Rootkit detection mechanism and detection method based on kernel-based virtual machine
A technology of a kernel virtual machine and a detection method, which is applied to the rootkit detection mechanism and detection field based on a kernel virtual machine, can solve the problems of lag, the detection thread is easily affected by the rootkit, and the coupling is not good, so as to achieve the effect of small attack.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
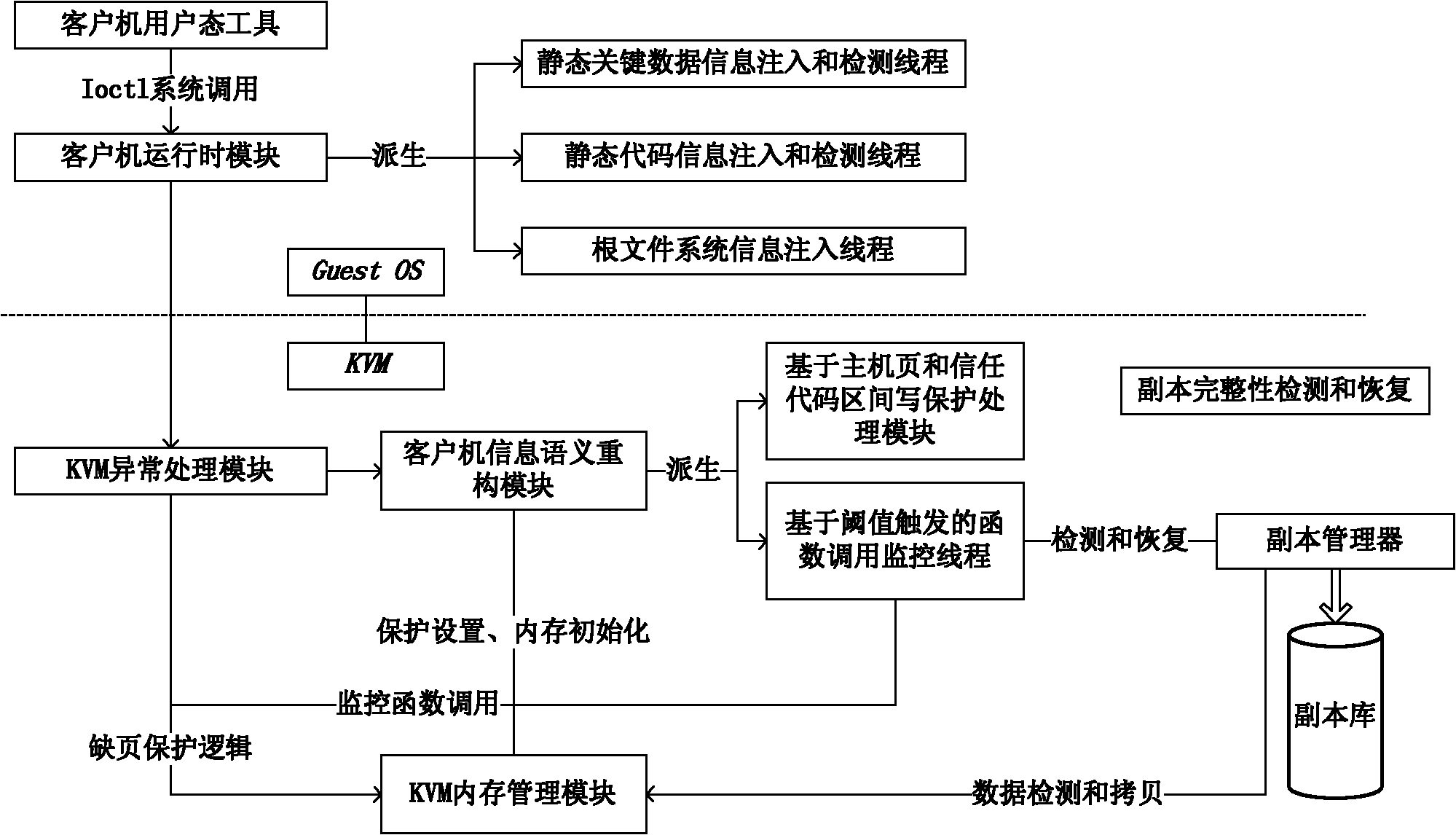
[0027] The invention is based on the rootkit detection mechanism of the kernel virtual machine. Firstly, the rootkit implementation form object is abstracted into four types: static kernel code, static kernel data, dynamic allocation code function and kernel heap space data structure.
