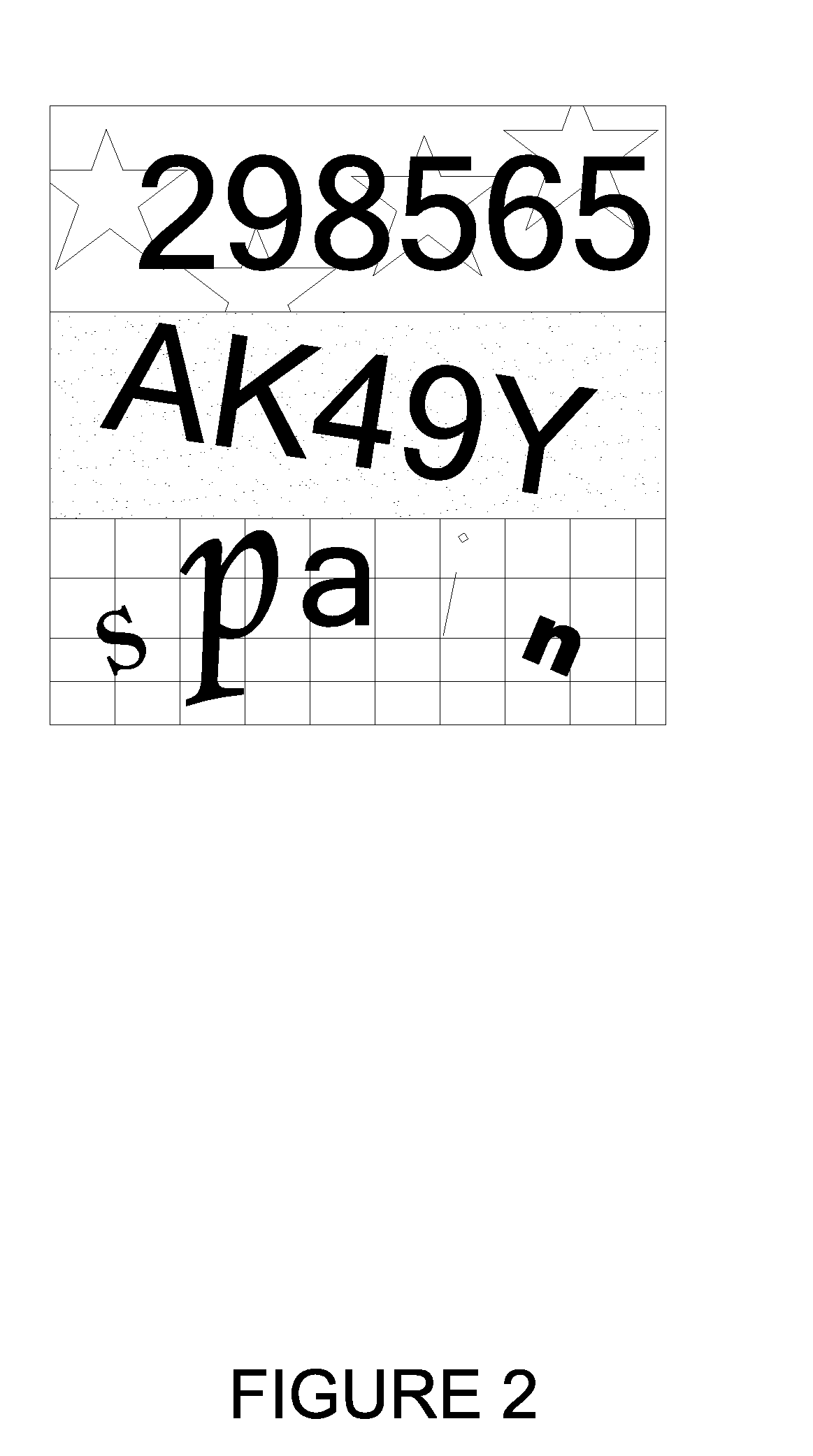Patents
Literature
1706results about "Digital function generators" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Location virtualization in an RFID system
ActiveUS20060170565A1Improve reliabilityRandom number generatorsFrequency-division multiplex detailsVirtualizationRadio frequency
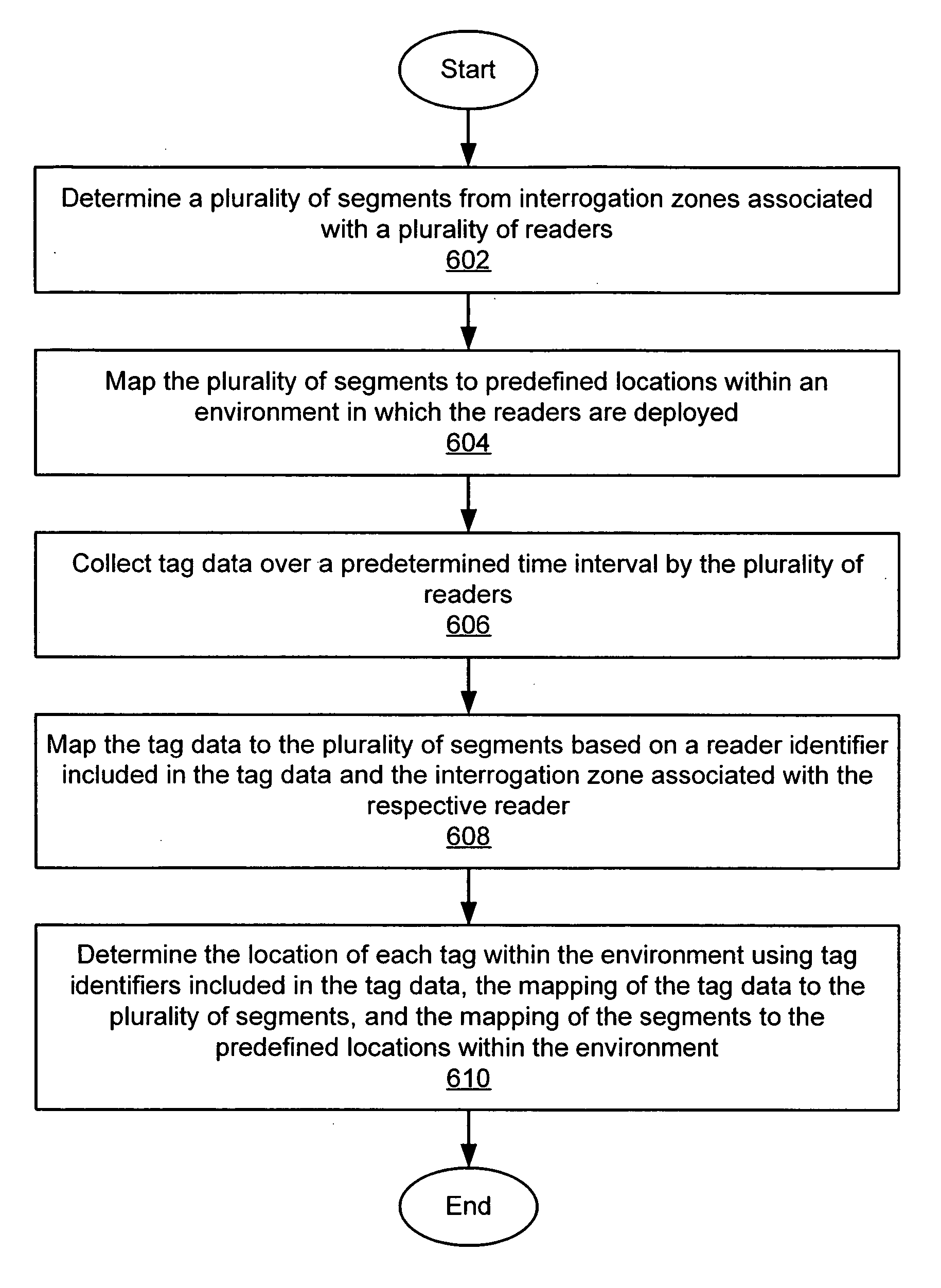
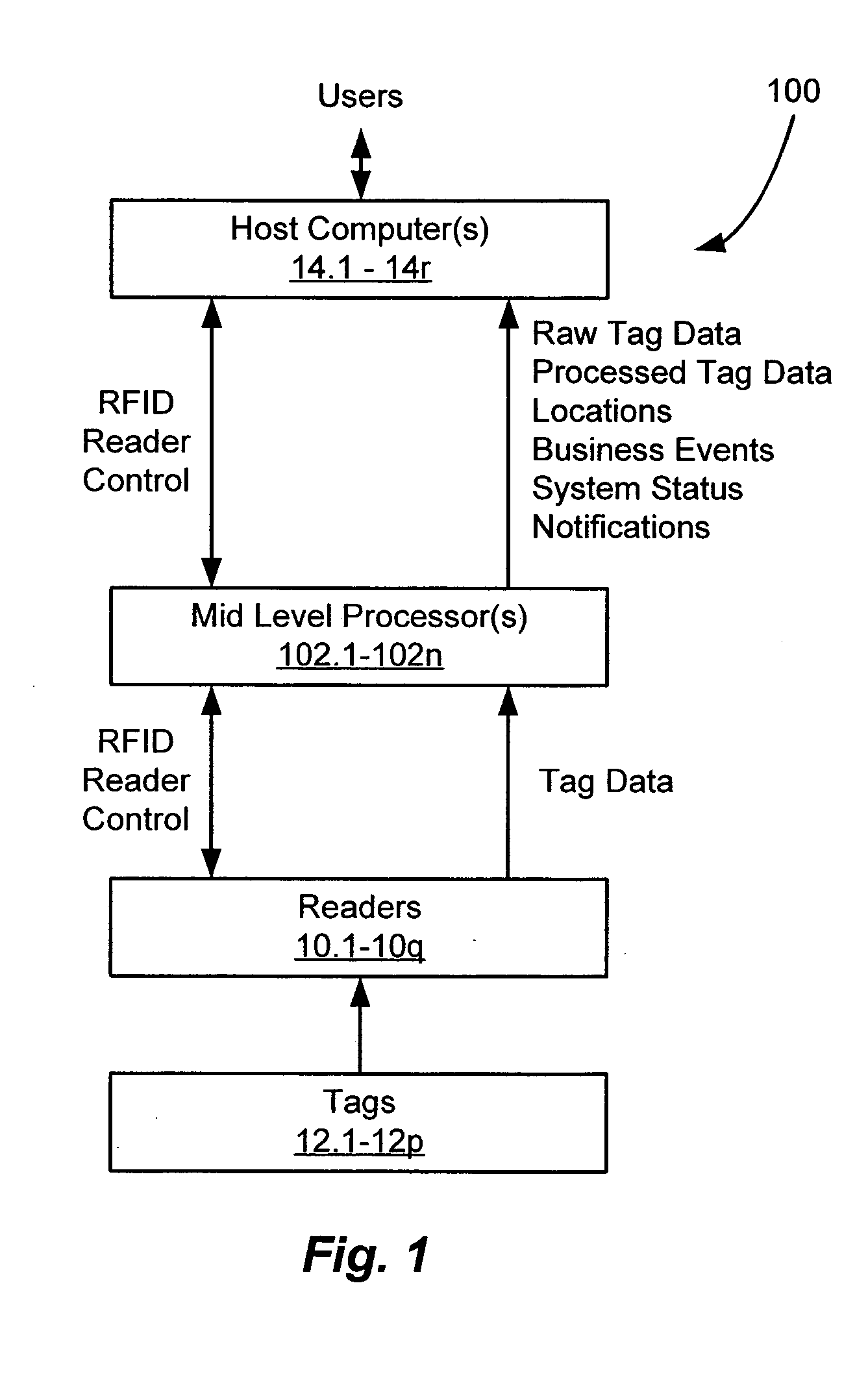
A system and method of determining locations of one or more RFID tags within an RFID environment. The system includes a plurality of RFID readers, each operative to transmit and receive RF signals for scanning a tag disposed within an RF coverage region associated with the reader, and for receiving tag data in response to the scanning of the tag. A plurality of sub-locations is determined within the environment, each corresponding to at least a portion of at least one of a plurality of RF coverage regions associated with the readers. The sub-locations are mapped to a plurality of predefined locations within the environment. A reader scans a tag, and receives tag scan data from the tag in response to the scanning of the tag. The tag scan data includes a tag identifier associated with the scanned tag. The tag scan data is mapped to the sub-locations based on the RF coverage region associated with the reader. The location of the scanned tag is then determined with reference to the predefined locations within the environment, based on the tag identifier included in the tag scan data, the mapping of the tag scan data to the sub-locations, and the mapping of the sub-locations to the predefined locations.
Owner:ODIN SOFTWARE INC +1
Method, apparatus and article for computational sequence generation and playing card distribution
A computationally generated playing card sequence (e.g., pseudo-random, non pseudo-random, or partially pseudo-random) allows shuffled distribution of playing cards. Playing cards may be organized into card holders by at least one or a rank and a suit, and retrieved in the computationally generated order. Alternatively, playing cards may be organized into card holders in order of a computationally generated sequence, and retrieve as necessary. Unreadable playing cards may be automatically removed from play.
Owner:BALLY GAMING INC +1
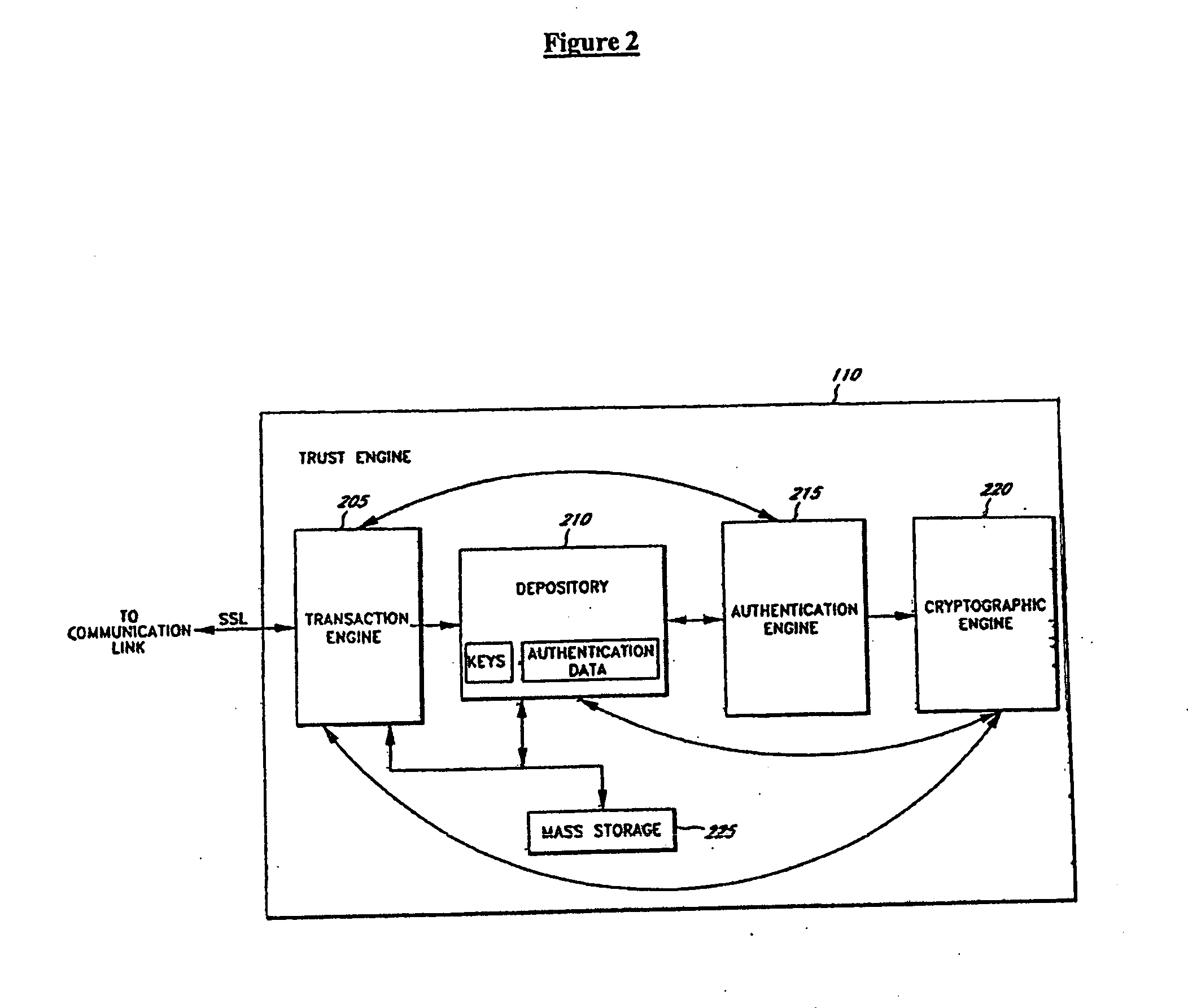
Systems and methods for distributing and securing data
ActiveUS20080137857A1Key distribution for secure communicationRandom number generatorsInformation dispersalCiphertext
A robust computational secret sharing scheme that provides for the efficient distribution and subsequent recovery of a private data is disclosed. A cryptographic key may be randomly generated and then shared using a secret sharing algorithm to generate a collection of key shares. The private data may be encrypted using the key, resulting in a ciphertext. The ciphertext may then be broken into ciphertext fragments using an Information Dispersal Algorithm. Each key share and a corresponding ciphertext fragment are provided as input to a committal method of a probabilistic commitment scheme, resulting in a committal value and a decommittal value. The share for the robust computational secret sharing scheme may be obtained by combining the key share, the ciphertext fragment, the decommittal value, and the vector of committal values.
Owner:SECURITY FIRST INNOVATIONS LLC
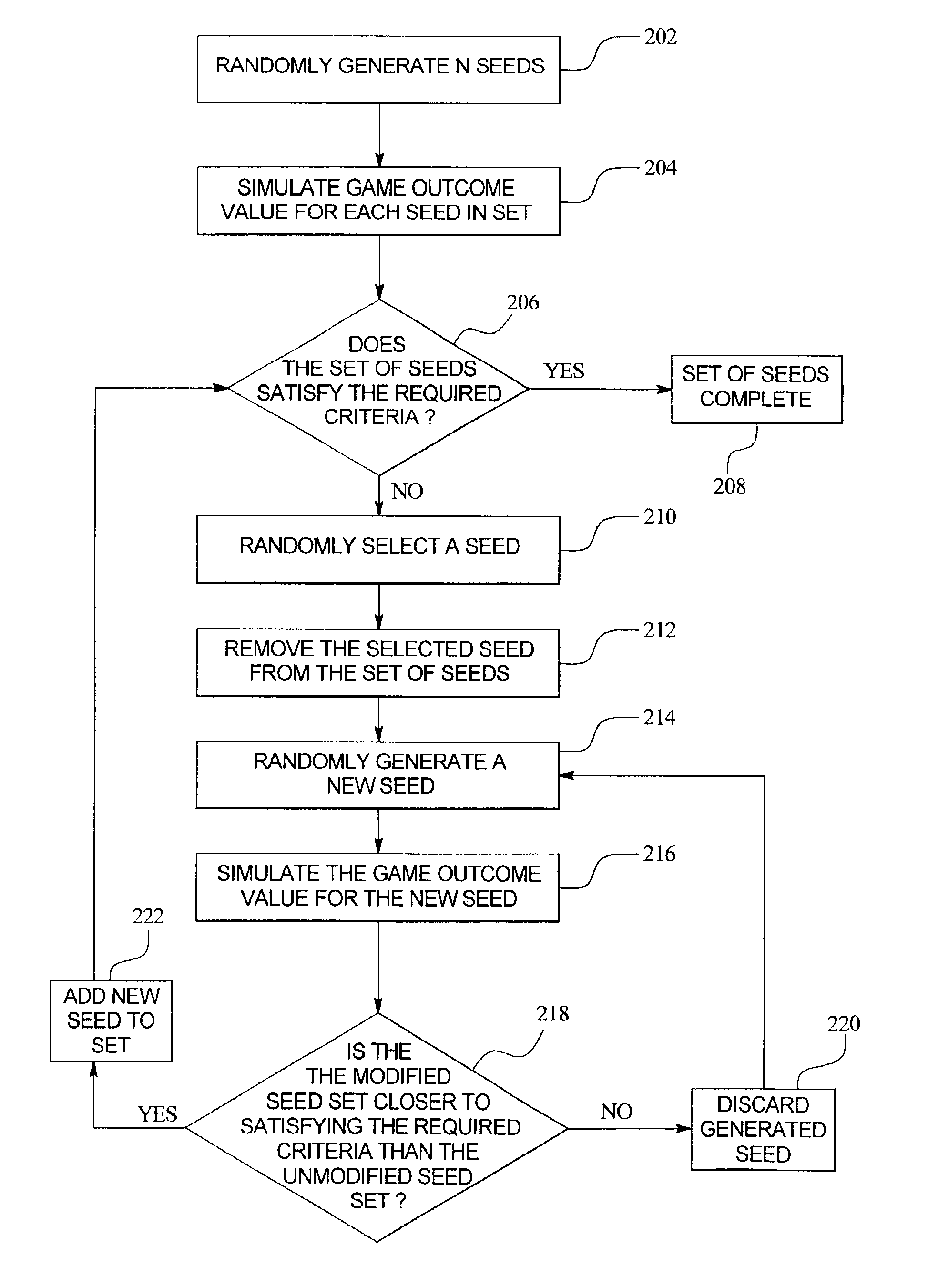
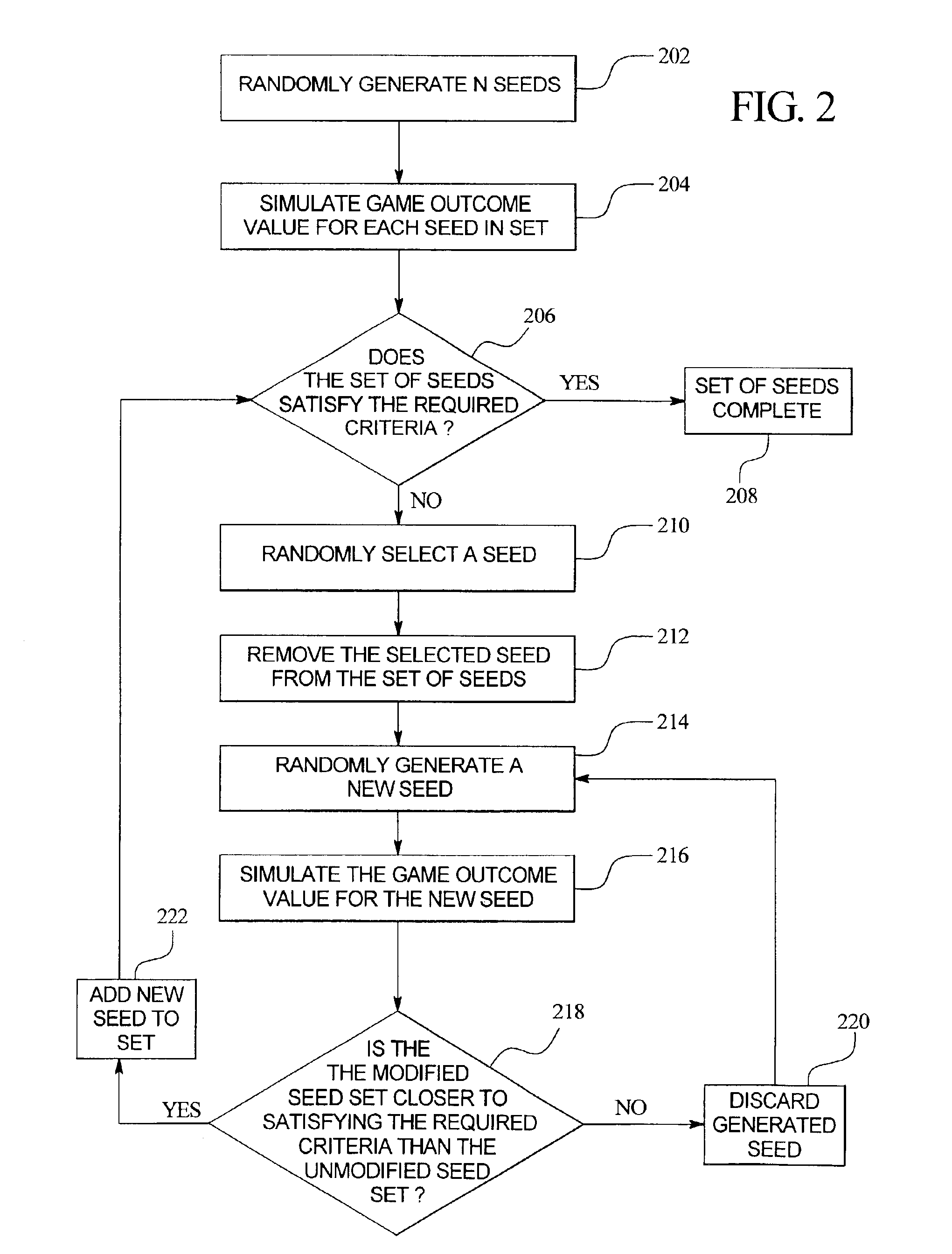
Apparatus and method for generating a pool of seeds for a central determination gaming system
InactiveUS6866584B2Random number generatorsApparatus for meter-controlled dispensingRandom Number SeedComputer science
An apparatus and method for generating one or more pools or sets of seeds for use in a central determination gaming system. In one embodiment of the present invention, a processor of the apparatus or seed generator randomly generates a predetermined number of random number seeds. After the predetermined number of seeds are generated, the processor simulates the game outcome value that each generated seed ultimately determines. Having simulated a game outcome value for each generated seed, the processor determines if the set of seeds satisfies a required condition or criteria. If the required conditions or criteria are satisfied, the set is complete and ready for use in a central determination gaming system. If the required conditions or criteria are not satisfied, the processor modifies the generated set of seeds until the required conditions or criteria are satisfied.
