Patents
Literature
58results about How to "Increase resource consumption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Positioning technique
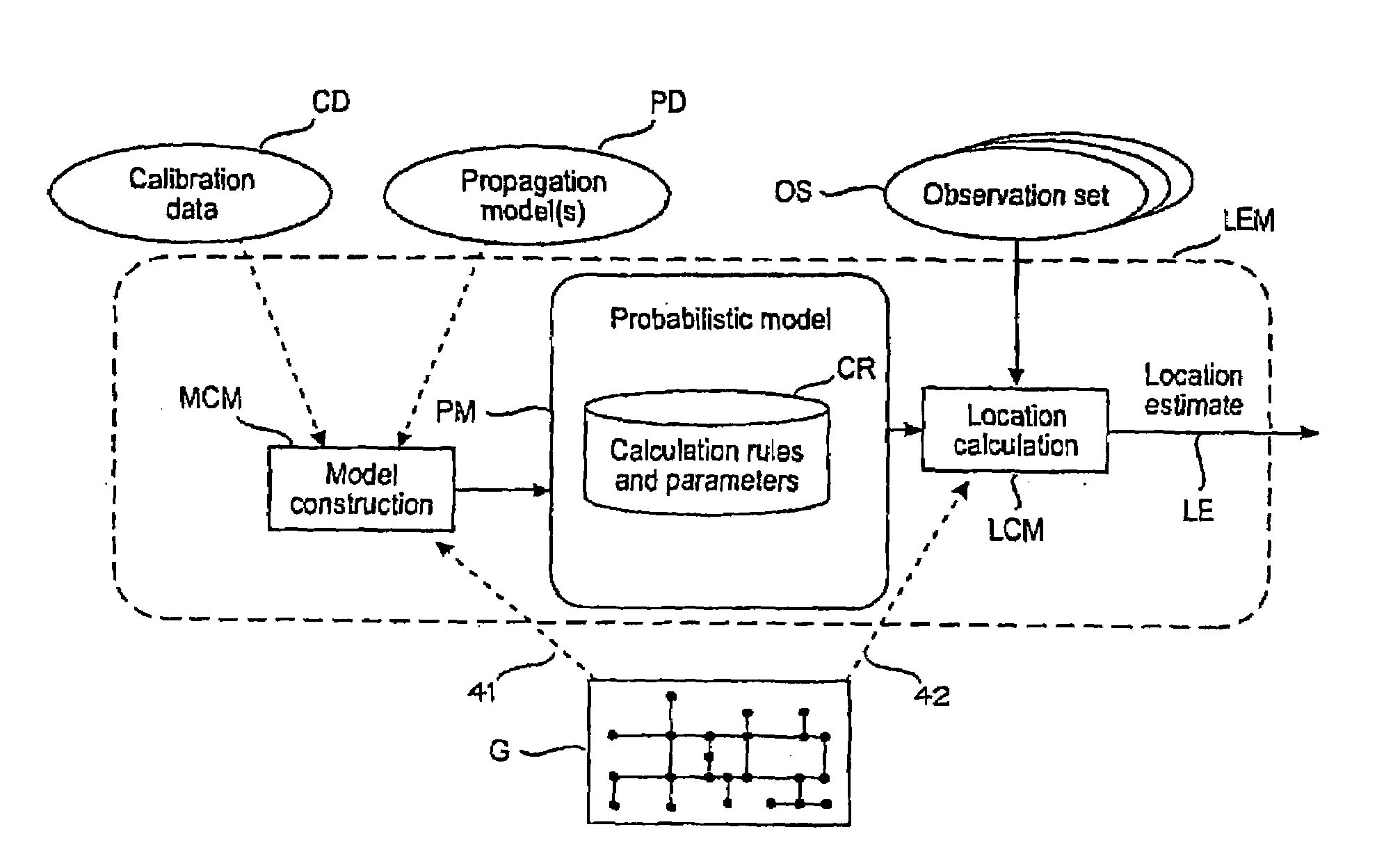
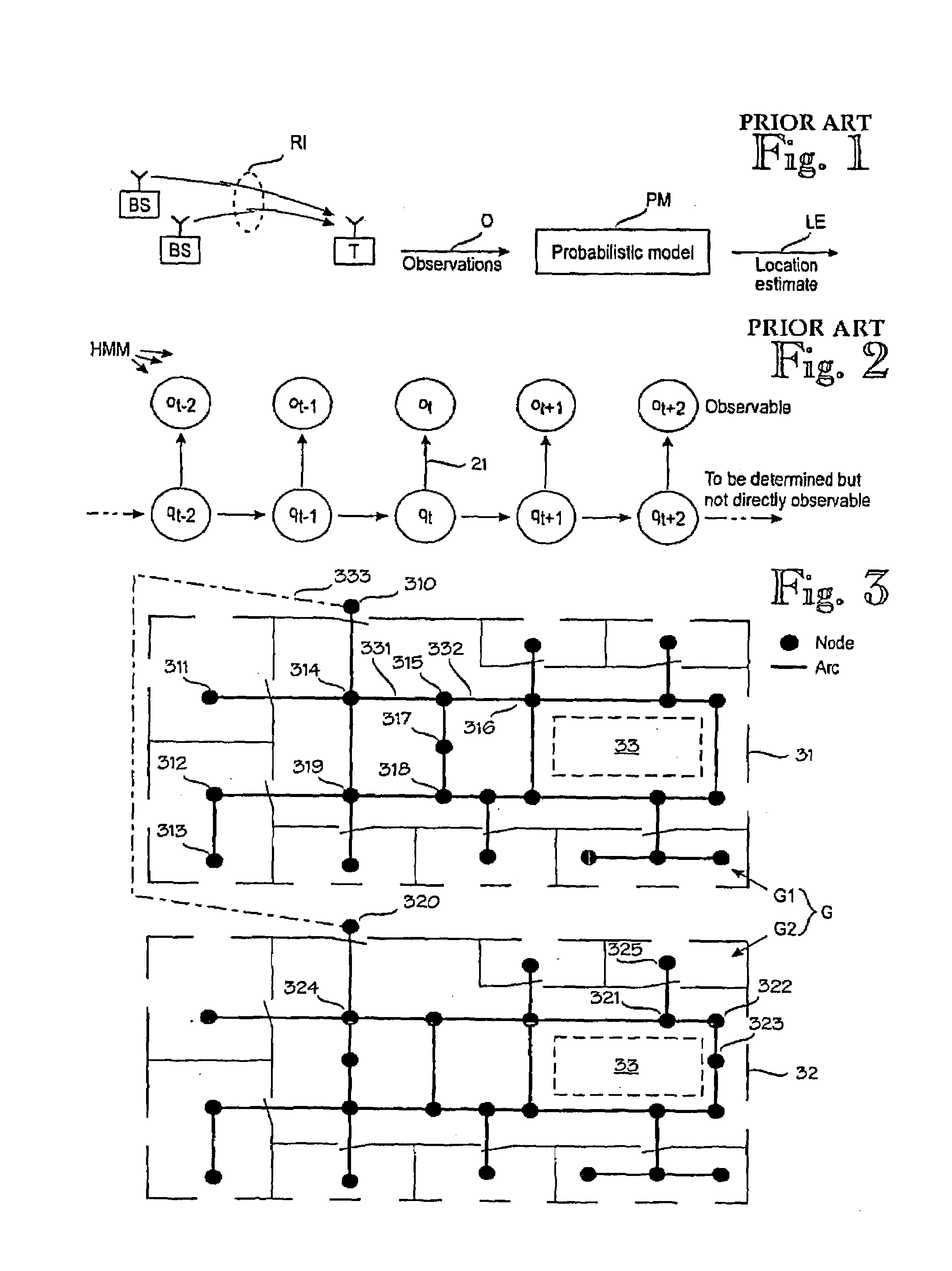
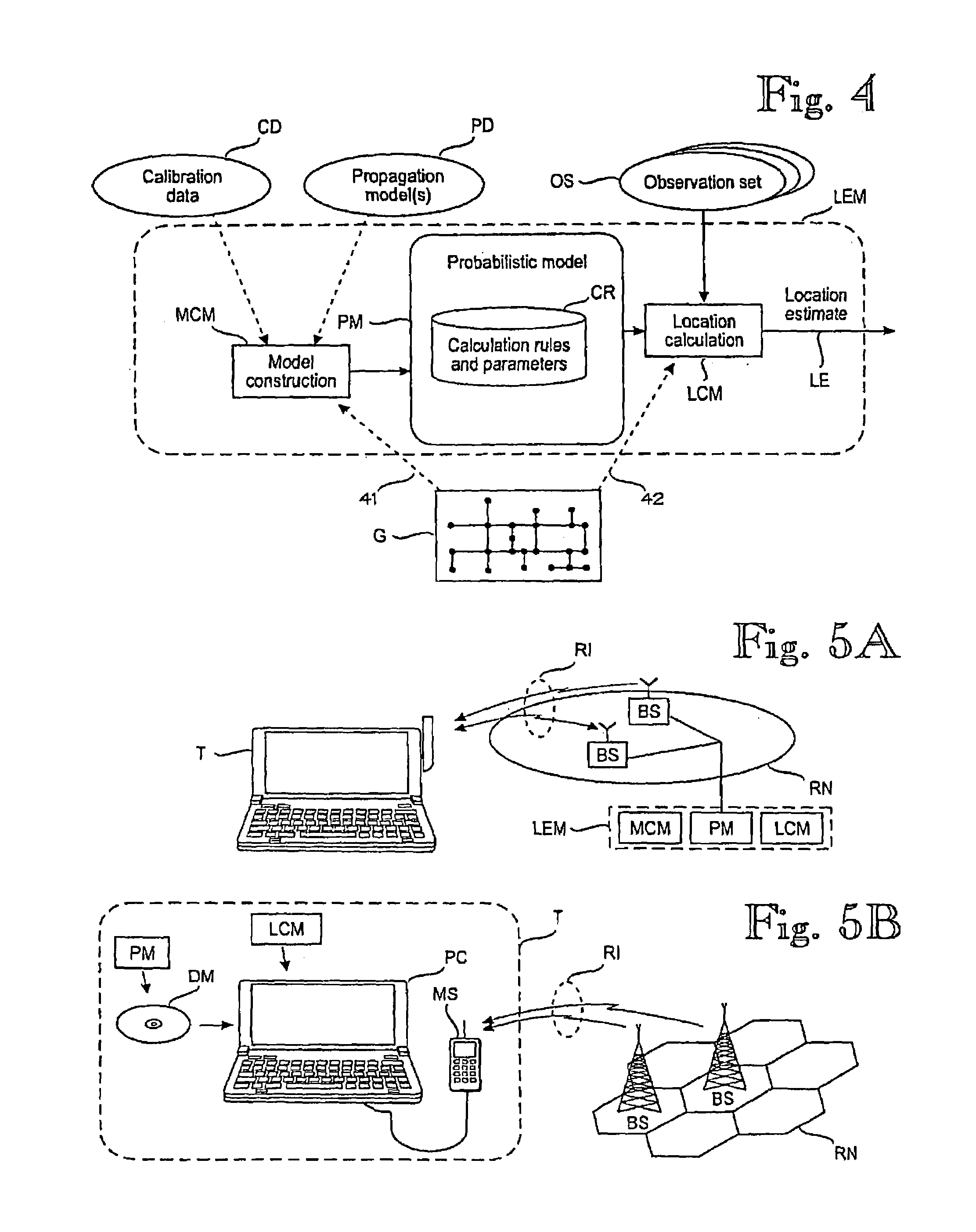
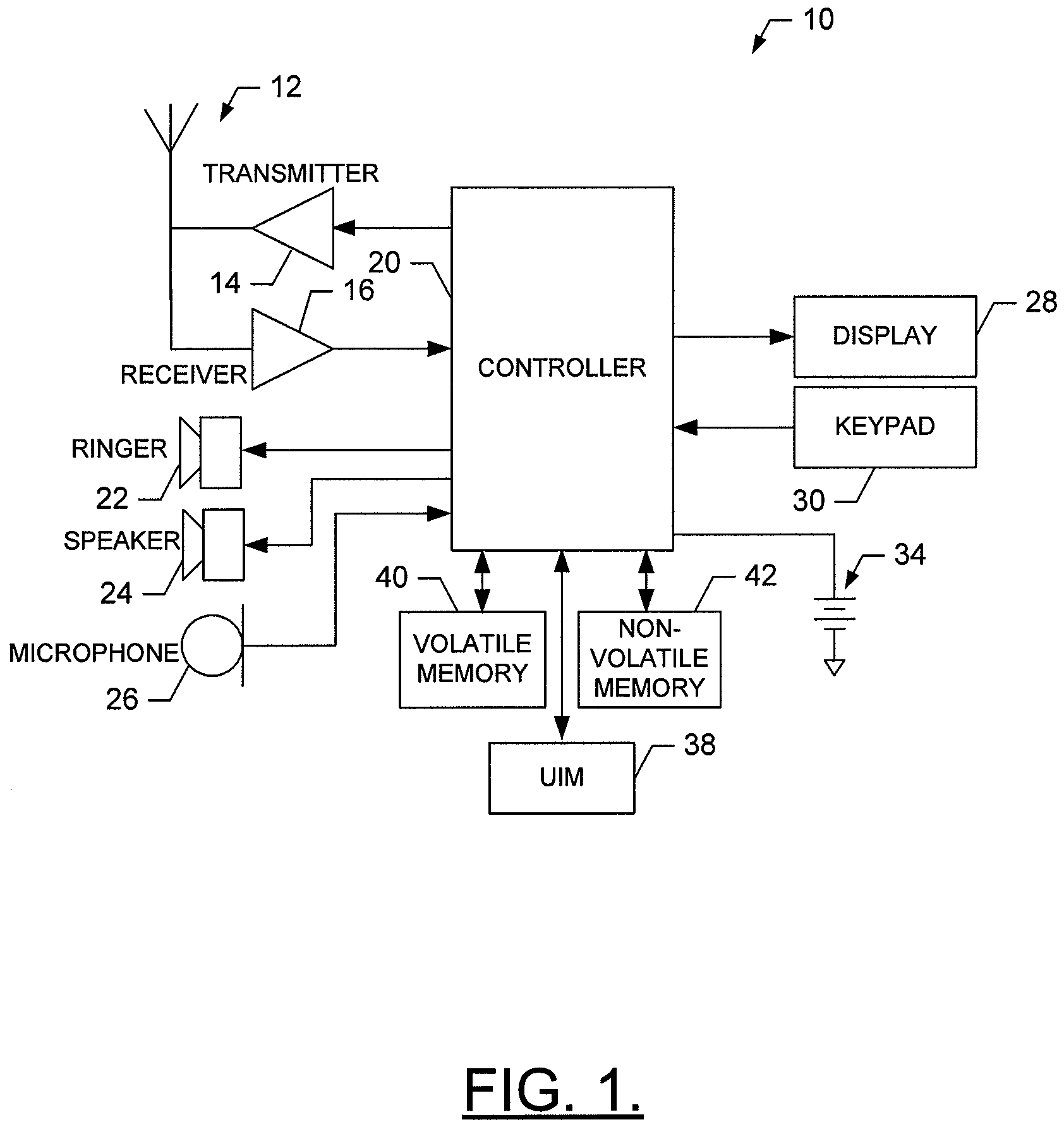
ActiveUS7299059B2Good basisEasy to analyzePosition fixationRadio/inductive link selection arrangementsProbit modelGraphics
A target device's location in a radio network is estimated by maintaining a probabilistic model for several sample points that indicate expected distributions of signal values at a given location. The target device observes signal values, wherein the sequence of observations and the respective locations constitute a Hidden Markov Model. A graph models the topology of the positioning environment. The graph indicates several nodes which are permissible locations in the environment and several arcs which are permissible transitions between two nodes. The graph is used to estimate the target device's location based on the probabilistic model and the sequence of observations.
Owner:AIRISTA FLOW INC +1
Method, Apparatus and Computer Program Product for Providing Adaptive Language Model Scaling
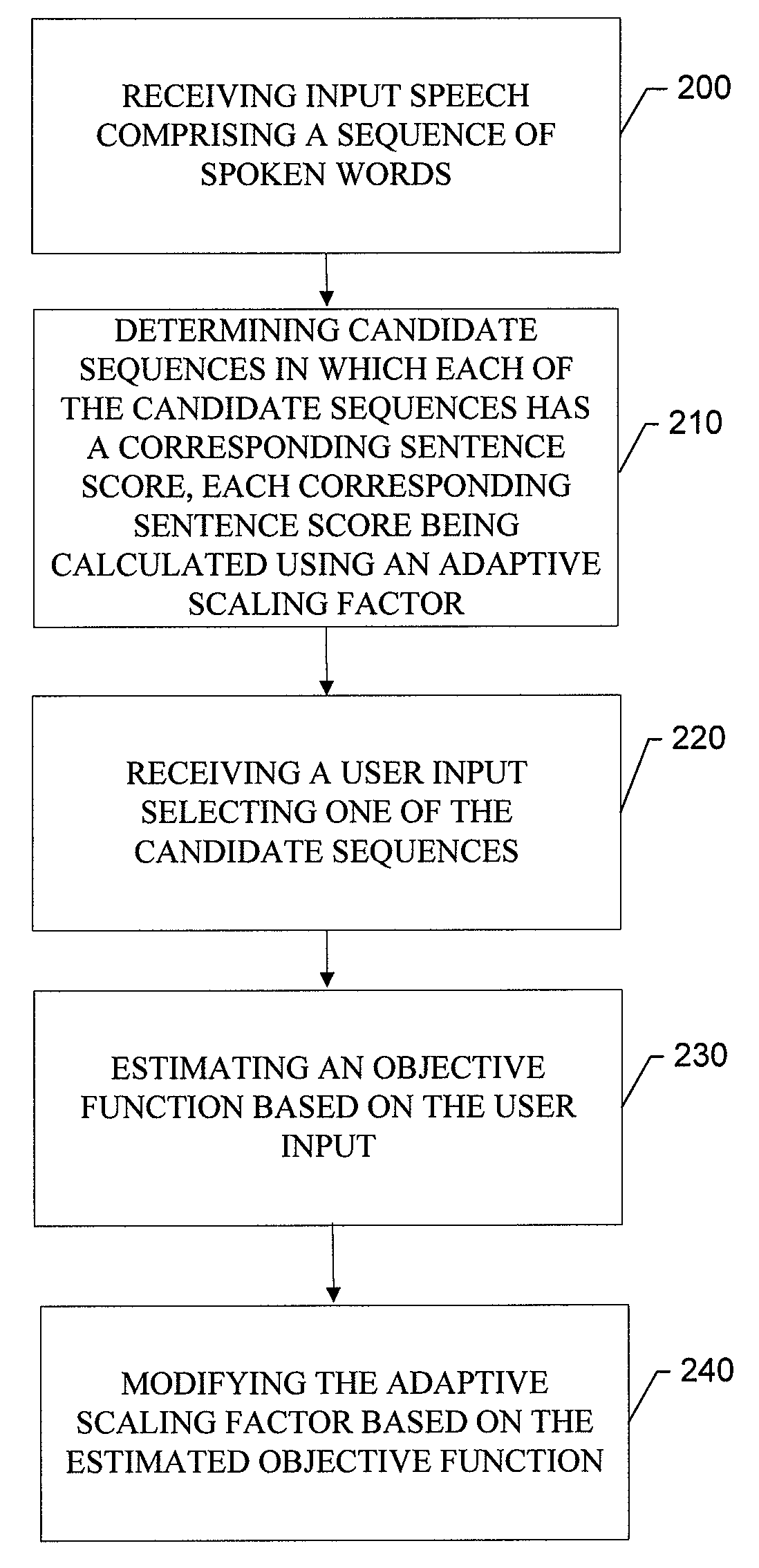
InactiveUS20080004877A1Increase resource consumptionEfficient and adaptive language model scalingSpeech recognitionSpoken languageUser input
An apparatus for providing adaptive language model scaling includes an adaptive scaling element and an interface element. The adaptive scaling element is configured to receive input speech comprising a sequence of spoken words and to determine a plurality of candidate sequences of text words in which each of the candidate sequences has a corresponding sentence score representing a probability that a candidate sequence matches the sequence of spoken words. Each corresponding sentence score is calculated using an adaptive scaling factor. The interface element is configured to receive a user input selecting one of the candidate sequences. The adaptive scaling element is further configured to estimate an objective function based on the user input and to modify the adaptive scaling factor based on the estimated objective function.
