Portable high-speed stream encryption hardware device and method
A hardware device and stream encryption technology, applied in computer security devices, computer parts, internal/peripheral computer component protection, etc., can solve the problems of single function, large size, high cost, etc., to ensure security, improve data security, The effect of ensuring fluency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
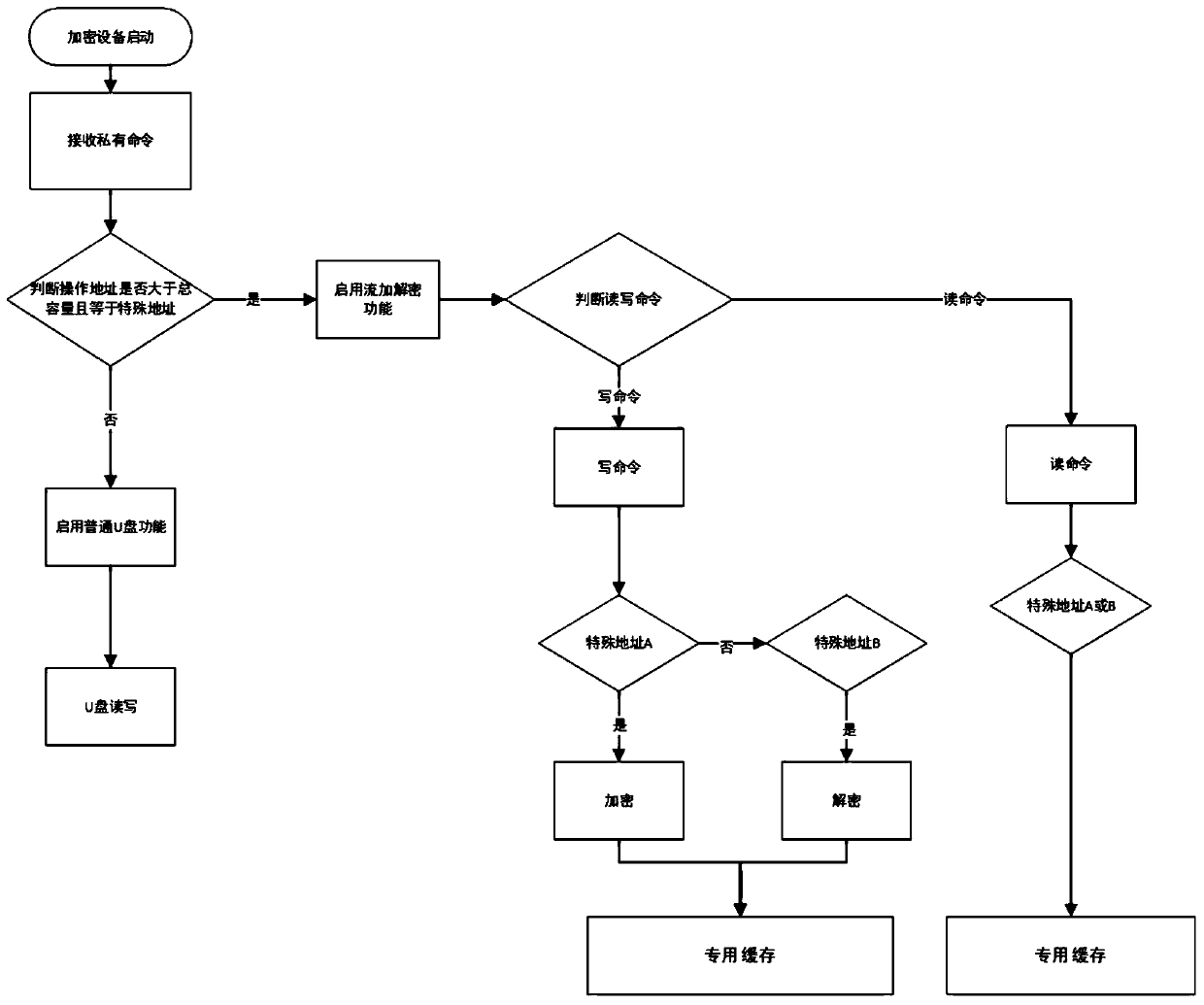
[0036] In a typical implementation of the present application, such as figure 1 As shown, a portable high-speed stream encryption hardware device is proposed.
[0037] This application is mainly used for file encryption, decryption and storage on the PC side. The stream encryption hardware device is only the size of an ordinary U disk and is easy to carry. Use the USB interface to connect with the PC (host side), which can be plug-and-play. The encrypted ciphertext files and ciphertext data are automatically stored in the hidden partition of the hardware device by the host computer. The hidden partition is invisible on the PC side and must be accessed using a dedicated file system to ensure the security of files stored in the hidden partition.