Owner:IGT
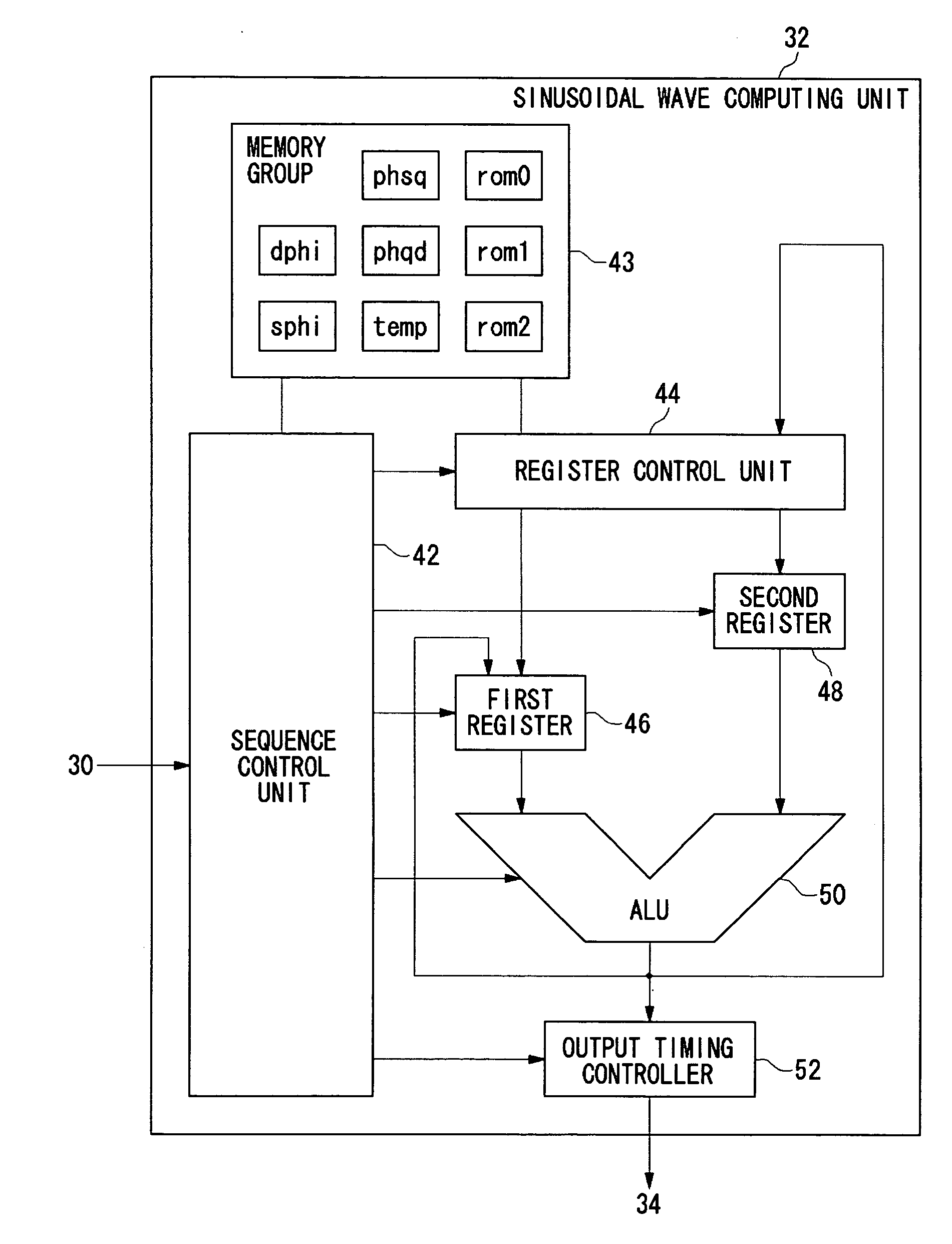
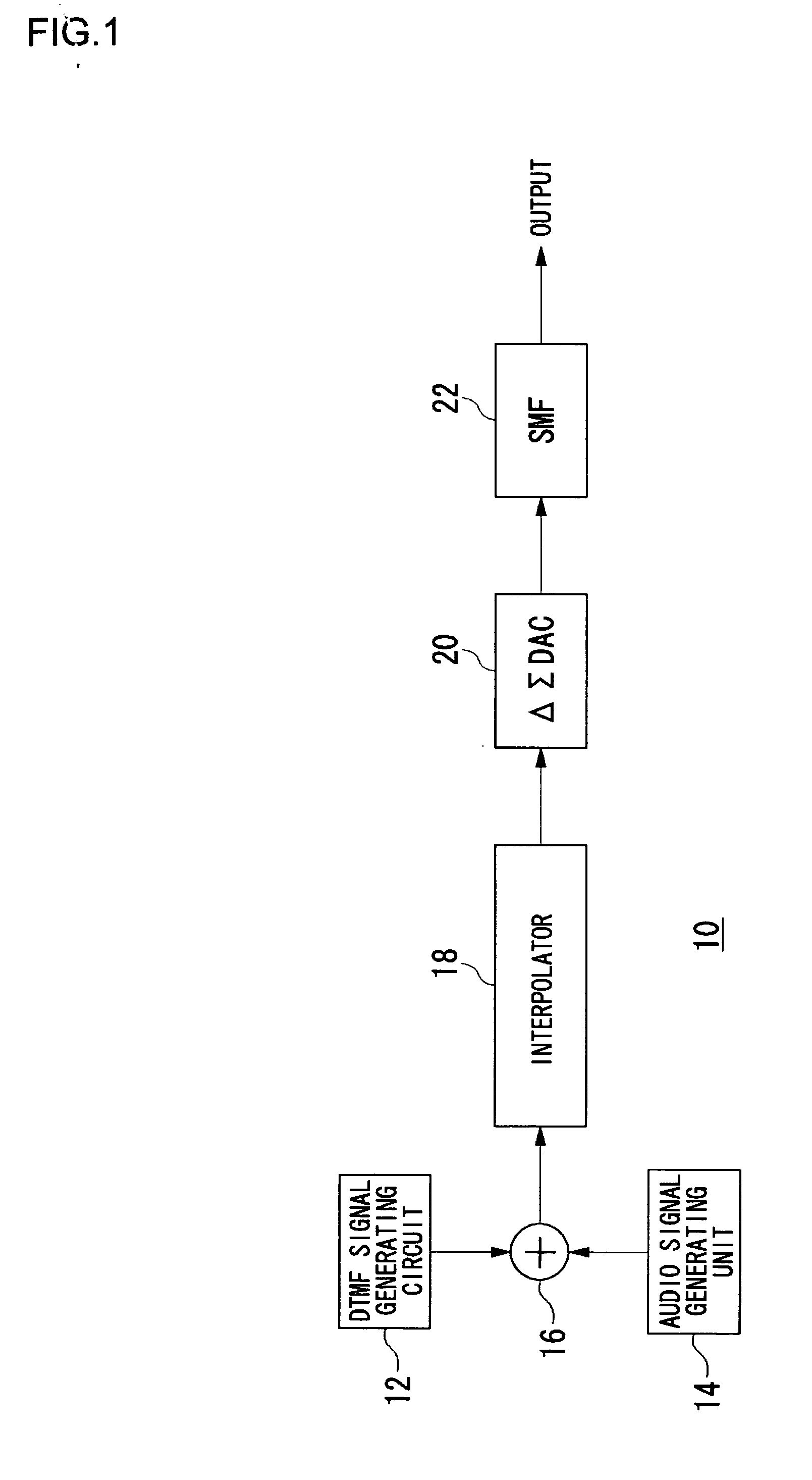
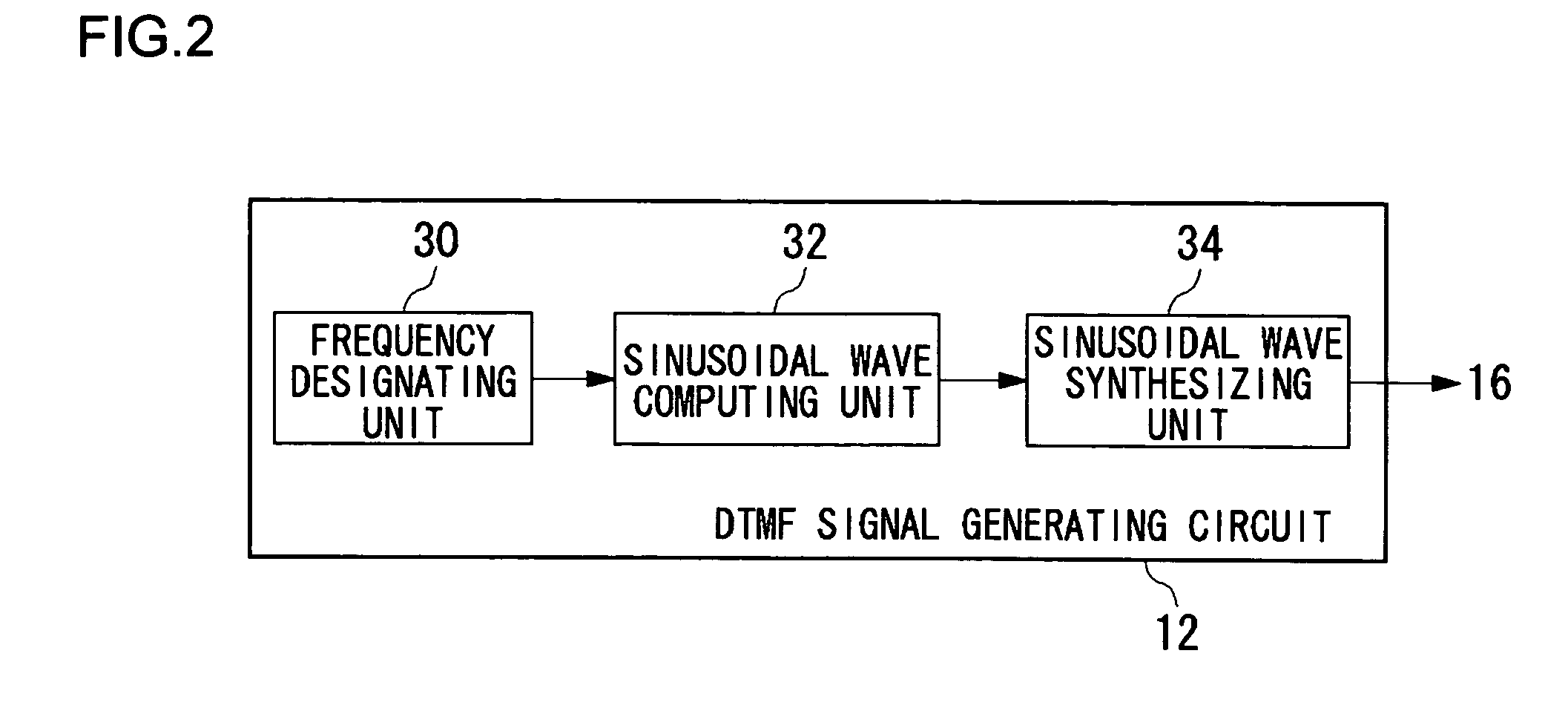
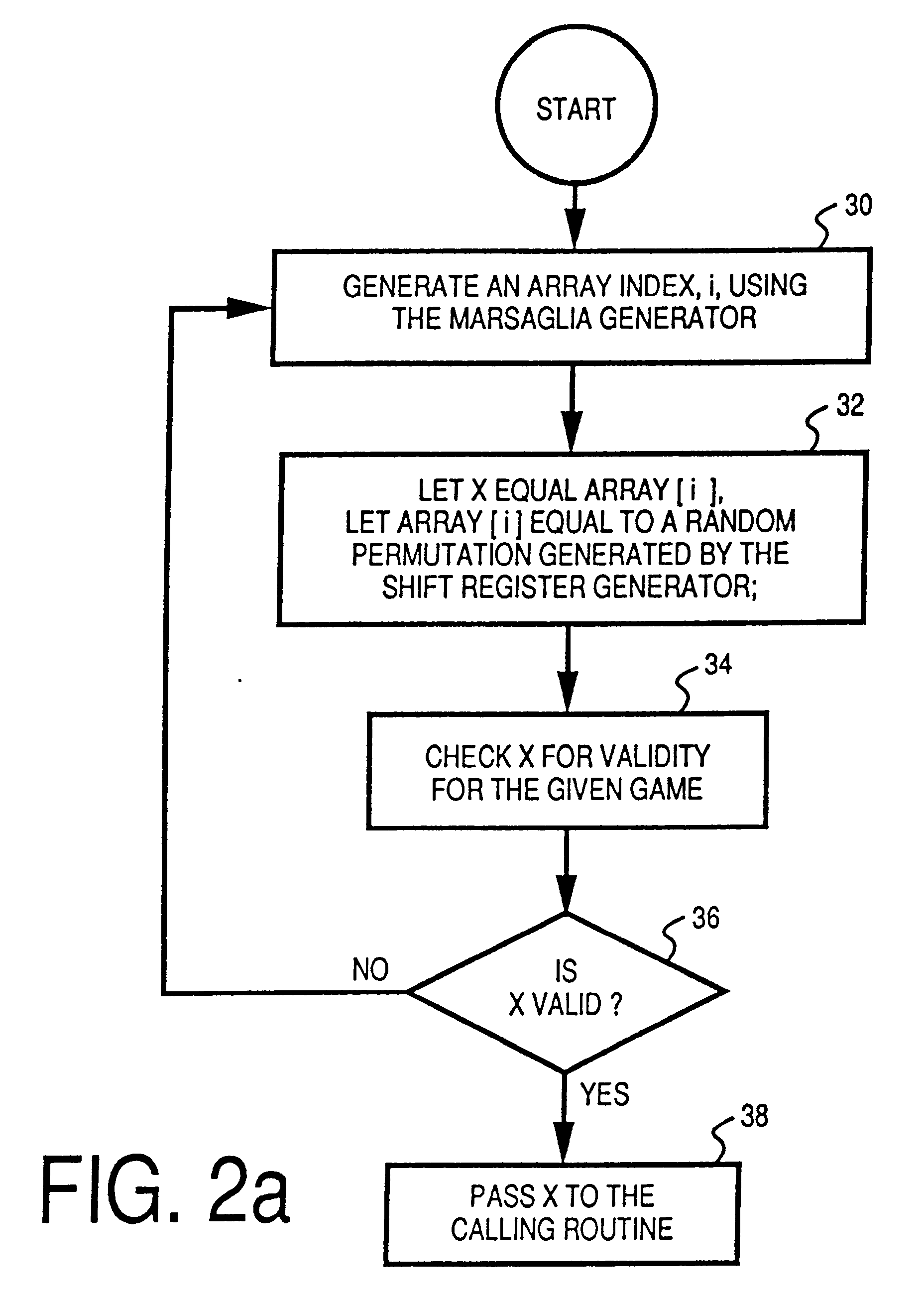
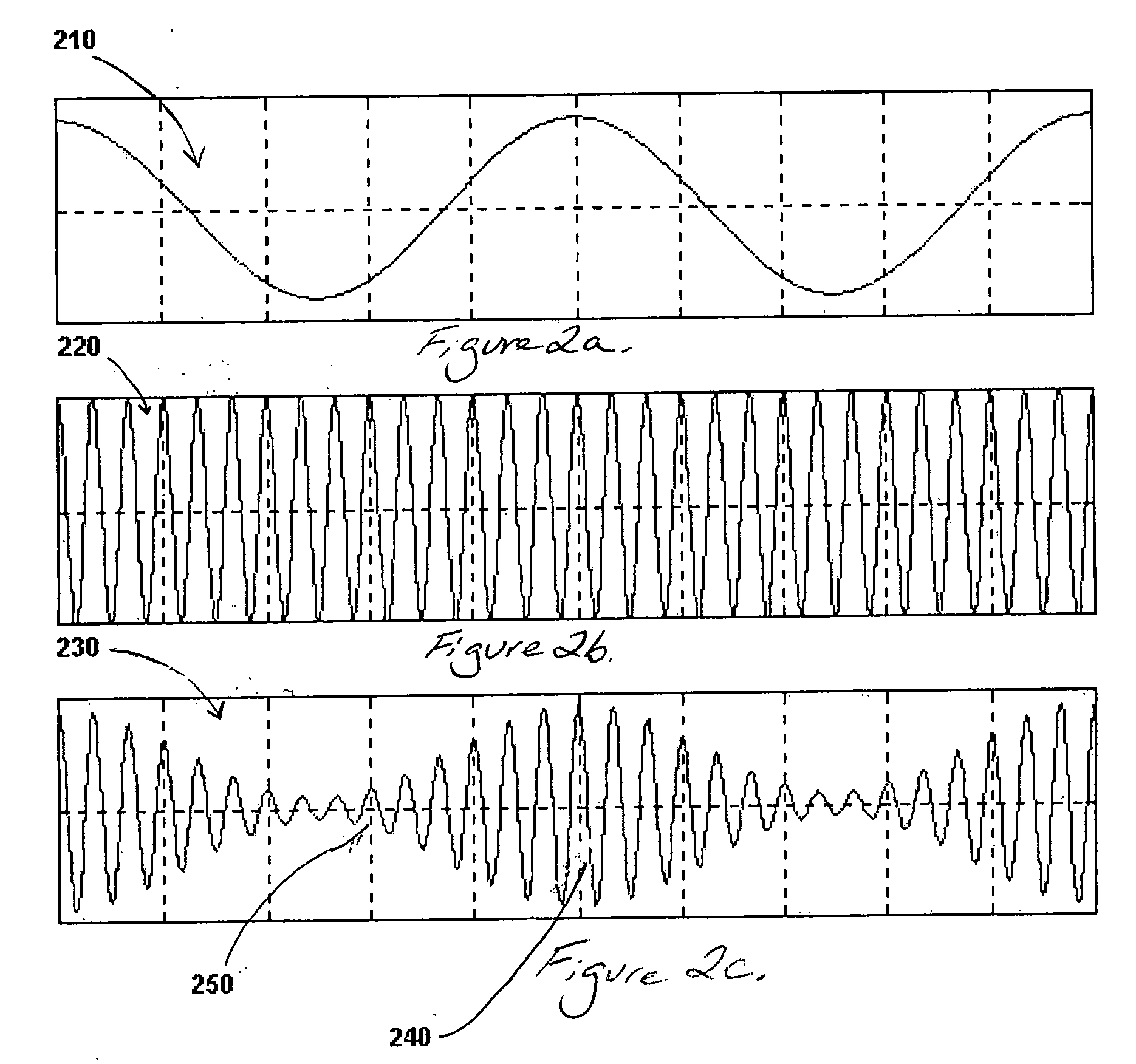
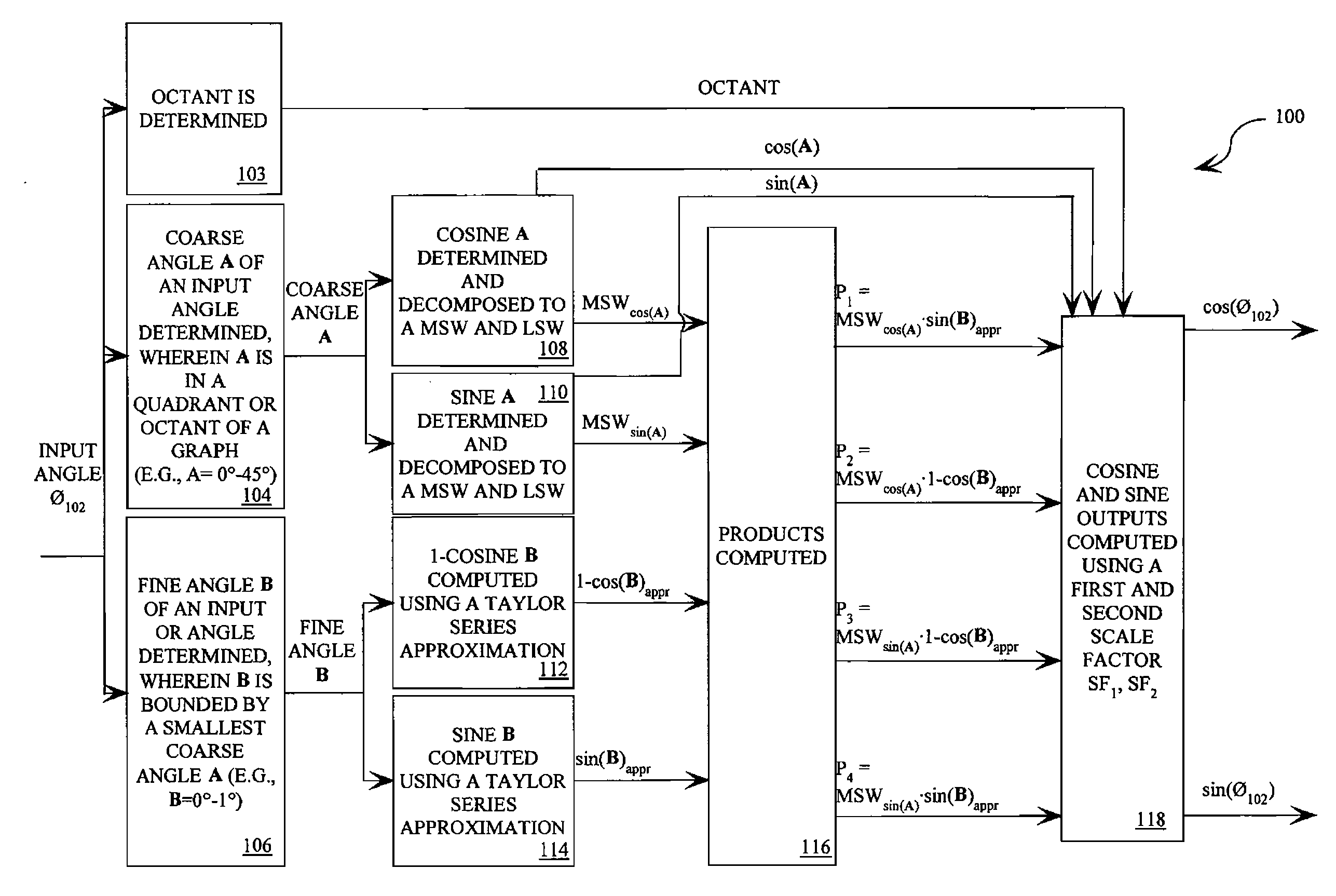
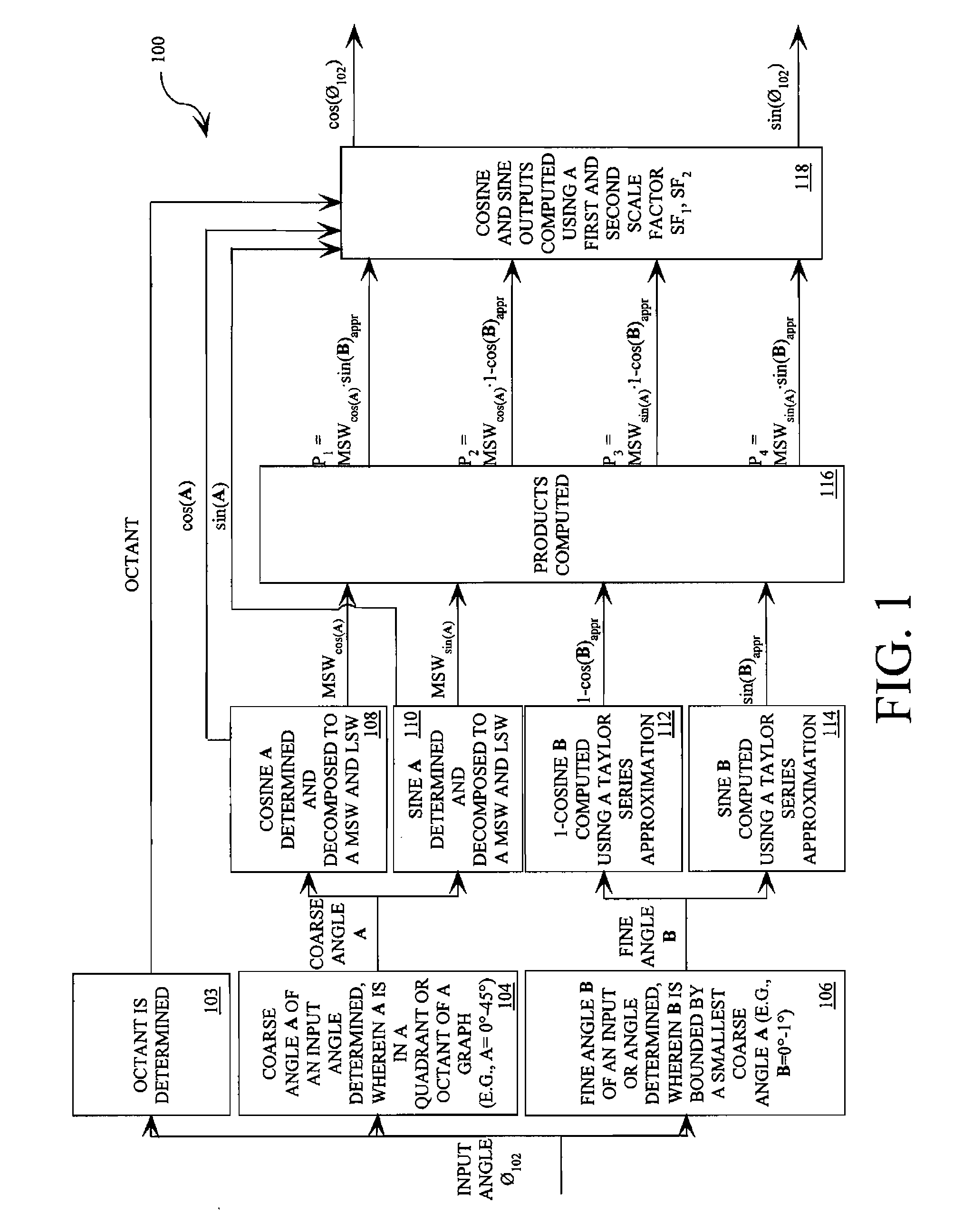
Trigonometric wave generation circuit using series expansion
InactiveUS20050262175A1Reduce circuit areaReduce functionMulti-frequency code systemsDigital function generatorsSinewave synthesisSeries expansion
A DTMF signal generating circuit is provided with a frequency designating unit which designates frequencies to form a DTMF signal, a sinusoidal wave computing unit which computes sinusoidal waves by referring to frequencies designated by the frequency designating unit, and a sinusoidal wave synthesizing unit which synthesizes two sinusoidal waves computed by the sinusoidal wave computing unit. The sinusoidal wave computing unit is provided with operators such as an adder-subtracter and a multiplier and generates a sinusoidal wave by determining terms of a Taylor expansion of a sinusoidal function by arithmetic operation.
Owner:ROHM CO LTD
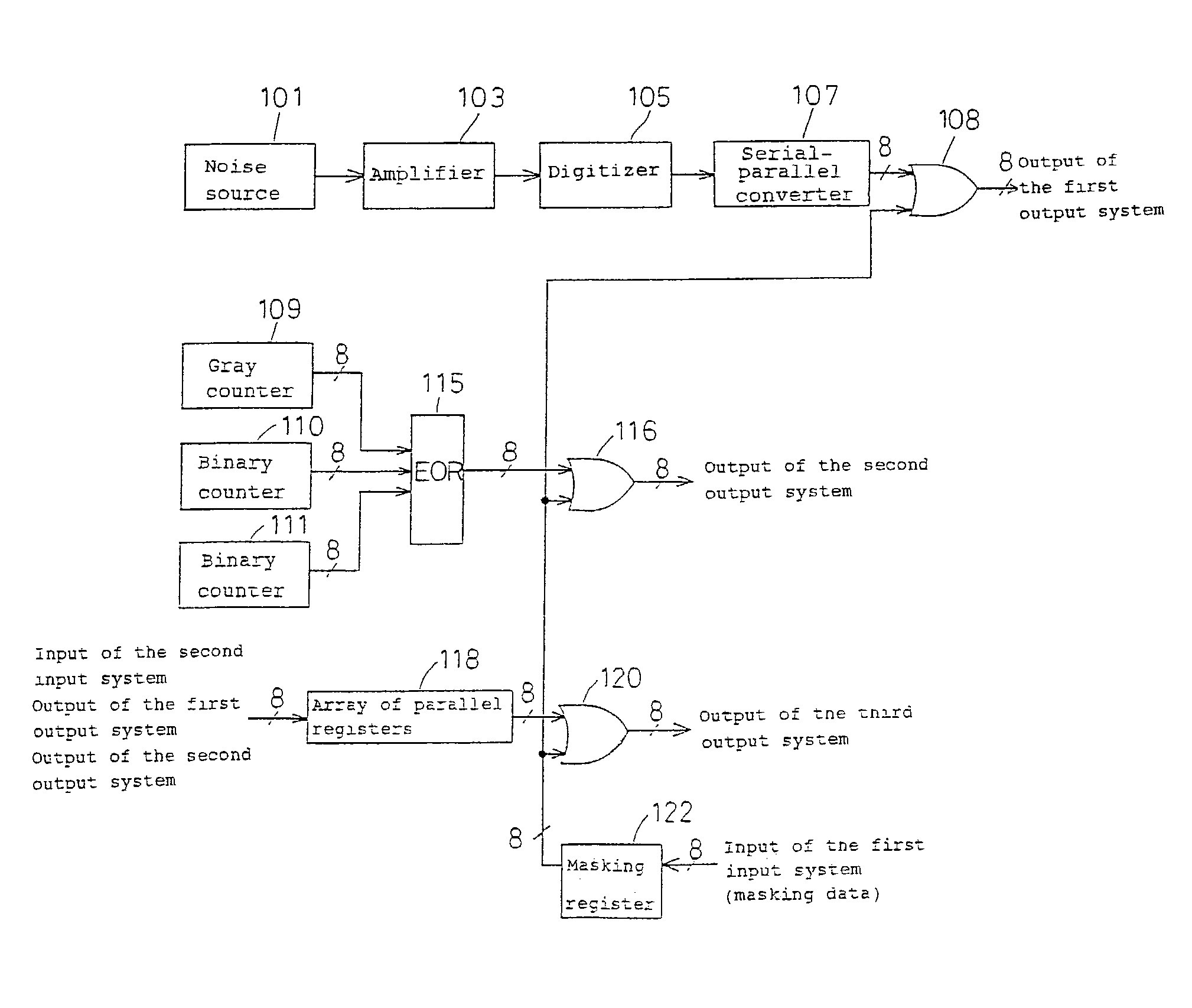
Random number generator
InactiveUS7124157B2Promote generationStable structureRandom number generatorsDigital function generatorsAudio power amplifierNumber generator
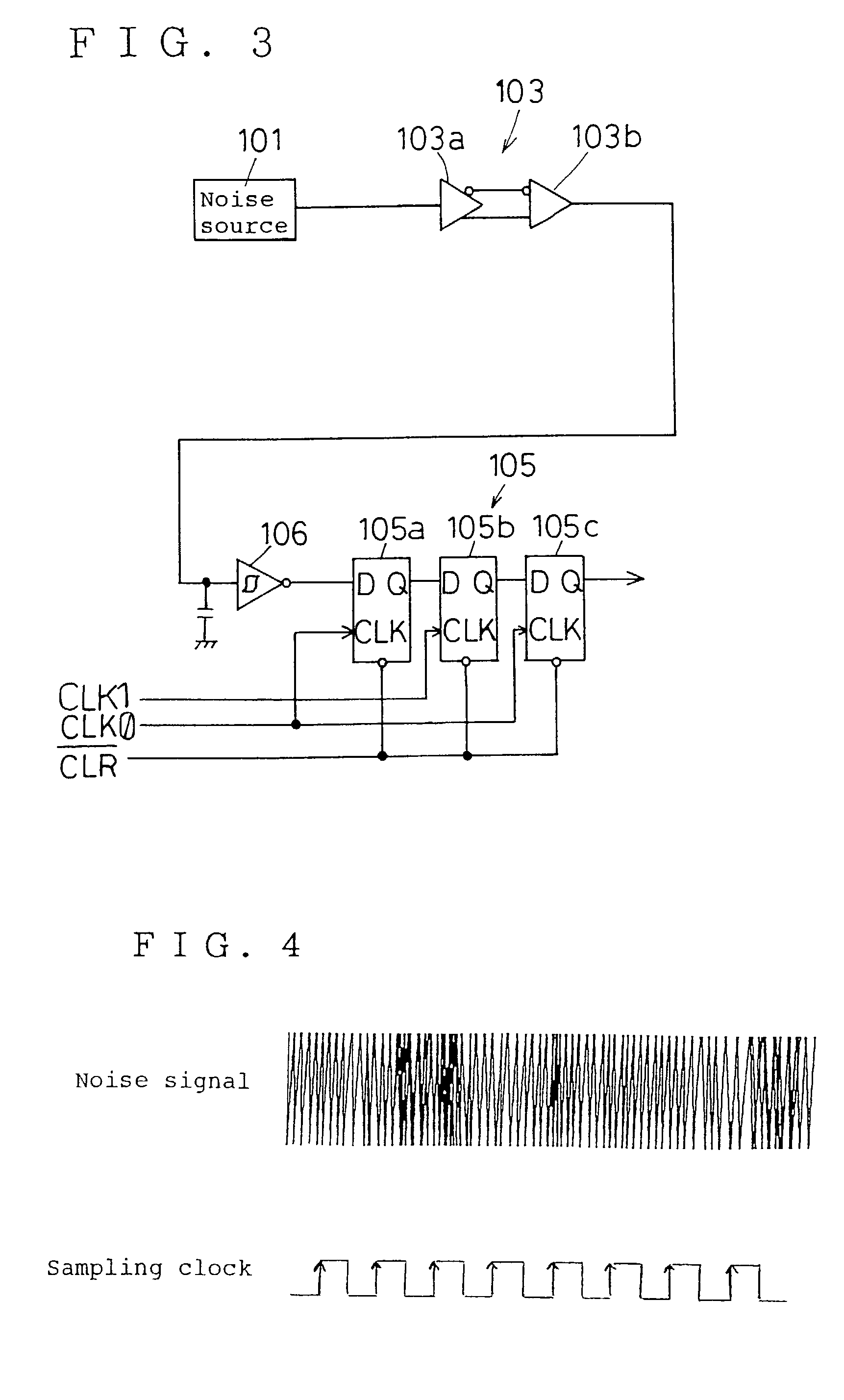
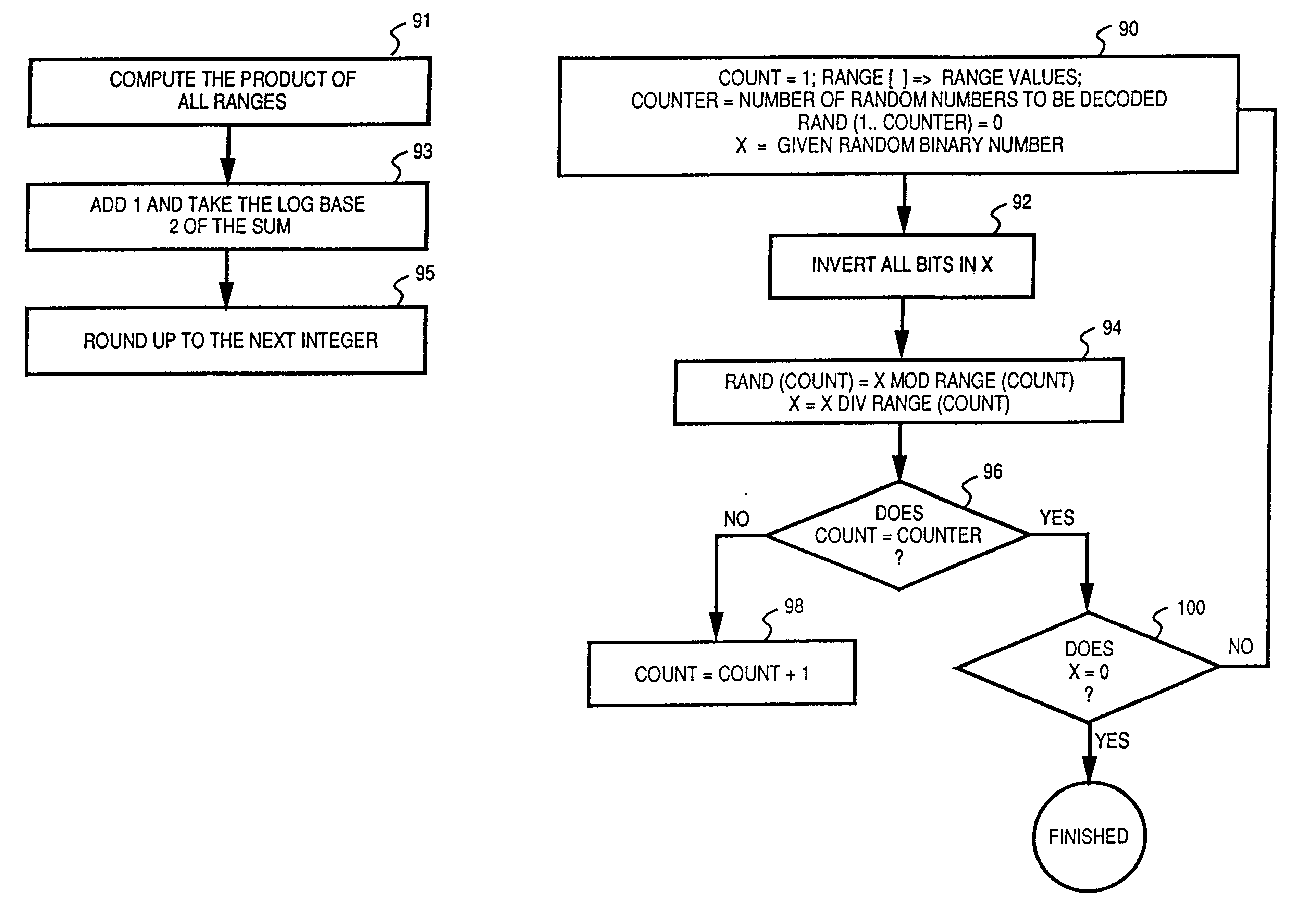
A random number generator having a simple construction which generates physical random numbers necessary for encryption. The random number generator has an amplifier to amplify noise signals generated from a noise source and digitizer to digitize the amplified noise signals. The digitizer includes a serial register.
Owner:HMI
Random number generator for electronic applications
InactiveUS6193607B1Fast executionLottery apparatusRandom number generatorsGeneration processNumber generator
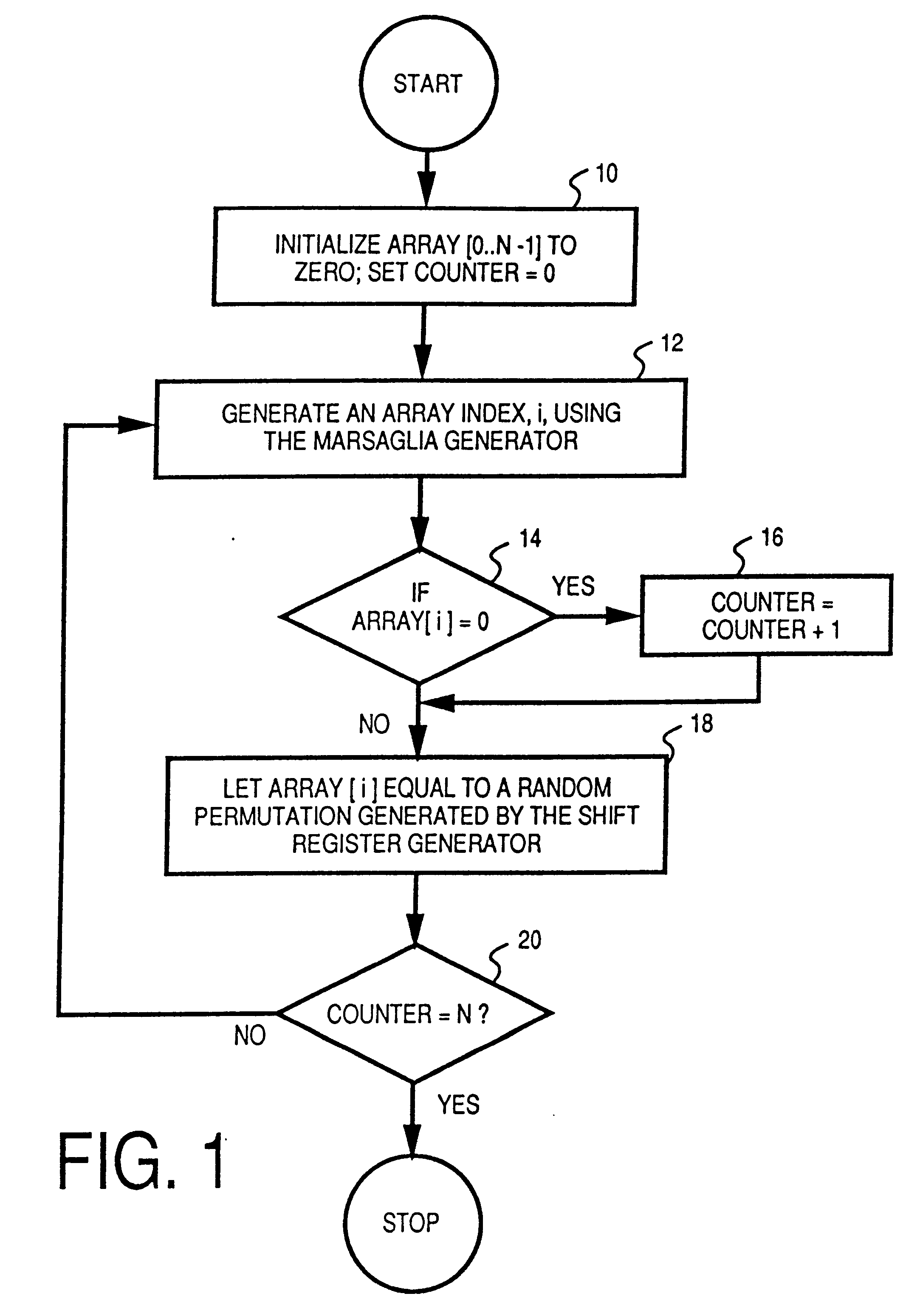
A method and apparatus for generating random numbers for use in electronic applications is disclosed. A given sequence of random binary numbers of a certain length can be decoded into several random numbers for a specific application. The upper range values of the random numbers to be decoded determine the number of bits required for the generation of the these random numbers. In the decoding process, the given random binary number divides a range value to generate a remainder and a quotient. The quotient becomes the new random binary number for the generation of other random numbers while the remainder is the generated random number. The process then repeats to generate other random numbers. At the end of the generation process, the last quotient determines the validity of the generated random numbers.
Owner:IGT
Method, apparatus and article for computational sequence generation and playing card distribution
A computationally generated playing card sequence (e.g., pseudo-random, non pseudo-random, or partially pseudo-random) allows shuffled distribution of playing cards. Playing cards may be organized into card holders by at least one or a rank and a suit, and retrieved in the computationally generated order. Alternatively, playing cards may be organized into card holders in order of a computationally generated sequence, and retrieve as necessary. Unreadable playing cards may be automatically removed from play.
