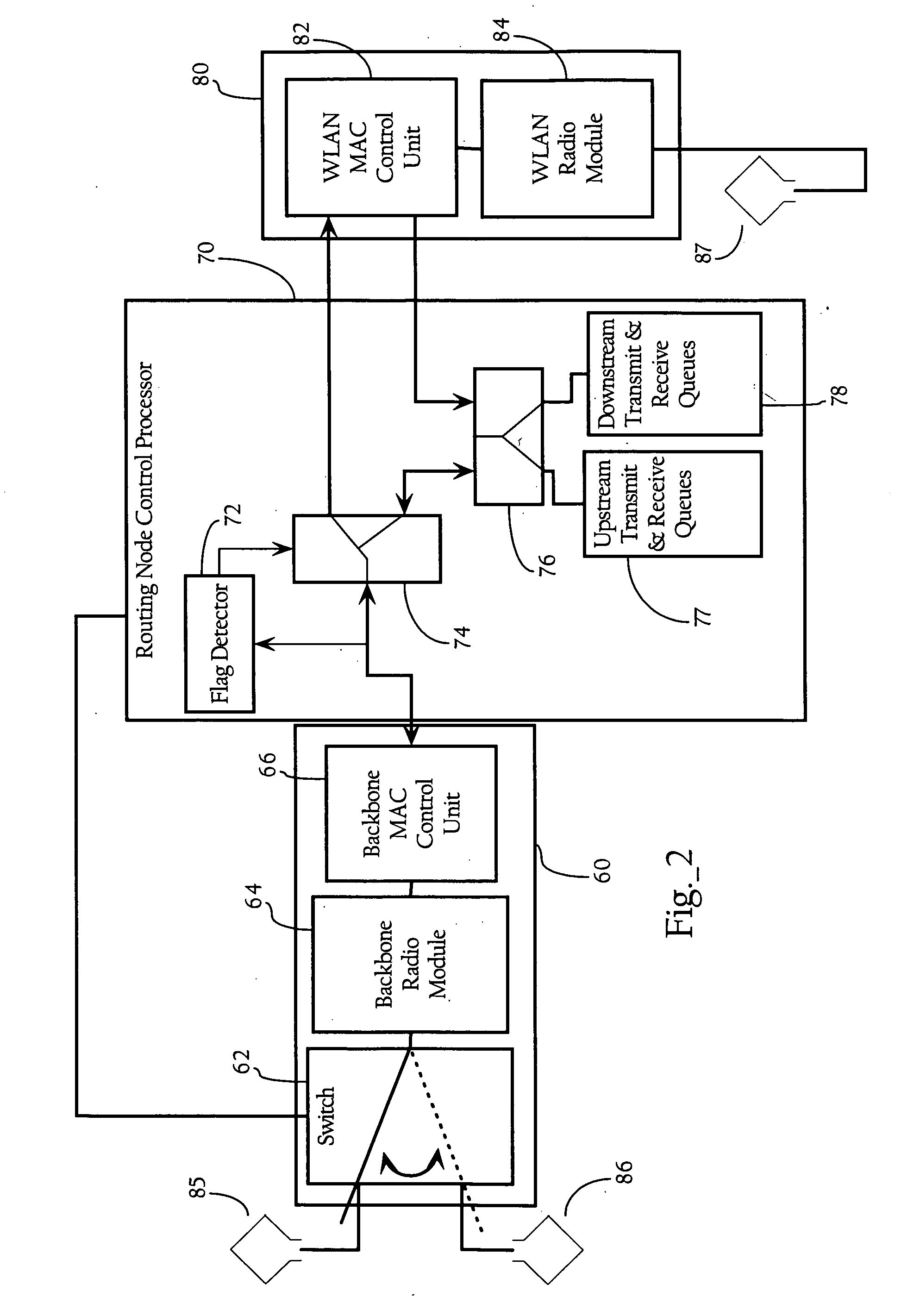
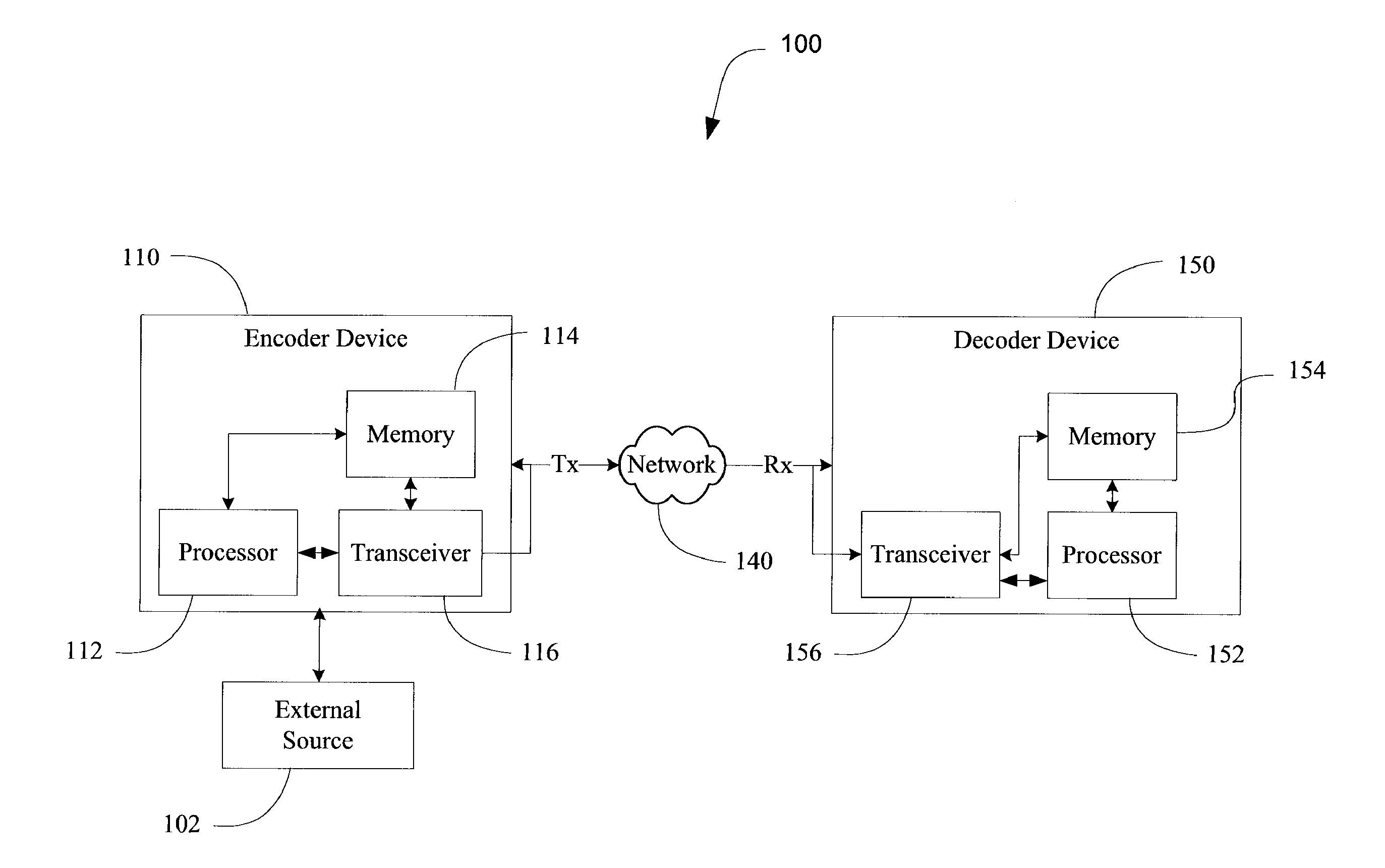
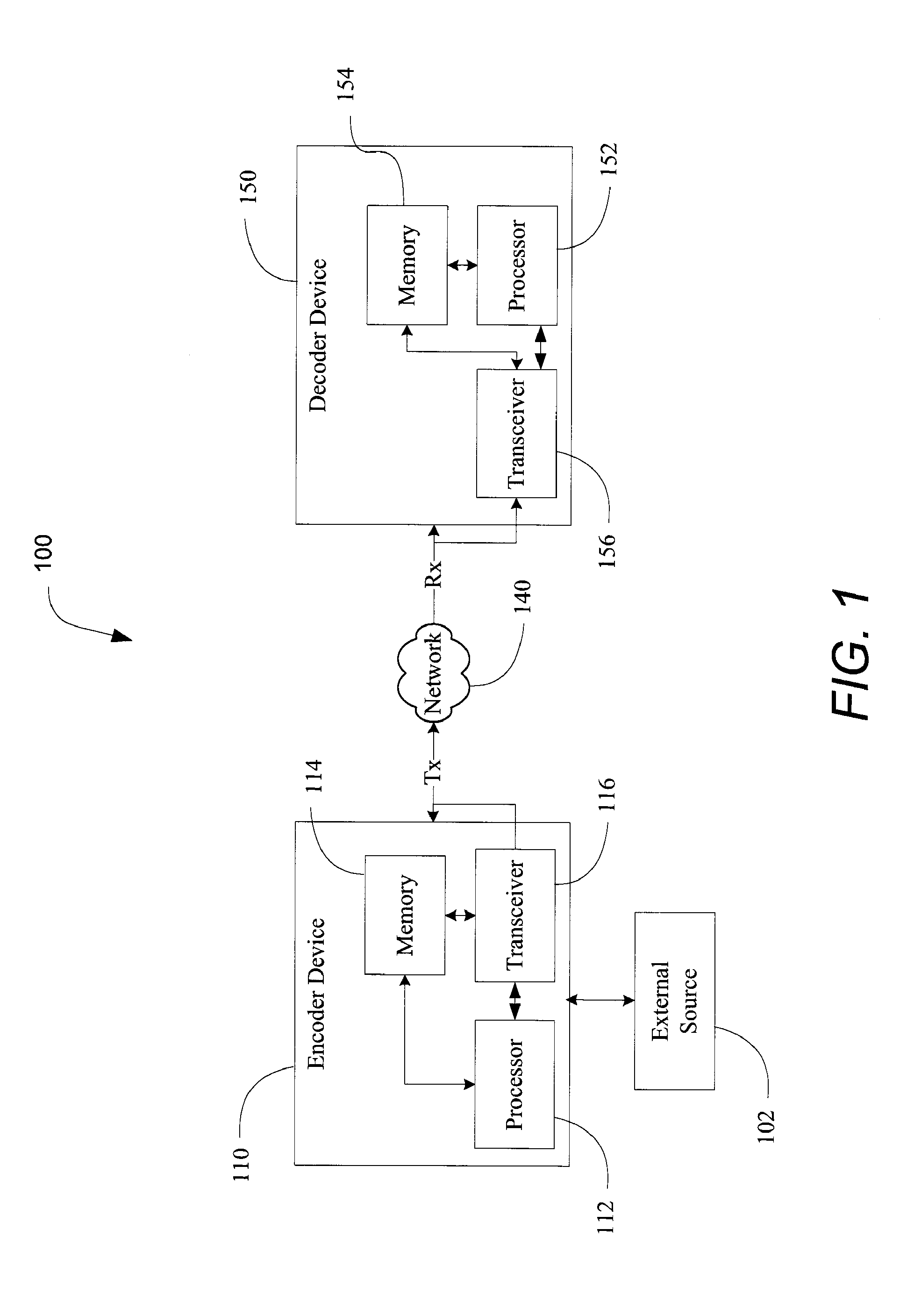
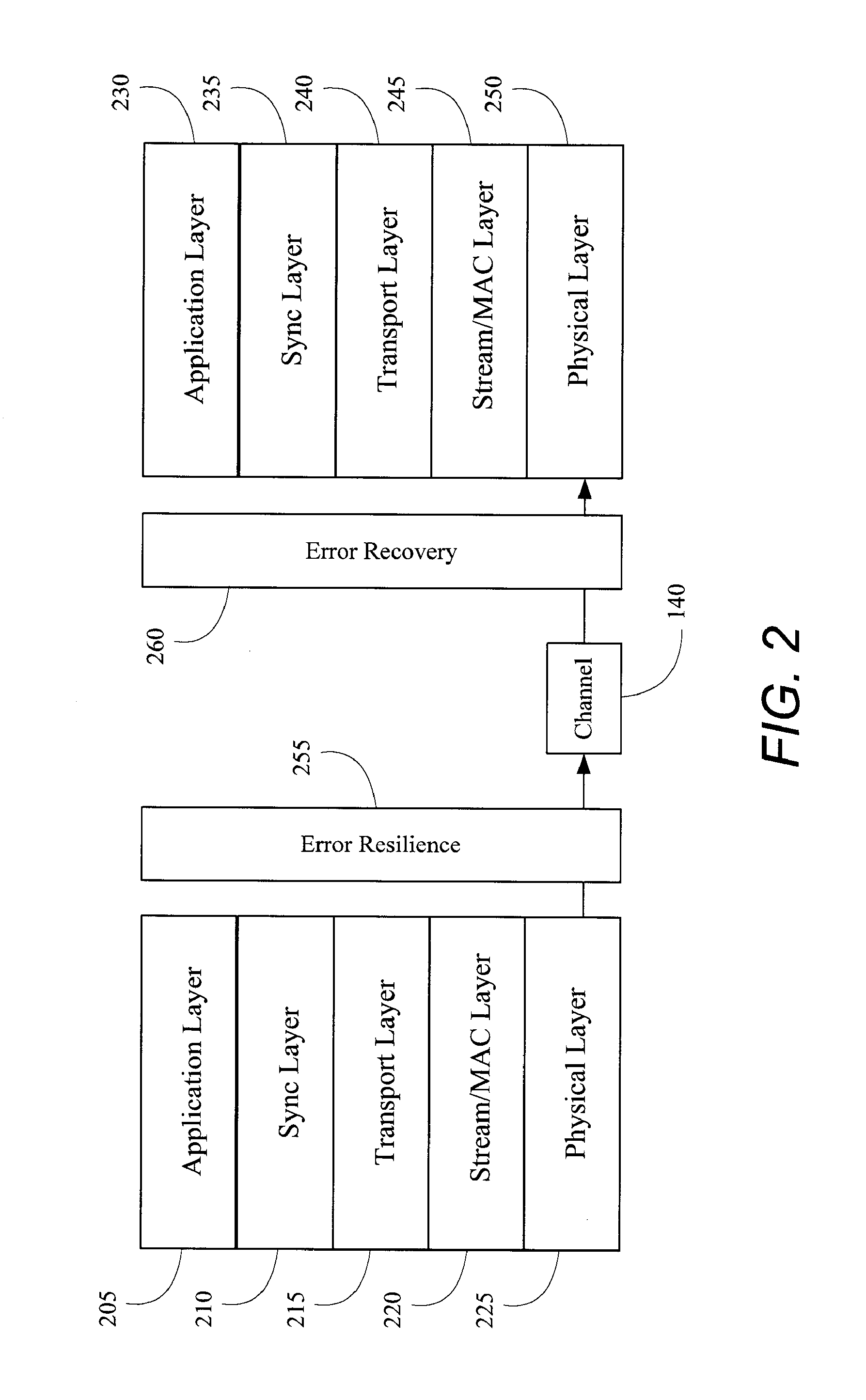
Patents
Literature
1259 results about "Recovery mechanism" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Recovery mechanism. Designated indigenous or surrogate infrastructure that is specifically developed, trained, and directed by US forces to contact, authenticate, support, move, and exfiltrate designated isolated personnel from uncertain or hostile areas back to friendly control.
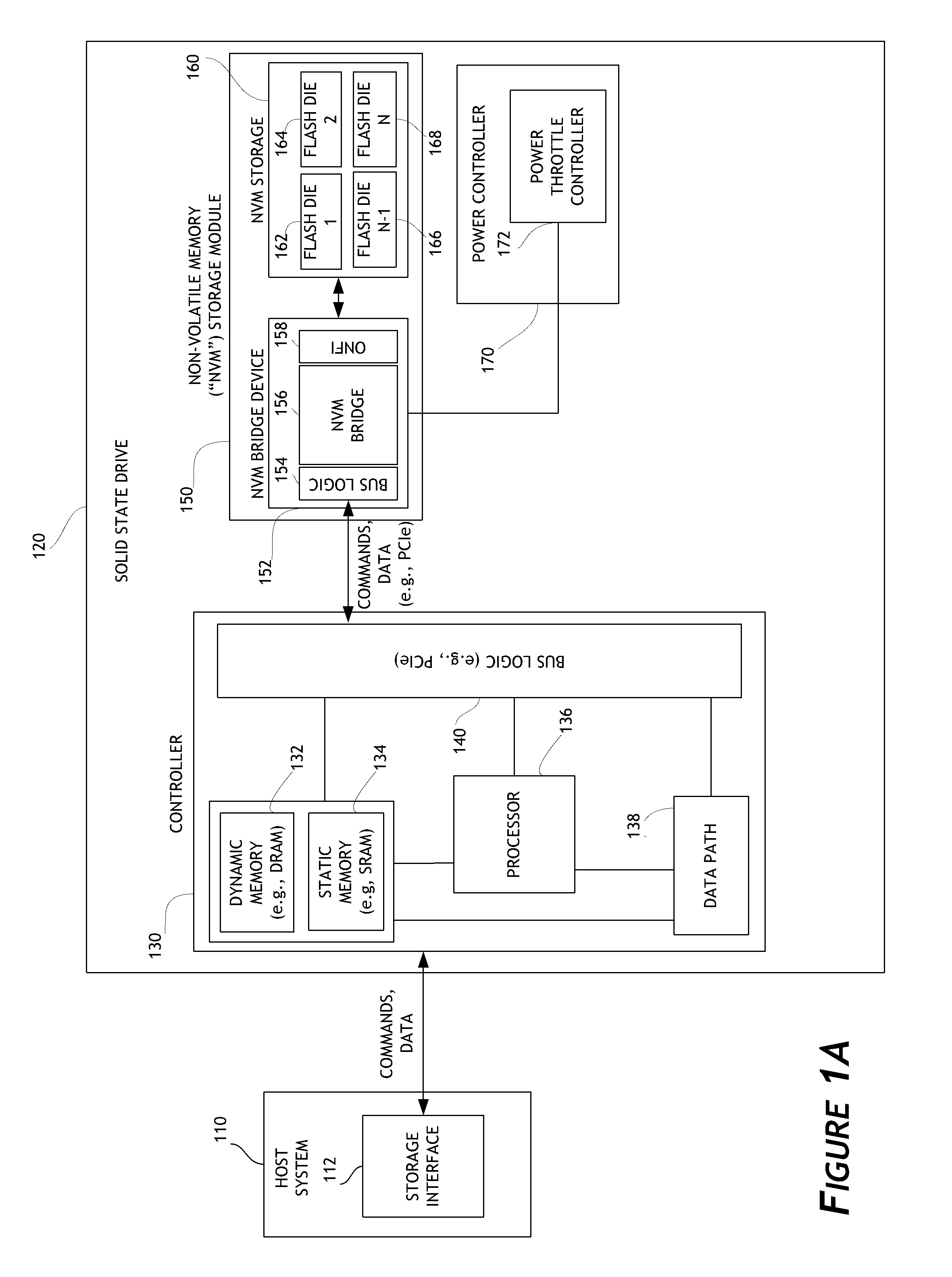
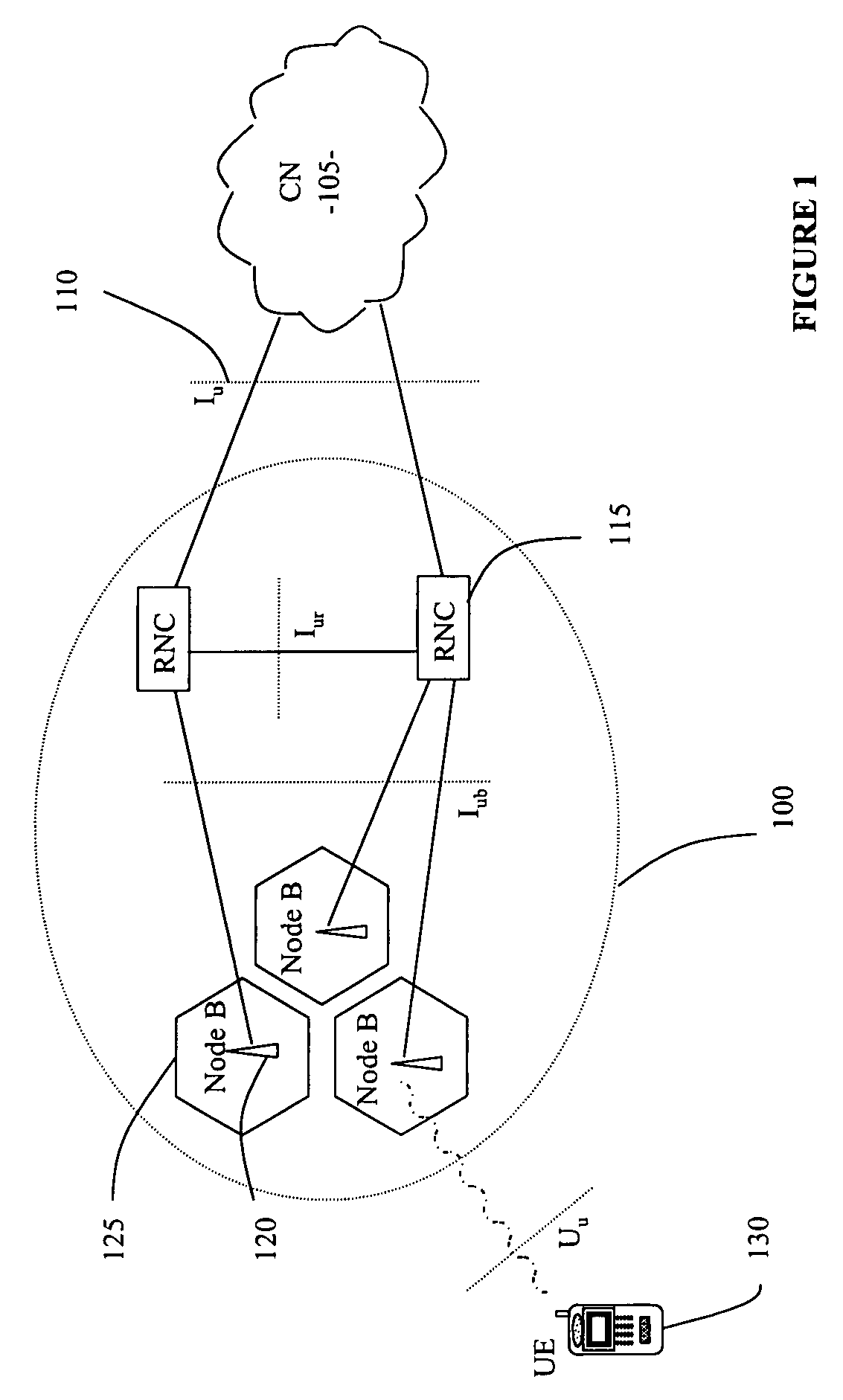
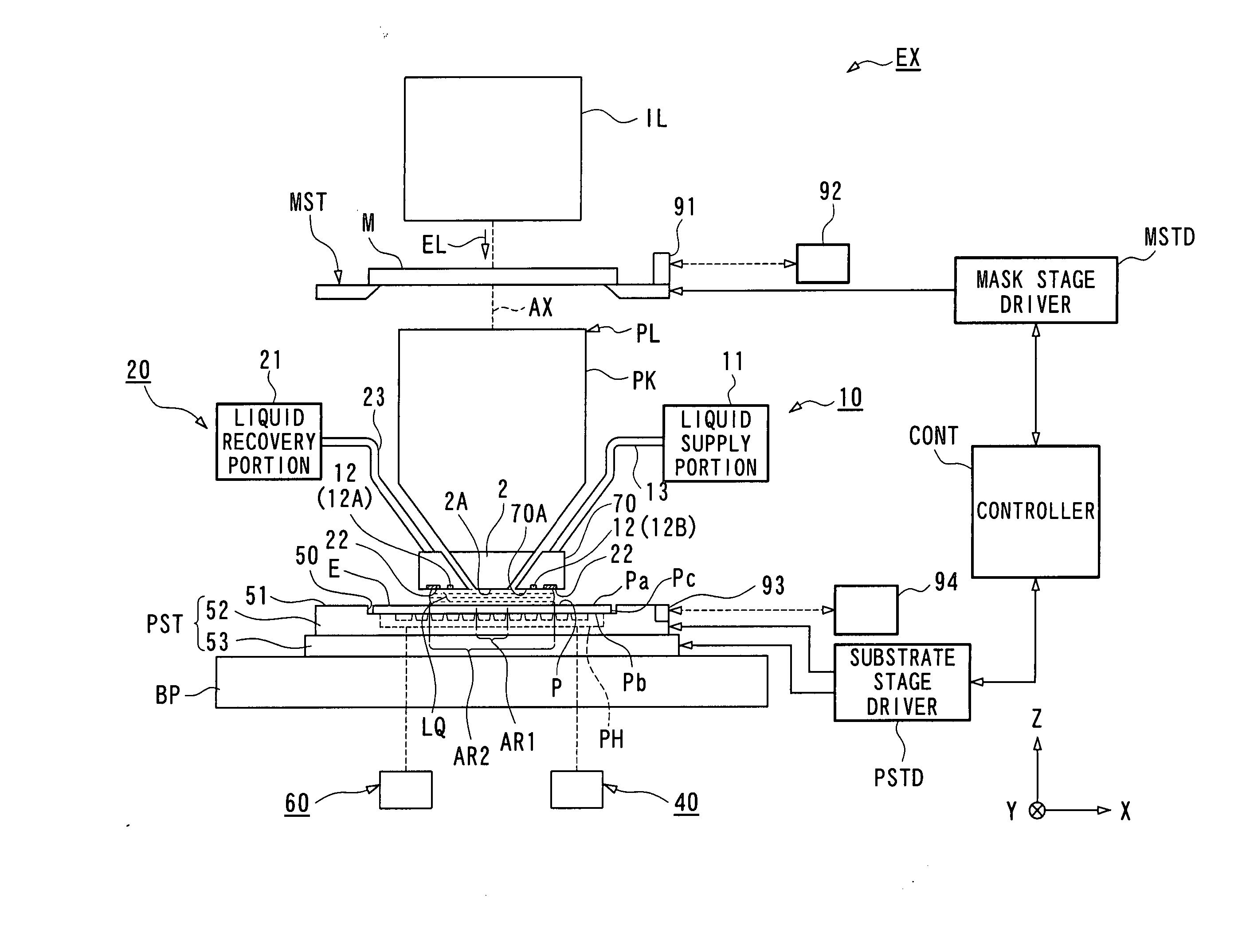
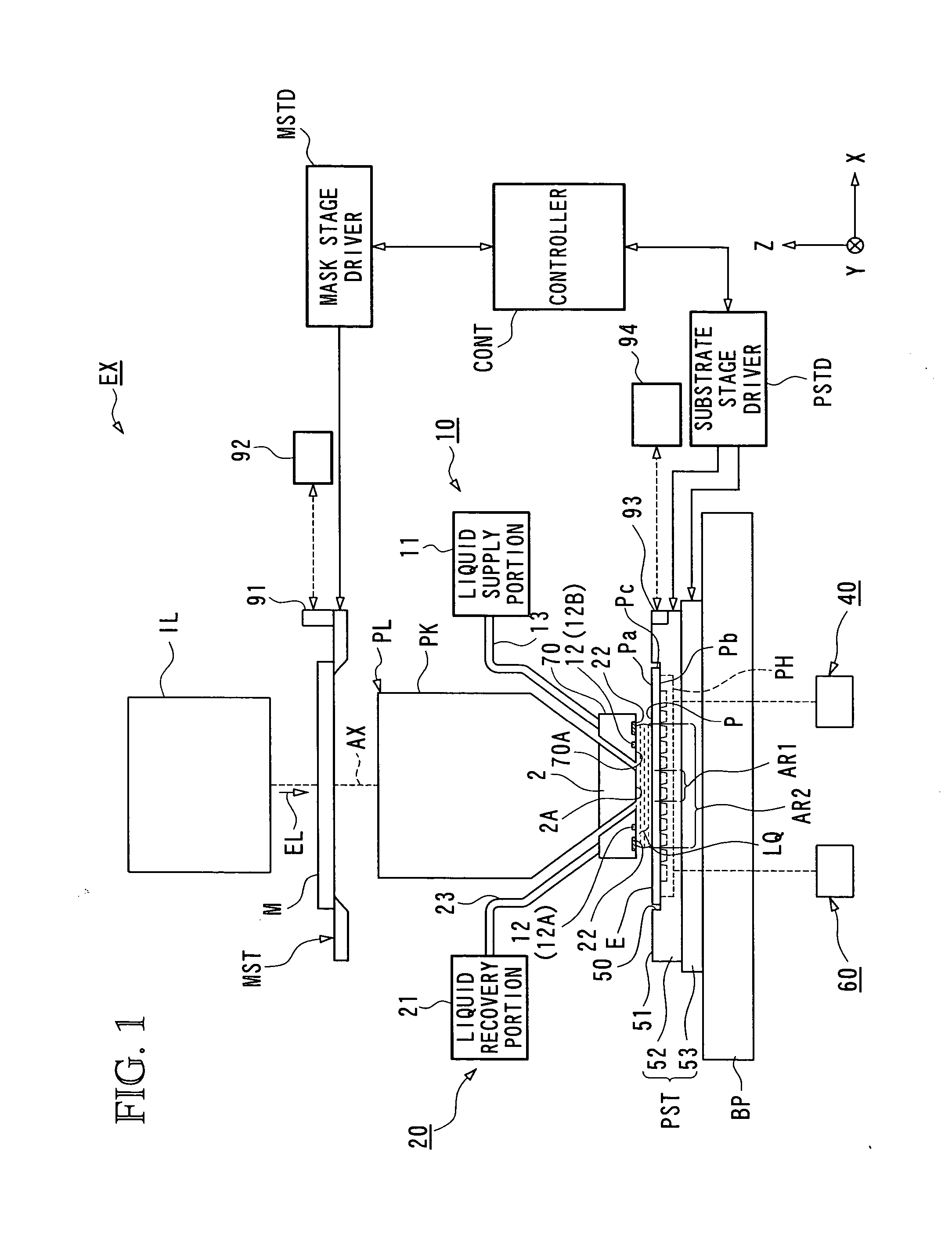
Exposure apparatus and device manufacturing method
InactiveUS20050259234A1Pressure of waterRaise transfer toSemiconductor/solid-state device manufacturingPhotomechanical exposure apparatusEngineeringElectrical and Electronics engineering
Liquid is supplied by a supply mechanism to a space between a lens and a wafer via a supply nozzle on one side of the lens, and the liquid is recovered by a recovery mechanism via a recovery pipe on the other side of the lens. When the supply and the recovery of the liquid are performed in parallel, a predetermined amount of liquid (exchanged at all times) is held between the lens and the substrate on the stage. Accordingly, when exposure (pattern transfer on the substrate) is performed in this state, an immersion method is applied and a pattern is transferred with good precision onto the substrate. In addition, in the case the liquid leaks out from under the lower edge of a peripheral wall, the liquid that could not be recovered is recovered by an auxiliary recovery mechanism via a slit. And, by such operations, the substrate is freed from the residual liquid on the substrate.
