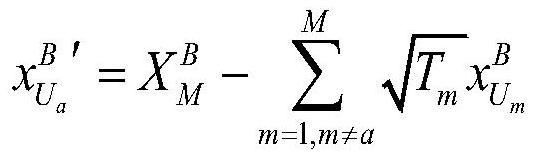Continuous variable quantum secret sharing implementation method capable of autonomously selecting users, electronic equipment and computer readable storage medium
A self-selecting, quantum-secret technology, applied to electrical components and key distribution, can solve problems such as high cost of use, low communication efficiency, and low detection efficiency, and achieve the effects of ensuring security, improving security, and having a wide range of applications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
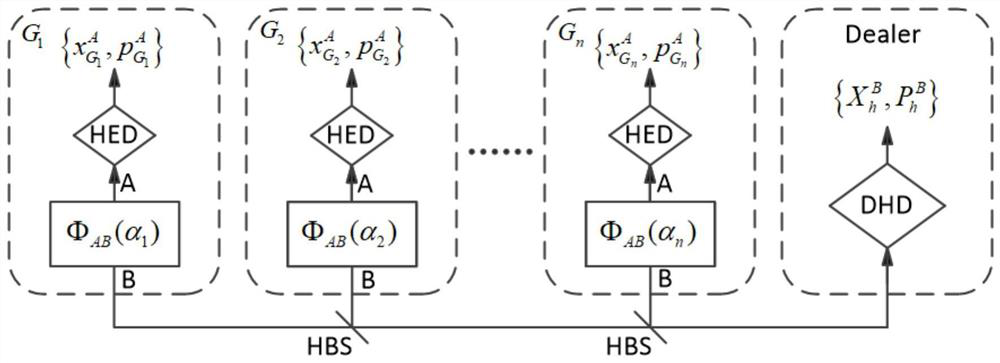
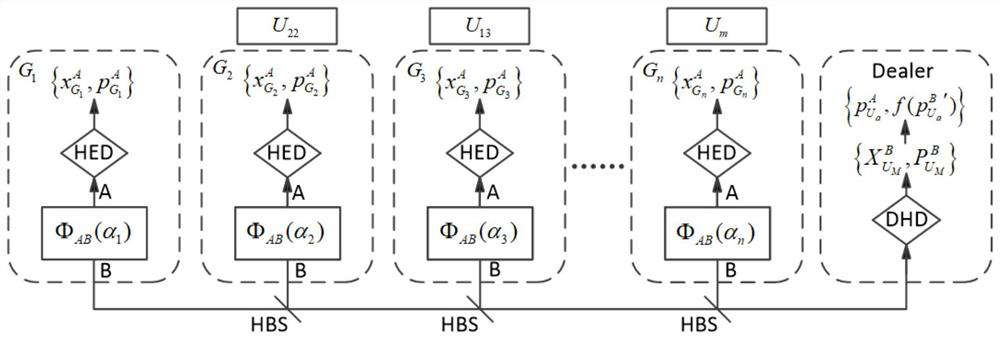
[0046] The method for implementing continuous variable quantum secret sharing that can independently select users includes the following steps:
[0047] Step 1, all participants generate a dual-mode entangled state, and use the heterodyne detector HED to perform projection measurement on the mode A of the dual-mode entangled state to obtain two regular components Project the modulo B to any coherent state of discrete modulation and send it to the data distributor Dealer. The data distributor uses the double homodyne detector DHD to detect the two regular components of the modulo B coherent state sent by all participants until sufficient Quantitative initial data information;
[0048] Step 2, the data distributor Dealer randomly selects legitimate participants among all participants, and reorders them, and calculates the regular component of the modulo B coherent state when each legitimate participant is the only honest participant based on Split the initial secret informa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com