Anti-power-attack method and device for DES (Data Encrypt Standard) algorithm
An algorithm and energy technology, applied in the field of information security, can solve the problems of leaking password information, not considering the characteristics of multiple iterations of block ciphers, and being unable to effectively resist power consumption attacks, etc., to achieve the effect of resisting energy attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
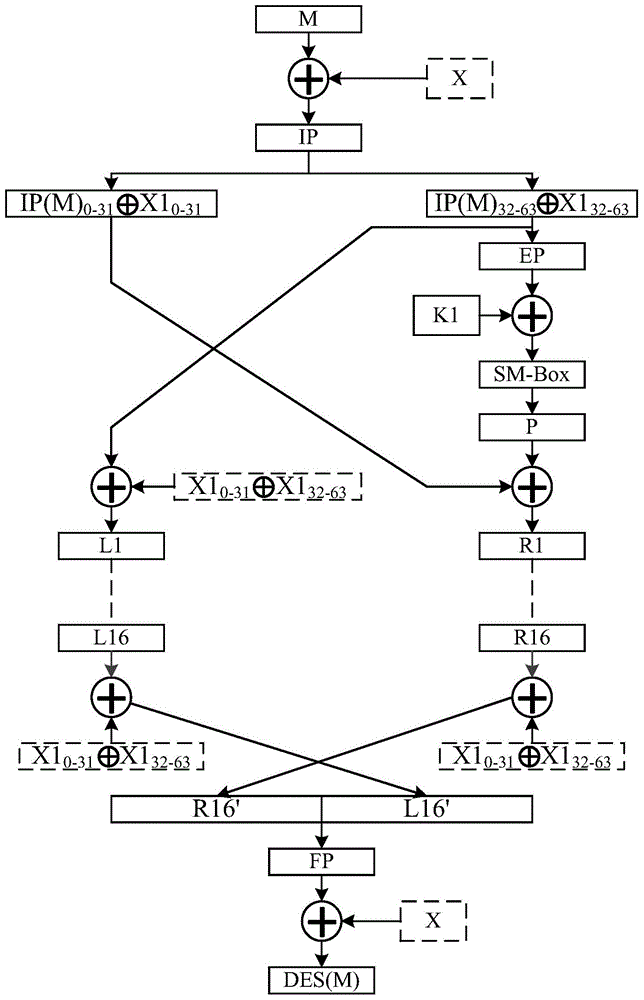
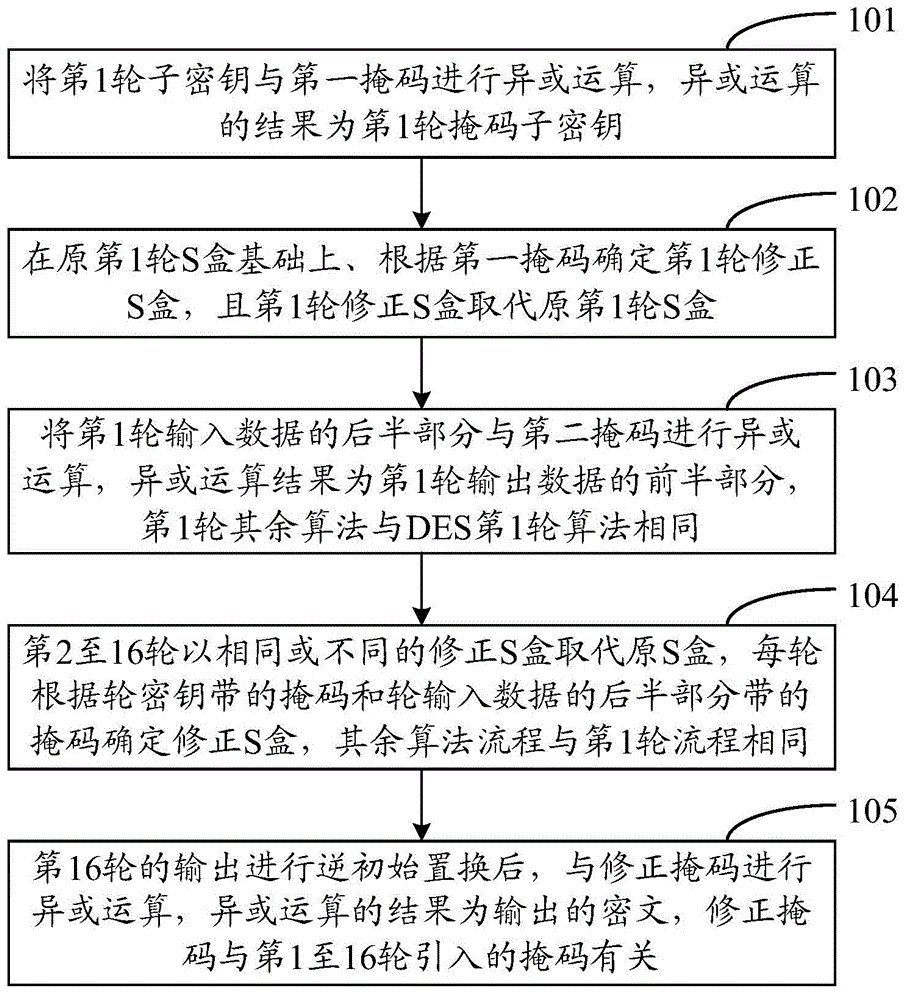
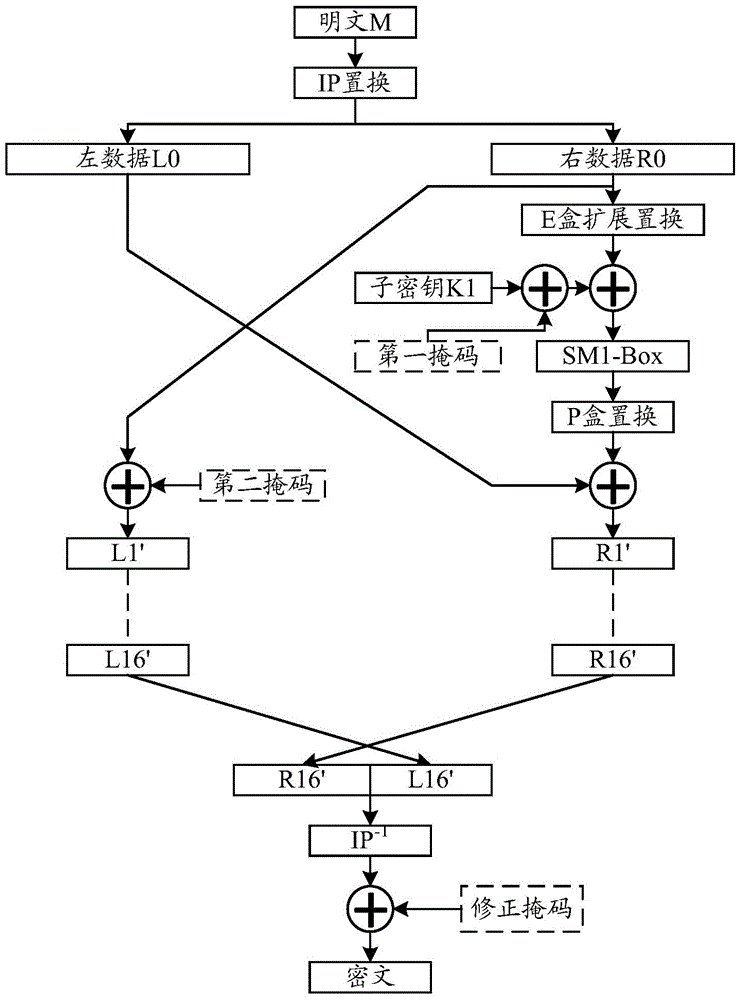
[0061] In Embodiment 1, different modified S-boxes are used in the first and second rounds of DES calculations, the same modified S-boxes are used in the 3rd to 14th rounds of DES calculations, and different modified S-boxes are used in the 15th and 16th rounds of DES calculations; The random number generator randomly generates three masks, which are 32bit mask X1, 32bit mask X2 and 32bit mask X3. In Embodiment 1, only the first round key is masked, and the rest of the subkeys are not masked. The specific algorithm flow is as follows.
[0062] The first round of DES algorithm in the first embodiment:
[0063] see figure 2 As shown, firstly, the E-box expansion replacement is performed on the 32-bit mask X1, and the 32-bit mask X1 is expanded into a 48-bit mask E(X1), and then the XOR operation is performed on the subkey K1 and the mask E(X1) , to get the submask key K1', namely
[0064] K 1 , = ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com