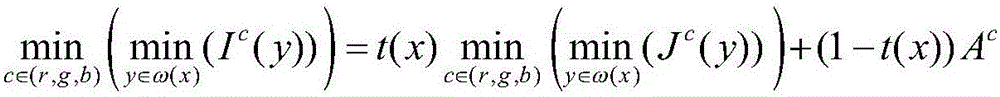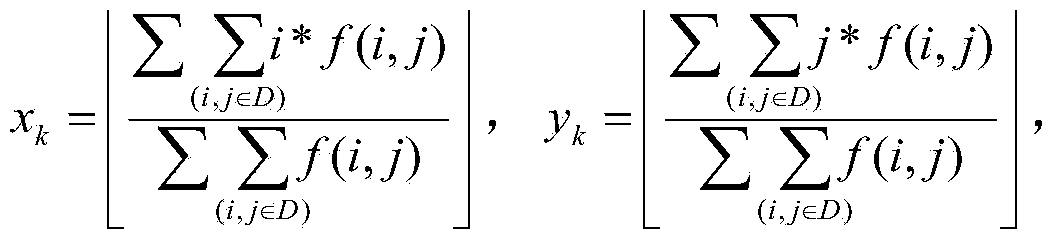Patents
Literature
195 results about "Initial Seed" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Seed capital is the initial capital used when starting a business, often coming from the founders' personal assets, friends or family, for covering initial operating expenses and attracting venture capitalists.
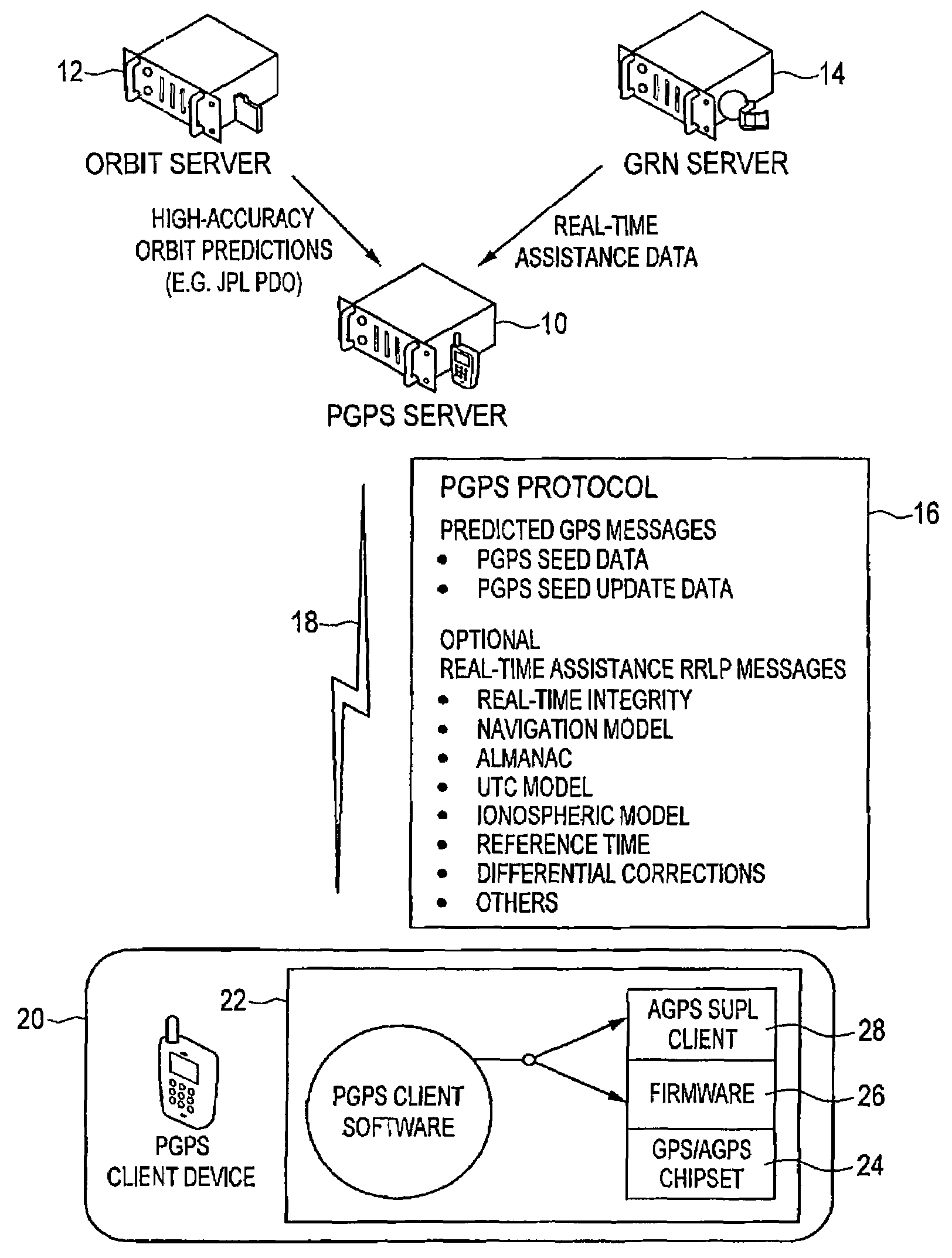
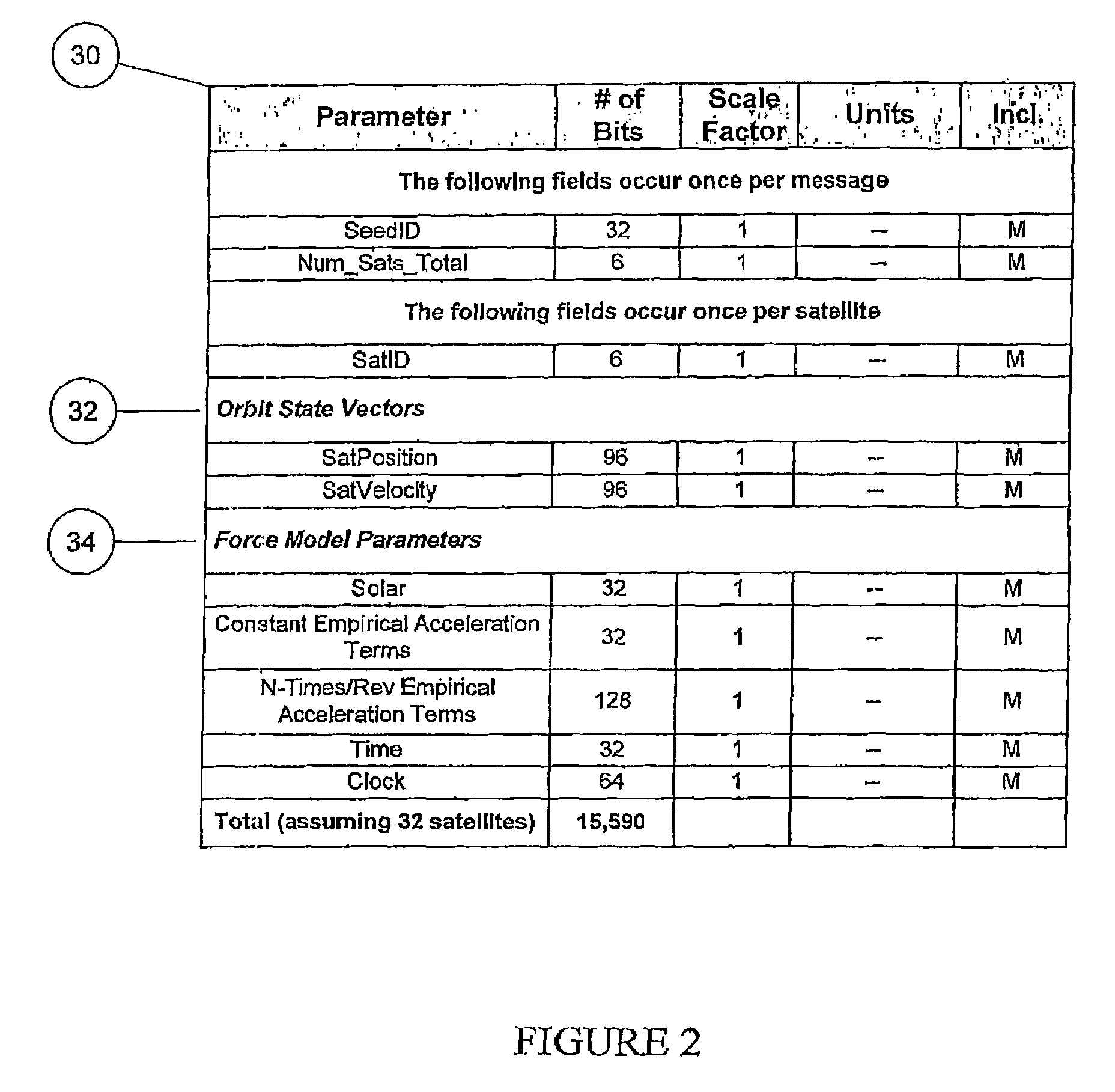
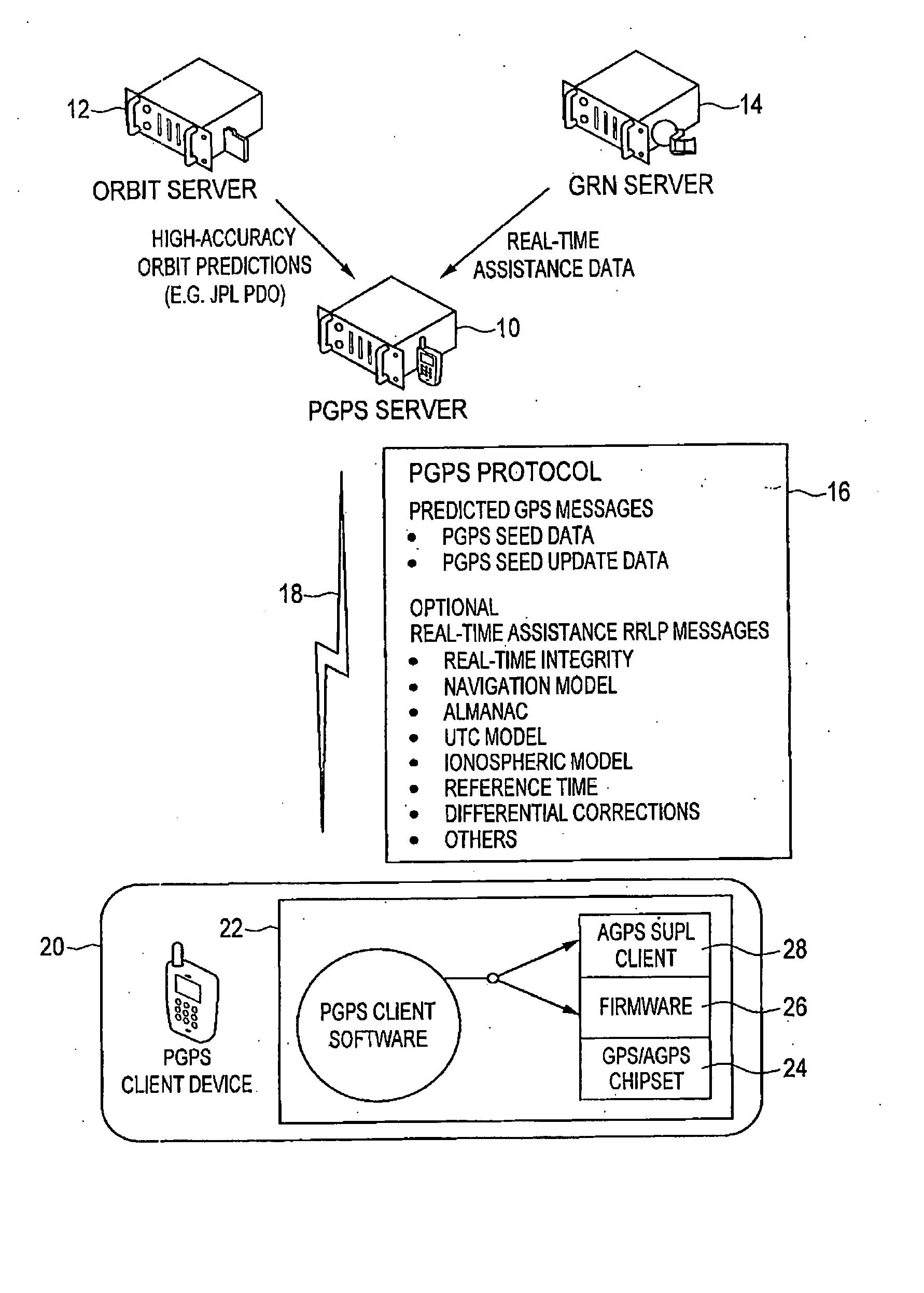
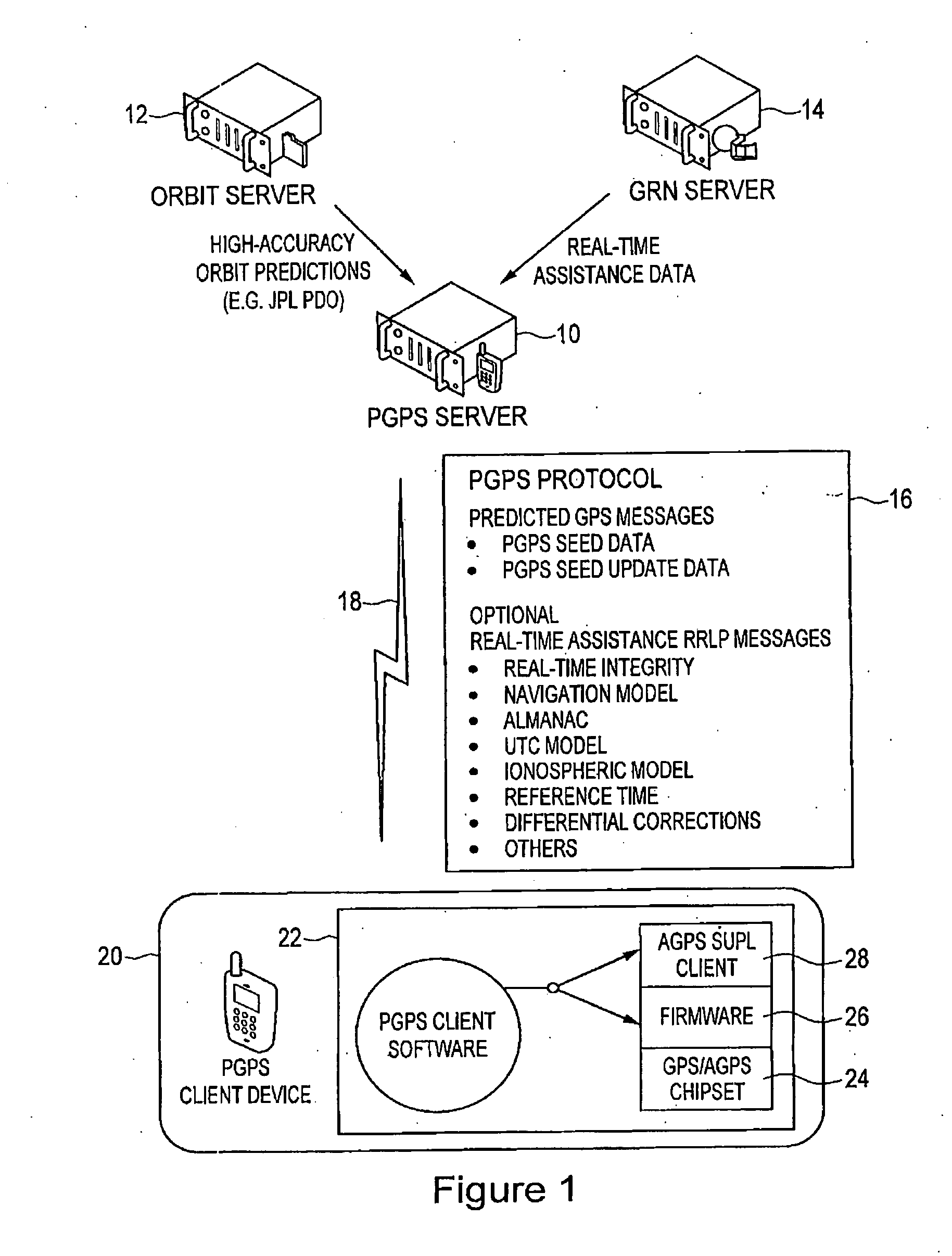
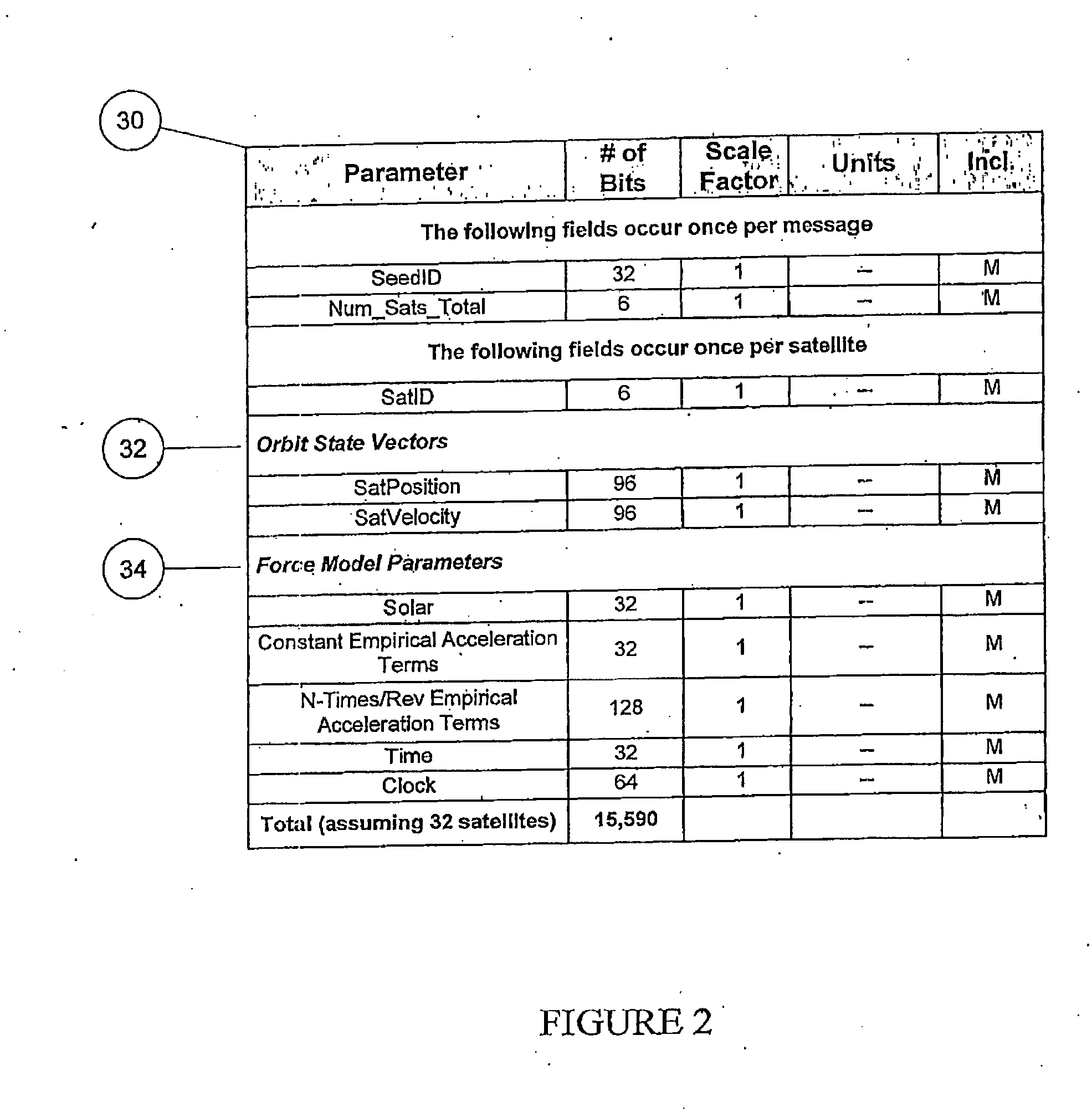
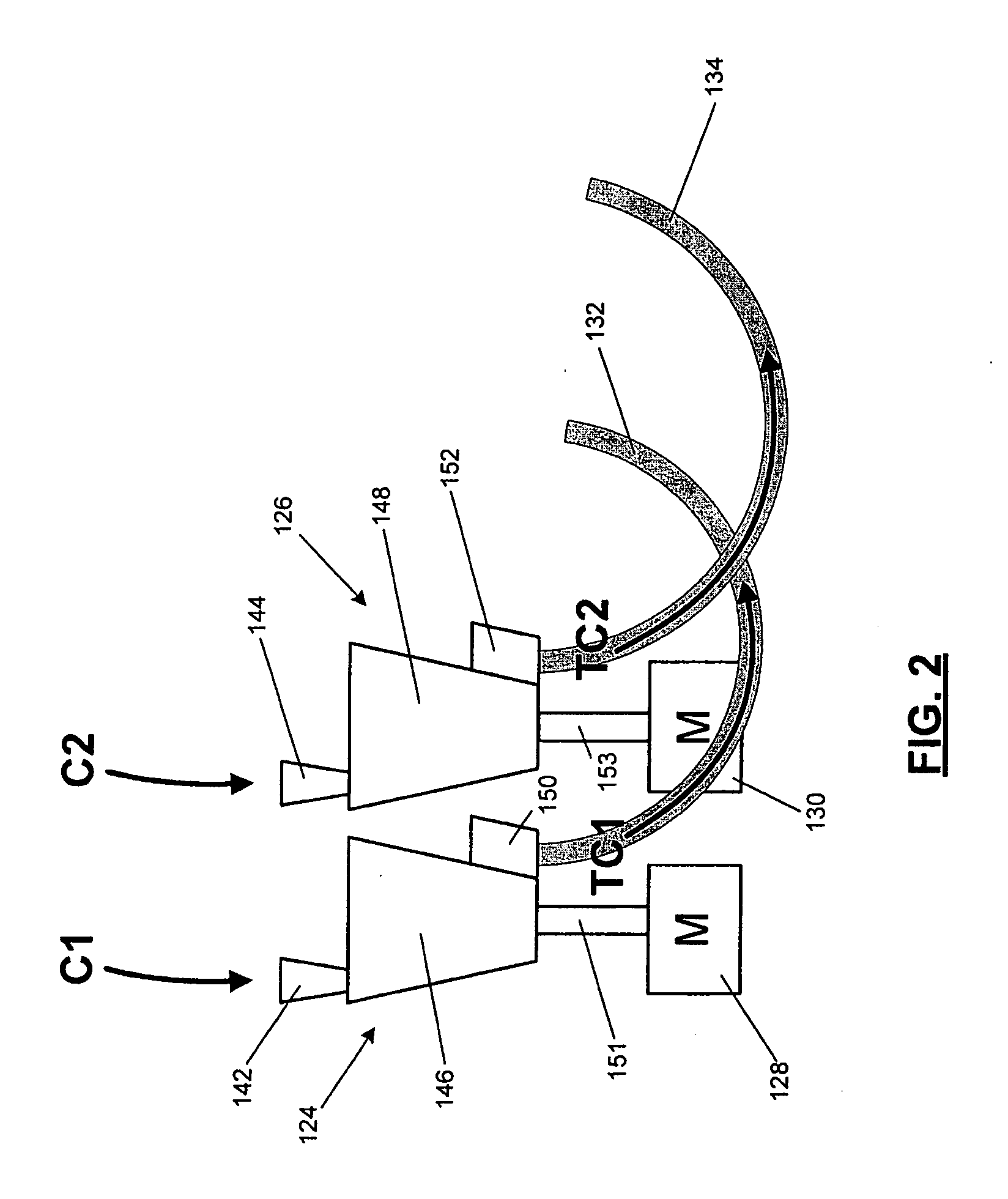
Distributed orbit modeling and propagation method for a predicted and real-time assisted GPS system
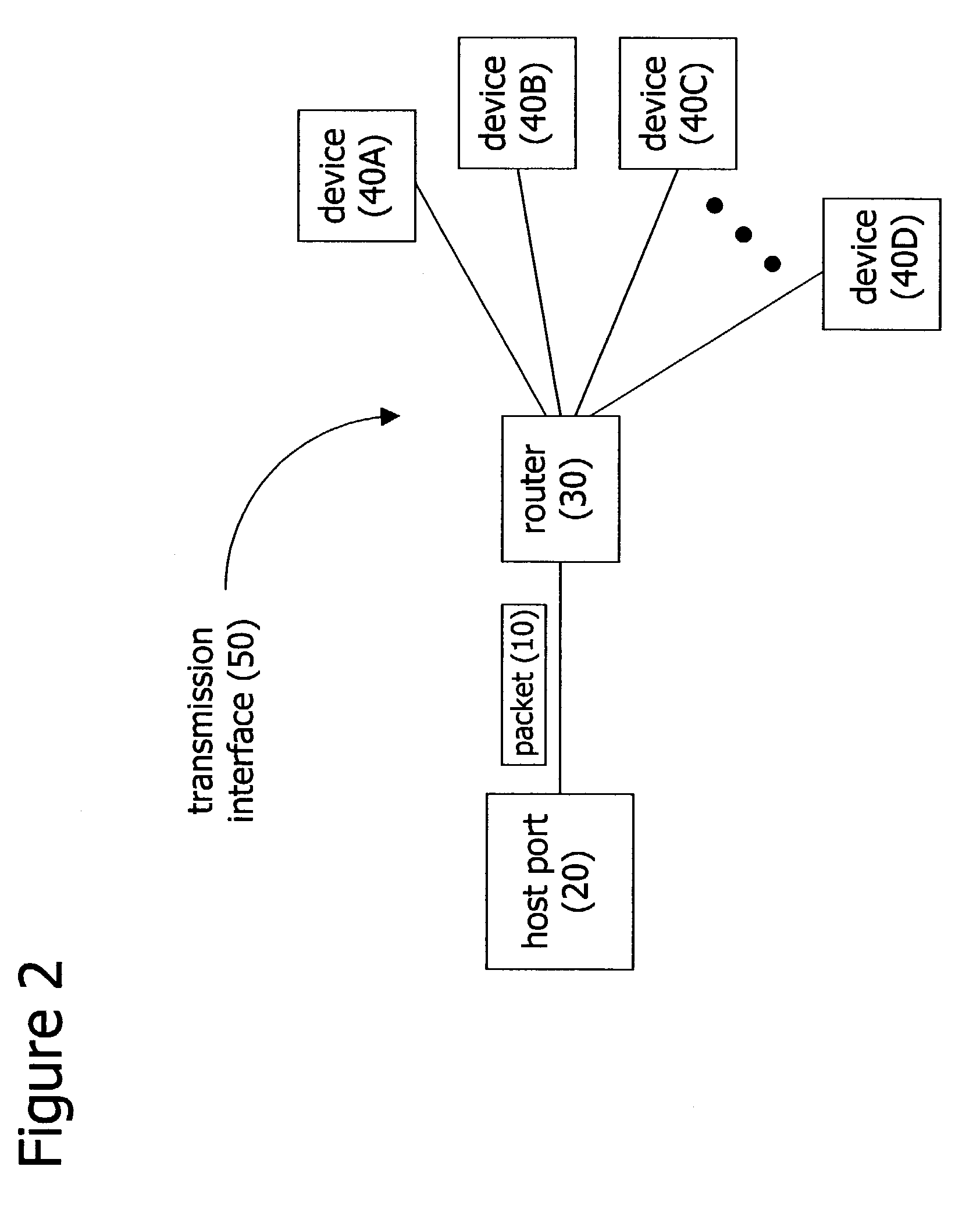
ActiveUS7612712B2Easy to integrateNavigational calculation instrumentsSatellite radio beaconingData setTime to first fix
A distributed orbit and propagation method for use in a predicted GPS or GNSS system, which includes a predicted GPS server (PGPS Server), a source of high accuracy orbit predictions (Orbit Server), a global reference network (GRN Server) providing real-time GPS or GNSS assistance data to the PGPS Server, a predicted GPS client (PGPS Client) running on a device equipped with a GPS or AGPS chipset. In response to requests from the PGPS Client, the PGPS Server produces and disseminates an initial seed dataset consisting of current satellite orbit state vectors and orbit propagation model coefficients. This seed dataset enables the PGPS Client to locally predict and propagate satellite orbits to a desired future time. This predictive assistance in turn helps accelerate Time To First Fix (TTFF), optimize position solution calculations and improve the sensitivity of the GPS chip present on, or coupled with, the device. In contrast with other conventional predicted GPS systems that forward large volumes of predicted orbits, synthetic ephemeris or synthetic almanac data, this method optimally reduces data transfer requirements to the client, and enables the client to locally synthesize its own predicted assistance data as needed. This method also supports seamless notification of real-time satellite integrity events and seamless integration of predicted assistance data with industry standard real-time assistance data.
