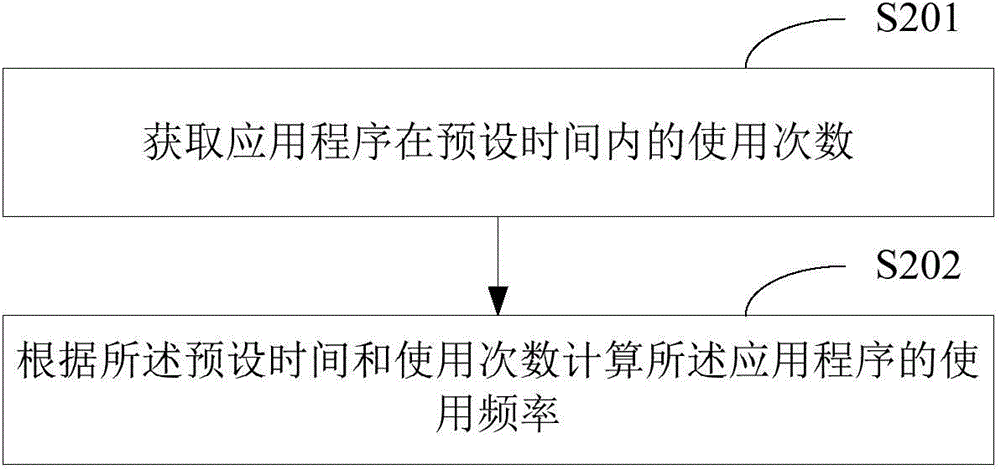
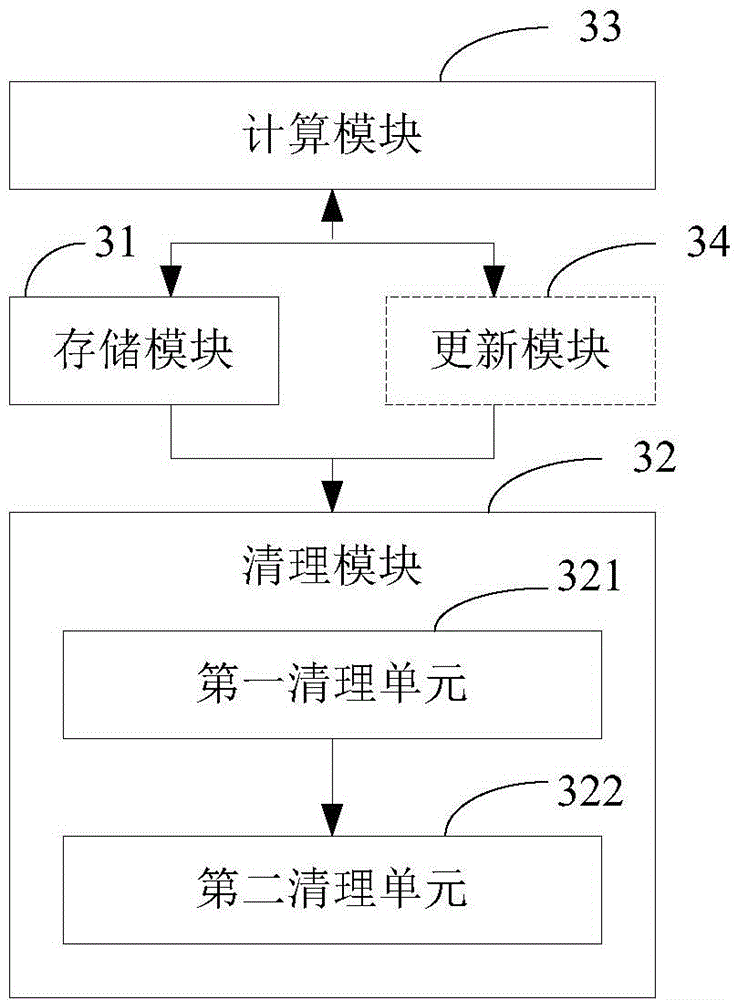
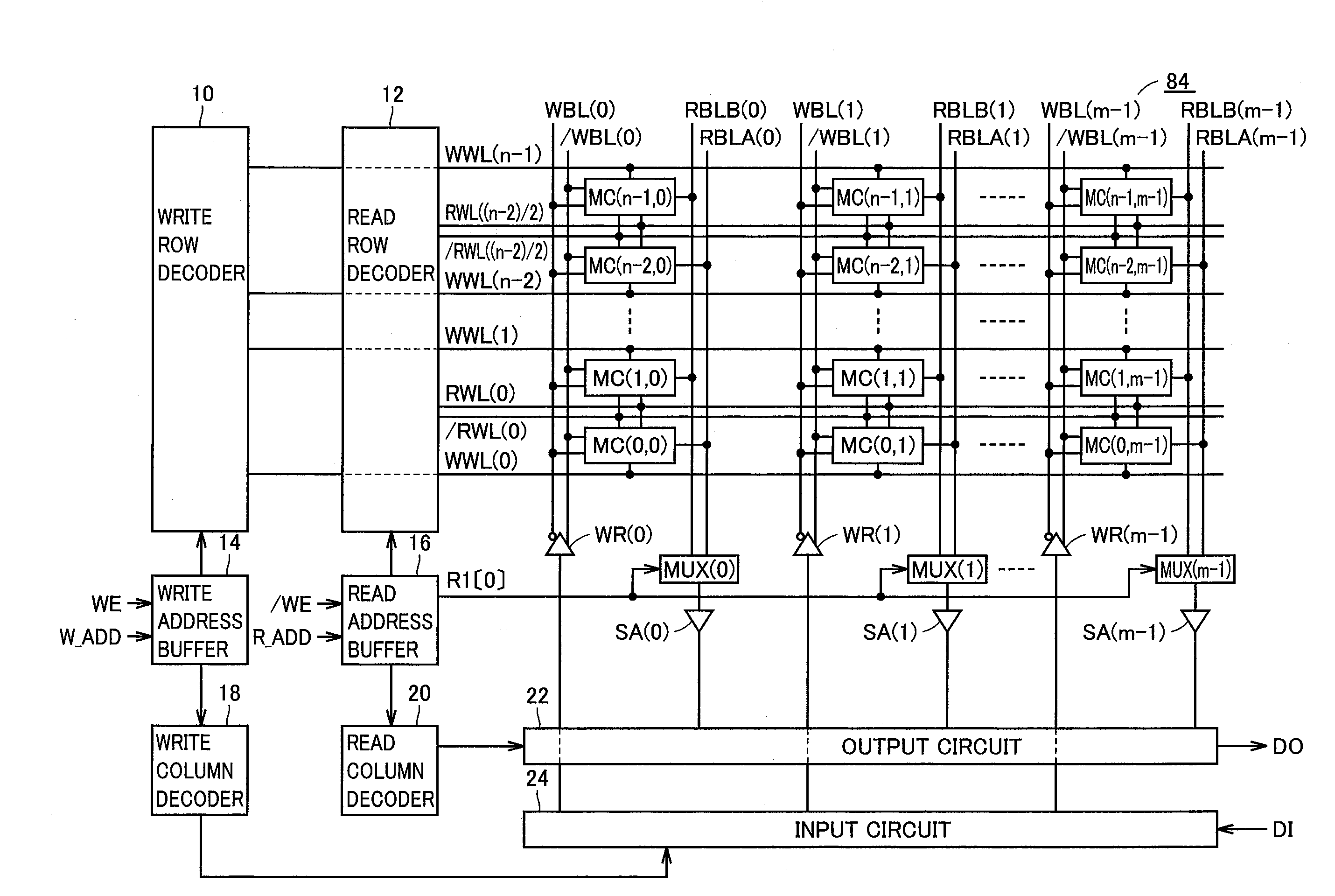
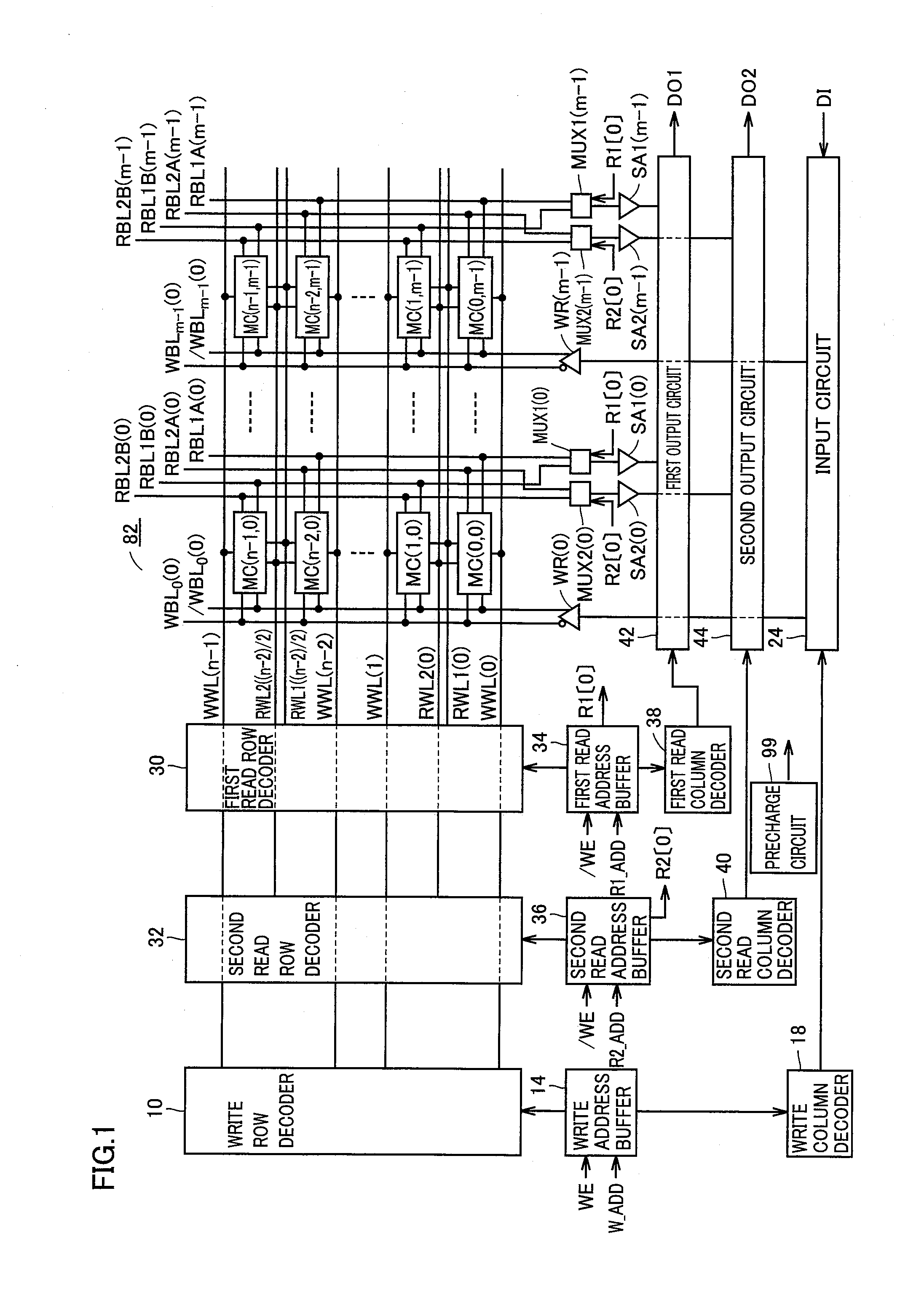
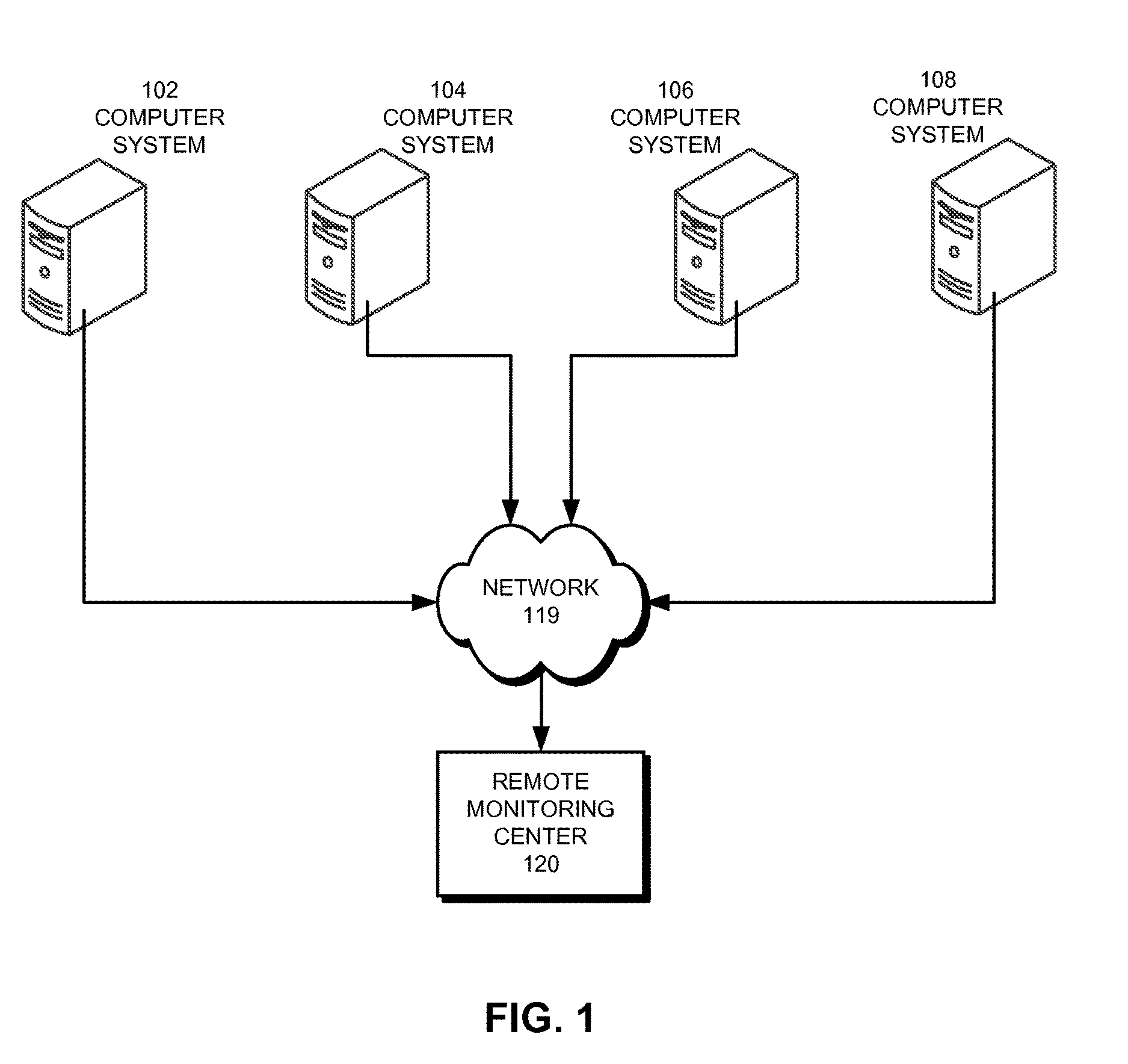
Patents
Literature
312 results about "Out of memory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Out of memory (OOM) is an often undesired state of computer operation where no additional memory can be allocated for use by programs or the operating system. Such a system will be unable to load any additional programs, and since many programs may load additional data into memory during execution, these will cease to function correctly. This usually occurs because all available memory, including disk swap space, has been allocated.
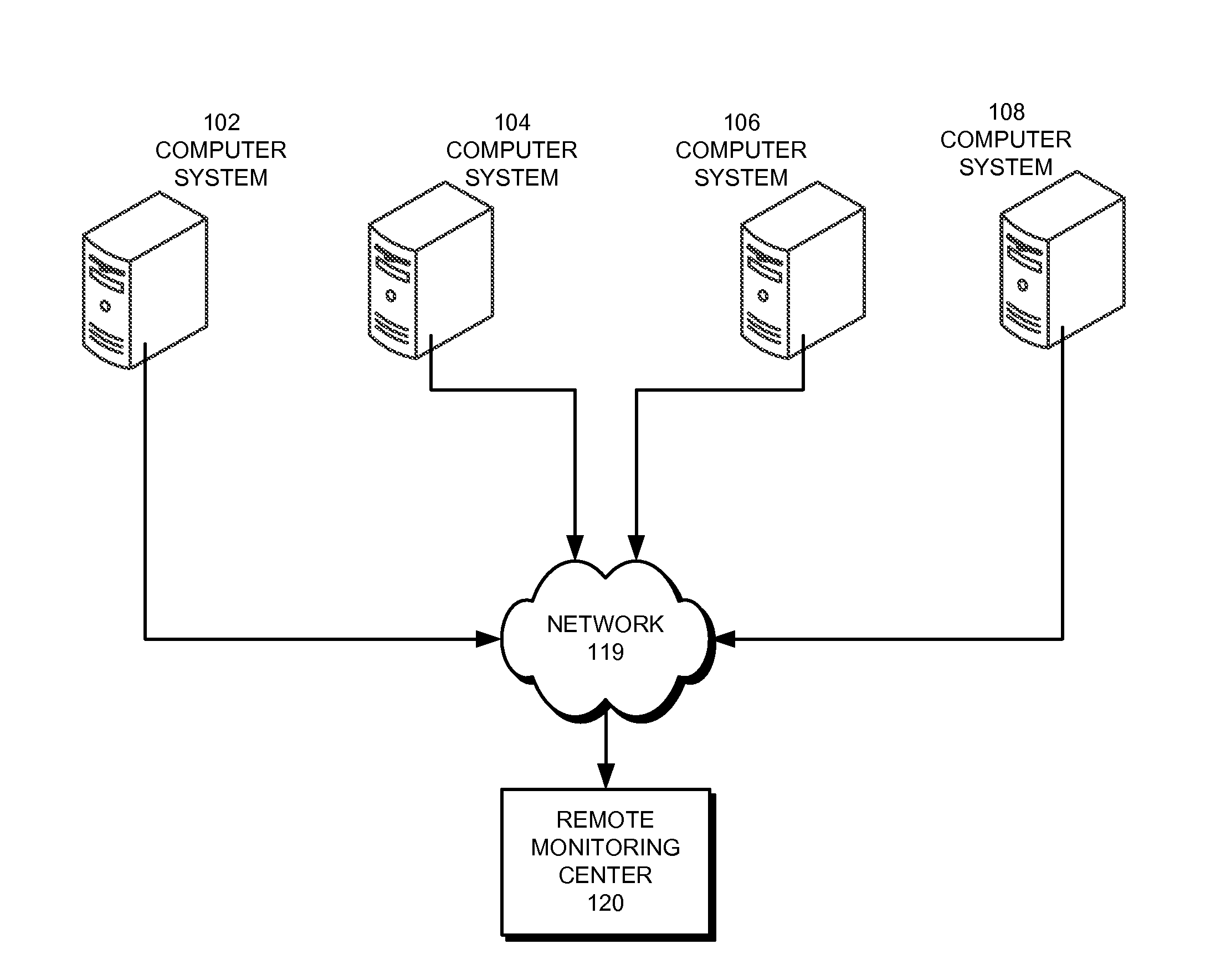
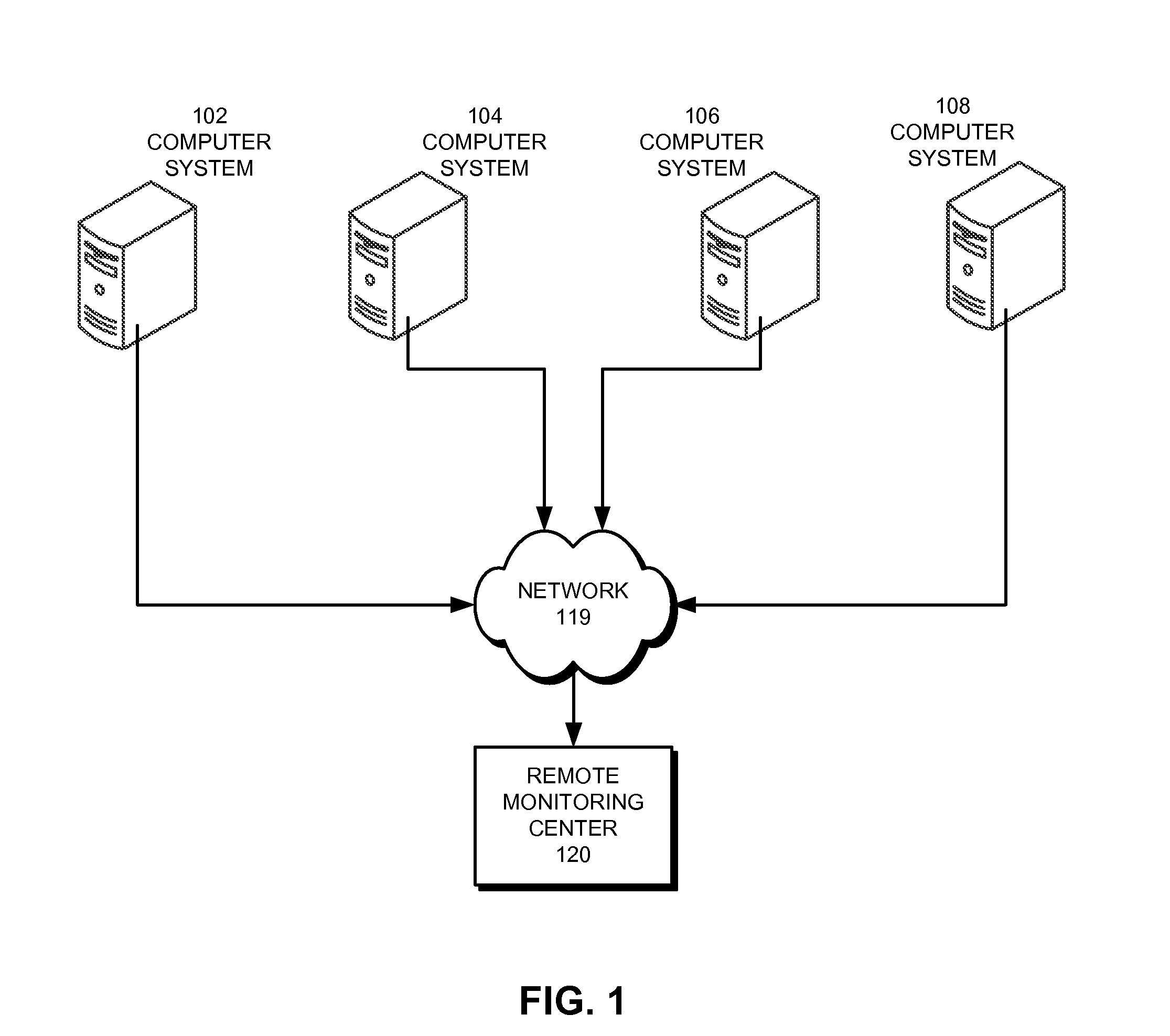
Computer system with adaptive memory arbitration scheme
InactiveUS6286083B1Raise priorityAvoid accessMemory systemsInput/output processes for data processingOut of memoryParallel computing
A computer system includes an adaptive memory arbiter for prioritizing memory access requests, including a self-adjusting, programmable request-priority ranking system. The memory arbiter adapts during every arbitration cycle, reducing the priority of any request which wins memory arbitration. Thus, a memory request initially holding a low priority ranking may gradually advance in priority until that request wins memory arbitration. Such a scheme prevents lower-priority devices from becoming "memory-starved." Because some types of memory requests (such as refresh requests and memory reads) inherently require faster memory access than other requests (such as memory writes), the adaptive memory arbiter additionally integrates a nonadjustable priority structure into the adaptive ranking system which guarantees faster service to the most urgent requests. Also, the adaptive memory arbitration scheme introduces a flexible method of adjustable priority-weighting which permits selected devices to transact a programmable number of consecutive memory accesses without those devices losing request priority.
