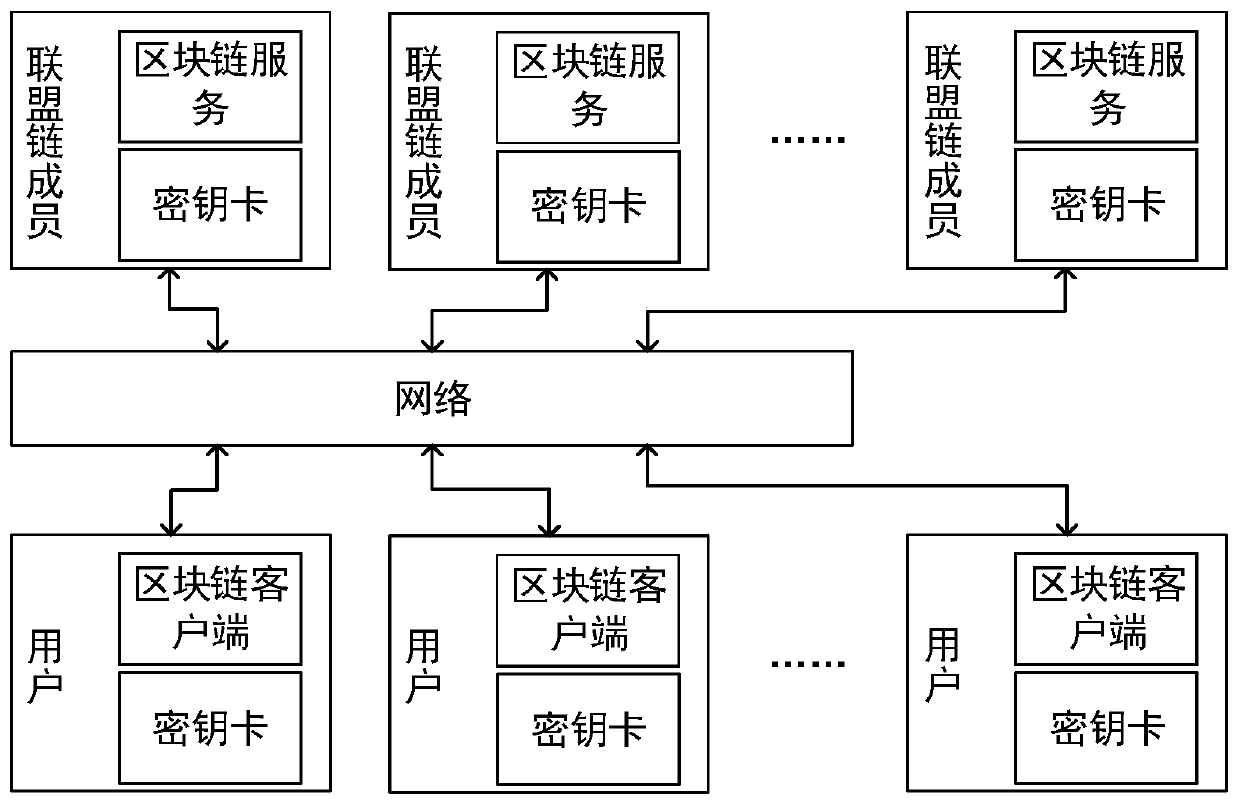
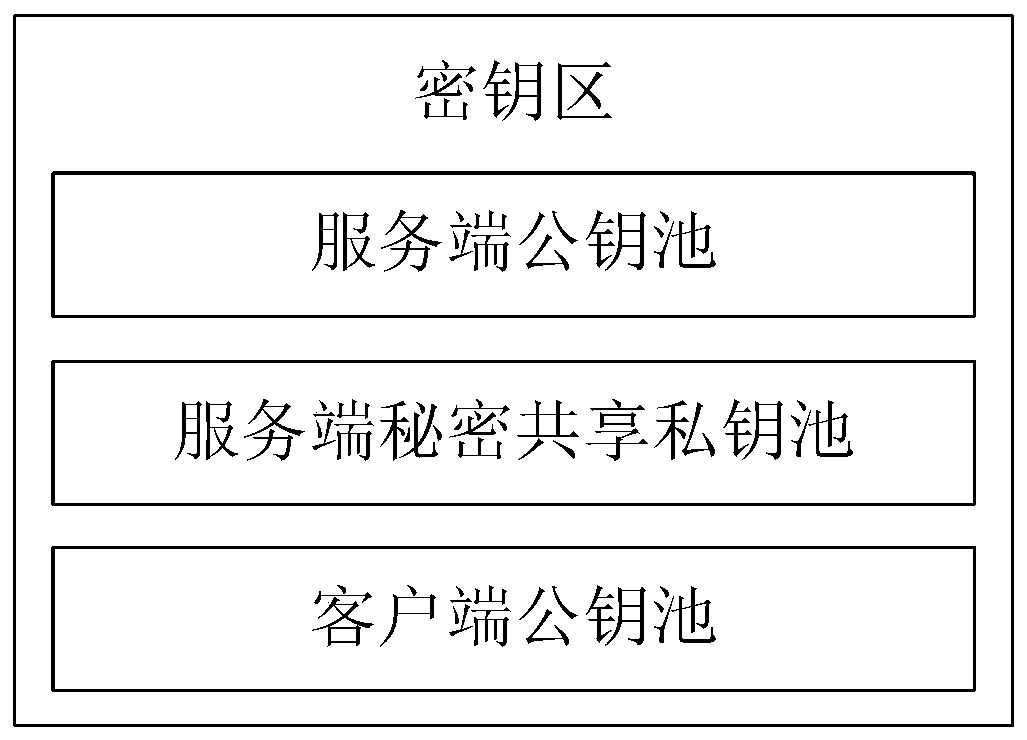
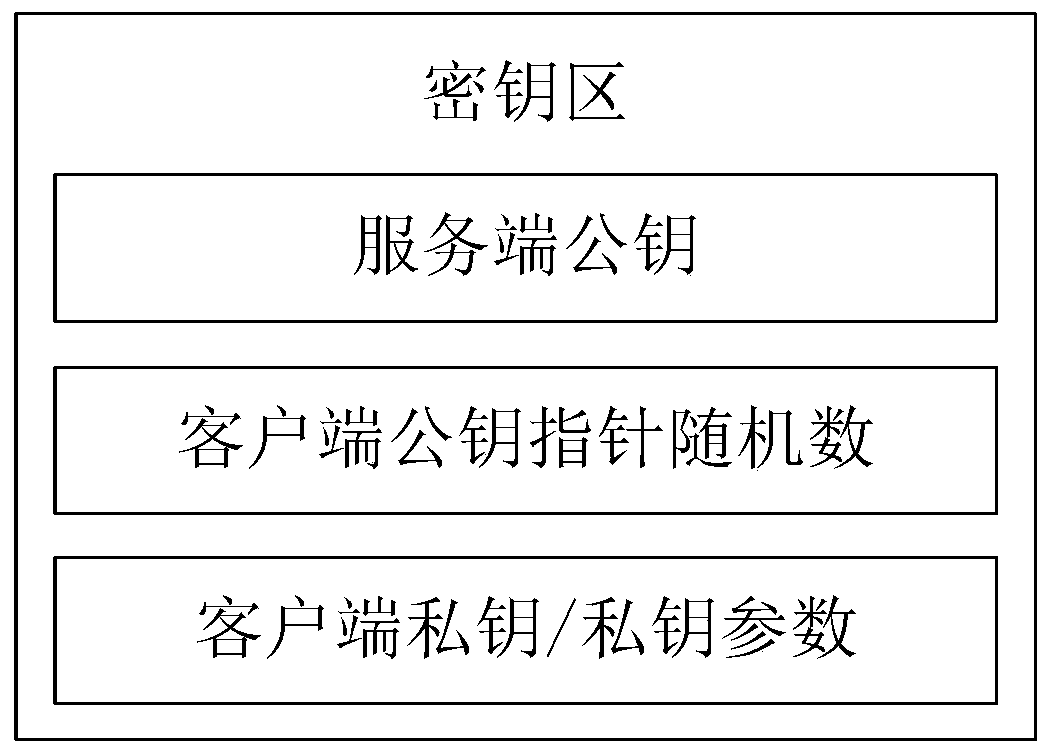
Anti-quantum computing cloud storage method and system based on alliance chain and implicit certificate
A quantum computing and implicit certificate technology, applied in the field of alliance chain, can solve the problems of anti-tampering, low anti-repudiation ability, data worries, user data decryption, etc., to avoid key leakage, improve security, and improve security sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0121] Example 1: Query whether the file exists:
[0122] User queries whether file F exists.
[0123] Step 1: User proposes a transaction.
[0124] User performs Hash calculation on file F to obtain HF.
[0125] User sends a transaction to N Endorsers, and the transaction tx can be expressed as {proposal, userSig'}.
[0126] The proposal can be expressed as {IDU, chaincodeID, txPayload, timestamp}. The chaincode chaincodeID is the number of the smart contract function; txPayload is the parameter of the function, which can be expressed as txPayload=HF. timestamp is the initiation time of the transaction.
[0127] userSig is the User's signature on the proposal. Set SIGN=ECDSA to get userSig=SIGN(proposal, SKU)={UR, US}.
[0128] User extracts the server public key pkU and pkSU from the key card, and calculates PKUR for offset calculation, which can be expressed as PKUR=H(IDU||HF||timestamp||pkU||pkSU). H(*) is a hash function that maps integers to points on an elliptic ...
Embodiment 2
[0143] Embodiment 2: The first user uploads a file:
[0144] Step 1: User1 proposes a transaction.
[0145] Suppose the first uploader of a file F is User1, the public and private key of User1 is PKU1 / SKU1, and the server public key stored in the key card is pkU1 / pkSU1.
