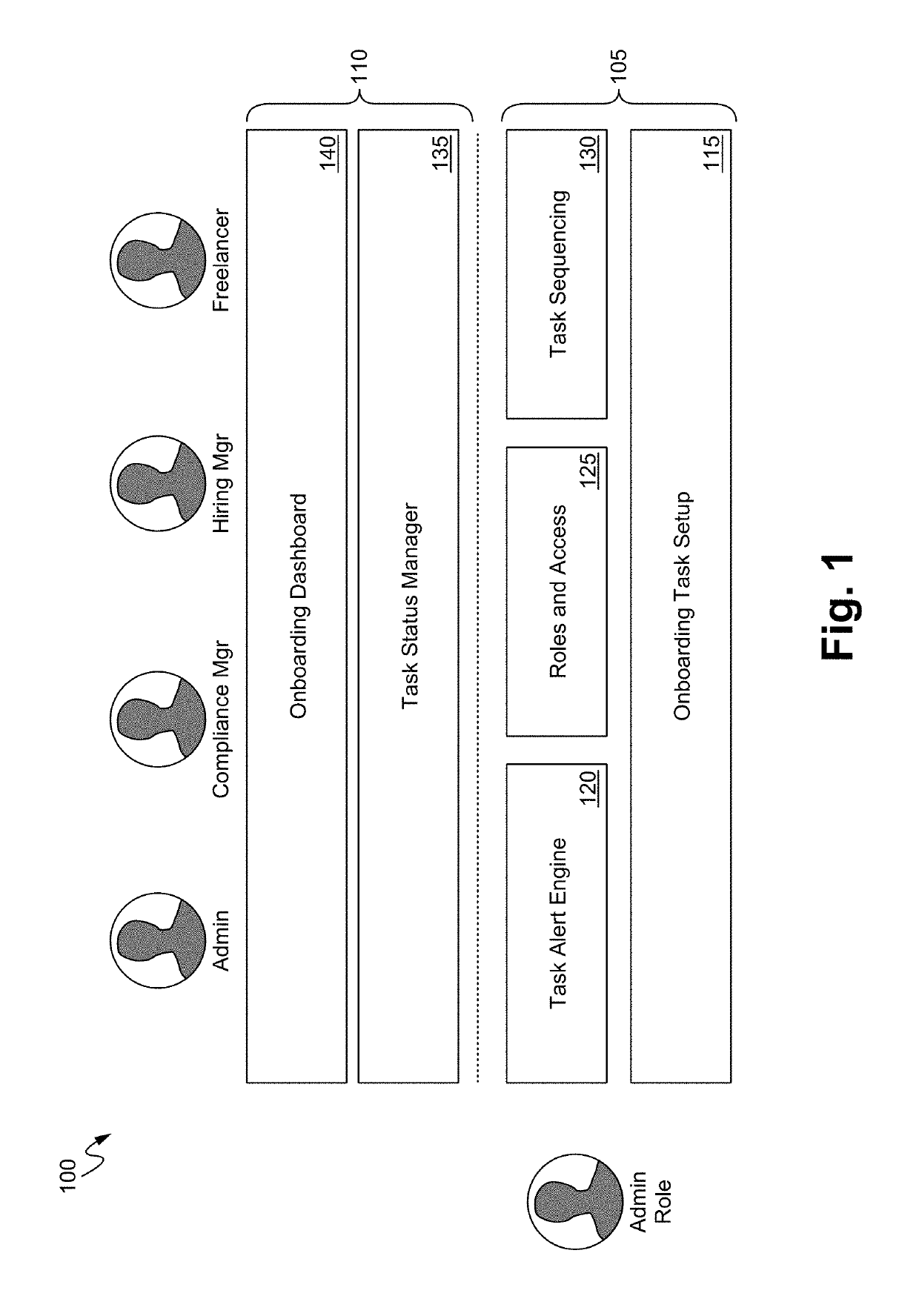
Apparatus, method and system for classifying freelancers
ActiveUS10430763B1Ensure completeEliminate delaysDatabase updatingRelational databasesMultiple categoryWorkaround
Embodiments of the present invention are directed to a classification engine that classifies freelancers in one of a plurality of categories. The classification engine captures data to perform a first classification evaluation of each engaged freelancer. The first classification evaluation is used to drive different levels of onboarding to ensure appropriate onboarding tasks are completed for each engaged freelancer before the freelancer starts work for a client. Depending on the level of onboarding, the classification engine either uses the first classification evaluation to make a determination regarding the classification of the freelancer or captures additional data to perform a second classification evaluation to make the determination. The classification engine eliminates delays, manual workarounds and helps scale work with enterprise clients.
Owner:UPWORK INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com