Owner:NIKON CORP
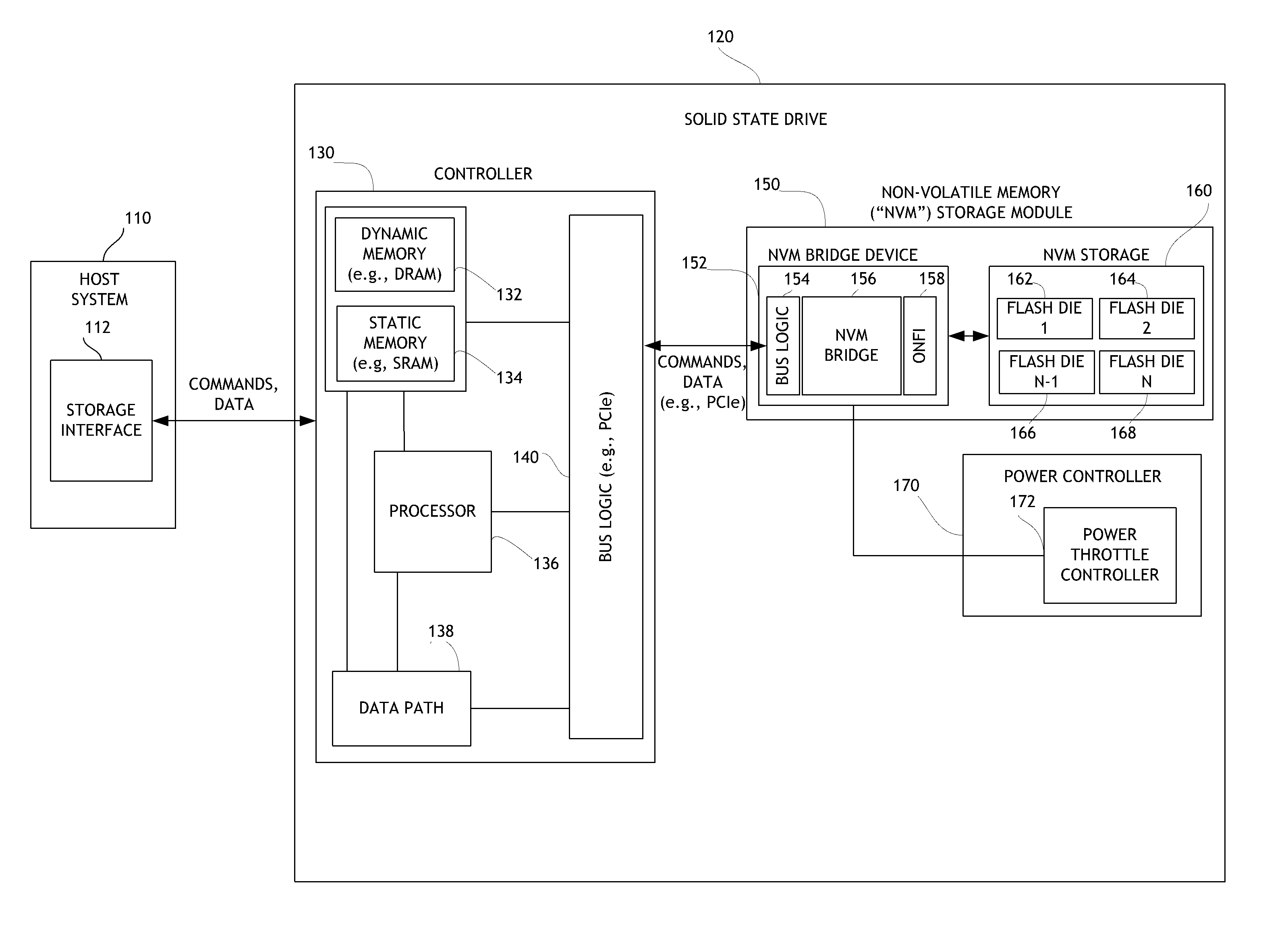
Systems and methods for error injection in data storage systems
ActiveUS8707104B1Solving precise measurementsTested and reliableDetecting faulty computer hardwareRead-only memoriesSolid-state storageHybrid storage system
Embodiments of the solid-state storage system provided herein are configured to perform improved mechanisms for testing of error recovery of solid state storage devices. In some embodiments, the system is configured to introduce or inject errors into data storage commands or operations performed in the non-volatile memory. Injected errors include corruption of data stored in the non-volatile memory, deliberate failure to execute storage operations, and errors injected into communication protocols used between various elements of the device. In some embodiments, injected errors can include direct errors that trigger an immediate execution of error recovery mechanisms and delayed errors that trigger execution of error recovery mechanisms at a later time. Error recovery mechanisms can be tested in an efficient, reliable, and deterministic manner to help ensure effective operation of storage devices. The integrity of non-volatile memory can also be tested.
Owner:WESTERN DIGITAL TECH INC
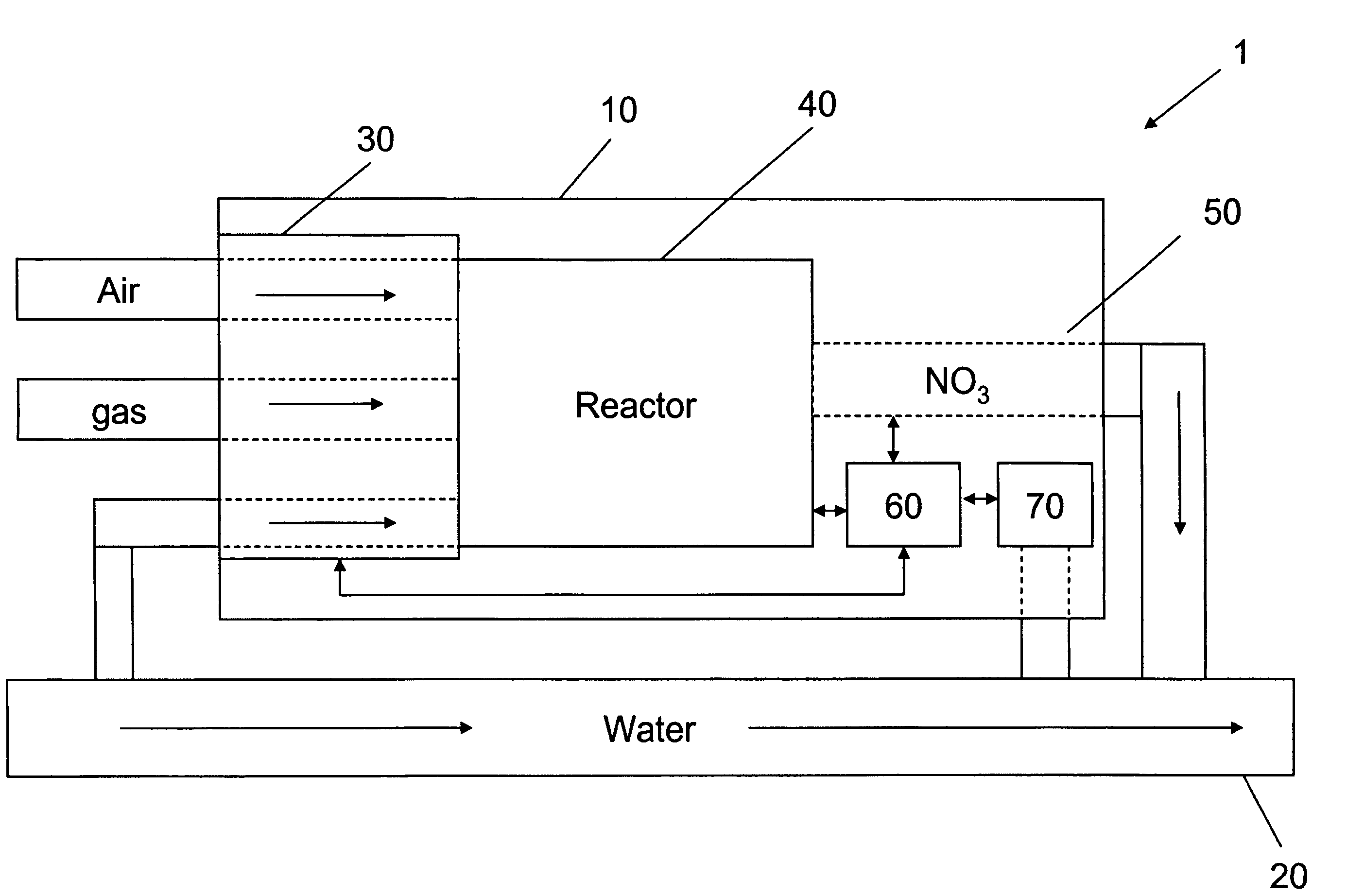
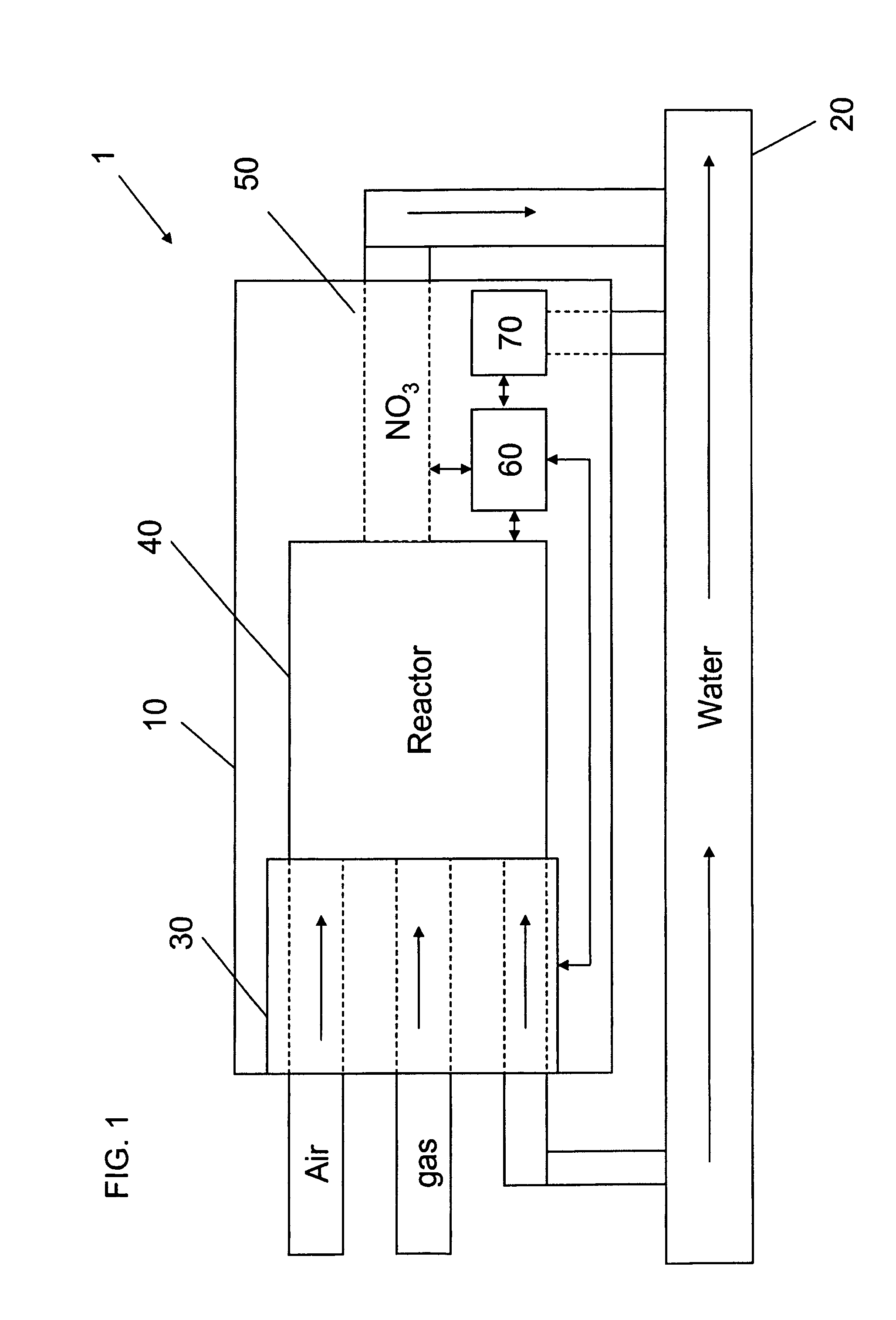
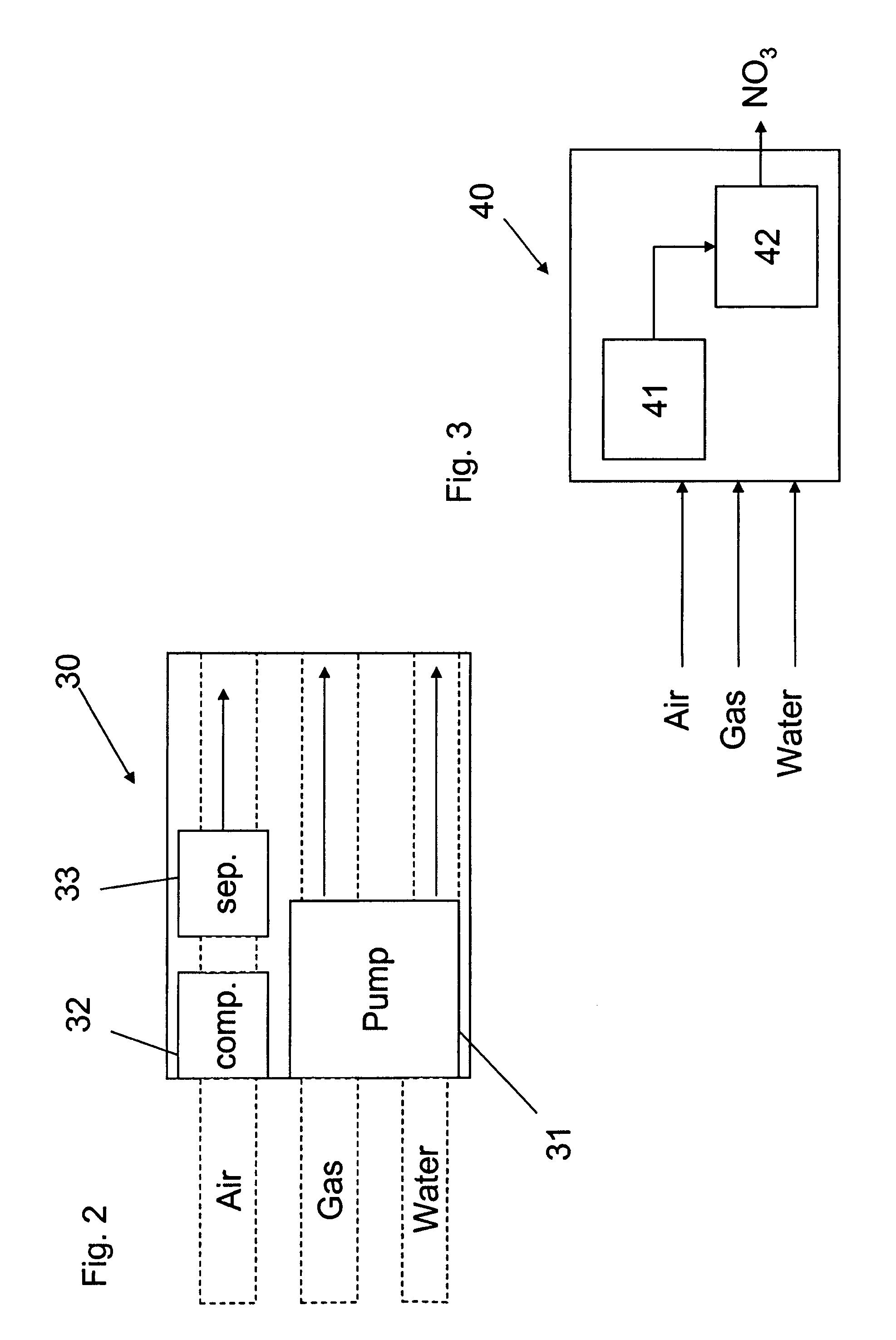
Apparatus for on-site production of nitrate ions
InactiveUS7514058B1Enhanced overall recoveryWater treatment parameter controlWater treatment compoundsMicrobial enhanced oil recoverySulfate-reducing bacteria
An apparatus and method produces nitrate ions on-site from water, natural gas and air extracted in proximity to the apparatus. The apparatus generates nitrate ions and brings the nitrate ions into contact with an aqueous system. Hydrogen sulfide present in the aqueous system is removed and the production of hydrogen sulfide by sulfate-reducing bacteria (SRB) is eliminated by introducing into the system nitrate ions, whereby denitrifying microorganisms, using nitrate, outcompete the sulfate-reducing bacteria for the available carbon nutrients, thus preventing the SRB from producing hydrogen sulfide. Nitrate ions generated by the apparatus and added to the aqueous system which contains the denitrifying microorganisms can enhance oil recovery by means of microbial enhanced oil recovery mechanisms.
Owner:NITRA GEN LLC
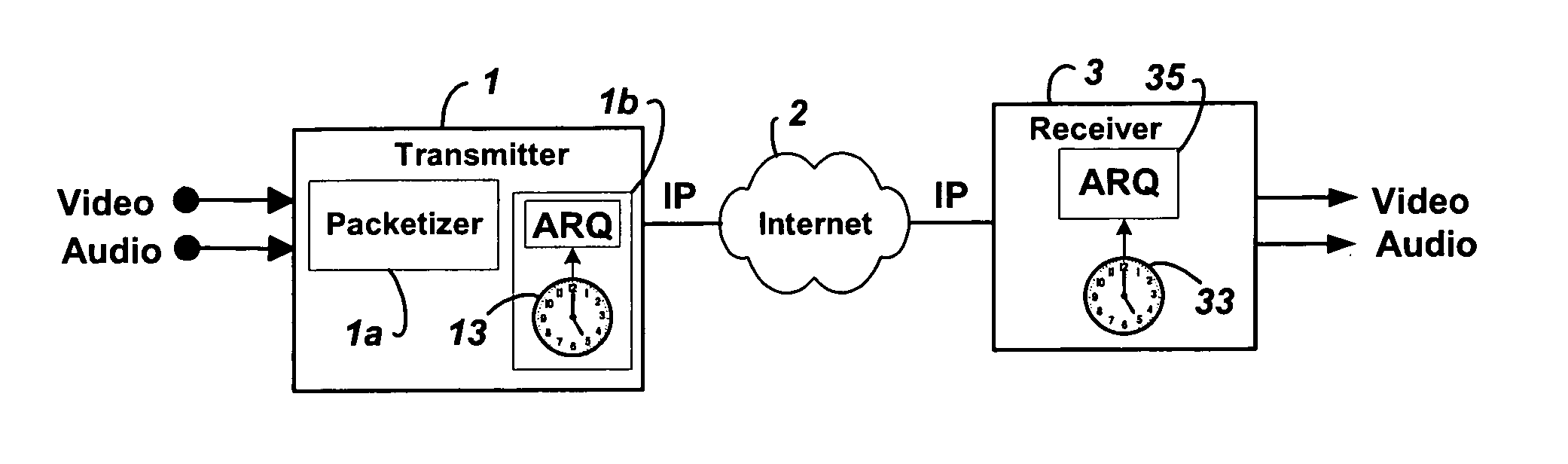
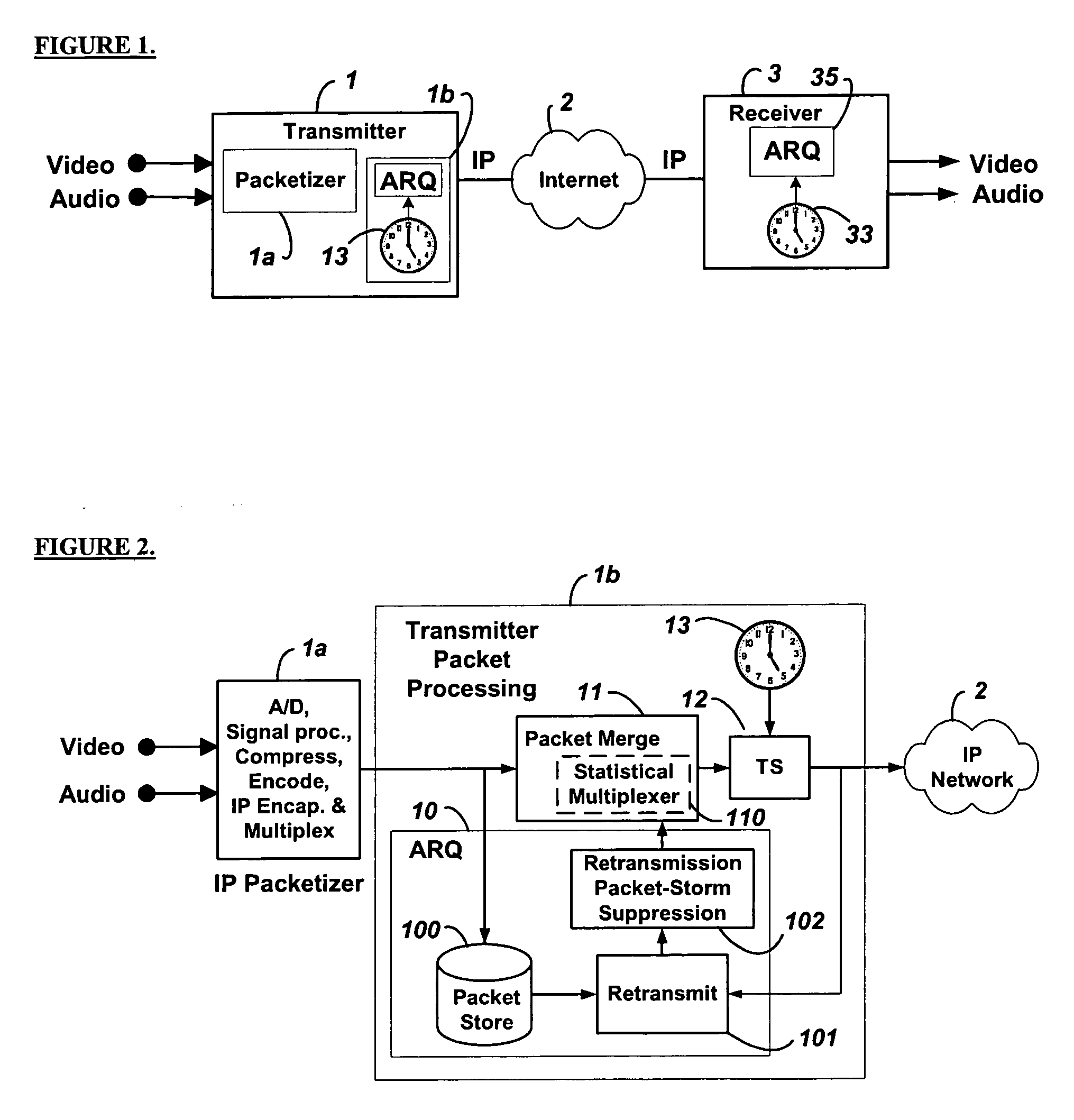
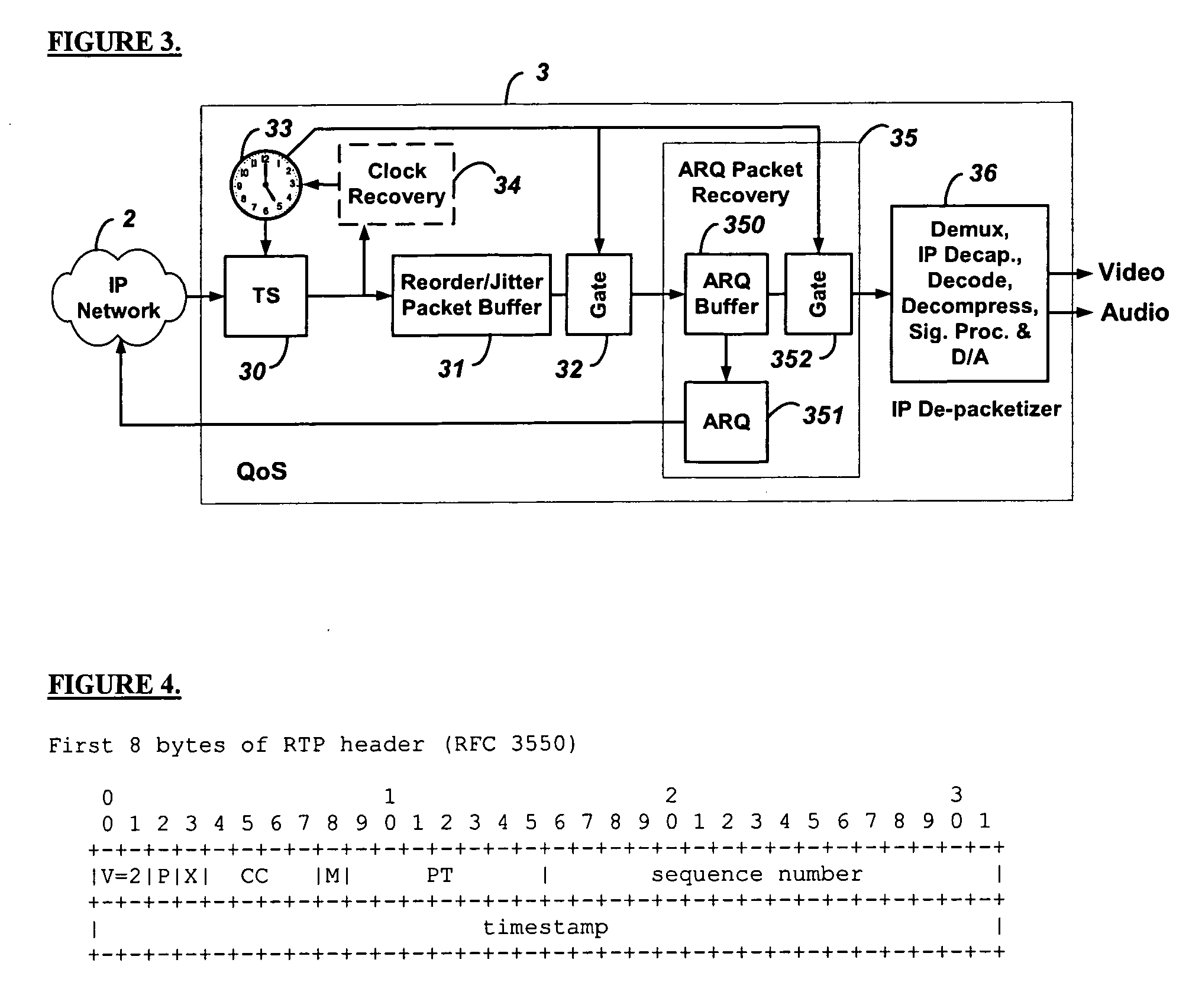
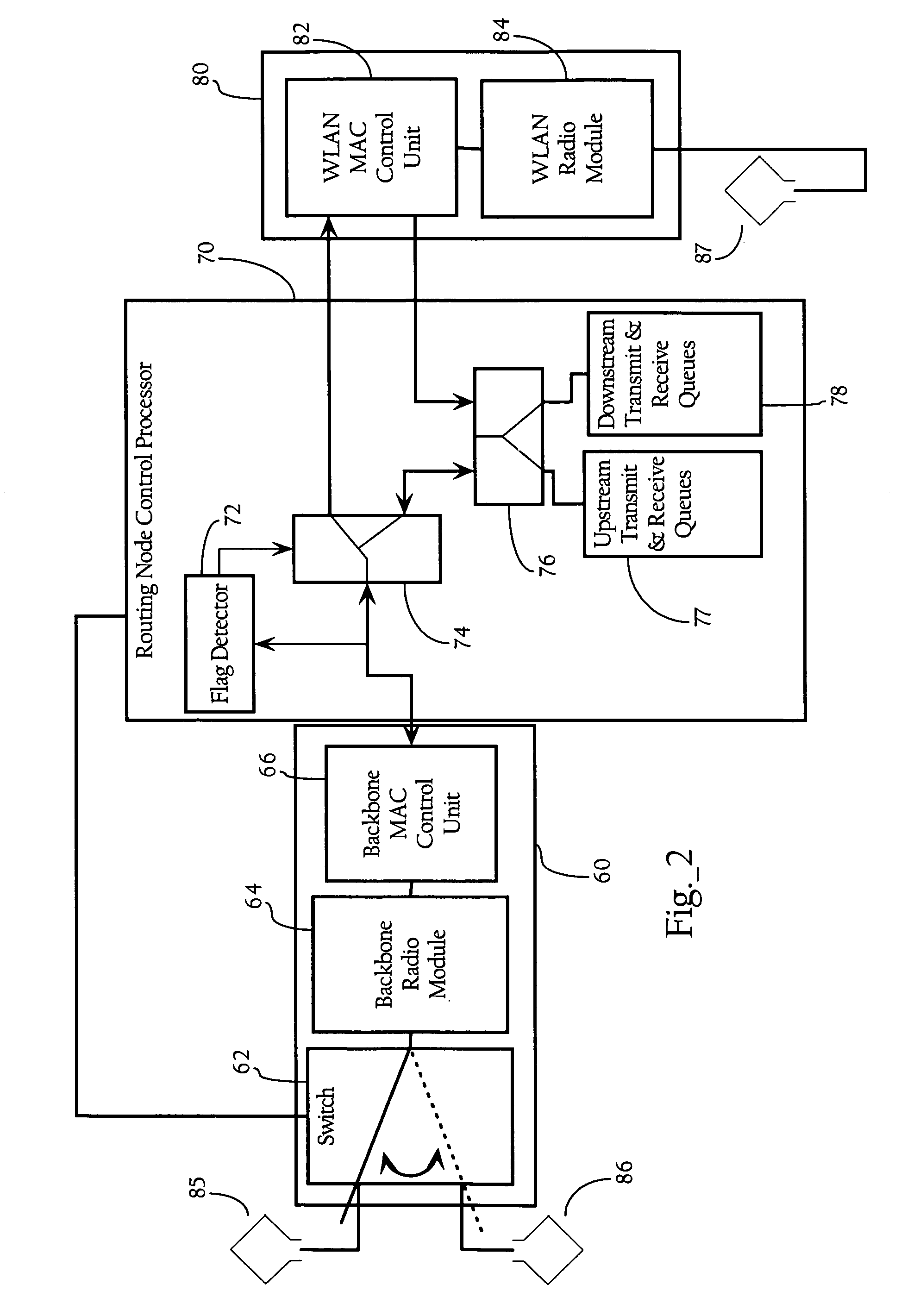
Low-latency automatic repeat request packet recovery mechanism for media streams
ActiveUS20060104279A1Robust and low-latency transportDelay minimizationError preventionFrequency-division multiplex detailsAutomatic repeat requestLatency (engineering)
An Automatic Repeat reQuest (ARQ) error correction method optimized for protecting real-time audio-video streams for transmission over packet-switched networks. Embodiments of this invention provide bandwidth-efficient and low-latency ARQ for both variable and constant bit-rate audio and video streams. Embodiments of this invention use timing constraints to limit ARQ latency and thereby facilitate the use of ARQ packet recovery for the transport of both constant bit rate and variable bit rate media streams.
