Quantum secret sharing method and system without monitoring channel
A quantum secret and channel technology, applied in the field of quantum communication, can solve the problems of complex system and execution operations, large information acquisition value, and difficult quantum cryptography sharing scheme.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
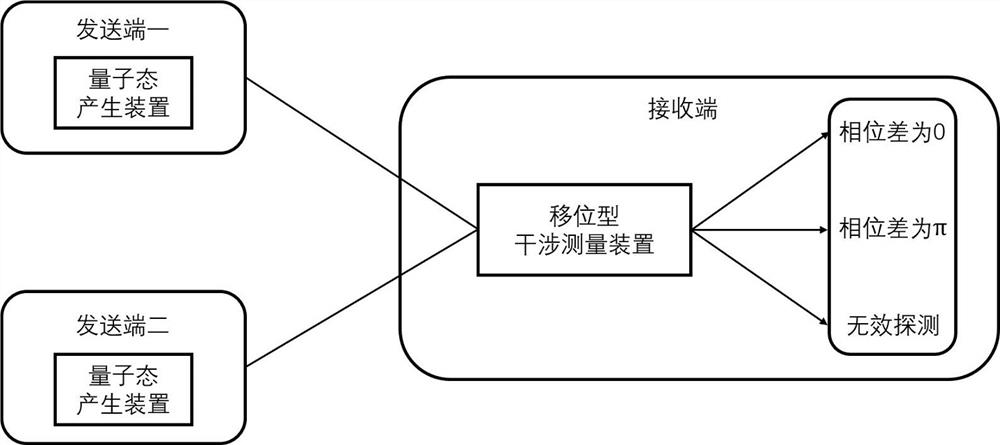
[0058] In this embodiment, the specific structure of the quantum secret sharing system that does not need to monitor the channel is as follows figure 2 As shown, it includes: sender 1, sender 2, and receiver. In this embodiment, the channel symmetry is considered, that is, the channel from sender 1 to the receiver is symmetrical to the channel from sender 2 to the receiver.
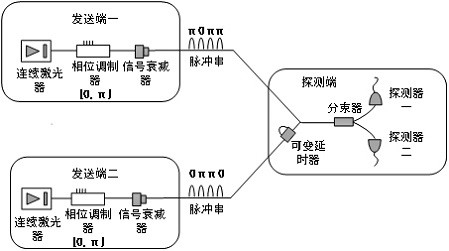
[0059] Sending end 1 and sending end 2 have the same structure, both including: continuous laser, intensity modulator and signal attenuator; among them, the continuous laser generates a phase-stable and time-continuous optical signal; the phase modulator is used to phase-encode the passing optical signal (0 or π) to obtain a pulse sequence signal; the signal attenuator is used to perform weak light modulation on the pulse sequence optical signal output by the phase modulator, attenuate it to be lower than the single photon level, and then output it to the detection end.
[0060] The receiving end include...
Embodiment 2
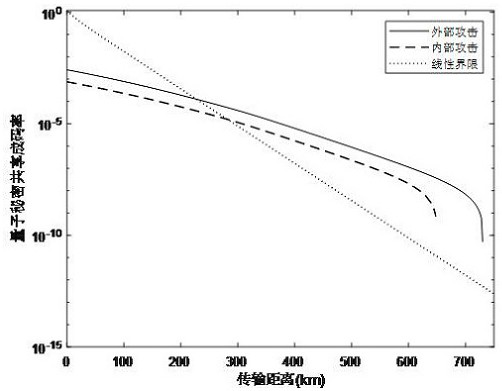
[0093] This implementation is implemented in an asymmetric channel, that is, the length of the quantum channel from Alice to Charlie is different from the length of the quantum channel from Bob to Charlie, and the total light intensity of the pulse train sent by Alice to Charlie is different from the total light intensity of the pulse train sent by Bob to Charlie. The rest of the operations are the same as in the first embodiment, and the formula for calculating the coding rate is still the same as in the first embodiment.
Embodiment 3
[0095] In Embodiments 1 and 2, Alice and Bob use time patterns to encode quantum states. Under this scheme, only one of the L pulses in each round of experiments can be used to generate a security key, resulting in low channel transmission capacity. .
[0096] In this embodiment, the spatial light mode will be used to encode and decode the quantum state, and the encoding space of the secret information will be extended to the L-dimensional system, so as to improve the communication capacity and spectral efficiency of quantum secret sharing.
[0097] Alice and Bob prepare photon sequences by encoding bit strings of length L on the phases of different orbital angular momentum eigenstates of single photons, and then send the photon sequences to Charlie simultaneously through an insecure quantum channel.
[0098] At the receiving end, Charlie implements displacement-type interferometry by inserting a phase element on one arm of a balanced interferometer. Other operations are the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com