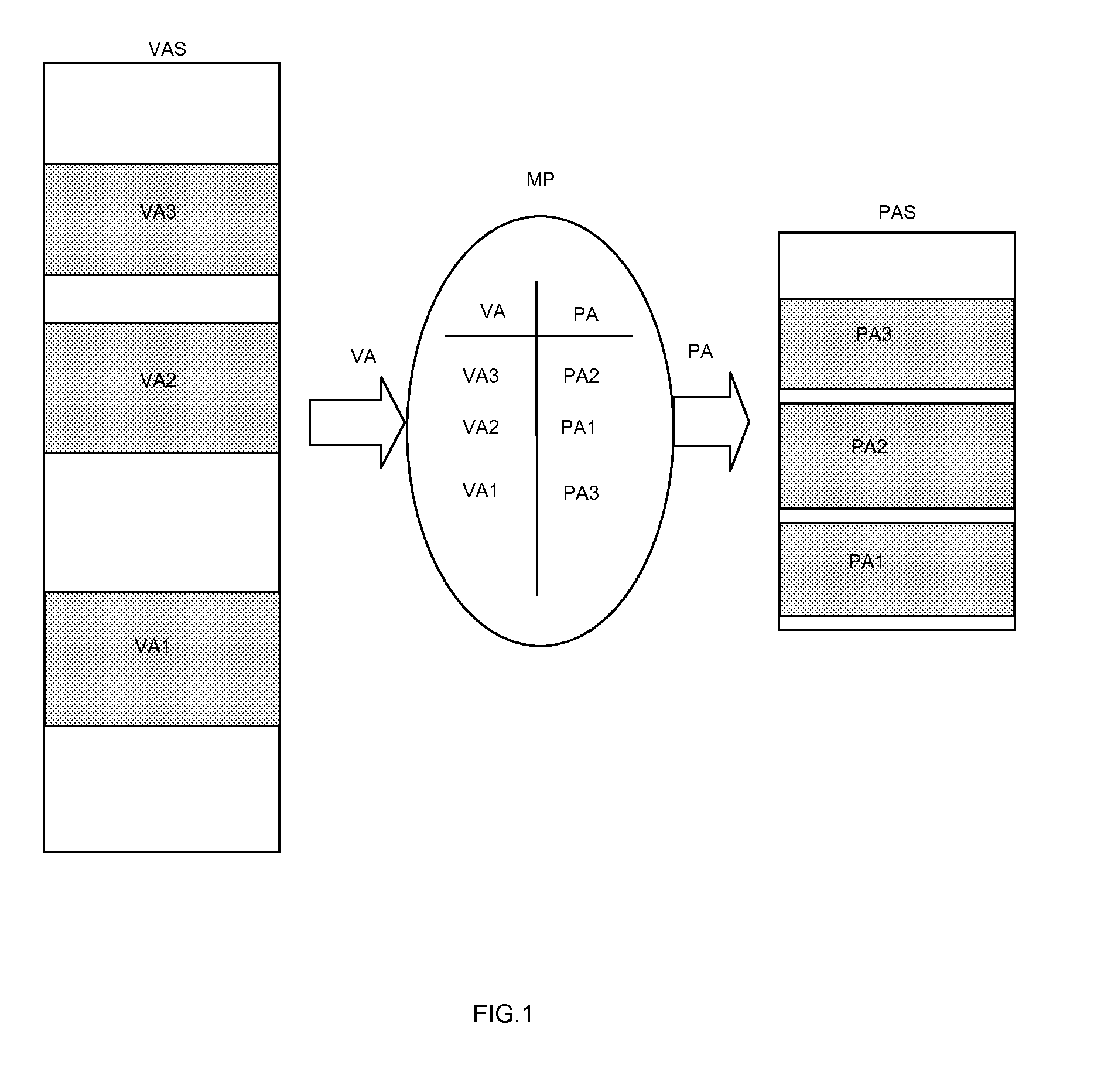
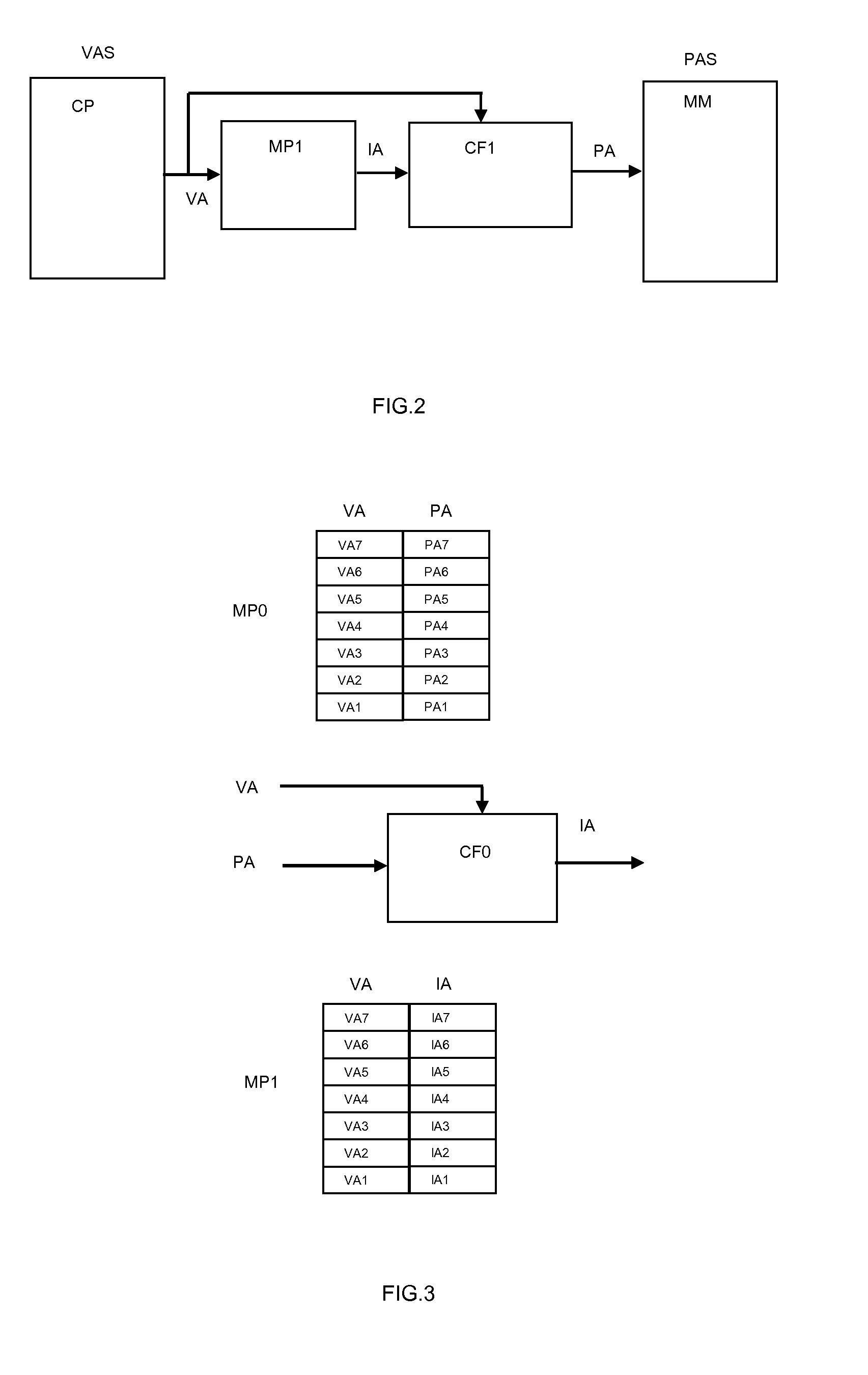
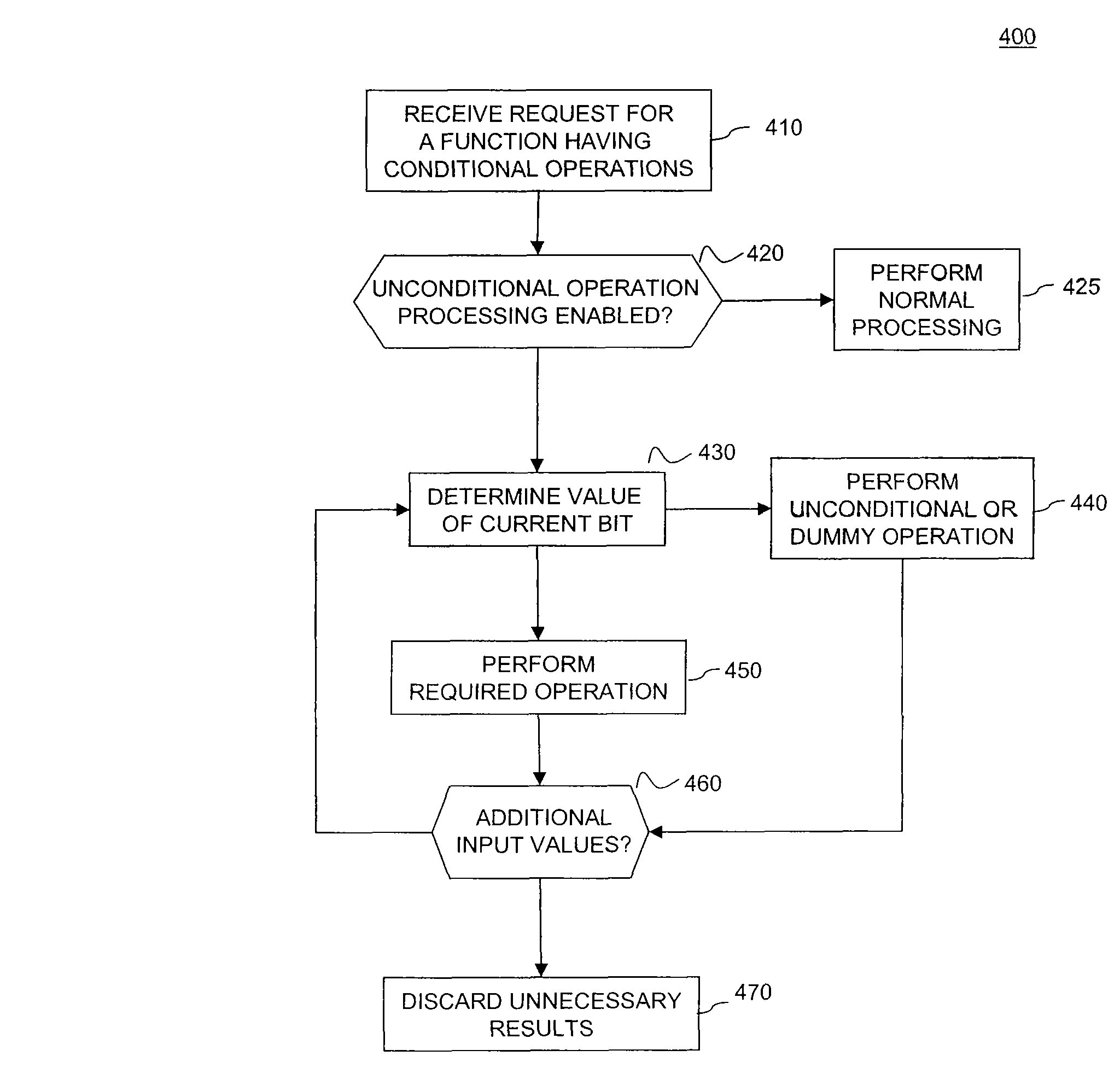
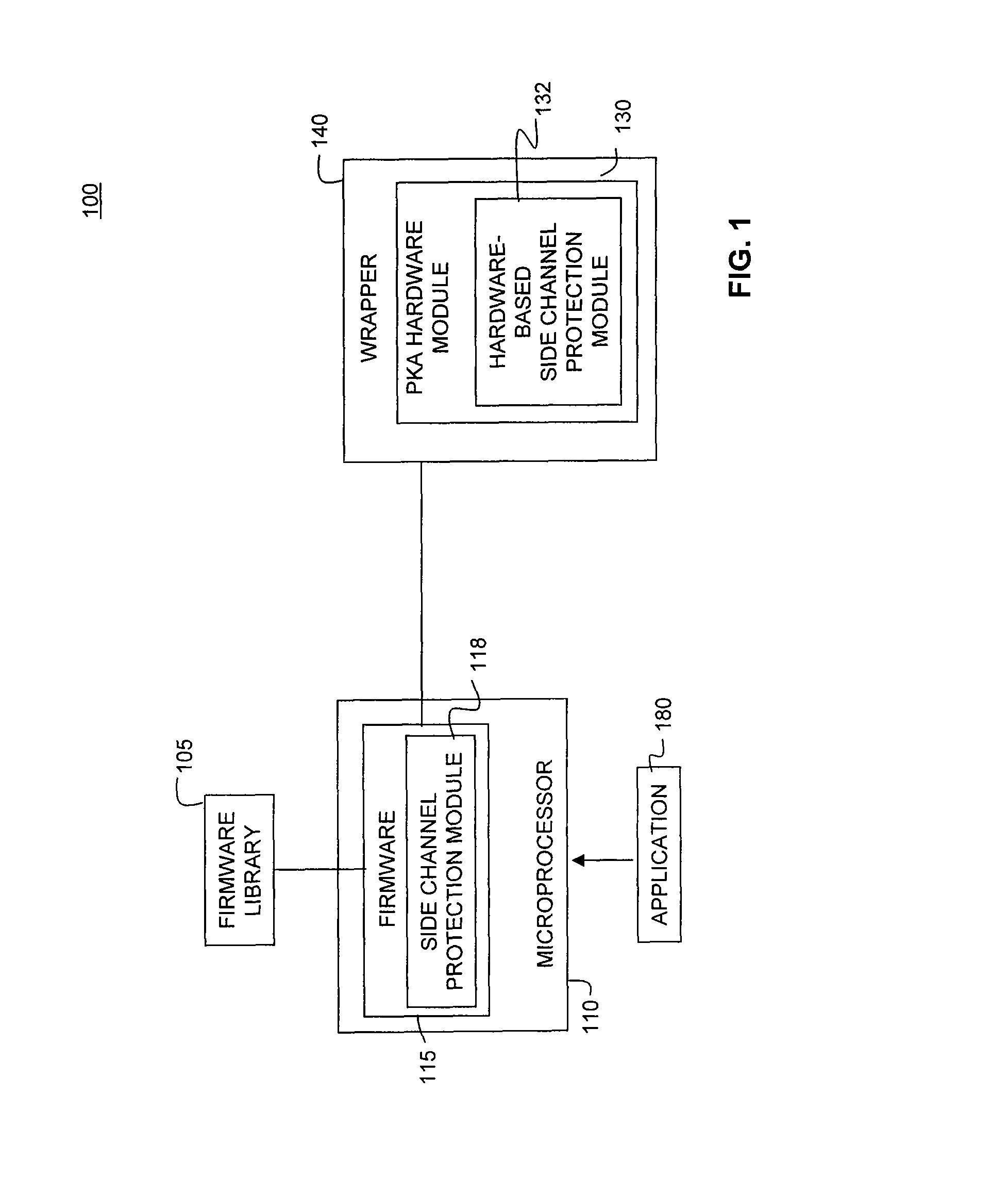
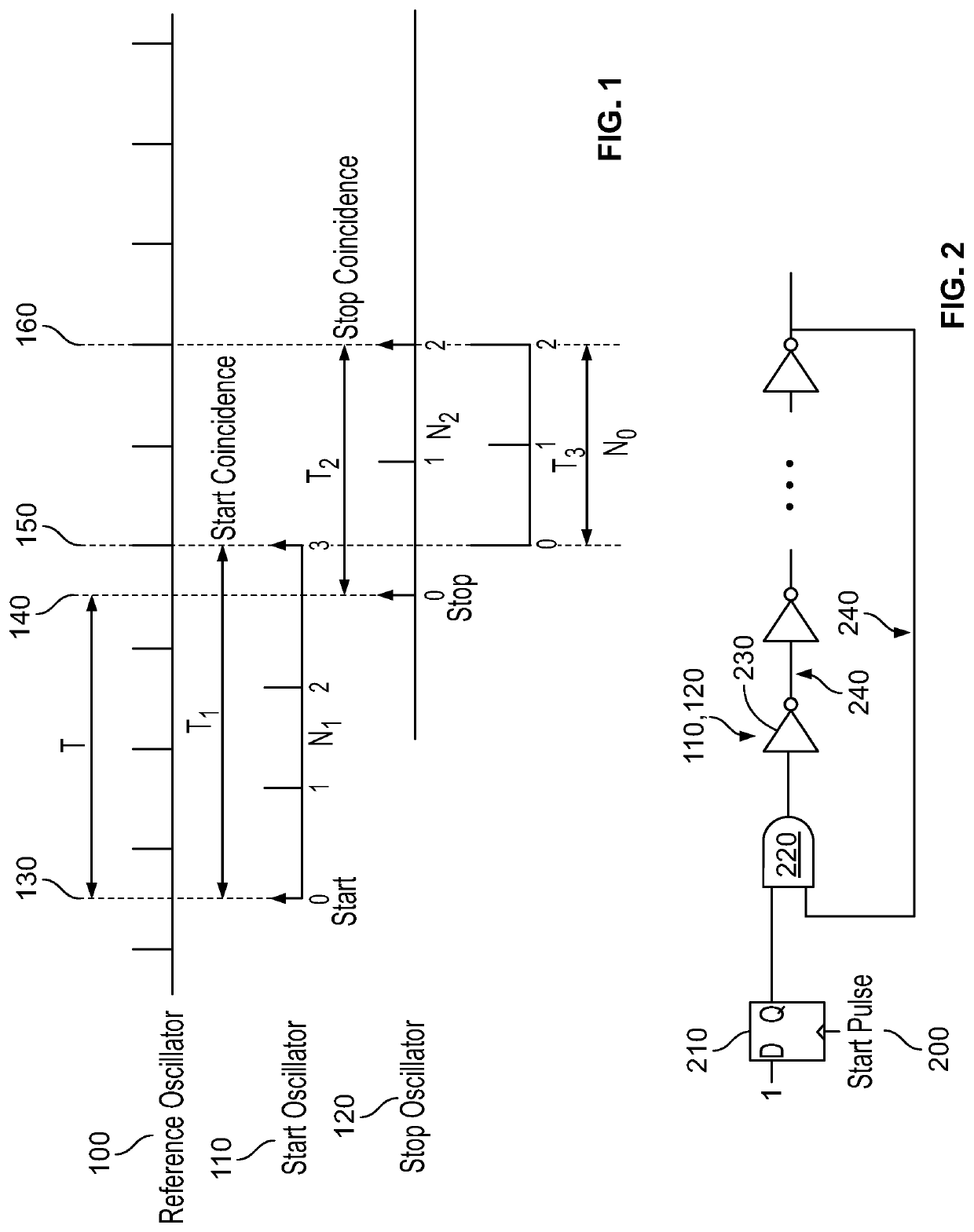
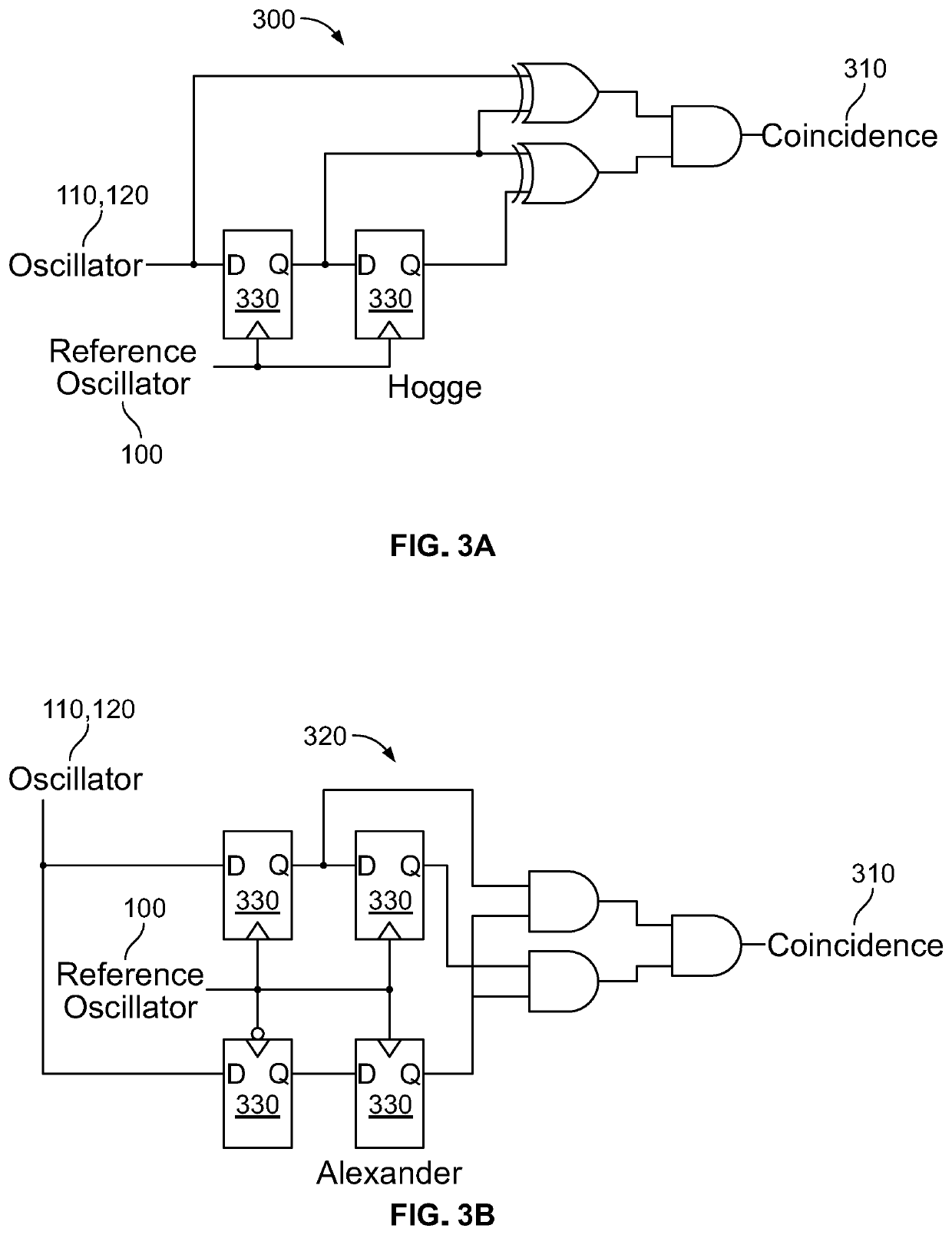
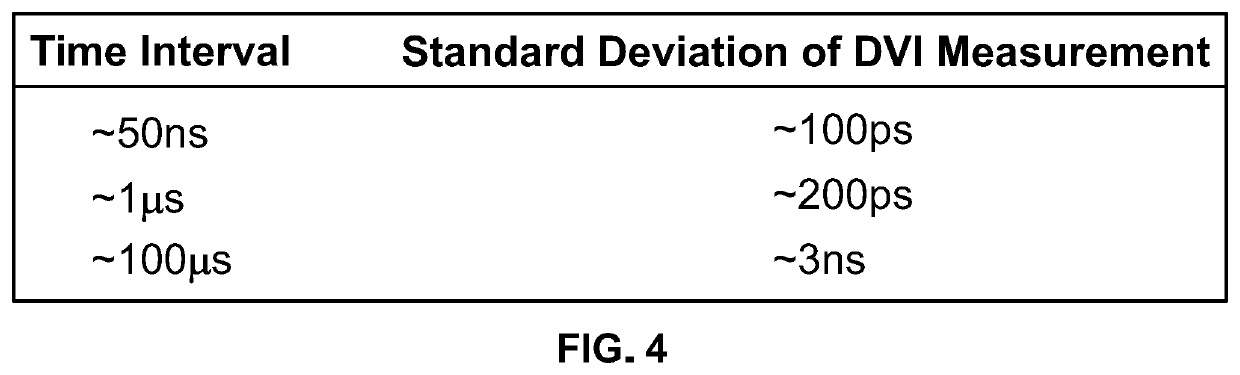
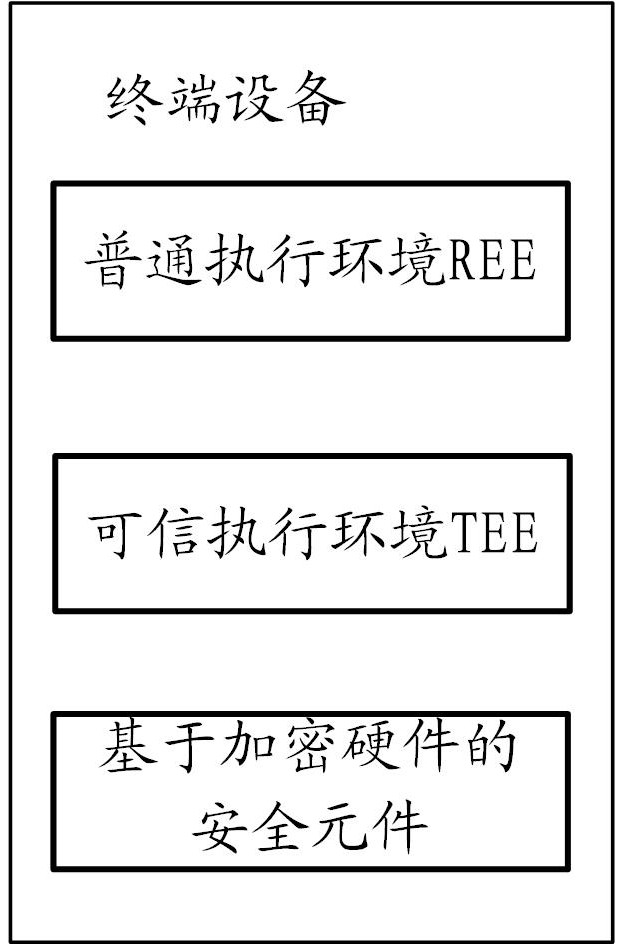
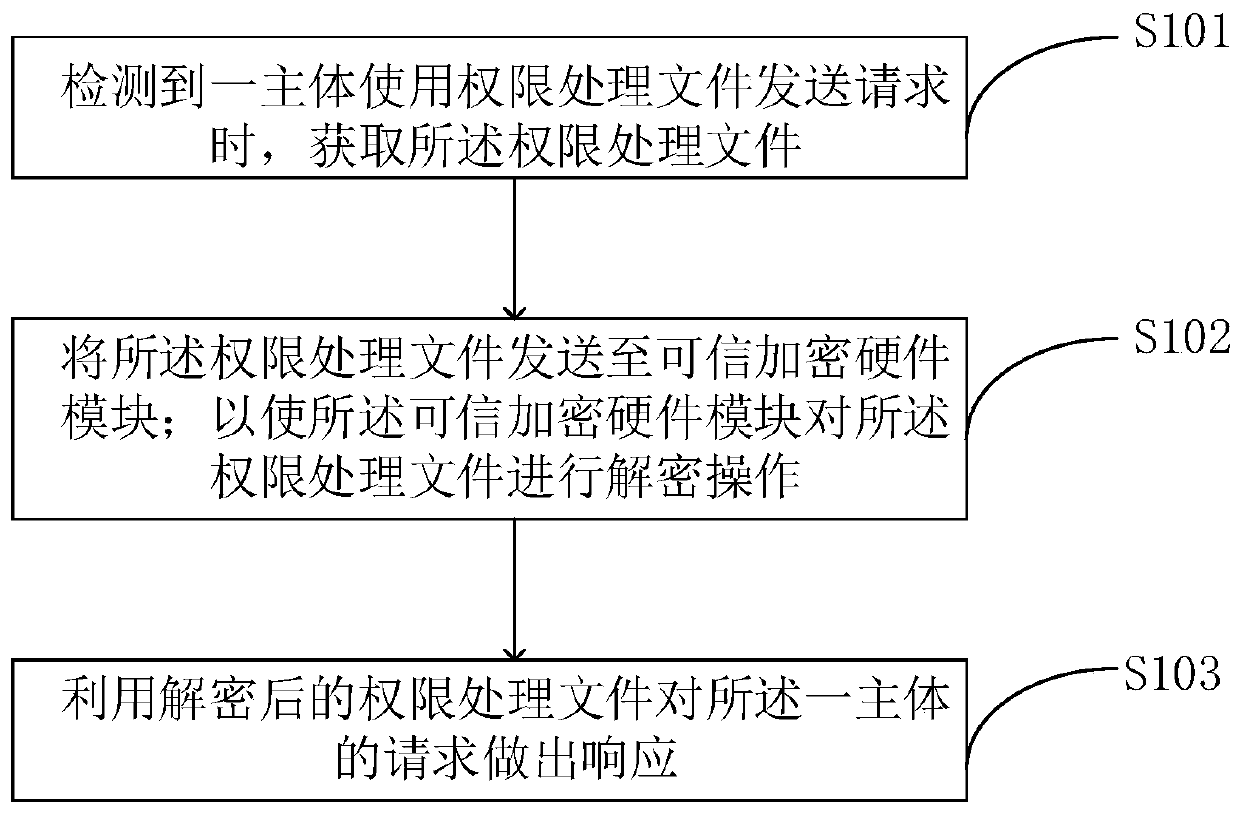
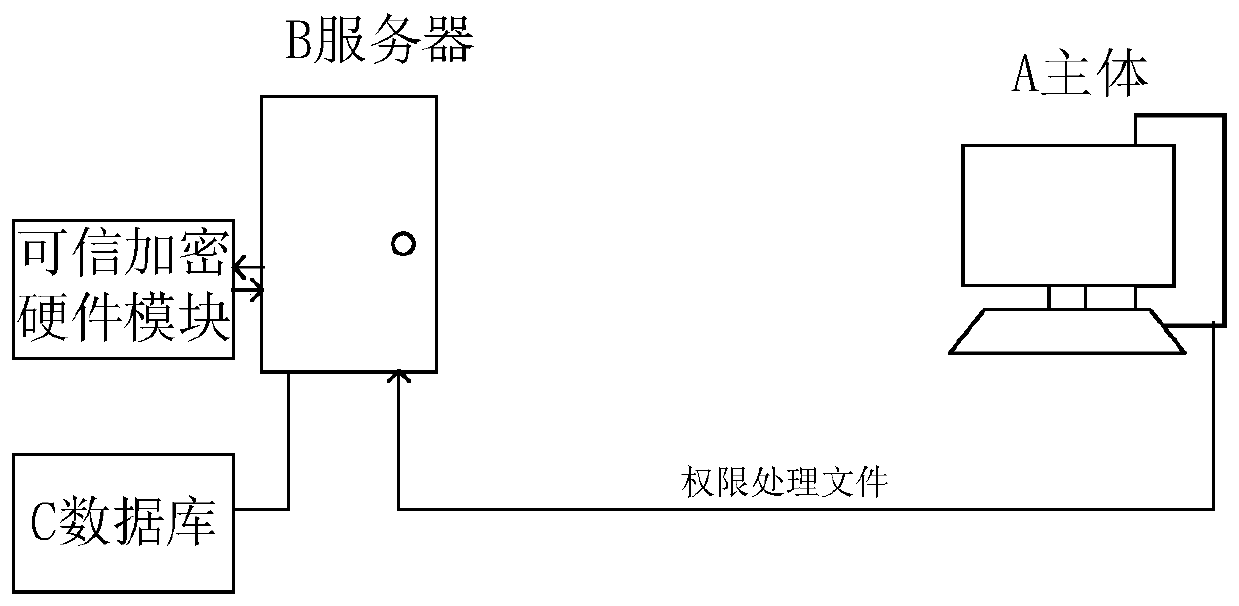
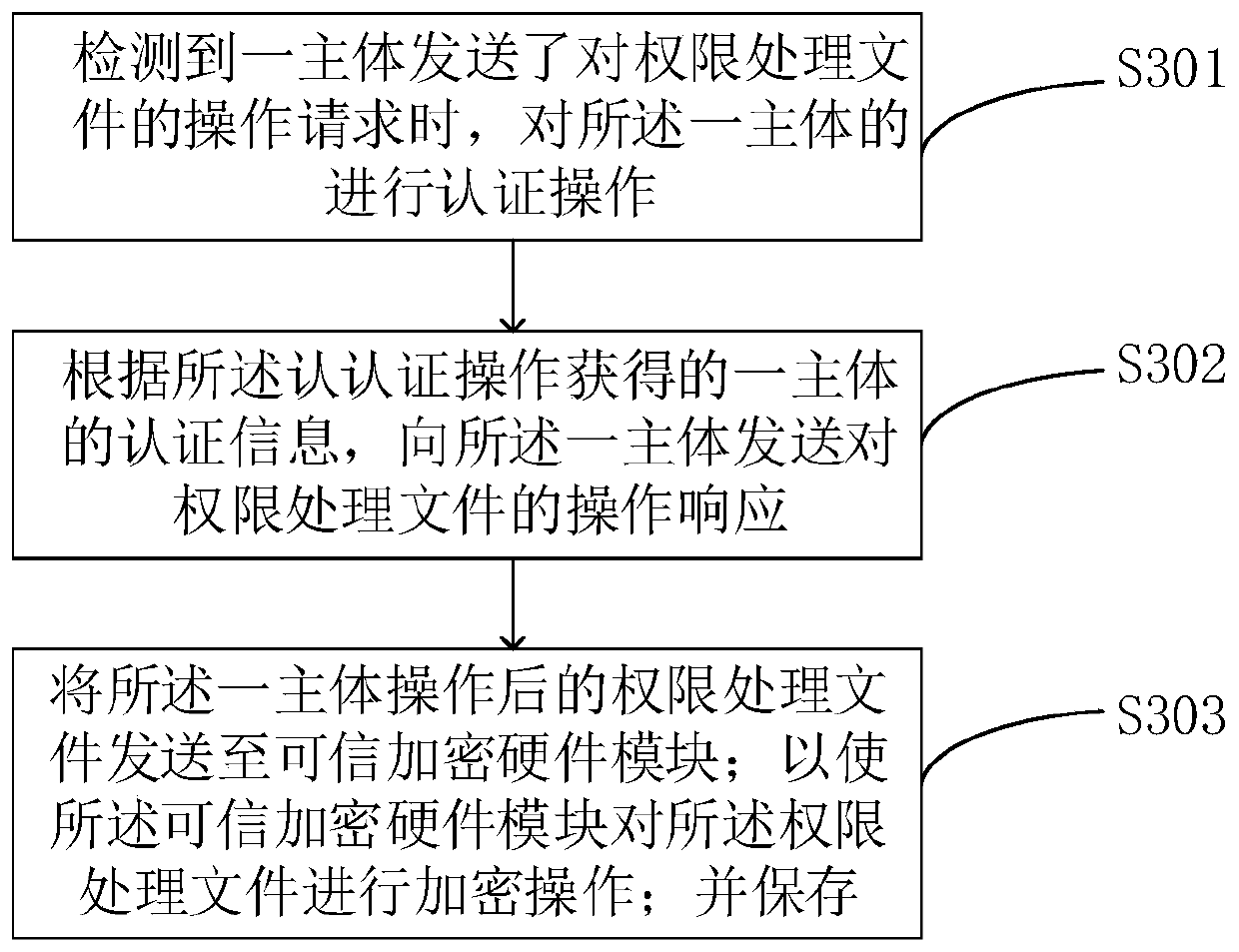
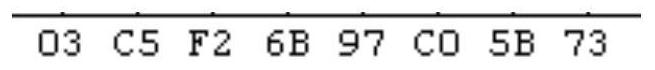Patents
Literature
40 results about "Cryptographic hardware" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Hardware-Bonded Credential Manager Method and System
ActiveUS20090259838A1Improve authentication methodReduce chanceSecuring communicationThe InternetUser authentication
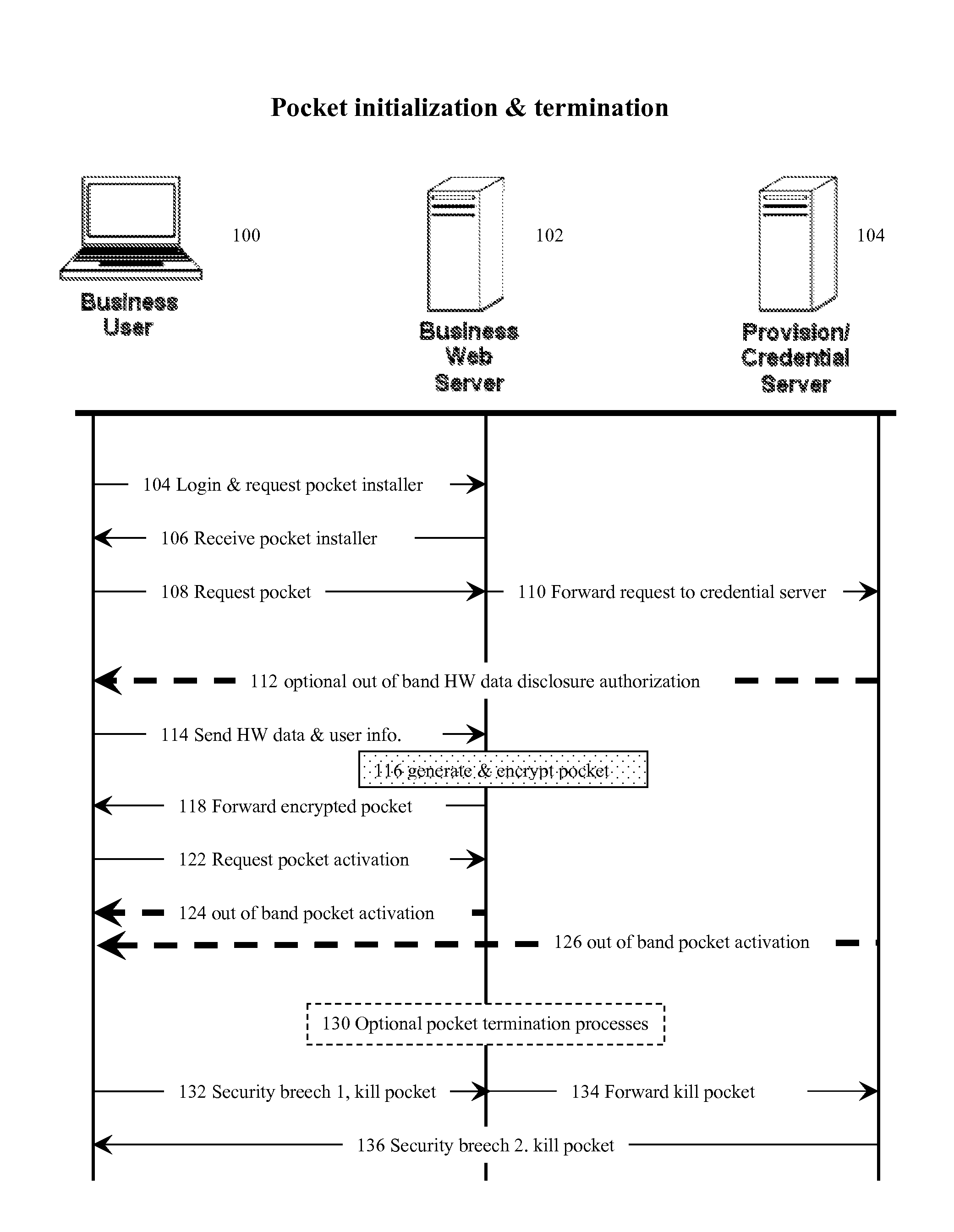
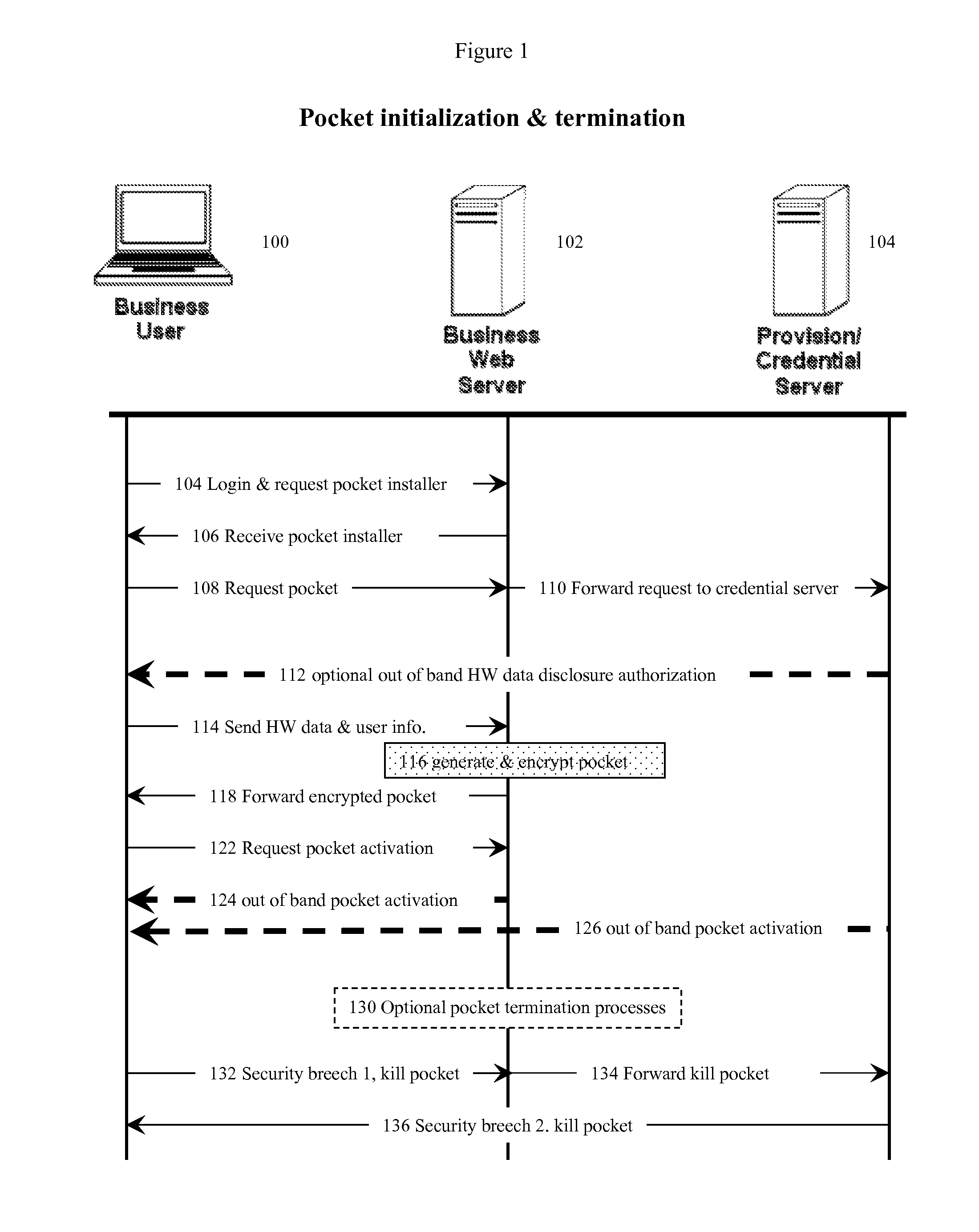
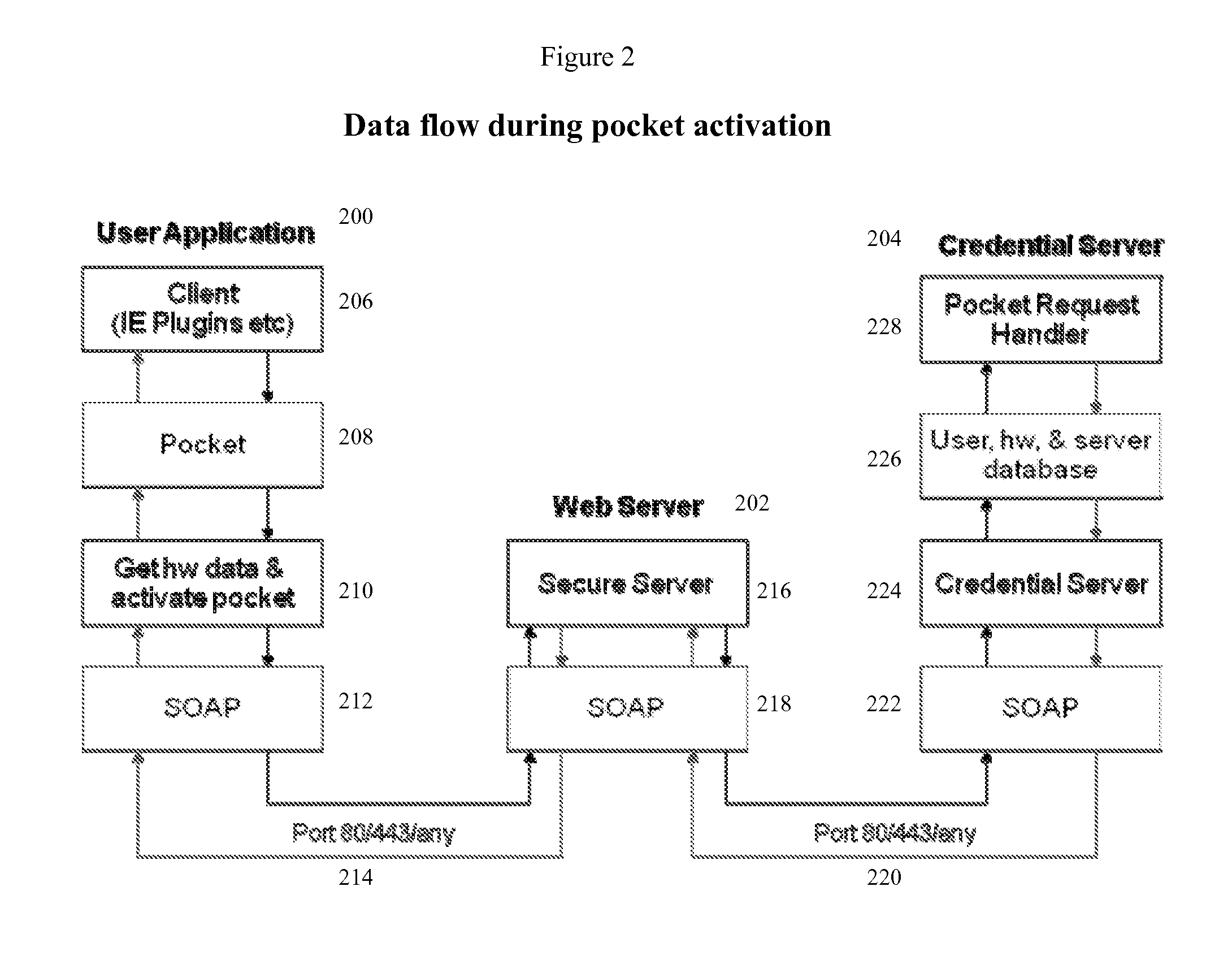
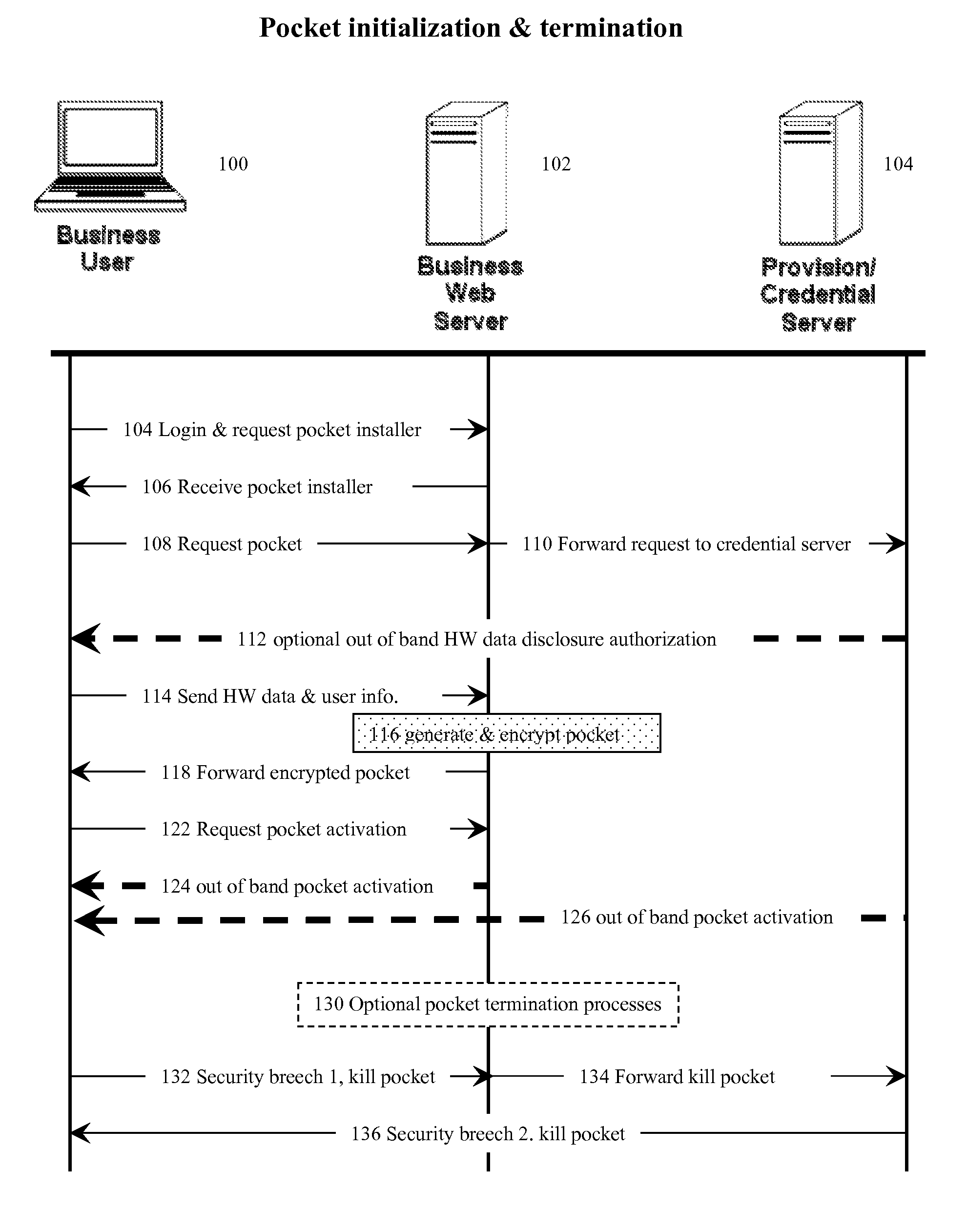
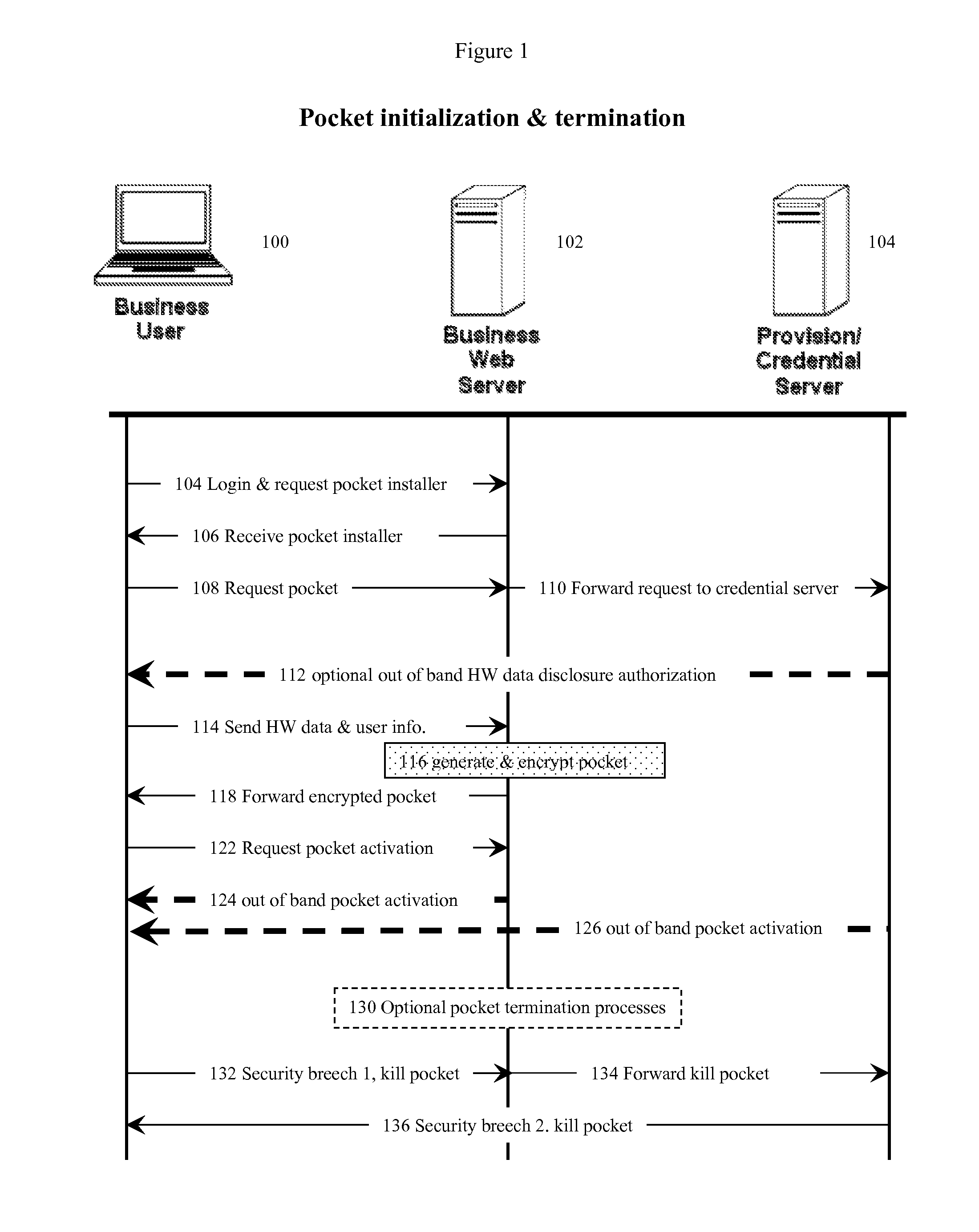
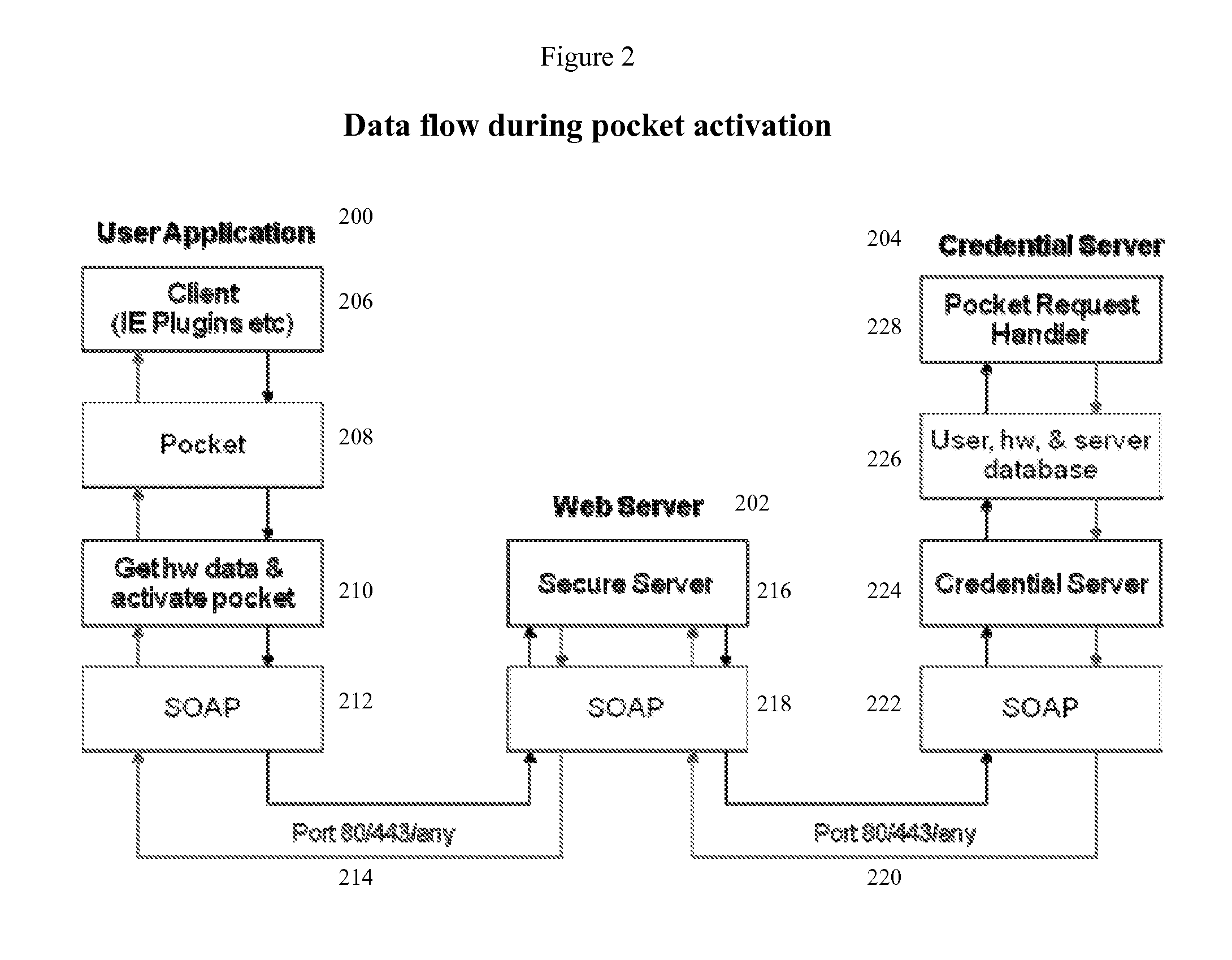
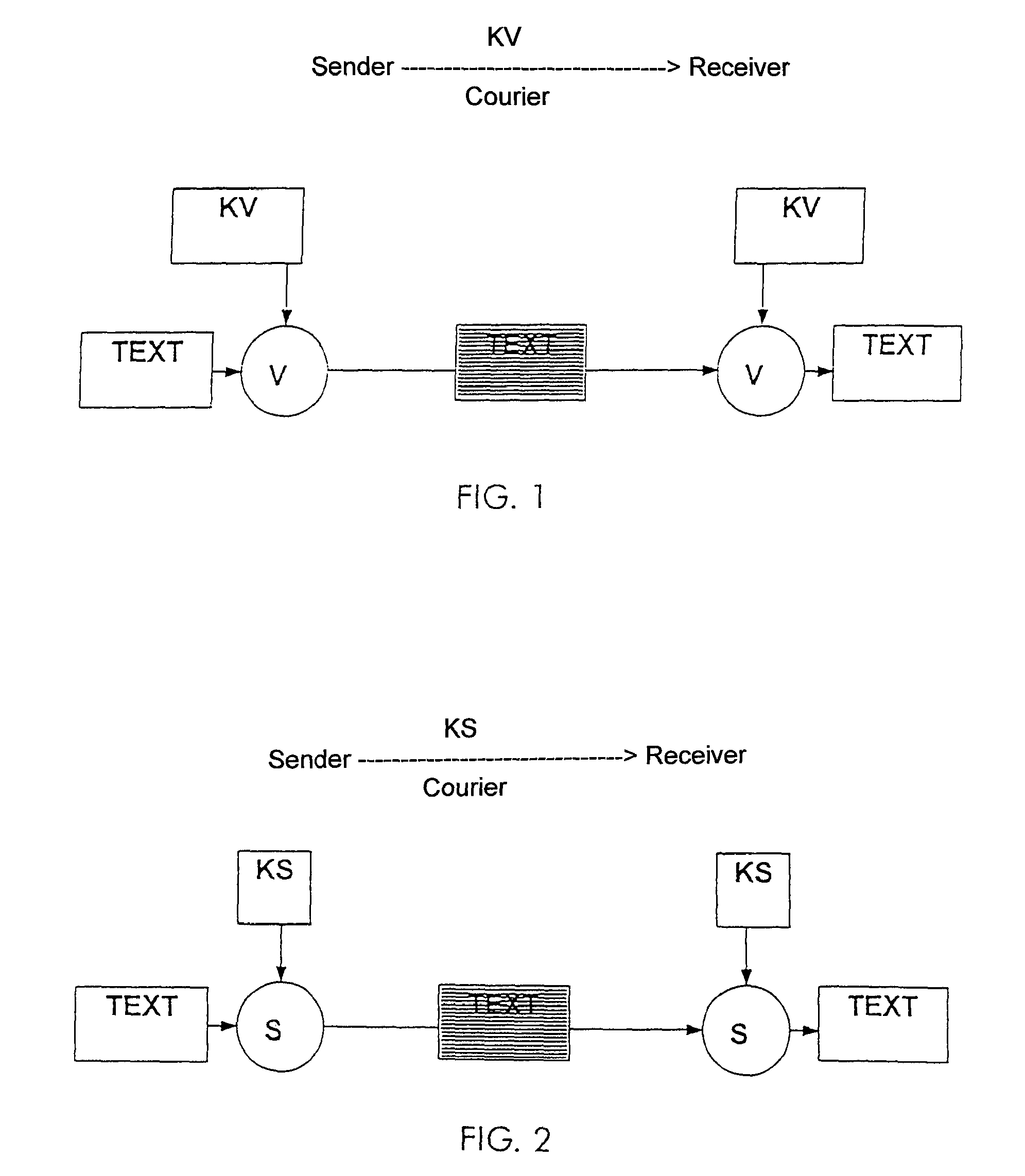
An internet data exchange authentication method that can provide much of the user authentication assurance and capability of dedicated computer security cryptographic hardware, without requiring that the user actually have such hardware. This method allows users with computerized devices to communicate securely with secure servers by creating customized challenge-response authentication objects (pockets) where both the challenge and the response is based partially on the hardware identity of the user's computerized device, and partially on a secret (such as a random number) known only by the secure server. The secure server receives the device's hardware identity, generates the secret, creates the pocket, encrypts the pocket, and sends the encrypted pocket back to the user's device. The secure server, or a third trusted credential server, then sends the decryption key for the encrypted pocket back to the user using a different, “out of band” communications modality, thus reducing the chances of interception.