Owner:BALLY GAMING INC +1
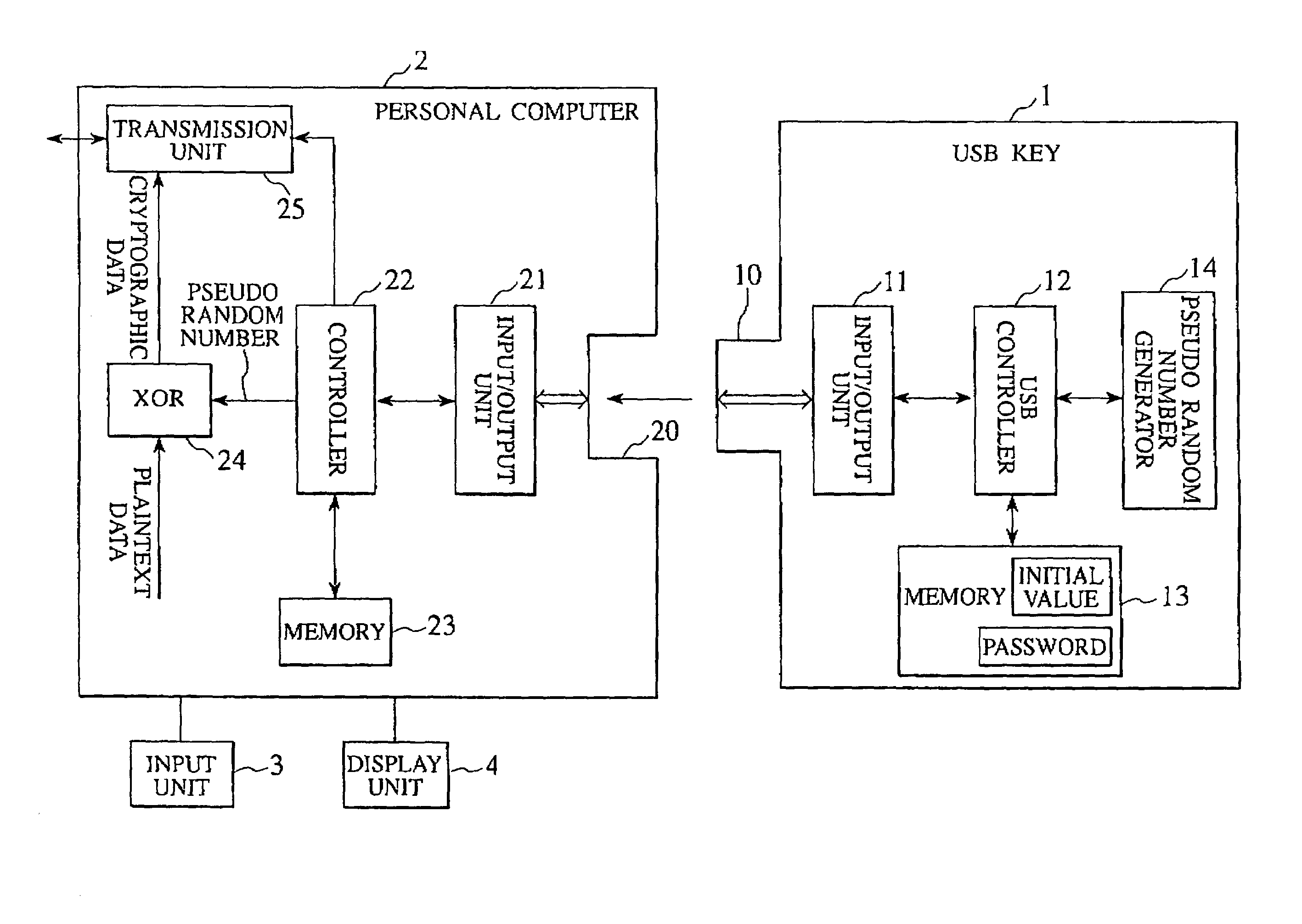
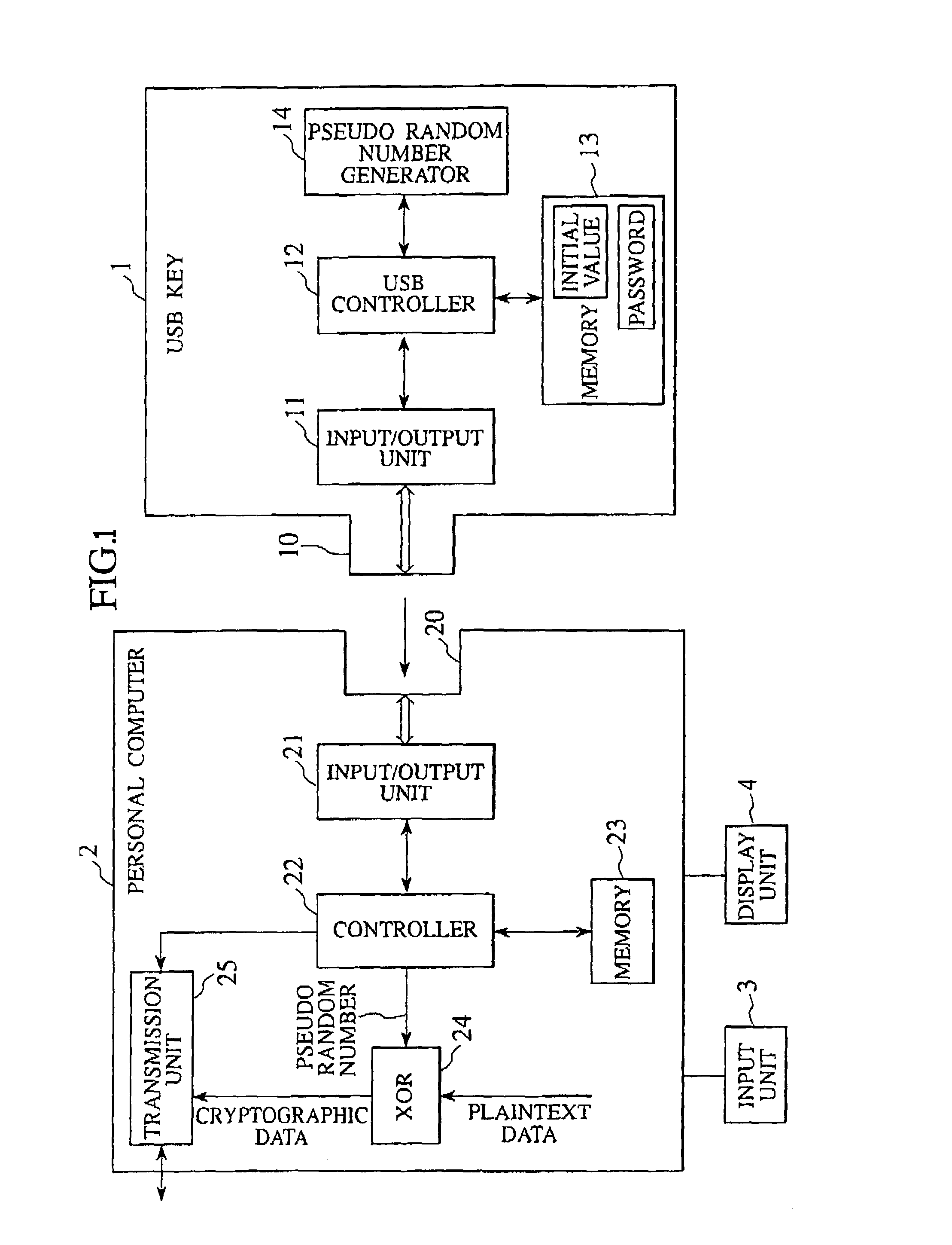
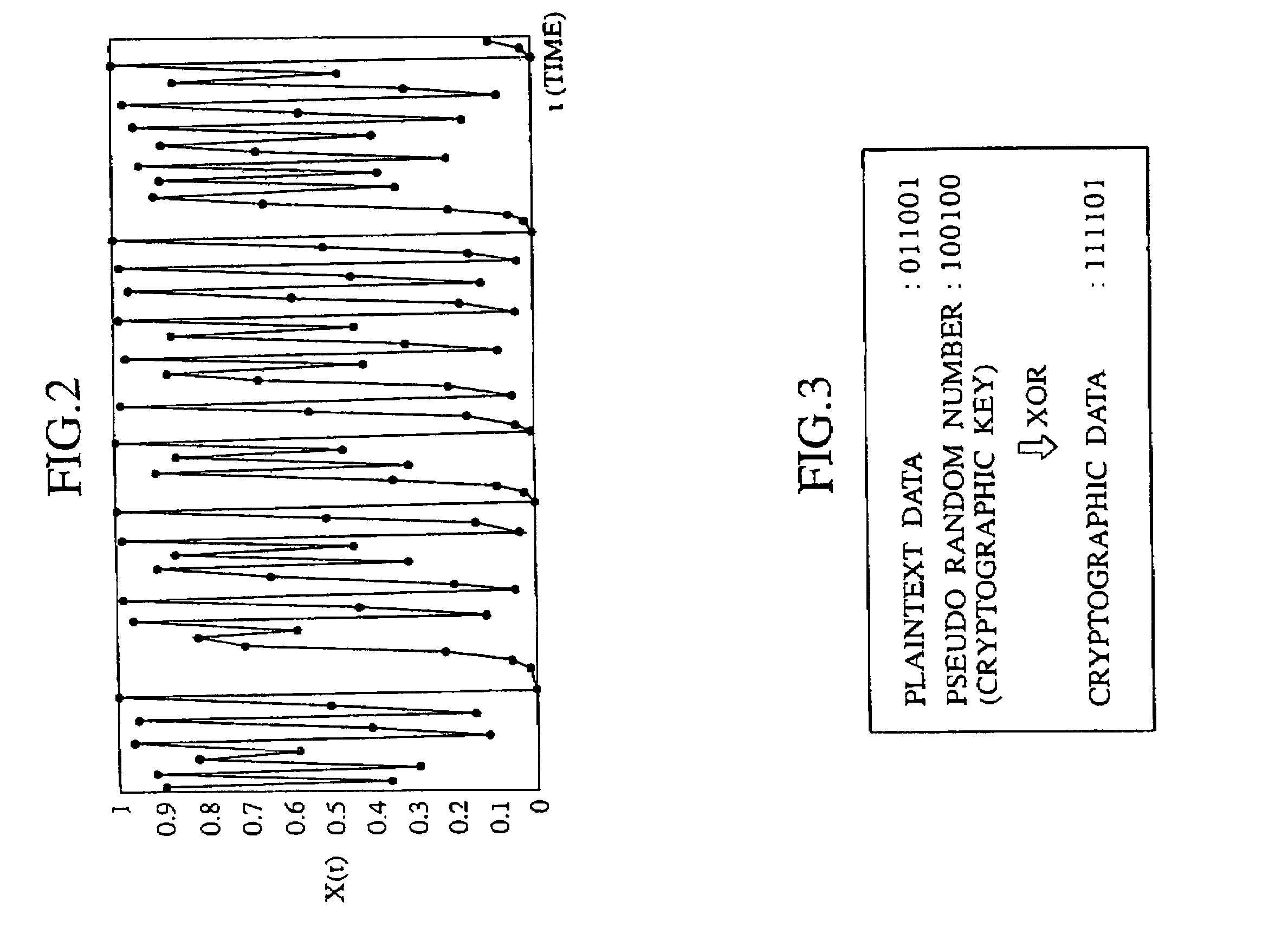
Cryptographic communications using pseudo-randomly generated cryptography keys
InactiveUS7120696B1High strengthImprove securitySynchronising transmission/receiving encryption devicesRandom number generatorsSecure communicationCommunications system
An apparatus and method for generating pseudo-random cryptographic keys in a cryptographic communications system, whereby, given a common set of initializing configuration data, the pseudo-random cryptographic keys can be duplicatively generated by various independent pseudo-random key generators of the cryptographic communications system. In accordance with the preferred embodiment of the present invention, users of the communications system can each possess an independent pseudo-random key generator to securely communicate with other users also holding independent pseudo-random key generator that share the same initialization configuration data, no matter where the other users are located or whether the users are connected via wire or wireless communication network. The present invention facilitates secure communication without the need to transport decryption keys in advanced, thereby reducing the risk of the secure communication becoming compromised via interception of decryption keys.
Owner:STEALTHKEY
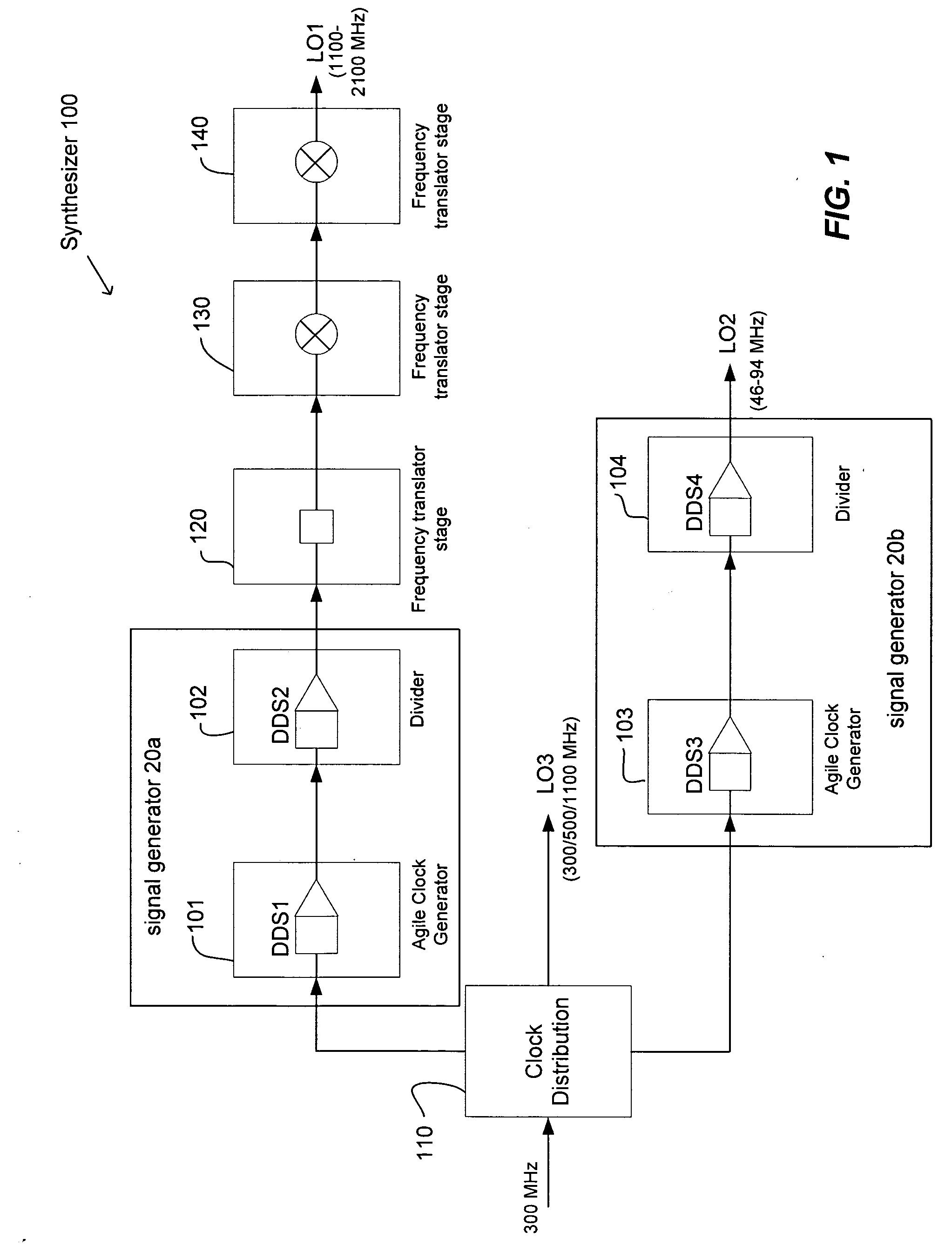
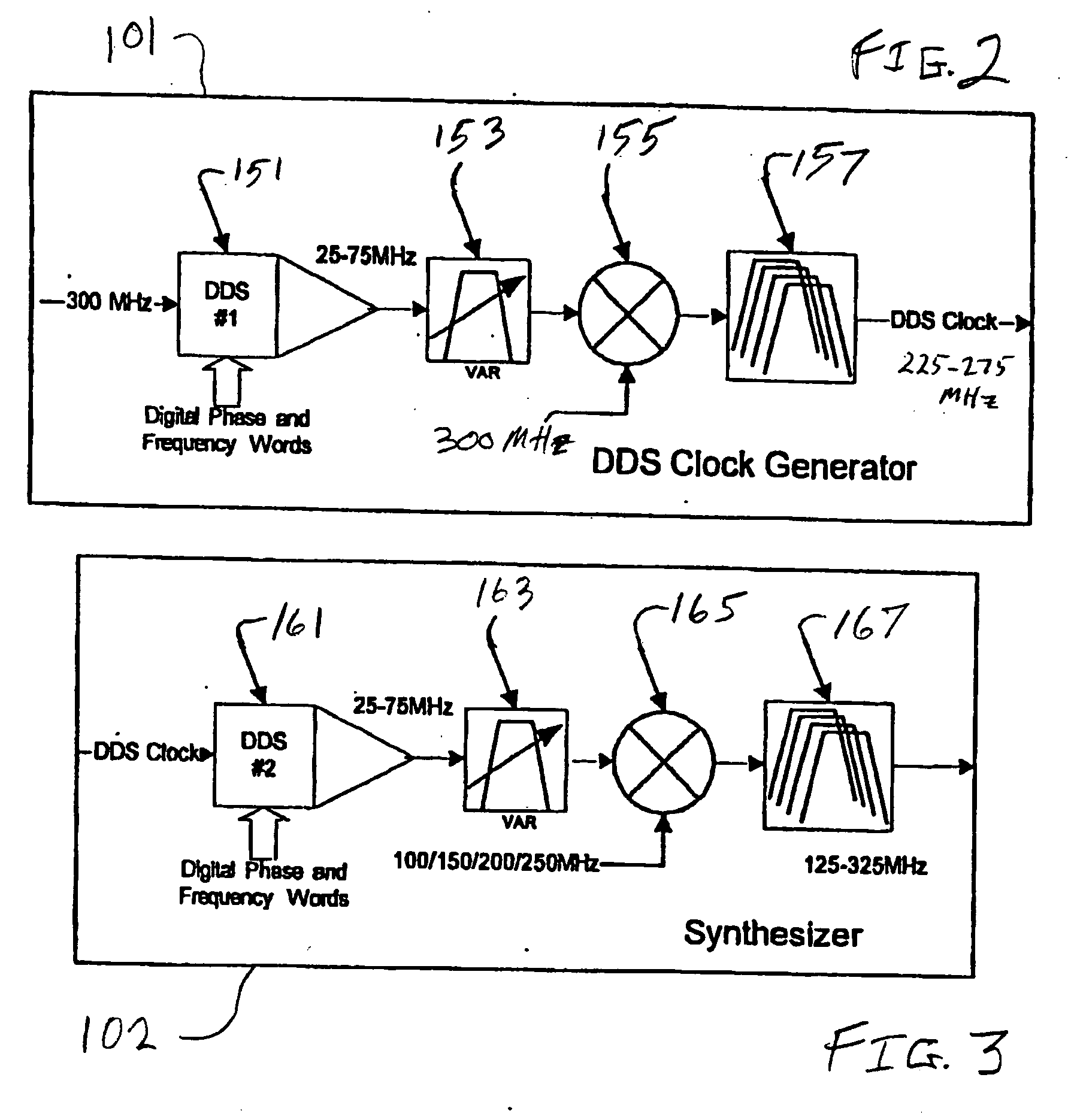
Wideband signal generators, measurement devices, methods of signal generation, and methods of signal analysis
ActiveUS20050003785A1Small sizeReducing or avoiding spurious DDS responsesPulse automatic controlContinuous to patterned pulse manipulationMeasurement deviceSignal analyzer
A wideband signal generator according to one embodiment of the invention includes a variable frequency source and a direct digital synthesizer. Local oscillators, signal analyzers, modulators, demodulators, and other equipment including one or more such generators are also disclosed.
Owner:MERCURY SISTEMS INC
System and method of generating electrical stimulation waveforms as a therapeutic modality
InactiveUS20070299895A1Easy to upgradeEasy to processElectrotherapyGain controlElectricityEngineering
Embodiments of the present invention provide an apparatus and method of generating electrical stimulation waveforms using Direct Digital Synthesis (DDS). The waveform generation substantially reduces intensive processor calculations and commands required for the generation of waveforms via Pulse Width Modulation (PWM). DDS technology is integrated into single-integrated circuit components, capable of generating waveforms based on singular digital word commands. The use of DDS integrated circuits allows for rapid changes in frequencies, automatically sweeps frequencies between user defined limits, and are capable of a wide range of frequencies. Further, utilization of DDS in waveform generation allows for software updatable functionality. Additionally, because DDS technology outputs a smooth sine wave, the need for extensive filtering is drastically reduced. Further, DDS technology can be utilized in an amplitude modulation stage beyond the DDS waveform generator, further reducing the burden on processor systems.
Owner:AXIOM WORLDWIDE
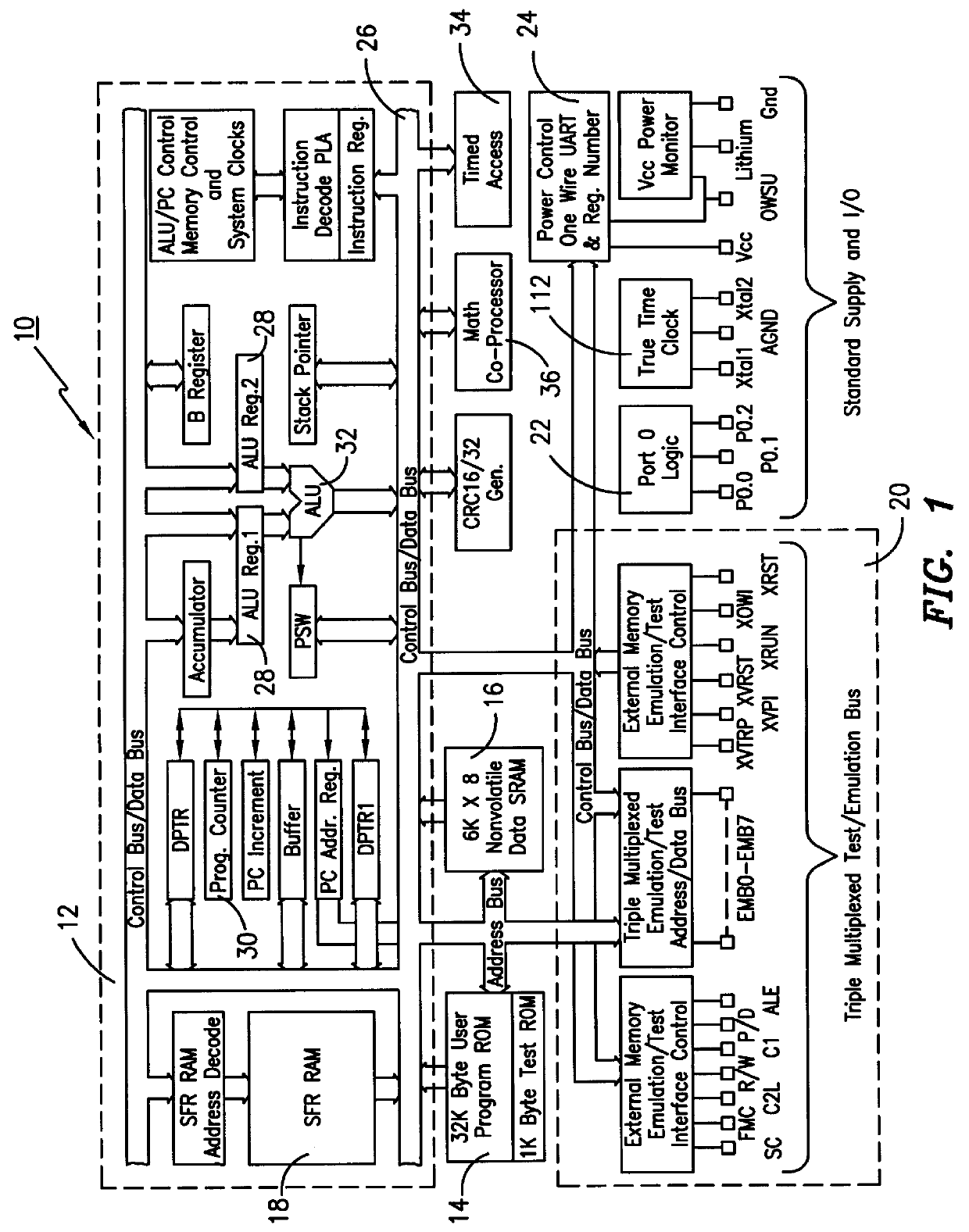
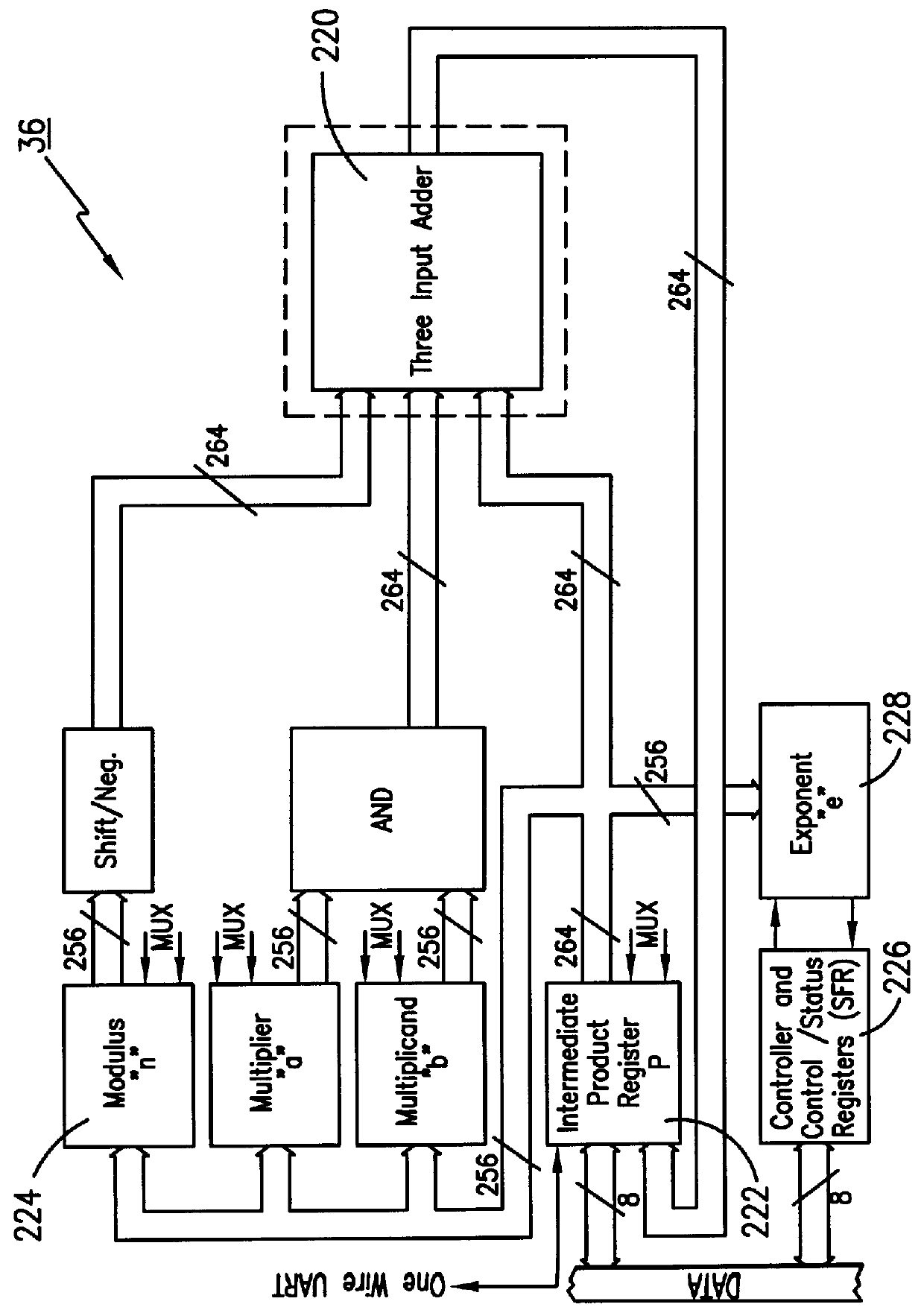
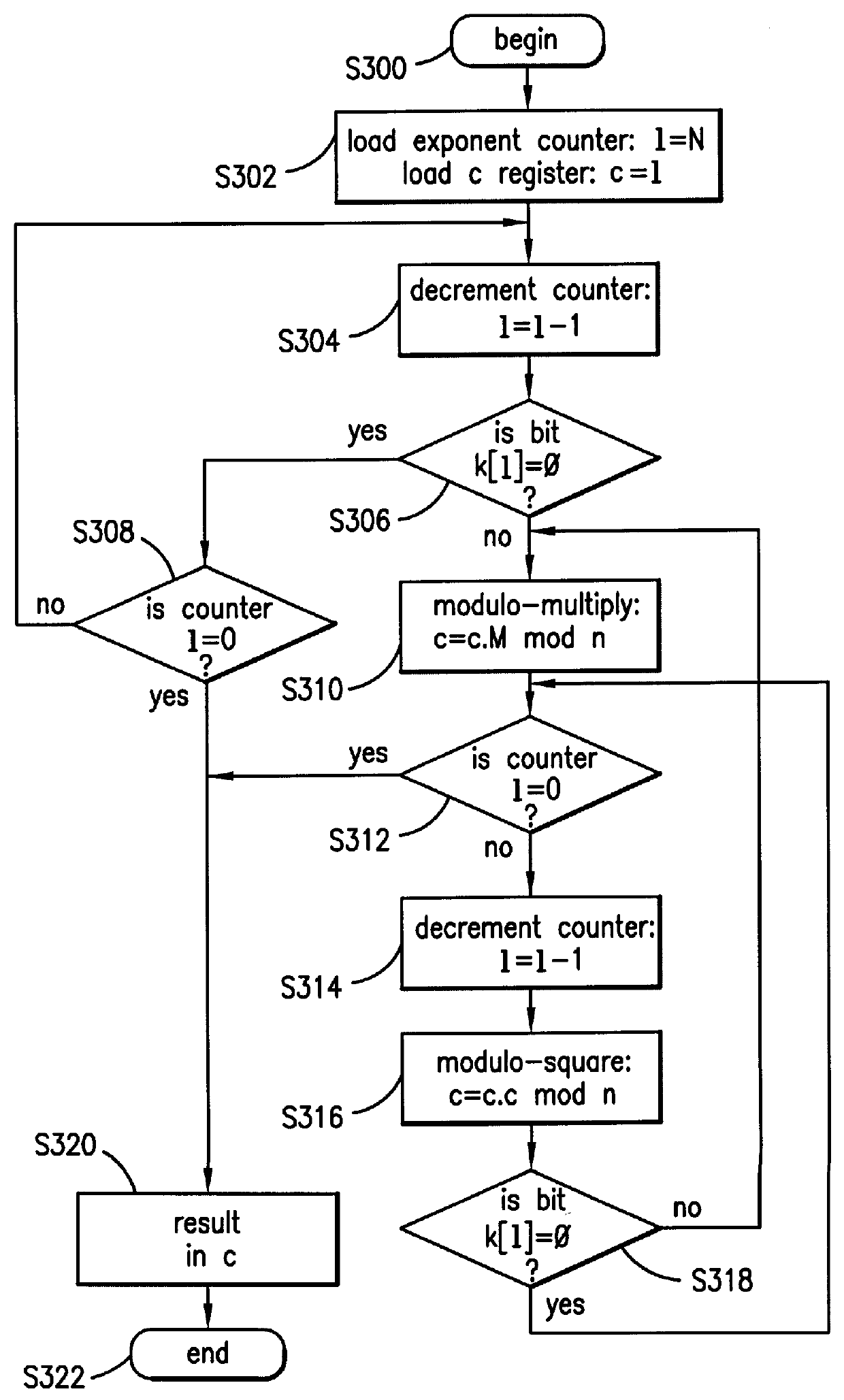
Method and apparatus for masking modulo exponentiation calculations in an integrated circuit
InactiveUS6064740APublic key for secure communicationComputation using non-contact making devicesComputer hardwareIntegrated circuit
Circuitry which performs modular mathematics to solve the equation C=Mk mod n and n is performed in a manner to mask the exponent k's signature from timing or power monitoring attacks. The modular exponentation function is performed in a normalized manner such that binary ones and zeros in the exponent are calculated by being modulo-squared and modulo-multiplied.