Owner:HEWLETT PACKARD DEV CO LP
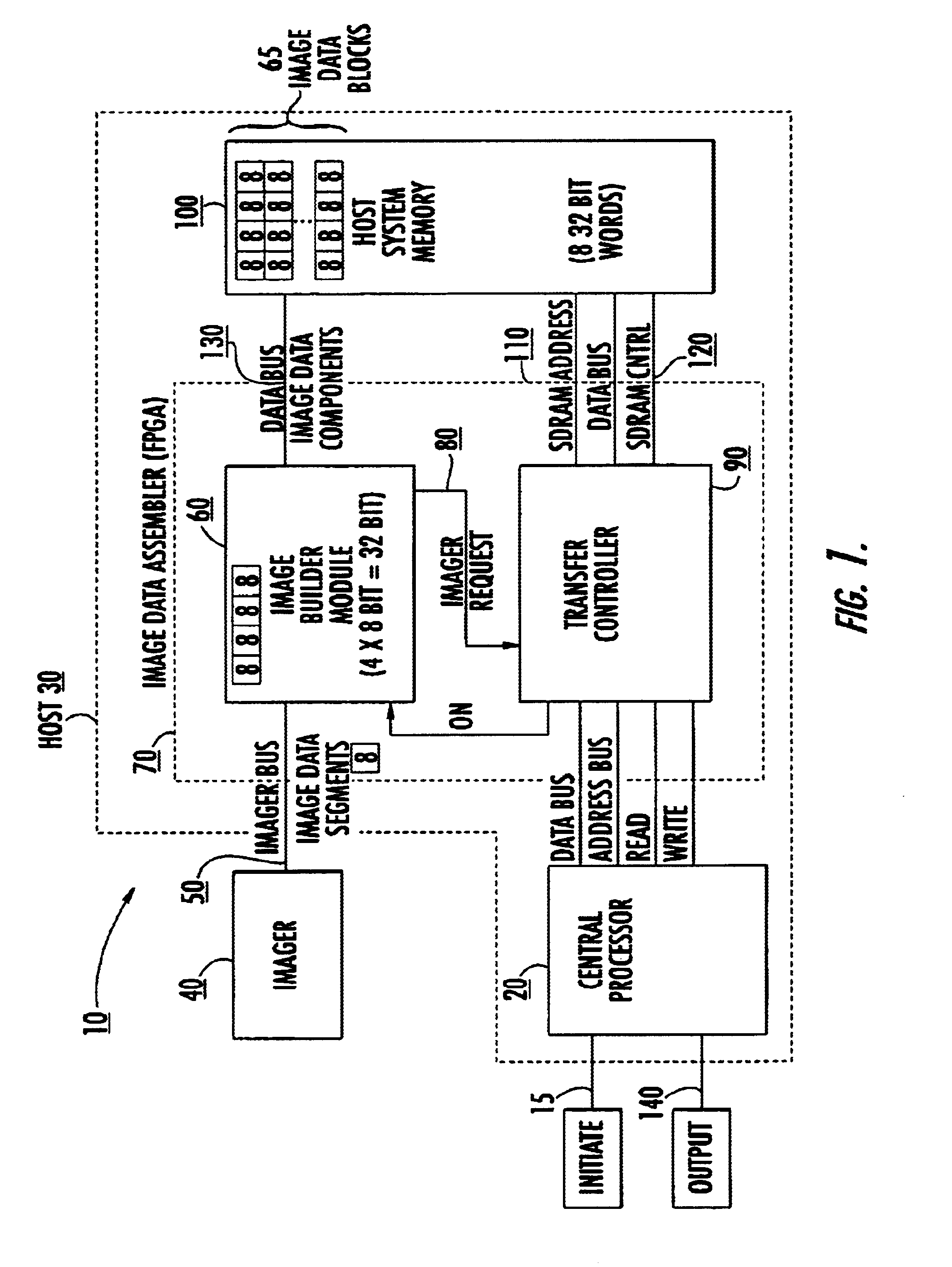
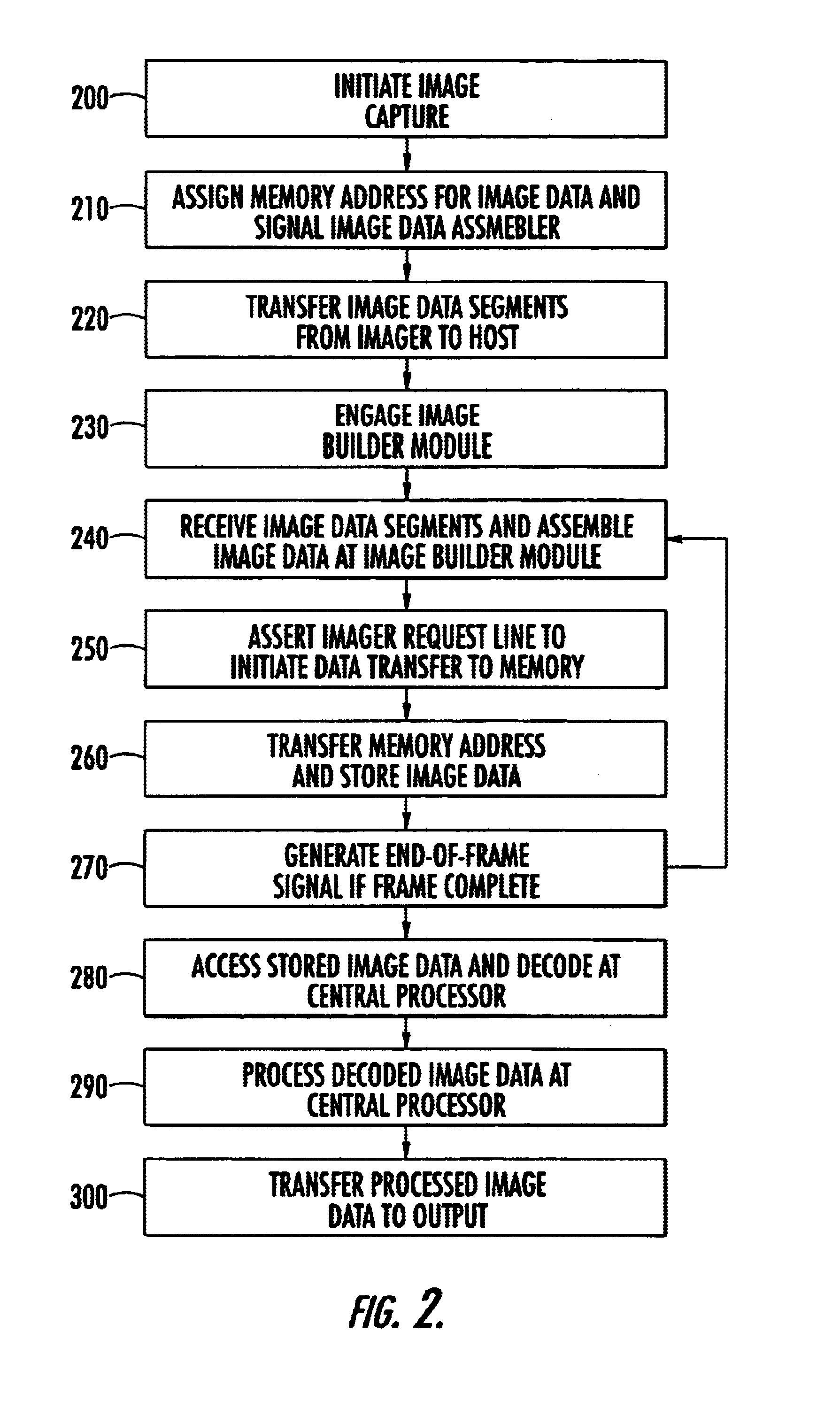
Methods and apparatus for image capture and decoding in a centralized processing unit
InactiveUS6947612B2Timely and efficientEliminate needCharacter and pattern recognitionSensing record carriersMemory addressDigital signal processing
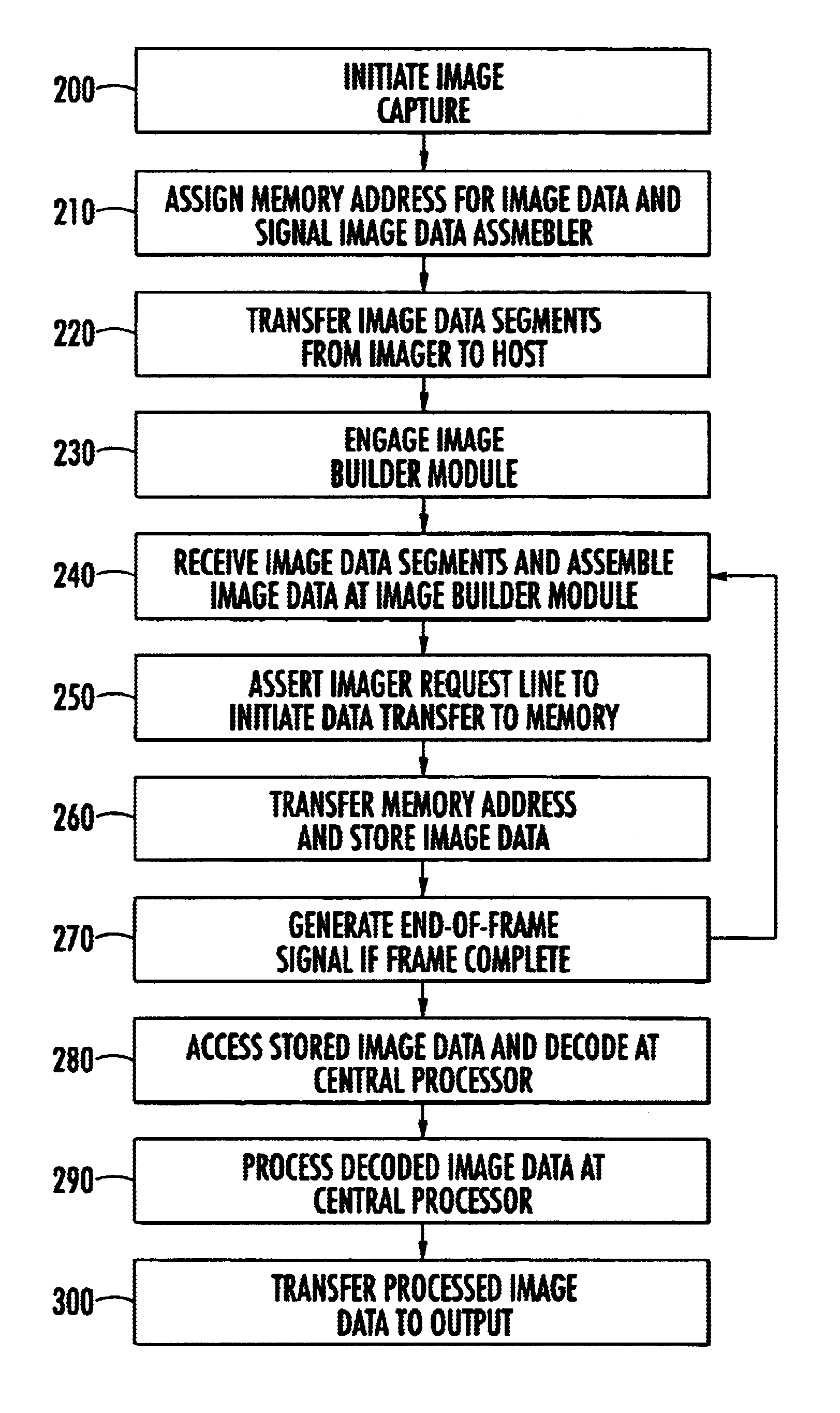
An improved method and device for capturing image data benefits from having a single central processor execute the operating system, and the image capture, decode and processing programs. A method for capturing of image data comprises transmitting image data from an imager, assembling the image data, assigning a memory address to the assembled image data and transferring the assembled image data into system memory. This method is capable of central processing whereby the capturing of image data is executed via the main processor without having to invoke a dedicated processor or incorporate external components, such as additional PCBs, external digital signal processing or external data storage. Additionally, an imaging device comprises an image builder module that receives image data from the imager bus and assembles the data, and a transfer controller that initiates the image builder module and controls the transfer of image data into and out of memory.
Owner:HAND HELD PRODS
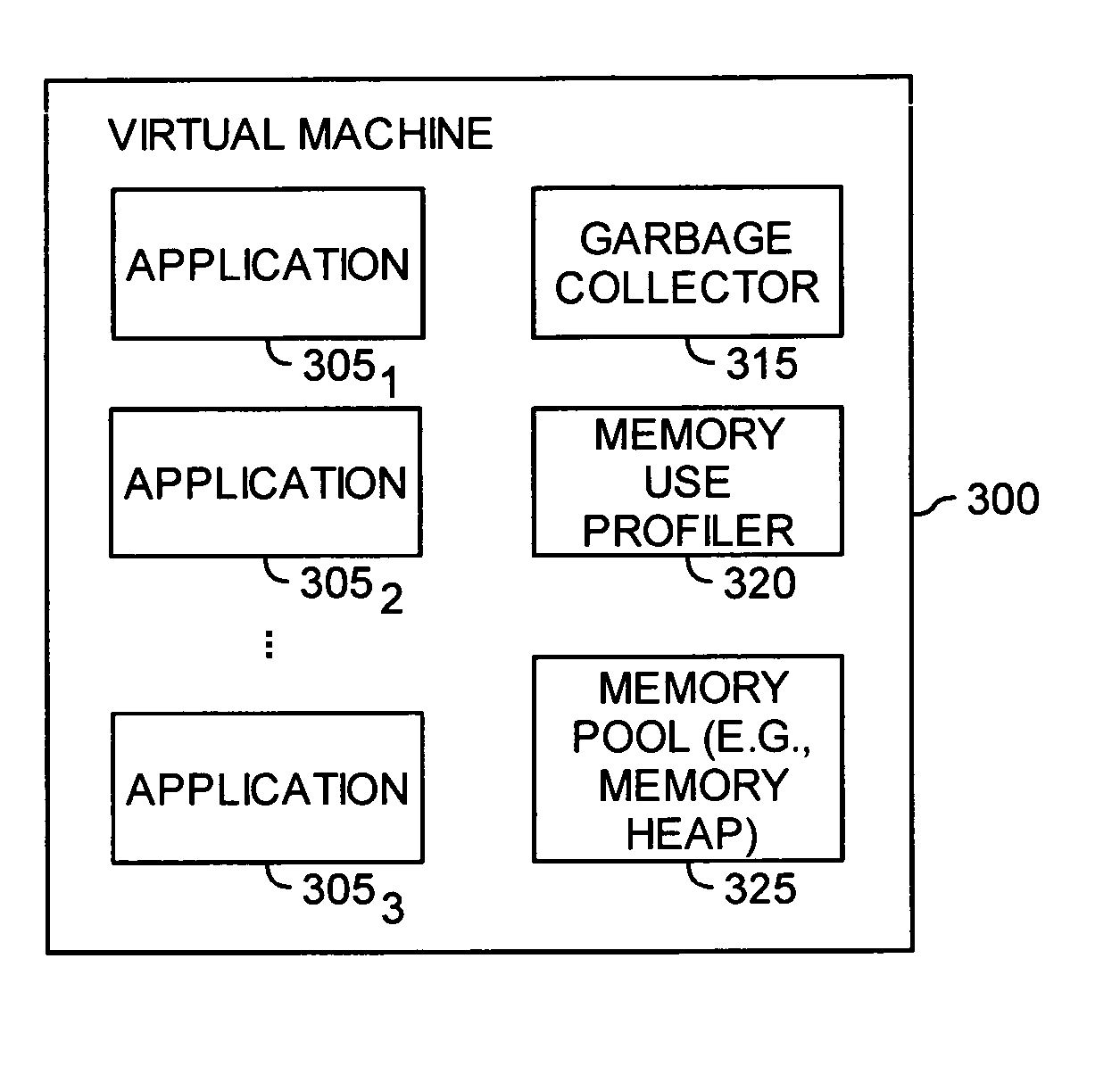
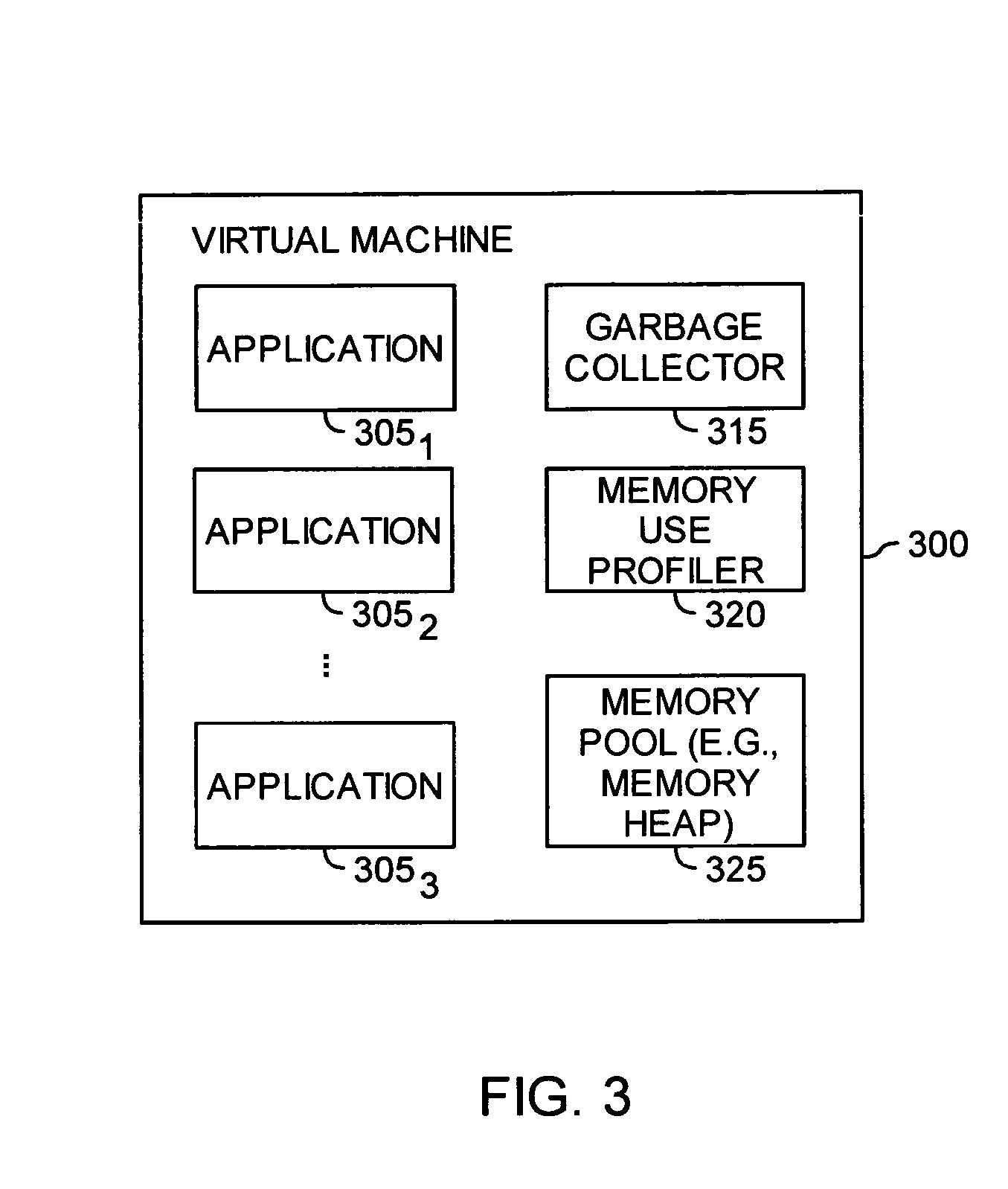
Automatic prediction of future out of memory exceptions in a garbage collected virtual machine
InactiveUS20070136402A1Special data processing applicationsMemory systemsOut of memoryParallel computing
A method, article of manufacture and apparatus for automatically predicting out of memory exceptions in garbage collected environments are disclosed. One embodiment provides a method of predicting out of memory events that includes monitoring an amount of memory available from a memory pool during a plurality of garbage collection cycles. A memory usage profile may be generated on the basis of the monitored amount of memory available, and then used to predict whether an out of memory exception is likely to occur.
Owner:IBM CORP
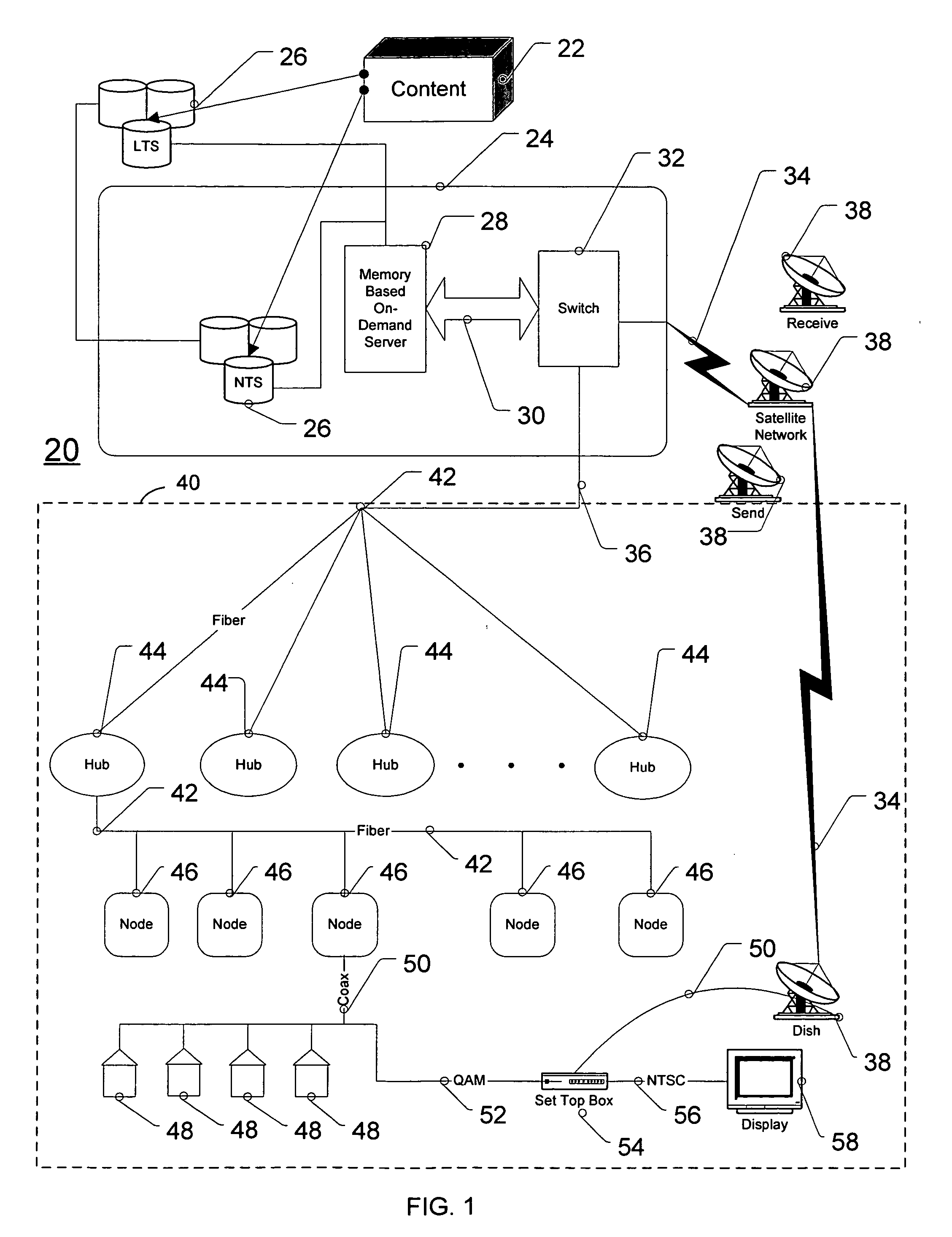
Method and system for resource management in a video on-demand server
ActiveUS20050267948A1Minimizes disk accessImprove overall utilizationMultiple digital computer combinationsTwo-way working systemsOut of memoryResource management
An on-demand server configured to dynamically control and optimize memory utilization while minimizing access to disk storage by monitoring content addressable memory (CAM) usage so as to remove the content from resident CAM memory and page the same adaptively and to eliminate creating separate files for trick playback of content streamed to a customer. The method and system dynamically uses the current concurrency count of the contents to optimize memory utilization so as to swap content in and out of memory as the concurrency values change in conjunction with an on-demand memory based server to provided advantages of optimizing the usage of server resources.
Owner:GOOGLE TECH HLDG LLC
Incremental heap expansion in a real-time garbage collector
InactiveUS6286016B1Data processing applicationsMemory adressing/allocation/relocationLocality of referenceOut of memory
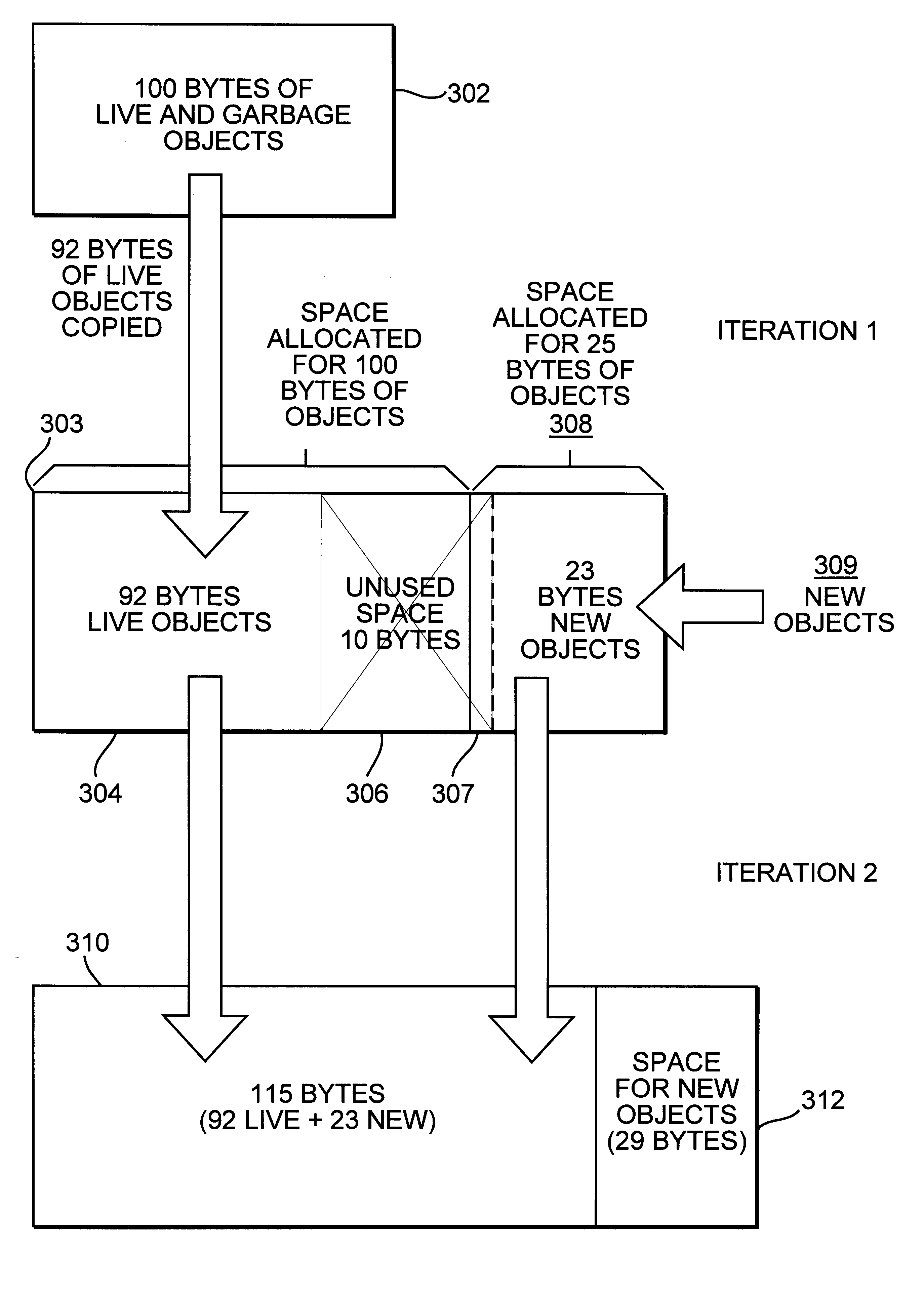
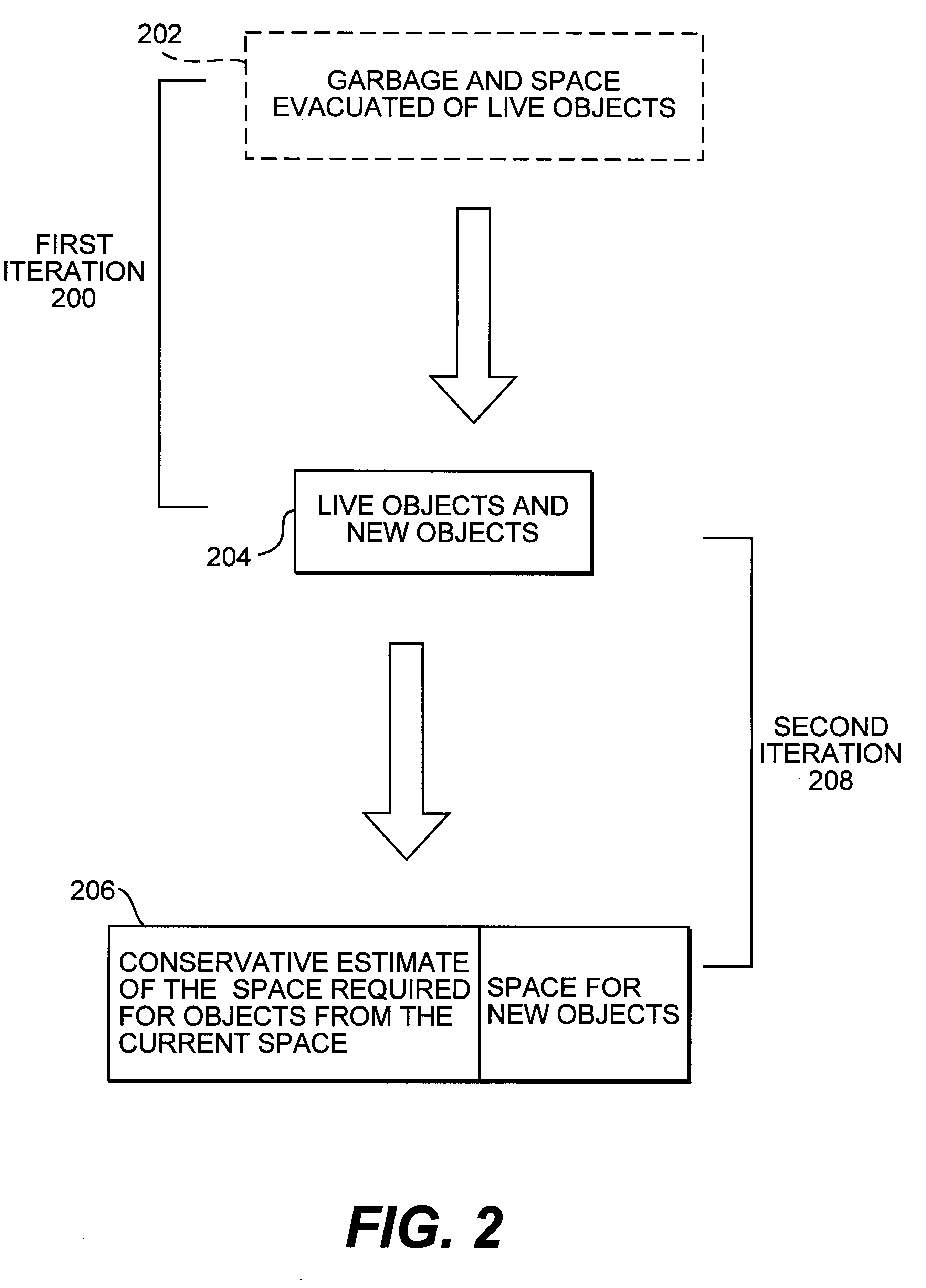
A system that performs real-time garbage collection by dynamically expanding and contracting the heap is provided. This system performs real-time garbage collection in that the system guarantees garbage collection will not take more time than expected. The system dynamically expands and contracts the heap to correspond to the actual memory space used by live objects. This dynamic resizing of the heap has the advantages of expanding when the amount of objects increases and contracting to free memory space for use by other procedures when the amount of objects decreases. Keeping the heap as small as possible frees resources for other processes and increases the locality of reference for the application. This dynamic resizing also ensures that the new memory space will not run out of memory before all of the live objects from the old memory space are copied, even if all of the live objects in the old memory space survive.