Owner:QVIDIUM TECH
Automatic error recovery mechanism for a database system
ActiveUS20120144234A1Avoid errorsAvoid problemsNon-redundant fault processingRedundant operation error correctionExecution planProgram planning
A computer-implemented method, apparatus and article of manufacture for performing an automatic error recovery in a database system. Automatic error recovery is performed for a query execution plan, following errors, problems or failures that occur during execution, by automatically or manually deactivating and / or activating components, features or code paths, and then re-submitting the query execution plan for execution in the computer system.
Owner:TERADATA US
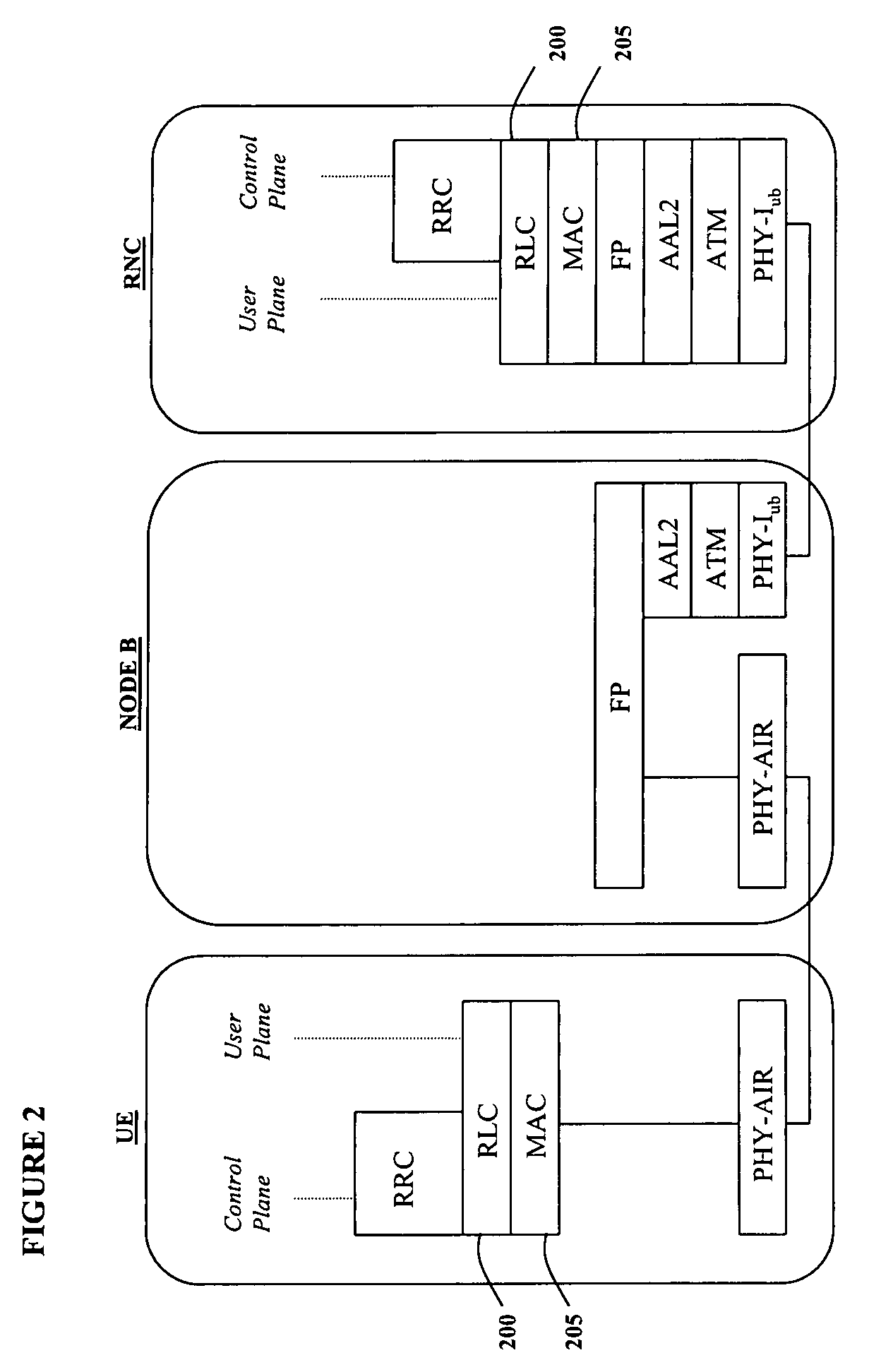
Data unit management in communications
ActiveUS7525908B2Error prevention/detection by using return channelTransmission systemsTelecommunicationsRadio Link Control
In Radio Link control (REC) apparatus, a mechanism is provided for detecting missing or corrupted data units at the receiving end of a transmission link, requesting retransmission and then monitoring the response to the retransmission request. Distinctively, a receiving communications entity 300 is equipped to act on a nil response. If no data unit is retransmitted, the receiving entity triggers at least one repeat retransmission request. This is the case even if no further data unit is received after the retransmission request is triggered. Retransmission requests are repeated up to a preset number, whereafter a different recovery mechanism is triggered.
Owner:MALIKIE INNOVATIONS LTD
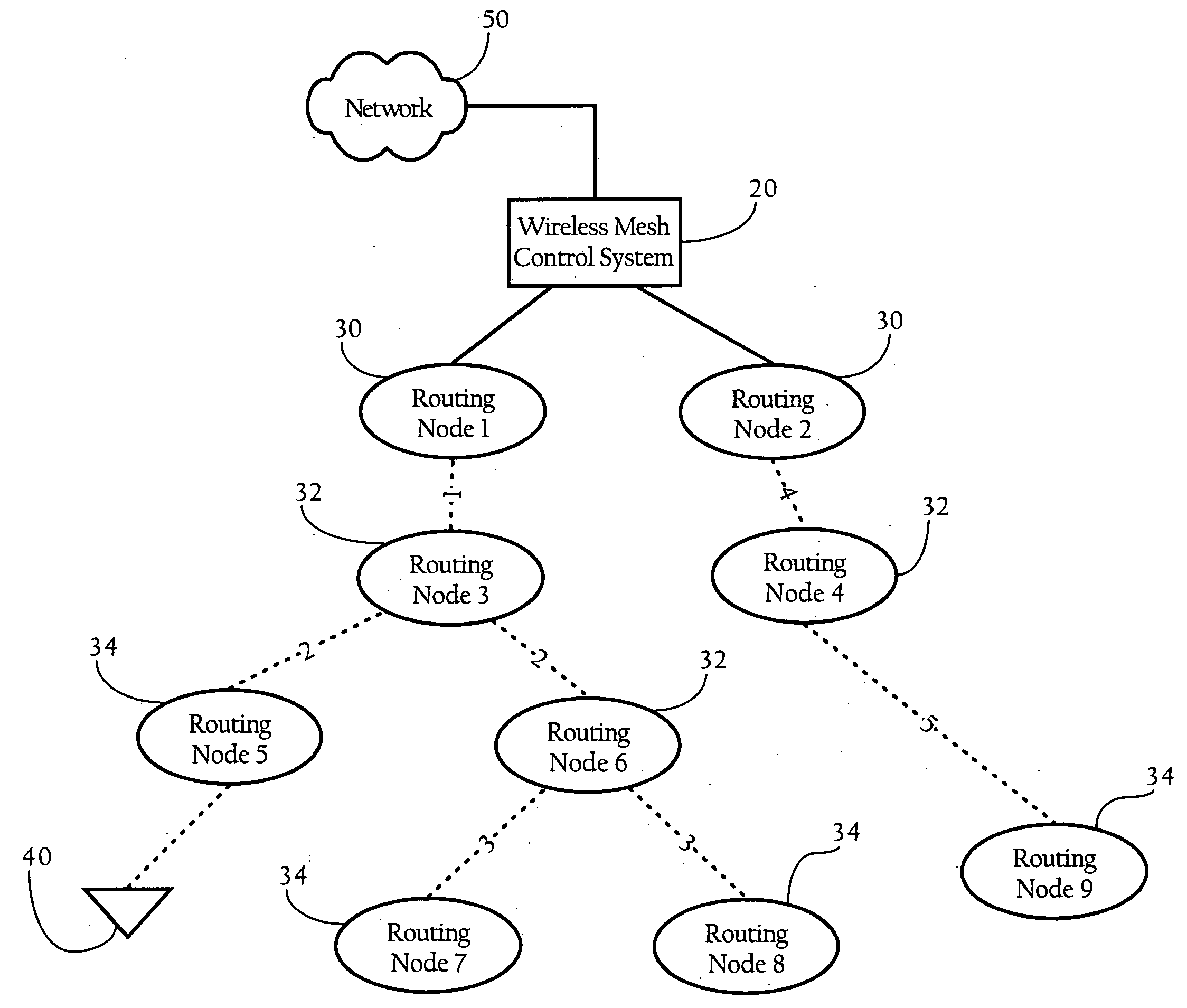
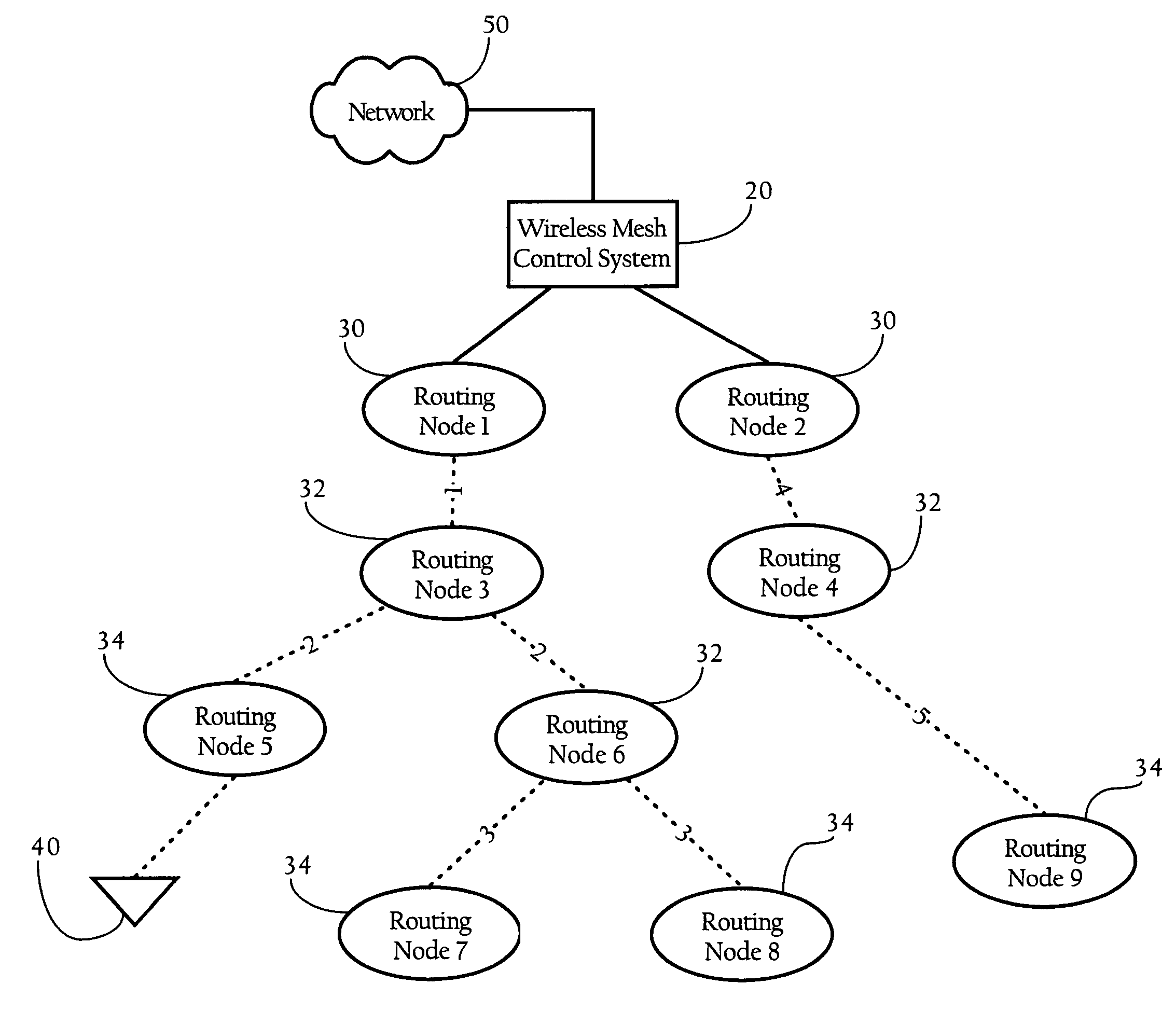
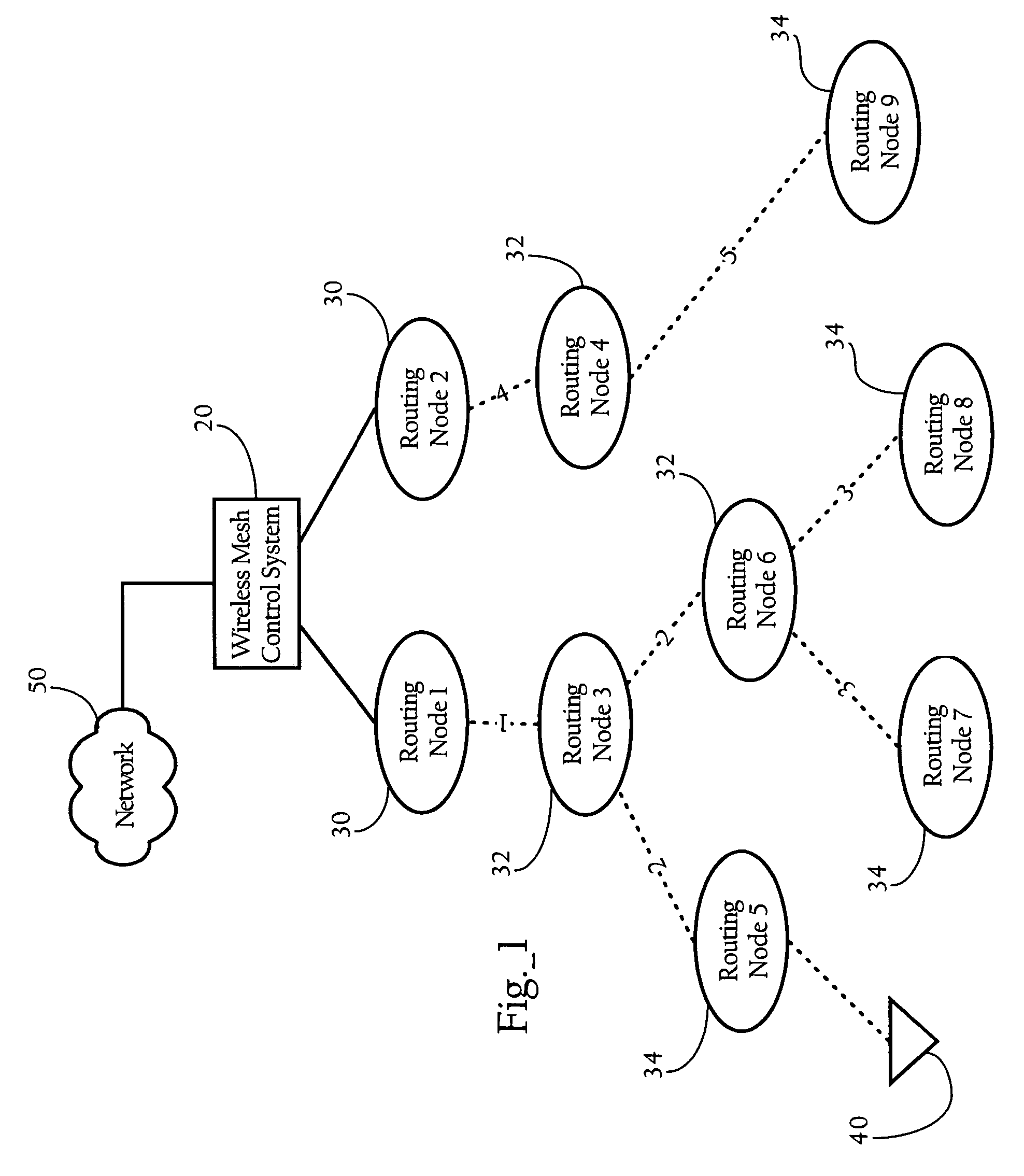
Configuration of failure and acquire timeouts to facilitate recovery from failures in hierarchical mesh networks
InactiveUS20060215581A1Synchronisation arrangementNetwork topologiesWireless mesh networkDistributed computing
Methods, apparatuses and systems directed to providing an efficient failure recovery mechanism in hierarchical wireless mesh networks. In one implementation, the present invention mitigates the effect of synchronization loss between a parent and child node on the hierarchical wireless mesh network. In one implementation, the present invention employs a configuration scheme whereby the parent node failure timeouts are greater than the time to acquire a parent node to mitigate the effect of synchronization loss on downstream nodes in the hierarchical mesh network.
Owner:CISCO TECH INC
Frame level multimedia decoding with frame information table
ActiveUS20070291836A1Improve errorImprove efficiencyError preventionPicture reproducers using cathode ray tubesScalable compressionEncoder decoder
Apparatus and method to decode video data while maintaining a target video quality using an integrated error control system including error detection, resynchronization and error recovery are described. Robust error control can be provided by a joint encoder-decoder functionality including multiple error resilience designs. In one aspect, error recovery may be an end-to-end integrated multi-layer error detection, resynchronization and recovery mechanism designed to achieve reliable error detection and error localization. The error recovery system may include cross-layer interaction of error detection, resynchronization and error recovery subsystems. In another aspect, error handling of a scalable coded bitstream is coordinated across a base-layer and enhancement layer of scalable compressed video.
Owner:QUALCOMM INC
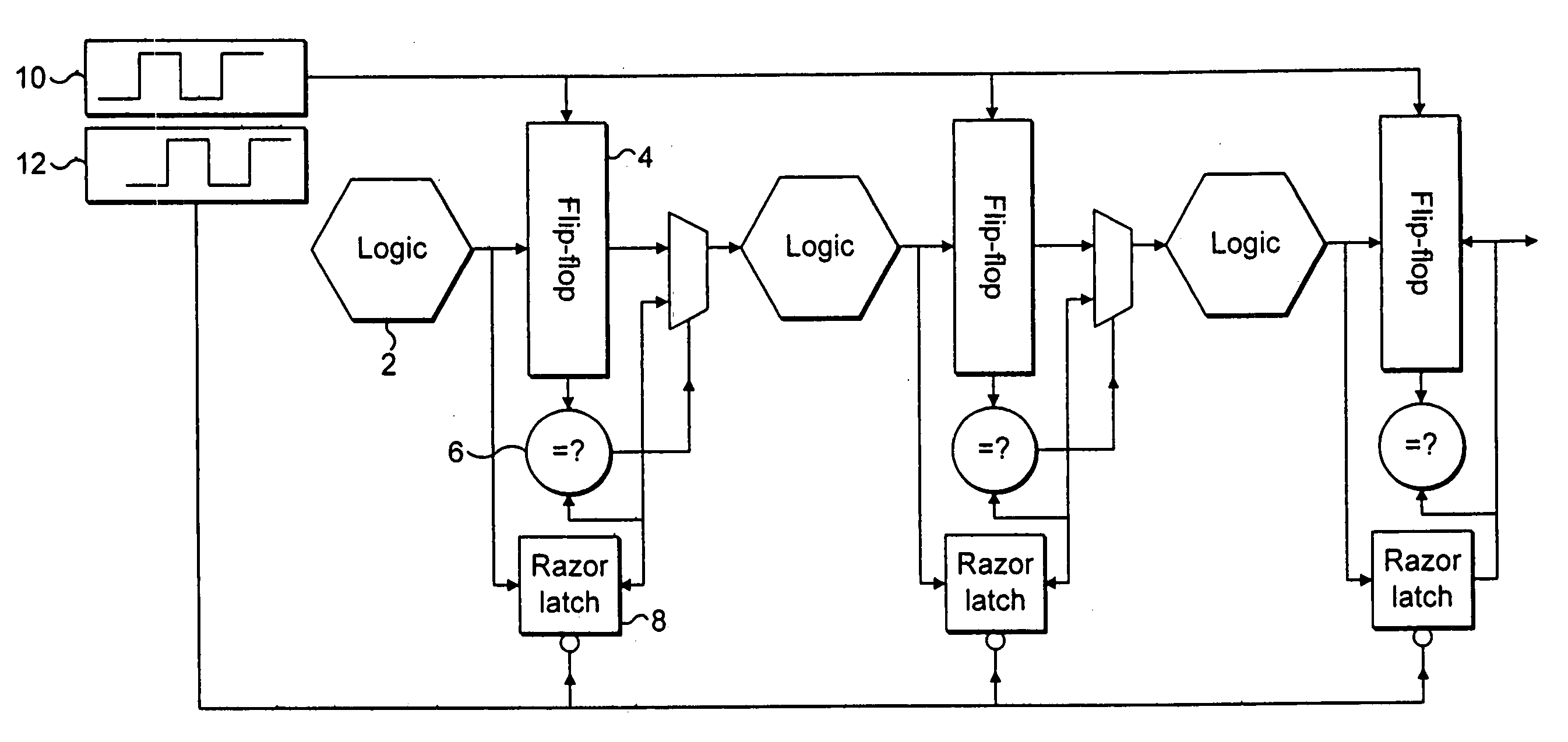
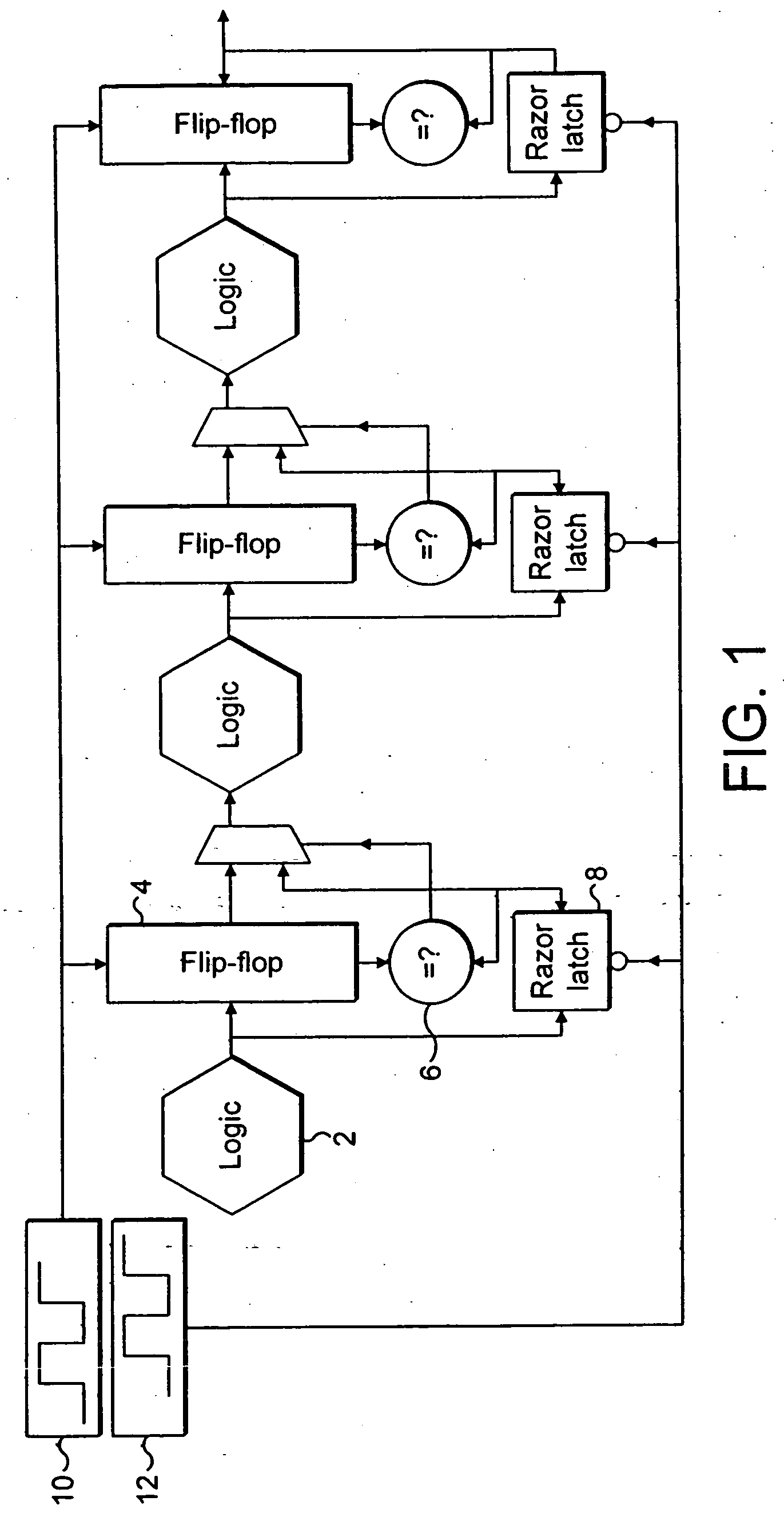
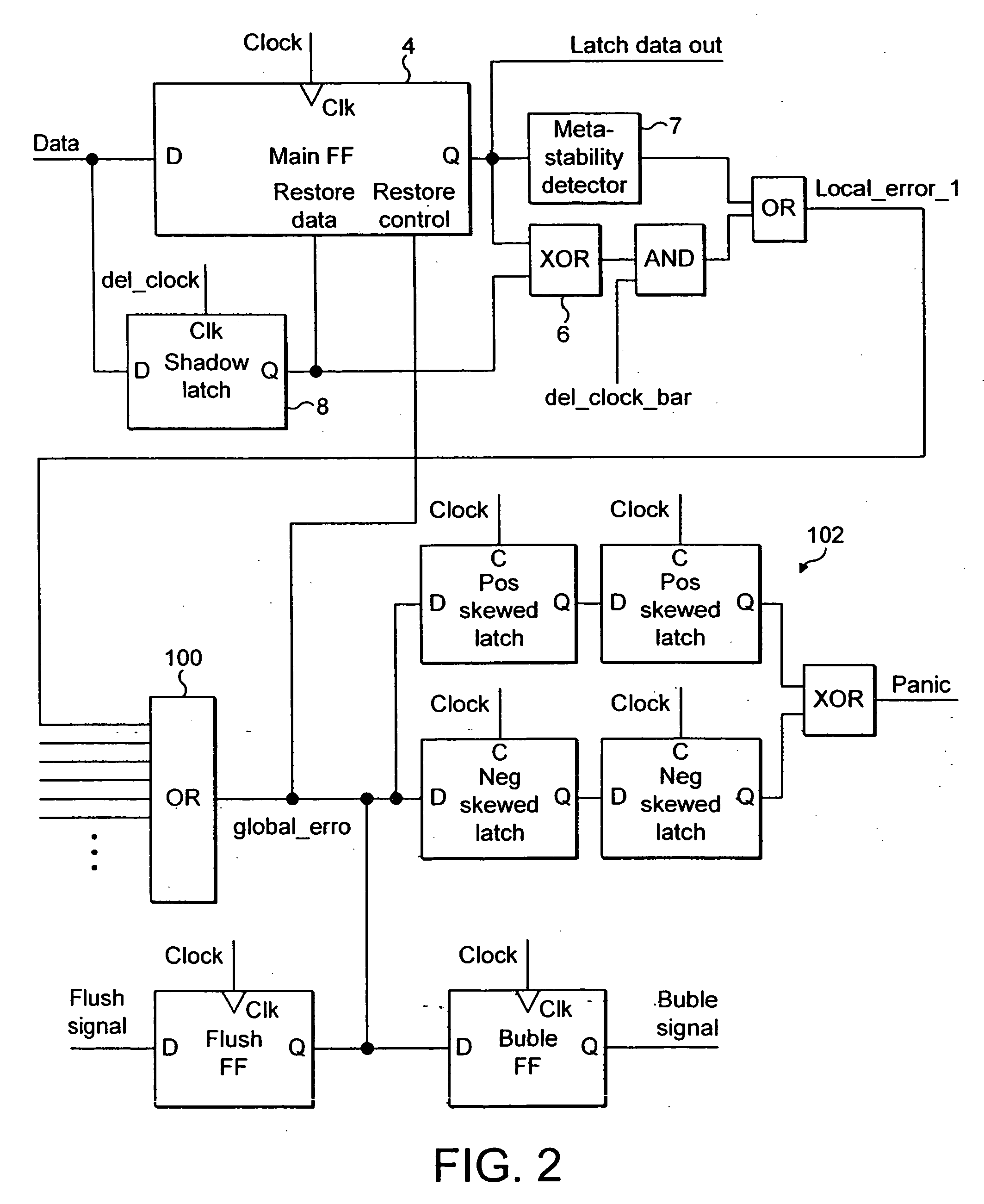
Error recovery within processing stages of an integrated circuit
ActiveUS20050246613A1Easy to modifyReduce the possibilityCode conversionFrequency/rate-modulated pulse demodulationError checkClock rate
An integrated circuit includes a plurality of processing stages each including processing logic 1014, a non-delayed signal-capture element 1016, a delayed signal-capture element 1018 and a comparator 1024. The non-delayed signal-capture element 1016 captures an output from the processing logic 1014 at a non-delayed capture time. At a later delayed capture time, the delayed signal-capture element 1018 also captures a value from the processing logic 1014. An error detection circuit 1026 and error correction circuit 1028 detect and correct random errors in the delayed value and supplies an error-checked delayed value to the comparator 1024. The comparator 1024 compares the error-checked delayed value and the non-delayed value and if they are not equal this indicates that the non-delayed value was captured too soon and should be replaced by the error-checked delayed value. The non-delayed value is passed to the subsequent processing stage immediately following its capture and accordingly error recovery mechanisms are used to suppress the erroneous processing which has occurred by the subsequent processing stages, such as gating the clock and allowing the correct signal values to propagate through the subsequent processing logic before restarting the clock. The operating parameters of the integrated circuit, such as the clock frequency, the operating voltage, the body biased voltage, temperature and the like are adjusted so as to maintain a finite non-zero error rate in a manner that increases overall performance.
