Hardware 3DES for using digital power consumption compensation to prevent from power consumption power attack
A technology of power consumption attack and 3DES-1, which is applied in the field of smart cards, can solve problems such as power consumption attacks and hidden dangers, and achieve the effect of preventing power consumption attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
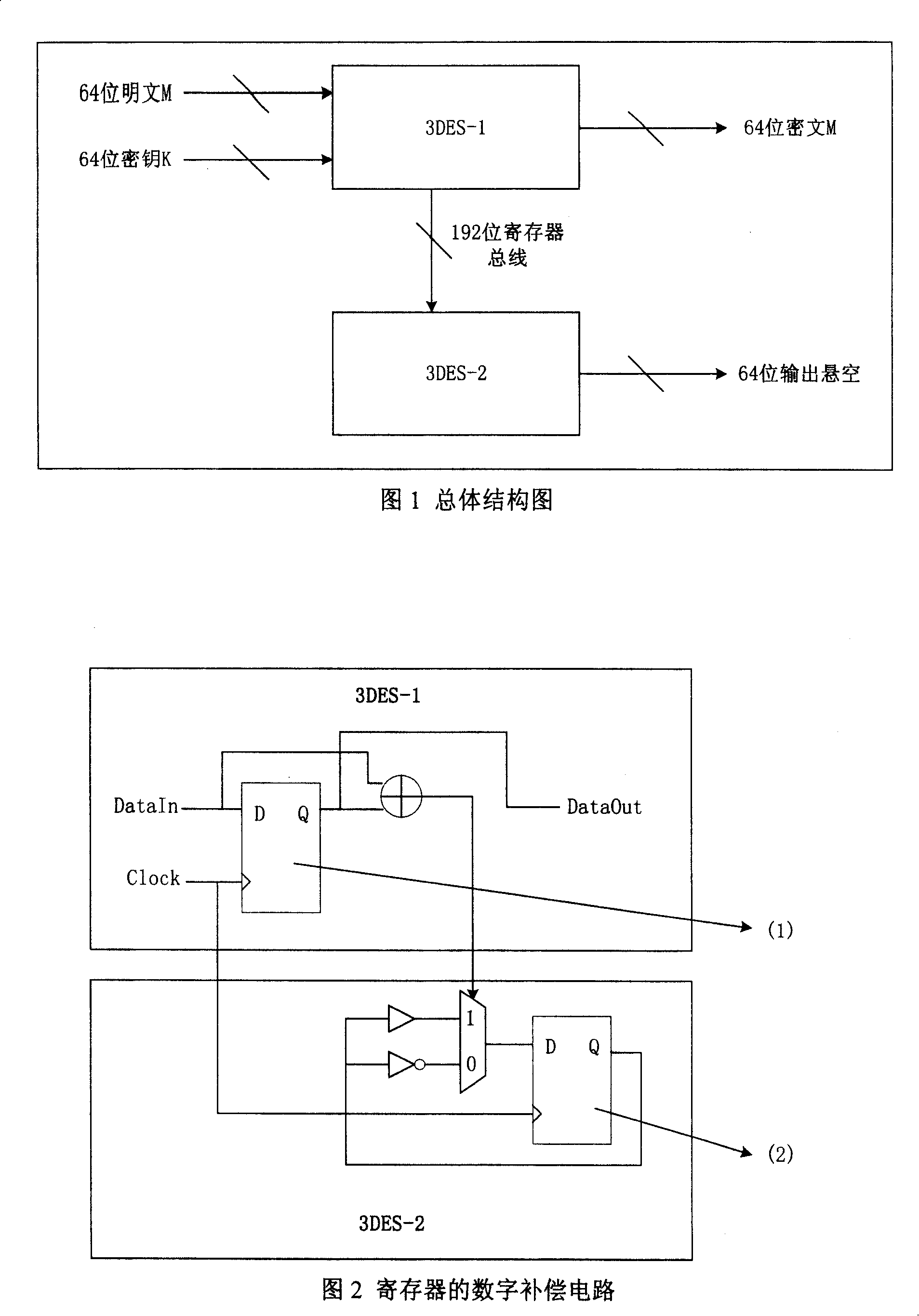
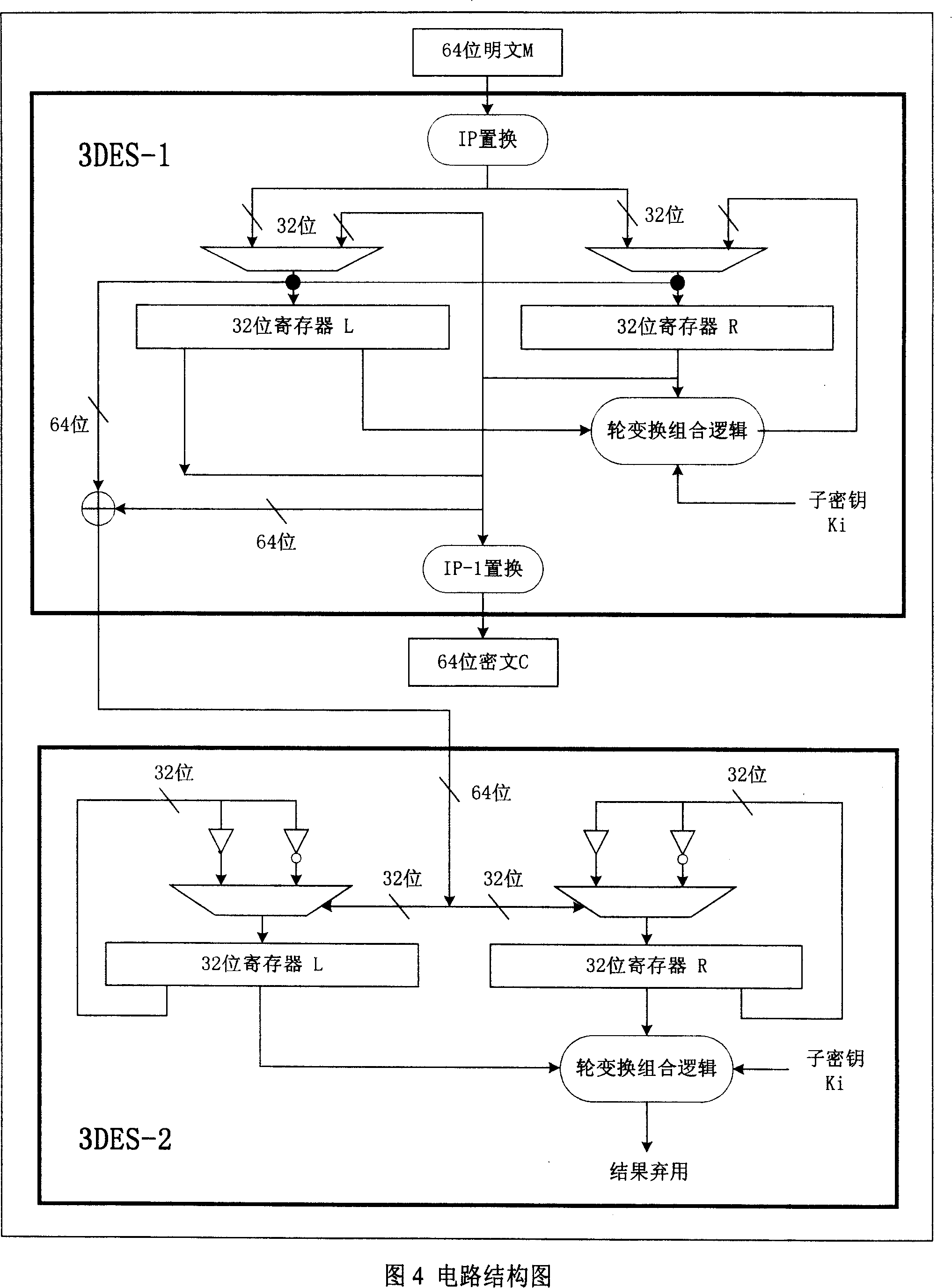
[0014] Fig. 1 is the general structural diagram of the present invention. The hardware 3DES-1 module realizes high-speed 3DES encryption operation. In addition, a digital power consumption compensation circuit module 3DES-2 is designed to compensate the power consumption of the 3DES-1 module. To perform power consumption compensation, the change of power consumption of 3DES-2 should be opposite to that of 3DES-1 module, so that the sum of the two is constant, and the situation of the key cannot be analyzed from the power consumption of the chip.
