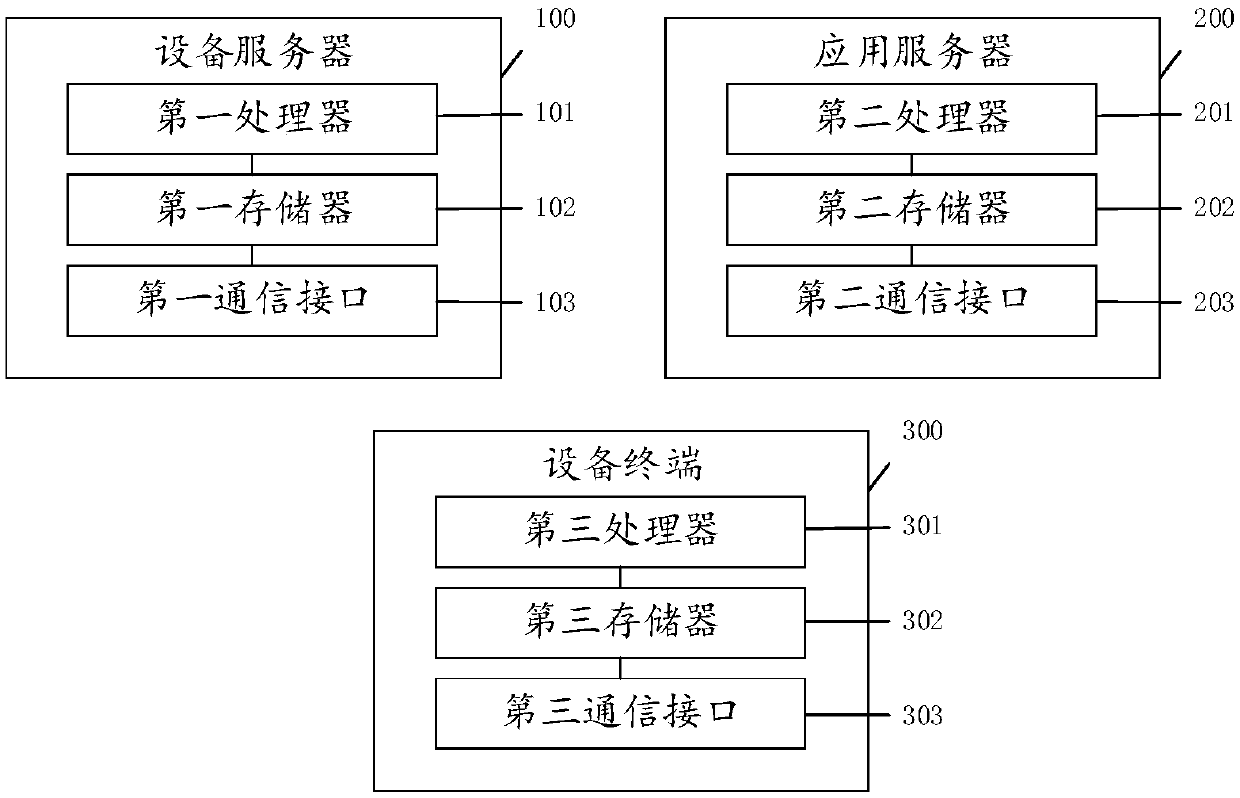
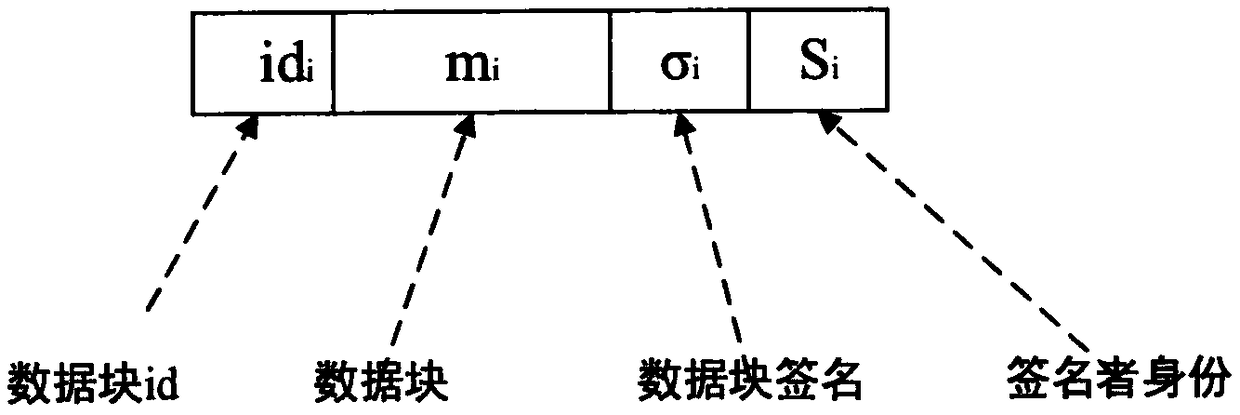
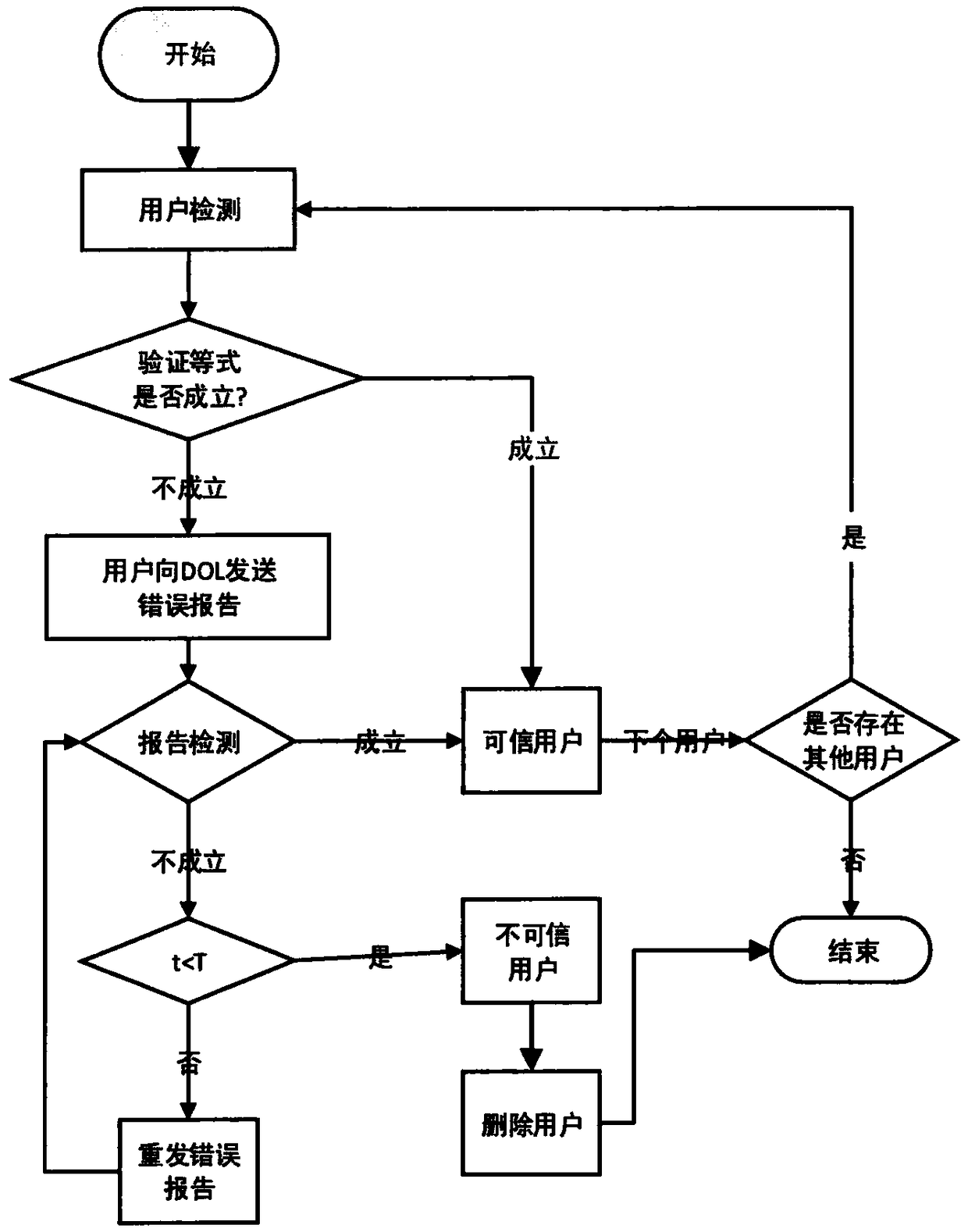
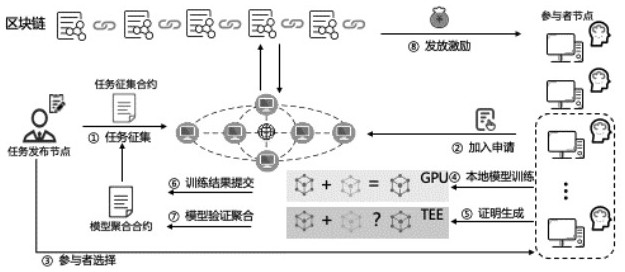
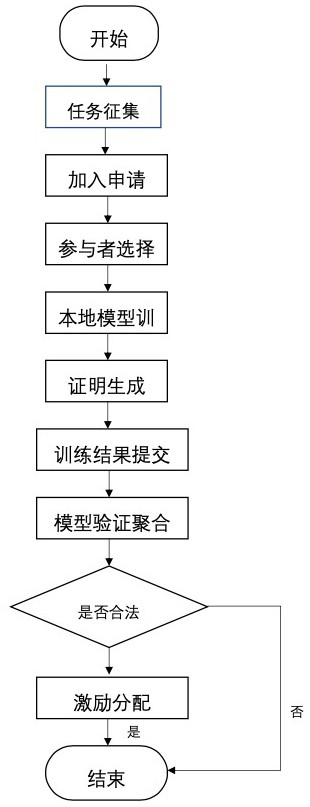
Patents
Literature
38results about How to "Solve untrustworthy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
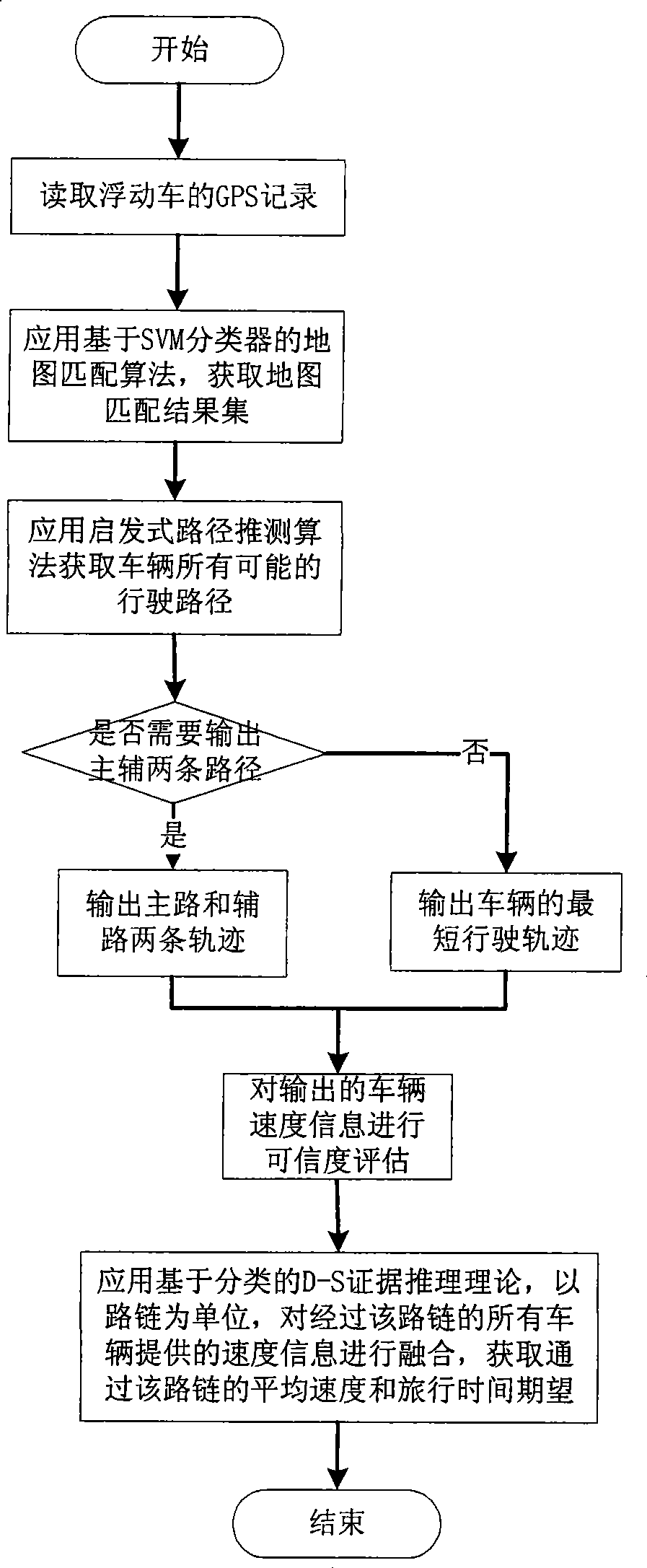
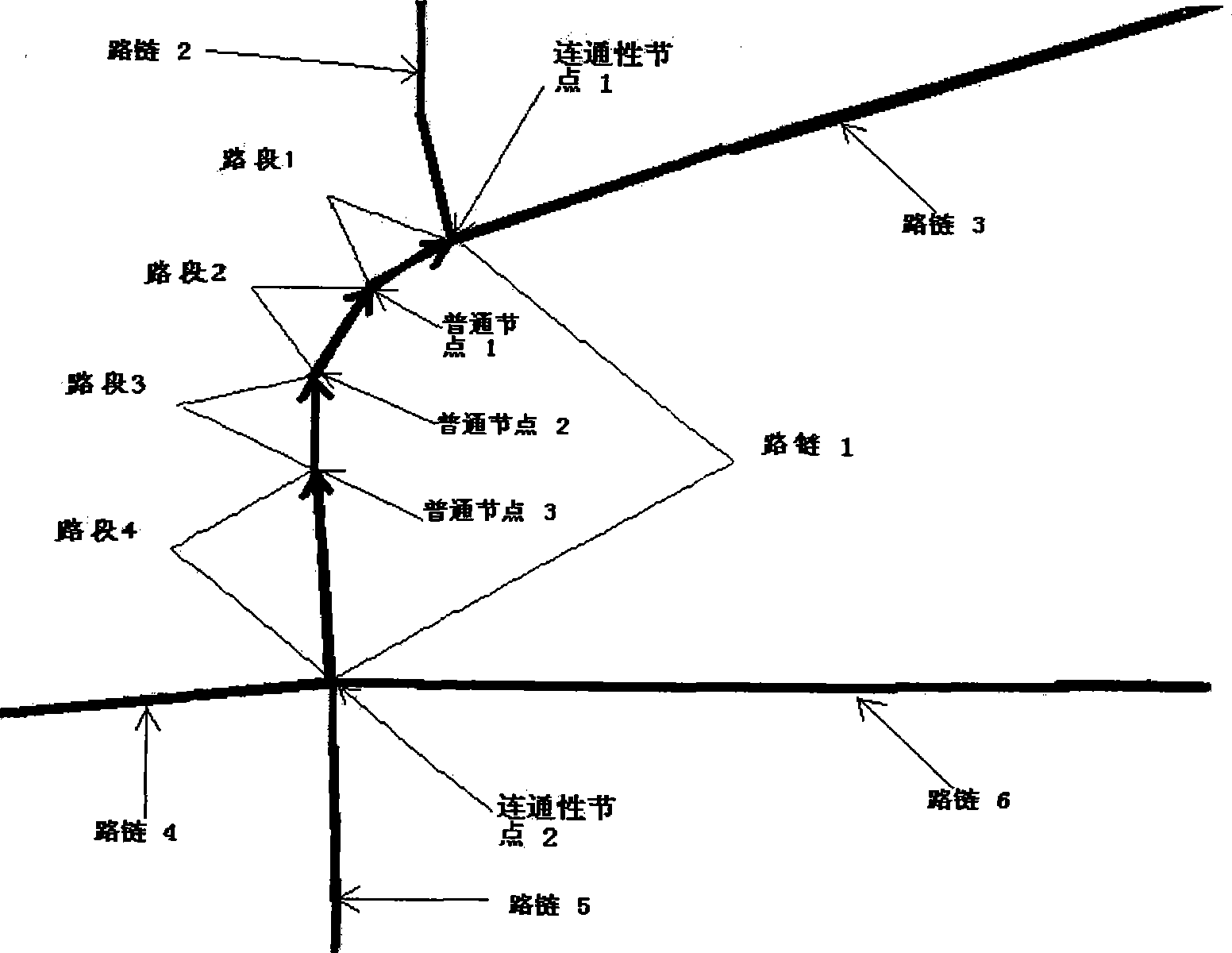
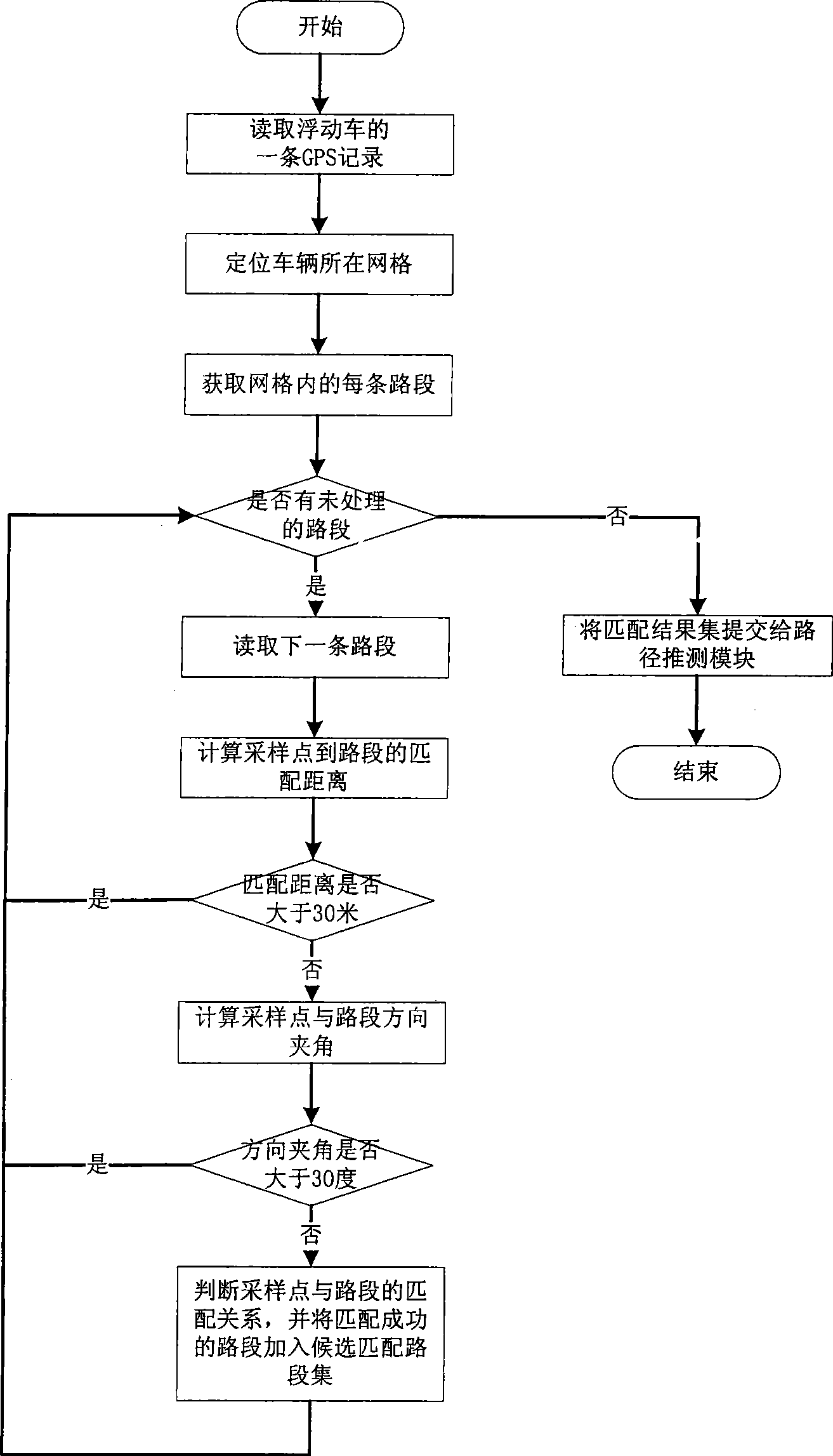
Floating vehicle information processing method under parallel road network structure
InactiveCN101383090AHigh precisionImprove processing accuracyInstruments for road network navigationRoad vehicles traffic controlInformation processingEvidence reasoning
The invention relates to a method for processing the information of float cars under the structure of a parallel road network, which is mainly applied to the service field of the intelligent dynamic traffic information. The method comprises the steps: step 1, an SVM (Support Vector Machine) sorter is adopted to judge the matching relationship between sampling points and roads, and map match is carried out; step 2, according to map match information, a heuristic route deduction algorithm is adopted to deduce possible running routes of a car, and according to the properties of road chains contained in the routes, whether the car runs in the structure of a parallel road network or not is judged; the shortest running route or a main running route and a subsidiary running route are selectively output in different circumstances, and the reliability of average running speed information provided by the car is estimated; step 3, the D-S (Dempster-Shafer) evidence reasoning theory based on classification is adopted to merge road condition information provided by all the float cars passing by a certain road chain in a current period and consider the reliability of the road condition information in a merging process so as to obtain the mathematical expectations of the average speed and the travel time of the float cars passing by the road chain in the current period. On the basis that the data quality of the prior float cars is kept unchanged, the invention realizes the acquisition of the real-time dynamic traffic information under the structure of a parallel road network.
