Method for realizing elliptic curve cryptosystem algorithm over prime field in integrated circuit
A technology of elliptic curve cryptography and integrated circuits, which is applied to calculations using non-numerical representations, calculations using residual algorithms, and public keys for secure communications. Poor and other problems, to achieve the effect of reducing computing overhead, reducing area, and not affecting performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] Embodiments of the present invention will be described in further detail below in conjunction with the accompanying drawings, but the present embodiments are not intended to limit the present invention, and all similar structures, methods and similar changes of the present invention should be included in the protection scope of the present invention.
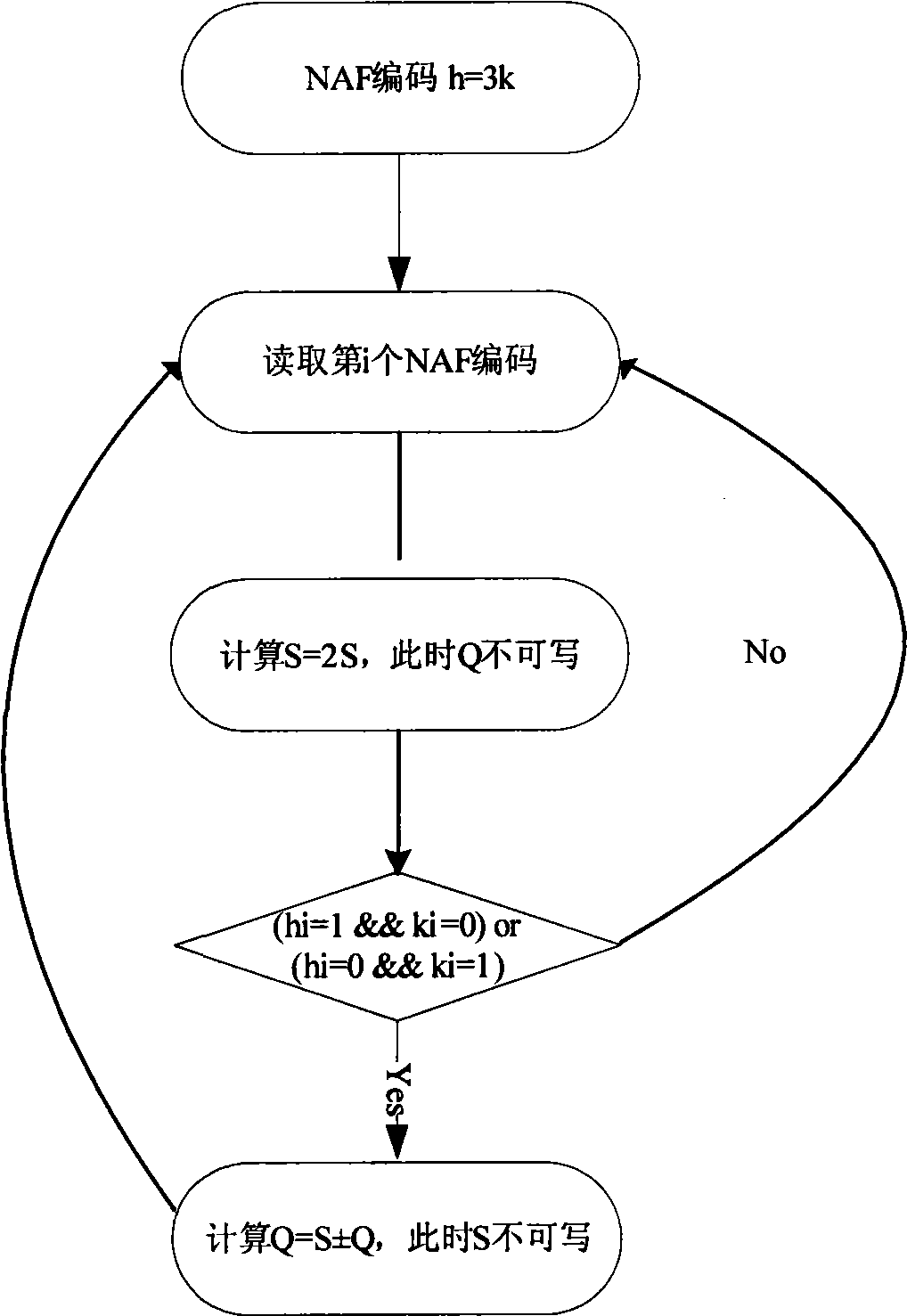
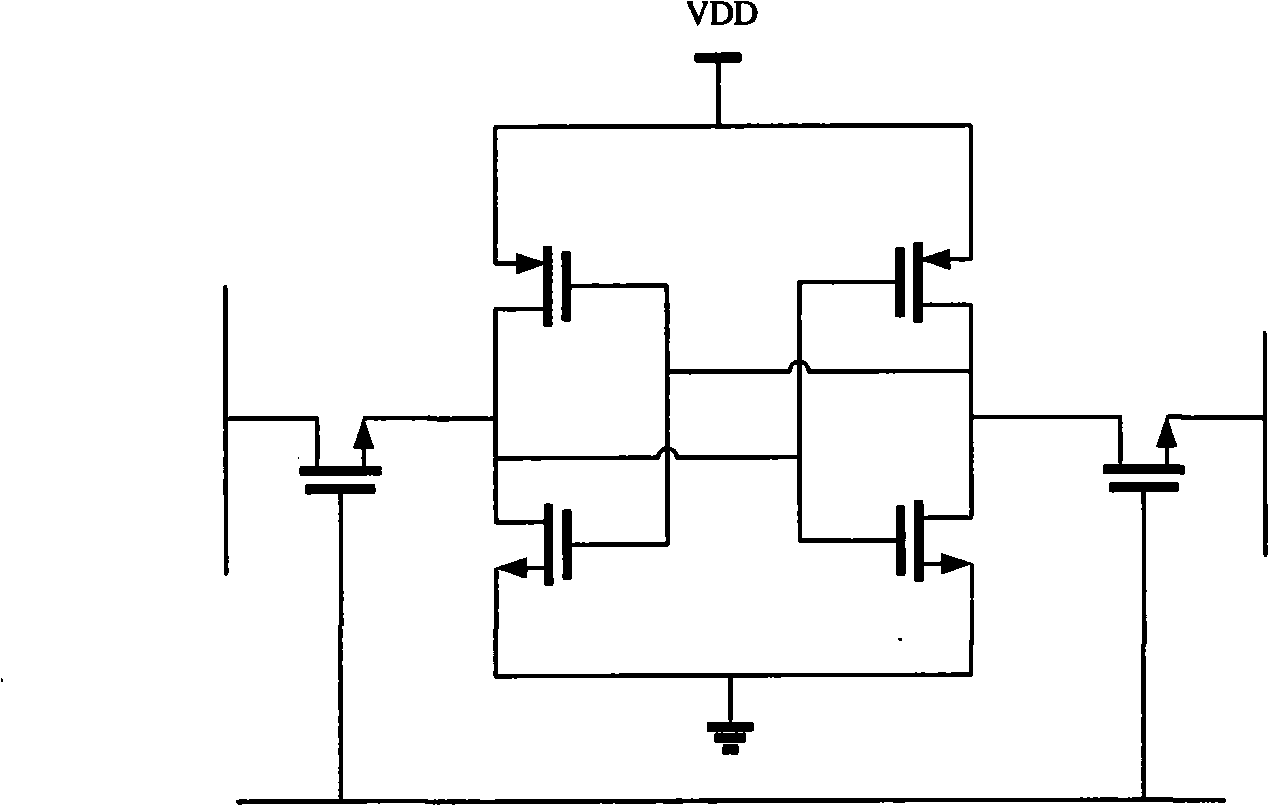
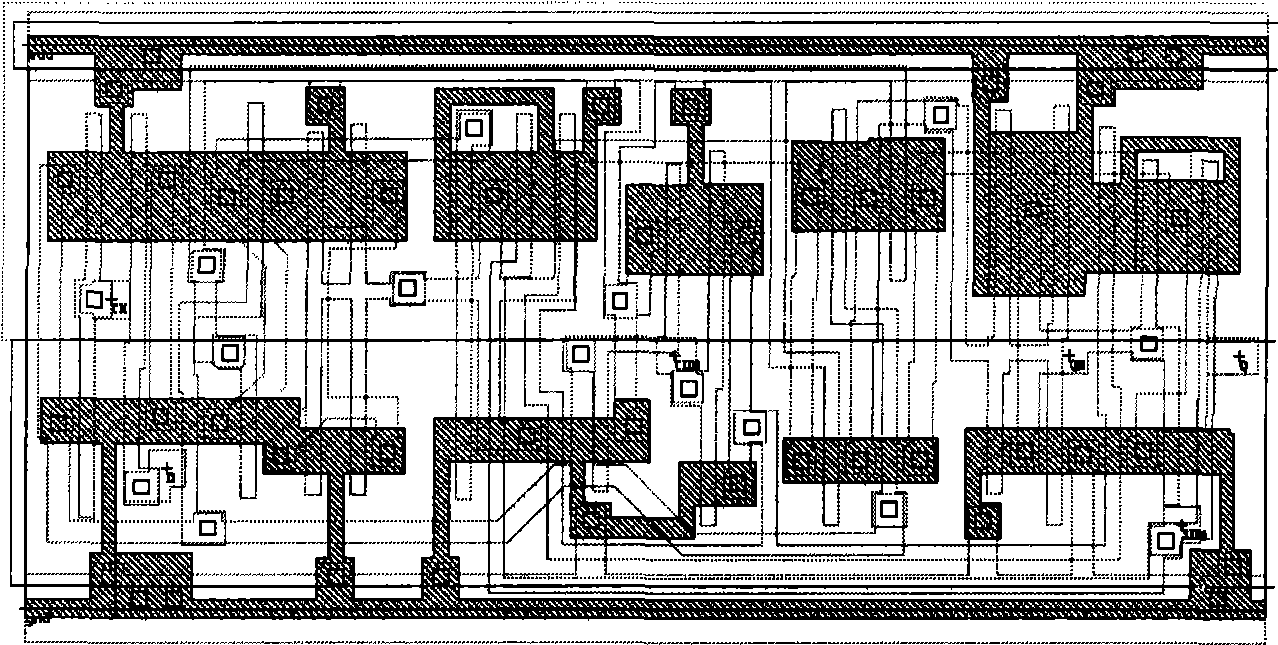
[0047]The ECC implementation of the present invention is an ECC dedicated coprocessor (IP core) designed based on various applications of the prime number finite field public key algorithm, which can support up to 544bit arbitrary elliptic curve point addition, point subtraction, doubling and point multiplication operations , the elliptic curve equation:
[0048] the y 2 =x 3 +ax+b (4a 3 +27b 2 ≠0) a, b ∈ GF(p)
[0049] In addition to supporting point operations on elliptic curves, the IP also supports finite-field operations such as RSA, modular multiplication, modular addition and subtraction, and modular inversion ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com