Method for defending Sybil attacks in block chain based on improved PBFT algorithm
A blockchain and algorithm technology, applied in the transmission system, electrical components, etc., can solve the problems of lack of consideration of participating nodes having different speaking rights, and the limited role of Sybil nodes, so as to achieve the effect of defending against Sybil attacks and reducing the number of communications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be described in detail below in conjunction with specific embodiments shown in the accompanying drawings.
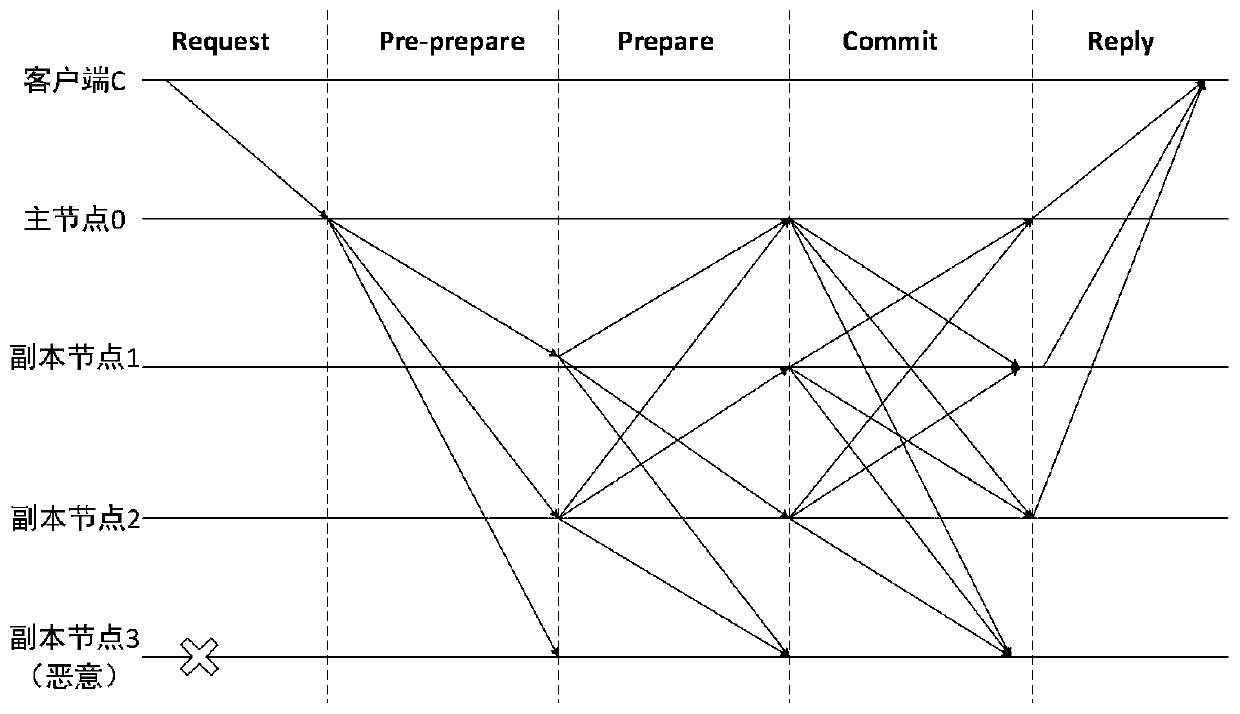
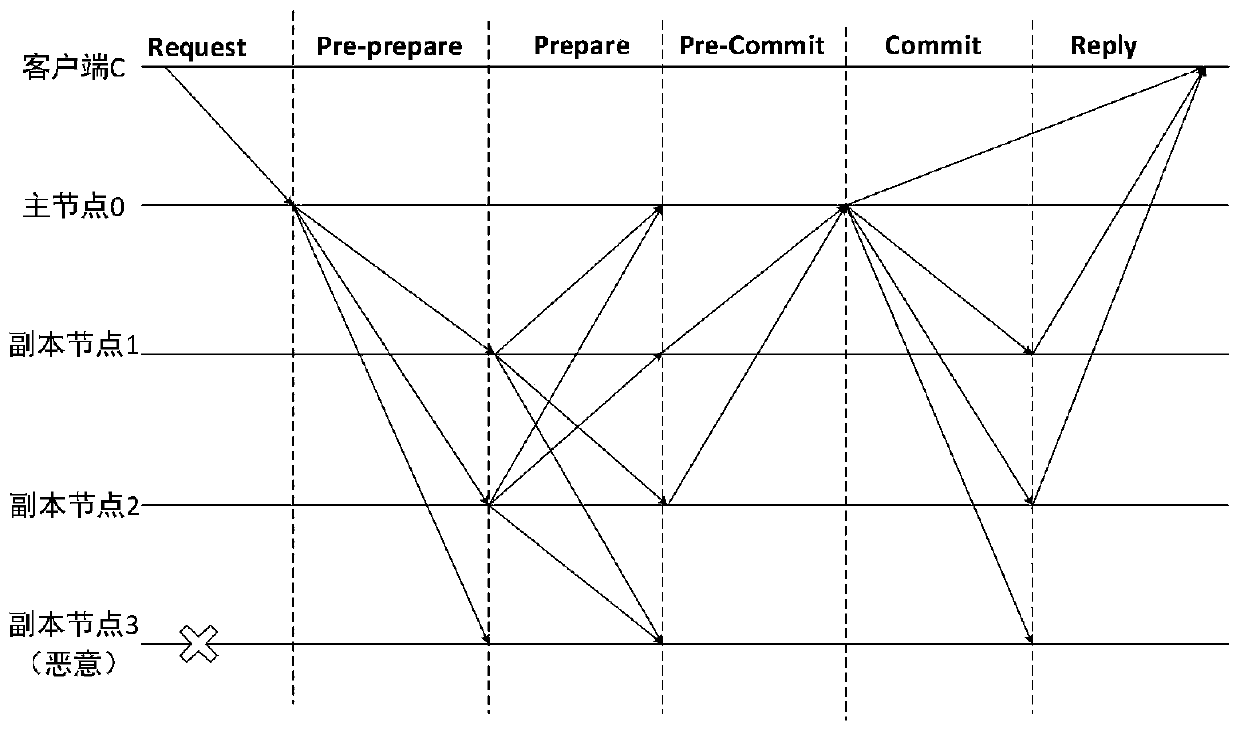
[0035] figure 1 It is the work flow chart of the original PBFT algorithm, in which the core three stages of the consensus algorithm are the Pre-prepare stage (pre-preparation stage), the Prepare stage (preparation stage), and the Commit stage (commit stage).