Owner:AUTHENEX
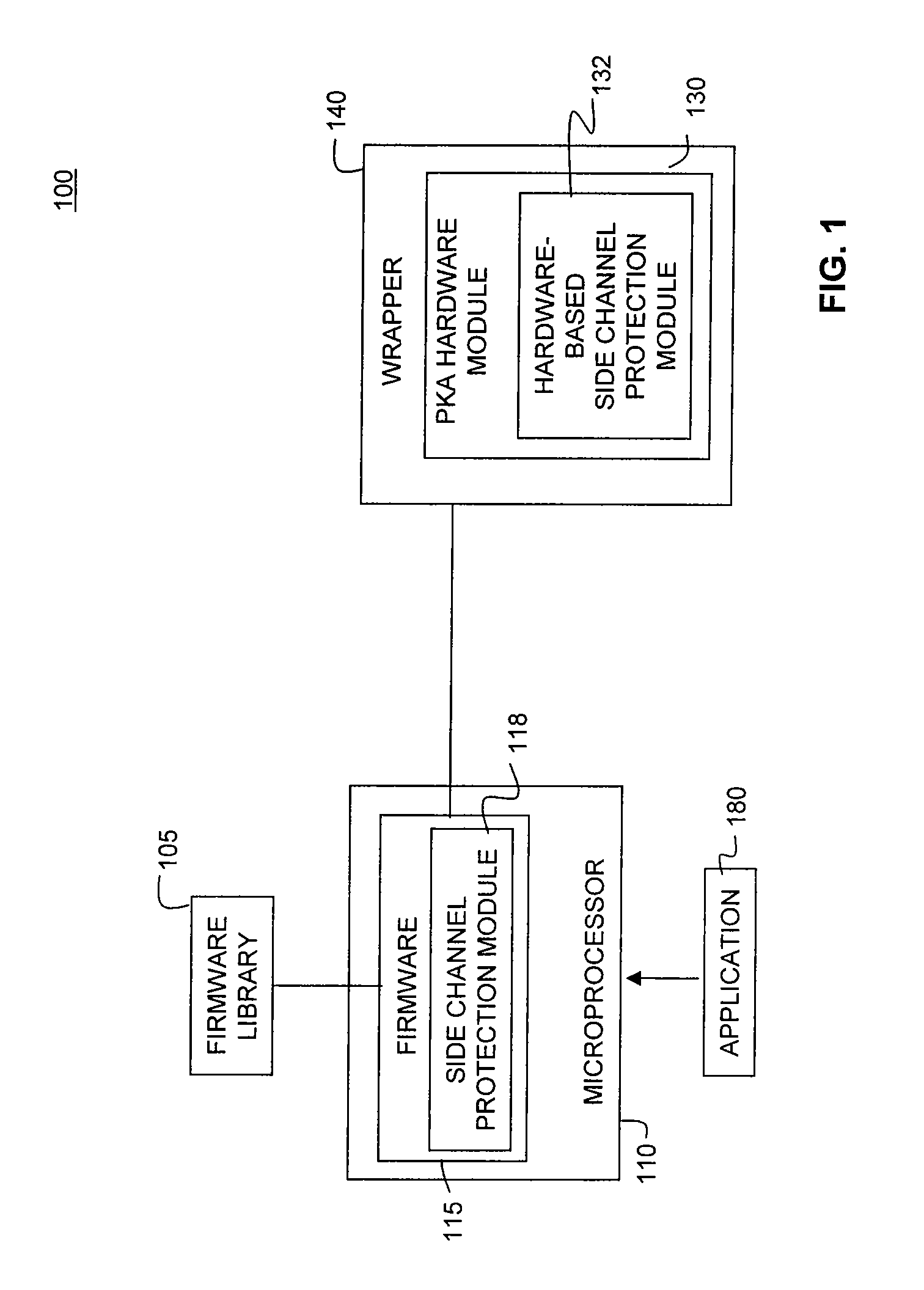
System and Methods for Side-Channel Attack Prevention
InactiveUS20090010424A1Internal/peripheral component protectionSecret communicationProcessor registerCryptosystem
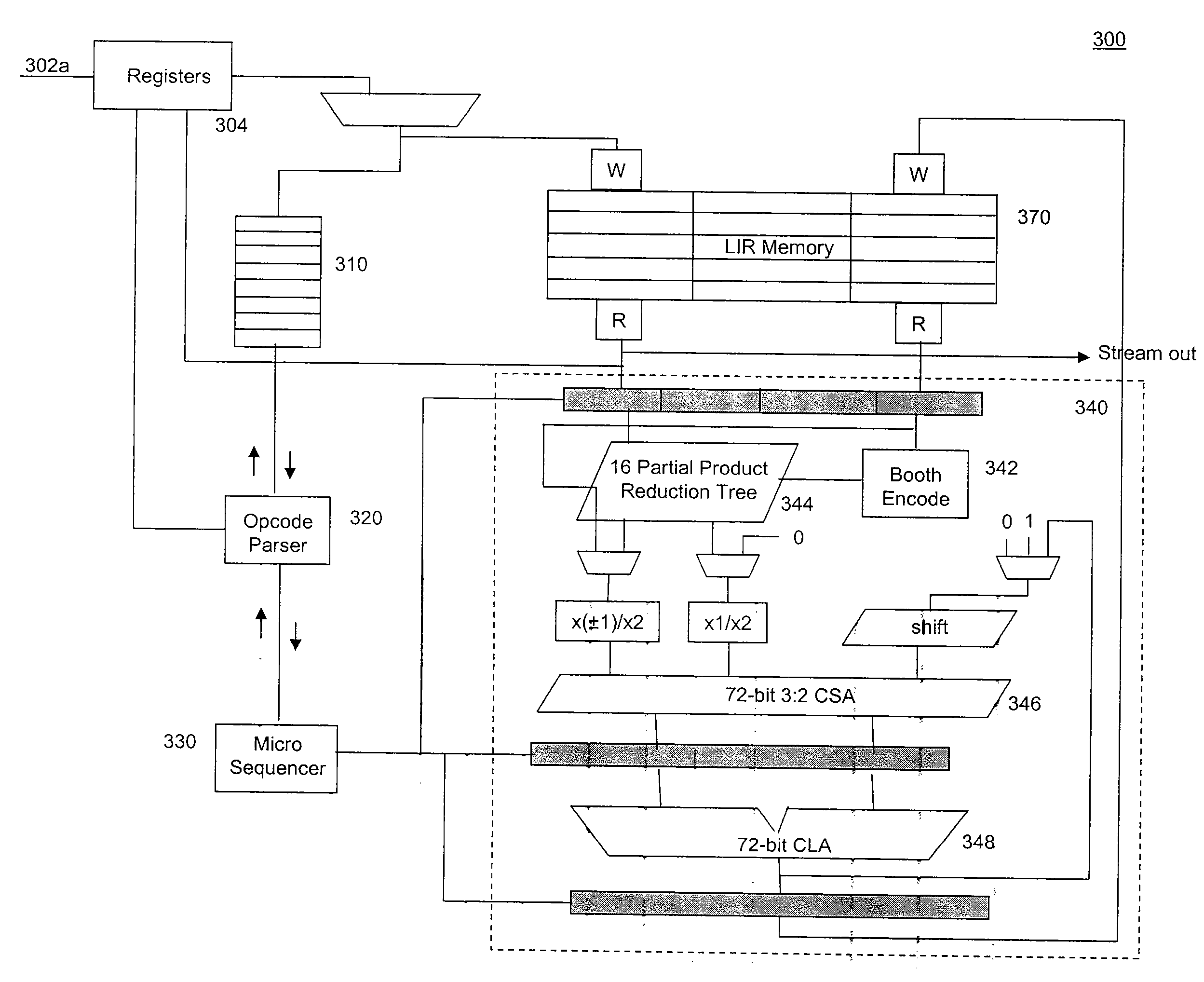
A side channel attack utilizes information gained from the physical implementation of a cryptosystem. Software and hardware-based systems and methods for preventing side channel attacks are presented. Cryptographic hardware may introduce dummy operations to compensate for conditional math operations in certain functions such as modular exponentiation. Cryptographic hardware may also introduce random stalls of the data path to introduce alterations in the power profile for the operation. A cryptographic function may be mapped to a micro code sequence having a plurality of instructions. Firmware in the cryptosystem may alter the micro code sequence by altering the order of instructions, add dummy operations in the micro code sequence, break the micro code sequence into multiple sub micro code sequences and / or change the register location for source and destination operands used in the sequence. These alterations are designed to randomly change the timing and power profile of the requested function.
Owner:AVAGO TECH INT SALES PTE LTD
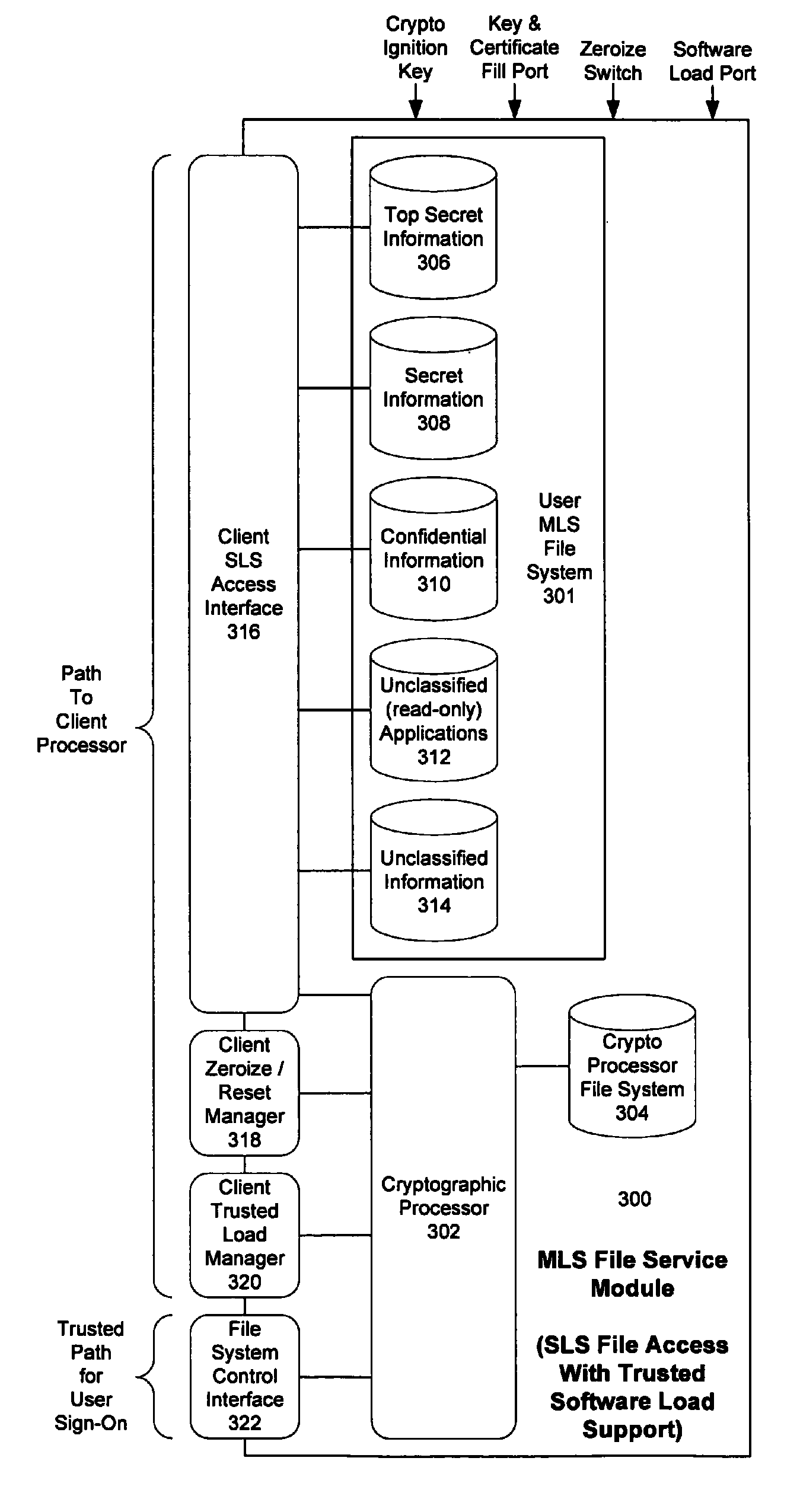
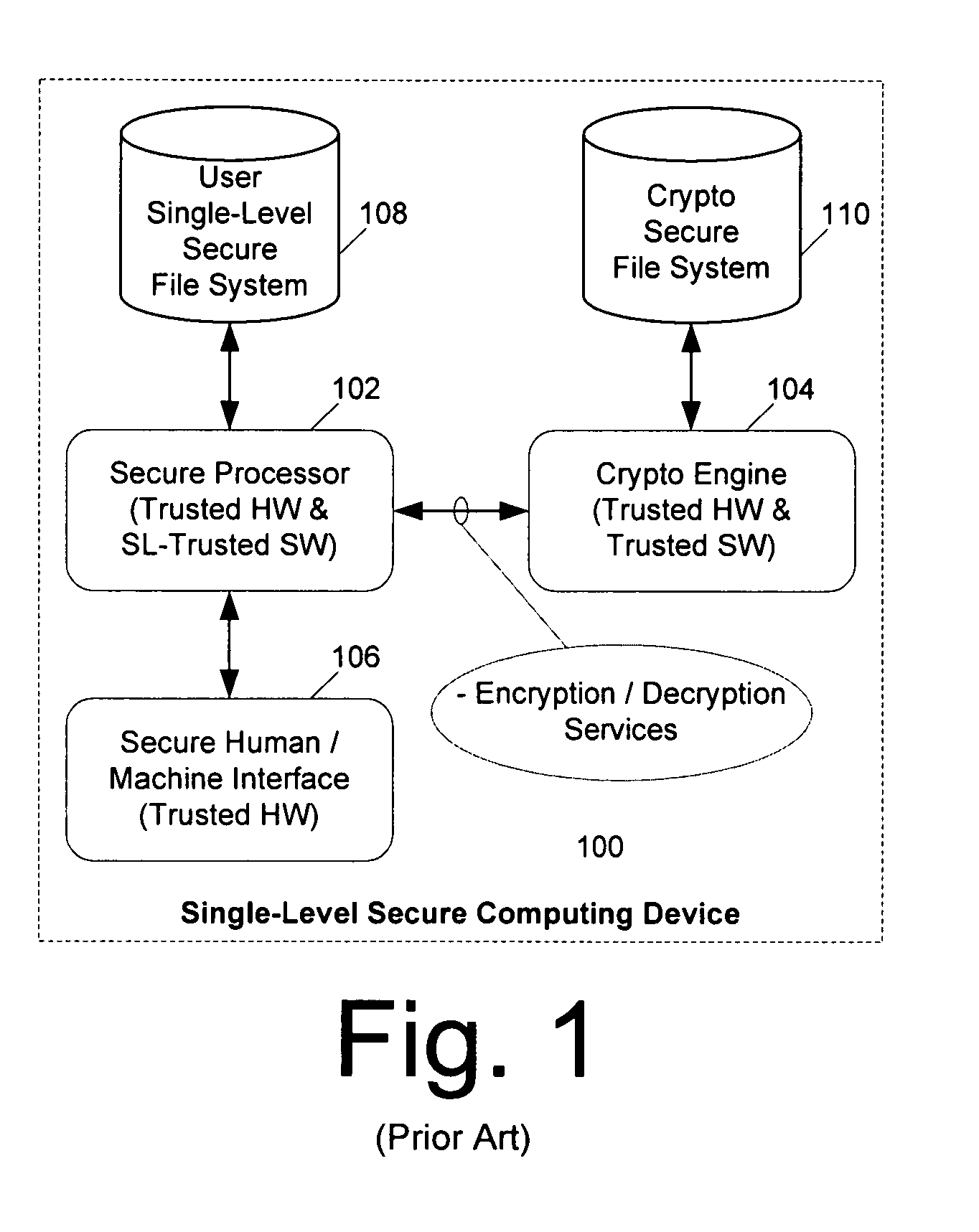
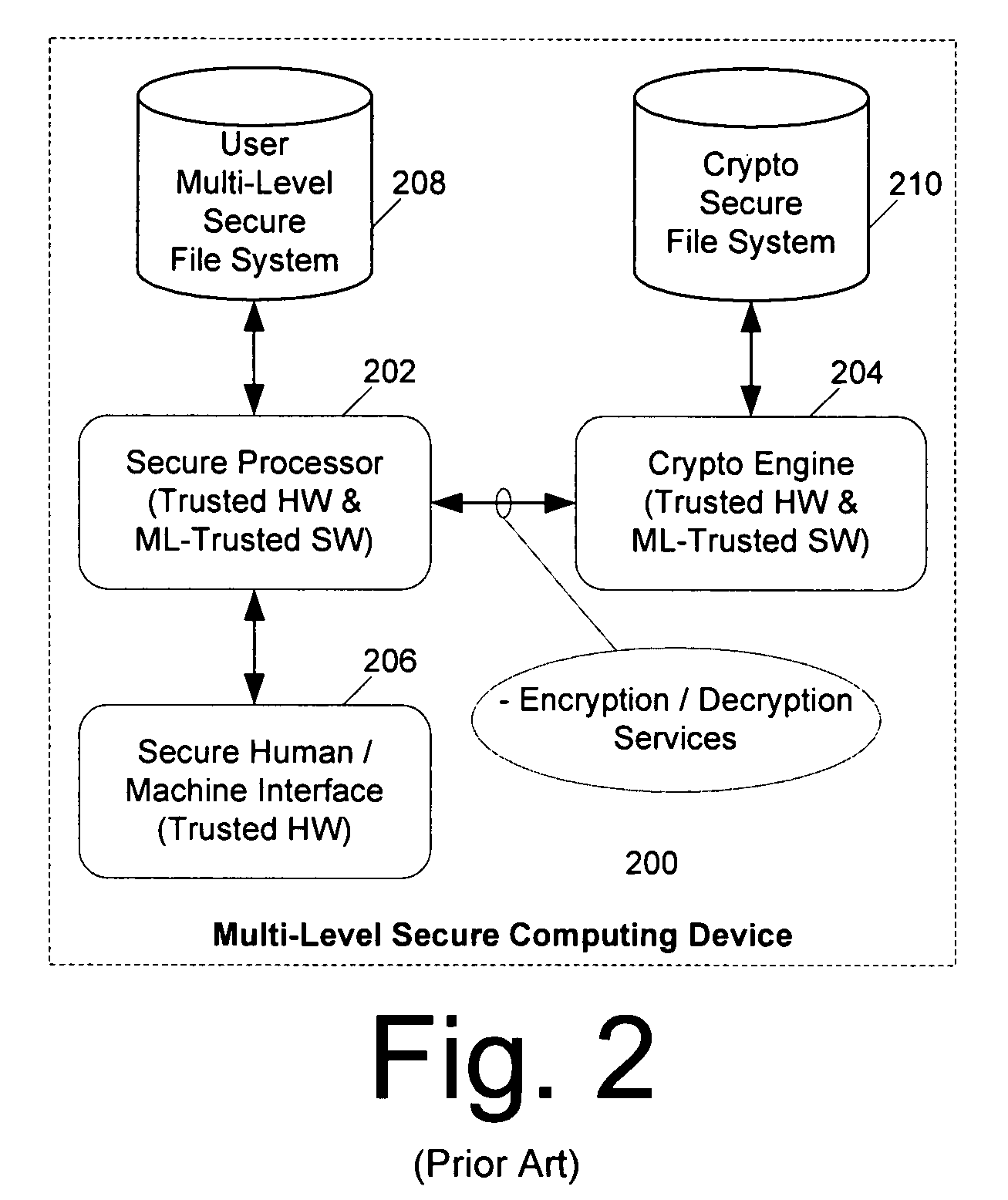
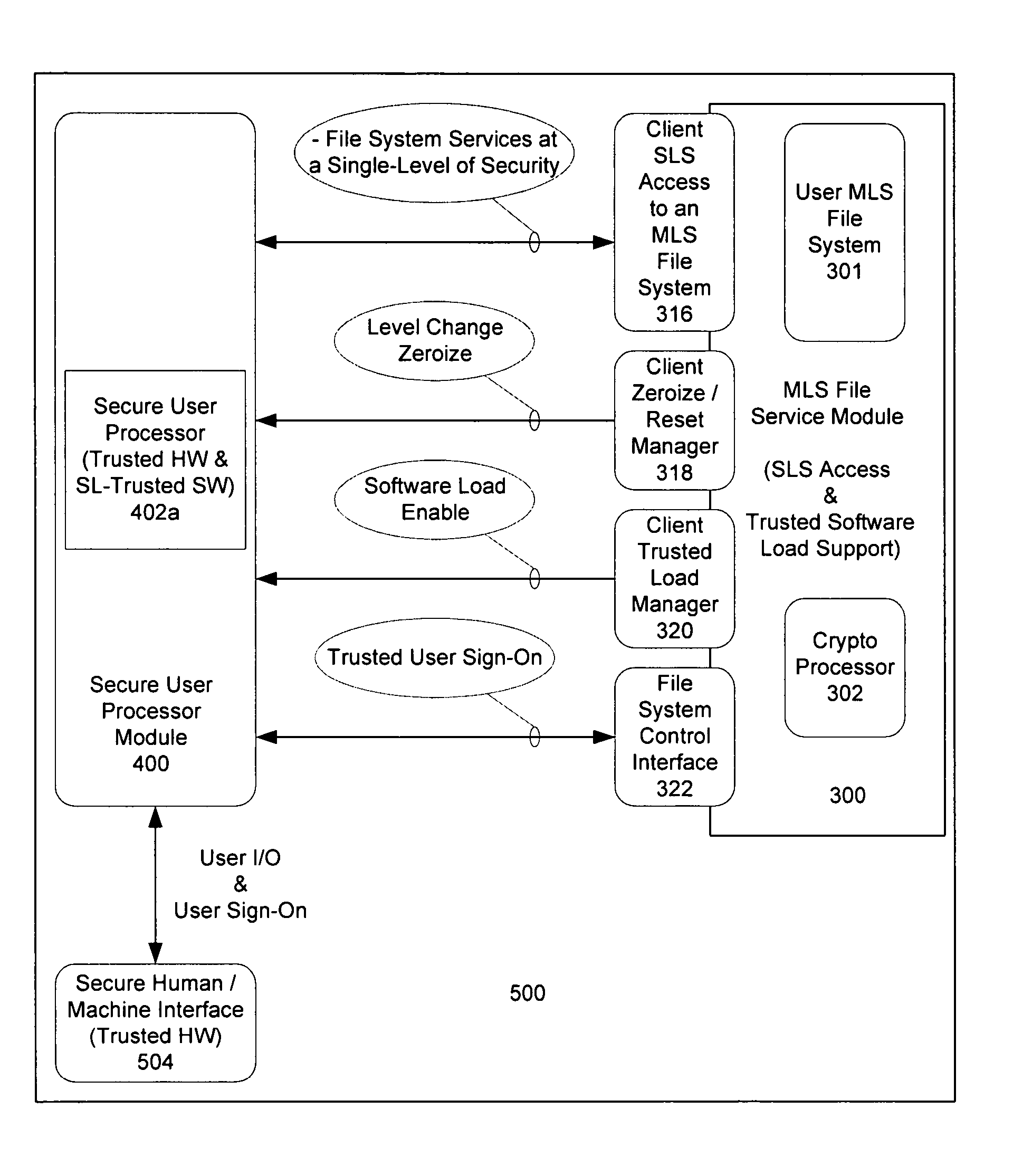
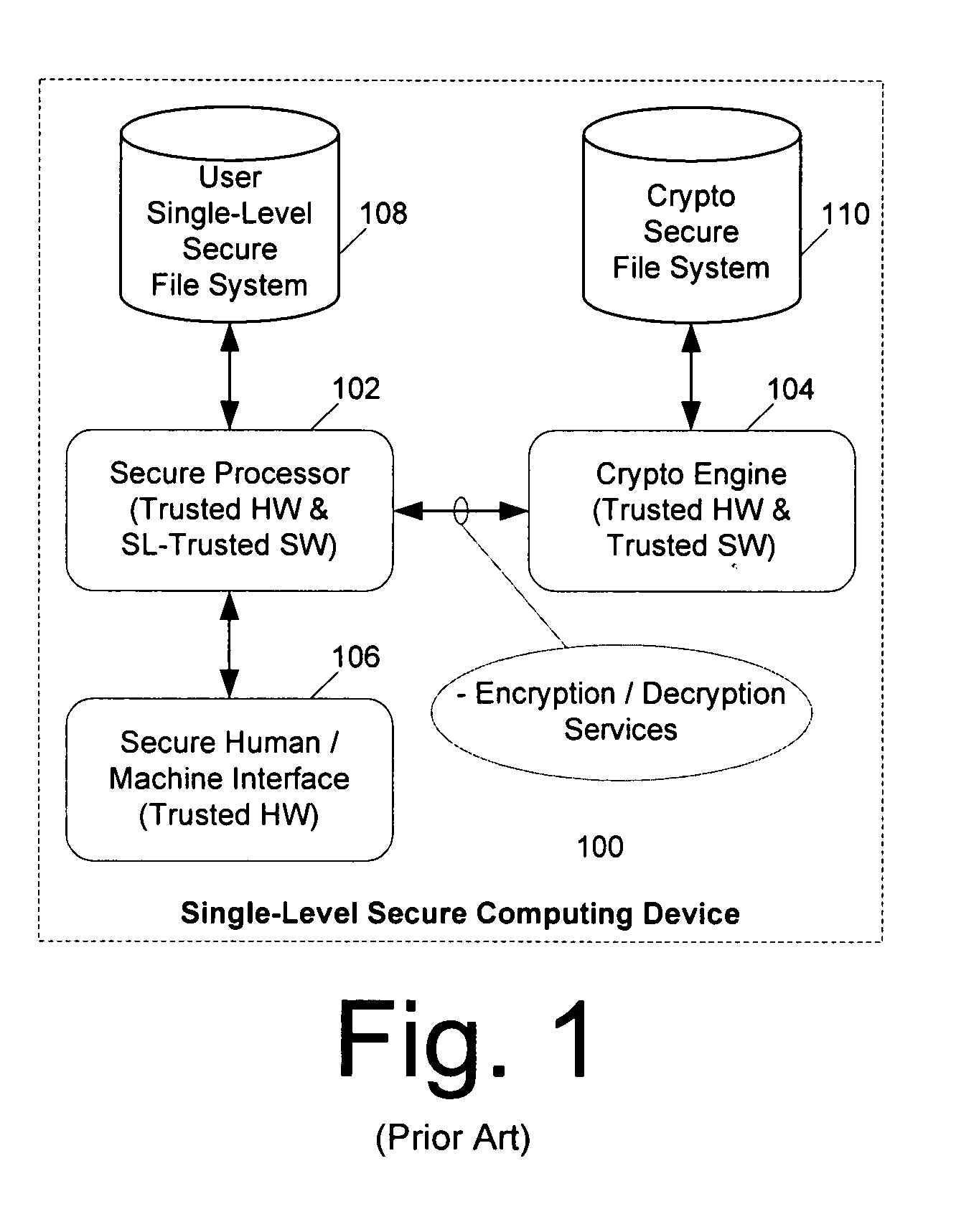
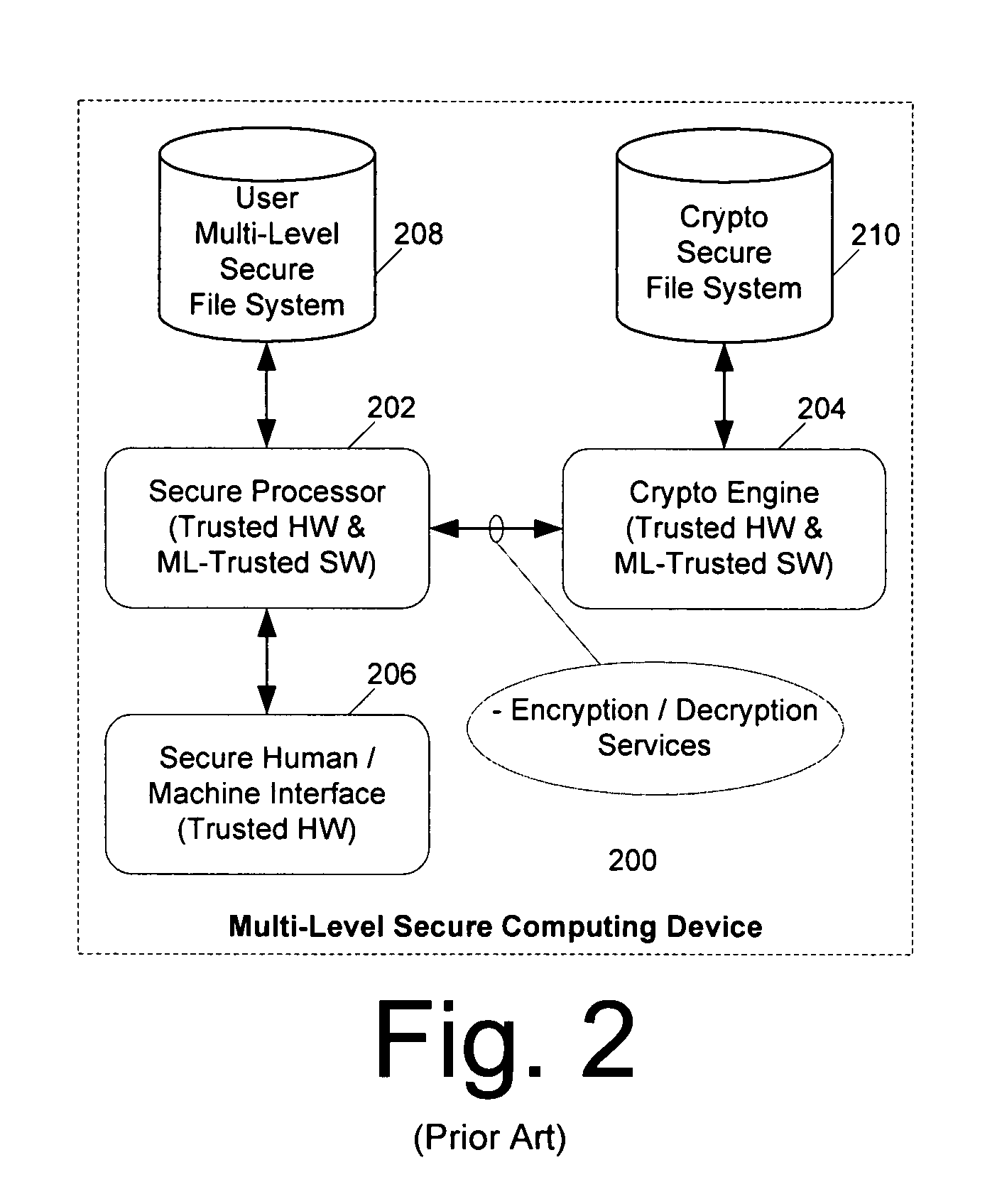
Computer architecture for an electronic device providing SLS access to MLS file system with trusted loading and protection of program execution memory
ActiveUS8041947B2Digital data processing detailsUnauthorized memory use protectionFile systemComputer module
System for providing a secure file service includes an MLS file service module (300) comprised of a cryptographic processor (302). The MLS file service module also includes an MLS file system (301) hosted by the cryptographic processor. A secure user processor (402) includes programming and communications hardware for requesting at least one classified file from the MLS file service module. The cryptographic processor includes cryptographic hardware and software to decrypt the classified file. The cryptographic processor is also performs an integrity check on the classified file. Once the file is decrypted and its integrity checked by the cryptographic processor, the MLS file service module serves the classified file to the secure user processor in decrypted form. If the classified file is an executable file, the method also includes selectively enabling a write function for program memory of the secure user processor. This write function is disabled immediately after the classified executable file has been loaded into the program memory to guard against self modifying programs.
