Light-weight authentication key negotiation method based on implicit certificate
An authentication key negotiation and lightweight authentication technology, which is applied to the public key and key distribution of secure communication, can solve the problems of slow calculation speed and reduced algorithm operation efficiency, and achieve the effect of low collision rate and high calculation speed.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] A non-limiting embodiment is given below in conjunction with the accompanying drawings to further illustrate the present invention.
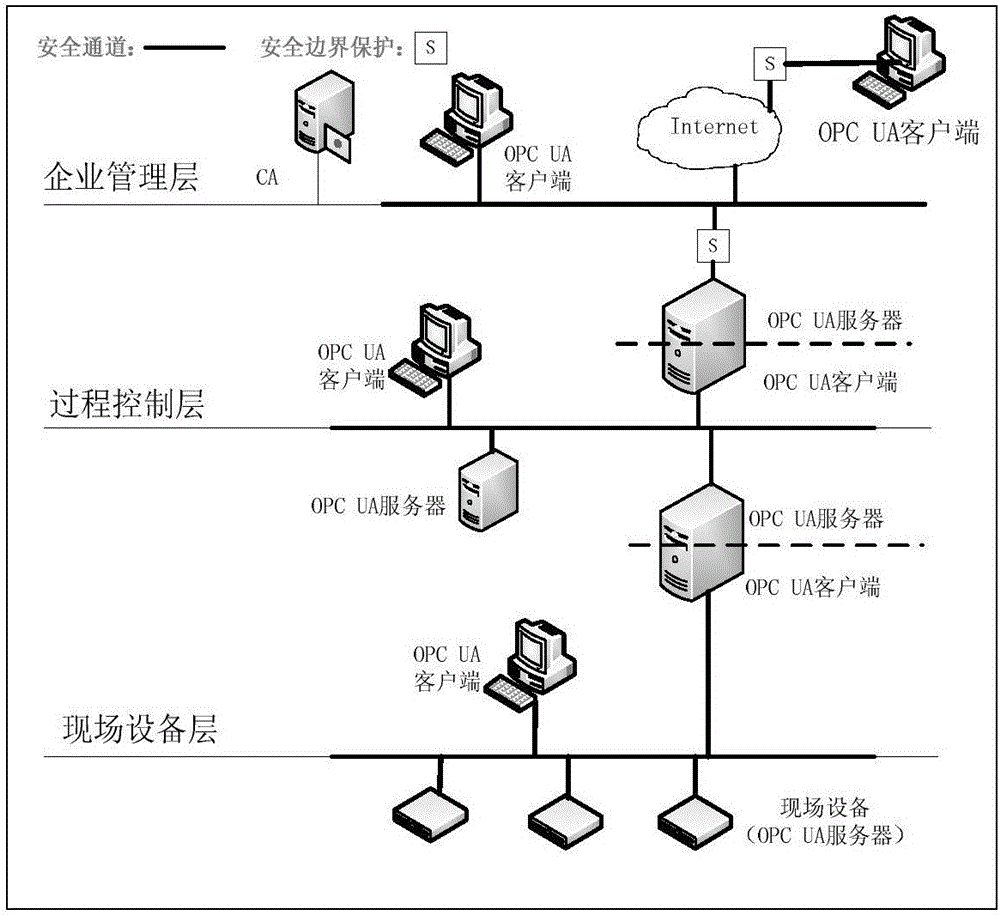
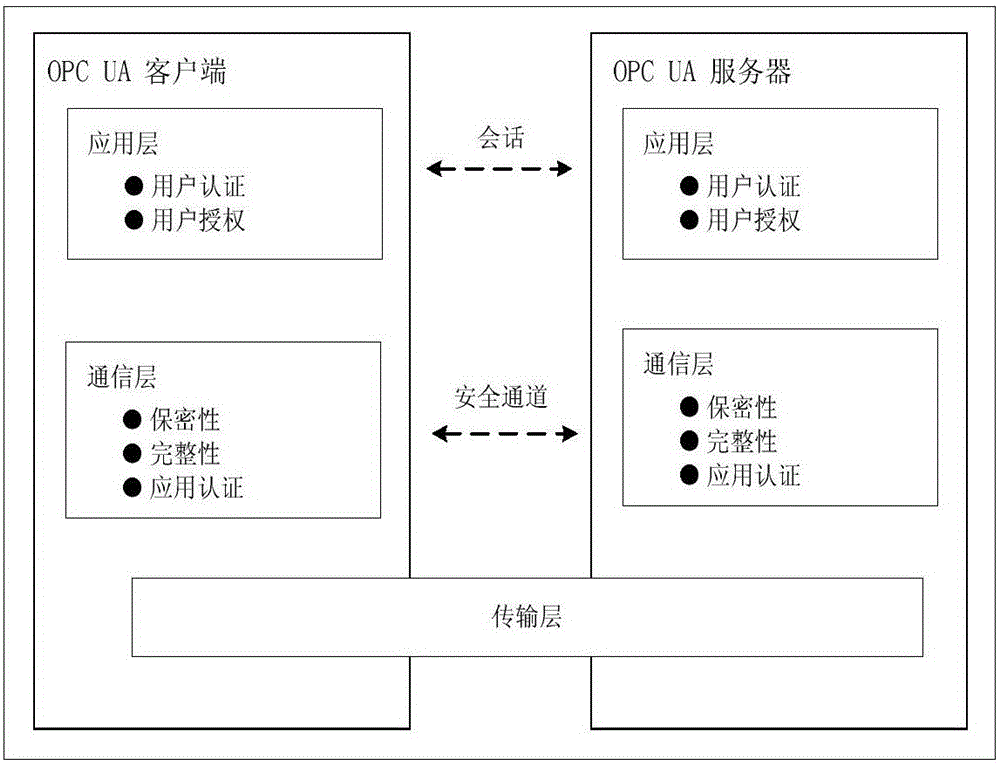
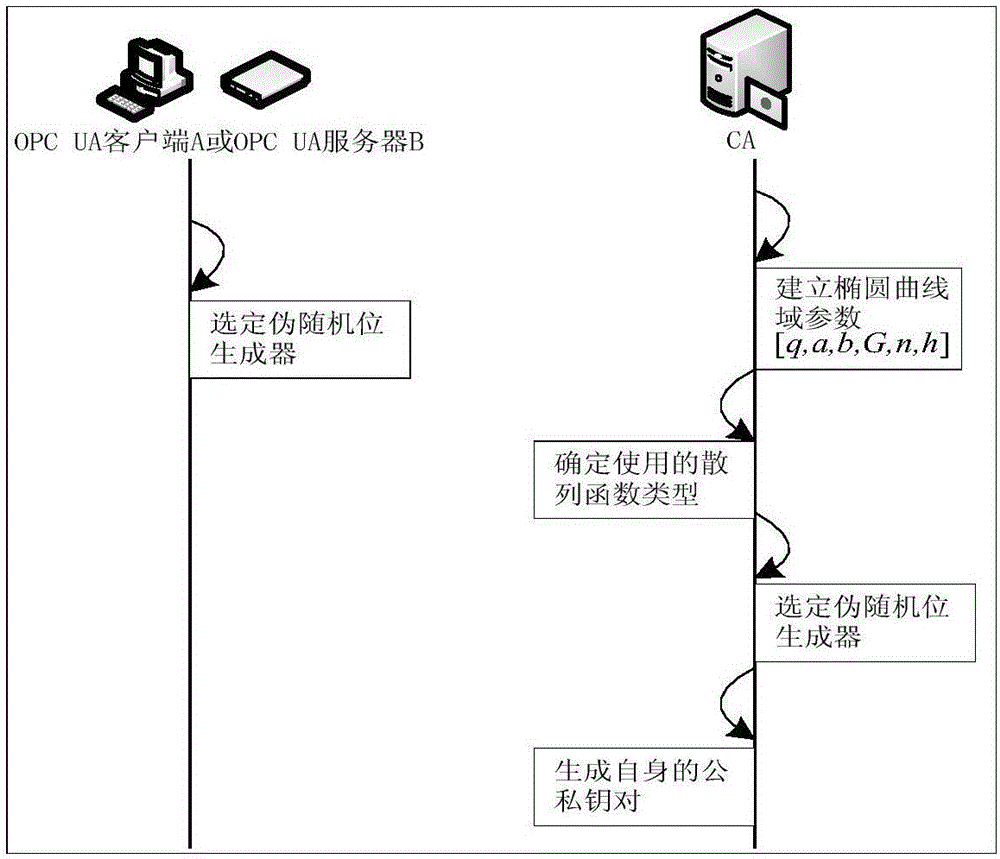
[0045] The invention relates to a light-weight authentication key agreement method based on an implicit certificate, which is used for establishing a secure channel and generating a session key between an OPC UA server and an OPC UA client. figure 1 For the OPC UA communication network architecture model, such as figure 1 As shown, the model consists of three parts: enterprise management layer, process control layer and field device layer. The information interaction of enterprise management is generally carried out through the Internet, and its functions include data management, customer management, generation scheduling, etc. The process control layer needs to have the ability to maintain two-way communication with the enterprise management layer and the field device layer, receive the production plan from the enterprise management lay...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com