Owner:ARM LTD +1
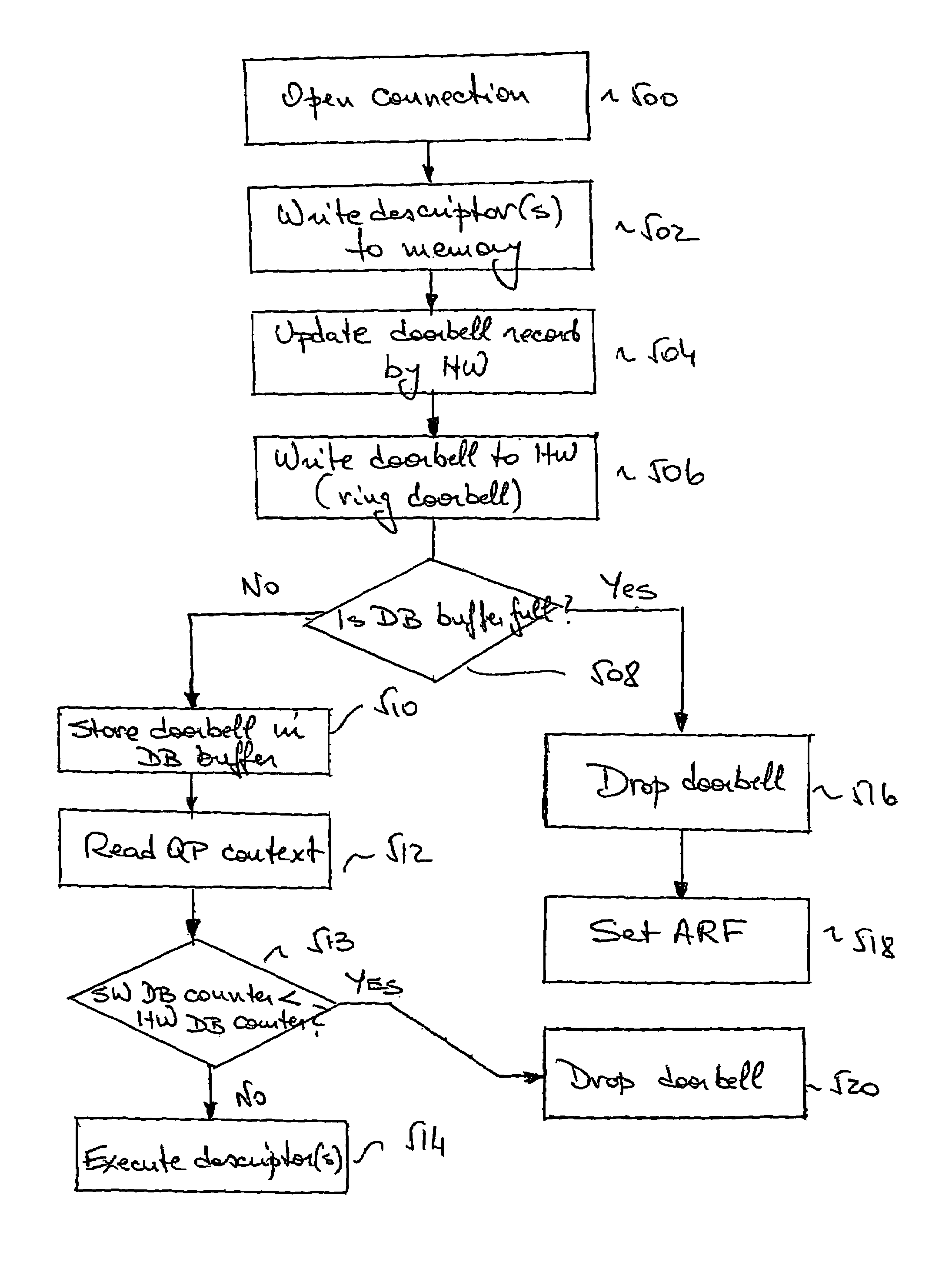
Method, system and protocol that enable unrestricted user-level access to a network interface adapter
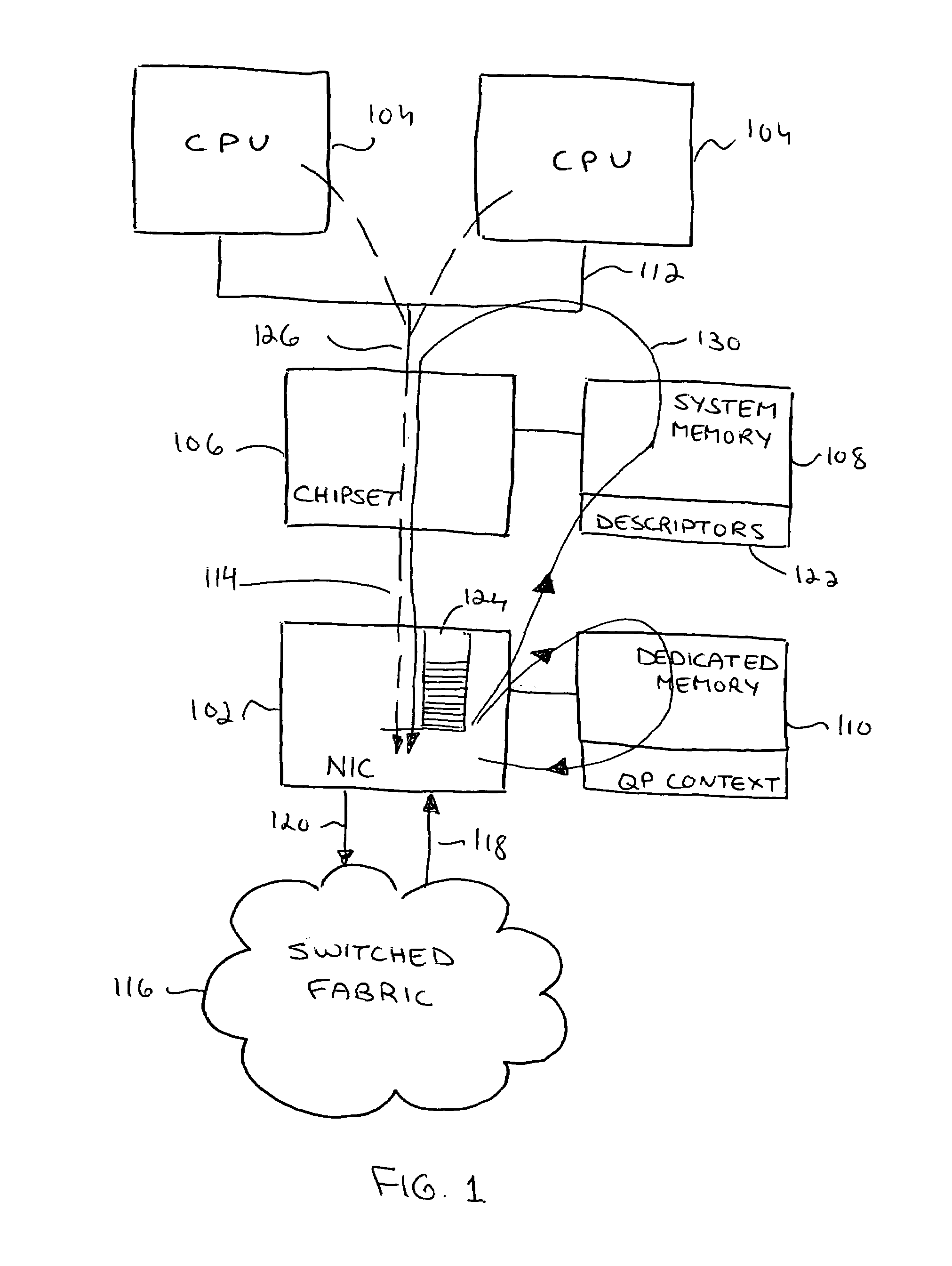
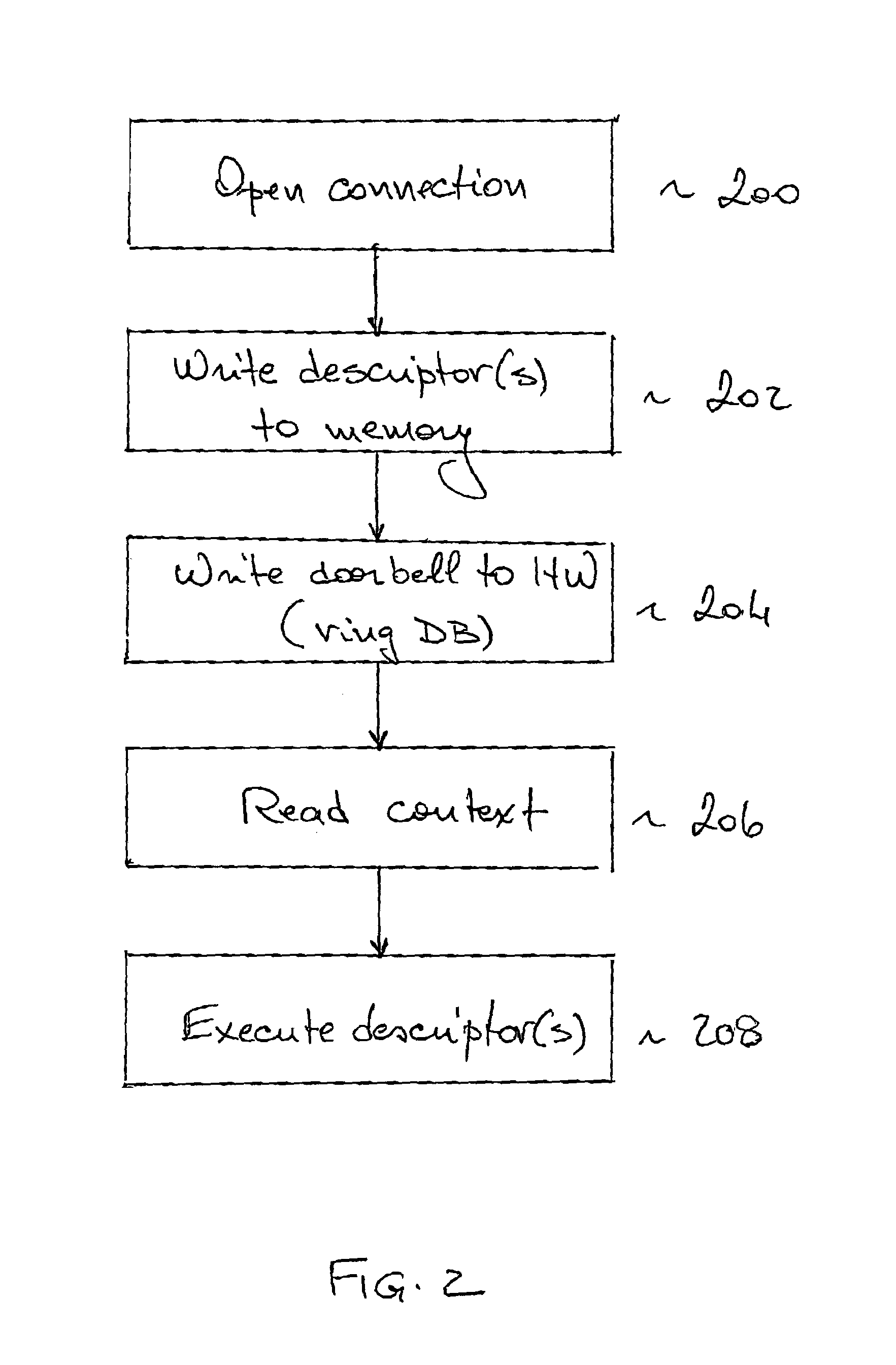
ActiveUS7653754B2Avoid deadlockUnrestricted user-level access to the NICConveying record carriersMultiple digital computer combinationsDoorbellApplication software
A method for preventing deadlock in communication between a host software application and a network interface card (NIC), comprises writing a doorbell associated with at least one descriptor having a descriptor context to a buffer in the NIC, dropping at least one doorbell from the buffer if the buffer is full, thereby allowing a write of a new doorbell to the buffer, and recovering each dropped doorbell for further execution of descriptors associated with this doorbell. The descriptor execution is in order of posting by the application to the NIC. A system implementing the method comprises a doorbell drop mechanism and a doorbell recovery mechanism.
Owner:MELLANOX TECHNOLOGIES LTD
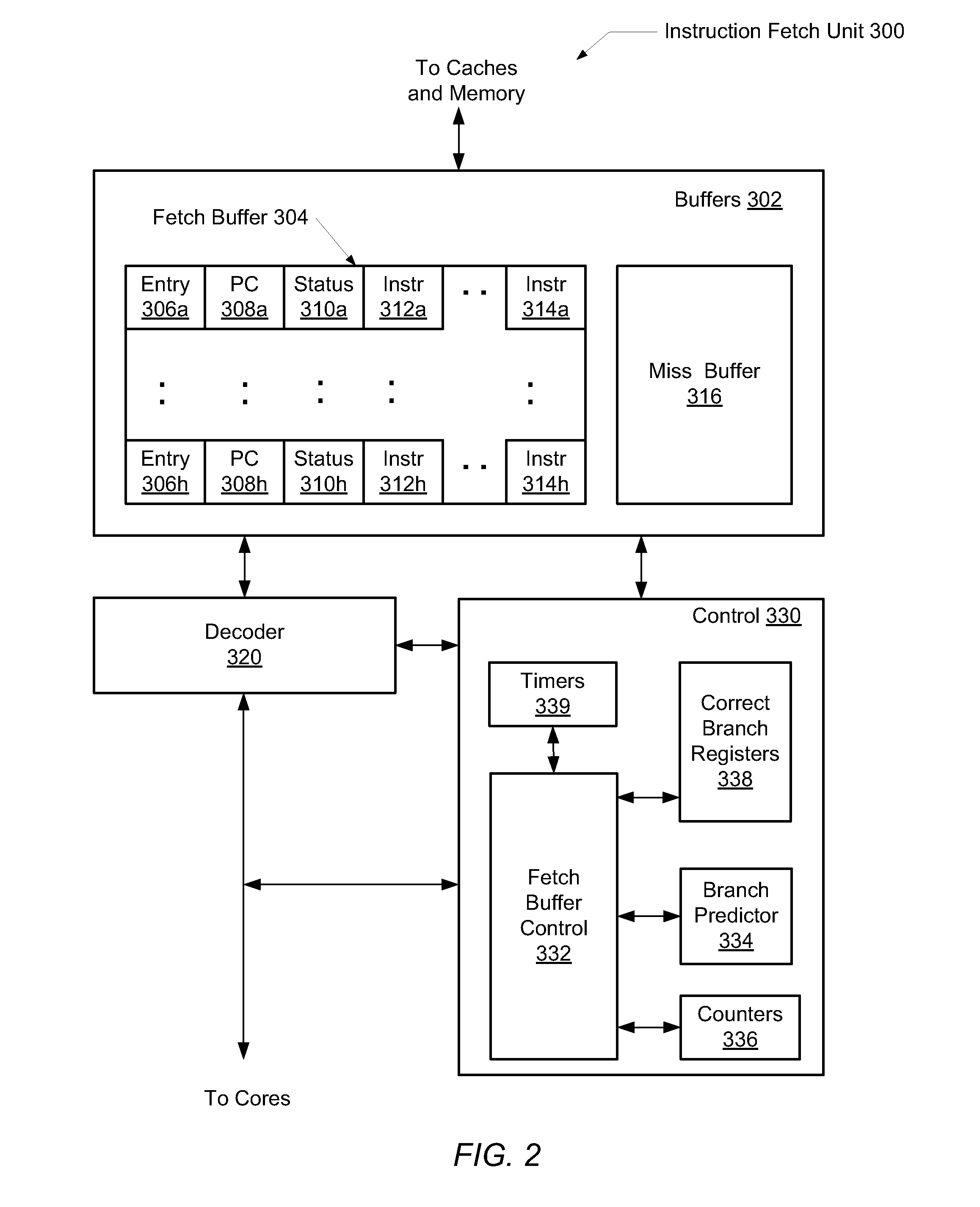
Branch misprediction recovery mechanism for microprocessors
ActiveUS20100169611A1Improve performanceDigital computer detailsSpecific program execution arrangementsParallel computingTimer
A system and method for reducing branch misprediction penalty. In response to detecting a mispredicted branch instruction, circuitry within a microprocessor identifies a predetermined condition prior to retirement of the branch instruction. Upon identifying this condition, the entire corresponding pipeline is flushed prior to retirement of the branch instruction, and instruction fetch is started at a corresponding address of an oldest instruction in the pipeline immediately prior to the flushing of the pipeline. The correct outcome is stored prior to the pipeline flush. In order to distinguish the mispredicted branch from other instructions, identification information may be stored alongside the correct outcome. One example of the predetermined condition being satisfied is in response to a timer reaching a predetermined threshold value, wherein the timer begins incrementing in response to the mispredicted branch detection and resets at retirement of the mispredicted branch.
Owner:ORACLE INT CORP
Full-automatic feeding, cutting and receiving equipment and processing method thereof
ActiveCN102145453AAffect normal workIncrease stiffnessOther manufacturing equipments/toolsPositioning apparatusLeveling mechanismMechanical equipment
The invention relates to the field of production machining mechanical equipment and discloses full-automatic feeding, cutting and receiving equipment. A material slot of a feeding device of the full-automatic feeding, cutting and receiving equipment is provided with a shifting mechanism consisting of a shifting fork and a shifting rod. The end of the shifting mechanism, which corresponds to a rear baffle plate of the feeding device, is provided with a leveling mechanism. A feeding bracket at the side of an unloading mechanism, which is correspondingly connected with a tube cutting device, is provided with a clamping mechanism. A lower roller and a side roller which are connected are arranged in the unloading mechanism. A split clamp of the tube cutting device is arranged on a tube cutting bracket through a trapezoid block. A recovery device consists of a recovery mechanism and a return mechanism, wherein the recovery mechanism is arranged at one side of the split clamp in a leveling mode; and the return mechanism is arranged on a recovery bracket at the rear end of the recovery mechanism. A brush wheel is arranged in the return mechanism. A machining method of the equipment comprises the steps of adding, aligning, feeding, cutting and receiving. The full-automatic feeding, cutting and receiving equipment is smooth to feed materials and is clear to separate the materials, so that resource waste is avoided, the machining procedures of the engineering are reduced, the cutting quality is improved, both manpower and material resources are saved and the production efficiency is improved.
Owner:东莞市机信机械有限公司
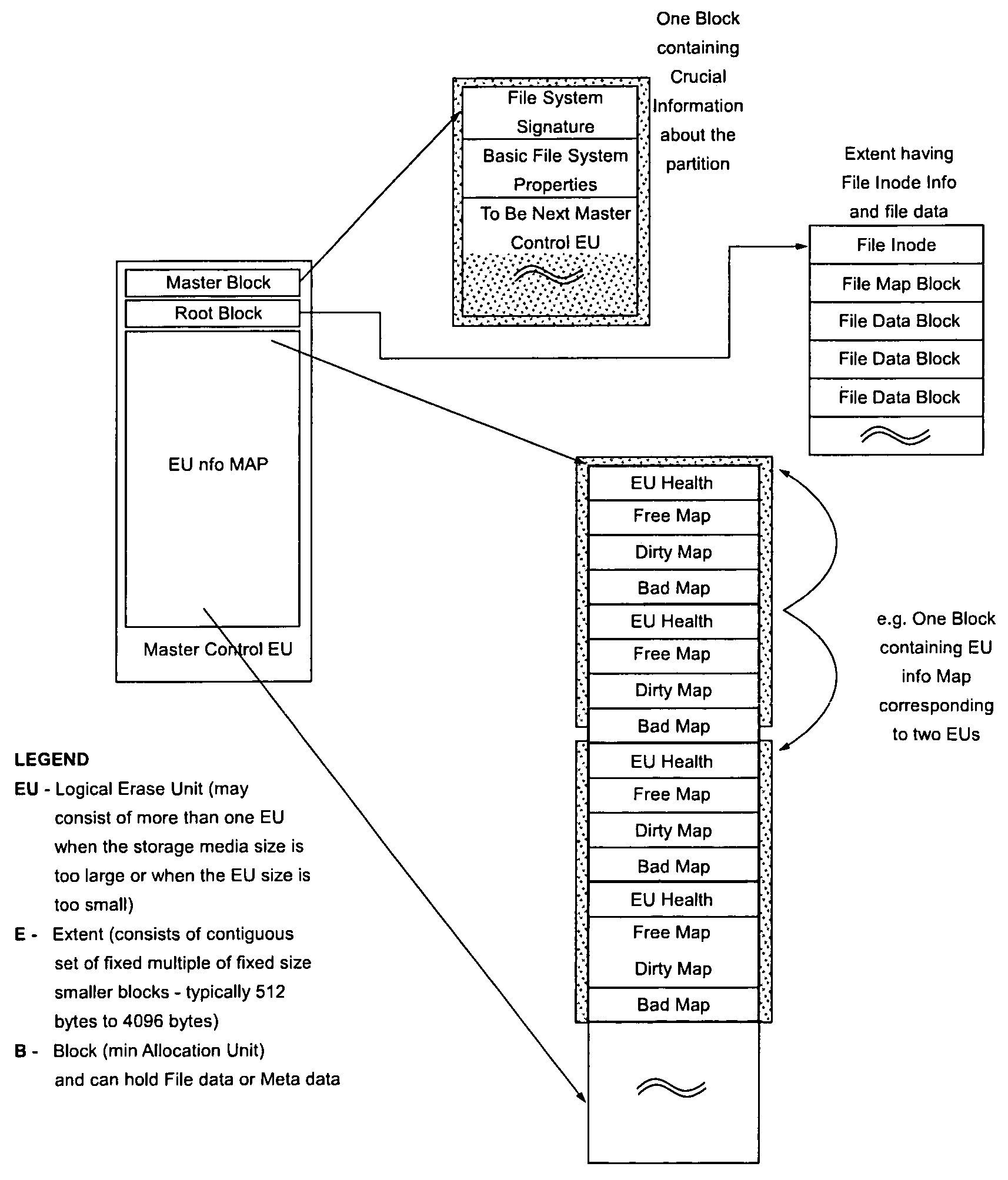
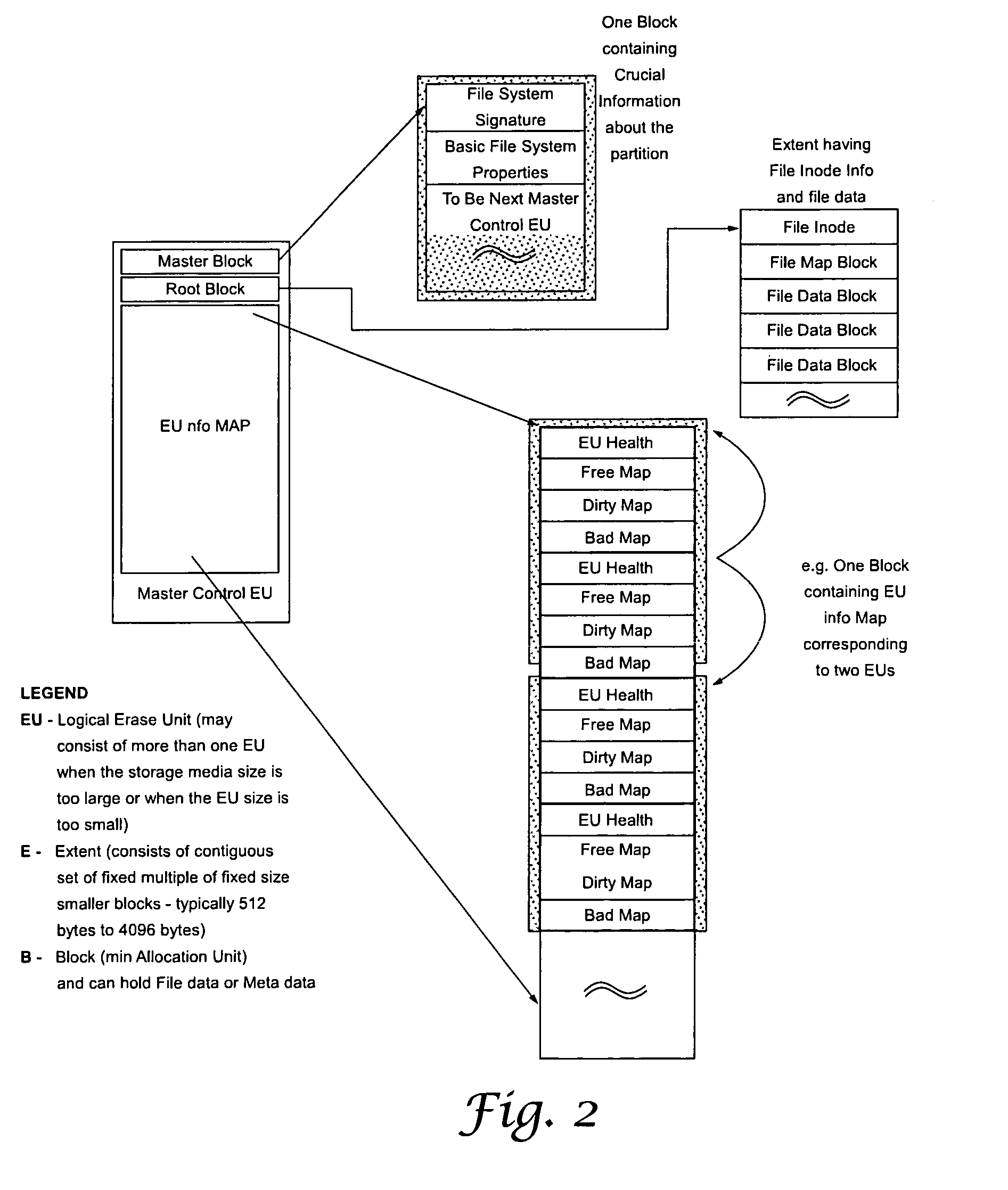
Efficient journaling and recovery mechanism for embedded flash file systems
InactiveUS20080077590A1Eliminate incomplete file operationEliminate operationDigital data information retrievalError detection/correctionStable stateFlash file system
Implicit journaling of a file operation relating to a file stored in a flash memory is performed by locking a semaphore corresponding to the file on which a file operation is to be performed, by initializing journaling of the file operation using the file map, by performing the file operation on the file, by completing journaling of the file operation using a file map corresponding to the file, and unlocking the semaphore. Additionally or alternatively, a file system is placed in a stable state following an interruption occurring during a file operation by scanning File Maps corresponding to the files, determining whether a file operation is incomplete based on validity flags contained in the file maps, and performing remediation so as to eliminate the incomplete file operation.
