Network security management method and server
A management method and network security technology, applied in the network security management method and the server field, can solve problems such as threats to the data security of big data systems, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
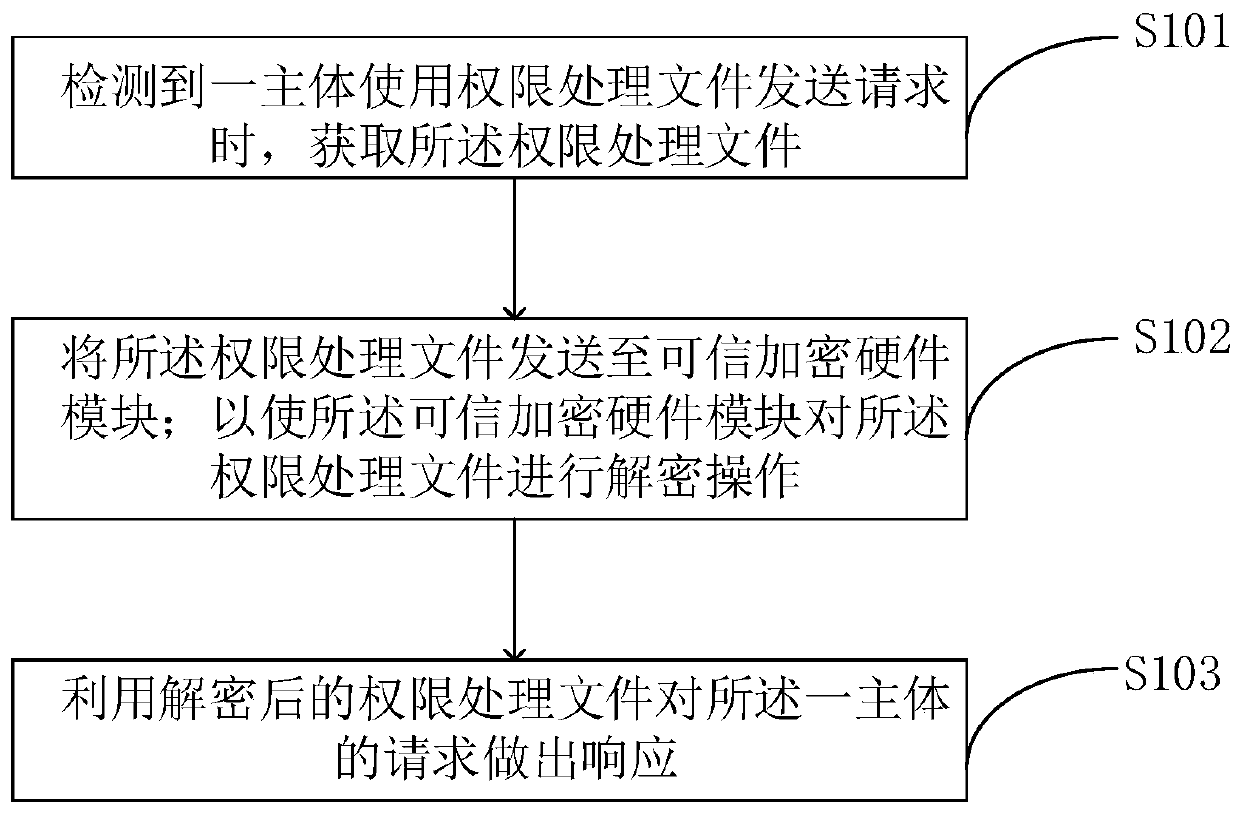
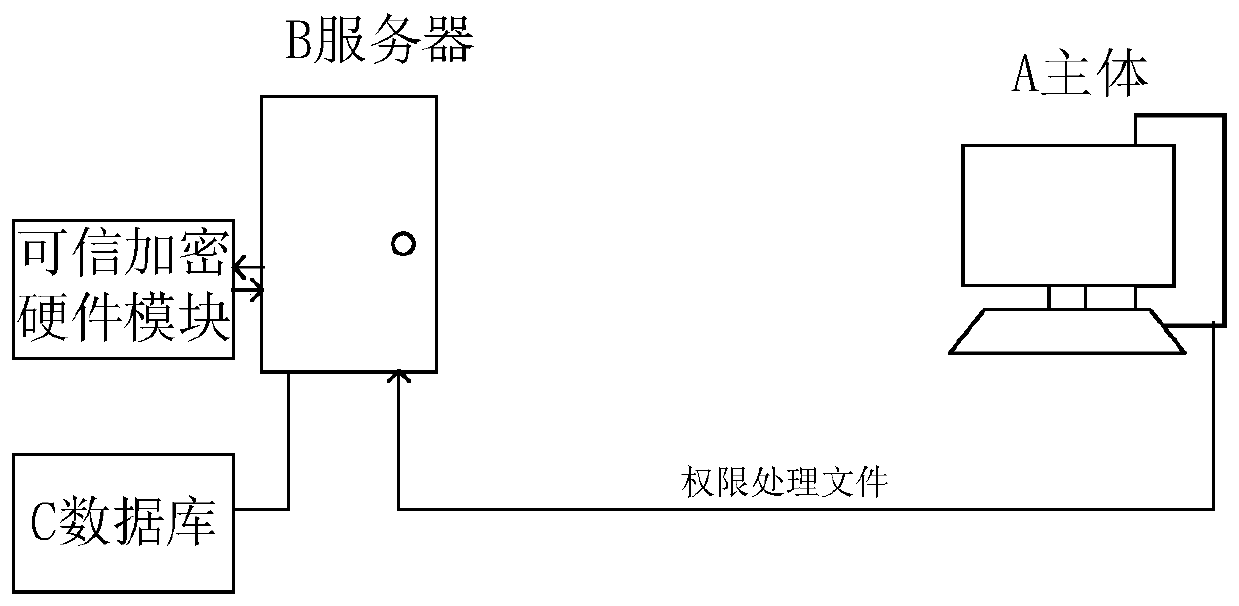
[0051] This embodiment provides a method for network security management. Specifically, the method is applied to a large data cluster, where there are multiple principles (principles), where the principals may be servers, and the principals can communicate with each other. When the current cluster management platform manages the authority of each subject, it mainly stores the subject's authority processing file in the database. When any subject wants to use the authority processing file to operate, it needs to verify the authority processing file. That is, when the server detects that a subject uses the permission processing file to send a request, it obtains the permission processing file, and sends the permission processing file to the trusted encryption hardware module; Decryption operation: if the authority processing file can be decrypted, it means that the subject has the request authority, and respond to the subject's request. Since the trusted encryption hardware modul...
Embodiment 2
[0065] Based on the method described in Embodiment 1, this embodiment provides several specific ways to verify the subject.
[0066] Mode 1, before the server invokes the trusted encryption hardware module to decrypt the authority processing file, it also needs to perform identity verification on sending the request to determine whether the request is legal. Obtain a first judgment result according to the identity authentication information of the request; when the first judgment result shows that the request has legal identity authentication information, the trusted and encryptable hardware module decrypts the authority processing file . For example, in one of the application scenarios, the request has timed out, and the server may not respond to the timed-out request.
[0067] Method 2: After judging that the request is legal, the server also needs to judge whether the request has access rights, that is to say, verify the access rights of the request and obtain a second jud...