Owner:RX NETWORKS INC
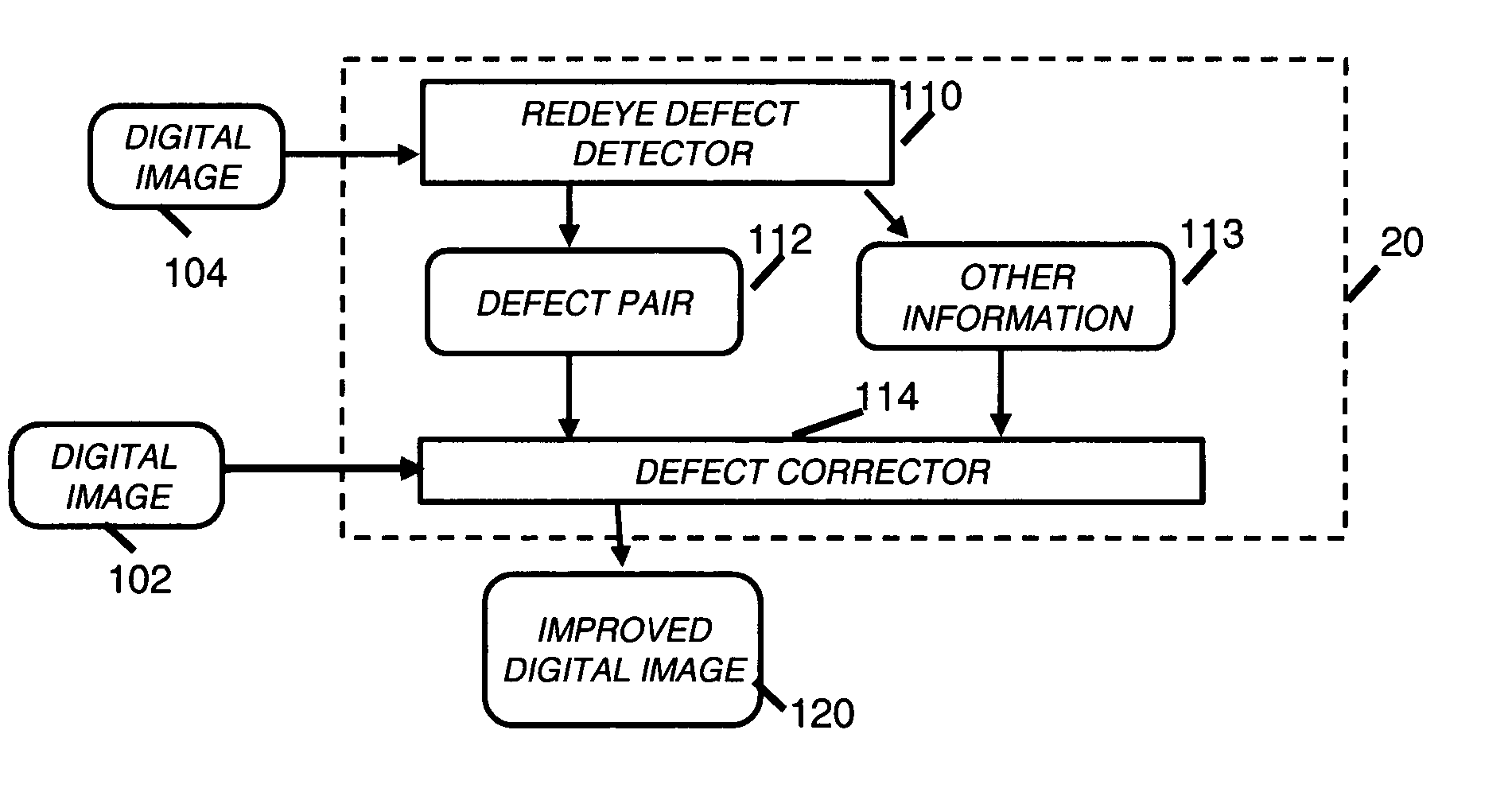
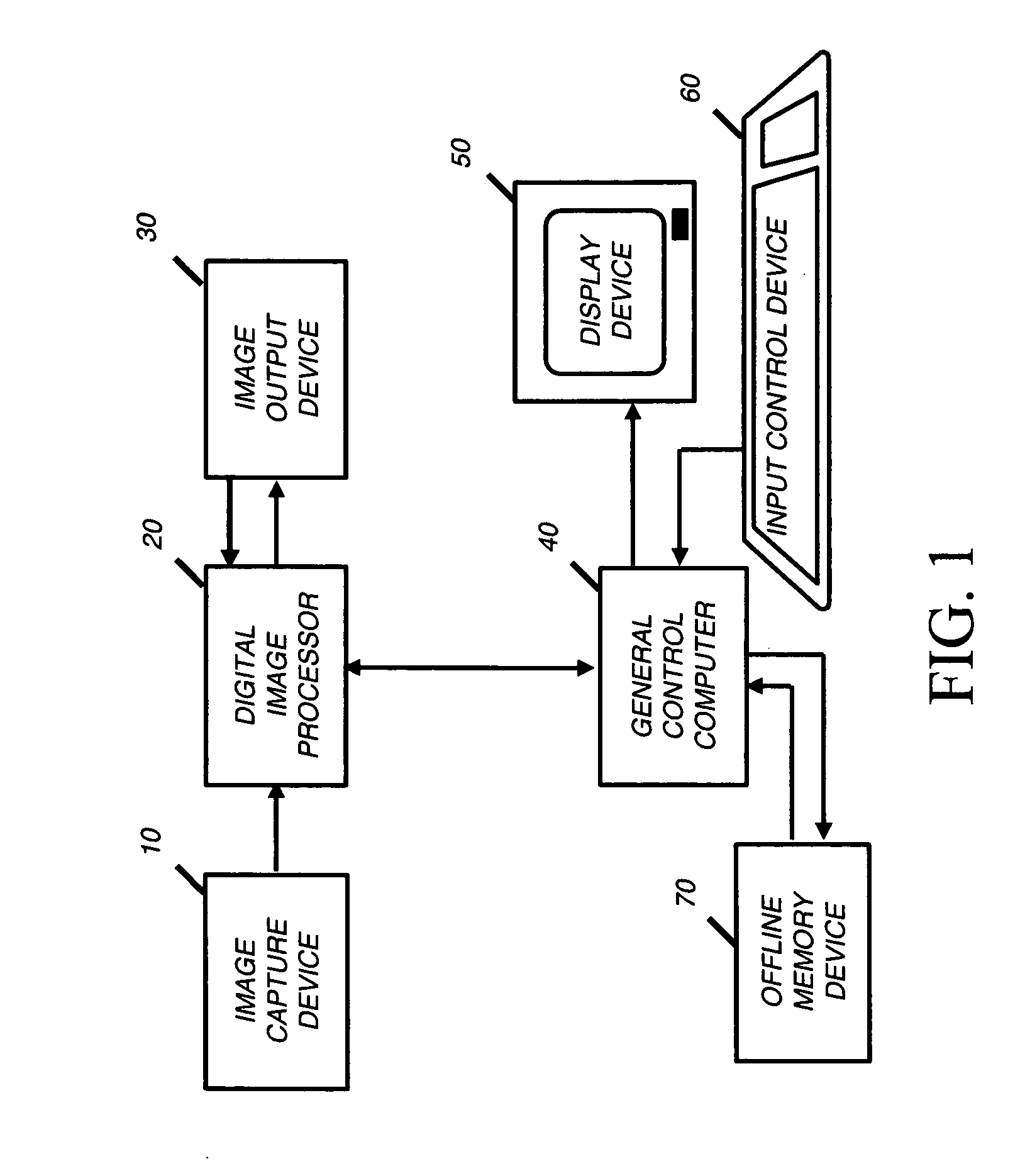
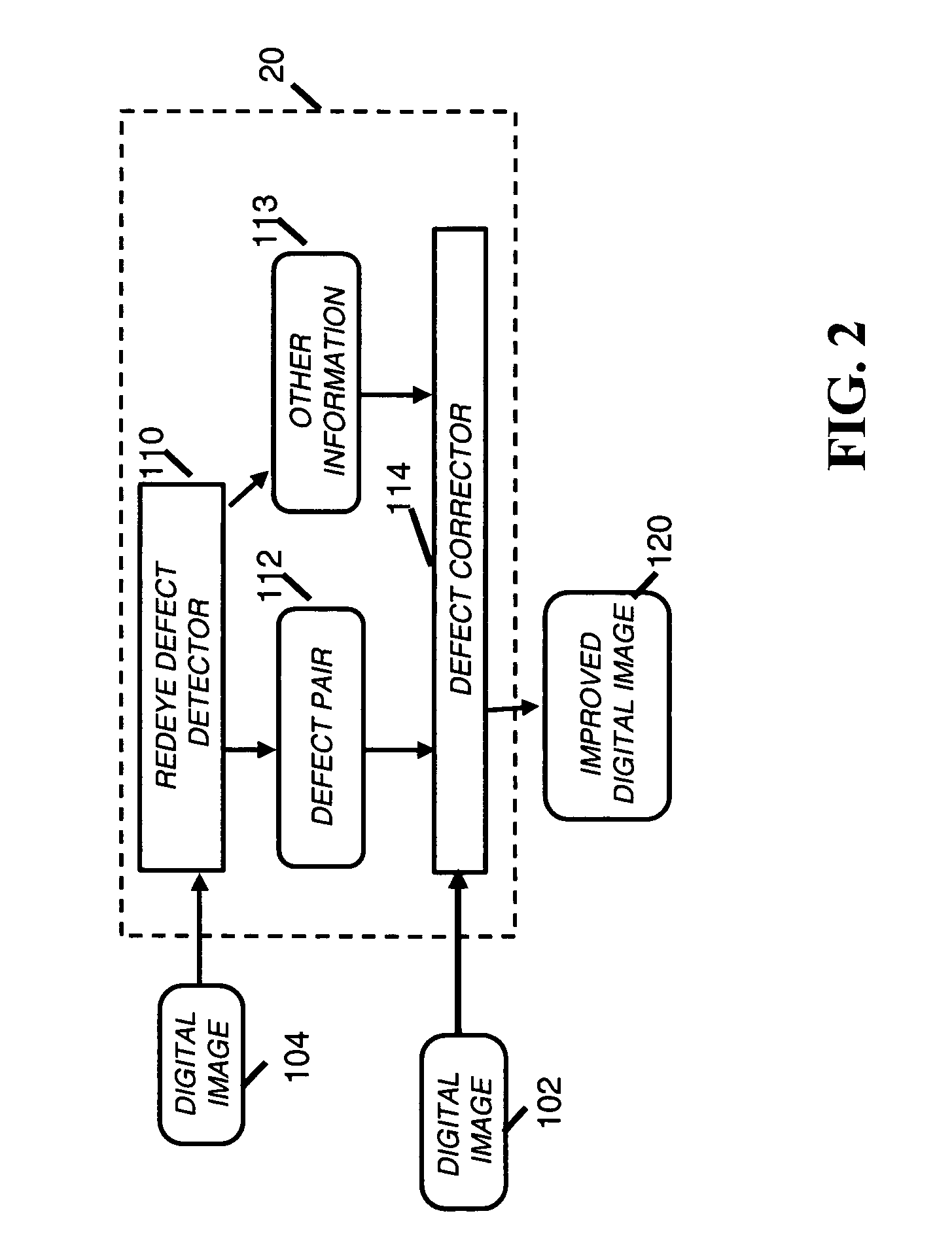
Correction of redeye defects in images of humans
In a method and system for correcting redeye in a digital image of a human, a defect pair separation is measured. The members of the defect pair are each redeye defects in the image. Each defect has one or more pixels. The defects are adjusted, that is, retained unchanged or reduced in size to provide adjusted defects. The adjustment can follow growth of initial seed defects. The adjustment is responsive to the defect pair separation and can include trimming of pixels beyond a size limit calculated using the defect pair separation. Following the adjustment, the color of the adjusted defects is changed to reduce redeye.
Owner:MONUMENT PEAK VENTURES LLC
Distributed orbit modeling and propagation method for a predicted and real-time assisted GPS system
ActiveUS20080018527A1Easy to integrateNavigational calculation instrumentsRadio transmissionData setTime to first fix
A distributed orbit and propagation method for use in a predicted GPS or GNSS system, which includes a predicted GPS server (PGPS Server), a source of high accuracy orbit predictions (Orbit Server), a global reference network (GRN Server) providing real-time GPS or GNSS assistance data to the PGPS Server, a predicted GPS client (PGPS Client) running on a device equipped with a GPS or AGPS chipset. In response to requests from the PGPS Client, the PGPS Server produces and disseminates an initial seed dataset consisting of current satellite orbit state vectors and orbit propagation model coefficients. This seed dataset enables the PGPS Client to locally predict and propagate satellite orbits to a desired future time. This predictive assistance in turn helps accelerate Time To First Fix (TTFF), optimize position solution calculations and improve the sensitivity of the GPS chip present on, or coupled with, the device. In contrast with other conventional predicted GPS systems that forward large volumes of predicted orbits, synthetic ephemeris or synthetic almanac data, this method optimally reduces data transfer requirements to the client, and enables the client to locally synthesize its own predicted assistance data as needed. This method also supports seamless notification of real-time satellite integrity events and seamless integration of predicted assistance data with industry standard real-time assistance data.
Owner:RX NETWORKS INC
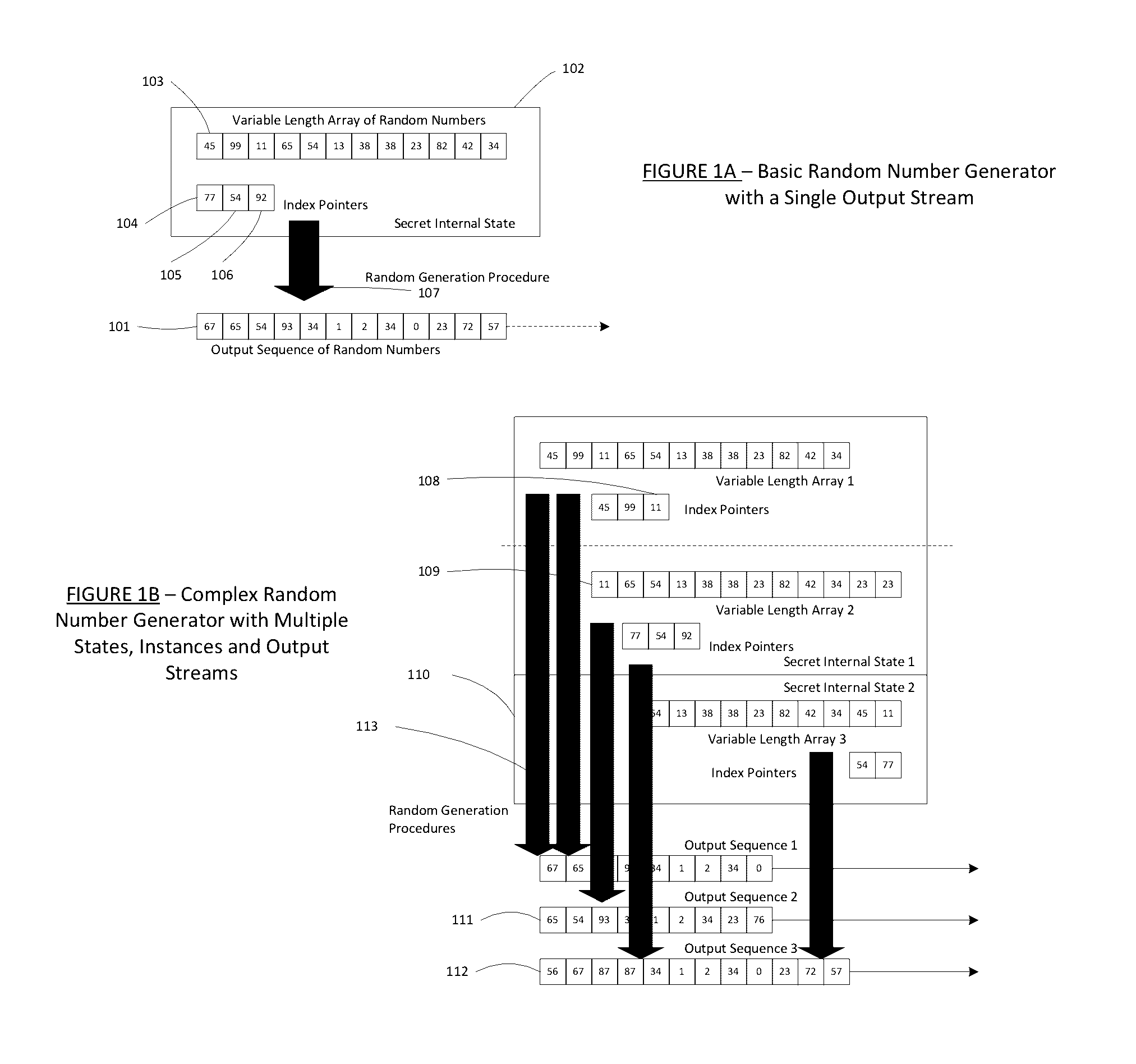
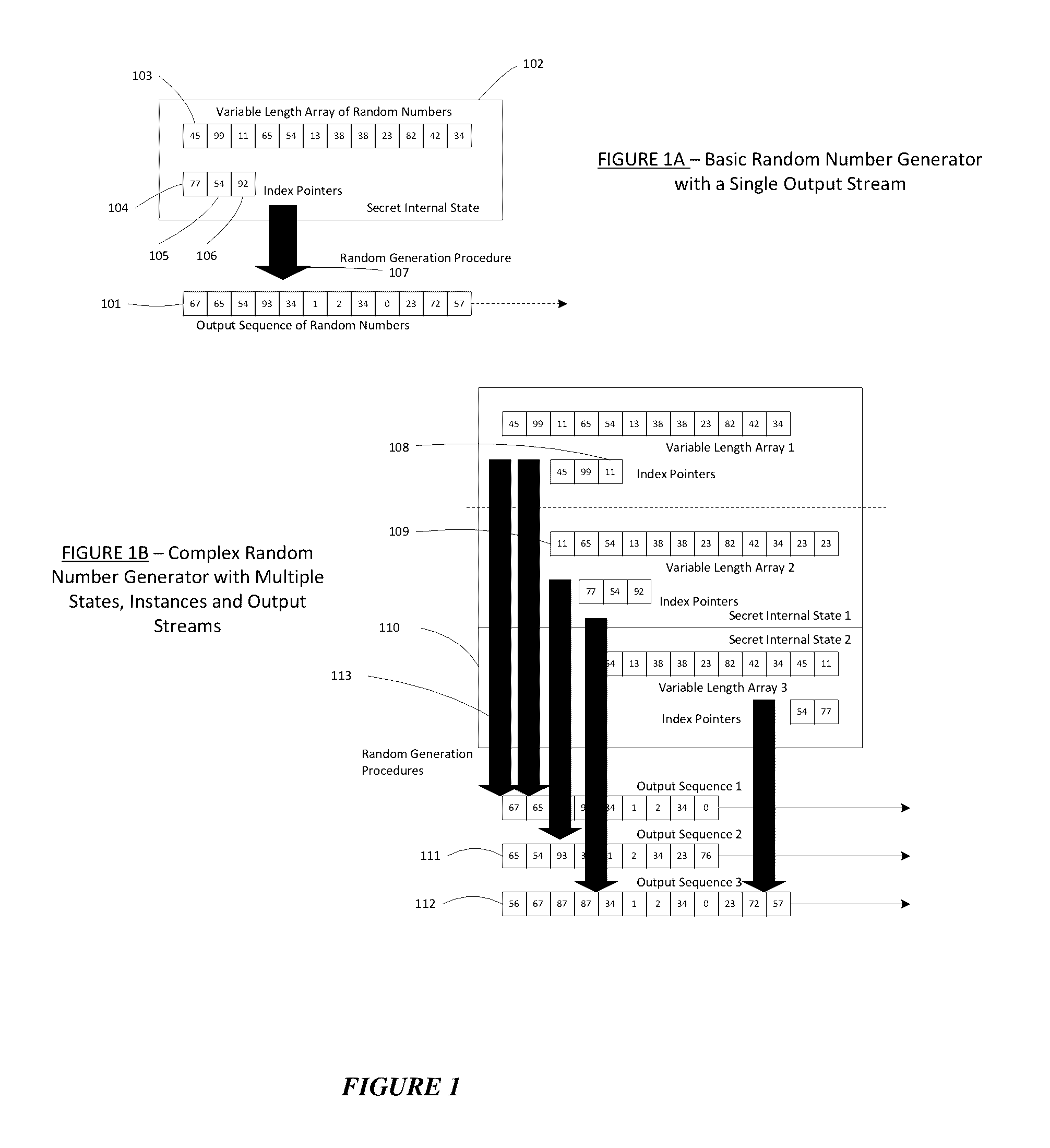
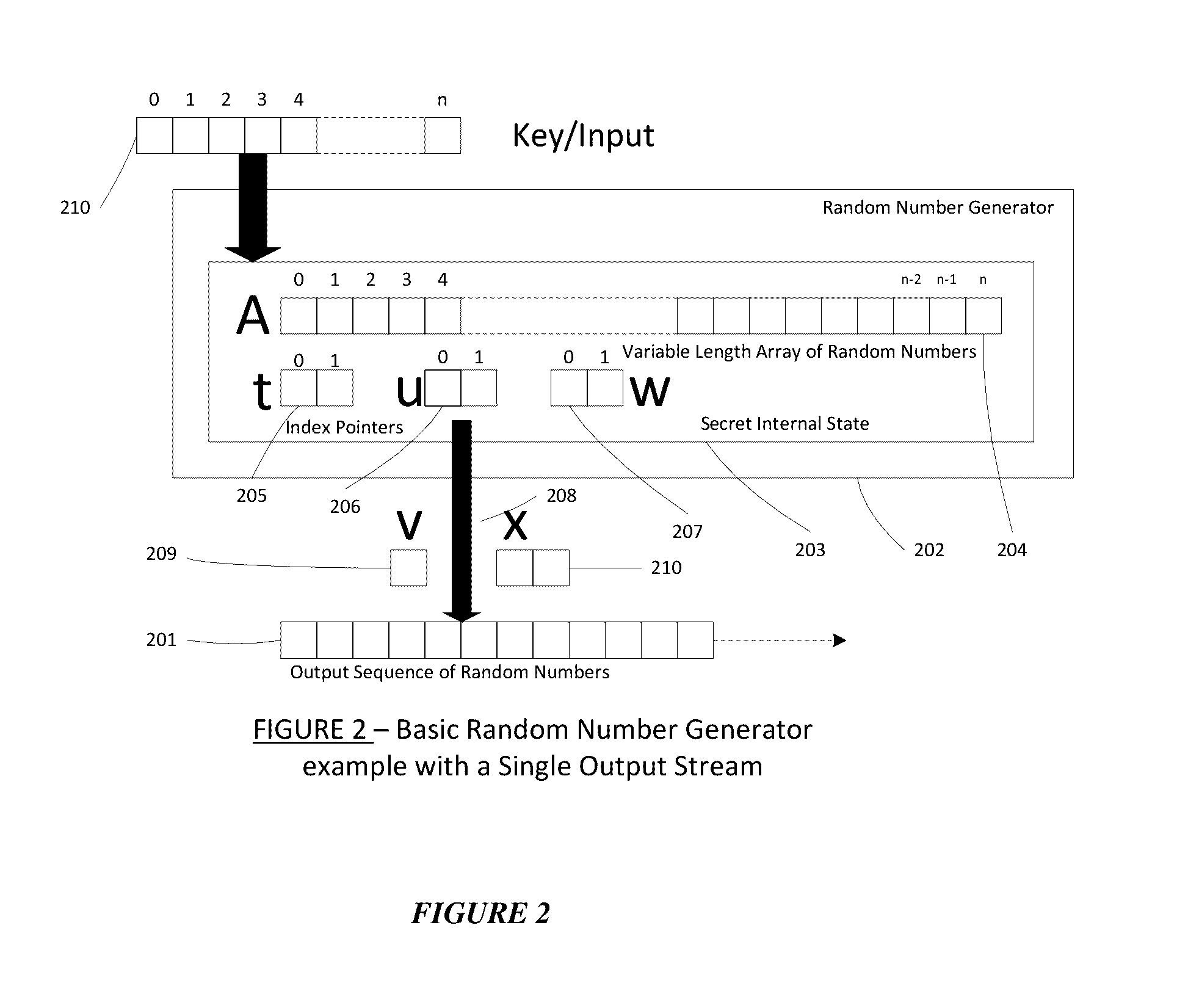
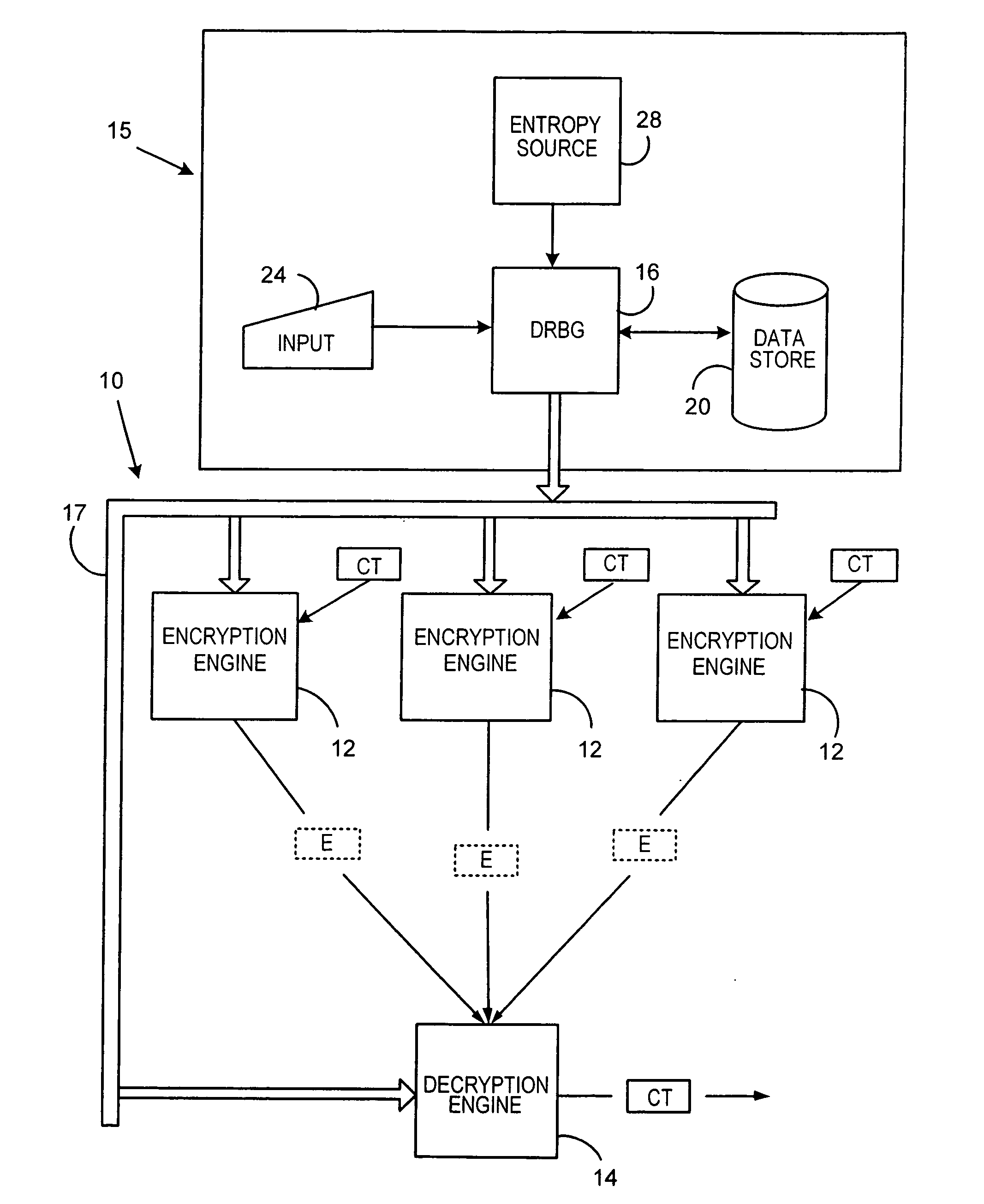
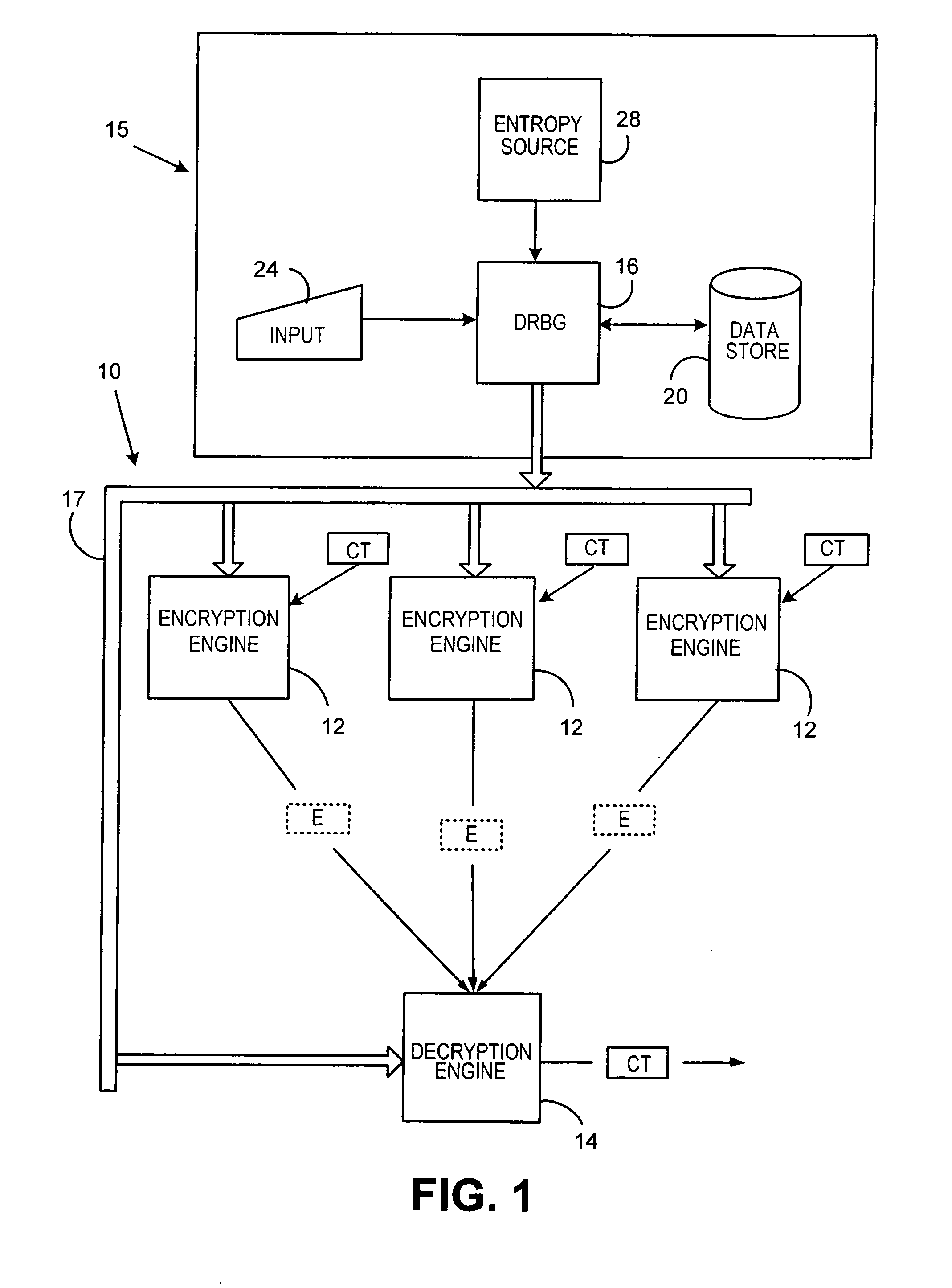
Method for a Dynamic Perpetual Encryption Cryptosystem
A dynamic computer communication security encryption method or system using an initial seed key and multiple random number generators of a specific design, whereby a sequence of independent random entropy values is produced by one set of random number generators and encrypted along with the message stream using the initial seed key, or the output of a second set of random number generators initialized with the initial seed key, and following the subsequent transmission of the variable encrypted entropy / message block, the entropy values are used to symmetrically or identically augment or increase the current uncertainty or entropy of the cryptosystem at both the sender and the receiver, prior to the next encryption block operation. The encryption process effectively entailing the use of multiple encryption ciphers, and the entropy augmentation process entailing the encryption or application of various logical mathematical operations on the already dynamic but deterministic internal state values of the second set of random number generators, effectively altering their deterministic outputs in a random probabilistic manner.Random length message value sequences from one or more data sources is combined with one or more random length entropy value sequences from an independent source, following which the entropy “updates” may also be used to alter, or change any cryptosystem variable, value or component in a randomly determined manner. In addition, whilst ensuring synchronization, the random entropy sequences also serve to “pollute” the cipher-stream and thereby hinder most current forms of cryptanalysis, whilst simultaneously injecting additional entropy into the cryptographic system and allowing for its propagation to affect any connected system nodes, and thereby introducing unpredictable entropy into the system pseudorandom number generator outputs, and thereby ensuring the perpetual generation of unpredictable random numbers.Super-encryption mechanics are independent of the user data, simple, fast and efficient, and can incorporate compression, error correction and asymmetric encryption authentication routines. But most importantly, super-encryption ensures resistance to brute force attacks (not possible to verify if a message was even sent), an ability to exceed “perfect secrecy” requirements, and an improvement on previous super-encipherment design, since overhead can be dramatically reduced from 100% overhead.Communication links previously established by system nodes with central authorities may be used for secure node authentication and registration, whilst allowing the central authority to broker and synchronize communication channels and providing mutual authentication and other security functions between the system nodes.