Owner:MAXIM INTEGRATED PROD INC
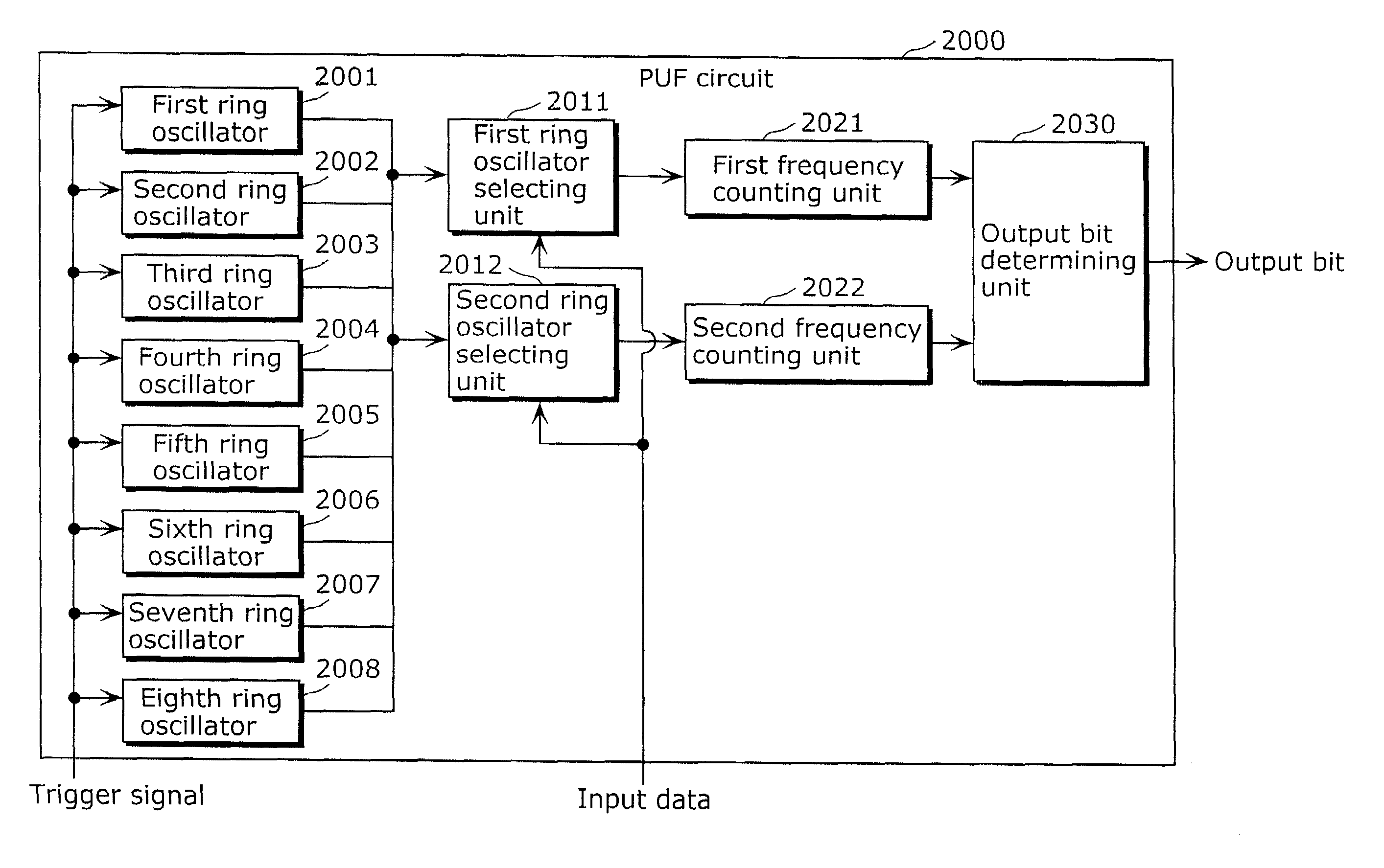
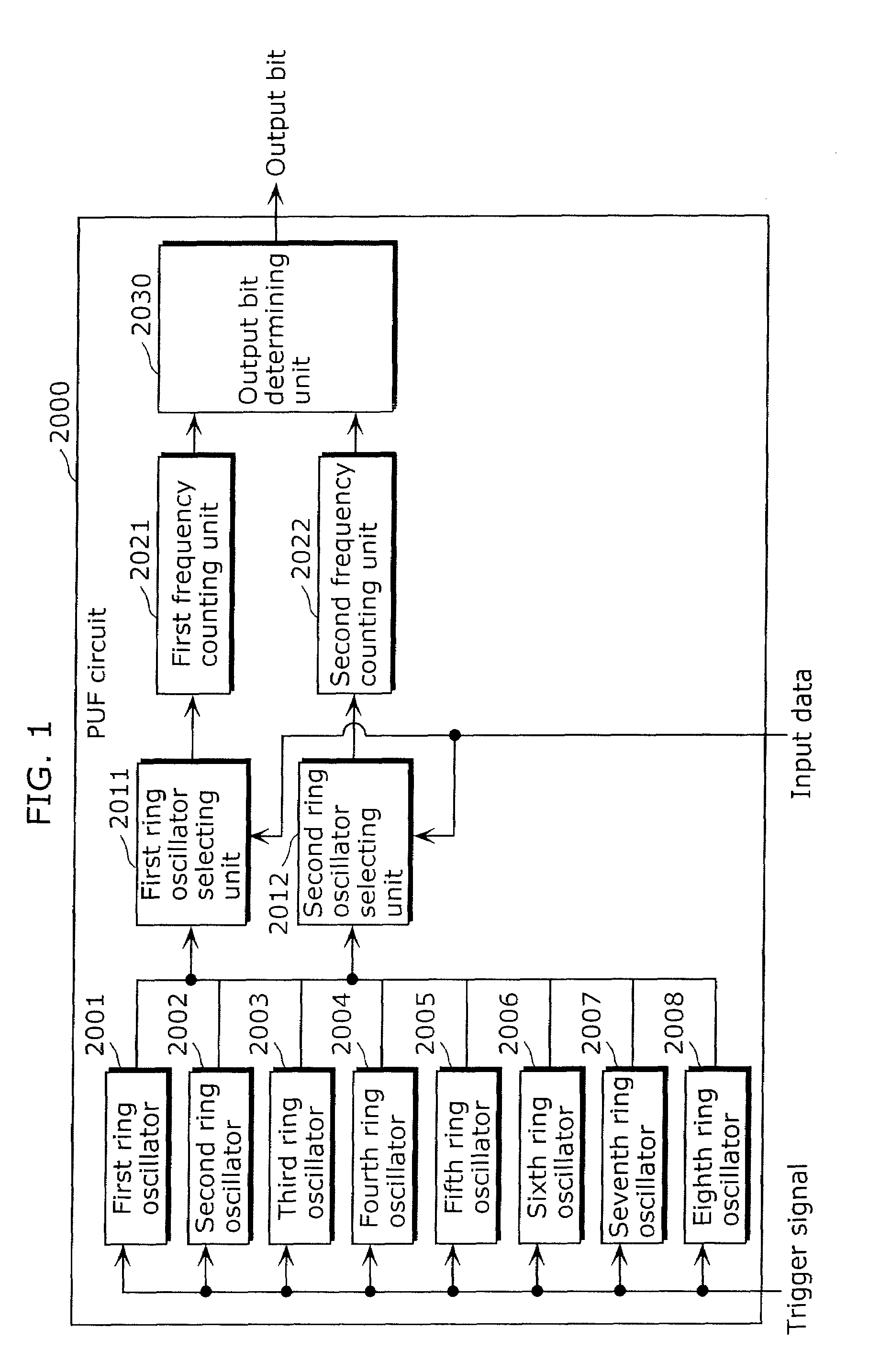
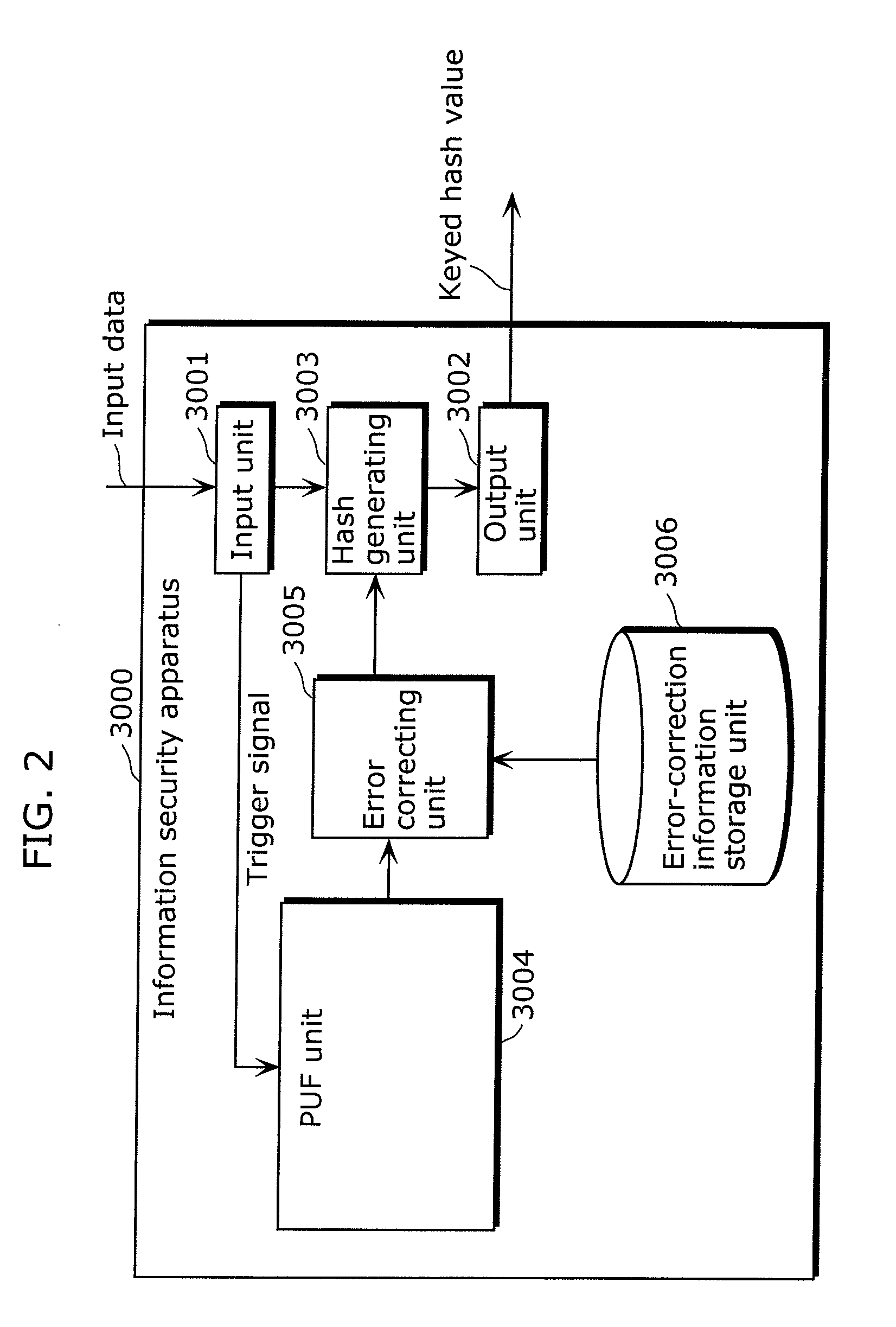
Information security apparatus
ActiveUS20100031065A1Low costImprove output stabilityError preventionRandom number generatorsComputer hardwareTamper resistance
Provided is an information security apparatus (1100) that has enhanced stability and confidentiality of a hash key. The information security apparatus (1100) includes an information generating PUF unit (1104) that has tamper resistance set, using physical characteristics, so as to output a preset hash key, a partial error-correction information storage unit (1107) that stores partial error-correction information, an error correcting PUF unit (1106) that has tamper-resistance set, using physical characteristics, so as to output error-correcting PUF information, an error-correction information generating unit (1108) that generates error-correction information using partial correction information and the error-correcting PUF information, and an error correcting unit (1105) that corrects an error for the hash key outputted from the information generating PUF unit (1104) and outputs an error-corrected hash key.
Owner:PANASONIC CORP
Sine/cosine generator
Owner:HARRIS CORP
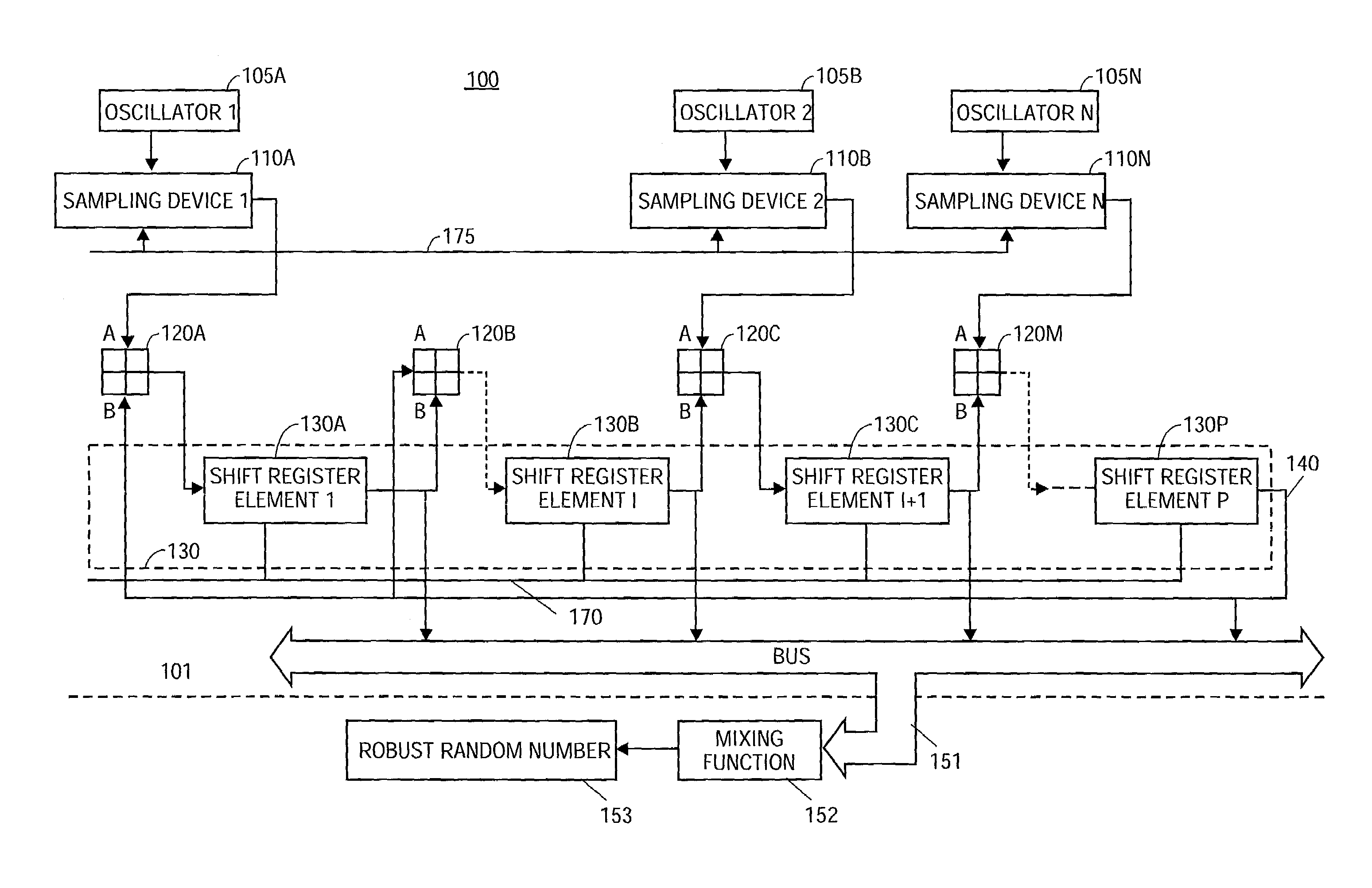
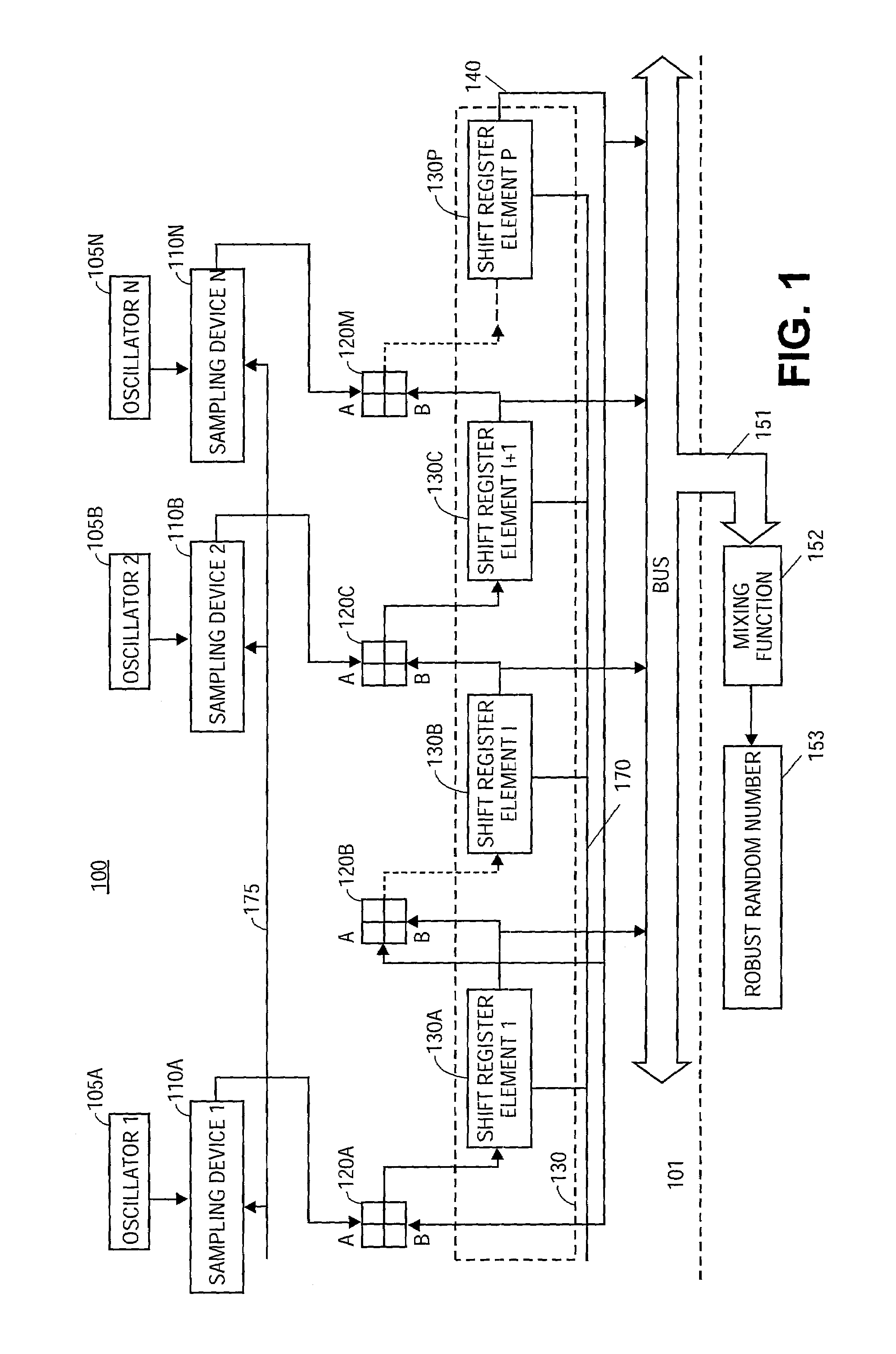
Random number generator
A random number generator comprising an oscillator with an output signal dependant upon a random source, a sampling device to sample the output signal from the oscillator to obtain a sampled oscillator output, and a fixed frequency clock driven linear feedback shift register (LFSR) communicatively coupled to the sampling device via a digital gate to receive the sampled oscillator output, and to provide a random number at an output of the LFSR. Additionally, the random number generator may comprise an optional mixing function communicatively coupled to the LFSR to read the random number, and to insert the random number into an algorithm to obtain a robust random number.
Owner:MARVELL ASIA PTE LTD
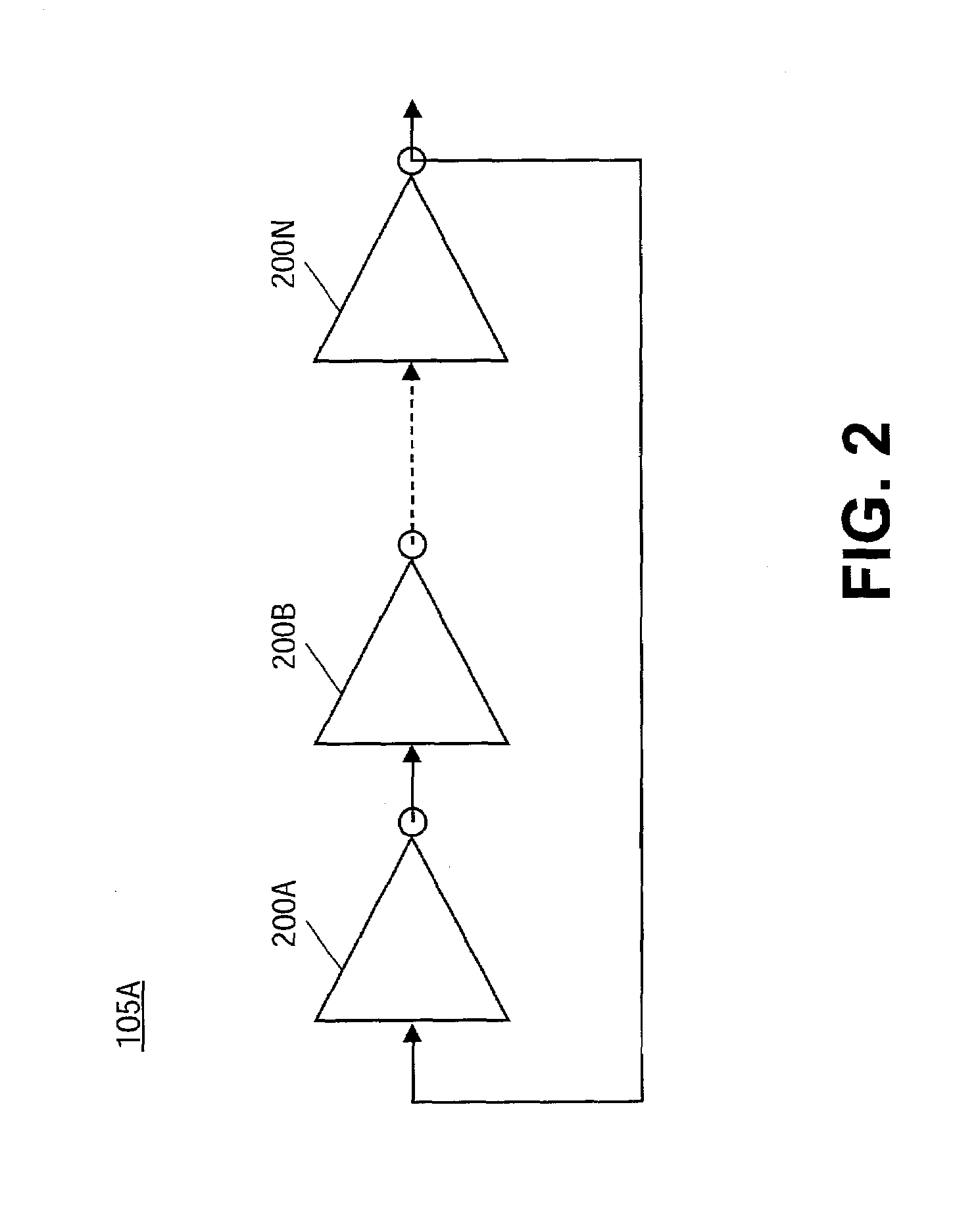
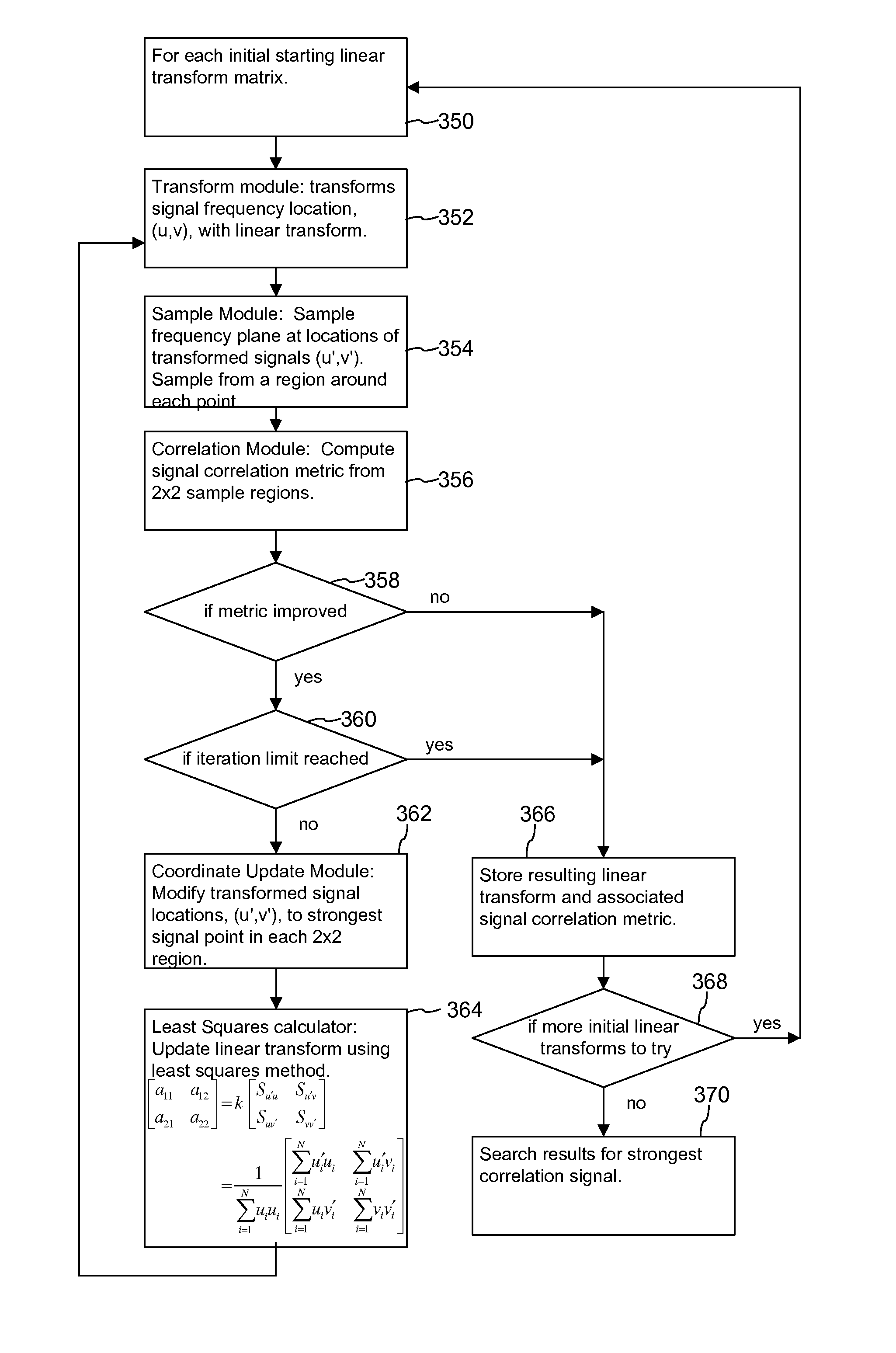
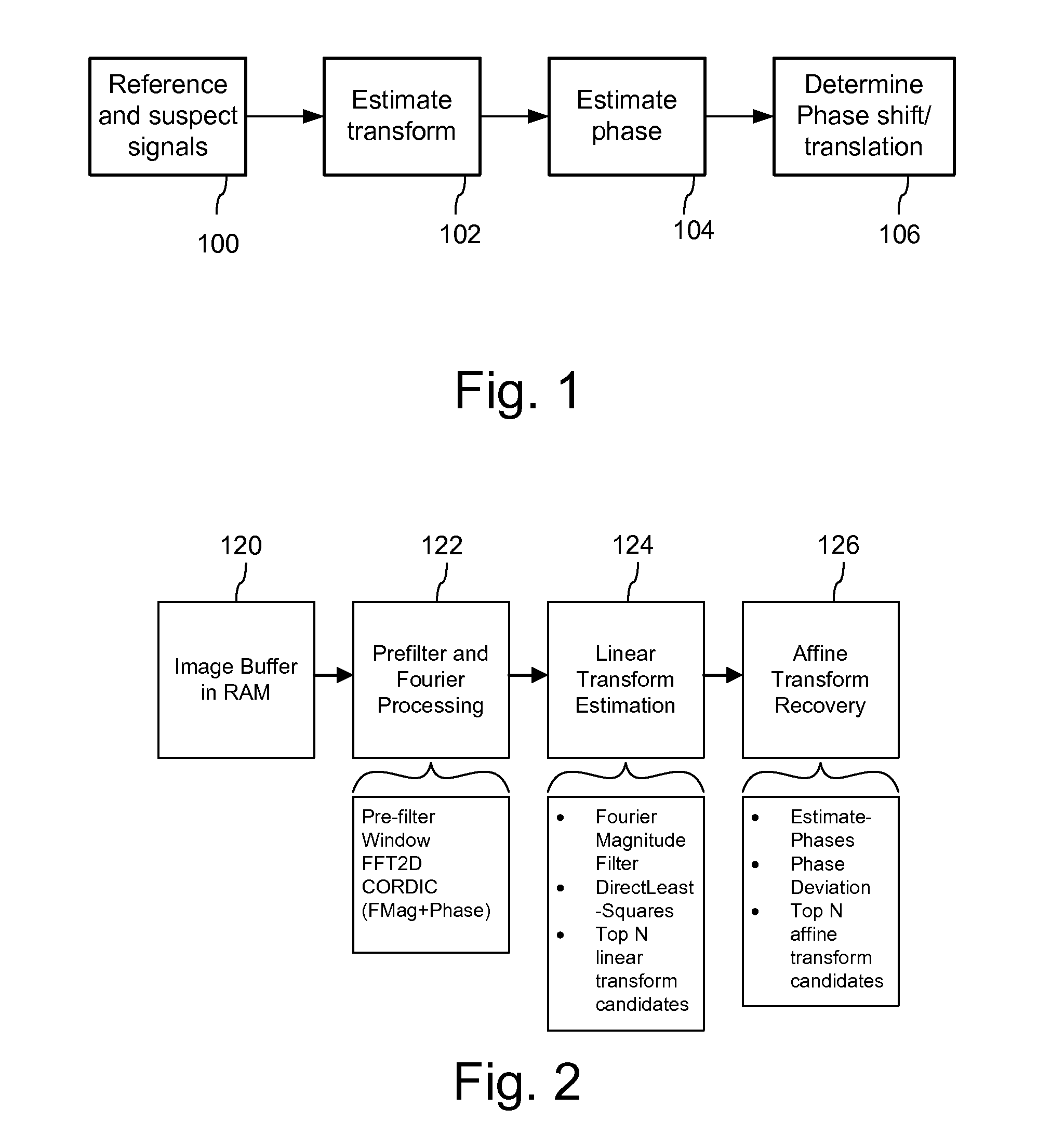
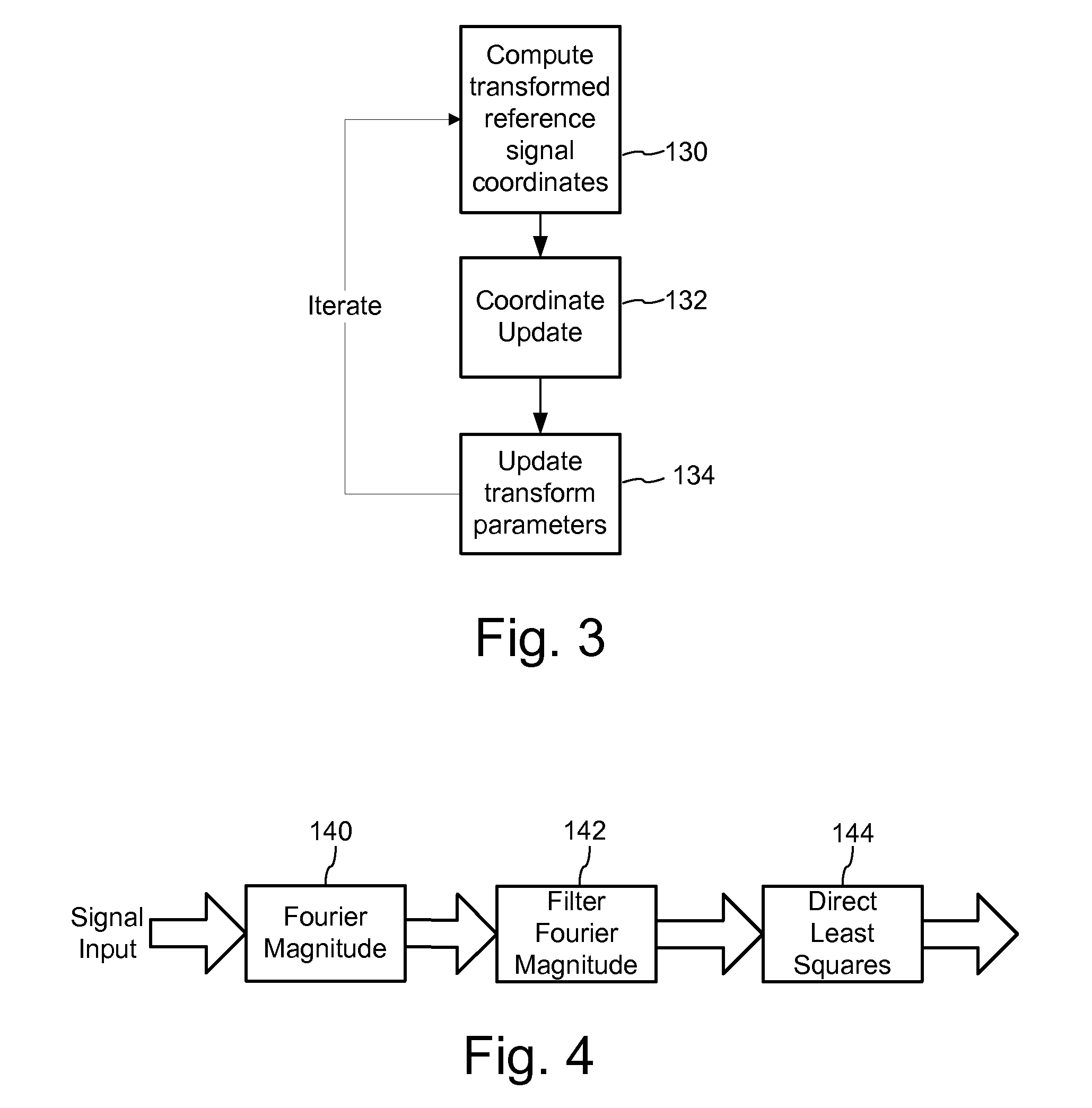
Signal Processors and Methods for Estimating Transformations Between Signals with Least Squares
ActiveUS20120078989A1Computed accurately and efficientlyAccurate detectionGeometric image transformationCharacter and pattern recognitionAlgorithmLeast squares
Signal processing devices and methods estimate transforms between signals using a least squares technique. From a seed set of transform candidates, a direct least squares method applies a seed transform candidate to a reference signal and then measures correlation between the transformed reference signal and a suspect signal. For each candidate, update coordinates of reference signal features are identified in the suspect signal and provided as input to a least squares method to compute an update to the transform candidate. The method iterates so long as the update of the transform provides a better correlation. At the end of the process, the method identifies a transform or set of top transforms based on a further analysis of correlation, as well as other results.