Owner:NOKIA CORP
Method for random access in wireless communication system and apparatus for the same
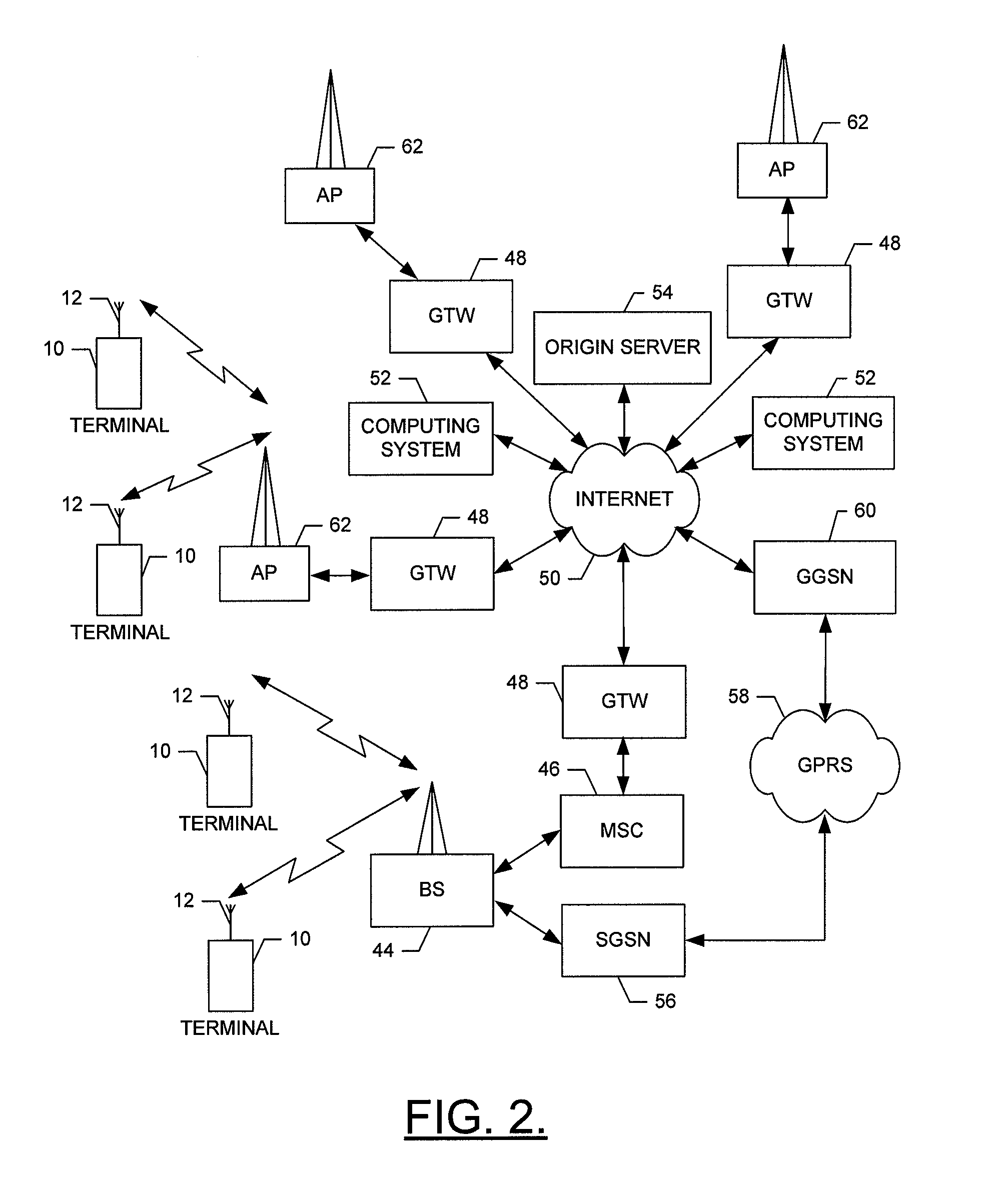
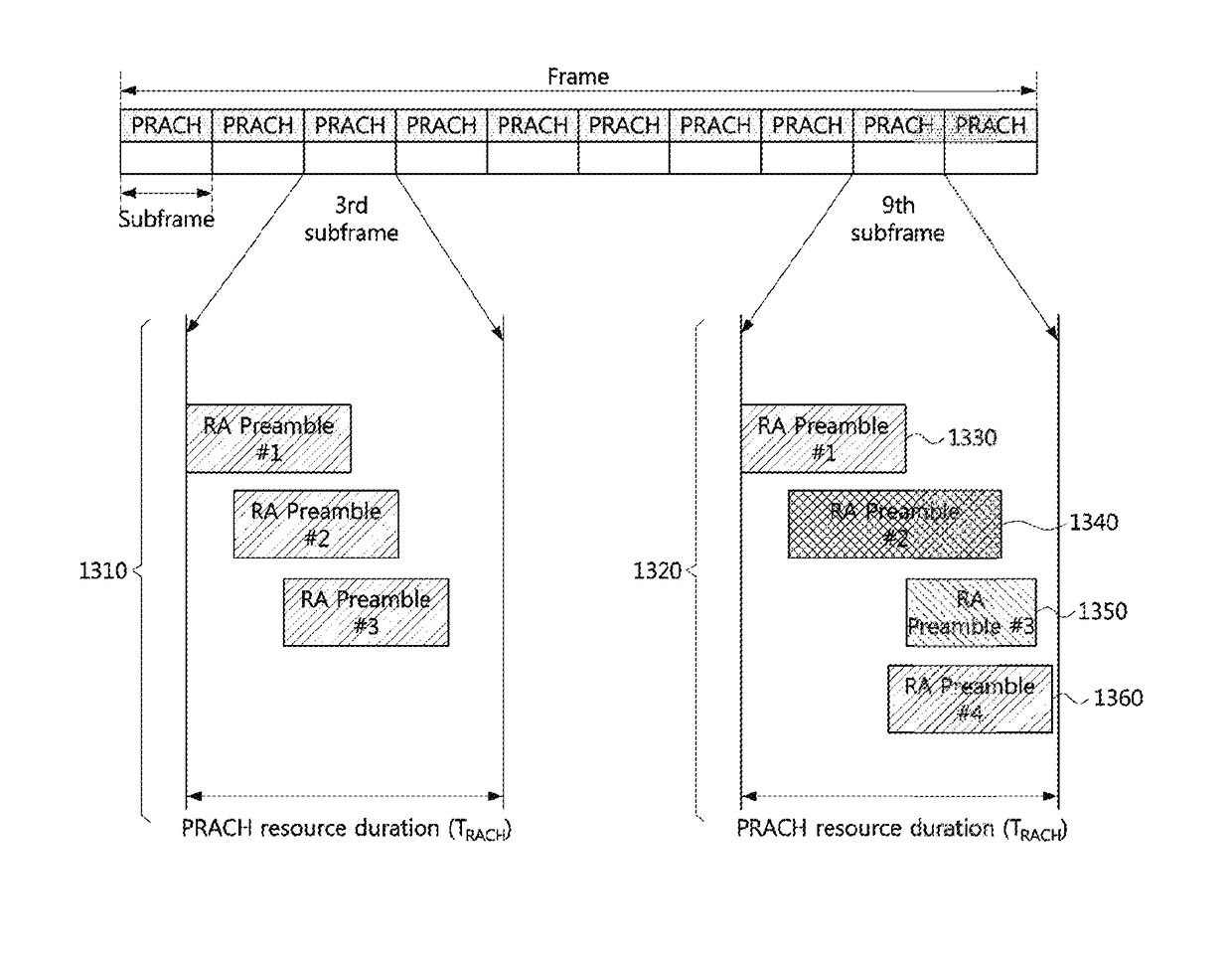
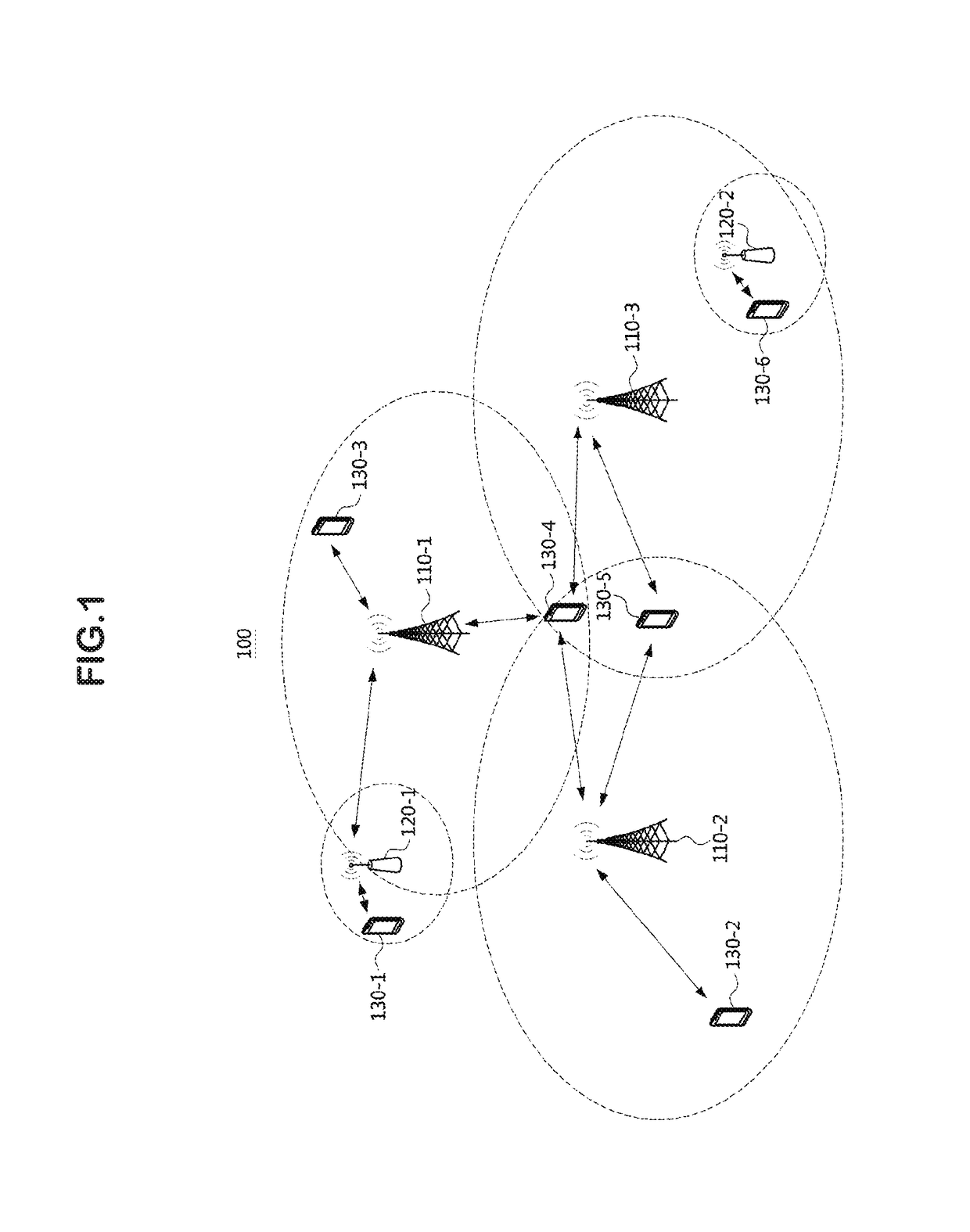
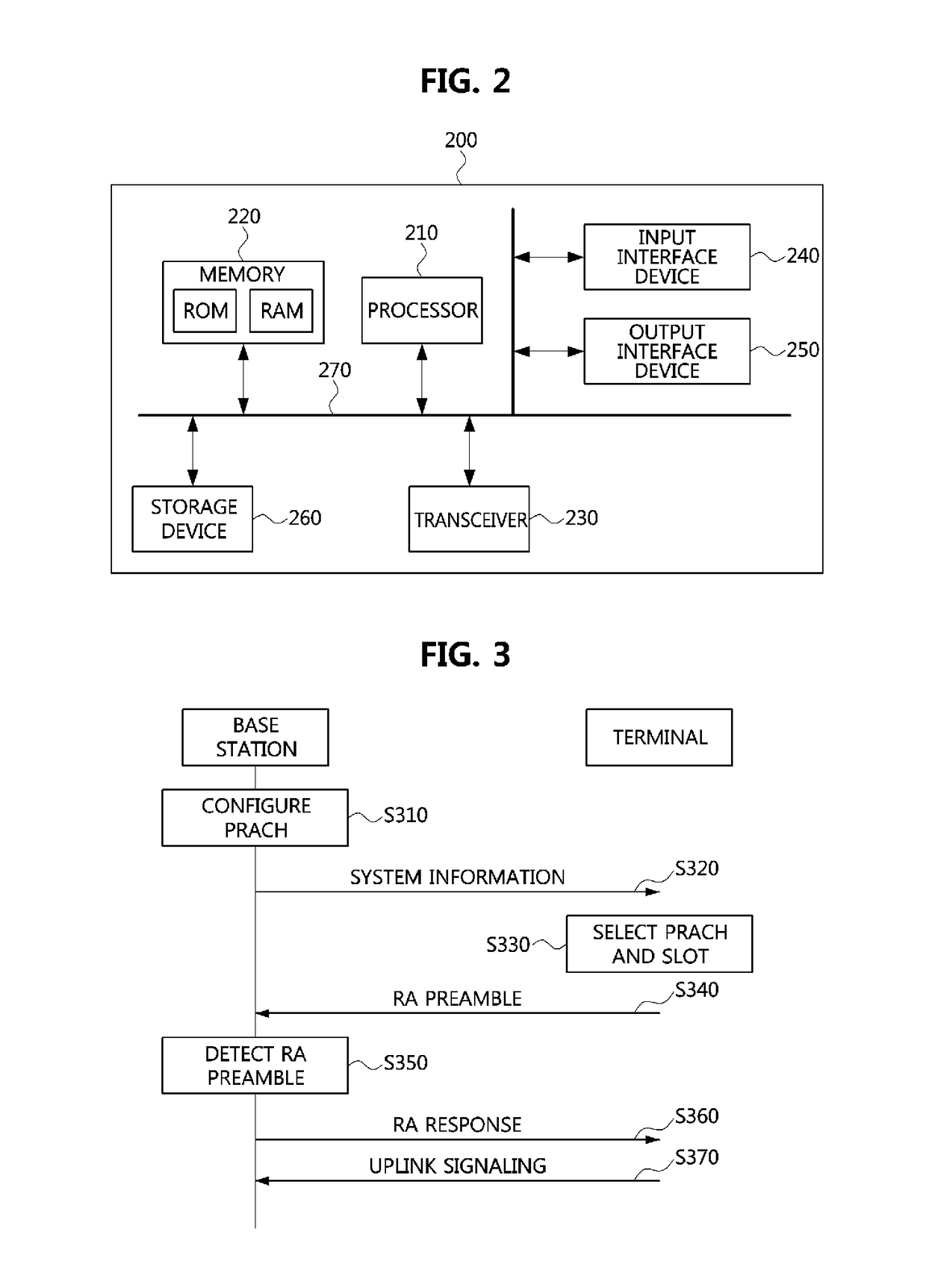
ActiveUS20180220466A1Increase resource consumptionReduce delay timeWireless communicationPreambleSystem information
Disclosed are a random access method and a random access apparatus in a wireless communication system. An operation method of a terminal in a communication system, according to the present invention, comprises receiving system information including configuration information on a physical random access channel (PRACH) composed of a plurality of access slots from a first base station; selecting one access slot among the plurality of access slots based on the configuration information; and transmitting a random access preamble to the first base station through the one access slot. Therefore, the capacity of the random access channel can be increased without further occupation of radio resources.
Owner:ELECTRONICS & TELECOMM RES INST
Live broadcast assistant audio/video processing method and device for
ActiveCN107027050AIncrease resource consumptionIncreased flexibility of useSelective content distributionImaging processingNetwork packet
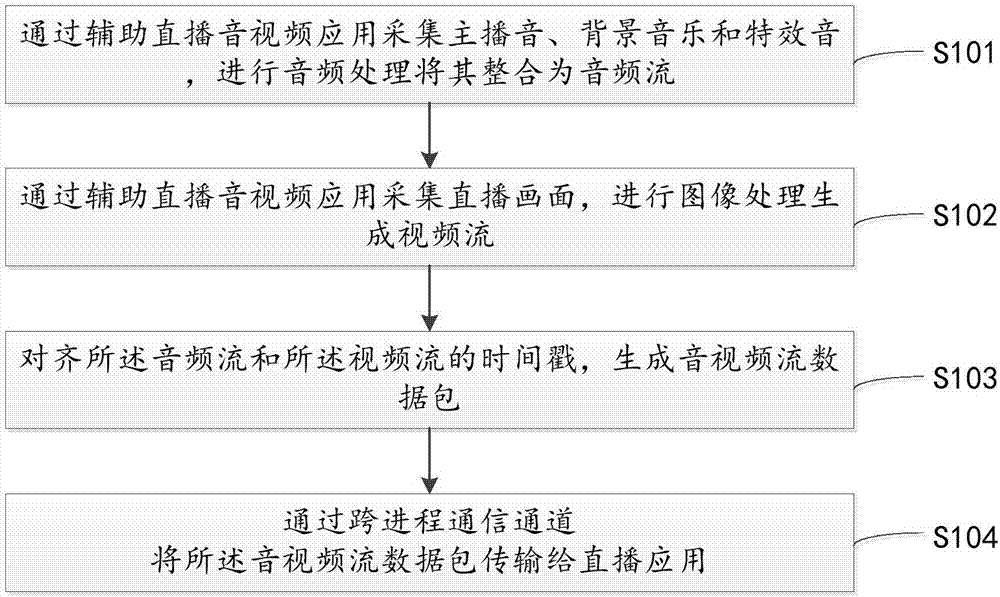
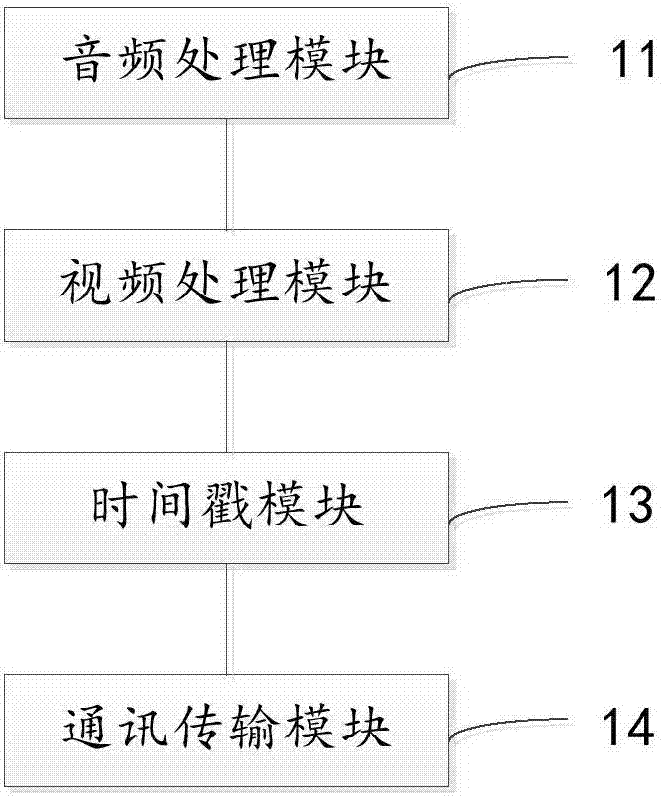
The invention relates to the technical field of the Internet and discloses a live broadcast assistant audio / video processing method and device. The method comprises the steps of collecting anchor audios, background music and special effect audios through a live broadcast assistant audio / video application, carrying out audio processing and integrating the anchor audios, the background music and the special effect audios into an audio stream; collecting live broadcast images through the live broadcast assistant audio / video application, carrying out image processing to generate a video stream; aligning time stamps of the audio stream and the video stream to generate an audio / video stream data packet; and transmitting the audio / video stream data packet to a live broadcast application through a cross-process communication channel. The audios in the live broadcast process are effectively integrated into the audio stream, the time stamps of the audio stream and the video stream are aligned, the audio stream and the video stream are transmitted to the live broadcast application, various audios in the live broadcast process are prevented from mutual interference, and the fusion effect of the live broadcast application for the audios in the live broadcast process is relatively good.
Owner:广州方硅信息技术有限公司
Method, apparatus and computer program product for providing adaptive language model scaling
InactiveUS7716049B2Increase resource consumptionEfficient and adaptive language model scalingSpeech recognitionSpoken languageUser input
Owner:NOKIA CORP
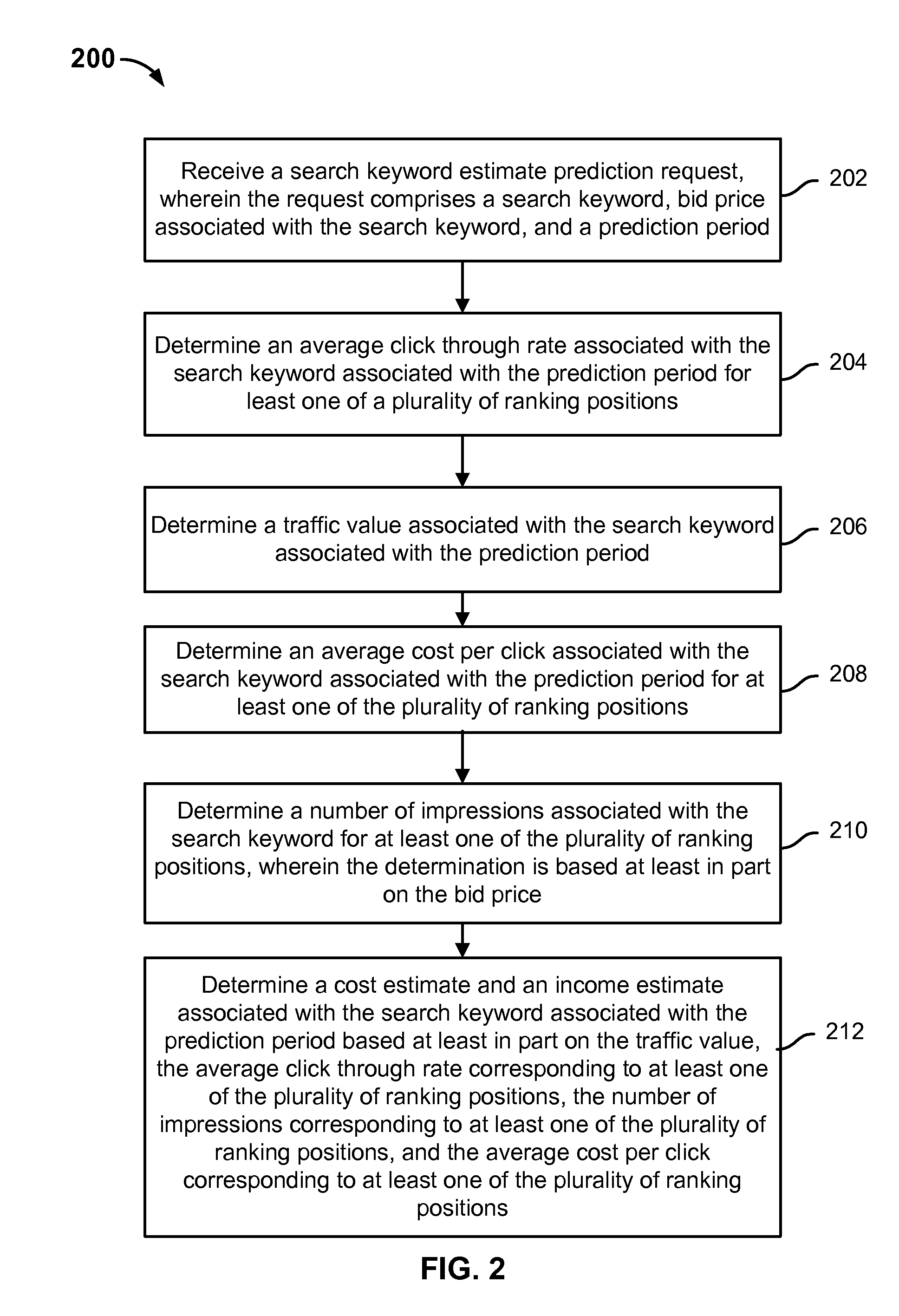
Prediction of cost and income estimates associated with a bid ranking model
InactiveUS20120130804A1Increase resource consumptionReduce usageMarketingData miningClick-through rate
Prediction of cost and income estimates associated with a bid ranking model is disclosed, including: receiving a search keyword estimate prediction request, wherein the request comprises a search keyword, a bid price associated with the search keyword, and a prediction period; determining an average click through rate associated with the search keyword associated with the prediction period for a ranking position; determining a traffic value associated with the search keyword associated with the prediction period; determining an average cost per click associated with the search keyword associated with the prediction period for the ranking position; determining a number of impressions associated with the search keyword for the ranking position; and determining a cost estimate and an income estimate associated with the search keyword associated with the prediction period.
Owner:ALIBABA GRP HLDG LTD
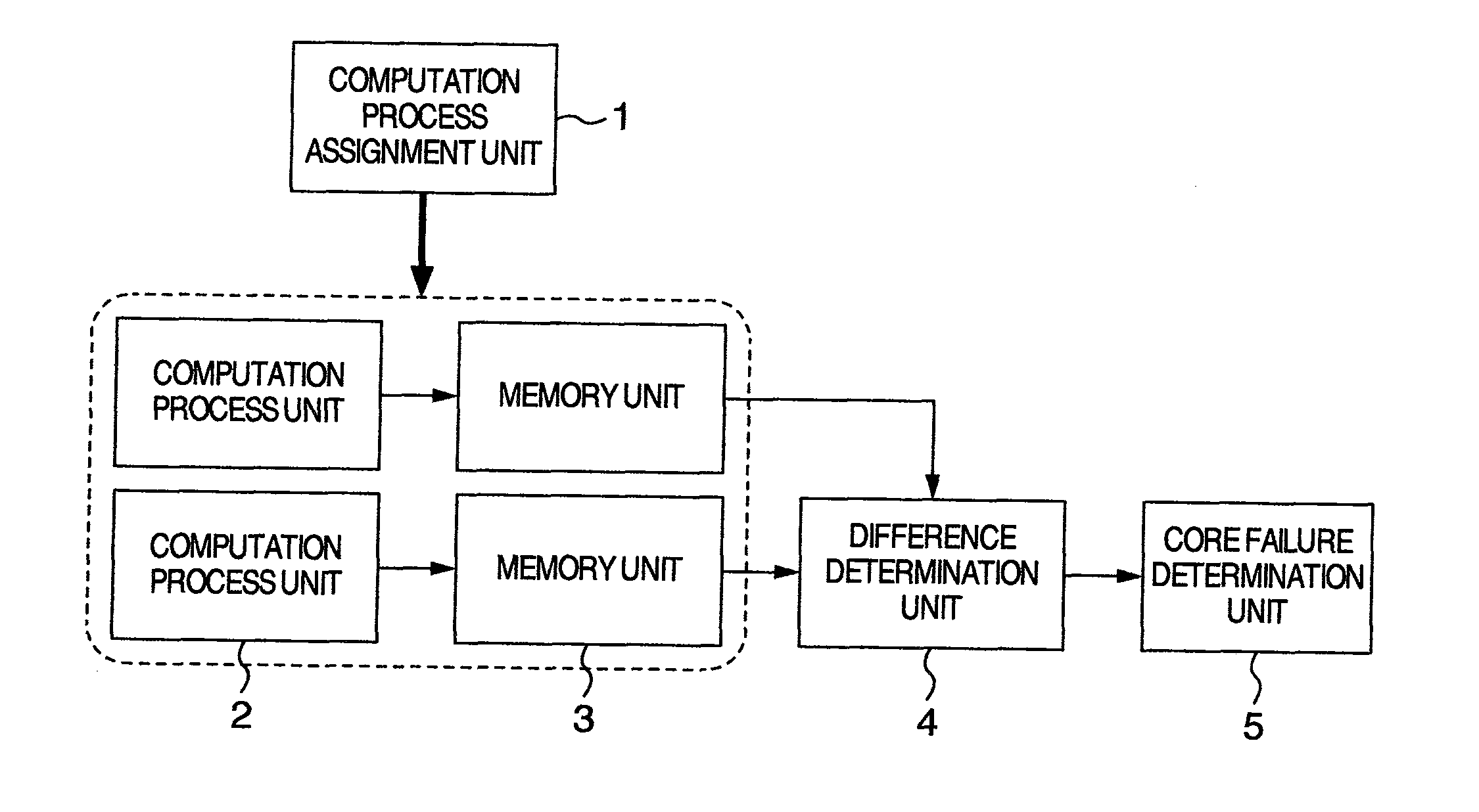
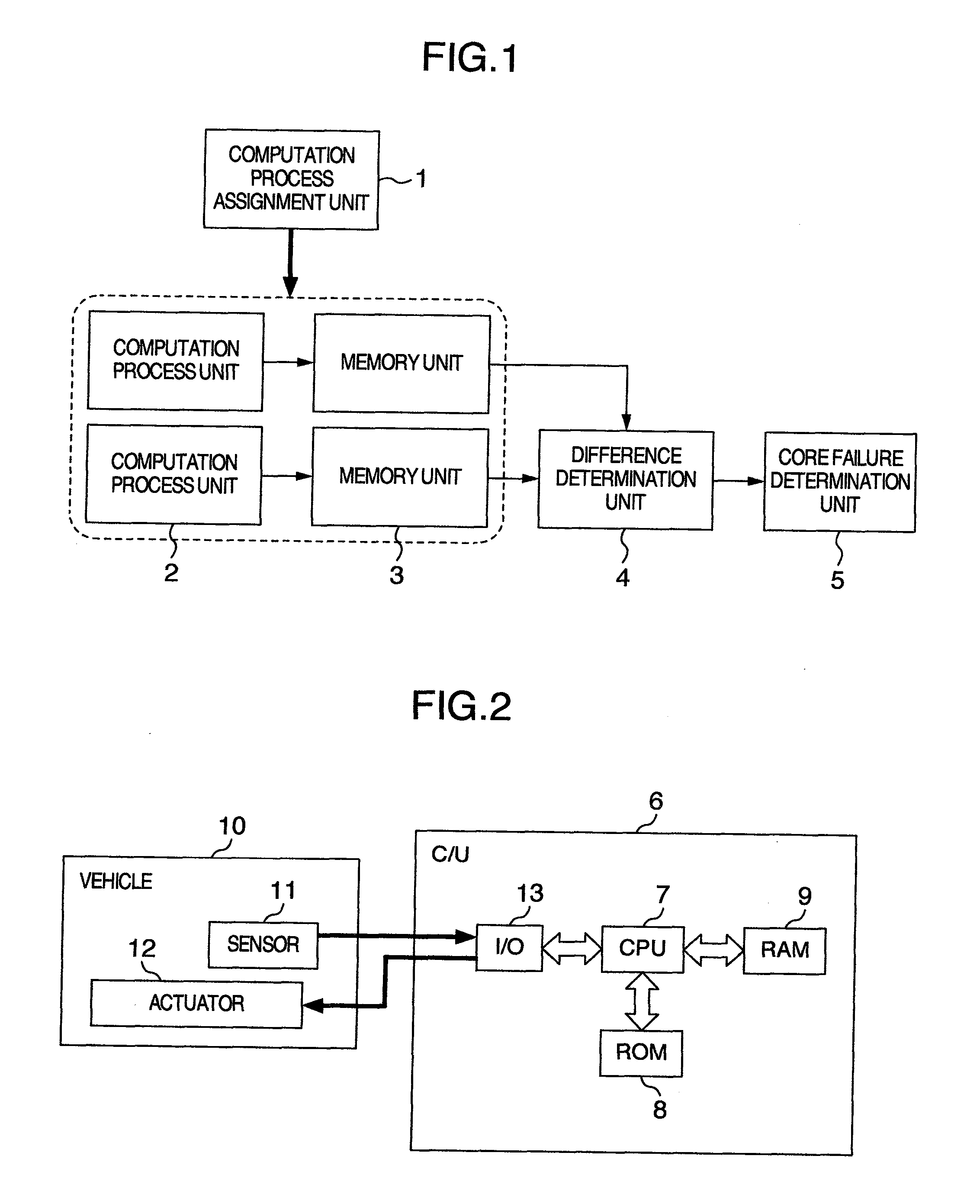
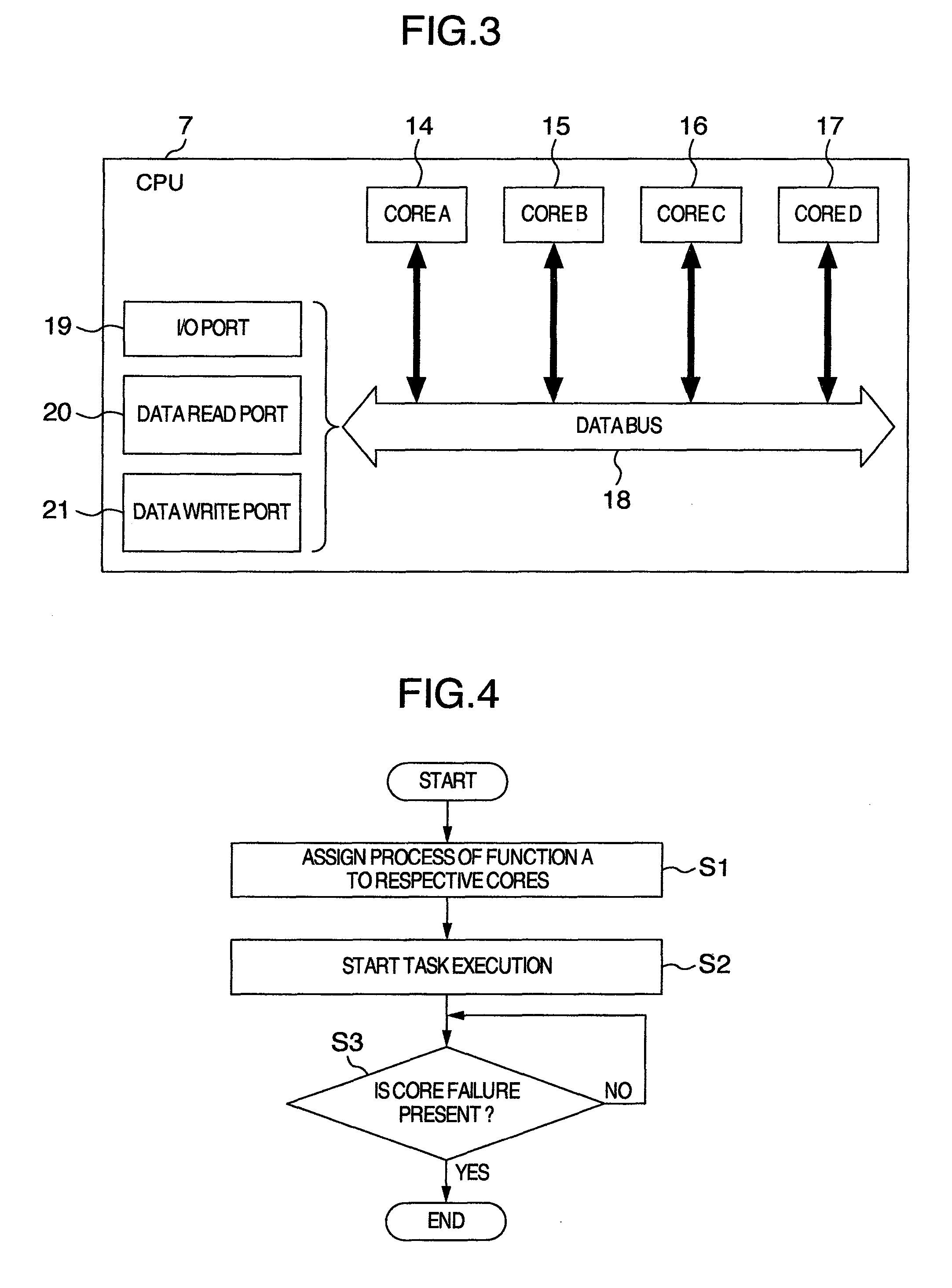
Multi-Core Processing System for Vehicle Control Or An Internal Combustion Engine Controller
ActiveUS20100138693A1Less of computational burdenEasy to useSafety arrangmentsFault responseComputation processInternal combustion engine
A vehicle control multi-core system for controlling a device mounted on a vehicle by using a plurality of cores, includes a computation process unit that is executed on the plurality of cores and required for the control of the device, and a core failure determination unit that compares a result of a computation process executed by the computation process unit at a specific timing on a specific core among the plurality of cores, with a result of a computation process executed by the computation process unit at a timing different from the specific timing on another core different from the specific core among the plurality of cores to determine that a failure occurs on the specific core.