Owner:FIGUEIRA HELDER SILVESTRE PAIVA
Keyword based topic-focused web crawler design method
ActiveCN106709052AImprove crawling efficiencyImprove effectivenessWeb data indexingSpecial data processing applicationsHyperlinkWeb crawler
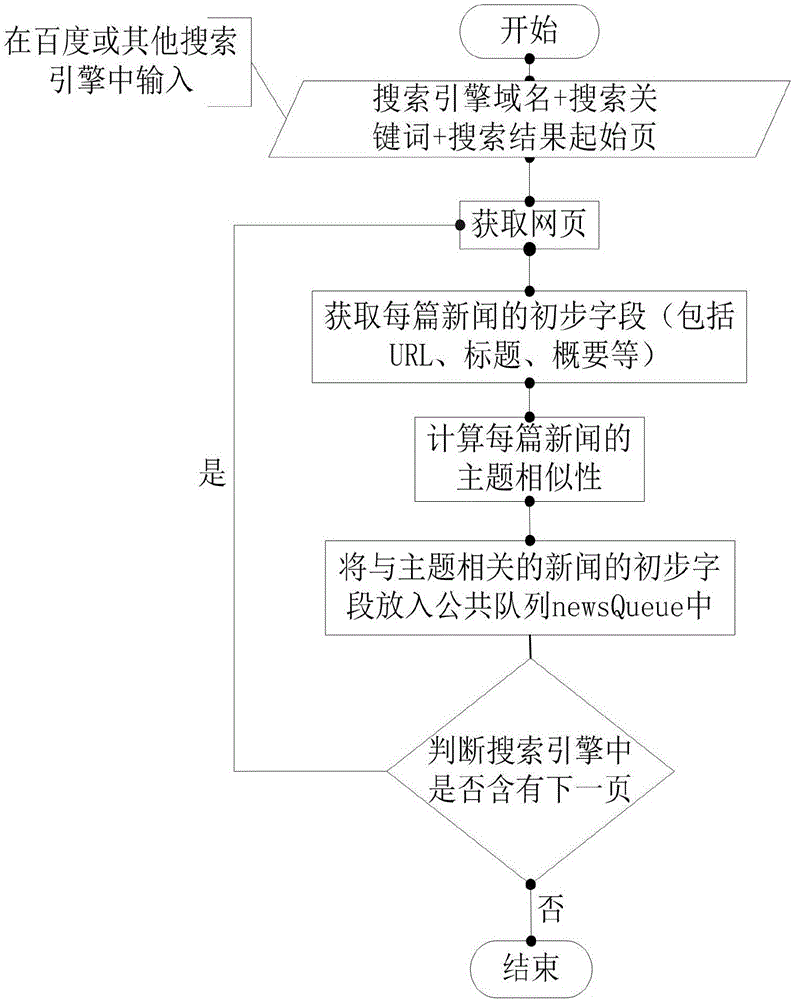
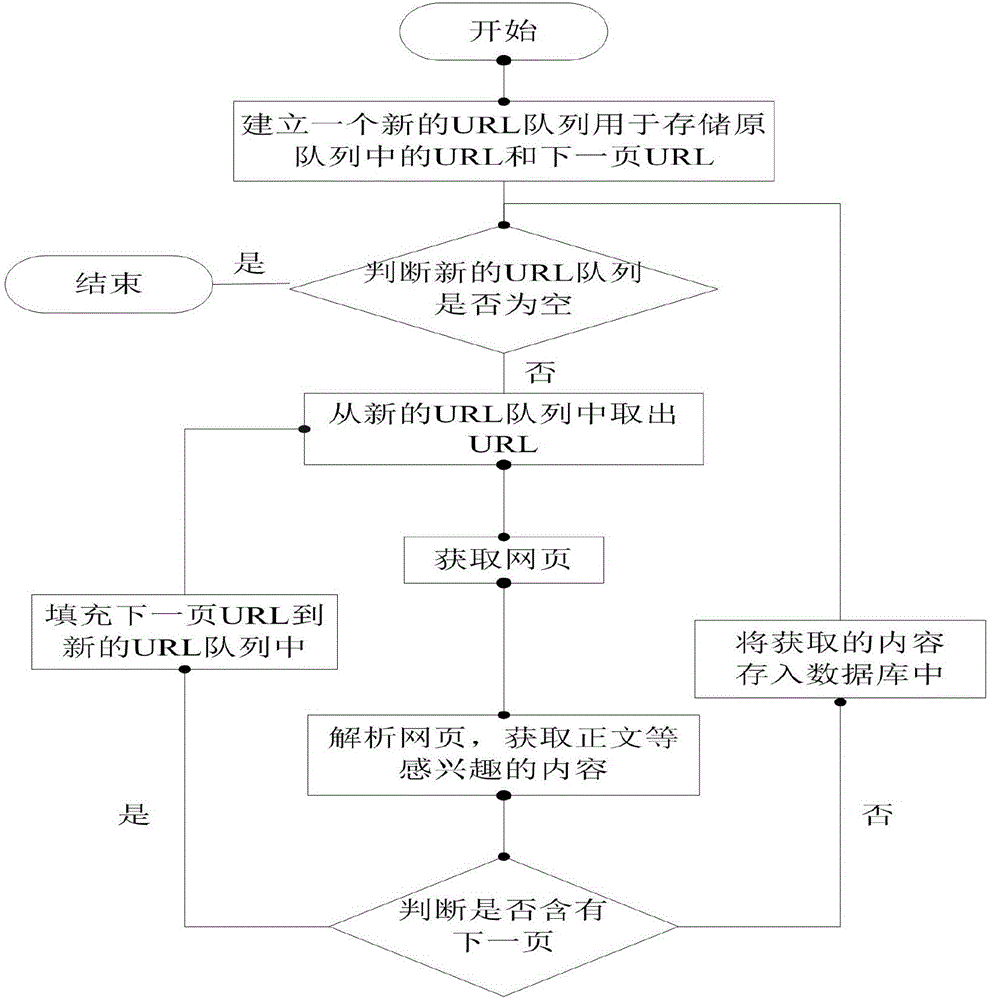
The invention provides a keyword based topic-focused web crawler design method. The method comprises the following steps: step (1), configuring a search URL of a topic keyword, and forming an initial seed hyperlink originalURL; step (2), according to the originalURL, searching and downloading web pages in a search engine, and extracting a preliminary field of news based on webpage contents; step (3), according to a topic correlation algorithm, obtaining the similarity between each news and the topic, keeping news fields relevant to the topic and putting the news fields in a public queue newsQueue, and filtering out news not relevant to the topic; step (4), downloading a webpage content of the next page according to a nextPage URL, extracting the nextPageURL and the relevant field in step (3), putting the relevant field into the public queue newsQueue, and repeating step (4) until there is no next page hyperlink nextPageURL; and step (5), taking out the URL from the newsQueue and handing the URL to a crawler processing thread, that is a consumer thread. The keyword based topic-focused web crawler design method provided by the invention improves the crawling efficiency of the topic-focused web crawler, and enhances the effectiveness of crawled URL resources.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
An intelligent medical image segmentation method based on three-dimensional reconstruction
ActiveCN109509199AEfficient use ofGood segmentation effectImage enhancementImage analysisImage segmentationImaging data
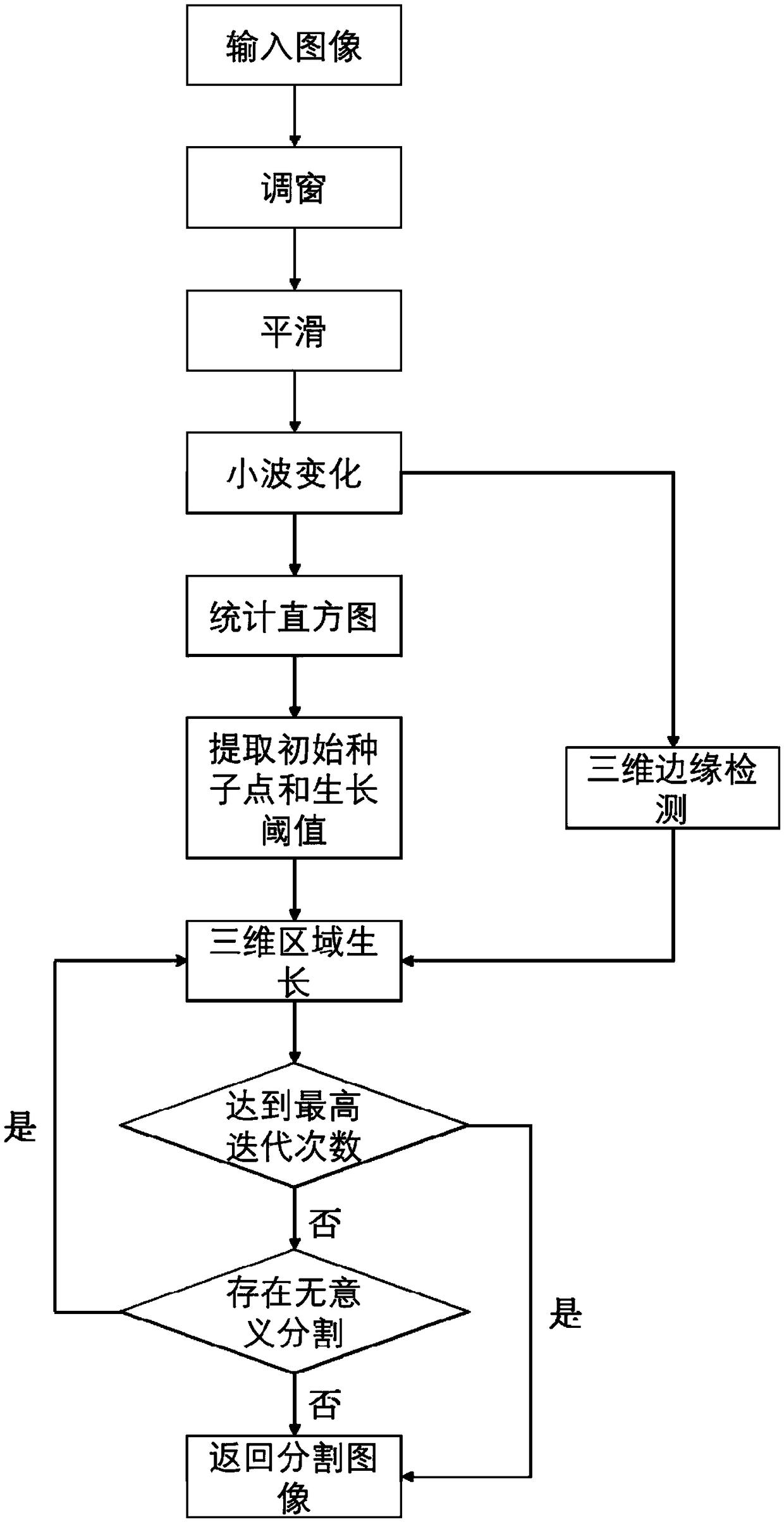
The invention discloses an intelligent segmentation method of medical image organization based on three-dimensional reconstruction, which comprises the following steps: 1) inputting DICOM medical image sequence, preprocessing the image and adjusting the window; 2) performing wavelet transformation on that image to reduce the image data to 1 / 4 of the original image; 3) performing statistic gray histogram to extract initial seed point and growth threshold; 4) carrying out three-dimensional edge detection on that image to obtain an edge contour map; 5) carrying out three-dimensional space regiongrowth by combining gray level and edge information; 6) Calculating the region attributes after segmentation, optimize the seed point and growth threshold. Through statistical histogram, the inventioncan automatically extract initial seed points required for region growth and threshold required for growth criterion, and then carry out three-dimensional region growth combined with edge contour information of an image, and continuously optimize initial seed points and growth threshold through iterative growth, thereby improving segmentation results. At that same time, the invention reduces theimage data to 1 / 4 of the original image through the wavelet change, thereby shortening the operation time.
Owner:SOUTH CHINA UNIV OF TECH
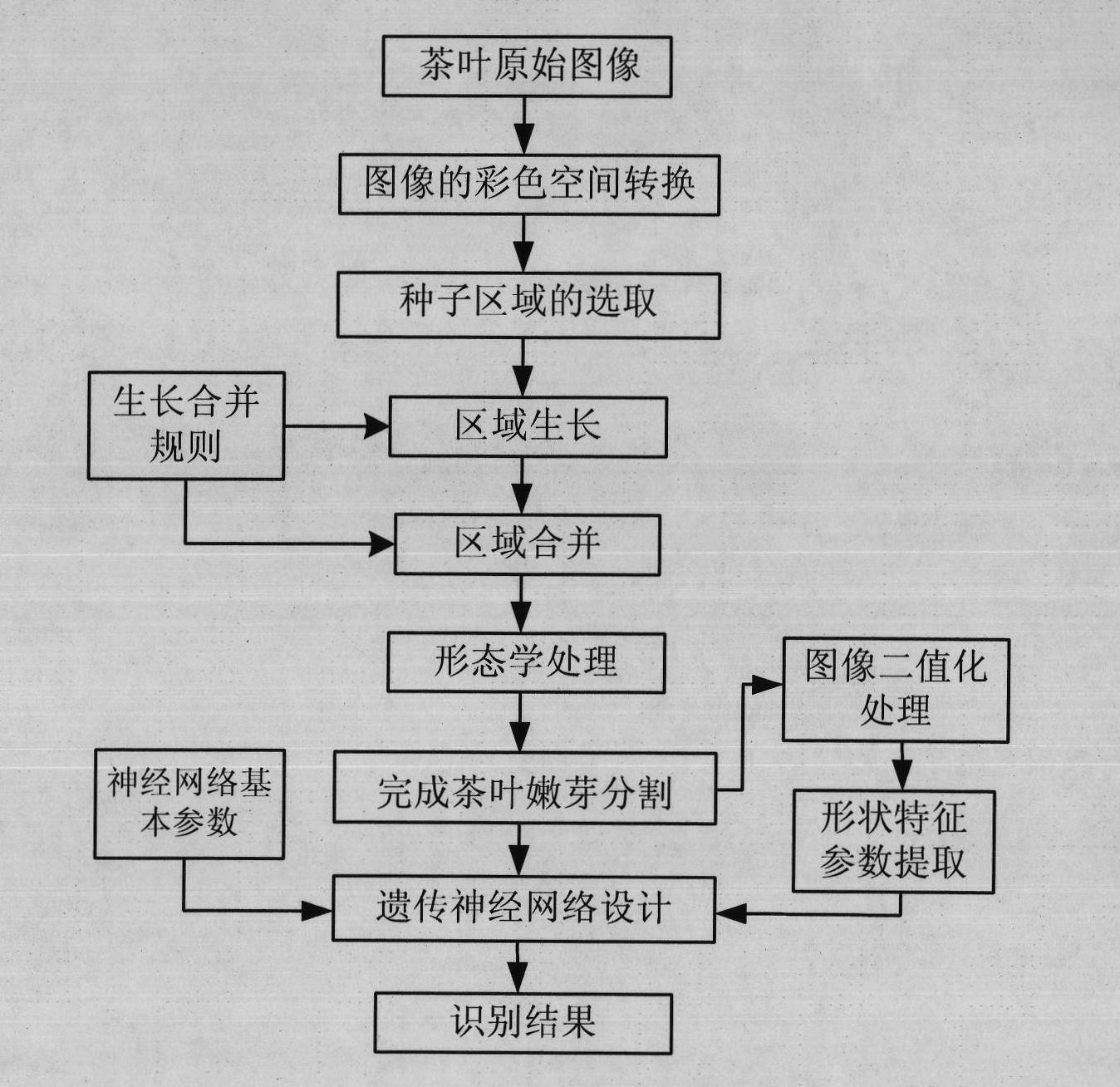
Tea tender shoot segmentation and identification method based on color and region growth
InactiveCN102013021AEasy to divideOvercome the shortcoming of easy to fall into local minimumImage enhancementCharacter and pattern recognitionColor imageImaging processing
The invention provides a novel tea tender shoot segmentation and identification method based on color and region growth, relating to the technical field of image processing. The method comprises the following steps of: firstly, converting the original tea RGB (Red, Green, Blue) color image into an HIS color space, and carrying out initial seed selection according to the parameters of hue H and saturation S therein; then carrying out region growth on a seed region according to the color similarity and region contiguity; carrying out region growth and combination by combining with color distance and edge distance to segment tea tender shoots; then extracting the shape feature parameters of binarized color and tender shoot images; and finally finishing identification through an improved hereditary neural network. Through a segmentation and identification experiment on the tea tender shoots in the tea image, the result shows that the algorithm can well separate the tea tender shoots from the tea image, well store the outline information of the tea tender shoots and obtain very good identification results.