Owner:DIGIMARC CORP
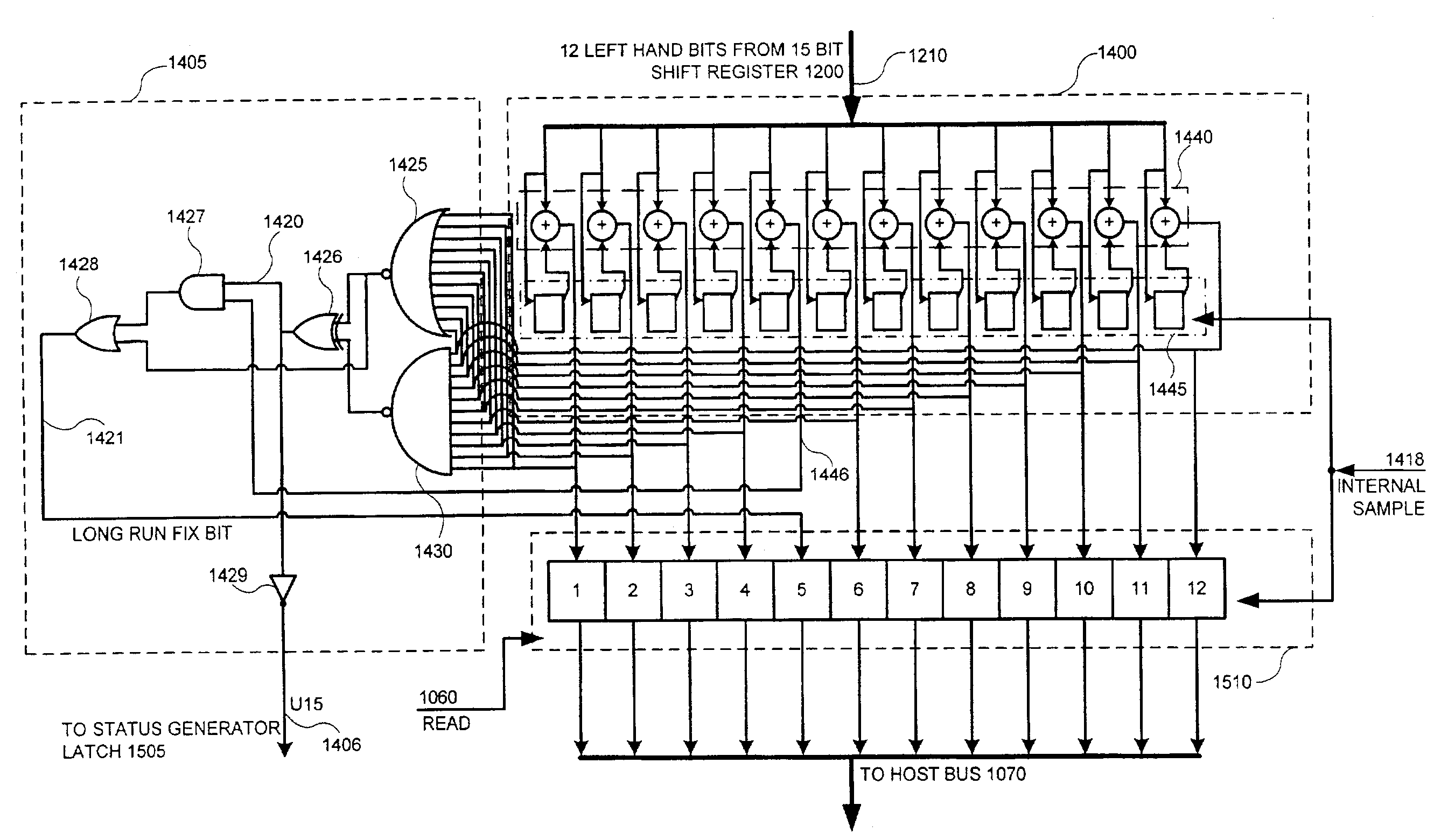
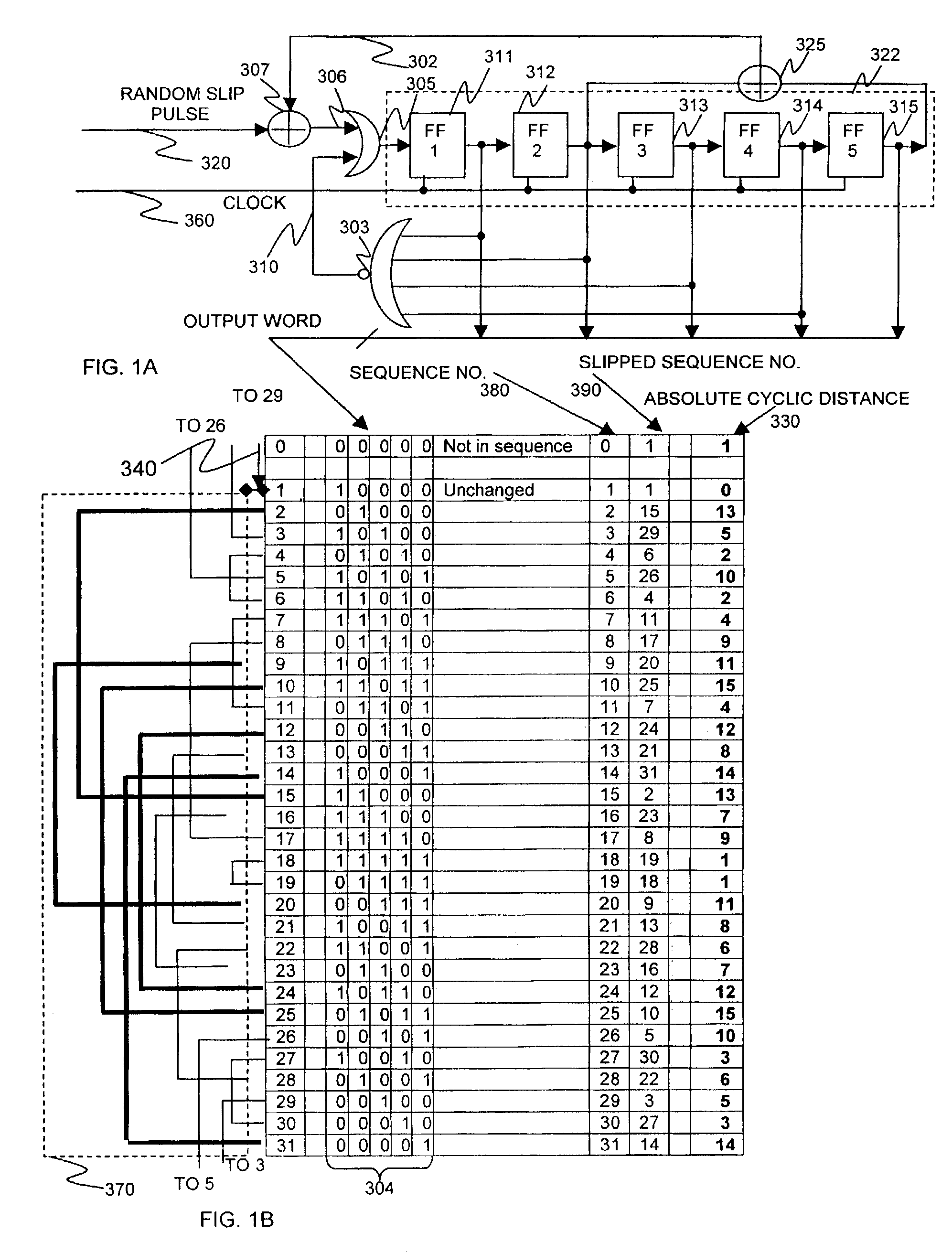
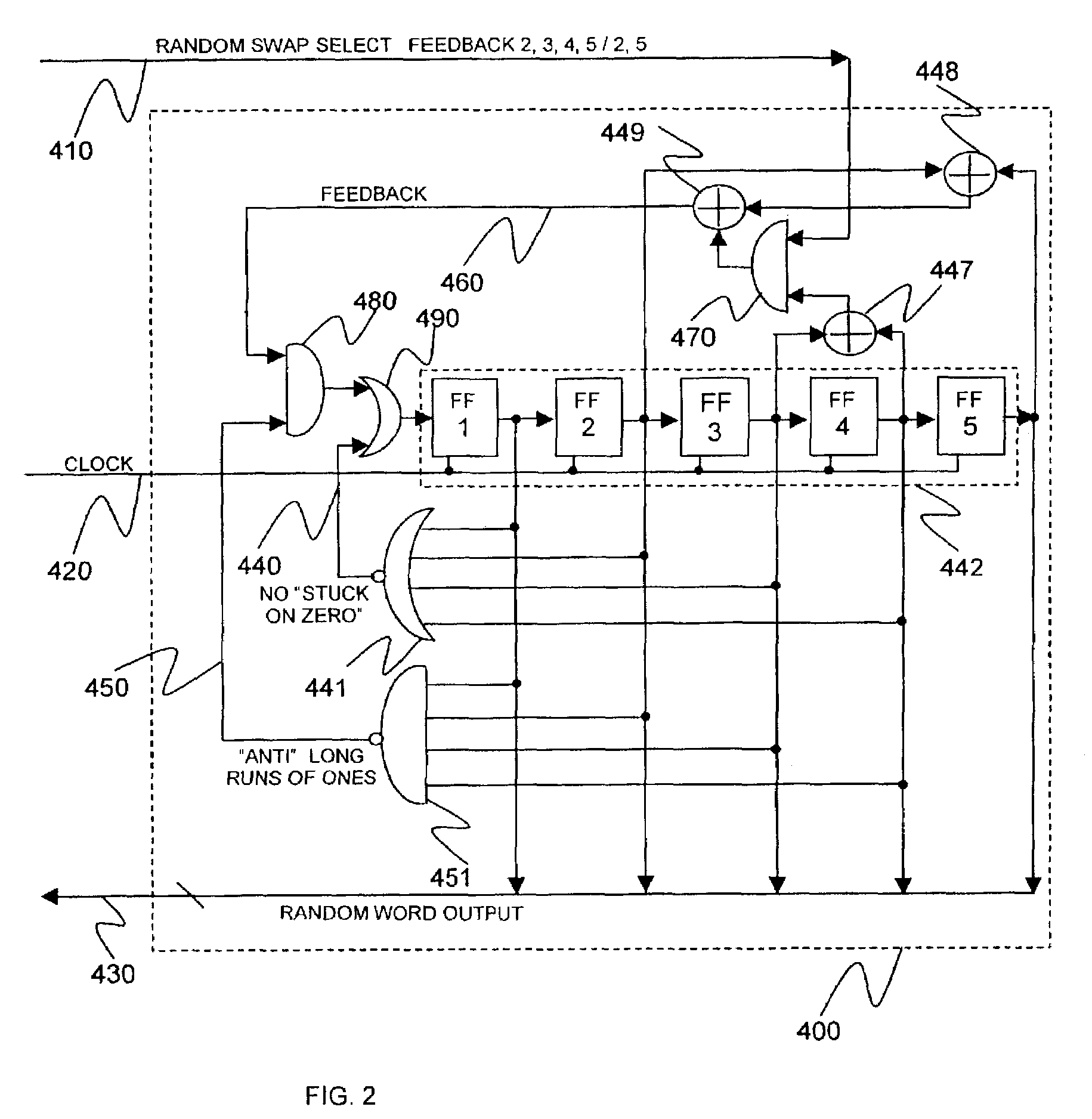
Random number slip and swap generators
InactiveUS7206797B2Increase unpredictabilityIncrease randomnessRandom number generatorsDigital function generatorsAlgorithmElectronic equipment
A microelectronic apparatus and method for generating random binary words including at least one clocked pseudorandom binary number sequence generator normally operative to generate a cyclic output sequence of binary numbers, each number including a string of binary symbols, the cyclic output sequence including a basic sequence which is generated repeatedly, at least one bit stream generator generating a clocked bit stream including a stream of binary symbols of a first type occasionally interrupted by a binary symbol of a second type, wherein a first varying time interval between the occasional interruptions is intractably correlated to the output sequence of the number sequence generator, wherein each occurrence of an interruption of the stream of binary symbols of the first type by a binary symbol of the second type causes a pseudorandom modification of the cyclic output sequence of the number sequence generator and a sampling device operative to sample the cyclic output sequence of binary numbers thereby to generate a sampled output sequence including at least one sampled binary word.
Owner:SANDISK IL
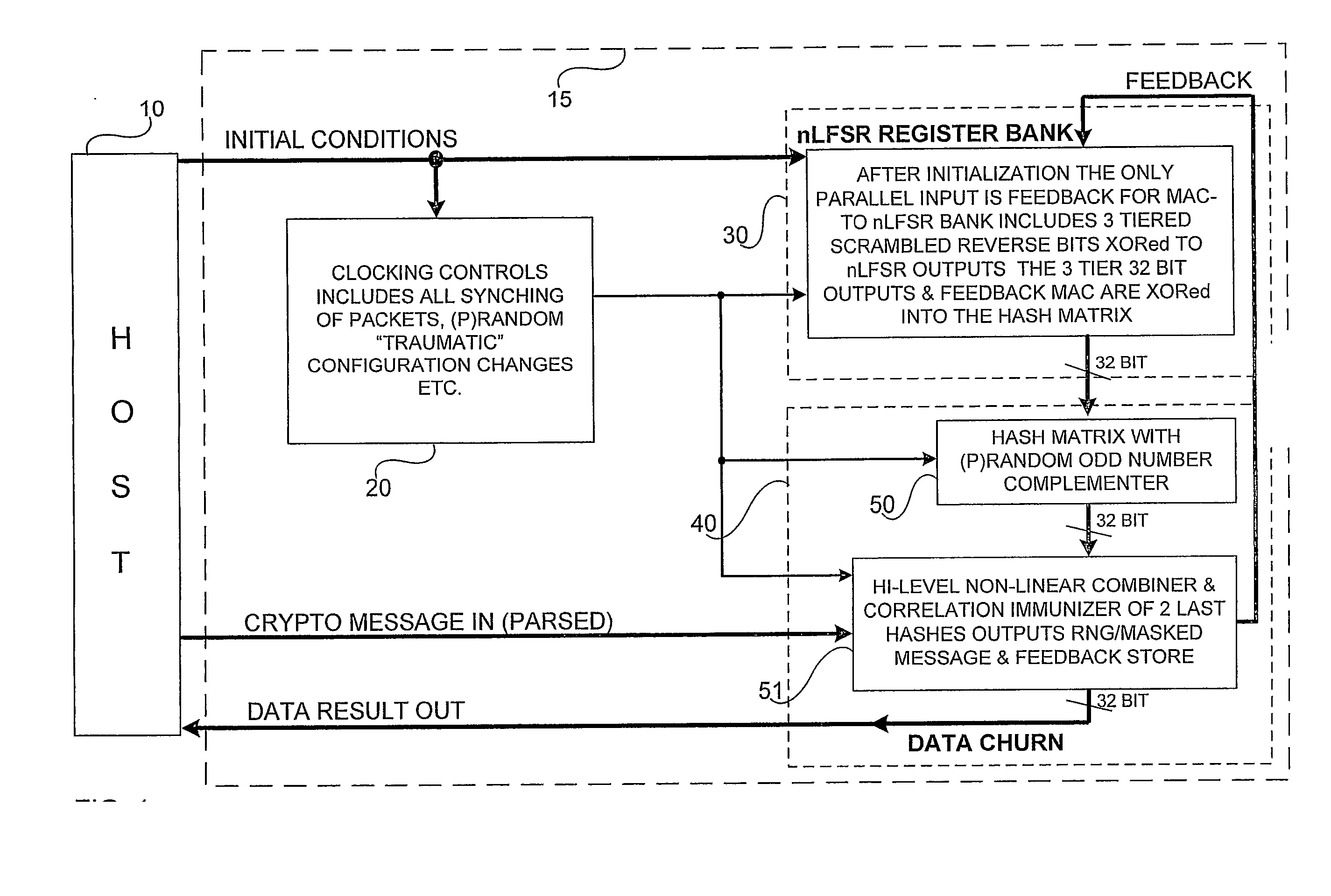
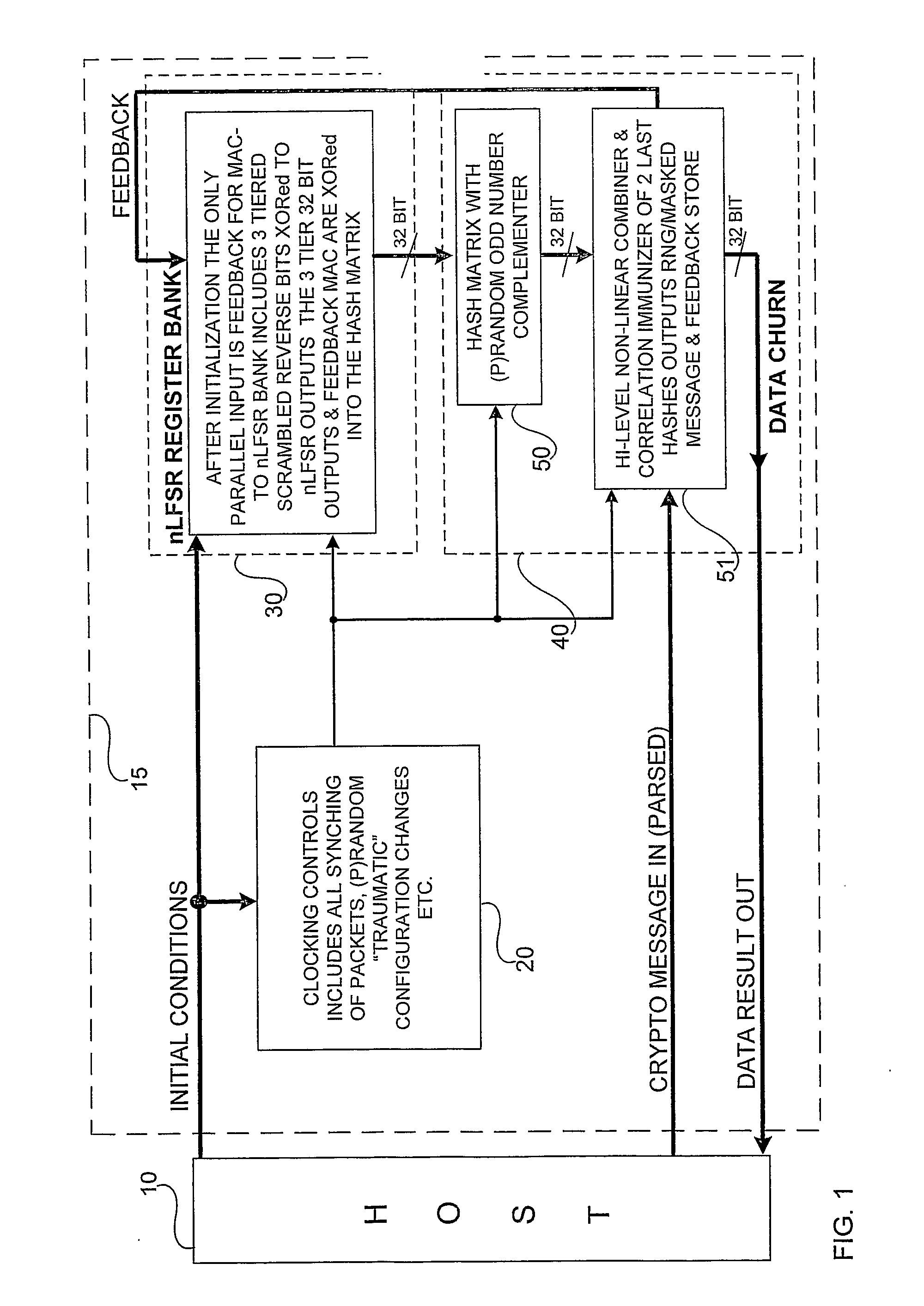
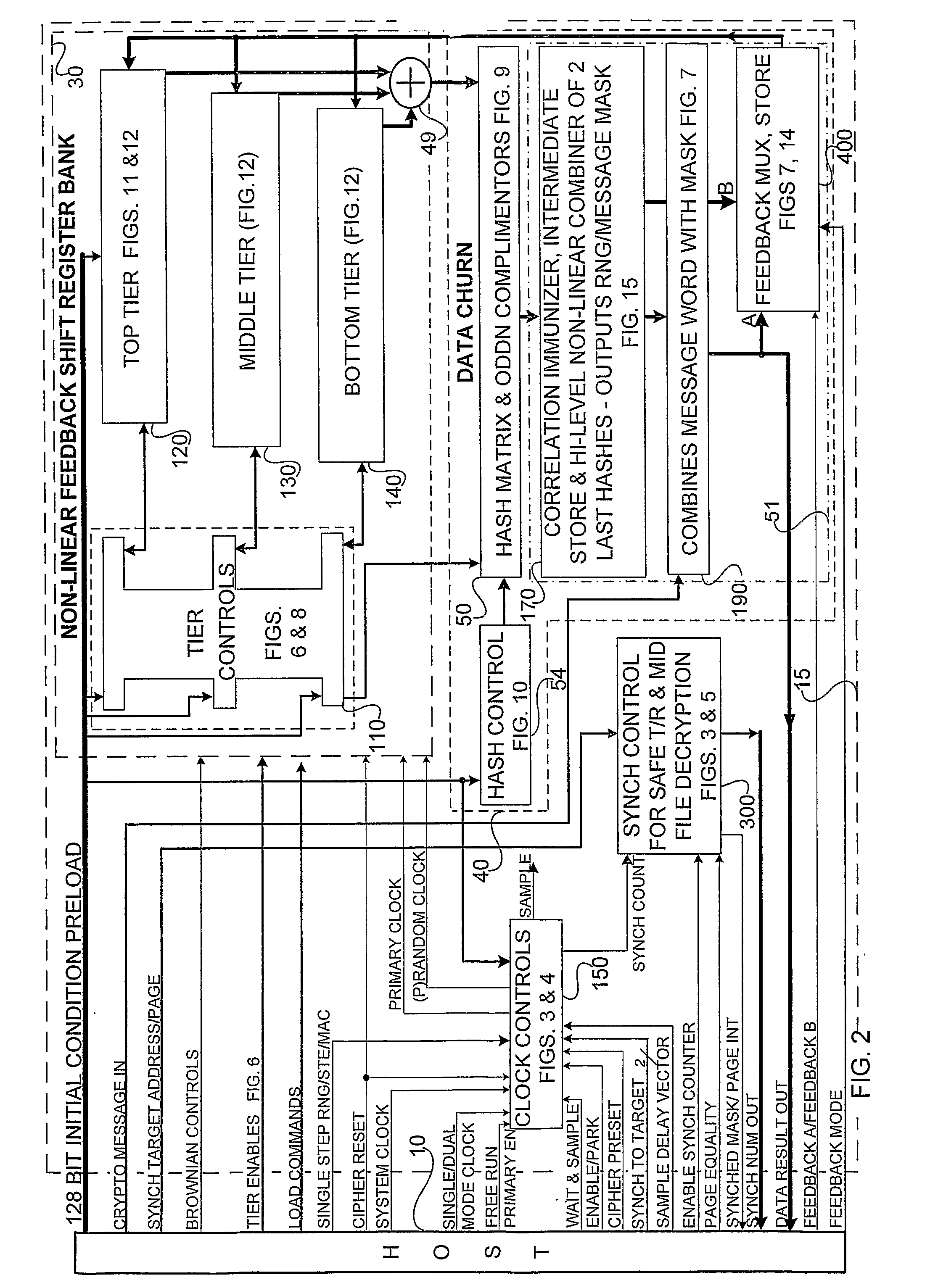
Accelerated Throughtput Synchronized Word Stream Cipher, Message Authenticator and Zero-Knowledge Output Random Number Generator
ActiveUS20070244951A1Small loss of entropyNecessary numberSynchronising transmission/receiving encryption devicesRandom number generatorsComputer hardwareFrame sequence
Systems and methods are disclosed, especially designed for very compact hardware implementations, to generate random number strings with a high level of entropy at maximum speed. For immediate deployment of software implementations, certain permutations have been introduced to maintain the same level of unpredictability which is more amenable to hi-level software programming, with a small time loss on hardware execution; typically when hardware devices communicate with software implementations. Particular attention has been paid to maintain maximum correlation immunity, and to maximize non-linearity of the output sequence. Good stream ciphers are based on random generators which have a large number of secured internal binary variables, which lead to the page synchronized stream ciphering. The method for parsed page synchronization which is presented is especially valuable for Internet applications, where occasionally frame sequences are often mixed. The large number of internal variables with fast diffusion of individual bits wherein the masked message is fed back into the machine variables is potentially ideal for message authentication procedures.
Owner:FORTRESS GB
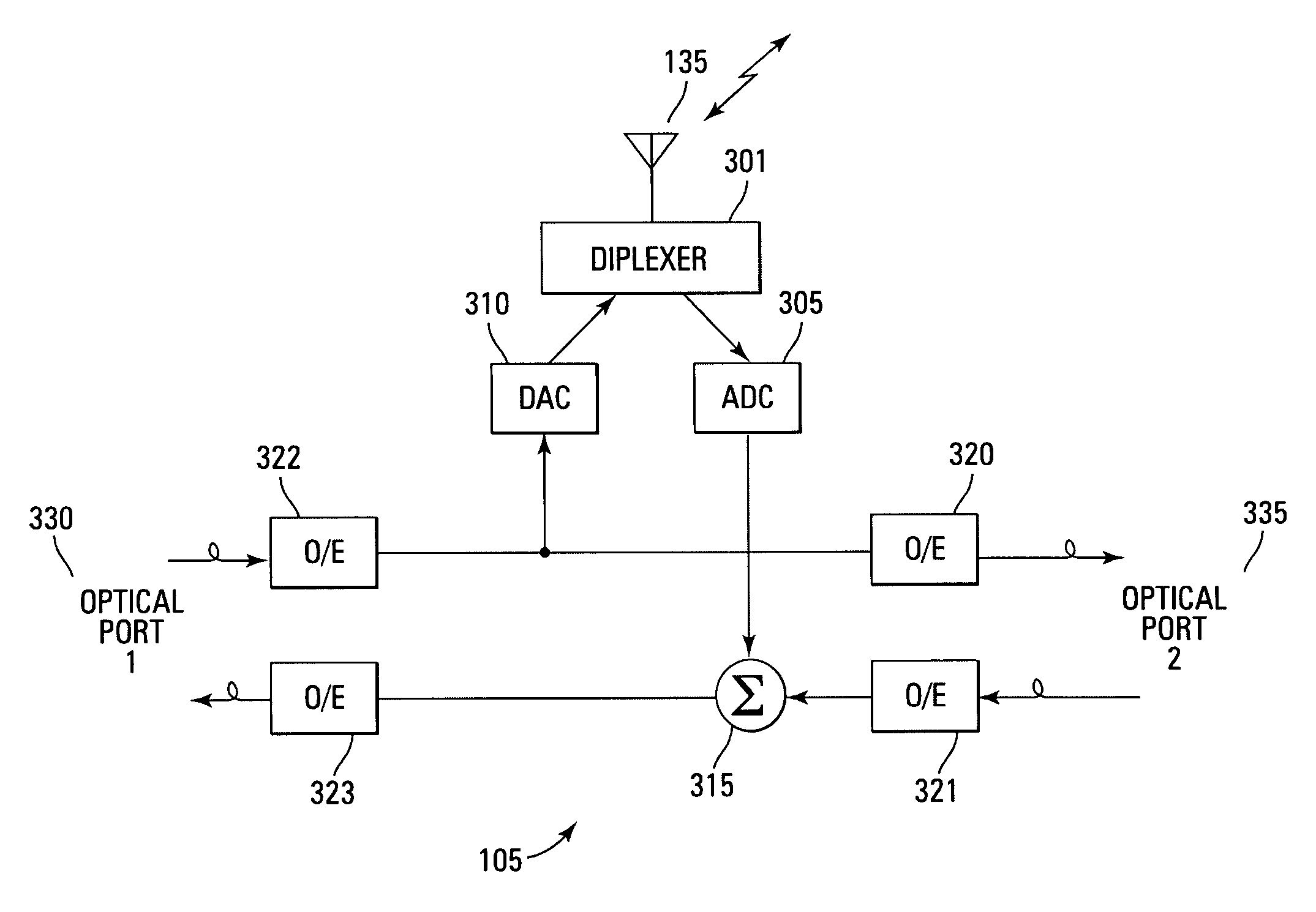
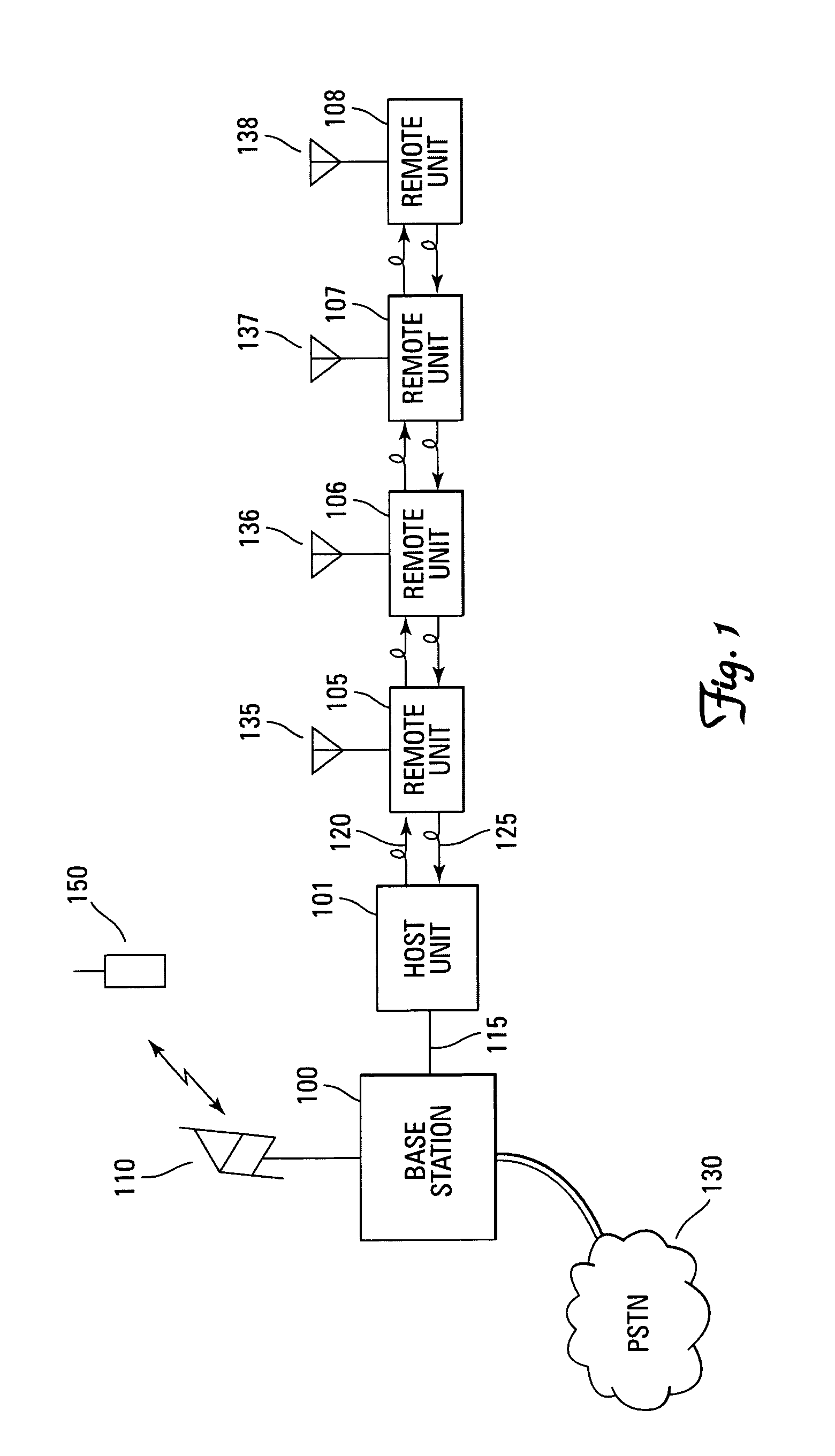
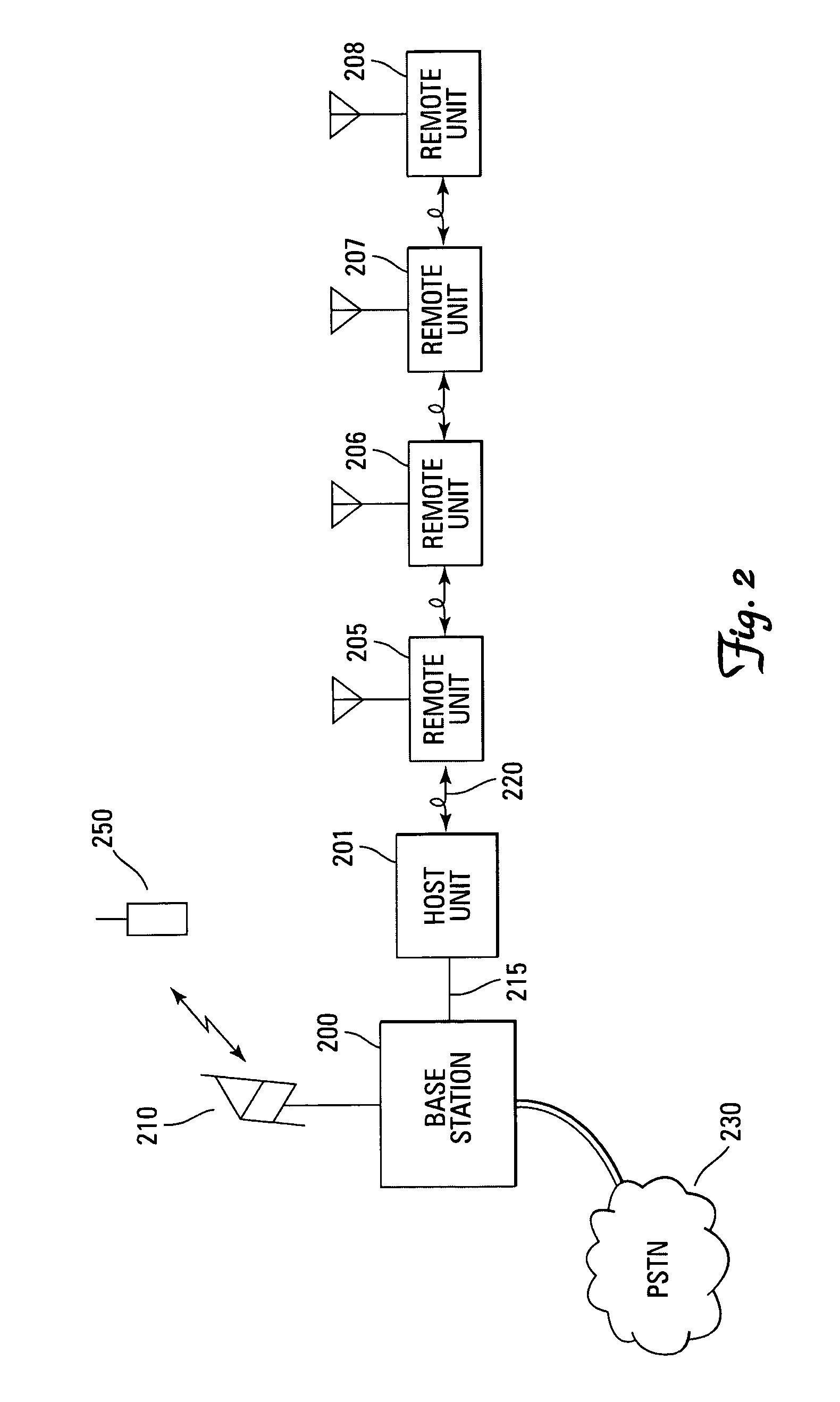
Distributed digital antenna system
An optical medium, such as fiber, is tapped to provide an antenna port wherever radio service coverage is desired. Each antenna port is a bi-directional remote unit that receives a digital optical signal from a host unit and transforms the signal to a radio frequency signal for transmission by the remote unit. The remote unit receives radio frequency signals that are converted to digital signals and summed with signals from other remote units and converted to an optical signal for transmission to the host unit.
Owner:COMMSCOPE TECH LLC
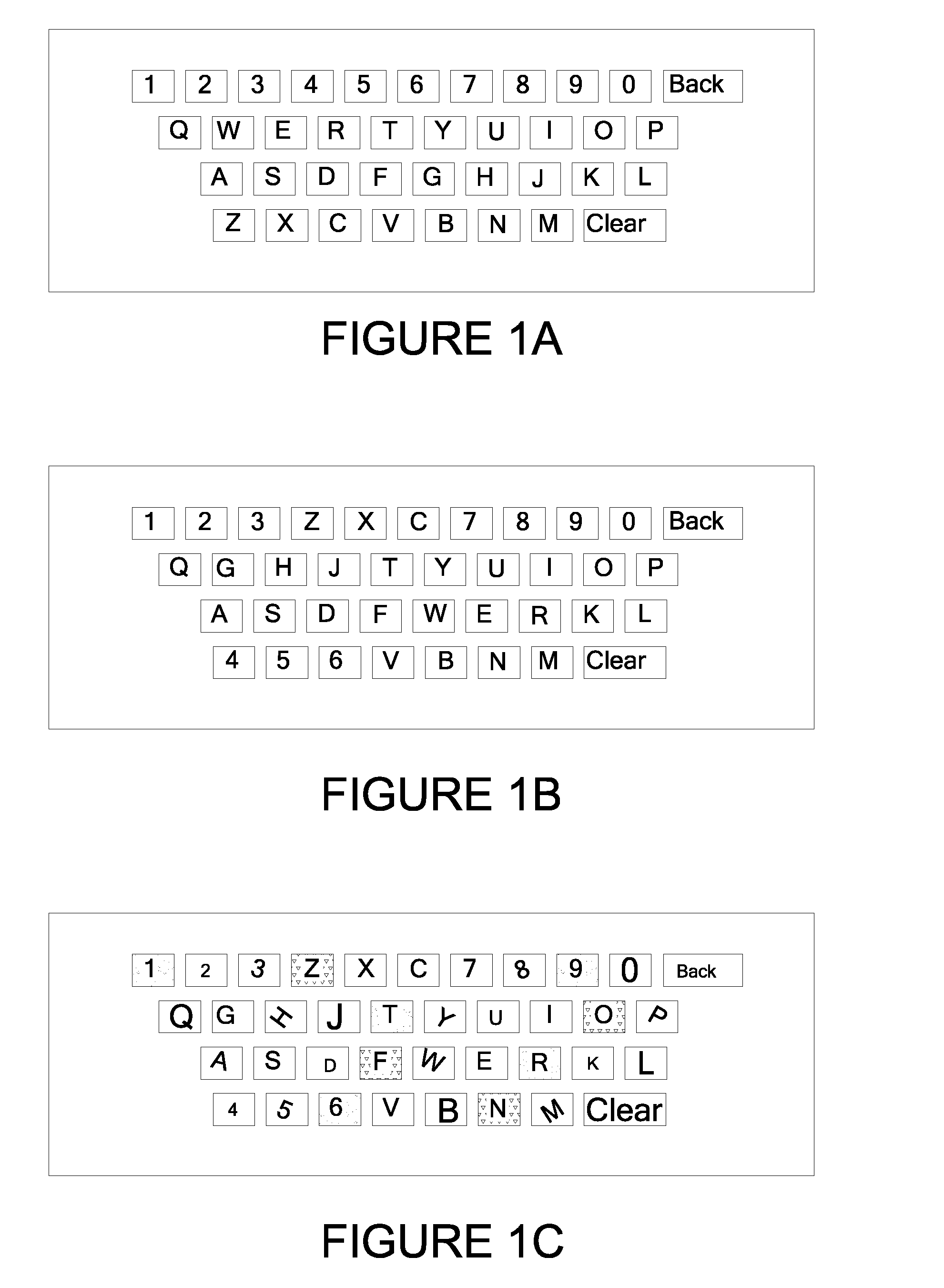
System and Method for Generating and Displaying a Keyboard Comprising a Random Layout of Keys
InactiveUS20090044282A1Random number generatorsUser identity/authority verificationUser inputTheoretical computer science
Systems and methods for generating and displaying a keyboard comprising a random layout of keys are described here. One embodiment includes displaying a keyboard comprising a random layout of keys, to receive a user entered key phrase to be entered to gain access to secure data, and receiving the user entered key phrase by the user selecting keys of the keyboard via a pointing input device. The displaying includes, individually mapping keys of the keyboard to a separate value within a first value range, selecting a key for the keyboard based on the random value generated, and repeating the generating the random value and selecting a key for the keyboard based on the random value to select a remainder of keys for generating the random layout of keys for the keyboard.