Owner:HITACHI ASTEMO LTD
Method, system and related equipment for routine test
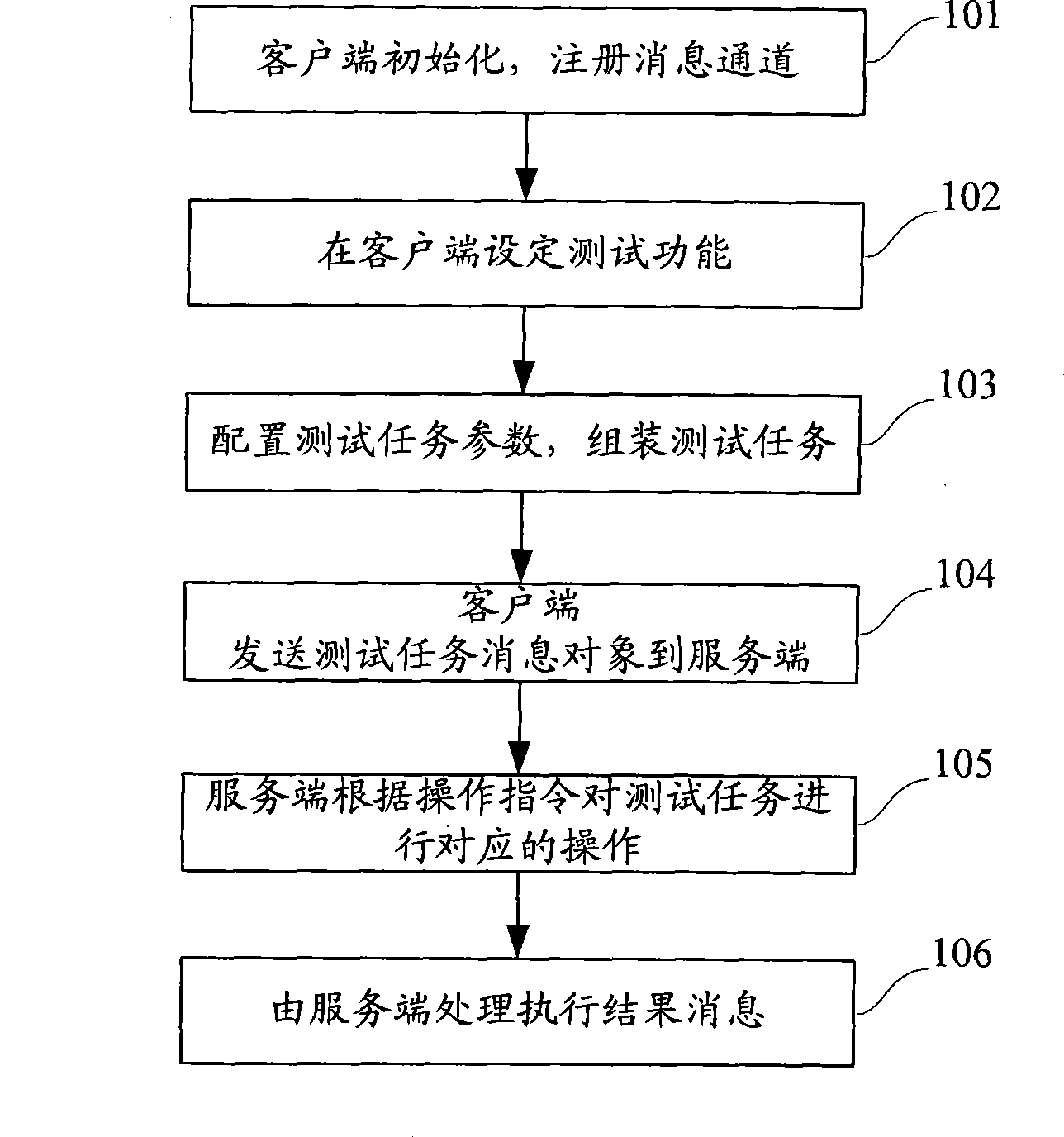
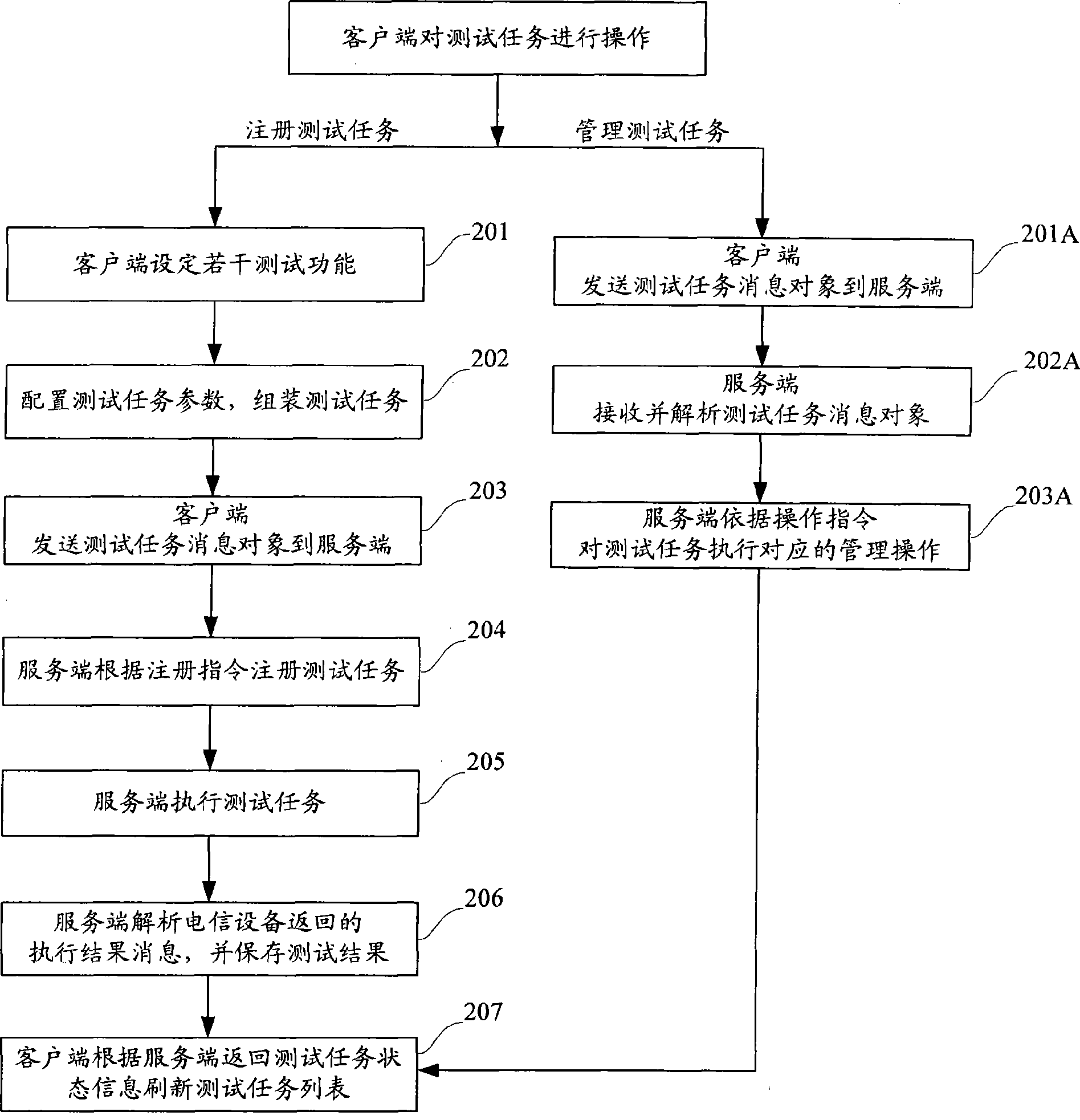
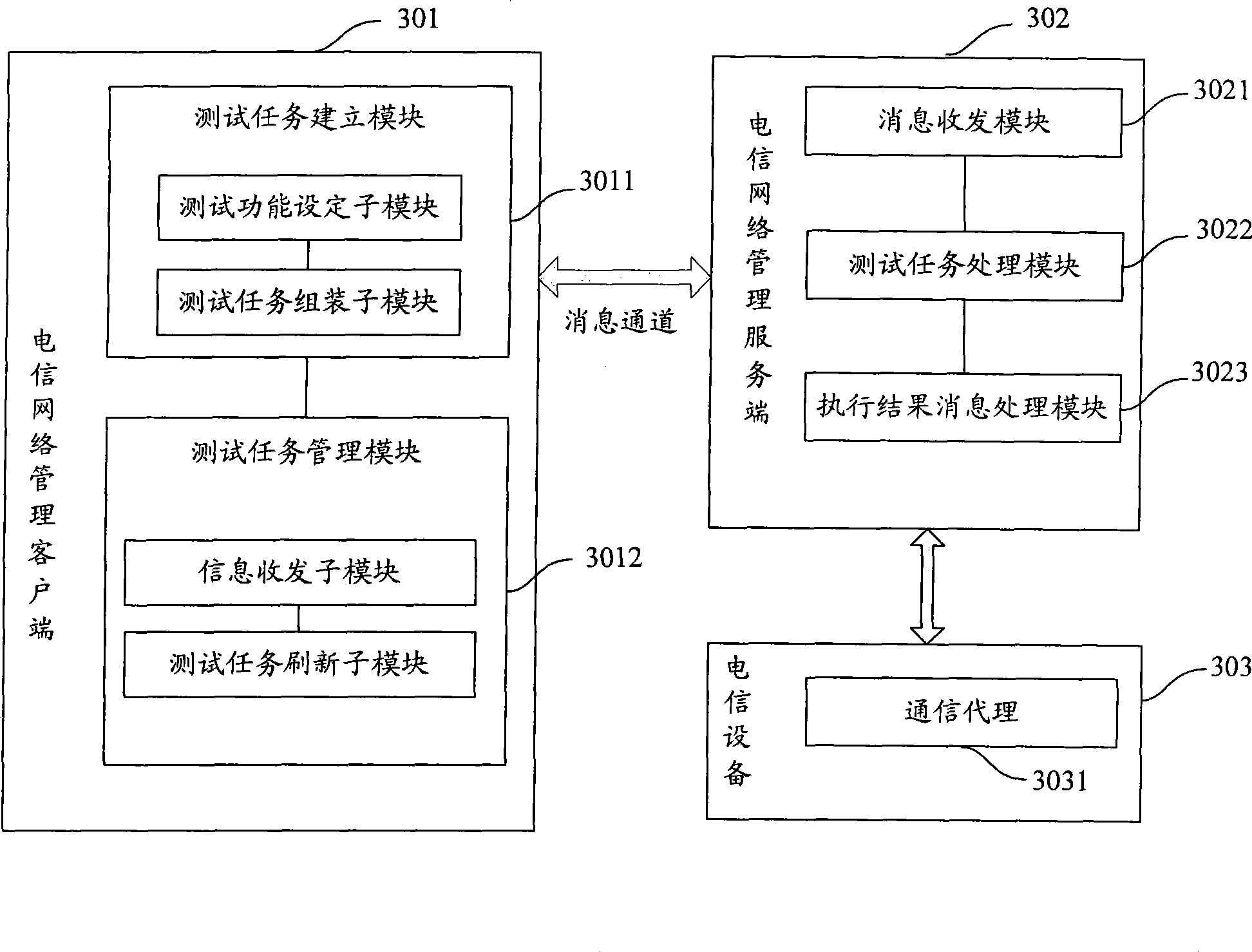
ActiveCN101483562AImprove the efficiency of daily testingRealize unified managementData switching networksTelecommunications networkInformation object
The invention discloses a routine-test method. On the basis of same or different telecommunication equipments, various test functions are established and the test functions are combined into test tasks which are then storied in a telecommunication network management service terminal. When the test tasks are executed, the test functions are analyzed and test instructions corresponding to the test functions is obtained and distributed to different telecommunication apparatuses, and then execution results returned by different telecommunication apparatuses are processes, and the processed test results are storied in a memory space assigned by the service terminal. In order to realize the method, the invention also provides a routine-test system and related devices. The routine-test system comprises a client terminal and the service terminal, wherein, the client terminal is used for packaging and sending test task information objects identified by the service terminal, the service terminal is used for receiving and analyzing the test task information objects, executing the test tasks and providing management functions for the test tasks and test results.
Owner:ZTE CORP
Internal memory and file system mixing rearrangement method based on HASH algorithm
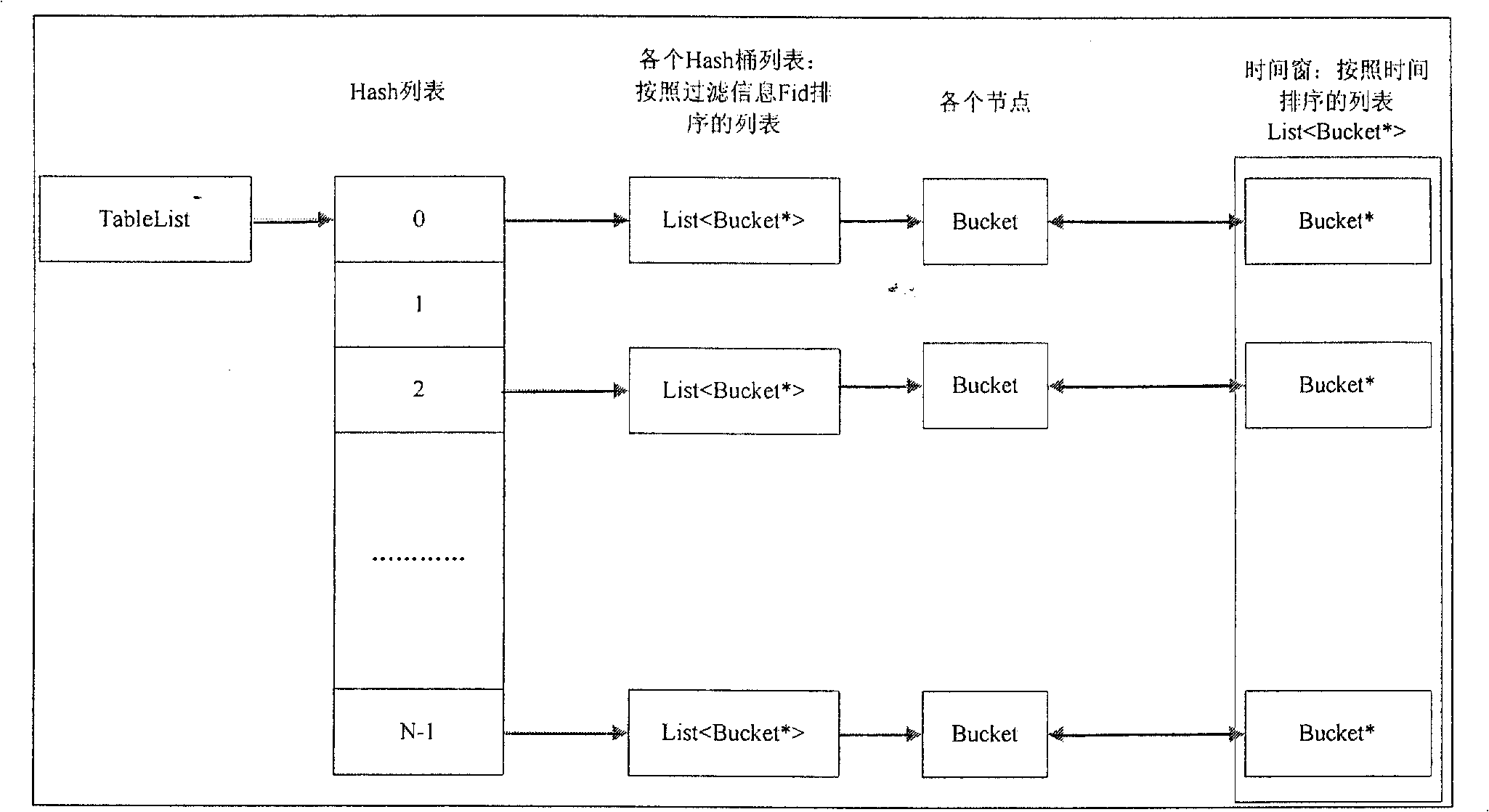
InactiveCN101493835ASolve efficiency problemsSolve functionAccounting/billing servicesSpecial data processing applicationsInternal memoryFile system
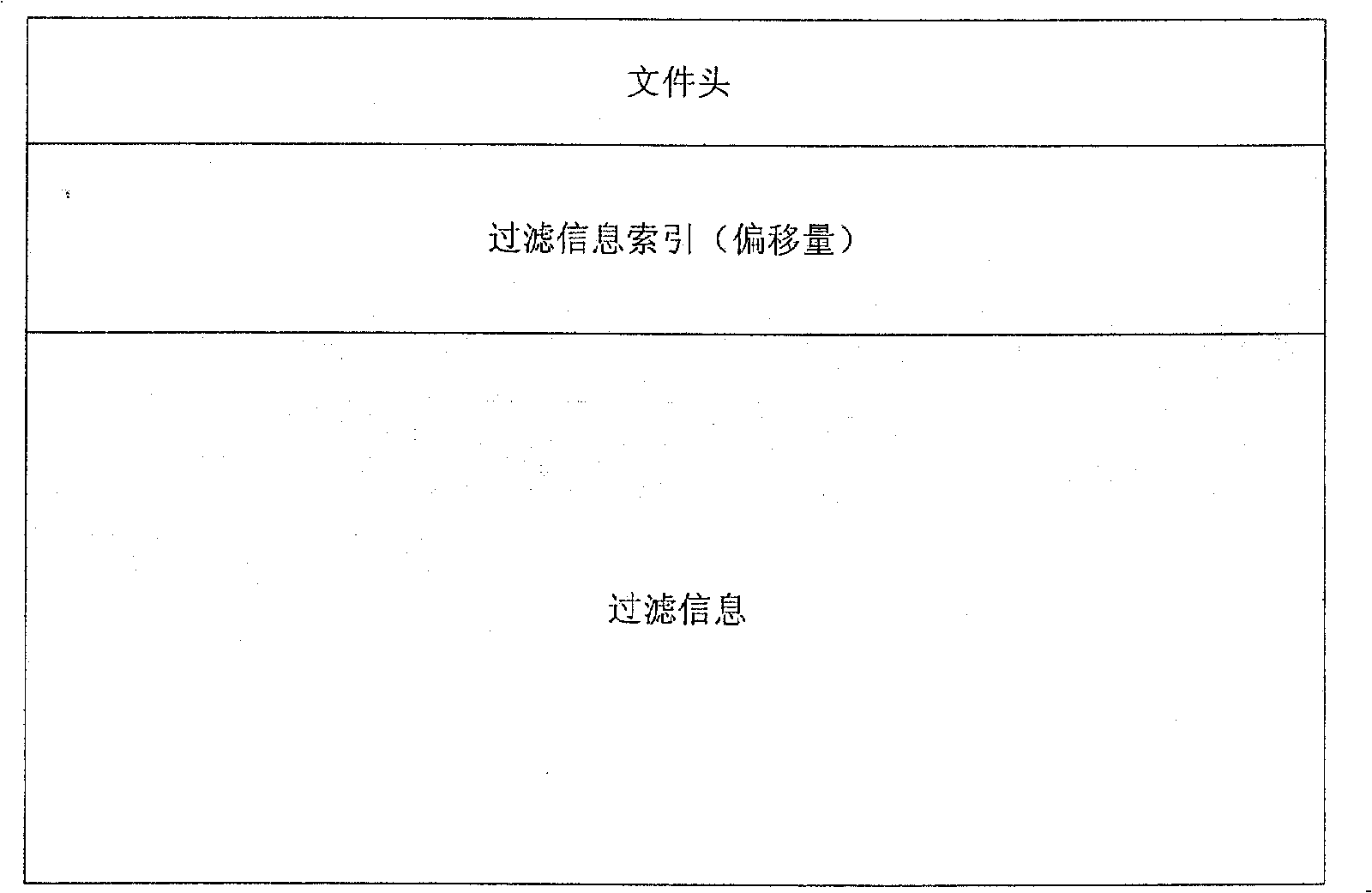
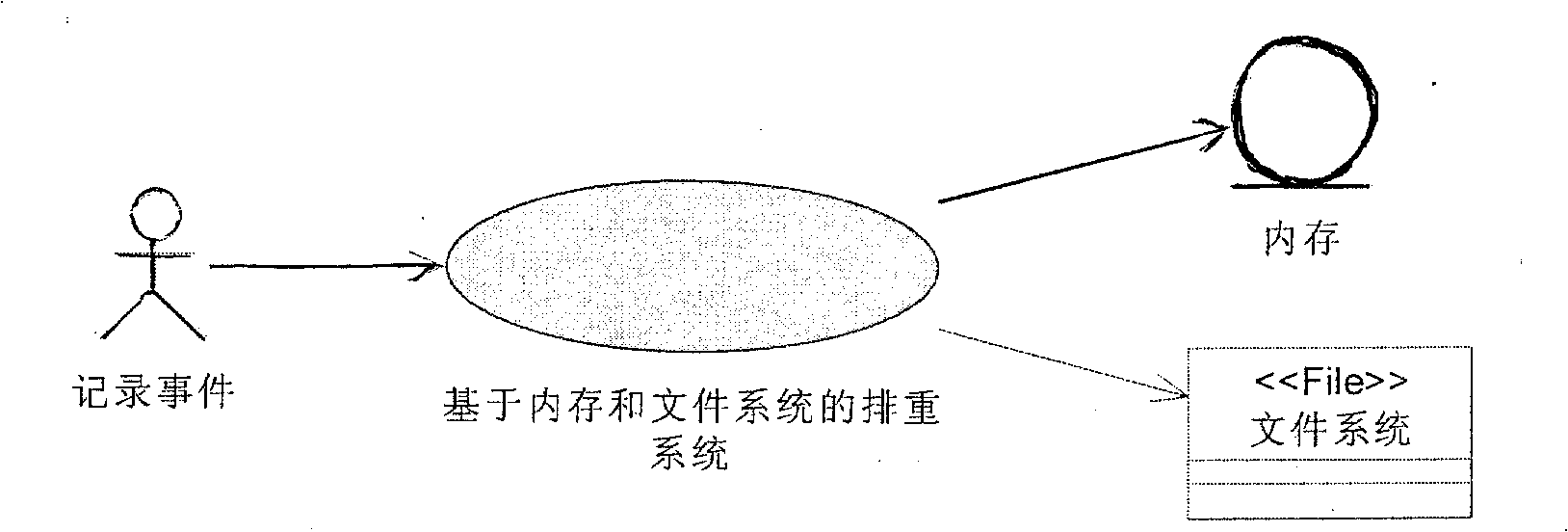
The invention relates to an implement method based on mixed tautology removal of an HASH algorithm memory and a file system, which adopts the combination of the tautology removal of the memory and the tautology removal of the file system so as to achieve a win-win result of data storage use space and processing efficiency. The implement method has the procedure that tautology removal information in a certain period of time is loaded into the memory and the tautology removal of the memory is adopted, and beyond the time the tautology removal of the document is adopted. The implement method mainly has the following steps: step 1. tautology removal configuration information (record format information, tautology removal types) is loaded into the memory; step 2. the tautology removal information in a certain period of time (configurable) is loaded into a private memory; step 3. the tautology removal of memory is performed, i.e., the tautology is removed according to the filtering information in the memory; and step 4. tautology removal of a file is performed, the tautology is removed according to the historical filtering information in the file. The storage structure of the information of the tautology removal in the memory has two characteristics of HASH lists and time window.