Owner:SICHUAN AGRI UNIV
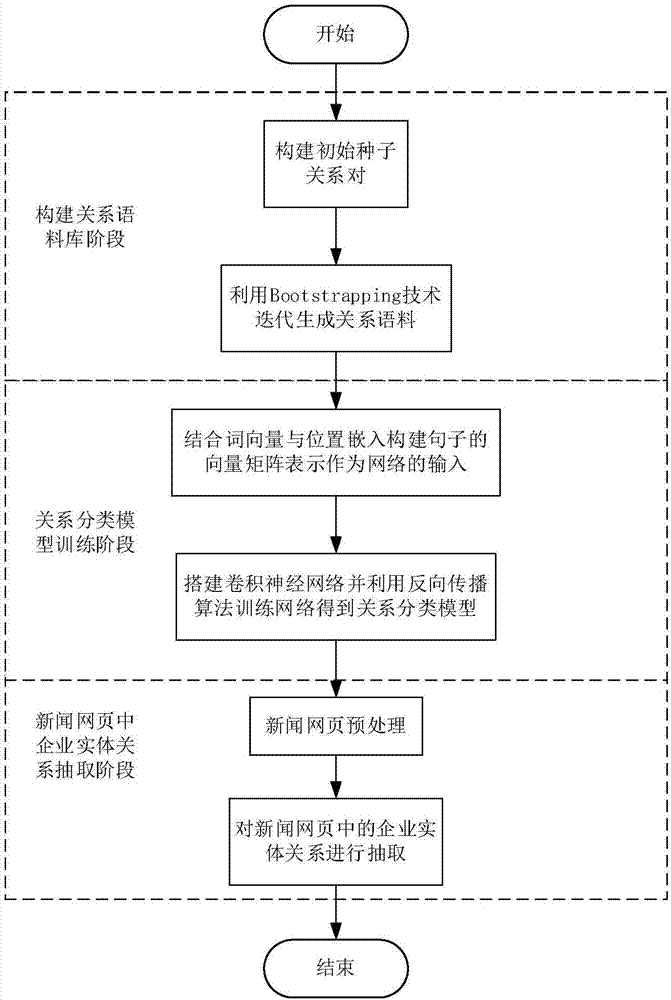
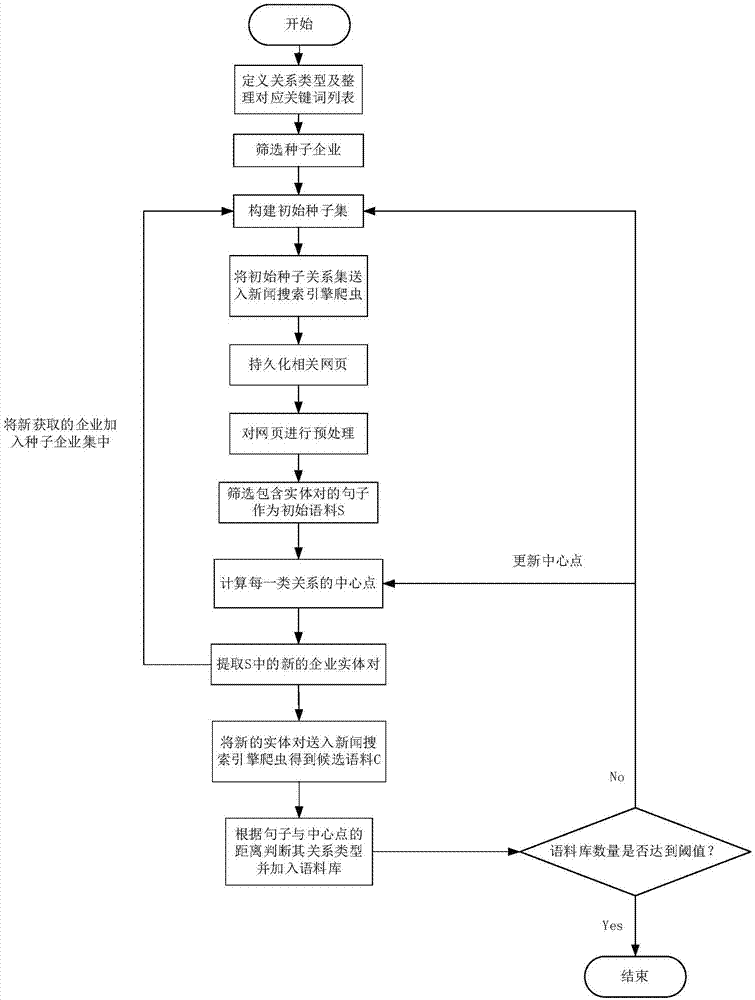
Enterprise entity relation extraction method based on convolutional neural network
InactiveCN107220237AAccurate and more efficient extractionAvoid the disadvantages of time-consuming and labor-intensive manual labelingNatural language data processingSpecial data processing applicationsRelation classificationNamed-entity recognition
The invention discloses an enterprise entity relation extraction method based on a convolutional neural network. The method comprises the steps of a relation corpus building stage, wherein an initial seed relation pair set is built artificially, and by means of an internet search engine and a Bootstrapping technology, relation language materials are generated in an iteration mode, and finally a relation corpus is formed; a relation classification model training stage, wherein term vectors and position embedding are combined to build a sentence vector matrix representation to serve as input of a network, the convolutional neural network is built, the network is trained by means of a back propagation algorithm, and a relation classification model is obtained; an enterprise entity relation extraction stage in a web page, wherein the web page is preprocessed by combining web page text extraction with a named entity identification technology, and then enterprise entity relation extraction is conducted on the preprocessed web page. By means of the method, not only the defects of an artificial feature method can be overcome, but also the enterprise entity relation can be extracted from the web page more accurately and efficiently.
Owner:NANJING UNIV
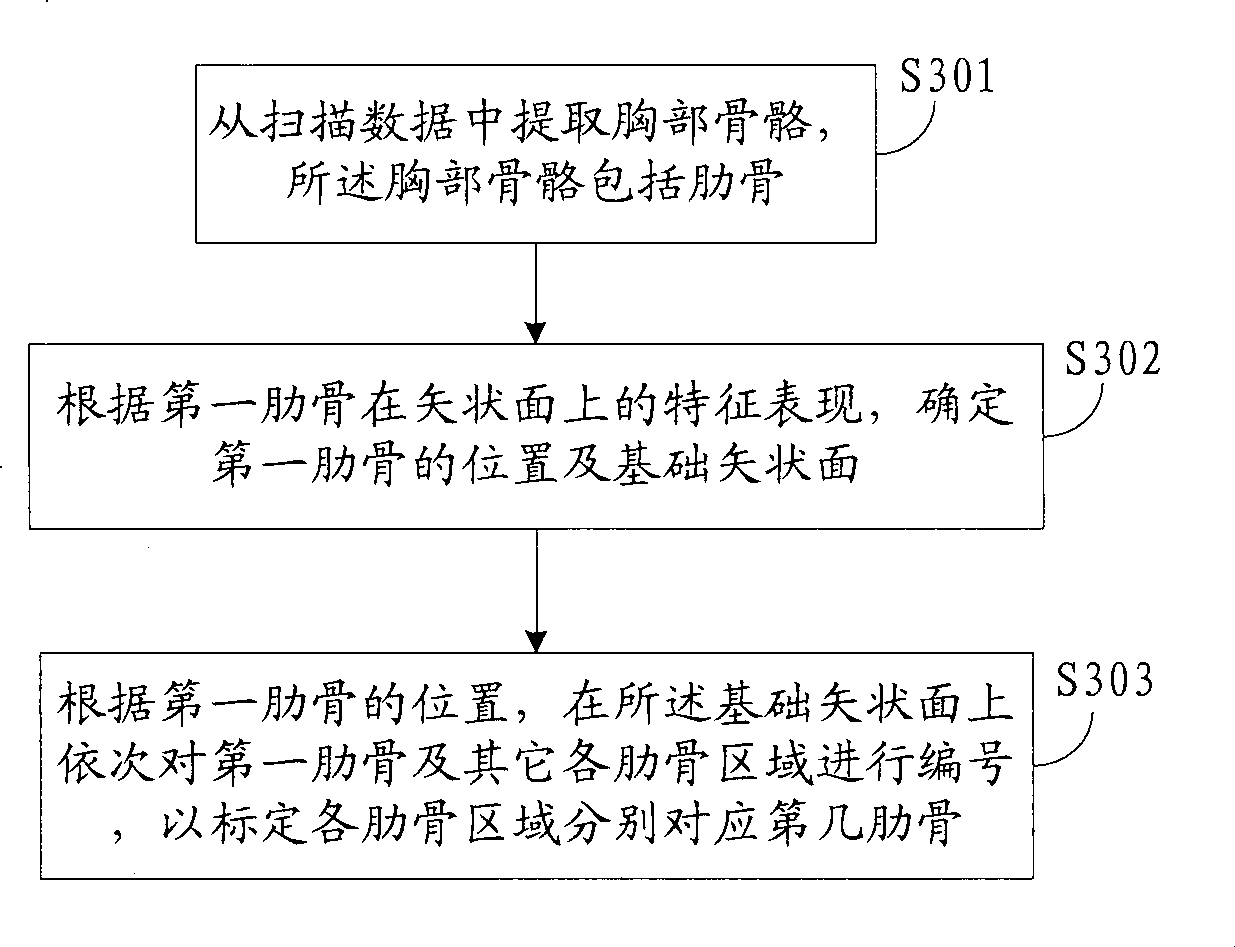
Rib auto-demarcating method and device
ActiveCN101452577AEasy to determinePrecise positioningImage analysisComputerised tomographsThoracic boneSagittal plane
The invention discloses an automatic rib marking method, which comprises: extracting thoracic bones from scan data, wherein the thoracic bones comprise ribs; according to the feature representation of a first rib on a sagittal plane, determining the position of the first rib and a basic sagittal plane; according to the position of the first rib, coding the first rib and other rib regions on the basic sagittal plane to mark the sequence number of the ribs corresponding to the rib regions. The invention also discloses an automatic rib marking device. The method can accurately mark the rib regions according to the feature presentation of the ribs on the sagittal plane; in addition, the method can obtain ideal rib outlines easily, facilitate the initial seed points of the ribs and consequently complete the positioning of the whole ribs accurately.
Owner:NEUSOFT MEDICAL SYST CO LTD
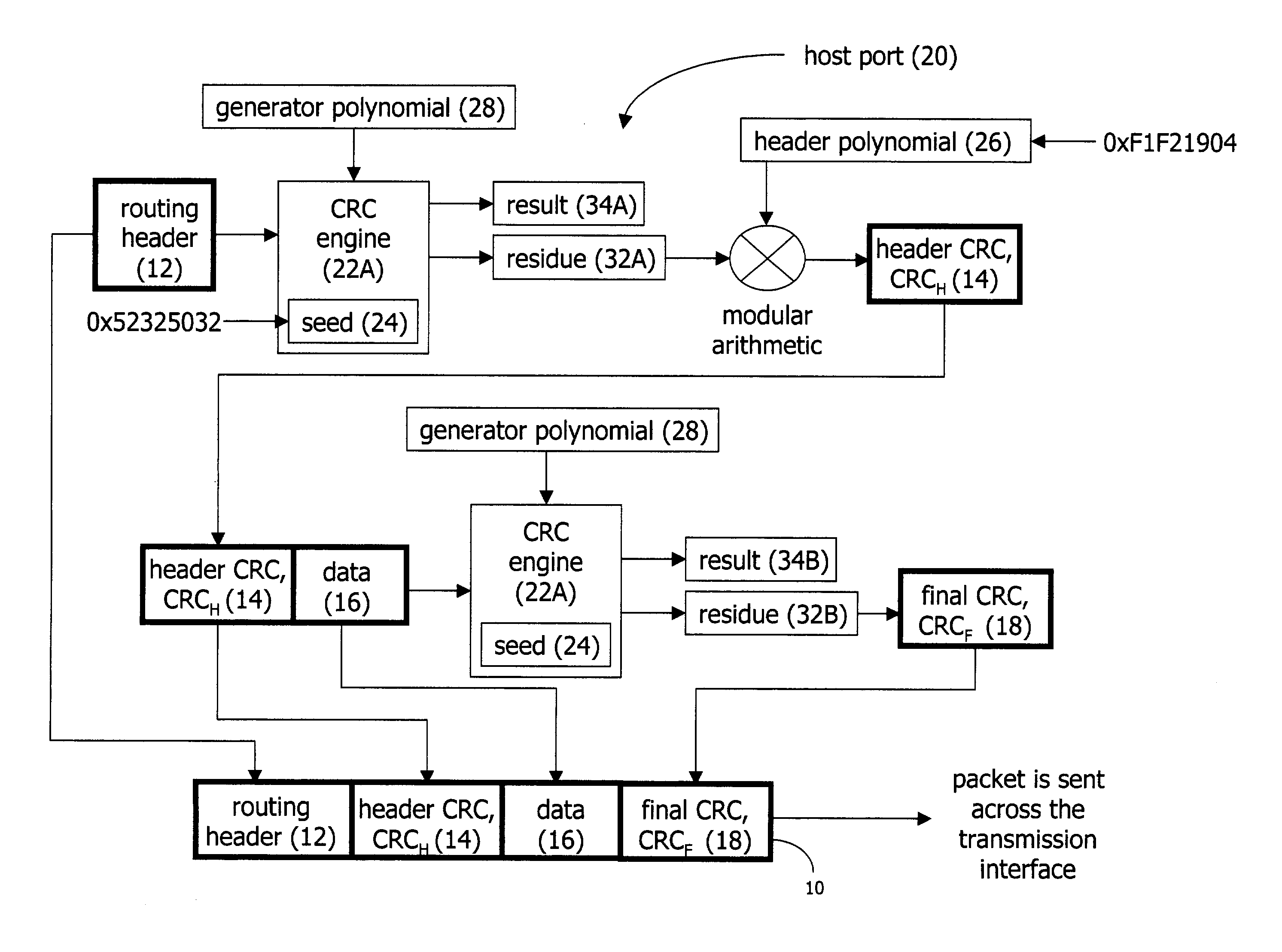
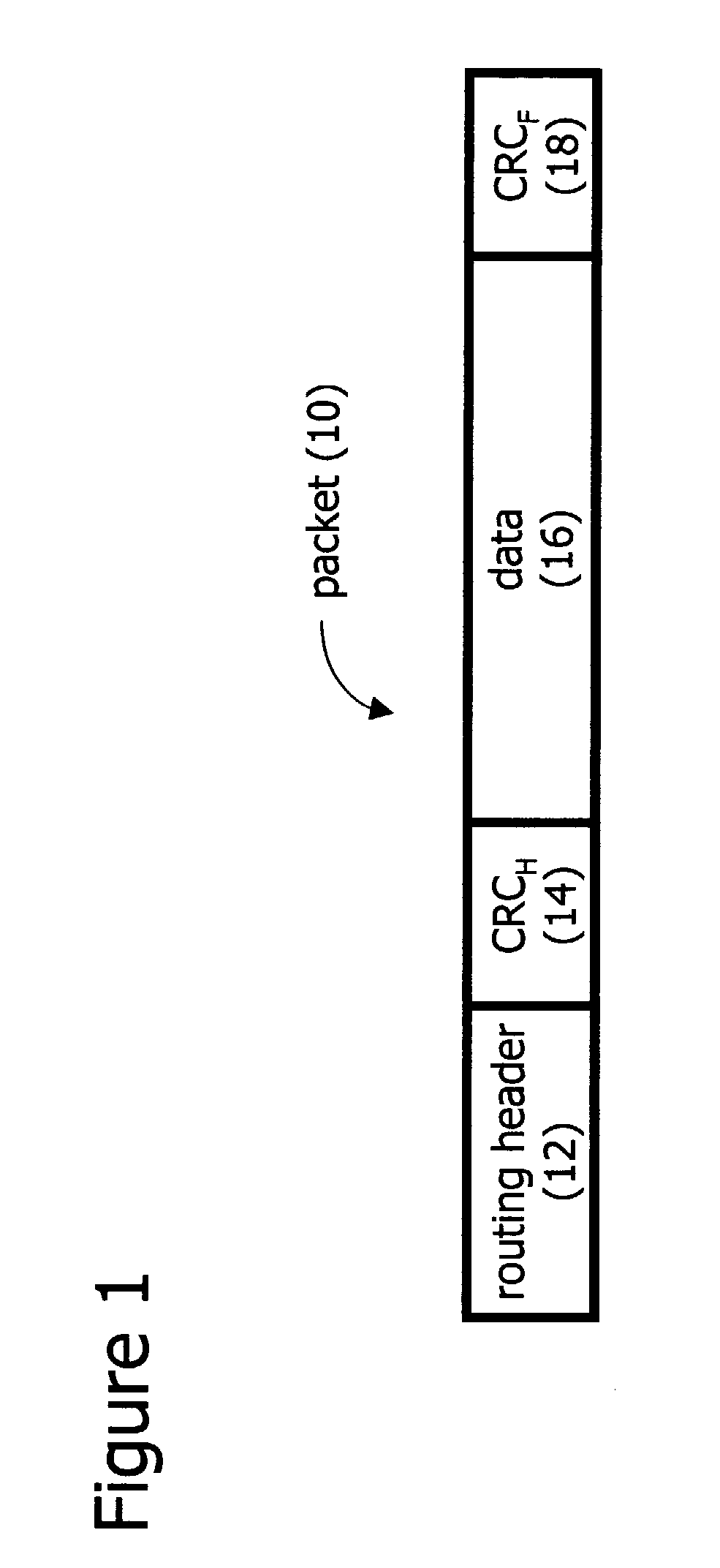
CRC calculation for data with dynamic header
A method for performing CRC calculations on packets with dynamic headers is disclosed. The header may be changed during transmission across a network. When the header is changed, a CRC associated with the header is recalculated such that a residue of the initial seed value is always obtained. A final CRC covers the entire packet including the header and its header CRC, or just the data portion of the packet. The final CRC remains valid and unchanged during transmission of the packet, allowing an endpoint along the network to confirm the validity of the entire packet. By only changing the CRC associated with the changed portion of the packet (the header CRC), the introduction of errors during transmission of the packet is minimized.
Owner:INTEL CORP
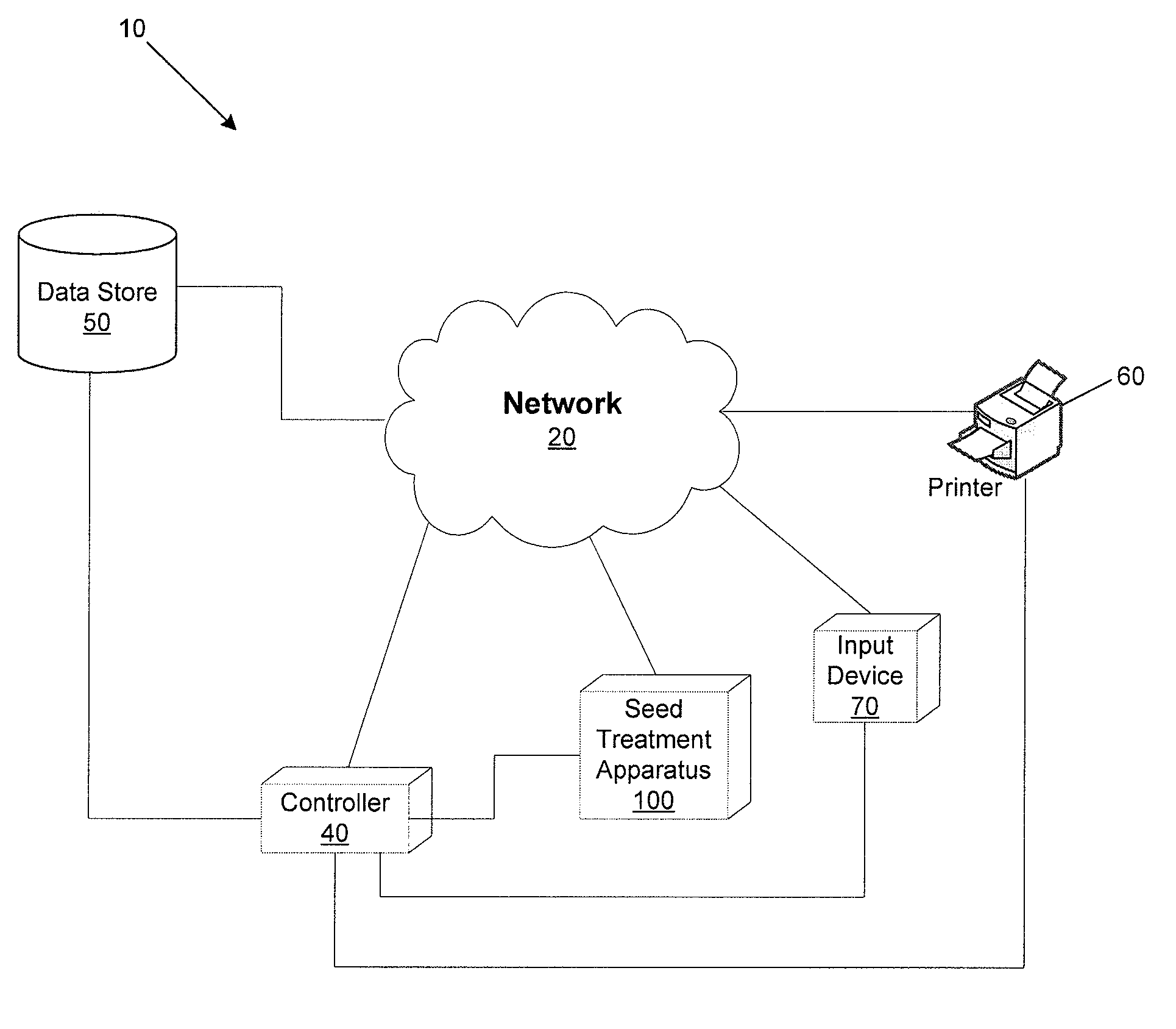
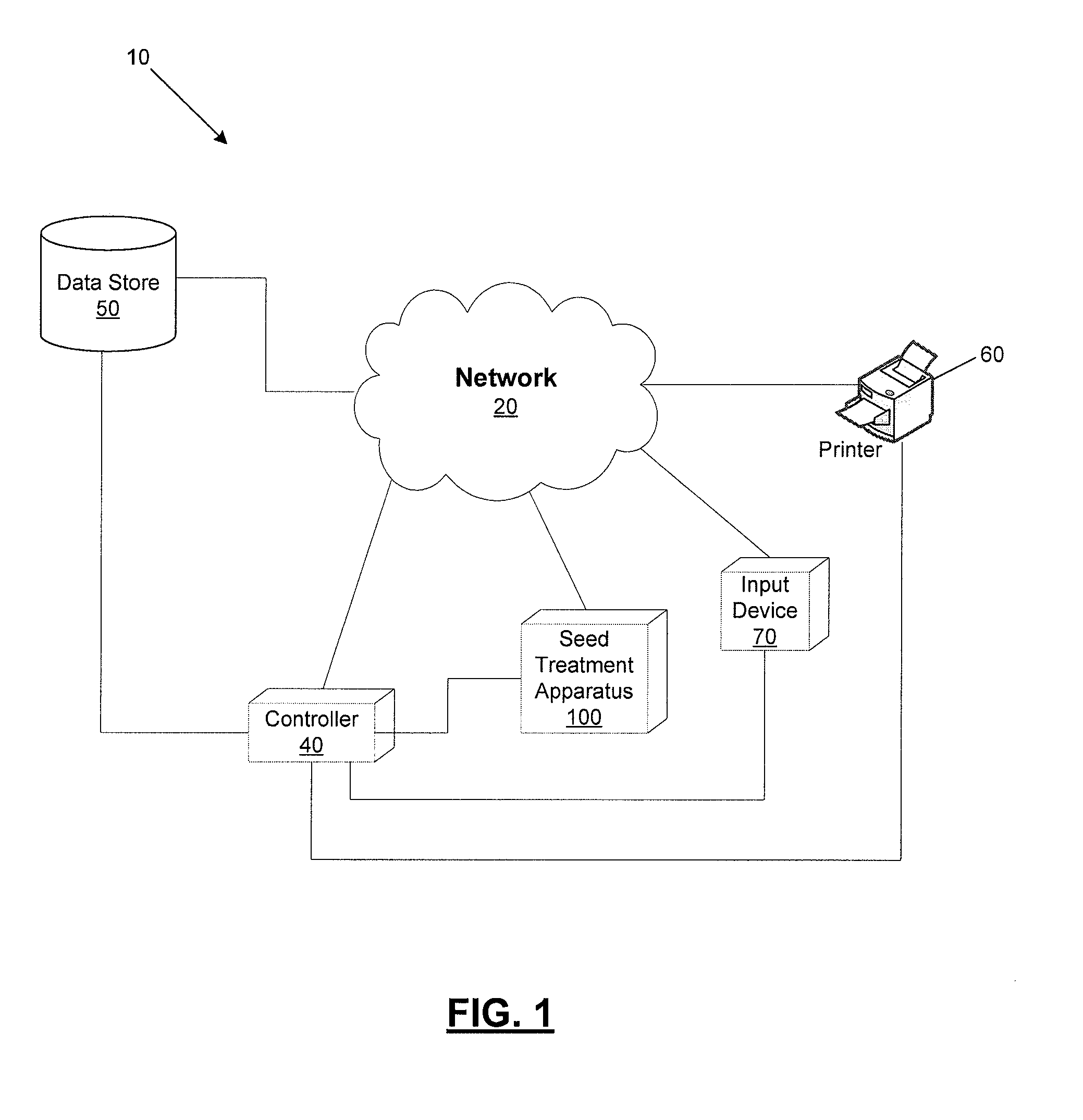
Intelligent seed treatment system and method
ActiveUS20090125552A1Accurately and consistently and predictably treating seed sampleAccurate informationSeed and root treatmentSpecial data processing applicationsEngineeringResearch plan
A system and method for treating a least a portion of an initial seed sample to create one or more treated seed samples is provided. In various embodiments, one or more seed treatment apparatus components are in communication with one or more controllers such that seed samples treated by a seed treater may be treated at least in part based on one or more instruction sets that may be associated with one or more research plans. As a result, the method and system are configured to accurately, consistently, and predictably treat seed samples, and to adapt and change the treatment of seed samples based on changing research plans.