Owner:BEIHANG UNIV
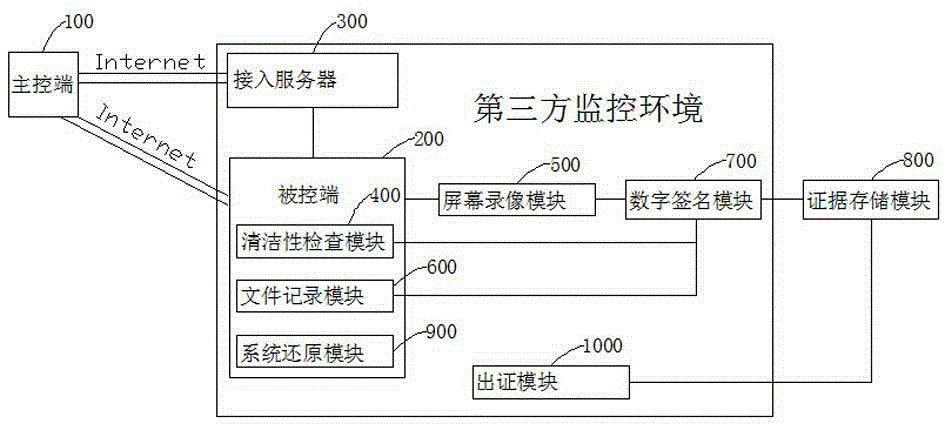
Network electron evidence processing system and processing method
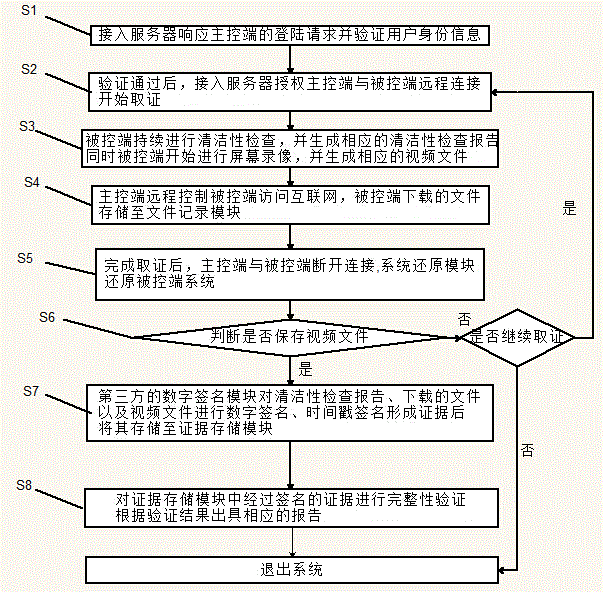
InactiveCN105046168ASolve untrustworthyGuaranteed cleanlinessUser identity/authority verificationDigital data protectionThird partyEngineering
The invention discloses a network electron evidence processing system and a processing method; the processing system comprises a main control end, an access server, a controlled end remotely connected with the main control end, a cleanness check module, a screen recording module, a file recording module, a digital signature module, an evidence storage module, a system reduction module, and a testify module; the access server, the controlled end, the cleanness check module, the screen recording module, the file recording module, the digital signature module, the system reduction module and the testify module are respectively under a third party monitoring environment. The processing method comprises the following steps: a user uses the main control end to remotely control the controlled end to visit the internet; simultaneously the screen recording module carries out screen recording; the third party uses the digital signature module to do digital signature on evidence obtaining files, and stores the files; when needing testify, the testify module can do integrity verification for the evidence with digital signature, and provides a corresponding report. The evidence obtaining, evidence storage and a testifying process are witnessed by the third party, so a user networking real process can be restored.
Owner:上海人科数据科技有限公司
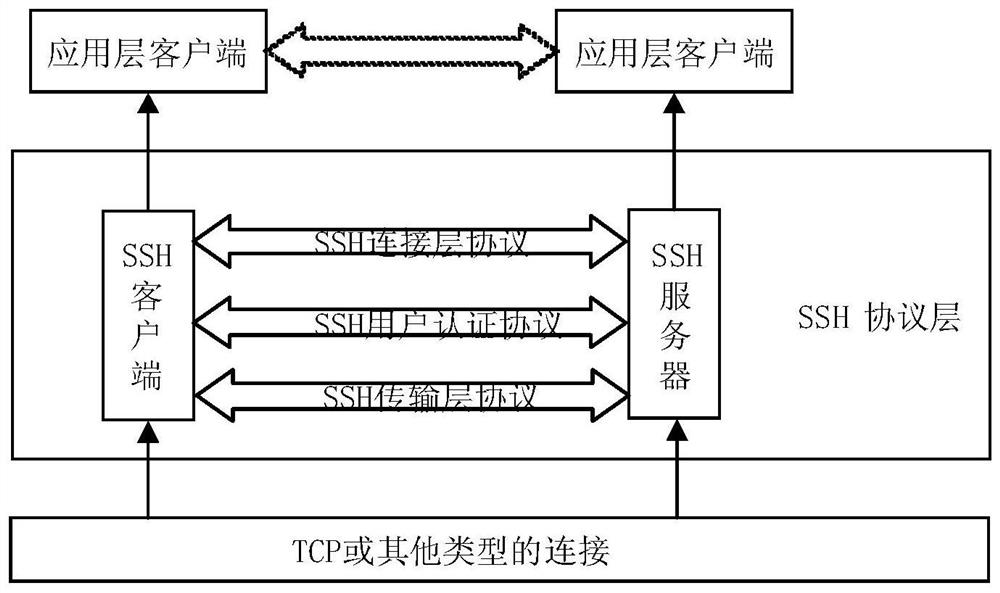
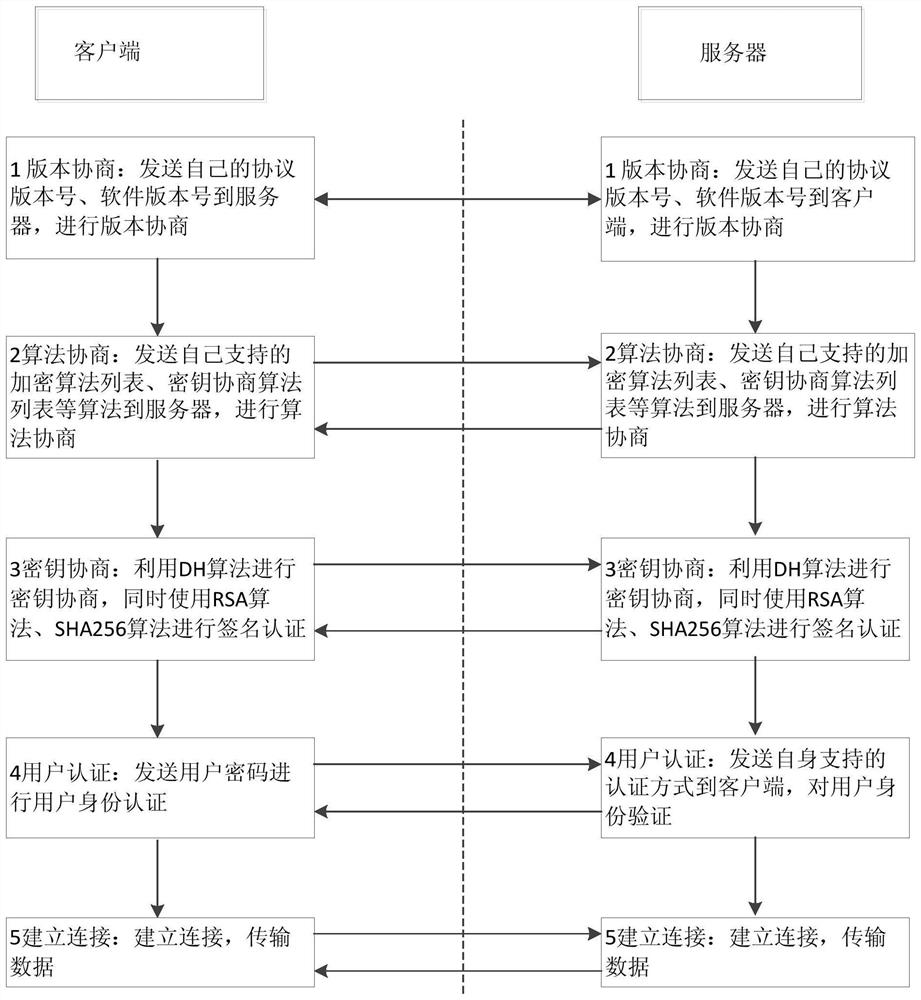
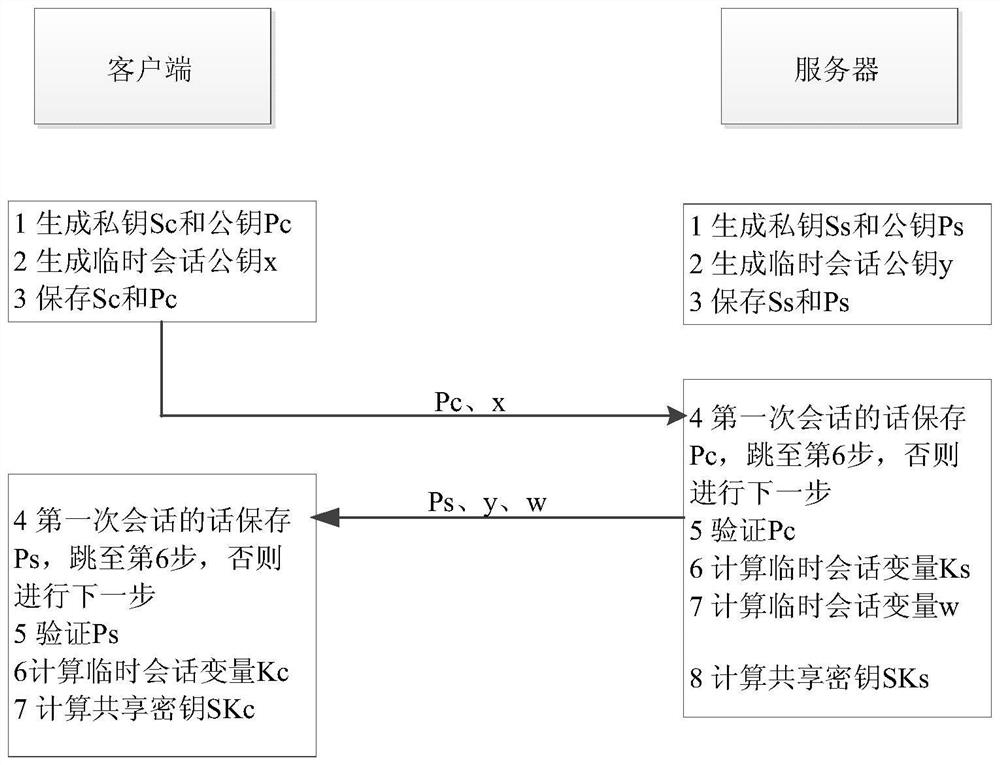
Method and system for achieving SSH protocol based on post-quantum key exchange
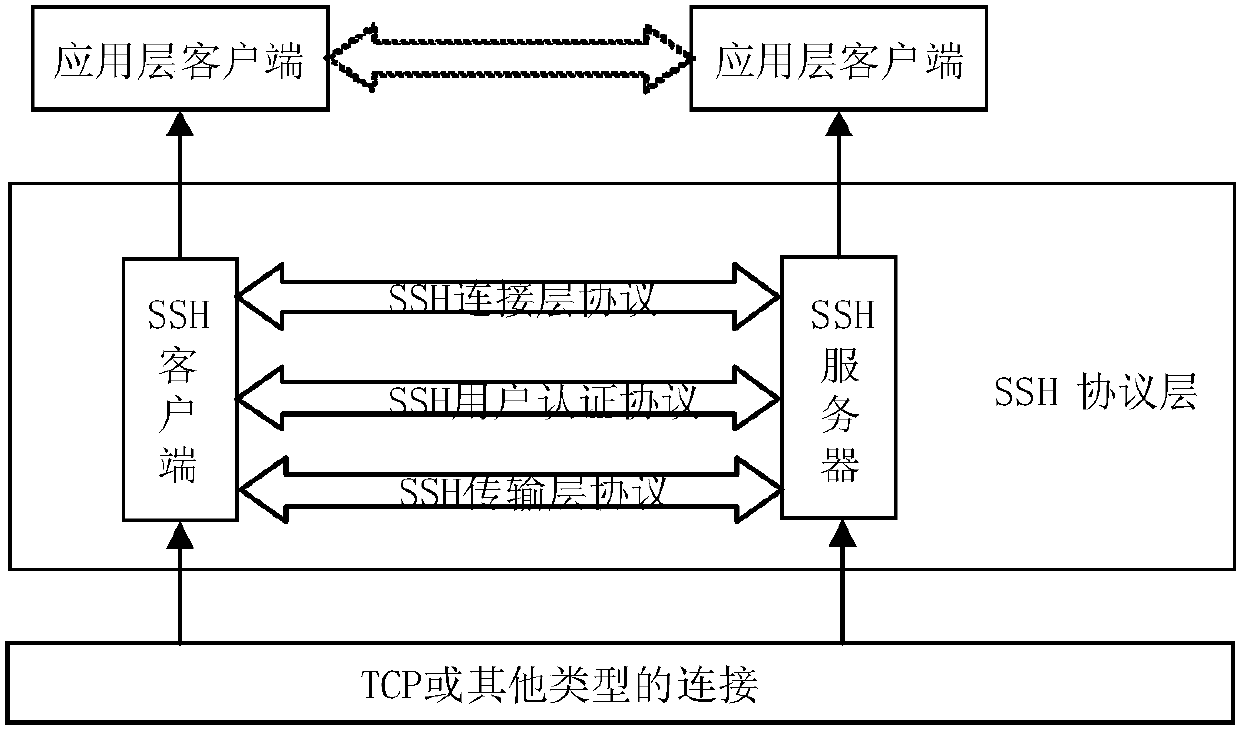
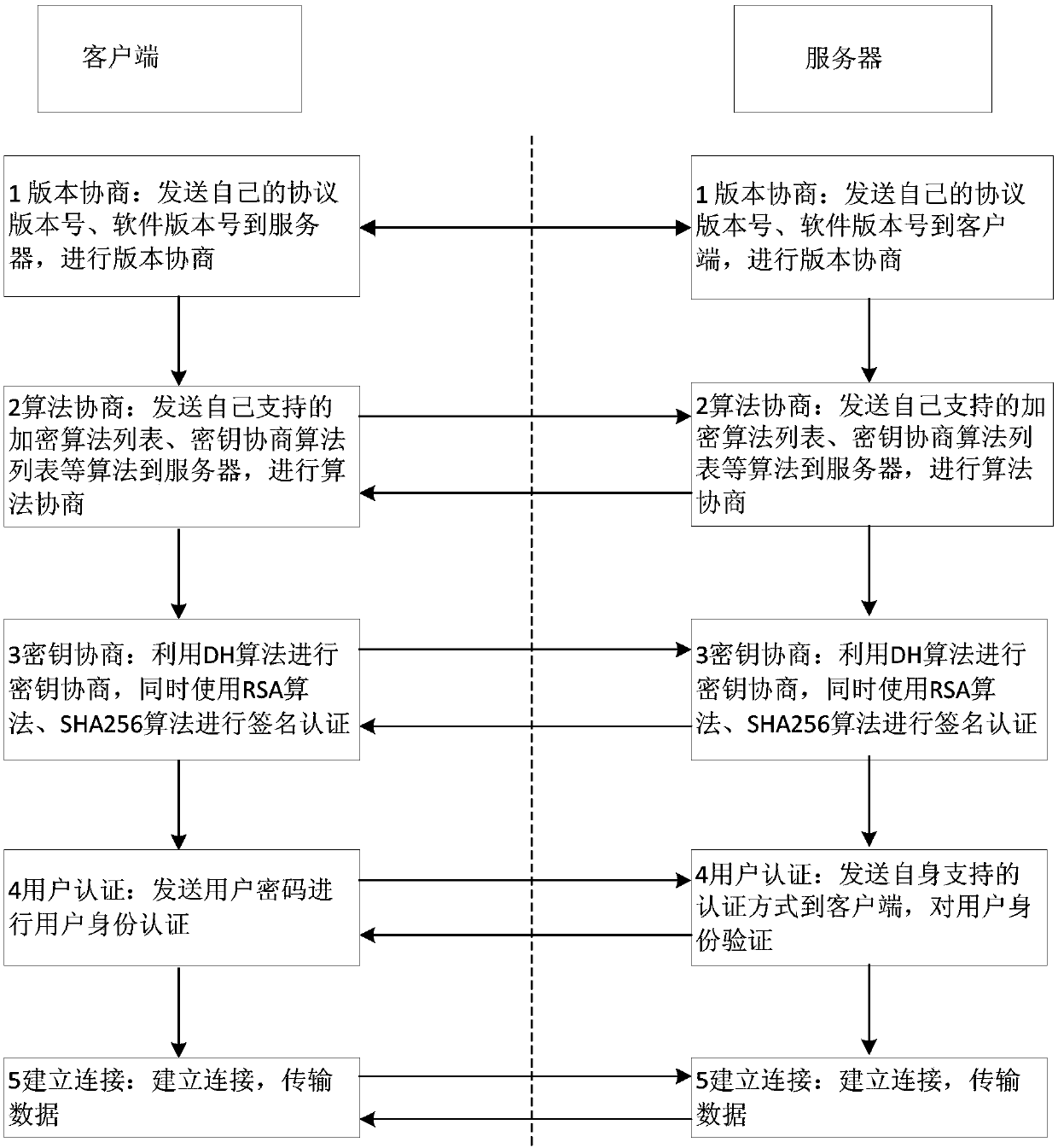
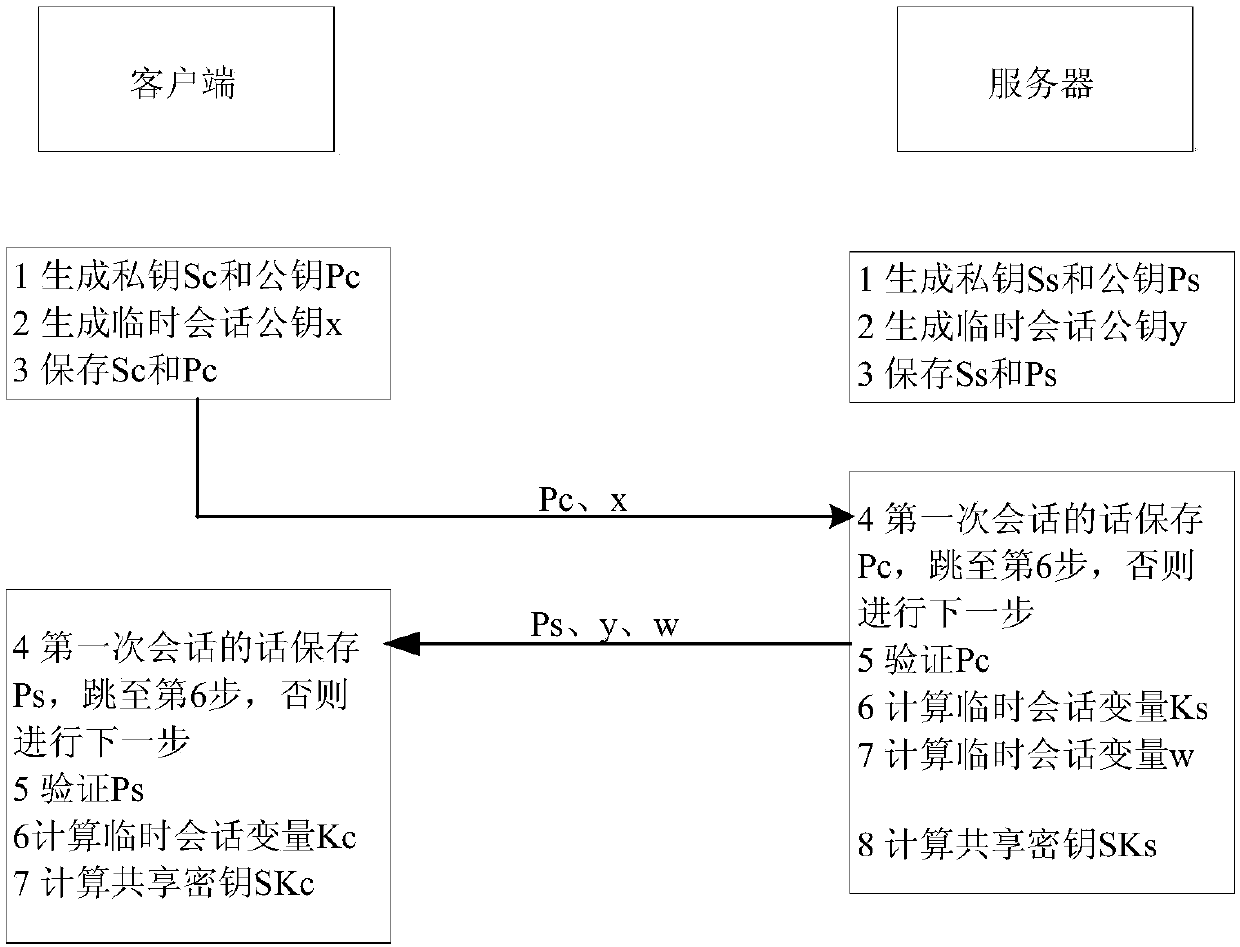
ActiveCN108111301ASolve untrustworthyKey distribution for secure communicationUser identity/authority verificationKey exchangeQuantum algorithm
The invention belongs to the technical field of information, and particularly relates to a method and system for achieving SSH protocol based on post-quantum key exchange. The method comprises the steps of a client and a server respectively calculating a public and private key pair; calculating a temporary session public key of the client, and sending the client public key and the client temporarysession public key to the server; the server performing identity verification on the client; calculating a temporary session public key of the server; calculating a temporary session variable of theserver and a temporary session error eliminating variable, the server sharing secret key initial seeds; the server generating a final server sharing secret key of the conversation through the post-quantum algorithm; the client side verifying the identity of the server according to the public key of the server; the client passes the identity identification of the server, calculating the temporary session variables of the client and the initial seed of the shared secret key of the client; and the client side using a post-quantum algorithm to generate a final client shared secret key of the conversation. According to the method and the system, the attack of the quantum computer can be effectively resisted, and the safety of the network is ensured.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Method and device for preventing information tampering
InactiveCN109600392ASolve untrustworthyKey distribution for secure communicationUser identity/authority verificationApplication serverComputer security
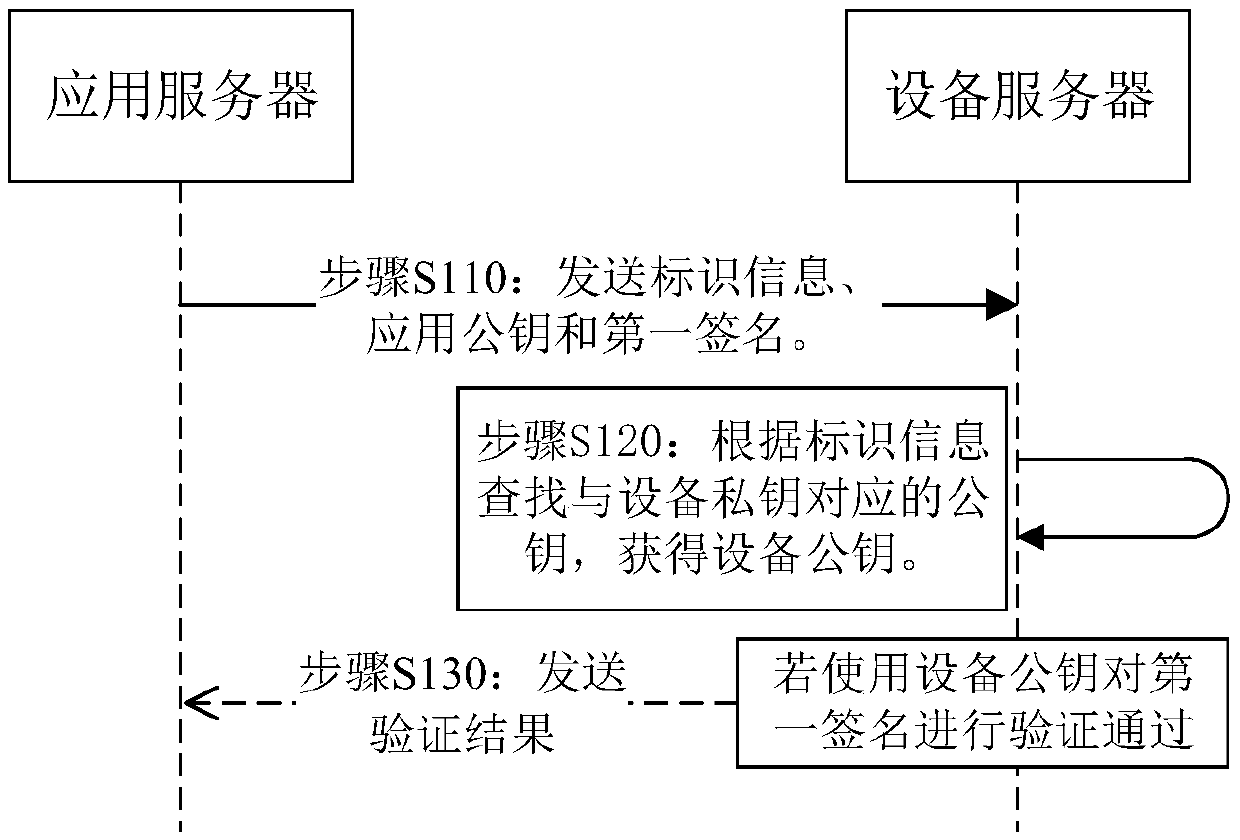
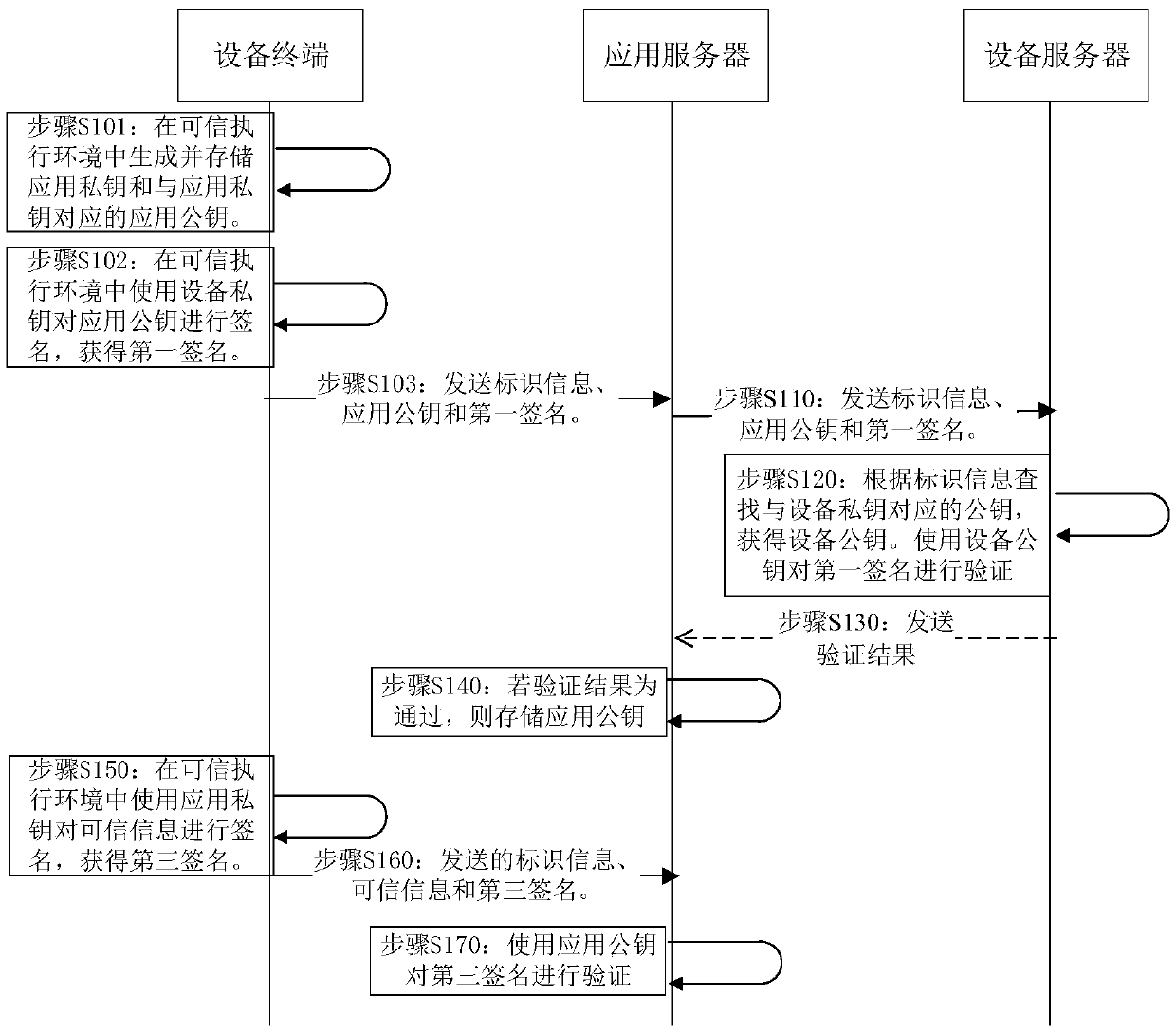
The invention provides a method and device for preventing information tampering. The method and the device are used for solving the problem that information acquired by a server is untrusted due to the fact that terminal position information can be tampered in the prior art. The method comprises the steps: receiving identification information sent by an application server, and applying a public key and a first signature, wherein the identification information is identification information of an equipment terminal, the application public key is generated by the equipment terminal and sent to the application server, the first signature is obtained by the equipment terminal by using an equipment private key to sign the application public key in a trusted execution environment, and the information stored in the trusted execution environment cannot be modified by an untrusted application program; searching a public key corresponding to the equipment private key according to the identification information to obtain the equipment public key which corresponds to the equipment private key stored in the equipment terminal; and sending a verification result to the application server if the first signature is verified successfully by using the device public key.