Owner:ORACLE INT CORP
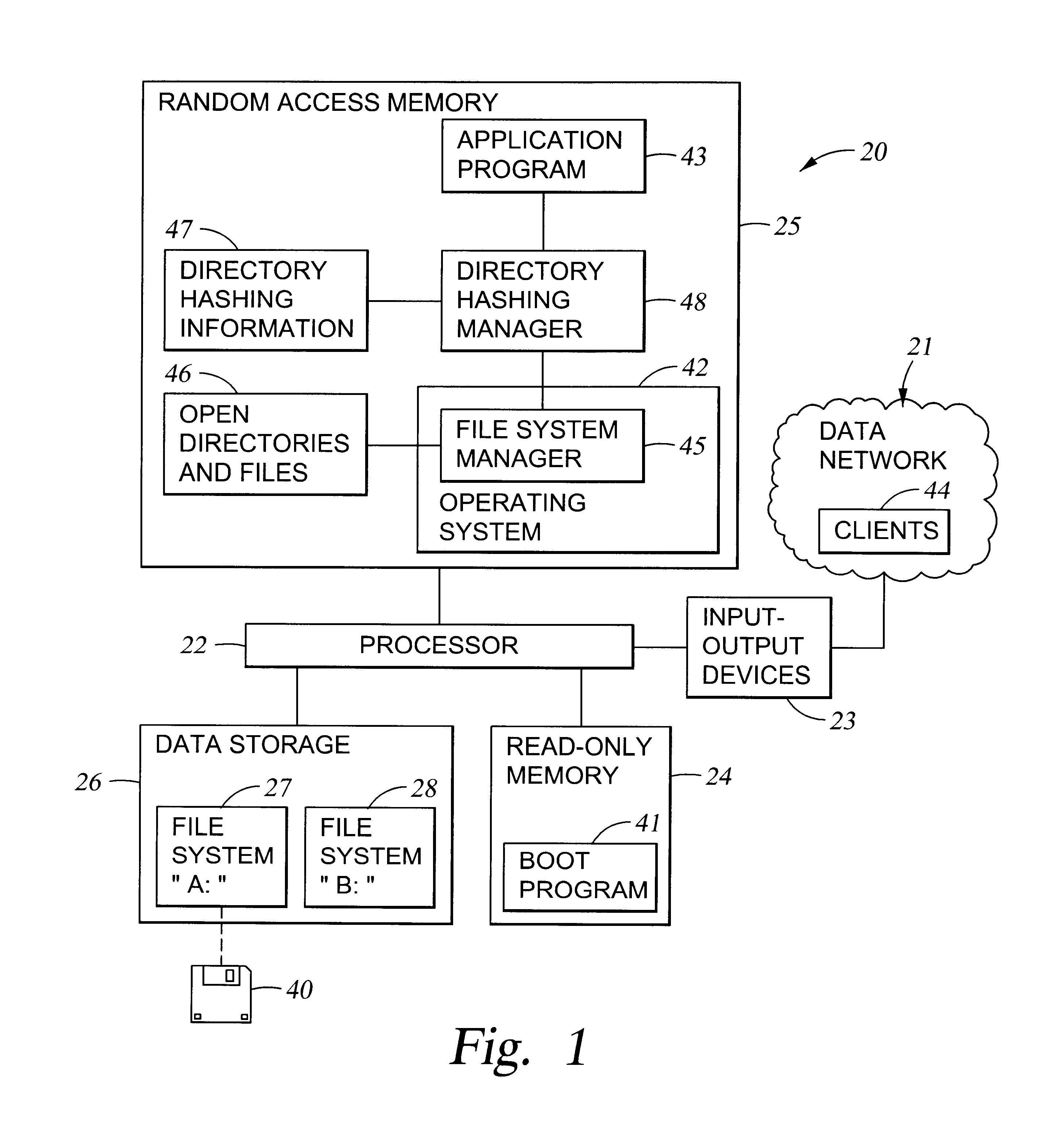
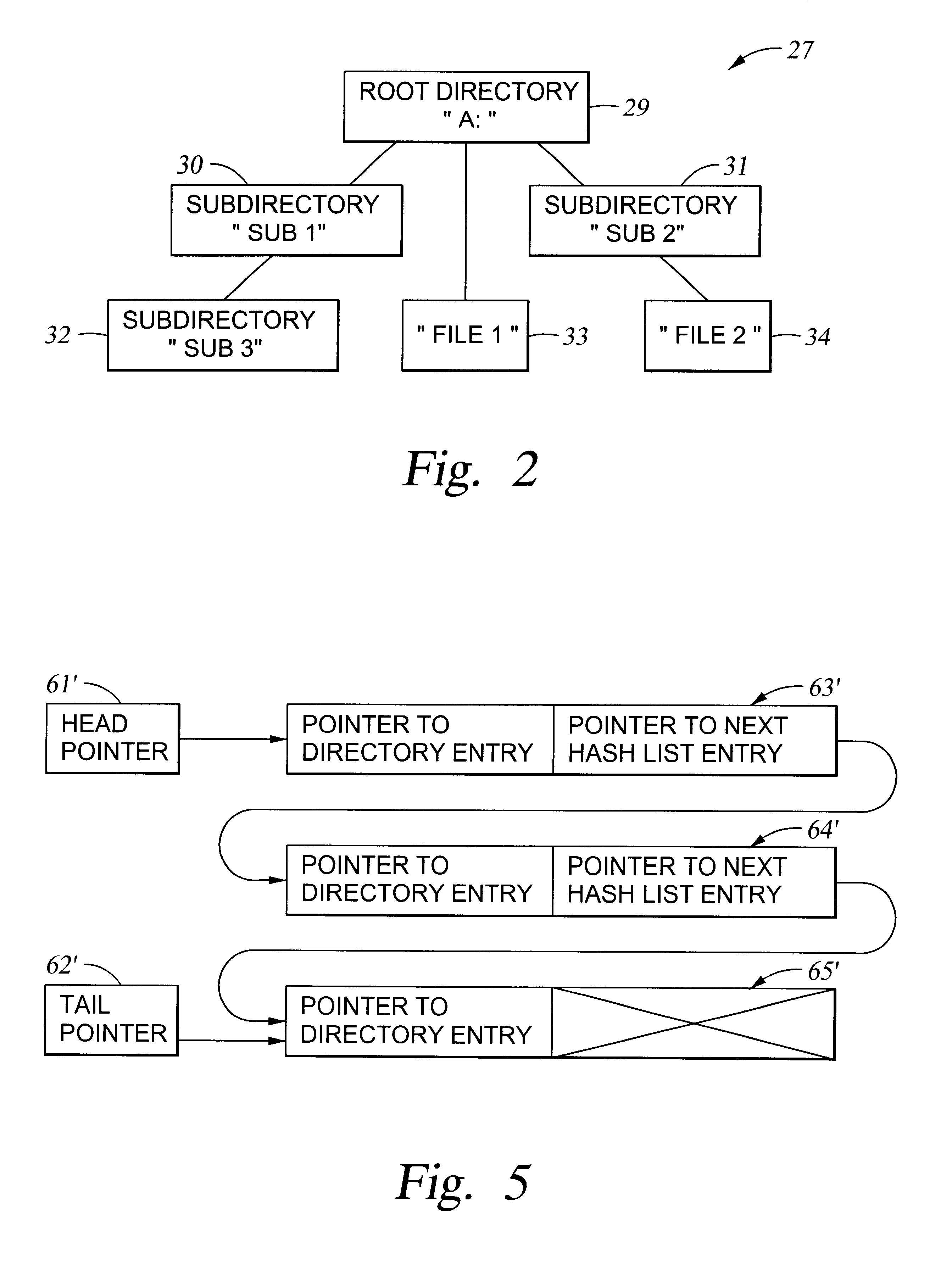
Very efficient in-memory representation of large file system directories
InactiveUS6625591B1Data processing applicationsDigital data information retrievalFile systemOut of memory
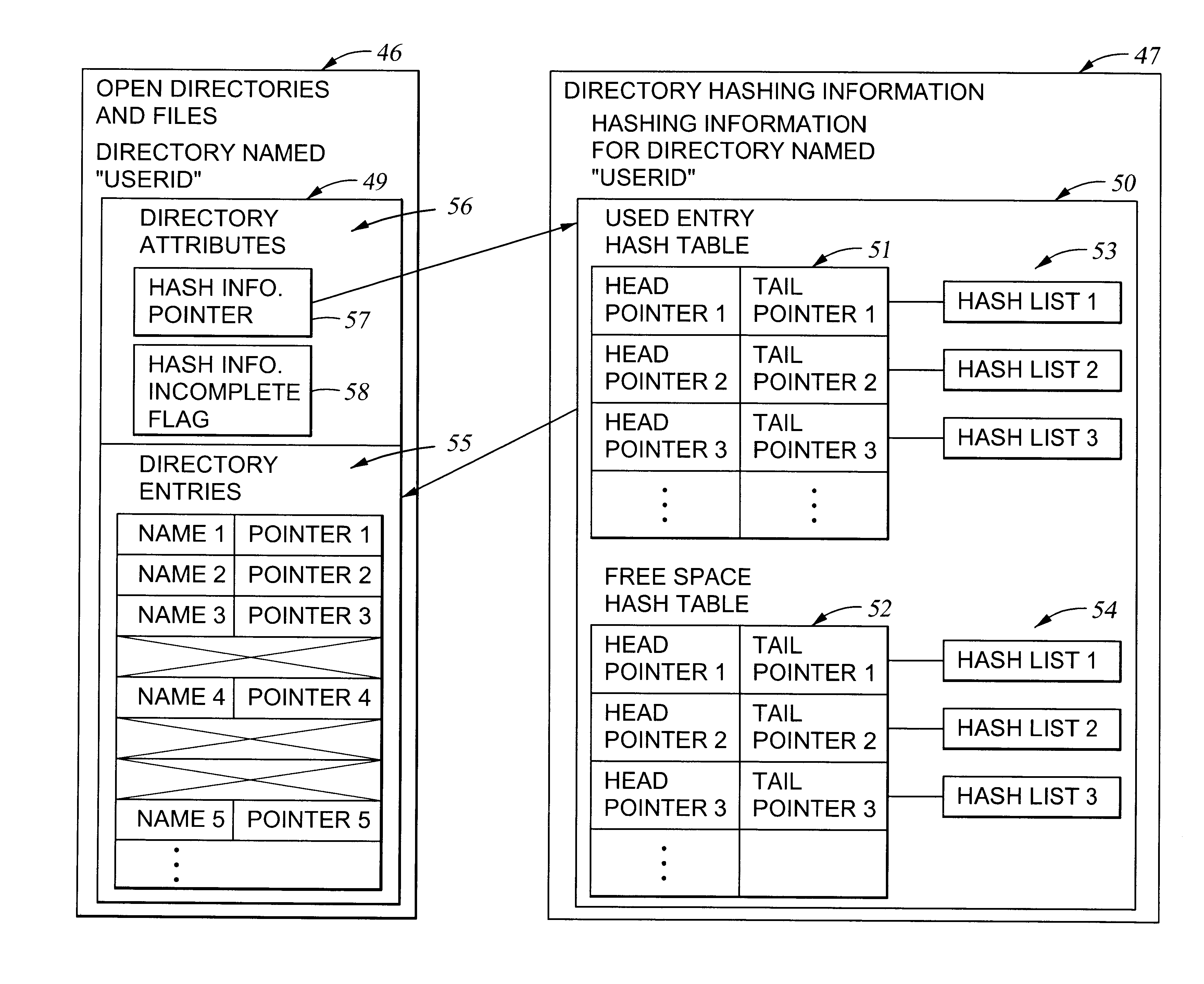
To accelerate searching of large file system directories, hashing information for a selected directory is compiled and retained in random access memory prior to a need for access to the directory to satisfy a file access request from an application. No change in the on-disk file system representation is required, nor is there any need for nonvolatile storage of the hashing information. If memory is scarce, the hashing information can be incomplete yet give hints for searching the most-recently-accessed directory entries. In a preferred implementation, the hashing information for a directory includes a hash table for searching for names of objects such as files, subdirectories or links in the directory, and a hash table for searching for free space in the directory.
Owner:EMC IP HLDG CO LLC
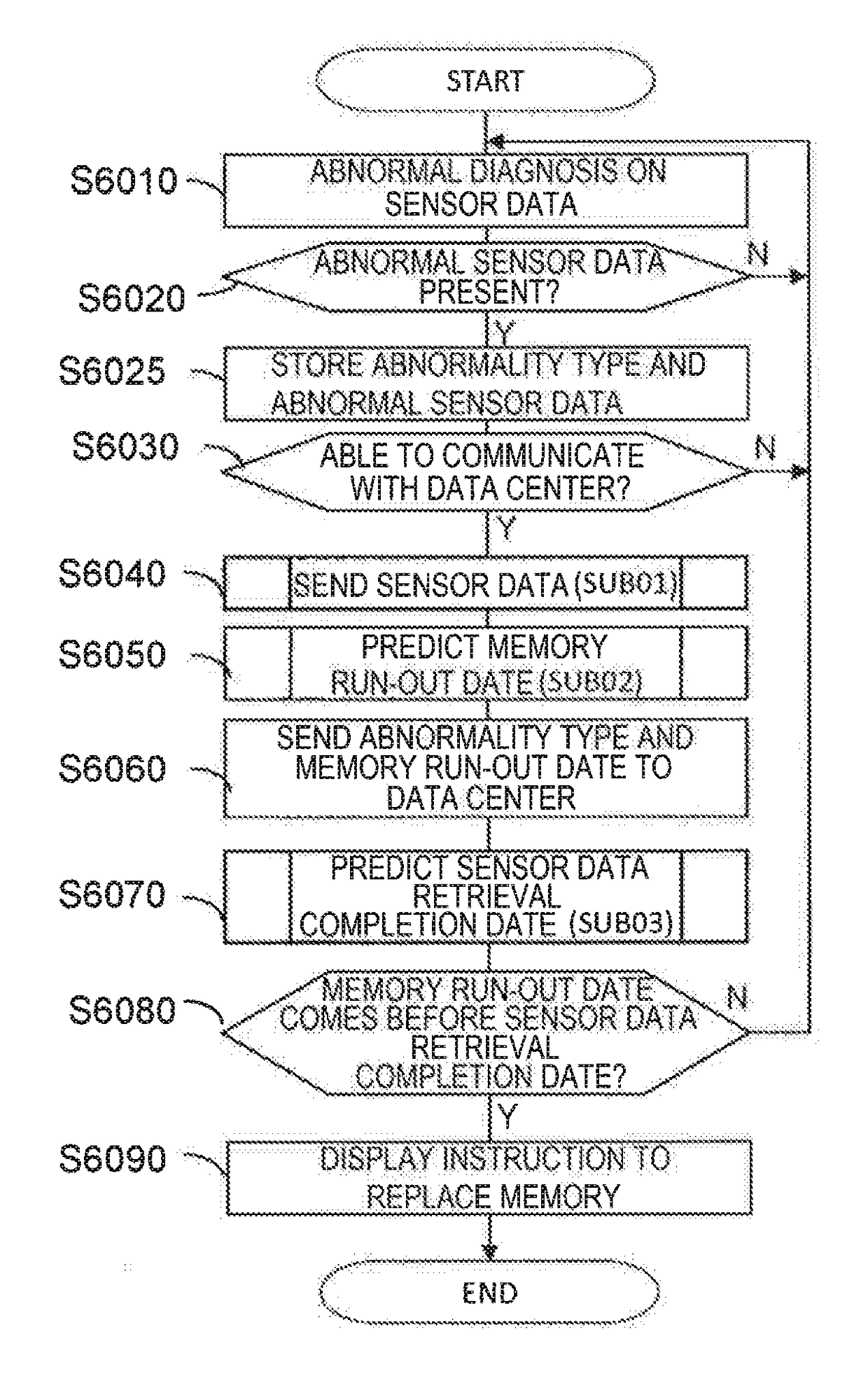
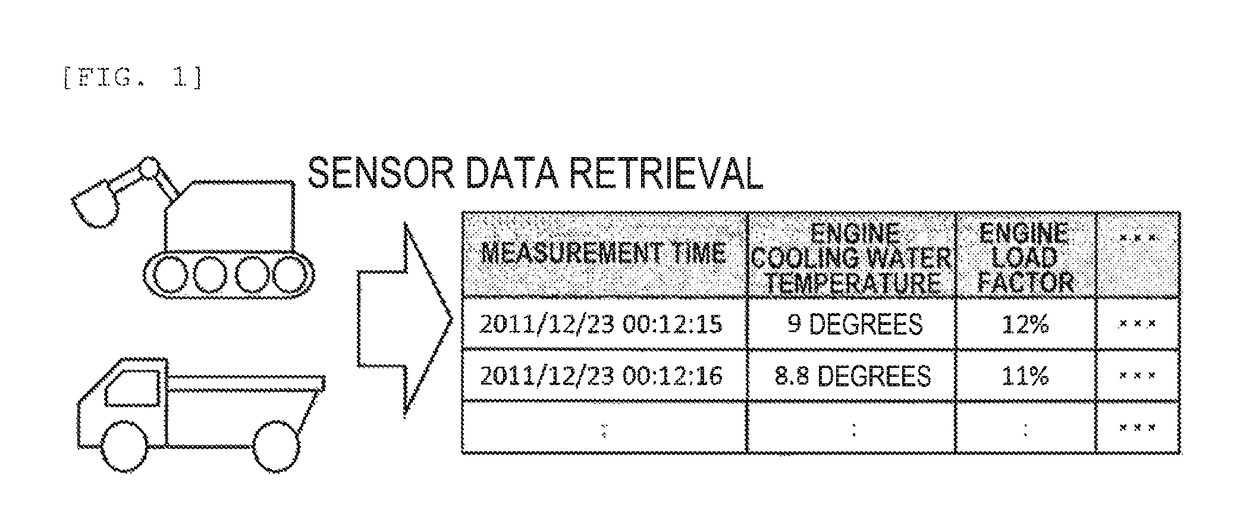
Abnormality diagnosis method and device therefor
ActiveUS10073447B2Detected as abnormalityProgramme controlRegistering/indicating working of vehiclesMechanical AbnormalityDiagnosis methods
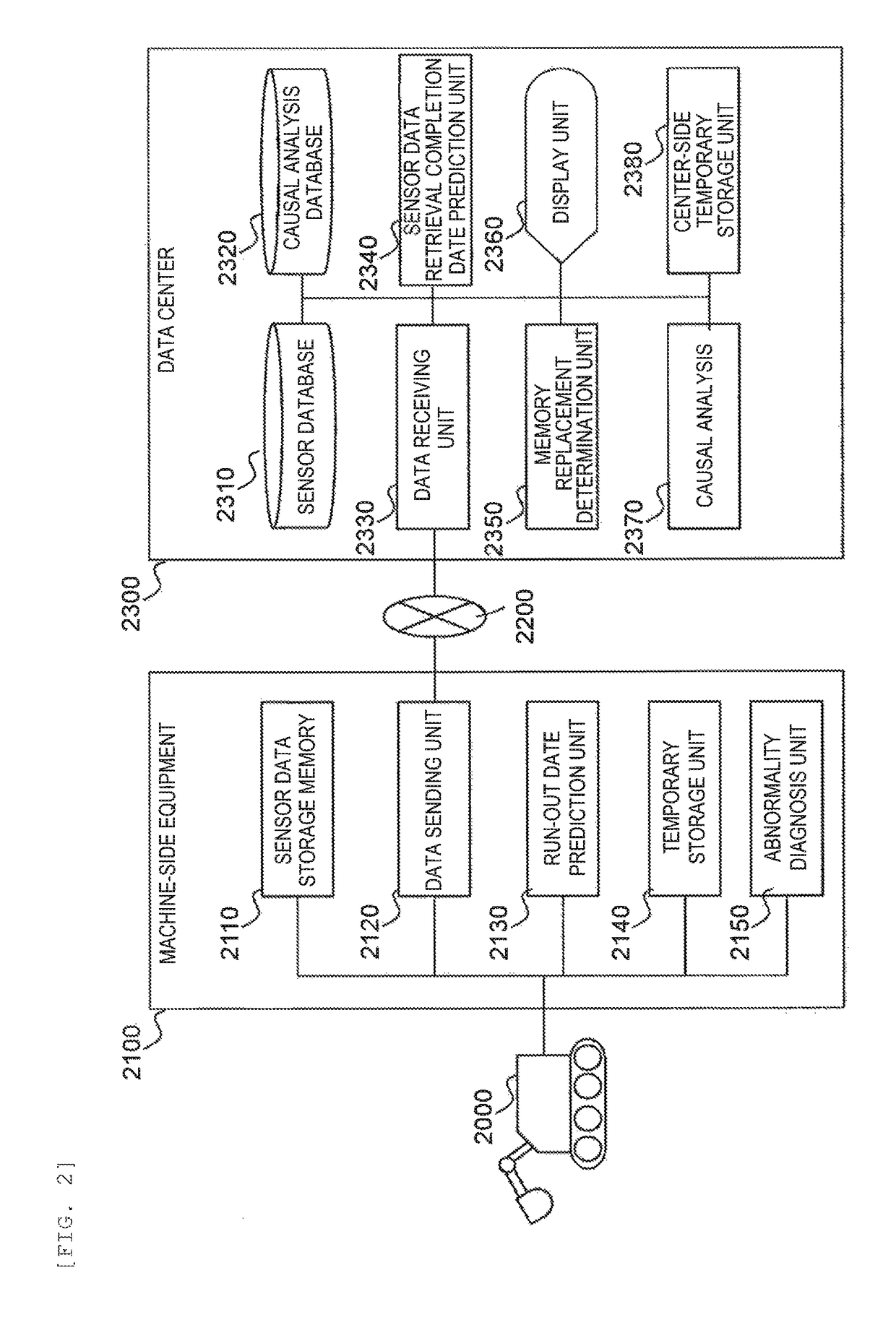
In industrial machine abnormality diagnosis, if the machine is diagnosed to have abnormality, then sensor data from the machine needs to be sent to a management center for causal analysis. However, since machines operated at a remote site cannot always communicate with a management center, it has been found that, in some cases, sensor data that has failed to be sent from a machine remains in the memory of the machine, resulting in lack of available memory capacity. In view of this, the present invention determines beforehand whether the diagnosed machine will run out of available memory capacity before the completion of sending the amount of sensor data required for causal analysis for the machine, and instructs a maintenance person to recover memory. This determination as to whether the machine will run out of available memory capacity before the completion of sending the amount of sensor data required for the causal analysis for the machine, is made as follows: (1) first, the machine predicts the run-out date on which the machine will run out of memory capacity for storing sensor data generated in the machine, and sends a notification of the predicted run-out date to the management center for the machine; and (2) next, from the amount of sensor data required for the causal analysis and the reception rate of sensor data, the management center calculates the number of days required to retrieve the necessary data for the causal analysis and determines whether the management center can retrieve the data by the predicted run-out date.
Owner:HITACHI LTD
System, method, and apparatus for improving application-launch latencies
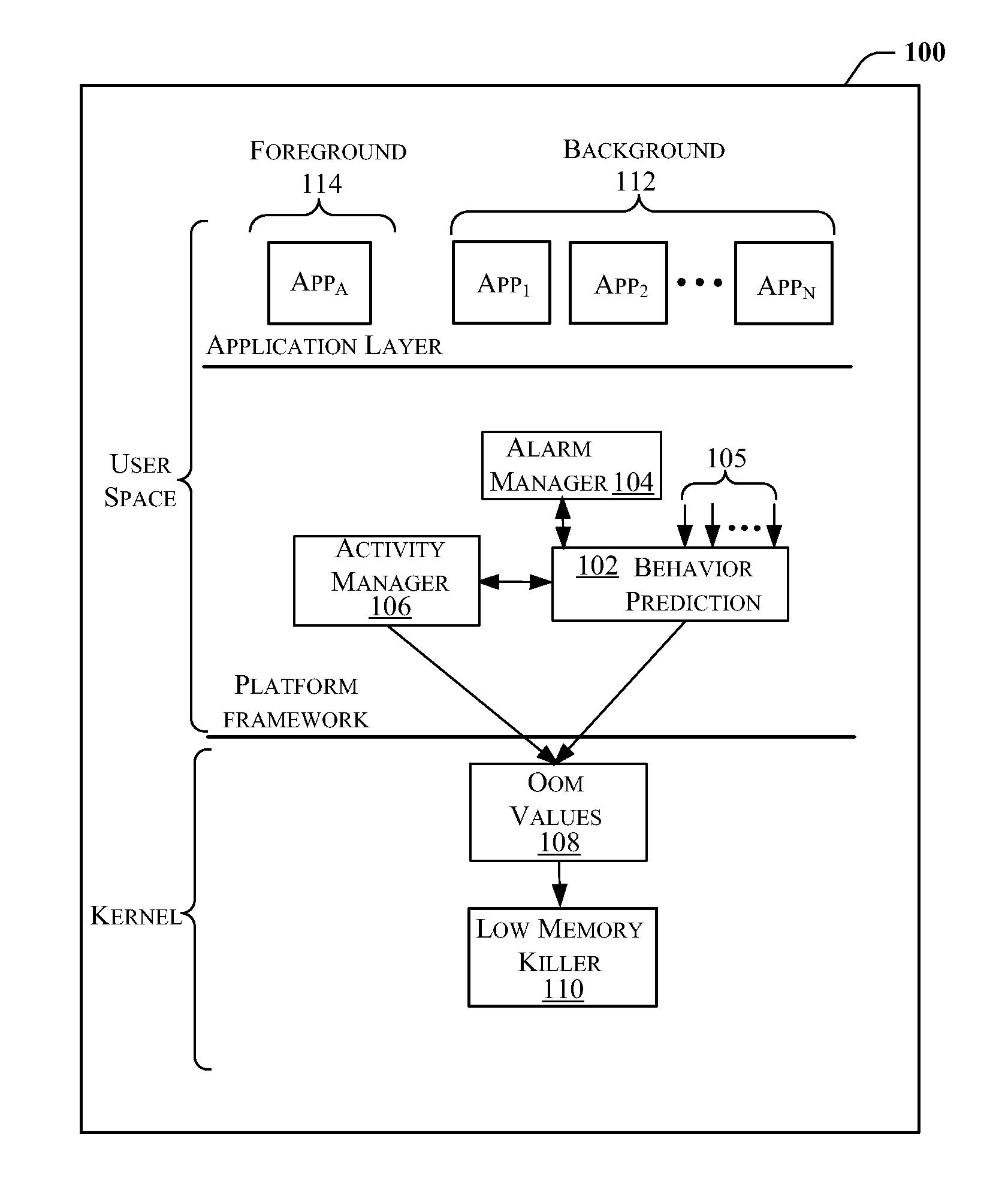
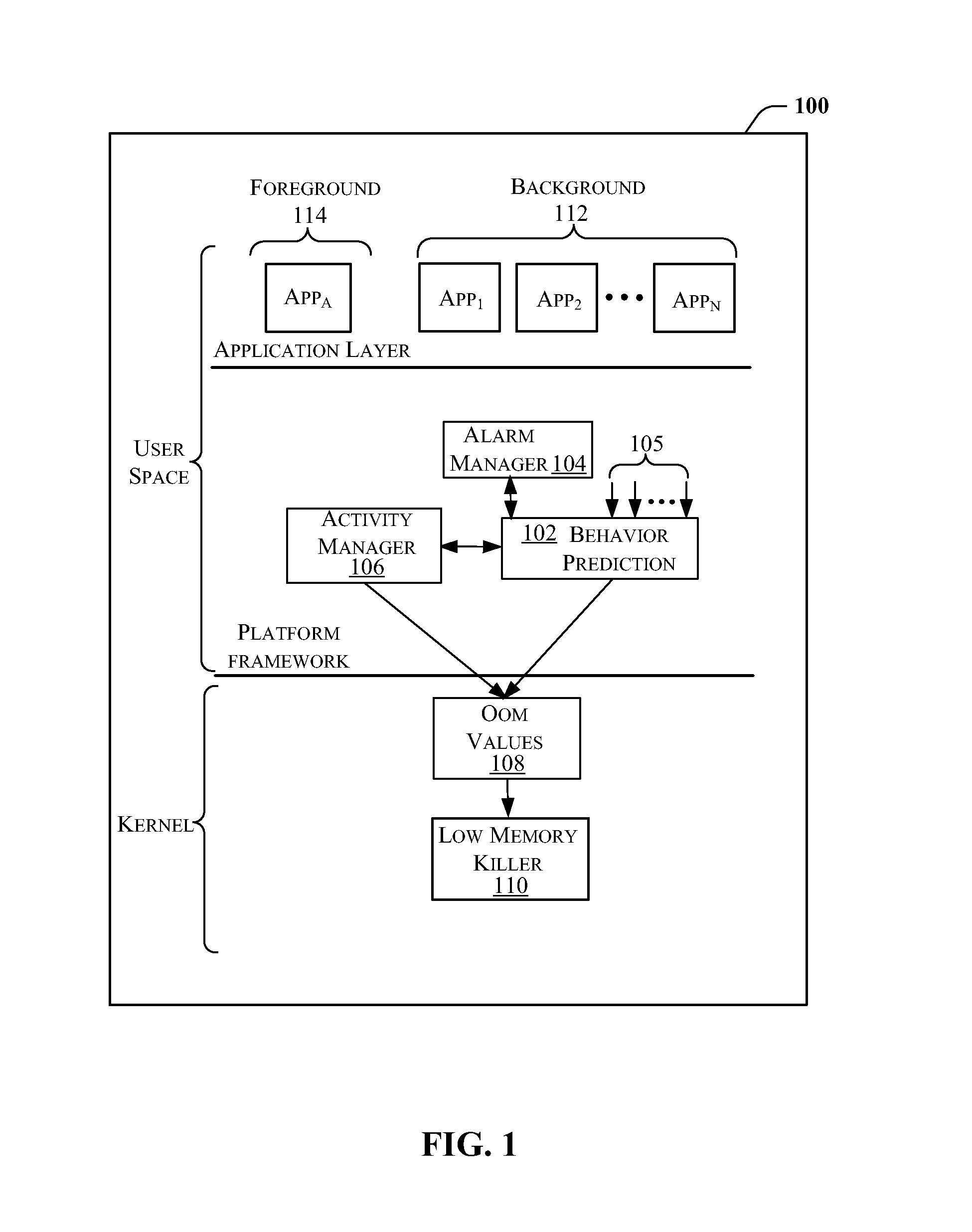
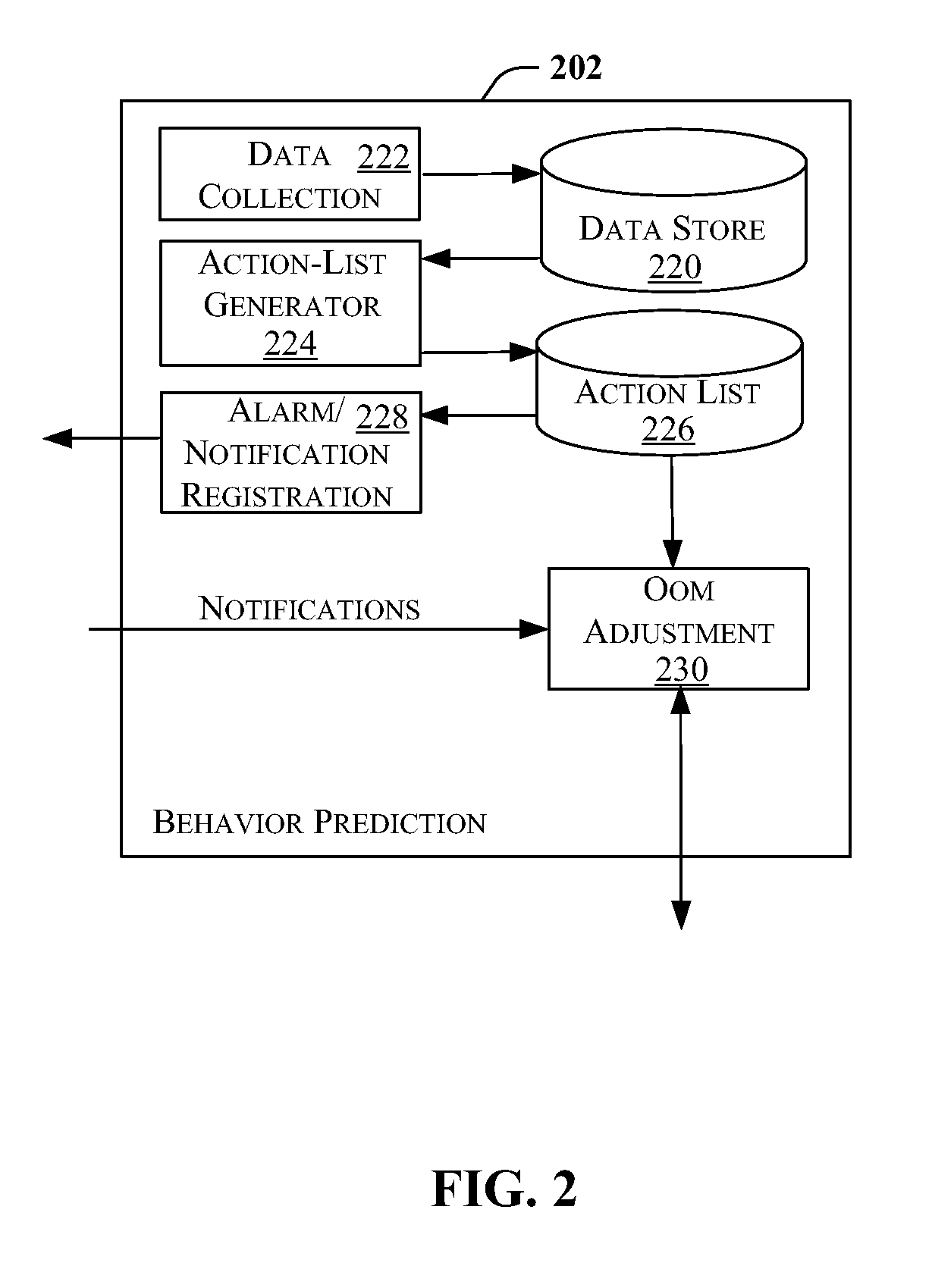
InactiveUS20140143791A1Shorten launch timeMultiprogramming arrangementsLocation information based serviceOut of memorySoftware engineering
Owner:QUALCOMM INNOVATION CENT
Method for predicting and avoiding danger in execution environment
InactiveUS20050240641A1Reduce loadShort timeData processing applicationsMemory adressing/allocation/relocationApplication serverOut of memory
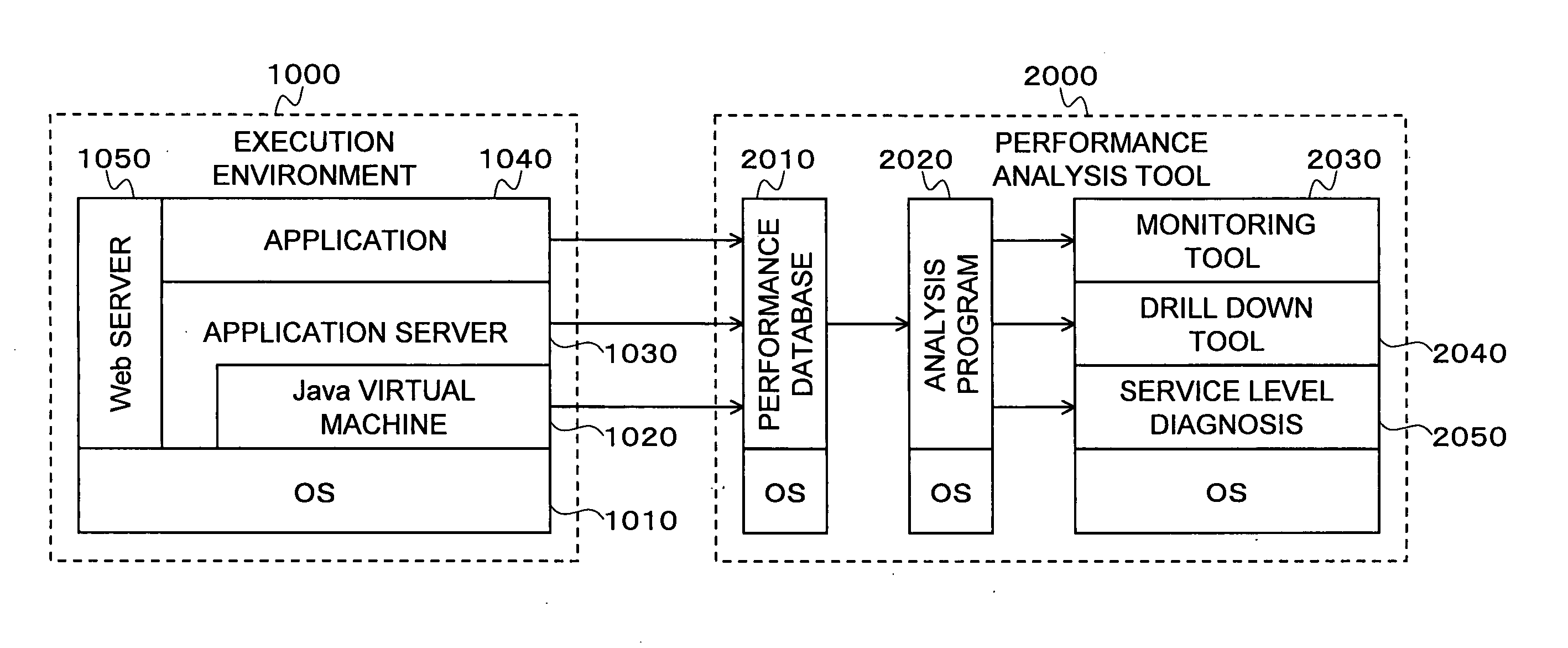