Owner:PIONEER HI BRED INT INC
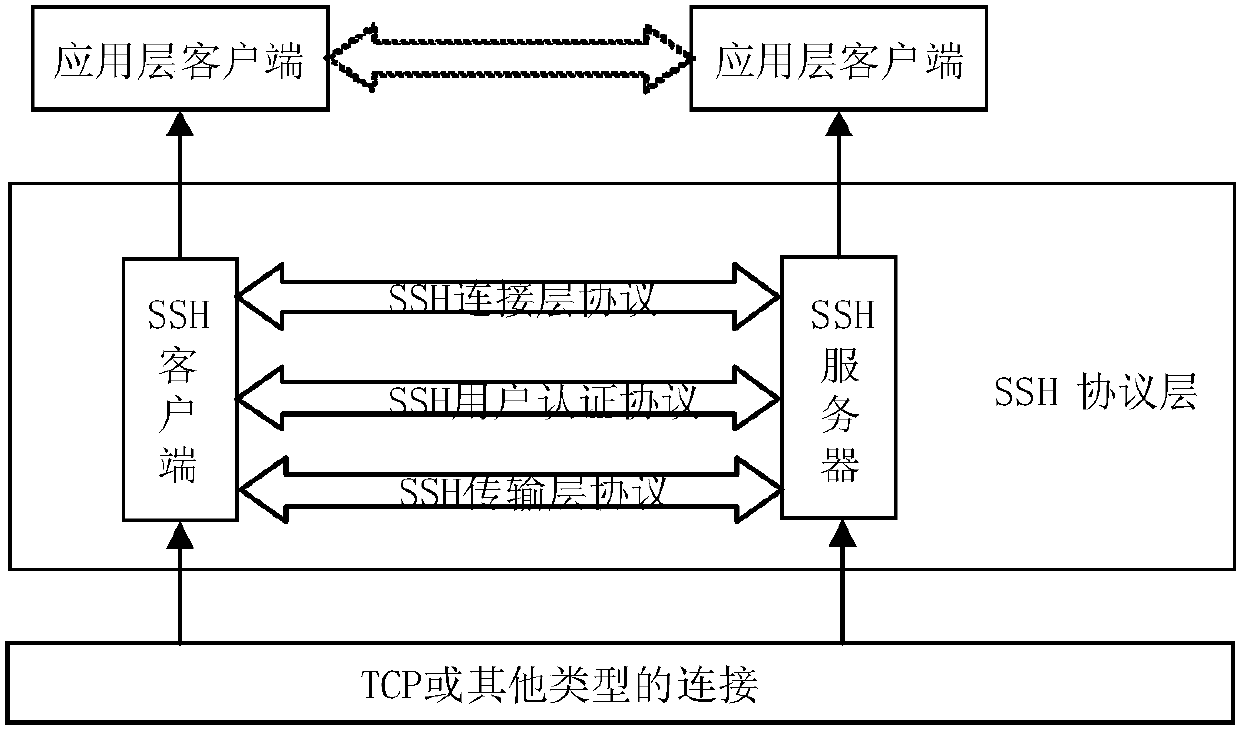
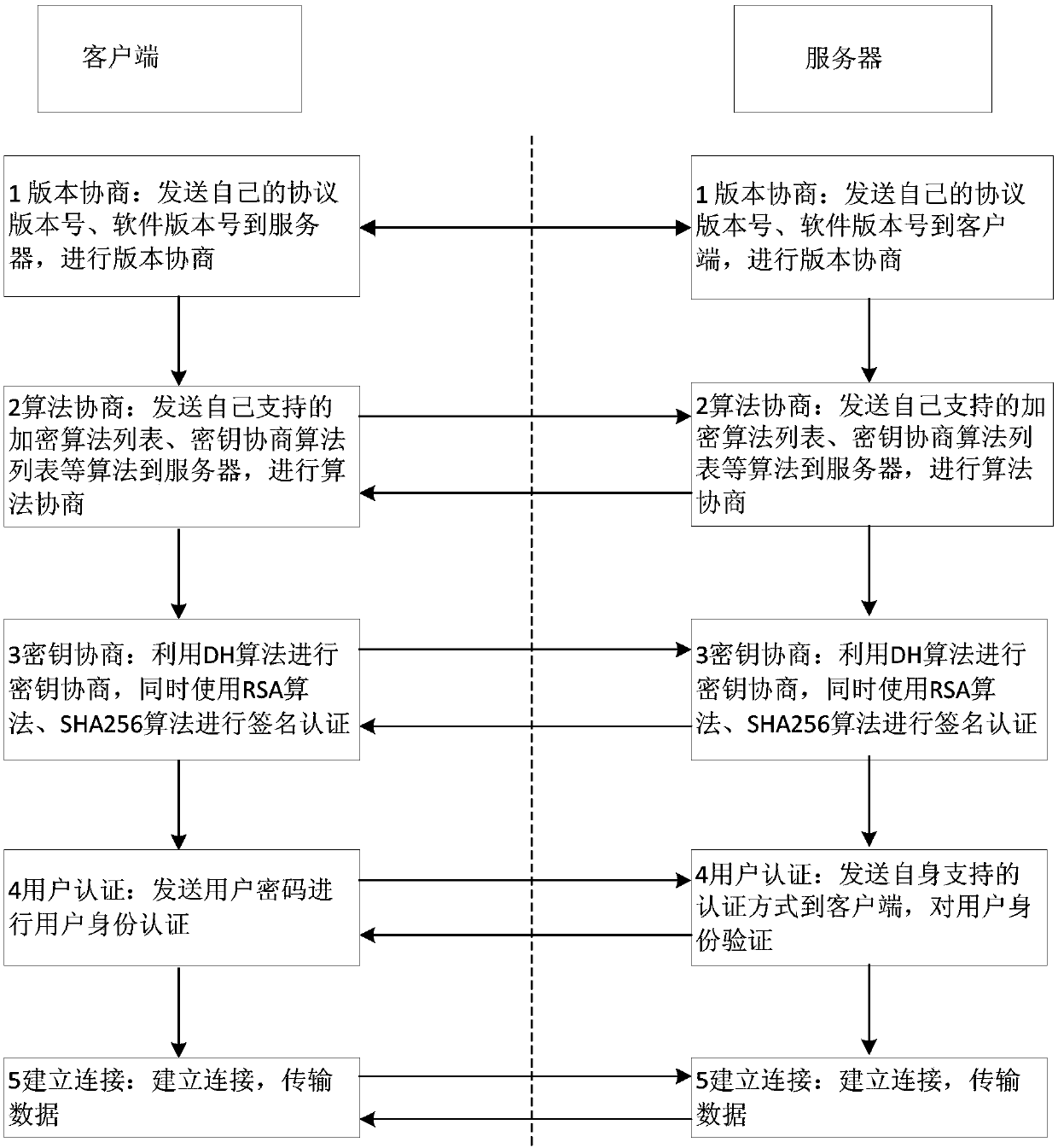
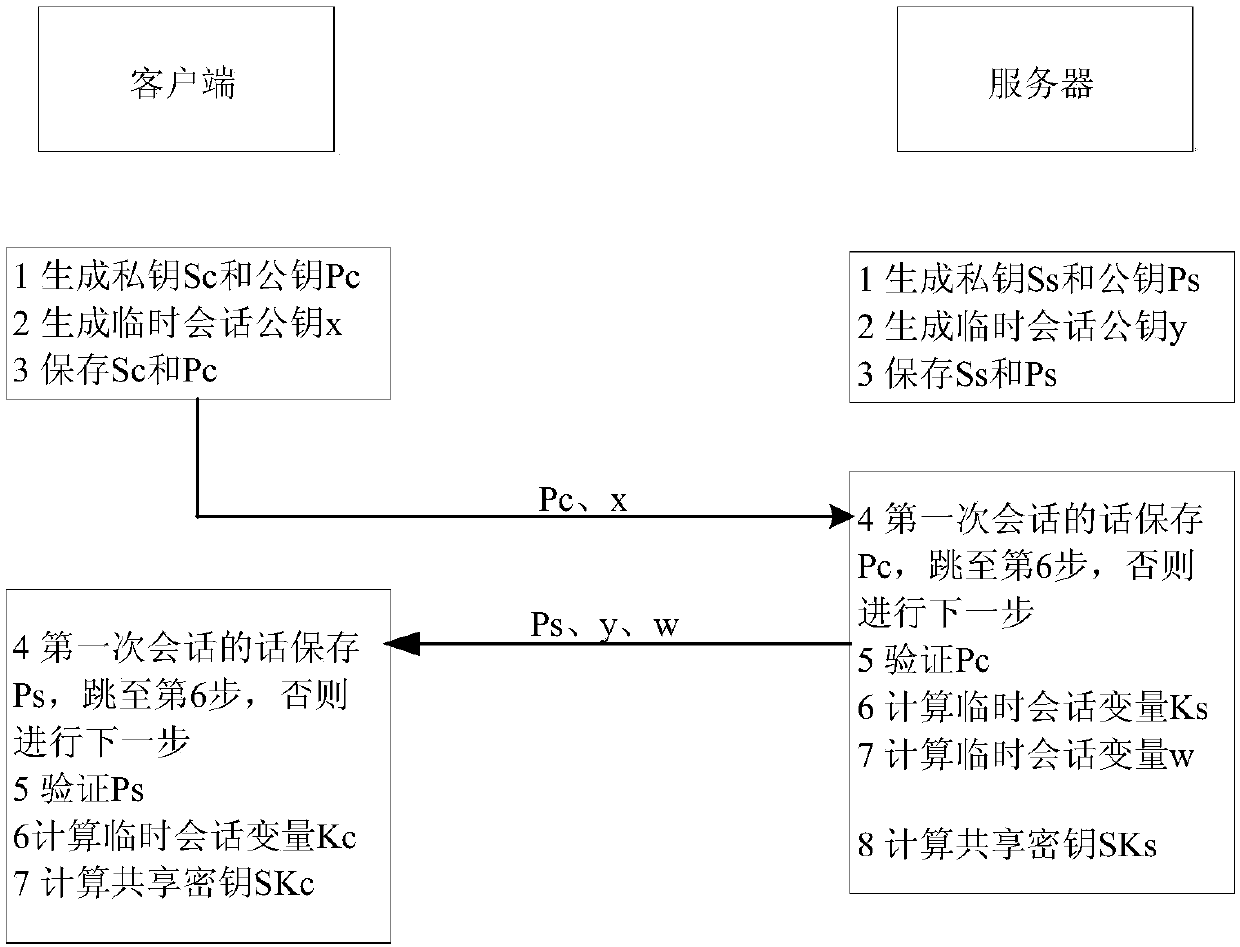
Method and system for achieving SSH protocol based on post-quantum key exchange
ActiveCN108111301ASolve untrustworthyKey distribution for secure communicationUser identity/authority verificationKey exchangeQuantum algorithm
The invention belongs to the technical field of information, and particularly relates to a method and system for achieving SSH protocol based on post-quantum key exchange. The method comprises the steps of a client and a server respectively calculating a public and private key pair; calculating a temporary session public key of the client, and sending the client public key and the client temporarysession public key to the server; the server performing identity verification on the client; calculating a temporary session public key of the server; calculating a temporary session variable of theserver and a temporary session error eliminating variable, the server sharing secret key initial seeds; the server generating a final server sharing secret key of the conversation through the post-quantum algorithm; the client side verifying the identity of the server according to the public key of the server; the client passes the identity identification of the server, calculating the temporary session variables of the client and the initial seed of the shared secret key of the client; and the client side using a post-quantum algorithm to generate a final client shared secret key of the conversation. According to the method and the system, the attack of the quantum computer can be effectively resisted, and the safety of the network is ensured.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
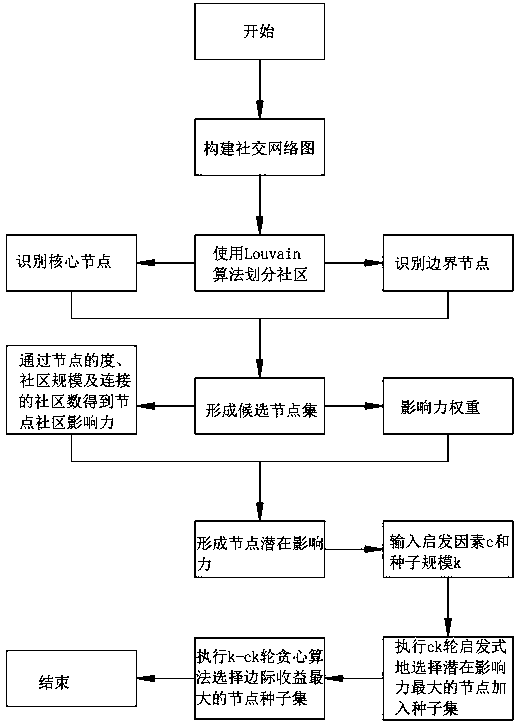
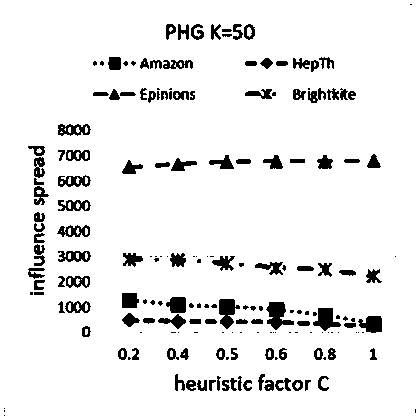
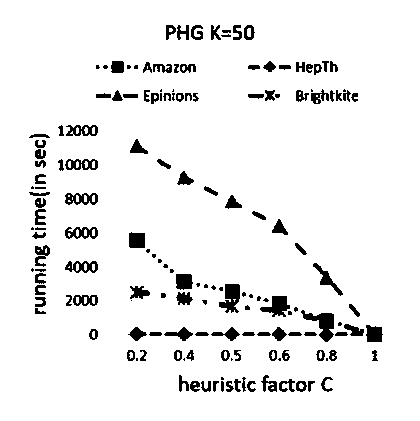
Social network influence maximization method based on community structure
ActiveCN108492201ASolving the Influence Maximization ProblemImprove accuracyData processing applicationsNODALCommunity based
The invention discloses a social network influence maximization method based on a community structure. The method comprises the following specific processes that: (1) dividing a community, forming a candidate node set, dividing a network to identify a kernel node and a boundary node in the network, and forming the candidate node set; (2) heuristically selecting nodes, and for each node in the candidate node set, verifying potential influence through a node degree, a community scale, a connected community number and influence weight so as to heuristically select and add the node with the highest influence into a seed set; and (3) executing a greedy algorithm, and utilizing the greedy algorithm to select and add the node with the highest marginal income into the seed set. By use of the method, the function of the community structure in influence spreading is analyzed to further improve accuracy and operation efficiency for mining initial seed nodes, and the problem of social network influence maximization is effectively solved.
Owner:SHANDONG UNIV OF SCI & TECH
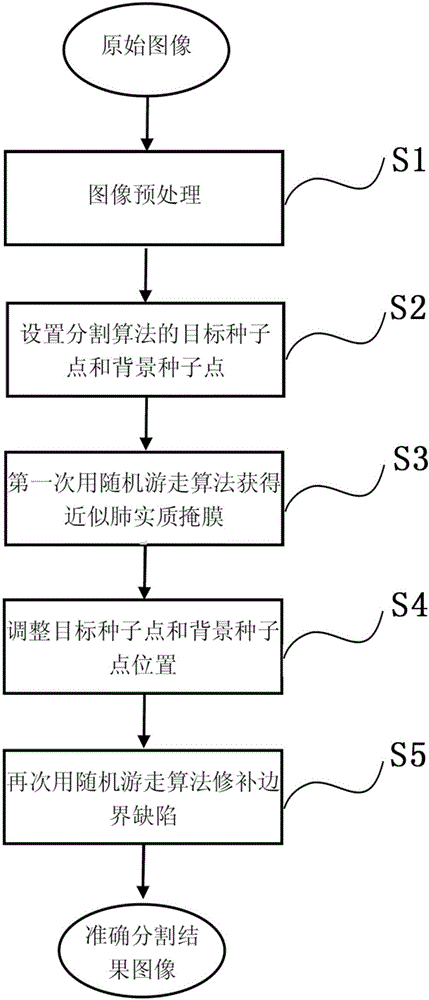
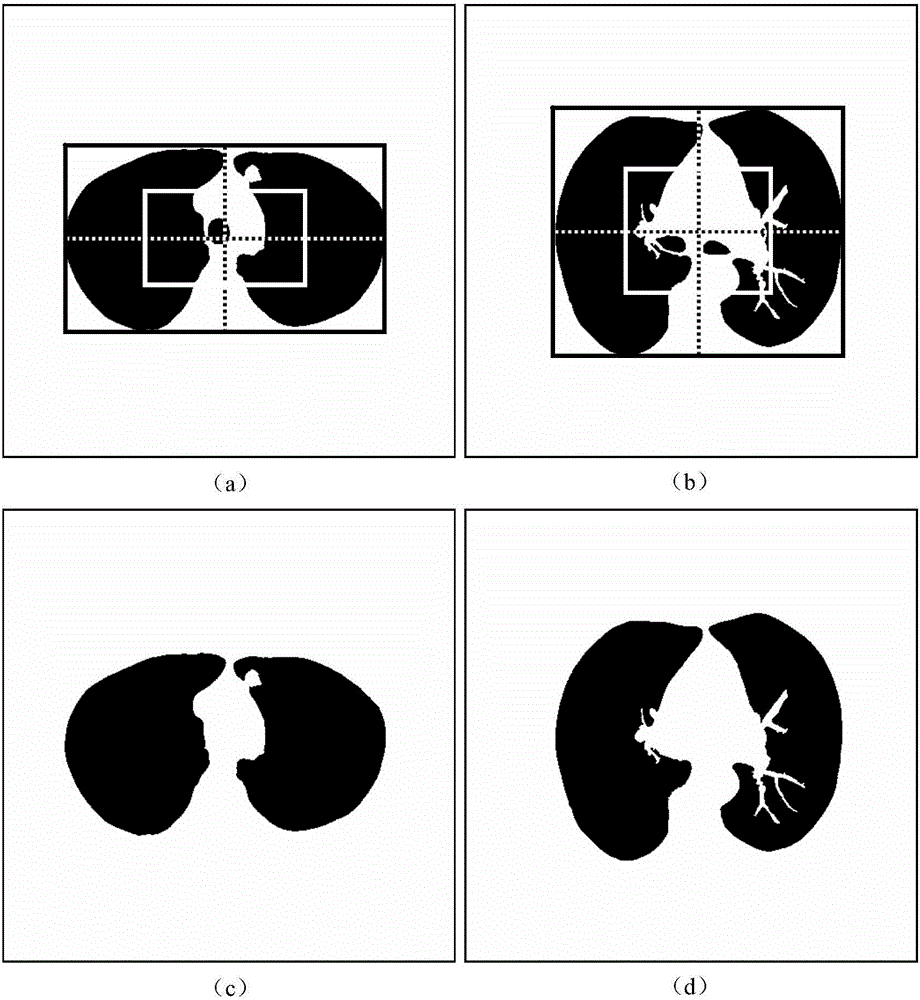
Automatic division method for pulmonary parenchyma of CT image
InactiveCN104992445AThe segmentation result is accurateImprove applicabilityImage enhancementImage analysisPulmonary parenchymaNatural science
The invention provides an automatic division method for pulmonary parenchyma of a CT image. According to the automatic division method, the CT is divided through carrying out a random migration algorithm for two times to obtain the accurate pulmonary parenchyma; in the first time, the random migration algorithm is used for dividing to obtain a similar pulmonary parenchyma mask; and in the second time, the random migration algorithm is used for repairing defects of the periphery of a lung and dividing to obtain an accurate pulmonary parenchyma result. Seed points, which are set by adopting the random migration algorithm to divide, are rapidly and automatically obtained through methods including an Otsu threshold value, mathematical morphology and the like; and manual calibration is not needed so that the working amount and operation time of doctors are greatly reduced. According to the automatic division method provided by the invention, a process of 'selecting the seed points for two times and dividing for two times' is provided and is an automatic dividing process from a coarse size to a fine size; and finally, the dependence on the selection of the initial seed points by a dividing result is reduced, so that the accuracy, integrity, instantaneity and robustness of the dividing result are ensured. The automatic division method provided by the invention is funded by Natural Science Foundation of China (NO: 61375075).