Owner:MCM PORTFOLIO LLC
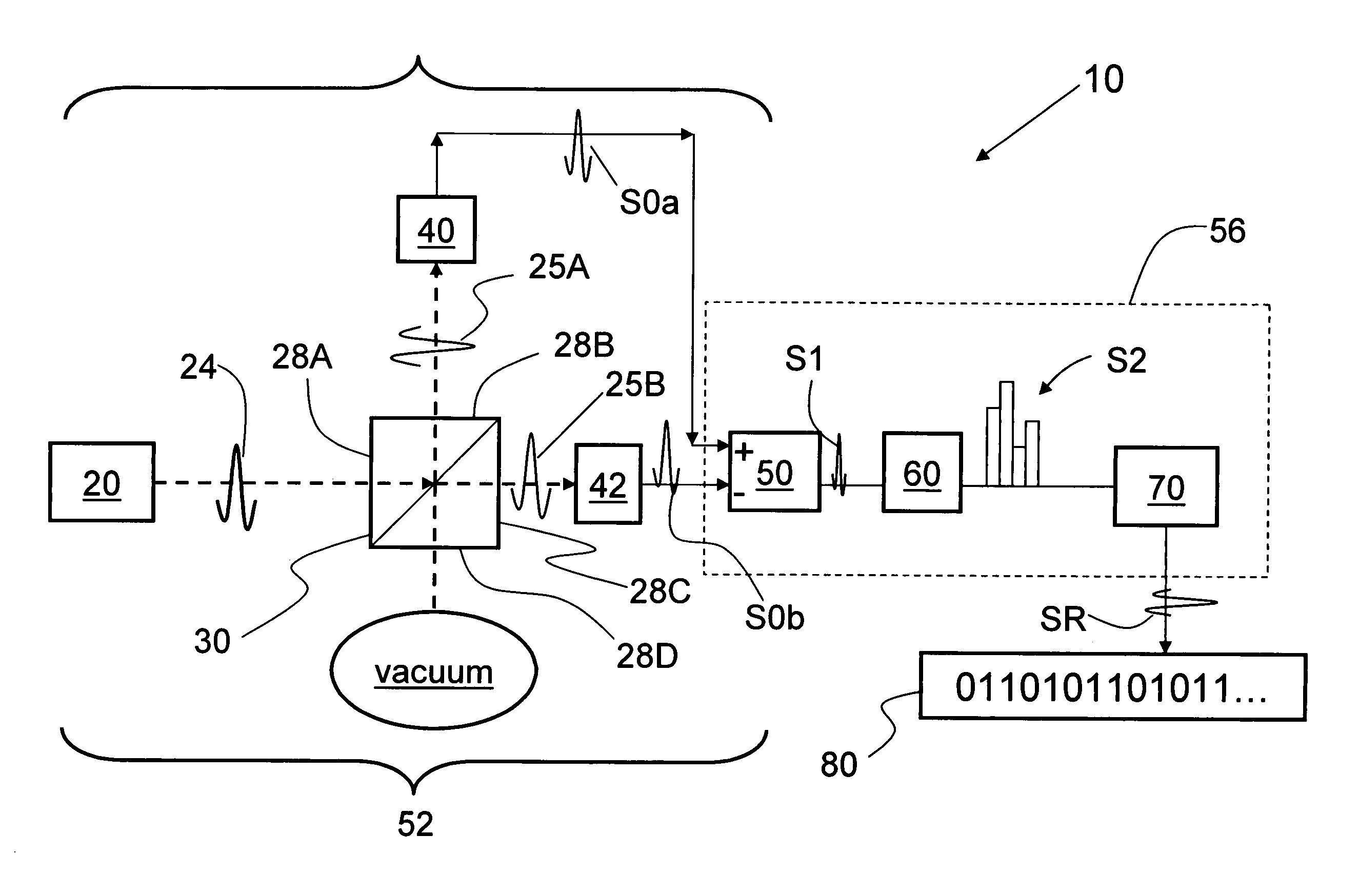
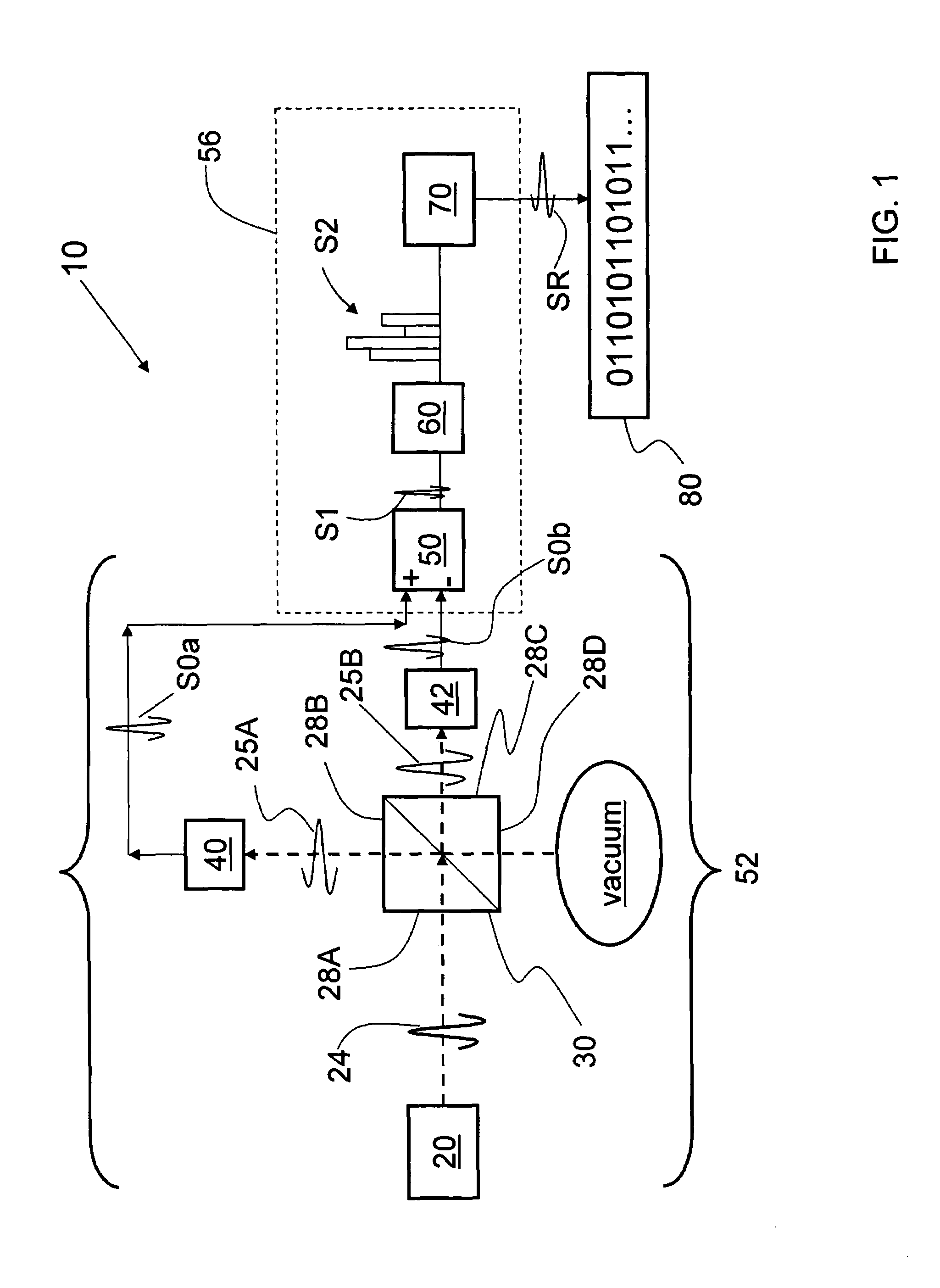
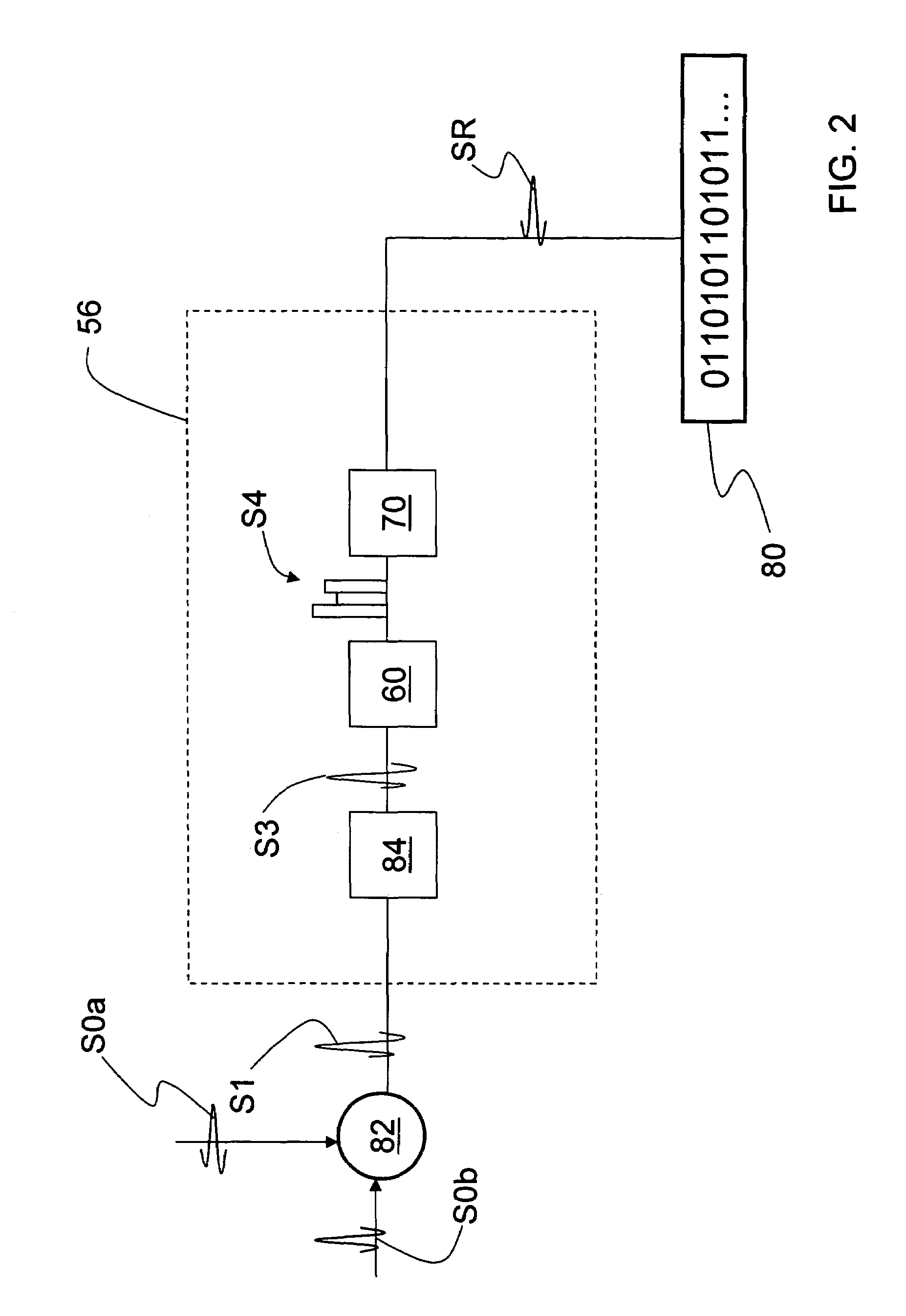
Quantum noise random number generator
A quantum noise random number generator system that employs quantum noise from an optical homodyne detection apparatus is disclosed. The system utilizes the quantum noise generated by splitting a laser light signal using a beamsplitter having four ports, one of which receives one of which is receives the laser light signal, one of which is connected to vacuum, and two of which are optically coupled to photodetectors. Processing electronics process the difference signal derived from subtracting the two photodetector signals to create a random number sequence. Because the difference signal associated with the two photodetectors is truly random, the system is a true random number generator.
Owner:MAGIQ TECH INC
Cryptographic key, encryption device, encryption/decryption device, cryptographic key management device, and decryption device
ActiveUS7269258B2Random number generatorsSecuring communication by chaotic signalsComputer hardwareCryptographic nonce
Owner:YAZAKI CORP
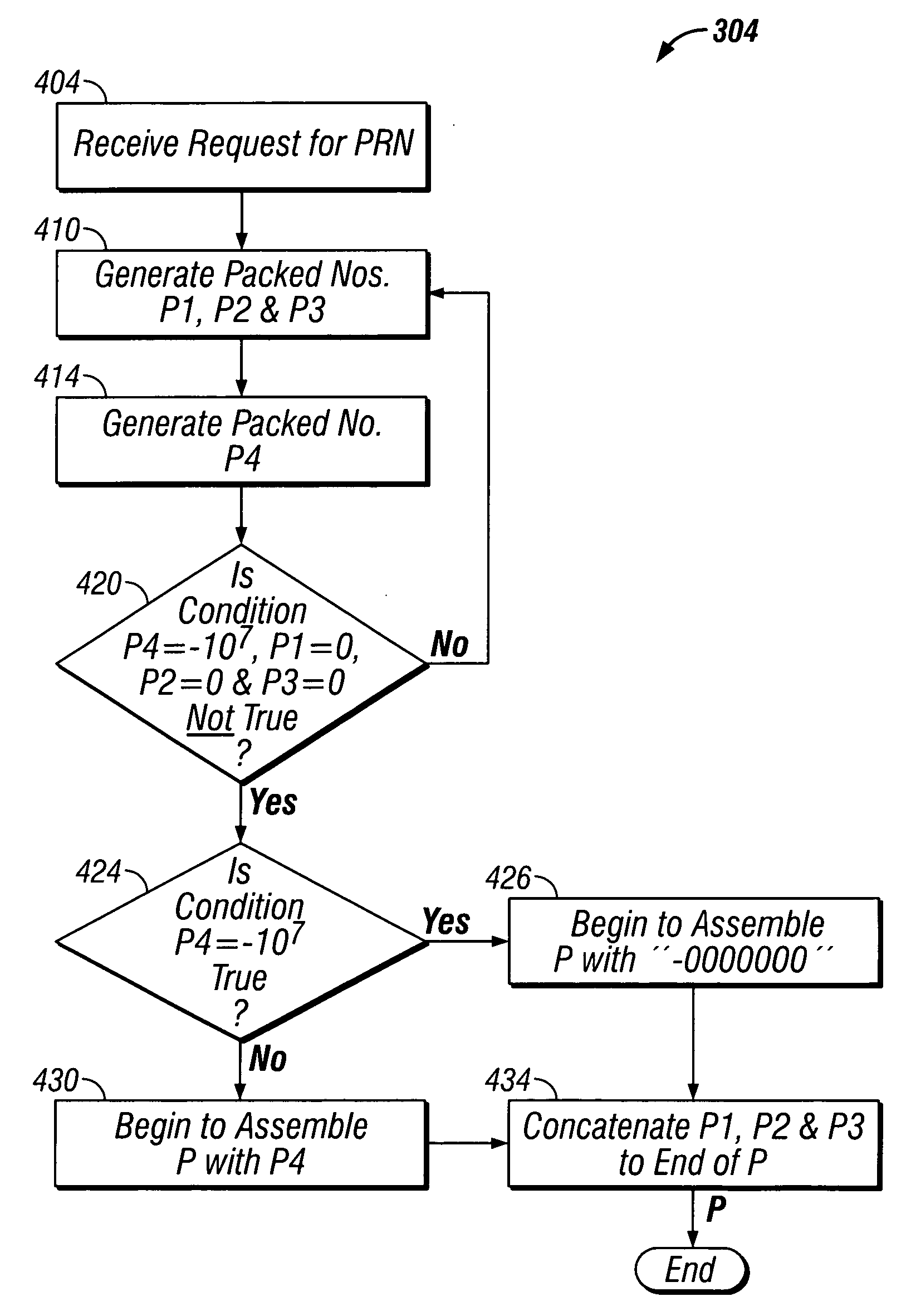
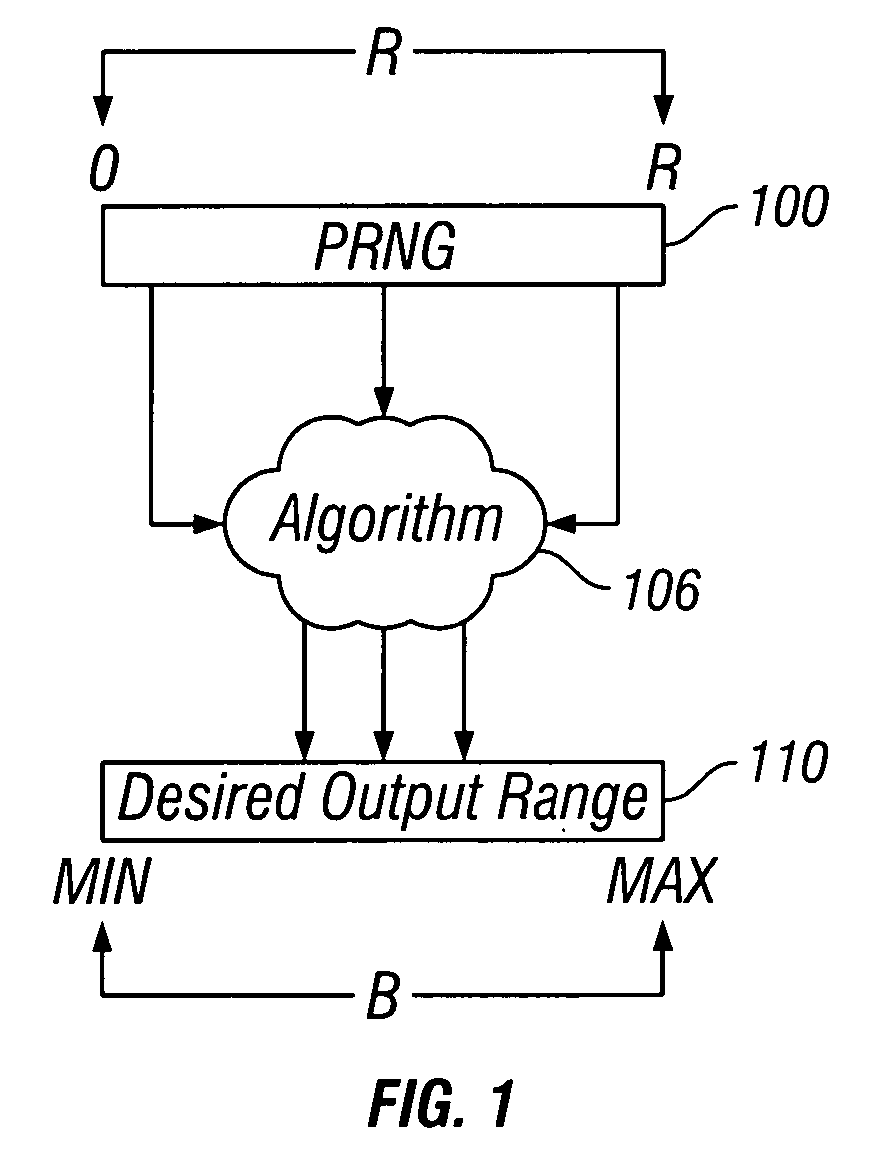
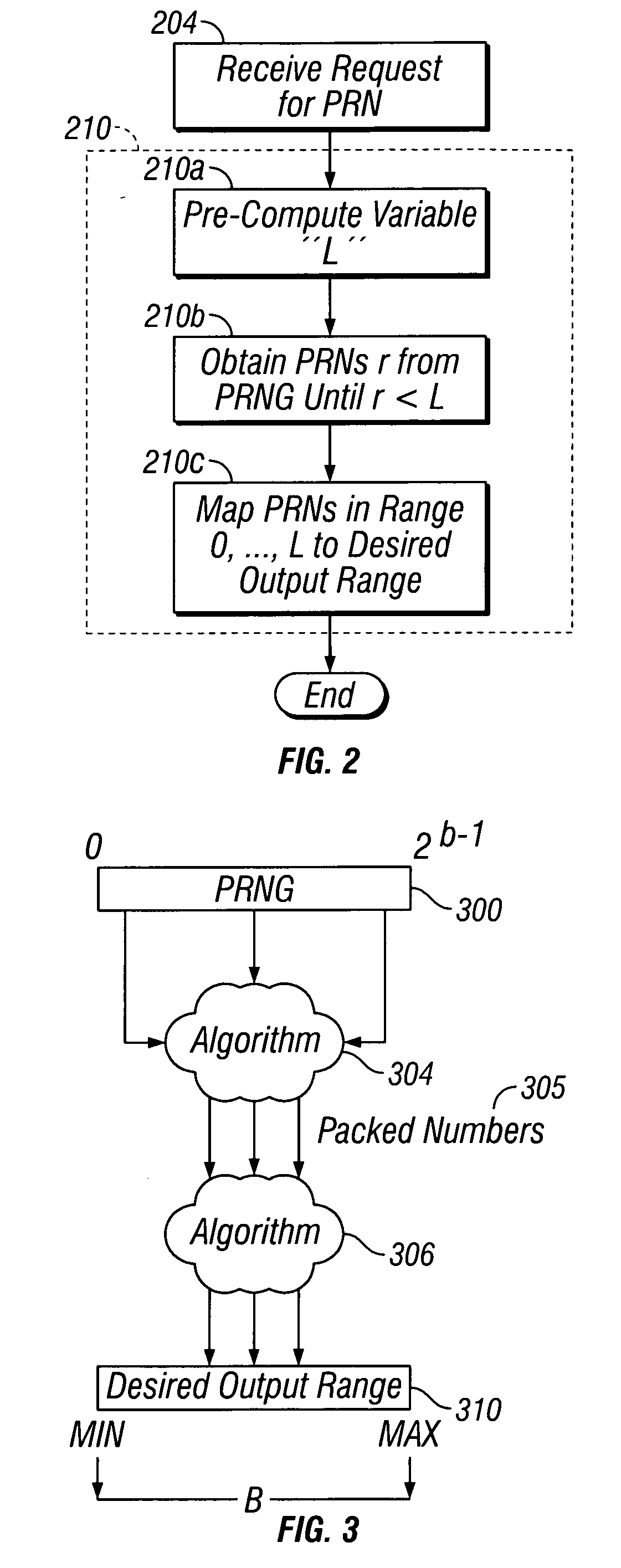
Mapping pseudo-random numbers to predefined number ranges
ActiveUS20050050121A1Low costDiminish pseudo randomnessRandom number generatorsDigital function generatorsSmall targetComputer science
Pseudo-random numbers (PRNs) generated by a PRN generator are mapped to predefined number ranges or target ranges. The target range may be smaller or larger than the range of the PRN generator. Mapping to a smaller target range may include generating PRNs (e.g., integers) from a particular bit-input stream (e.g., 32-bit) having a uniform distribution across the range of numbers; selecting an optimal subset of the generated PRNs to map; and mapping the selected PRNs to a corresponding number in a target range such that the mapped numbers are uniformly distributed across the target range. Mapping to a larger target range may include generating uniformly distributed PRNs; applying a generation function to the PRNs to generate uniformly distributed packed numbers; and applying a mapping function to map selected packed numbers to the target range such that the mapped numbers are uniformly distributed.