Owner:LINKAGE SYST INTEGRATION
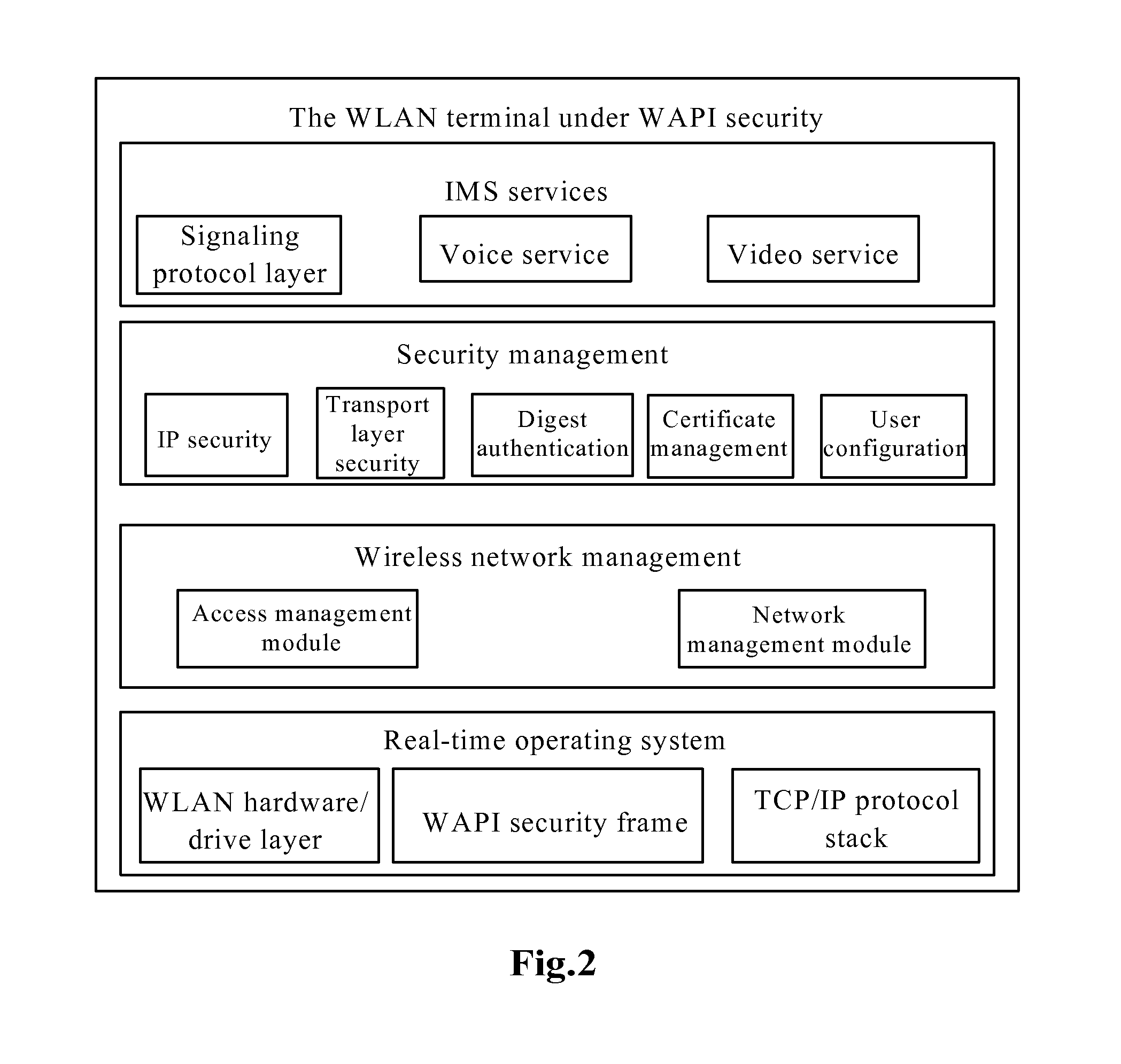
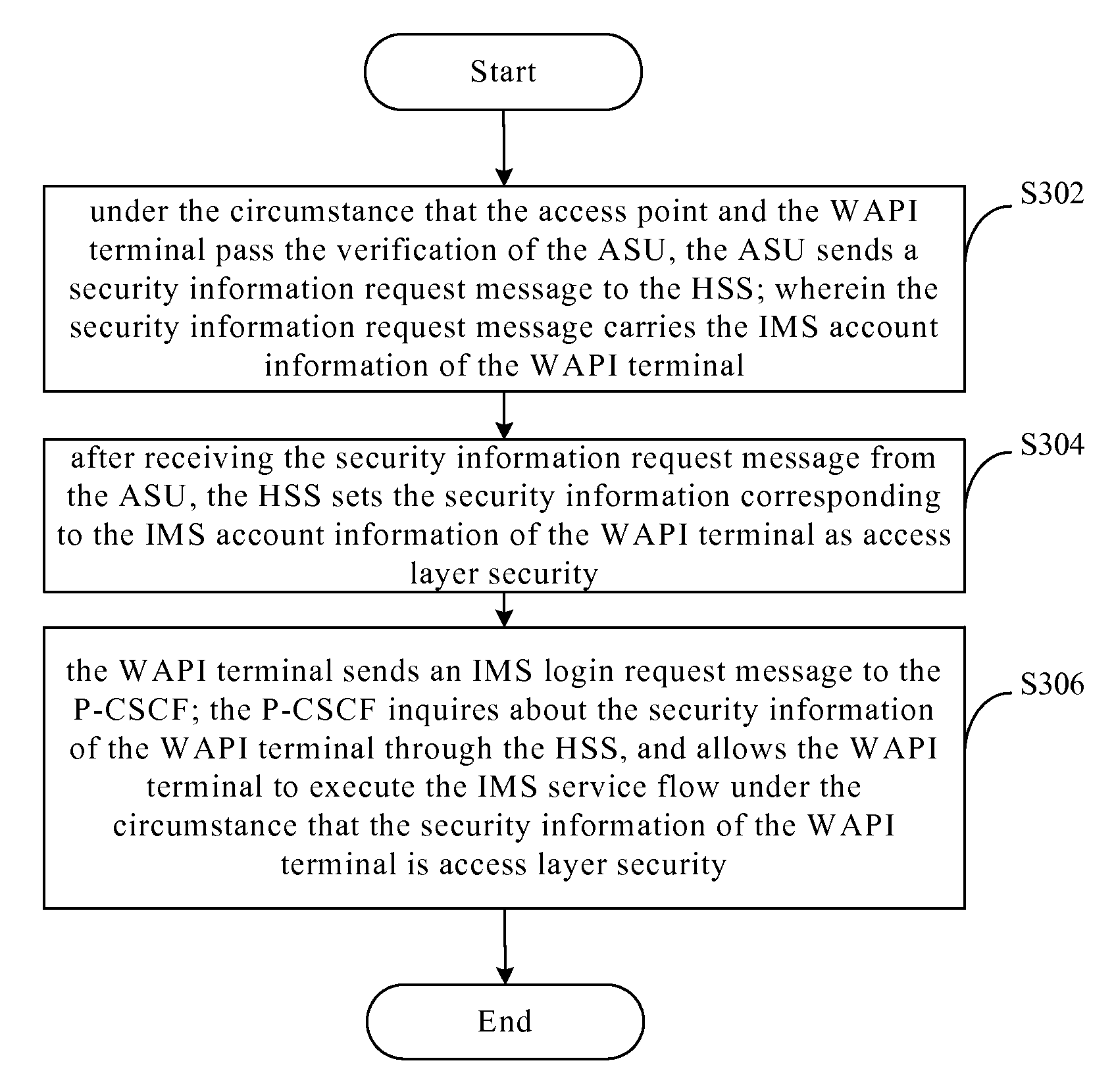
Security management method and system for wapi terminal accessing IMS network
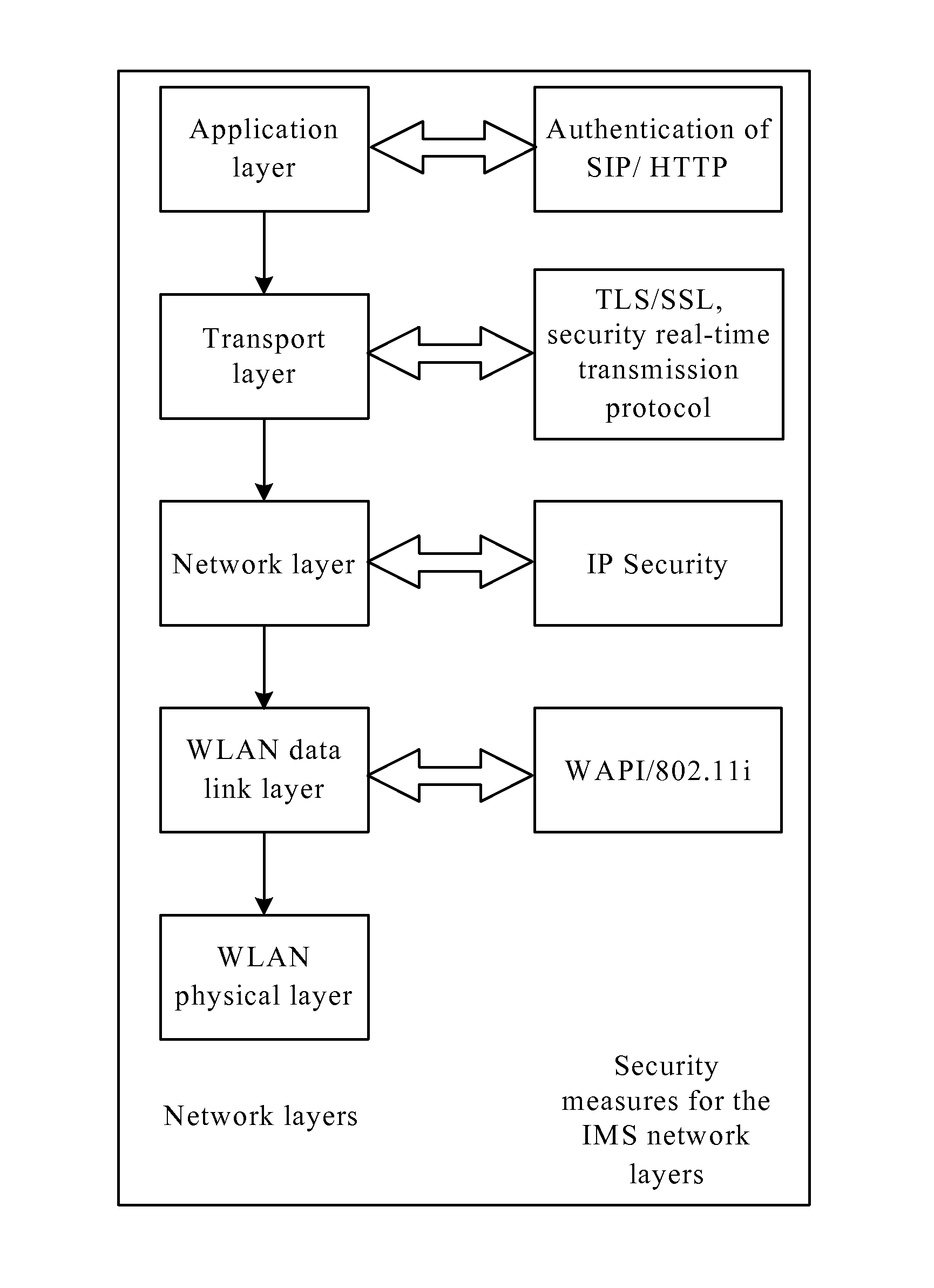
InactiveUS20110276798A1Reduce power consumptionImprove user experienceEnergy efficient ICTDigital data processing detailsService flowSession control
The present invention discloses a security management method and a security management system for a WAPI terminal accessing an IMS network. The method comprises: an authentication service unit (ASU) sending, under the circumstance that an access point and the WAPI terminal pass the verification of the ASU, a security information request message to a home subscriber server (HSS) (S302); the HSS setting security information corresponding to the IMS account information of the WAPI terminal as access layer security after receiving the security information request message from the ASU (S304); a proxy-call session control function (P-CSCF) receiving an IMS login request message from the WAPI terminal, inquiring about the security information of the WAPI terminal through the HSS, and allowing the WAPI terminal to execute an IMS service flow under the circumstance that the security information of the WAPI terminal is the access layer security (S306).
Owner:ZTE CORP
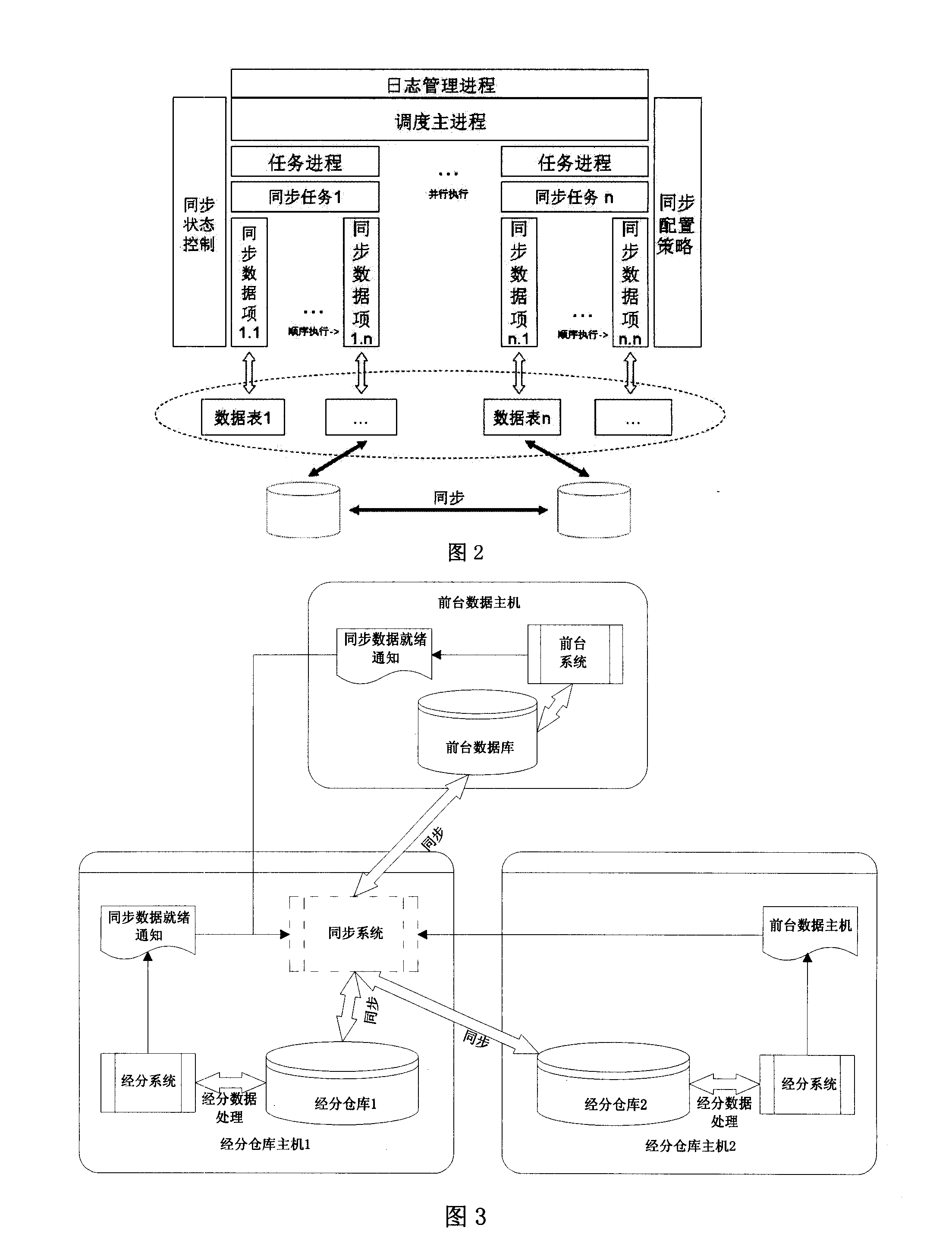
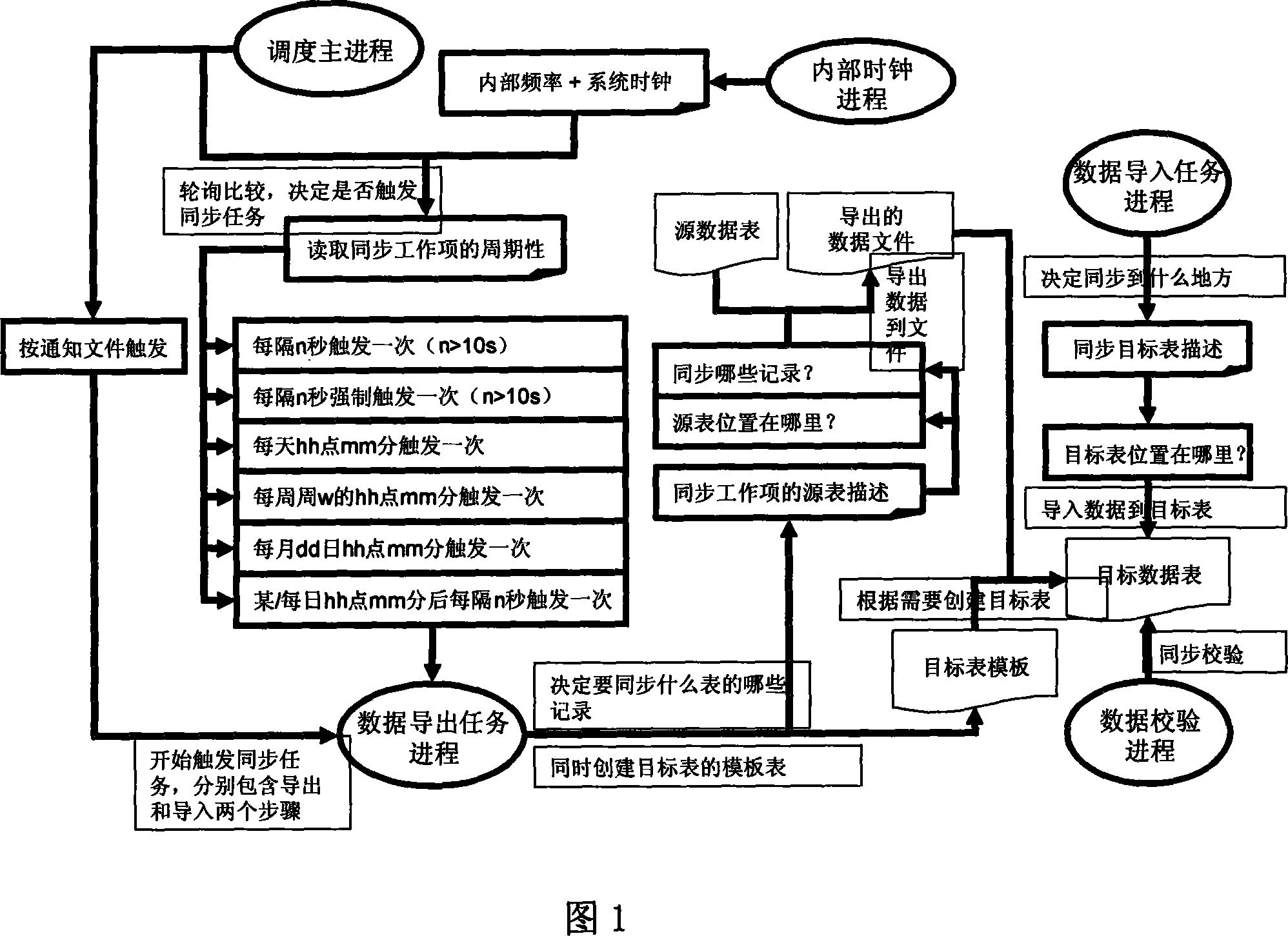
Data synchronization method for double-nucleus library
ActiveCN101226527AEasy to manageIncrease resource consumptionRedundant operation error correctionSpecial data processing applicationsFile synchronizationResource consumption
The invention discloses a binuclear base data synchronization method, which is characterized in that the binuclear base comprises a data bin and a foreground application lib, the binuclear stores the data accessed by a business analysis system user in the data bin and stores a backup in the foreground application lib, when the business analysis system user accesses, the invention uses multilayer mechanism that when the access of the foreground application lib fails, the business analysis system automatically switches to access the data bin, the data between the data bin and the foreground application lib according to self periodicity to realize real-time synchronization via a synchronization system. The invention realizes a plurality of periodicities of synchronization as timed synchronization, circulating synchronization or trigger synchronization, which can be managed according to missions to manage the data demanding synchronization, eliminate the system resource consumption caused by database self-synchronization mechanism and make detection on the synchronization easy. Each synchronization process can be repeated without effect on result. The invention can manually start one synchronization process, besides automatic synchronization operation.