Owner:HEBEI UNIVERSITY
System and method for generating user recommendations
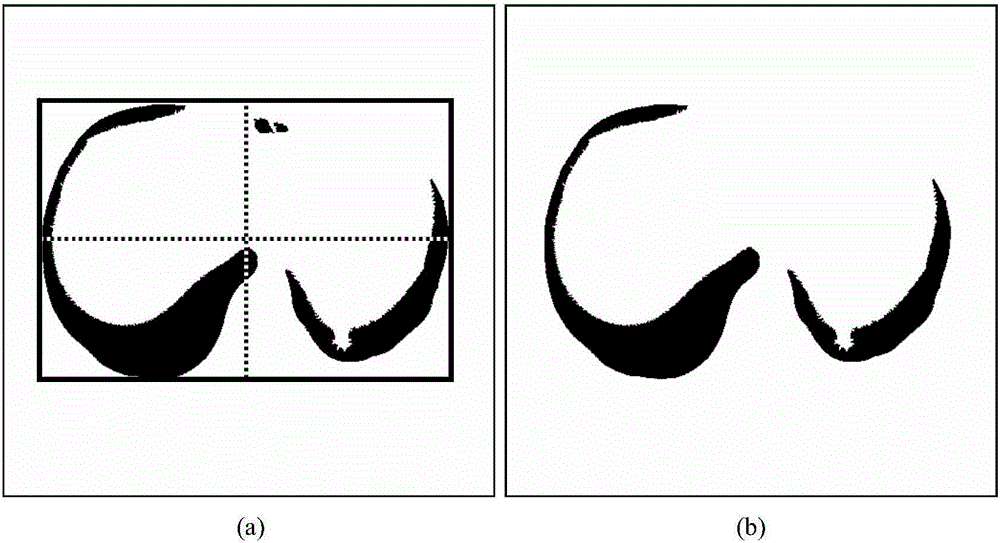
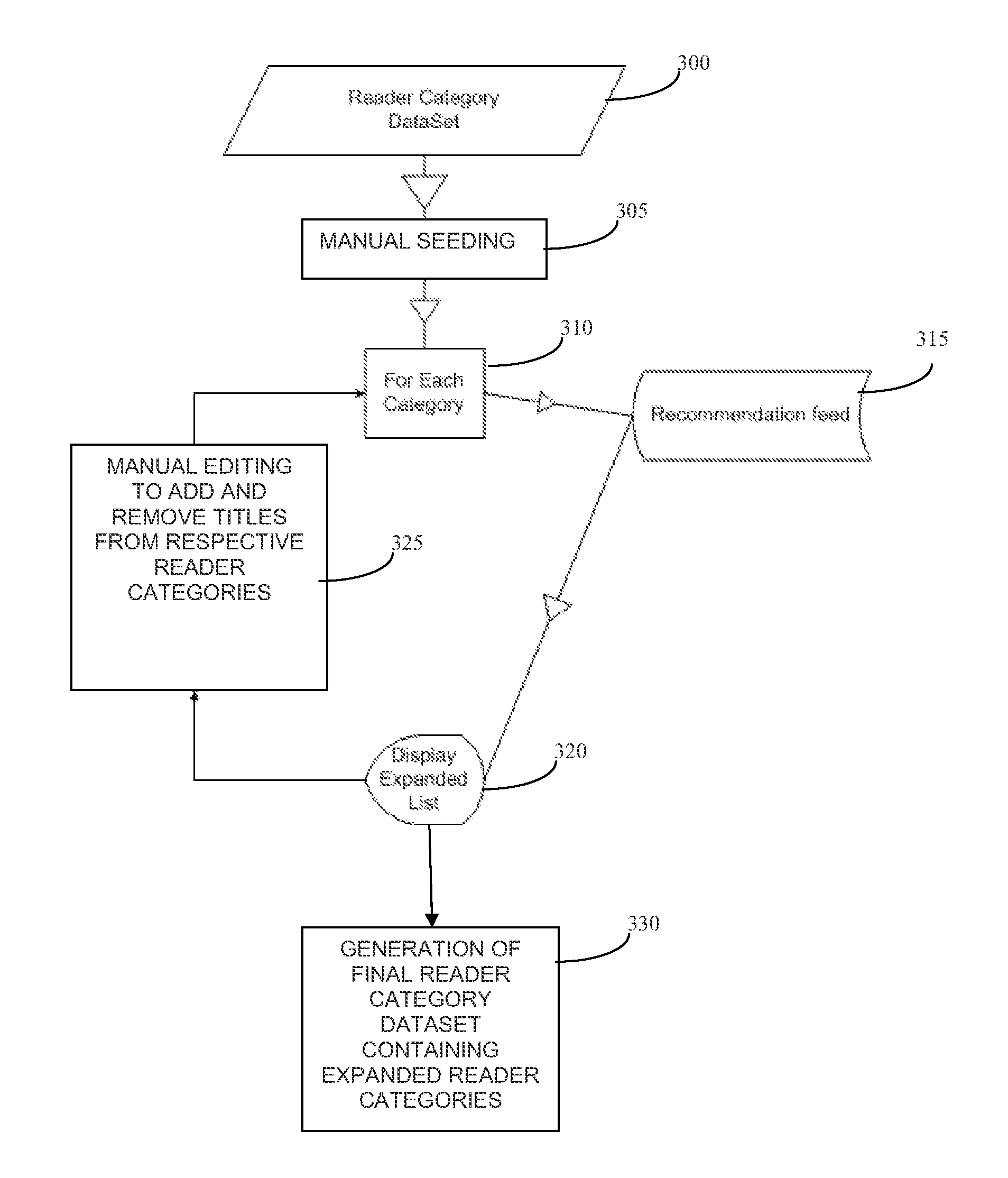
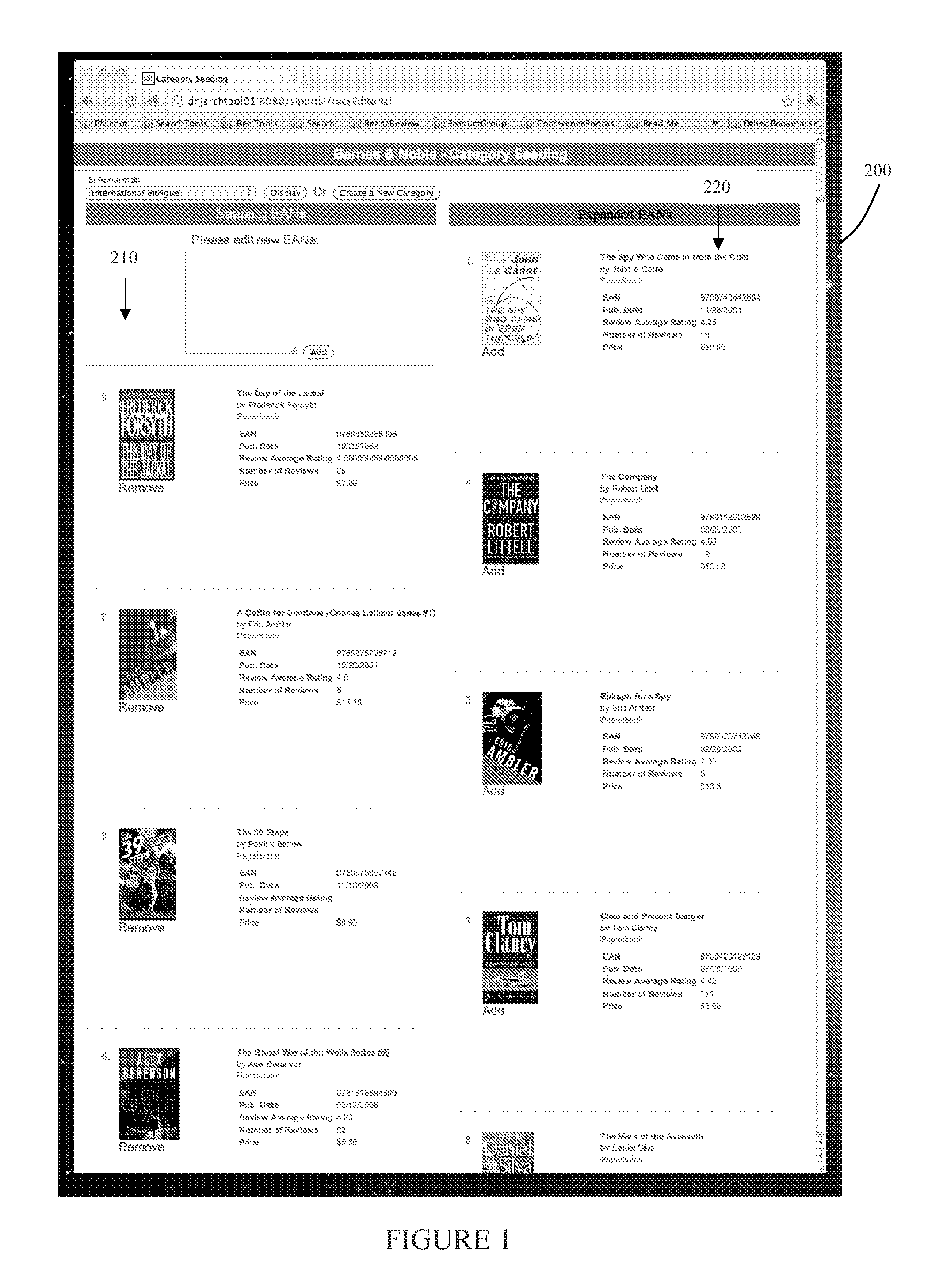
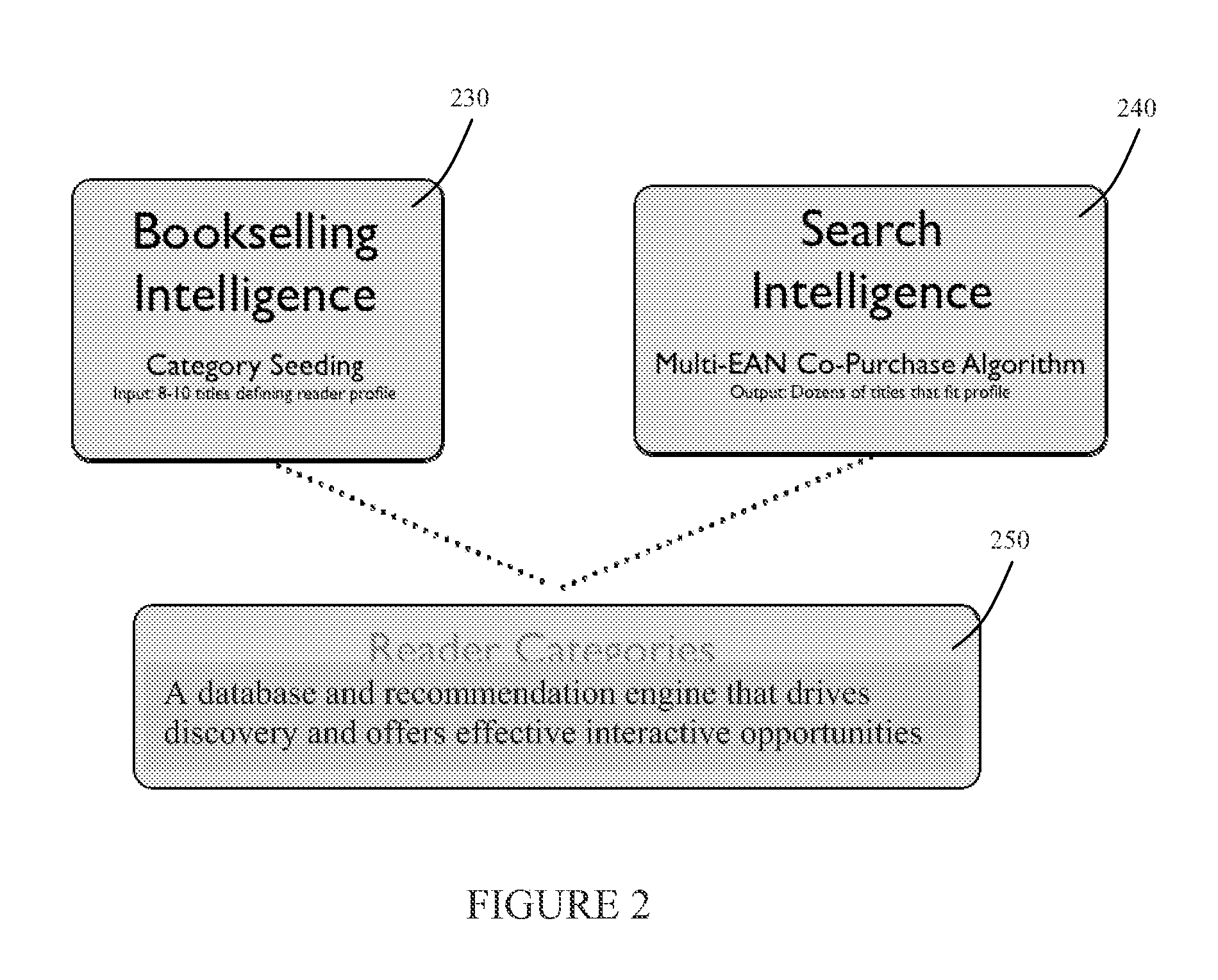
InactiveUS20130166406A1Accurate and compelling recommendationPrecise alignmentBuying/selling/leasing transactionsComputer scienceInitial Seed
The present invention creates a new taxonomy called Reader Categories that incorporates a bookseller's bookselling knowledge to generate more accurate and compelling recommendations to users. An initial “seeding” of the Reader Categories with content is performed by an editorial staff. A recommendation engine is then executed with respect to the initial seeds to generate recommendation of additional content for the Categories. A tool is provided that the editorial staff can use for the seeding and for providing feedback on the quality of algorithmically generated results. This helps the present invention extend the power of its recommendation algorithms by facilitating editorial ranking and seeding.
Owner:NOOK DIGITAL
Unmanned aerial vehicle airborne LiDAR point cloud filtering method based on adaptive gradient
ActiveCN106529469AImprove search efficiencyKeep the original informationImage enhancementImage analysisTerrainPoint cloud
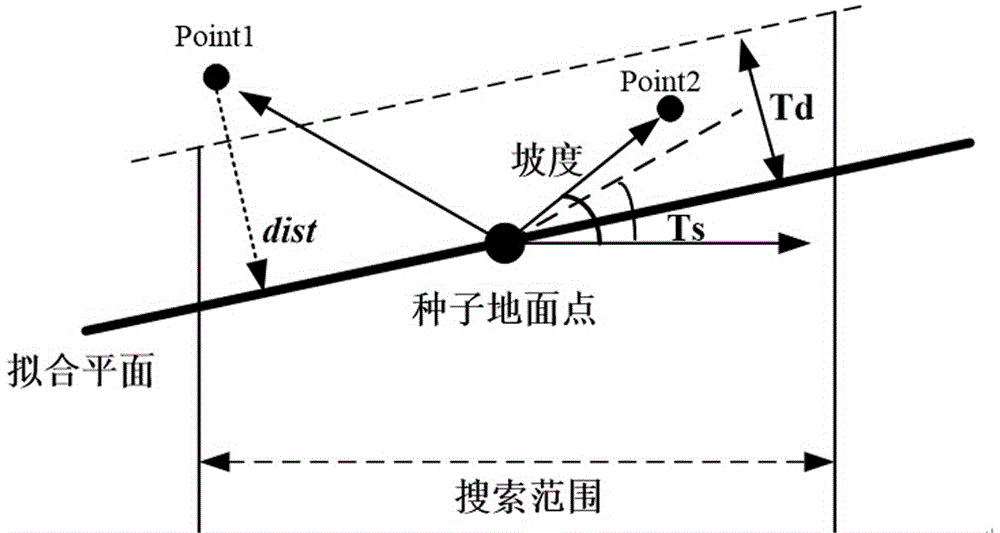
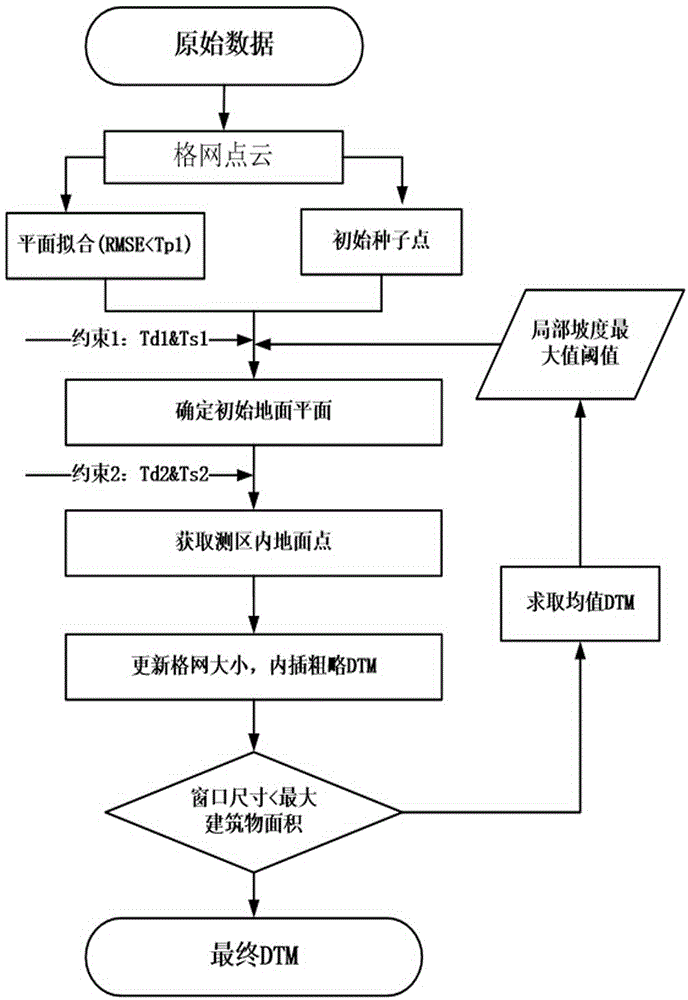
The invention provides an unmanned aerial vehicle airborne LiDAR point cloud filtering method based on adaptive gradient. The method comprises the following steps: obtaining point cloud data in a test region and carrying out filtering on the point cloud data; 2) establishing index for the point cloud data; 3) carrying out calculation and keeping an optimal plane in a grid; 4) selecting an elevation lowest point in a preset window as an initial seed point of a ground point; 5) calculating the distance between the optimal plane and the ground point and gradient from the ground point to the center of the optimal plane, and obtaining a ground point set according to gradient threshold; 6) serving a point in the initial ground point set as a base point, and generating a digital terrain model through an inverse distance weighted interpolation method; and 7) through the newly-generated digital terrain model, obtaining update value of the gradient threshold, repeating the steps 4)-6) and obtaining a final ground point set. The filtering method based on adaptive gradient improves algorithm operation efficiency.
Owner:NORTH CHINA UNIV OF WATER RESOURCES & ELECTRIC POWER
Dark channel experience and minimal image entropy based traffic smog visibility detection method
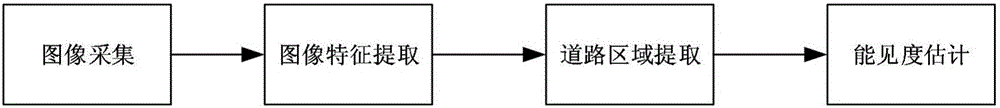
ActiveCN105931220ASmall amount of calculationReduce detection errorImage enhancementImage analysisVisibilityFeature extraction
The invention relates to a dark channel experience and minimal image entropy based traffic smog visibility detection method. In an image feature extraction module, dark channel experience processing is carried out on an image I to be detected to obtain a rough estimated value of the air transmittance, a guiding and filtering edge smoothing operator is used to smooth and refine the rough estimated value of the transmittance, and depth information of each pixel point is obtained; in a road area extraction module, a road area is extracted from the image I in an area growth method, and area growth comprises the steps including setting an initial seed point, setting a target growth area, calculating the minimum of adjacent gray scale difference, determining whether a target pixel belongs to the road area and updating the seed point; and in a visibility estimation module, the minimal image entropy of the area is calculated, an optimal value of the extinction coefficient is obtained, and the smog visibility is estimated effectively. The detection method has the advantages that a target interest area extraction step is added to an image entropy solving process, the computation amount is reduced, and the operation speed and robustness are improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
Semantic segmentation of weakly supervised images based on iterative mining of common features of objects
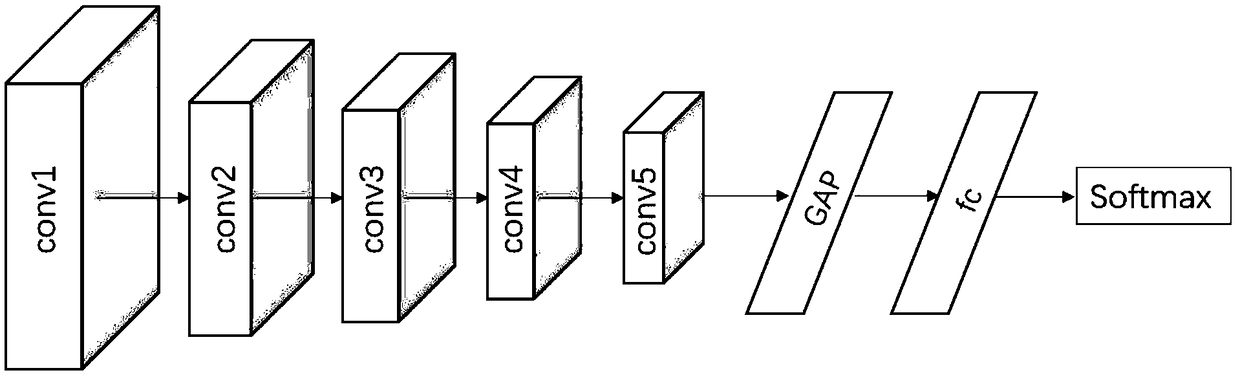
ActiveCN109063723AReliable Semantic SegmentationLow application costCharacter and pattern recognitionNeural architecturesColor imageTraining phase
The invention provides a weak supervised image semantic segmentation method based on iterative mining common features of objects, belonging to the technical field of pattern recognition. In the training phase, the method acquires the training data set, constructs and trains the multi-label classification network, and acquires the initial seed area corresponding to each training image. Then, the superpixel region and the region label of each training image are obtained for training the region classification network, and the updated region label of the superpixel region is obtained for trainingthe semantic segmentation network. After iteration, when the performance of the semantic segmentation network converges, the trained semantic segmentation network is obtained. In the use stage, the color image is input into the trained semantic segmentation network, and the network outputs the semantic segmentation results of the image. The invention can realize reliable pixel-level semantic segmentation under the condition of only image class label, reduces the time and labor cost of data labeling, and has wide application prospect.
Owner:TSINGHUA UNIV
Method and system for generation of cryptographic keys for use in cryptographic systems
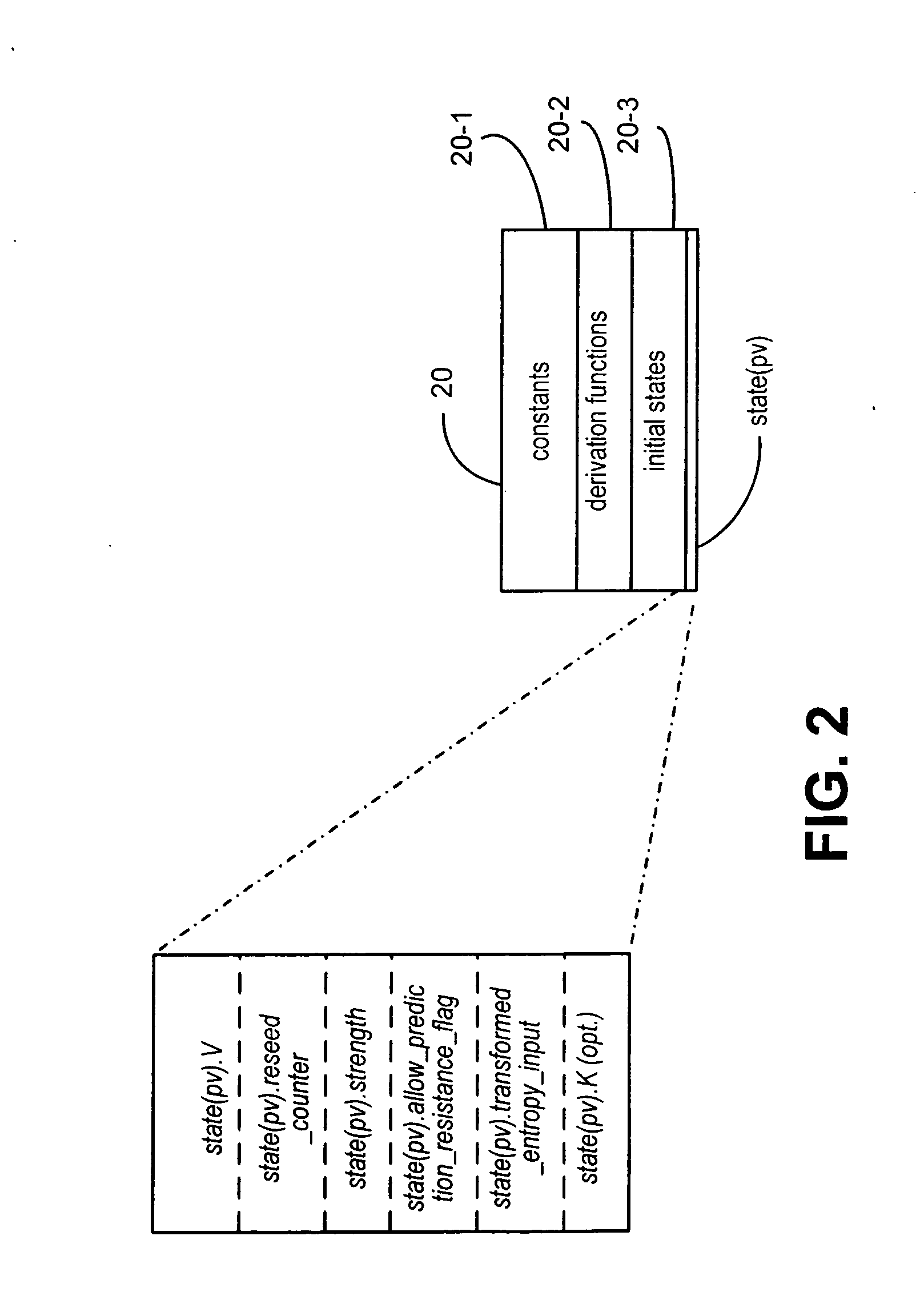
A method and deterministic random bit generator system operating in accordance with the method, for generating cryptographic keys and similar secret cryptographic inputs which are hard to guess. A entropy is input from an entropy source; and an initial seed is generated as a function of the entropy input. When a request to generate a cryptographic key is received a temporary seed is generated by applying the function to the seed. The requested cryptographic key is generated by applying a second function to the temporary seed; and output. A new seed is then generated by applying a third function to the temporary seed. In one embodiment of the subject invention all three functions are carried out by applying the same operator to appropriate inputs. In another embodiment of the subject invention new entropy is incorporated into the seed from time to time.
Owner:PITNEY BOWES INC
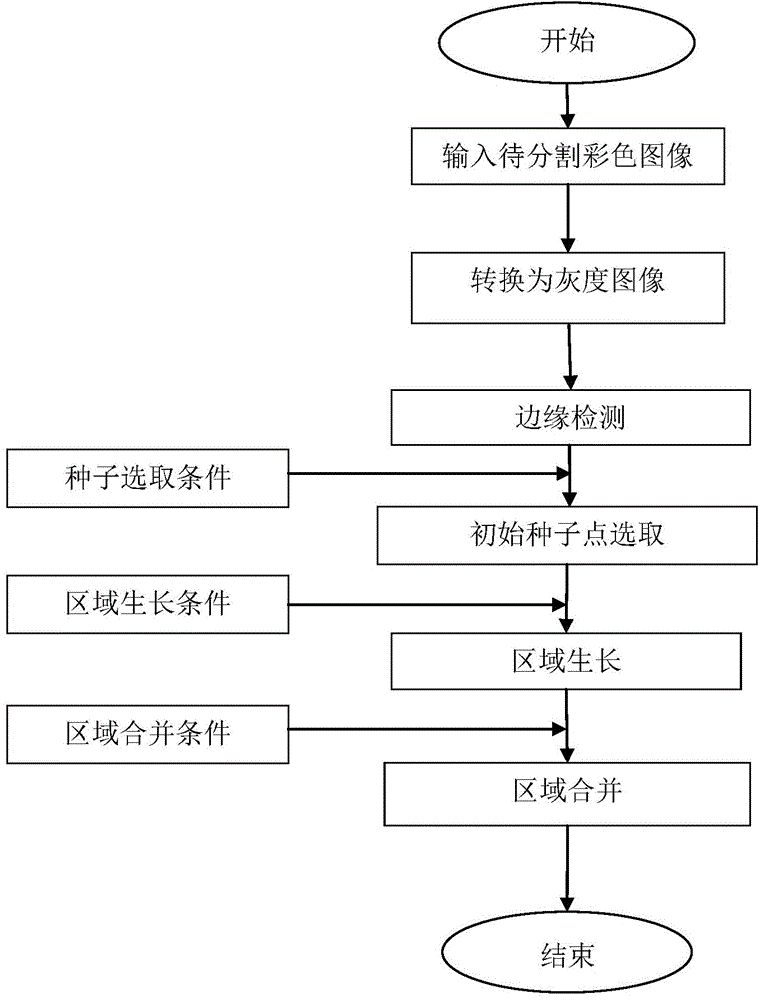
Color image segmentation method integrating region growth and edge detection
InactiveCN104376551AGuaranteed accuracyNot affected by region growingImage enhancementImage analysisColor imageImage segmentation
The invention provides a color image segmentation method integrating region growth and edge detection. The color image segmentation method comprises the steps that an image to be segmented is input; the image is converted into a gray level image, and according to a Canny edge detection algorithm, edge detection is conducted with the maximum between-cluster variance threshold value obtained through the Otsu method as a high threshold value; the image is converted into an RGB color image, the maximum Euclidean distance between one point and all points of an eight neighborhood of the point is calculated, and if the maximum Euclidean distance is smaller than a regulated threshold value, the point can be used as a candidate seed point; seed selection is completed, if one point is the candidate seed point obtained in the step (2) but not the edge point obtained in the step (1), the point can be used as an initial seed point; growth is conducted on a seed area according to a growth rule, and pixel points according with the growth rule are classified into the seed area; area blocks, which are adjacent in the space and accord with an area combination rule, in the image are combined according to the area combination rule; the steps are executed repeatedly until an area combination stopping condition is met; color image segmentation is completed.
