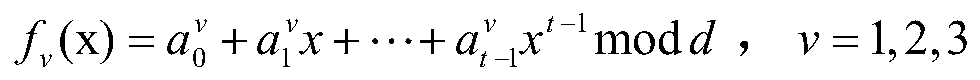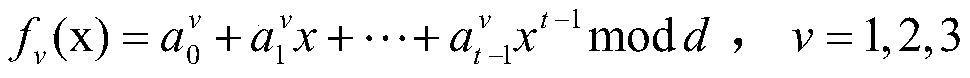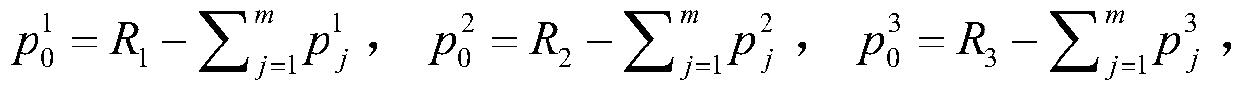Verifiable quantum secret sharing method
A quantum secret and secret sharing technology, applied in the field of verifiable quantum secret sharing, can solve problems such as not meeting the security requirements of secret sharing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The technical solutions of the present invention will be further described below in conjunction with specific embodiments.
[0028] A verifiable quantum secret sharing method, comprising the following steps:
[0029] Step 1, sub-secret distribution stage
[0030] Let Alice denote the secret distributor, Bob 1 , Bob 2 ,..., Bob n represent n agents respectively, the specific process is as follows:
[0031] (1) Alice randomly selects three polynomials
[0032]
[0033] here, in As the main secret, GF(d) is a finite field whose order is an odd prime number d;
[0034] (2) For each agent Bob j (j=1,2,...,n), Alice calculates f v (x j )(v=1,2,3) as Bob j subsecret of x j for Bob j public identity information of , and x j ≠x r Unless j=r; then, Alice uses the secure channel to transfer f 1 (x j ), f 2 (x j ), f 3 (x j ) to Bob j ;
[0035] Step 2. Secret sharing stage
[0036] Suppose Alice intends to share the secret M 1 and M 2 Distributed to m ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com