Negotiation system and negotiation method based on quantum truly random number negotiation secret key
A key negotiation and true random number technology, applied in key distribution, can solve the problems of wireless application and WAN remote link key distribution, storage capacity limitation of key groups, and key cracking, etc. Channel eavesdropping attack channel, high security, the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
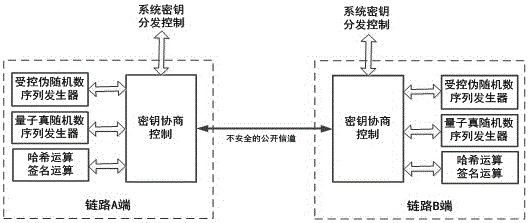
[0030] Such as figure 1 As shown, a key agreement system based on quantum true random number agreement, each end of the link includes a controlled pseudo-random number sequence generator and a quantum true random number sequence generator respectively connected to the key agreement control module and a hash operation module; the quantum true random number sequence generator produces a quantum true random number sequence code stream, and provides a true random number data block for the key agreement process; the controlled pseudo-random number sequence generator generates a pseudo-random number The sequence code stream provides the required pseudo-random number sequence data blocks for the key agreement process; the key agreement control module implements the key agreement protocol, that is, the negotiation process of the shared key at both ends of the link.
specific Embodiment 2
[0032] On the basis of the specific embodiment 1, a digital signature computing module is also included to provide digital signature computing functions.
specific Embodiment 3
[0034] On the basis of specific embodiment 1 or 2, the quantum true random number sequence generator is a true random number sequence generator based on optical quantum noise, and generates a quantum true random number sequence code stream based on the true random characteristic of optical quantum noise.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com