Owner:HONEYWELL INT INC
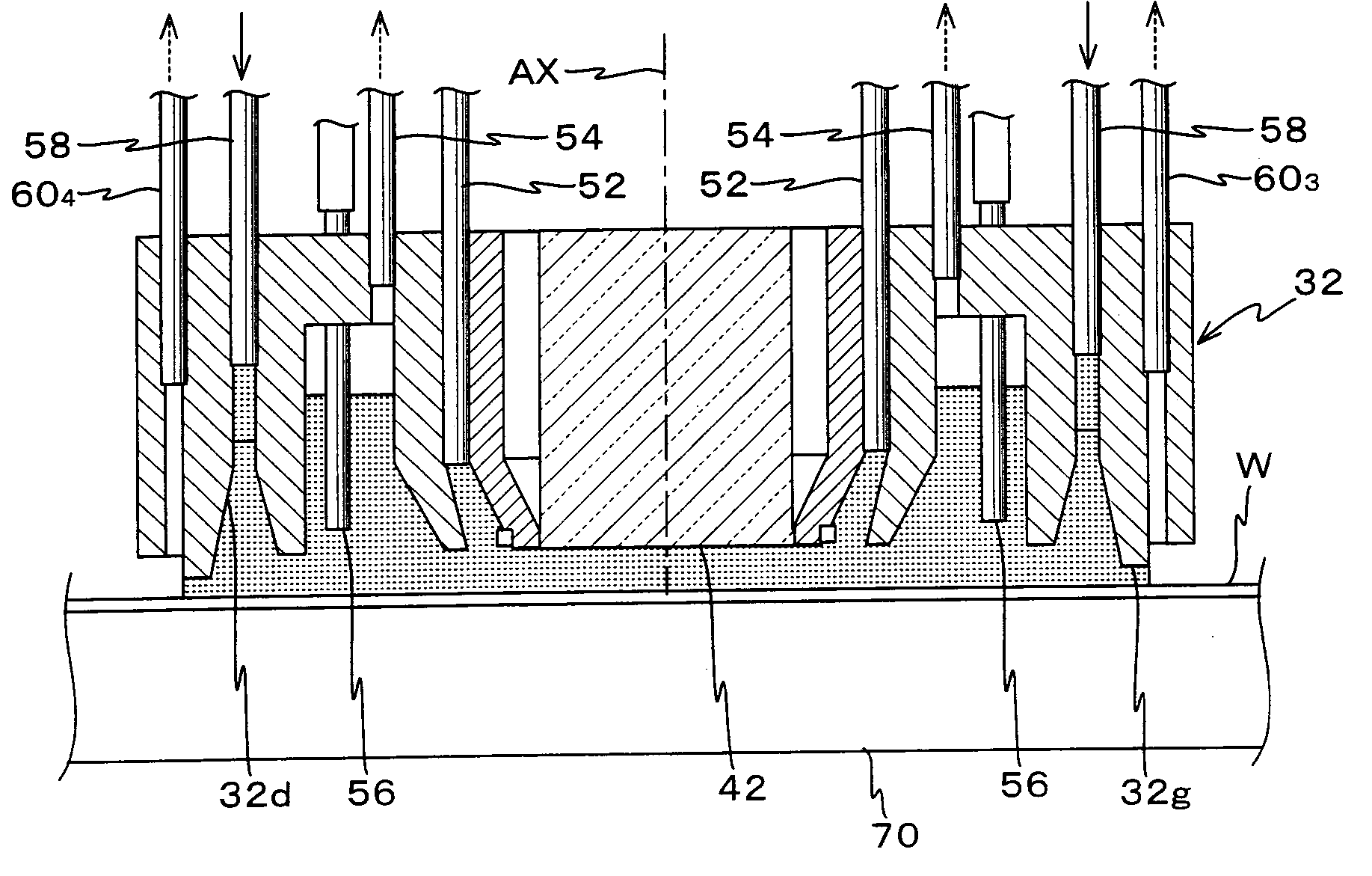
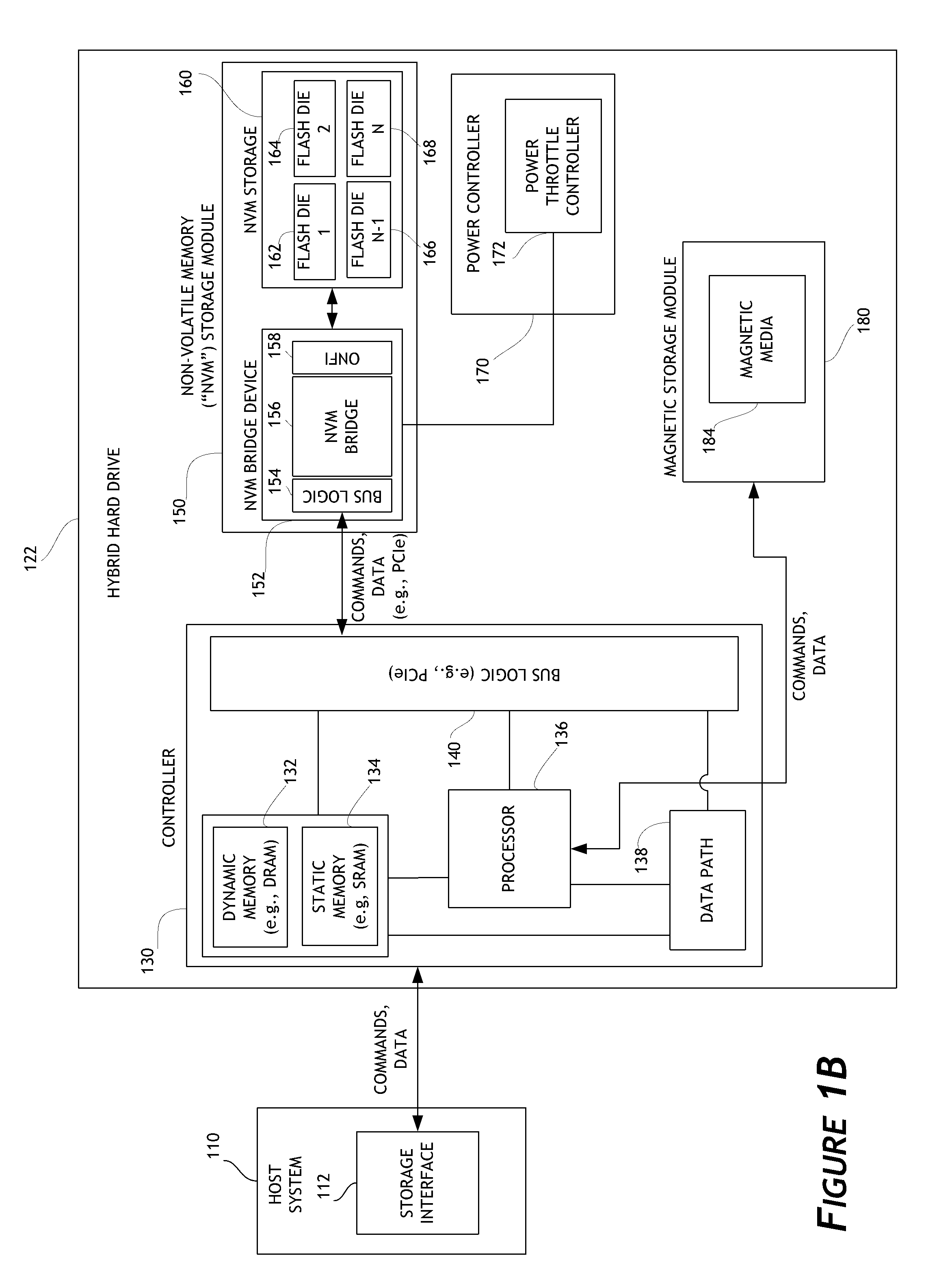
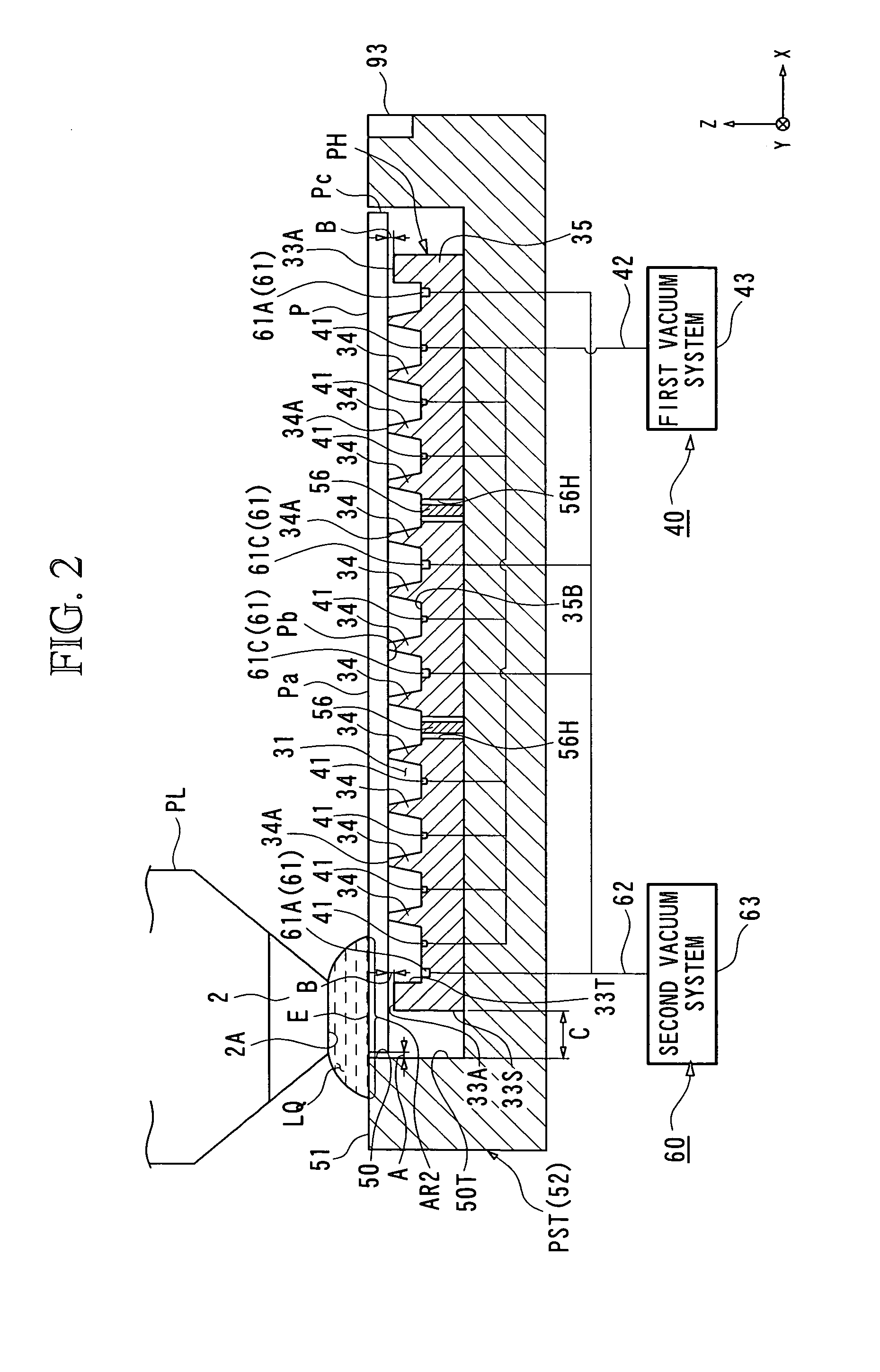
Exposure Apparatus and Device Manufacturing Method
InactiveUS20080043210A1Avoid it happening againSemiconductor/solid-state device manufacturingPhotomechanical exposure apparatusEngineeringMechanical engineering
An exposure apparatus that can prevent disadvantages due to a leaked liquid is provided. The exposure apparatus includes: a substrate holder (PH) that includes a peripheral wall portion (33) and supporting portions (34) located on an inside of the peripheral wall portion (33) and that supports a substrate (P) with the supporting portions (34) by negatively pressurizing a space (31) surrounded by the peripheral wall portion (33); and a recovery mechanism that includes a collection inlets (61) provided on the inside of the peripheral wall portion (33) and a vacuum system (63) connected to the collection inlets (61), in which a liquid penetrated from an outer periphery of the substrate (P) is sucked and recovered, in the state with an upper surface (33A) of the peripheral wall portion (33) and a back surface (Pb) of the substrate (P) being spaced at a first distance.
Owner:NIKON CORP
Shale gas reservoir recovery simulation experimental device
InactiveCN102944666AAccurately simulate the mining processEarth material testingDesorptionModel system
The invention relates to an experimental device in the field of natural gas recovery, and particularly relates to a shale gas reservoir recovery simulation experimental device. The shale gas reservoir recovery simulation experimental device comprises a high-pressure gas source system, an injection system, a model system, a thermostat system, a pressure return system and a data acquisition system, wherein an intermediate container in the injection system and a core holding unit in the model system are positioned in a thermostat. The shale gas reservoir recovery simulation experimental device has the advantages that a plate model core clamping device and two full-diameter core clamping devices are connected, the cores of different dimensions are connected in series, multi-scale pore characteristics in the shale gas reservoir can be simulated, the multi-scale characteristics of shale gas seepage influenced by the multi-scale effect are reflected, the recovery process of the shale gas reservoir can be accurately simulated, and recovery mechanisms and recovery dynamics of the shale gas reservoir in different modes can be comprehensively evaluated; and meanwhile, a large-scale shale core adsorption / desorption experiment can be performed by utilizing the experimental device, and a gas adsorption / desorption rule of the large-scale shale core under different conditions is researched.
Owner:SOUTHWEST PETROLEUM UNIV
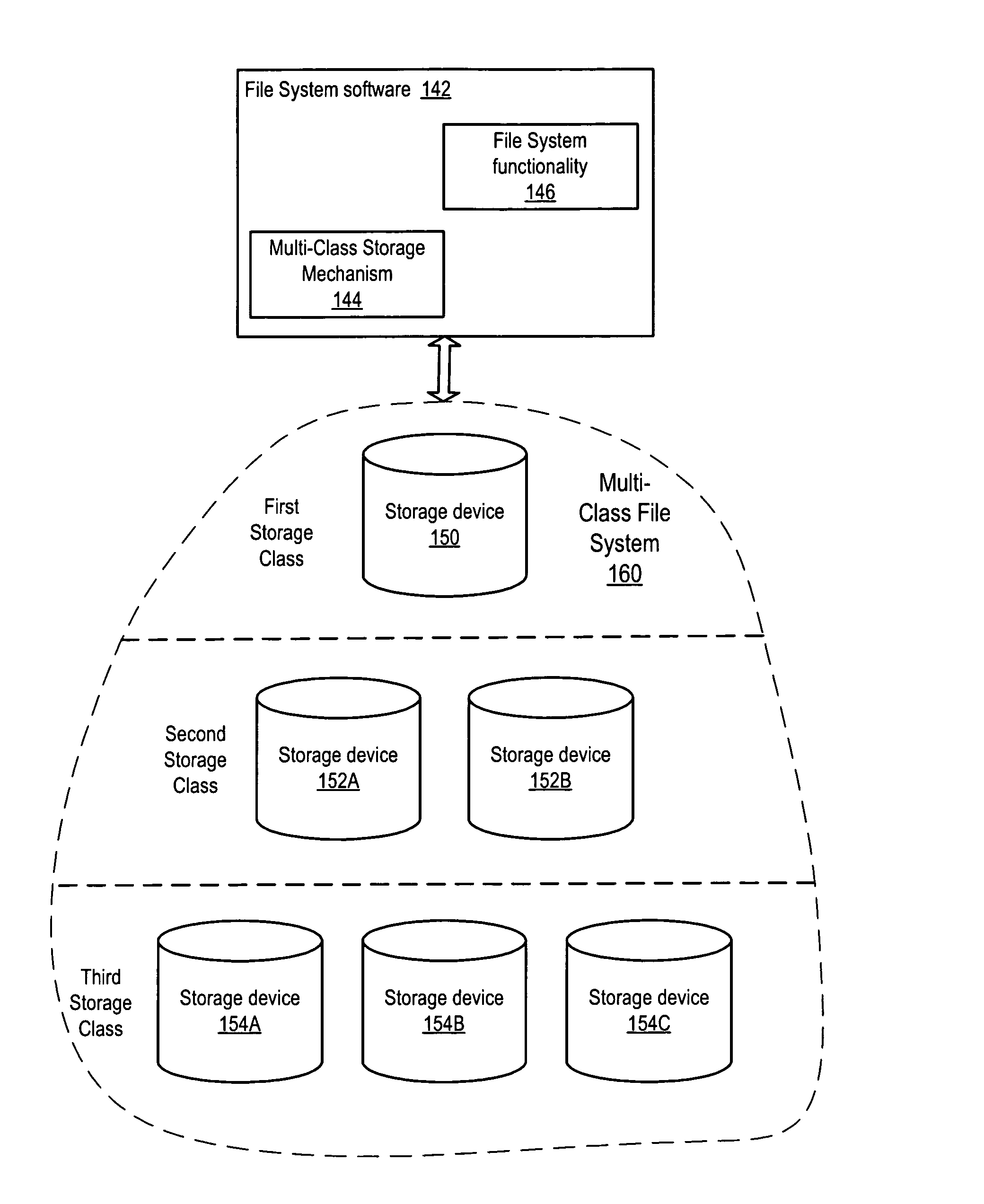
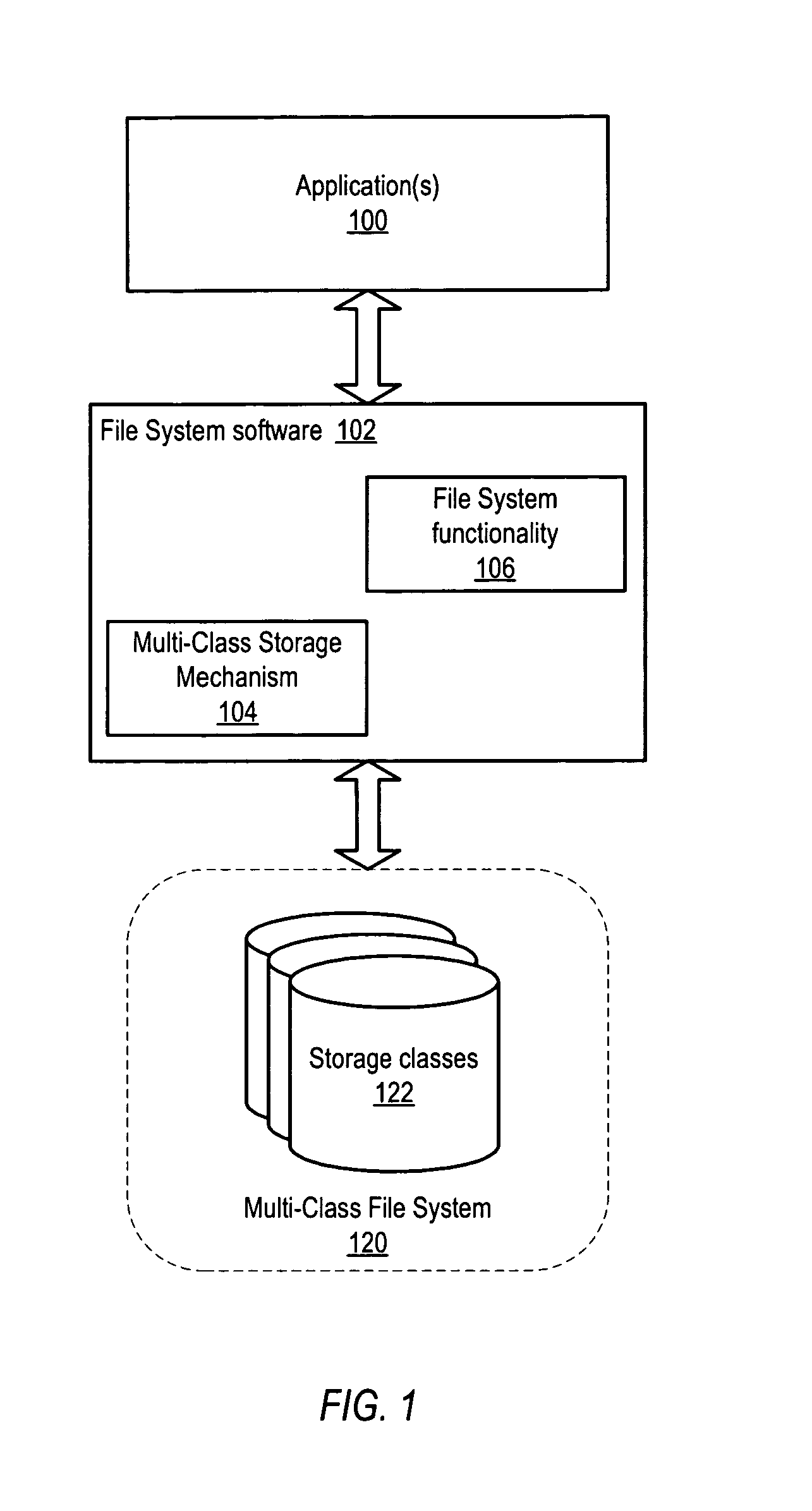
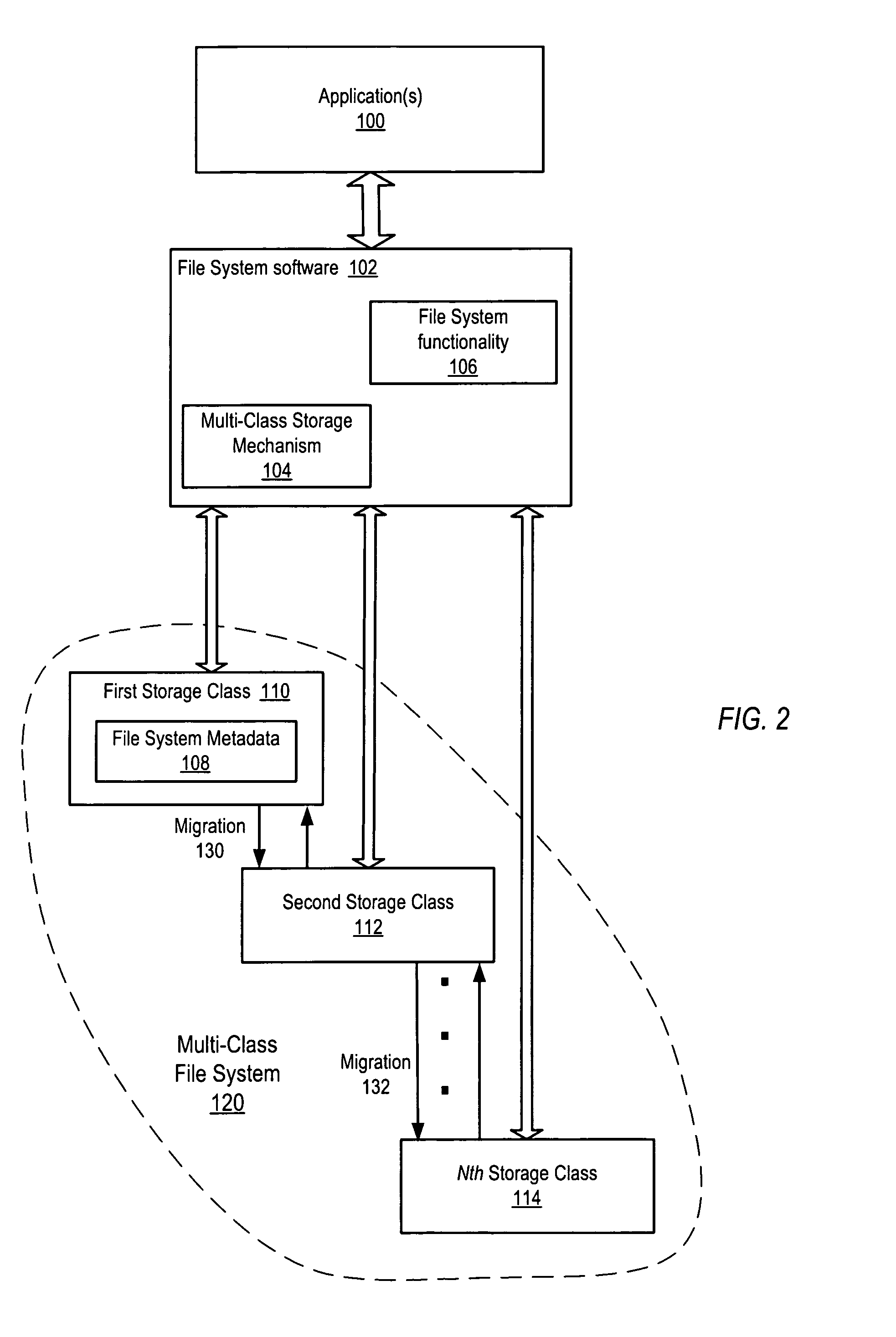
Restore mechanism for a multi-class file system
ActiveUS8127095B1Reduce delaysAvoid accessDigital data information retrievalError detection/correctionFile systemRecovery mechanism
System and method for performing optimized restores of a multi-class file system. More actively accessed data may be assigned to higher storage classes and less actively accessed data may be assigned to lower storage classes in the multi-class file system. In a restore, the higher storage class(es) including more actively accessed data may be restored first. The multi-class file system may then be brought online for access by application(s). The lower storage class(es) may then be restored. In one embodiment, if a request for data that have not been restored is received, the file system may obtain an estimated time until restore of the requested data from the restore mechanism. The file system may then notify the application of the estimated time until restore. The application may notify a user of the estimated time, and may generate another request for the data after the estimated time has elapsed.
Owner:SYMANTEC OPERATING CORP
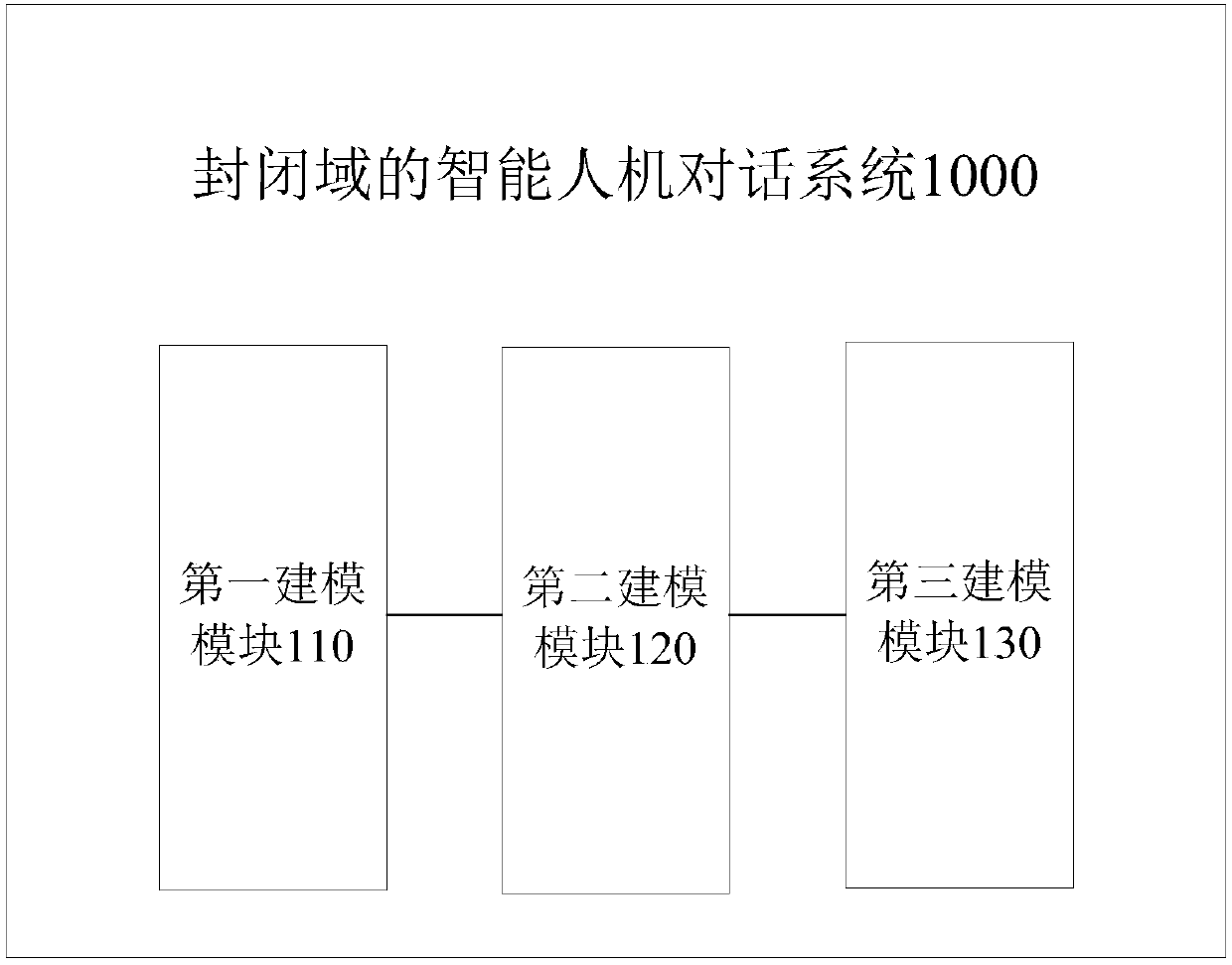
Intelligent man-machine conversation system in closed domain
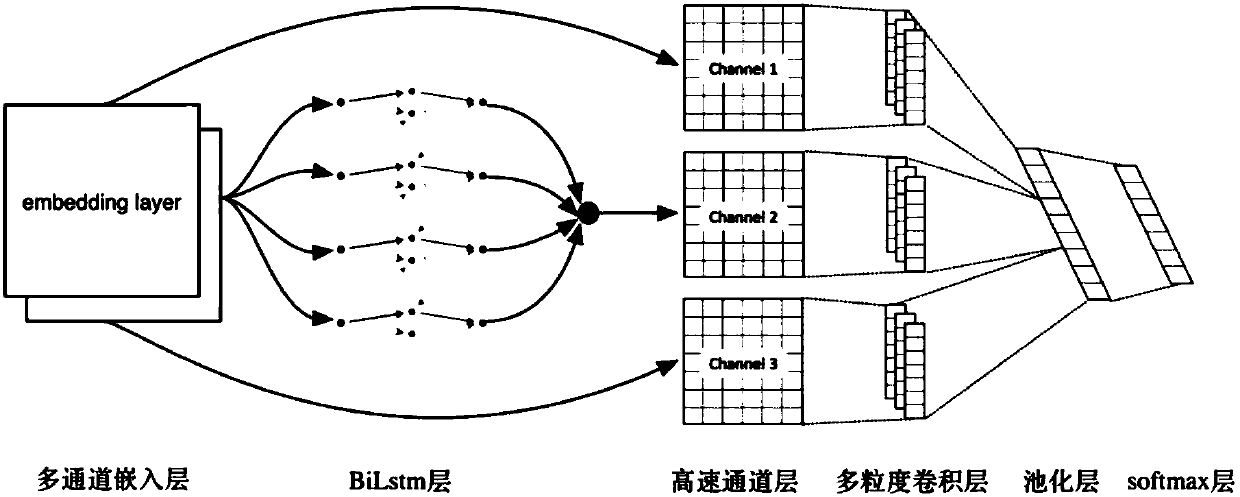
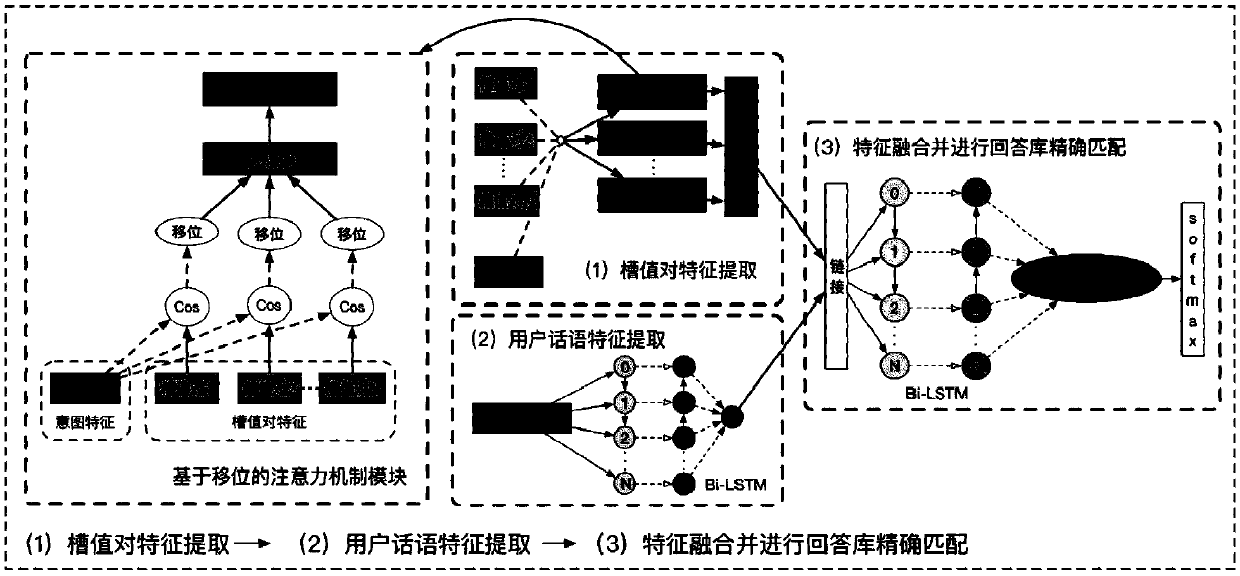
ActiveCN108415923AHigh intent recognition accuracyImprove accuracySemantic analysisCharacter and pattern recognitionShort-term memoryDialog system
The invention discloses an intelligent man-machine conversation system in a closed domain. The system comprises a first modeling module, a second modeling module and a third modeling module, wherein the first modeling module is used for constructing a multi-feature fusion deep intention recognition model on the basis of a bidirectional long / short-term memory network and a convolutional neural network; the second modeling module is used for constructing an MC-BLST-MSCNN-based conversation state tracking model by adoption of a man-machine conversation system current state input and context statement combined modeling manner; and the third modeling module is used for constructing a Bi-LSTM matching model on the basis of an extraterritorial recover mechanism of a displacement attention mechanism, and inputting recognized user intentions and user slot values into a displacement network to carry out weight distribution the attention mechanism, so as to realize conversation state encoding andconversation control matching. The system has higher intention recognition accuracy, conversation state tracking correctness and conversation control stability, so as to enhance the cognition intelligence capability of man-machine systems.
