Method and system for achieving SSH protocol based on post-quantum key exchange
A quantum key and key exchange technology, applied in the field of systems that implement SSH protocol based on post-quantum key exchange, can solve the problems of being vulnerable to selected ciphertext attack, SQL injection, intrusion or illegal control by undetermined attackers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0129] This embodiment provides a method for implementing the SSH protocol based on post-quantum key exchange, which can effectively prevent the shared key generated by the communicating client and server from being breached by a quantum computer; trusted status.
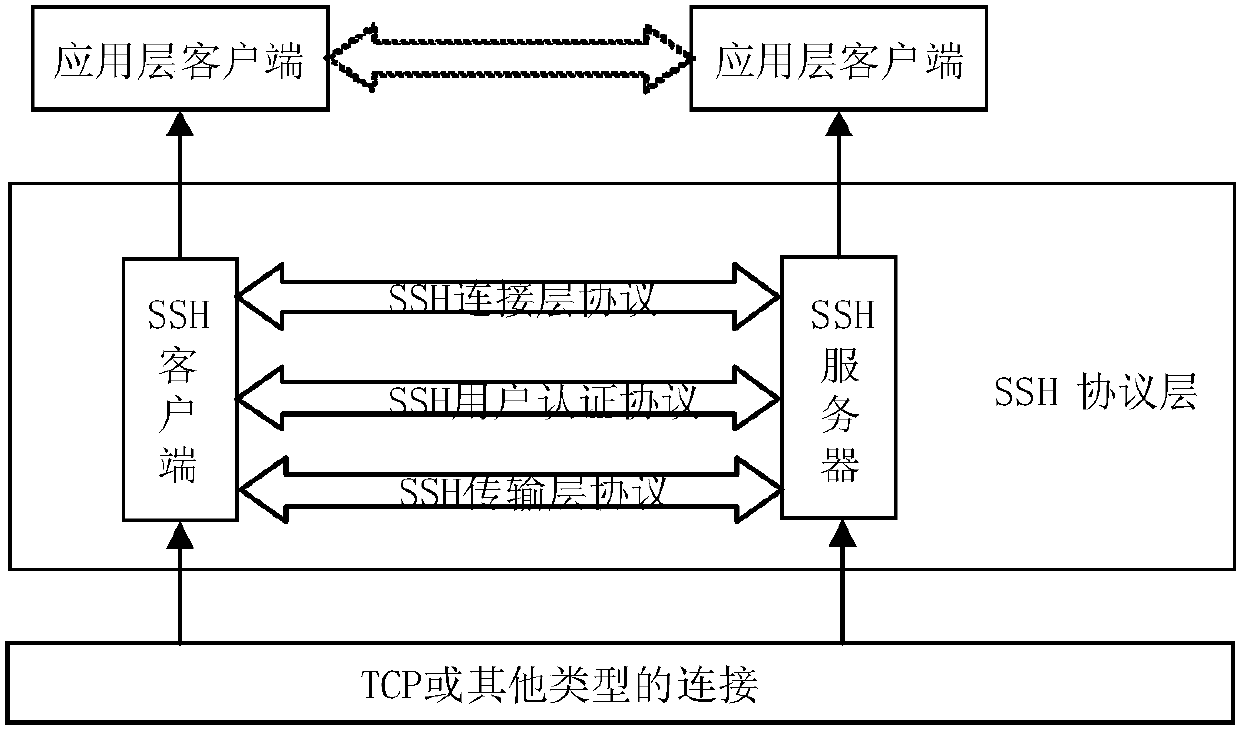
[0130] The protocol structure of the SSH improvement scheme is the three-layer system architecture stipulated by the current SSH protocol. For the specific protocol architecture, refer to figure 1 . From bottom to top, SSH is the transport layer, user authentication, and connection establishment. The session establishment process includes version negotiation, algorithm negotiation, key negotiation, user authentication, and connection request.