[0146] After User1 finds that the file F does not exist through the query in Embodiment 1, he sends a transaction to N Endorsers, and the transaction tx can be expressed as {proposal, userSig'}.
[0147] User1 generates a random number KF as a file key.
[0148] User1 generates a file characteristic value according to the file, and uses the file characteristic value to encrypt the file key KF to obtain the data key DKF. The calculation method of the file feature value is a predefined algorithm, which can be but not limited to Hash calculation, file compression or other file feature calculation algorithms.
[0149] User1 generates a personal key PKF1. The process is as follows:
[0150] (1) User1 uses the...
Embodiment 3
[0184] Embodiment 3: The second user uploads a file:
[0185] Step 1: User2 proposes a transaction.
[0186] Let User2 be the non-first uploader of a certain file F, let User2’s public and private key be PKU2 / SKU2, and the server’s public key stored in the key card be pkU2 / pkSU2.
[0187] After User2 discovers the existence of the file F through the query in Embodiment 1, it generates a file characteristic value according to the file, and uses the file characteristic value to decrypt the data key DKF to obtain the file key KF. Then make the personal key PKF2 according to the file key KF, the specific steps are as follows:
[0188] (1) User2 uses the personal public key PKU2 and the ECIES algorithm to encrypt the file key KF to obtain ENC(KF, PKU2) = (KFR2, KFc2, KFt2).
[0189] (2) User2 extracts the server public keys pkU2 and pkSU2 from the key card, and calculates PKKFR2 for offset calculation, which can be expressed as PKKFR2=H(HF||pkU2||pkSU2).
[0190] (3) Calculate t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com