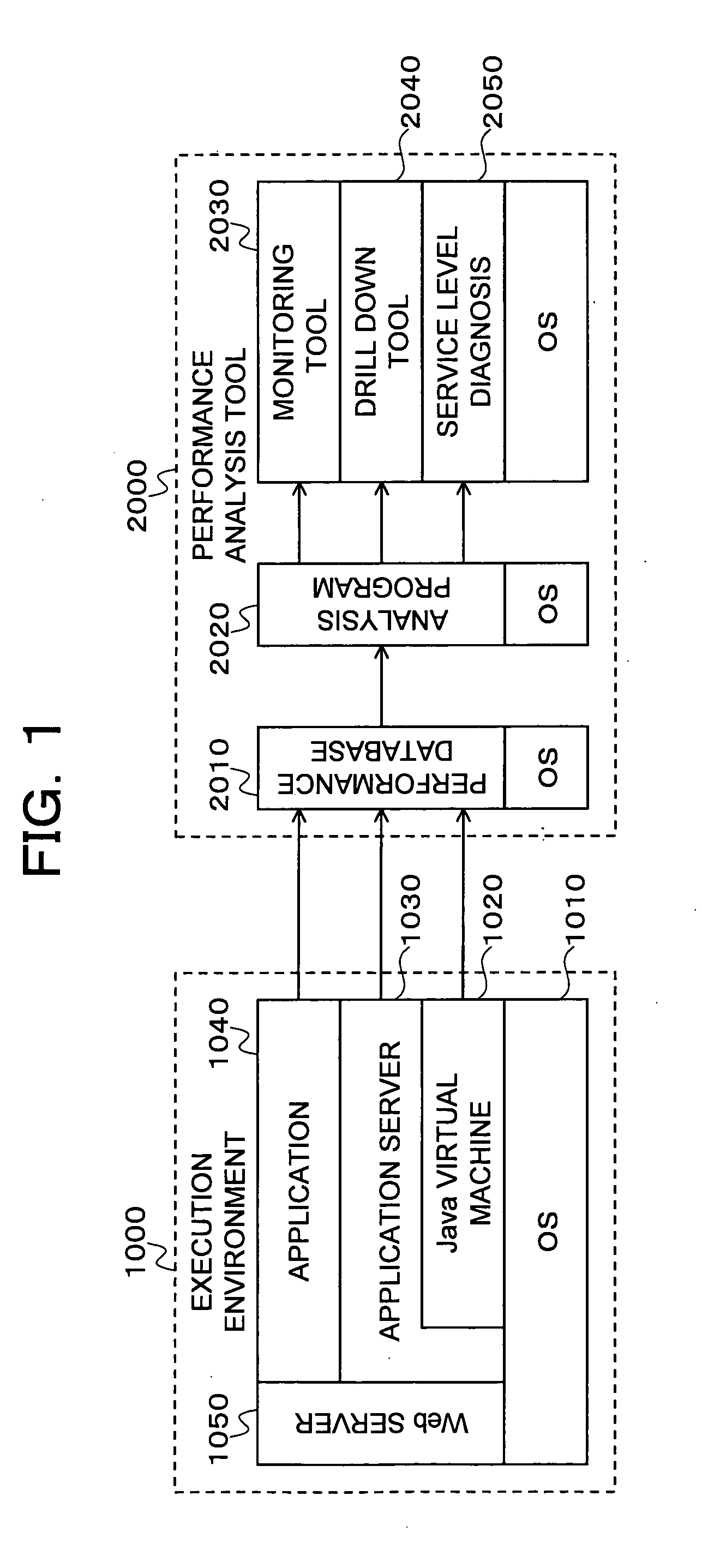
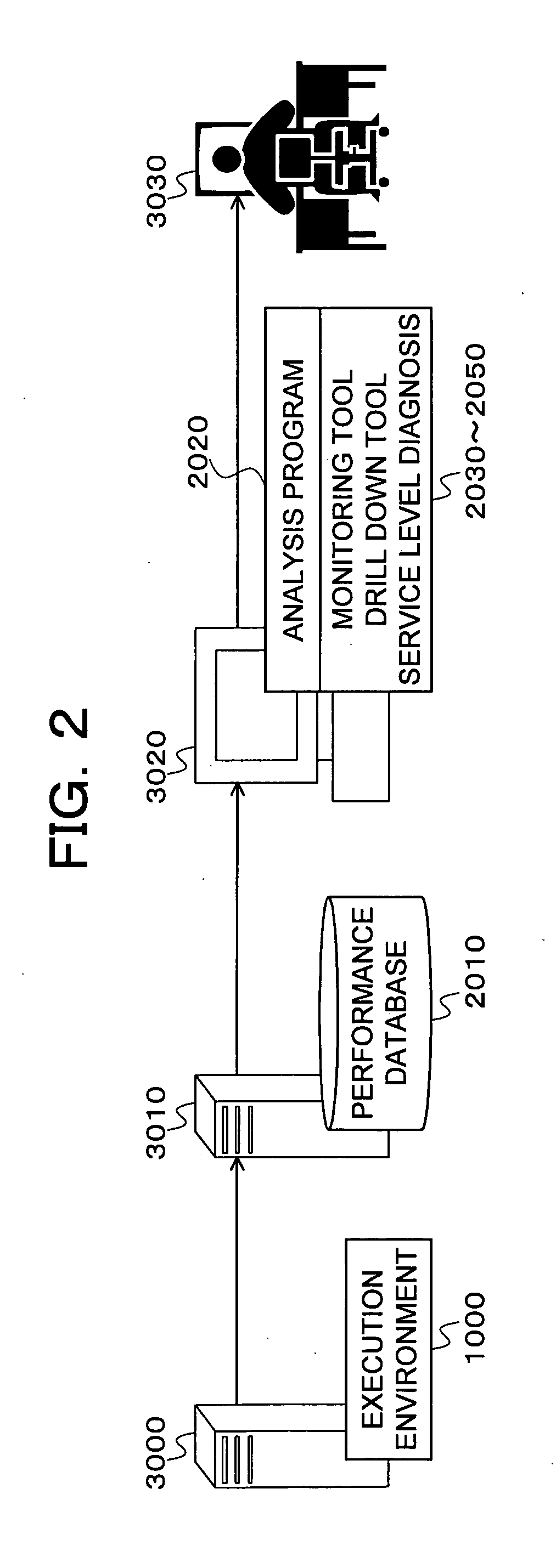
Measurement / analysis unit in a Java virtual machine has the function of measuring data when an event of garbage collection occurs, and the function of periodically measuring data. The measurement / analysis unit analyzes the measured data and predicts a danger of a memory shortage, and predicts a danger using an algorithm depending on the type of garbage collection used by the Java virtual machine. An application server is notified of a warning of the predicted danger of a memory shortage by an analysis result notification means by an inter-process communication, or the like. The measurement / analysis unit calculates a memory capacity required to avoid the predicted danger of a memory shortage, and the calculated memory capacity is transmitted to the application server by the analysis result notification means by an inter-process communication, or the like in the same way as the warning.
Owner:FUJITSU LTD
Efficiently boosting priority of read-copy update readers in a real-time data processing system
ActiveUS7734879B2Raise priorityMinimum of processing overheadProgram synchronisationMemory systemsReal-time dataRead-copy-update
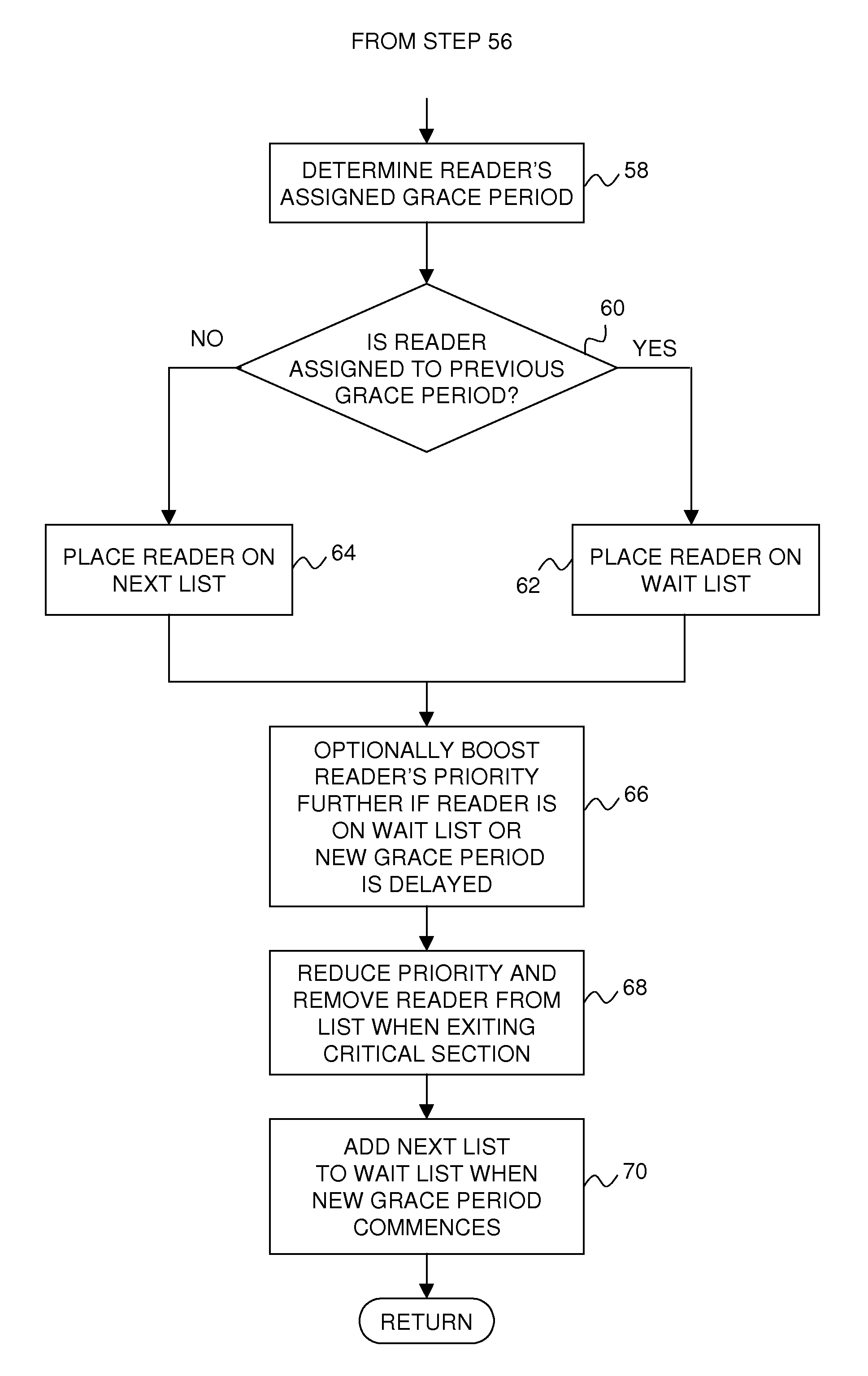
A technique for efficiently boosting the priority of a preemptable data reader in order to eliminate impediments to grace period processing that defers the destruction of one or more shared data elements that may be referenced by the reader until the reader is no longer capable of referencing the data elements. Upon the reader being subject to preemption or blocking, it is determined whether the reader is in a read-side critical section referencing any of the shared data elements. If it is, the reader's priority is boosted in order to expedite completion of the critical section. The reader's priority is subsequently decreased after the critical section has completed. In this way, delays in grace period processing due to reader preemption within the critical section, which can result in an out-of-memory condition, can be minimized efficiently with minimal processing overhead.
Owner:TWITTER INC
EMS memory sharing system, device and method
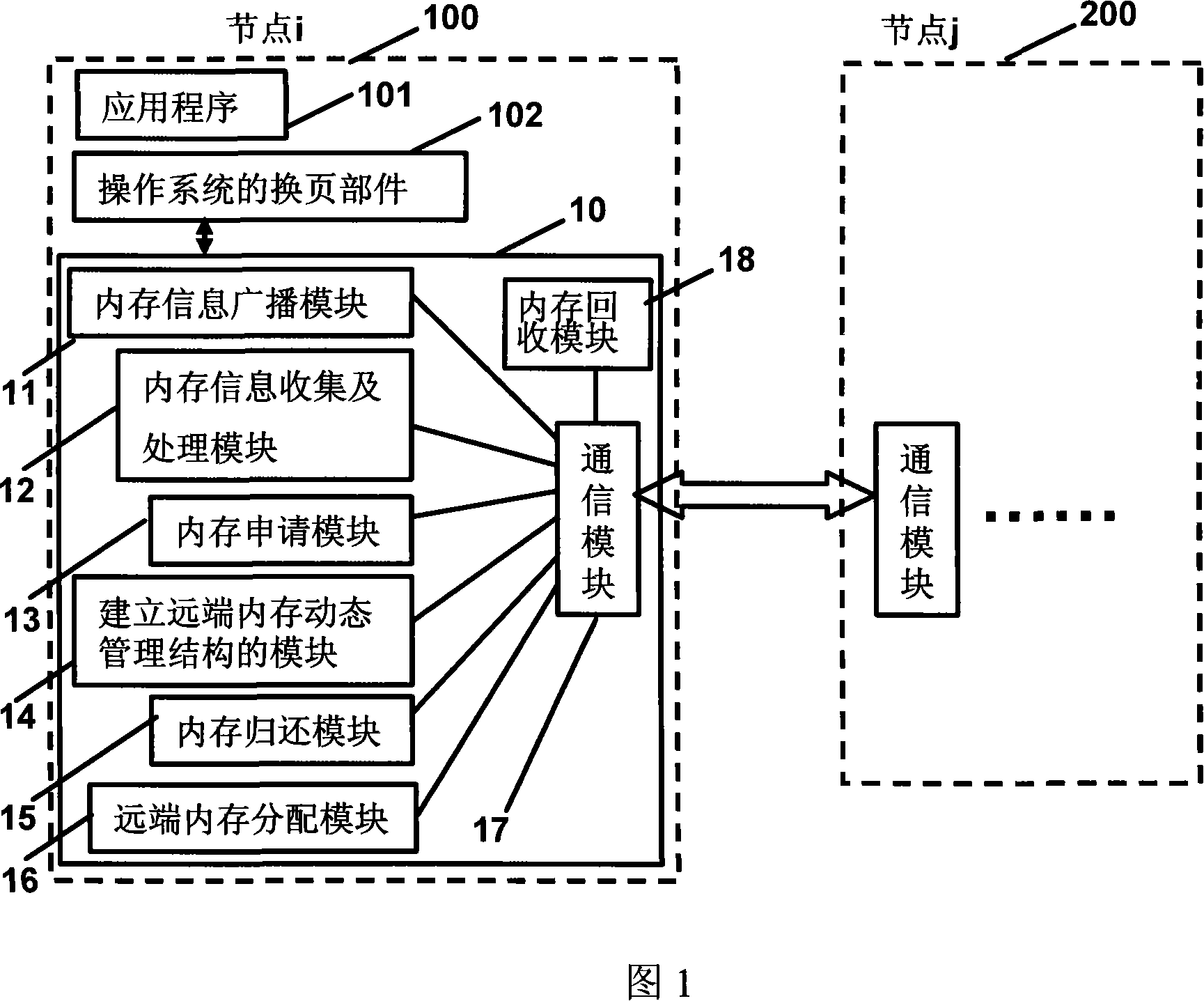
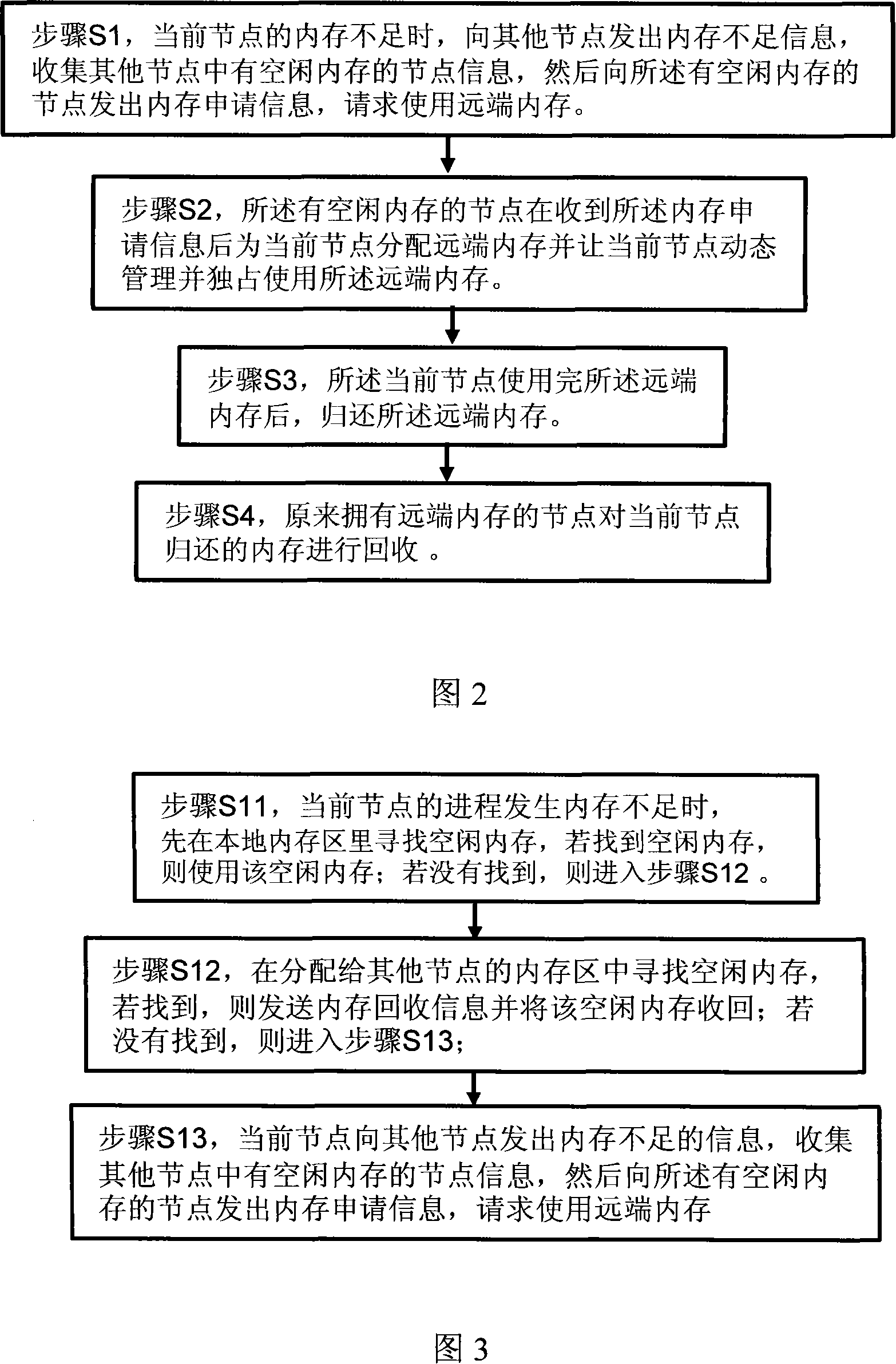
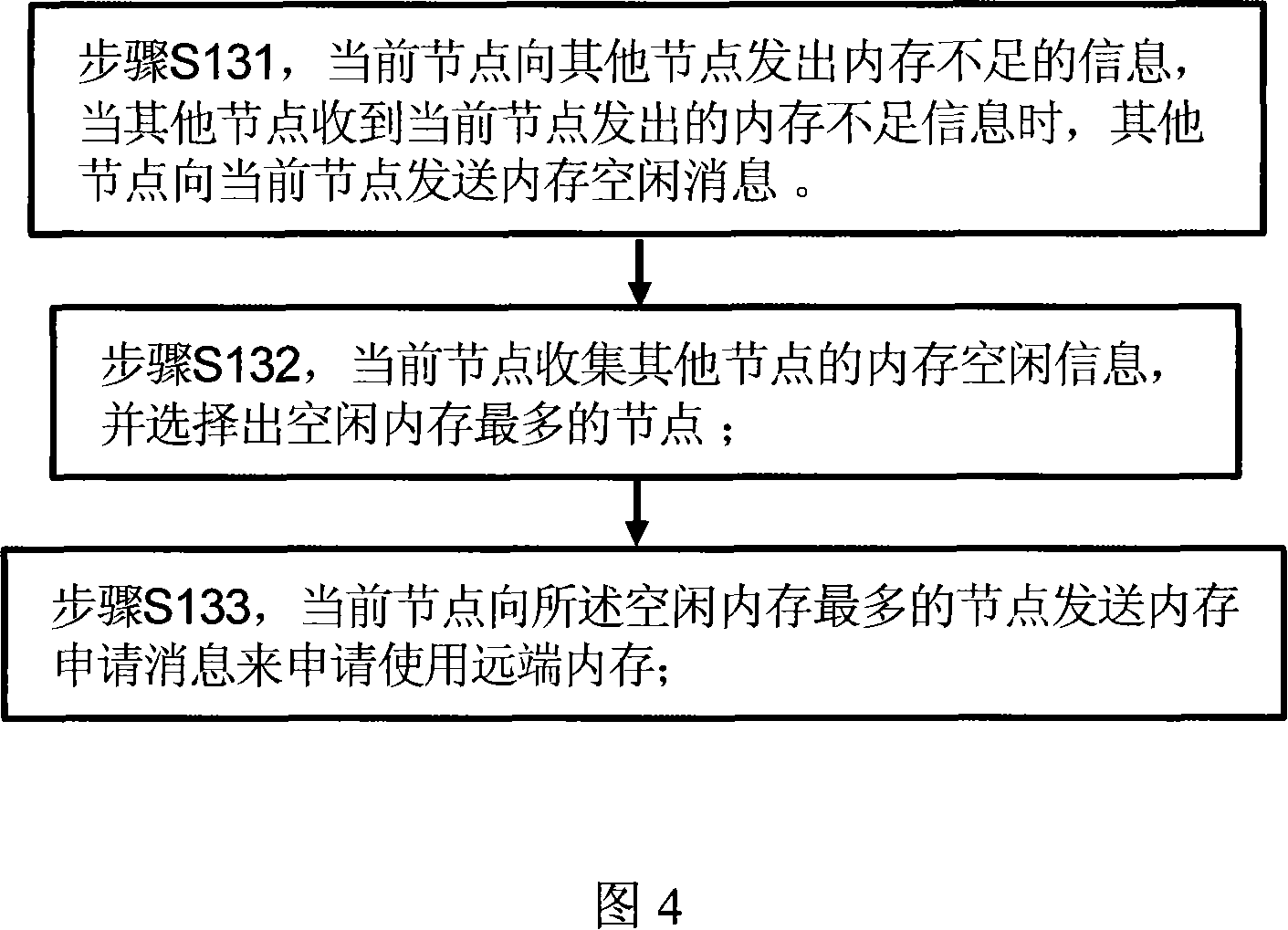
ActiveCN101158927AIncrease profitImprove reliabilityMemory adressing/allocation/relocationOperational systemOut of memory
The invention discloses a memory shared system and a device, as well as a method in a multi-core NUMA system. The system comprises a plurality of nodes; the operating system of each node comprises a memory shared device, the memory shared device comprises: a memory information collection and processing module, a memory application module, as well as a module establishing a distant end memory dynamic management structure and connected with a communication module. The method comprises the following steps: step S1, when the memory of a front node is deficient, the memory deficiency information is sent to other nodes, the node information of vacant memory in other nodes is collected, then the memory application information is sent to the nodes with vacant memory requesting the use of distant end memory; step S2, after receiving the memory application information, the nodes with vacant memory distributes the distant end memory with the current node, and let the current node dynamically manages and exclusively uses the distant end memory. The invention borrows the distant end vacant memory to accomplish the load leveling of the entire system.