Owner:HARRIS GLOBAL COMM INC
Computer architecture for an electronic device providing SLS access to MLS file system with trusted loading and protection of program execution memory
ActiveUS20070226493A1Digital data processing detailsUser identity/authority verificationFile systemComputer module
System for providing a secure file service includes an MLS file service module (300) comprised of a cryptographic processor (302). The MLS file service module also includes an MLS file system (301) hosted by the cryptographic processor. A secure user processor (402) includes programming and communications hardware for requesting at least one classified file from the MLS file service module. The cryptographic processor includes cryptographic hardware and software to decrypt the classified file. The cryptographic processor is also performs an integrity check on the classified file. Once the file is decrypted and its integrity checked by the cryptographic processor, the MLS file service module serves the classified file to the secure user processor in decrypted form. If the classified file is an executable file, the method also includes selectively enabling a write function for program memory of the secure user processor. This write function is disabled immediately after the classified executable file has been loaded into the program memory to guard against self modifying programs.
Owner:HARRIS GLOBAL COMMUNICATIONS INC
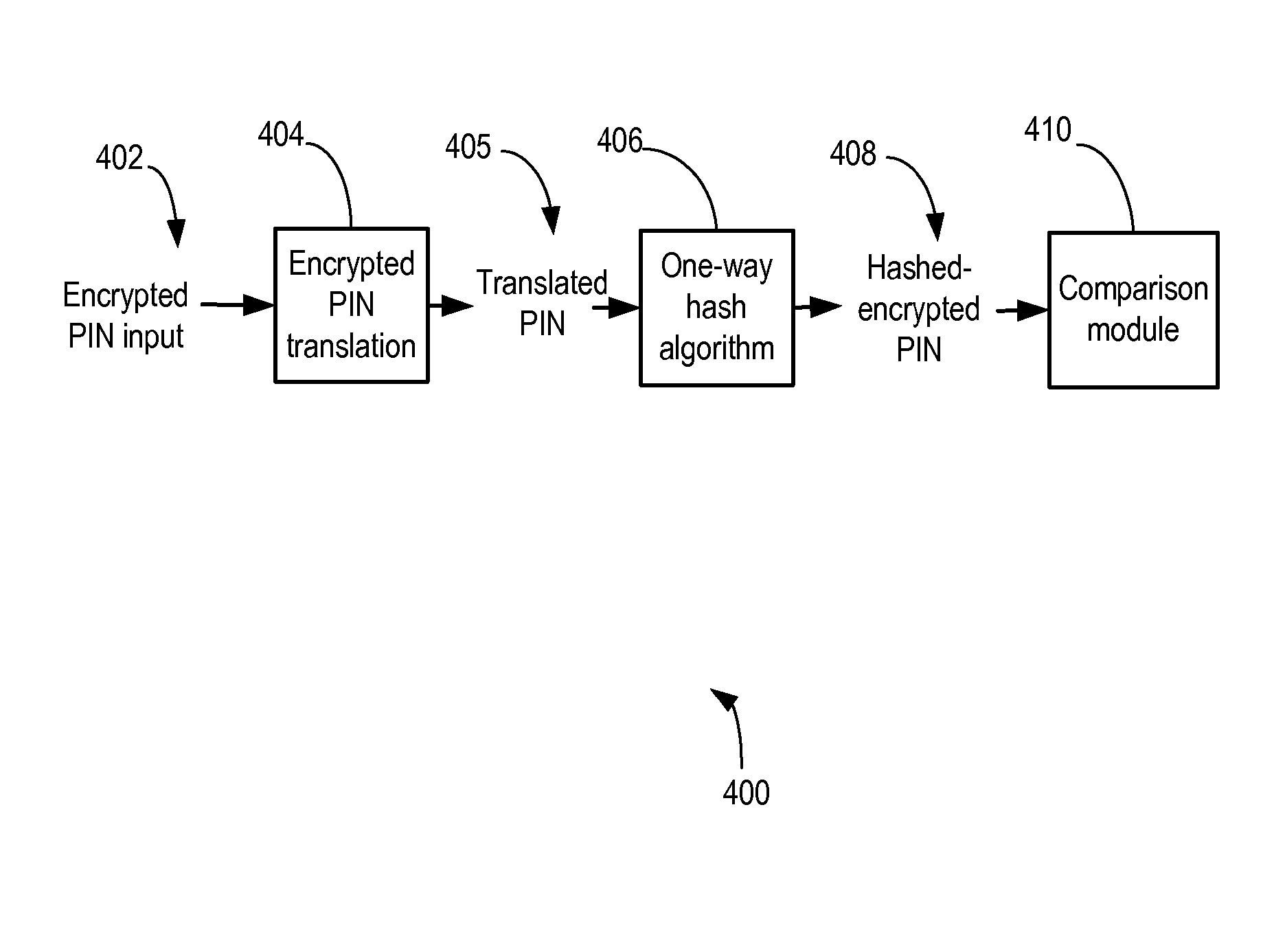
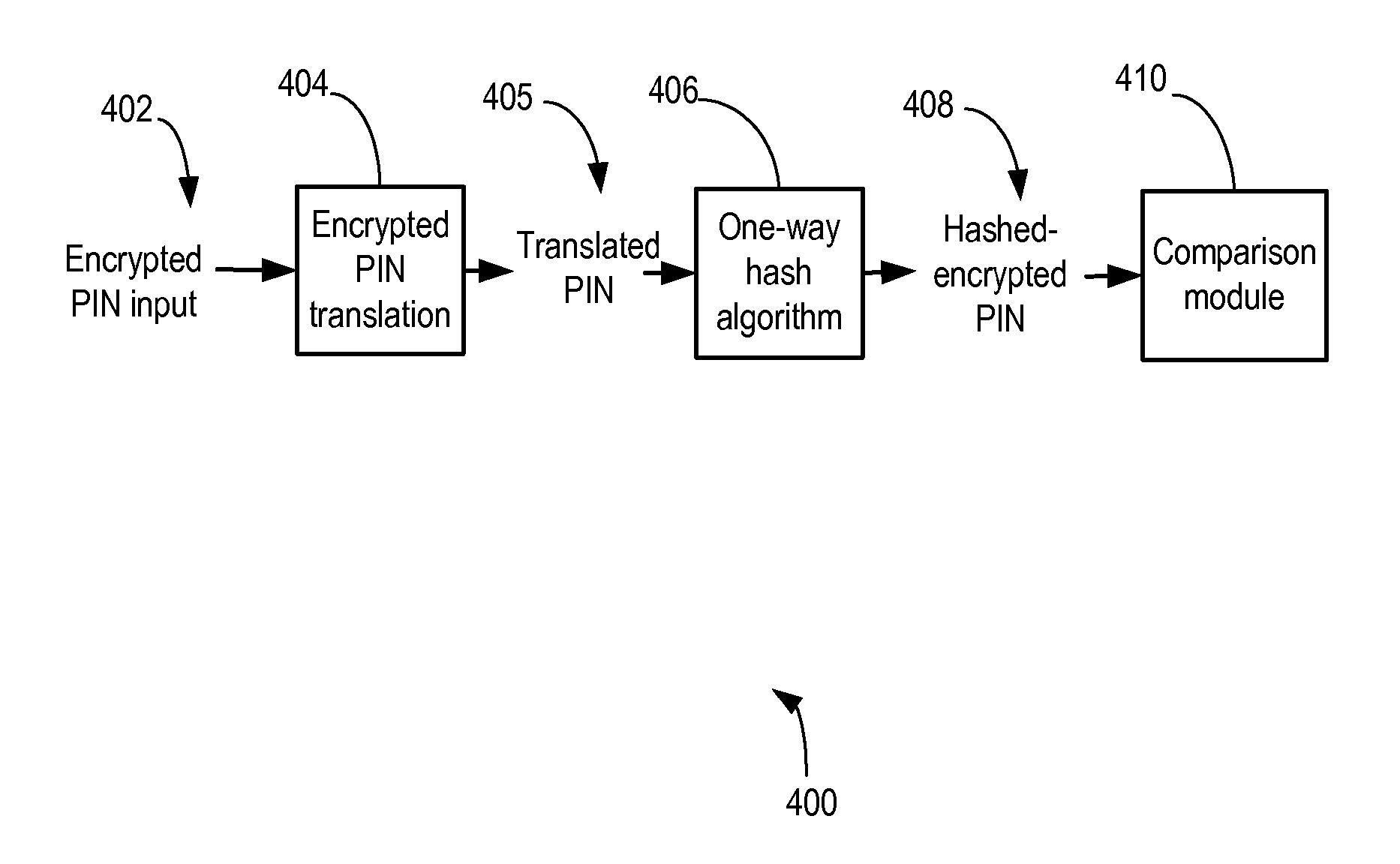
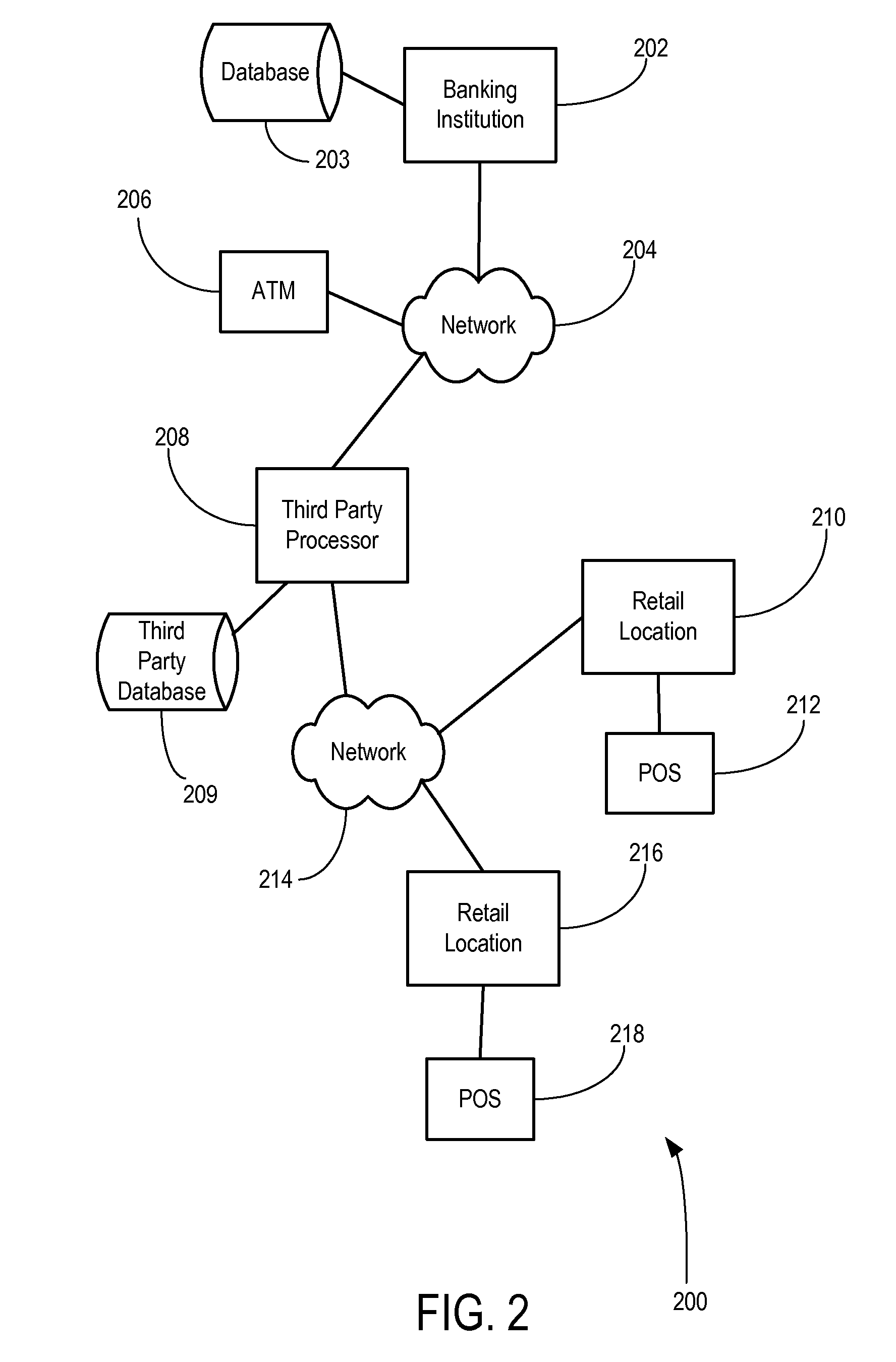
System and method for secure verification of electronic transactions
InactiveUS20080077798A1Acutation objectsUser identity/authority verificationThird partyPersonal identification number
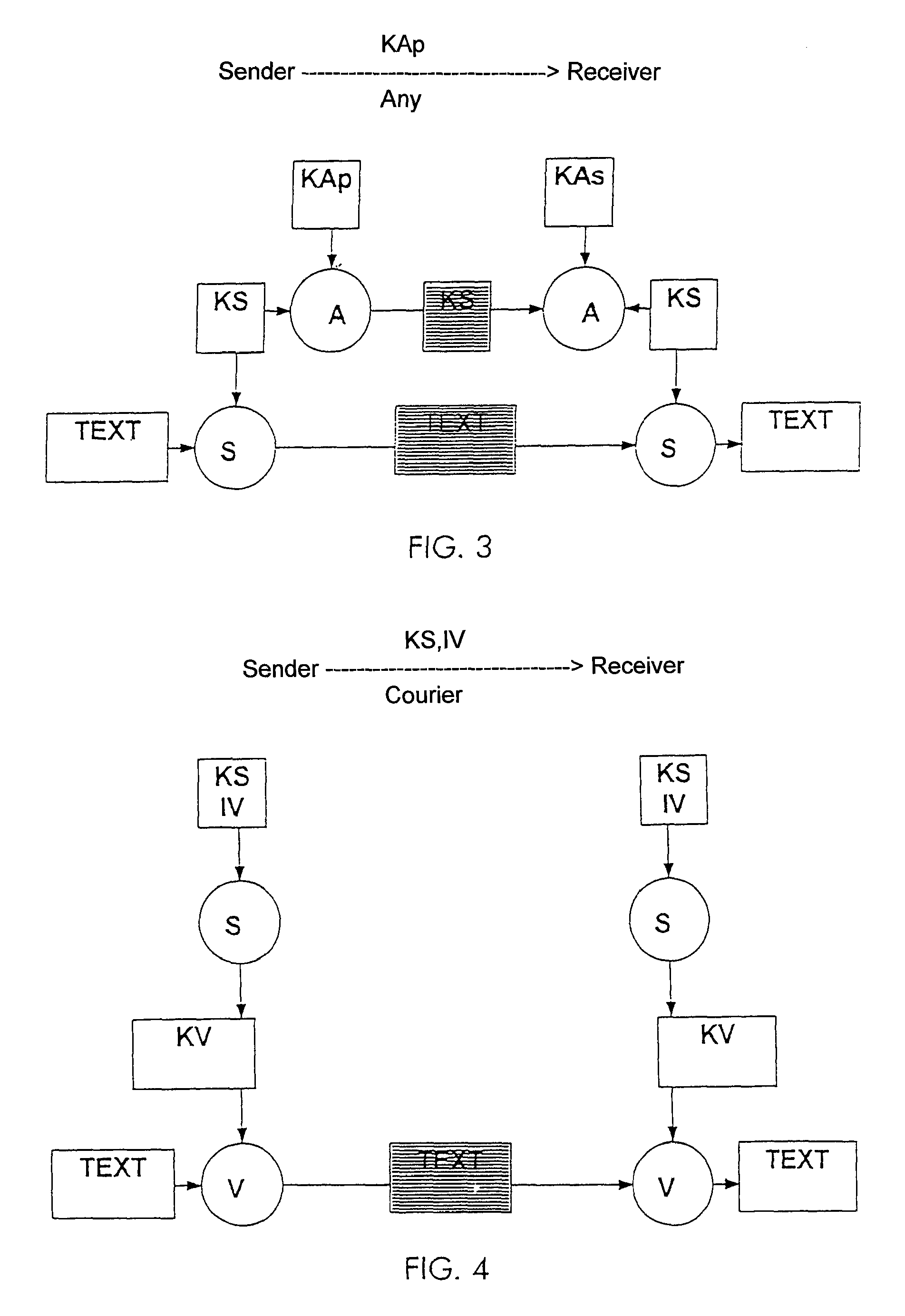
The present invention relates to a system and method for secure verification of electronic transactions, and in particular secure processing of personal identification numbers when third party processors are involved. In an embodiment, a variable length PIN associated with a credit card or debit card is encrypted, then hashed using a one-way hash algorithm before it is passed along to and stored by a third party processor. The encrypted-hashed PIN always remains in an encrypted form while in the hands of the third party processor. At the third party processor, secure cryptographic hardware is used to store the one-way hash algorithm. Encrypted PIN values received for verification are converted and hashed using the one-way hash algorithm, and the resulting hashed-encrypted value is compared against the hashed-encrypted PIN values previously stored at the third party processor. As the PIN has a variable length, and the third party processor has no access to the hash algorithm, the encrypted PIN values are highly resistant to reverse engineering or decryption.
Owner:IBM CORP
Method and apparatus for enforcing a predetermined memory mapping
ActiveUS20110099387A1Unauthorized memory use protectionHardware monitoringData processing systemApplication software
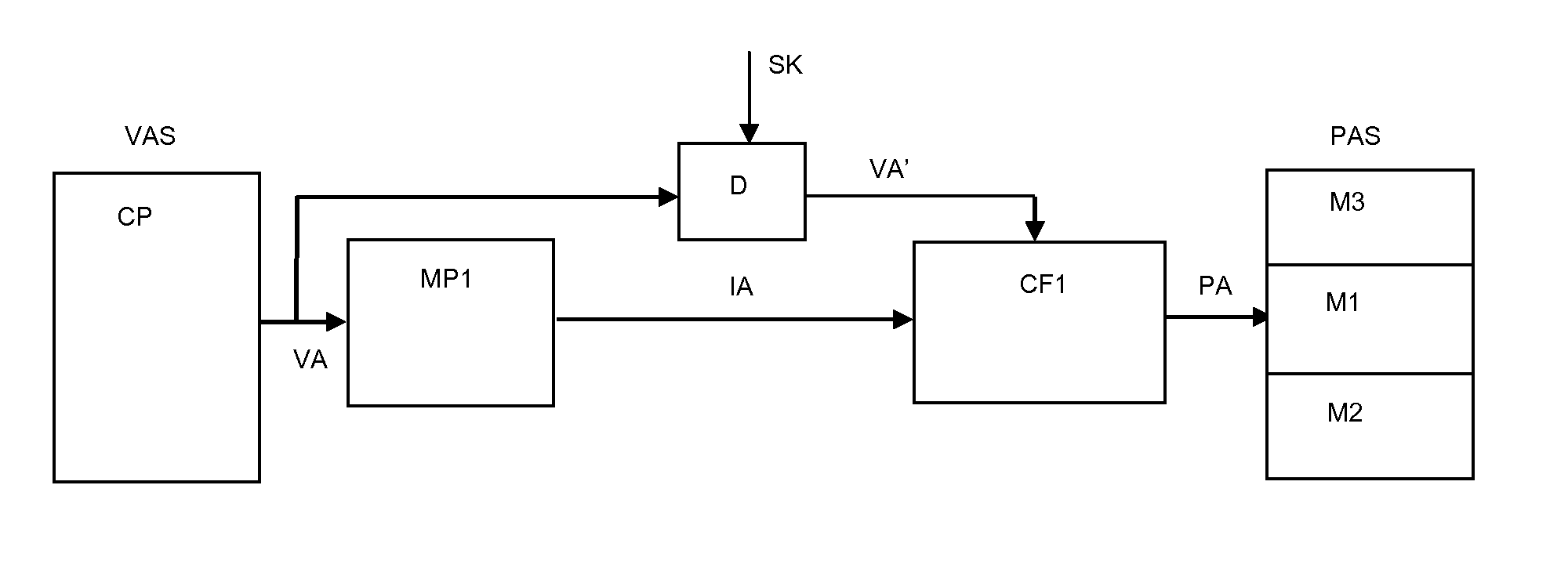
A system and a method are disclosed for enforcing a predetermined mapping of addresses in a physical address space to addresses in a virtual address space in a data processing system including a processor in the virtual address space and a memory in a physical address space. During the compilation and linking of an application to be run on the data processing system, in at least one embodiment, the mapping table is generated linking the virtual addresses to physical addresses. This mapping table is kept secret. A second mapping table is generated using a cryptographic function of the physical address with the virtual address as a key to link virtual addresses to intermediate addresses. The second mapping table is loaded into the memory management unit. The data processing system further includes cryptographic hardware to convert the intermediate address to the physical address using the inverse of the cryptographic function which was used to calculate the intermediate address.
Owner:NAGRAVISION SA
System and methods for side-channel attack prevention
InactiveUS8781111B2Digital data processing detailsInternal/peripheral component protectionProcessor registerCryptosystem
Owner:AVAGO TECH INT SALES PTE LTD
Hardware-bonded credential manager method and system
An internet data exchange authentication method that can provide much of the user authentication assurance and capability of dedicated computer security cryptographic hardware, without requiring that the user actually have such hardware. This method allows users with computerized devices to communicate securely with secure servers by creating customized challenge-response authentication objects (pockets) where both the challenge and the response is based partially on the hardware identity of the user's computerized device, and partially on a secret (such as a random number) known only by the secure server. The secure server receives the device's hardware identity, generates the secret, creates the pocket, encrypts the pocket, and sends the encrypted pocket back to the user's device. The secure server, or a third trusted credential server, then sends the decryption key for the encrypted pocket back to the user using a different, “out of band” communications modality, thus reducing the chances of interception.