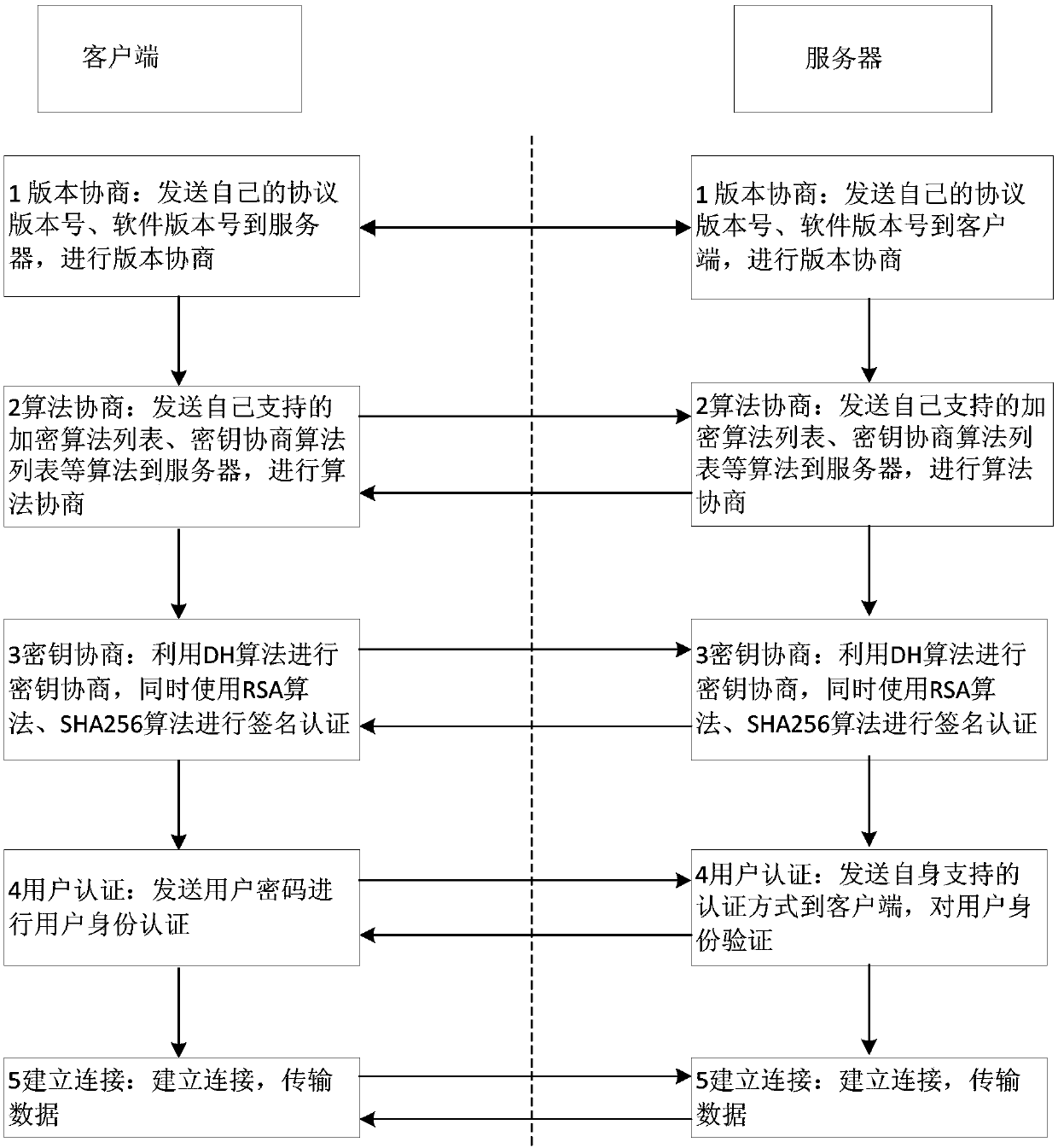
[0131] At present, the process of remote login between the communication parties using the SSH protocol is as follows: figure 2 shown.
[0132] The first step is version negotiation: the client and the server send their protocol version number and software version number ...
Embodiment 2
[0288] This embodiment provides a system for implementing the SSH protocol based on post-quantum key exchange, which can effectively prevent the shared key generated by the communicating client and server from being breached by a quantum computer; on the other hand, it can also verify both the client and the server trusted status.