Owner:BEIJING UNIV OF POSTS & TELECOMM
D-BUS high-speed bus technology based on ring type Ethernet and auxiliary network
InactiveCN102347879ASimple wayEasy wiringLoop networksBus networksStructure of Management InformationEmbedded system
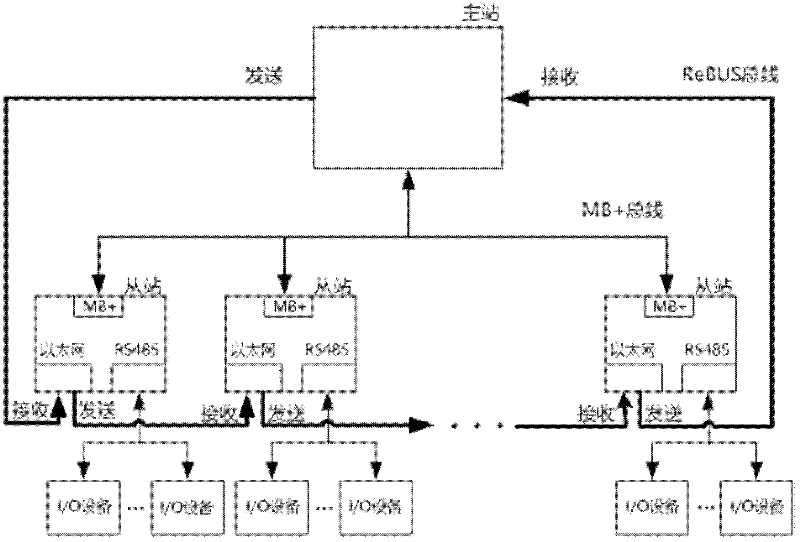
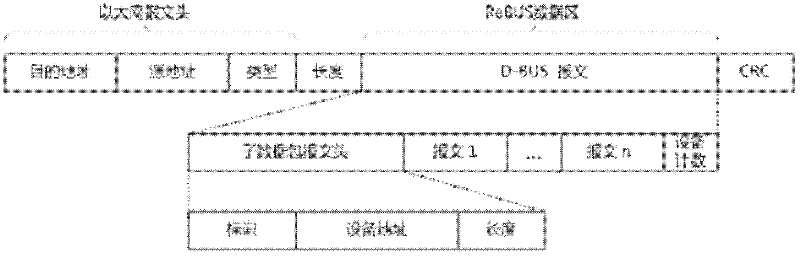
The invention provides a D-BUS high-speed bus technology based on a ring type Ethernet and an auxiliary network, which belongs to the technical field of industrial control. The D-BUS high-speed bus technology is characterized in that a D-BUS (Dual-BUS) high-speed bus network consists of a high-speed ring type Ethernet ReBUS and an auxiliary network MB+, wherein the ReBUS bus utilizes the physical layer specification of Ethernet IEEE802.3, a main station is connected with slave stations in series to form a ring type topological structure, the wiring mode for the main station and the slave stations is same with that of the slave stations with the slave stations, a receiving terminal of each equipment is connected with a transmitting terminal of the former equipment, the transmitting terminal of the equipment is connected with a receiving end of a latter terminal, the receiving terminals are sequentially connected with the transmitting terminals in the mode to form a ring type network structure, I / O equipment are connected with the slave stations through RS485 serial ports and serve as the expansion I / O of the slave stations, and failure detection comprising failure diagnosis, failure location and communication redundancy is realized by the MB+ bus. The invention has the beneficial effects that the ring type wiring cost is low, the data exchange of all network nodes is realized by one message, the communication efficiency is high, a failure detection and failure recovery mechanism is provided, and the reliability is high.
Owner:大连爱智控制系统有限公司
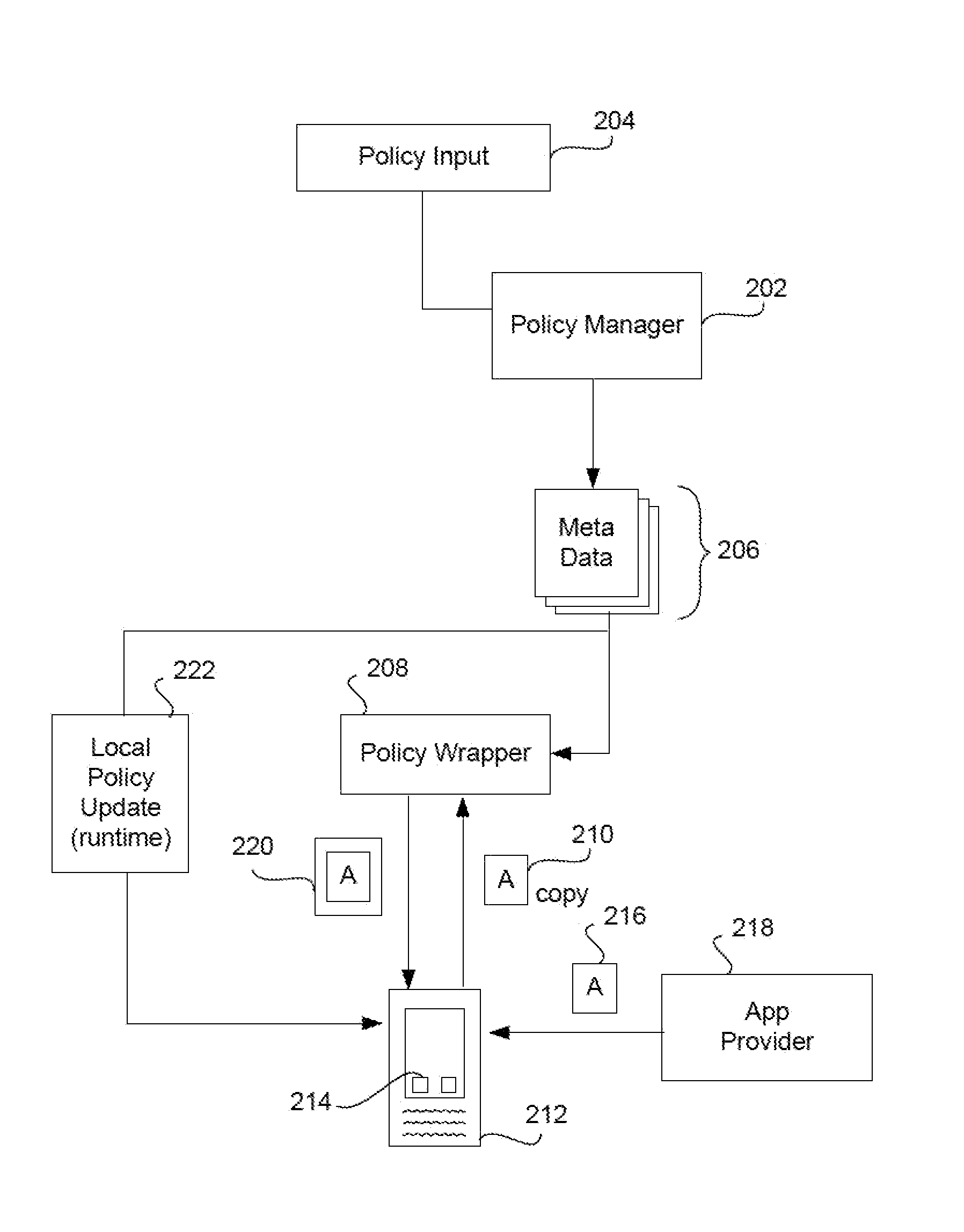
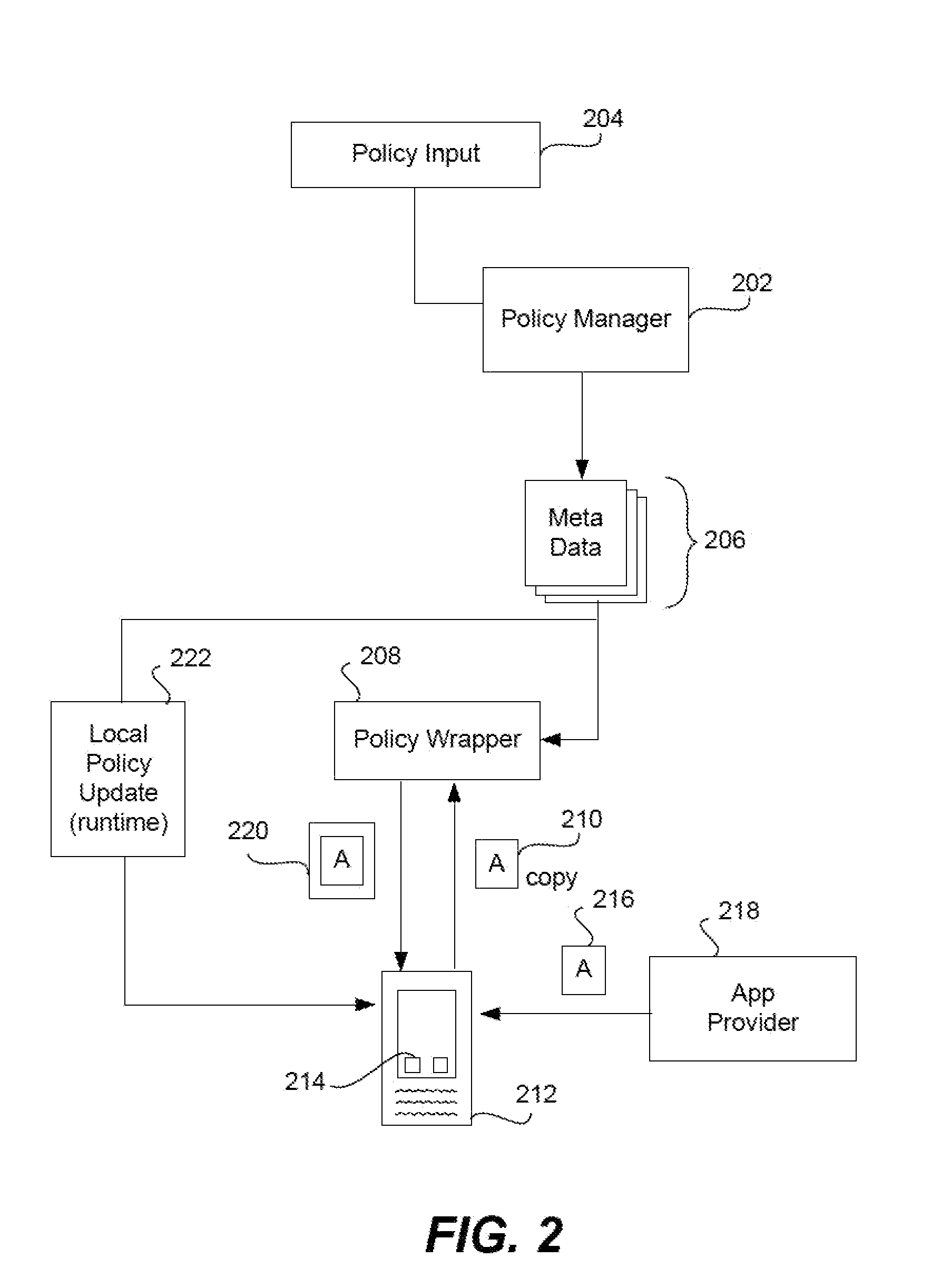
Secure unlocking and recovery of a locked wrapped app on a mobile device
InactiveUS20140040622A1Key distribution for secure communicationUnauthorised/fraudulent call preventionPassphraseApplication software
A security-wrapped app that is locked and inaccessible is unlocked and recovered using a secure and user-friendly protocol. Apps that are security wrapped are passphrase protected. The app security keystore on the device becomes locked. The keystore is encrypted with a recovery key which is only in an encrypted form on the device and cannot be decrypted or otherwise accessed by the user. As such, the user cannot unlock the keystore on the device and therefore is not able to unlock the app. The app can be unlocked using a recovery mechanism that is highly secure in all communications between the mobile device and the service provider server. At the same time the recovery mechanism is easy for the end user to carry out.
Owner:BLUE CEDAR NETWORKS INC
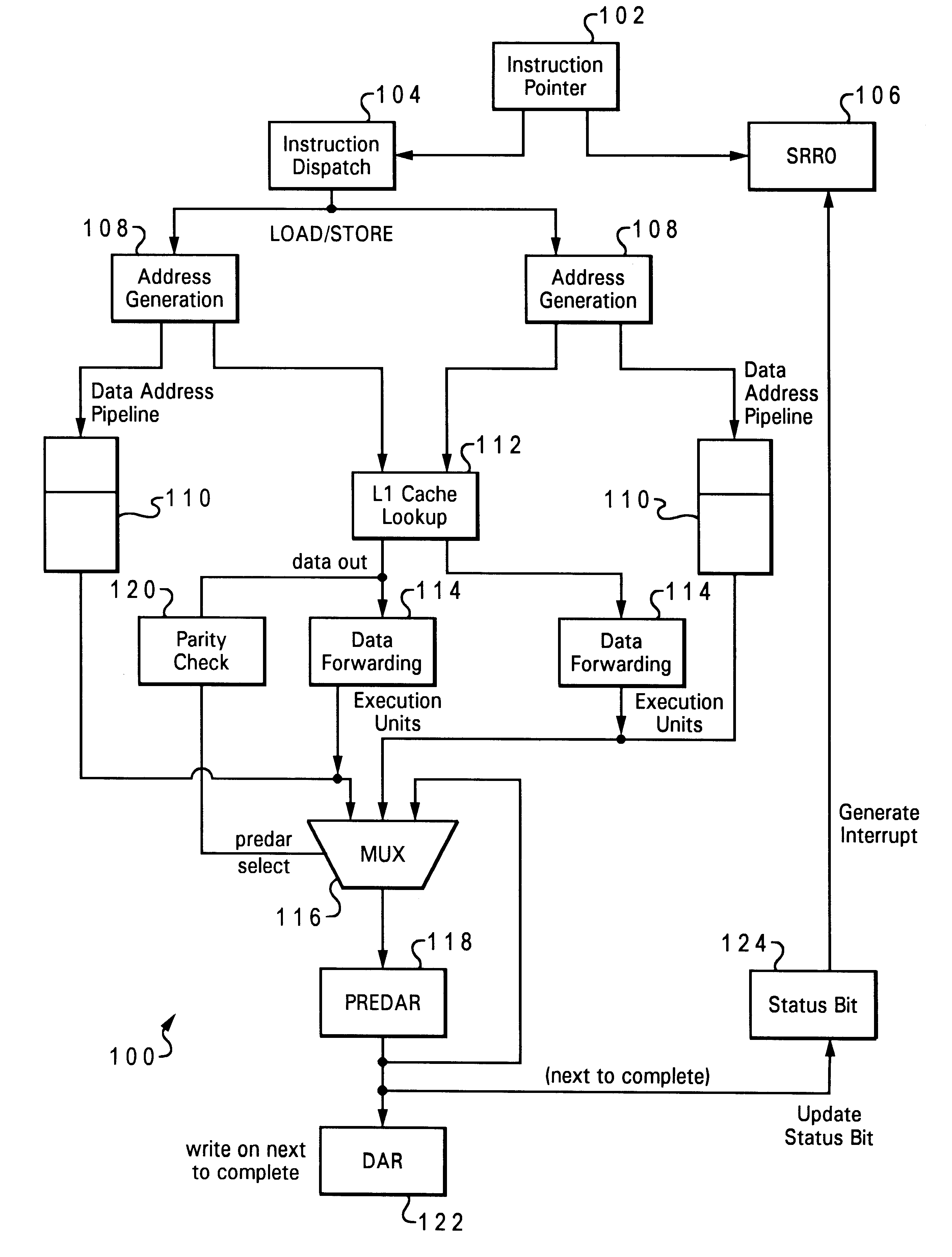
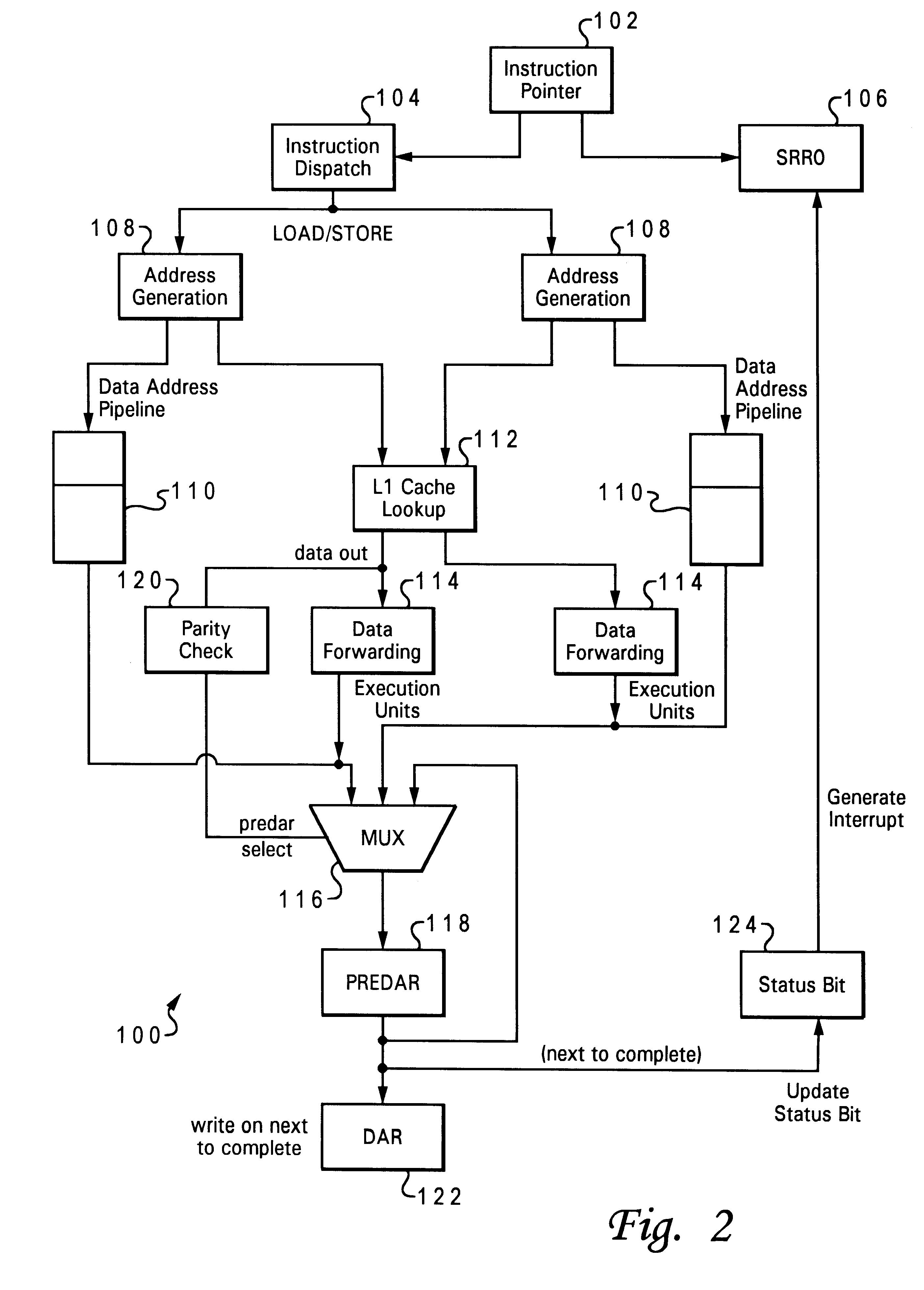
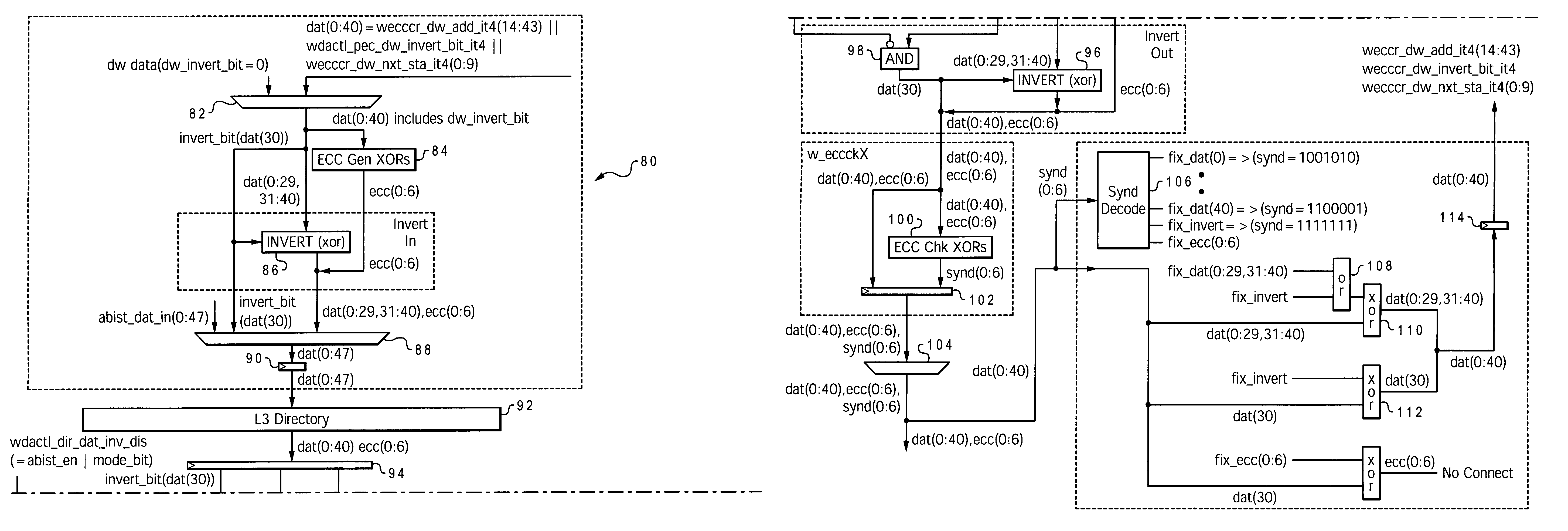
Recovery mechanism for L1 data cache parity errors
A method of handling a cache error (such as a parity error), which allows a software recovery, by reporting the error using an unrelated system resource, such as an interrupt service, and particularly a data storage interrupt. The parity error can be reported by generating a data storage interrupt and using the data storage interrupt status register (DSISR) to indicate that the data storage interrupt is a result of the parity error. The context of the processor can be fully synchronized while handling the parity error.
Owner:IBM CORP
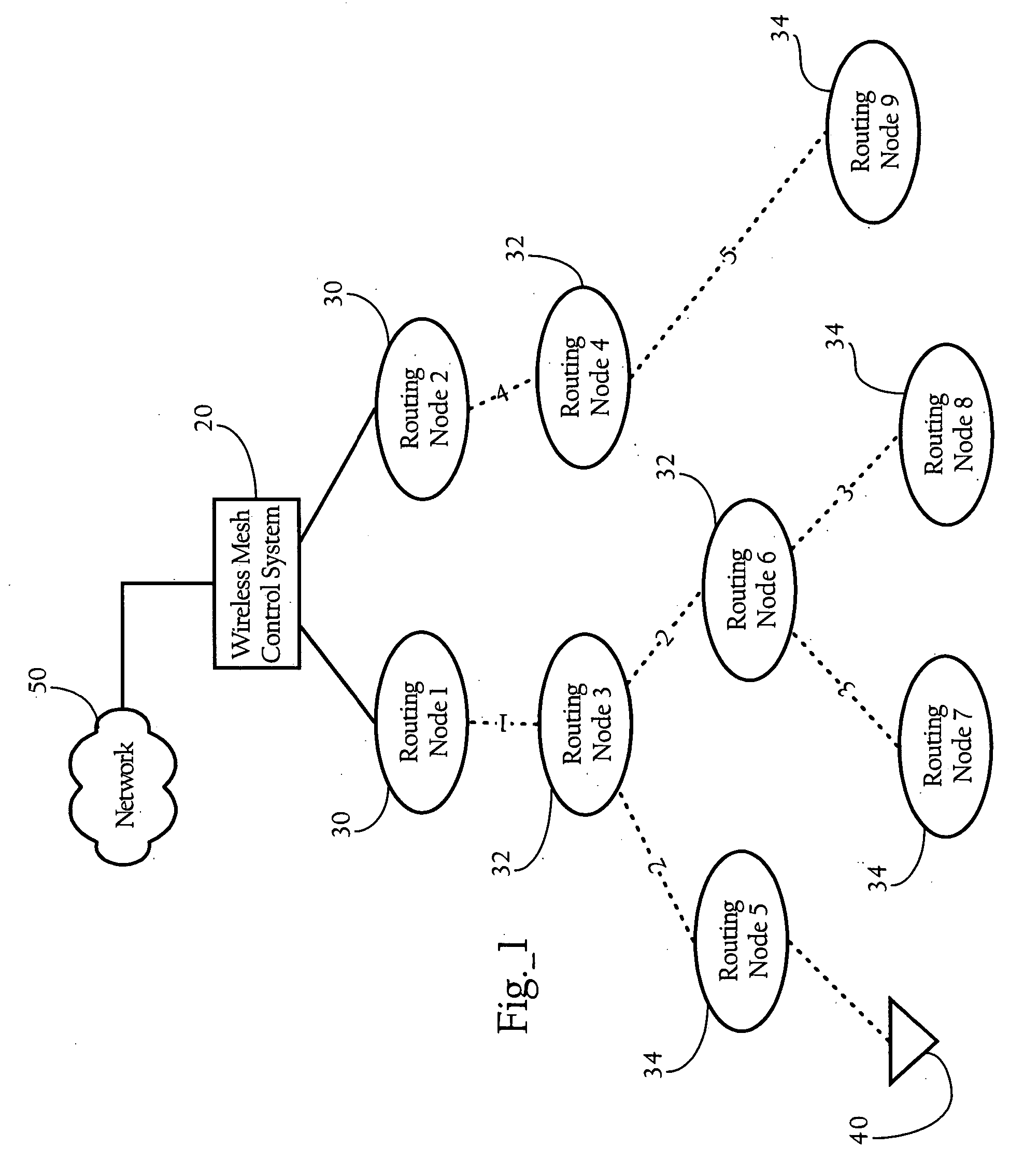
Configuration of failure and acquire timeouts to facilitate recovery from failures in hierarchical mesh networks
InactiveUS7505450B2Synchronisation arrangementNetwork topologiesWireless mesh networkComputer science
Methods, apparatuses and systems directed to providing an efficient failure recovery mechanism in hierarchical wireless mesh networks. In one implementation, the present invention mitigates the effect of synchronization loss between a parent and child node on the hierarchical wireless mesh network. In one implementation, the present invention employs a configuration scheme whereby the parent node failure timeouts are greater than the time to acquire a parent node to mitigate the effect of synchronization loss on downstream nodes in the hierarchical mesh network.