Owner:CHINA MOBILE GROUP SICHUAN
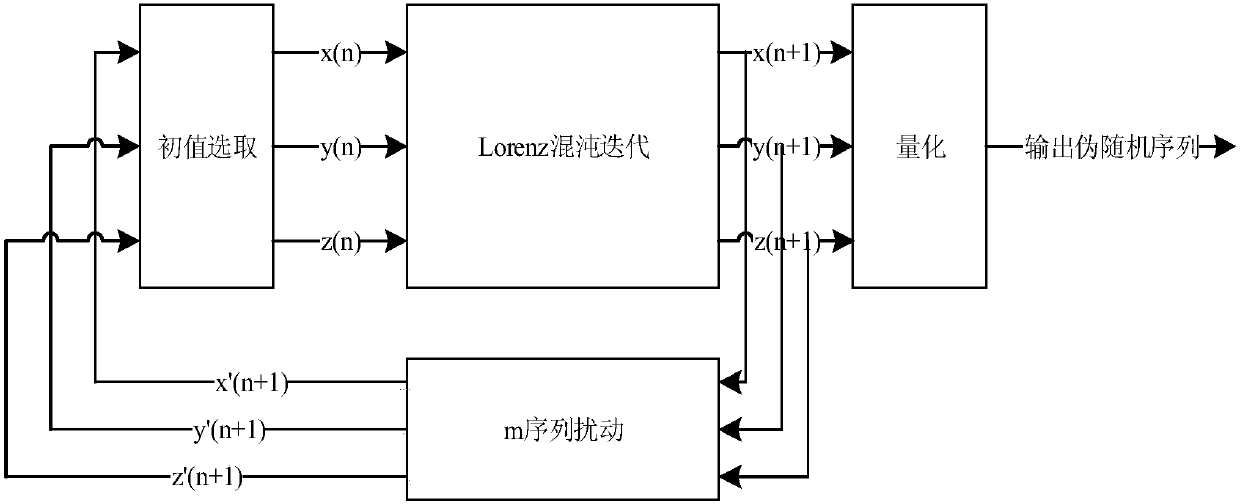
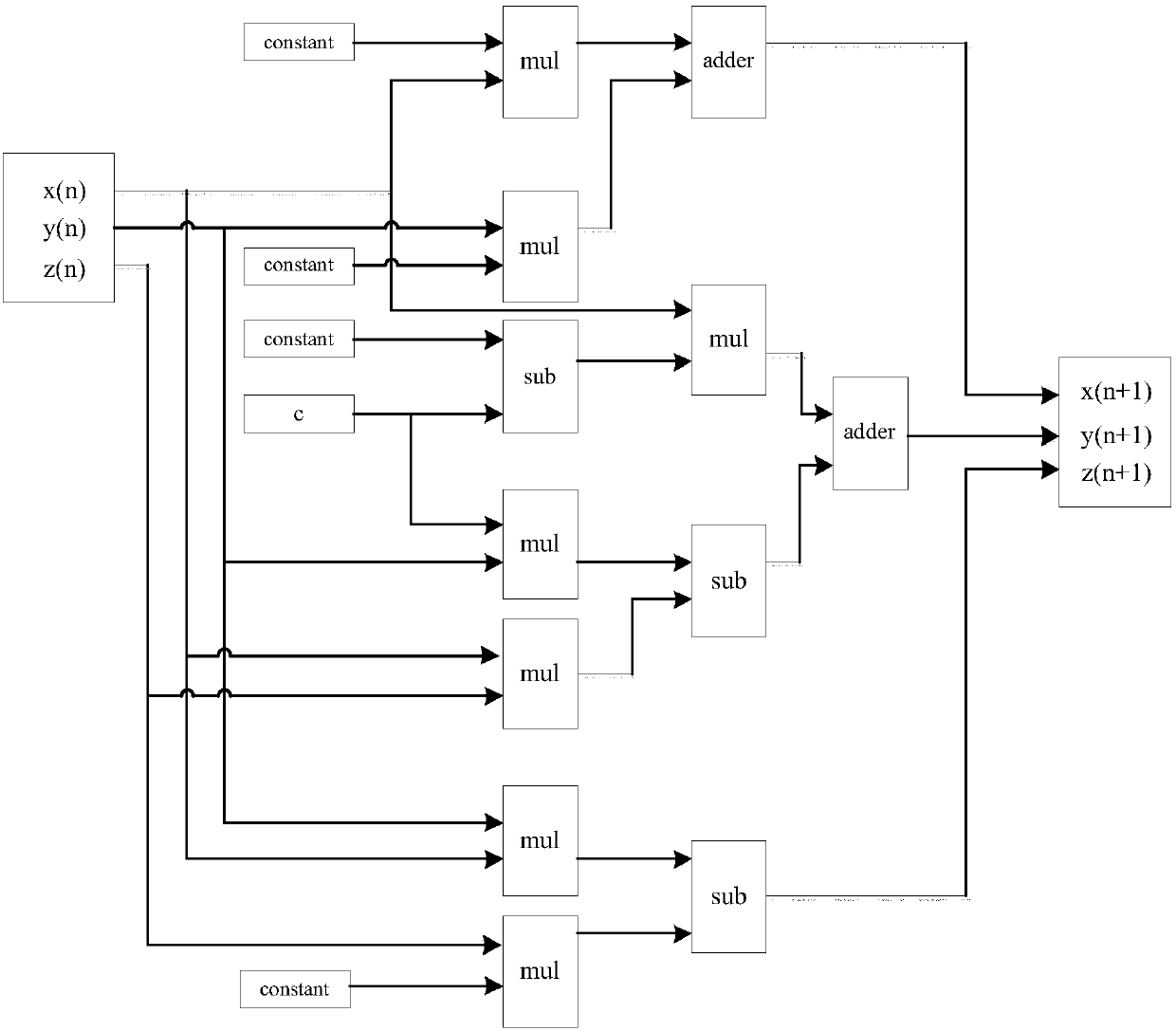
Lorenz chaotic pseudo-random sequence generator based on m sequence
InactiveCN107678729AImprove randomnessIncrease resource consumptionRandom number generatorsChaoticSequence design
Owner:SOUTHEAST UNIV
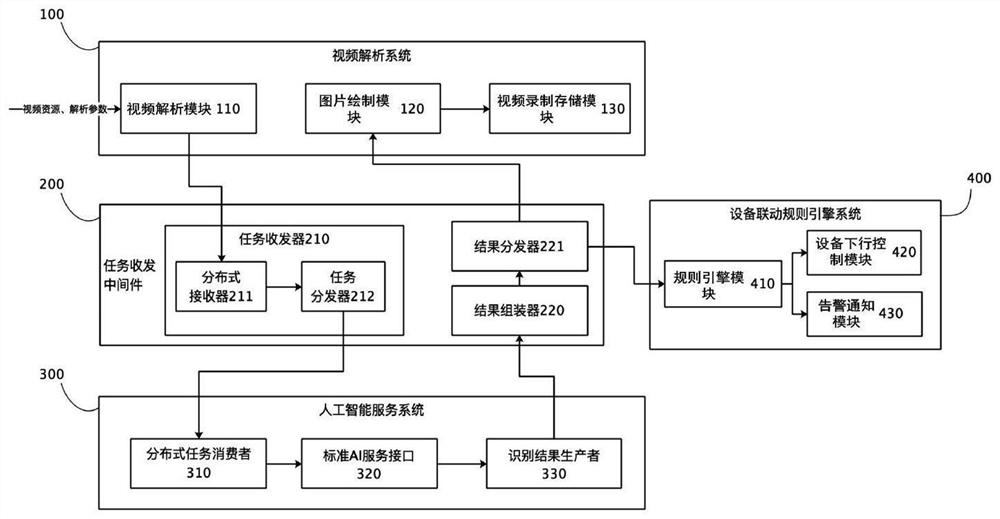
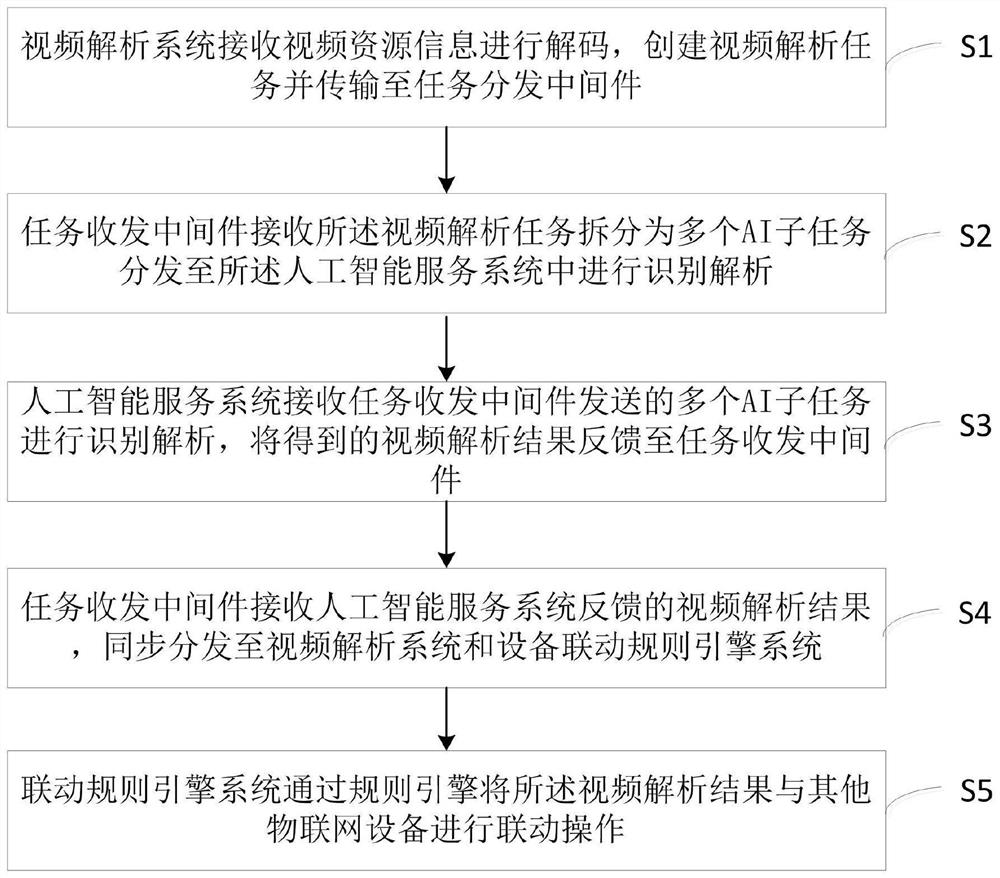
Equipment linkage system and method based on distributed artificial intelligence video analysis
PendingCN112183222AUnlimited expansion of AI servicesRich recognition result resourcesResource allocationCharacter and pattern recognitionVideo monitoringDistributed structure
The embodiment of the invention provides an equipment linkage system and method based on distributed artificial intelligence video analysis. The equipment linkage system comprises a video analysis system, task transceiving middleware, an artificial intelligence service system and an equipment linkage rule engine system.According to the equipment linkage system and method based on distributed artificial intelligence video analysis, an application system of artificial intelligence and the Internet of Things is adopted, video monitoring is subjected to Internet of Things, a distributed structureis adopted in the system, the real-time performance of video analysis and the stability and expandability of artificial intelligence analysis can be improved, and the linkage control problem of videoequipment in the Internet of Things is better solved through the equipment linkage function. According to the invention, video resources can be accessed to carry out decoding analysis processing, structural data of AI analysis can be synchronously output and linked with other Internet of Things devices, and video recording and storage can be carried out.
Owner:方株(武汉)科技有限公司
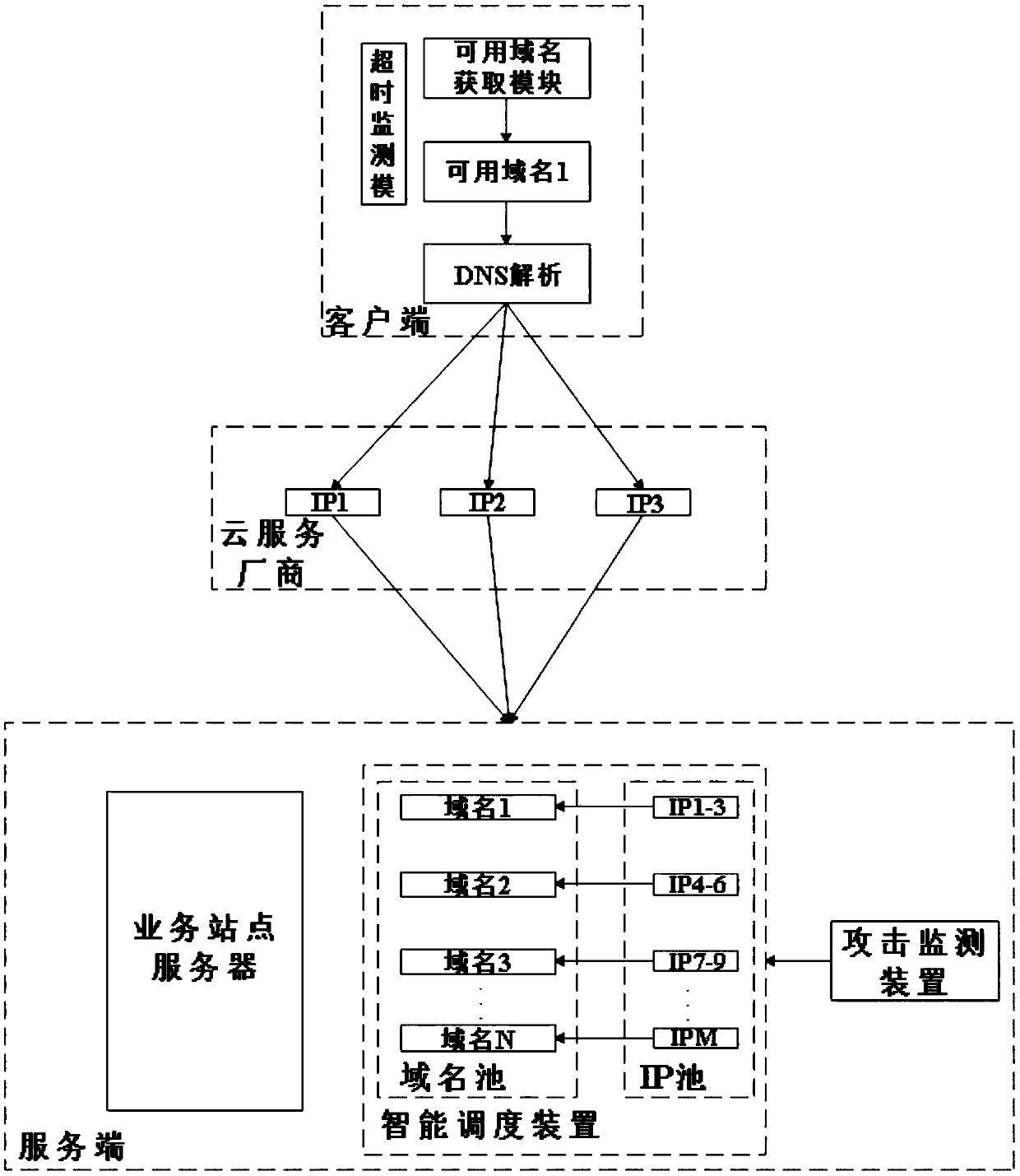
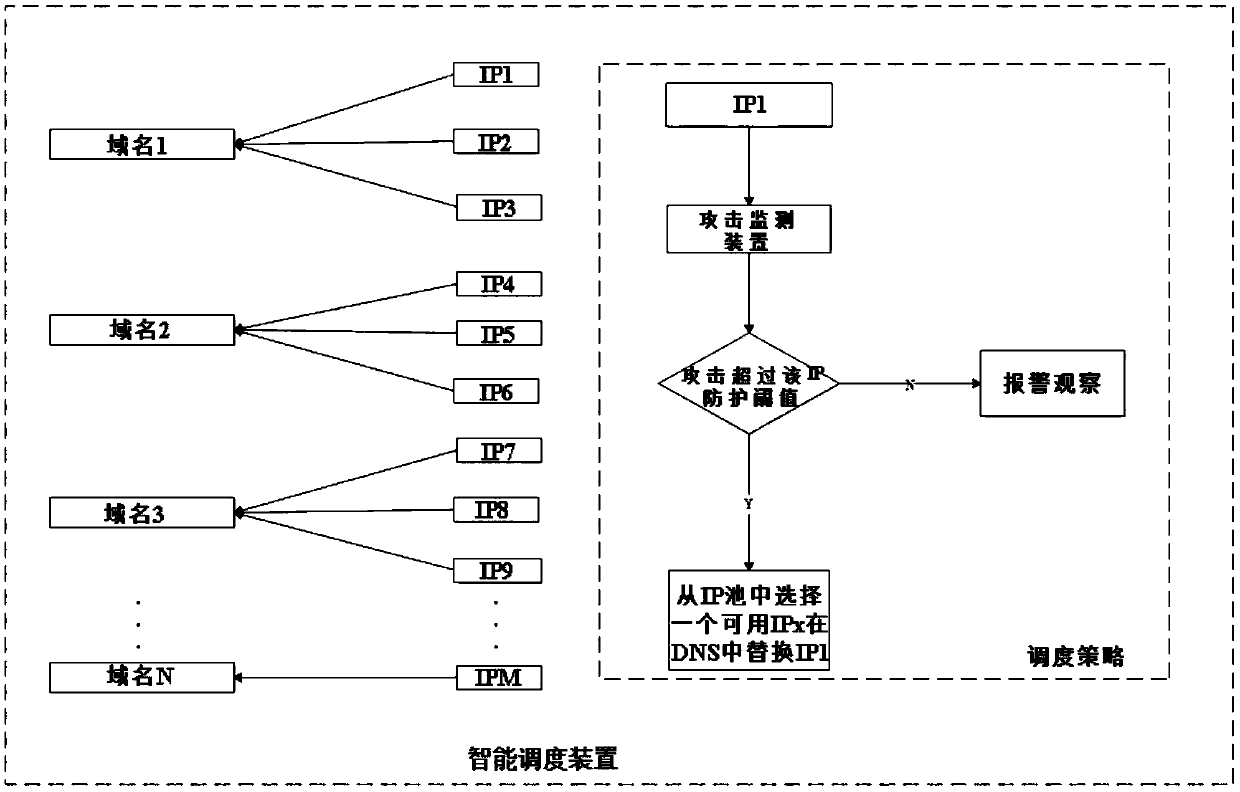
Device of using intelligent switching of multiple domain names for DDoS (Distributed Denial of Service) attack defence
The invention discloses a device of using intelligent switching of multiple domain names for DDoS (Distributed Denial of Service) attack defence. The device includes a domain name acquisition module and a timeout monitoring module disposed at a client, and also includes an attack monitoring device and an intelligent scheduling device disposed at a service end. The domain name acquisition module acquires the at least two available domain names from an available domain name pool of a service end intelligent scheduling device at an interval of time T, one thereof is used as a currently used domain name, and the rest is used as an alternate domain name. The timeout monitoring module monitors time when the client issues a request to the service end. The attack monitoring device carries out real-time monitoring, and determines a domain name under an attack. The intelligent scheduling device schedules the domain name under the attack if the attack monitoring device detects the domain name under the attack. The device of using intelligent switching of the multiple domain names for DDoS (Distributed Denial of Service) attack defence can paralyze an attacker in certain time, prolong time after which an attack is initiated thereby again, increase attack resource and cost consumption of the attacker, increase attack difficulty, reduce impacts caused by the attack, and thus achieve the purpose of defence against the DDoS attack.
Owner:成都知道创宇信息技术有限公司
Systems and methods of achieving equal distribution of packets in a multicore system which acts as a tunnel end point
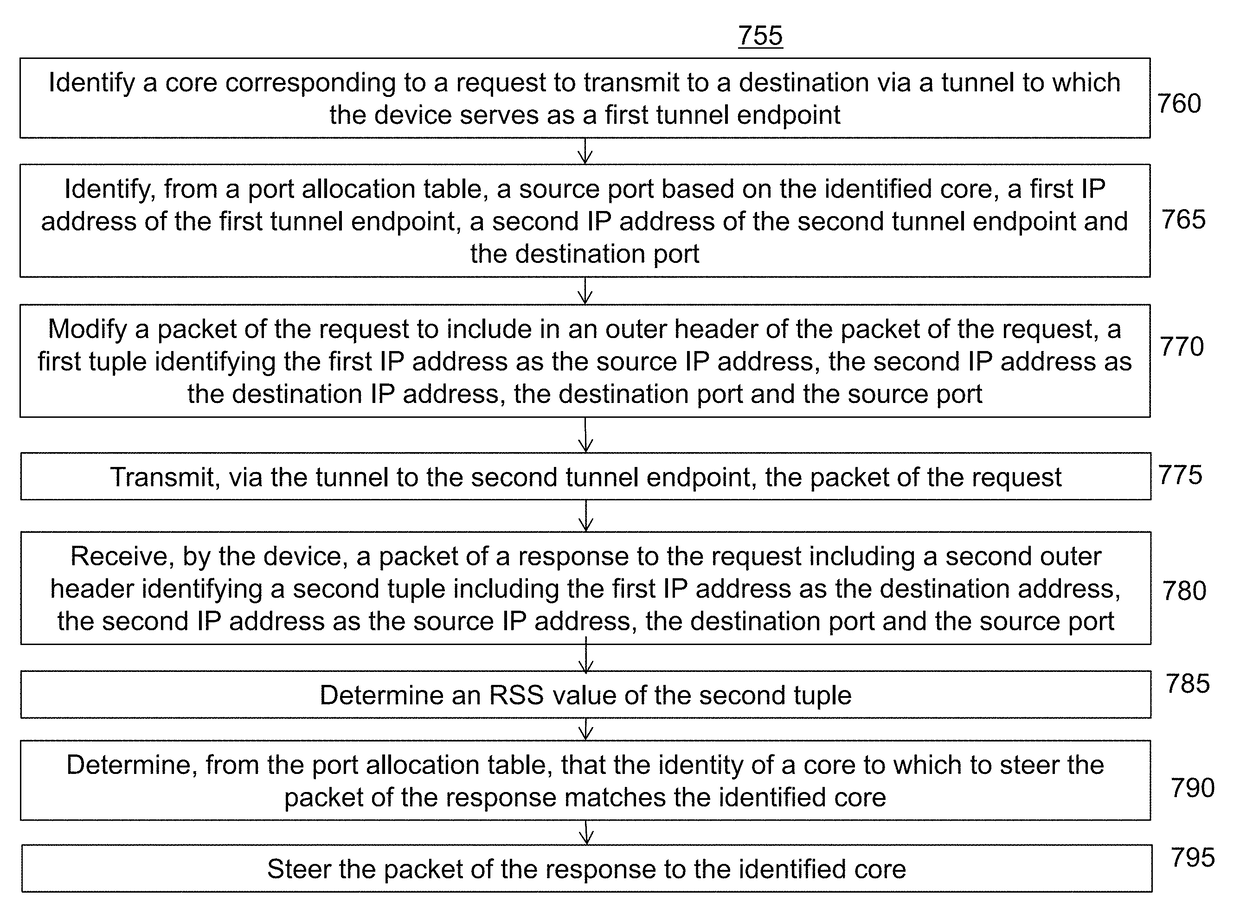
ActiveUS9923818B2Improve latencyIncrease resource consumptionNetworks interconnectionIp addressComputer science
The present disclosure is directed towards systems and methods of steering packets received by a multi-core device serving as a tunnel endpoint. A device including a plurality of cores identifies a core corresponding to a request to transmit to a destination via a tunnel. The tunnel is established between the first tunnel endpoint and a second tunnel endpoint. The device identifies, from a port allocation table, a source port based on the identified core, a first IP address of the first tunnel endpoint, a second IP address of the second tunnel endpoint and the destination port to steer a response to the request to the identified core. The device modifies a packet of the request to include in an outer header of the packet of the request, a first tuple identifying the first IP address, the second IP address, the destination port and the identified source port.
Owner:CITRIX SYST INC
Method and apparatus for detecting secondary synchronization signal
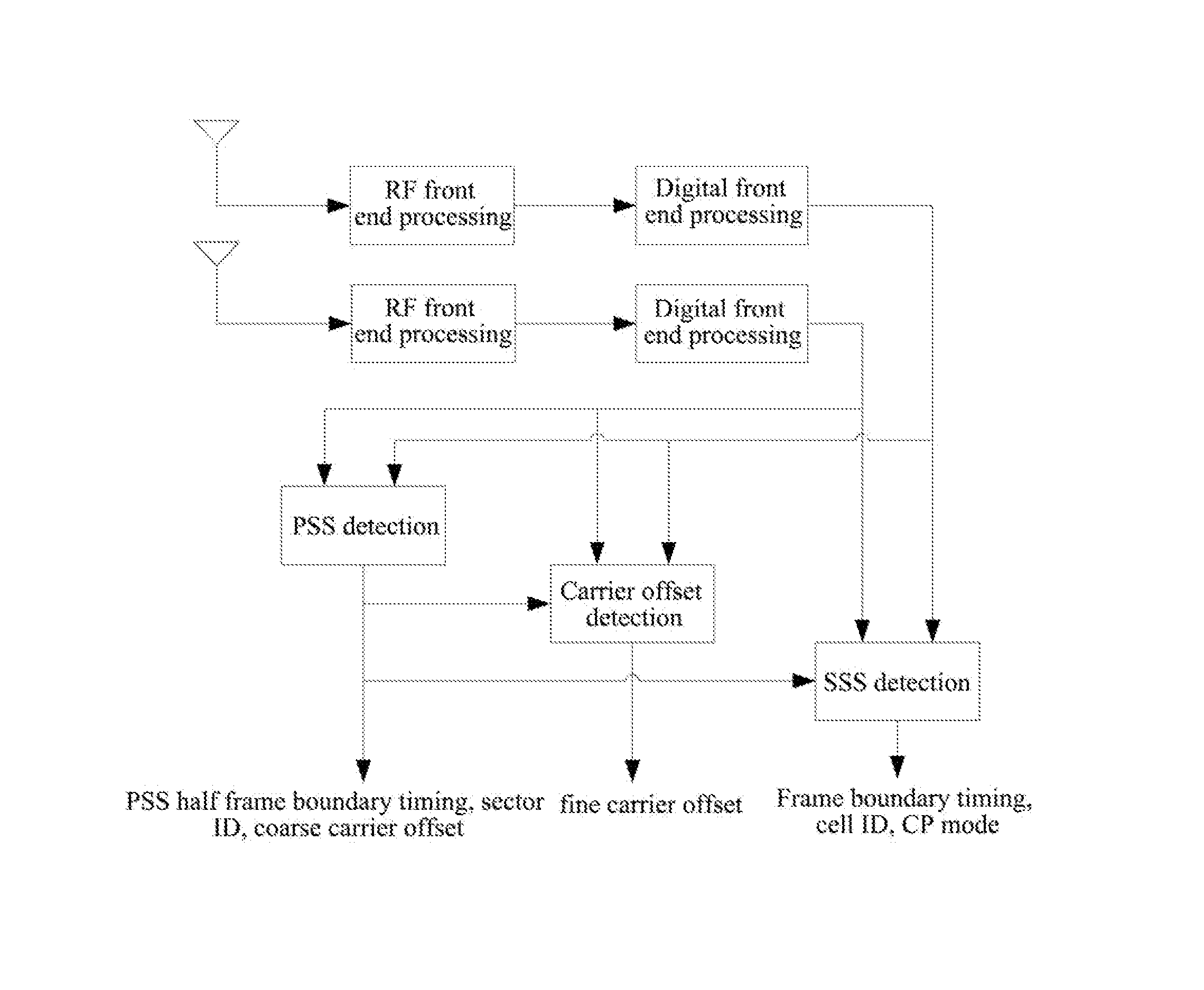
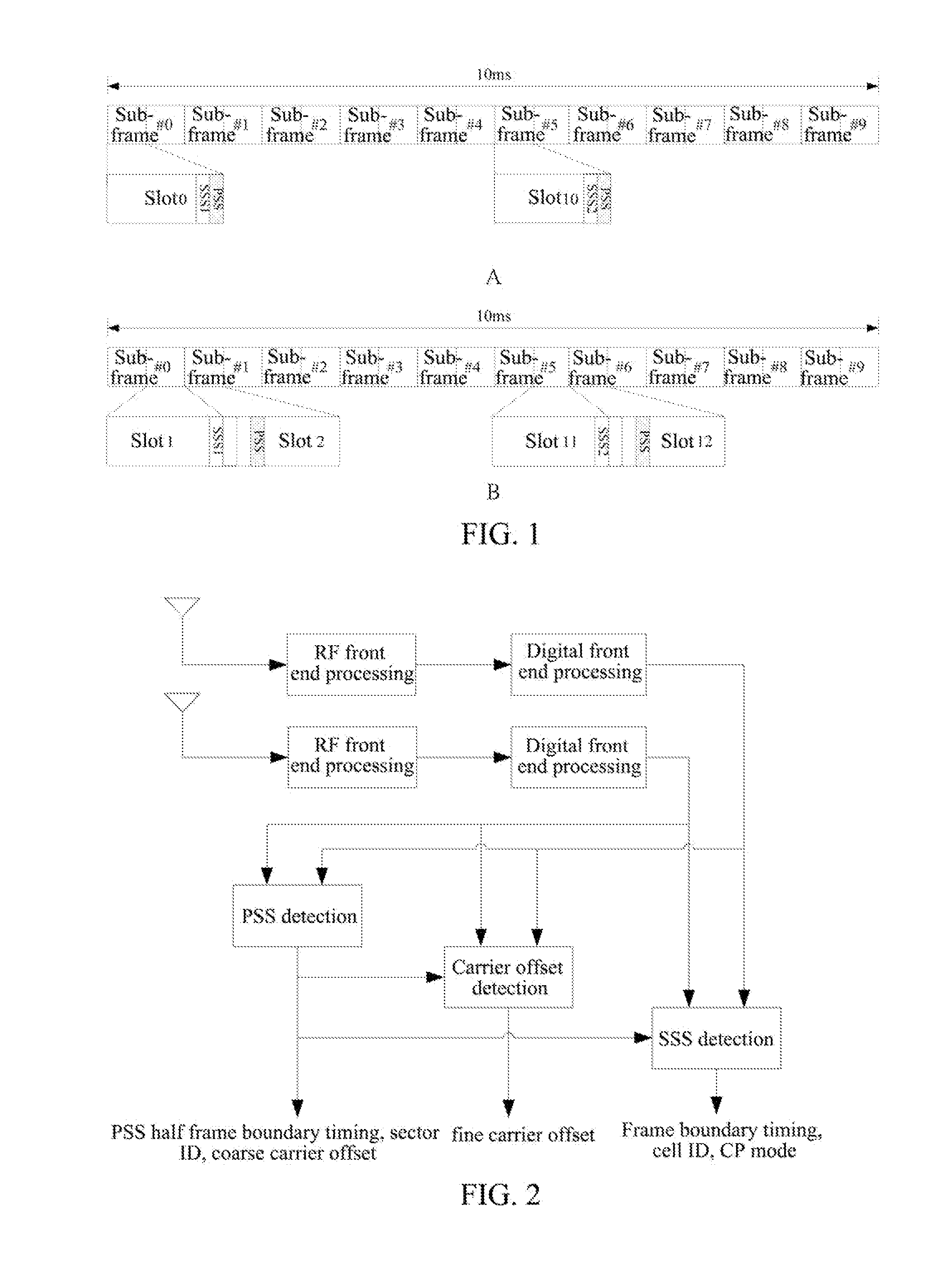
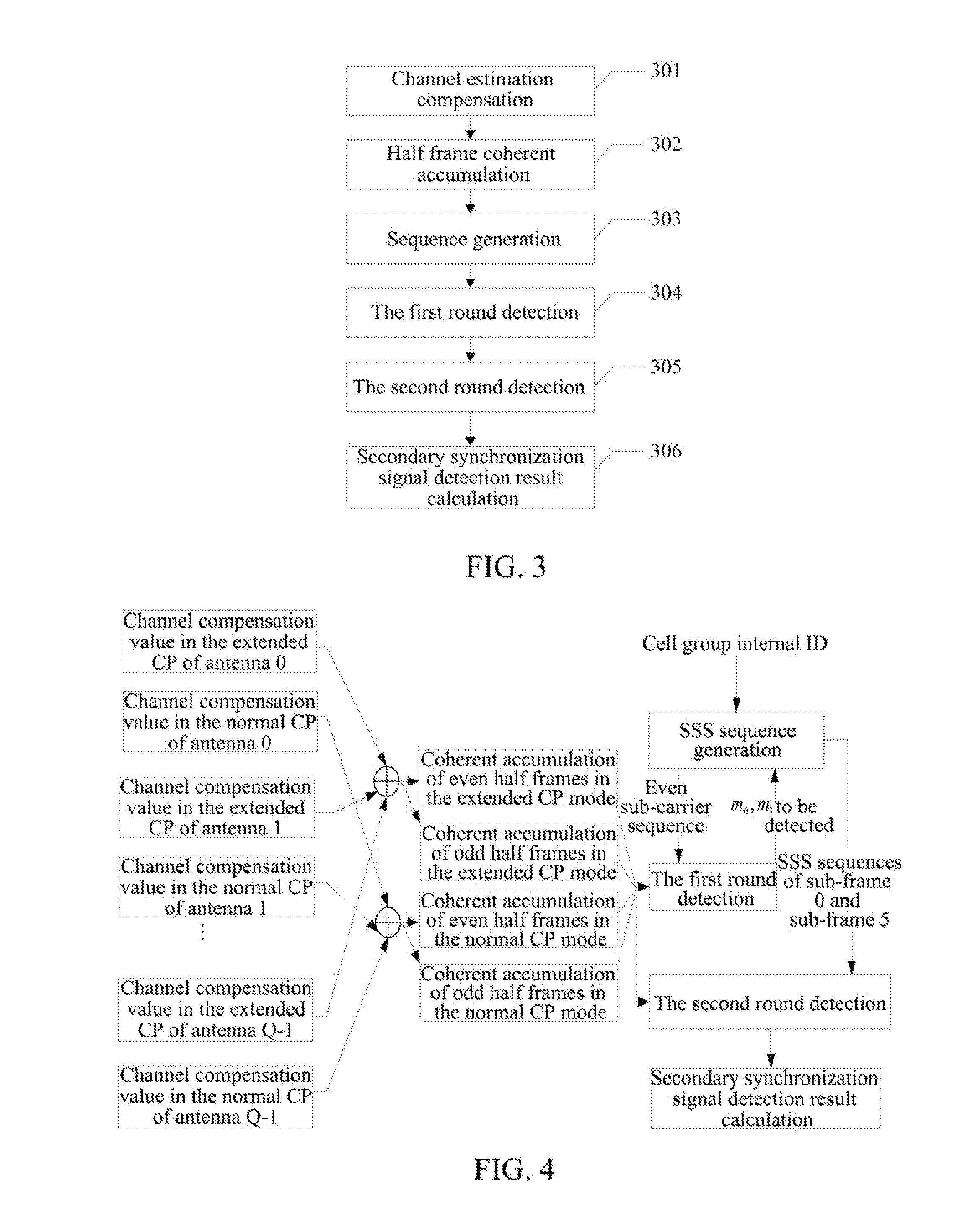
ActiveUS8576810B2Computational complexity is reducedReduce the amount of calculationSynchronisation arrangementModulated-carrier systemsTelecommunicationsCell ID
a method and apparatus for detecting a secondary synchronization signal, the method including: calculating a channel estimation compensation value of each sub-carrier of a Secondary Synchronization Signal (SSS) symbol in different Cyclic Prefix (CP) modes; obtaining-a coherent accumulative results of even half frames and odd half frames of each sub-carrier according to the channel estimation compensation value of each sub-carrier of said SSS symbol; generating a SSS sequence; obtaining an index of the SSS sequence corresponding to an over-threshold value of a first round detection, determining indexes composed of the SSS sequence used in a second round detection according to said index, using coherent accumulative results of all the sub-carriers in the even and odd half frames and SSS sequences of all the sub-carriers to obtain an over-threshold value of the second round detection; and obtaining a CP mode, and calculating a cell ID and a radio frame boundary.
