Elliptic curve cryptosystem based on identity
A technology of identification and encryption, applied to the public key and key distribution of secure communication, can solve the problems of increasing system security, reliability, lack of IBC encryption product certification standards, and not supporting IBC, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0135] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
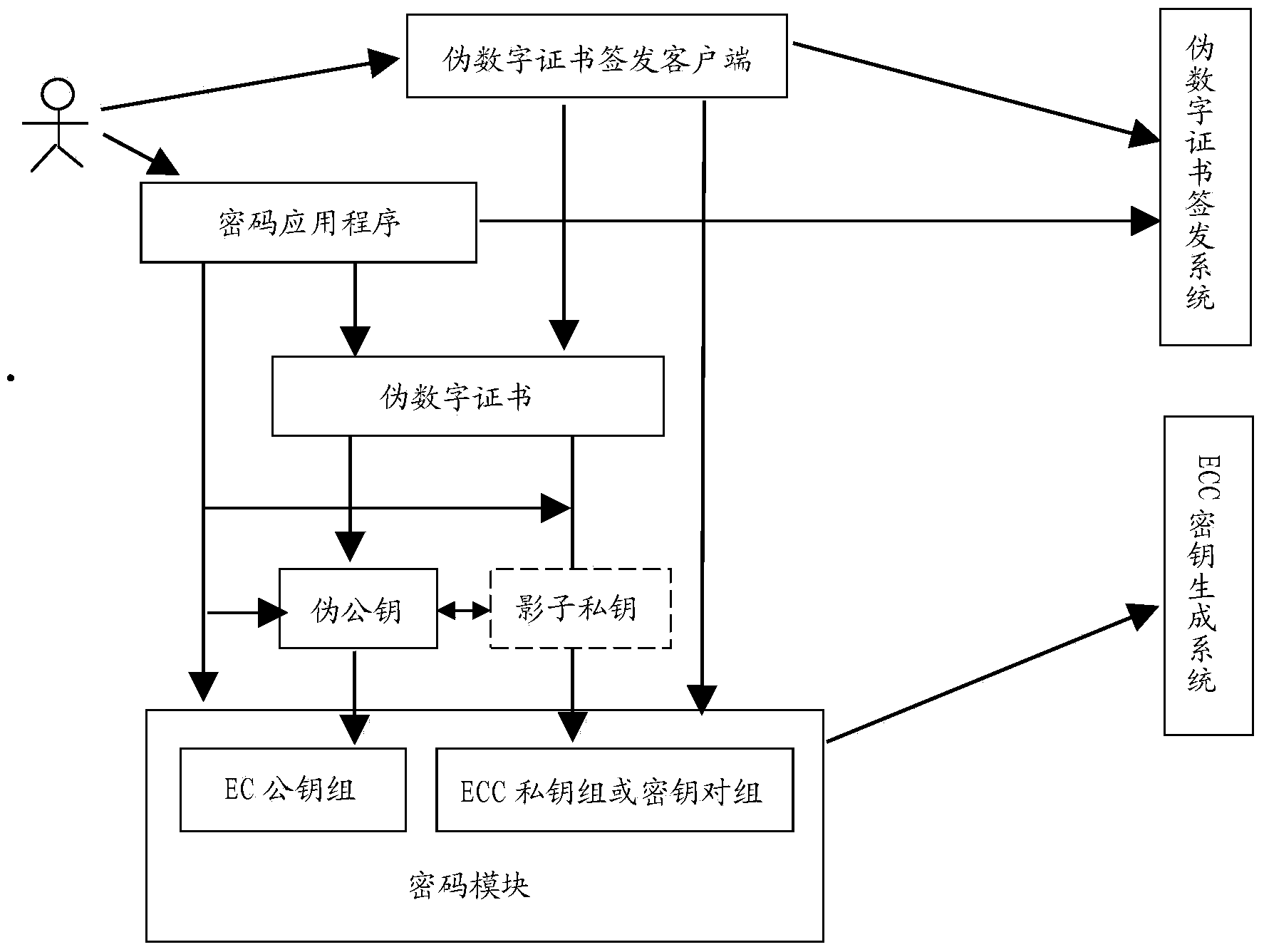
[0136] Adopt the structural block diagram of cryptographic system of the present invention as figure 1 shown.