Owner:CISCO TECH INC
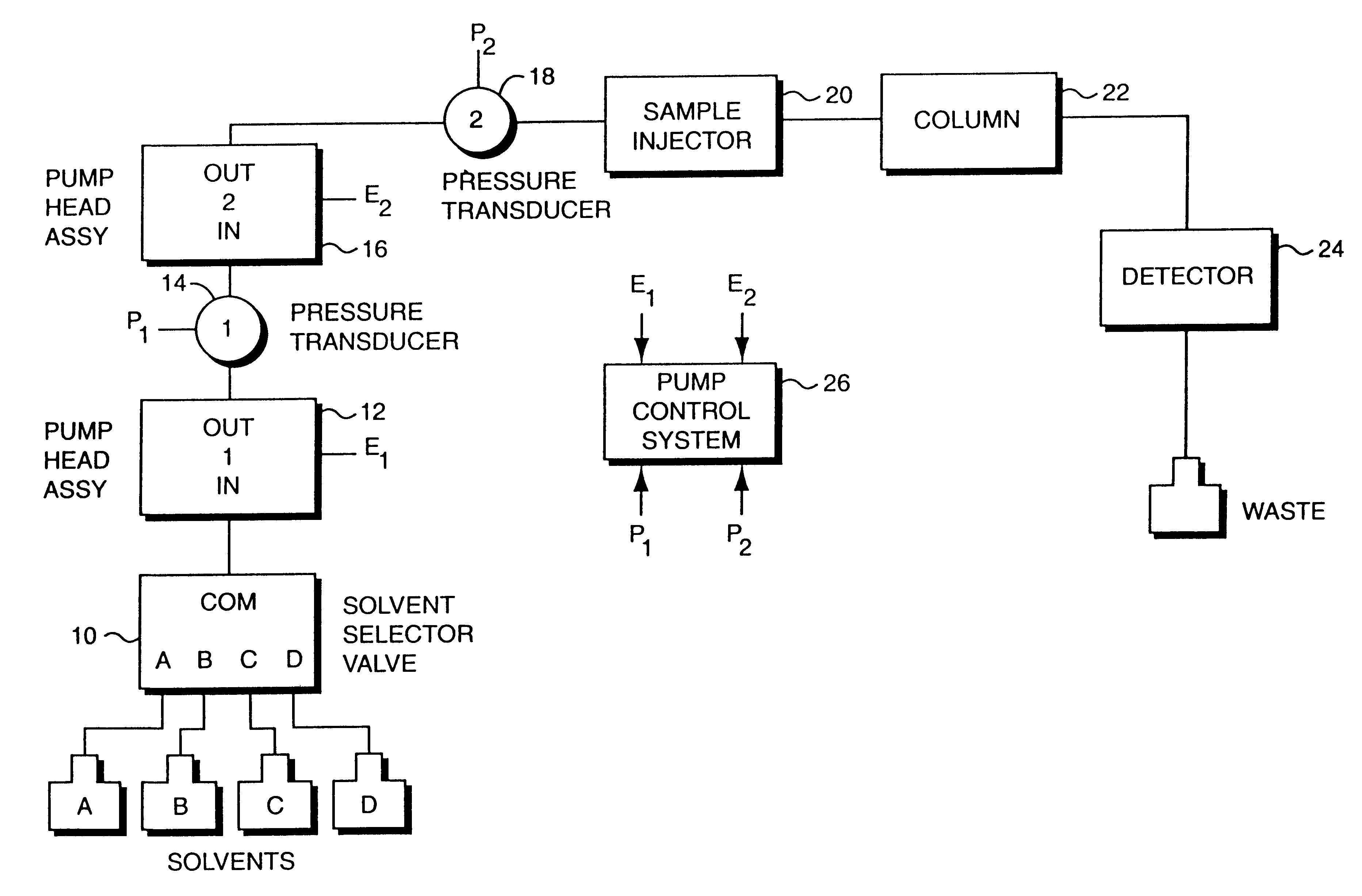
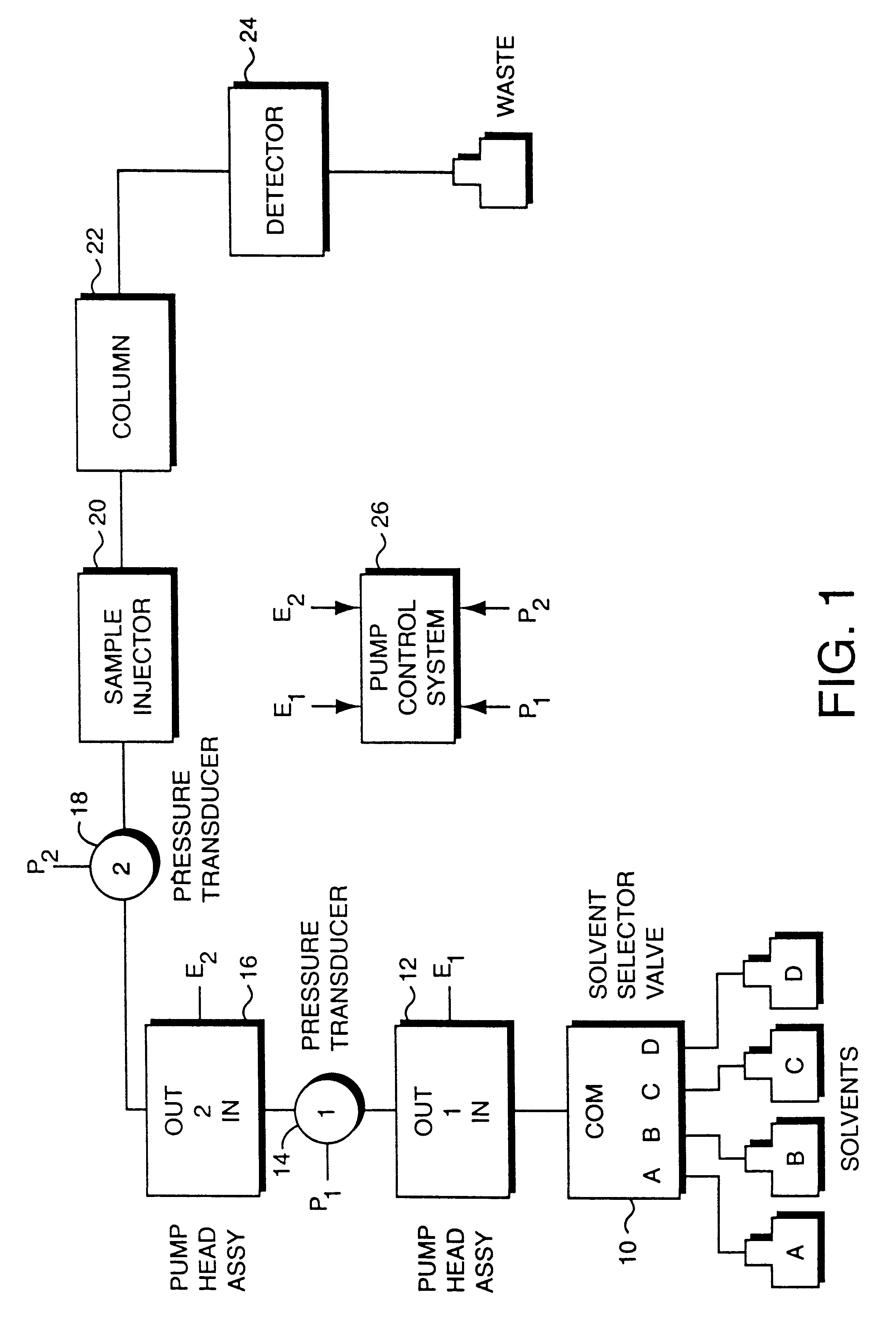
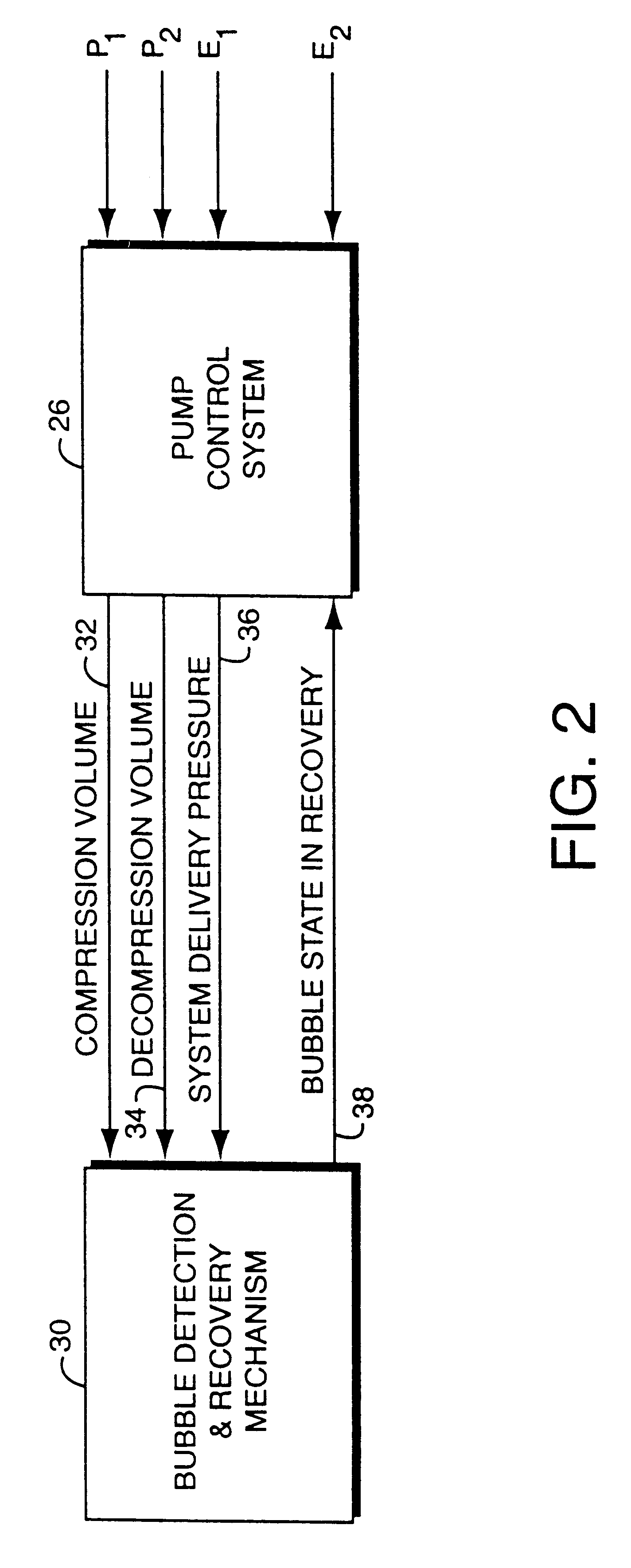
Bubble detection and recovery in a liquid pumping system
InactiveUSRE37553E1Minimizes delay volumeMinimizes compositional rippleIon-exchanger regenerationLoose filtering material filtersGas to liquidsEngineering
A serial, dual piston high pressure fluid pumping system that overcomes the difficulties of gas in the fluid stream without the need for added mechanical valves or fluid paths. A bubble detection and recovery mechanism monitors compression and decompression volumes of the serially configured dual pump head pump, and the overall system delivery pressure. Bubble detection is effected by sensing a ratio of compression to decompression volume and determining if the ratio exceeds an empirical threshold that suggests the ratio of gas-to-liquid content of eluent or fluid in the system is beyond the pump's ability to accurately meter a solvent mixture. The magnitude of the ratio of compression to decompression volume indicates that either the intake stroke has a bubble or that the eluent has a higher-than-normal gas content. Once a bubble has been detected, recovery is effected by forcing the pump into a very high stroke volume with the compression and decompression stroke limits constrained to obtain the largest delivery stroke compression ratio that will expel a bubble or solvent that has detrimental quantities of gas.
Owner:WATERS INVESTMENTS
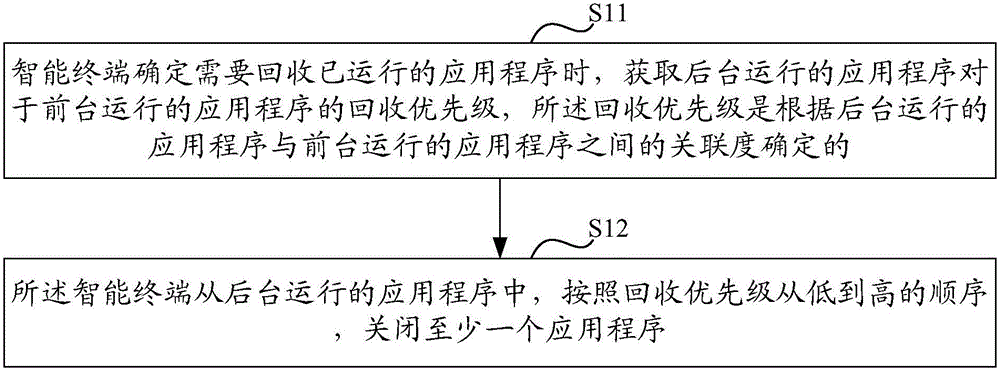
Application program management method and device in intelligent terminal
ActiveCN105843650AImprove experienceProgram loading/initiatingProgram managementDegree of association
The invention discloses an application program management method and device in an intelligent terminal, which are used for solving the problem that the existing recovery mechanism is realized based on the length of running time of an application program, so that the switching efficiency is affected. The method comprises the following steps: when determining that the application program which has been run needs to be recovered by the intelligent terminal, acquiring a recovery priority of application programs running in the background for application programs running in the foreground, wherein the recovery priority is determined according to a degree of association between the application programs running in the background and the application programs running in the foreground; and closing at least one application program from the application programs running in the background according to the recovery priority from low to high. Since the recovery priority of each application program is determined according to a degree of association between this application program and the application programs running in the foreground, the higher the degree of association, the higher the use frequency of users, so that the application program management method and device in the intelligent terminal provided by the invention can reduce the probability of closing the application programs which are frequently used by the users, thus the user experience can be improved.
Owner:QINGDAO HISENSE MOBILE COMM TECH CO LTD
Cache directory array recovery mechanism to support special ECC stuck bit matrix
InactiveUS7272773B2Simple structureEasy to useMemory adressing/allocation/relocationCode conversionData applicationCorrection code
A method of correcting an error in an ECC protected mechanism of a computer system, such as a cache or system bus, by applying data with a number of bits N to an error correction code (ECC) matrix to yield an error detection syndrome, wherein the ECC matrix has a plurality of rows and columns with a given column corresponding to a respective one of the data bits, and selected bits are set in the ECC matrix along each column and each row such that encoding for the ECC matrix allows N-bit error correction and (N−1)-bit error detection. When an error is detected and after it is corrected, the corrected data is inverted and then rewritten to the cache array. The corresponding inversion bit for this entry is accordingly set to indicate that the data as currently stored is inverted.
Owner:INT BUSINESS MASCH CORP
Joint-layer restoration in packet-over-optical networks
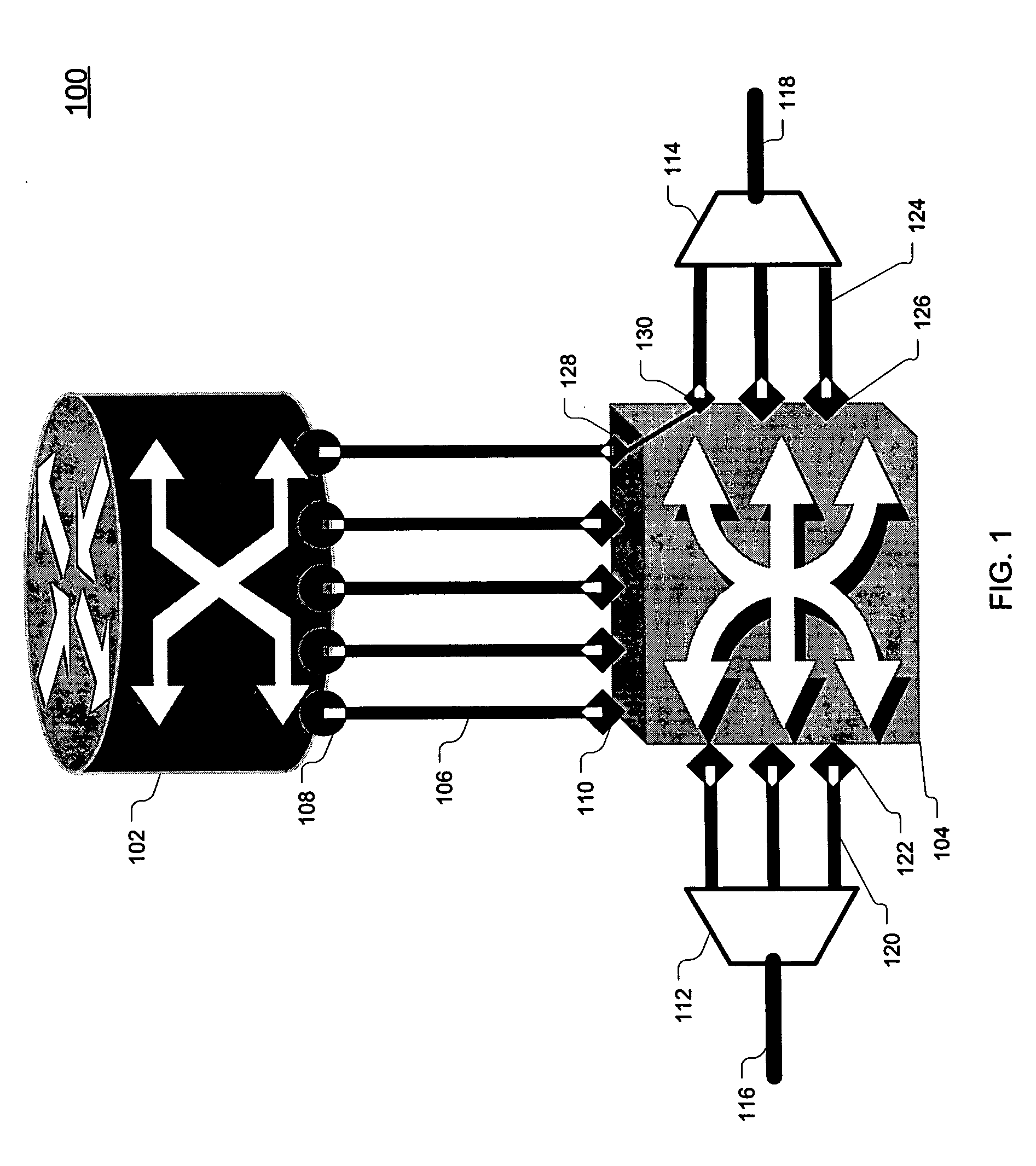
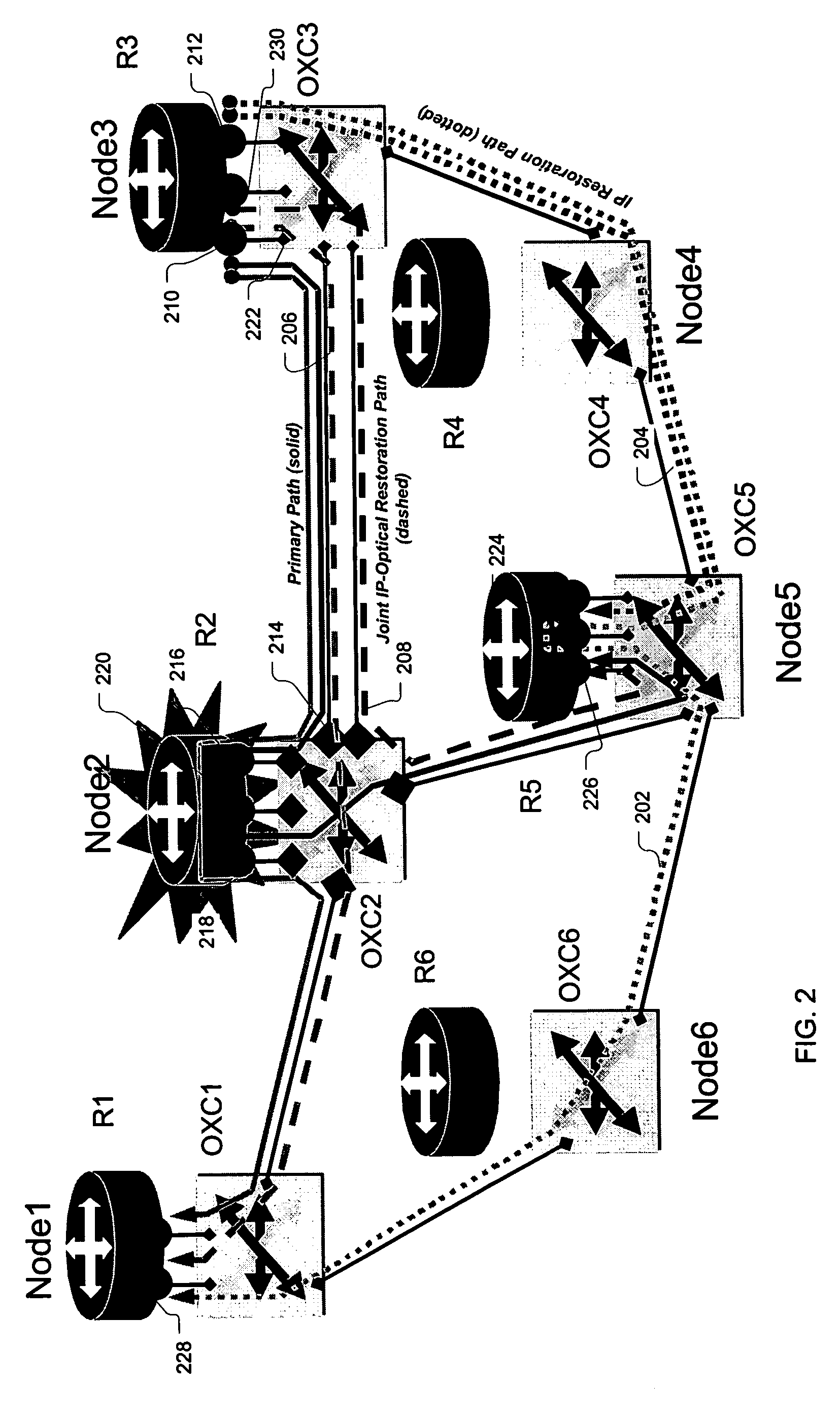
A joint “packet-optical” layer restoration mechanism protects against single, packet-layer router failures by managing network resources from both the packet layer and the optical transport layer in a synergistic manner. It reuses packet-layer router service-ports and / or transport-layer service wavelengths associated with optical switch-ports instead of reserving additional standby packet-layer router service-ports. It can reuse resources from primary paths that are unaffected by router failures and paths that exist for link-failure protection at the optical layer. Embodiments feature a modified node structure that includes both an IP router and a dynamically reconfigurable OXC, which dynamically establishes connectivity between IP-router ports and transport-layer optical fibers. The joint-layer router provides fine-granularity grooming at the IP layer and full-fledged wavelength networking via dynamic wavelength switching and / or wavelength translation at the optical layer. The latter can change the wavelength cross-connections on-demand to perform restoration or to modify the connectivity between IP routers in the network.
Owner:LUCENT TECH INC
Routing method and routing path recovery mechanism in wireless sensor network environment
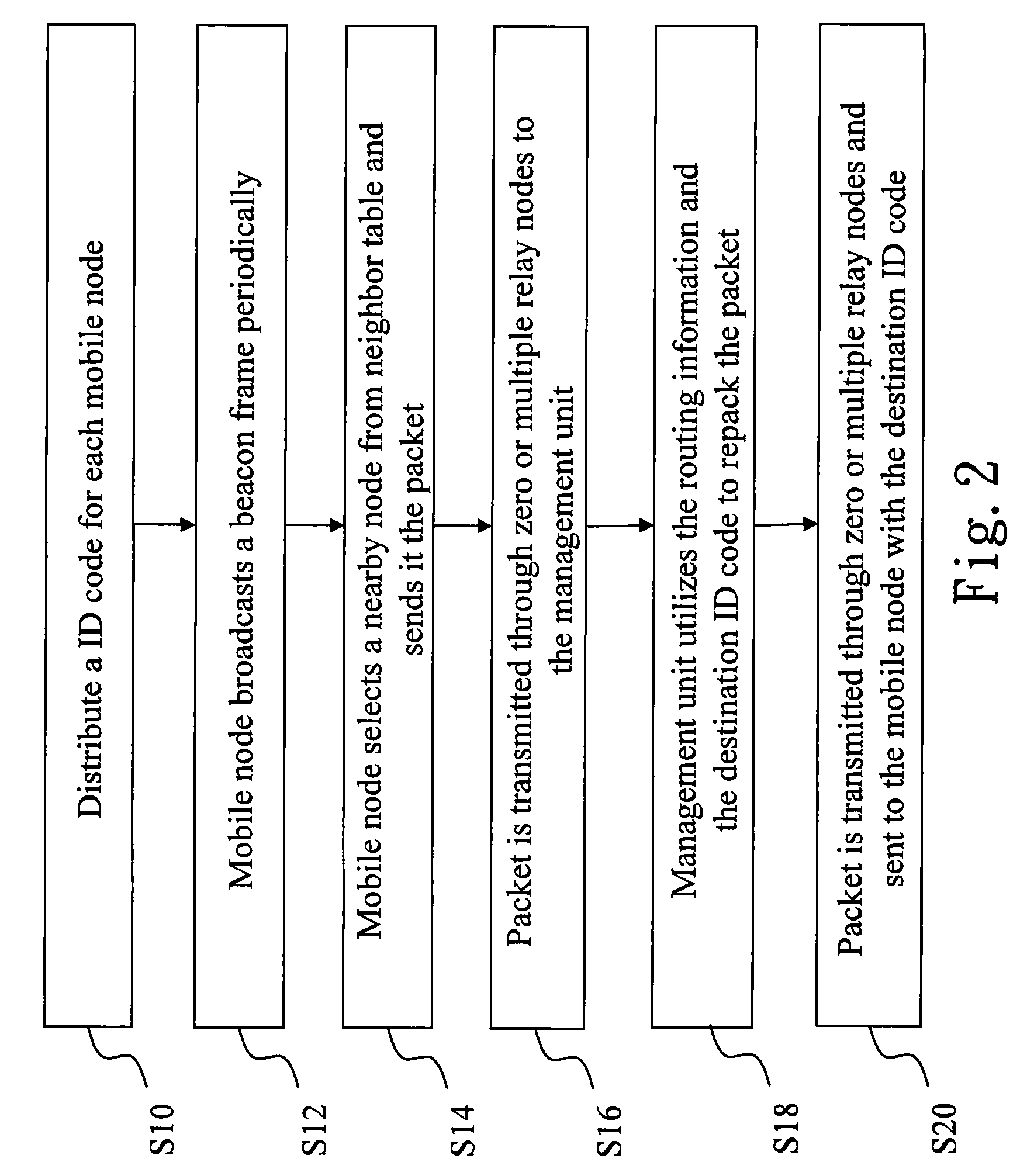
InactiveUS20100260071A1Quick buildFrequency-division multiplex detailsTime-division multiplexManagement unitWireless sensor networking
The present invention discloses an asymmetric routing method and routing path recovery mechanism. The wireless sensor network environment includes at least a management unit, at least a gateway, and mobile nodes. When joining, each mobile node obtains an unique ID code and, additionally, a depth as the gradient to the management unit. Accordingly, a mobile node sends an uplink packet via a nearby node with lower depth to the management unit; while the management unit transmits a downlink packet to a mobile node by utilizing the source route method. When the parent node of a mobile node is damaged or moves to another position or said mobile node with its sub-tree descendants changes their position together, the uplink routing path is recovered via selecting a nearby node of the sub-tree as relay node and the downlink routing path is recovered via sending a control message to the management unit.
Owner:NAT CHIAO TUNG UNIV
Liquid ejection head unit and image forming apparatus
InactiveUS20090058921A1Simple configurationInking apparatusOther printing apparatusLight beamImage formation
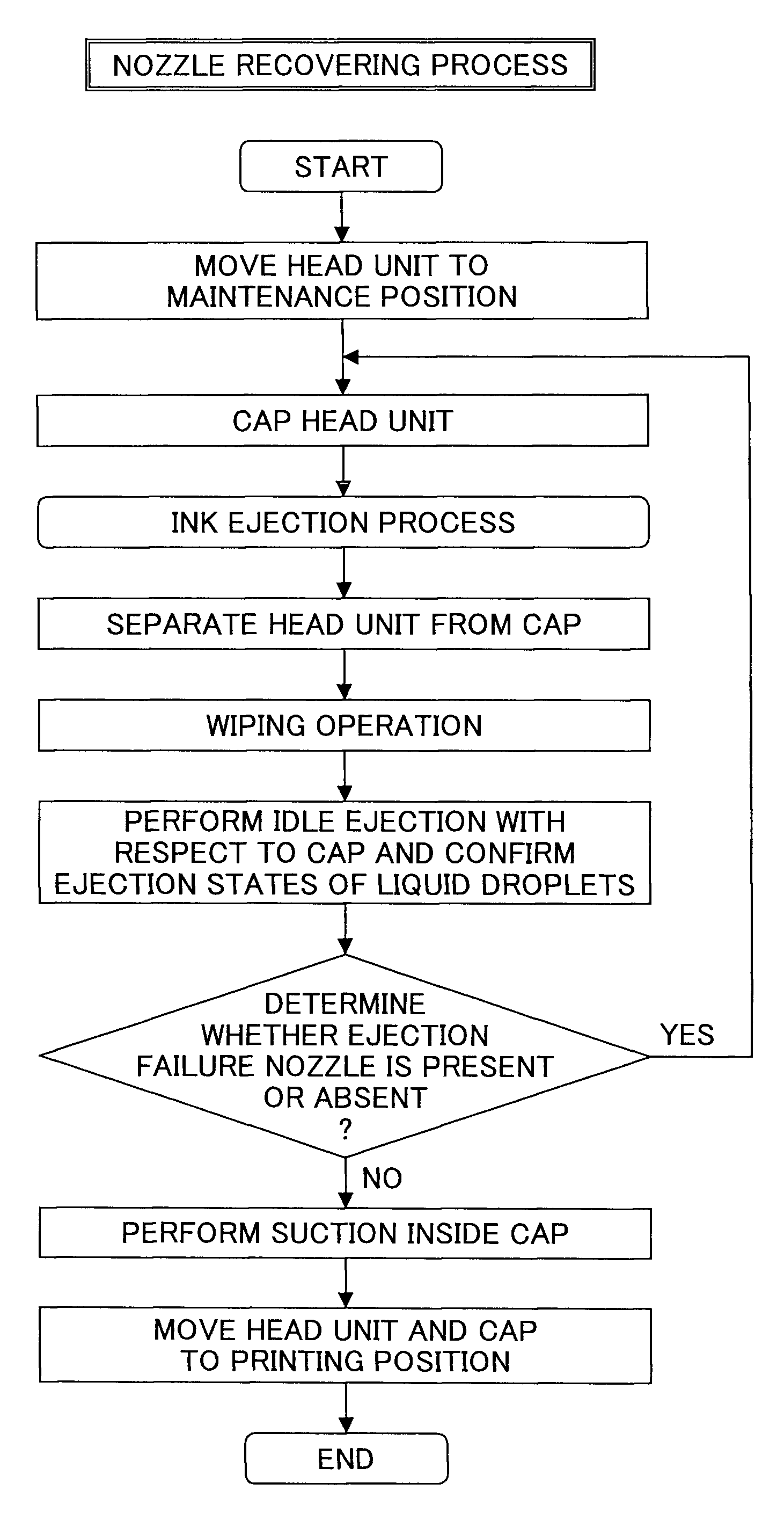
A liquid ejection head unit has plural liquid ejection heads and a liquid droplet detection device that detects liquid droplets ejected from the heads. The liquid droplet detection device has LD arrays that are provided at one side surface in the longitudinal direction of the head unit and serve to emit light beams; photo diodes that are provided at the other side surface in the longitudinal direction of the head unit and serve to receive the light beams emitted from the LD arrays; and a light path forming unit that causes the light beams emitted from the LD arrays to pass through along a head surface as detection light beams from the outer side of an area capped by a cap of a maintenance and recovery mechanism of an image forming apparatus and that causes the emitted light beams to be incident on the light-receiving unit provided at the outer side of the area.