Owner:HUAWEI TECH CO LTD
EL display apparatus and drive method of EL display apparatus
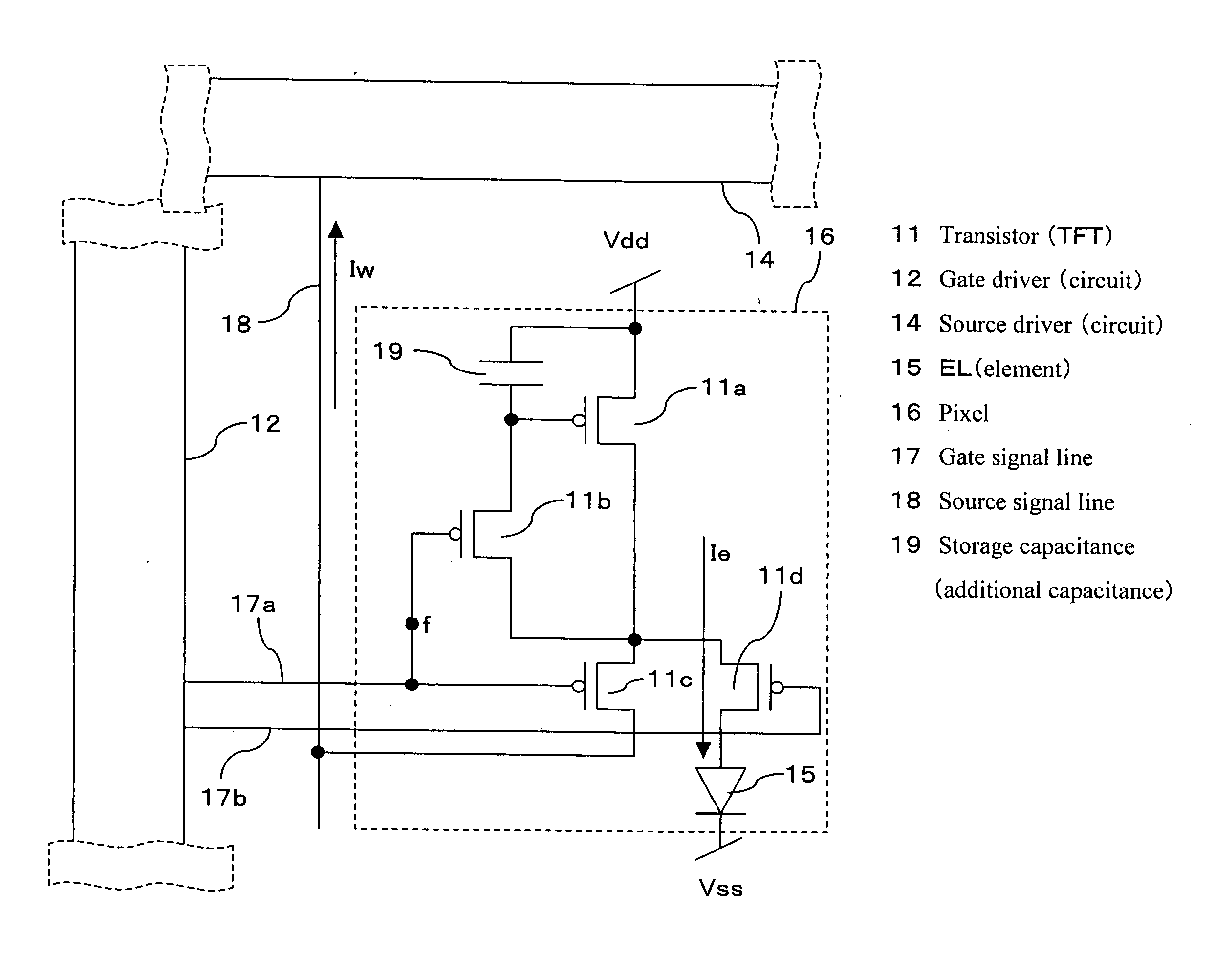
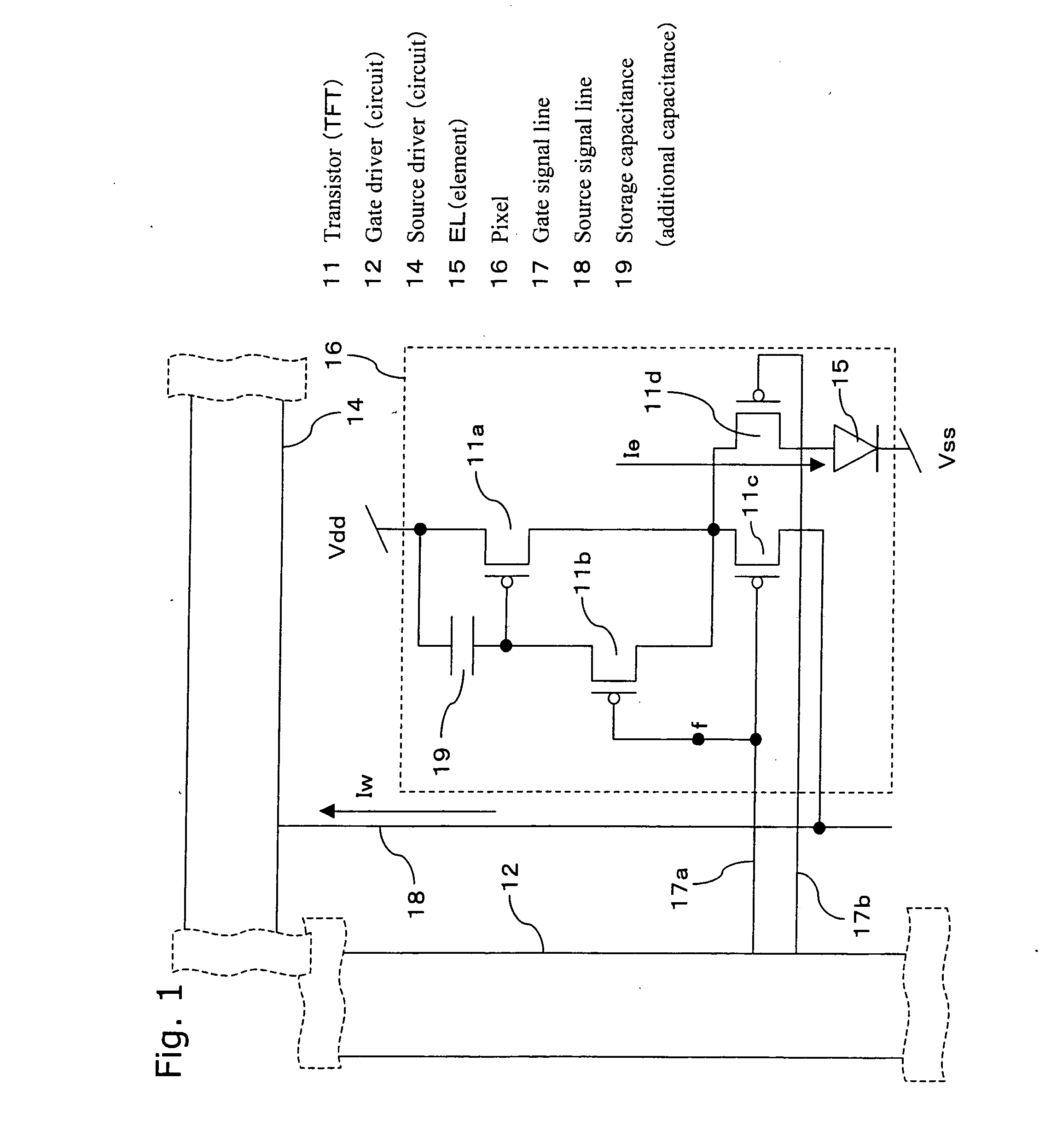
ActiveUS20070046587A1Avoid insufficient writingAvoiding insufficient writingSewerage structuresCathode ray tubes/electron beam tubesTerminal voltageOut of memory
A precharge voltage Vp is applied in period A. The precharge voltage Vp is generated by applying a constant current Iw to a pixel driving transistor of a display panel and using gate terminal voltage of the driving transistor which passes the constant current Iw. The gate terminal potential is held in memory. When displaying images on a display panel, the gate terminal potential is read out of memory, and used as the precharge voltage Vp after arithmetic processing. By the application of the precharge voltage Vp, a source signal line is charged and discharged quickly so that an almost target tone current will flow through the driving transistor. Furthermore, a more accurate program current is written into the pixel during period B.
Owner:JAPAN DISPLAY CENT INC
Extended instruction set for packet processing applications
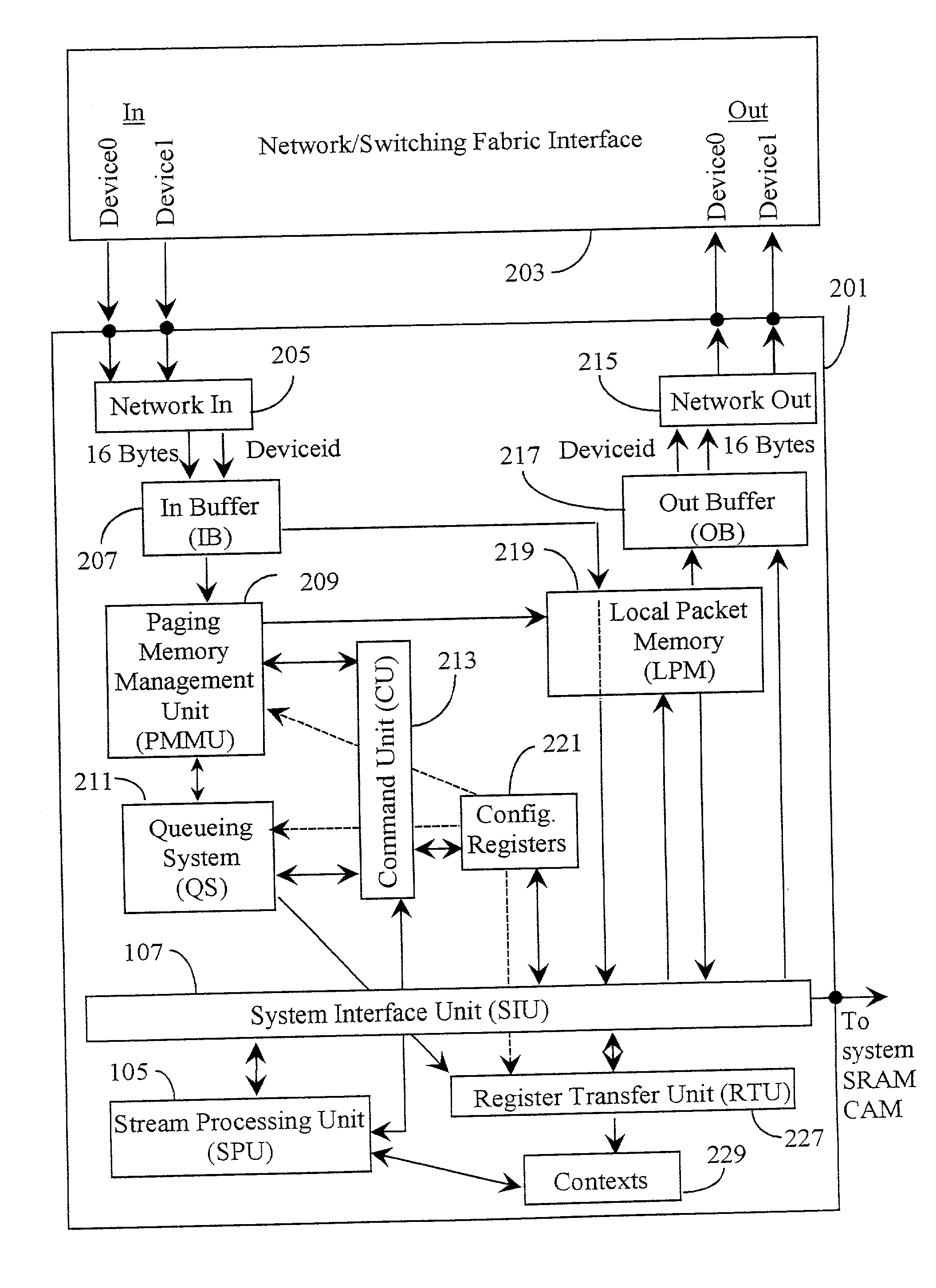
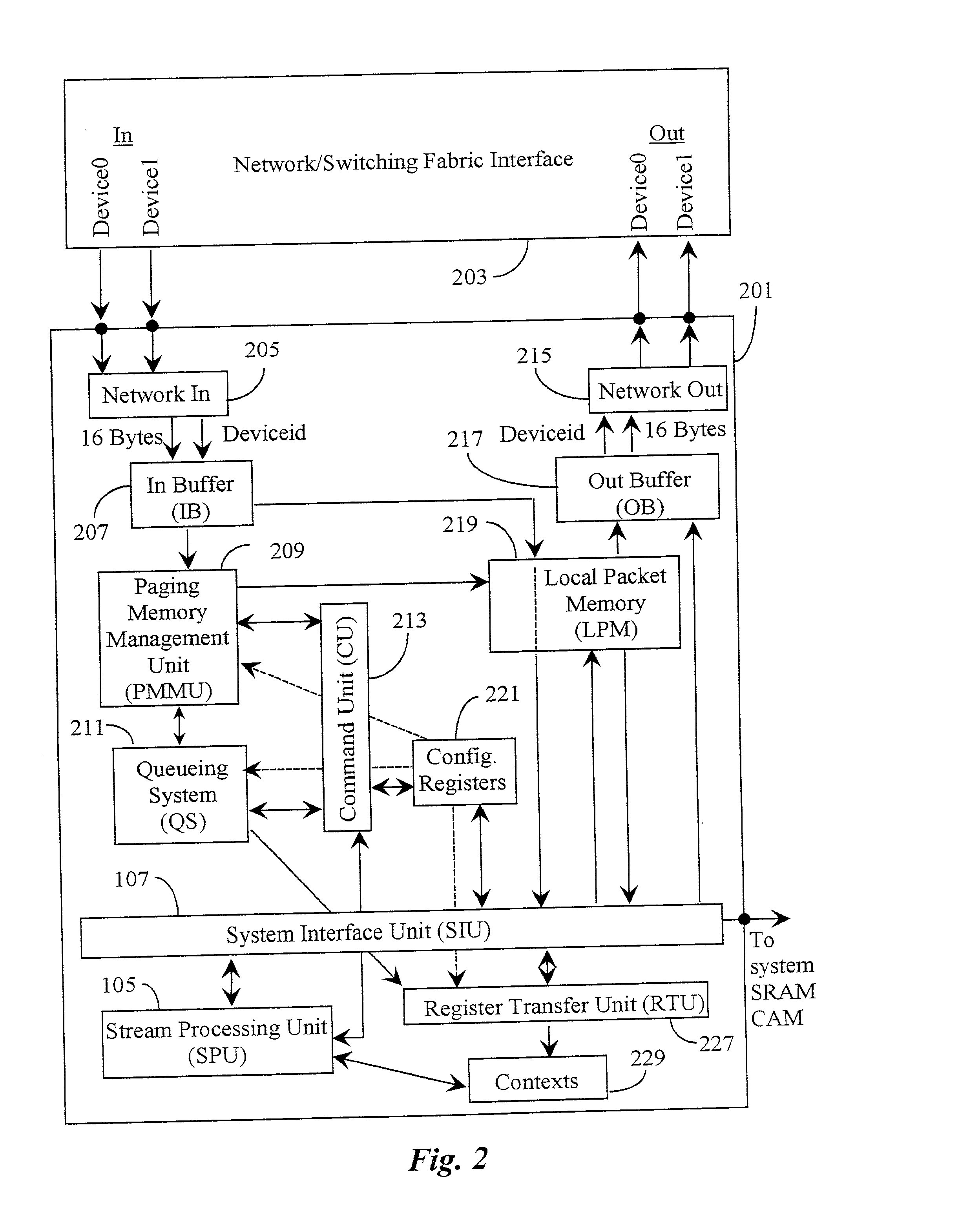
InactiveUS20020054603A1Memory adressing/allocation/relocationDigital computer detailsManagement unitOut of memory
A software program extension for a dynamic multi-streaming processor is disclosed. The extension comprising an instruction set enabling coordinated interaction between a packet management component and a core processing component of the processor. The software program comprises, a portion thereof for managing packet uploads and downloads into and out of memory, a portion thereof for managing specific memory allocations and de-allocations associated with enqueueing and dequeuing data packets, a portion thereof for managing the use of multiple contexts dedicated to the processing of a single data packet; and a portion thereof for managing selection and utilization of arithmetic and other context memory functions associated with data packet processing. The extension complements standard data packet processing program architecture for specific use for processors having a packet management unit that functions independently from a streaming processor unit.
Owner:ARM FINANCE OVERSEAS LTD
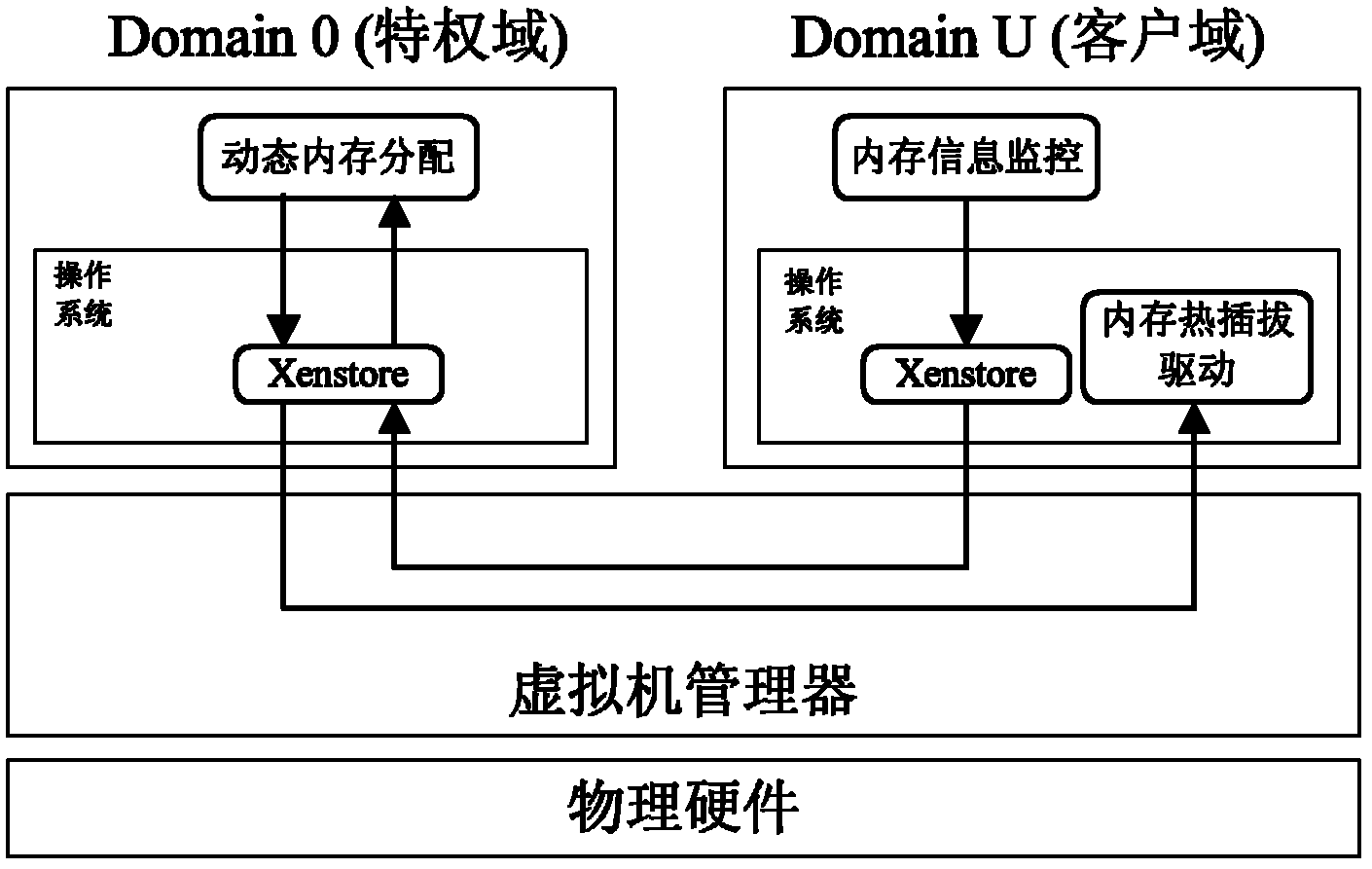
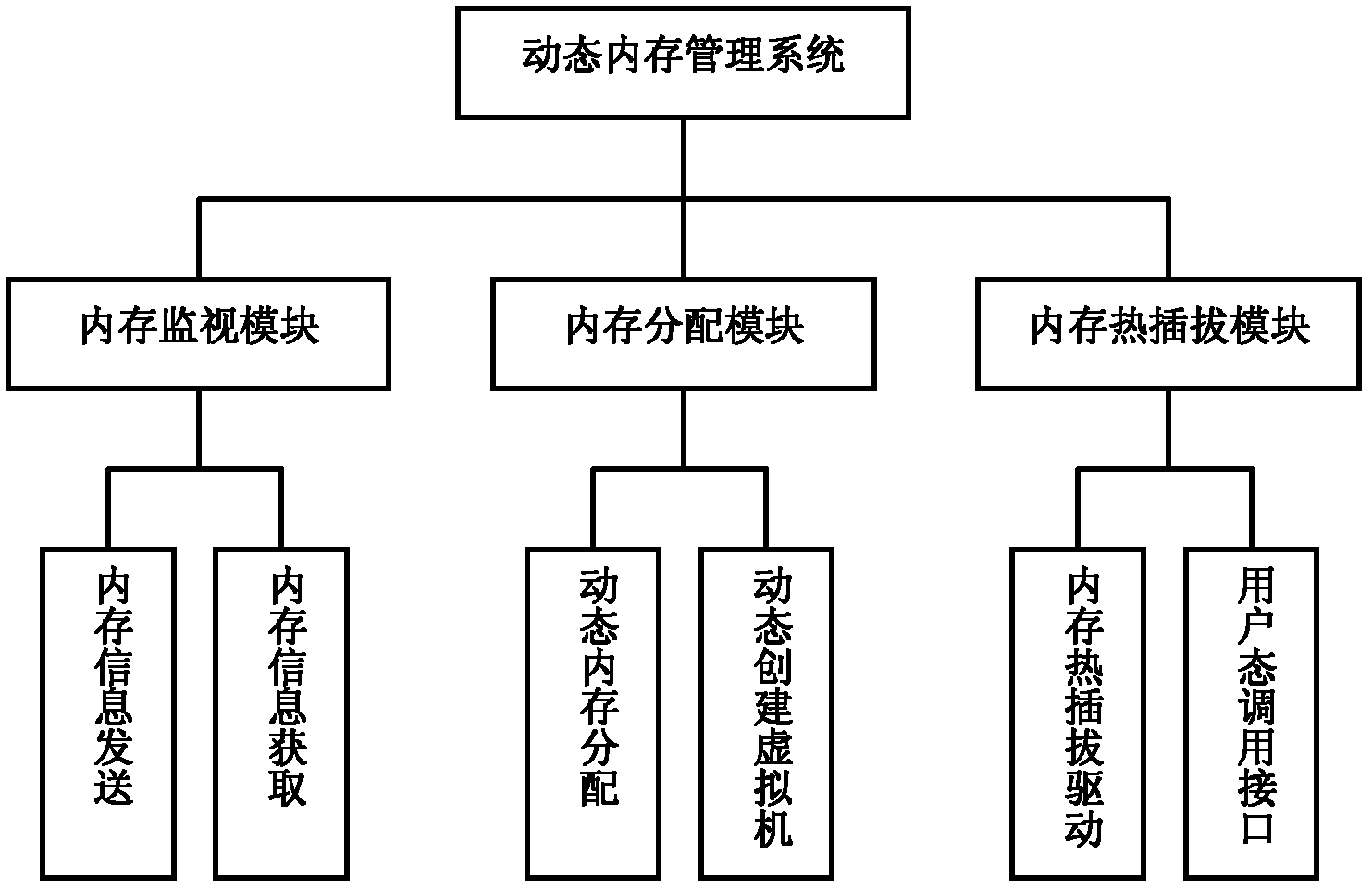
Dynamic memory management system based on memory hot plug for virtual machine
InactiveCN102222014AMemory Pressure PredictionMemory pressure balanceMemory adressing/allocation/relocationSoftware simulation/interpretation/emulationOut of memoryGNU/Linux
The invention discloses a dynamic memory management system based on memory hot plug for a virtual machine, comprising a memory monitoring module, a memory distributing module and a memory hot plug module. The memory hot plug module adopts Linux memory hot plug mechanism to realize memory hot plug on a semi-virtual Linux virtual machine, thereby breaking through the initial memory toplimit of the virtual machine and efficiently improving the memory expandability of the virtual machine by increasing and reducing the memory randomly. On one hand, the memory distributing module dynamically predicts the memory requirement of the virtual machine and balances the memory pressure of each virtual machine, thereby being capable of satisfying the memory requirement of the virtual machine and also improving the memory utilization ratio of a physical machine; on the other hand, the memory distributing module can establish a new virtual machine by reasonably reducing the memory of the existing virtual machine when the memory of the physical machine is not enough, thereby realizing memory overuse and improving the memory utilization ratio of the physical machine.