Owner:AUTHENEX
System and method for preventing unauthorized access to information
InactiveUS20090235083A1User identity/authority verificationUnauthorized memory use protectionAuthentication systemAccess to information
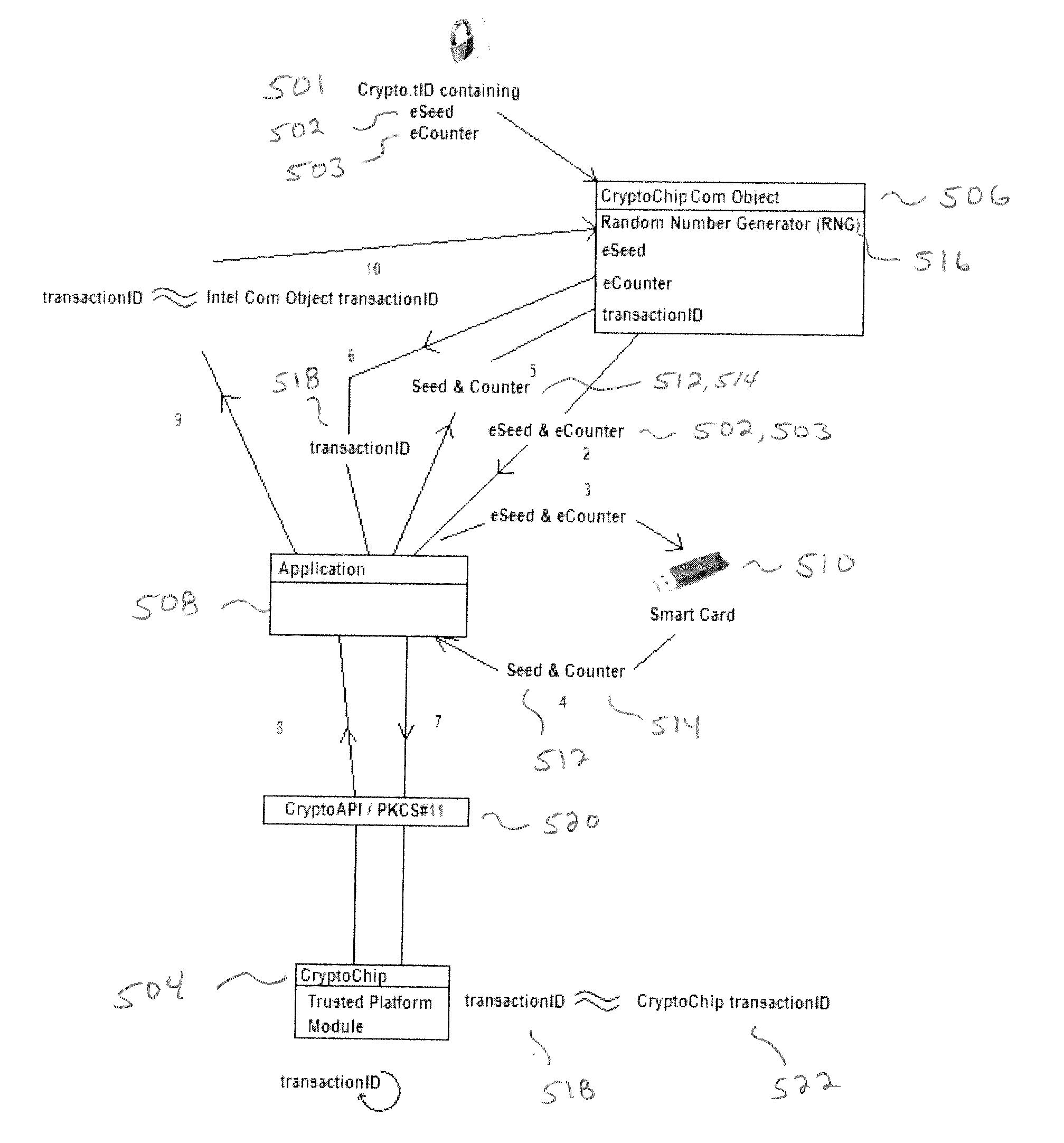
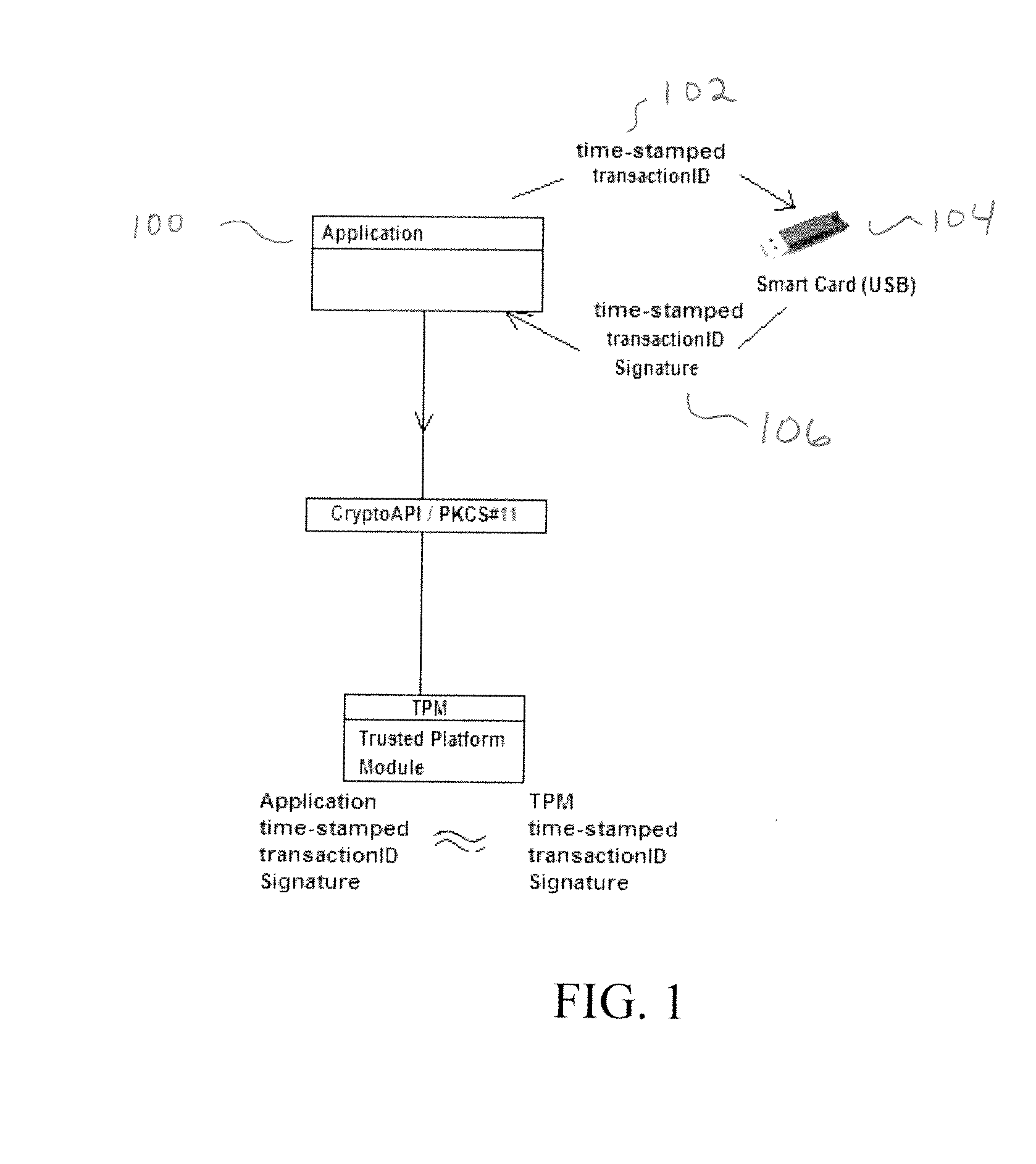
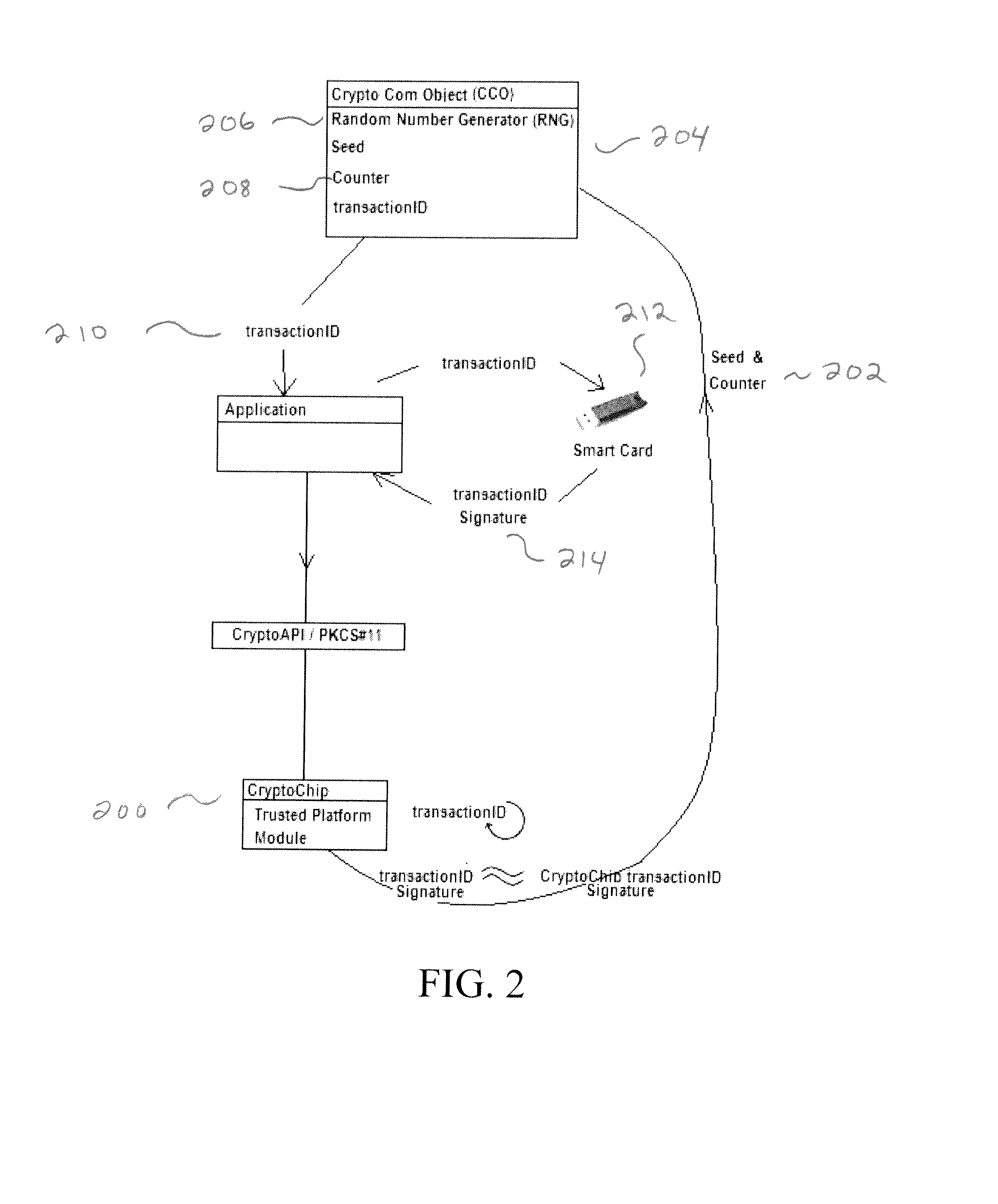
An authentication system protects a hardware cryptographic chip from being commanded to decrypt or sign data by someone other than the legitimate owner(s) of the certificate residing on the chip. Openness of present cryptographic hardware systems are limited by imposing a condition that the cryptographic chip will only perform critical cryptographic tasks if the task is accompanied by a signed time-stamped transaction identifier which only the legitimate owner of the chip can provide.
Owner:BLEAHEN MICHEAL
Dual-mode processing of cryptographic operations
ActiveUS20180006806A1Encryption apparatus with shift registers/memoriesCoding/ciphering apparatusComputer hardwareDual mode
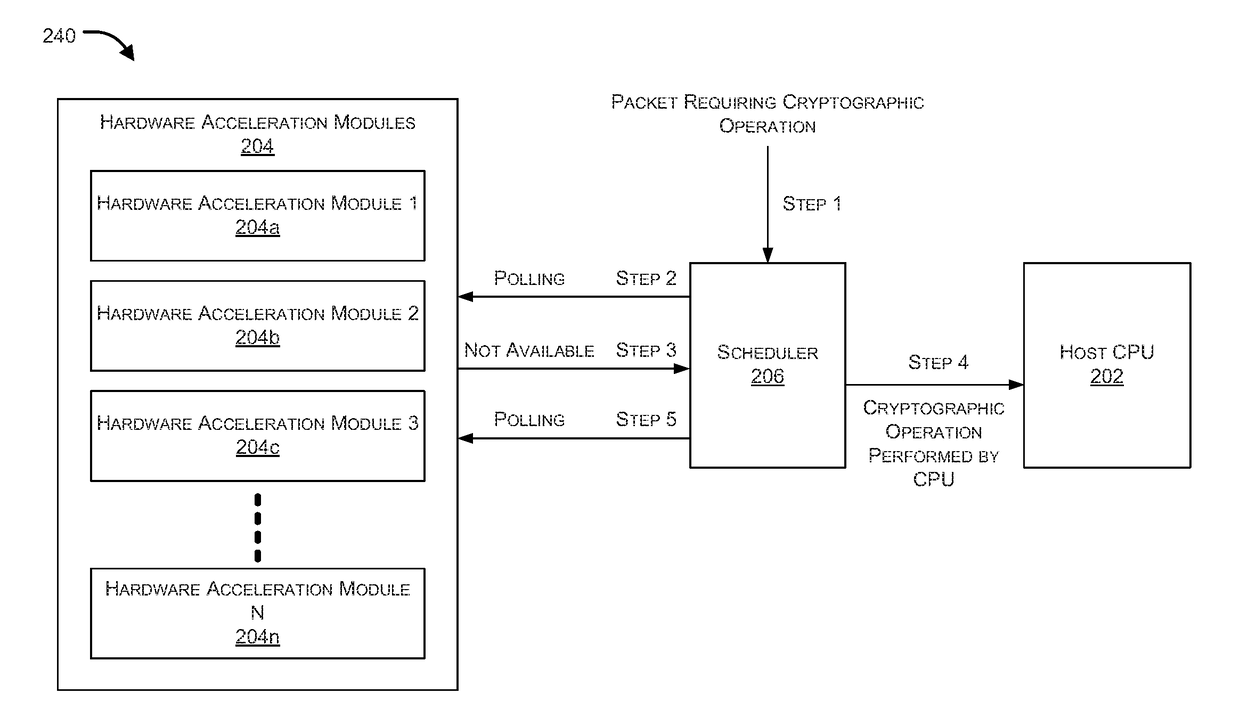
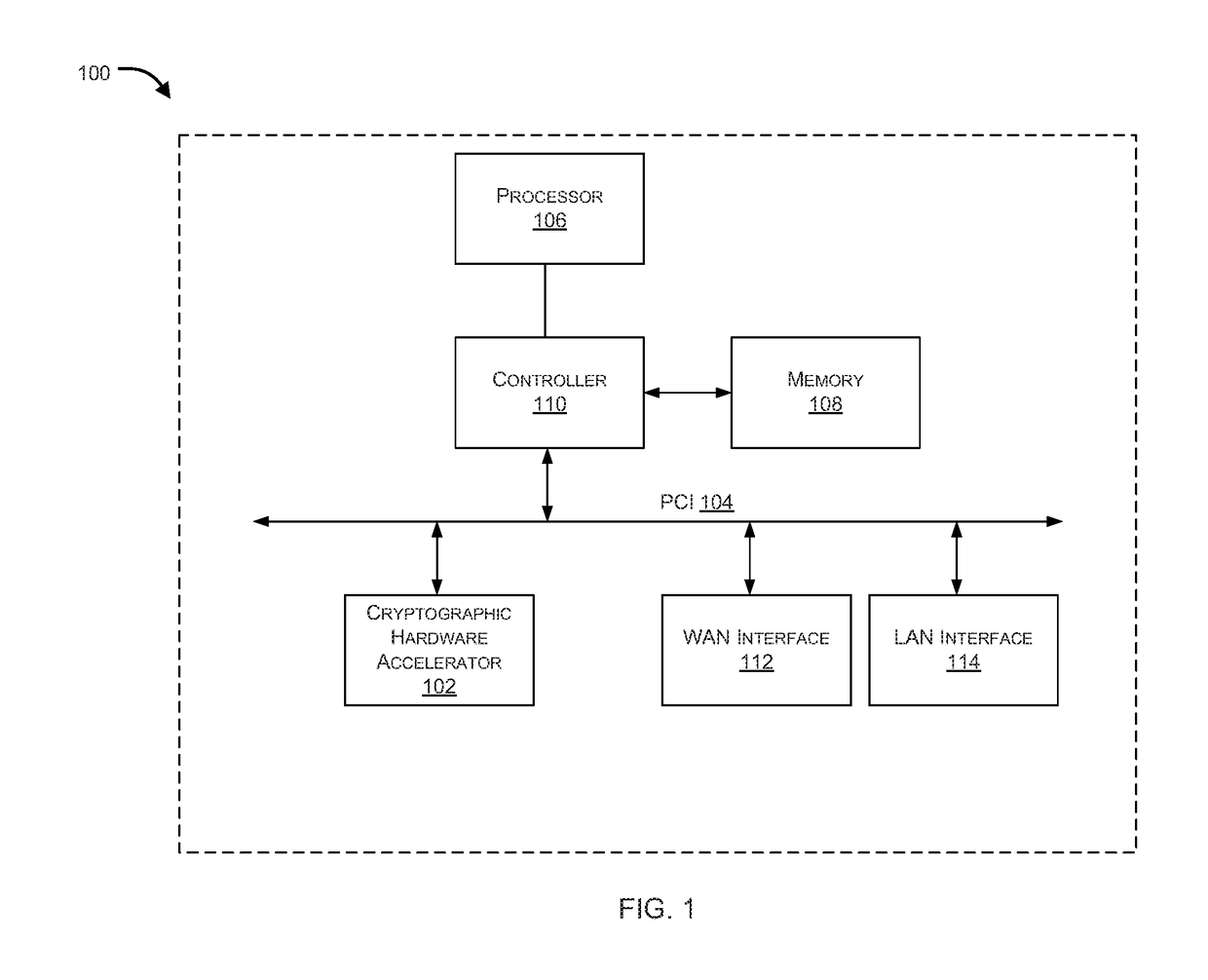
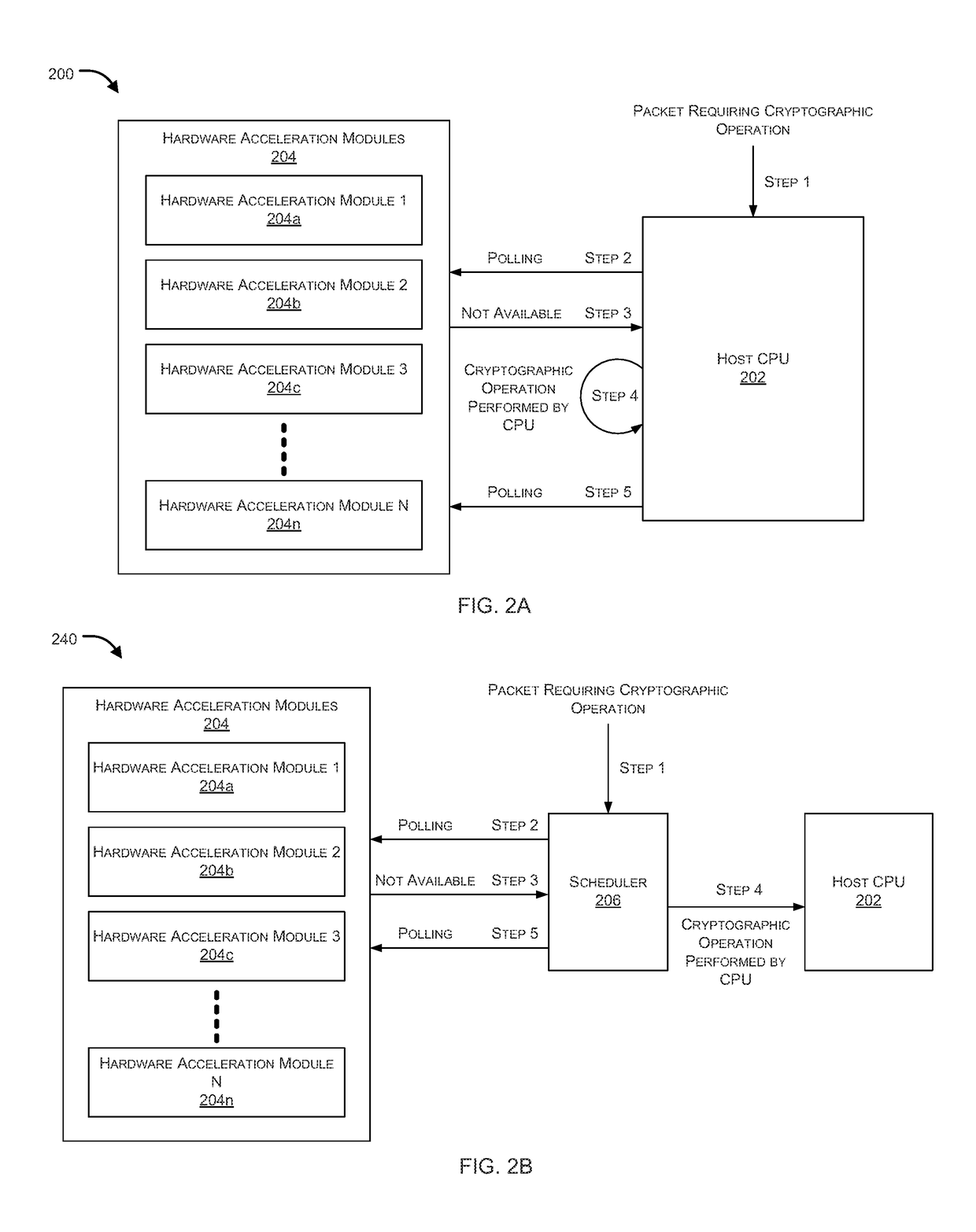
Systems and methods for dual mode hardware acceleration for cryptographic operations are provided. According to one embodiment, data upon which a cryptographic operation is to be performed is receive by a computer system that includes a host CPU and a cryptographic hardware accelerator. The data is divided into multiple blocks. Performance of the operation on a first block is offloaded to the hardware accelerator. For each remaining block: (i) the CPU requests state information of the hardware accelerator; (ii) when the state satisfies a condition, then performance of the operation is offloaded to the hardware accelerator; (iii) otherwise, the operation is performed by the CPU by invoking a native hardware supported cryptographic instruction. In this manner, the cryptographic operation is performed on at least one of the blocks by the hardware accelerator and the operation is performed on at least another of the blocks by the CPU.