Owner:RICOH KK
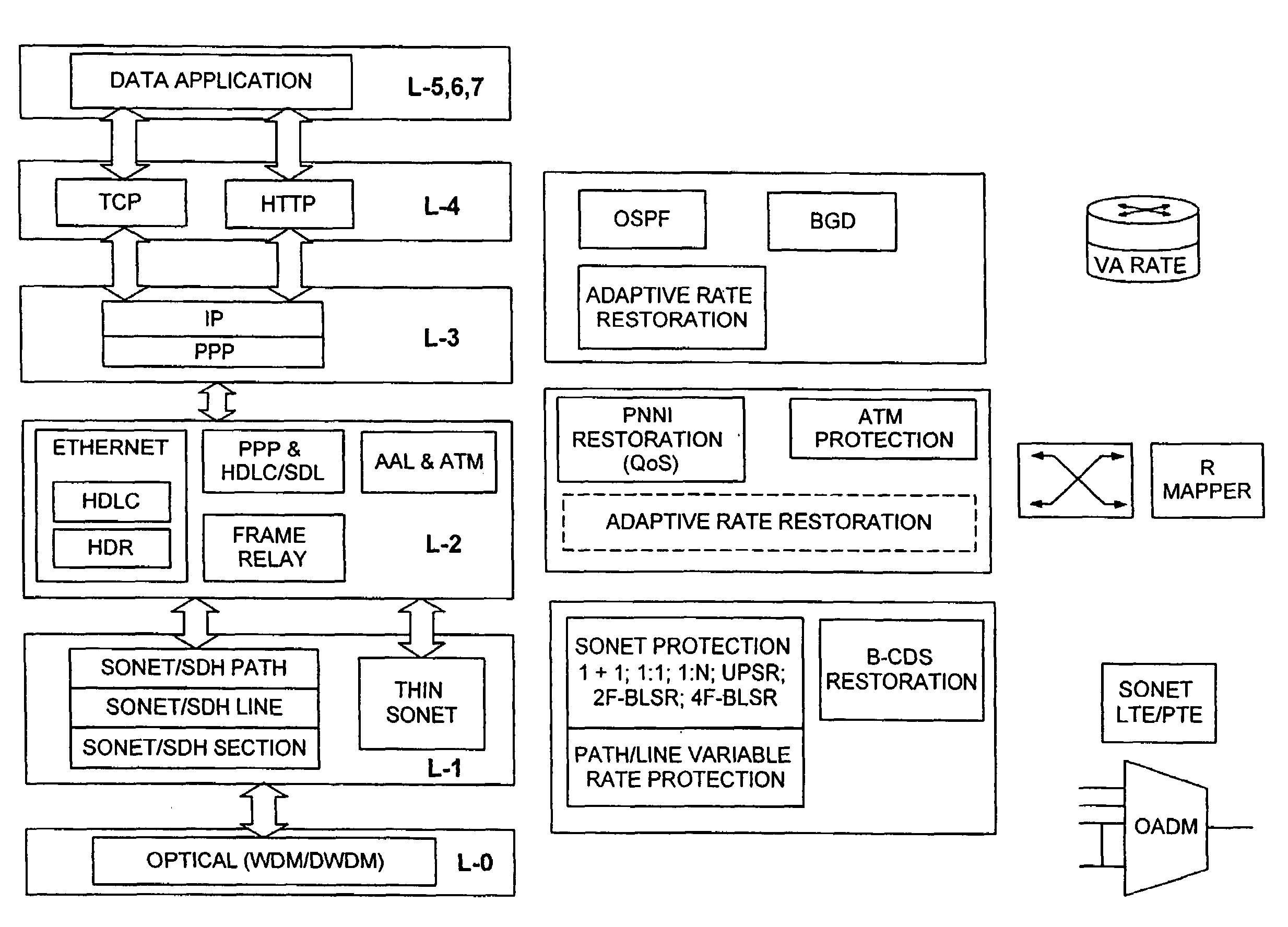
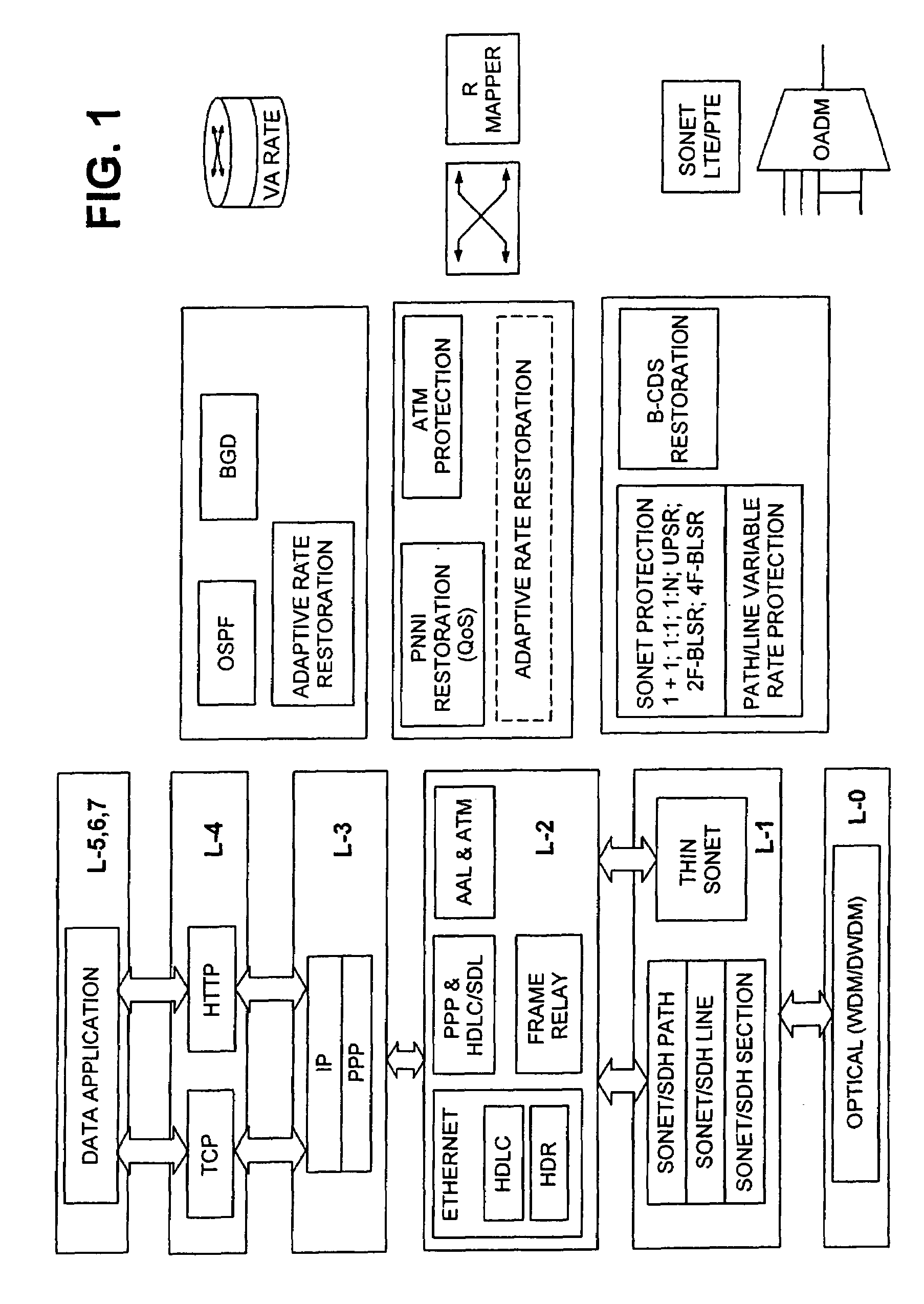
Adaptive rate traffic recovery mechanism for communication networks
A traffic recovery mechanism for communication networks uses a layer-1 adaptive rate protection scheme that compliments layer-3 restoration mechanisms. The protection scheme allocates less bandwidth to the traffic during a protection switch than during the normal operating conditions. This scheme allows the network to roll off more gracefully from the perspective of the applications routed through it. Rate adaptation is effected by a new interface between the data equipment and the transport network, which switches information transfer rate between two or more predetermined levels.
Owner:CIENA
Method for fault-injection test based on virtual machine
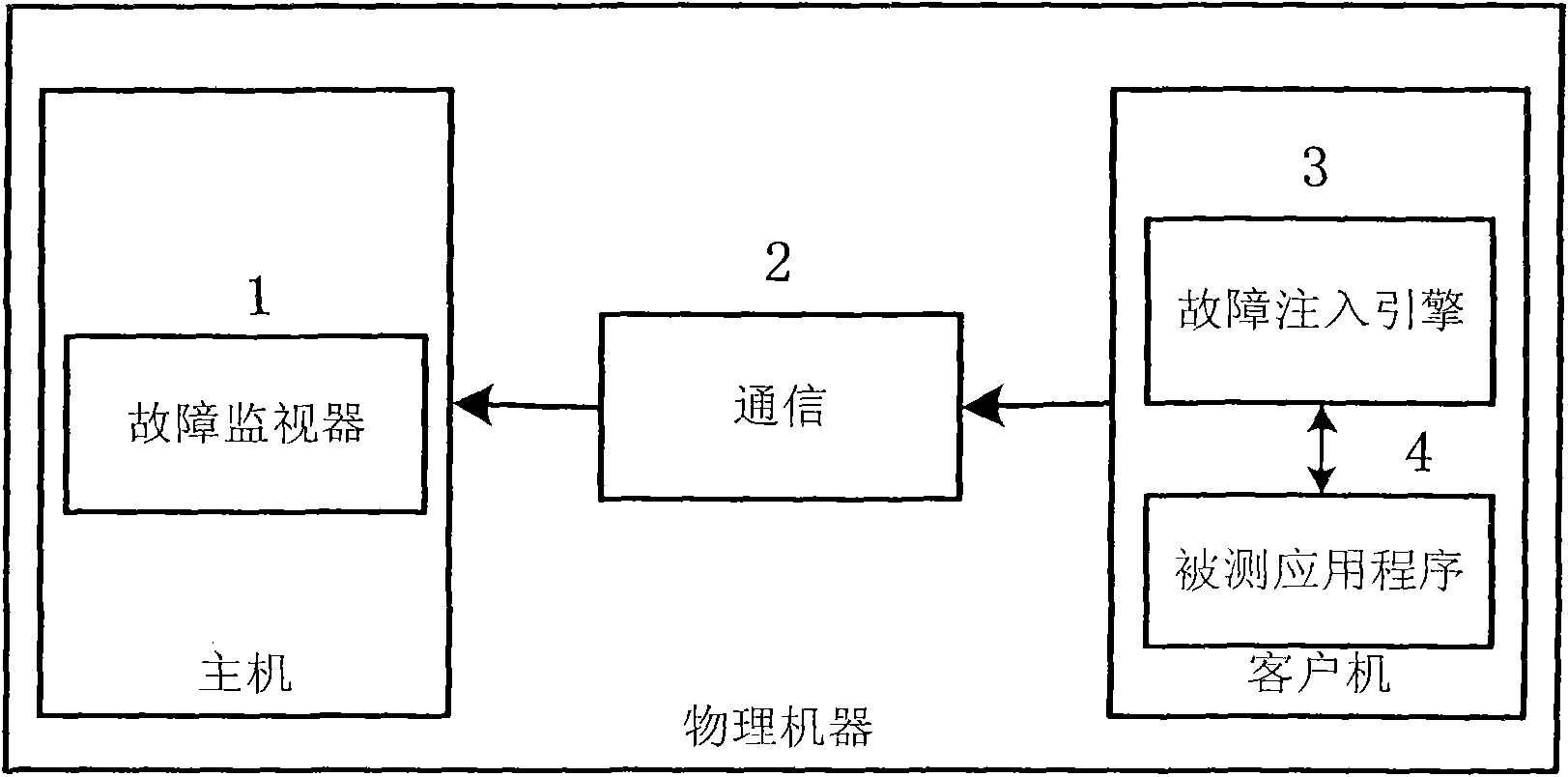
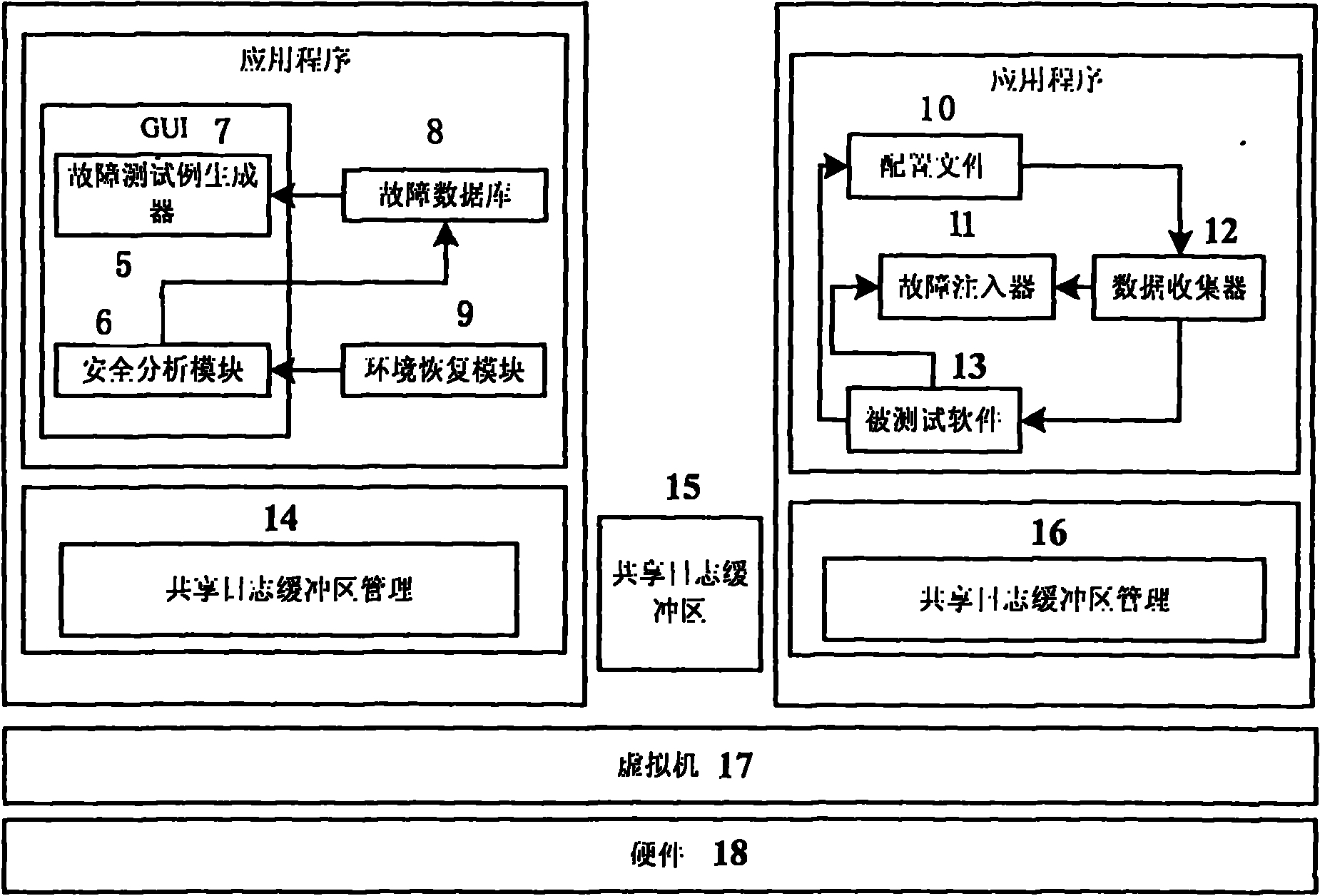
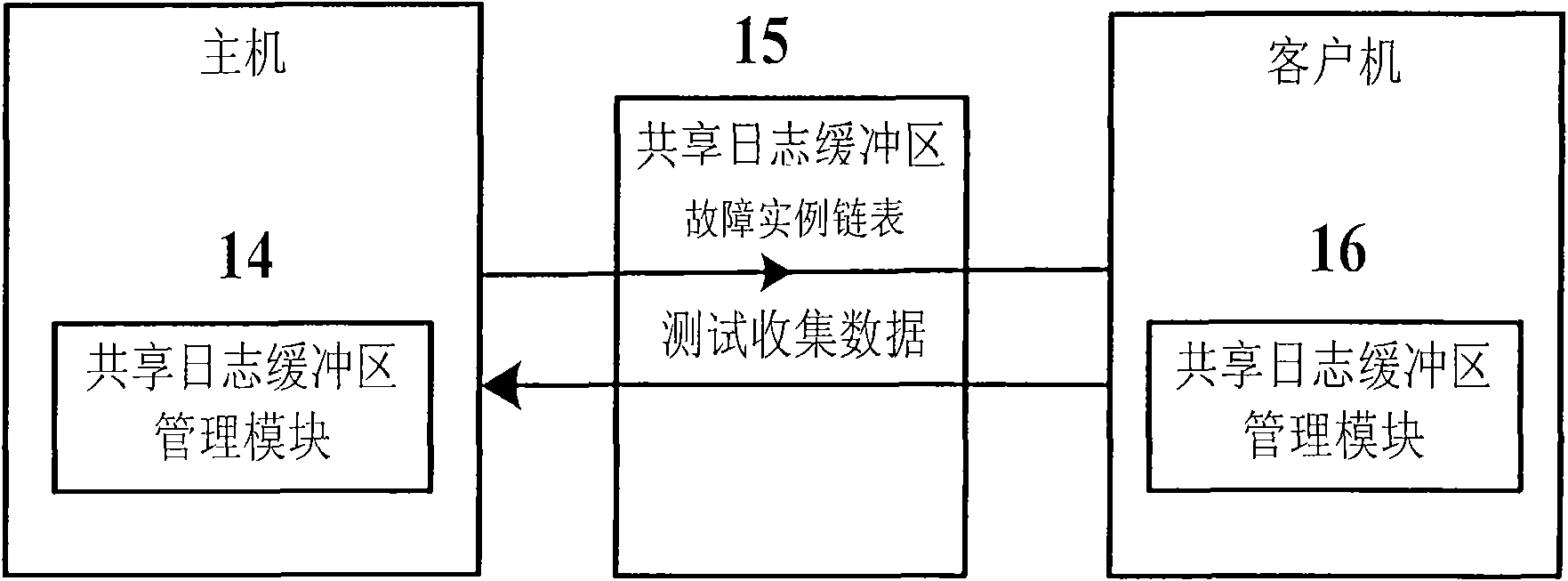
The invention provides a method for using a virtual machine to improve the performance in software-testing based on fault injection. Based on the EAI (environment-application interaction) model put forward by WENLIANG DU, Syracuse University (US), the fault injection is carried out on the interaction point of the application program and the environment thereof in the invention to disturb the environment and further test the software vulnerability, thus reducing the semantic difference between the injected fault and the actual fault, reducing the number of test cases and respectively achieving the two functional parts of the test tool at the host and guest of the virtual machine; and based on the shared files between the virtual machine and the guest, and the backup and recovery mechanism of the virtual machine, the invention can improve the robustness and flexibility of the test tool. The tool generated by the method comprises an application program configuration file (10), a fault test case generator (5), a security analysis module (6), a graphical user interface (7), an environment recovery module (9), a fault injector (11) and a data collector (12), wherein the tool further comprises software (13) to be tested and shared memory auxiliary modules (14), (15) and (16) of the virtual machine for sharing the data related to the tests. The method of the invention is capable of effectively detecting and simulating the security breaches in the software and improving the security of the software.
Owner:曾凡平 +2
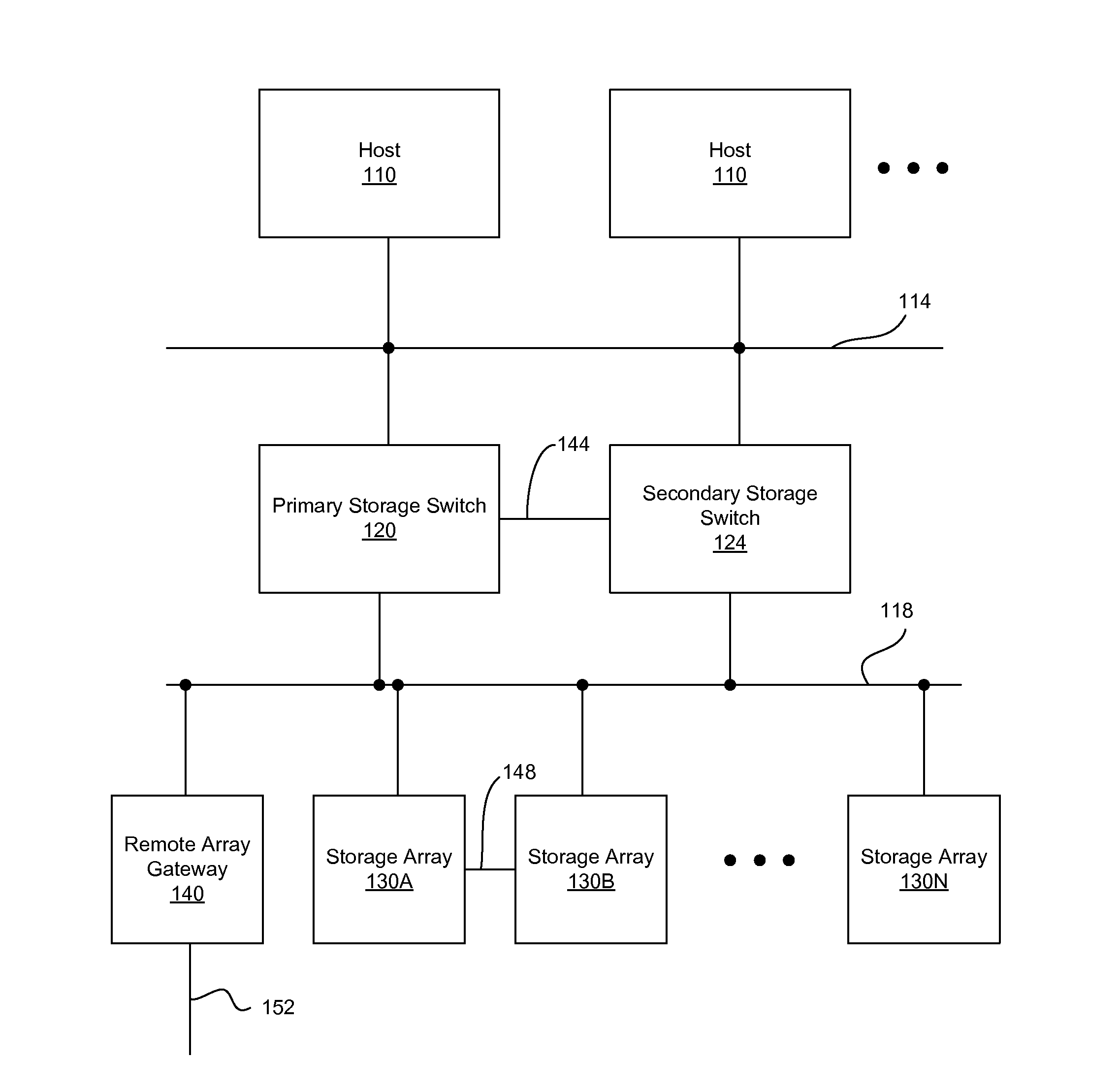
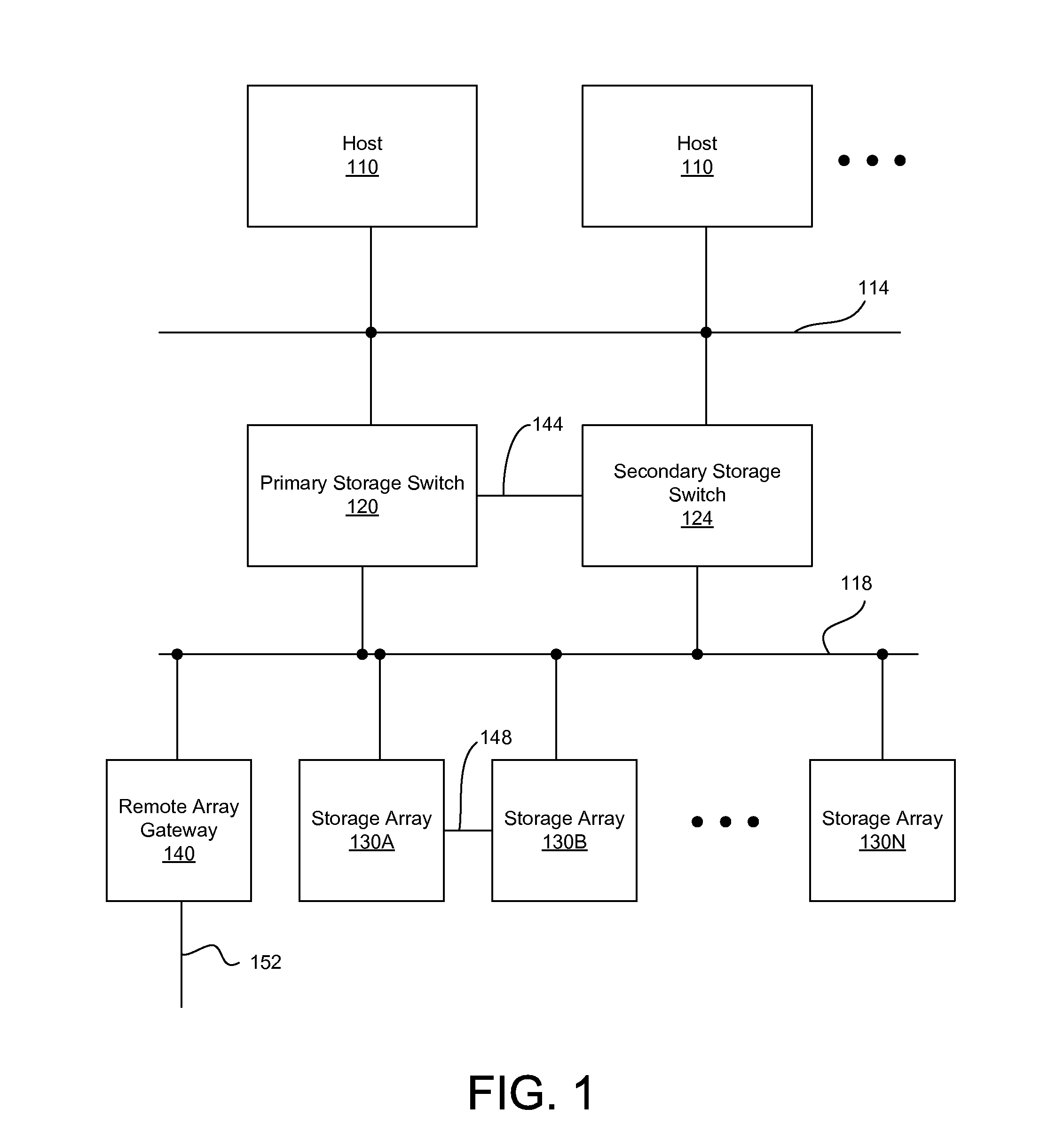
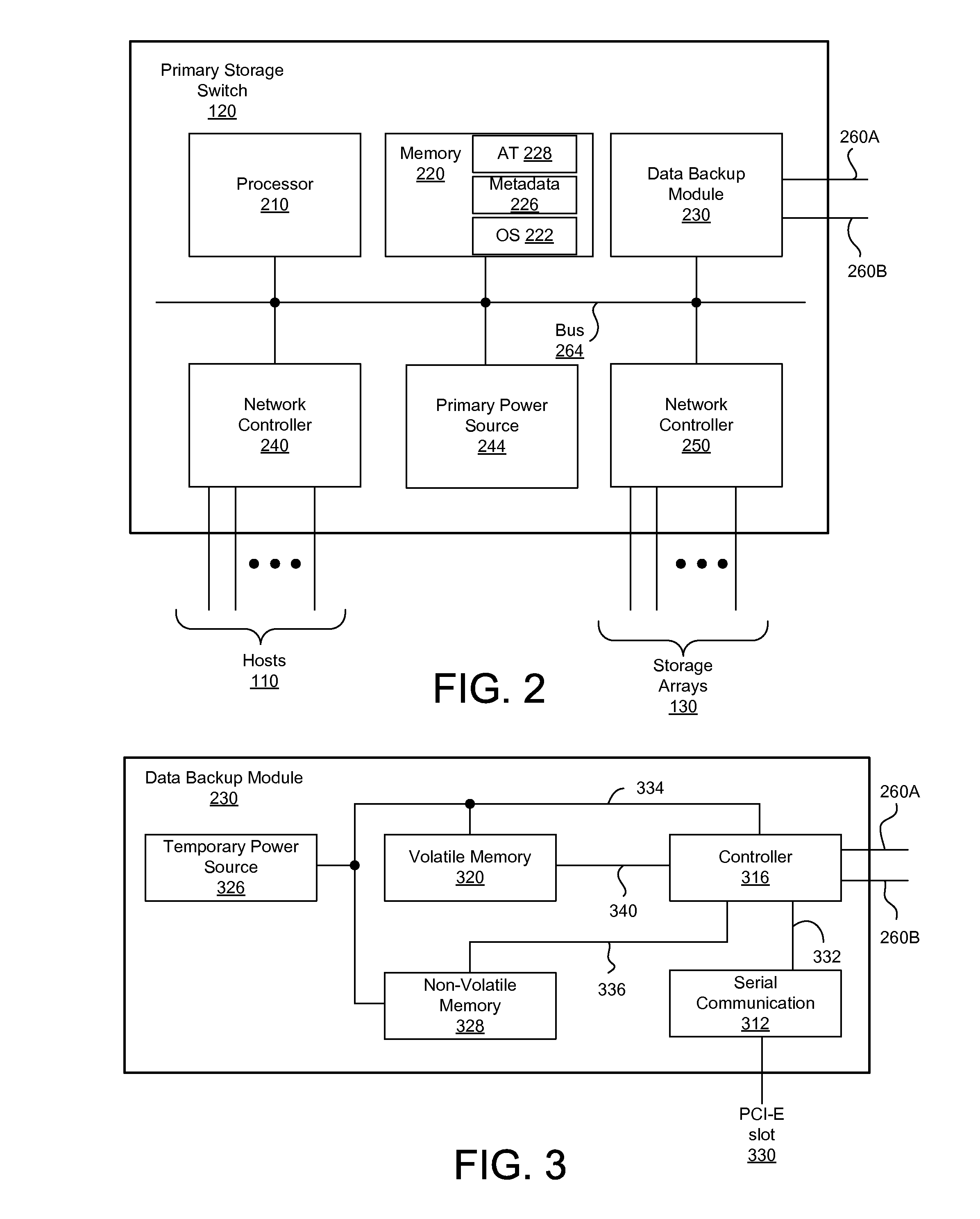
Power failure management in components of storage area network
A storage area network (SAN) is provided with redundancy and recovery mechanism. A primary storage switch performs dynamic address translation between logical storage addresses received from host devices and physical addresses of SAN storage arrays. When power failure in the primary storage switch is detected, metadata associated with the dynamic address translation operation is sent to a secondary storage switch via a network connection to provide the dynamic address translation in lieu of the primary storage switch. A storage array experiencing power failure similarly sends cached data to another storage array via a network connection so that the other storage array can substitute the failed storage array. During the power failure, a data backup module in the primary storage switch or the storage array is powered by a temporary power source.
Owner:INTERMODAL DATA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com