Owner:HUAZHONG UNIV OF SCI & TECH
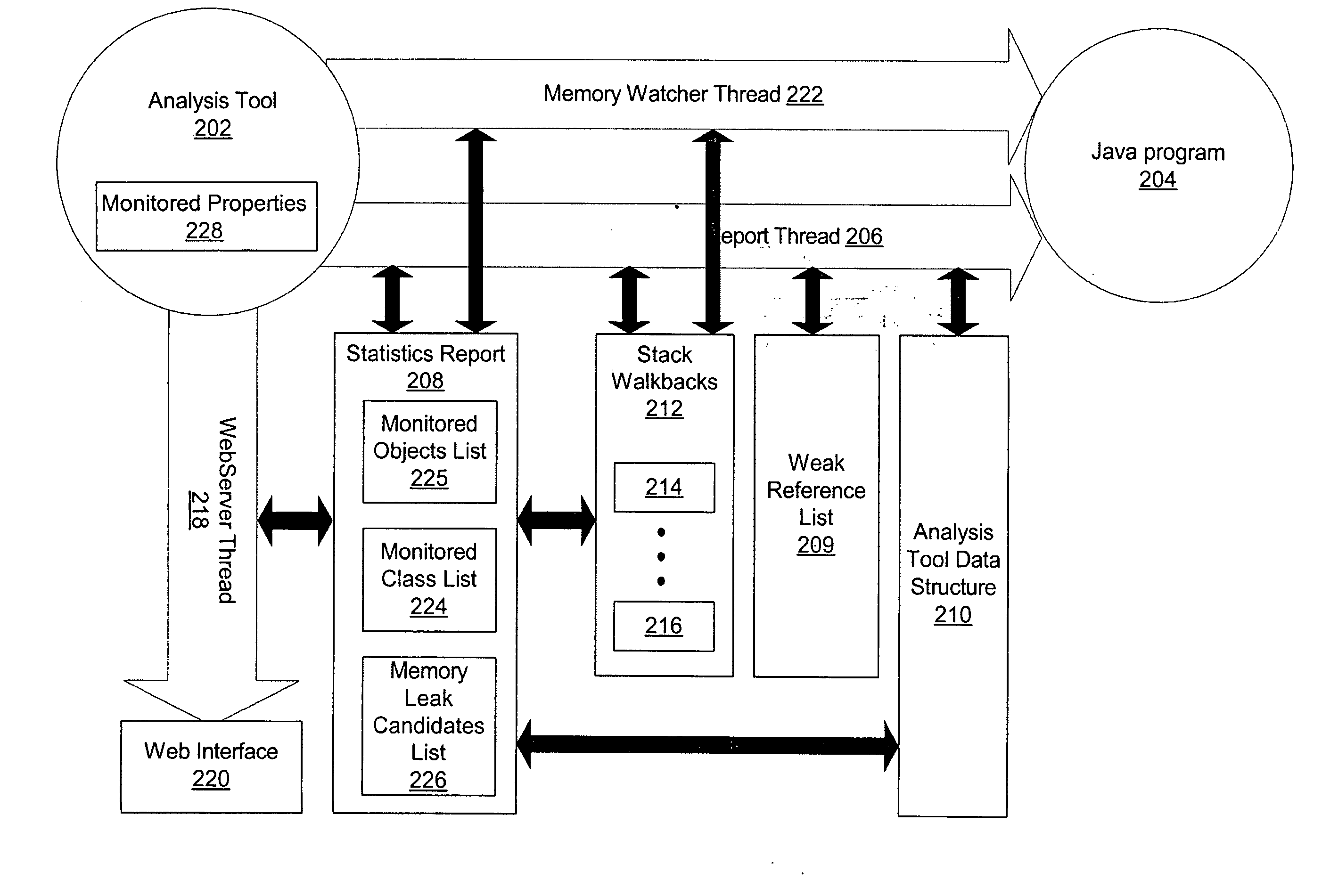
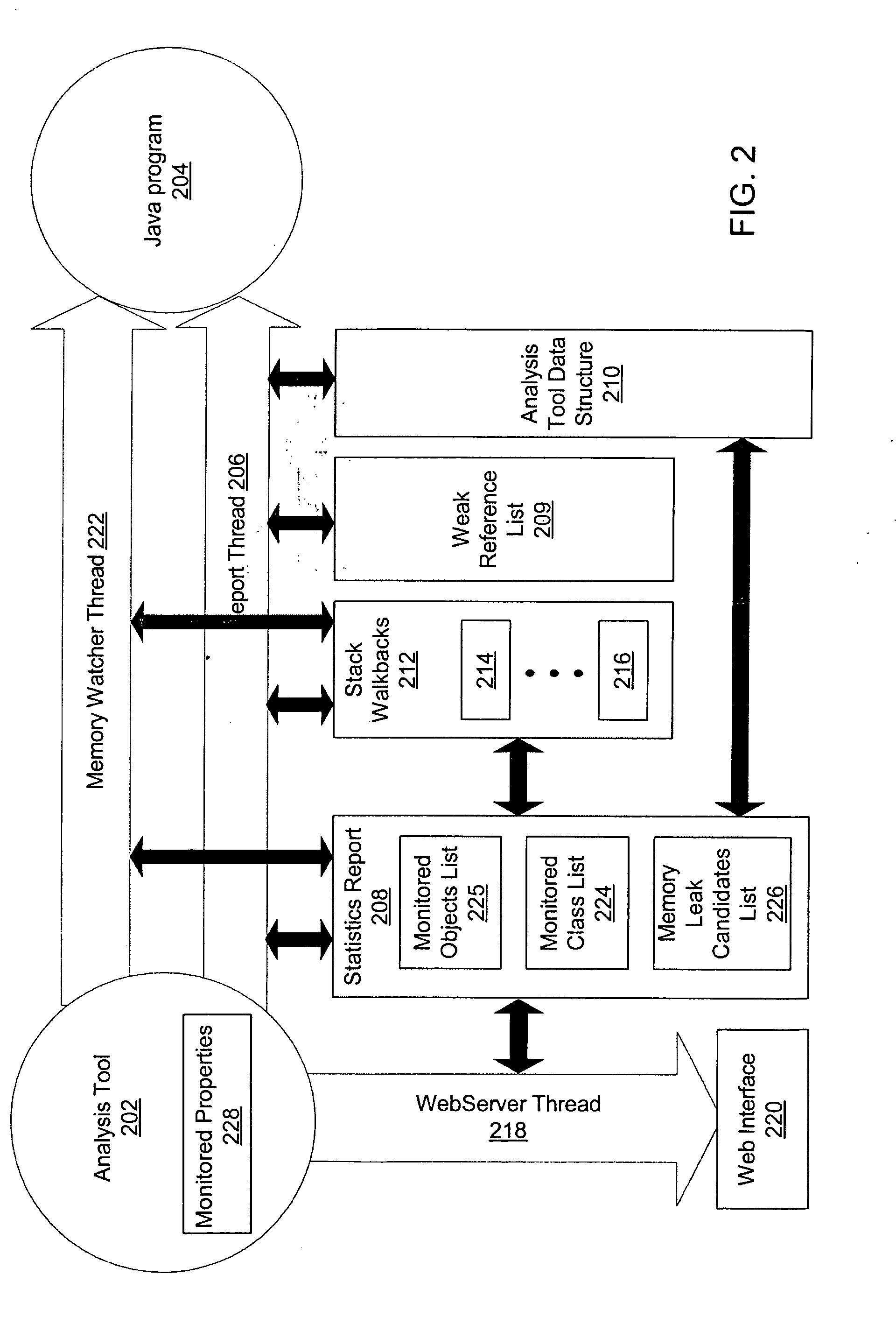
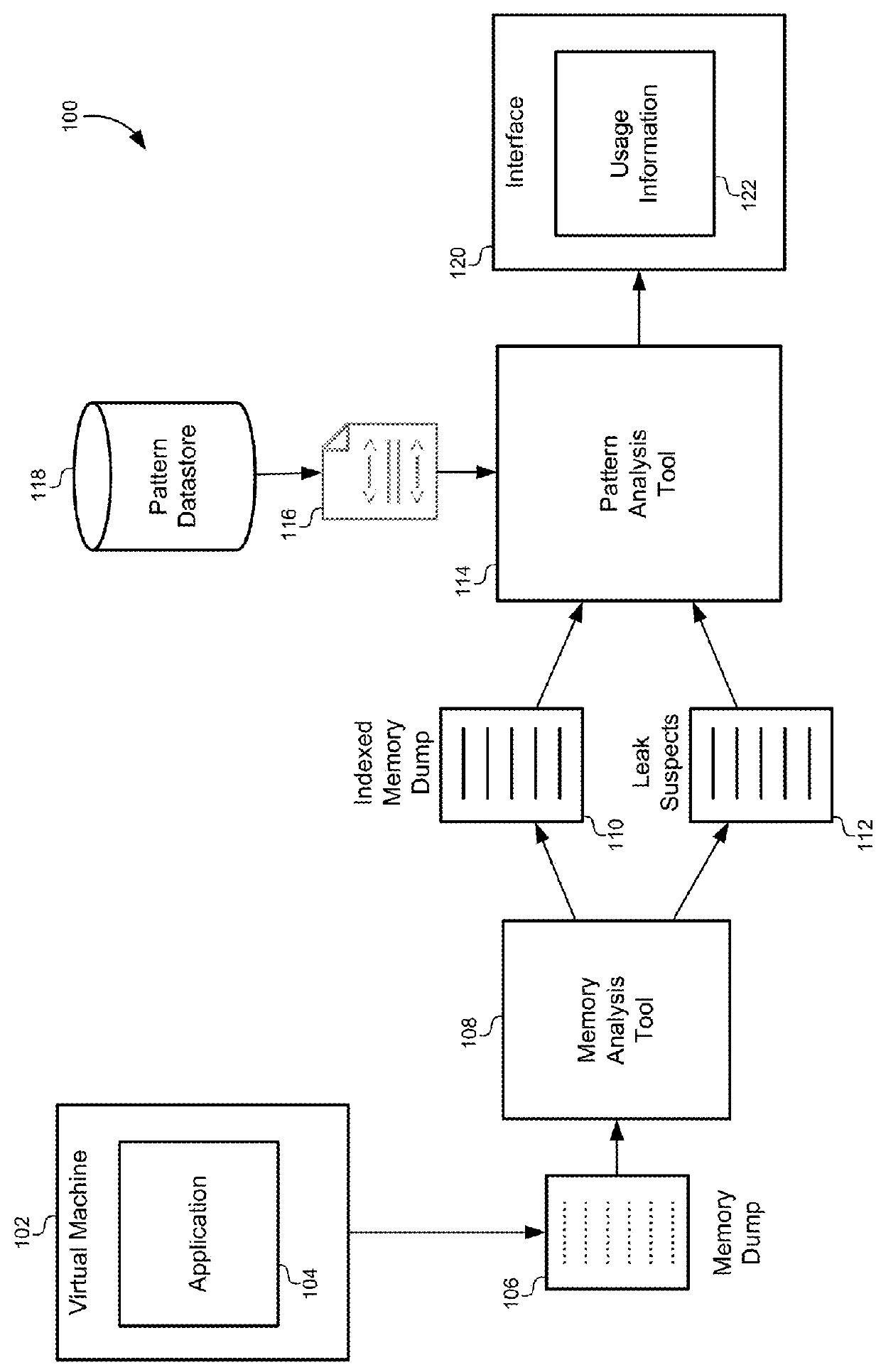
Method, system and article for detecting critical memory leaks causing out-of-memory errors in Java software
InactiveUS20050204341A1Error detection/correctionSpecific program execution arrangementsObject ClassSoftware system
An analysis tool for specifically identifying the cause and location of critical memory leaks within a large software system is provided. The analysis tool transparently adds multiple processing threads that collaborate to identify sources of potential memory leaks in the software being analyzed. These threads provide notifications of object classes executing in the software that have had excessive instance counts or have exceeded the average lifetime of an object. A stack walkback is performed on objects being monitored as an out-of-memory condition approaches and while there is still sufficient memory available to unwind and store the stack walkback. By saving the stack walkbacks just prior to the out-of-memory failure, the analysis tool operator is thereby provided sufficient information to make a final determination of objects that are possible candidates for memory leaks and subsequently modify the software to reduce or eliminate the memory leaks.
Owner:IBM CORP
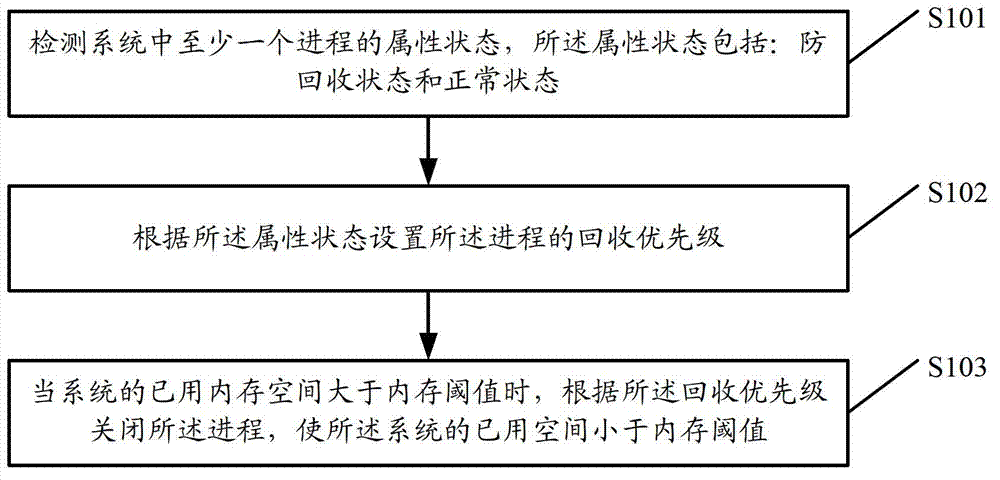
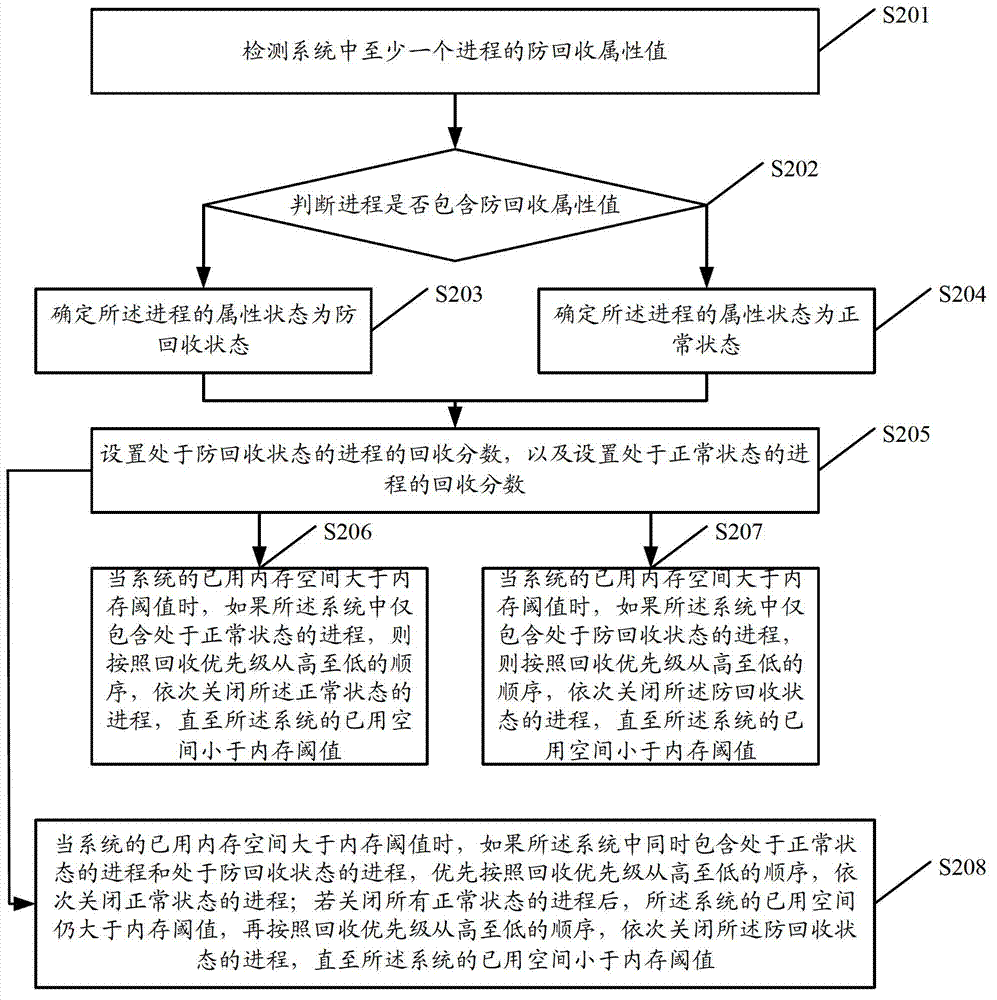
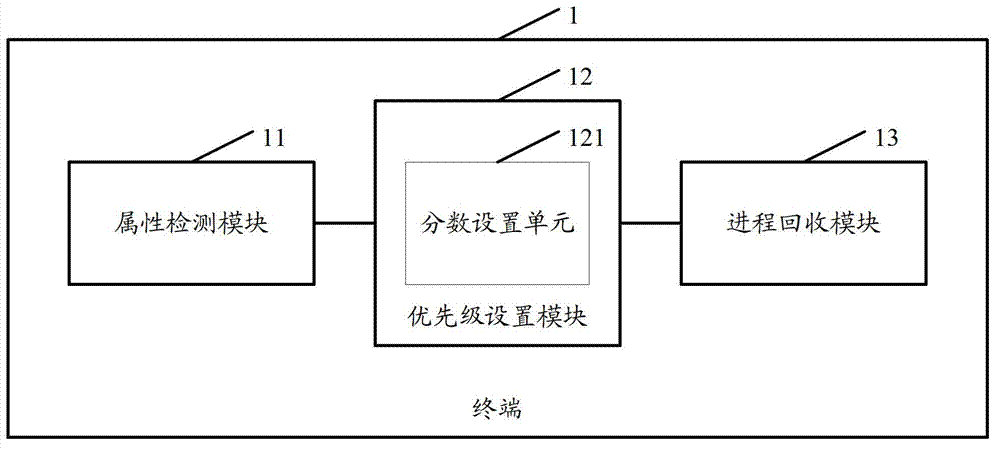
Method and terminal of process management
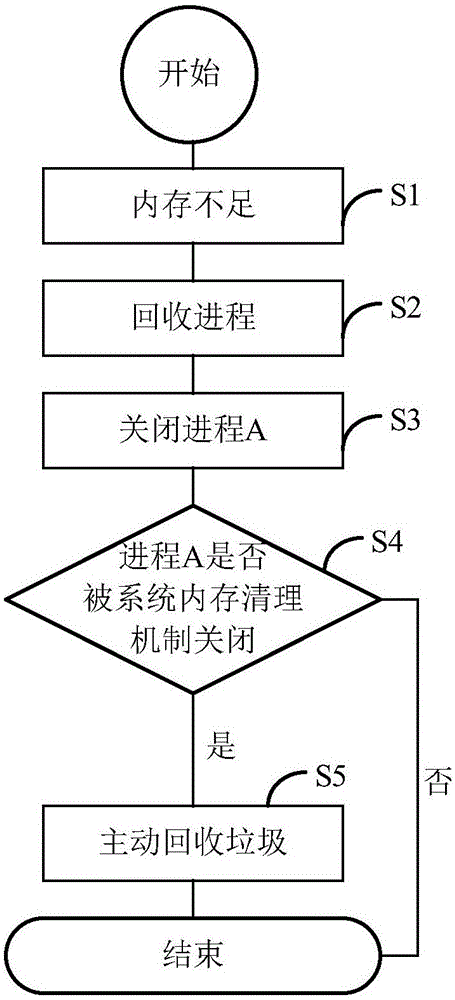
InactiveCN103092689AImprove intelligenceGuaranteed fluencyMultiprogramming arrangementsOut of memoryComputer science
The invention discloses a method and a terminal of process management. The method of the process management comprises detecting attribute states of at least one course in a system, wherein the attribute states comprise a recovery prevention state and a normal state; setting recovery priority of the course according to the attribute states; and closing the course according to the recovery priority when used memory space of the system is larger than an internal storage threshold value, and enabling the used memory space of the system to be smaller than the internal storage threshold value. The method and the terminal of the process management are capable of reducing possibility that an important course is closed because of insufficient memory, and improve intelligence of the terminal of the process management.
Owner:SHENZHEN GIONEE COMM EQUIP
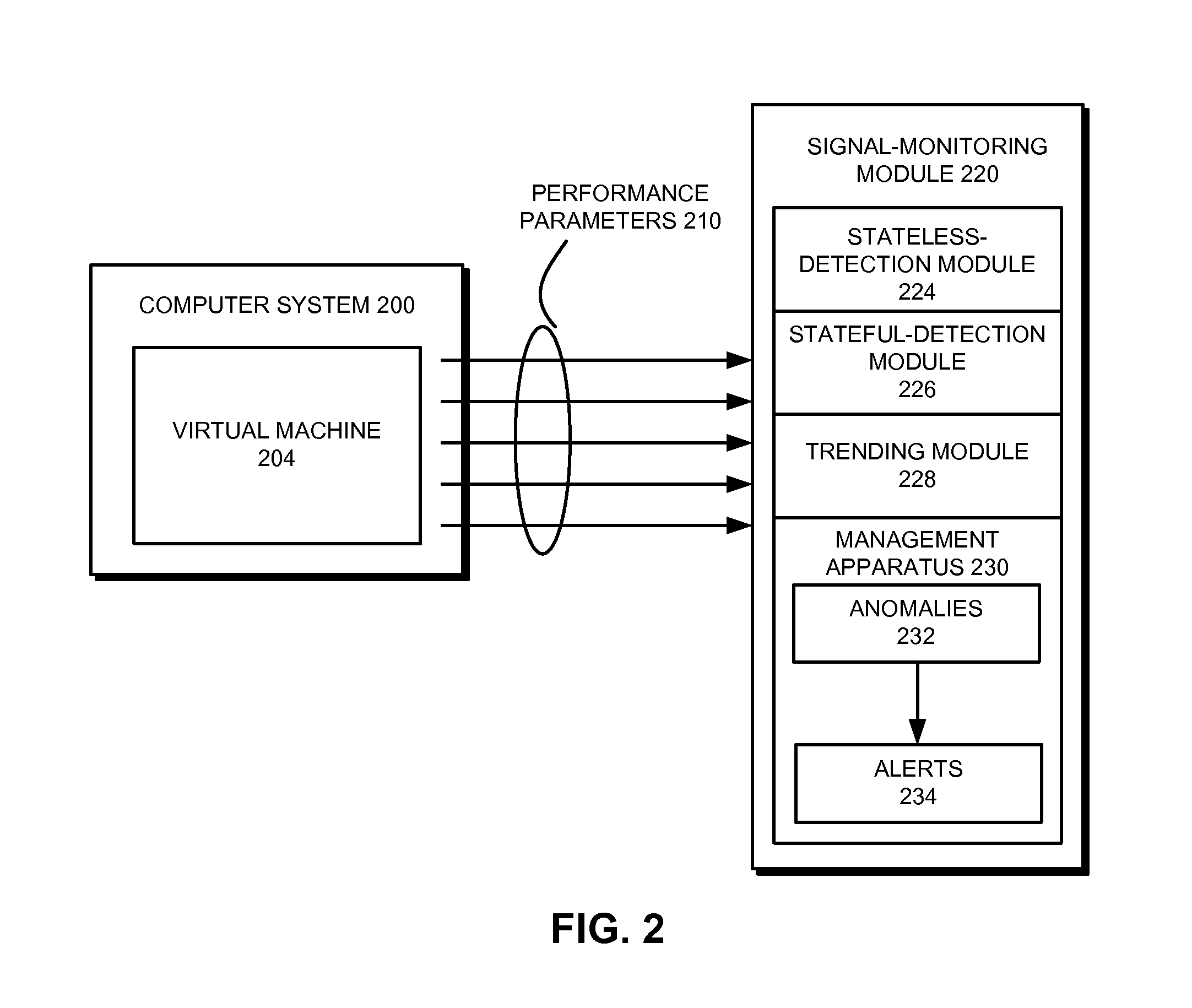
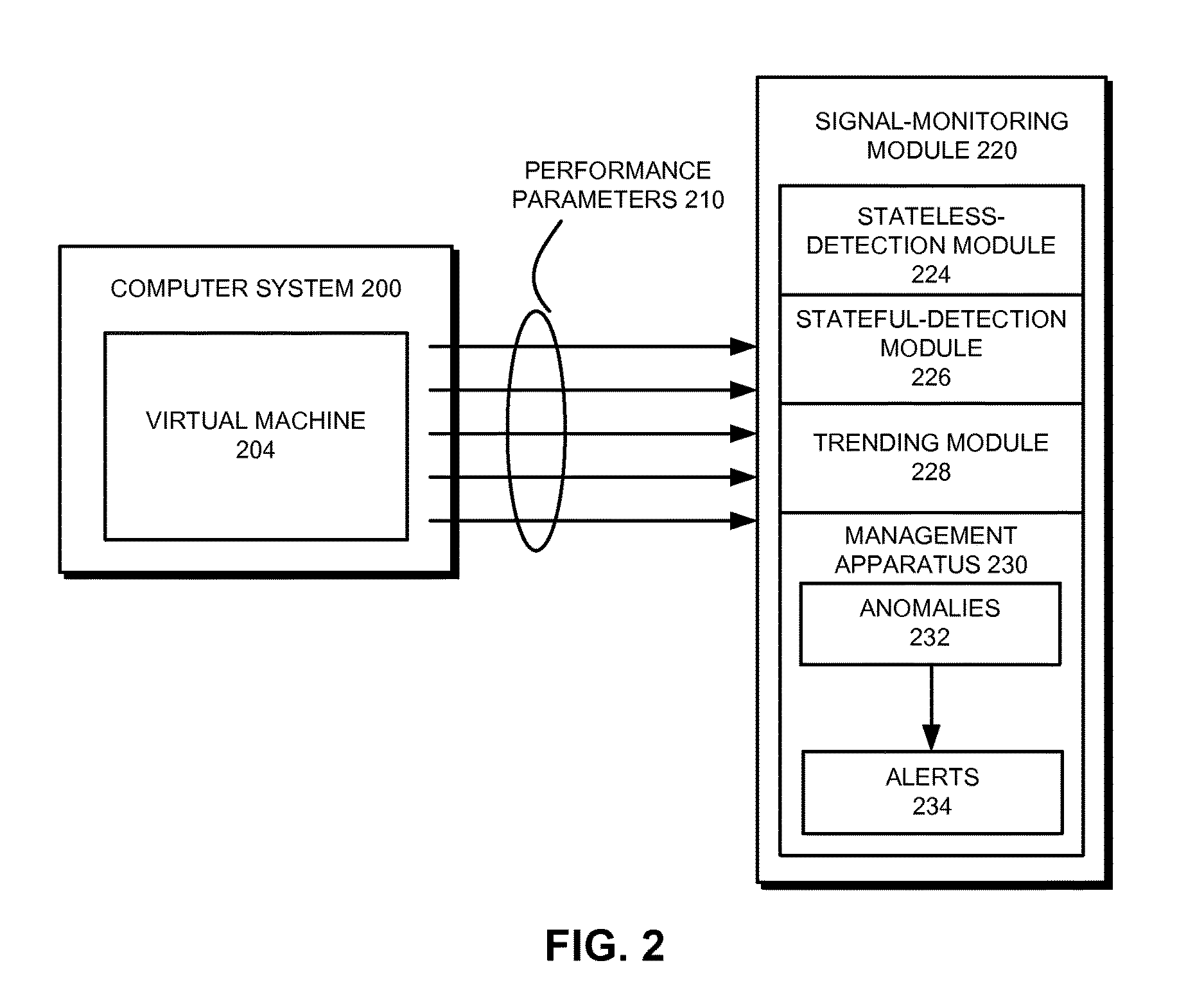
Stateless detection of out-of-memory events in virtual machines
ActiveUS20160371181A1Input/output to record carriersMemory adressing/allocation/relocationOut of memoryComputerized system
The disclosed embodiments provide a system that detects anomalous events in a virtual machine. During operation, the system obtains time-series garbage-collection (GC) data collected during execution of a virtual machine in a computer system. Next, the system generates one or more seasonal features from the time-series GC data. The system then uses a sequential-analysis technique to analyze the time-series GC data and the one or more seasonal features for an anomaly in the GC activity of the virtual machine. Finally, the system stores an indication of a potential out-of-memory (OOM) event for the virtual machine based at least in part on identifying the anomaly in the GC activity of the virtual machine.
Owner:ORACLE INT CORP
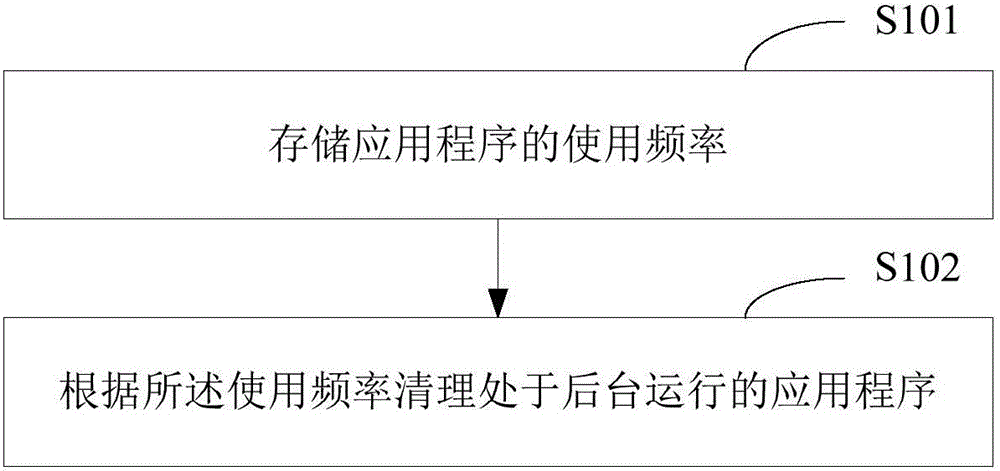
Application clearing method and application clearing device
ActiveCN104866366ASolve the problem of not running smoothlyProgram loading/initiatingOperational systemOut of memory
The invention is applicable to the technical field of an intelligent terminal, and provides an application clearing method and an application clearing device. The method comprises the following steps of storing the use frequencies of applications and clearing background running applications according to the use frequencies. The method and the device have the advantages that the goal of intelligently clearing inactive applications in an operating system according to the use conditions of the applications by a user is achieved, so that a system memory is released, and the problem of unsmooth operation of a mobile phone due to insufficient memory after the long-time use of an intelligent mobile phone is solved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Semiconductor memory device highly integrated in direction of columns
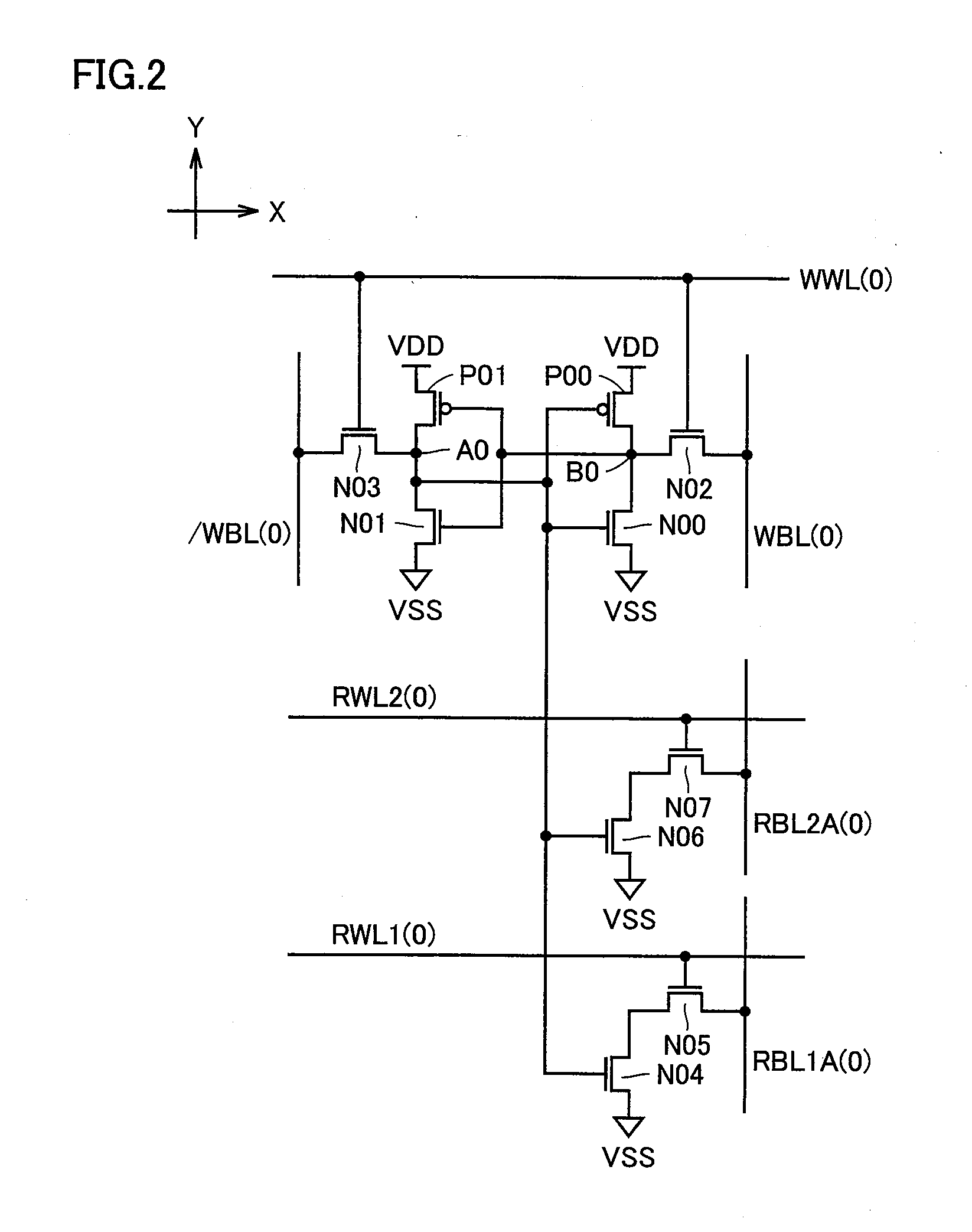
InactiveUS20090244950A1Stable readingEasy to integrateTransistorSolid-state devicesComputer architectureOut of memory
First and second read word lines are provided in each set made of two adjacent rows. First, second, third, and fourth read bit lines are provided in each column. Each of the first and second read word lines is connected to memory cells in a corresponding one of the sets. Each of the first and third read bit lines is connected to a memory cell in one row in each of the sets, out of memory cells in a corresponding one of the columns. Each of the second and fourth read bit lines is connected to a memory cell in the other row in each of the sets, out of the memory cells in the corresponding one of the columns.