Owner:SANECHIPS TECH CO LTD
Security management method and system for WAPI terminal accessing IMS network
InactiveUS8595485B2Lower quality of serviceIncrease resource consumptionEnergy efficient ICTKey distribution for secure communicationService flowSafety management systems
The present invention discloses a security management method and a security management system for a WAPI terminal accessing an IMS network. The method comprises: an authentication service unit (ASU) sending, under the circumstance that an access point and the WAPI terminal pass the verification of the ASU, a security information request message to a home subscriber server (HSS) (S302); the HSS setting security information corresponding to the IMS account information of the WAPI terminal as access layer security after receiving the security information request message from the ASU (S304); a proxy-call session control function (P-CSCF) receiving an IMS login request message from the WAPI terminal, inquiring about the security information of the WAPI terminal through the HSS, and allowing the WAPI terminal to execute an IMS service flow under the circumstance that the security information of the WAPI terminal is the access layer security (S306).
Owner:ZTE CORP
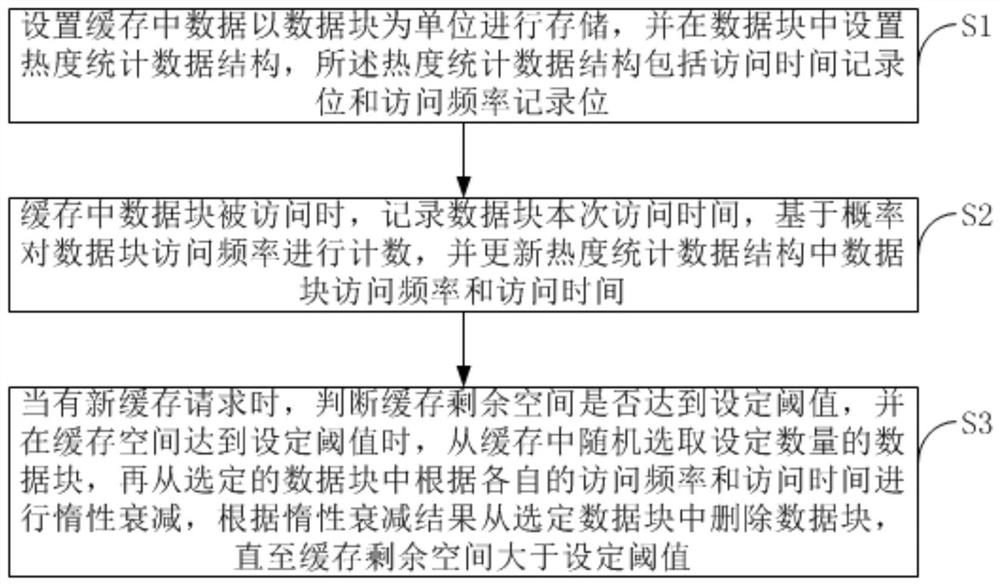
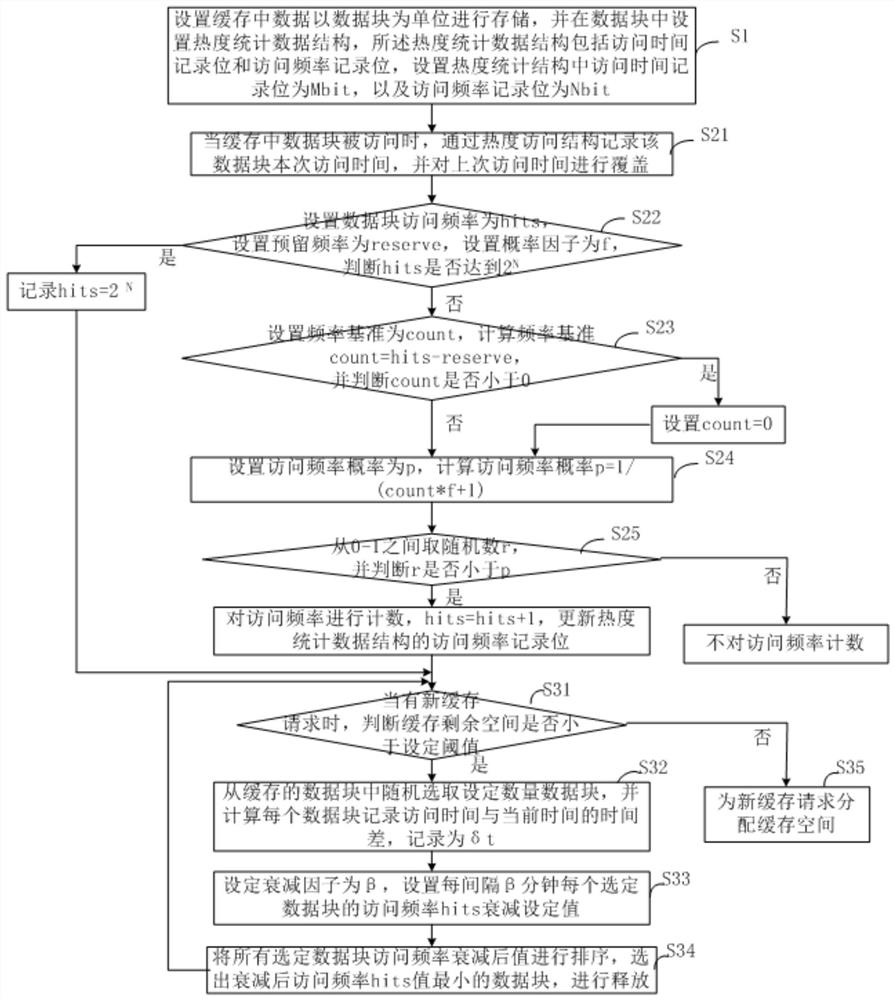
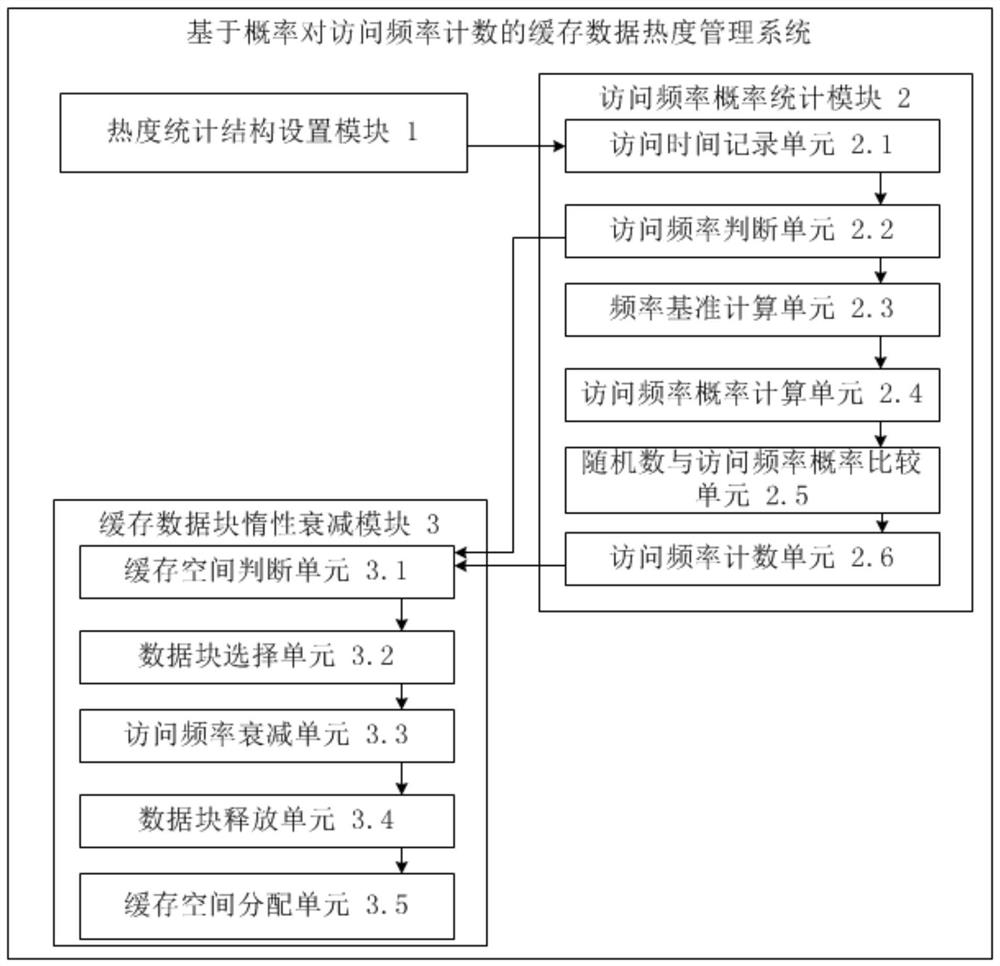
Cache data popularity management method and system for counting access frequency based on probability
ActiveCN111858403AImprove efficiencyReduce occupancyEnergy efficient computingMemory systemsAccess timeParallel computing
The invention provides a cache data popularity management method and system for counting access frequency based on probability. The method comprises the following steps: S1, setting data in a cache tobe stored by taking a data block as a unit, and setting a popularity statistical data structure in the data block, the popularity statistical data structure comprising an access time record bit and an access frequency record bit; s2, when the data block in the cache is accessed, recording the current access time of the data block, counting the access frequency of the data block based on the probability, and updating the access frequency and the access time of the data block in the popularity statistical data structure; s3, when a cache request exists, judging whether the cache residual spacereaches a set threshold value or not; and when the cache space reaches a set threshold value, randomly selecting a set number of data blocks from the cache, carrying out inertia attenuation from the selected data blocks according to respective access frequencies and access time, and deleting the data blocks from the selected data blocks according to an inertia attenuation result until the cache residual space is greater than the set threshold value.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
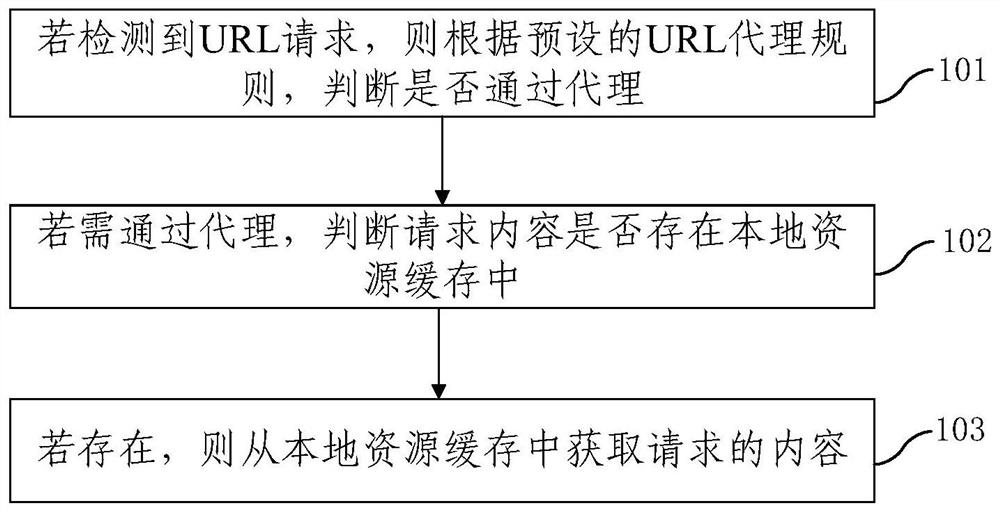
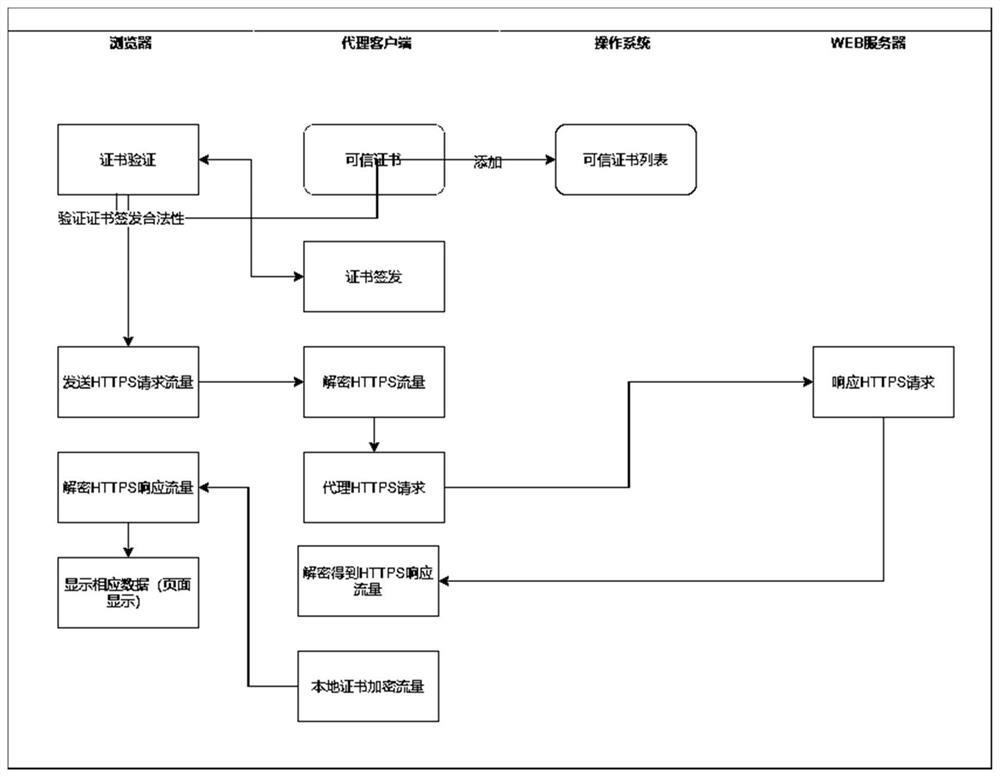
WEB site access acceleration method and device
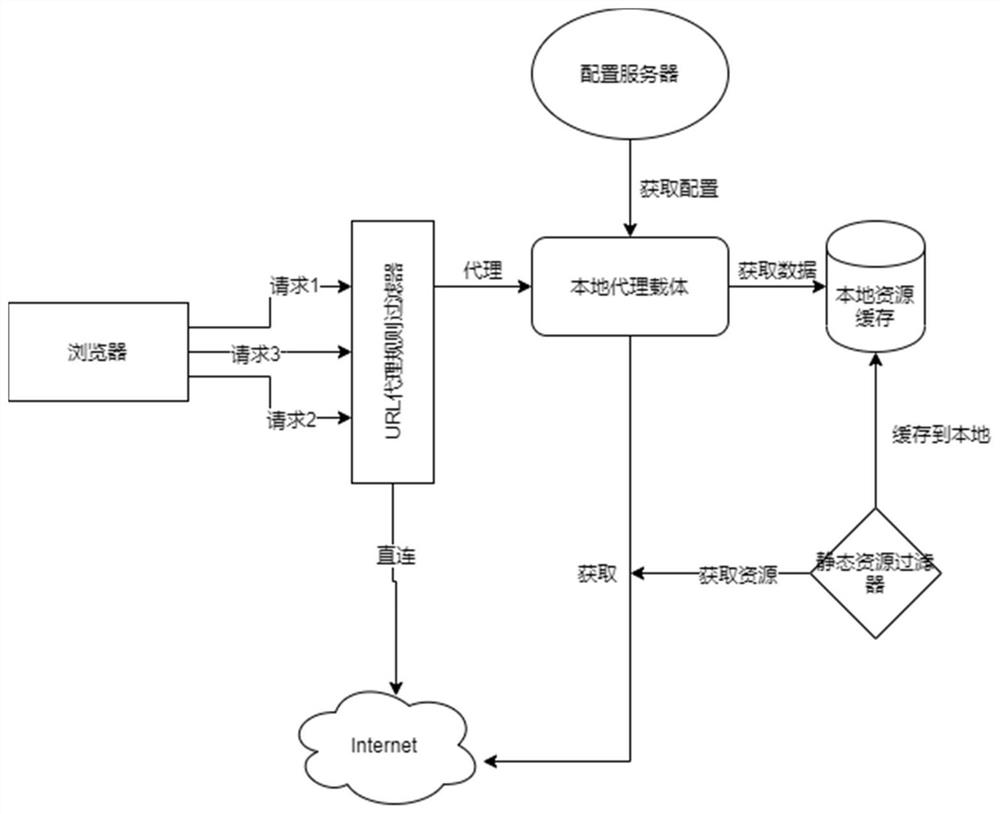
PendingCN112364274AAvoid sendingIncrease resource consumptionSpecial data processing applicationsWeb data browsing optimisationWeb siteEngineering
The embodiment of the invention provides a WEB site access acceleration method and device, and the method comprises the steps of judging whether agency is passed or not according to a preset URL agency rule if a URL request is detected; if yes, judging whether the request content exists in a local resource cache or not; and if so, obtaining the requested content from the local resource cache. According to the method, whether agency is passed or not is judged according to the preset URL agency rule, agency acceleration does not need to be carried out on all the content, and the situation that agency-free flow is sent into the agency server, and resource consumption of the agency server is increased is avoided. If the request content exists in the local resource cache, the request content isacquired from the local resource cache, and the content does not need to be requested from the proxy server, so that the load overhead of the proxy server is further reduced, the request blockage isavoided, the user experience of proxy access can be remarkably improved, meanwhile, the frequency of acquiring data from a proxy is reduced, and the data security and privacy are improved.
Owner:北京中科网威信息技术有限公司
Simultaneous frame and bit combined estimation method for EBPSK (extended binary phase shift keying) communication system
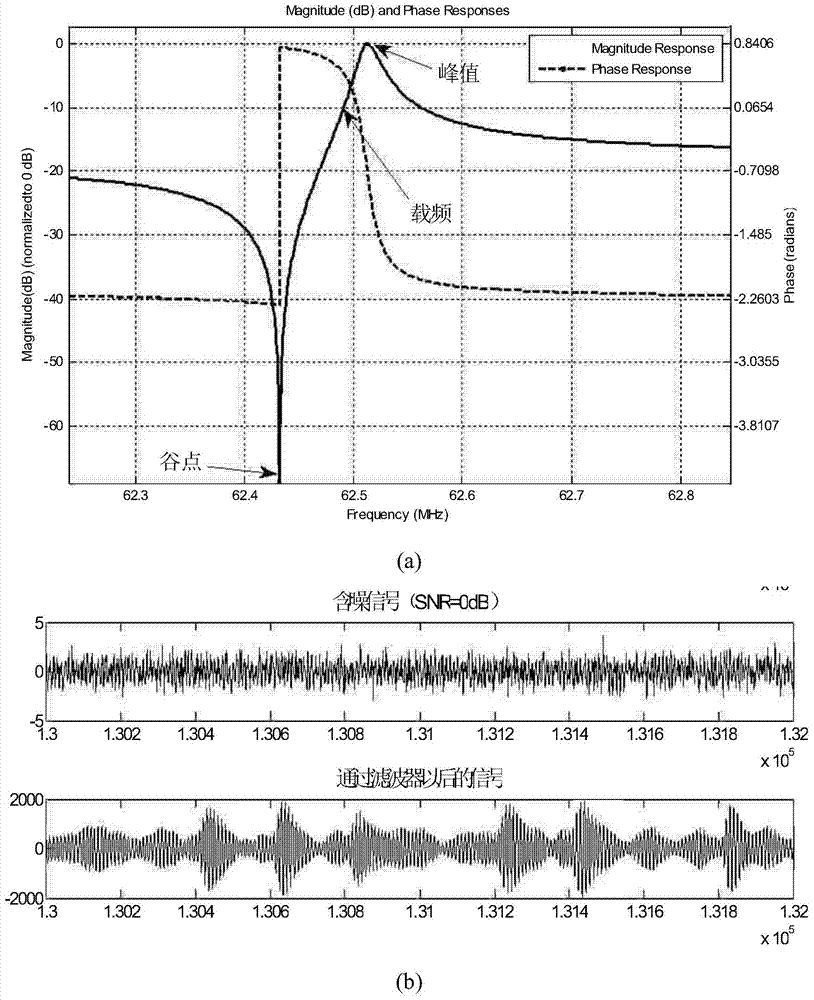
ActiveCN104506472AImprove synchronization efficiencyShorten the timePhase-modulated carrier systemsHigh level techniquesData streamCommunications system
The invention discloses a simultaneous frame and bit combined estimation method for an EBPSK (extended binary phase shift keying) communication system. The method comprises the steps: framing sending data at a transmitting end, and then performing EBPSK modulation; sending a receiving signal into an impact filter at a receiving end, and converting the receiving signal into parasitic amplitude modulation impact at a code element '1'; performing down sampling on output data of the impact filter according to a relative relation with a baseband code element rate; calculating peak values of 13 continuous data points of each group in a data stream subjected to down sampling, marking the moment that the peak values are greater than a certain threshold value, calculating a relevance value to a frame header, and marking the moment, in which four times of the peak value is smaller than the relevance value, in the marked moments; searching the first peak value of the relevance value in the marked moment in the step, wherein the moment corresponding to the first peak value is a synchronous moment. According to the simultaneous frame and bit combined estimation method, frame and bit are simultaneously finished by one step, so that the synchronization efficiency is improved, the synchronization precision is improved, the demodulation performance is high, the synchronization expense is reduced, the transmission efficiency is high, the hardware expenses are reduced, and the receiving machine implementation cost is reduced.