Owner:SICHUAN PANOVASIC TECH
Cloud Data Sharing Method Based on Block Chain to Realize Data Tampering Resistance and User Collusion
ActiveCN109145612AEffective traceabilityEnsure safetyDigital data protectionTransmissionTamper resistanceConfidentiality
In recent years, with the application of cloud more and more widely, the problem of privacy leakage of cloud sharing data is constantly occurring at home and abroad. Privacy leakage in cloud data sharing has become the focus of attention, and relevant solutions are constantly proposed. Most of the existing schemes are composed of a single shareholder or a specific user. However, in actual data sharing scenarios, the shared data is usually provided by multiple data owners, which brings a series of new problems to protect the privacy of the data, such as malicious tampering of the shared data, collusion between malicious users, and collusion between users and cloud service providers. The invention provides a cloud data sharing method based on block chain for realizing data tampering prevention and user conspiracy. The method realizes that the data is not tampered with by malicious users when sharing by adopting the method of public bookkeeping and intelligent contract in the block chain,and realizes the confidentiality of the shared data by adopting a (p, t) threshold Paillier cryptosystem, thereby avoiding the problem that malicious users collude to steal the shared data.
Owner:DONGHUA UNIV
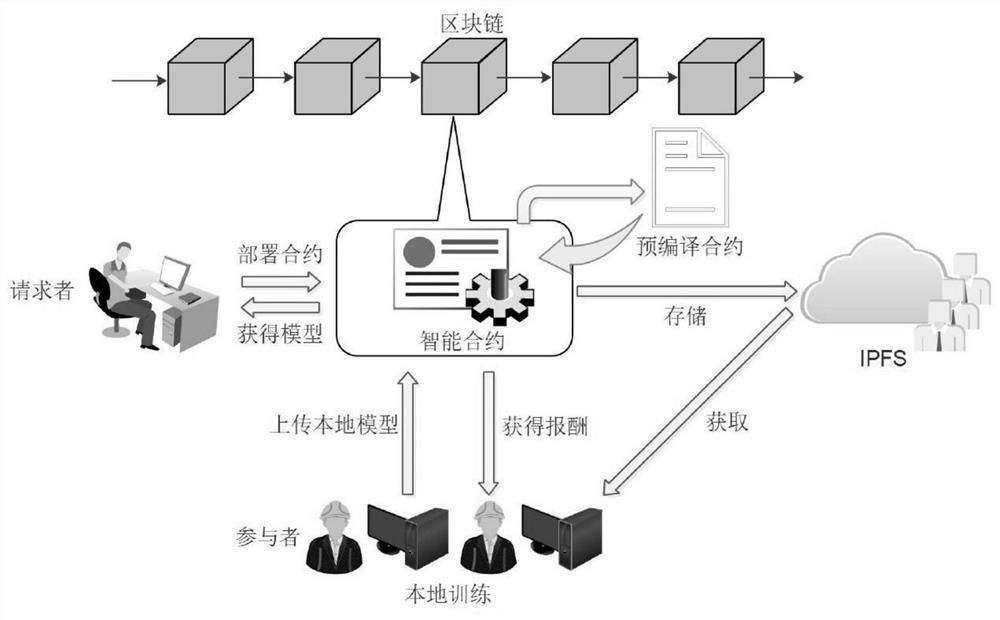
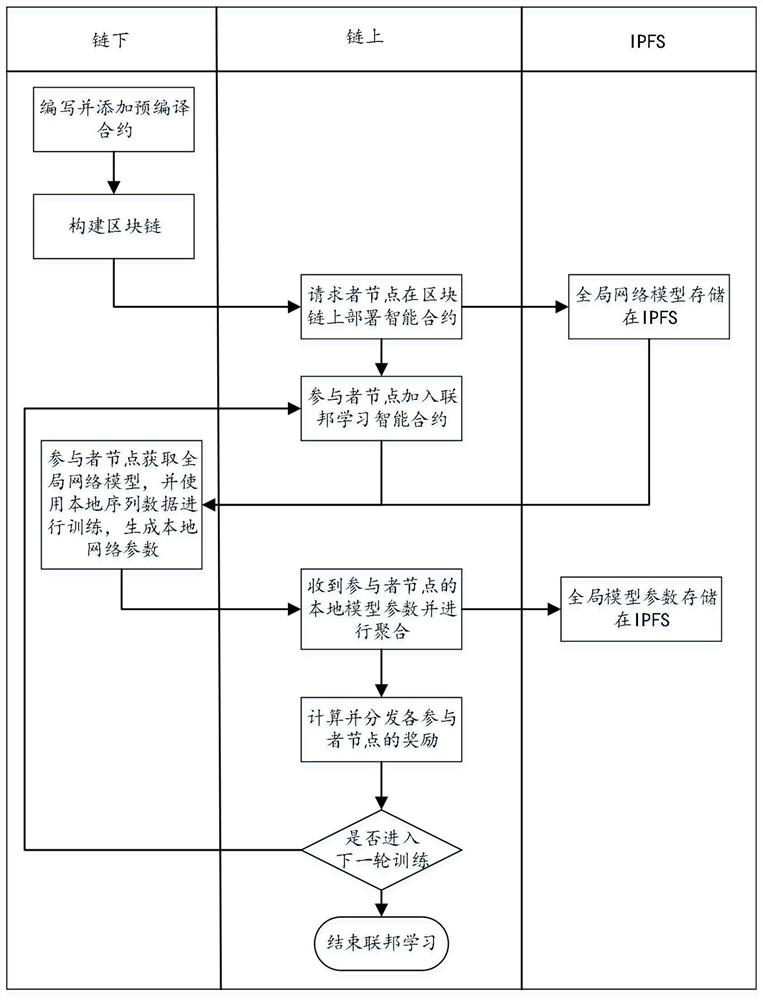
Federal learning method and system based on block chain and trusted execution environment
ActiveCN113837761AHigh Confidence VerificationPrevent model trainingMachine learningProtocol authorisationChain networkMachine learning
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Decentralized data transaction method based on block chain
ActiveCN111402055ASolve untrustworthySolve the central single point of failure problemFinanceDigital data protectionTransaction serviceData provider
The invention discloses a decentralized data transaction method based on blockchain. The method is applied to a big data transaction environment composed of a secret key generation center, a blockchain and an intelligent contract; data summary information collection of a data transaction market is achieved through the blockchain, evaluation information of data use conditions is recorded, and transaction records in data transaction are recorded; data requirements can be issued through the intelligent contract, data required by a data demander is matched and screened, and distribution of data rewards is automatically completed. The problem that a data transaction center is not credible can be solved, ownership and informed rights of a data provider to personal data in transaction are guaranteed, intelligence and high efficiency of the data transaction process are improved, and therefore safe and reliable big data transaction service can be provided for two transaction parties.
Owner:HEFEI UNIV OF TECH
Method and system for obtaining user position
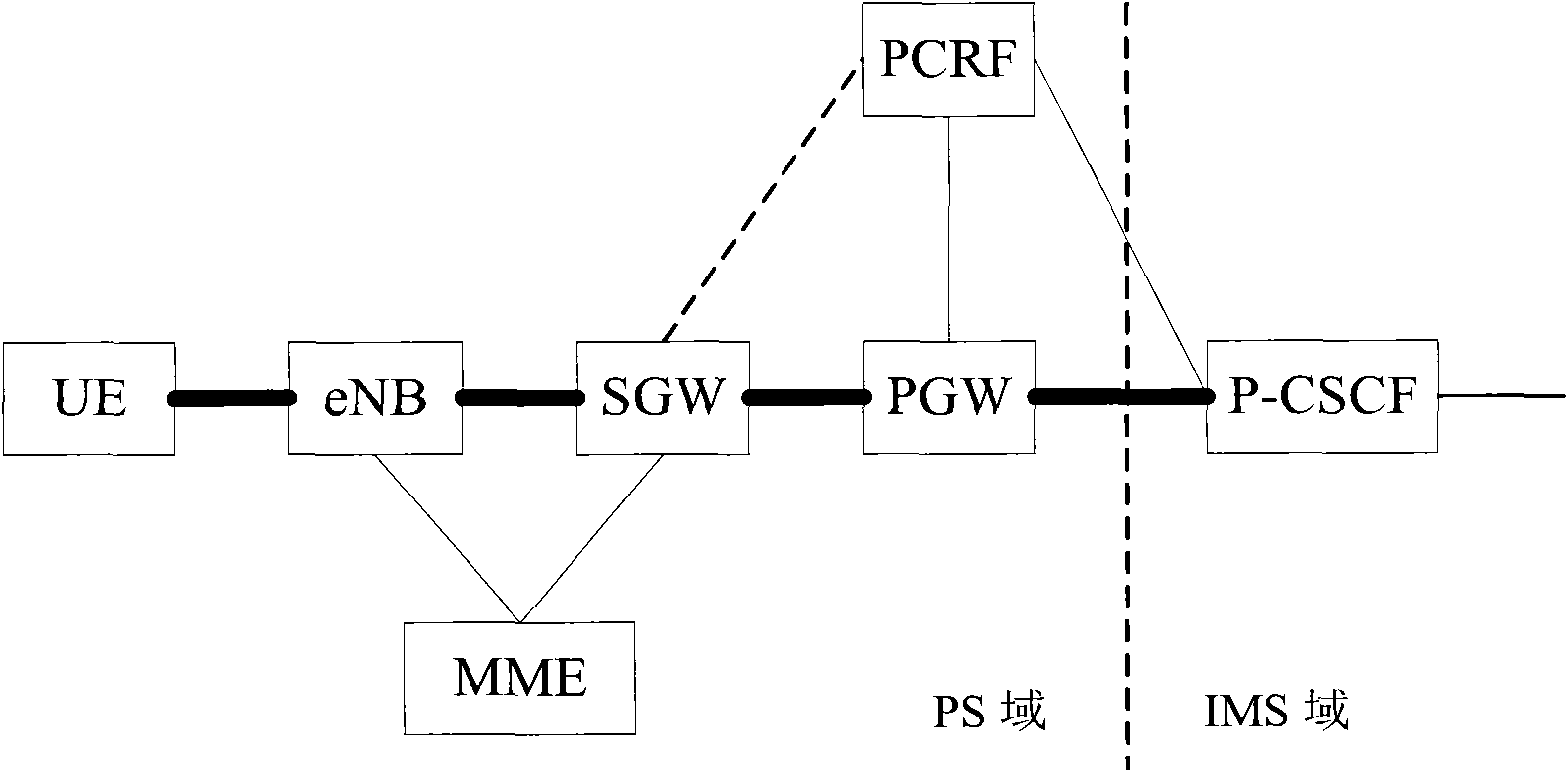
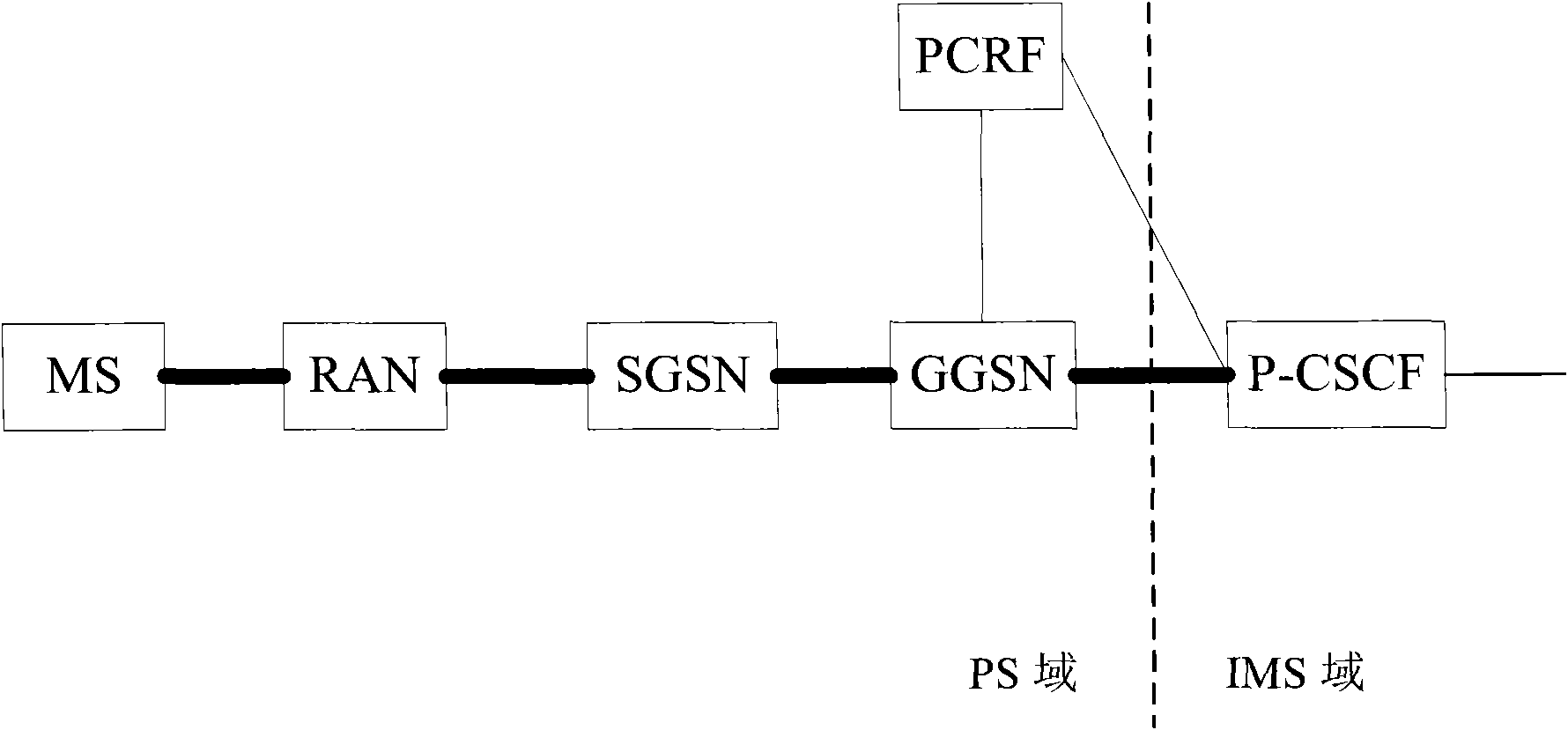
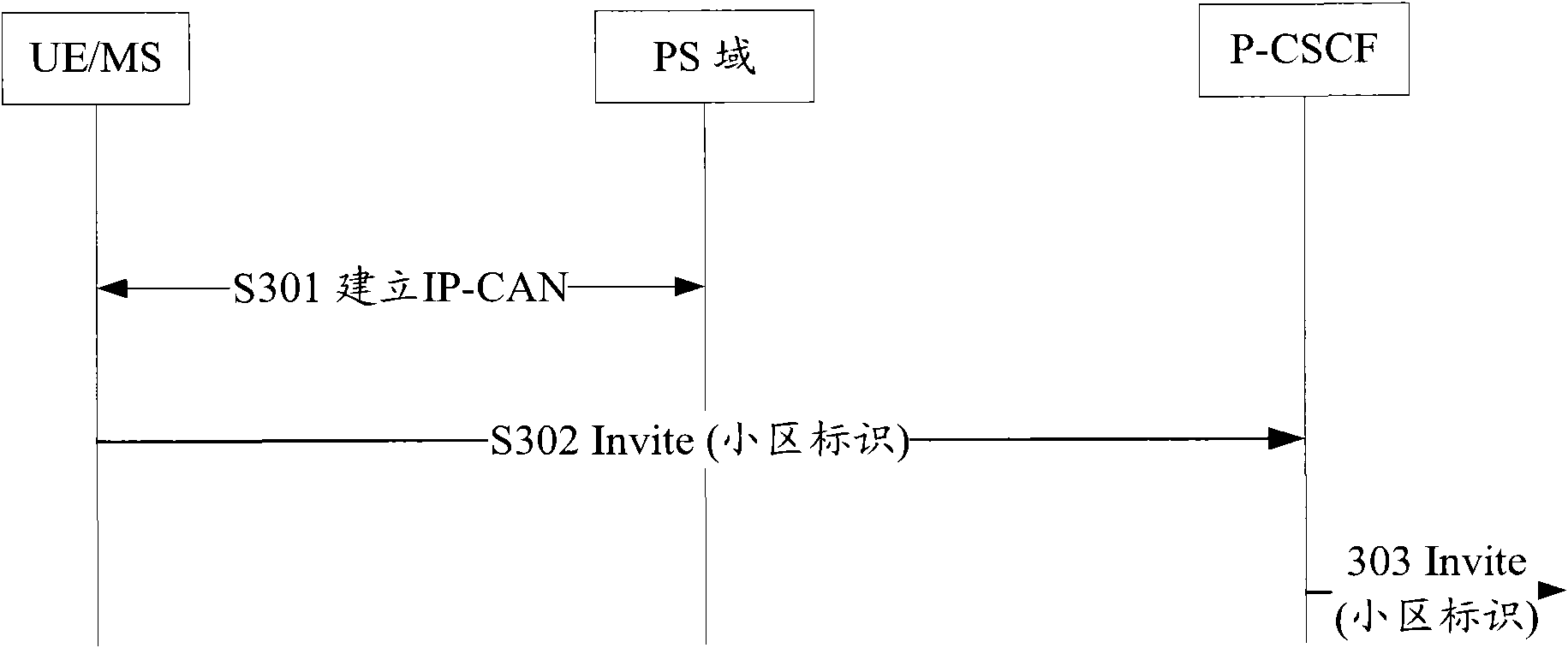
InactiveCN102316438ASolve untrustworthyImprove securityPosition fixationTransmissionComputer terminalInternet management
The invention discloses a method and a system for obtaining a user position, wherein the method comprises the following steps that: when an internet management specification (IMS) network element of an Internet multimedia sub system needs the position information of terminal user equipment (UE), the IMS network element requests the position information of the UE to a grouped exchange process status (PS) network element; and the PS network element obtains the position information of the UE and reports the position information of the UE to the IMS network element. According to the method and the system, the problem of unreliable position information reported by the UE is solved, and the safety of the system is enhanced.
