Signature method and device for generating SM2 algorithm through mutual coordination, and storage medium
A two-party, algorithmic technology, applied in the field of information security and cryptography, can solve the problem that the user's private key is easy to be stolen
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
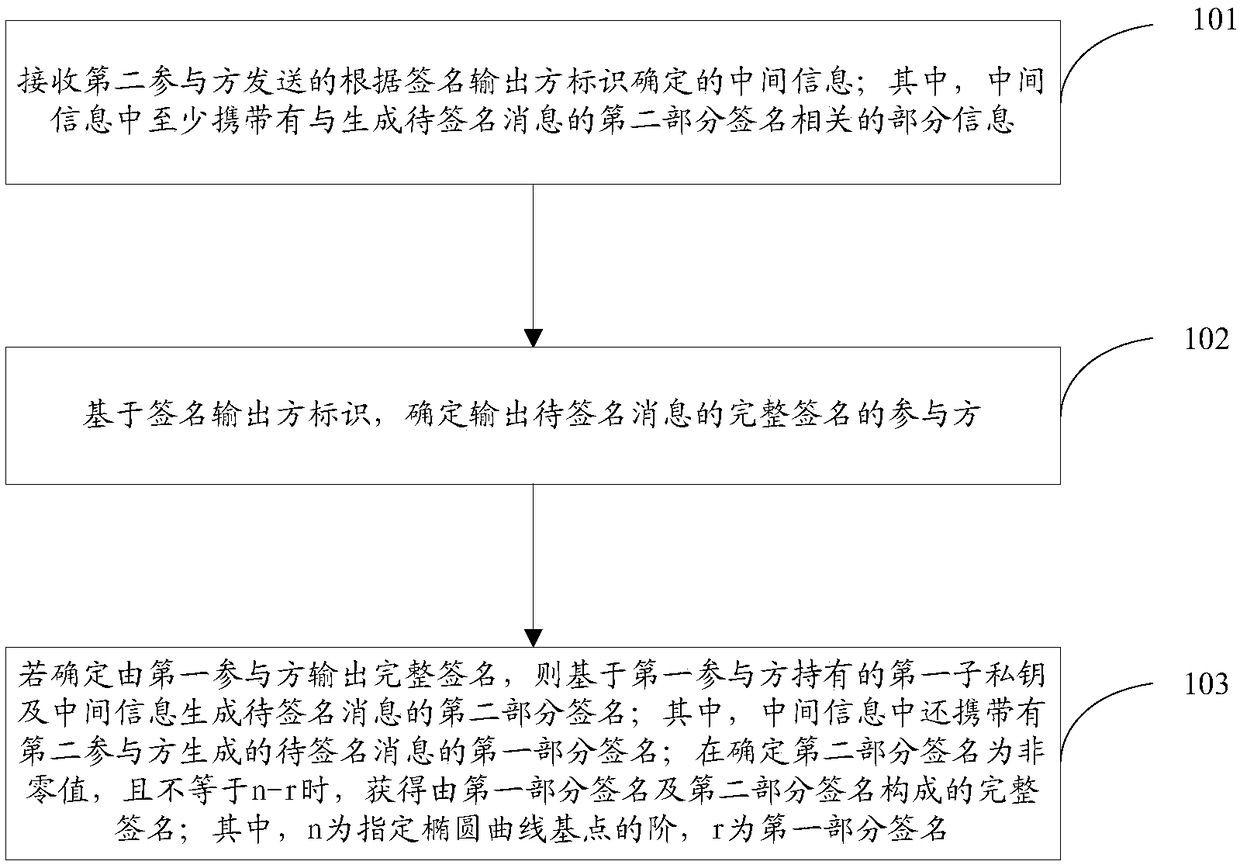
[0148] The embodiment of the present invention provides a signature method, device and storage medium for both parties to collaboratively generate the SM2 algorithm to solve the technical problem in the prior art that the user's private key is easily stolen without using cryptographic hardware.