Embodiment 3
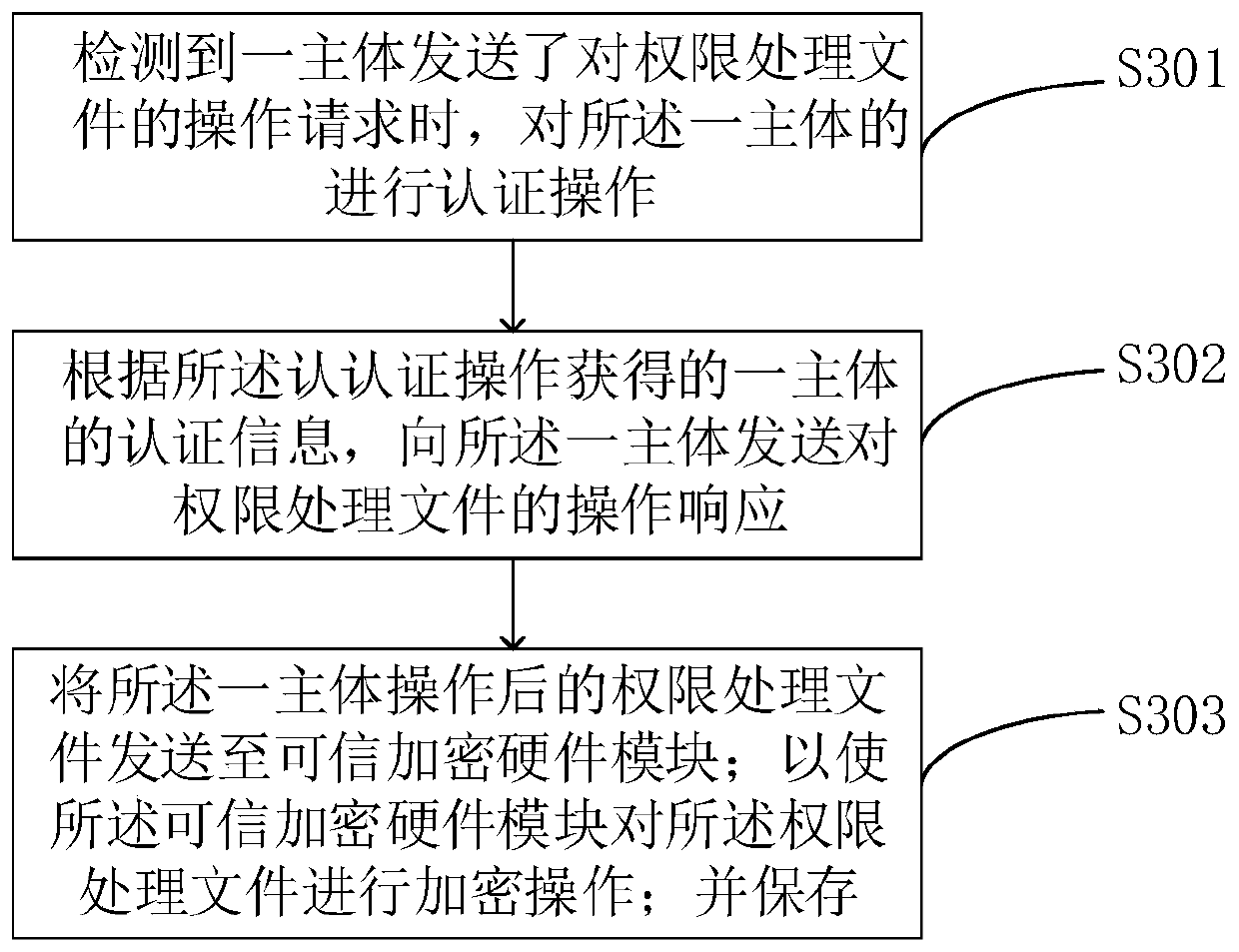
[0072] This embodiment provides a method for network security management. Specifically, the method is applied to a large data cluster, where there are multiple principles (principles), where the principals may be servers, and the principals can communicate with each other. When the current cluster management platform manages the authority of each subject, it mainly stores the subject's authority processing file in the database. When any subject wants to use the authority processing file to operate, it needs to verify the authority processing file. That is, when the server detects that a subject uses the permission processing file to send a request, it obtains the permission processing file, and sends the permission processing file to the trusted encryption hardware module; Decryption operation: if the authority processing file can be decrypted, it means that the subject has the request authority, and respond to the subject's request. Correspondingly, for the subject side, befo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com