Owner:ZTE CORP
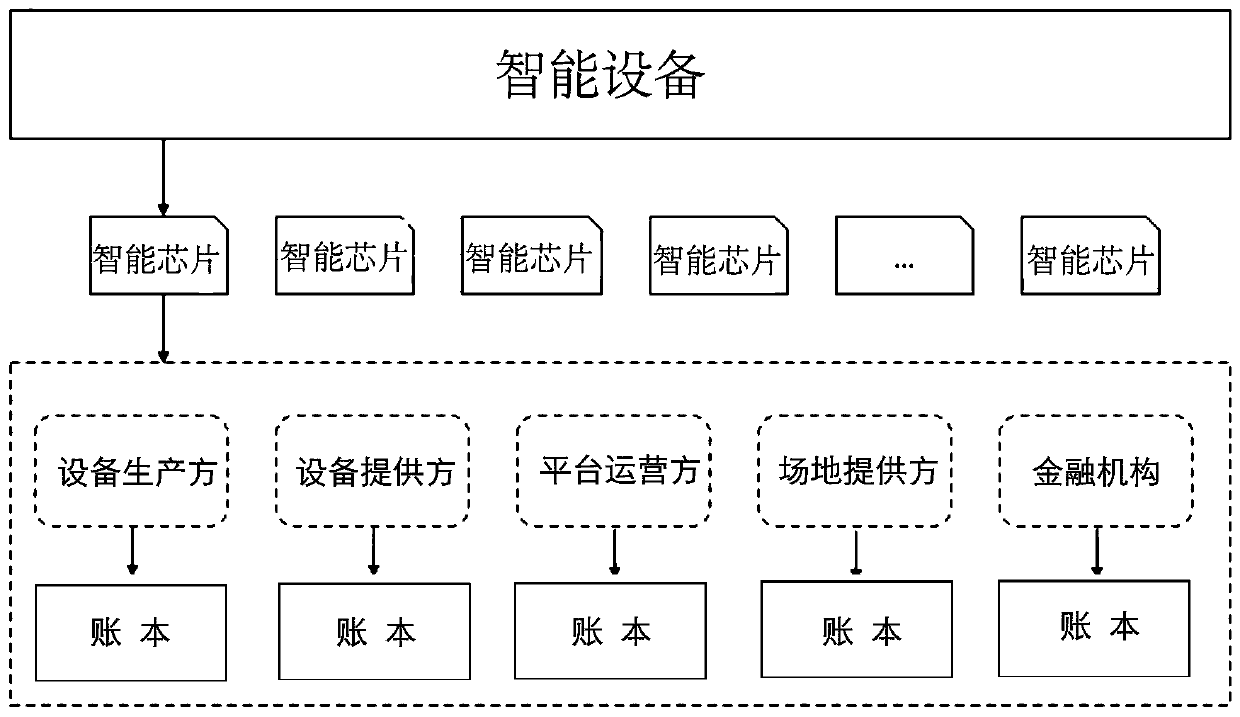
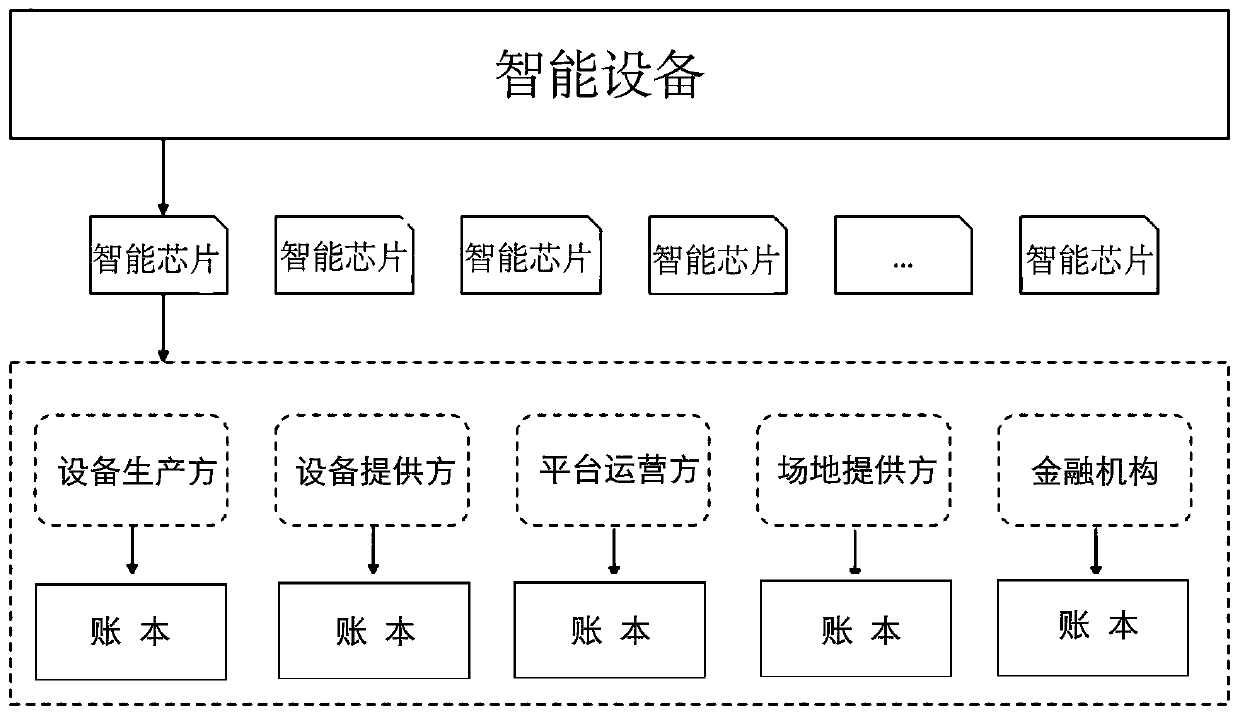
A shared economic accounting method based on a block chain
ActiveCN109685504AImprove operational efficiencySolve the untrustworthy sourceTransmissionProtocol authorisationAccounting methodBlockchain
The invention provides a shared economic accounting method based on a block chain. According to the method, a plurality of participation subjects of the shared economy are respectively provided with anode on a block chain; a plurality of nodes form an alliance chain; A block chain technology is introduced into traditional sharing economy; trust-free of the block chain in a sharing environment isutilized; The method has the advantages that the method is simple and easy to operate, the characteristics of medium removal, non-tampering and traceability are achieved, a trusted, ownership-ascertainable and traceable shared economic system is constructed, high trust among a demander, a supplier, a platform party and a site provider is achieved, then traceable and trusted value evaluation is provided for purchasing and financial means, and the operation efficiency of the shared economy is improved.
Owner:雄安新区智能城市创新联合会
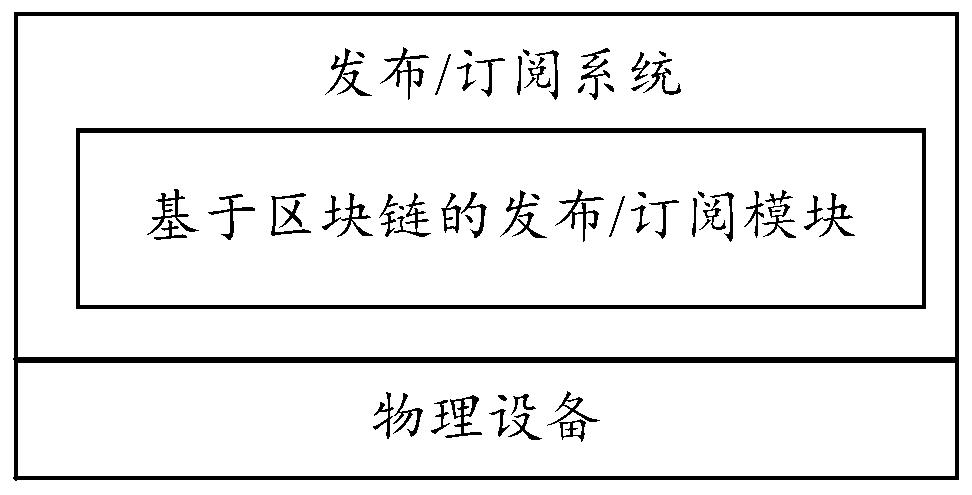
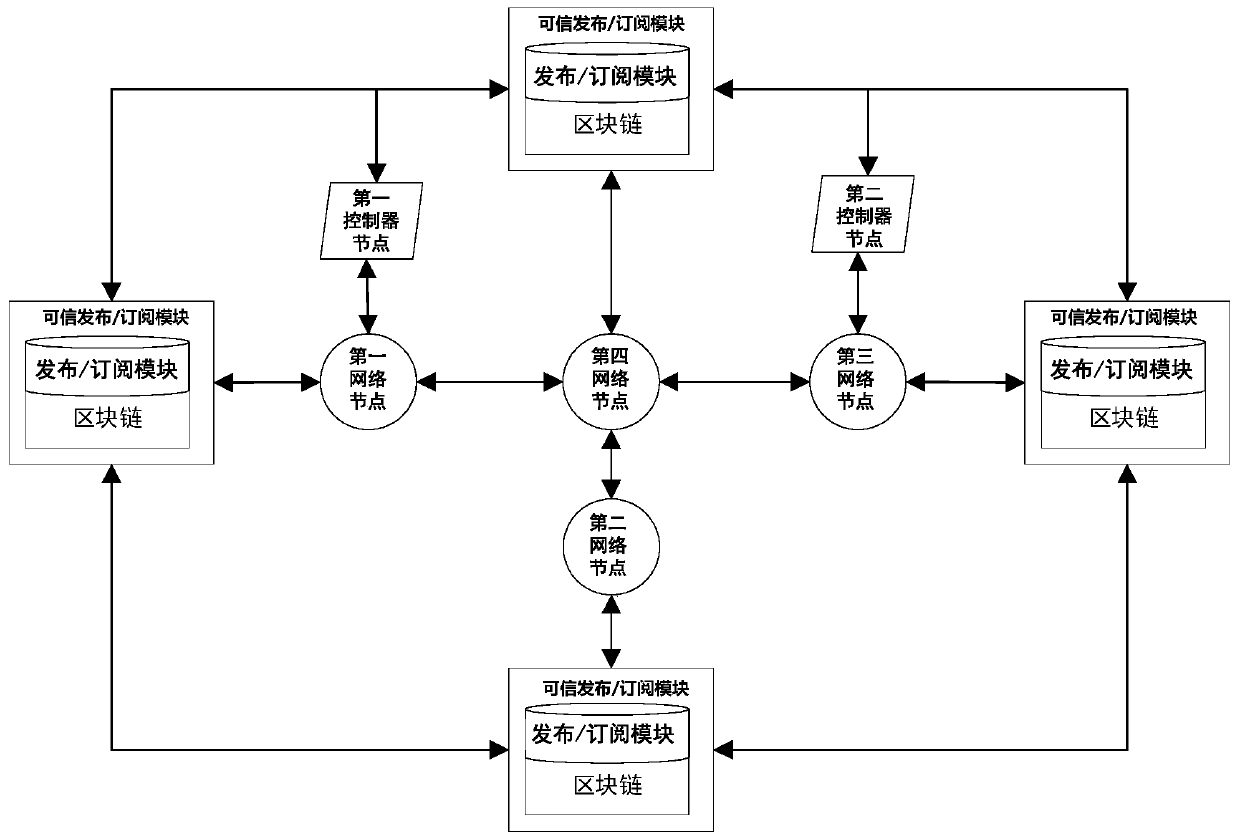
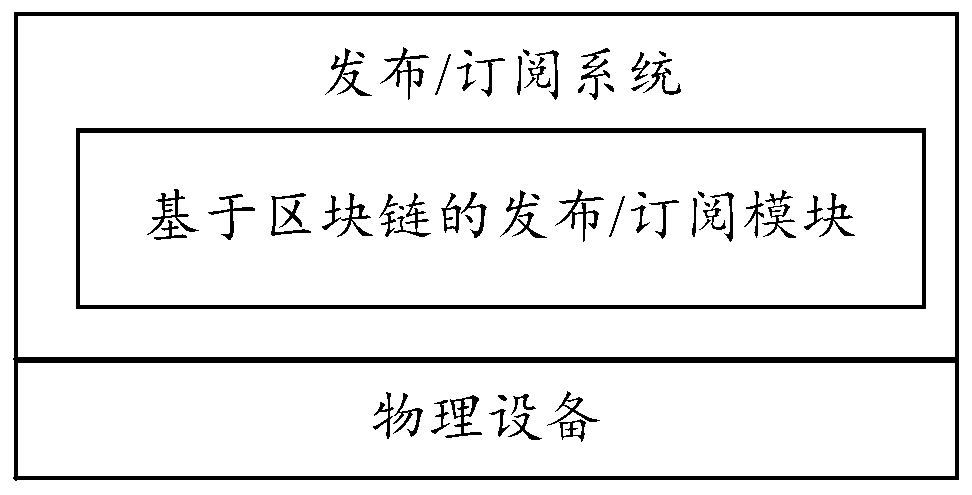
Publishing/subscribing system architecture based on block chain
InactiveCN110035081ASolve untrustworthyGuaranteed trusted relationshipTransmissionNetwork communicationPublish–subscribe pattern
The invention discloses a publishing / subscribing system architecture based on a block chain. The publishing / subscribing system architecture comprises physical equipment and a publishing / subscribing system installed on the physical equipment, the publishing / subscribing system comprises a publishing / subscribing module based on a block chain used for verifying and storing the identity information ofthe physical equipment. According to the invention, a publishing / subscribing system with a publishing / subscribing module based on a block chain is installed in physical equipment; trusted management and authentication mechanisms of the identity information of the physical equipment are realized based on the characteristic that the block chain cannot be tampered and a distributed consensus mechanism, the credible relationship between the equipment of the publishing / subscribing system is ensured, and the problem that the network communication is not credible in the publishing / subscribing systemin the prior art is solved.
Owner:CHINA ACADEMY OF ELECTRONICS & INFORMATION TECH OF CETC
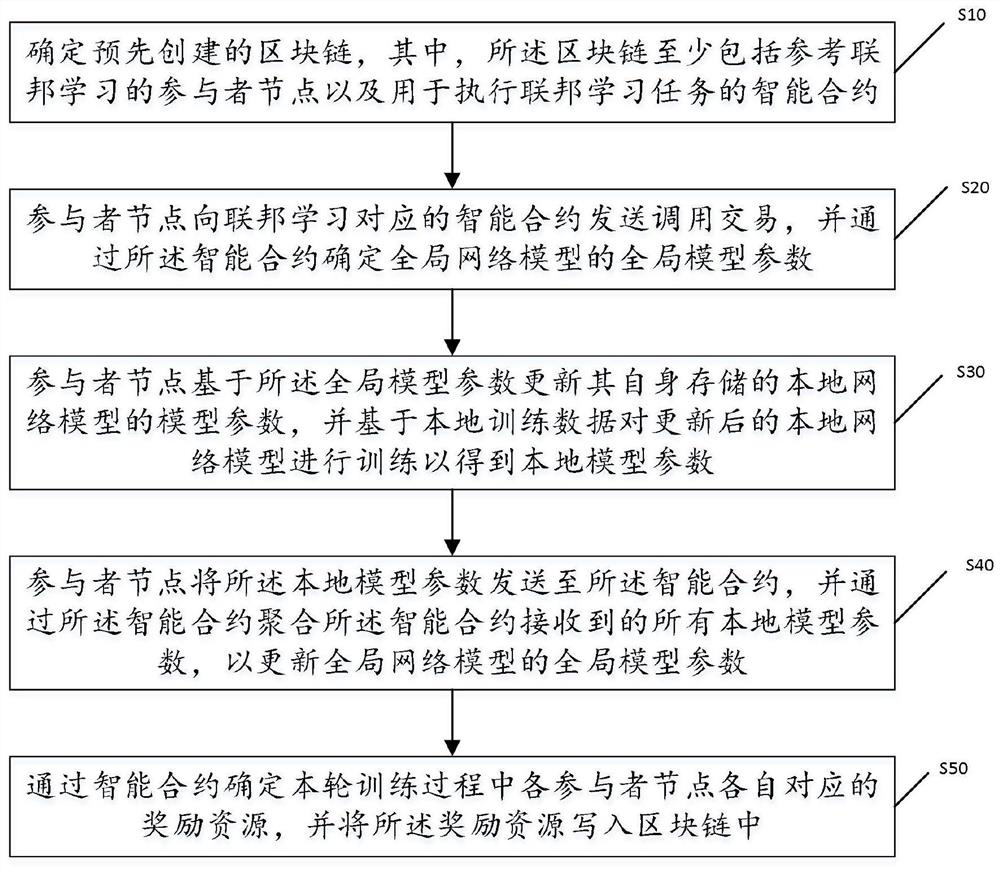
Block chain-based distributed federal learning method and apparatus, and terminal device
ActiveCN113408746ASolve untrustworthyEnsemble learningDatabase distribution/replicationTrusted ComputingTerminal equipment
The invention discloses a distributed federal learning method and device based on a block chain and terminal equipment. The method comprises the following steps: determining a pre-created block chain; the participant node determines a global model parameter through the intelligent contract, updates a model parameter of the local network model based on the global model parameter, and trains the updated local network model based on the local training data to obtain a local model parameter; the participant node sends the local model parameters to the intelligent contract, and aggregates all the received local model parameters through the intelligent contract to update the global model parameters; and determining the reward resource corresponding to each participant node in the training process through the intelligent contract. According to the application, the function of the central server in the traditional federated learning is realized by using the intelligent contract on the block chain, so that the central server in the federated learning is replaced by using the intelligent contract capable of performing trusted computing, and the problem that the central server in the federated learning is not trusted can be solved.