[0149] The technical solutions in the embodiments of this application are to solve the above-mentioned technical problems, and the general idea is as follows:
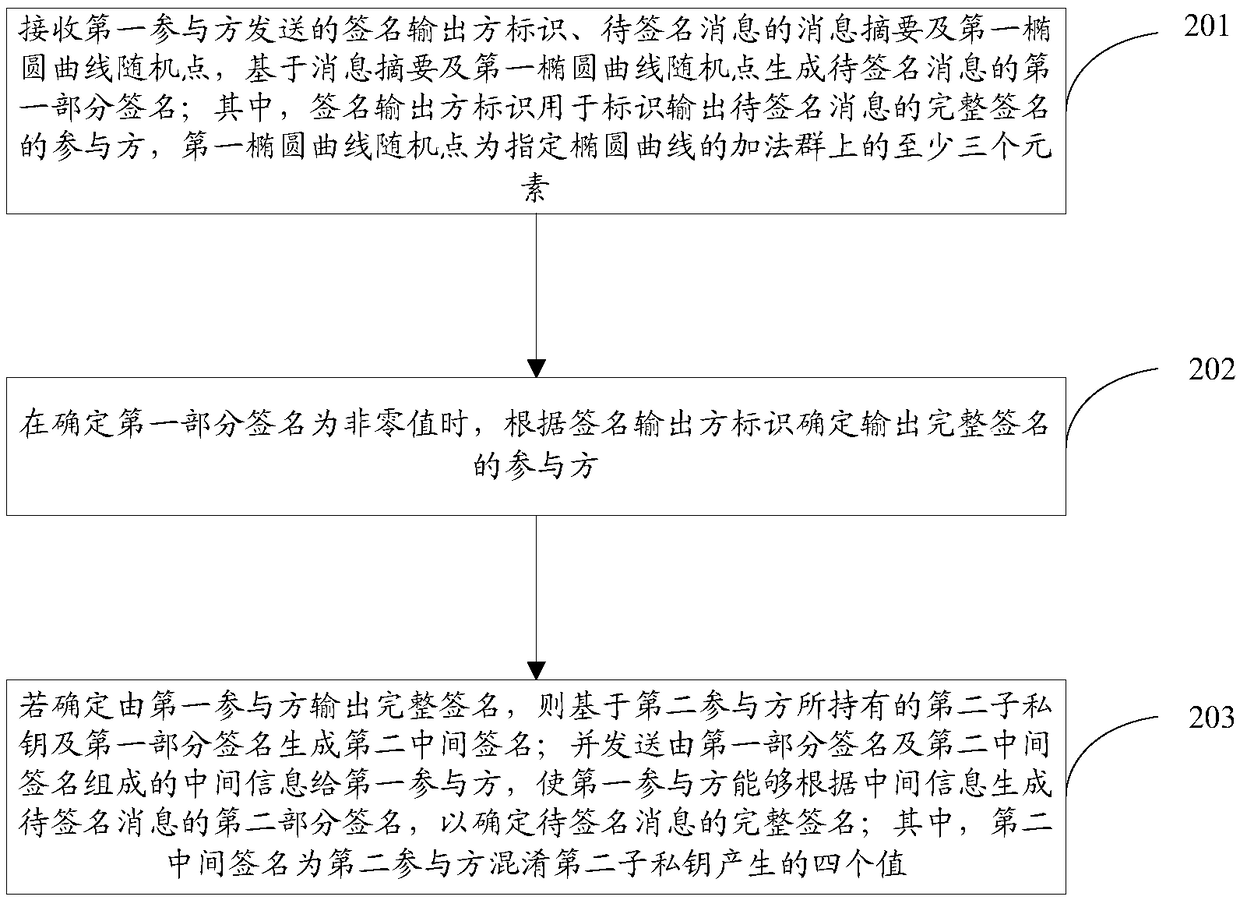
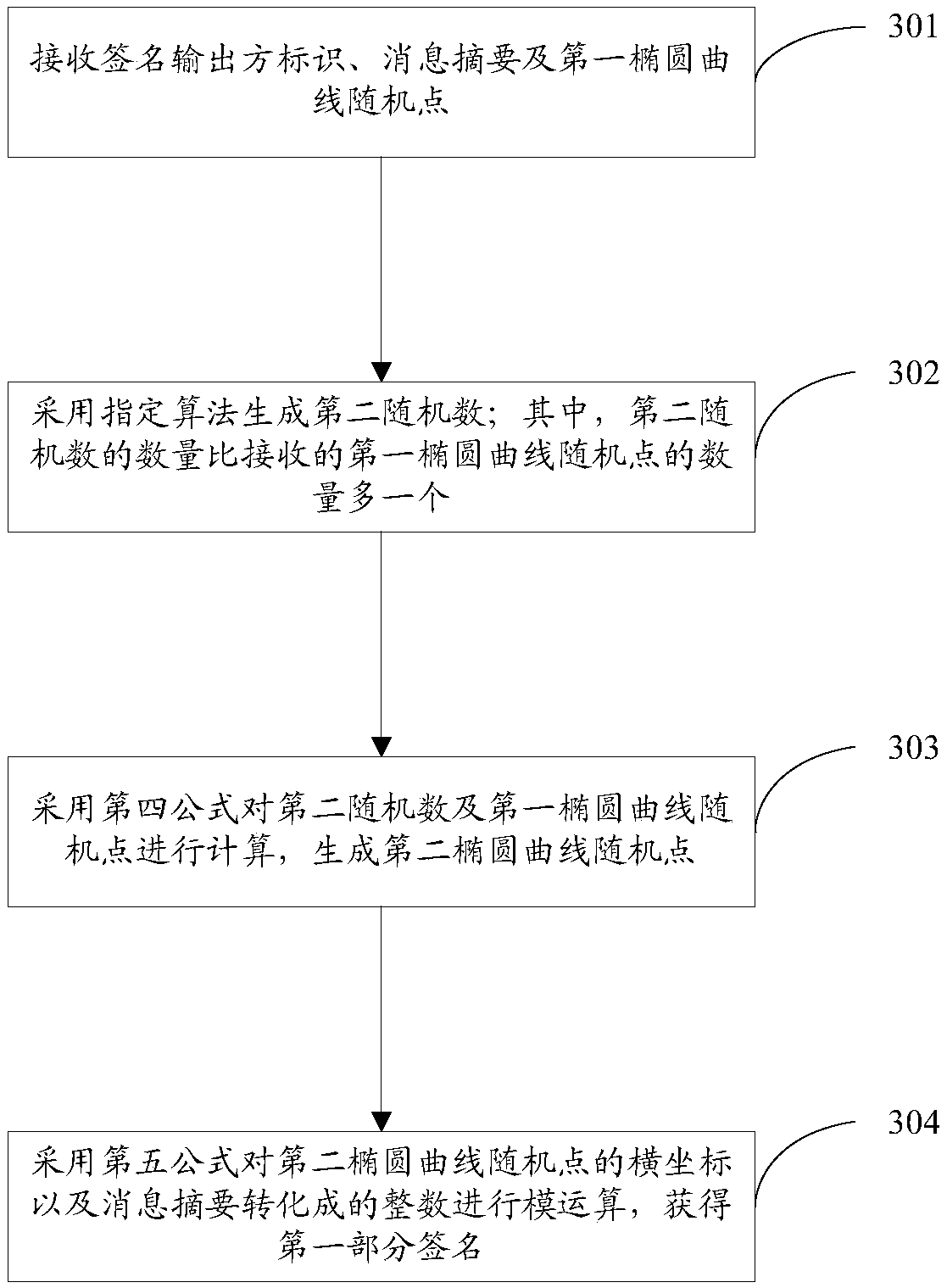
[0150] Provide a signature method for both parties to collaboratively generate the SM2 algorithm, including: receiving the intermediate information sent by the second participant and determined according to the signature output party identifier; wherein the intermediate information carries at least the part related to the generation of the second part signature of the message to be signed Information; Based on the signature output party identification, determine the participant who outputs the complete signature of the message to be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com