Attack studying and judging method and system for network attack and defense test platform and medium
A test platform and network attack technology, applied in the field of network security, to achieve the effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
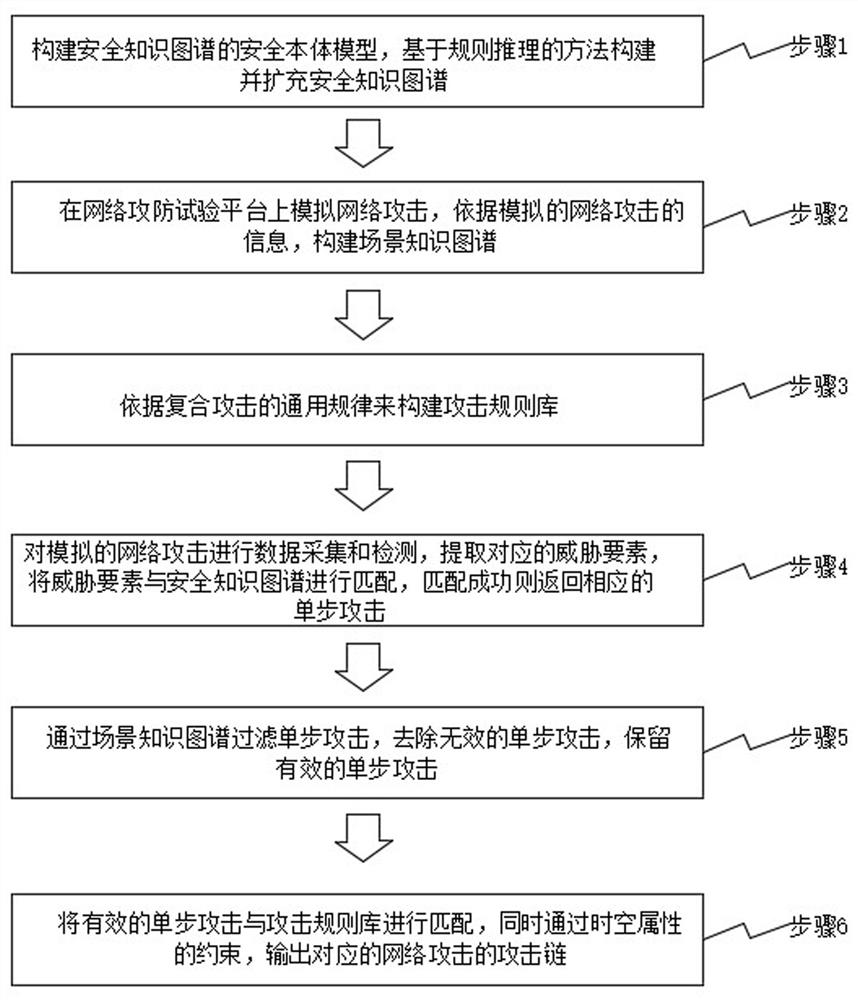
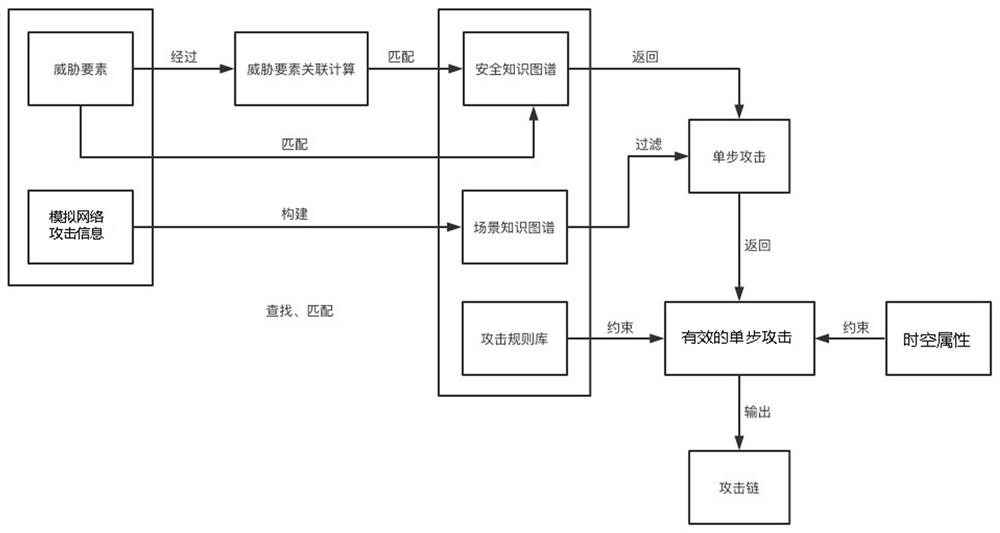
[0049] see figure 1 , 2. The attack research and judgment method oriented to the network attack and defense test platform of the present invention at least includes the following steps:
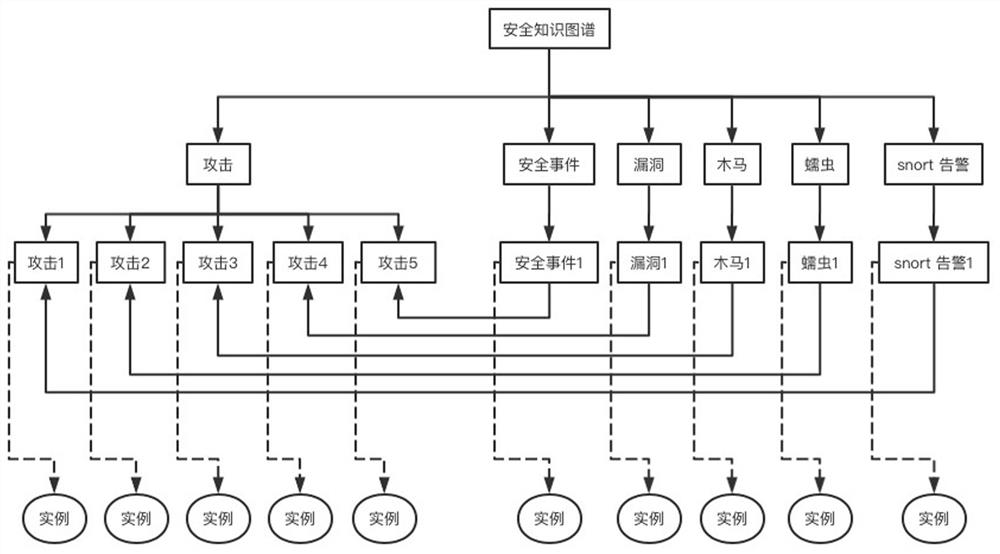
[0050] Step 1: Construct a security ontology model of the security knowledge graph, construct and expand the security knowledge graph based on the rule-based reasoning method;
[0051] Step 2: Simulate network attacks on the network attack and defense test platform, and construct a scene knowledge graph based on the simulated network attack information;
[0052] Step 3: Build an attack rule base according to the general laws of compound attacks;
[0053] Step 4: Perform data collection and detection of simulated cyber attacks, extract corresponding threat elements, match the threat elements with the security knowledge map, and return the corresponding single-step attack if the matching is successful;
[0054] Step 5: Filter single-step attacks through the scene knowledge graph, remove invalid single-st...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com