Owner:SHENZHEN UNIV
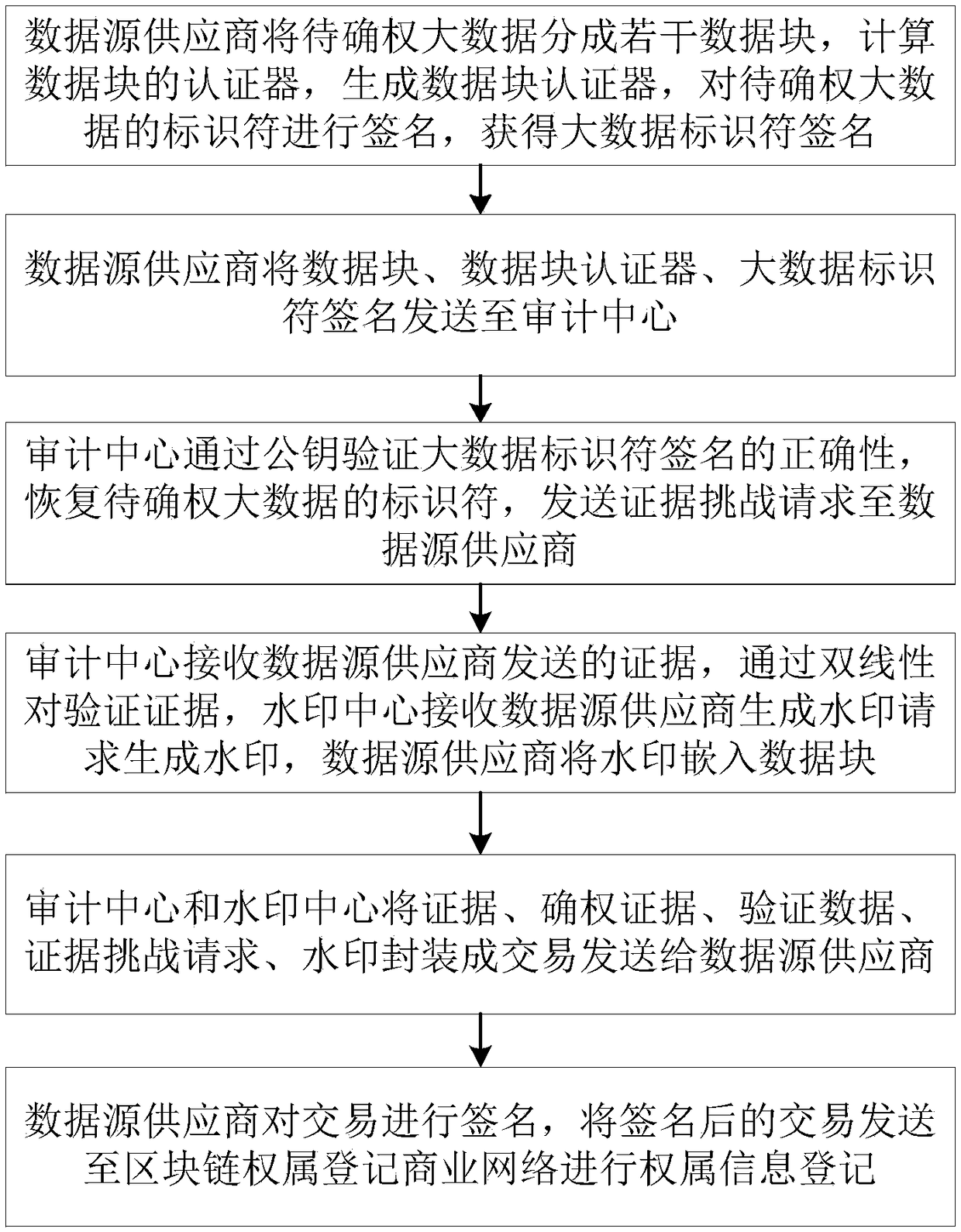
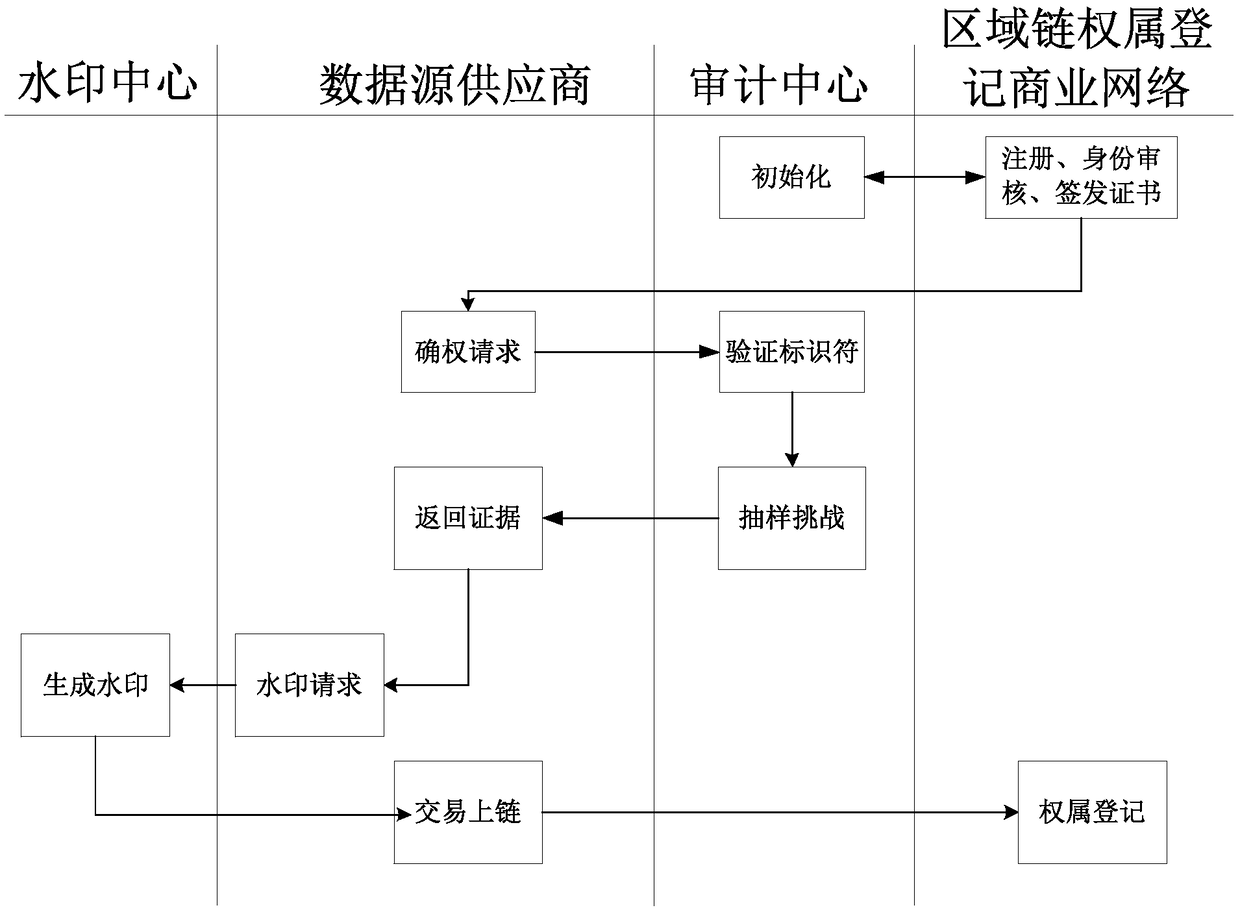
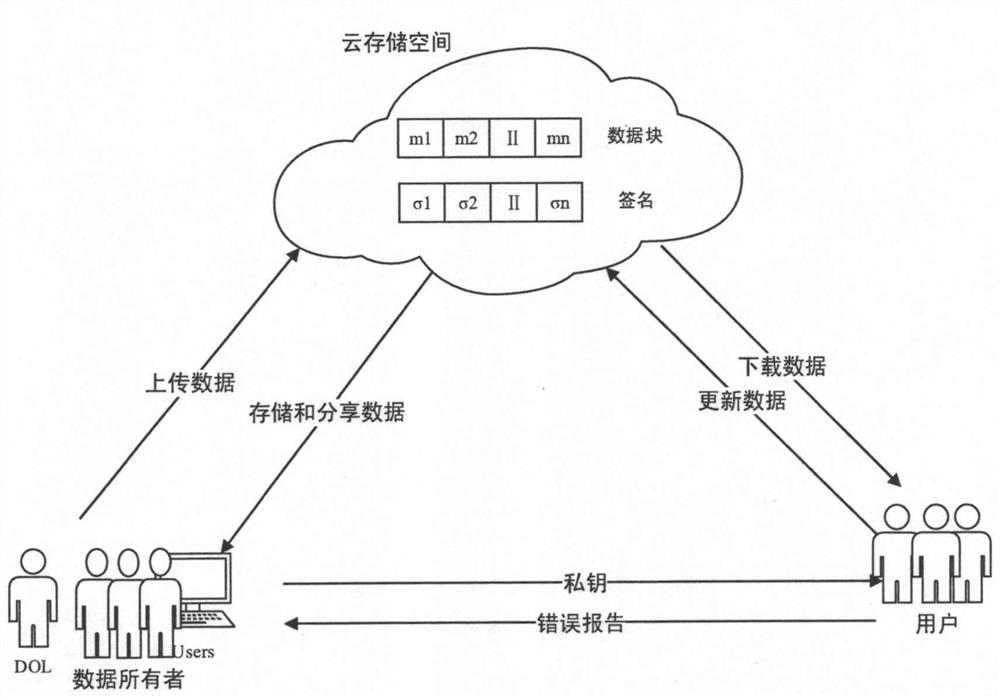
Big-data ownership determination method, electronic device, storage medium and system
InactiveCN109003076ASolve untrustworthyAvoid savingPayment protocolsData sourceFinancial transaction
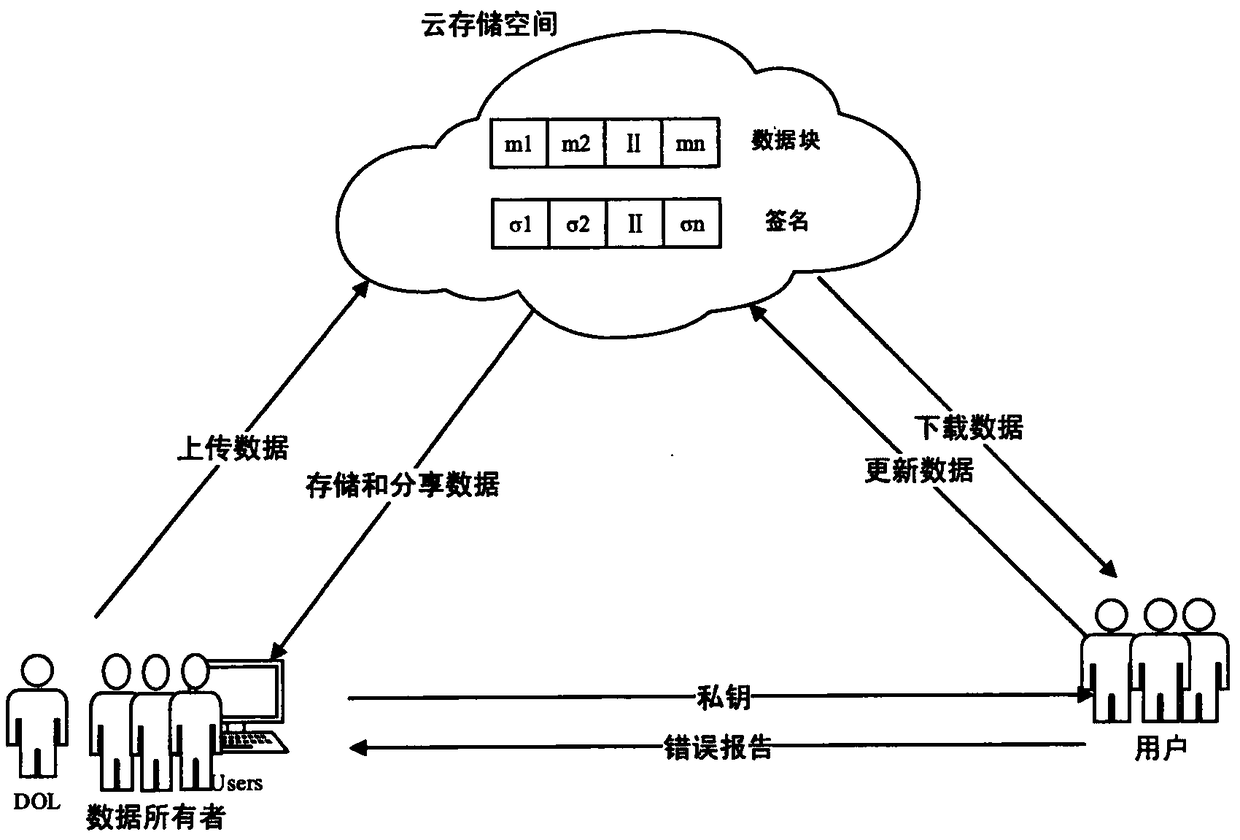
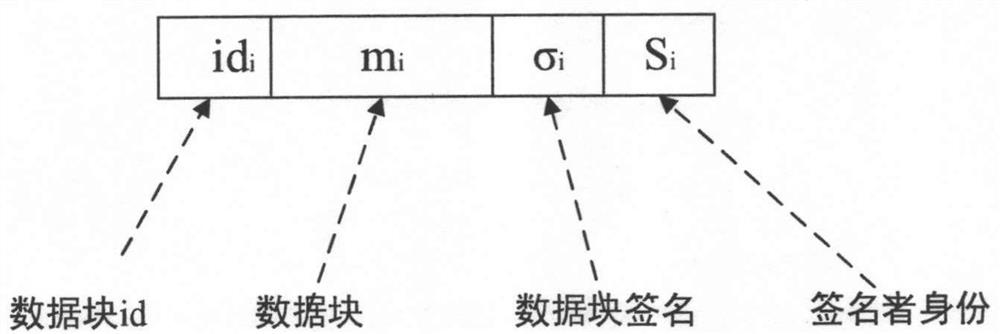
A big-data ownership determination method includes: dividing the big data for ownership determination into data blocks by a data source provider, calculating an authenticator of the data blocks, and signing the identifier of the big data for ownership determination; sending the data blocks, the data block authenticator and the big data identifier signature to an audit center by a data source provider; verifying the correctness of the signature of the big data identifier through a public key, recovering the identifier of the big data for ownership determination, and sending the evidence challenge request to the data source supplier by the audit center; verifying the evidence of the data source provider through bilinear pairing by the audit center, and generating a watermark by a watermark center and embedding the watermark into the data blocks; generating transactions and sending them to data source provider by the audit center and the watermark center; signing the transaction by the data source provider and sending the signed transaction to the block chain ownership registration commercial network to register the ownership information. The invention also relates to a device, a medium and a big-data ownership determination system. The invention guarantees the fairness, integrity and non-deception of the right determination.
Owner:ZHEJIANG JIESHANG ARTIFICIAL INTELLIGENCE RES & DEV CO LTD
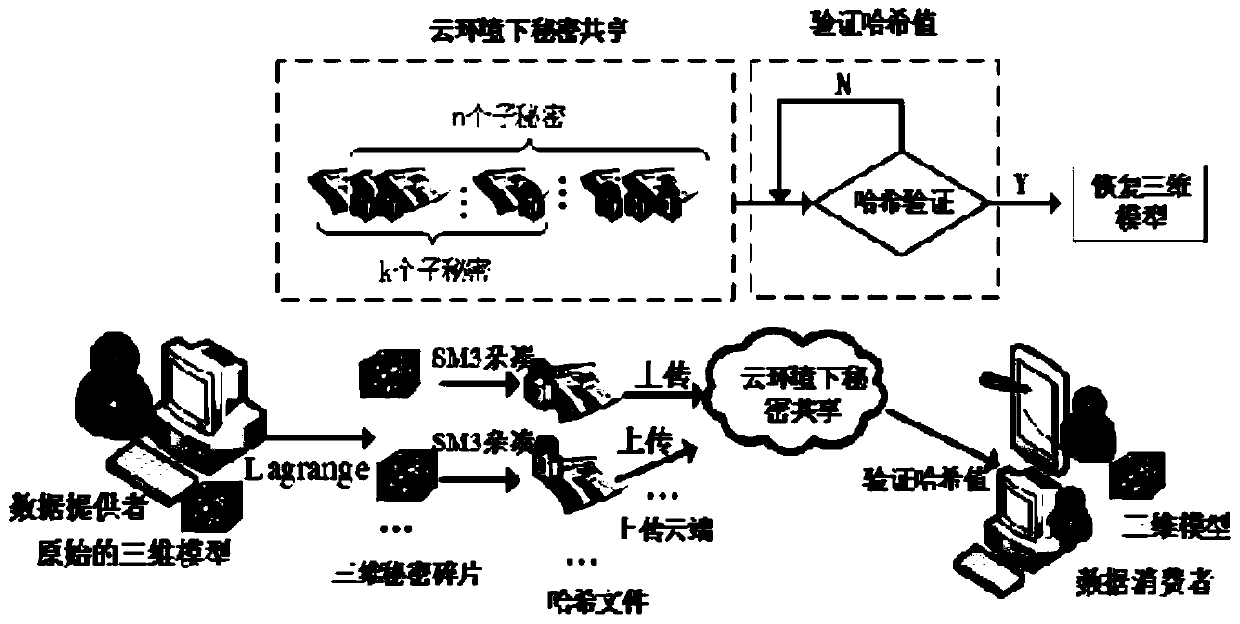
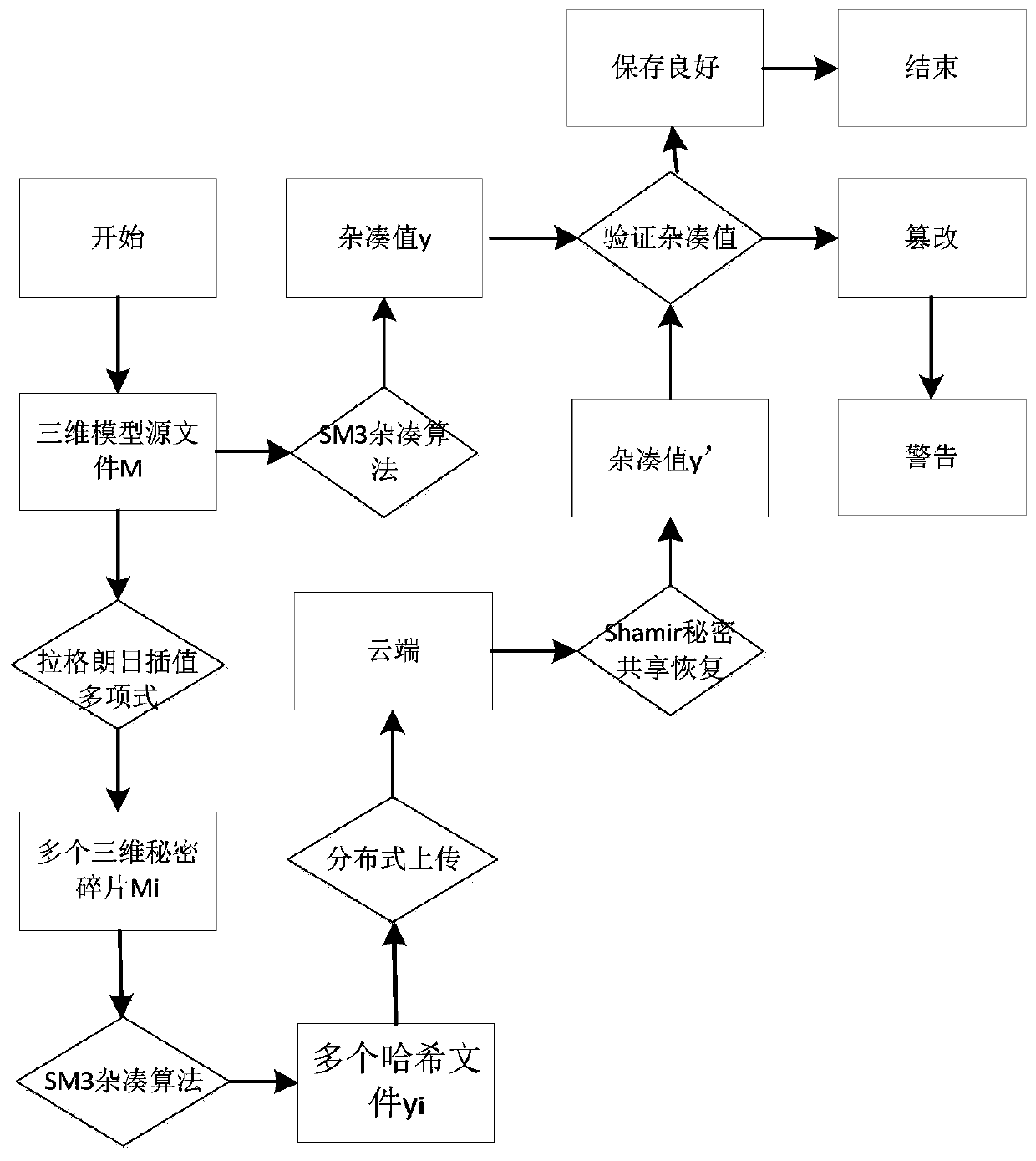
Authentication method of three-dimensional model file based on secret sharing in cloud environment
ActiveCN110610105AEnsure consistencyGuaranteed accuracyDigital data protectionThree dimensional modelEncryption
The invention provides an authentication method for a three-dimensional model file based on secret sharing in a cloud environment, which comprises the following steps of constructing a secret polynomial by adopting a Lagrange interpolation polynomial, generating the secret fragments from a source file, and transmitting and storing the secret fragments in a plurality of secret participants in a distributed manner; taking the source file and the secret fragments as the original structure carriers, respectively generating the digital abstracts from the secret fragments of the source file by utilizing an SM3 hash algorithm, and uploading the digital abstracts generated by the secret fragments to a cloud in a distributed manner; and recovering the digital digest of the three-dimensional model file based on a (k, n) threshold secret sharing method of Shamir, and performing consistency verification on the digital digest of the three-dimensional model file before encryption and after recovery.The invisibility, robustness and analysis resistance of the method are improved, and the fraudulent behaviors during the secret sharing process are effectively prevented. The method has the good performance at the aspect of protecting the integrity of the file, and particularly has the obvious advantages at the aspect of efficiency.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
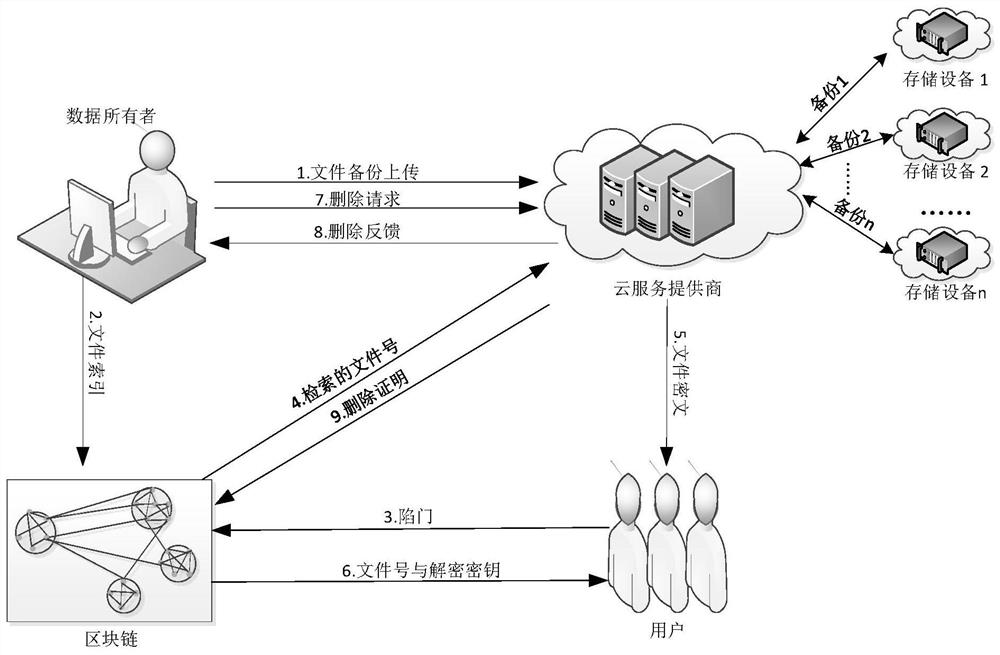
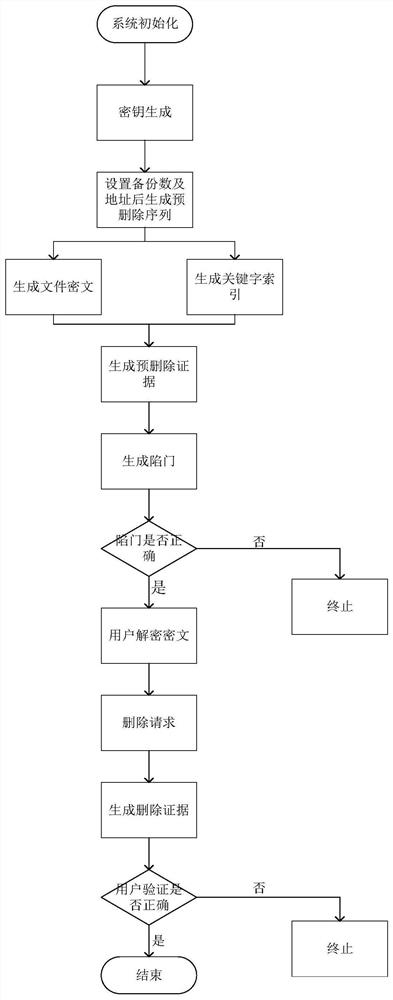
Multi-backup secure deletion method and system based on blockchain
InactiveCN112532650ASolve untrustworthyAchieving Accountability TraceabilityFinanceEncryption apparatus with shift registers/memoriesCiphertextEngineering
The invention discloses a multi-backup secure deletion method and system based on a blockchain, and the method comprises the following steps: setting a backup number and a corresponding backup addressthrough a cloud server after the initialization of the system and the generation of a secret key, transmitting the backup number and the corresponding backup address to a data owner, and generating apre-deletion sequence; encrypting a file by using different keys to generate a plurality of ciphertext backups, and generating an index according to keywords in the file; generating, by the data owner, preparatory integrity and delete evidences; in a ciphertext query stage, calculating, by a user, a trap door and uploading the trap door to a smart contract, and calculating, by the smart contract,a corresponding decryption key and querying a file number; sending, by the cloud server, a ciphertext backup to the user according to the file number, and decrypting, by the user, the ciphertext by using a decryption key; in a deleting stage, sending a deleting request to a cloud server, and deleting, by the cloud server, all backups of the corresponding file according to the request, generatingdeleting evidences, sending the evidences to the data owner and storing the evidences into the blockchain; and verifying, by the data owner, whether the cloud server deletes the evidences according tothe received evidences, and tracking the corresponding responsibility of the cloud server and the user according to the evidences of the evidence chain. According to the method, the requirements of cloud data sharing and safe deletion can be well met, and searchable encryption is provided for valid users.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
User-level code and data security and credibility protection method and device based on TrustZone
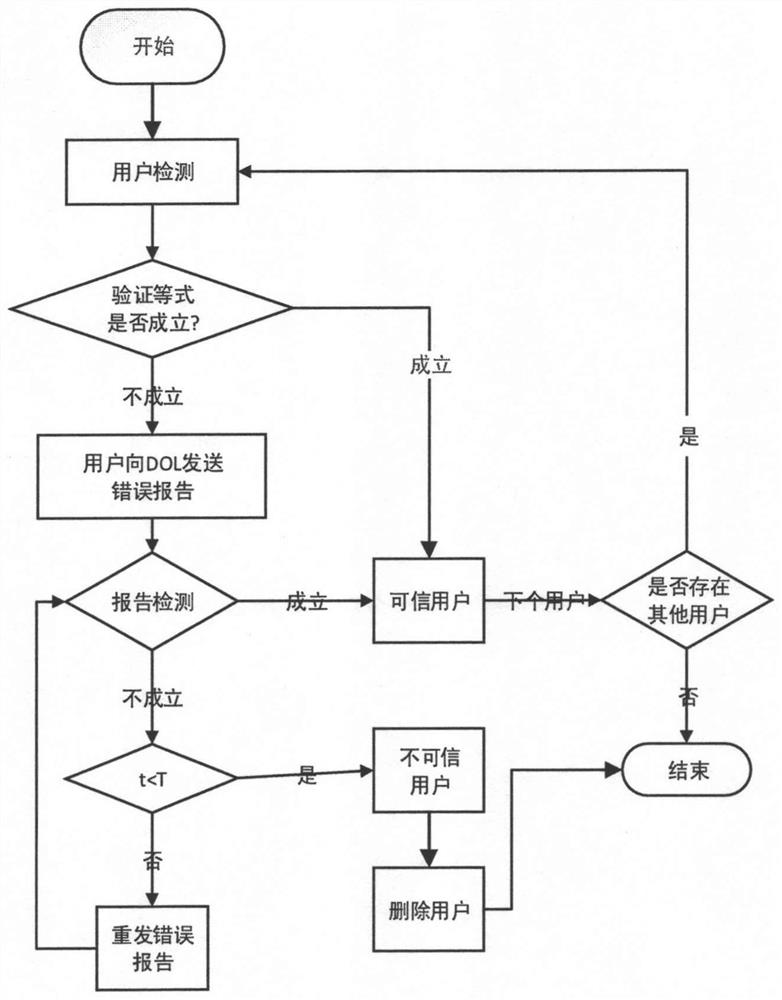
PendingCN112818327ALower the source of trustSolve untrustworthyDigital data authenticationPlatform integrity maintainanceSafe storageData security
The invention discloses a user-level code and data security and credibility protection method and device based on TrustZone. A key code is stored in a protected memory area through encryption, so that a user can load and access the key code and data belonging to the user, and other programs including privileged software cannot access the key code of the user. Meanwhile, mutual calling of the non-safe-state user and the safe-state user code is achieved through TrustZone, the non-safe-state user calls the safe-state user code to achieve safe operation such as safe storage and encryption, the safe-state user calls the non-safe-state user code to complete non-safe operation such as interruption and system calling, all the operations are distinguished, and the problems that privileged software such as an operating system is untrusted, and non-security codes threaten the security state are solved.