Owner:ZHEJIANG UNIV OF TECH
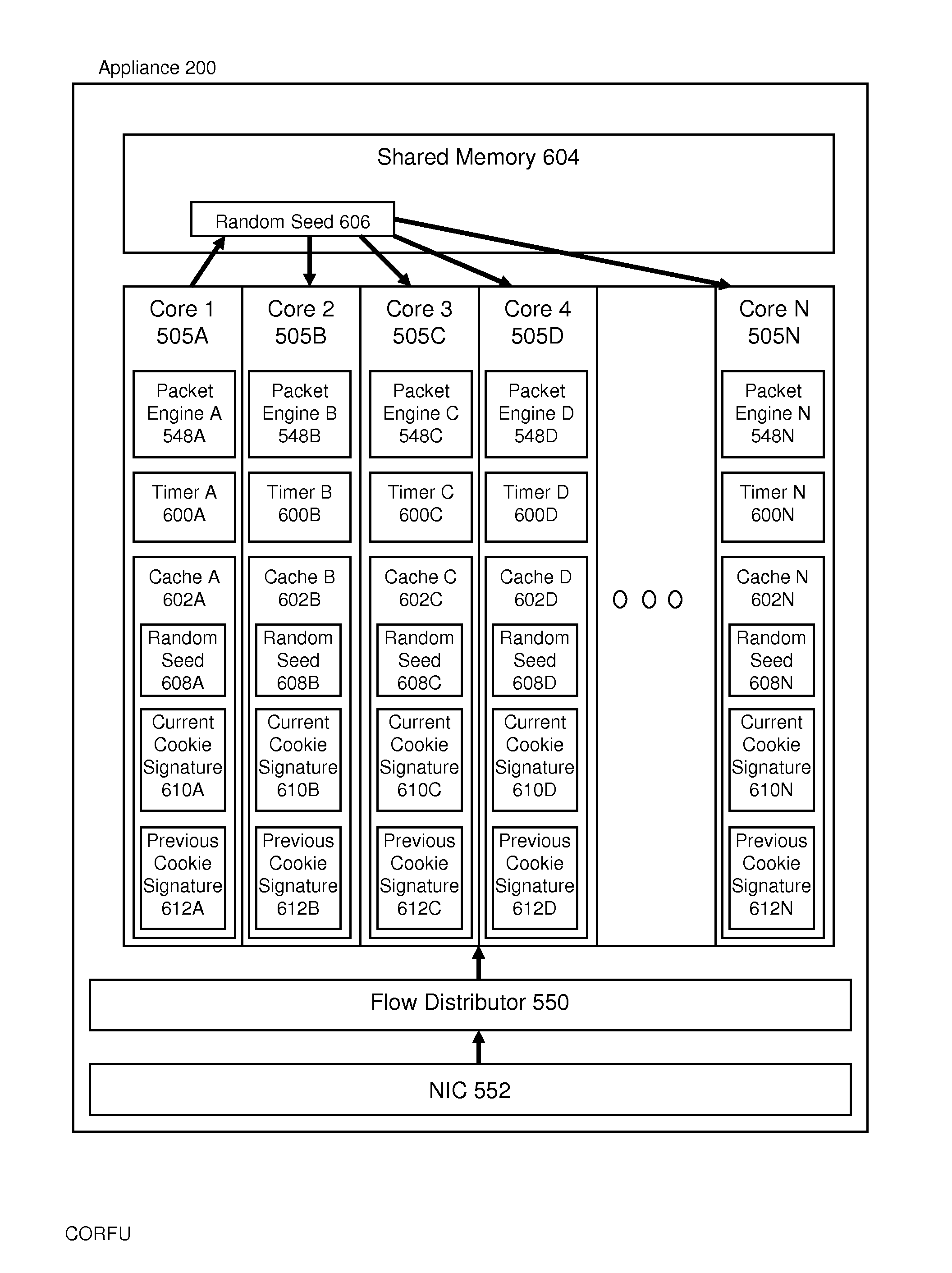
Systems and methods for generating and managing cookie signatures for prevention of HTTP denial of service in multi-core system
The present application is directed towards systems and methods for generating and maintaining cookie consistency for security protection across a plurality of cores in a multi-core system. A packet processing engine executing on one core designated as a primary packet processing engine generates and maintains a global random seed. The global random seed may be used as an initial seed for creation of cookie signatures by each of a plurality of packet processing engines executing on a plurality of cores of the multi-core system using a deterministic pseudo-random number generation function such that each core creates an identical set of cookie signatures.
Owner:CITRIX SYST INC
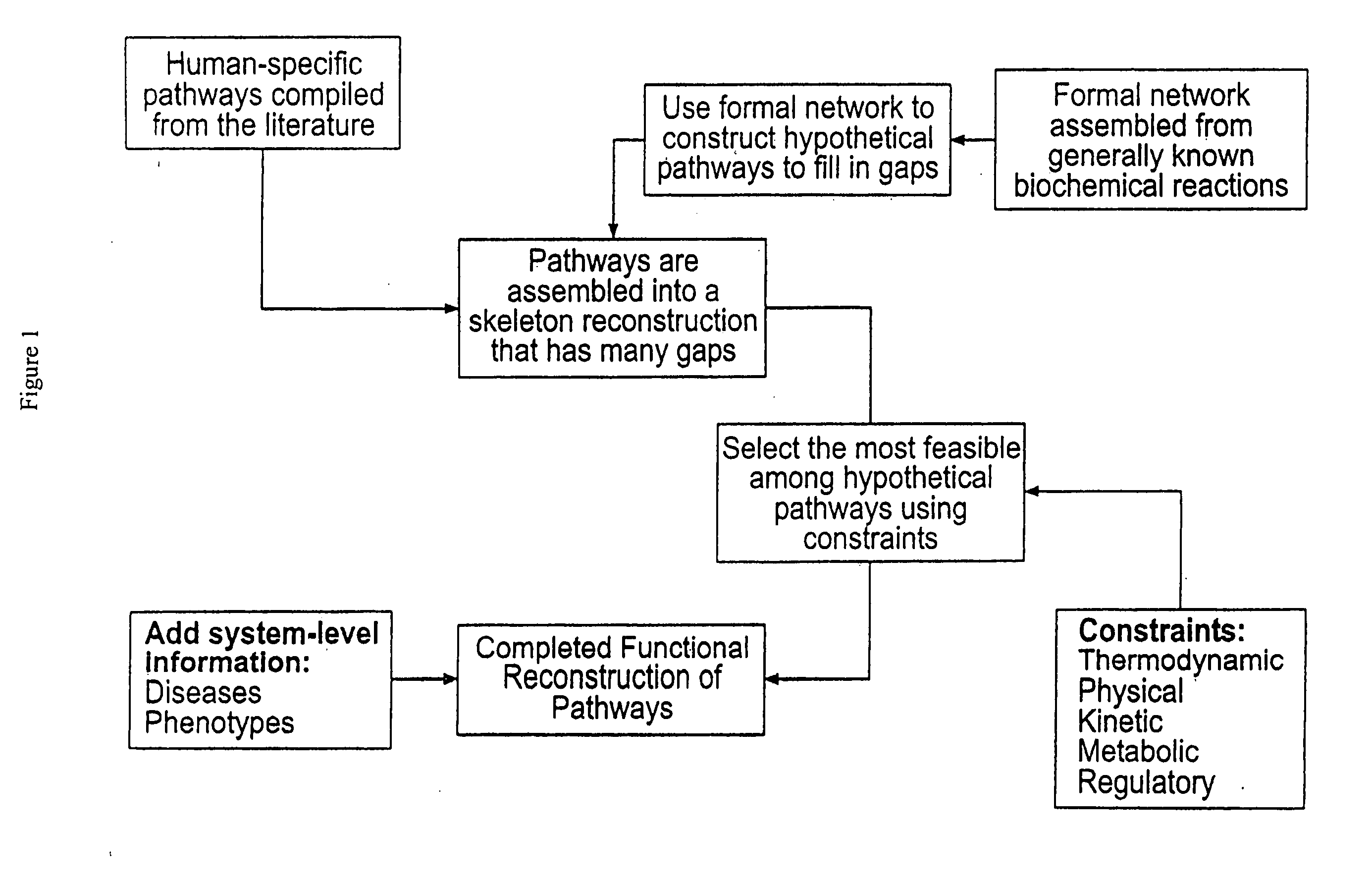
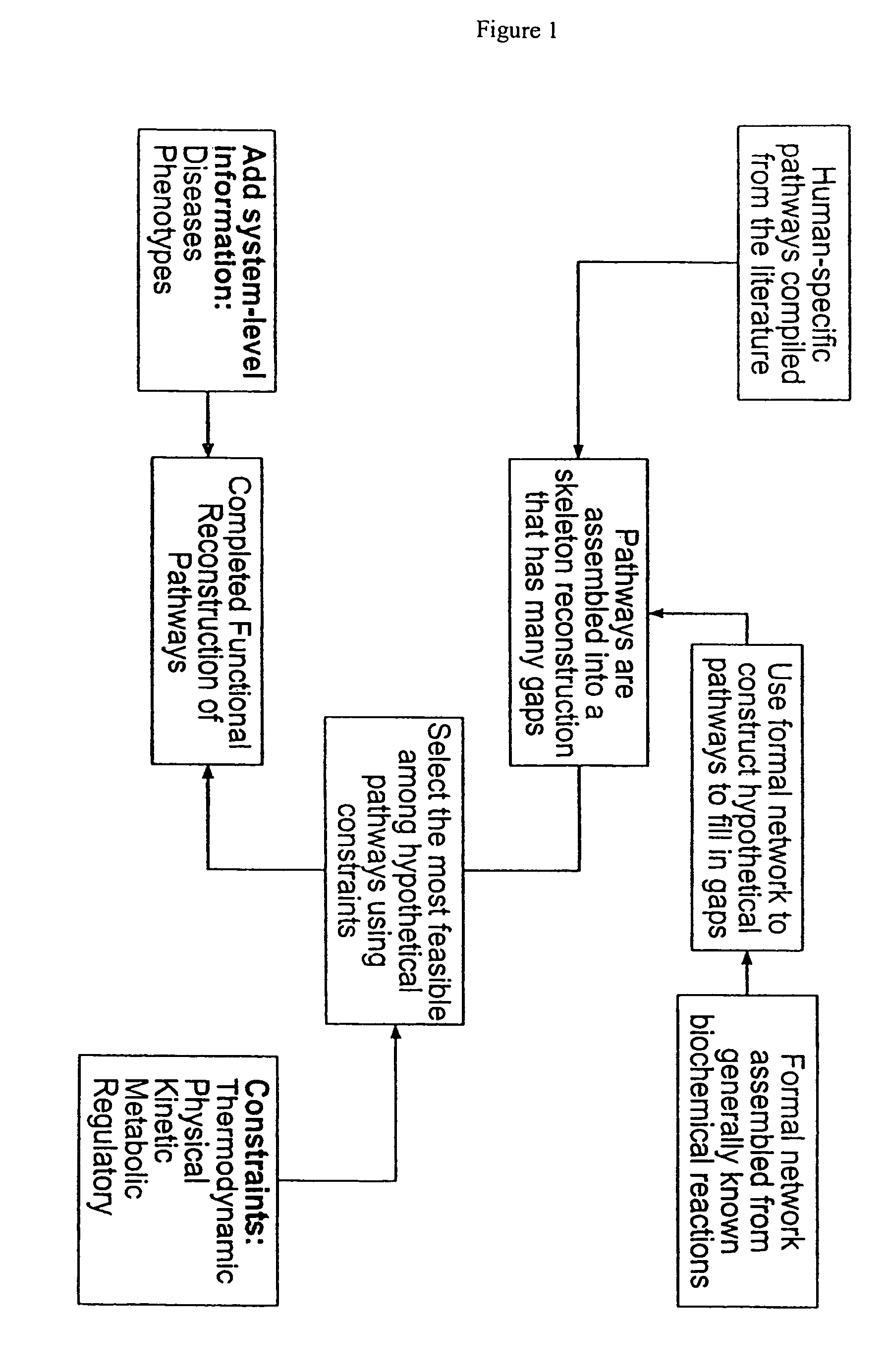
Methods for identification of novel protein drug targets and biomarkers utilizing functional networks
The process of System Reconstruction is used to integrate sequence data, clinical data, experimental data, and literature into functional models of disease pathways. System Reconstruction models serve as informational skeletons for integrating various types of high-throughput data. The present invention provides the first metabolic reconstruction study of a eukaryotic organism based solely on expressed sequence tag (EST) data. System Reconstruction also provides a method for the identification of novel therapeutic targets and biomarkers using network analysis. The initial seed networks are built from the lists of novel targets for diseases with the high-throughput experimental data being superimposed on the seed networks to identify specific targets.
Owner:CAMELOT UK BIDCO LTD
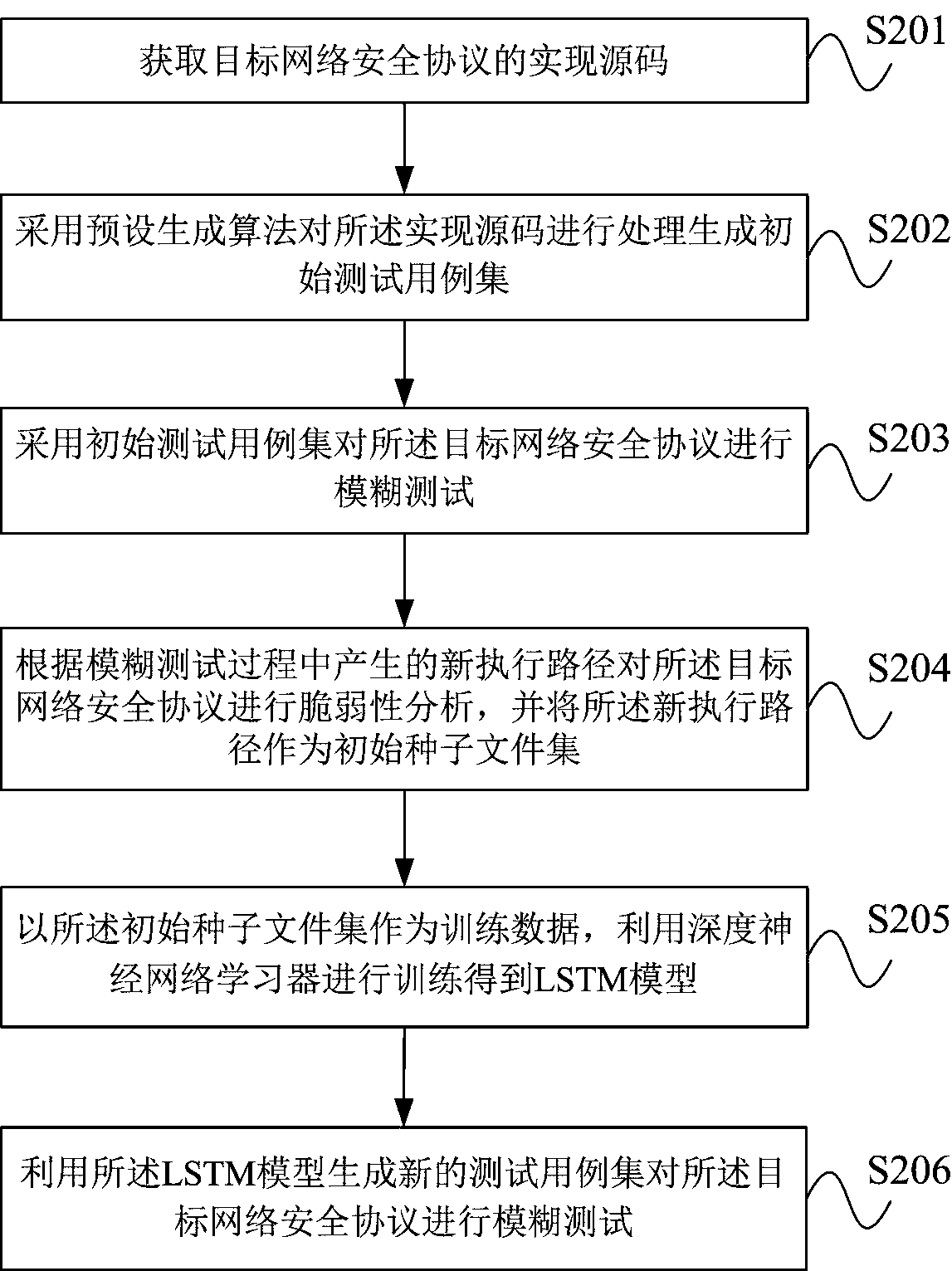
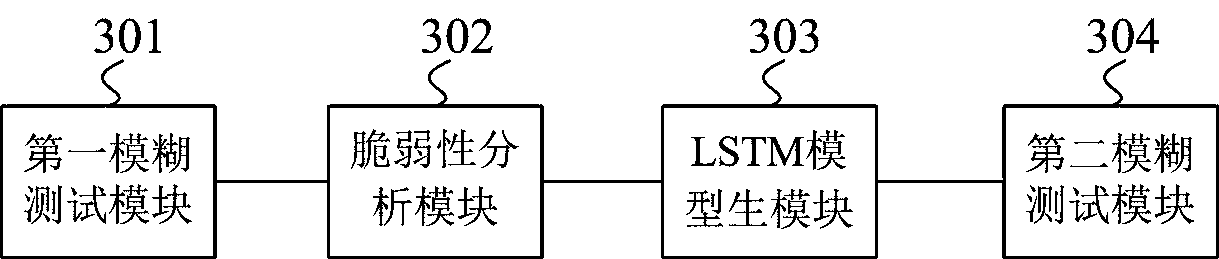
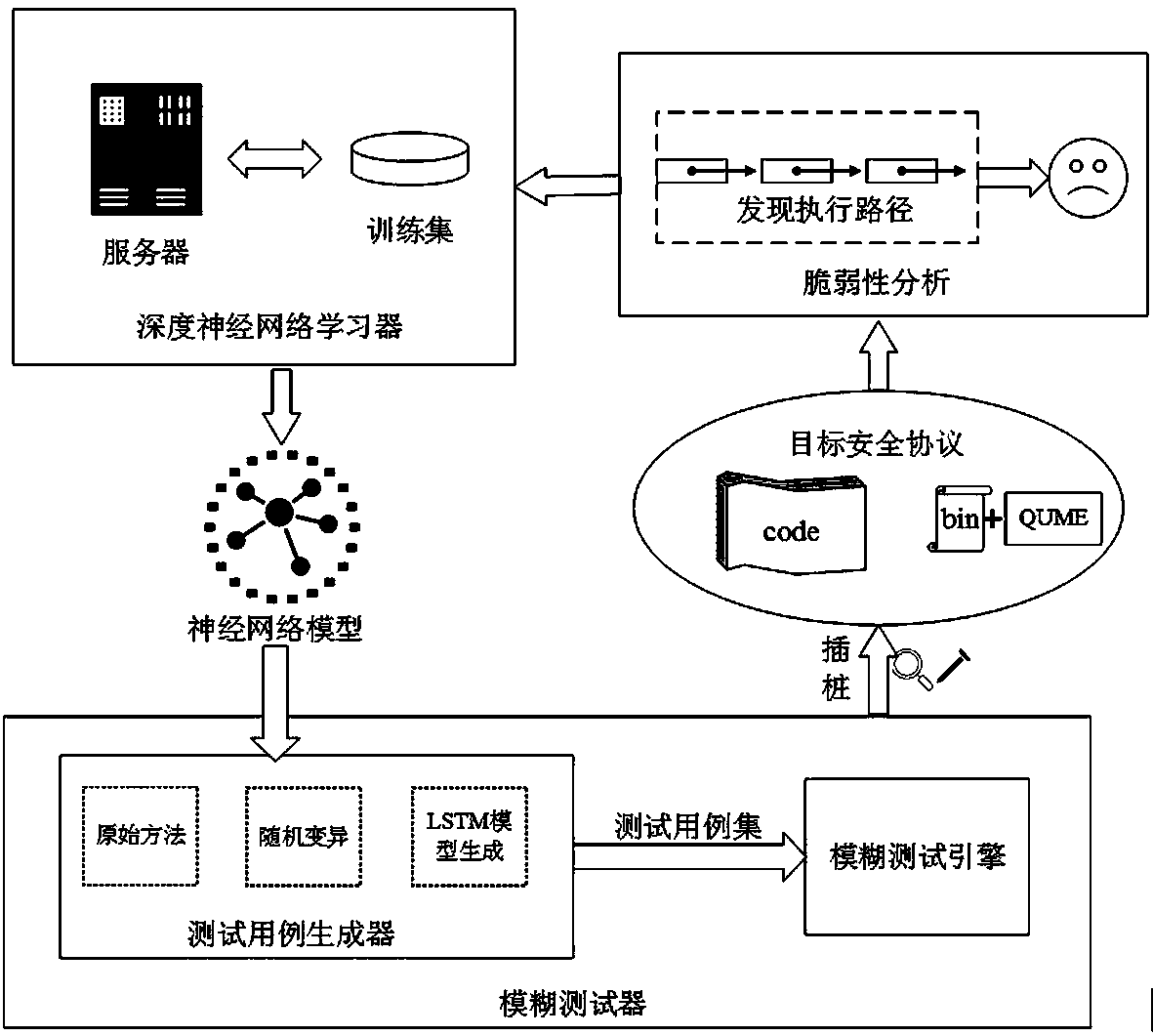
Network security protocol fuzz test method and system based on LSTM
ActiveCN109379329AIncrease coverageSolve the problem of discardingTransmissionGenetic algorithmsProgramming languageCryptographic protocol
The invention provides a network security protocol fuzz test method and system based on an LSTM. The method comprises the steps of: S1, carrying out an initial fuzz test on a target network security protocol by adopting an initial test case set; S2, carrying out vulnerability analysis on the target network security protocol according to a new execution path generated in the fuzz test process, andusing the new execution path as an initial seed file set; S3, using the initial seed file set as training data, and carrying out training by utilizing a deep neural network learner to obtain an LSTM model; and S4, generating a new test case set by utilizing the LSTM model so as to carry out the fuzz test on the target network security protocol. The system comprises a first fuzz test module, a vulnerability analysis module, an LSTM model generation module and a second fuzz test module. According to the invention, by training the LSTM neural network model to optimize a generation algorithm of test cases, so that a code coverage rate of the test cases is improved.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
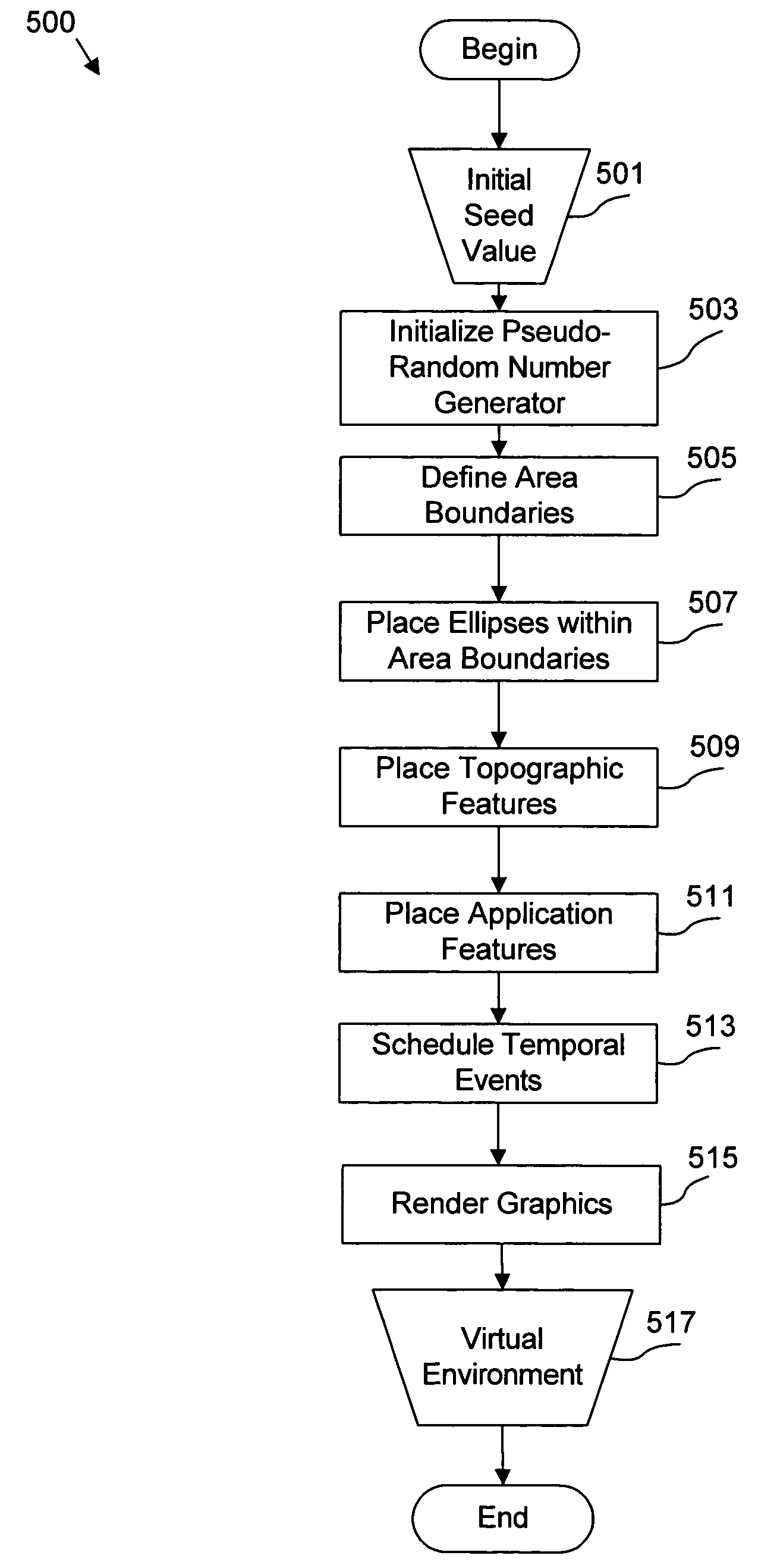
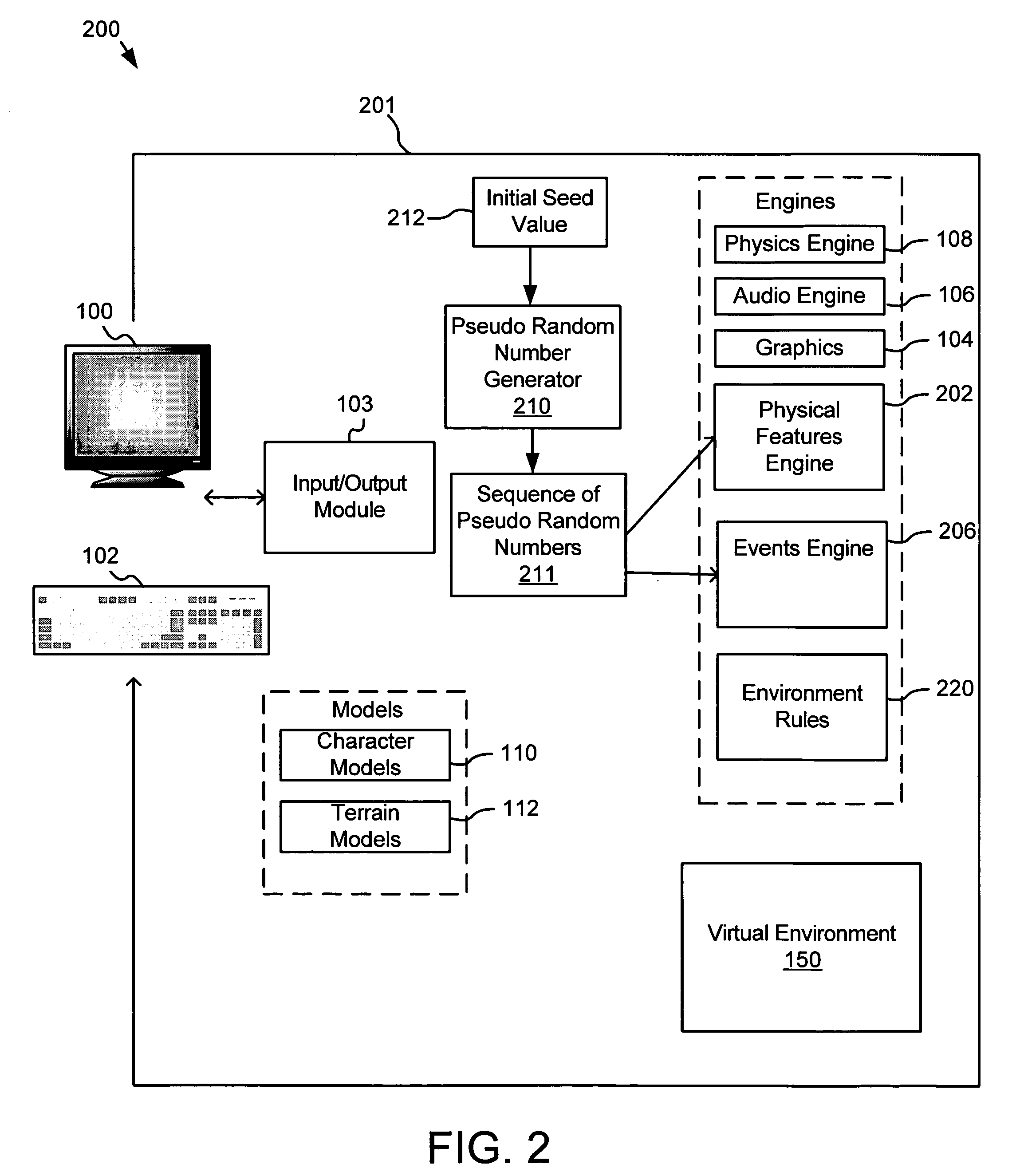
Apparatus, system, and method for automated generation of a virtual environment for software applications
InactiveUS20060030405A1Video gamesSpecial data processing applicationsSoftware engineeringAdemetionine
An apparatus, system, and method are disclosed for generating a reproducible virtual environment in a computer software program. This invention describes a method of generating a realistic virtual environment dependent on a sequence of pseudo-random numbers generated by a pseudo-random number generator initialized by a seed value that may be created by the user. If a user starts with the same initial seed, the same virtual environment is created each time the program is run. However, if a new seed is used, a new virtual environment will be created.