Owner:RENESAS ELECTRONICS CORP
Application control method and apparatus
ActiveCN105260117ASolve the problem of lag caused by insufficient memoryImprove smooth performanceInput/output processes for data processingMemory footprintOut of memory
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD +1
Method and device for managing internal memory of mobile communication equipment terminal
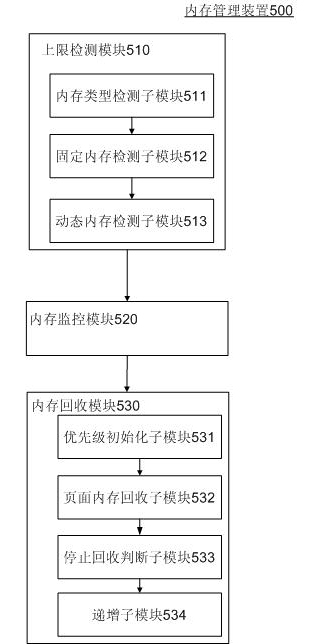
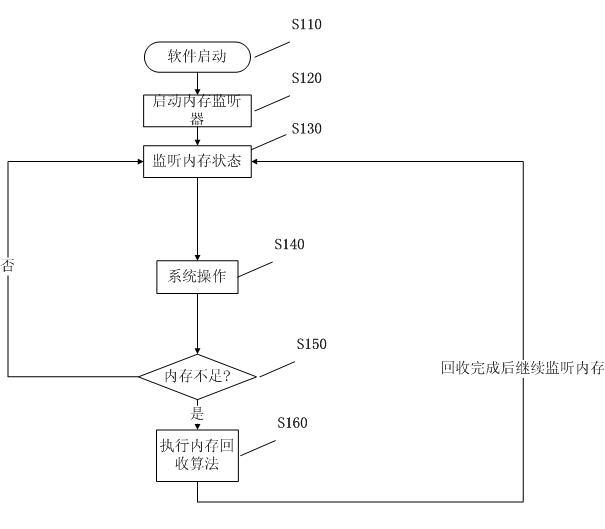
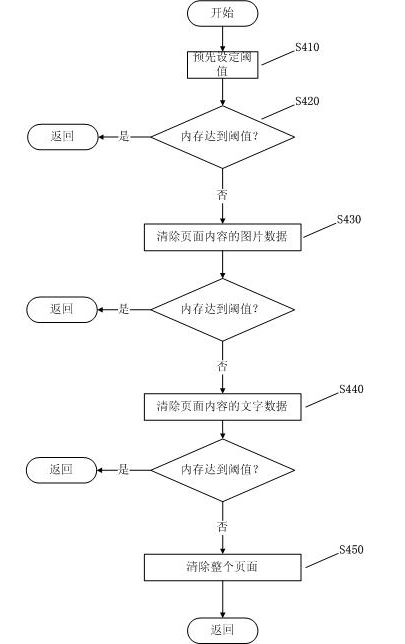
ActiveCN101908022AGuaranteed experienceSave money on internetMemory adressing/allocation/relocationSubstation equipmentInternal memoryTraffic capacity
The invention relates to the technical field of mobile communication equipment terminals, in particular to a method for managing an internal memory of a mobile communication equipment terminal. The method comprises the following steps of: detecting an upper limit, wherein the mobile communication equipment terminal determines the upper limit of the internal memory of a system; monitoring the internal memory, wherein the mobile communication equipment terminal monitors the internal memory state; and recovering the internal memory, wherein an internal memory recovery algorithm is executed when the mobile communication equipment terminal monitors that the internal memory is insufficient. The internal memory is optimally used, and the browsing experience of middle-and-low mobile communication equipment is ensured by using an intelligent internal memory management algorithm. The cache technology is optimized, page data is cached as much as possible, the frequent networking is reduced, and the traffic is reduced so as to reduce the internet access expenditure of a user. The dynamic internal memory is optimized, and the optimal utilization of the dynamic internal memory is ensured. The internal memory of the mobile communication equipment terminal is intelligently managed, and the smooth operation of programs and the stability of a mobile phone are ensured. The user experience is ensured.
Owner:UCWEB
Free memory trending for detecting out-of-memory events in virtual machines
ActiveUS20160371180A1Memory architecture accessing/allocationMemory adressing/allocation/relocationOut of memoryComputerized system
The disclosed embodiments provide a system that detects anomalous events in a virtual machine. During operation, the system obtains time-series virtual machine (VM) data including garbage-collection (GC) data collected during execution of a virtual machine in a computer system. Next, the system computes, by a service processor, a time window for analyzing the time-series VM data based at least in part on a working time scale of high-activity patterns in the time-series GC data. The system then uses a trend-estimation technique to analyze the time-series VM data within the time window to determine an out-of-memory (OOM) risk in the virtual machine. Finally, the system stores an indication of the OOM risk for the virtual machine based at least in part on determining the OOM risk in the virtual machine.
Owner:ORACLE INT CORP
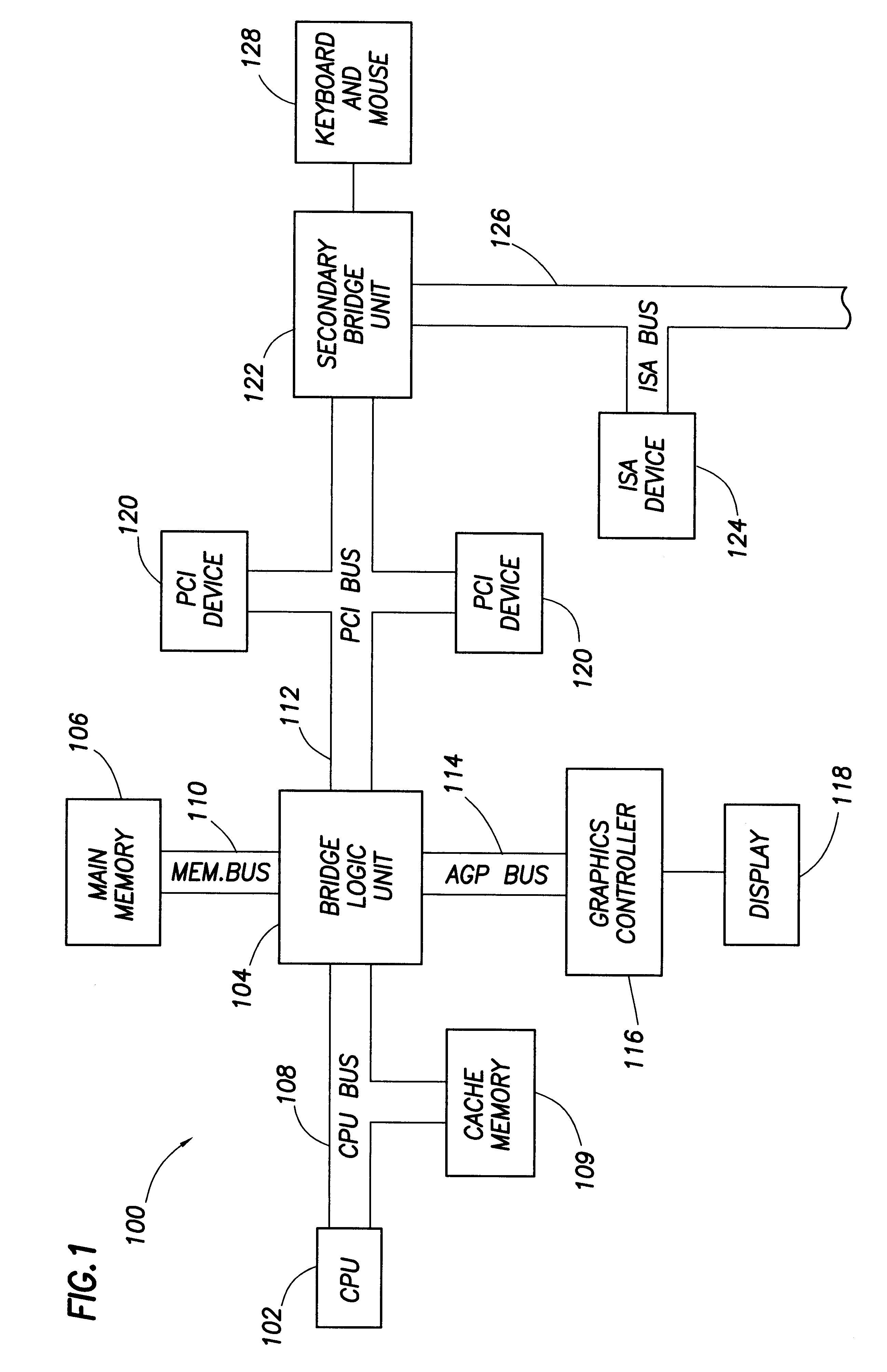
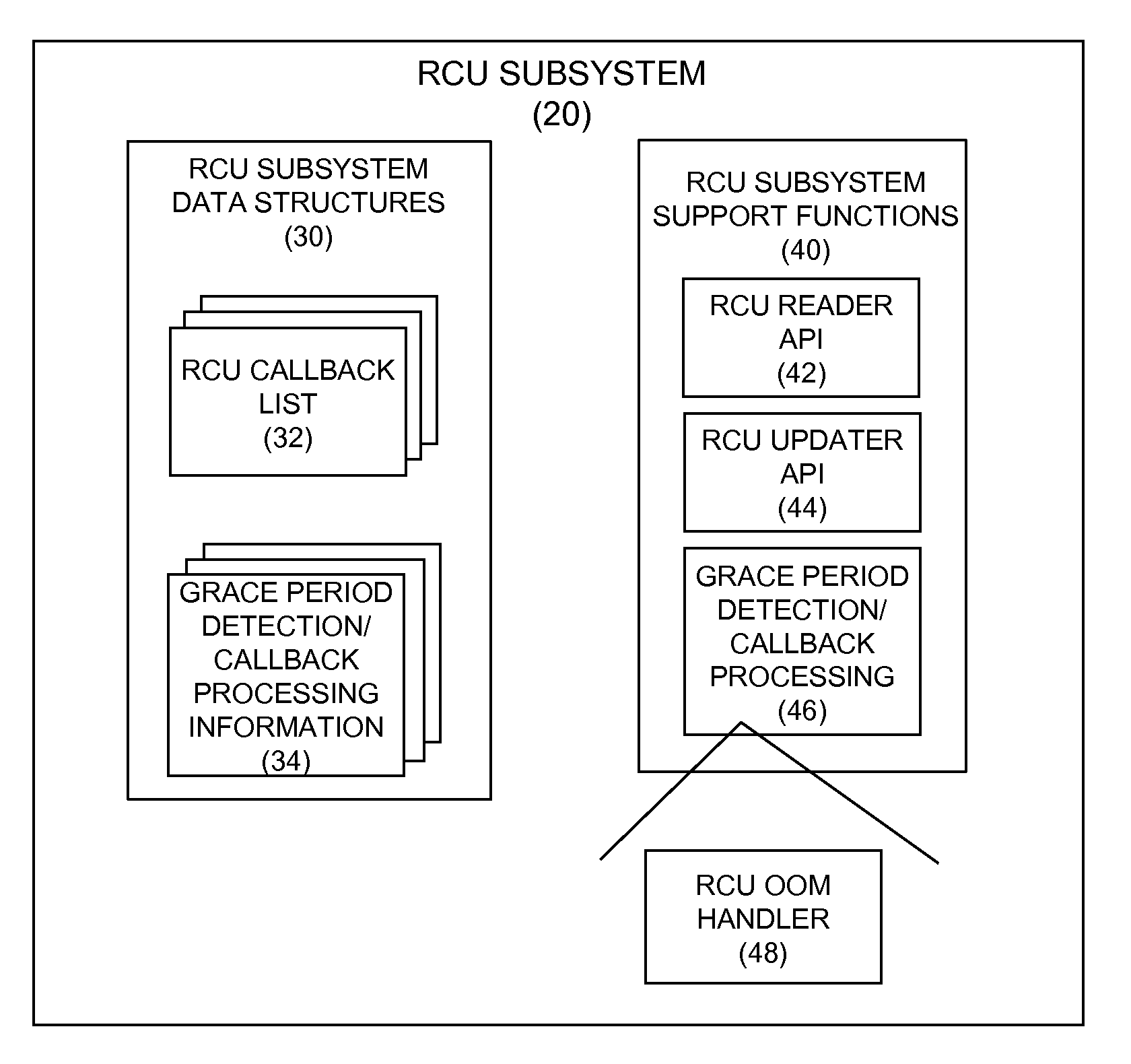
Motivating lazy RCU callbacks under out-of-memory conditions
InactiveUS8972801B2Input/output to record carriersError detection/correctionOut of memoryEmbedded system
Owner:INT BUSINESS MASCH CORP
Memory cleaning system and memory cleaning method
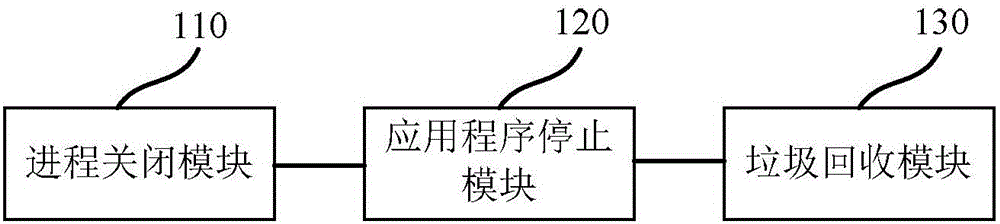
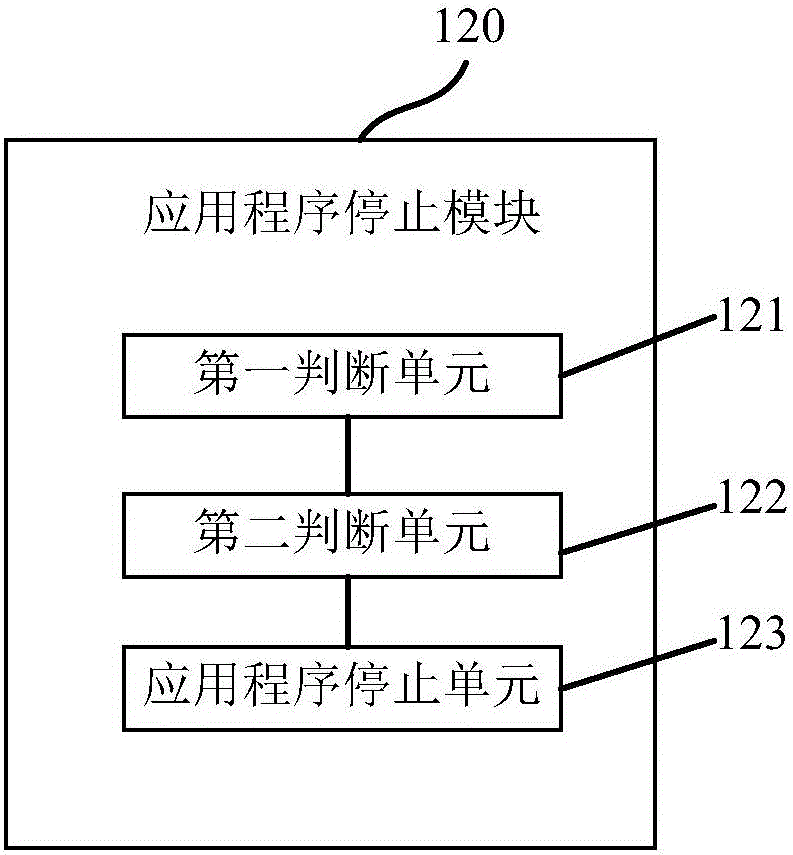
PendingCN106354562ARelease moreImprove cleaning efficiencyResource allocationOut of memoryComputer science
The invention discloses a memory cleaning system and a memory cleaning method. The memory cleaning system comprises a process closing module for closing a recyclable process at the condition of insufficient memory, an application stop module for stopping the application program belonging to the closed recyclable process, and a garbage recycling module for recycling garbage files generated by the closed process and the stopped application program during running, and releasing memory space. By the memory cleaning system, the memory cleaning efficiency can be improved.
Owner:SHENZHEN TECNO TECH CO LTD
Memory management method and device for multiprocess system
ActiveCN103425592AEasy to manageAvoid it happening againMemory adressing/allocation/relocationSpecific program execution arrangementsOperational systemOut of memory
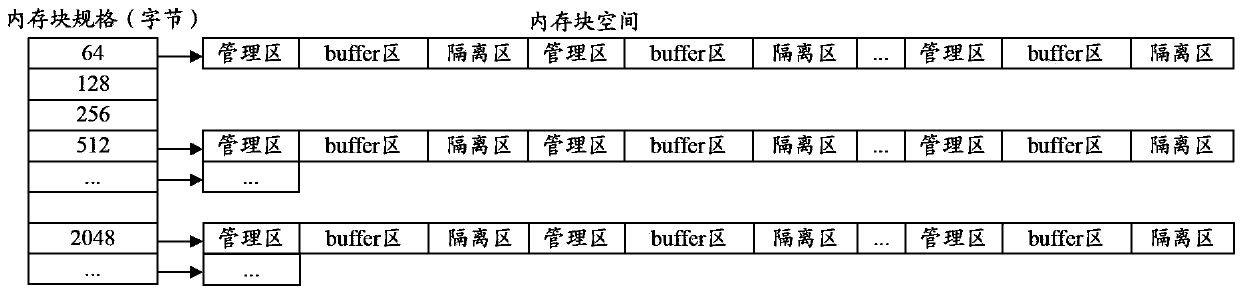
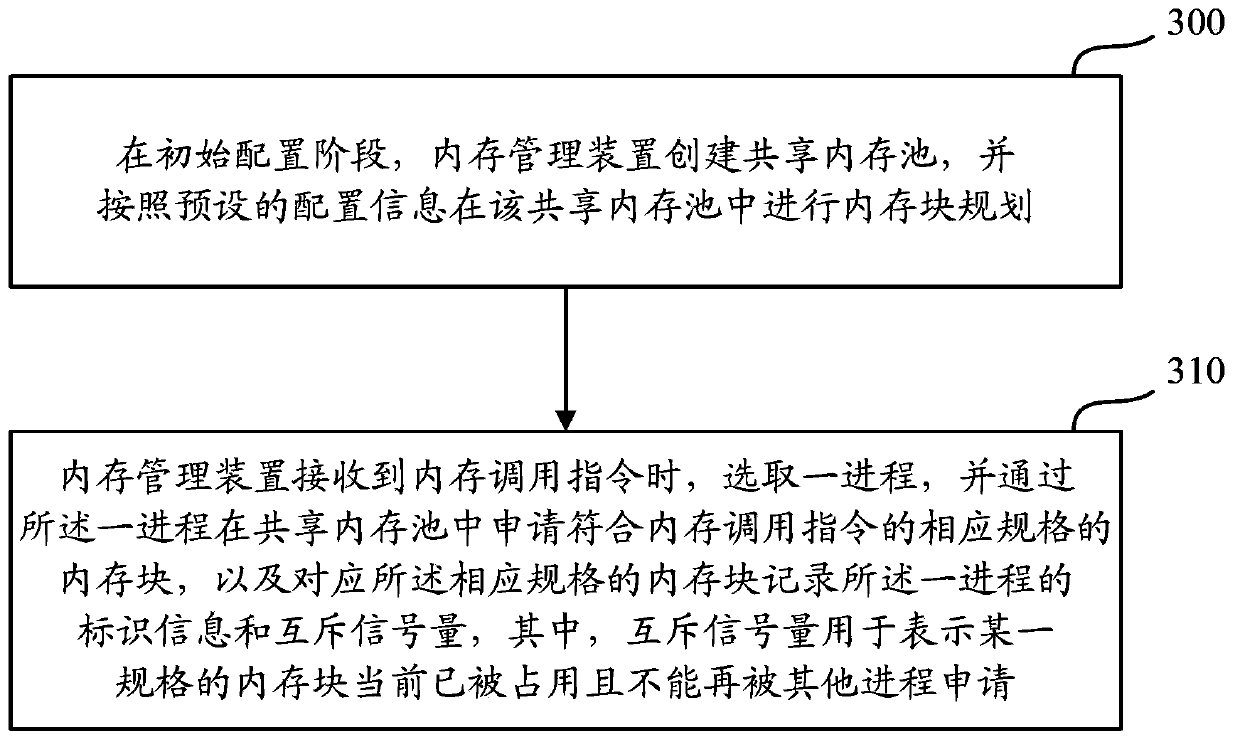
The invention discloses a memory management method and device for a multiprocess system. The memory management method and device for the multiprocess system are used for optimizing a memory management mode of the system and improving the memory utilization rate and the success rate of memory distribution. The memory management method for the multiprocess system comprises the steps that integrated planning of memory blocks is carried out by the memory management device by means of a shared memory pool, application and release of the memory blocks in the memory pool by multiple processes are distinguished according to identification information and mutually exclusive semaphore of the processes, the multiple processes can have access to memory blocks with the same specification without mutual interference, therefore, optimized memory management can be achieved, resource consumption caused by repeated application to an operation system due to the fact that the memory is not sufficient is avoided, a large amount of memory fragmentation is prevented from being generated in the operation system, and the memory utilization rate and the success rate of memory distribution of the system are effectively improved.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Garbage collecting method based on Java system on chip (SoC) with stack system structure
ActiveCN102722415APrevent allocation interleavingImprove efficiencyResource allocationMemory adressing/allocation/relocationOut of memoryWaste collection
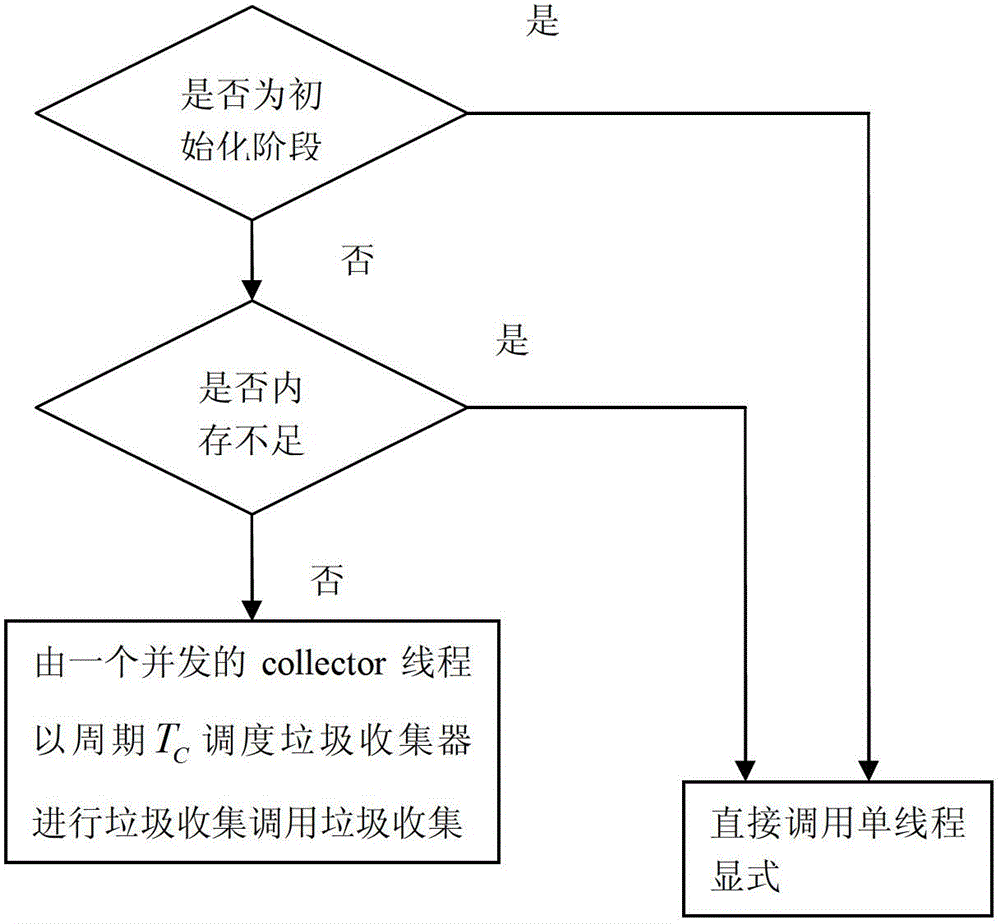
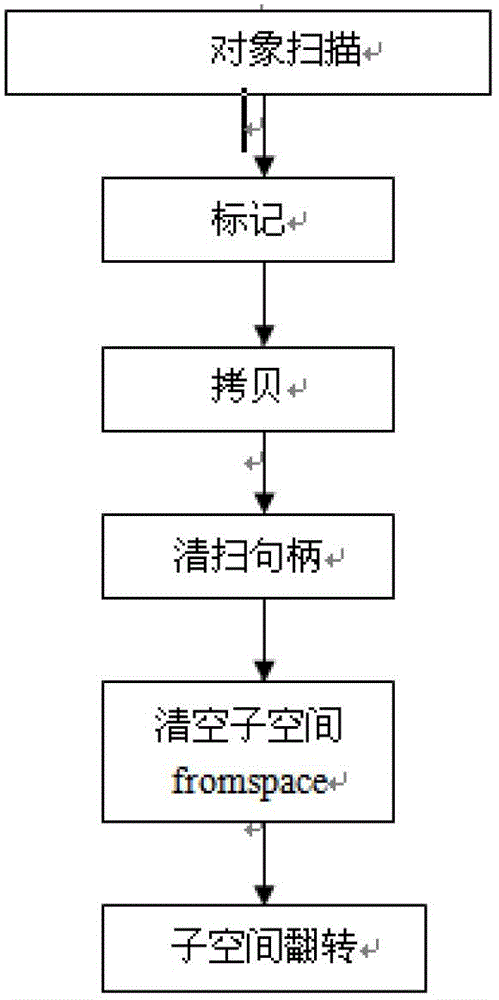
The invention discloses a garbage collecting method based on a Java system on chip (SoC) with a stack system structure, which is used for a multi-thread dynamic scheduling garbage collector and used for recovering garbage. The life cycle of the Java SoC is divided into a system initialization stage and a real-time task stage, wherein at the Java SoC initialization stage, a Java virtual machine actively calls the garbage collector to carry out single-thread explicit called garbage collection; when an abnormity of 'memory insufficiency' happens, the Java SoC triggers and calls the garbage collector to carry out single-thread explicit called garbage collection; and at the multi-thread real-time task operation stage, a concurrent collector thread schedules the garbage collector to collect garbage in a cycle TC. The garbage collection workflow of the garbage collector comprises the following steps of: 1) scanning root set objects in the Java SoC; 2) marking; 3) copying non-garbage objects from a subspace fromespace to a subspace tospace; 4) sweeping handles; 5) emptying the subspace fromespace; and 6) turning the subspaces fromespace and tospace over.