Owner:NAT UNIV OF DEFENSE TECH
Internet of vehicles node trust evaluation method based on block chain and system
ActiveCN112929845AImprove securityReduce computational overheadParticular environment based servicesVehicle wireless communication serviceComputer networkThe Internet
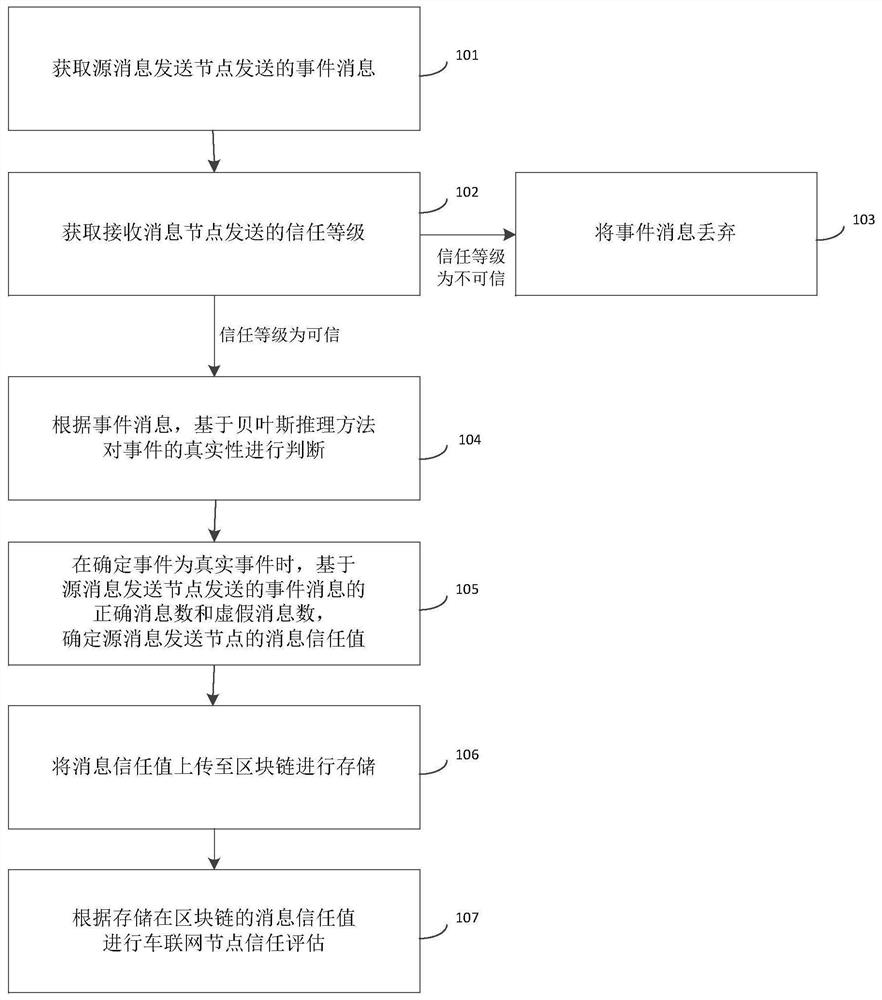
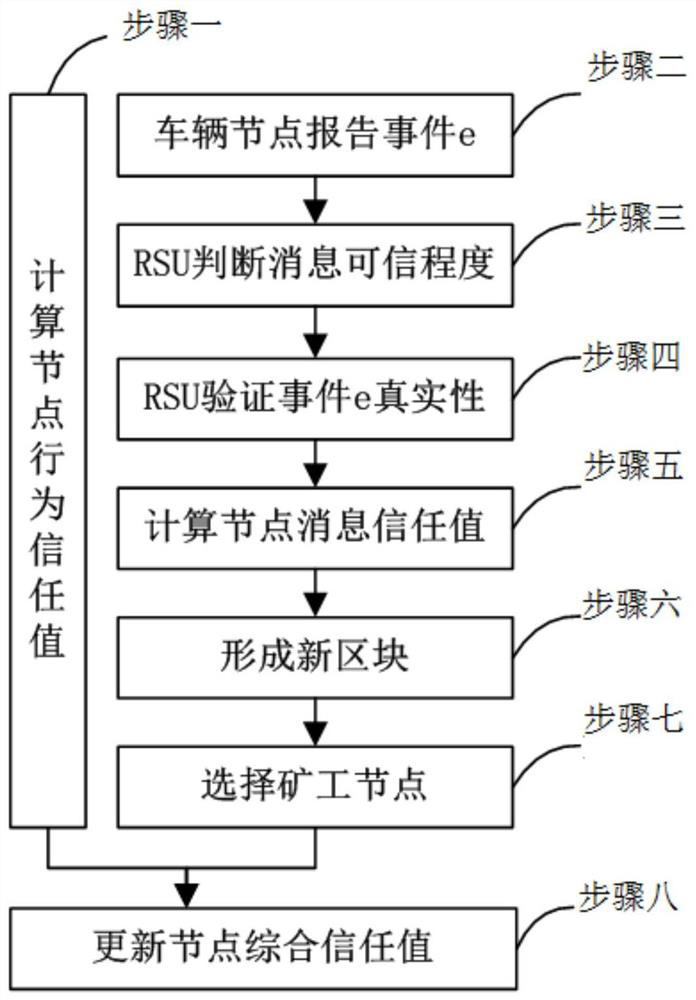
The invention discloses an Internet of Vehicles node trust evaluation method based on a block chain and a system thereof. The method comprises the following steps: acquiring an event message sent by a source message sending node; judging the authenticity of the event based on a Bayesian reasoning method according to the event message; when it is determined that the event is a real event, determining a message trust value of the source message sending node based on the correct message number and the false message number of the event messages sent by the source message sending node; uploading the message trust value to a block chain for storage; and performing Internet of Vehicles node trust evaluation according to the message trust value stored in the block chain. By adopting the method and system provided by the invention, the message trust value of the vehicle node is stored in the block chain, so that trust evaluation is carried out on the Internet of Vehicles node, and the security of the Internet of Vehicles can be improved.
Owner:LANZHOU UNIVERSITY OF TECHNOLOGY
Block chain-based road-vehicle node trusted network construction and consensus method
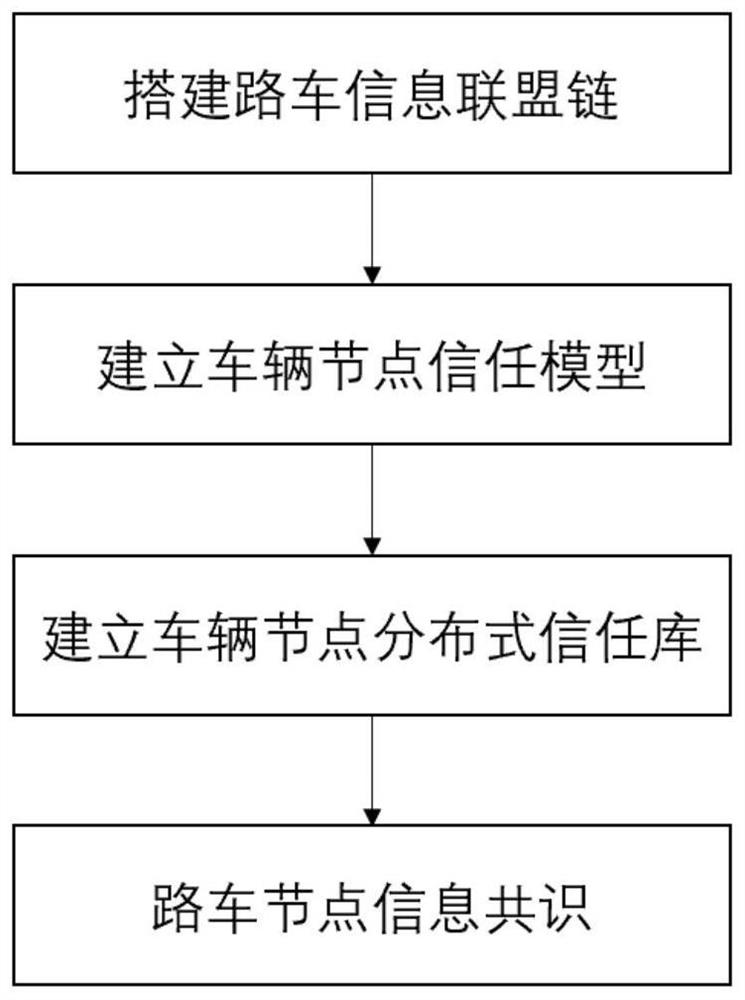
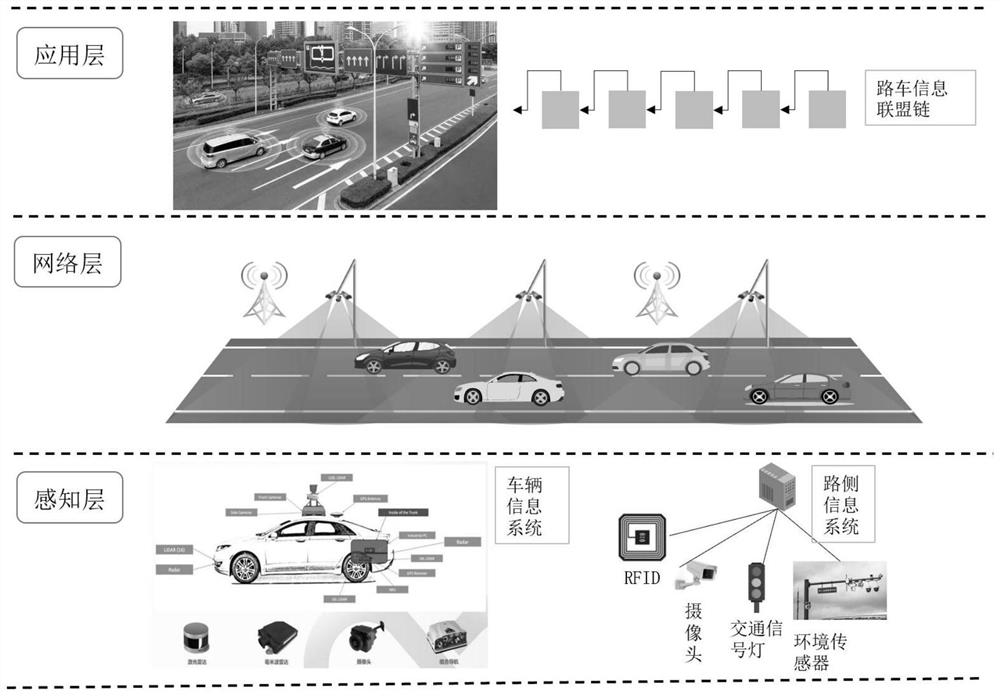
PendingCN114125775AImprove vehicle autonomySolve untrustworthyParticular environment based servicesDatabase distribution/replicationComputer networkNetwork construction
The invention discloses a block chain-based road-vehicle node trusted network construction and consensus method. According to the scheme of the method, the autonomous operation capacity of the vehicle in the road-vehicle fusion environment is improved through the technical means of building a road-vehicle information alliance chain, building a vehicle node trust model, building a vehicle node distributed trust library, consensus of road-vehicle node information and the like. The method can be widely applied to the fields of vehicle-road cooperation and the like.
Owner:HEFEI INNOVATION RES INST BEIHANG UNIV
Electronic educational background certificate verification method based on alliance blockchain platform
ActiveCN113010871AAddress lack of credibilitySolve untrustworthyDigital data protectionDigital data authenticationComputer networkEngineering
The invention discloses an electronic educational certificate verification method based on an alliance blockchain platform. The method comprises a step of issuing an electronic educational certificate based on an alliance blockchain; a step of verifying the electronic education background certificate based on the alliance blockchain; a step of generating and storing a distributed SSL certificate based on an alliance blockchain; and a step of distributed SSL certificate verification based on the alliance blockchain. According to the invention, the distributed storage of the electronic educational certificate is realized by combining the asymmetric encryption and the blockchain technology, so the problems that the credibility of the electronic certificate is insufficient, the certificate is easy to counterfeit and the like can be solved, and the security of the certificate platform is improved; on the other hand, a traditional tree structure CA is replaced with a distributed CA, distributed generation and verification of the SSL certificate are achieved, and the problems that a centralized database is high in risk, a trusted mechanism may be untrusted, and the certificate is illegally revoked can be solved; therefore, the method is high in reliability, good in safety and easy to implement.
Owner:CENT SOUTH UNIV
Privacy protection machine learning reasoning method and system based on secure multi-party computing
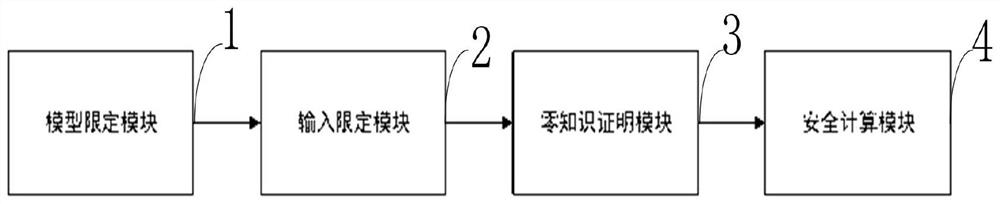
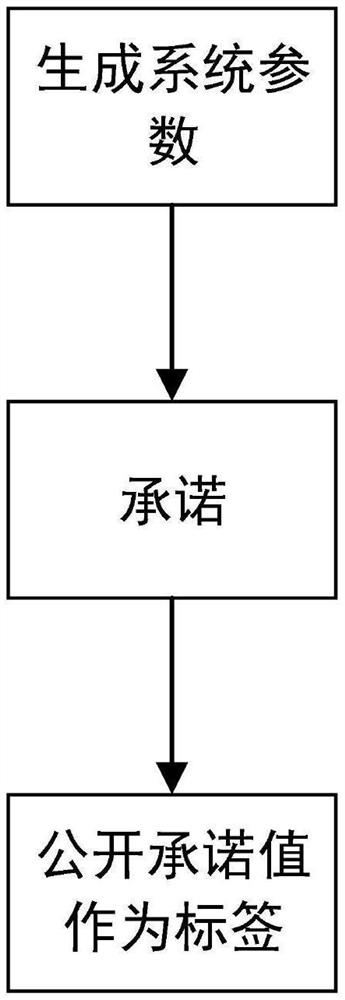
PendingCN114398662ASolve untrustworthyEnsure safetyDigital data protectionMachine learningPrivacy protectionComputation process
The invention belongs to the field of data security and the technical field of cryptography application, and discloses a privacy protection machine learning reasoning method and system based on secure multi-party computation.The privacy protection machine learning reasoning method based on secure multi-party computation.The privacy protection machine learning reasoning method based on secure multi-party computationcomprises the steps that a service provider commits a machine learning model provided by the service provider; generating a label to ensure one-to-one binding of the label and the model; the model is limited by using the label to ensure that the model is not changed after the user selects the label; before a user starts machine learning reasoning, verifying whether the selected label is changed or not by using zero-knowledge proof; and finally, the security of the calculation process is ensured by using a security calculation framework. According to the method, the characteristics that the commitment cannot be changed and zero knowledge proves zero knowledge are fully utilized, no trusted third party participates in the whole service process, that is, no third party masters the data of both parties at the same time, and the problem that the third party is not trusted is fundamentally solved.