[0036] figure 1 The C in it stands for the client, 0, 1, 2, and 3 represent the number of the node, among which 0 is the master node, and the crossed 3 means that it may be a faulty node or a problem node. The behavior shown here is that there is no request for other nodes. response. The whole process is as follows:
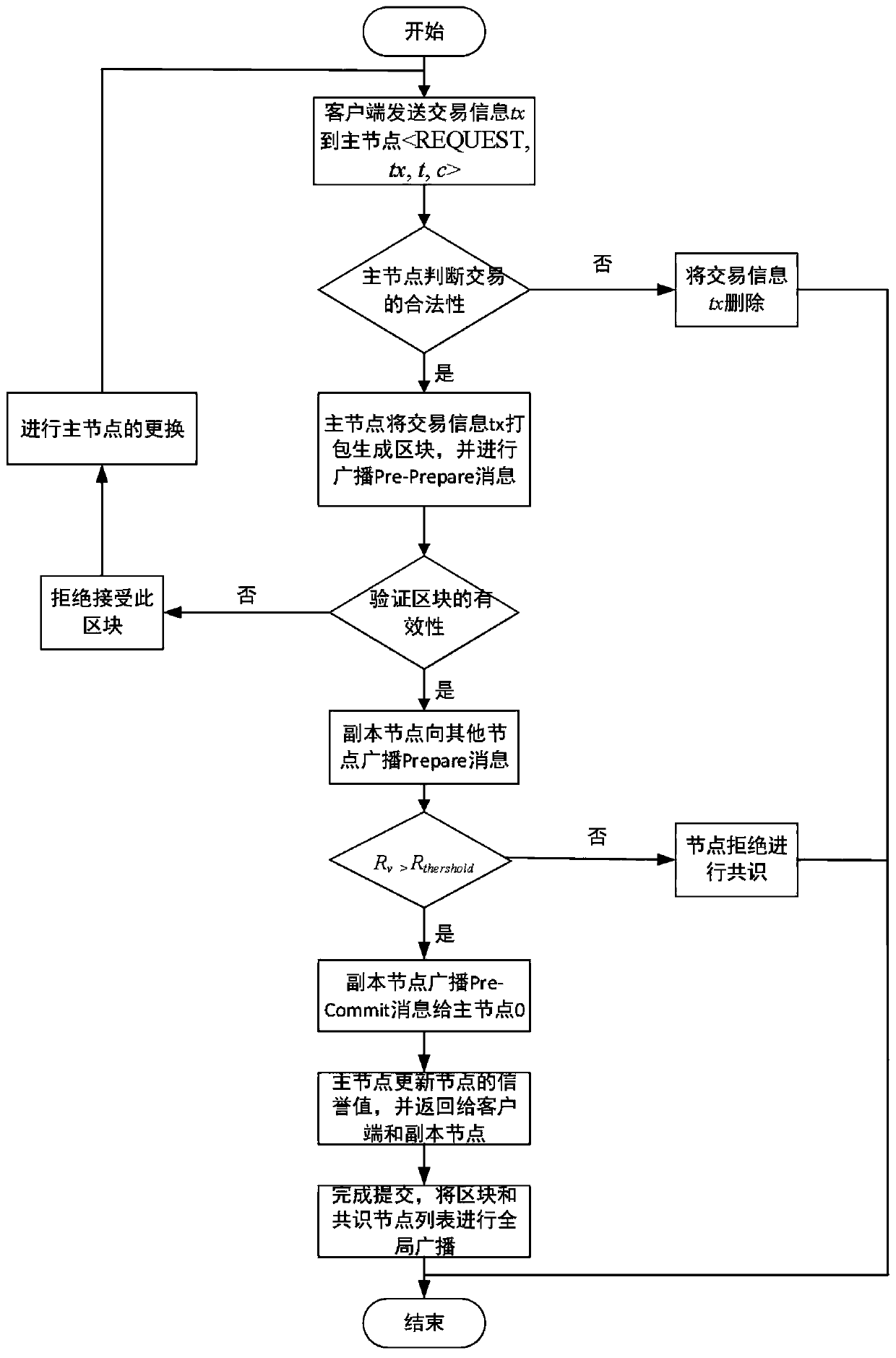
[0037] Step 11, REQUEST phase: client c sends a self-signed request to master node 0. o The specific operation of the request, t the timestamp appended by the client when requesting, c the client identifier, REQUEST contains the message content m, and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com