Owner:GUANGZHOU KINGRAY INFORMATION TECH +1
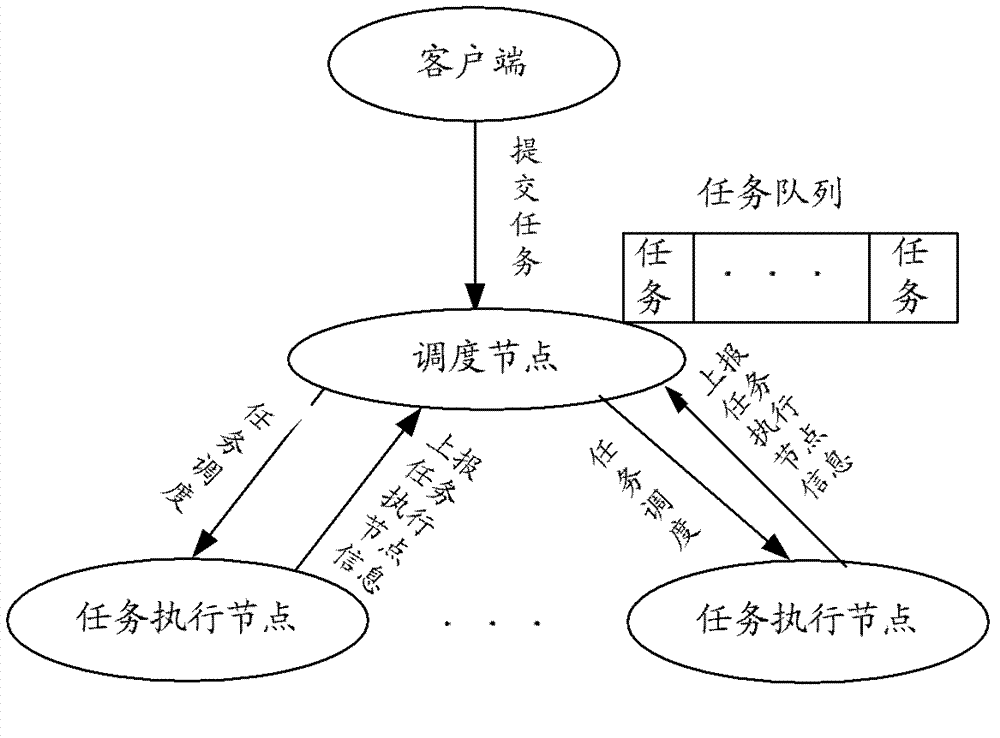
Multitask dispatching method and system based on capacity
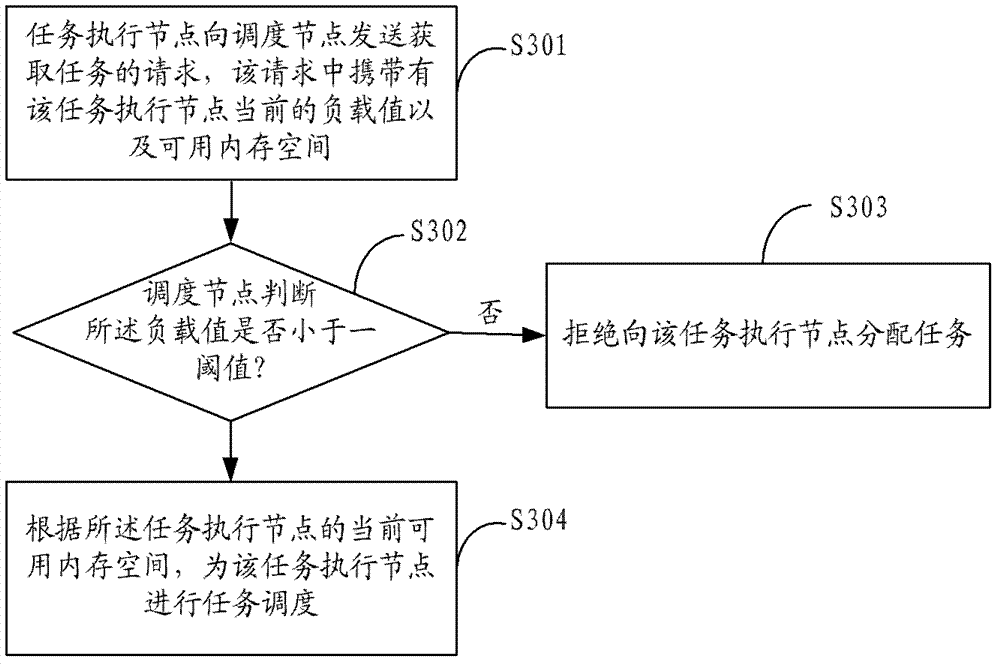
The invention is suitable for the technical field of data processing and provides a multitask dispatching method and system based on capacity. The multitask dispatching method comprises the steps: a task execution node sends a task obtaining request to a dispatching node, wherein the request carries a current load value and a current available memory space of the task execution node; and the dispatching node judges whether the load value is smaller than a threshold value or not, if so, task dispatching is performed to the task execution node according to the current available memory space of the task execution node. By means of the multitask dispatching method and system based on the capacity, the problems including overload, loading, insufficient memory and the like of the task execution node can be solved, the resource utilization rate of the task execution node is improved, and the task dispatching and executing efficiency is improved.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Terminal equipment and application program management method thereof
ActiveCN103294530AImprove experienceOrderly managementMultiprogramming arrangementsProgram managementOut of memory
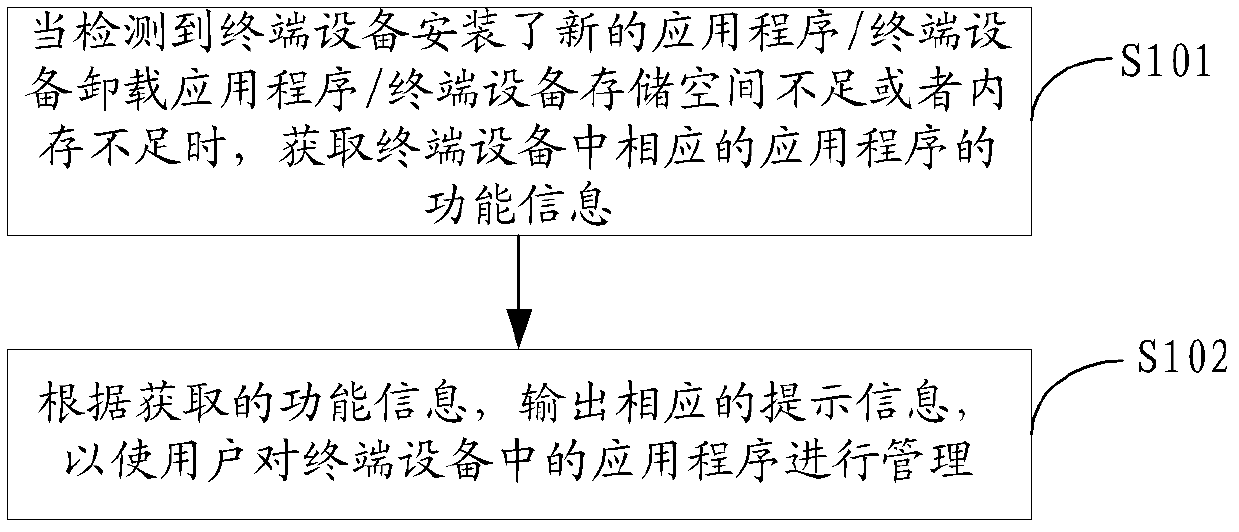
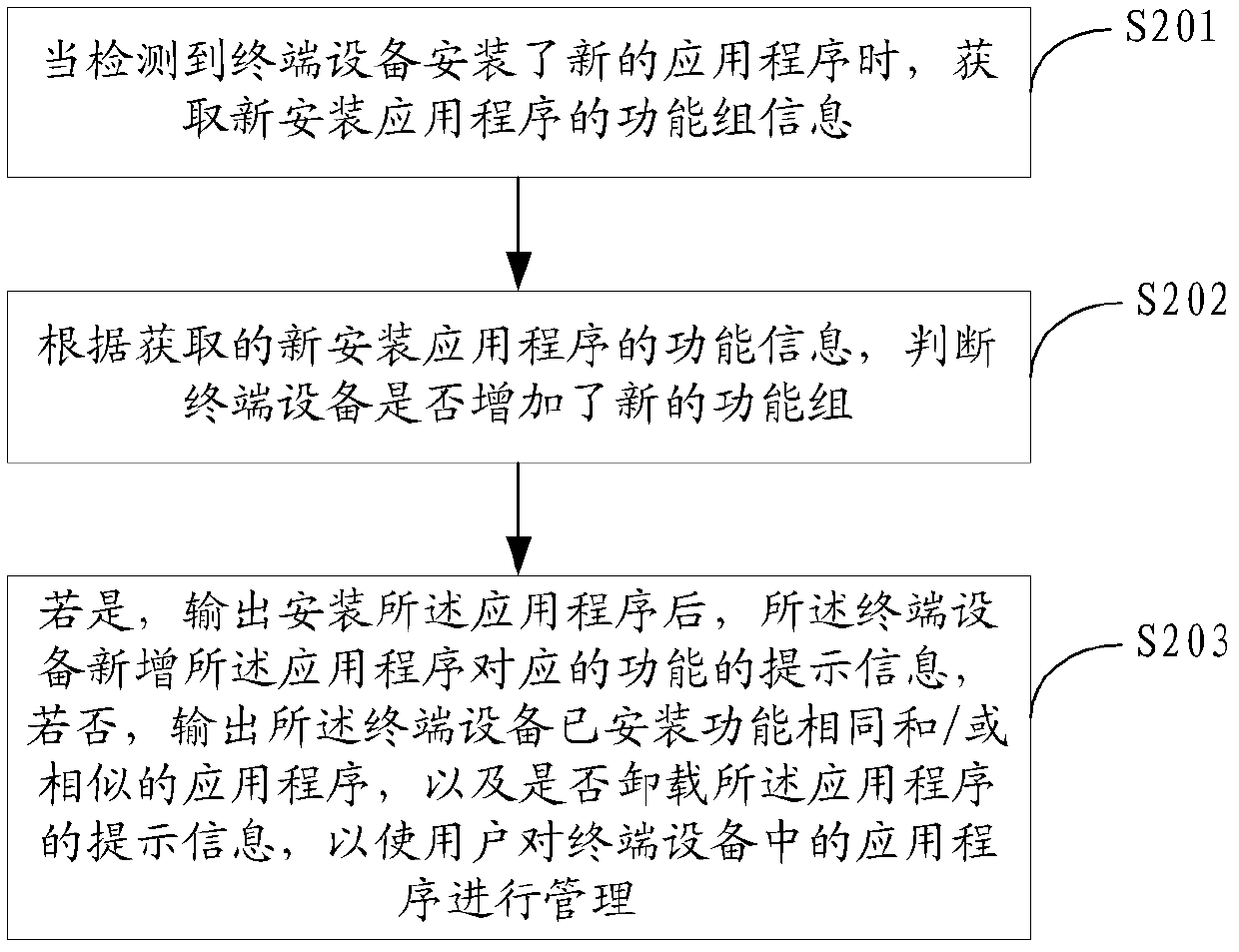
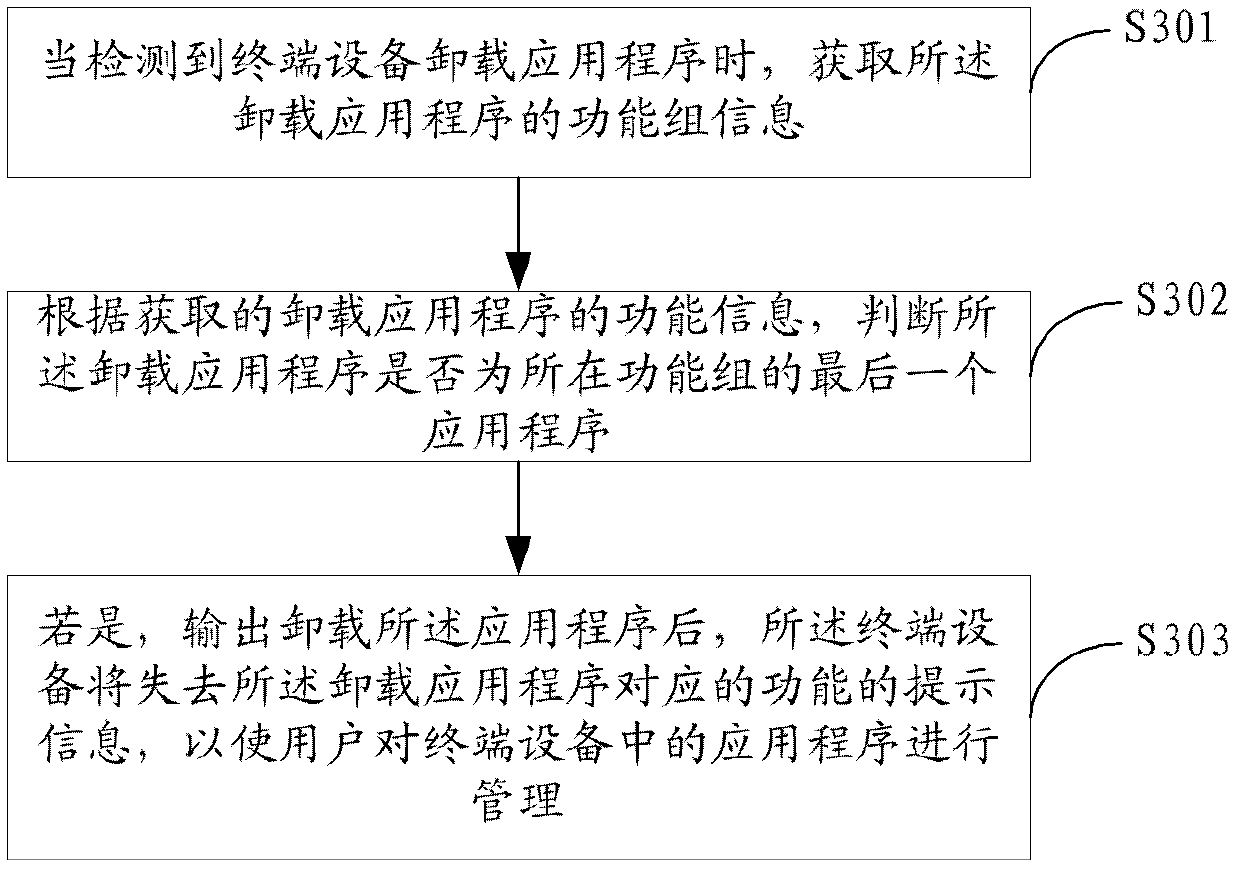
The invention is applicable to the technical field of communication, and provides terminal equipment and an application program management method thereof. The application program management method comprises the following steps: when detecting that the terminal equipment is installed with new application programs, or application programs are uninstalled from the terminal equipment, or the storage space or the memory of the terminal equipment is insufficient, acquiring function information of the corresponding application programs in the terminal equipment; and according to the acquired function information, outputting corresponding prompt information for a user to manage the application programs in the terminal equipment. Due to the application program management method, the user can sufficiently acquire the information of the application programs so as to comprehensively understand the functions of the terminal equipment of the user and the user can orderly manage the application programs of the terminal equipment, so that a user experience is improved.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
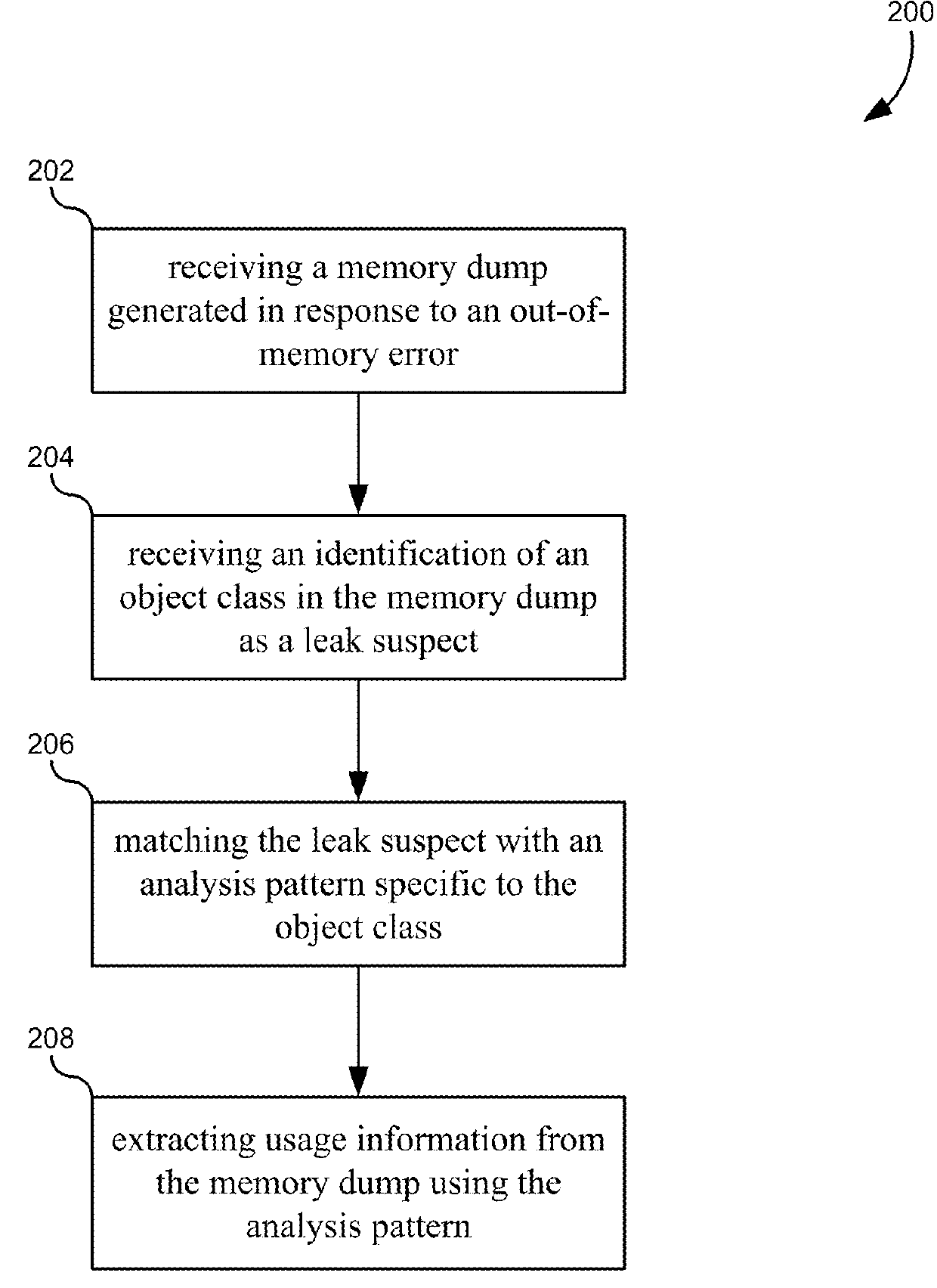
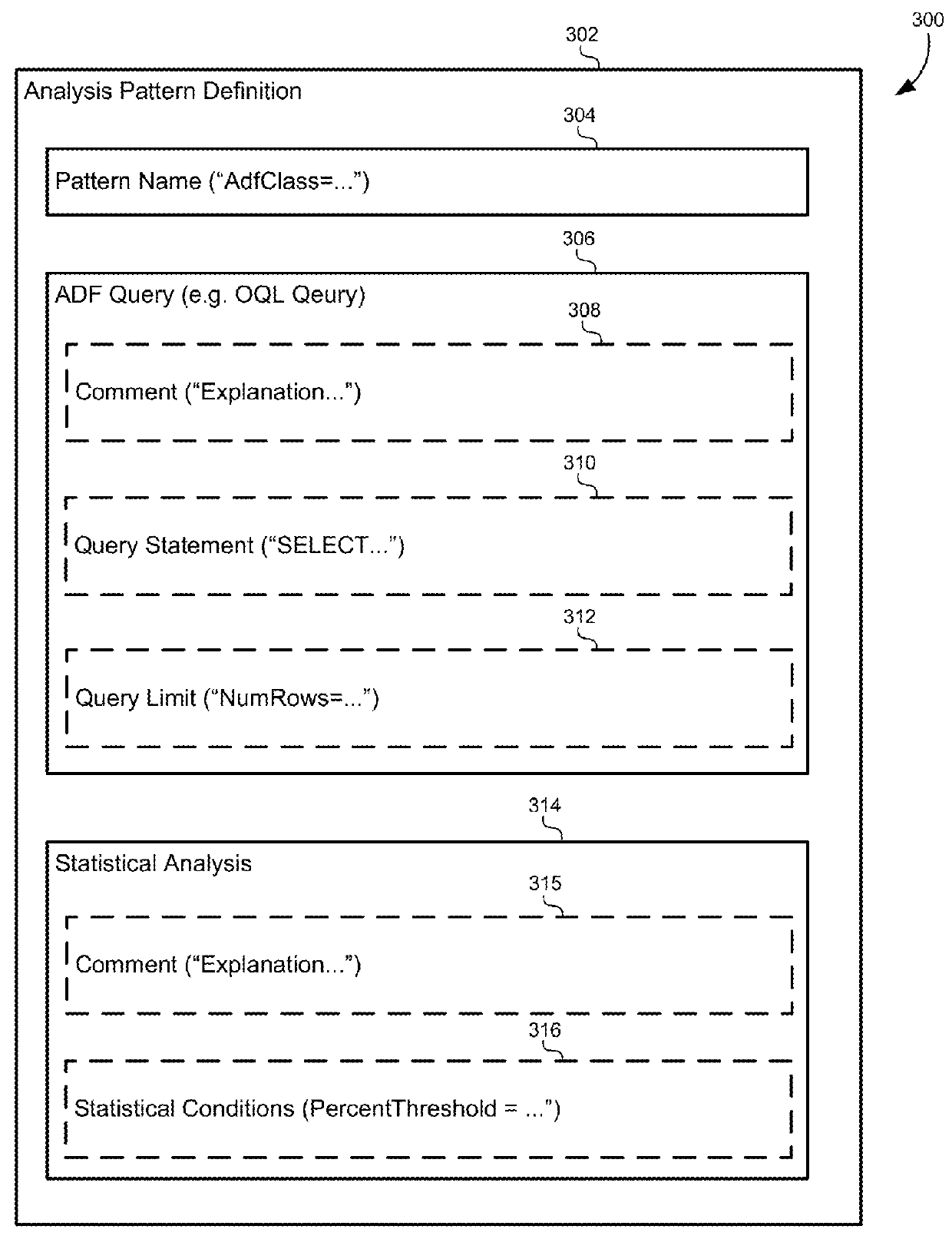
Pattern analysis for triaging memory leaks
A method of analyzing out-of-memory errors may include receiving a memory dump generated in response to an out-of-memory error, receiving an identification of an object class in the memory dump as a leak suspect that may be responsible for the out-of-memory error, matching the leak suspect with an analysis pattern specific to the object class, and extracting usage information from the memory dump using the analysis pattern.
Owner:ORACLE INT CORP
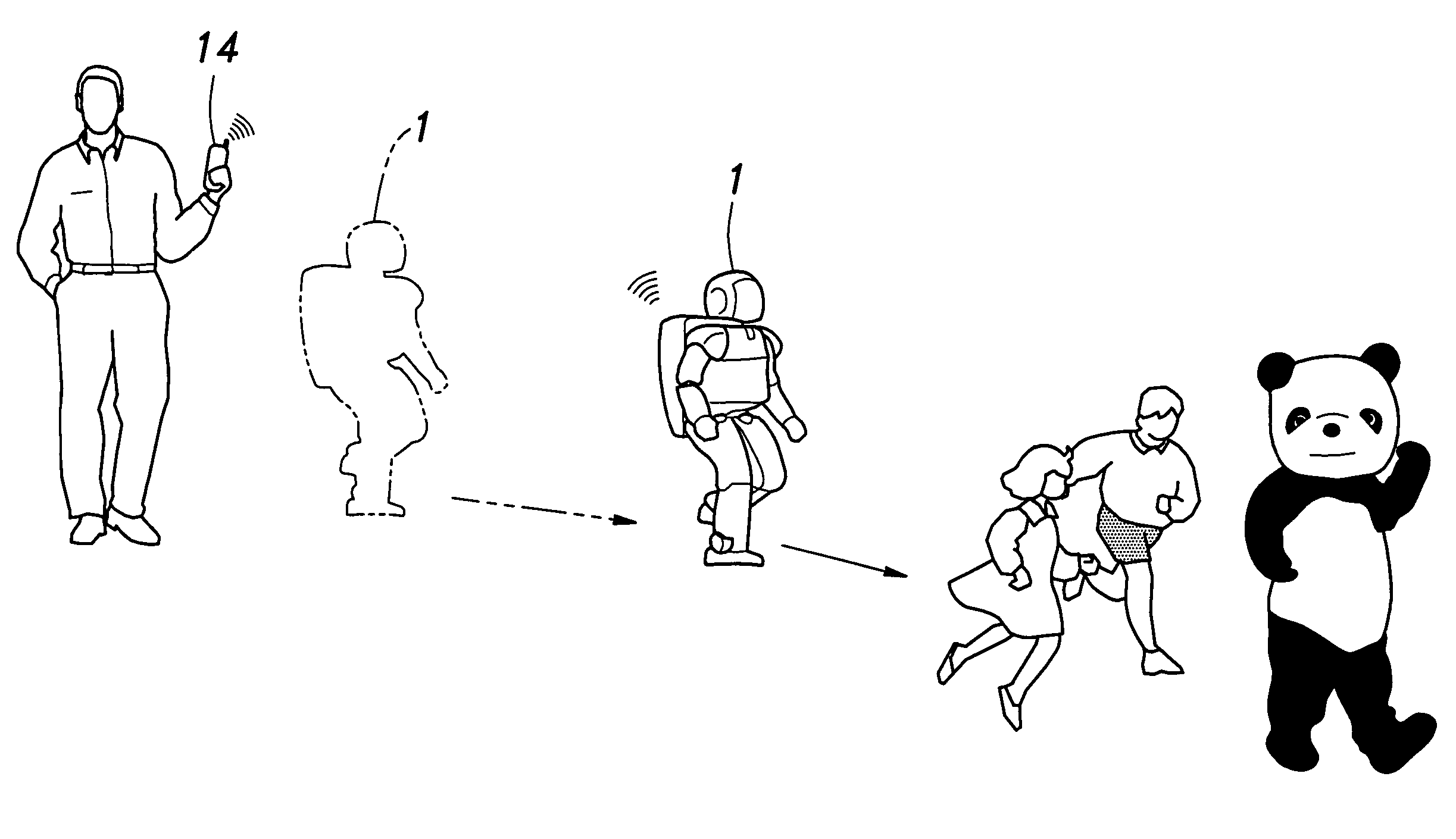
Picture taking mobile robot
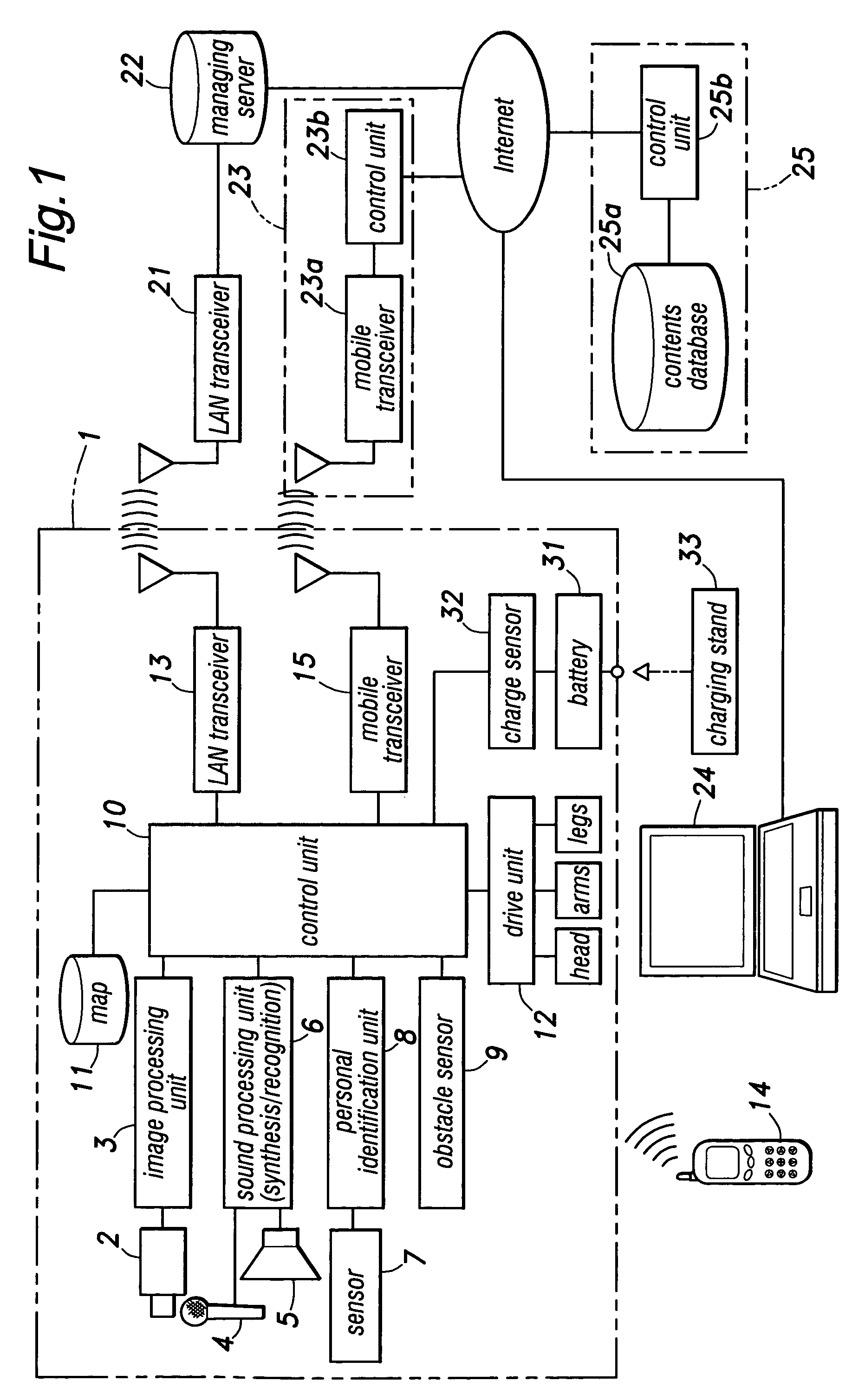
InactiveUS7756322B2Easy accessPrevent running outData processing applicationsCharacter and pattern recognitionComputer graphics (images)Out of memory
A mobile robot that is fitted with a camera and can be controlled from a remote terminal such as a mobile phone moves about in an event site to detect and track a moving object such as a visitor and entertainer. Because the camera along with the robot itself can change its position freely autonomously and / or according to a command from the mobile terminal, a desired frame layout can be accomplished by moving the position of the robot. Therefore, the operator is not required to execute a complex image trimming process or other adjustment of the obtained picture image so that a desired picture can be obtained quickly and without any difficulty. If the user is allowed access the managing server, the user can download the desired picture images and have them printed out at will. Also, because the selected picture images can be transmitted to the managing server, the robot is prevented from running out of memory for storing the picture images.
Owner:HONDA MOTOR CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com