Owner:ROBERTSON ALAN
Automatic batch extraction method for horizontal vector contour of building in satellite image
ActiveCN103699900AOvercome the disadvantages of manual selection one by one based on experienceImage analysisCharacter and pattern recognitionNatural satelliteBatch extraction
The invention provides an automatic batch extraction method for horizontal vector contours of buildings in satellite images. The method comprises the steps of firstly using a K-means algorithm to class the images to obtain the backbone parts of the buildings, and solving the problem of selection of initial seed points by taking mass centers of all building areas; after the areas of all the seed points are grown, separating the building areas from surrounding areas by virtue of image edge information and removing non-building areas according to characteristic parameters such as rectangularity and strip index to realize the automatic extraction of the horizontal pixel contours of the buildings; then using techniques such has Hough transformation and block processing to perform linear vector processing to the horizontal pixel contours, and finally obtaining the horizontal vector contours of all buildings in a batch. The automatic batch extraction method for the horizontal vector contours of the buildings in the satellite images is applicable to the batch and quick extraction of the horizontal vector contours of common polygonal buildings with top views which are of straight-line segment structures in the satellite images.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
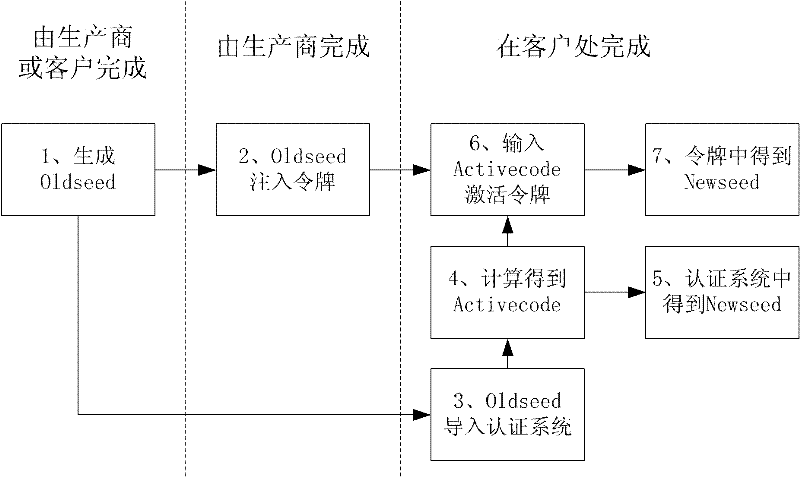
Injection and deformation method for seed key of dynamic token
ActiveCN102307095AWithout compromising securityImprove securityKey distribution for secure communicationMultiple keys/algorithms usagePasswordBiological activation
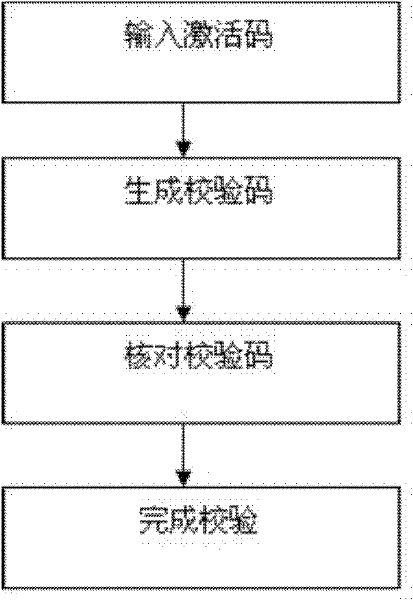
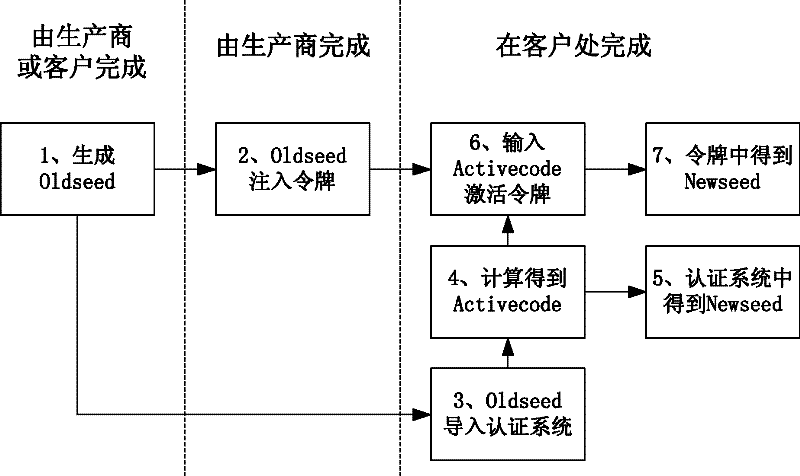
The invention discloses an injection and deformation method for a seed key of a dynamic token. The method comprises the following steps of: generating an initial seed key of the token in advance, and injecting the initial seed key into the token in production; when the token is issued to a final user, performing an activation operation, and performing an operation on an activation code and the initial seed key to obtain a new seed key, wherein the new seed key is a final seed key for the future working of the token; and simultaneously, importing the initial seed key on a dynamic password authentication system, and performing a seed key deformation operation the same as that of the token by using the authentication system to obtain the same new seed key. In such a way, the final new seed key is different from the initial seed key injected by a token producer after the activation operation of the token and the authentication system, thereby enhancing the privacy of the seed key.
Owner:DYNAMICODE
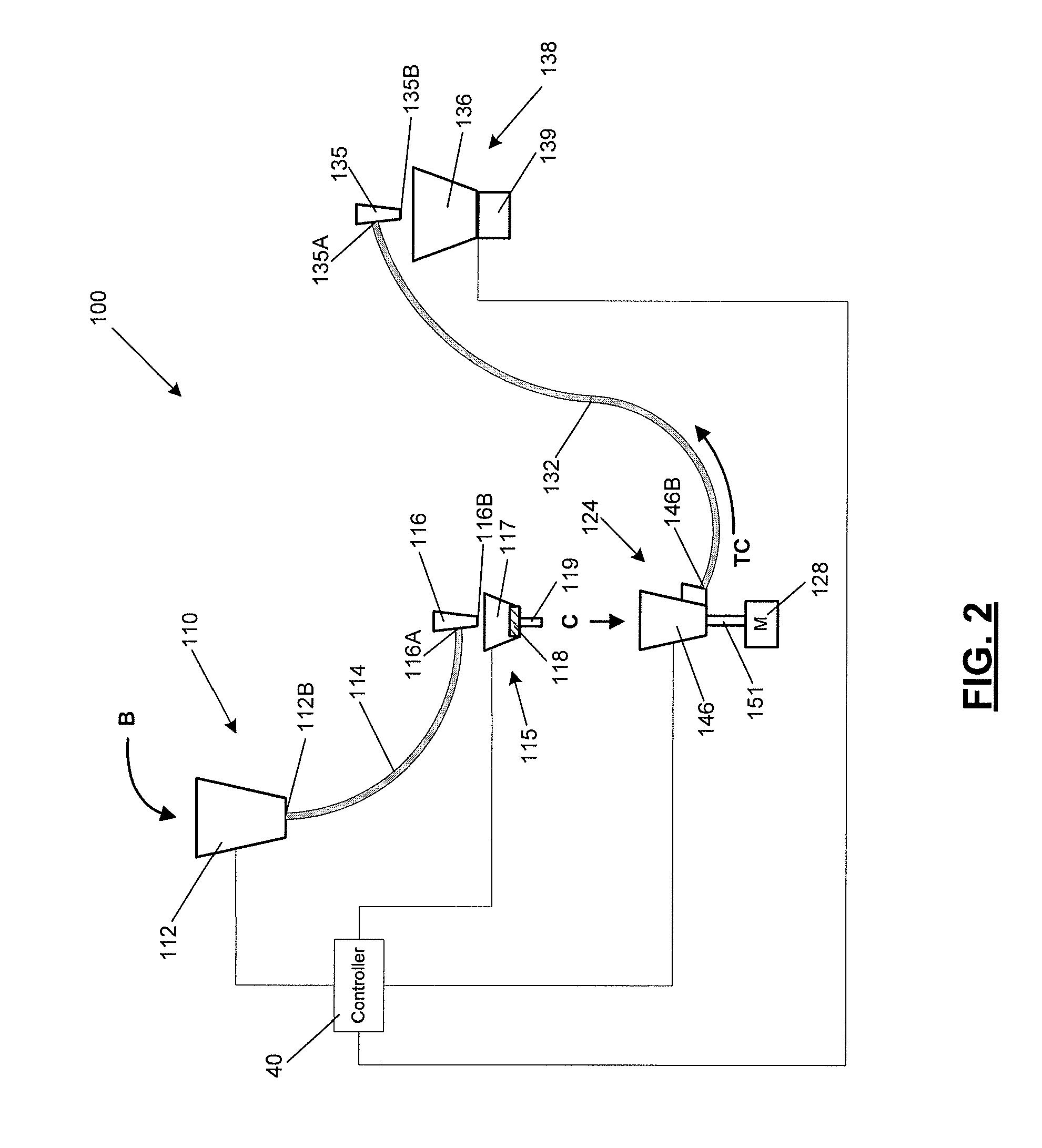
High speed seed treatment apparatus
ActiveUS20090119986A1Increase throughput timePrecision therapyDead plant preservationFlower preserving apparatusEngineeringSeed sample
An apparatus and method for treating a least a portion of one or more initial seed samples to create one or more treated seed samples for use in research applications is provided. In various embodiments, the apparatus and method utilize two or more seed treaters operating in parallel to increase throughput for treating a portion of one or more initial seed samples. The apparatus and method may also include a metering station configured to distribute at least a portion of the one or more initial seed samples to the two or more seed treaters. As a result, the apparatus and method are configured to efficiently and accurately treat seed samples.
Owner:PIONEER HI BRED INT INC
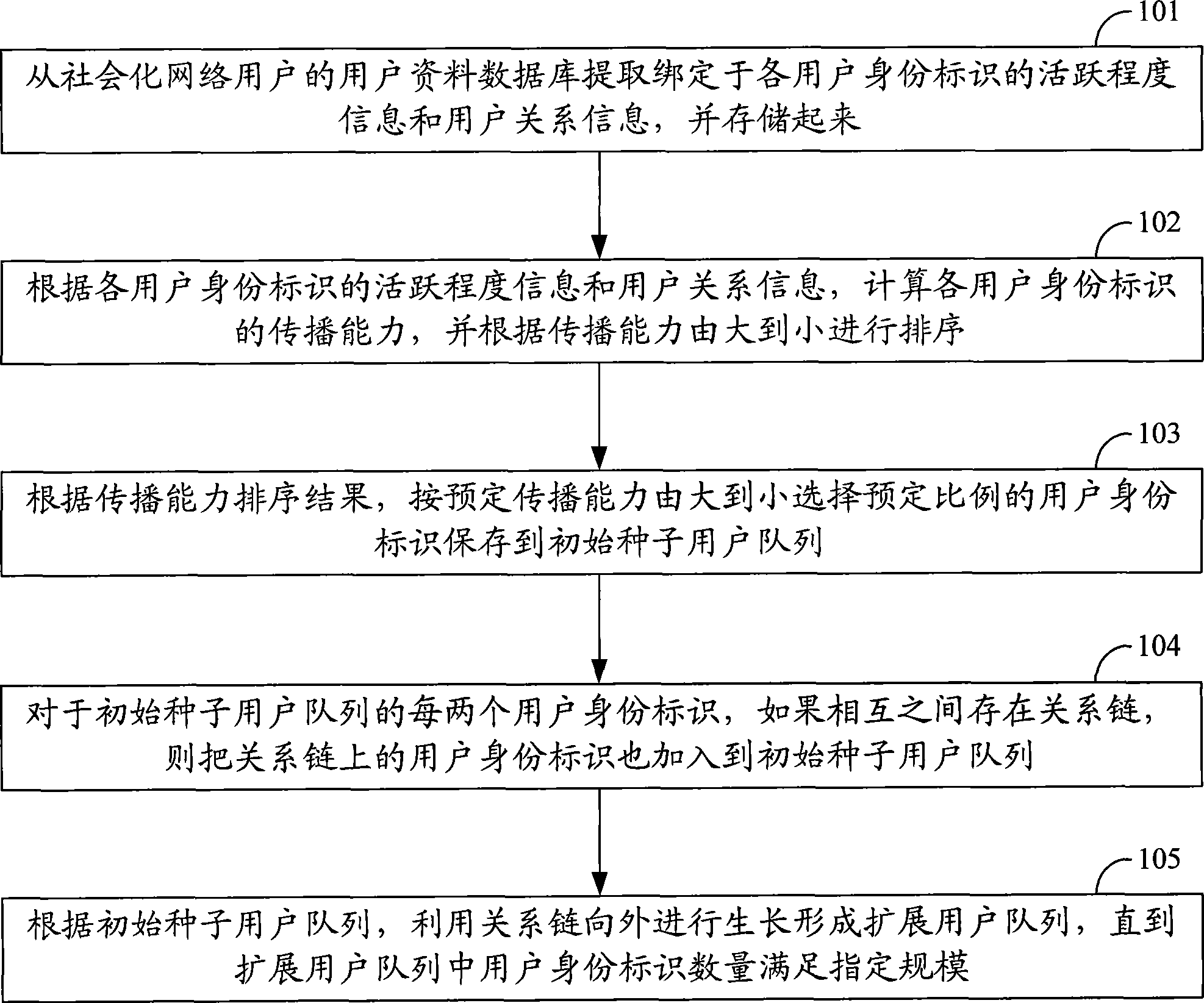
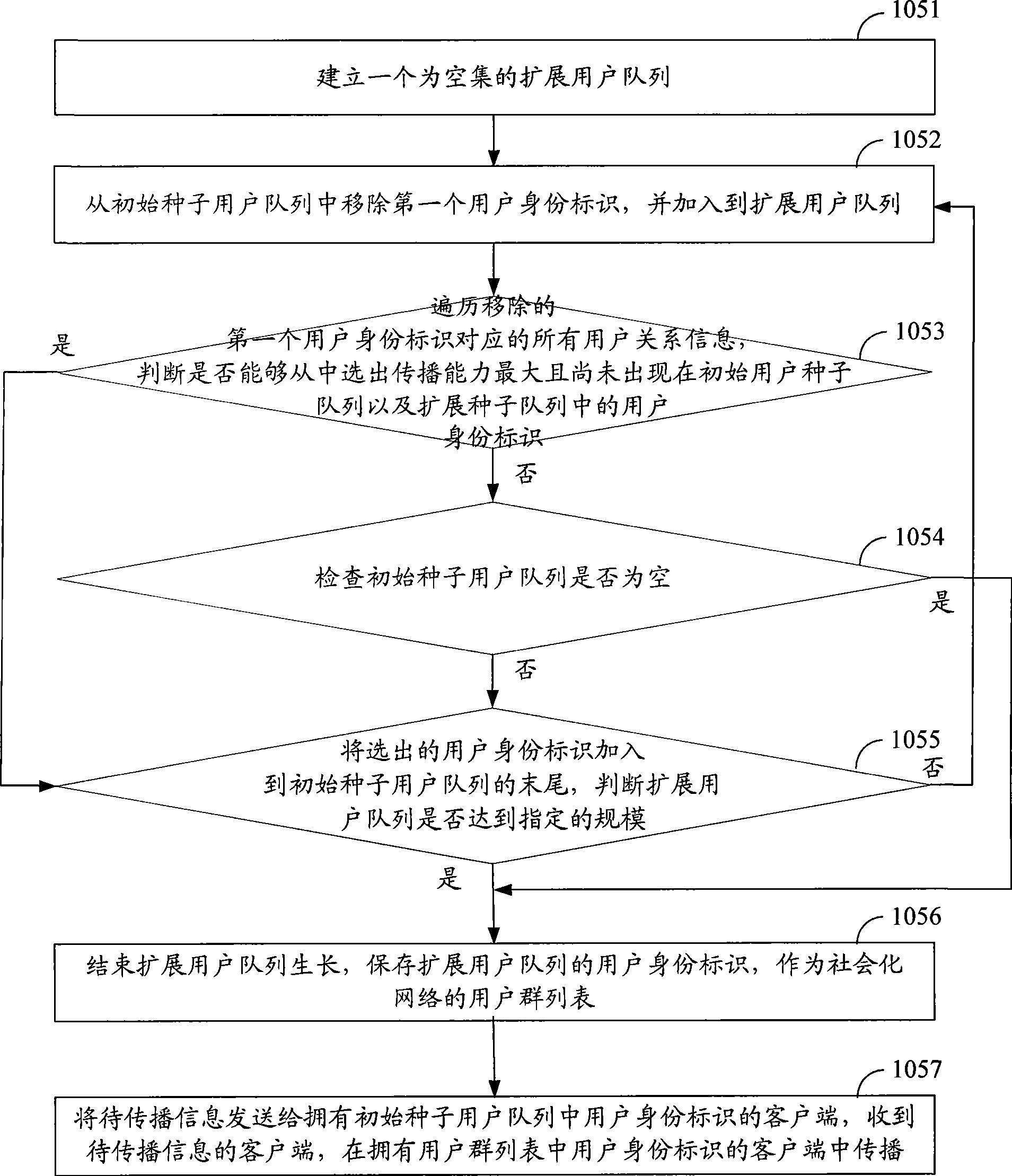
Information transmission method and system based on socialized network
The invention discloses a method and a system for information transmission based on a social network, which aims at solving the problem of high cost of information transmission resources among users of the prior the social network. The method disclosed in the invention comprises the following steps: according to acquired user information corresponding to user identifiers, calculating the corresponding information transmission capacities of the user identifiers; selecting the user identifiers with the transmission capacity greater than a preset threshold and saving the user identifiers in an initial seed user quene; and sending the information to be transmitted to clients having the user identifiers in the initial seed user quene. The information to be transmitted is specifically transmitted to users with higher transmission capacities, so that the resource cost of the information transmission among uses of the social network is reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Methods for identification of novel protein drug targets and biomarkers utilizing functional networks
ActiveUS8000949B2Analogue computers for chemical processesSequence analysisDrug targetBiomarker (petroleum)
The process of System Reconstruction is used to integrate sequence data, clinical data, experimental data, and literature into functional models of disease pathways. System Reconstruction models serve as informational skeletons for integrating various types of high-throughput data. The present invention provides the first metabolic reconstruction study of a eukaryotic organism based solely on expressed sequence tag (EST) data. System Reconstruction also provides a method for the identification of novel therapeutic targets and biomarkers using network analysis. The initial seed networks are built from the lists of novel targets for diseases with the high-throughput experimental data being superimposed on the seed networks to identify specific targets.
Owner:CAMELOT UK BIDCO LTD
Multichannel pulse coupling neural network based color image segmentation technology
InactiveCN104599262AHigh speedGuaranteed Image Segmentation QualityImage analysisBiological neural network modelsFeature vectorColor vector
A multichannel pulse coupling neural network based color image segmentation technology comprises the steps of step (1), inputting images to be segmented; step (2), using color vectors of all pixels of the images as input vectors of one input neuron and eight adjacent pixel color vectors as radial basis function (RBF) characteristic vectors, and determining initial seed points through seed selection conditions; step (3), growing the seed region through growing rules, classifying the pixel points in accordance with the growing rules in the seed region, and connecting the neurons and grouping and numbering the neurons; step (4), calculating the average characteristic vector of all connection regions, and replacing the characteristic vectors included in all neurons of the region with the obtained characteristic vector; step (5), connecting the qualified unconnected neurons with the proximate groups through a rapid connection rule; step (6),updating the preset threshold to be theta i = theta i1 +delta theta i, and repeating the step (5); step (7), performing rule merging on accordant regions in the images and merging proximate region blocks on space; repeating the step (7) till the region merging stopping conditions are met to complete color image segmentation.
Owner:ZHEJIANG UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com