Owner:SAP AG
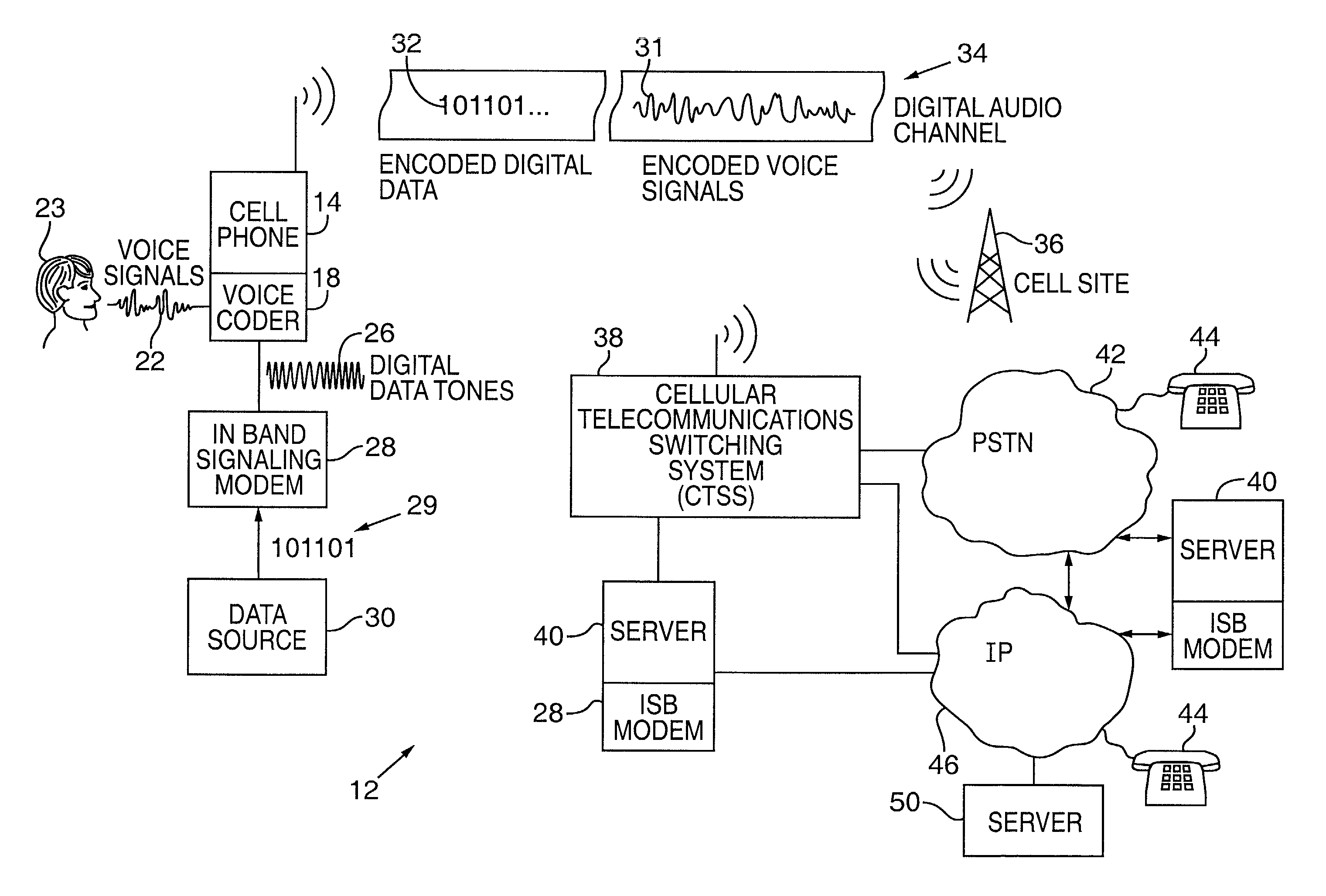
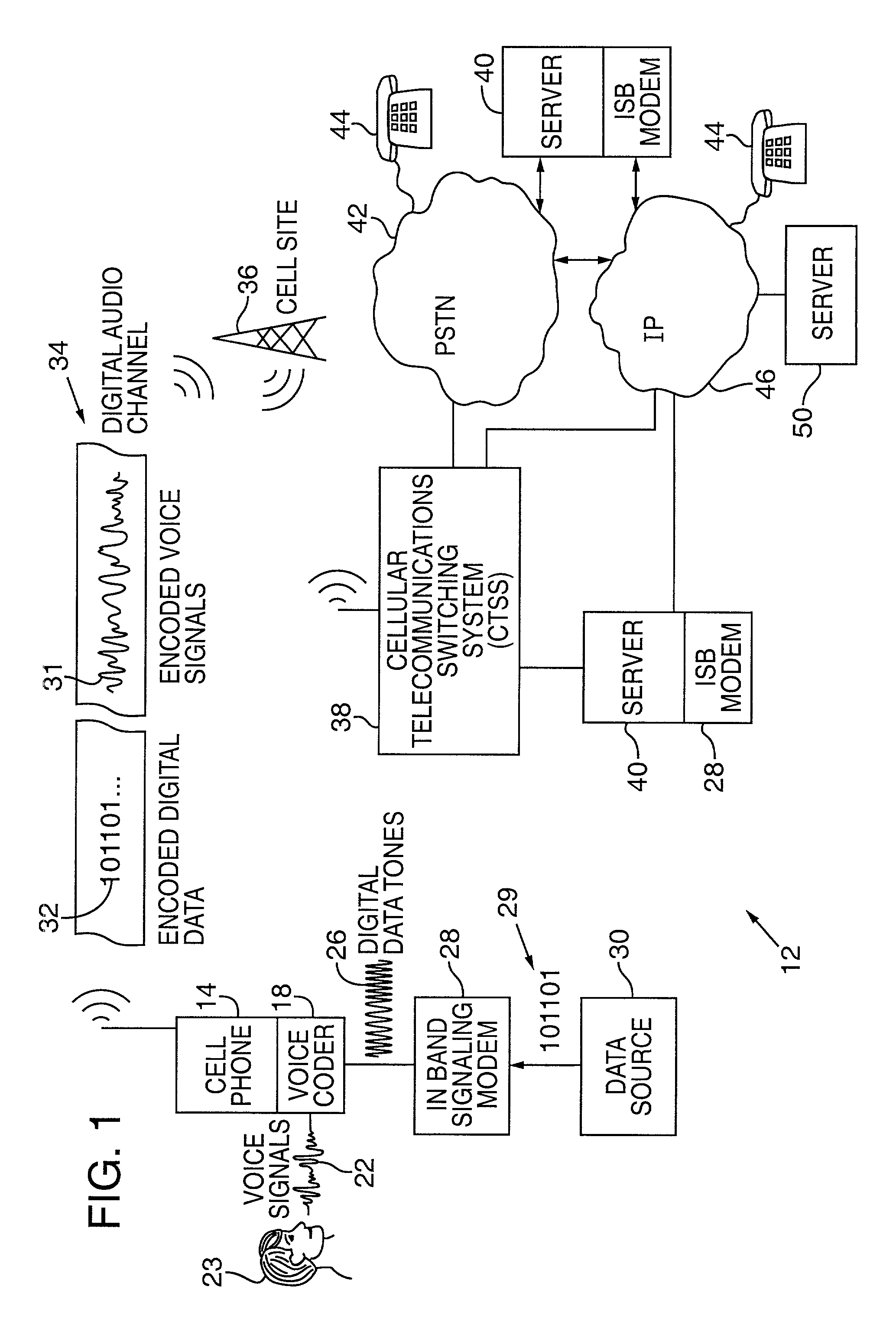
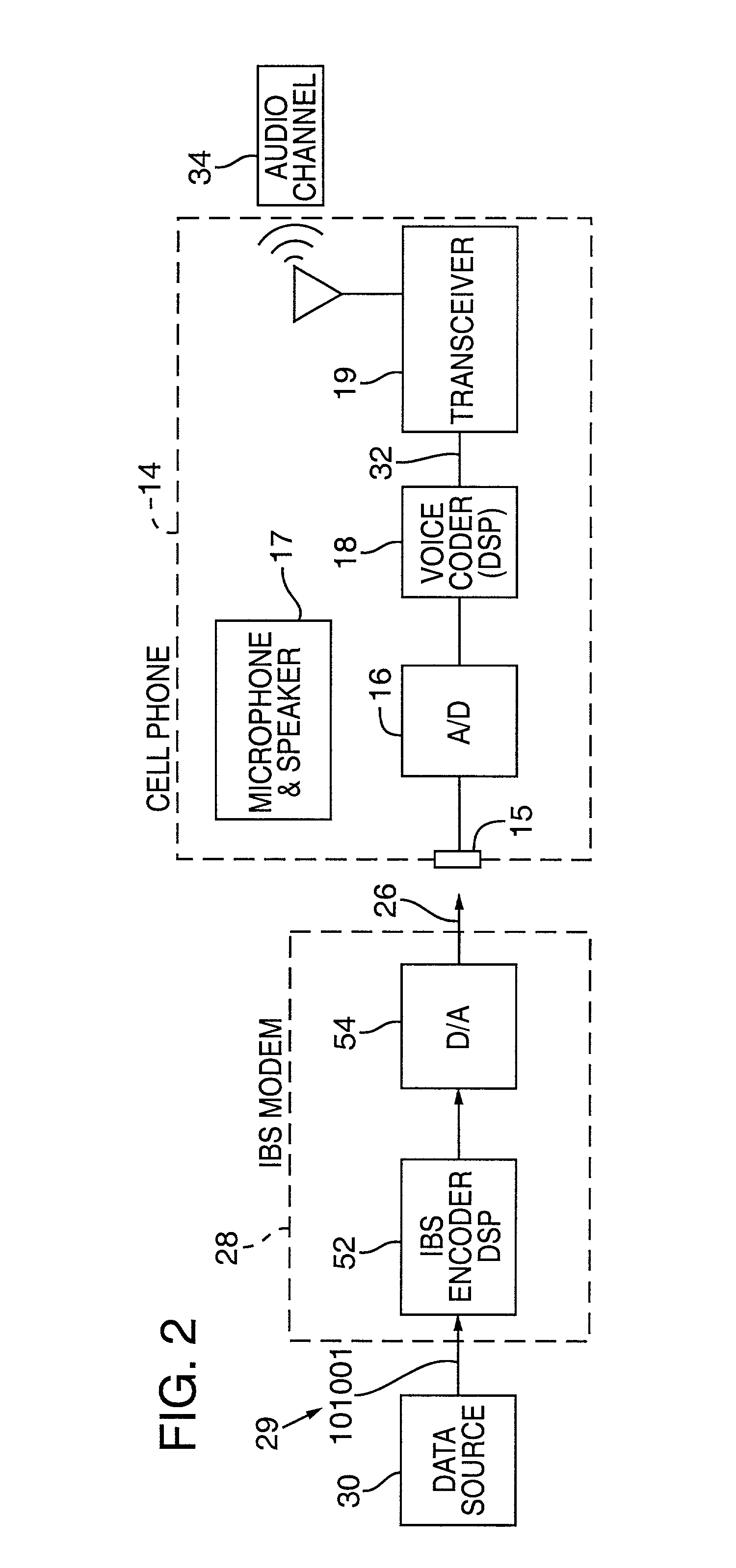
Cellular telephone having improved in-band signaling for data communications over digital wireless telecommunications networks
InactiveUS7221669B2Road vehicles traffic controlPosition fixationDigital dataTelecommunications link
Owner:AIRBIQUITY INC
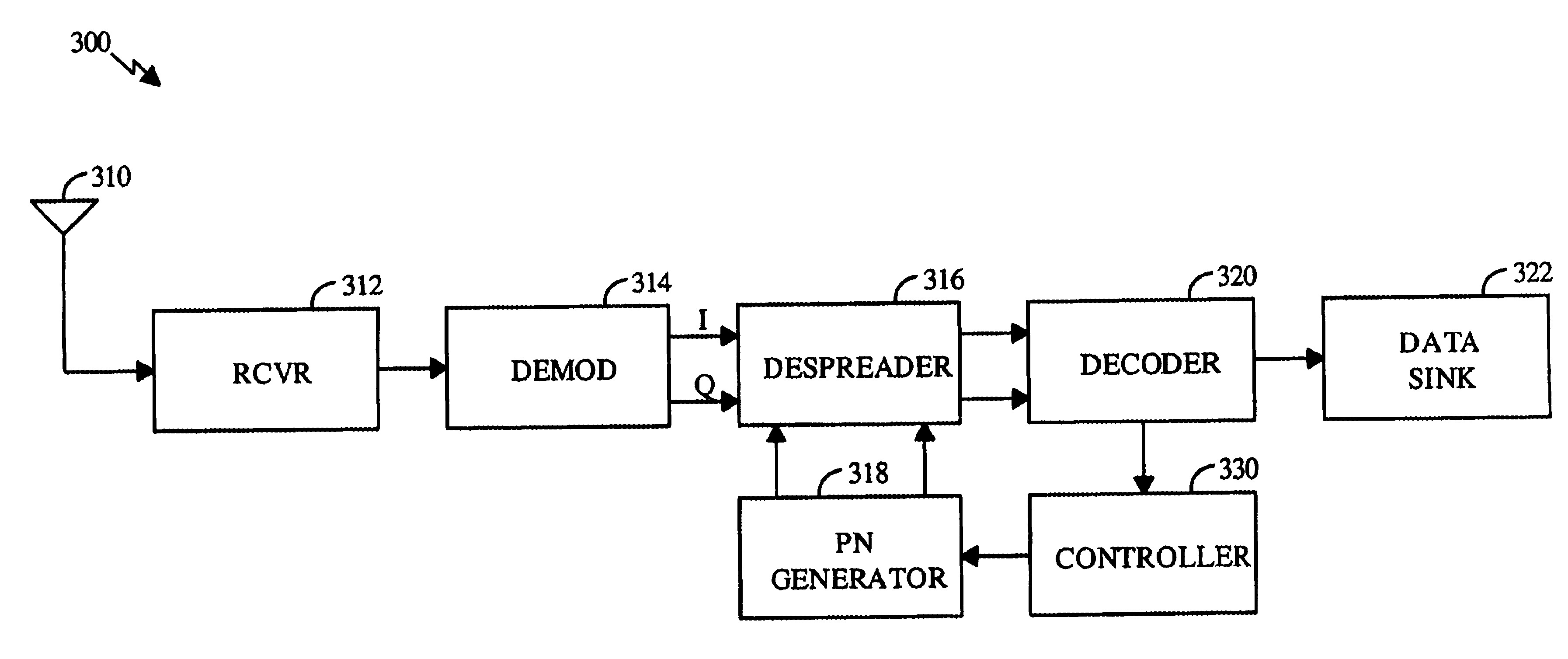
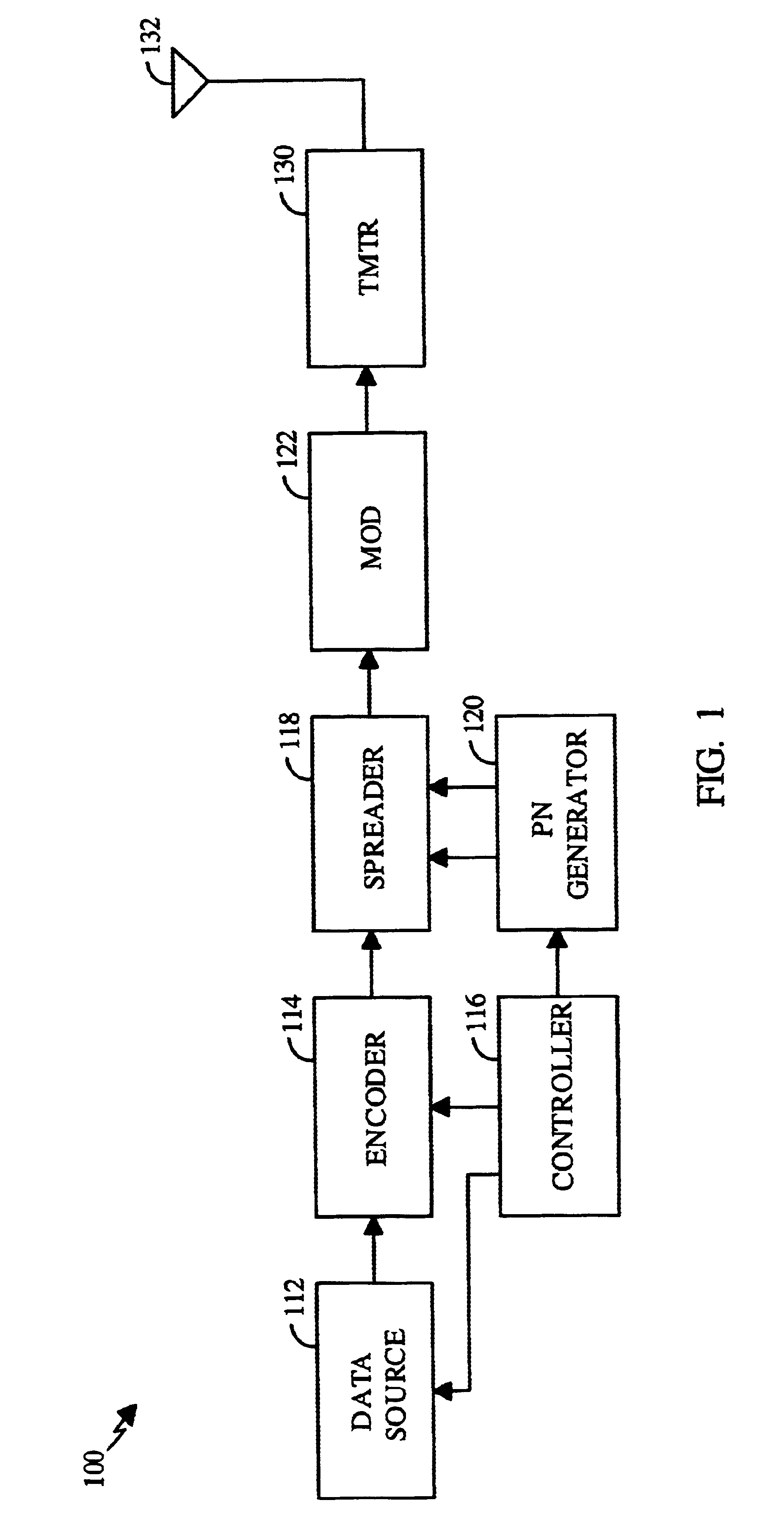
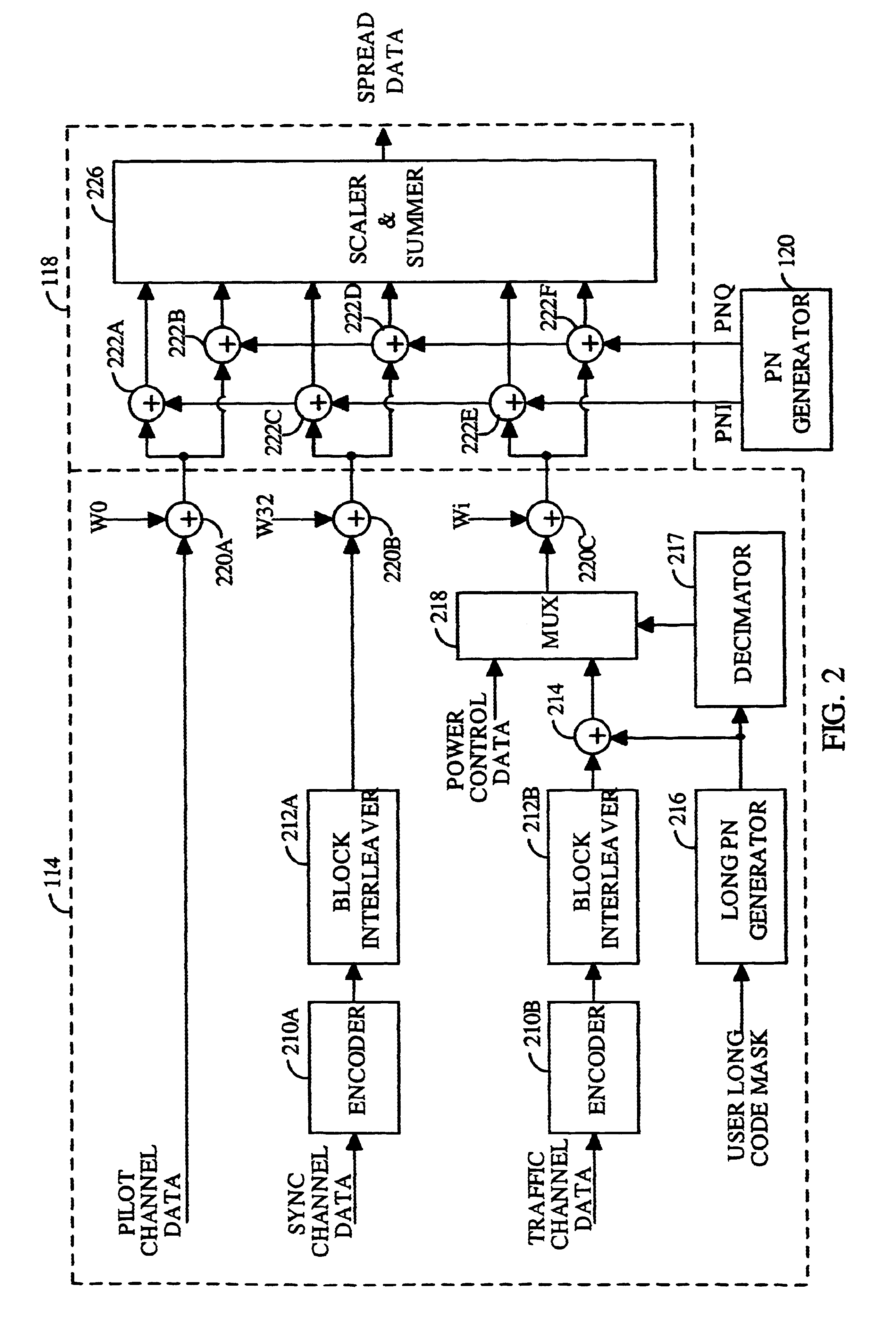
PN generators for spread spectrum communications systems
InactiveUS6661833B1Random number generatorsMultiplex code generationCommunications systemMobile station
Techniques to improve the acquisition process in a spread spectrum environment. The signals from different CDMA systems are spread with different sets of PN sequences, with the PN sequences in each set being uncorrelated to the PN sequences in the other sets. By using uncorrelated PN sequences, the likelihood of detecting a pilot signal from an undesired system is reduced or minimized, and the mean time to acquisition of the pilot signal from the desired system is improved. The mobile station can attempt to acquire the pilot signal by processing the received signal with a first set of PN sequences corresponding to a first hypothesis of the particular signal being acquired. If acquisition of the pilot signal fails, a second set of PN sequences corresponding to a second hypothesis is selected and used to process the received signal. The PN sequences in the second set are uncorrelated to the PN sequences in the first set. The PN sequences for the first set can be generated based on the characteristic polynomials defined by IS-95-A, and the PN sequences for the second set can be the reverse of the PN sequences for the first set.
Owner:QUALCOMM INC
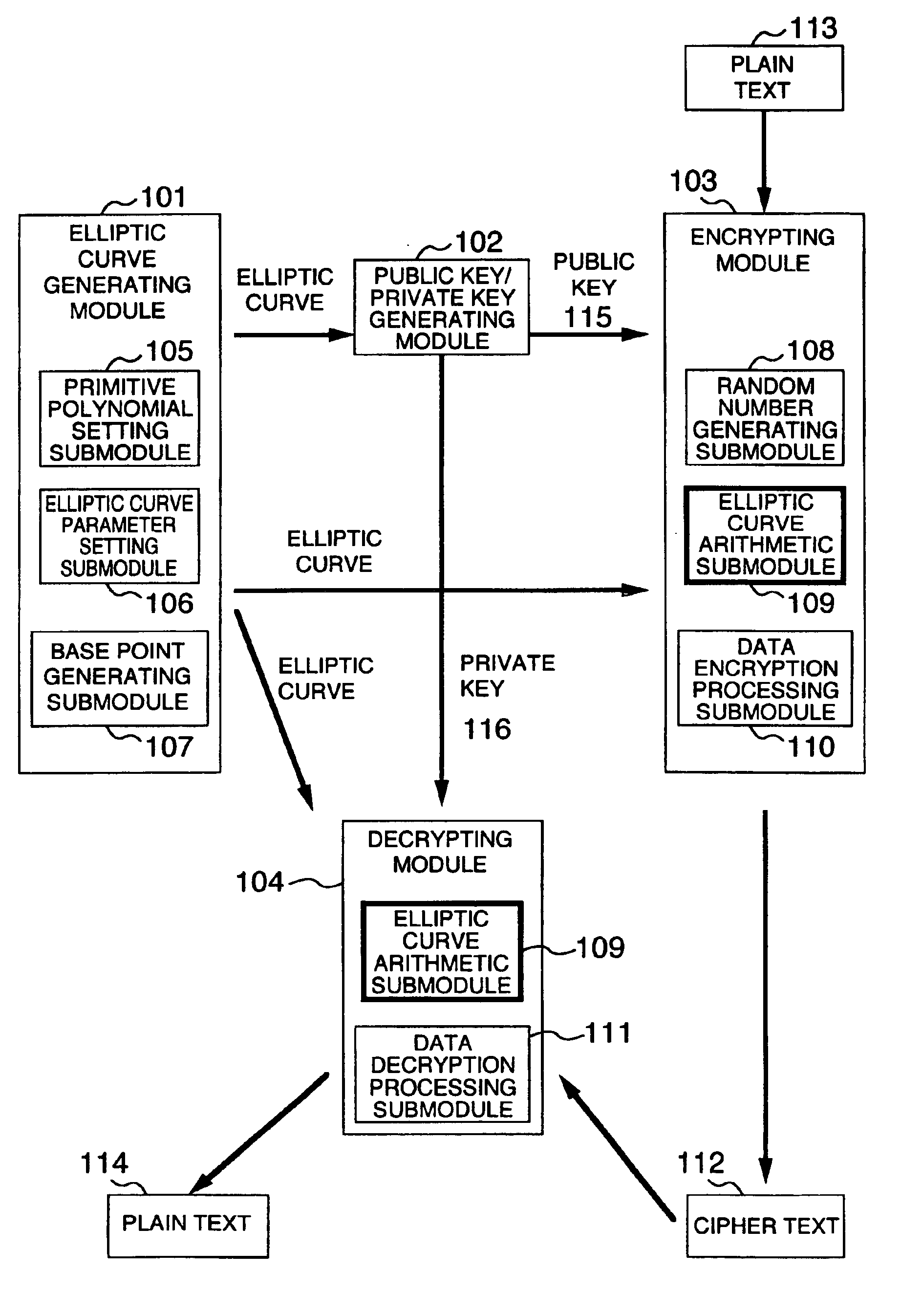
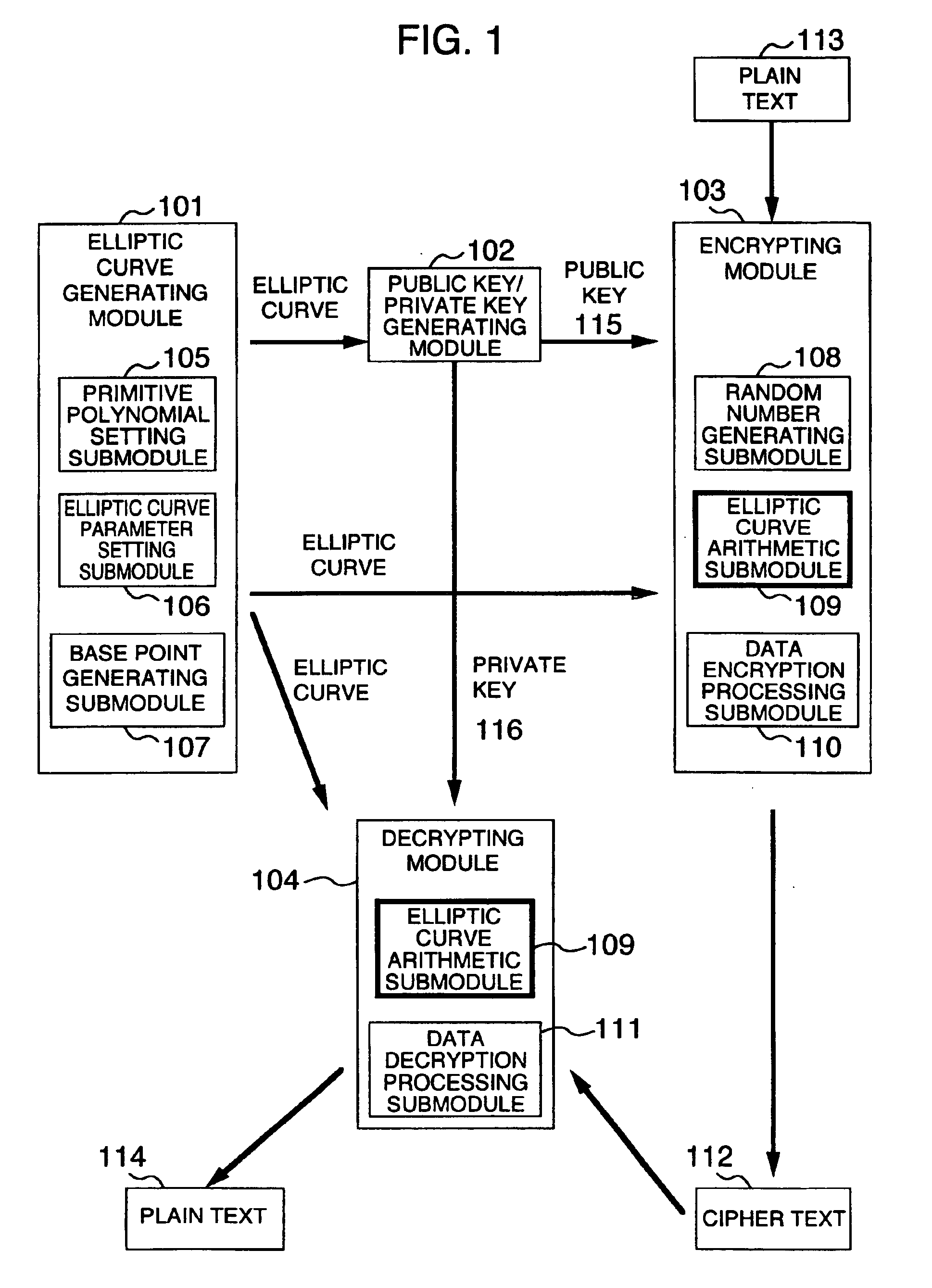
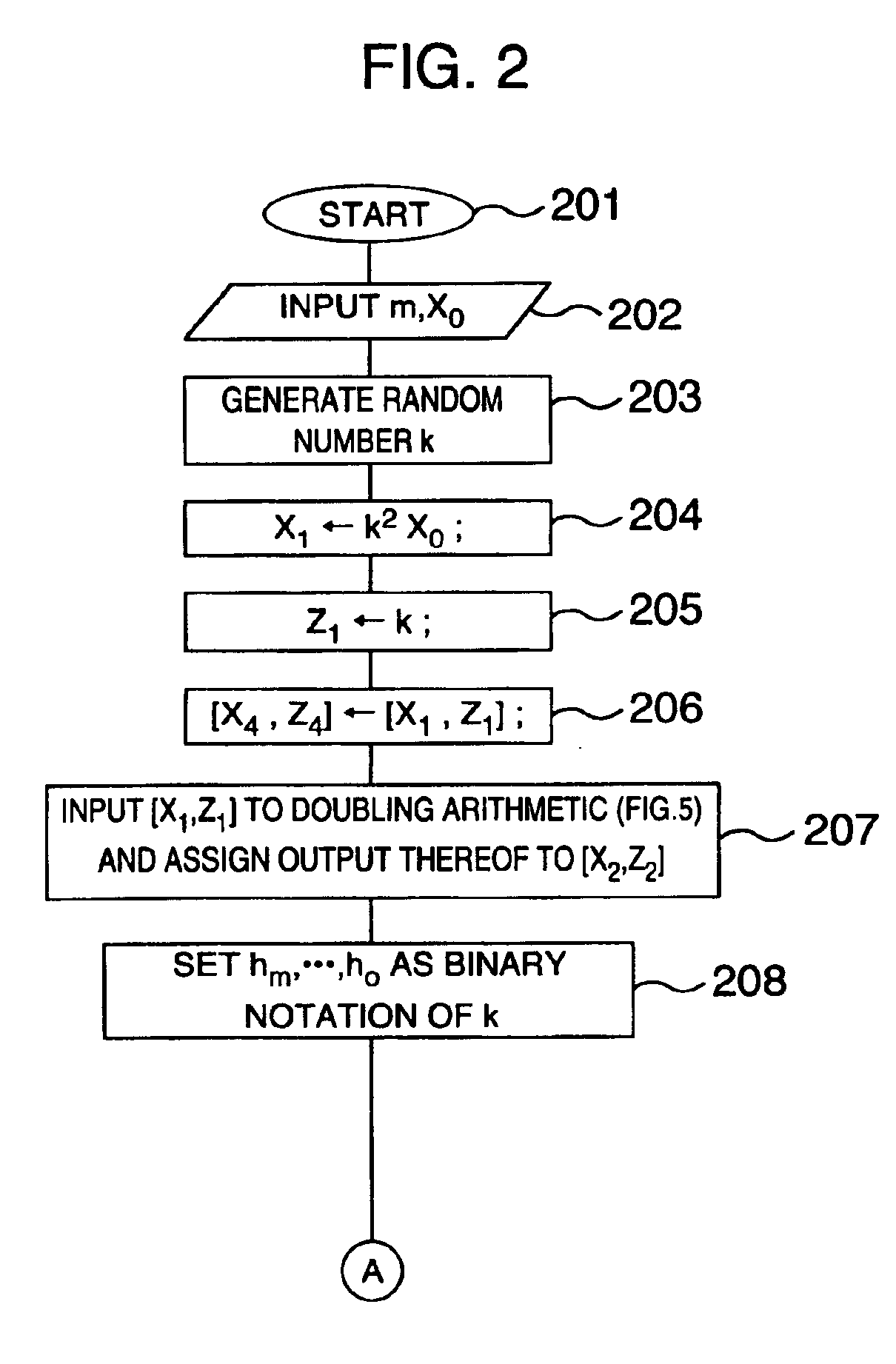
Method and apparatus for elliptic curve cryptography and recording medium therefore
InactiveUS6876745B1Prevent leakageRandom number generatorsPublic key for secure communicationComputer hardwarePower analysis
A method and an apparatus capable of realizing at a high speed an elliptic curve cryptography in a finite field of characteristic 2, in which the elliptic curve is given by y2+xy=x3+ax2+b (b≠0) and an elliptic curve cryptography method which can protect private key information against leaking from deviation information of processing time to thereby defend a cipher text against a timing attack and a differential power analysis attack are provided. To this end, an arithmetic process for executing scalar multiplication arithmetic d(x, y) a constant number of times per bit of the private key d is adopted. Further, for the scalar multiplication d(x, y), a random number k is generated upon transformation of the affine coordinates (x, y) to the projective coordinates for thereby effectuating the transformation (x, y)→[kx, ky, k] or alternatively (x, y)→[k2x, k3y, k]. Thus, object for the arithmetic is varied by the random number (k).
Owner:HITACHI LTD
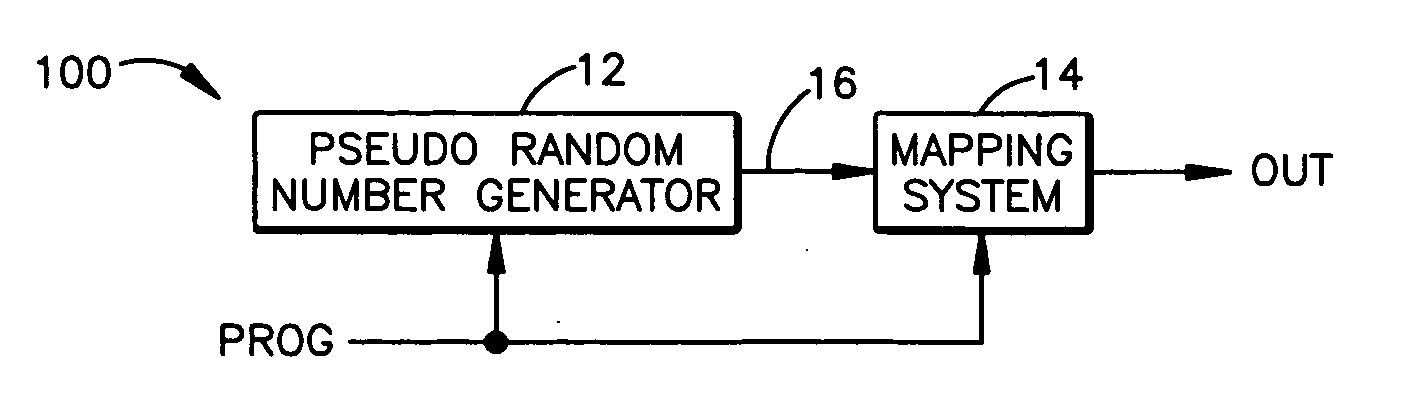
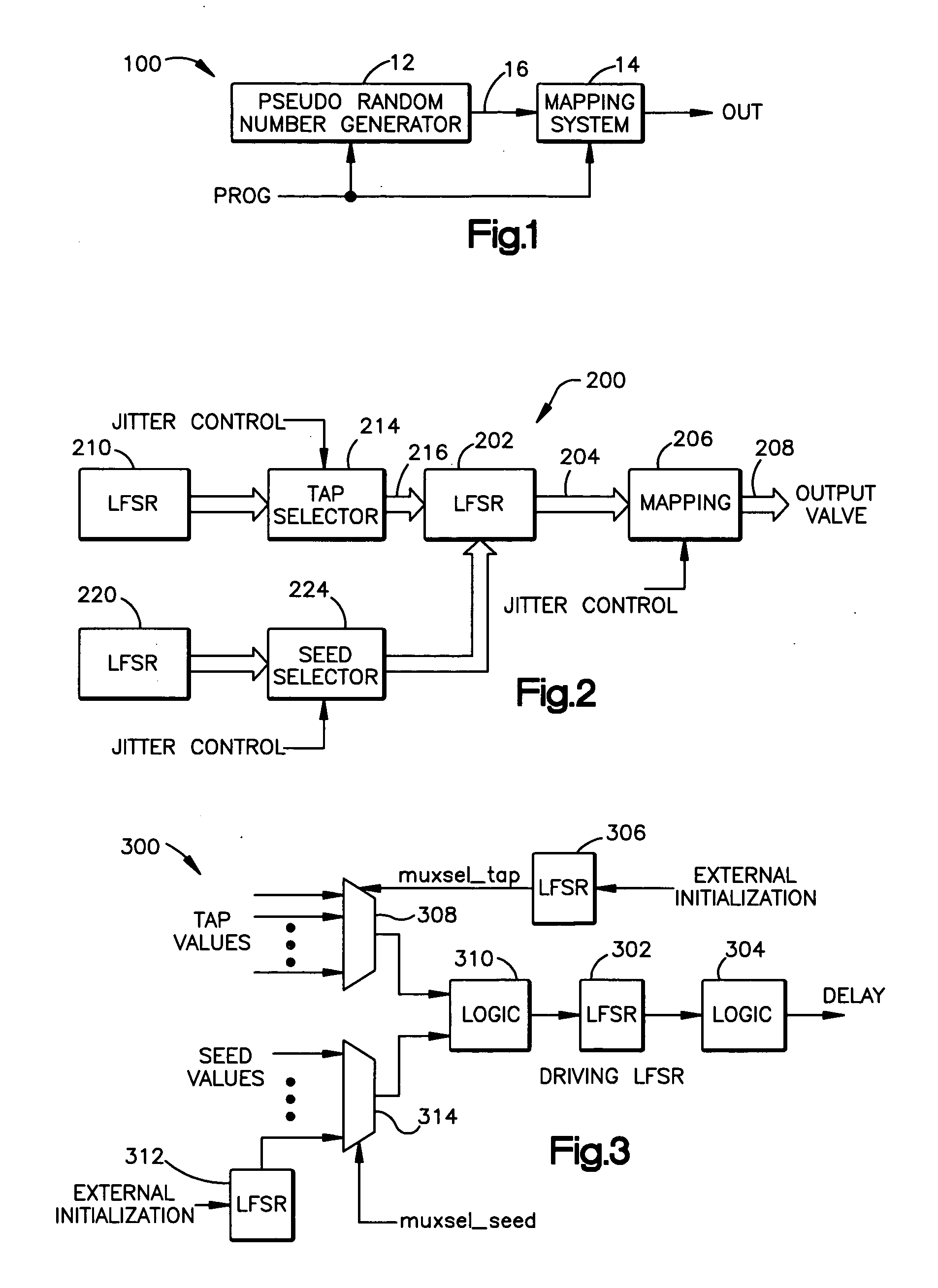
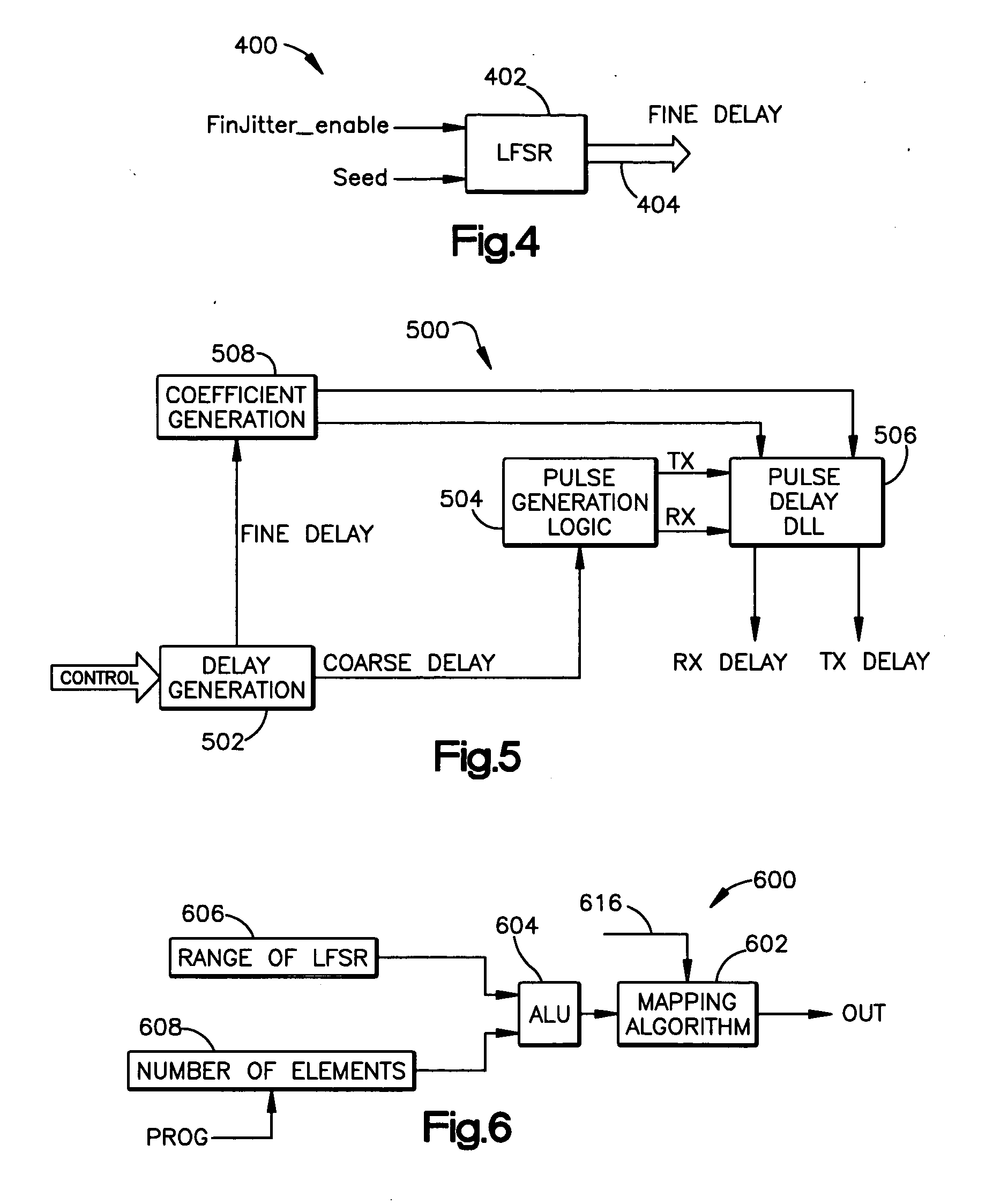
System and method for generating pseudorandom numbers
ActiveUS20050207574A1Random number generatorsSecuring communicationTheoretical computer scienceSystematic mapping
A system that has a pseudorandom number generator and a mapping system. The pseudorandom number generator generates a random number that is mapped by the mapping system to an output value that is selected from a set of predetermined output values. To increase the randomness of the sequence of numbers generated by the pseudorandom number generator, a tap and / or seed value of the pseudorandom number generator can be varied.