Owner:XIDIAN UNIV
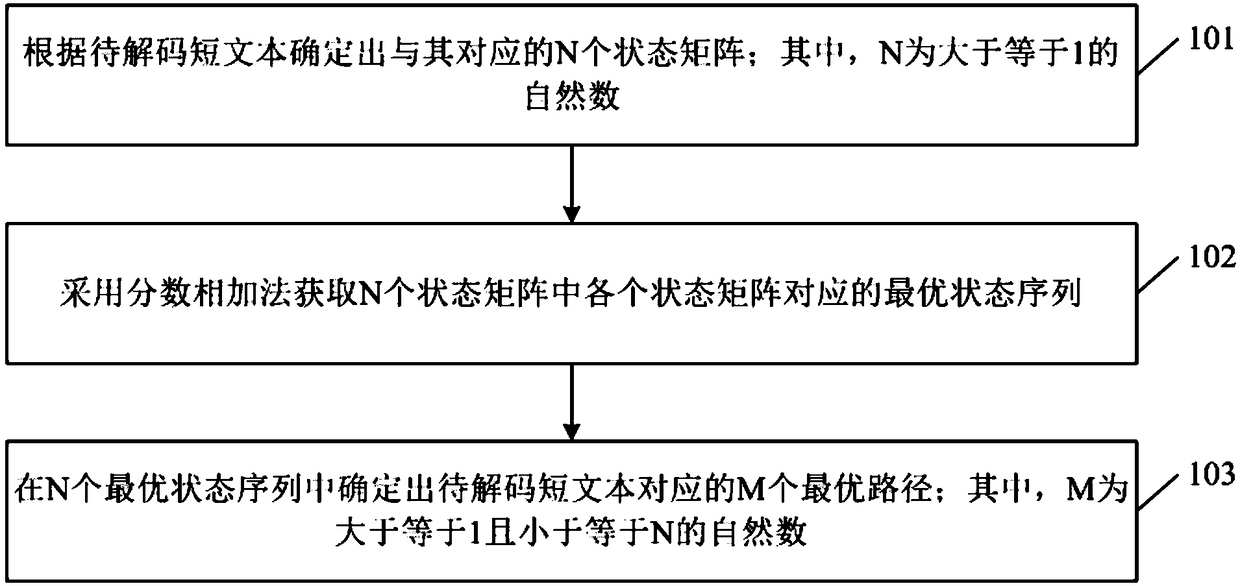
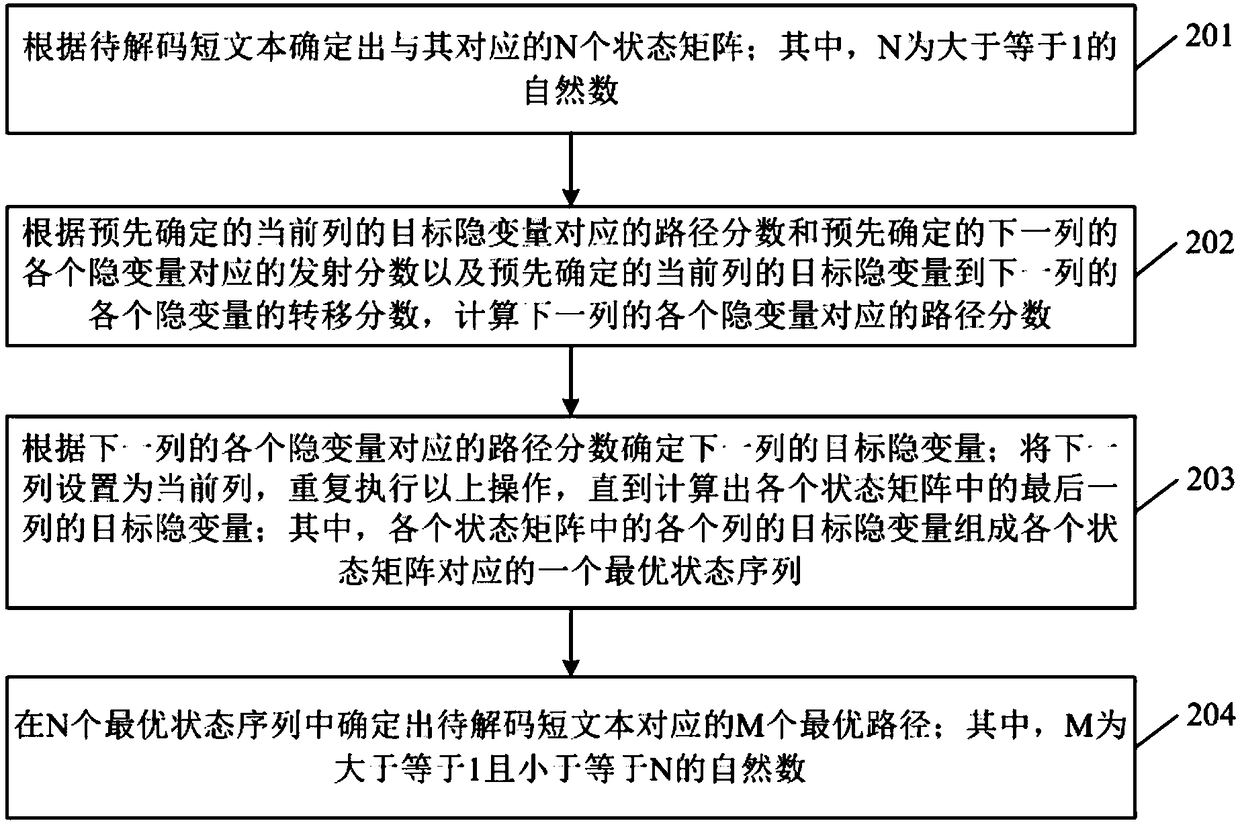
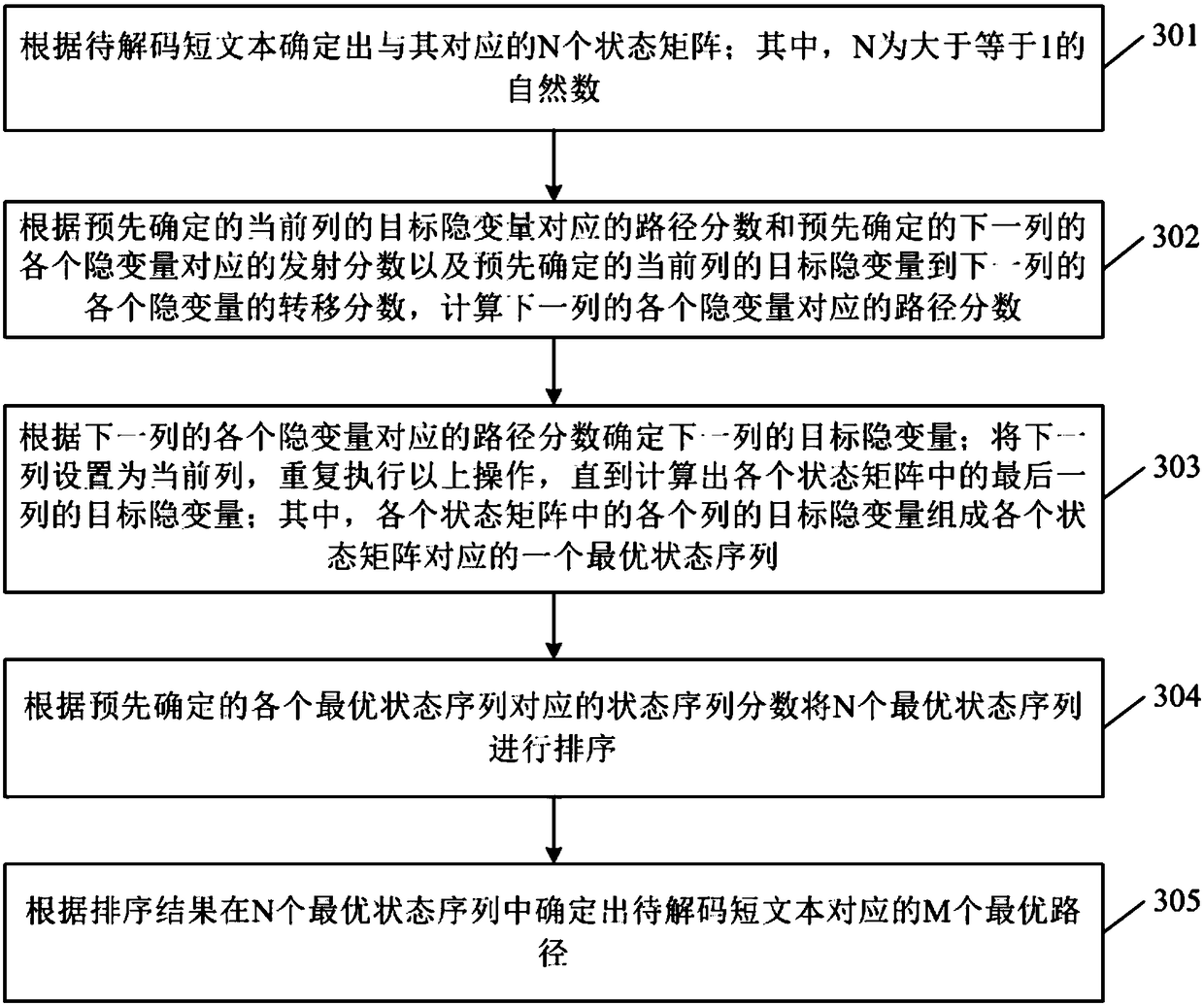
Path decoding method and device, computer device, and storage medium
ActiveCN109388404AImprove accuracySolve untrustworthyCode compilationDecoding methodsComputer science
The invention discloses a path decoding method and device, a computer device and a storage medium. The method comprises the following steps of: determining N state matrices corresponding to the shorttext to be decoded according to the short text to be decoded, wherein N is a natural number greater than or equal to 1; obtaining an optimal state sequence corresponding to each state matrix of the Nstate matrices by using a fractional addition method; determining M optimal paths corresponding to the short text to be decoded among N optimal state sequences, wherein M is a natural number greater than or equal to 1 and less than or equal to N. The method can improve the accuracy of obtaining the optimal path through HMM model, and solve the problem that the path score of HMM model is too smallto be trusted when it is applied to text path decoding.
Owner:北京如布科技有限公司
Cloud data sharing method based on block chain to realize anti-data tampering and user collusion
ActiveCN109145612BEffective traceabilityEnsure safetyDigital data protectionTransmissionComputer networkConfidentiality
Owner:DONGHUA UNIV
Battle data processing method and system based on blockchain distributed consensus algorithm
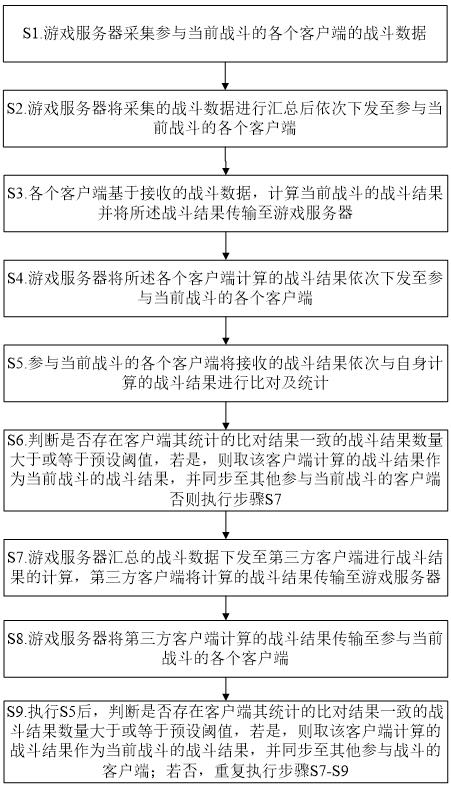
ActiveCN114225381BSolve untrustworthyReduce resource consumptionVideo gamesTransmissionEngineeringData mining
Owner:广州炫动信息科技有限公司
A shared economic accounting method based on blockchain
The invention provides a shared economic accounting method based on a block chain. According to the method, a plurality of participation subjects of the shared economy are respectively provided with anode on a block chain; a plurality of nodes form an alliance chain; A block chain technology is introduced into traditional sharing economy; trust-free of the block chain in a sharing environment isutilized; The method has the advantages that the method is simple and easy to operate, the characteristics of medium removal, non-tampering and traceability are achieved, a trusted, ownership-ascertainable and traceable shared economic system is constructed, high trust among a demander, a supplier, a platform party and a site provider is achieved, then traceable and trusted value evaluation is provided for purchasing and financial means, and the operation efficiency of the shared economy is improved.
Owner:雄安新区智能城市创新联合会
A Quantum Hermetic Auction Method Without Auctioneer
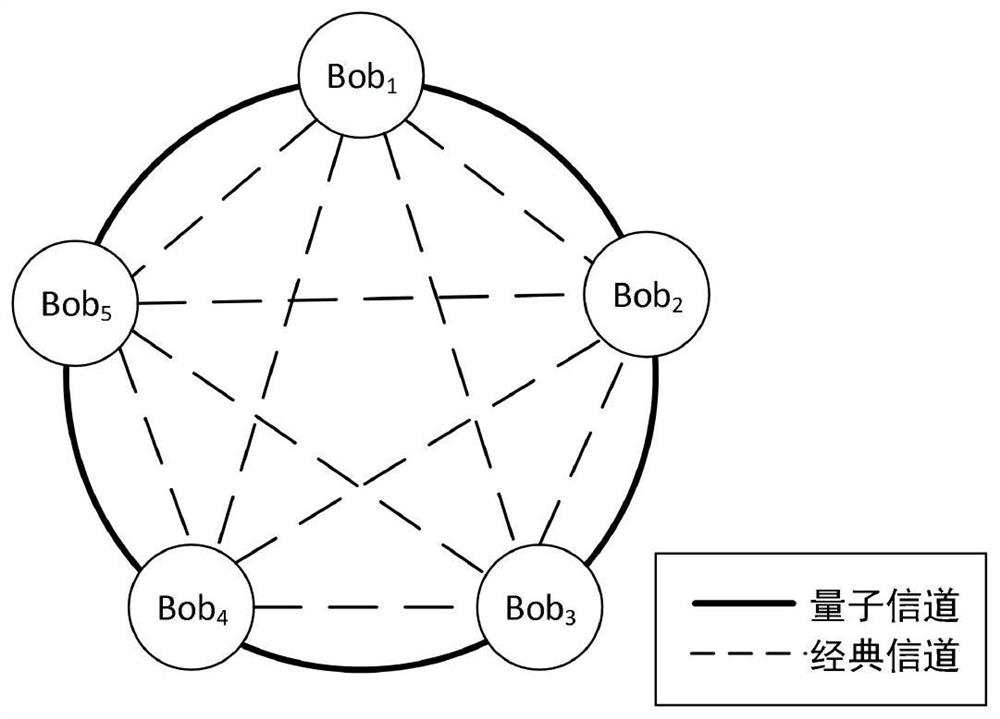
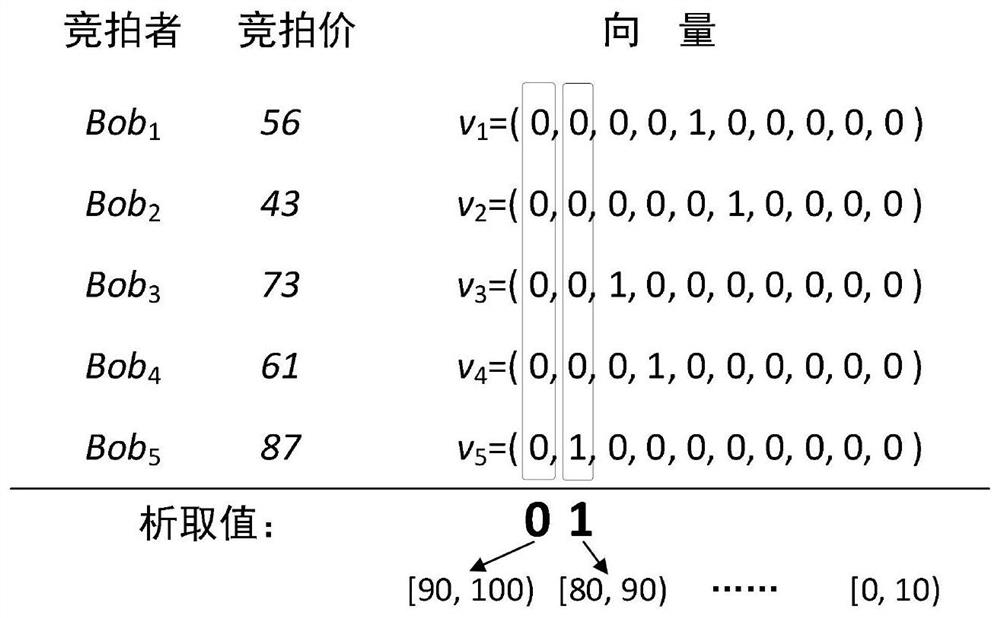
ActiveCN113660084BSolve untrustworthyGuaranteed correctnessKey distribution for secure communicationCommerceAlgorithmOperations research
The invention discloses a quantum sealed auction method without an auctioneer. No auctioneer is required. All bidders promise their bidding prices in advance, and then cooperate to find the highest bid by means of a quantum-safe multi-party extraction method. The sub-range of the price is located, and then the highest bidding price and its bidder are found out, and finally all bidders are verified, thus ensuring the correctness, fairness and privacy of the whole process. The invention can effectively solve security problems such as incomplete trustworthiness of auctioneers and leakage of bidding prices of unsuccessful bidders in the existing quantum sealed auction process, while using as few quantum resources as possible that are easy to prepare, while ensuring security Has strong practicability.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
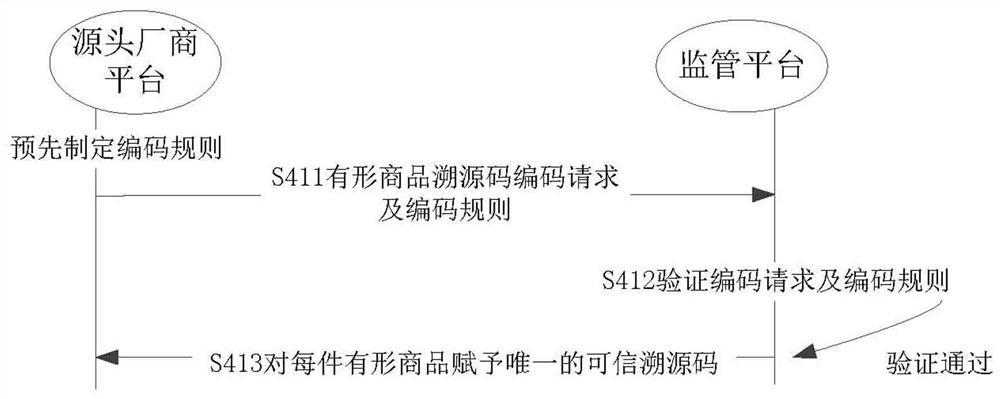
A credible traceability method and system for tangible commodities
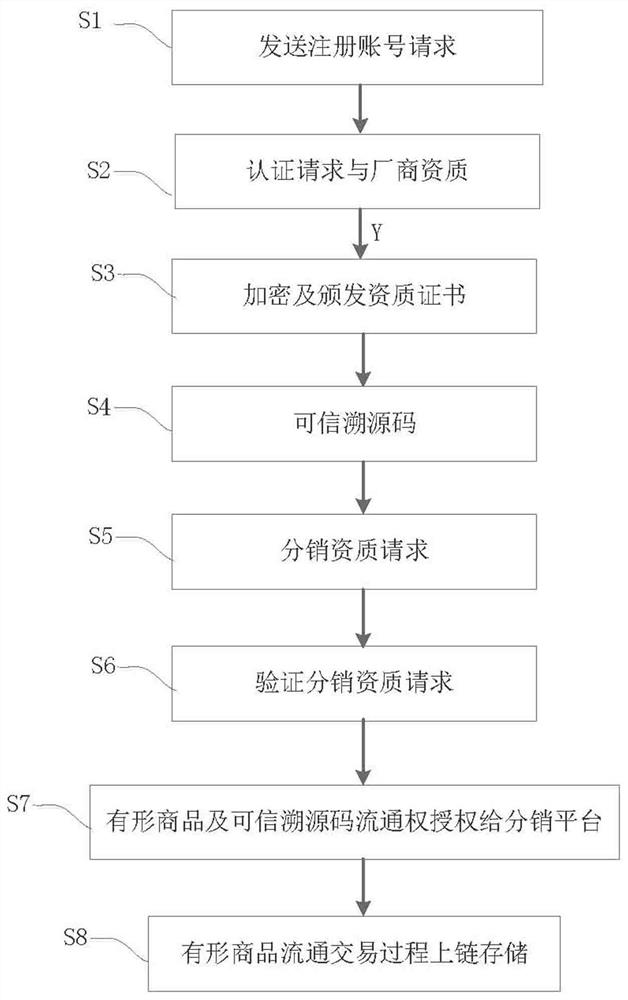
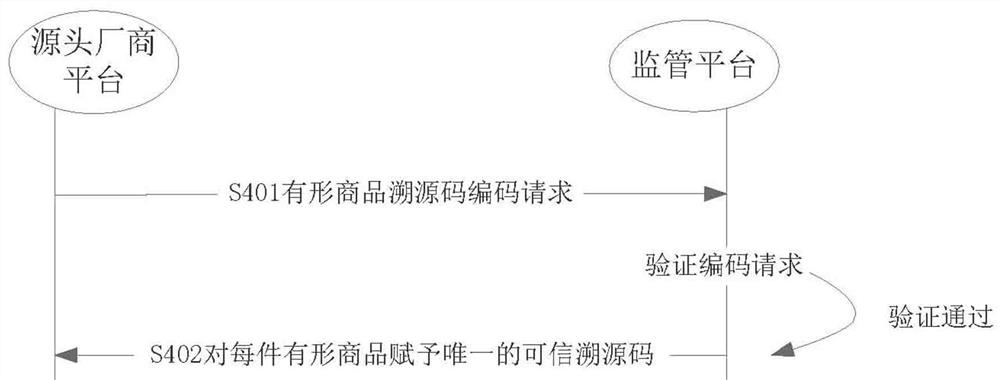
ActiveCN112270557BSolve untrustworthyDatabase distribution/replicationDigital data protectionProduct traceabilityAuthenticated encryption
This application discloses a credible tangible commodity traceability method and system, including: sending a registration account request of the source manufacturer platform to a supervision platform; authenticating the registration account request and manufacturer qualification; if the authentication is passed, encrypting the qualification certificate and identifying the source The manufacturer platform issues the qualification certificate; generates the trusted traceability source code corresponding to each tangible product; sends the distribution qualification request to the source manufacturer platform and the supervision platform in turn; verifies the distribution qualification request; ; Store each tangible commodity on the chain during the circulation and transaction process of the source manufacturer platform and the distribution platform. The supervision platform in this scheme is composed of multiple blockchain nodes that are pre-endowed with various supervision functions. During the commodity transaction process, all the processes of commodity and traceability source circulation are stored in the supervision platform. Due to its decentralization and non-tampering , forming a source of trustworthy traceability, which solves the problem of untrustworthiness in the process of product traceability.
