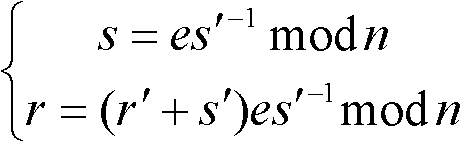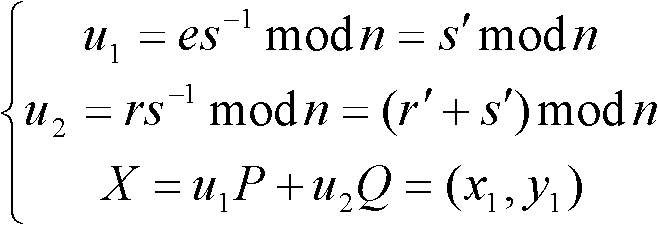SM2 signature authentication method and system
An authentication method and authentication system technology, which is applied in the field of digital signature and authentication, can solve the problem that ASIC chips cannot directly implement the SM2 algorithm, and achieve the effect of reducing the development cycle
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
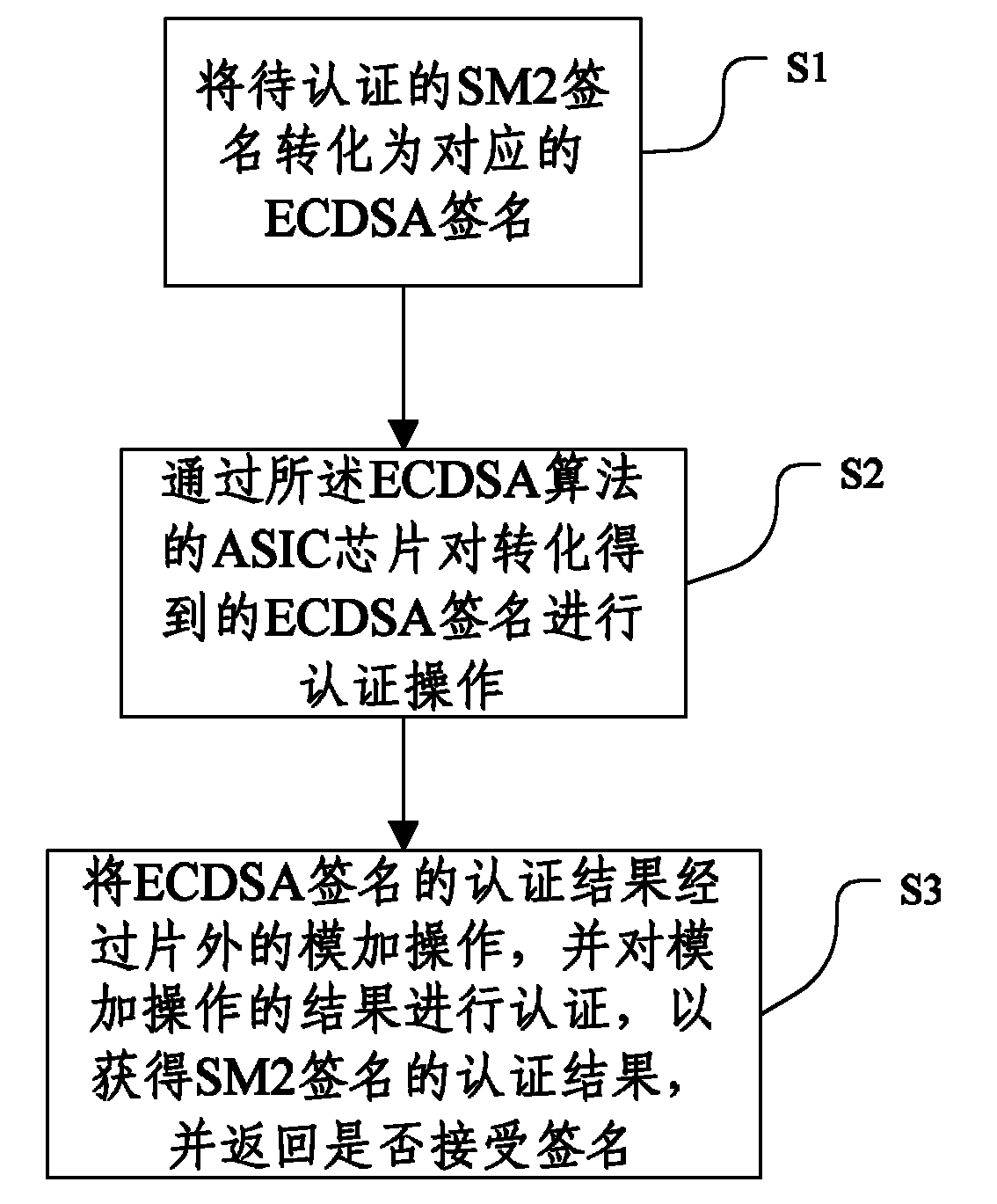
[0041] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
[0042] The notable feature of the present invention is that the existing application specific integrated circuit (Application Specific Integrated Circuit, ASIC) chip for realizing ECDSA signature authentication is used to realize the SM2 signature authentication operation, without specially designing the chip for SM2 signature authentication, which reduces the development cycle, It can also avoid performing elliptic curve point multiplication and point addition operations outside the chip, which reduces the overhead of the off-chip system and ensures that the performance of the system depends on the performance of the ASIC chip.
[0043] Another feature of the present inve...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com