Owner:FORTINET
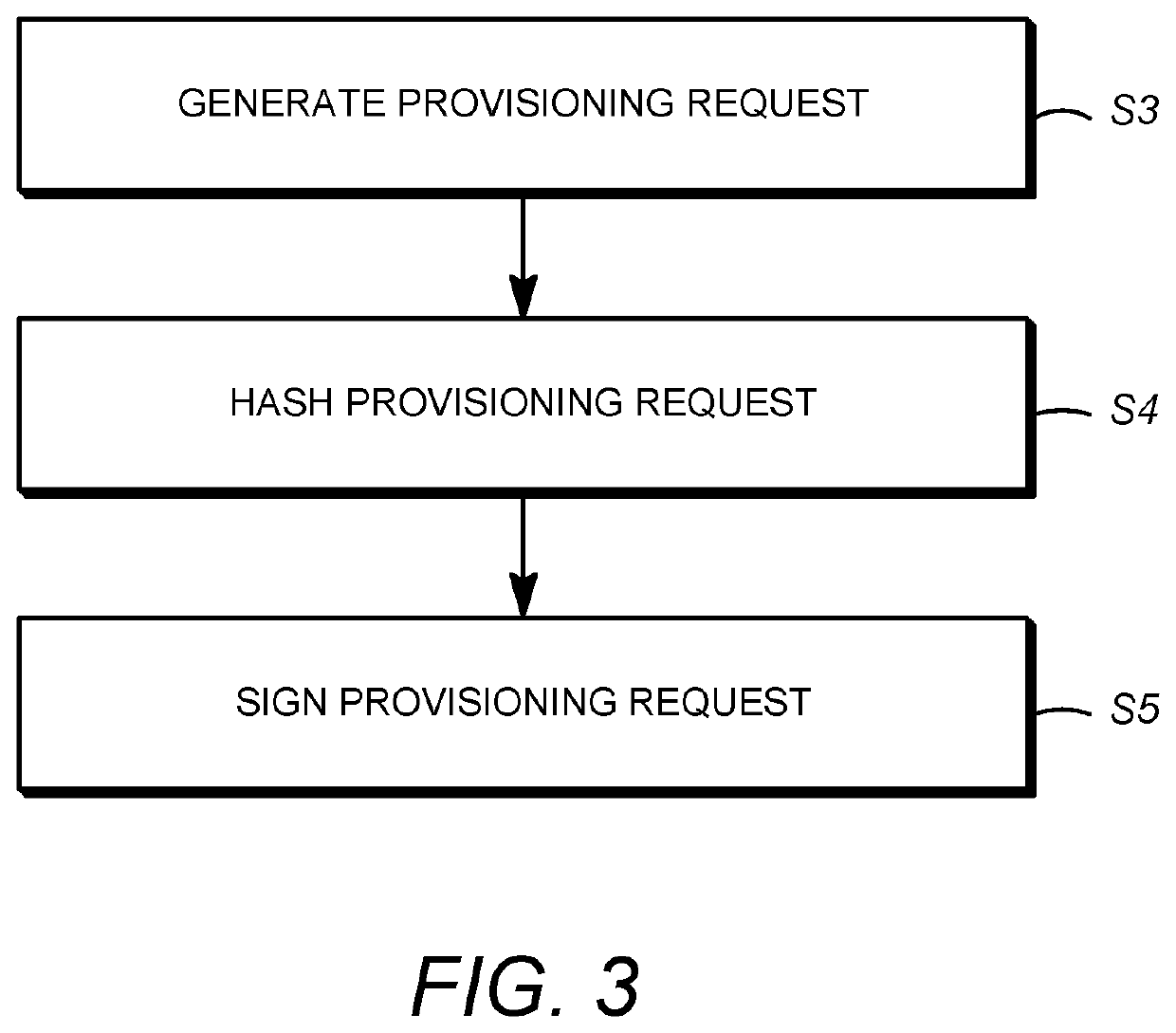
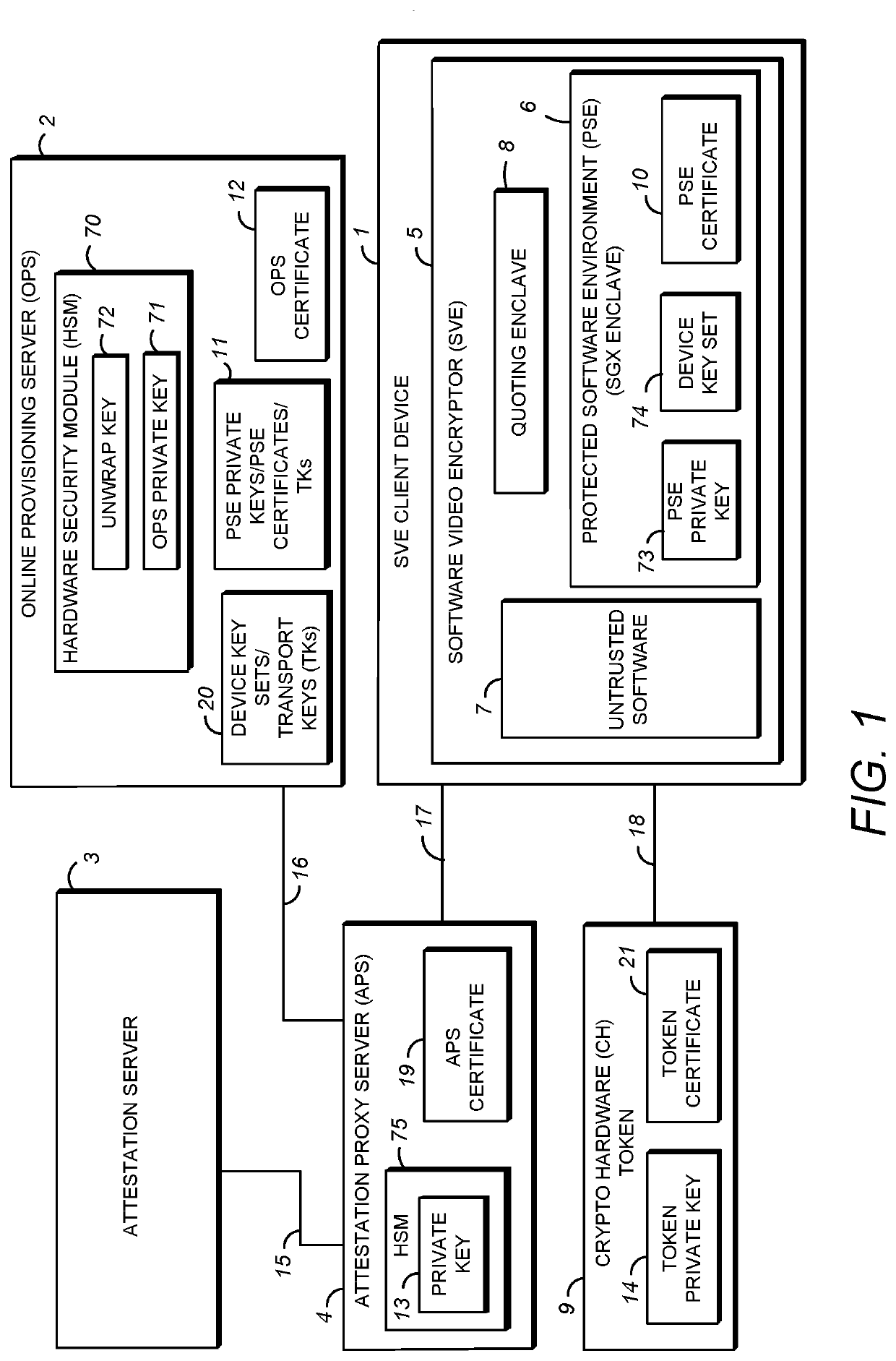
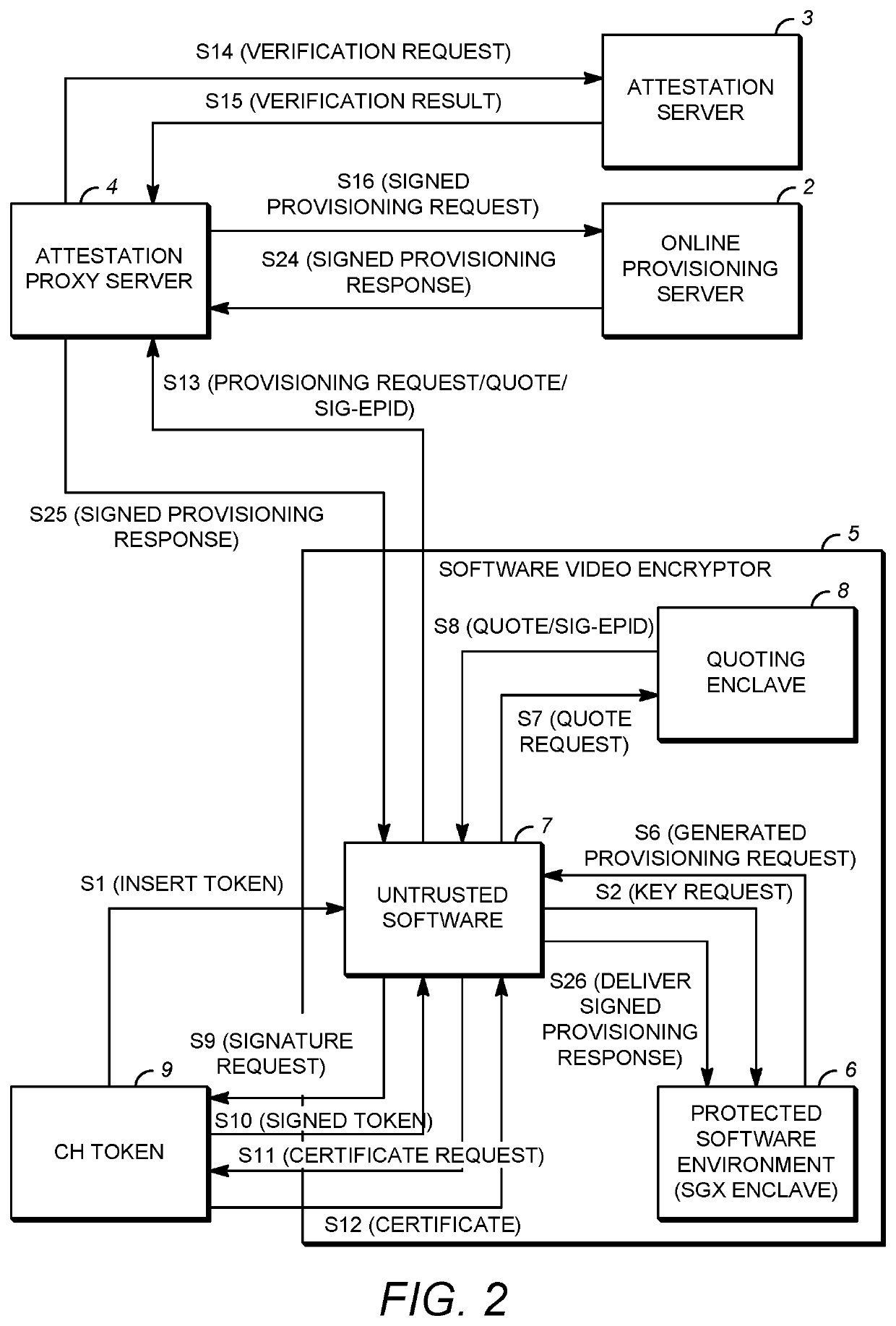
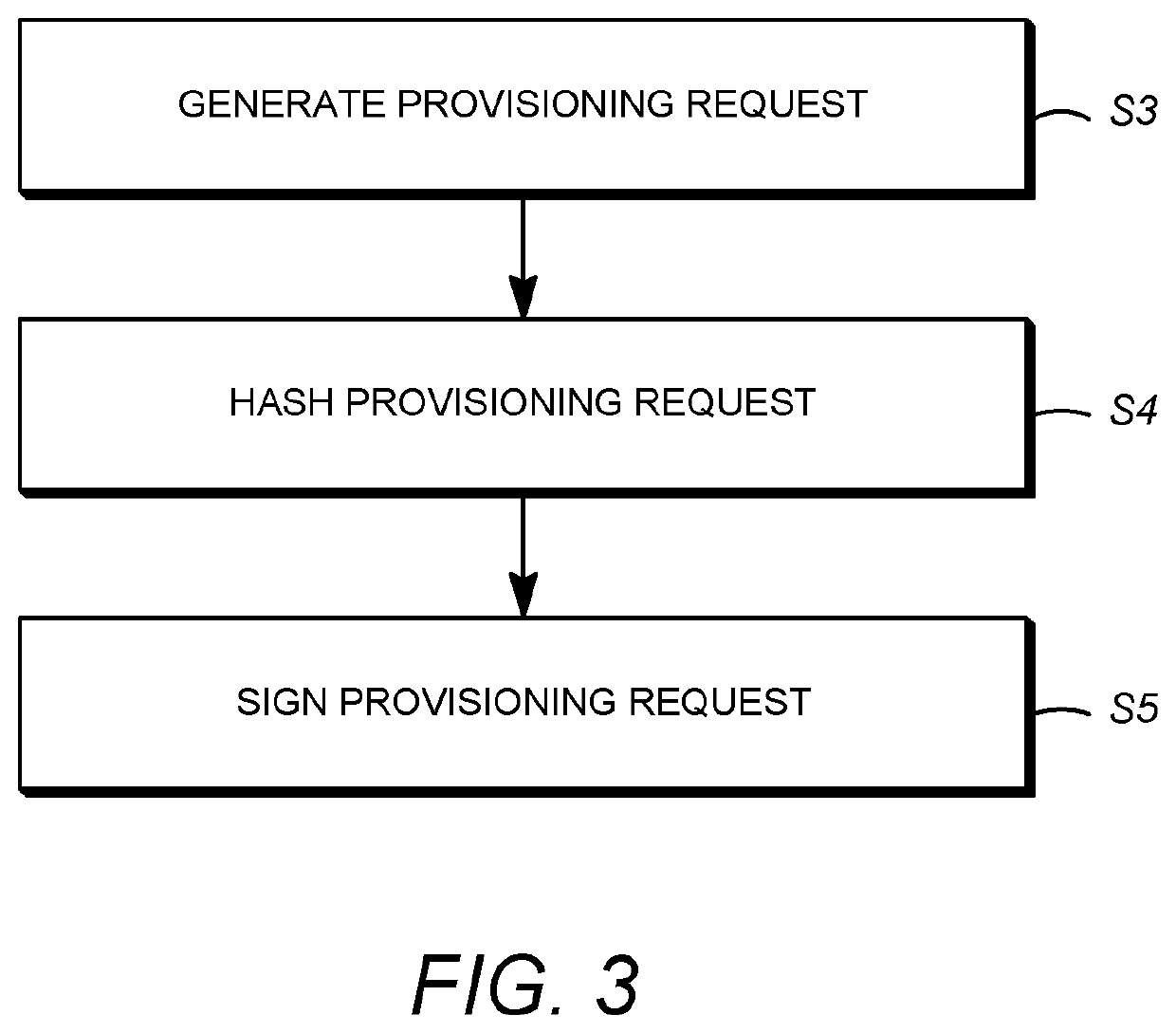
Secure distribution of device key sets over a network
ActiveUS20200304299A1Key distribution for secure communicationUser identity/authority verificationEngineeringProxy server
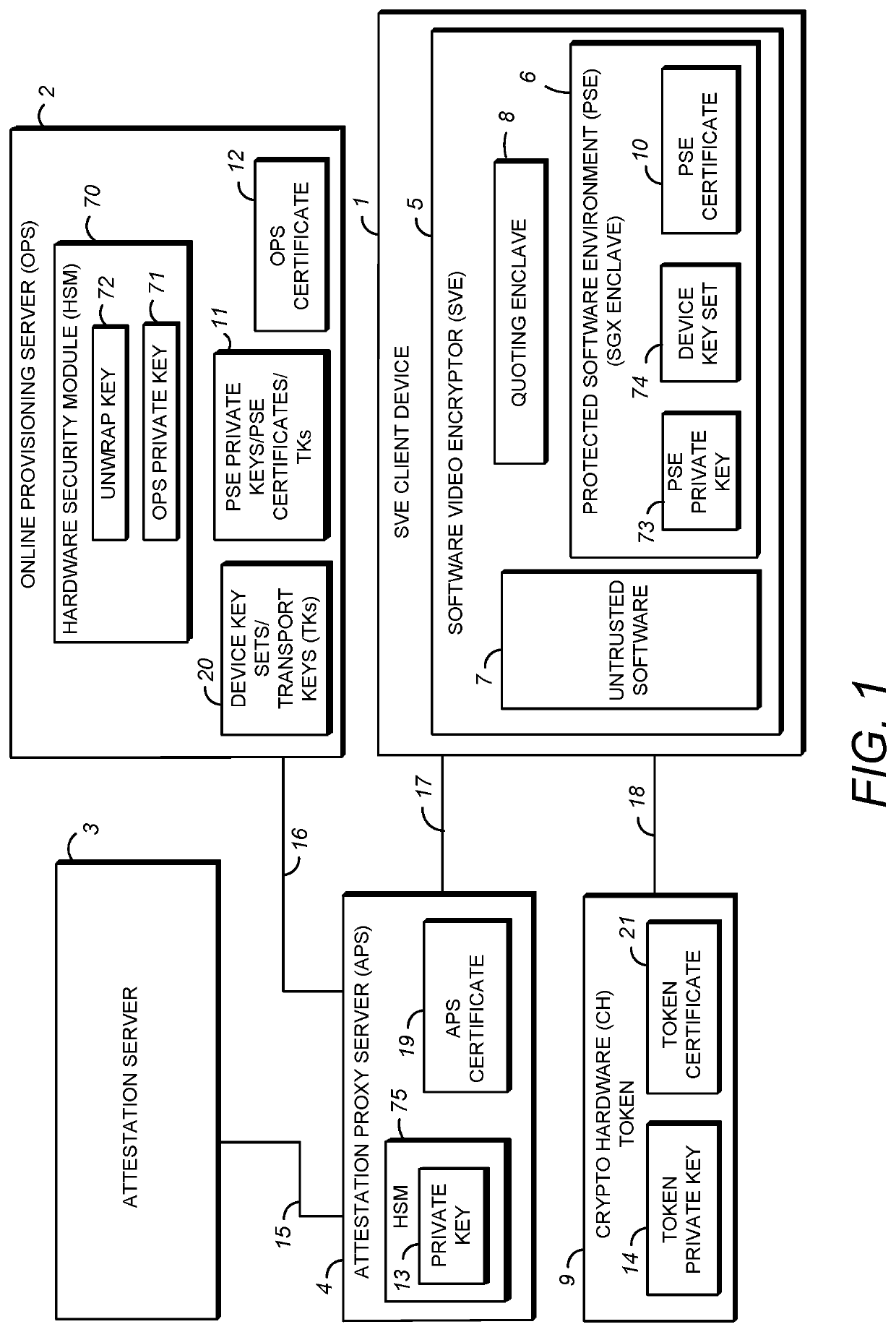
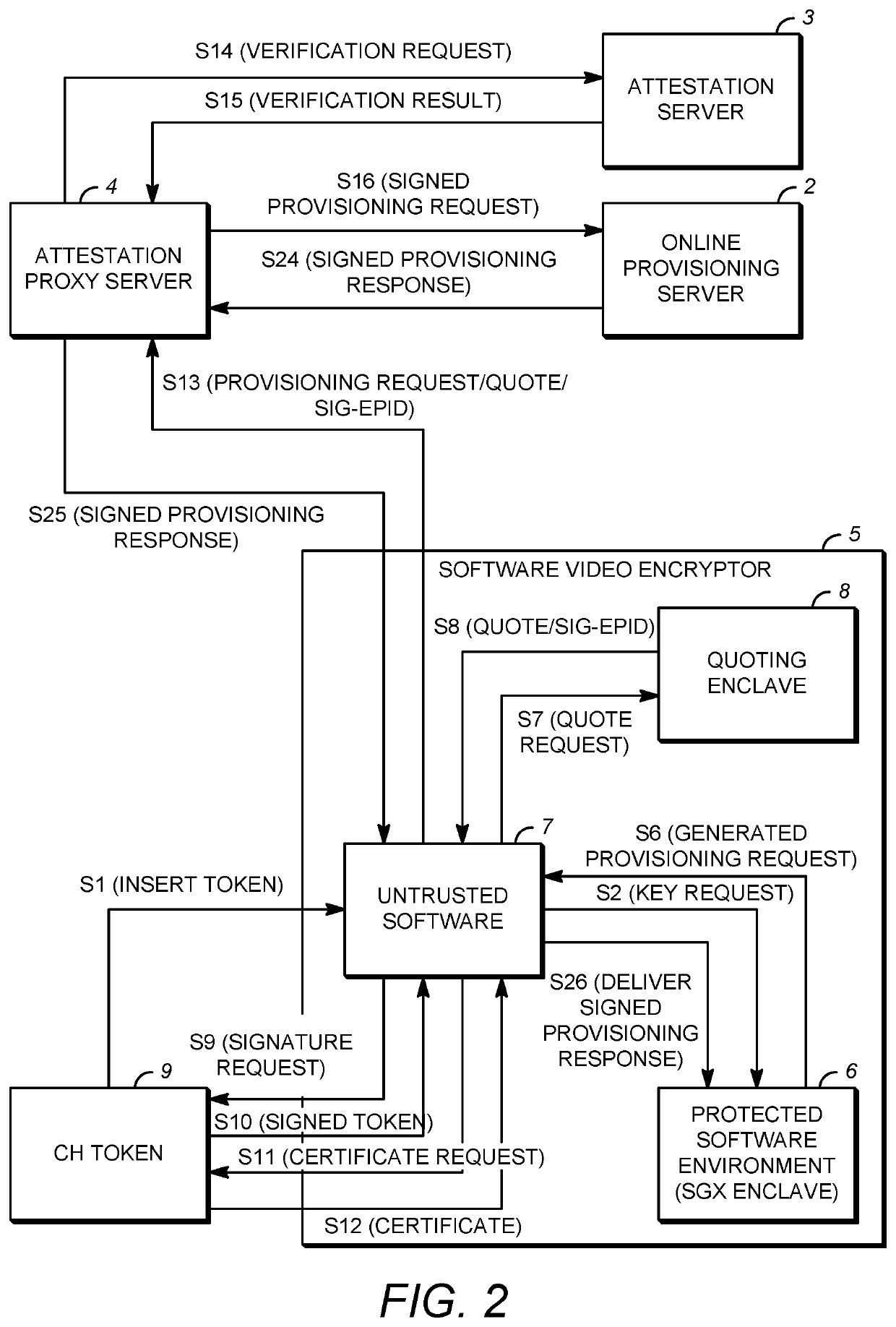
A system is provided for distribution of device key sets over a network in a protected software environment (PSE). In the system, a client device includes a connection interface for receiving a crypto hardware (CH) token belonging to a user, untrusted software, a quoting enclave, and a PSE for generating a provisioning request for a device key set. An attestation proxy server (APS) receives the provisioning message using a first network connection, and transmits the provisioning message to an online provisioning server (OPS) using a second network connection. The OPS constructs a provisioning response and an encrypted device key set, and delivers the provisioning response to the untrusted software using the first and second network connections. The PSE decrypts the encrypted device key set to obtain the device key set, re-encrypts the device key set with a local chip-specific key, and stores the re-encrypted device key set.
Owner:ARRIS ENTERPRISES LLC
Software authorization verification method
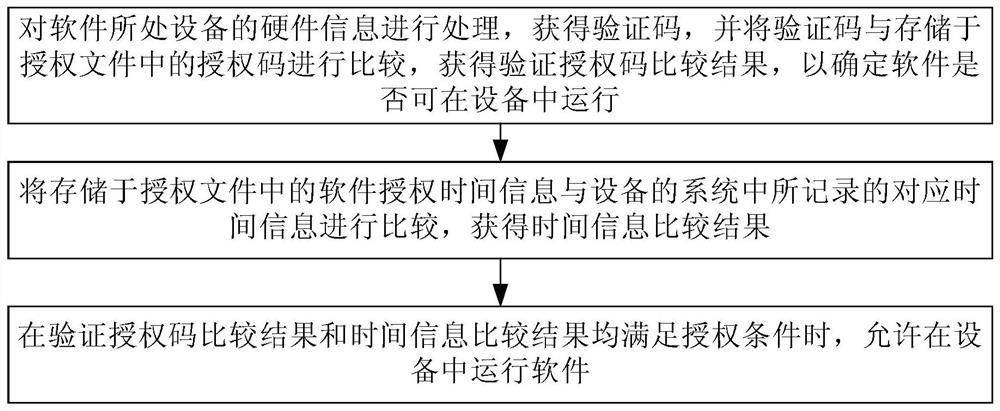
InactiveCN112231647AControl expiration dateReduce investmentDigital data protectionProgram/content distribution protectionTime informationSoftware engineering
The invention discloses a software authorization verification method. The method comprises the following steps of before software is started each time, processing hardware information of equipment inwhich the software is positioned to obtain a verification code, and comparing the verification code with an authorization code stored in an authorization file to obtain a verification authorization code comparison result; comparing the software authorization time information stored in the authorization file with corresponding time information recorded in a system of the equipment to obtain a timeinformation comparison result; and when the verification authorization code comparison result and the time information comparison result both meet the authorization condition, allowing the software torun in the equipment. According to the method, the authorization verification of the software is realized without depending on external pluggable encryption hardware equipment, a far-end authorization server, the Internet and a satellite positioning time service system, the content of the authorization file can be effectively prevented from being modified by a user, and the service life of the software is effectively controlled.
Owner:POTEVIO INFORMATION TECH
Signature method and device for generating SM2 algorithm through mutual coordination, and storage medium
ActiveCN109245903AMake sure it's not stolenImprove securityPublic key for secure communicationUser identity/authority verificationCryptographic hardwareComputer security
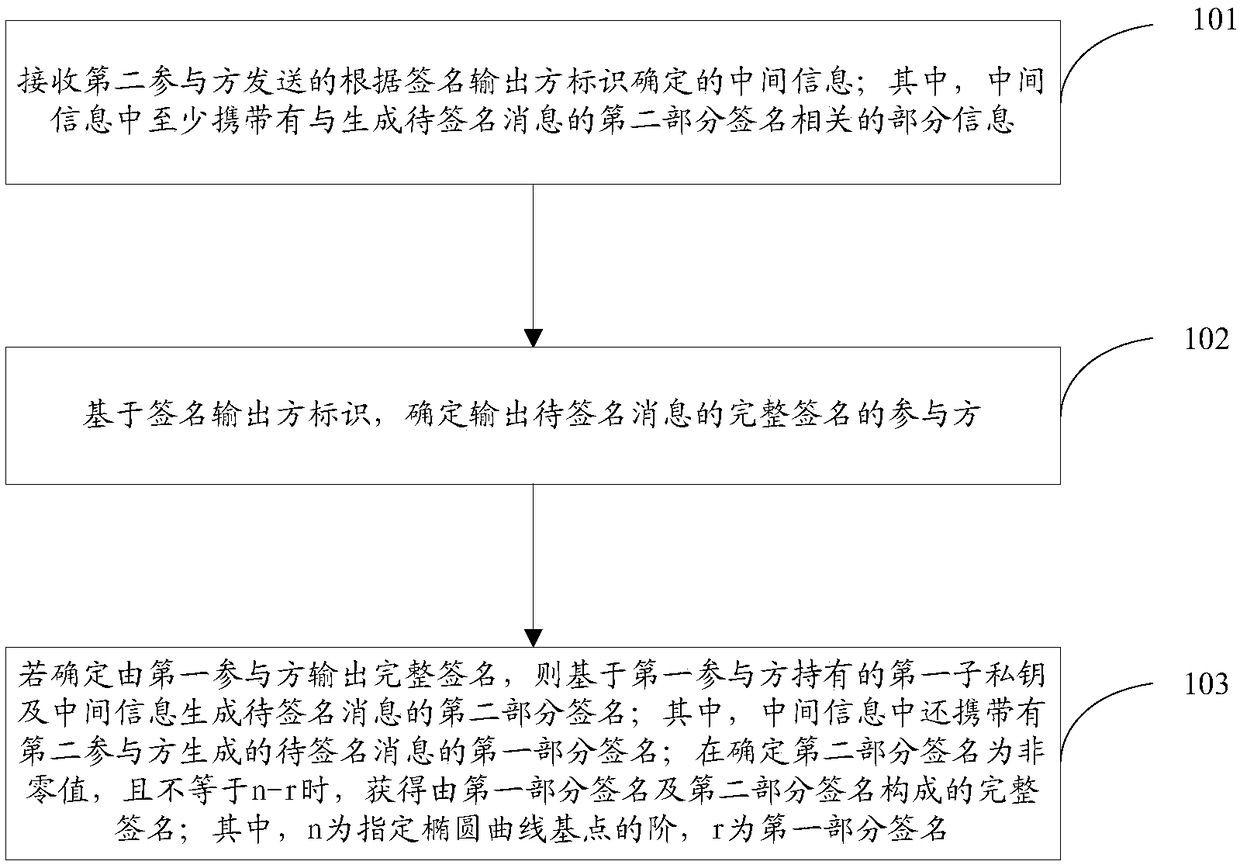
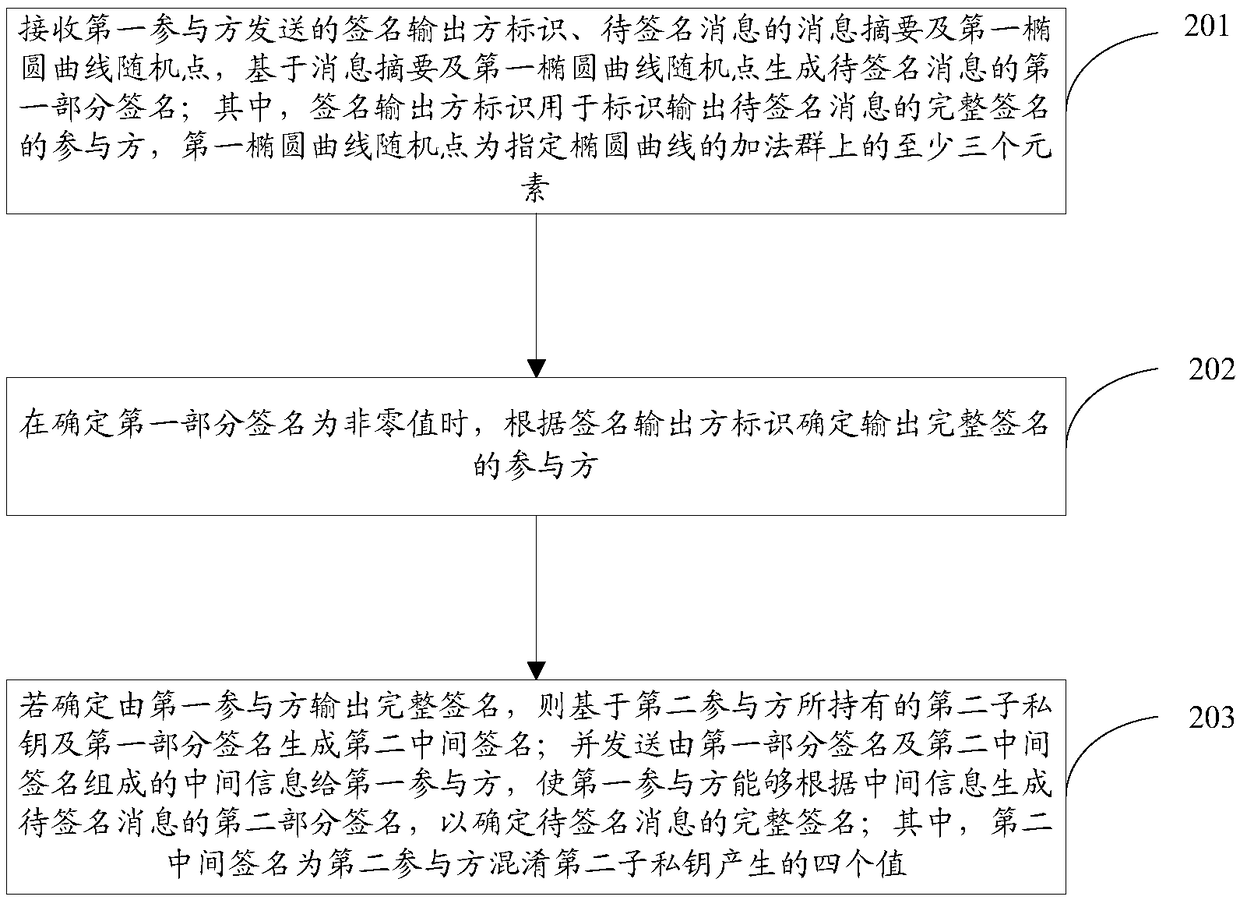
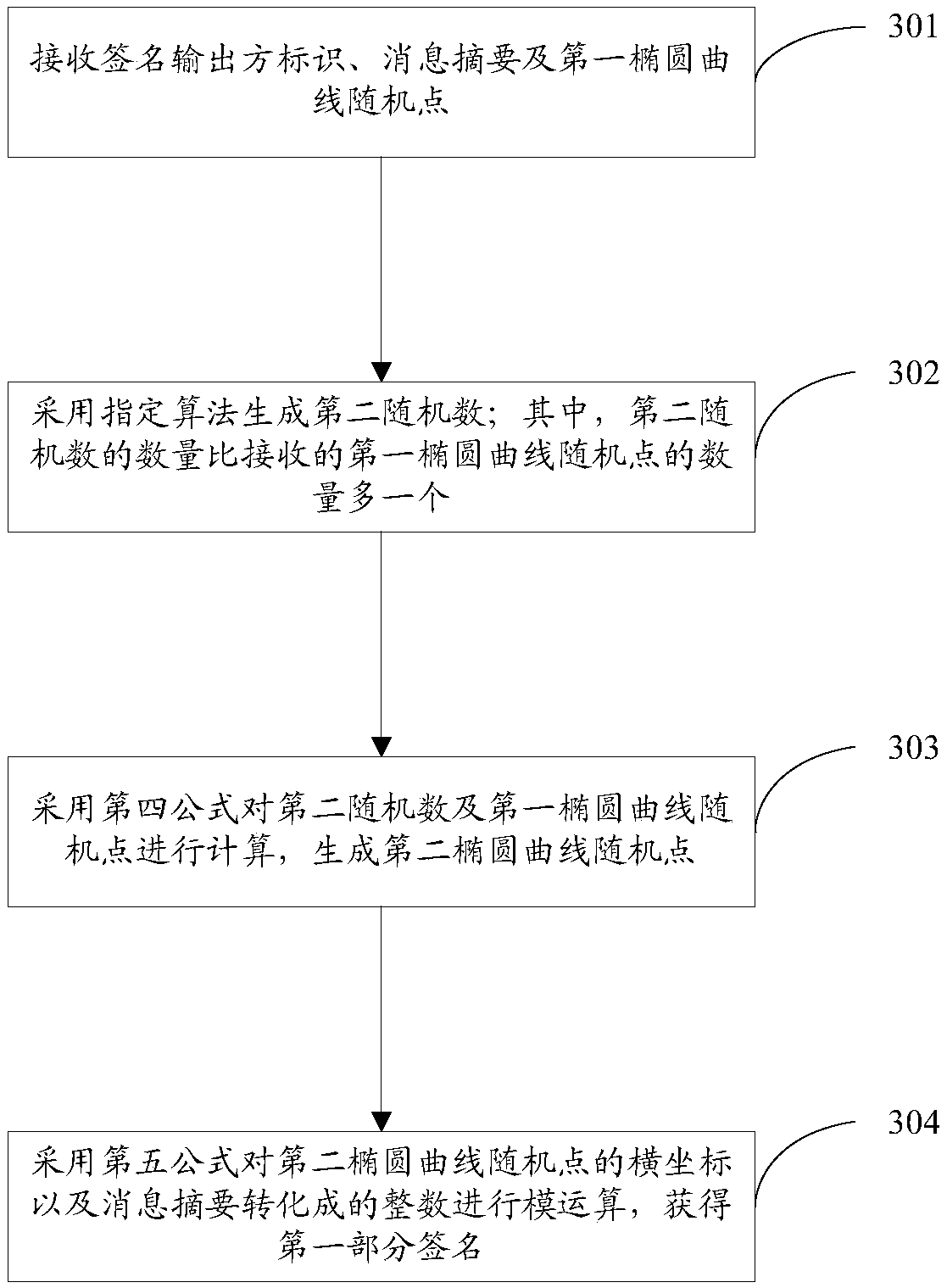
The invention discloses a signature method and device for generating an SM2 algorithm through mutual coordination, and a storage medium, and solves the problem that a user private key is easily stolenin the prior art under the condition of no cryptographic hardware. The signature method implemented by a first participant includes the steps: receiving intermediate information determined by a second participant according to a signature output party identifier; determining a participant of the complete signature of the to-be-signed message based on the signature output party identifier; generating a second partial signature of the to-be-signed message by using a first sub-private key and the intermediate information if the first participant outputs the complete signature, and outputting thecomplete signature consisting of the first partial signature and the second partial signature carried in the intermediate information; generating a first intermediate signature through the first sub-private key and the intermediate information of the second participant outputs the complete signature, and sends the first intermediate signature to the second participant, so that the second participant can generate a second partial signature of the to-be-signed message by using a second sub-private key and the first intermediate signature, so as to determine the complete signature.