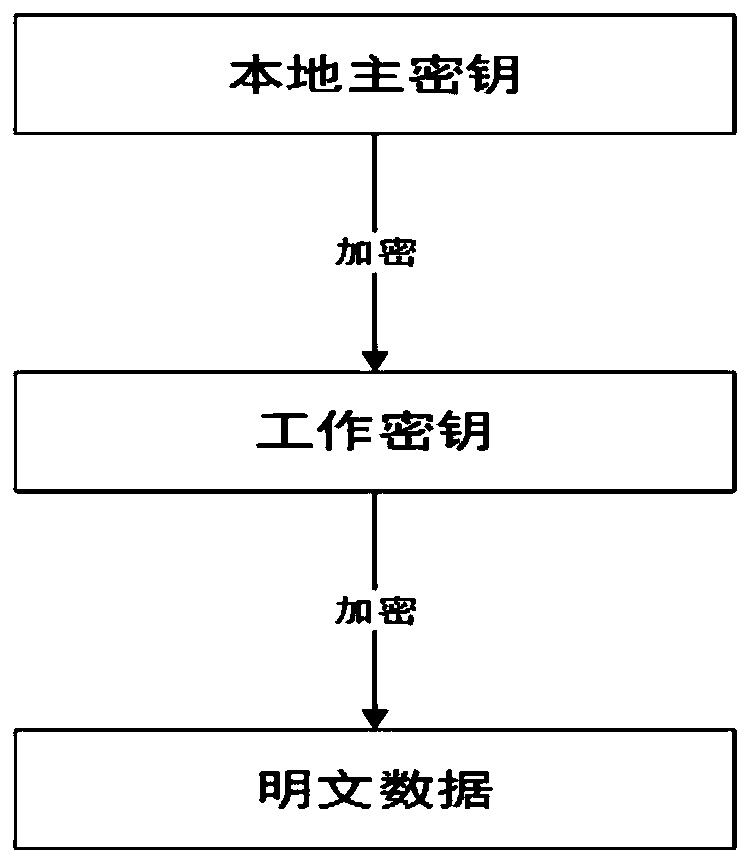
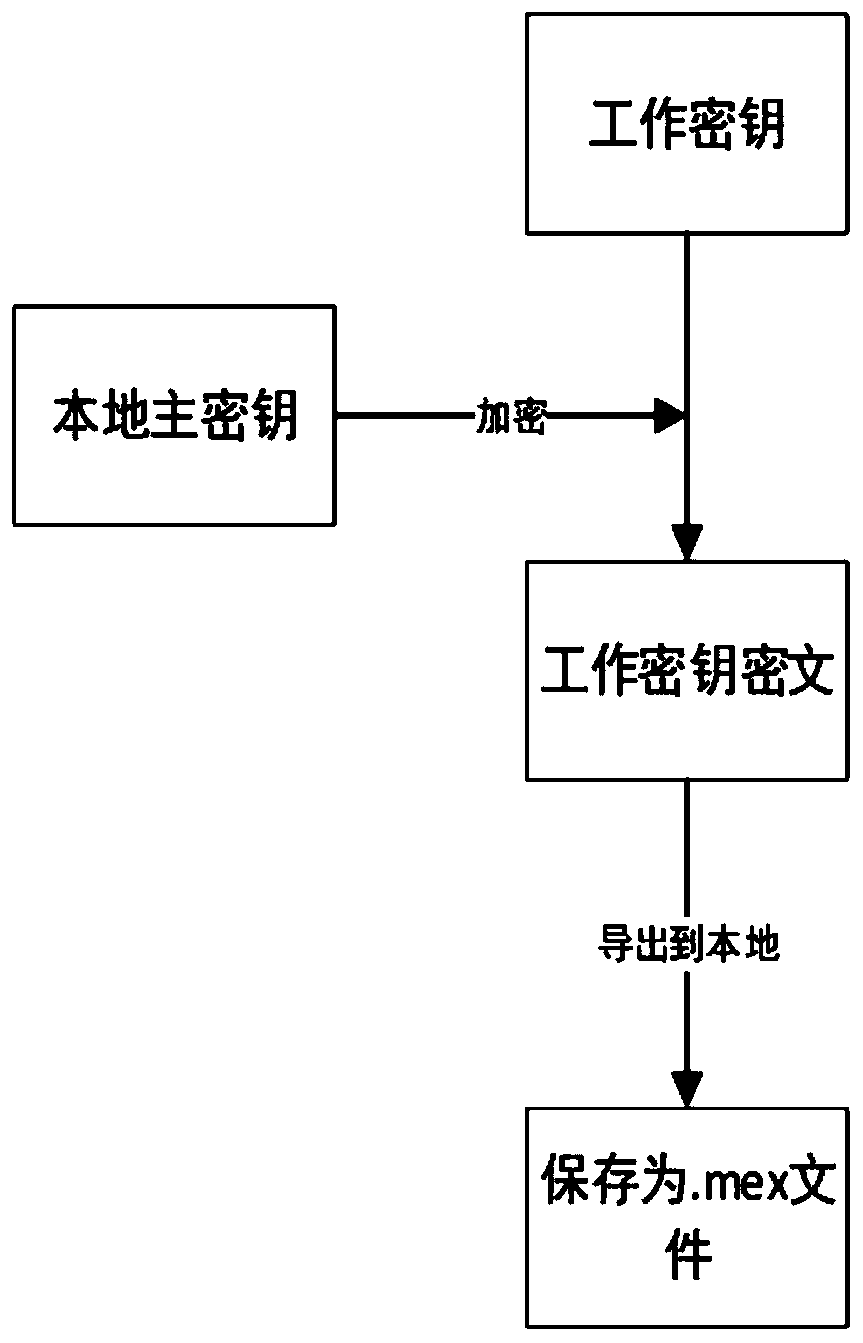
[0038] The stream encryption hardware device has an encryption function, a decryption function and a common storage function, wherein the encryption and decryption functions use a national secret symmetric algorithm (SM4 algorithm, E...
Embodiment 2
[0048] In another typical embodiment of the present application, such as Figure 2-Figure 4 As shown, a high-speed stream encryption method is provided.
[0049] The encryption method utilizes the stream encryption hardware device disclosed in Embodiment 1, comprising the following steps:
[0050] When the device is started, the PC sends private commands and data to the device;
[0051] The device receives the private command and judges whether the operation address is greater than the total capacity of the storage area. If it is greater than the total capacity of the storage area, the stream encryption and decryption function will be activated; if the data is written into the Flash of the device, if it is less than the total capacity of the storage area, the normal storage read and write function will be activated;
[0052] Determine whether the private command is a write command or a read command. If it is a write command, use the SM4 algorithm ECB mode to encrypt and dec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com