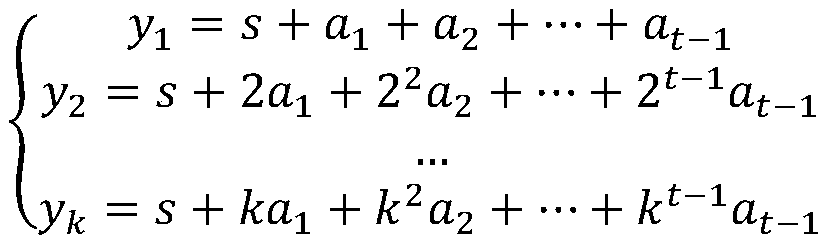Blockchain key sharing and dynamic updating method based on an elliptic curve
An elliptic curve and key sharing technology, which is applied to the public key and key distribution of secure communication, can solve the problems of node master key leakage, and does not support subkey dynamic addition and deletion of master keys, etc., to ensure security, The effect of enhancing trust and strengthening the degree of fit
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0043] The logic that each step of the present invention executes is as follows:
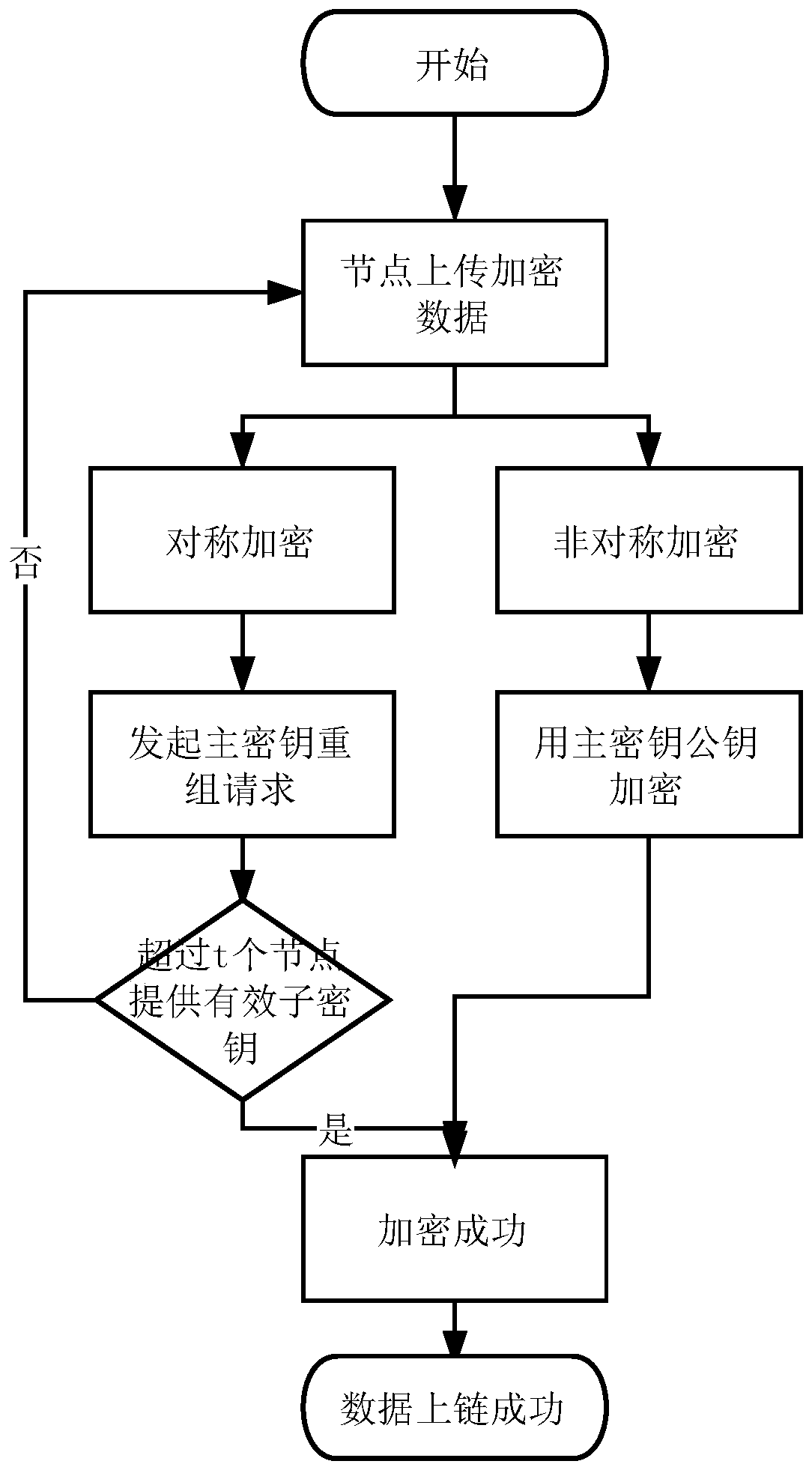
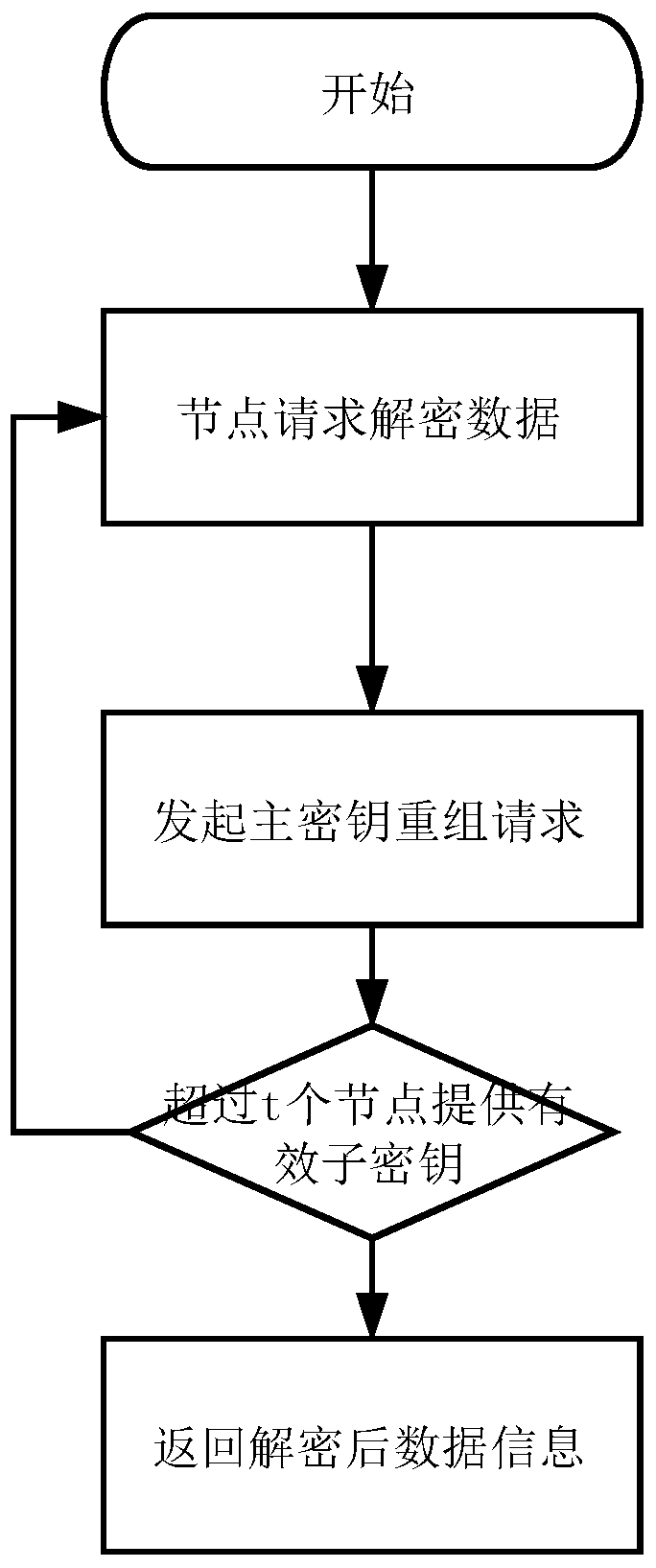
[0044] Node key initialization. When the blockchain runs for the first time, the key initialization contract method is executed in the blockchain environment to initialize the master key and subkey. The contract first randomly generates a master key S, and selects an elliptic curve equation E(a, b) on the prime number field GF, namely: y 2 =x 3 +ax+b, q>3, where 4a 3 -27b 2 ≠0,. The program randomly selects n different parameters on the elliptic curve, denoted as k 1 , k 2 ,…k n As the key of the child node, it is distributed to each node N through a secure channel i . Then, the program selects a base point G on the elliptic curve. Next, the program selects a polynomial of degree t-1 where f(0)=a 0 =S. For j = 1, 2, ... t-1, calculate A j =a j G(mod n), for i=1, 2, ... n, calculate D i =(i,y i )-k i G, and F i =H(k i G), where H(x) is a hash operation method. Then expose E,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com