Owner:北京信安世纪科技股份有限公司
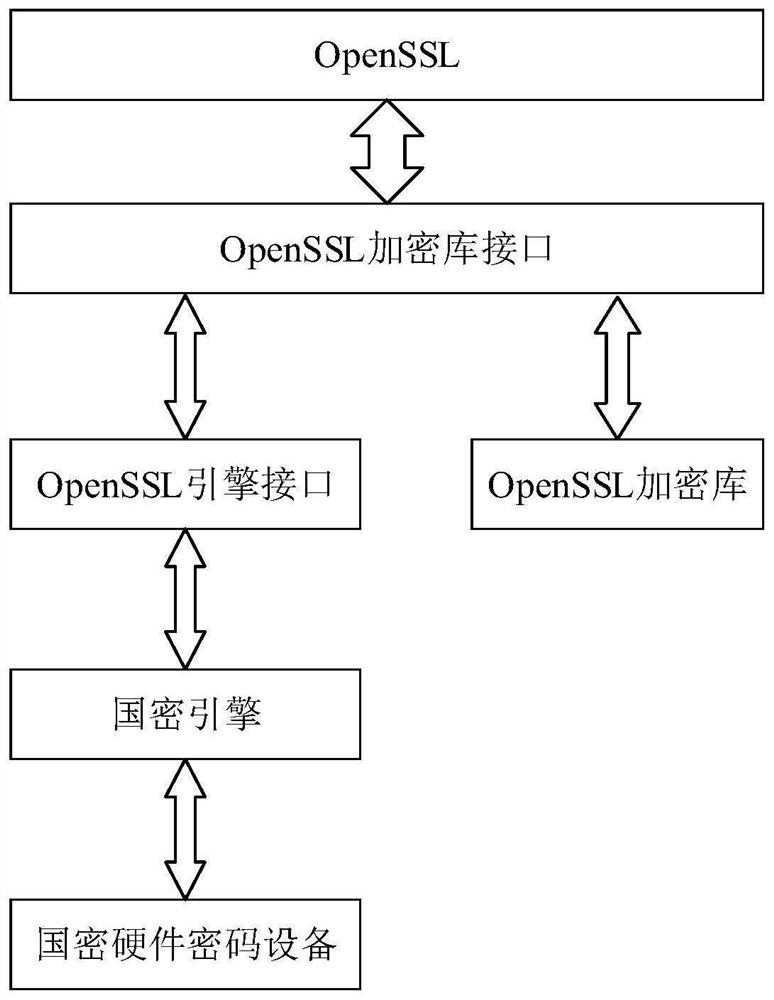
Data processing method and device based on national password, storage medium and electronic equipment
ActiveCN112398826AEasy to findEasy encryption and decryptionKey distribution for secure communicationUser identity/authority verificationComputer hardwarePassword
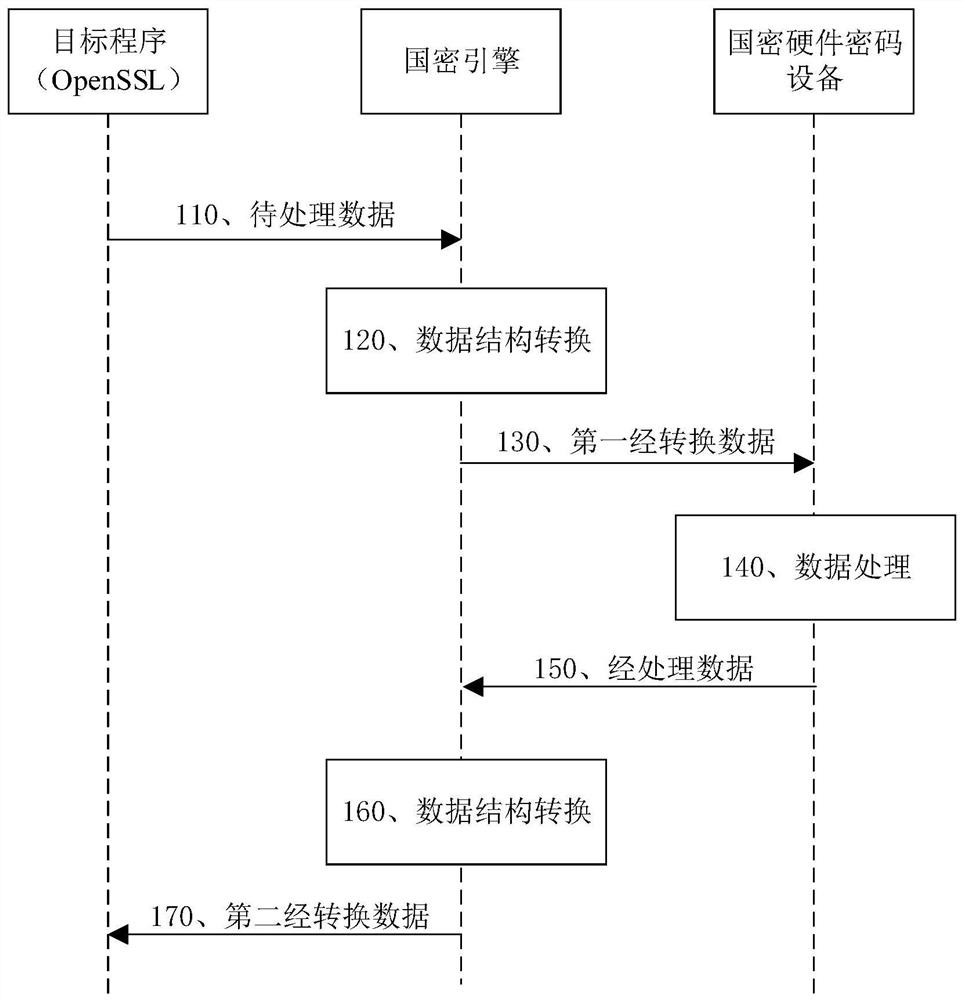
The invention relates to the technical field of network security, and provides a data processing method and device based on national secret, a storage medium and electronic equipment. The method comprises the steps of converting a data structure of to-be-processed data sent by a target program through an engine interface from a data outgoing standard structure specified by the target program intoa standard structure which can be analyzed by national cryptographic hardware cryptographic equipment to obtain first converted data; sending the first converted data to the national cryptographic hardware cryptographic equipment; converting the data structure of the processed data returned by the national cryptographic hardware cryptographic equipment from the data outgoing standard structure specified by the national cryptographic hardware cryptographic equipment into a standard structure which can be analyzed by the target program to obtain second converted data; and sending the second converted data to the target program through the engine interface, so that the target program performs a subsequent encryption communication process based on the second converted data. According to the method, the cryptographic hardware cryptographic equipment can be added into the target program through an engine mechanism, and core codes of the program do not need to be modified.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
System and method for secure verification of electronic transactions
InactiveUS8621230B2Acutation objectsDigital data protectionThird partyPersonal identification number
The present invention relates to a system and method for secure verification of electronic transactions, and in particular secure processing of personal identification numbers when third party processors are involved. In an embodiment, a variable length PIN associated with a credit card or debit card is encrypted, then hashed using a one-way hash algorithm before it is passed along to and stored by a third party processor. The encrypted-hashed PIN always remains in an encrypted form while in the hands of the third party processor. At the third party processor, secure cryptographic hardware is used to store the one-way hash algorithm. Encrypted PIN values received for verification are converted and hashed using the one-way hash algorithm, and the resulting hashed-encrypted value is compared against the hashed-encrypted PIN values previously stored at the third party processor. As the PIN has a variable length, and the third party processor has no access to the hash algorithm, the encrypted PIN values are highly resistant to reverse engineering or decryption.
Owner:INT BUSINESS MASCH CORP
Secure distribution of device key sets over a network
ActiveUS20210320789A1Key distribution for secure communicationUser identity/authority verificationEngineeringProxy server
A system is provided for distribution of device key sets over a network in a protected software environment (PSE). In the system, a client device includes a connection interface for receiving a crypto hardware (CH) token belonging to a user, untrusted software, a quoting enclave, and a PSE for generating a provisioning request for a device key set. An attestation proxy server (APS) receives the provisioning message using a first network connection, and transmits the provisioning message to an online provisioning server (OPS) using a second network connection. The OPS constructs a provisioning response and an encrypted device key set, and delivers the provisioning response to the untrusted software using the first and second network connections. The PSE decrypts the encrypted device key set to obtain the device key set, re-encrypts the device key set with a local chip-specific key, and stores the re-encrypted device key set.
Owner:ARRIS ENTERPRISES LLC
Device and Method for Hardware Timestamping with Inherent Security
ActiveUS20200036538A1Key distribution for secure communicationUser identity/authority verificationCryptographic key generationData pack
Disclosed are physical unclonable functions (“PUFs”) that provide both a hardware timestamp and an encryption key. The timestamp is more accurate than traditional timestamps generated by software calls to the computing device's operating system, while the encryption key can be used for, among other things, securing time-synchronization packets sent across a network. By combining timestamp generation with encryption key generation, the PUFs provide enhanced security while being cheaper to build and to operate than the specialized cryptographic hardware that they replace.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
Encryption method and device
InactiveUS8156328B1Easy to implementAvoiding expensive incompatibleUser identity/authority verificationPayment architectureLow speedEncrypted function
A method and a device are disclosed for the low-cost implementation even of high-performance encryption functions in an encryptor. The encryptor may be composed merely of PC software or the like, or of any other terminal / information system with integrated Vernam cipher which does not need to be supported by expensive crypto-hardware for the actual encryption process. The crypto-hardware is made either of a chipcard or a multifunctional PC interface adapter (e.g., PCMCIA module) with built-in special crypto-hardware. The encryptor, on the other hand, is a conventional personal computer, software or another terminal which, however, with the exception of the very simple Vernam cipher (e.g., EXOR), needs no further crypto-technology even for broad-band applications in software. The external crypto-modules contain all the complex crypto-functions which generate the Vernam key in reserve, the reserves being temporarily stored in an intermediate storage until they are gradually used up by the encryption process through logic operations of the method. The storage may be installed either in the PC or terminal, or also in the crypto-module. The encryptor always operates with the same Vernam cipher, even if the external crypto- or PCMCIA modules use different symmetrical and asymmetrical ciphers. External crypto-modules in the form of chipcards or PCMCIA modules are inexpensive to manufacture. All the complex crypto-functions are located outside of the encryptor. They are interchangeable by module and can be implemented in the proposed low-cost and somewhat lower-speed external crypto-modules.
Owner:DEUTSCHE TELEKOM AG
Distributed network node authentication method based on chip
ActiveCN111818074AEnsure safetyImprove securityKey distribution for secure communicationPublic key for secure communicationEngineeringNode authentication
The technical scheme of the invention discloses a distributed network node authentication method based on an encryption chip. The method comprises the following steps: a first node and a second node respectively generate a public and private key pair and a random number; the first node and the second node exchange random numbers and public key information with each other; the first node receives the second random number, processes the second random number by using the first private key and the second public key to obtain a first encrypted signature and transmits the first encrypted signature to the second node; the first node receives the second encrypted signature by using the first private key and the second public key to decrypt and obtain verification information; and if the verification results of the first node and the second node are consistent, the encrypted hardware number of the current node is bound with the current node to complete node verification. According to the distributed network node authentication method and system based on the chip provided by the invention, a hardware random number and information encryption combined method is adopted, so that the security ofidentity authentication information between different nodes in a distributed network is greatly improved.
Owner:上海朝夕网络技术有限公司
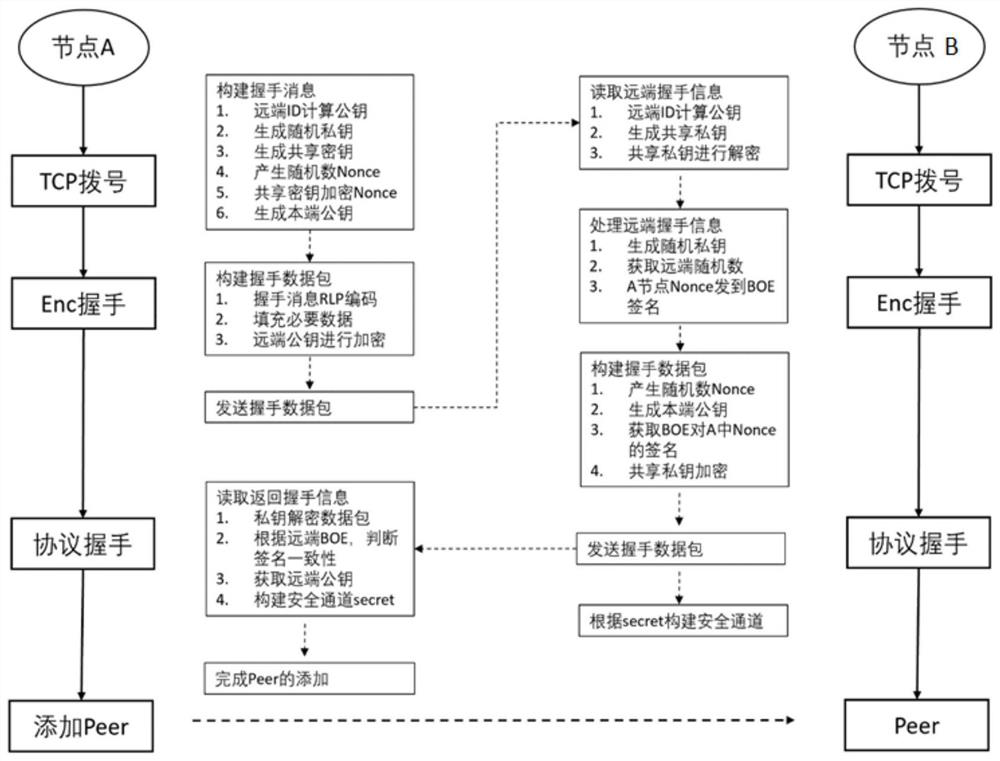
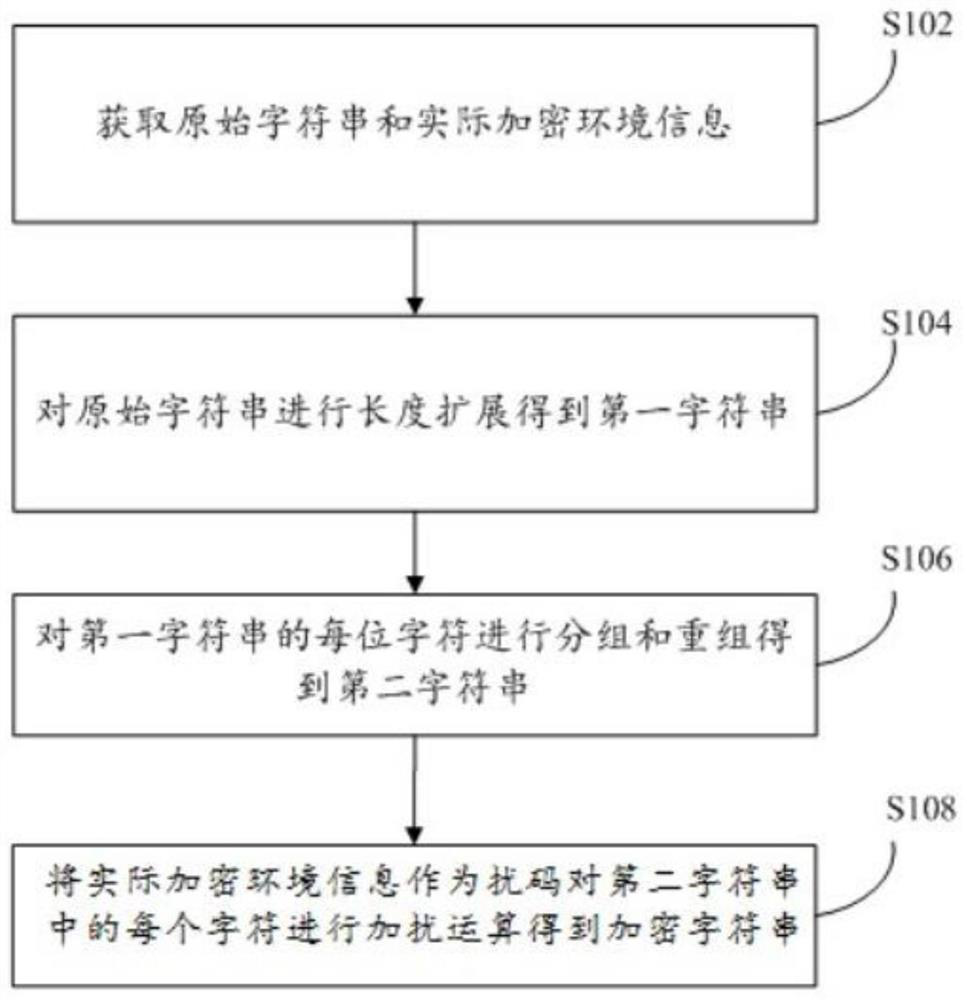
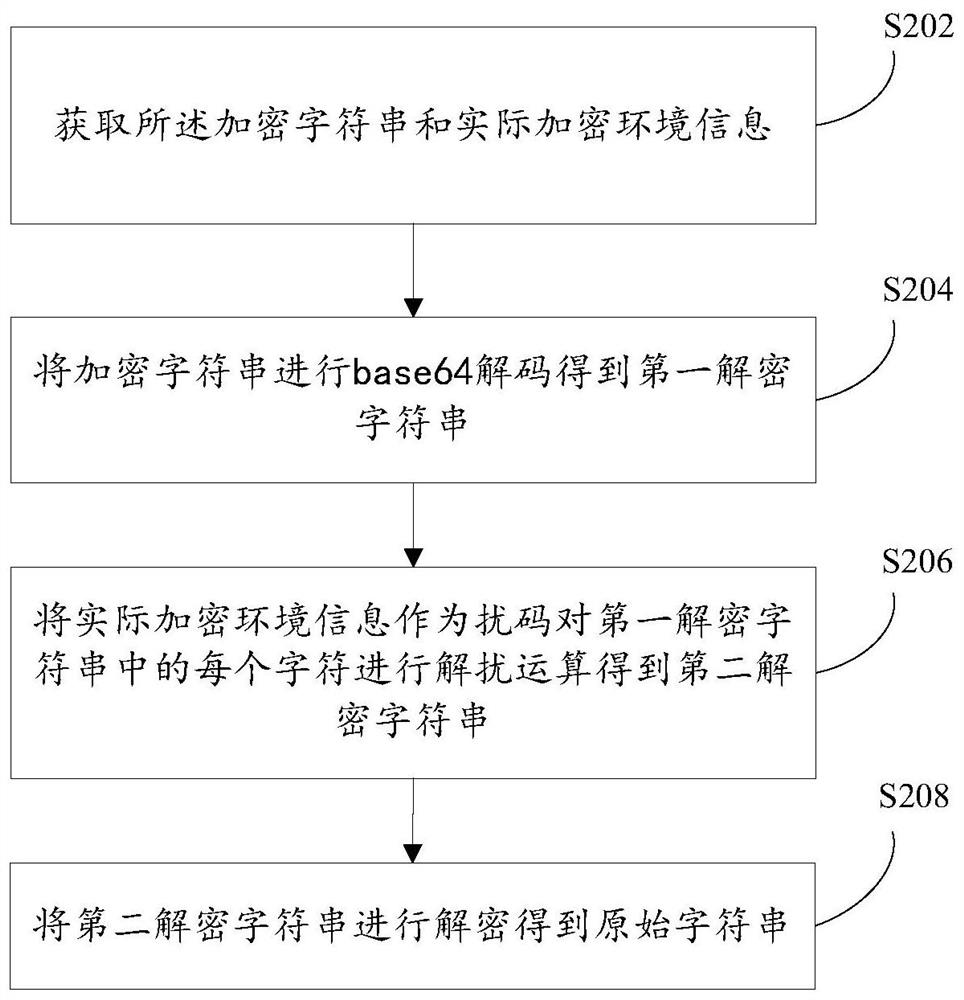
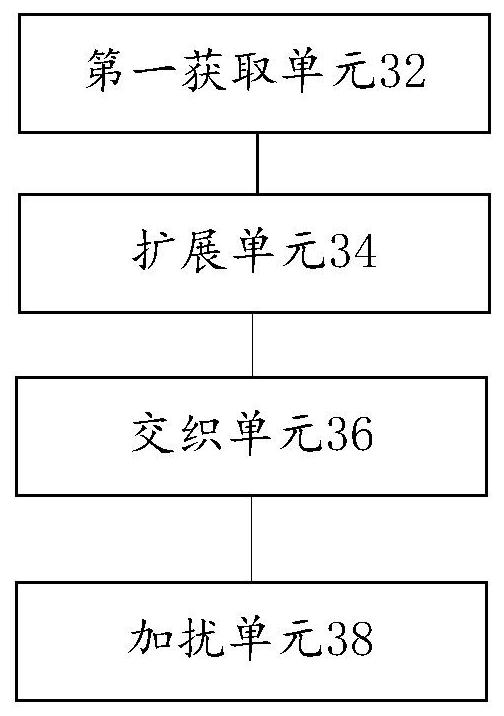
Character string encryption and decryption method and device, storage medium and processor
The invention discloses a character string encryption and decryption method and device, a storage medium and a processor. The method comprises the following steps: acquiring original character stringdata and actual encryption environment information; performing length extension on the original character string data to obtain first character string data; grouping and recombining each character ofthe first character string data to obtain second character string data; and performing operation on each character in the second character string data by taking the actual encryption environment information as a scrambling code to obtain an encrypted character string. According to the invention, the security problem that the ciphertext password is easy to crack under the condition that the plaintext password is encrypted through the ciphertext password without using an encryption function library or encryption hardware is solved.
Owner:国铁吉讯科技有限公司
Method and apparatus for enforcing a predetermined memory mapping
ActiveUS8347114B2Unauthorized memory use protectionHardware monitoringData processing systemApplication software
A system and a method are disclosed for enforcing a predetermined mapping of addresses in a physical address space to addresses in a virtual address space in a data processing system including a processor in the virtual address space and a memory in a physical address space. During the compilation and linking of an application to be run on the data processing system, in at least one embodiment, the mapping table is generated linking the virtual addresses to physical addresses. This mapping table is kept secret. A second mapping table is generated using a cryptographic function of the physical address with the virtual address as a key to link virtual addresses to intermediate addresses. The second mapping table is loaded into the memory management unit. The data processing system further includes cryptographic hardware to convert the intermediate address to the physical address using the inverse of the cryptographic function which was used to calculate the intermediate address.
Owner:NAGRAVISION SA
Data management method, device and system based on blockchain technology
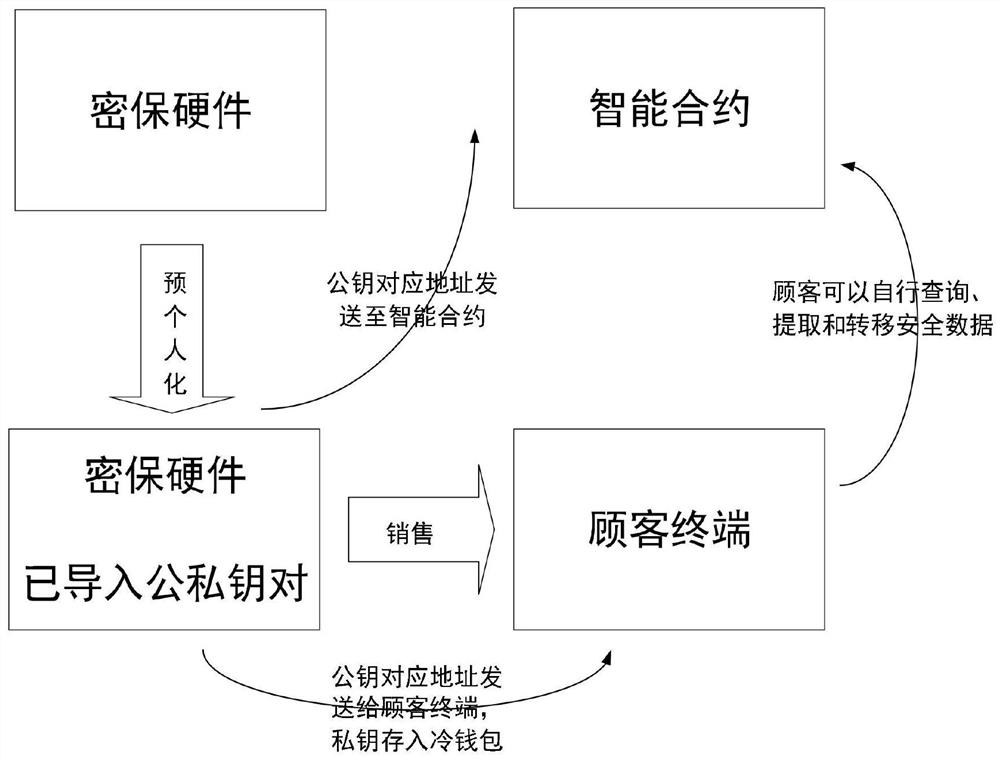
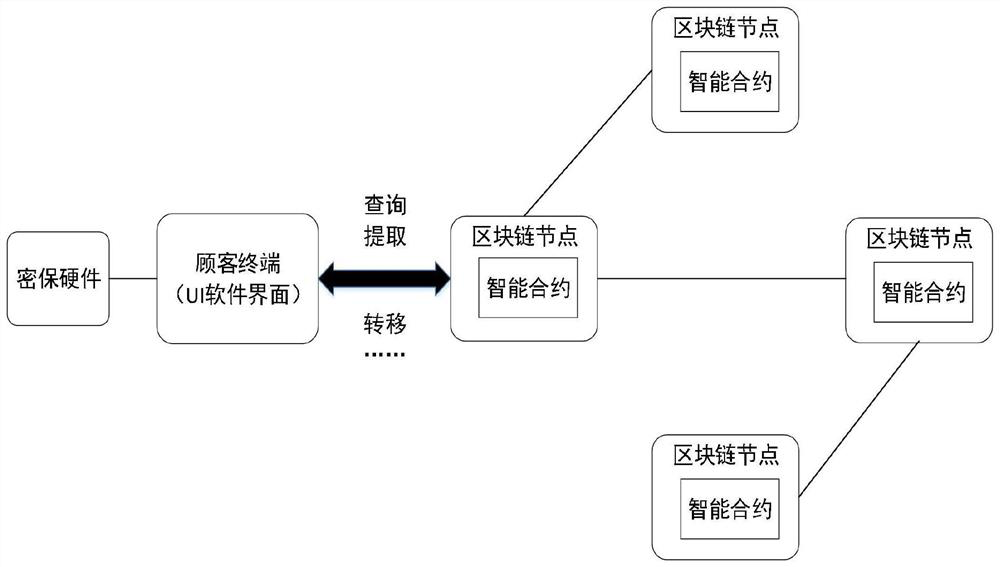
ActiveCN111737762AEnsure safetyAchieve publicityDatabase updatingDatabase distribution/replicationPassword protectionData management
The invention discloses a data management method, device and system based on a block chain technology. The system comprises password protection hardware, a customer terminal, an intelligent contract and intelligent contracts in other blockchain nodes in a blockchain network. The encryption hardware comprises a key storage module, an export module and a signature module; the intelligent contract comprises an address import module, a verification module and an operation notification module; and the customer terminal is connected with the password protection hardware and the intelligent contractto achieve data interaction between the password protection hardware and the intelligent contract in the blockchain node. According to the method, a private key in cryptographic hardware is used as averification key for data management, so that the data security is ensured; and an address generated by a factory public key is used for ensuring that customers participate in the full life cycle of data management, so that the publicity and transparency of the data are further realized.
Owner:JIANGSU HENGBAO INTELLIGENT SYST TECH CO LTD
Device and method for hardware timestamping with inherent security
ActiveUS10778451B2Key distribution for secure communicationUser identity/authority verificationCryptographic key generationData pack
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
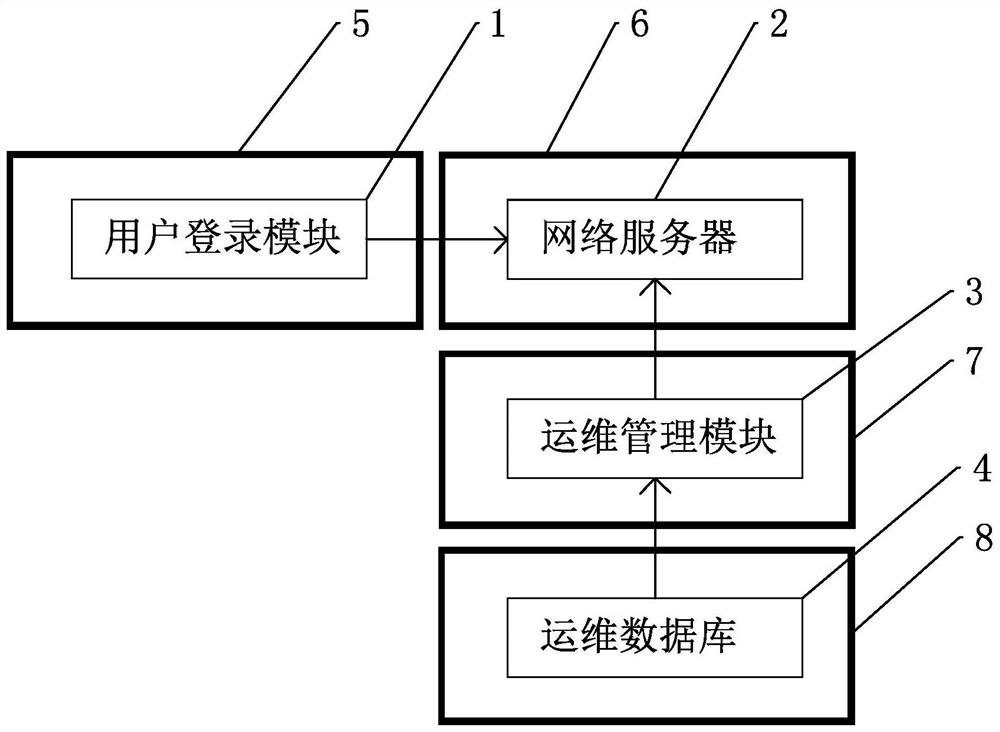
System security architecture based on SaaS platform
InactiveCN111756765AHigh level of data isolationImprove securityTransmissionSecurity complianceEngineering
The invention discloses a system security architecture based on an SaaS platform. The system security architecture comprises a user login module, a network server, an operation and maintenance management module and an operation and maintenance database, wherein the user login module is provided with an access control layer, and access control comprises identity authentication and authority management; the network server is provided with a security compliance layer, and the security compliance layer conforms to a GDPR; the operation and maintenance management module is provided with a management protection layer, and the management protection layer comprises a bastion host, a WAF and the like; and the operation and maintenance database is provided with an SSL encryption layer which comprises data encryption and decryption, file encryption and decryption service, cloud disk encryption, DLP, a hardware encryption machine, intrusion prevention and the like. The system security architecturesets the independent security protection layers respectively according to the main architecture of the SaaS system, and the independent databases are adopted among tenants on the platform, so that the user data isolation level is high, and the security is good.