Owner:TEXAS INSTR INC
Server preventing attacks by generating a challenge having a computational request and a secure cookie for processing by a client
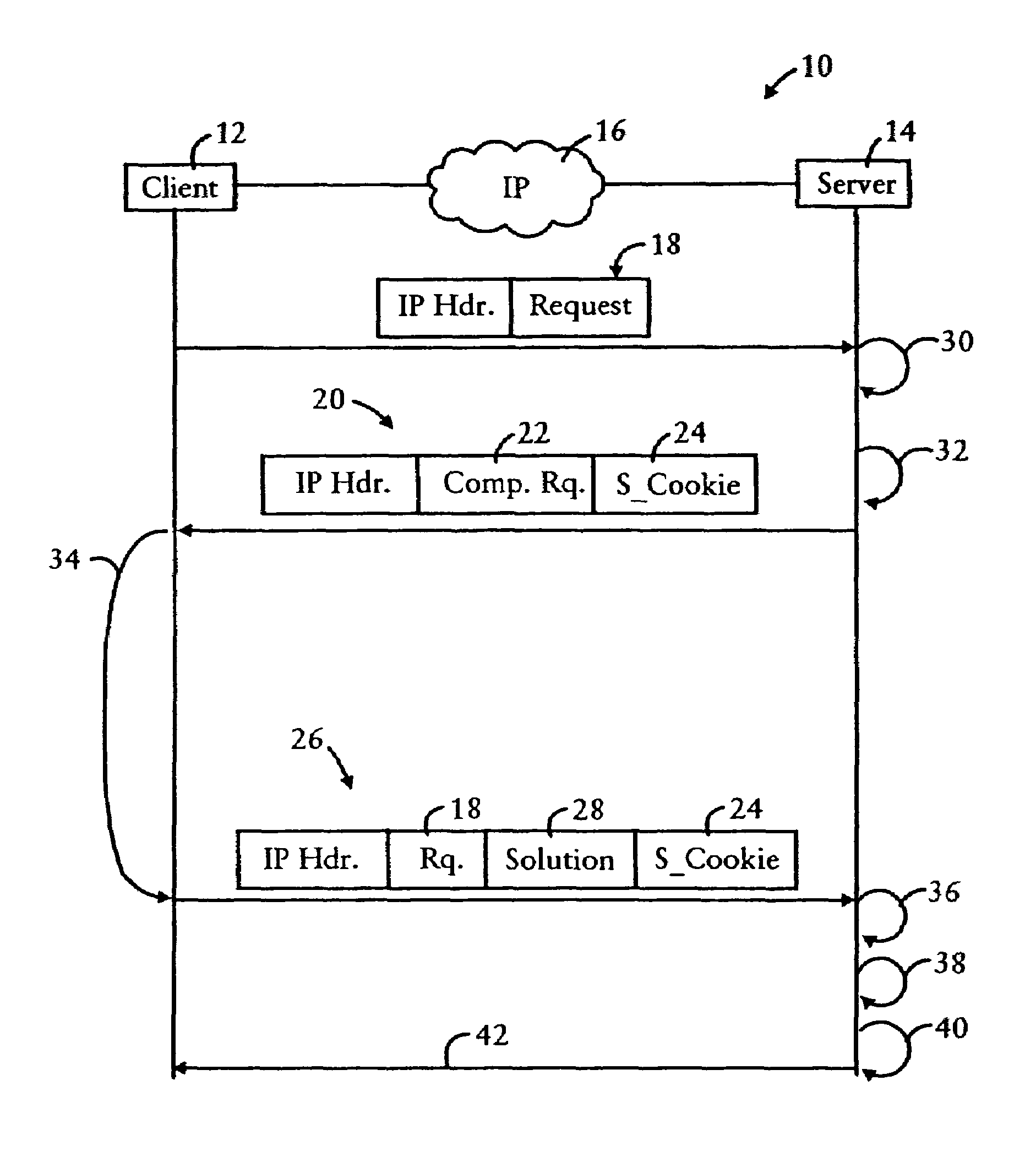
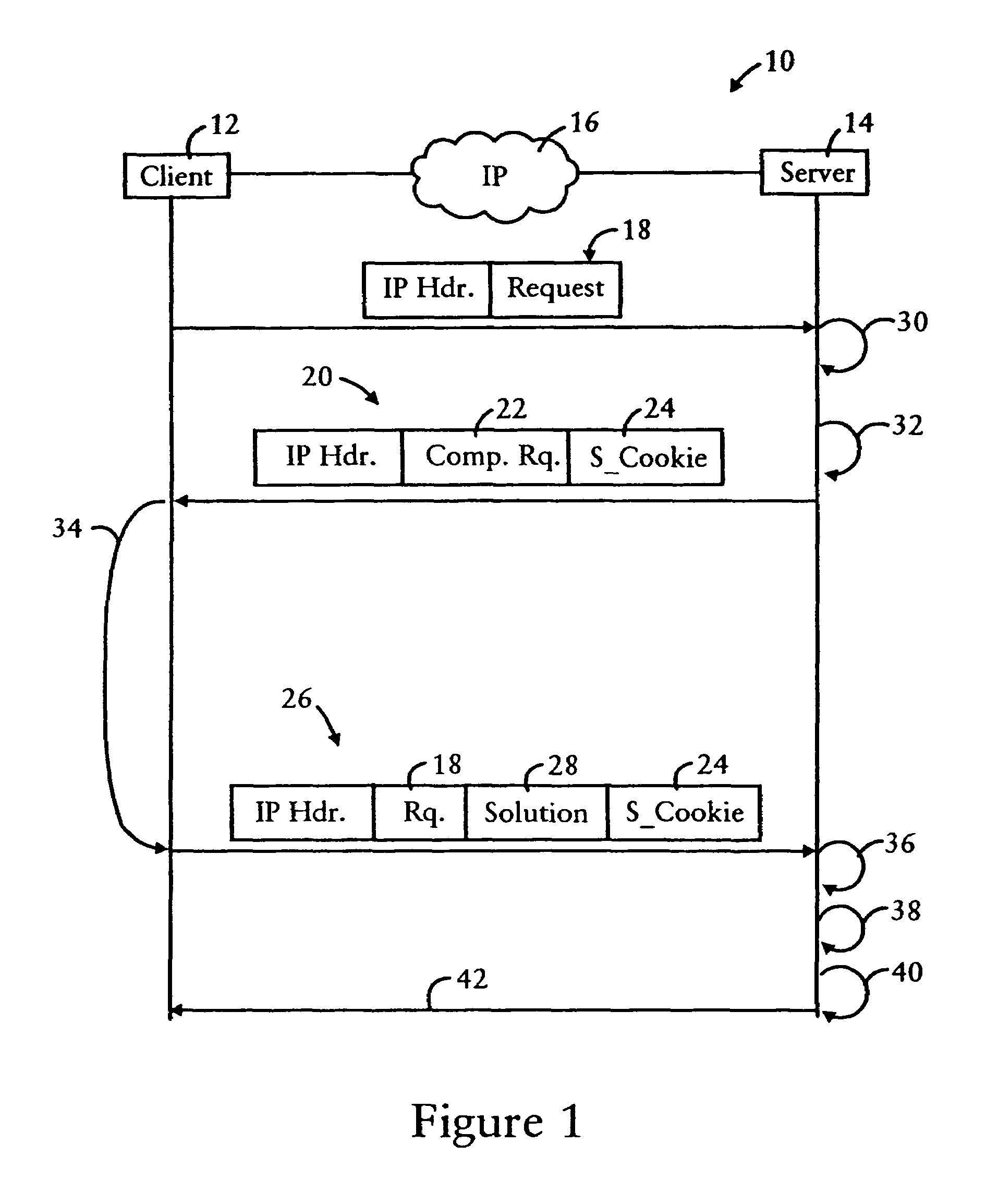
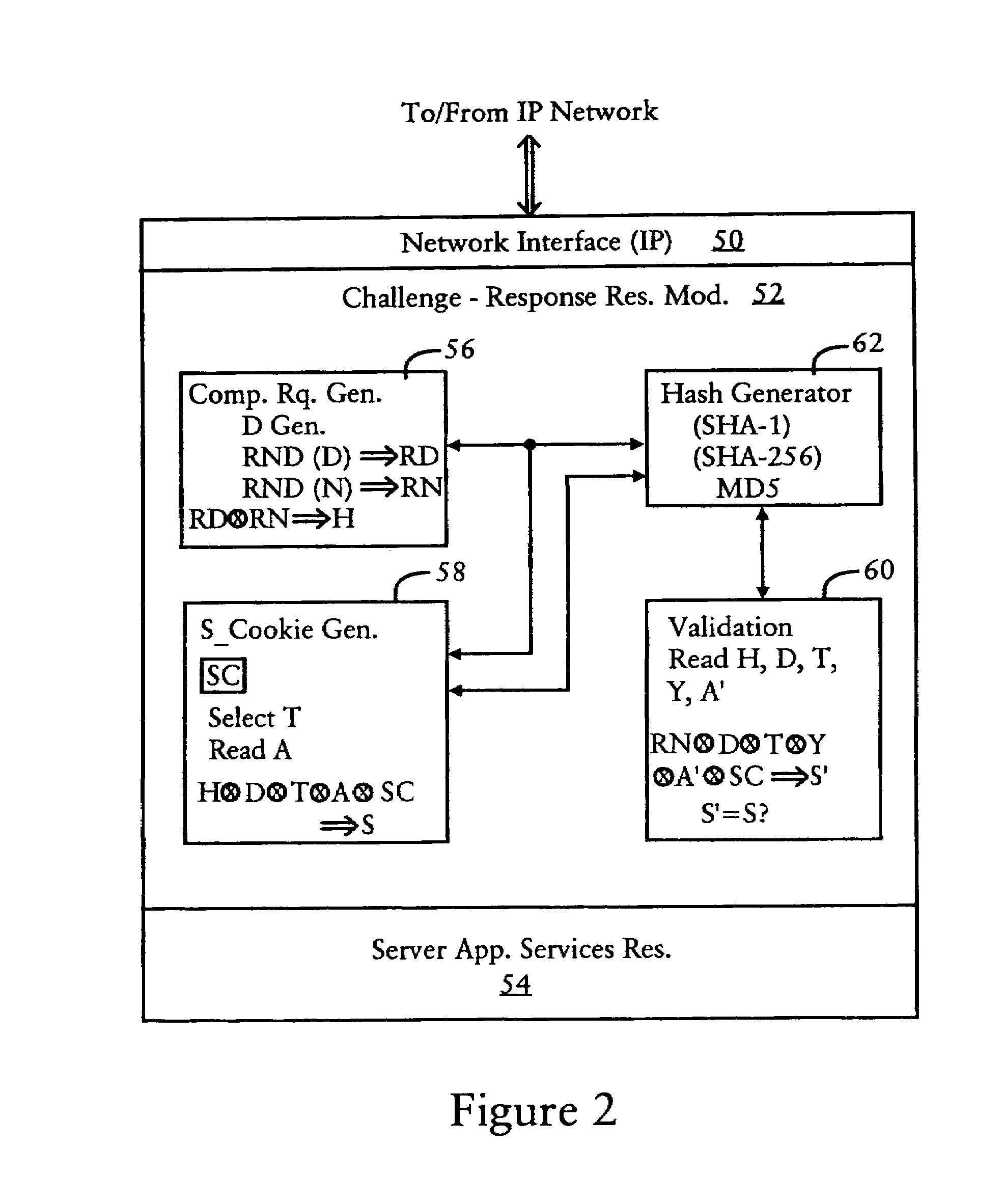
InactiveUS7694335B1Convenient verificationAvoid attackRandom number generatorsMemory loss protectionNetwork addressingUnique identifier
A server is configured for preventing flood attacks by a client having sent a request, by dynamically generating a challenge to be performed by the client before the server will perform any work for the client. The challenge includes a dynamically generated computational request and a dynamically generated secure cookie. The server generates a first hash result based on hashing a first random number, having a prescribed length, with a second random number having a dynamically selected length. A secure cookie is generated based on hashing the first hash result with a prescribed secure key known only by the server, and a unique identifier for the request such as the client network address with a time stamp. The challenge requires the client to determine the second random number based on the first random number and the hash result. The server validates the challenge results using the secure cookie.
Owner:CISCO TECH INC
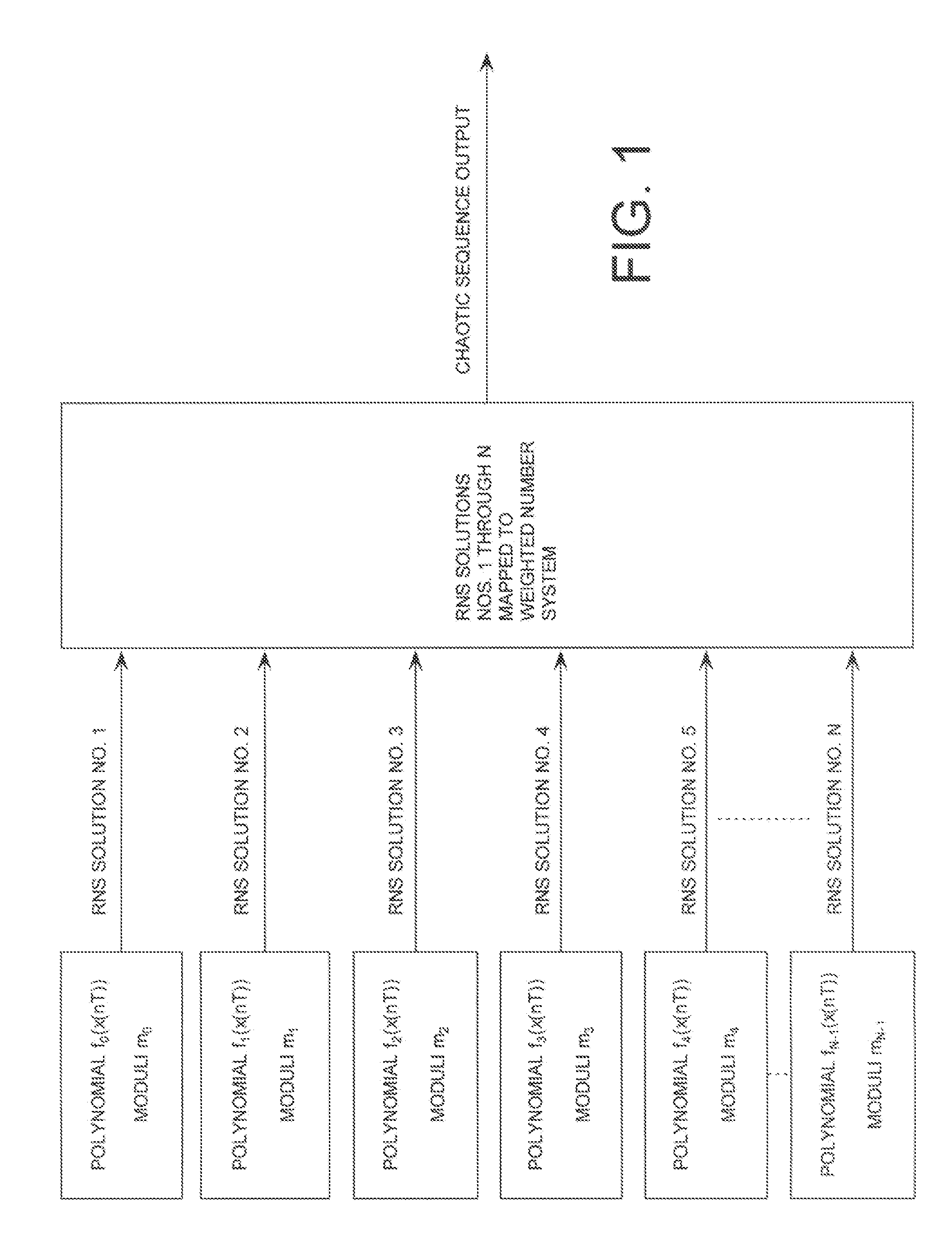
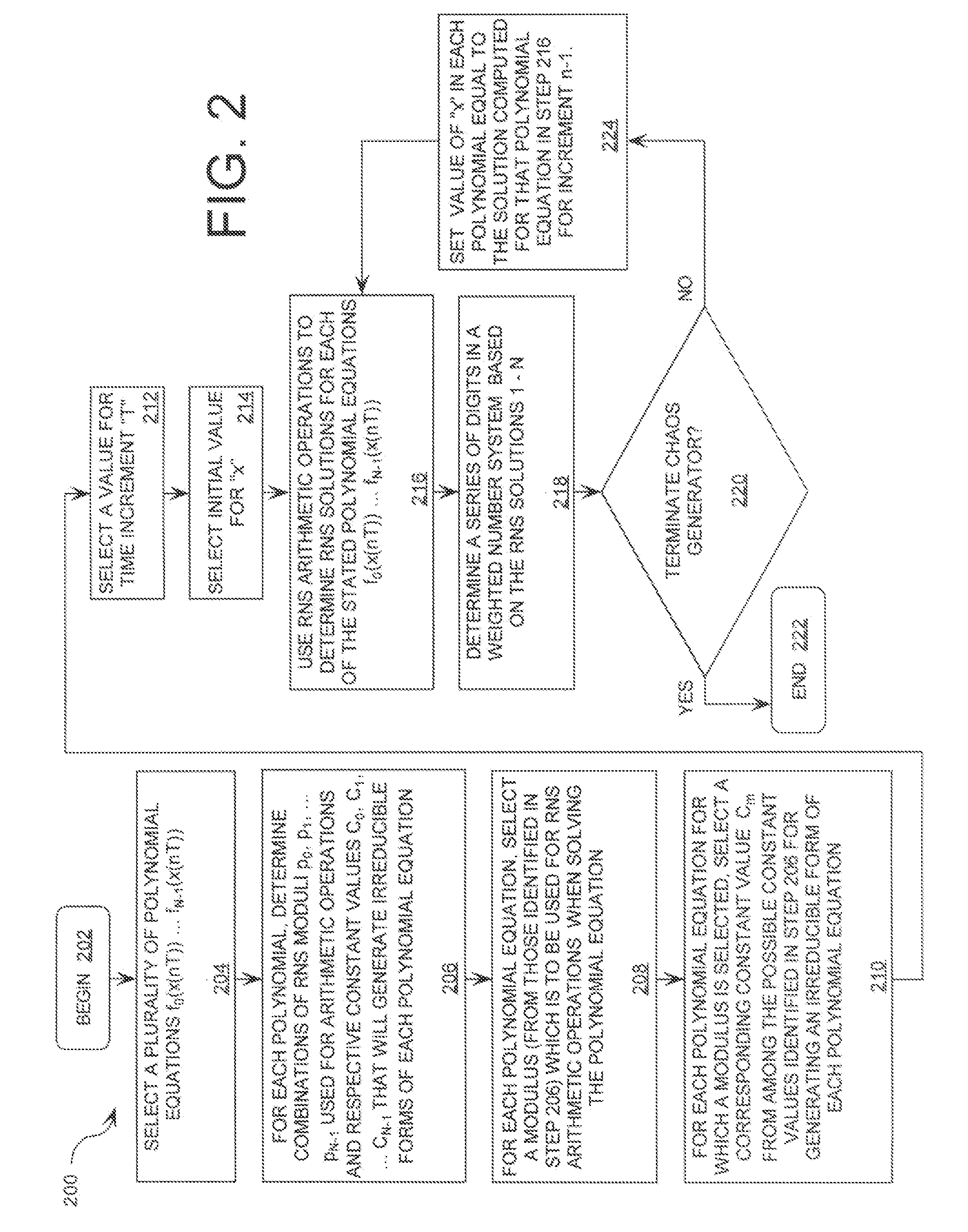
Digital Generation of a Chaotic Numerical Sequence
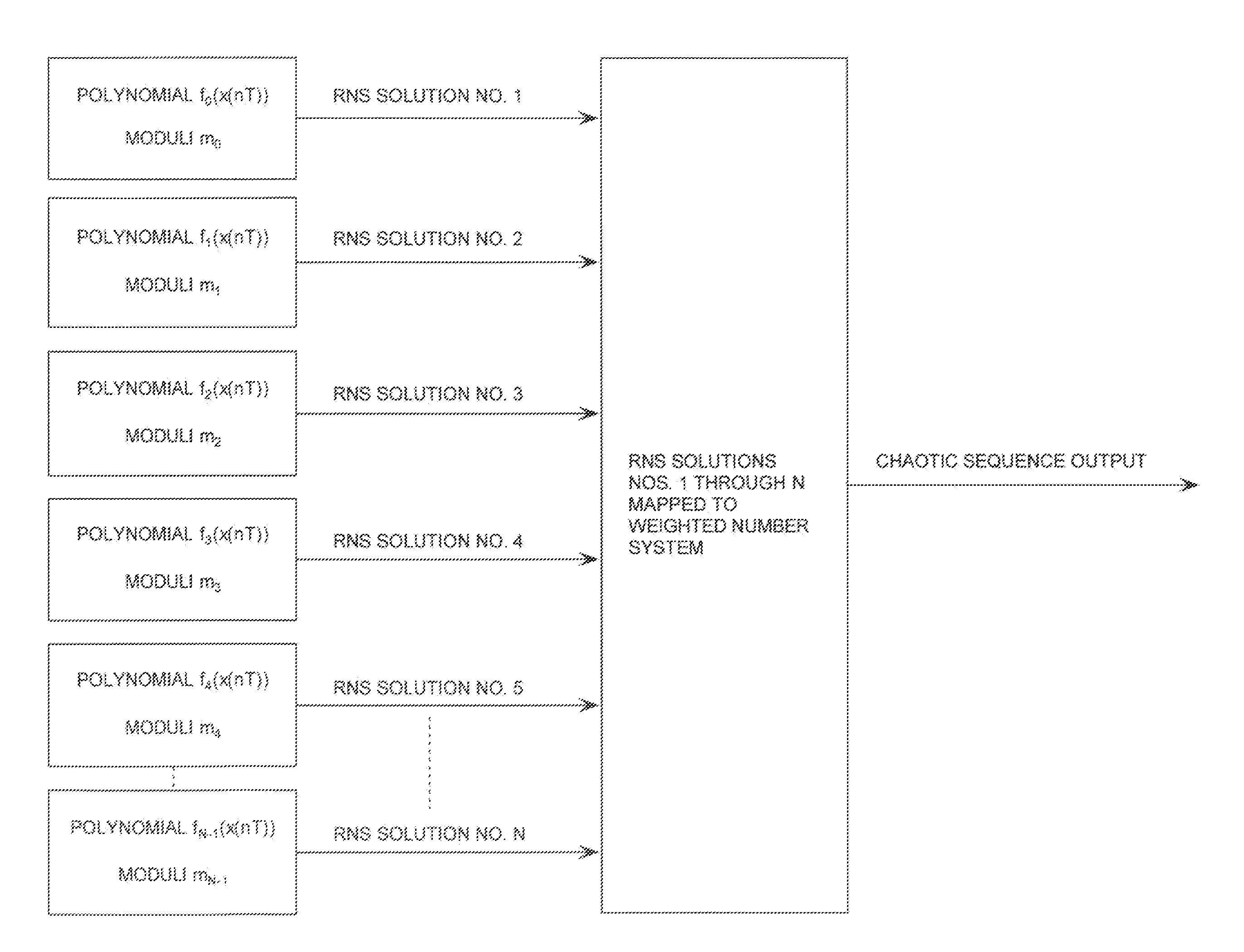
ActiveUS20080263119A1Random number generatorsComputations using residue arithmeticNumbering systemChinese remainder theorem
A method is provided for generating a chaotic sequence. The method includes selecting a plurality of polynomial equations. The method also includes using residue number system (RNS) arithmetic operations to respectively determine solutions for the polynomial equations. The solutions are iteratively computed and expressed as RNS residue values. The method further includes determining a series of digits in a weighted number system (e.g., a binary number system) based on the RNS residue values. According to an aspect of the invention, the method includes using a Chinese Remainder Theorem process to determine a series of digits in the weighted number system based on the RNS residue values. According to another aspect of the invention, the determining step comprises identifying a number in the weighted number system that is defined by the RNS residue values.
Owner:HARRIS CORP
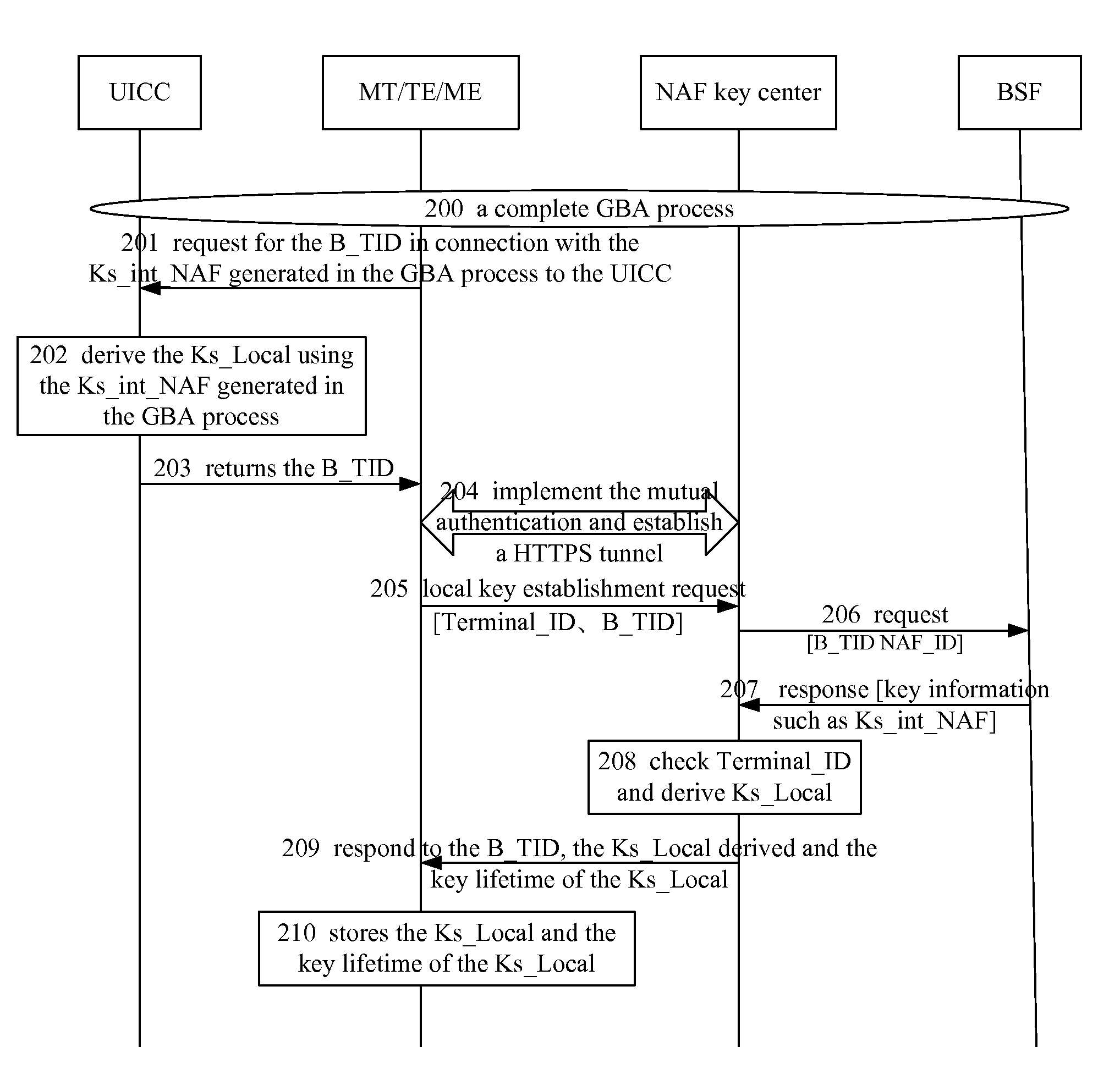
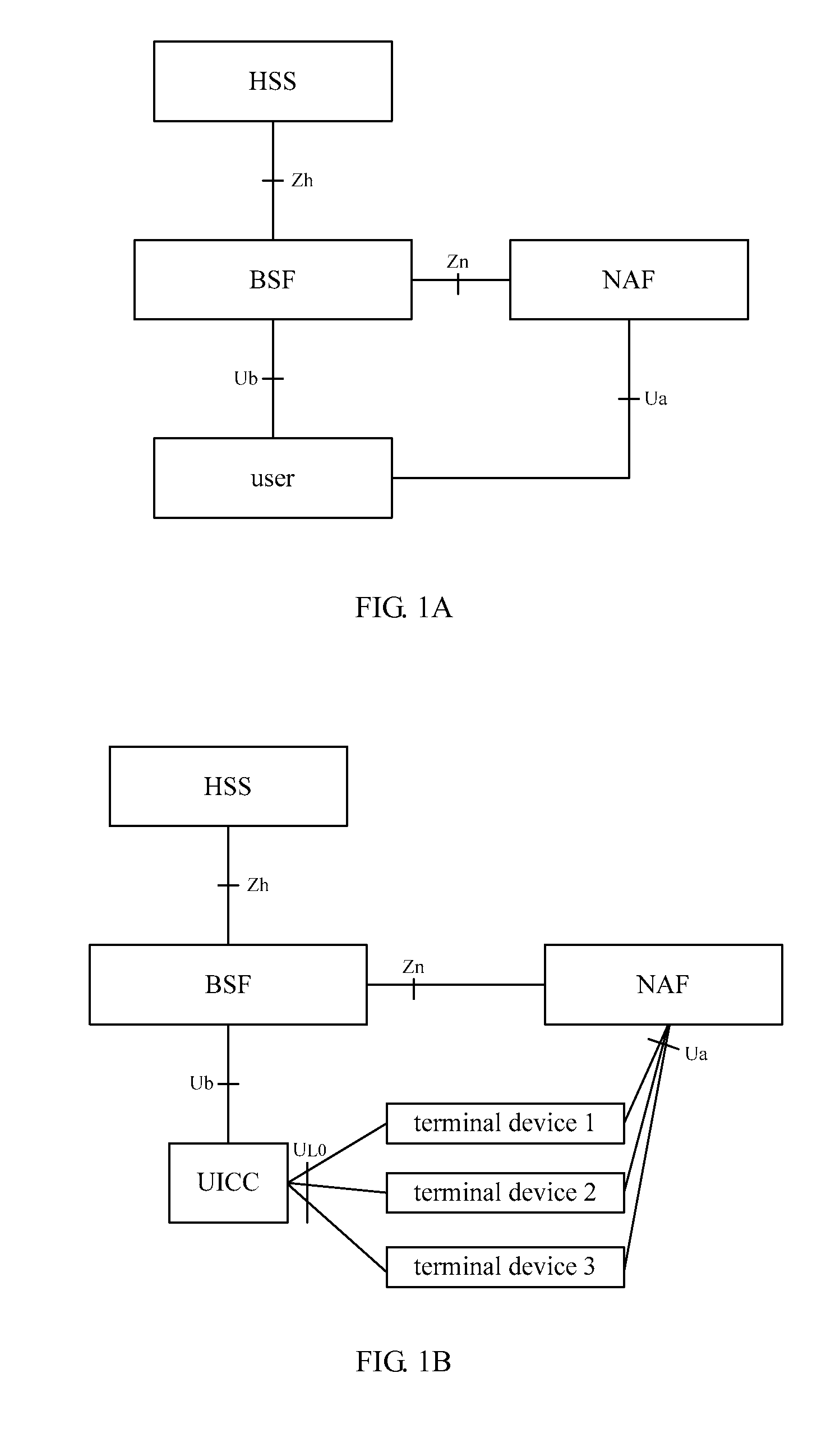
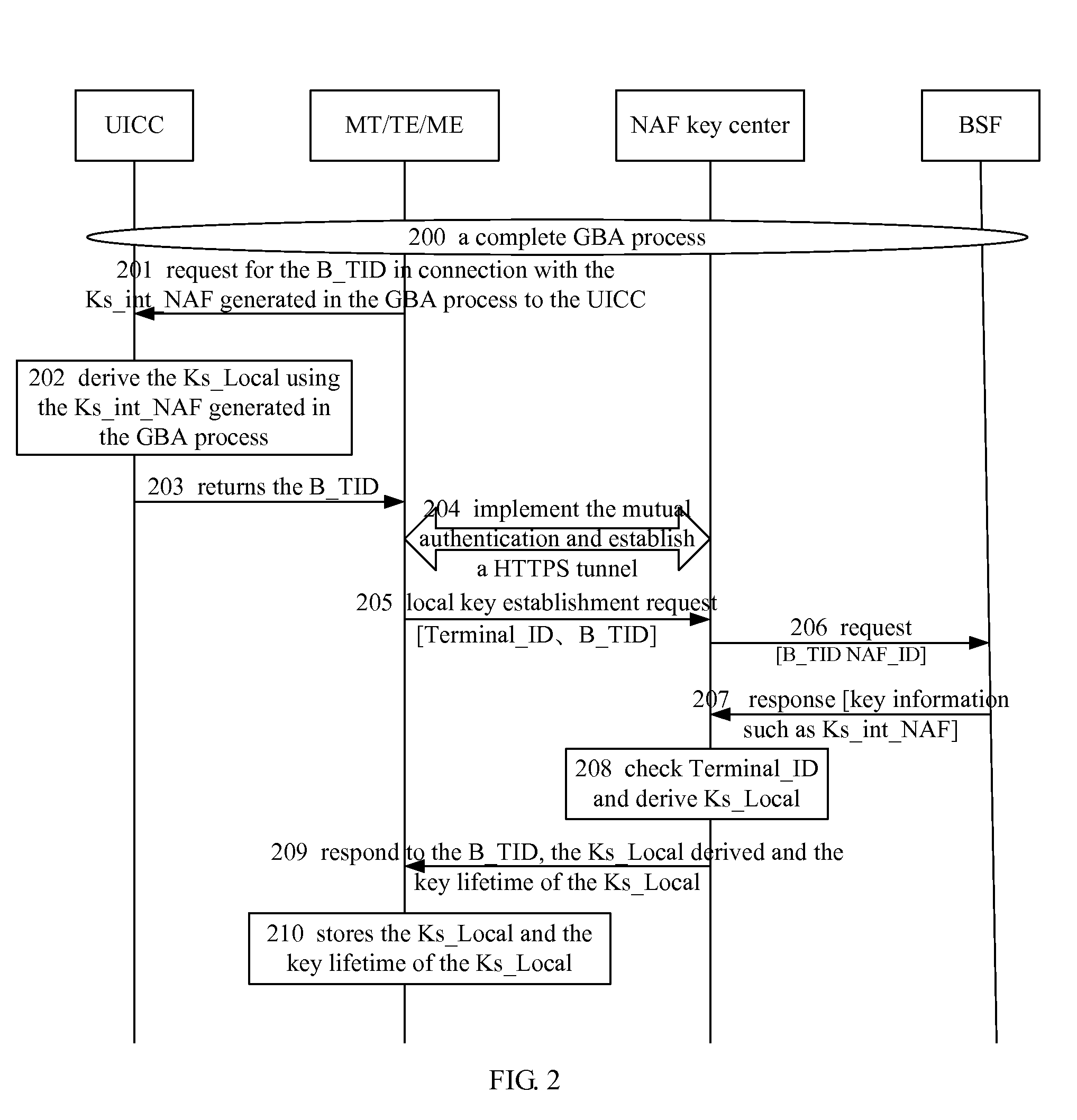
Method and device for generating local interface key
ActiveUS20090116642A1Simple processShorten the timeRandom number generatorsUser identity/authority verificationComputer hardwareSecurity level
A method for generating a local interface key includes: generating a variable parameter; and deriving the local interface key, according to the variable parameter generated and related parameters for calculating the local interface key. The method simplifies the process in which the terminal obtains the local interface key and the system resources are saved. Moreover, the local interface key is derived through the variable parameter and the valid key information. Thus, the security level between the UICC and the terminal is ensured.
Owner:HUAWEI TECH CO LTD
Popular searches
Memory record carrier reading problems Time-division multiplex Signalling system details Co-operative working arrangements Electric/electromagnetic visible signalling Wireless commuication services Subscribers indirect connection Burglar alarm by hand-portable articles removal Multiple keys/algorithms usage Digital data protection
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com