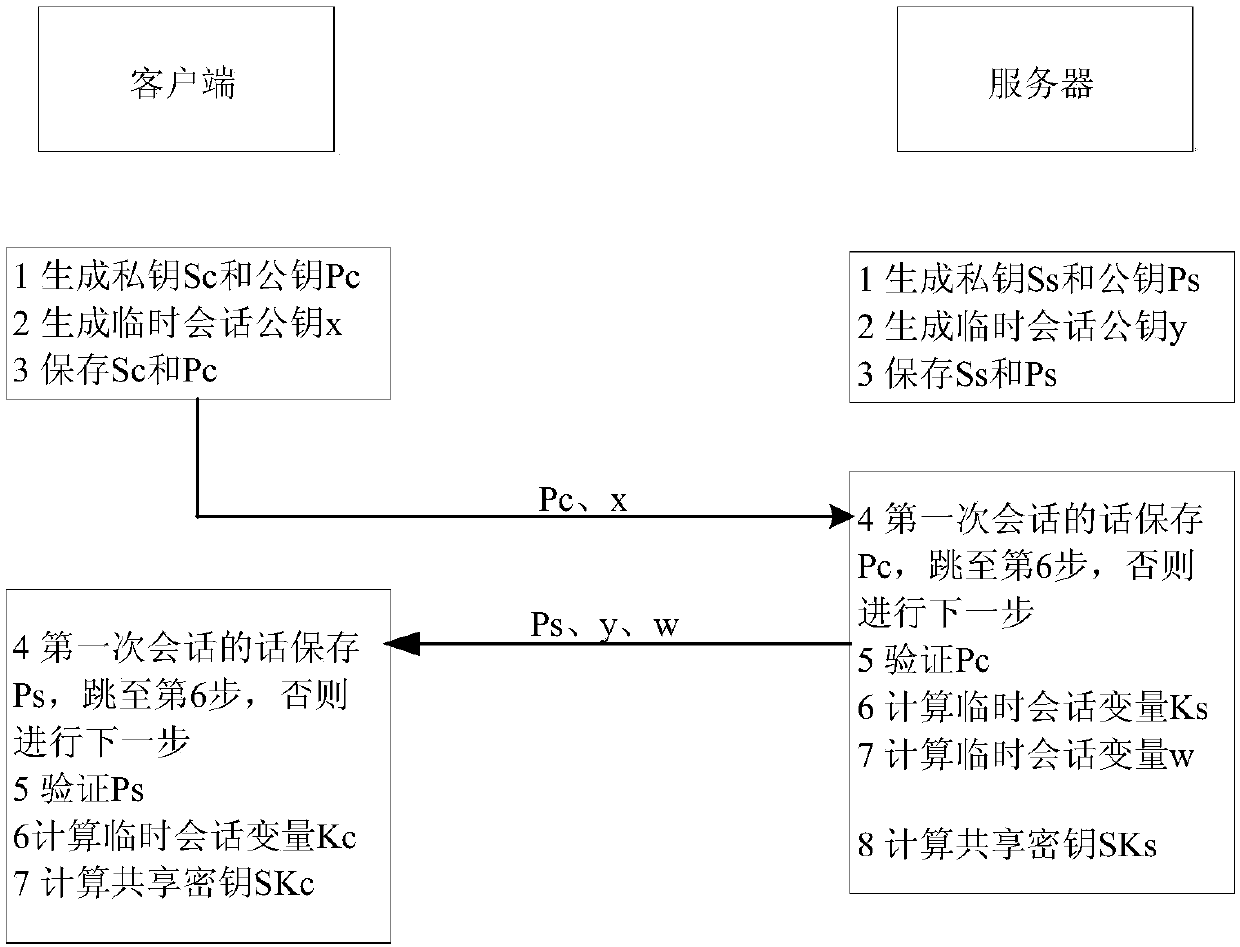
[0289] The system for implementing the SSH protocol based on post-quantum key exchange includes a key exchange module, and the key exchange module includes a first key unit, a second key unit, a first verification unit, and a second verification unit, wherein:
[0290] The first key unit is located in the server and is used to complete the following functions:
[0291] Randomly sample from the Gaussian distribution of the first parameter, and calculate the public-private key pair of the server;
[0292] After the first verification unit passes the identity authentication of the client, it calculates the temporary session public key of the server f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com