Owner:无锡启创梦网络科技有限公司
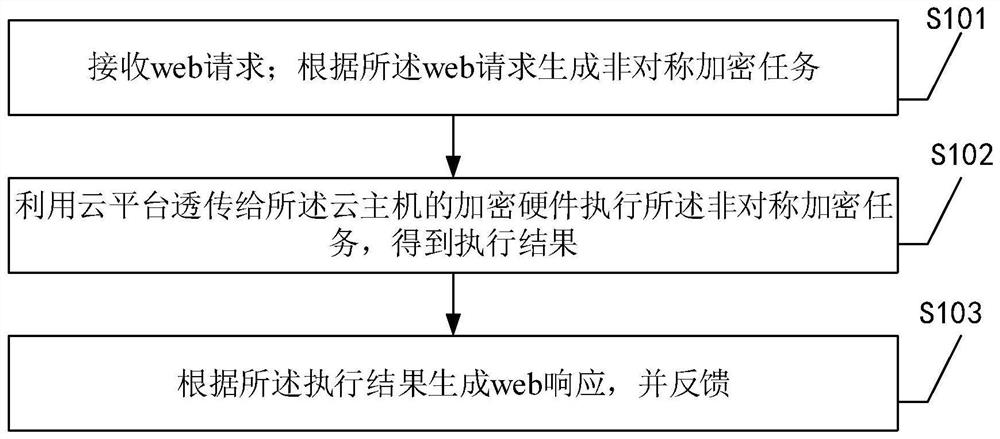
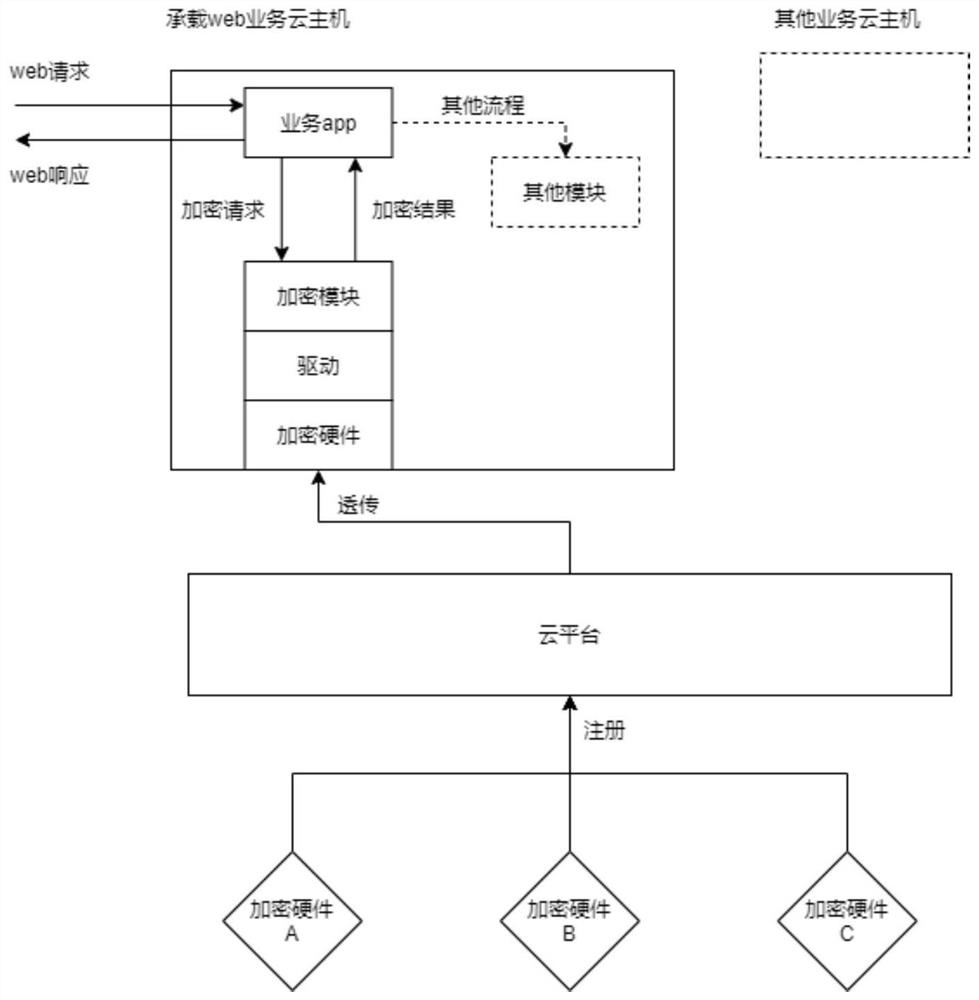
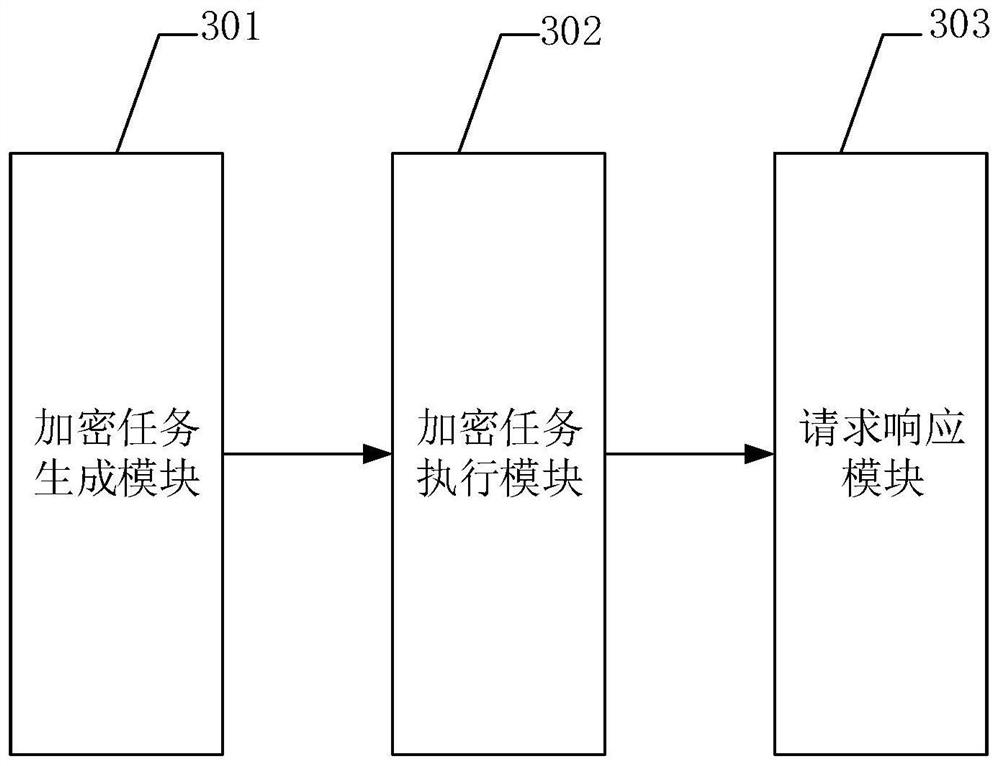
Request processing method, device, equipment and system for web server
ActiveCN112637201AImprove service efficiencyFast executionTransmissionEnergy efficient computingWeb applicationWeb service
The invention discloses a request processing method of a web server, which is applied to a cloud host and includes following steps: generating an asymmetric encryption task according to a web request after receiving the web request; executing the asymmetric encryption task by utilizing encryption hardware transparently transmitted to the cloud host by the cloud platform to obtain an execution result; and finally, generating a web response according to an execution result, and feeding back. Therefore, according to the method, the encryption process is transferred to the hardware equipment from the web application program, the burden of the CPU can be reduced while the data transmission security is ensured, the execution speed of the asymmetric encryption algorithm is increased, and the web service efficiency is improved. In addition, the invention further provides a request processing device, equipment and system of the web server and a readable storage medium, and the technical effect of the request processing device, equipment and system corresponds to the technical effect of the method.
Owner:北京浪潮数据技术有限公司
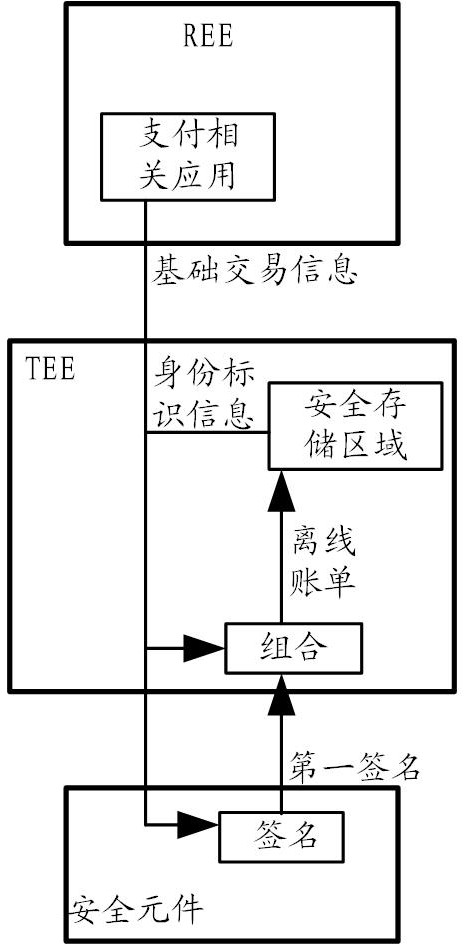
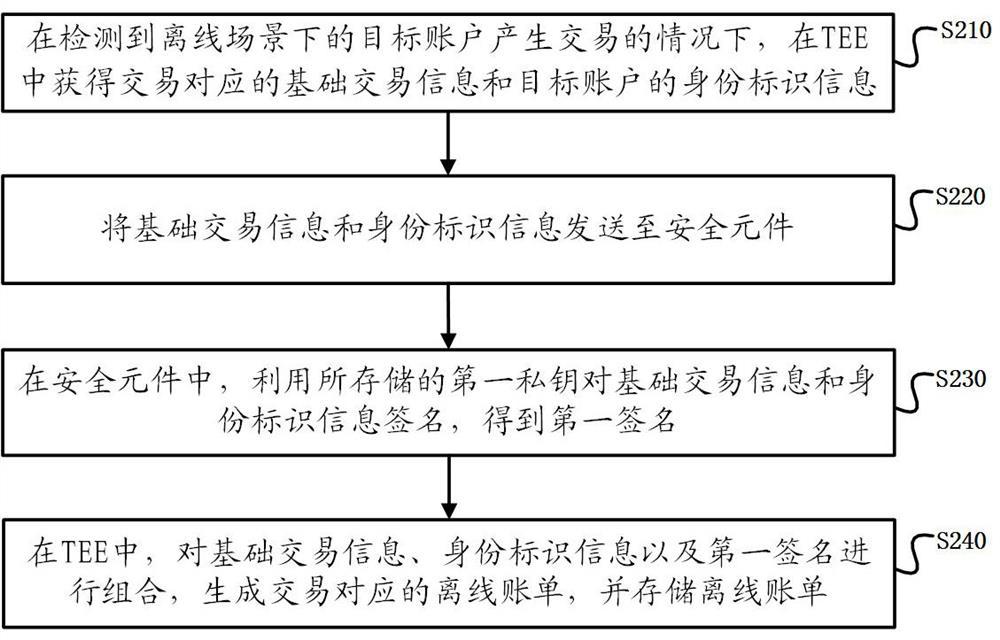
Offline bill generation method and device
ActiveCN113298526AEfficient storageEfficient managementPayment protocolsTerminal equipmentFinancial transaction
The embodiment of the invention provides an offline bill generation method and device, and the method comprises the steps that a terminal device comprises a trusted execution environment (TEE) and a security element based on encryption hardware, and the terminal device obtains basic transaction information corresponding to the transaction and identity identification information of the target account in the TEE under the condition that the terminal device detects that a target account generates a transaction in an offline scene; the basic transaction information and the identity identification information are sent to a secure element; in the secure element, the basic transaction information and the identity information are signed by using a stored first private key to obtain a first signature; and in the TEE, the basic transaction information, the identity identification information and the first signature are combined, an offline bill corresponding to the transaction is generated, and the offline bill is stored.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
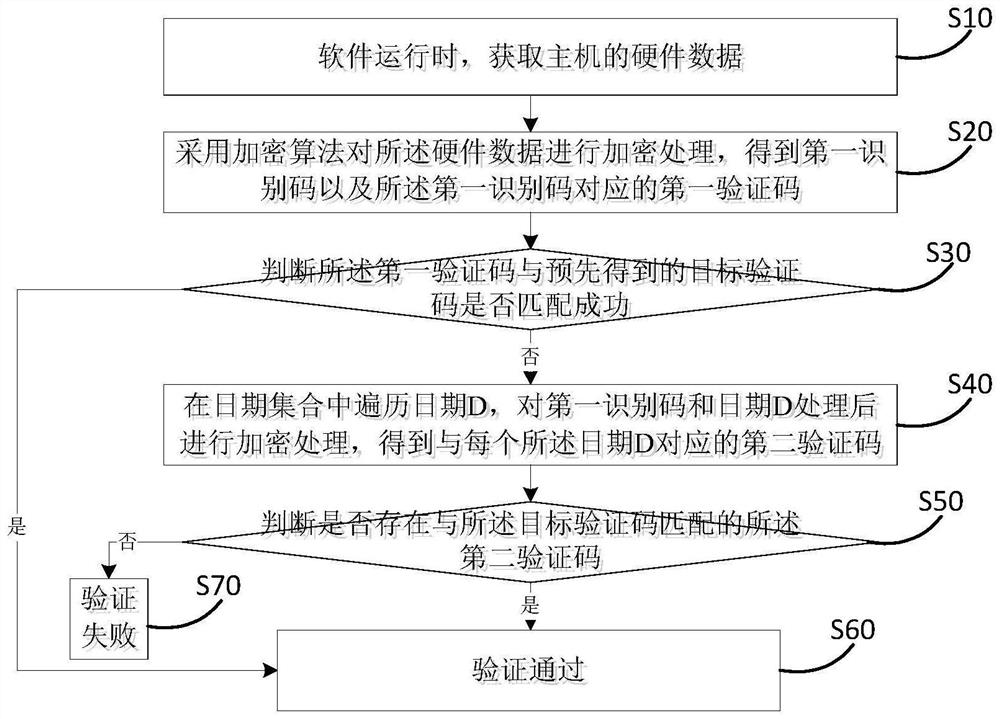
Software security and software validity period verification method and system
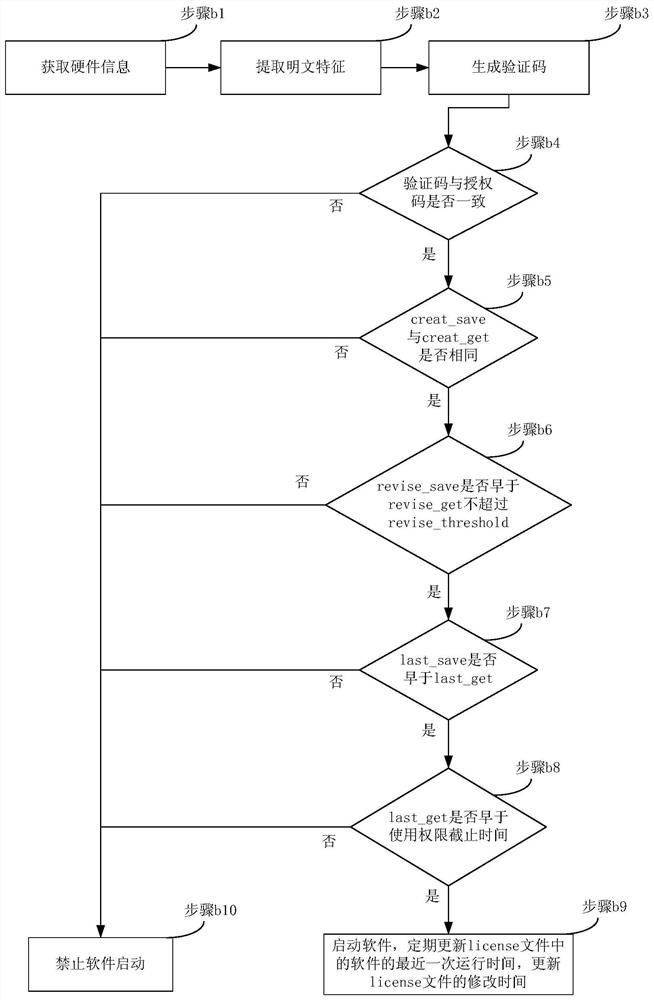
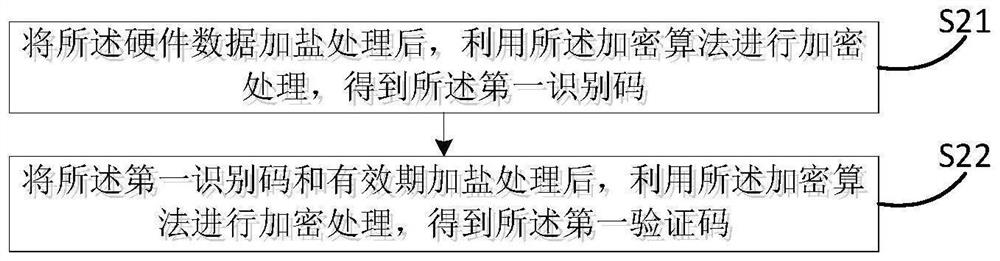
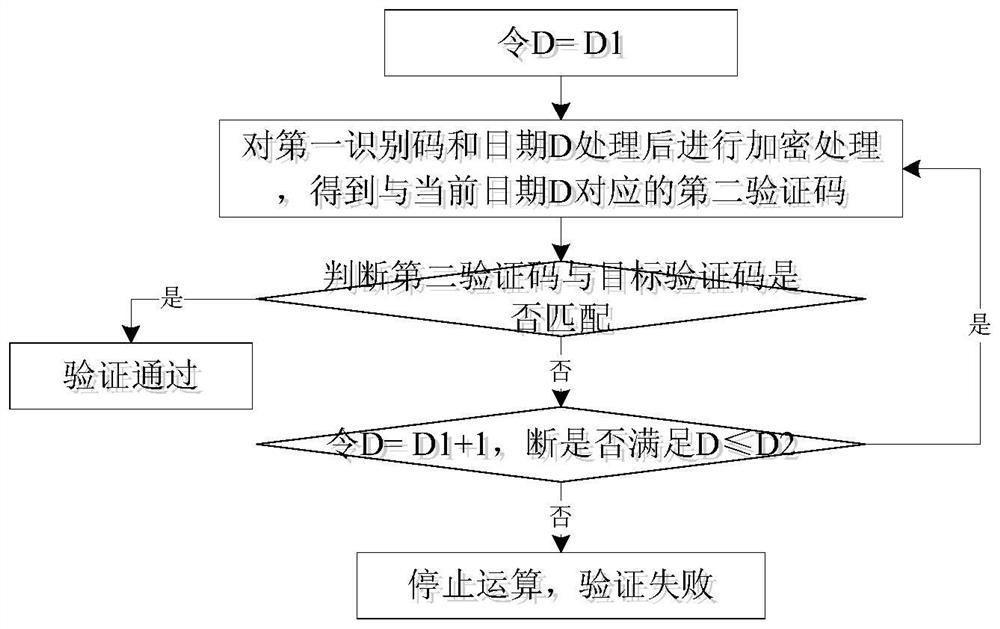
PendingCN114707122AConvenient verificationLow costDigital data protectionPlatform integrity maintainanceVerificationDatabase
The invention discloses a software security and validity period verification method and system, and the method comprises the steps: obtaining hardware data of a host when software runs; encrypting the hardware data by adopting an encryption algorithm to obtain a first identification code and a first verification code corresponding to the first identification code; judging whether the first verification code is successfully matched with a pre-obtained target verification code or not; if yes, verification is passed, otherwise, dates D are traversed in a date set, the first identification code and the dates D are processed and then encrypted, a second verification code corresponding to each date D is obtained, D belongs to [D1, D2], D is a positive integer, D2 is larger than or equal to D1, D1 is the current date of the system, and D2 is the expiration date of the validity period of the software; judging whether a second verification code matched with the target verification code exists or not; if yes, determining that the verification is passed, and if not, determining that the verification fails. According to the method, additional encryption hardware is not needed, the cost is reduced, the period is short, and verification of software in environments such as medical scenes which cannot be connected with an external network is facilitated.
Owner:合肥泽康电子科技有限公司
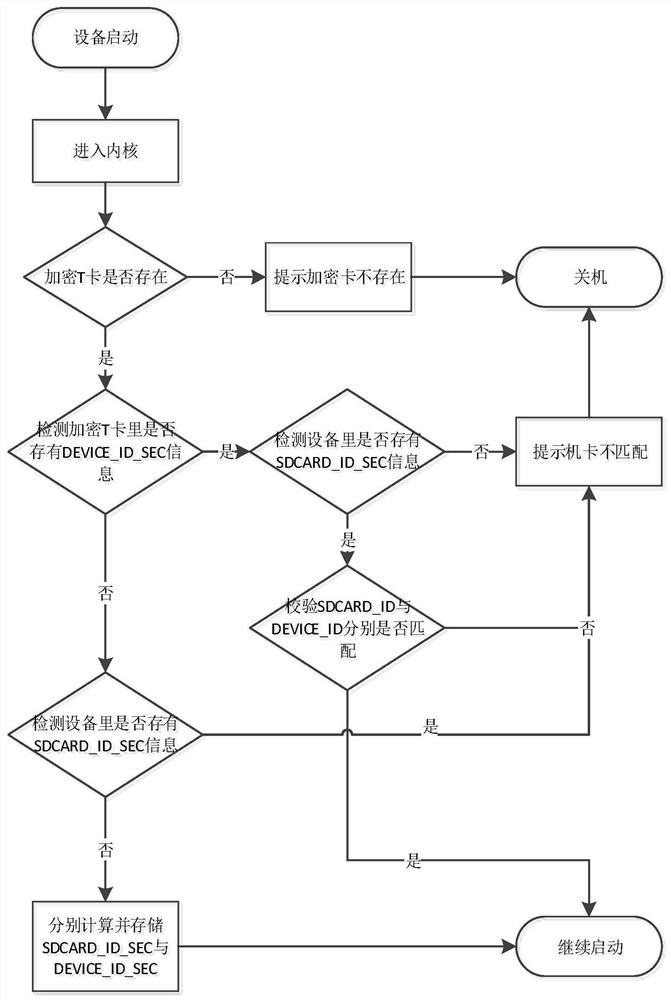
Equipment security management method based on encryption hardware
ActiveCN113901529AImplement one-to-one bindingImprove securityInternal/peripheral component protectionComputer hardwareSecurity management
The invention discloses an equipment security management method based on encryption hardware, which comprises the following steps of: S1, detecting whether equipment unique identification DEVICE_ID information is stored in the encryption hardware or not, and detecting whether encryption hardware unique identification SDCARD_ID information is stored in a sec-id partition of the equipment or not; S2, if neither the DEVICE_ID information nor the SDCARD_ID information exists, binding the encryption hardware with equipment, and continuing to start the equipment after binding; and S3, if the DEVICE_ID information or the SDCARD_ID information does not exist, or both the DEVICE_ID information and the SDCARD_ID information exist but the information is not matched, indicating that the encryption hardware cannot be matched with the equipment, shunting down the equipment, and if the information is matched, continuing to start the equipment. According to the equipment security management method, the starting process of the equipment is reconstructed based on t e hardware encryption hardware, one-to-one binding of the encryption hardware and the equipment is realized, the system can be normally started under the condition that the encryption hardware held by the user is matched with the equipment, and the safety of the starting process of the equipment is effectively improved.
Owner:上海盛本智能科技股份有限公司
Network security management method and server
Owner:LENOVO (BEIJING) LTD
Portable high-speed stream encryption hardware device and method
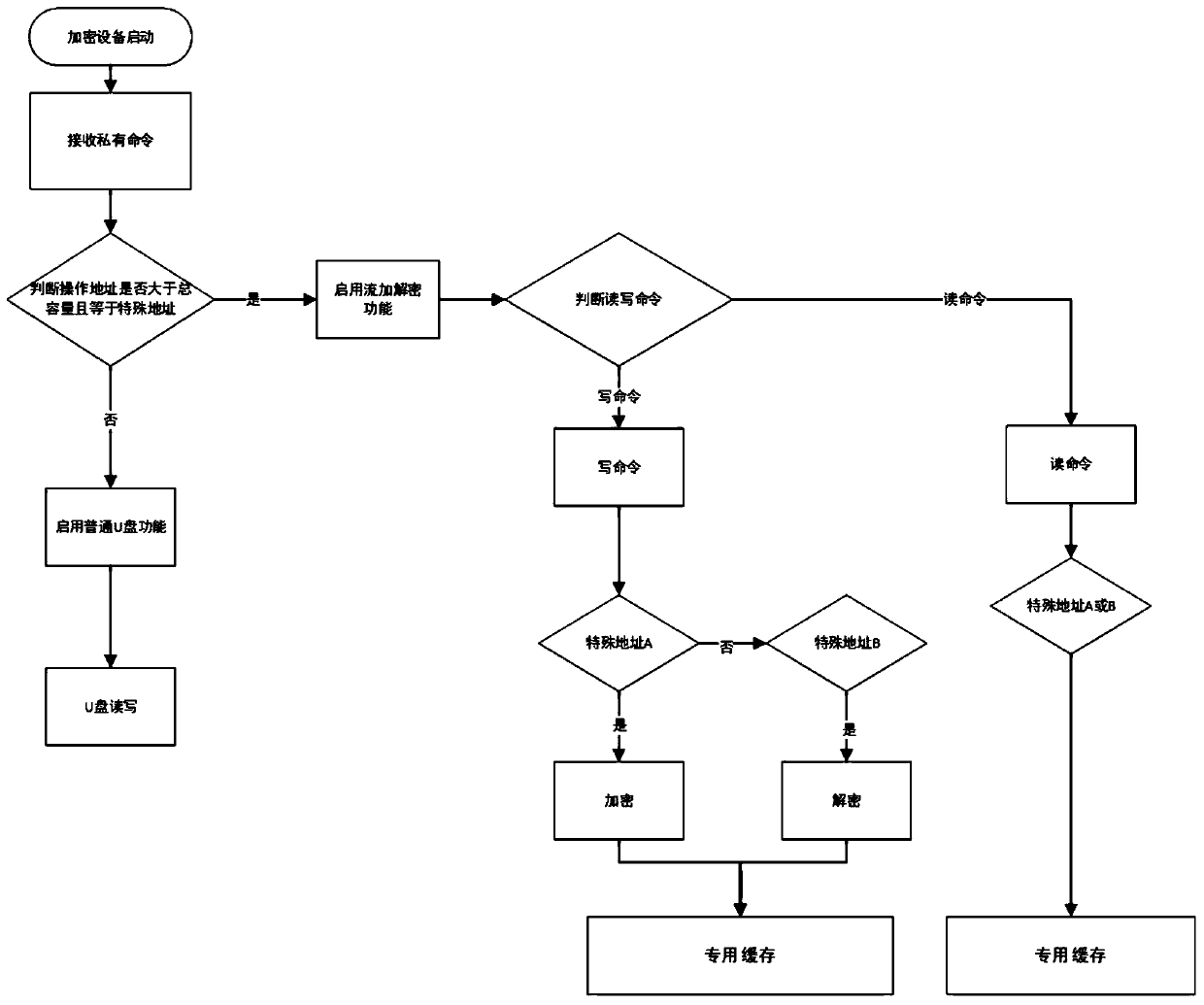
PendingCN111159783AGuaranteed fluencyImprove data securityDigital data protectionInternal/peripheral component protectionComputer hardwareFile system
The invention discloses a portable high-speed stream encryption hardware device and method. The method comprises the following steps of storing an encrypted ciphertext file and data into a hidden partition of encryption hardware equipment; wherein the hidden partition is invisible at the host end, so that the security of files stored in the hidden partition is ensured, matching the special file system with an encryption module and a decryption module to realize the process of stream encryption and stream decryption, the encryption capability of the hardware cryptographic equipment to data is improved, and the security of file data is improved.
Owner:TIH MICROELECTRONIC TECH CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com