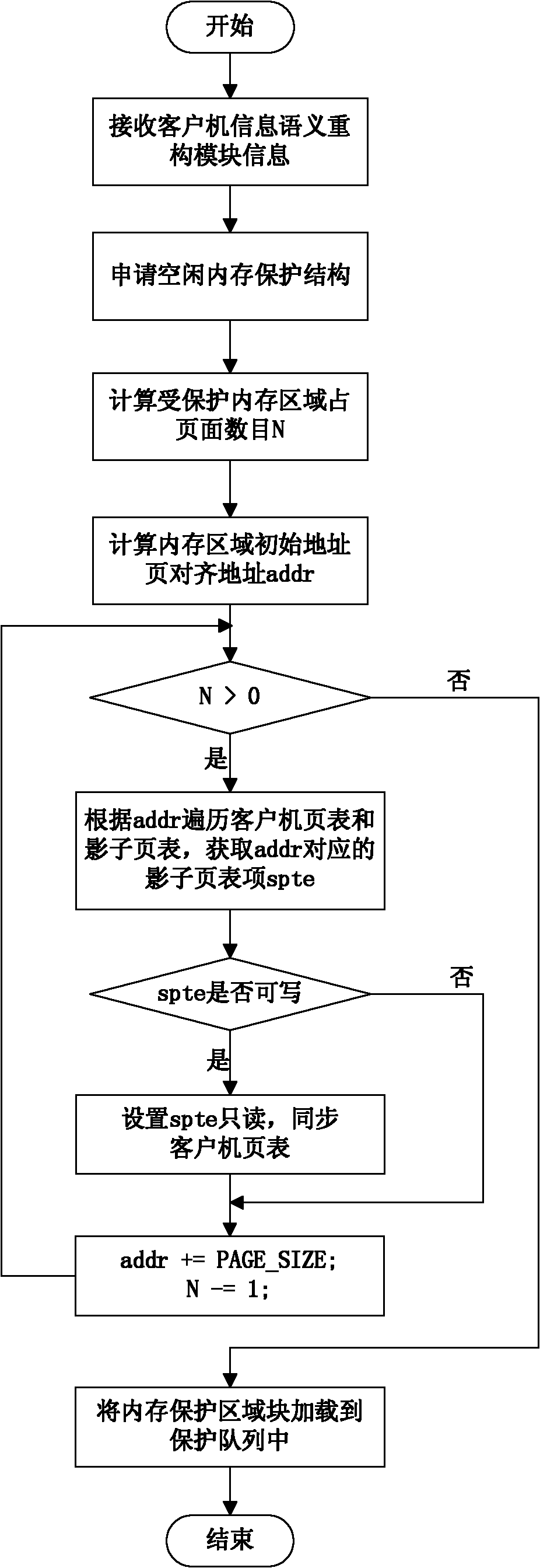
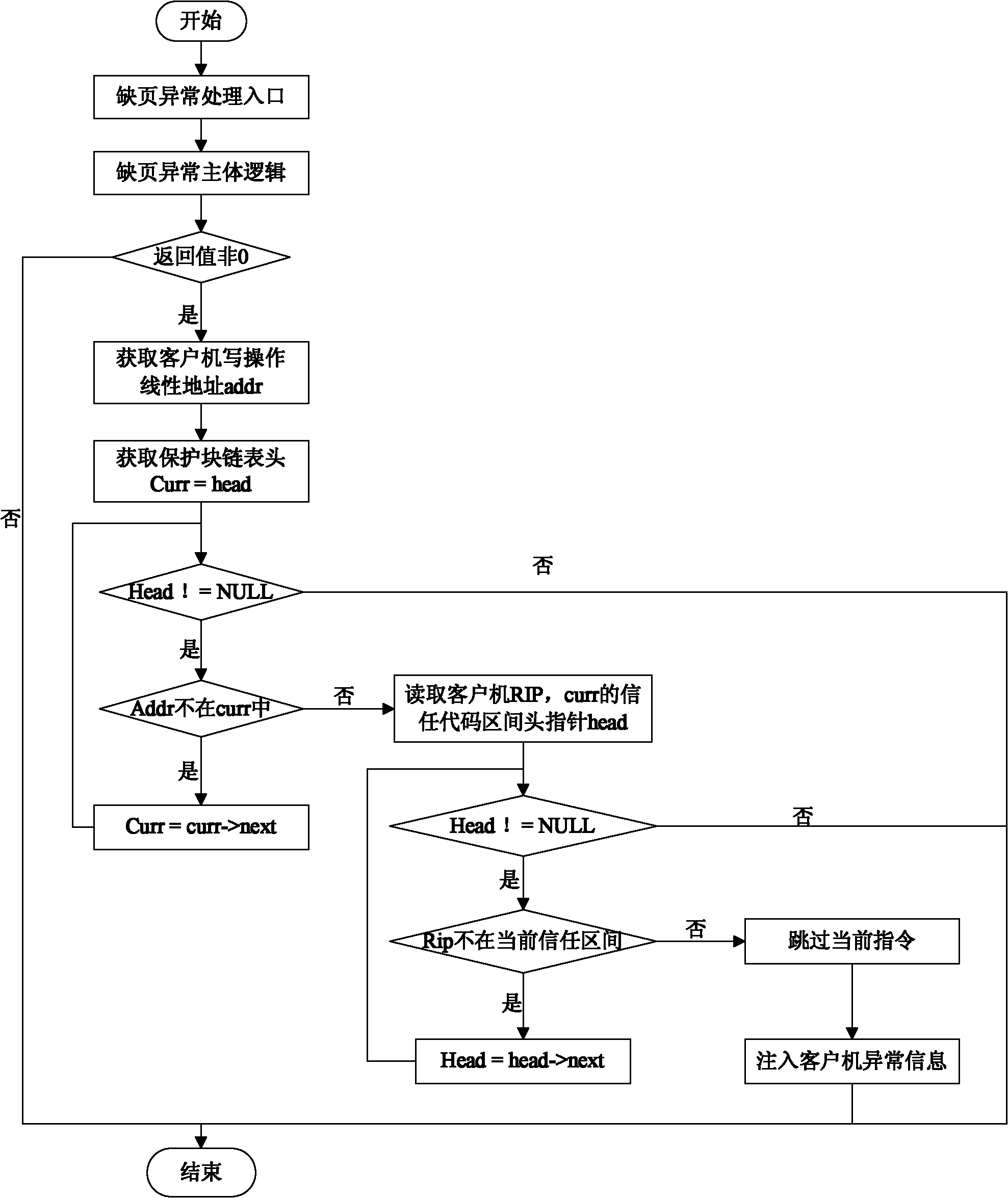
[0028] A runtime module and a monitoring thread are loaded in the client computer, wherein the purpose of the runtime module is to obtain relevant information of the client computer during runtime. As the underlying virtual machine monitor KVM, it cannot obtain client semantic information other than system-level information. Therefore, the runtime module of the client implements semantic interaction with the underlying client at runtime. The information obtained by the runtime module of the client computer during runtime includes: interrupt vector table, system call table, kernel code segment information, key data information of the file system, and the like. The runtime module of the client co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com