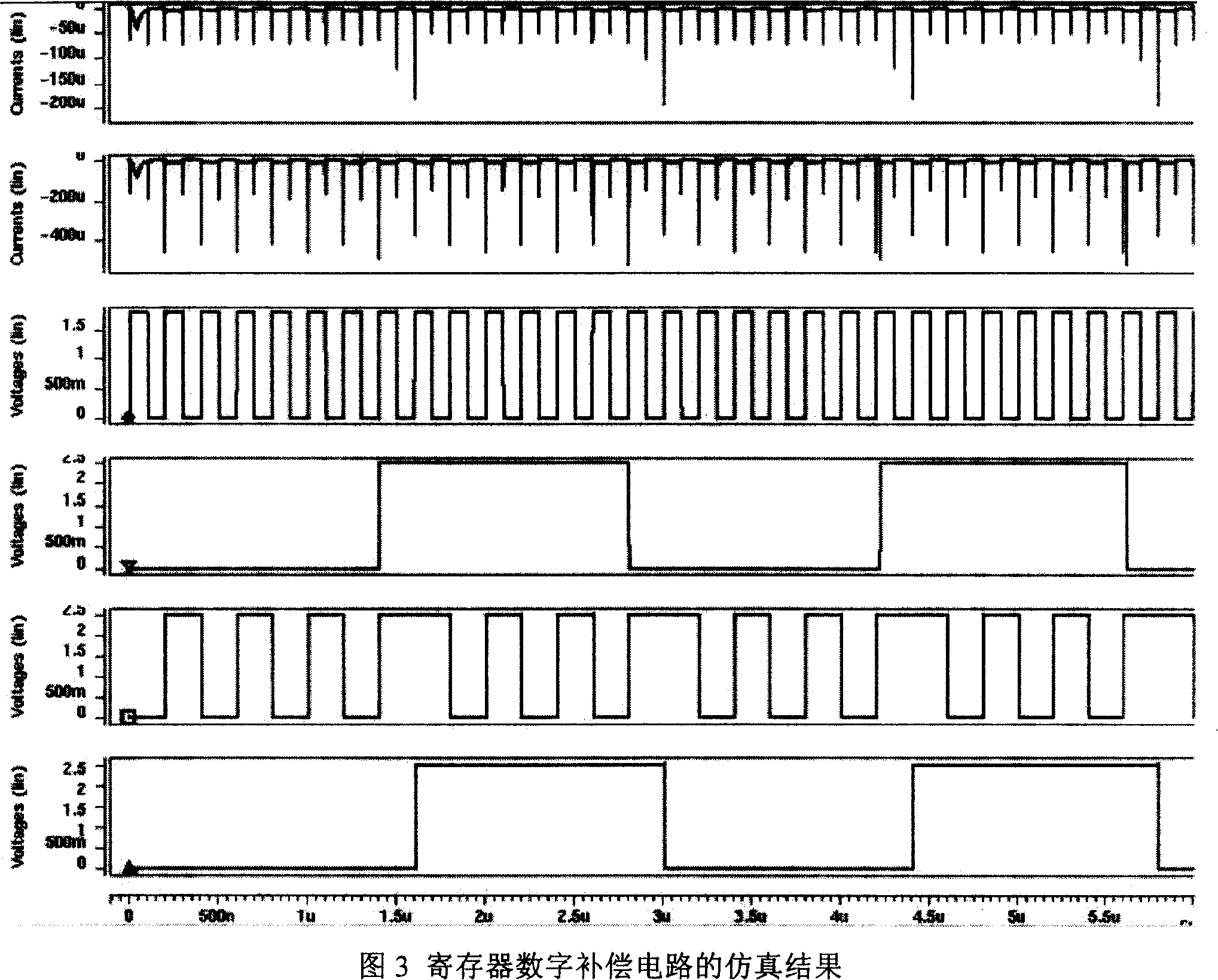
[0015] After analysis, the level of a certain node in the circuit has the following four situations: A.1->0; B.0->1; C.0->0; D.1->1. Among them, the power consumption of A and B flipping cases is basically the same, and the power consumption of C and D holding cases is basically the same, but the power consumption of flipping is much greater than the power consumption of holding. To compensate for the change in power consumption in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com