Owner:苏州东奇信息科技股份有限公司
Dynamic configuration method for program memory of computer
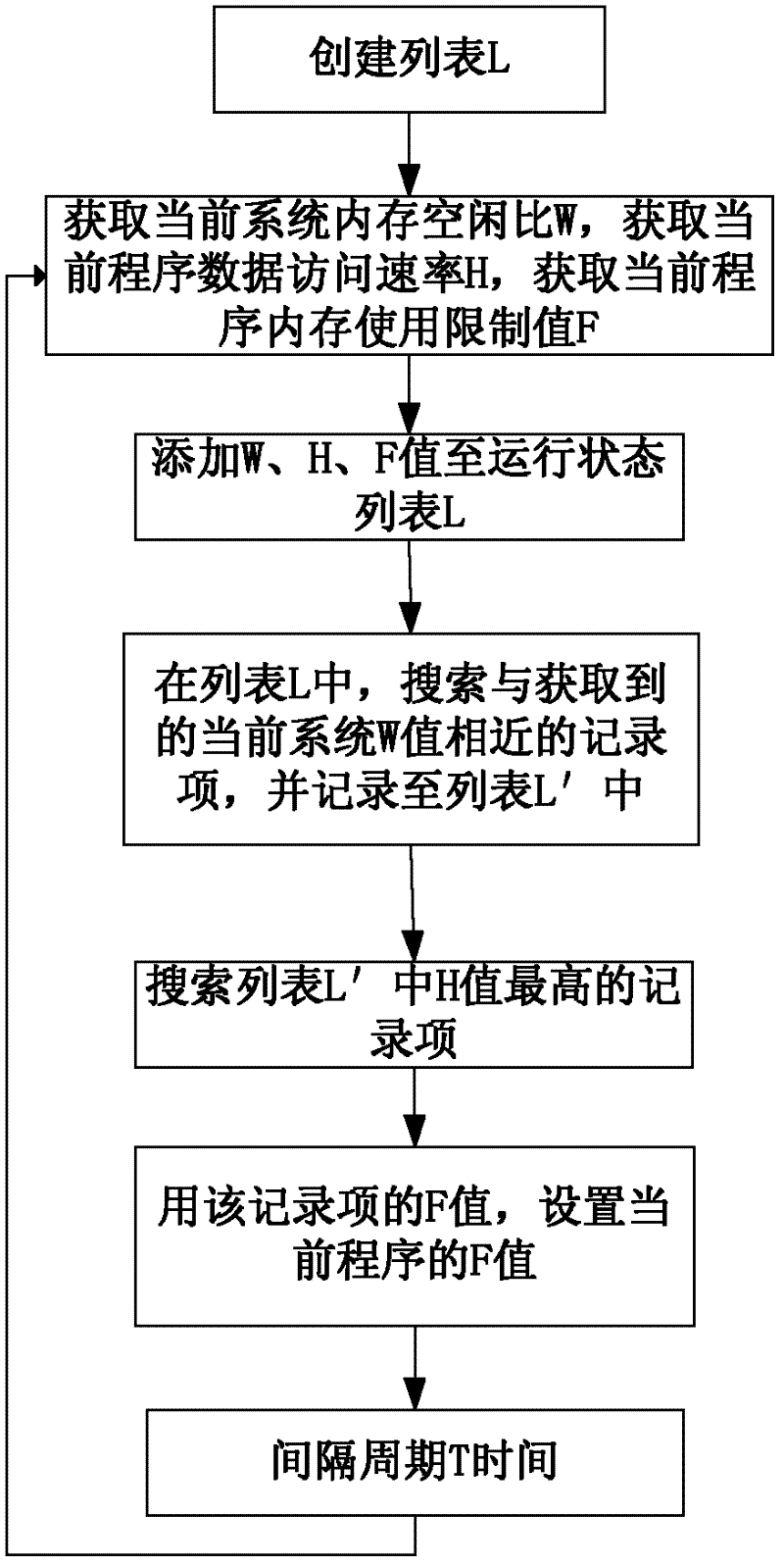
ActiveCN102495763AAvoid Improper Memory ConfigurationsImprove operating conditionsResource allocationMemory adressing/allocation/relocationComputerized systemLimit value
The invention relates to a configuration method for a program memory of a computer, and discloses a dynamic configuration method for a system memory of a computer, which aims to overcome shortcomings of inflexibility and inadaptability to change of a system environment of a memory configuration method of the prior art. The technical scheme includes that by the aid of the dynamic configuration method for a program memory of the computer, a service limit value of the memory is adjusted when a program runs by means of periodically detecting changes of an external environment, the dynamic configuration method is adaptable to environmental change at any time, and the problem of improper memory configuration due to changes of the external environment is avoided. Statistics of corresponding relation of environments and program running states is realized during long-term execution of the dynamic configuration method, and the optimal running condition under different environments of the program can be specified. Record and statistic data in a list can be more comprehensive along with extension of running time, and execution strategies based on the statistic list can be more intelligent as time goes on. The dynamic configuration method is used for intelligently configuring the memory of the computer, and running efficiency of the program can be improved.
Owner:CHENGDU YIWO TECH DEV CO LTD
Deodorant based on resource utilization
ActiveCN107320757AGood deodorizing effectIncrease resource consumptionDeodrantsChemistryCircular economy
The invention discloses a deodorant based on resource utilization. The deodorant is screenings of glass anti-mildew insulation powder with the particle size ranging from 60 mu m to 120 mu m. The deodorant has a good deodorant effect, can remove odors at any time like a common deodorant, requires no extra resource consumption and meets the requirement of cyclic economy.
Owner:南京汉旗新材料股份有限公司
A large capacity data and service management system
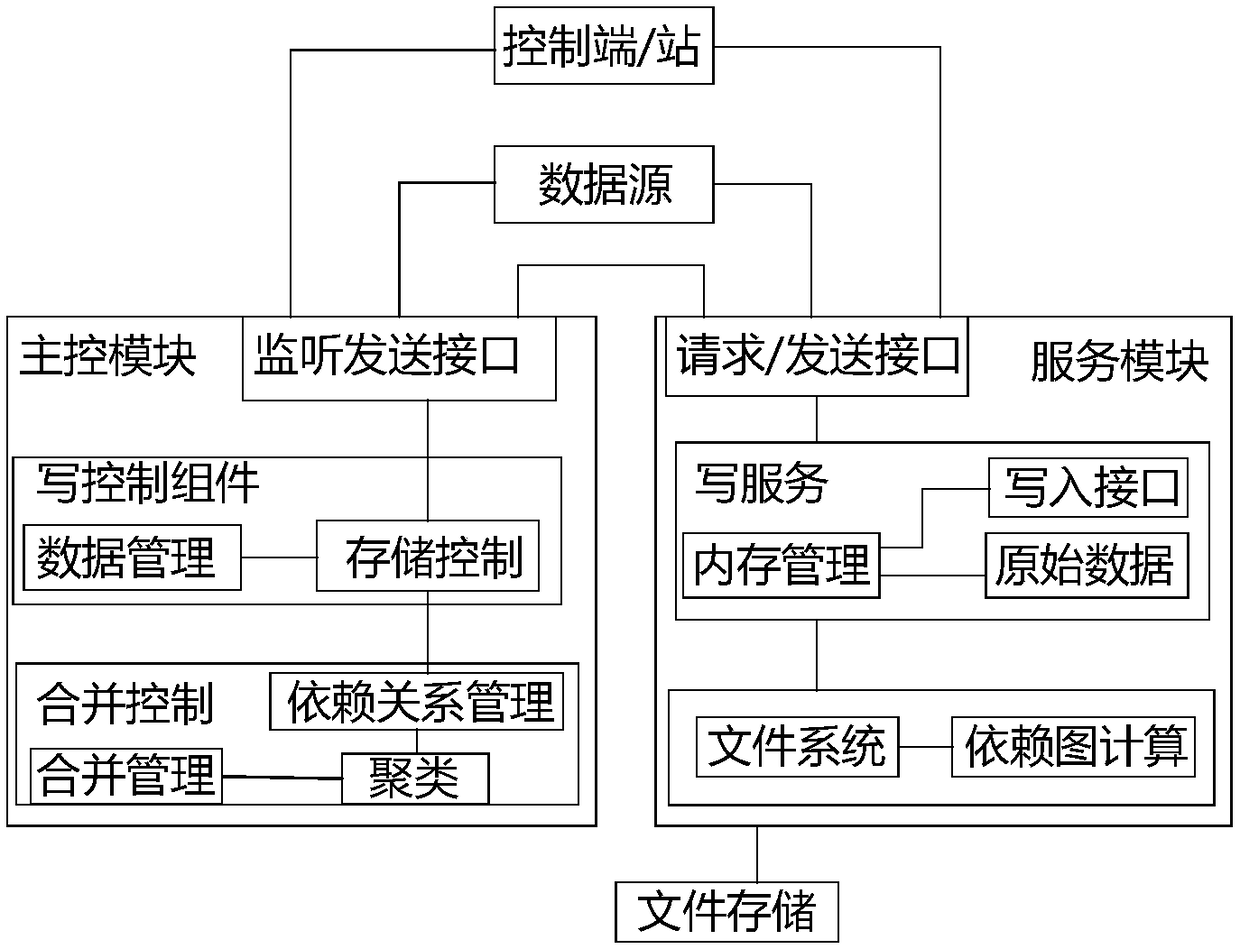
ActiveCN109508317AImprove the efficiency of transmission and storageSimplify positioning difficultyFile system administrationFile access structuresData fileStructure of Management Information
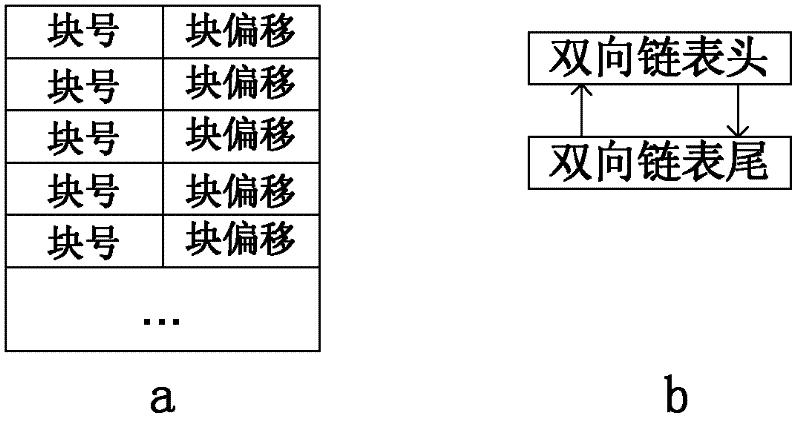
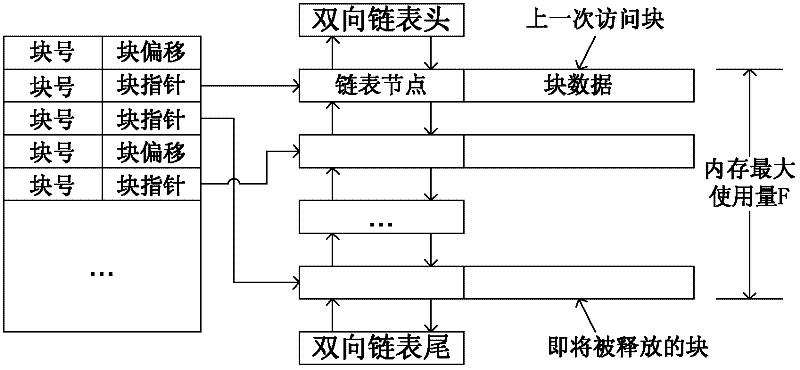
The invention belongs to the technical field of data management service, in particular to a large-capacity data and service management system. The large-capacity data and service management device ofthe invention improves the efficiency of file data transmission and storage, Increases resource consumption for data operations such as queries, can significantly reduce the number of nodes in the data file, improve the efficiency of the whole system operation in the large-capacity data system, the burden of system file processing is decreased, the file association structure based on dependency relation simplifies the difficulty of file location and management, simplifies the location operation of dependency node in the process of file location and clustering, reduces the thread consumption offile data reading and writing, and improves the reading and writing speed.
Owner:陕西合友网络科技有限公司
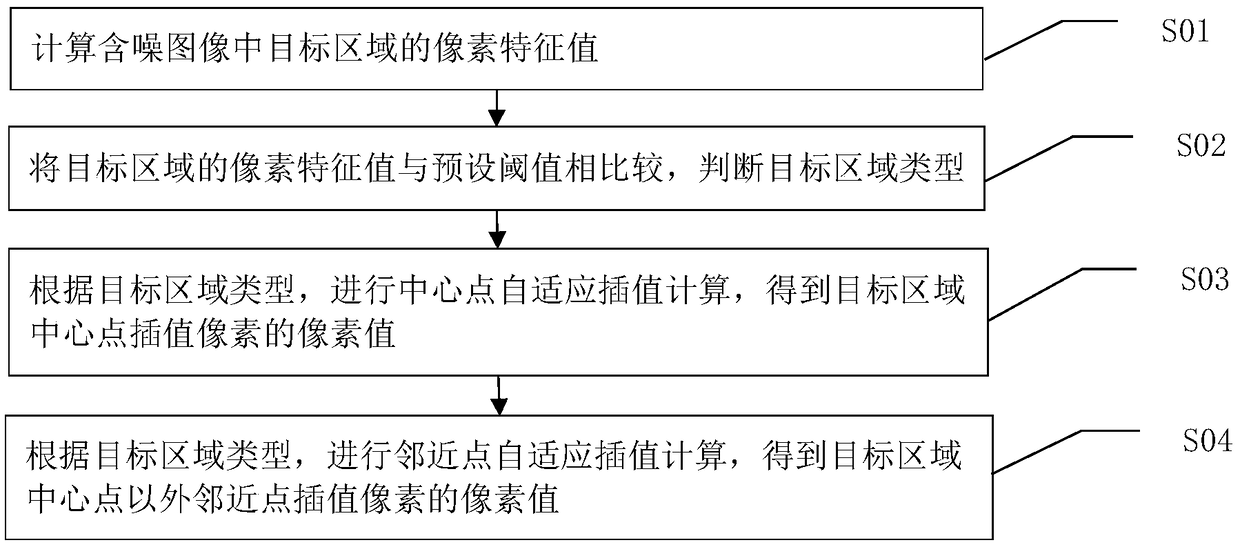
An image preprocessing method to improve the effect of wavelet denoising
ActiveCN109377463AIncrease spatial sampling rateImproving the effect of wavelet denoisingImage enhancementImage analysisWavelet denoisingAlgorithm
The invention discloses an image preprocessing method for improving the wavelet denoising effect, comprising the following steps: step S01: calculating the pixel eigenvalue of a target area in a noisyimage; Step S02: comparing the pixel eigenvalue of the target area with a preset threshold value, and judging the type of the target area; S03, according to the target area type, performing center point adaptive interpolation calculation to obtain the pixel value of the center point interpolation pixel of the target area; Step S04: According to the target area type, the adaptive interpolation calculation of the adjacent points is performed to obtain the pixel value of the adjacent point interpolation pixel outside the center point of the target area. The invention is based on a common waveletdenoising method, and obviously improves the effect of wavelet denoising without introducing a new method and increasing the complexity of the algorithm.
Owner:SHANGHAI INTEGRATED CIRCUIT RES & DEV CENT
Computer resource leak detection
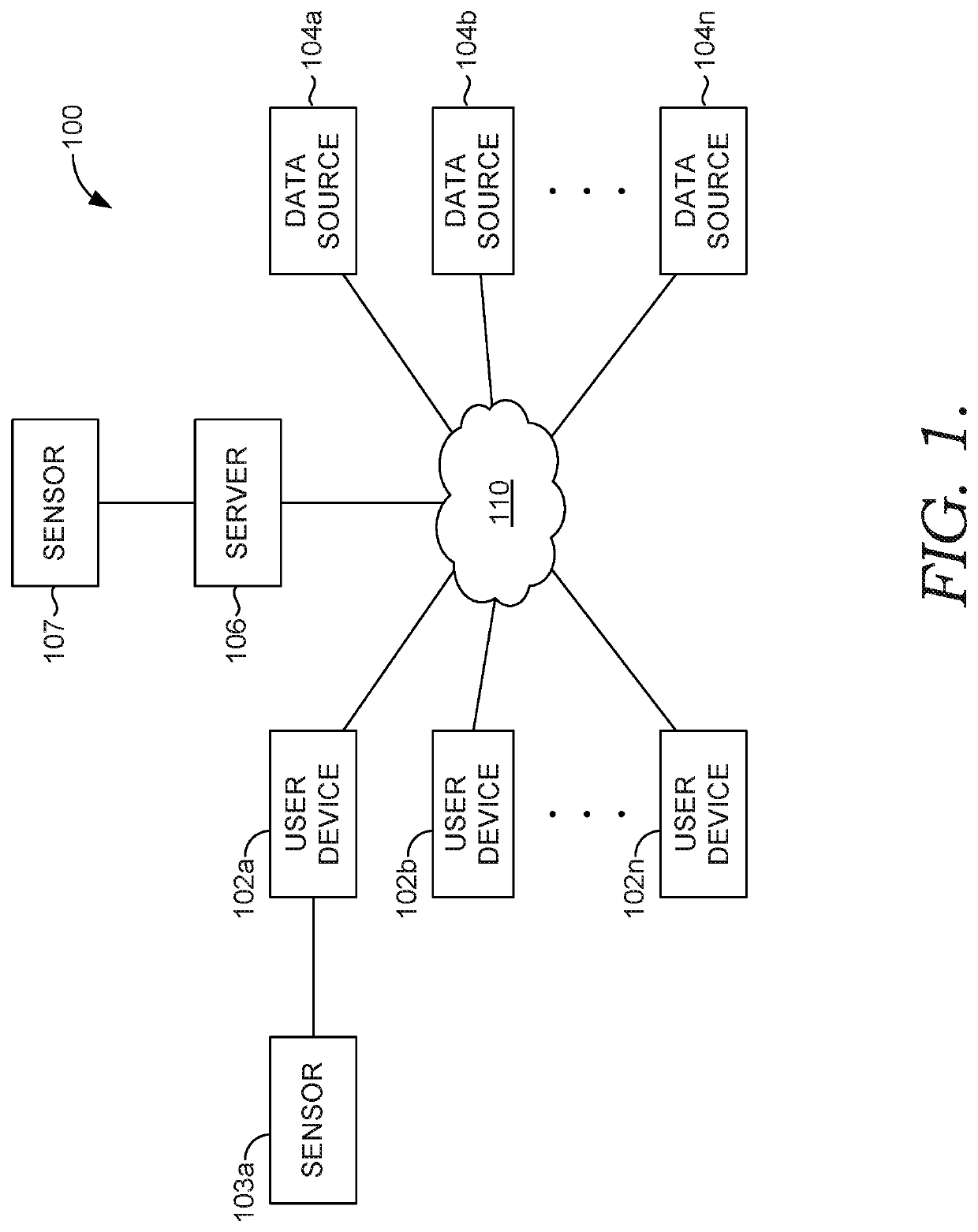
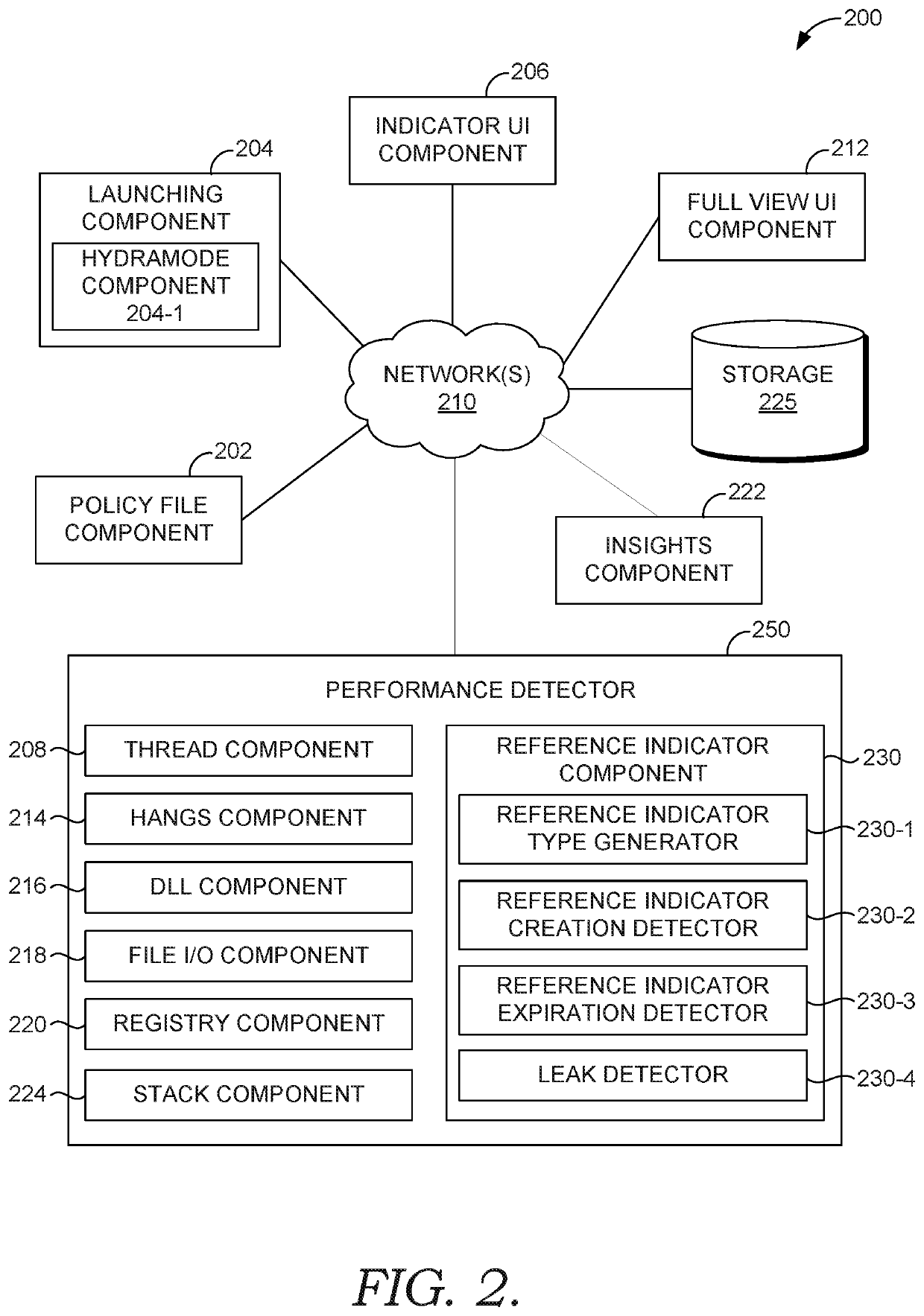
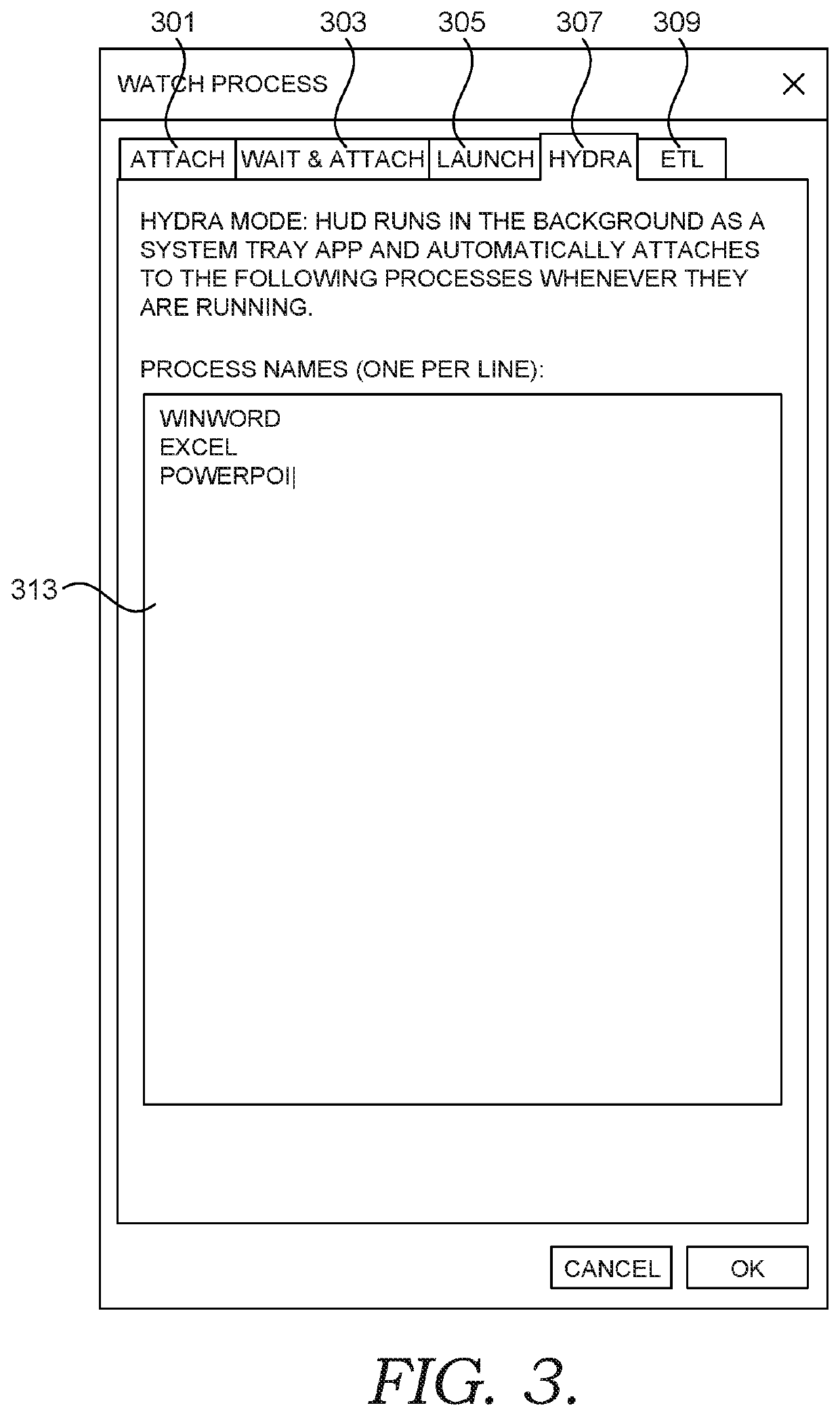
ActiveUS20210200593A1Quick fixIncrease resource consumptionMemory architecture accessing/allocationResource allocationComputer resourcesApplication procedure
Various embodiments discussed herein enable intelligent resource leak detection and associated user interface. In some aspects, if a kernel sends a tracing event (e.g., an ETW event) after a process or application has been requested to be shut down but before the process has actually been shut down, a resource leak can be detected. This is because the application should have requested the reference indicator to be removed in memory before the tracing event, as opposed to the kernel acting alone without an application request to remove the reference indicator. If a reference indicator has not been requested to be removed by the time this tracing event occurs, then it is indicative of the application never having sent a request to remove the reference indicator, which is indicative of a resource leak.