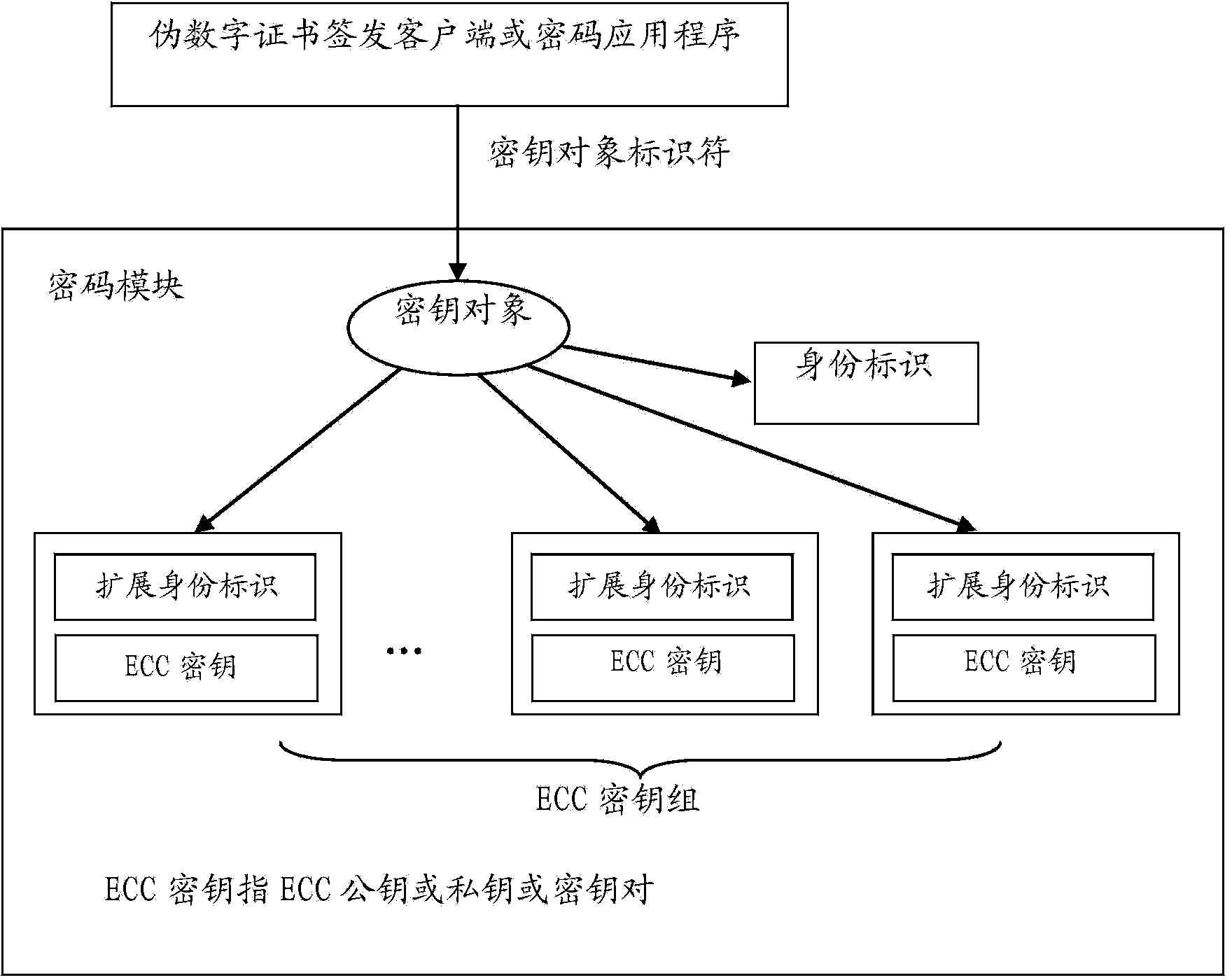
[0137] The implementation of the present invention first needs to determine the implementation scheme of the pseudo-public key. The pseudo-public key of the present invention can be implemented based on the RSA public key (pseudo-RSA public key), can also be implemented based on the ECC public key (pseudo-ECC public key), or can be implemented based on the public key of other public key cryptographic algorithms. Regardless of whether the RSA public key is used or the ECC public key is used (or the public key implementation of other algorithms), you can refer to the applicant of the patent application for this invention in his patent "A New Public Key Encryption Algorithm Based on a Pseudo-RSA Key" The implementation of the pseudo RSA key (fo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com