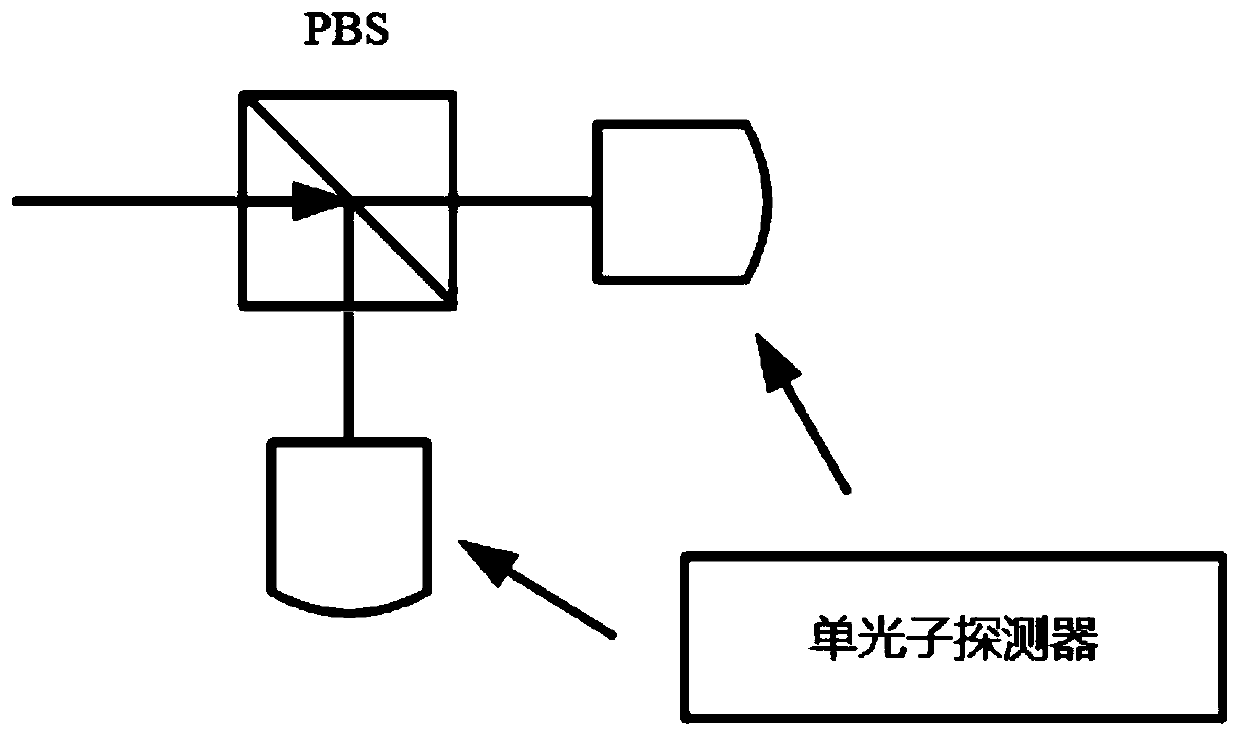
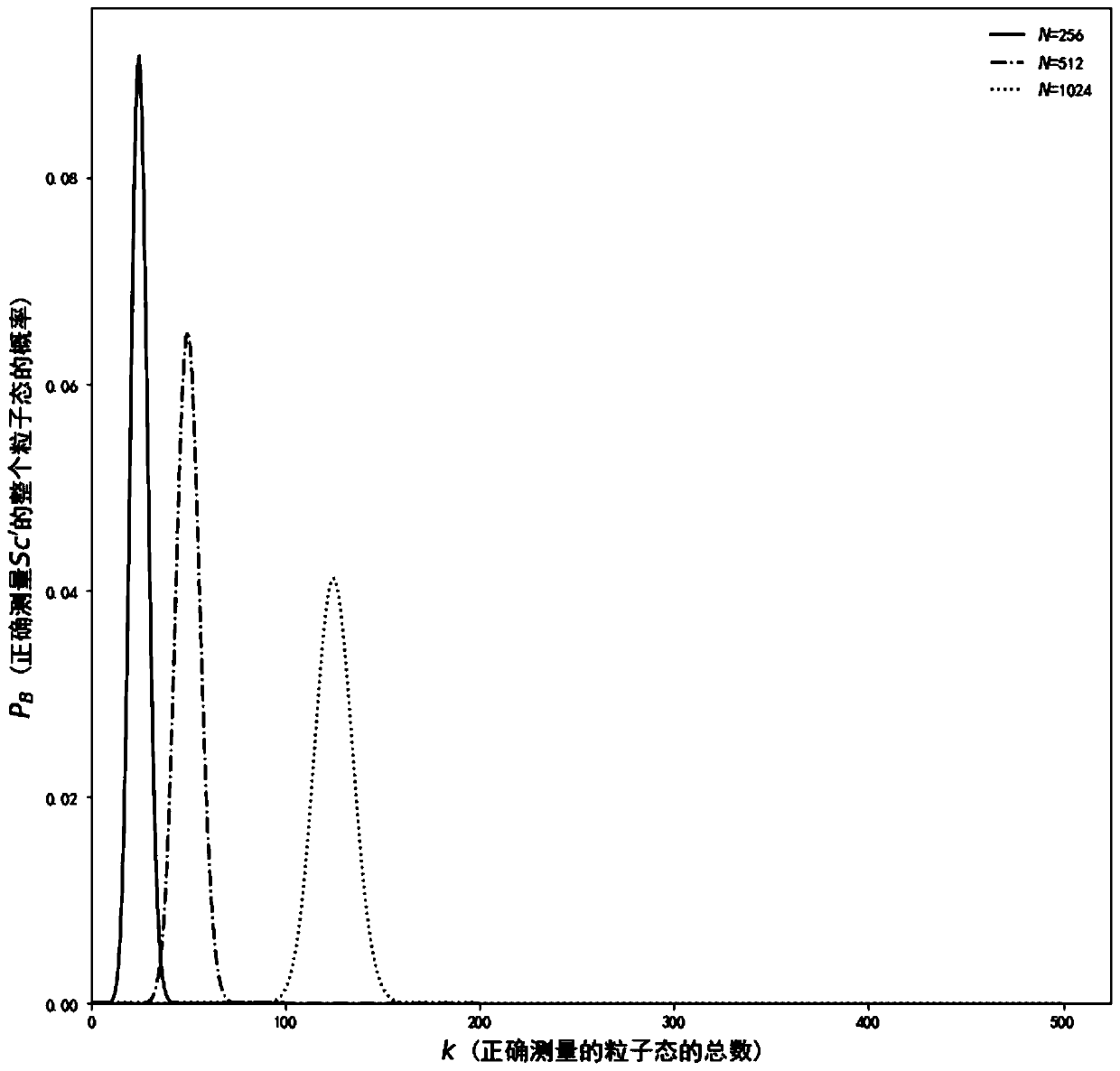
Quantum walking-based quantum secret sharing method and system with credible authentication
A quantum walk, quantum secret technology, applied in photon quantum communication, transmission system, digital transmission system and other directions, can solve the problem of secret information leakage, avoid attacks, prevent the acquisition of valid information, and resist interception/retransmission attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0105] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
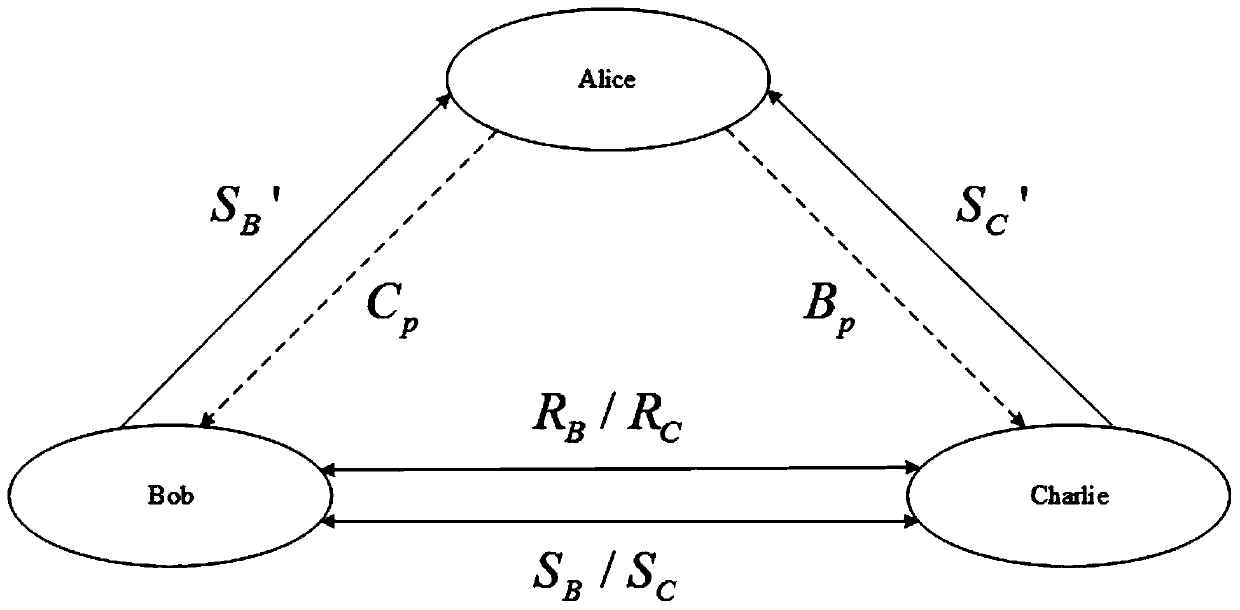
[0106] Such as figure 2 As shown, in the embodiment of the present invention, Alice is the secret distribution end, and Bob and Charlie are the secret participation ends. The method includes five stages: particle preparation stage, identity authentication stage, secret information encoding stage, secret information distribution stage and secret information recovery stage. Specifically include the following steps:
[0107] In the first step, Bob and Charlie randomly prepare N-bit single photons, each single photon is randomly located in {|0>,|1>, |+>,|->}, and the two qubit sequences formed are respectively denoted as S B and S C .
[0108] In the second step, Bob uses his identity authentication key h Bob (S ID-Bob ) to S B Each photon in performs the following operations: if h Bob (S ID-Bob ) with the i-th value of 0, then for the qubit sequ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com