Owner:MICROSOFT TECH LICENSING LLC
A Joint Estimation Method of Frame Bit Synchronization for EBPSK Communication System
ActiveCN104506472BImprove synchronization efficiencyShorten the timePhase-modulated carrier systemsHigh level techniquesData streamCommunications system
Owner:苏州东奇信息科技股份有限公司
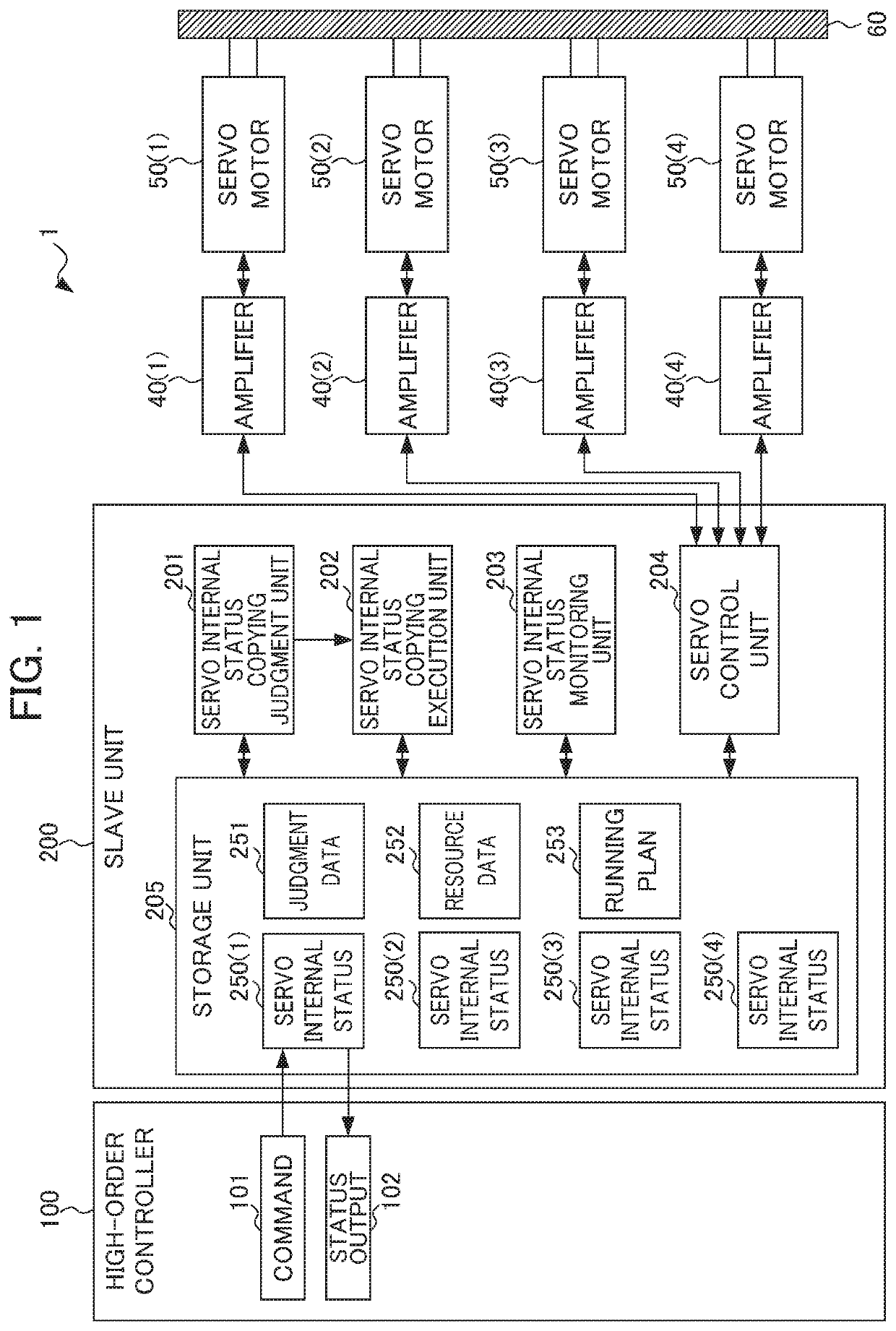
Slave unit and servo driving system
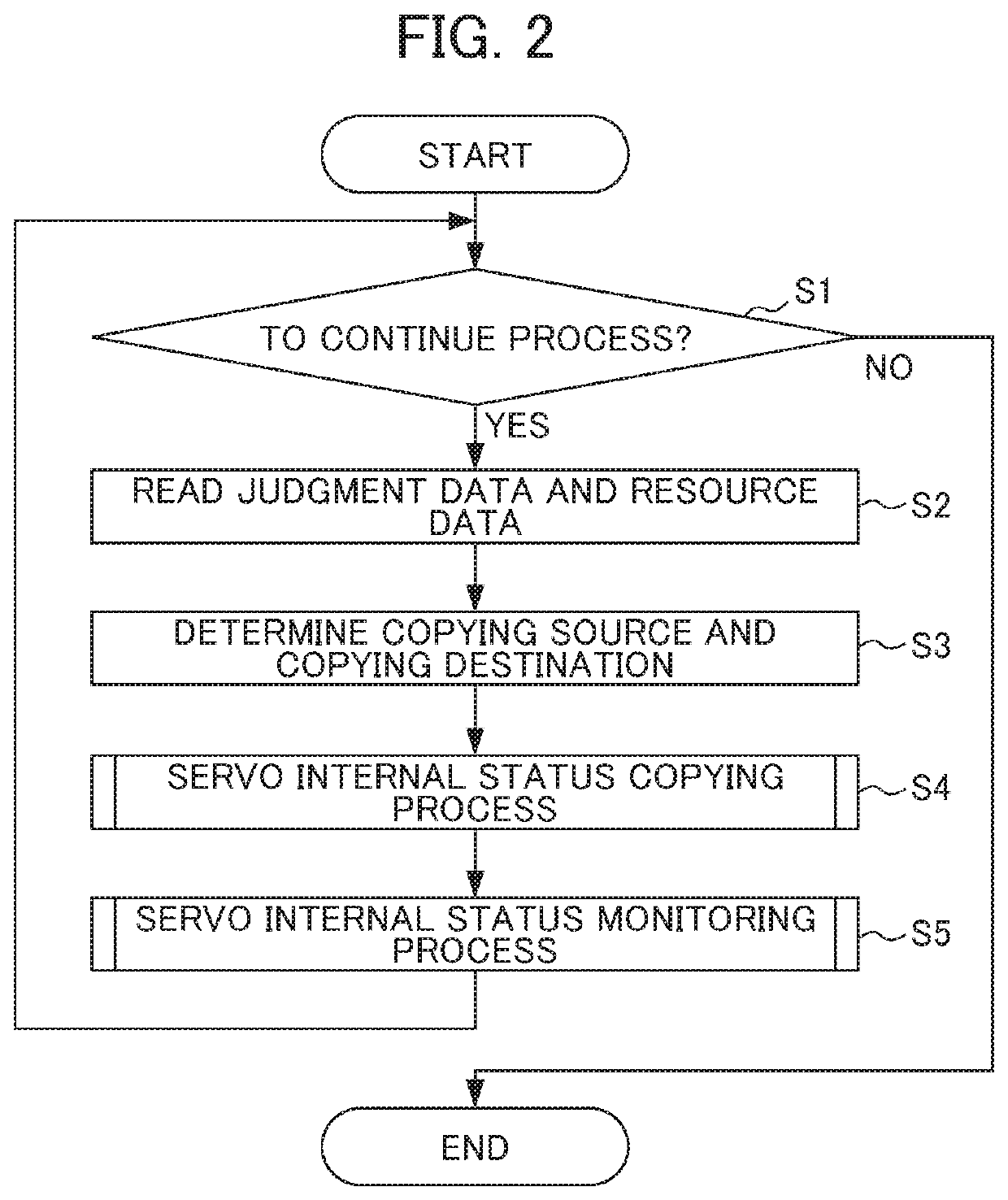
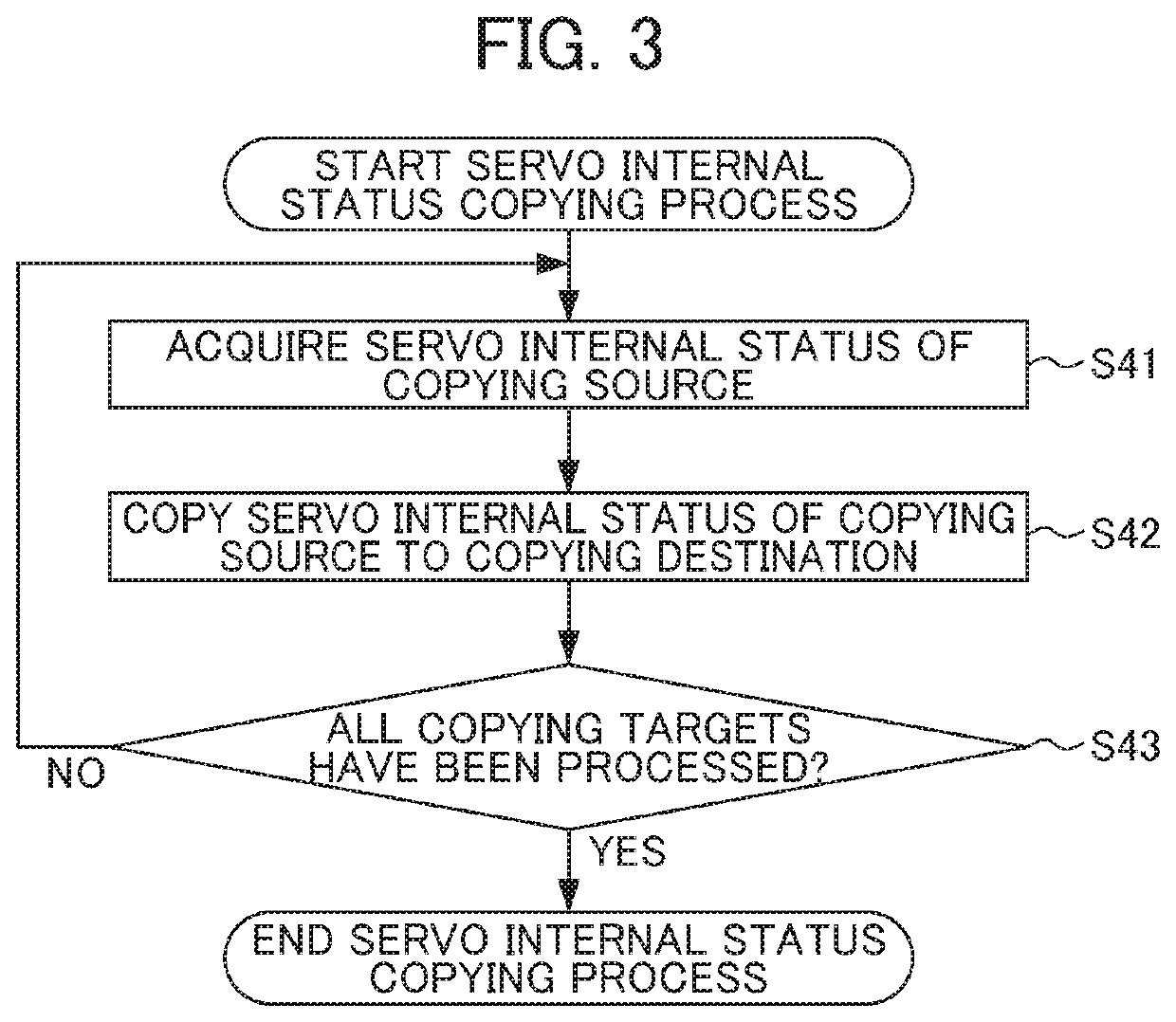
ActiveUS11283375B2Increase loadIncrease resource consumptionAC motor controlMultiple dynamo-electric motors speed regulationControl engineeringExecution unit
To avoid cost increase, delay of response, time, and performance degradation in driving a power source including a plurality of servo motors and / or a servo motor with a plurality of windings. A slave unit drives a power source including a plurality of servo motors and / or a servo motor with a plurality of windings using a plurality of amplifiers on the basis of a command from a high-order controller. The slave unit includes: a storage unit stores servo internal statuses of the respective servo motors and / or the respective windings, judgment data, and resource data; a servo internal status copying judgment unit determines a copying source and a copying destination, and judges whether to copy a servo internal status of the copying source to the copying destination to commonalize therebetween on the basis of the judgment data and the resource data; a servo internal status copying execution unit copies the servo internal status of the copying source to the copying destination; and a servo control unit outputs each of the plurality of servo internal statuses to the respective amplifiers to control driving of the power source.
Owner:FANUC LTD
Implementation method for networked system structure of numerical control system
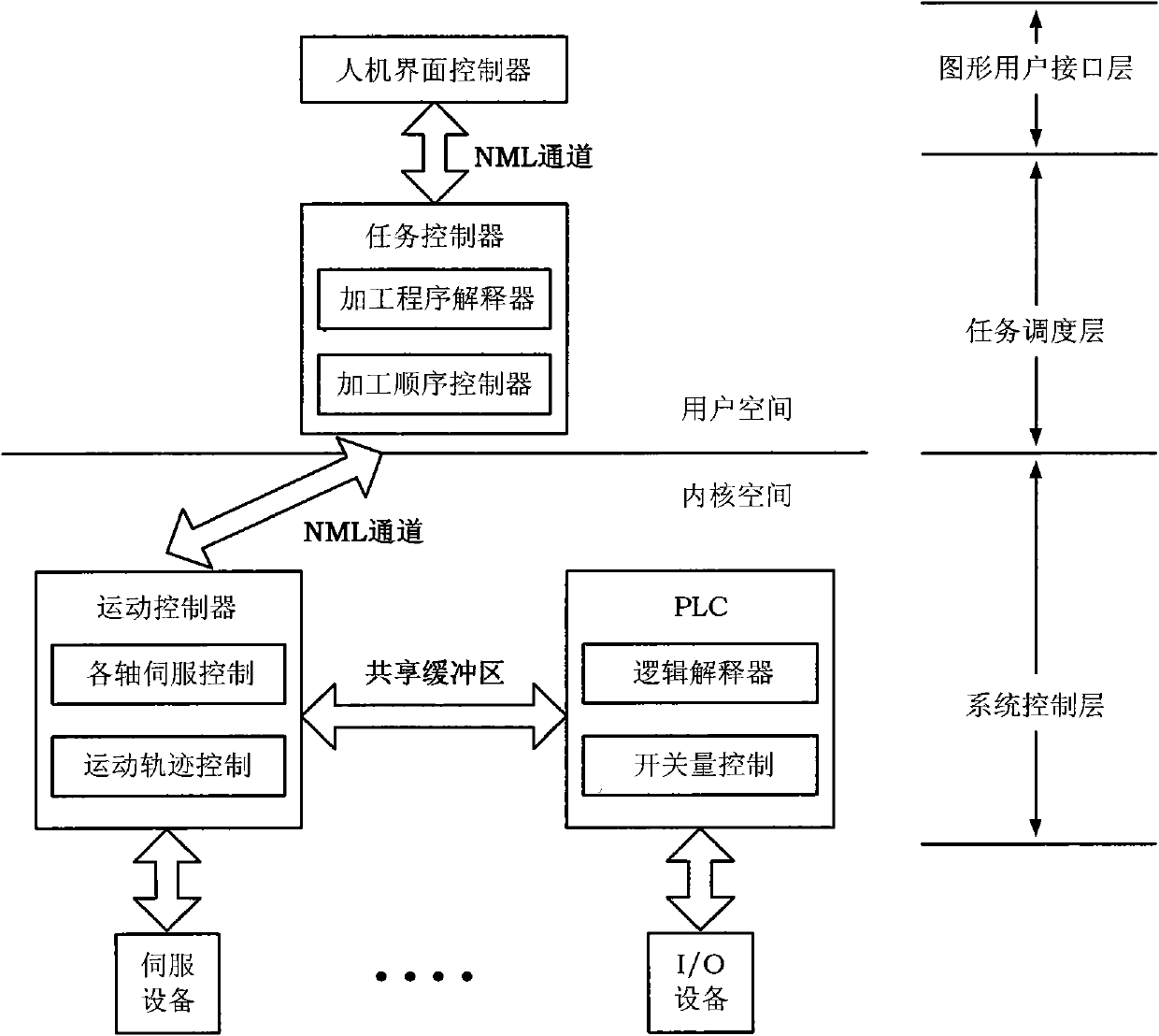
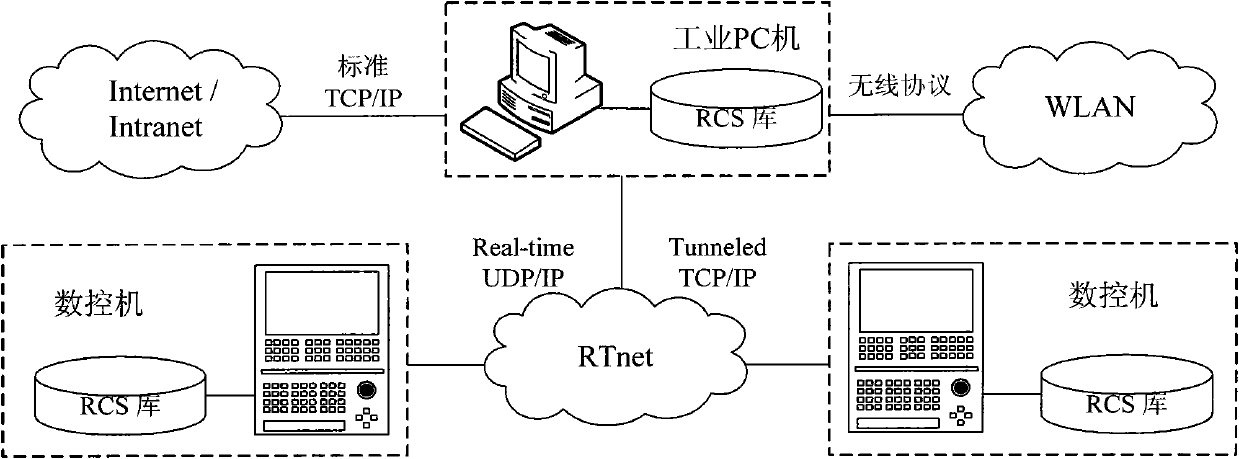
ActiveCN102253657BRelieve stressImprove controlTotal factory controlProgramme total factory controlHuman–machine interfaceNetworked system
The invention discloses an implementation method for a networked system structure of a numerical control system. The implementation method comprises the following steps of: separating a human-computer interface controller from a numerical control machine to run in an industrial personal computer (PC), and making a task controller, a motion controller and a programmable logical controller (PLC) run in the numerical control machine; implementing real time data processing of the human-computer interface controller through a soft real-time mechanism on the industrial PC; implementing real time data processing of a server and the task controller through a soft real-time mechanism on the numerical control machine, and communicating the task controller with the motion controller by using a mixedinteractive model; and connecting the industrial PC with the numerical control machine through a real-time Ethernet. By using the implementation method, the pressure of a processor can be relieved, the control performance of the numerical control system is improved, the real-time property of data transmission among cross-platform modules is ensured, and a speed of data processing of a user task, the data interactive performance among local modules and the stability of the system are improved.
Owner:SHENYANG GOLDING NC & INTELLIGENCE TECH CO LTD
Teacher personal homepage static resource generation method based on watermark feature rule string
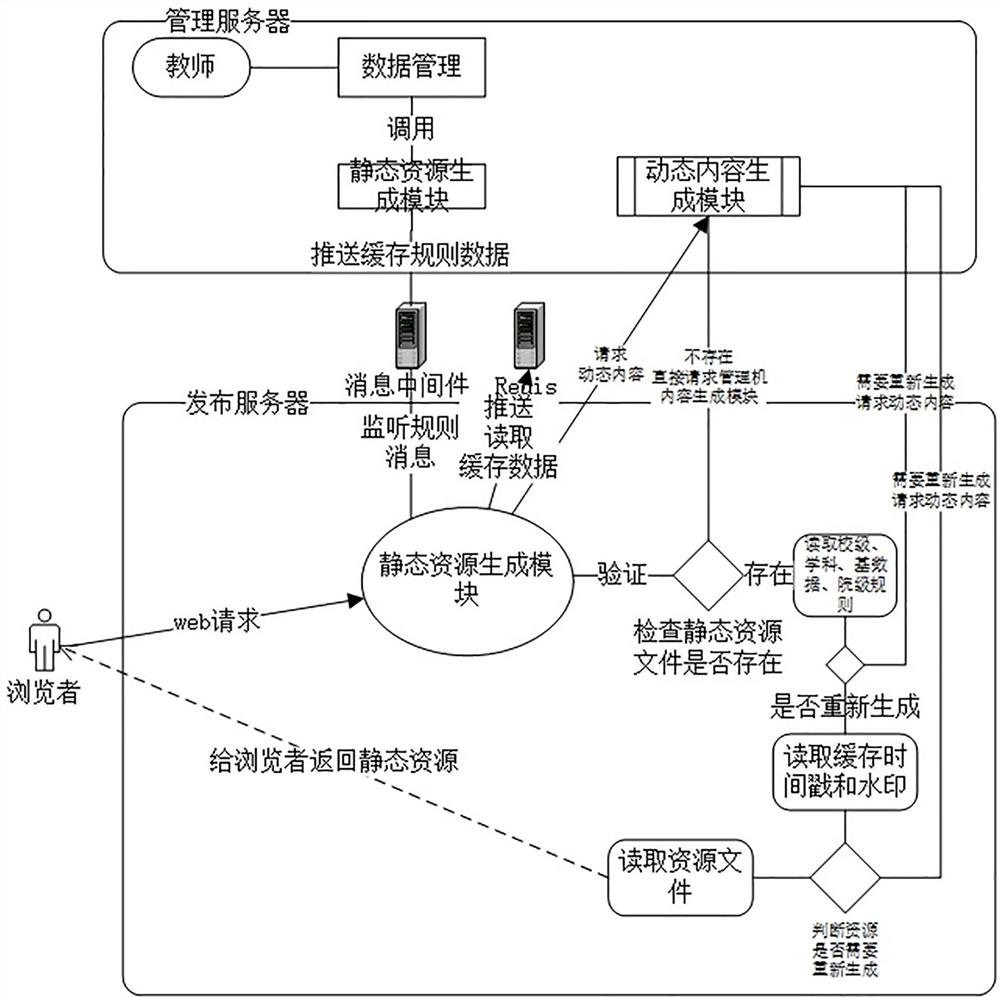
ActiveCN112632440AReduce build pressureCan't solve itDigital data protectionWebsite content managementApplication serverEngineering
The invention discloses a teacher personal homepage static resource generation method based on a watermark feature rule string. The method comprises the following steps: S1, content publishing: when a teacher manages and publishes personal information, an application server does not perform real static resource generation operation and only calculates rule information required to be subjected to static resource generation, pushing the rule information to a message system by calling message middleware; s2, static resource generation: a WEB server monitors a message system and caches rule information generated by a management machine into local redis; and S3, static resource recovery: through a built-in static resource tamper-proof function, the WEB server calls a tamper-proof module to perform static resource tamper-proof judgment when receiving the browsing request, and directly returns static resources to the browser if the static resource tamper-proof function is consistent with the static resource tamper-proof function. The static resource generation efficiency and the resource consumption of the WEB server on the tamper-proof module can be greatly improved, and the server load is reduced.
Owner:西安博达软件股份有限公司
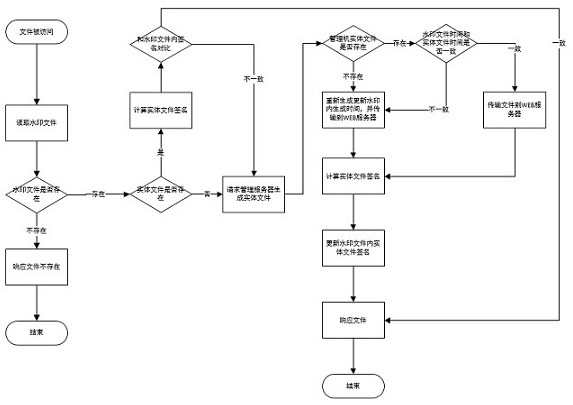
Static resource tamper-proofing method based on file watermark in CMS system
ActiveCN112632633AIncrease generation speedIncrease transfer speedDigital data protectionProgram/content distribution protectionPathPingWeb site
The invention discloses a static resource tamper-proofing method based on a file watermark in a CMS system, and the method comprises the following steps: S1, file publishing: not carrying out the real file generation operation in a webpage of a website published by a user and a resource file management server, only calculating the watermark file of a to-be-generated file, and transmitting the watermark file to a WEB server, wherein the watermark file generated by the management server only contains basic information of the entity file; s2, file checking: after a browser accesses the website request file, the WEB server reads the watermark file corresponding to the entity file from the watermark file directory according to the path of the requested entity file, when the watermark file does not exist, the file is directly responded to not exist, and when the watermark file exists, whether the entity file exists or not is checked; and S3, file recovery: for the tampered file, the WEB server requests the management server to obtain a correct file. According to the invention, the publishing efficiency of the file and the resource consumption of the WEB server on the tamper-proof module can be improved, and the load of the server is reduced.
Owner:西安博达软件股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com