Owner:AOWEI INFORMATION TECH (JIANGSU) CO LTD
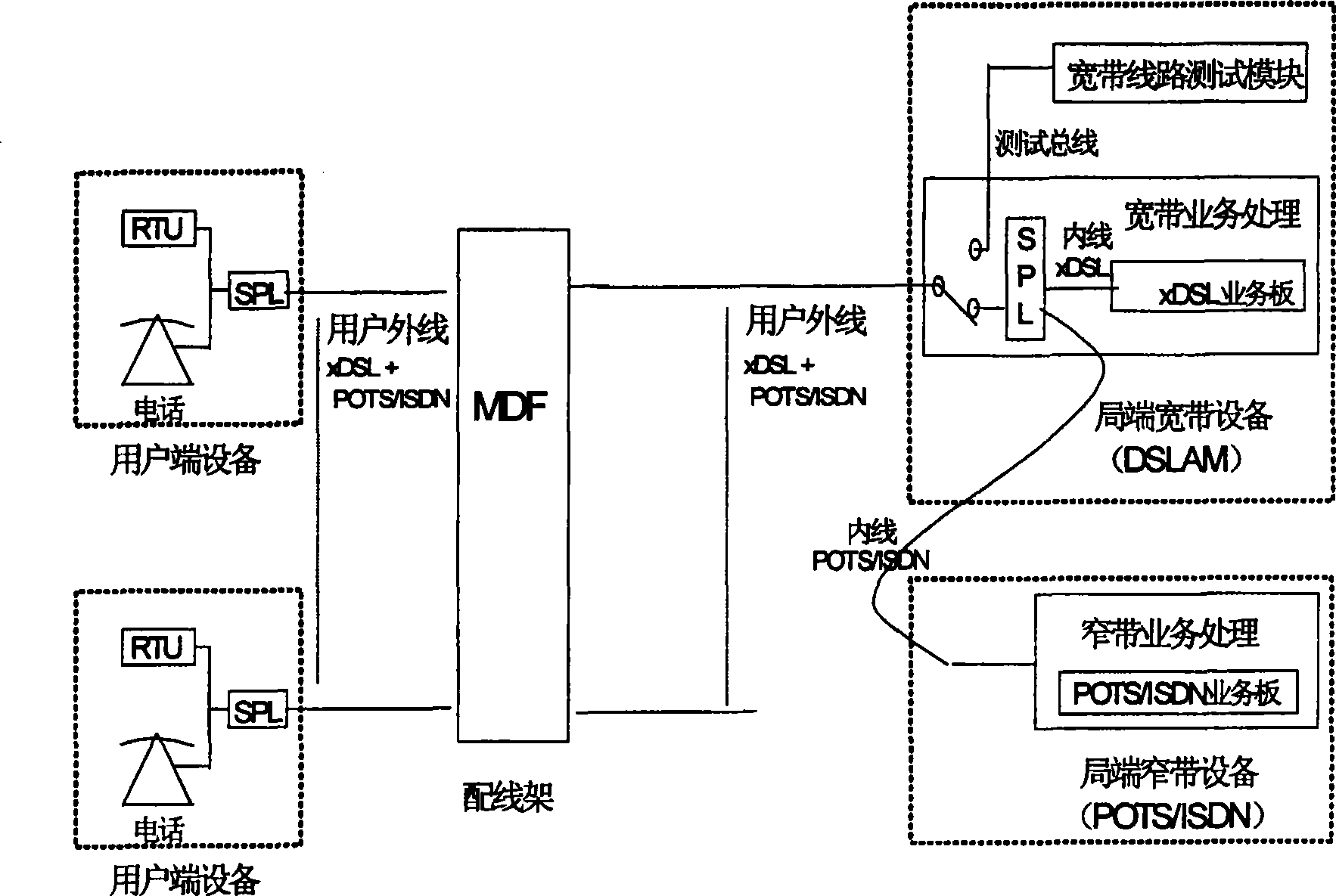
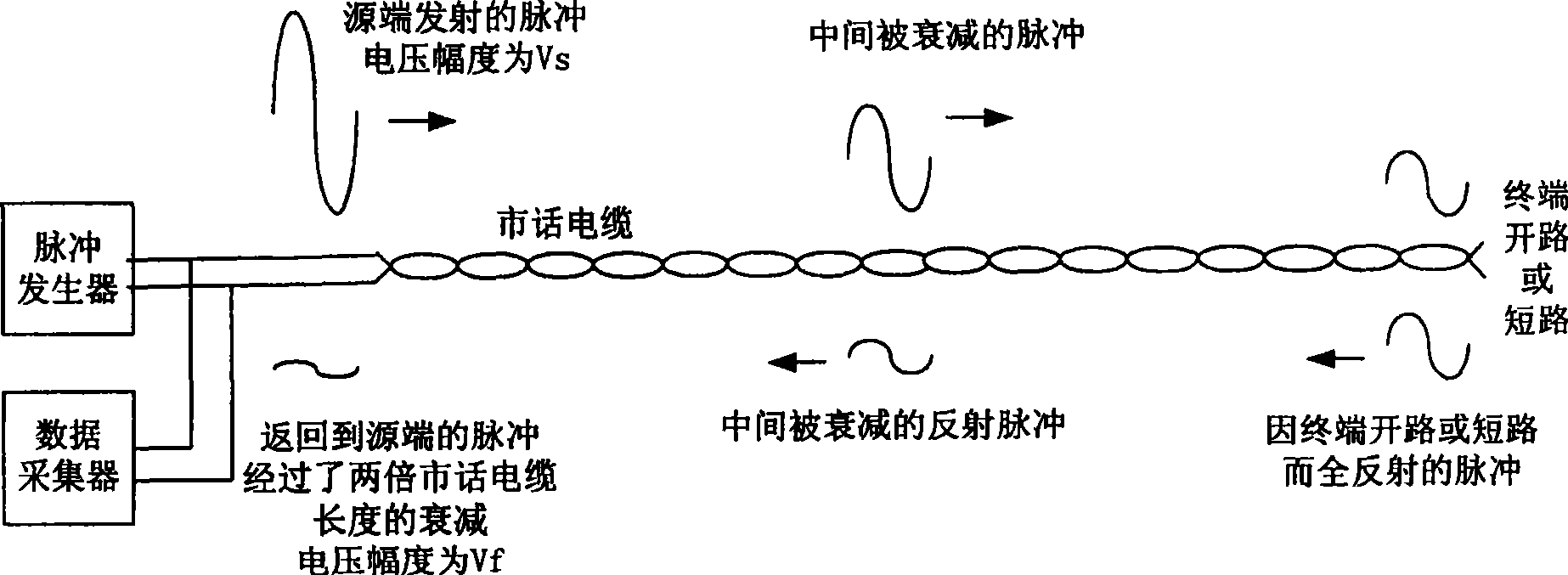
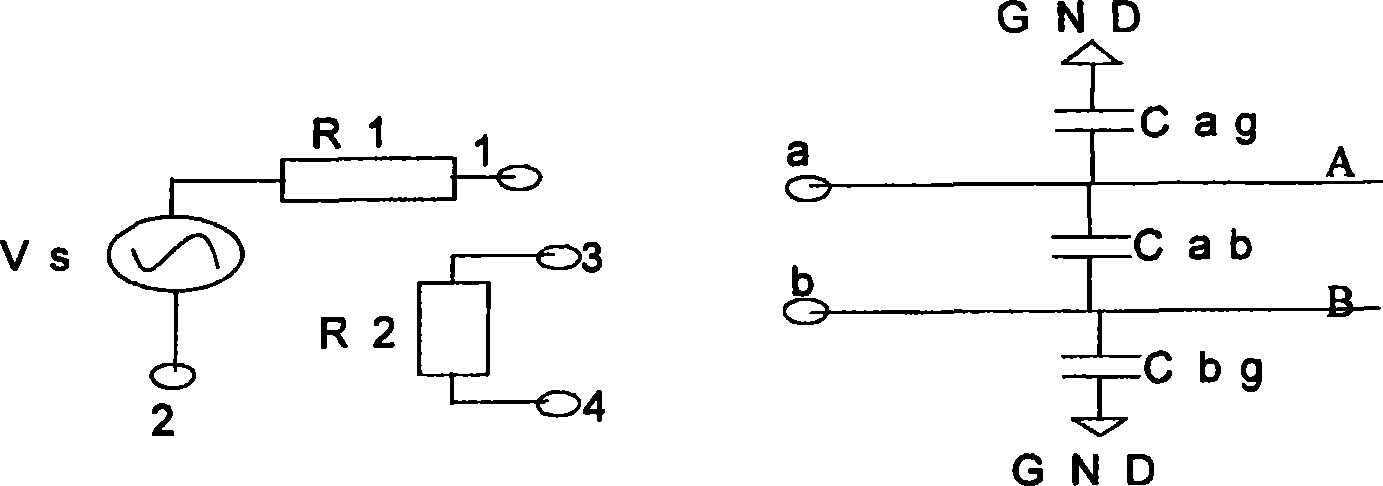
Method for testing local telephone cable frequency response
InactiveCN100499697CSimple methodSolve the problem of unreliable test resultsSupervisory/monitoring/testing arrangementsTime domainMultimeter
The present invention relates to a testing local cable frequency response method. It contains 1, obtaining cable narrowband parameter by digital multimeter, judging whether cable having narrowband fault, if having then reporting fault, otherwise executing step 2; 2, according to testing obtained local cable narrowband parameter judging cable fitting adopting digital multimeter testing or time domain reflection testing to obtain cable frequency response, and according to judging result adopting relevant testing to obtain frequency response. The present invention adopts two test methods combined mode to test local cable frequency response, to solve test result declinational problem due to cable earth capacitance inconsistency.
Owner:HUAWEI TECH CO LTD
System and data processing method for internet voting for absentee elections
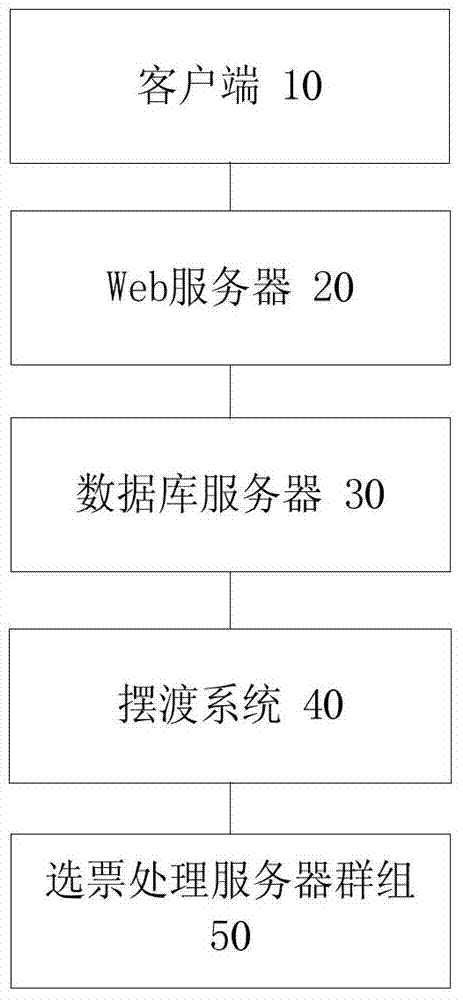
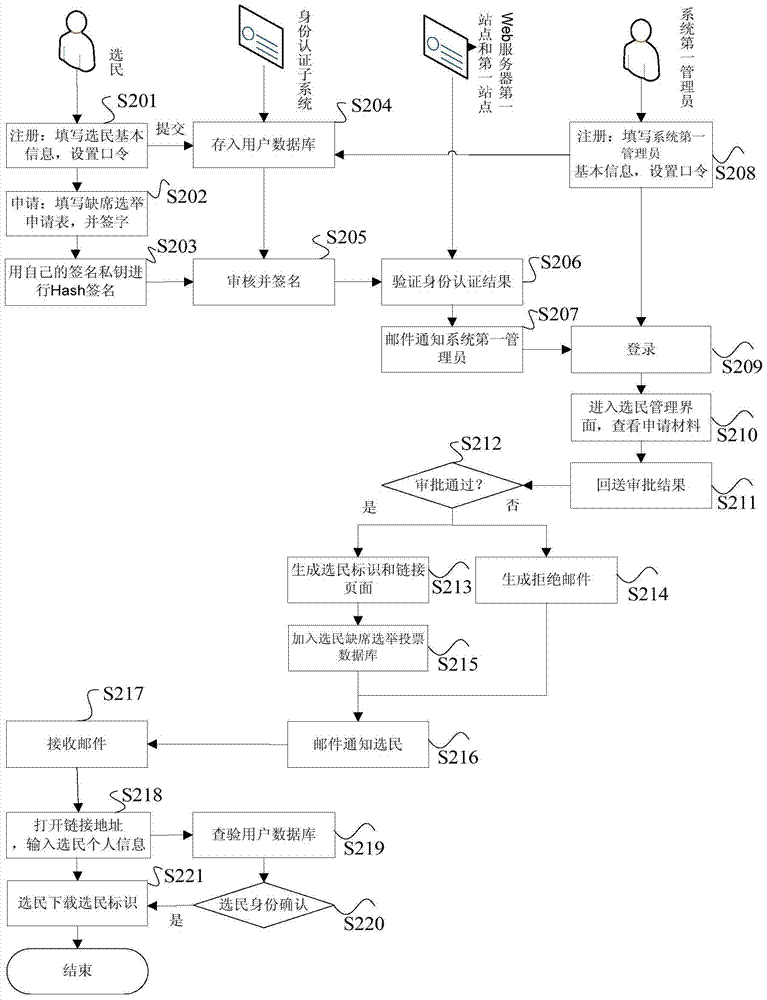
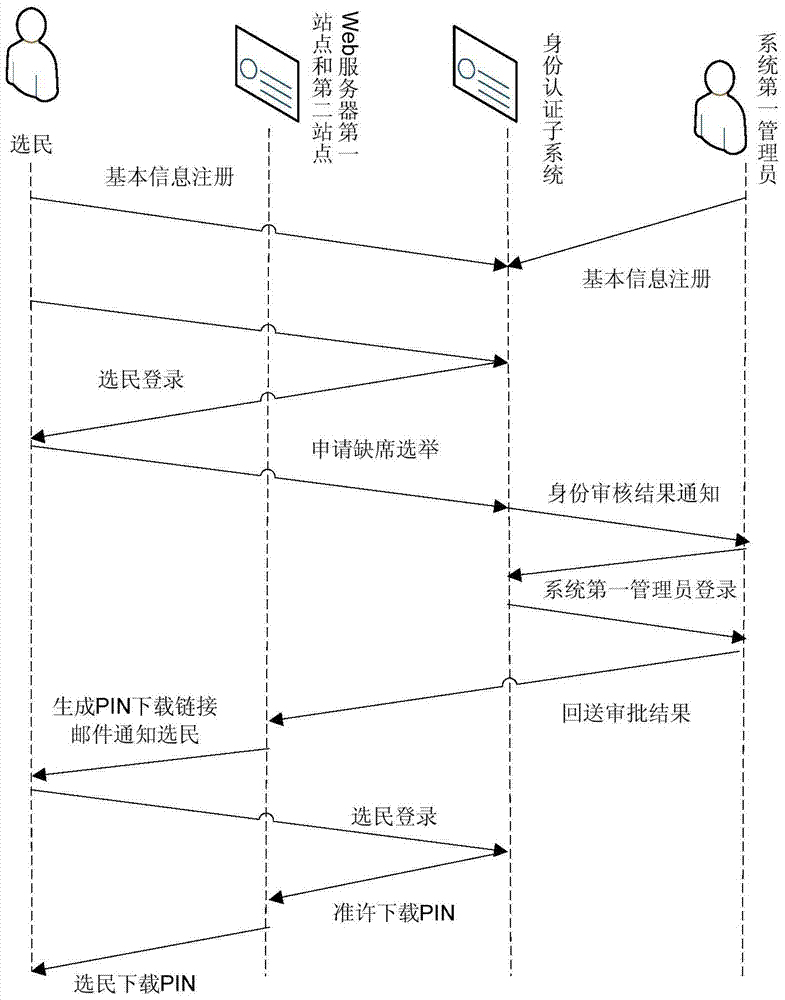
ActiveCN104618378BGuaranteed credibilitySolve untrustworthyVoting apparatusTransmissionWeb serviceDatabase server
Owner:JINHUA HONGZHENG TECH CO LTD
Ballot processing system, method and apparatus for network voting system
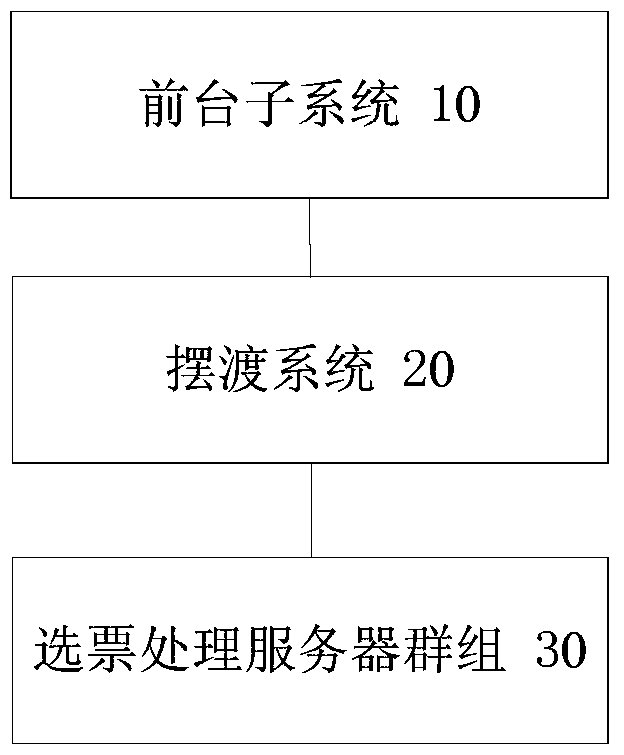
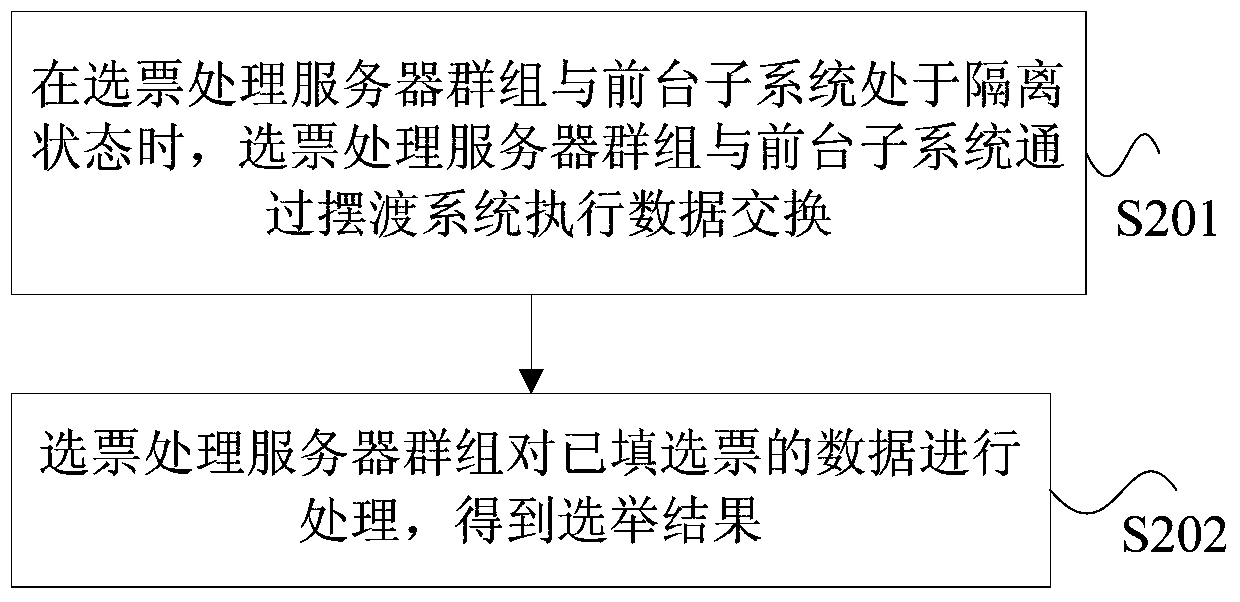
ActiveCN104935565BImprove securityGuaranteed credibilityVoting apparatusTransmissionComputer science
The present invention discloses a vote processing system used for a network voting system, a vote processing method used for the network voting system and a vote processing device used for the network voting system. The system comprises a vote processing server group, a foreground subsystem and a ferry system; the foreground subsystem comprises a citizens voting client, the ferry system is used to receive the externally inputted data of the written votes and send the data of the written votes to the vote processing server group when the vote processing server group and the foreground subsystem are located in an isolation state, and the vote processing server group is used to process the data of the written votes to obtain a voting result, wherein the data of the written votes is the data obtained by writing the blank votes on the citizens voting client. According to the present invention, the voting result unbelievable problem in the prior art caused by the processing method of the written votes in the network voting system is solved, the processing safety of the written votes in the network voting system is improved, and a voting result believable effect is guaranteed.
Owner:ZHEJIANG NORMAL UNIVERSITY
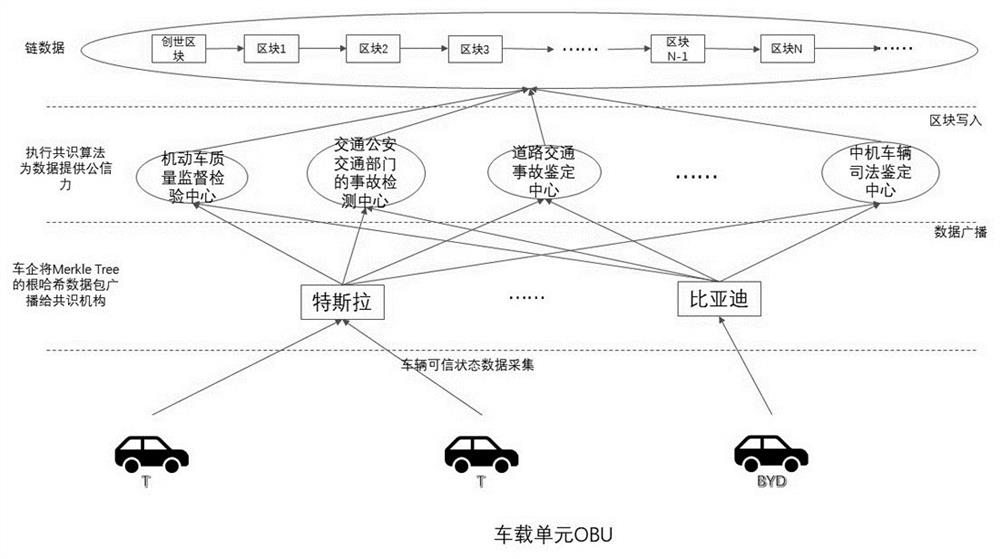
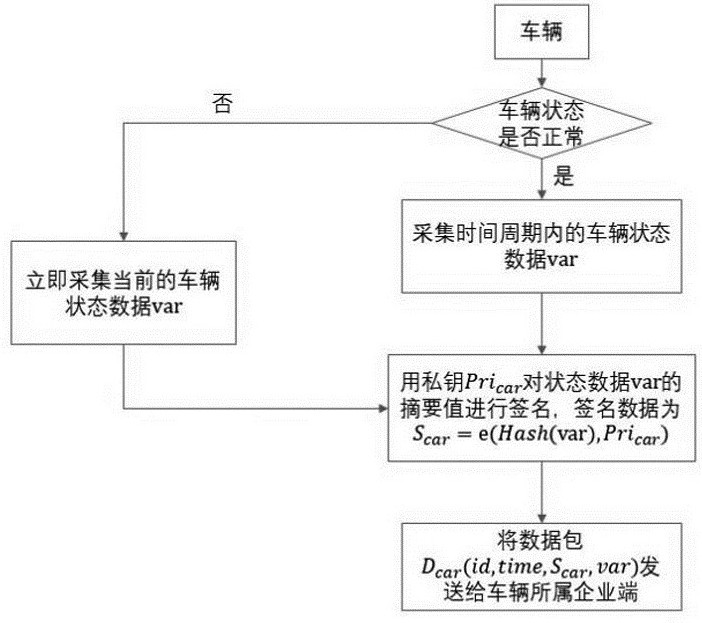
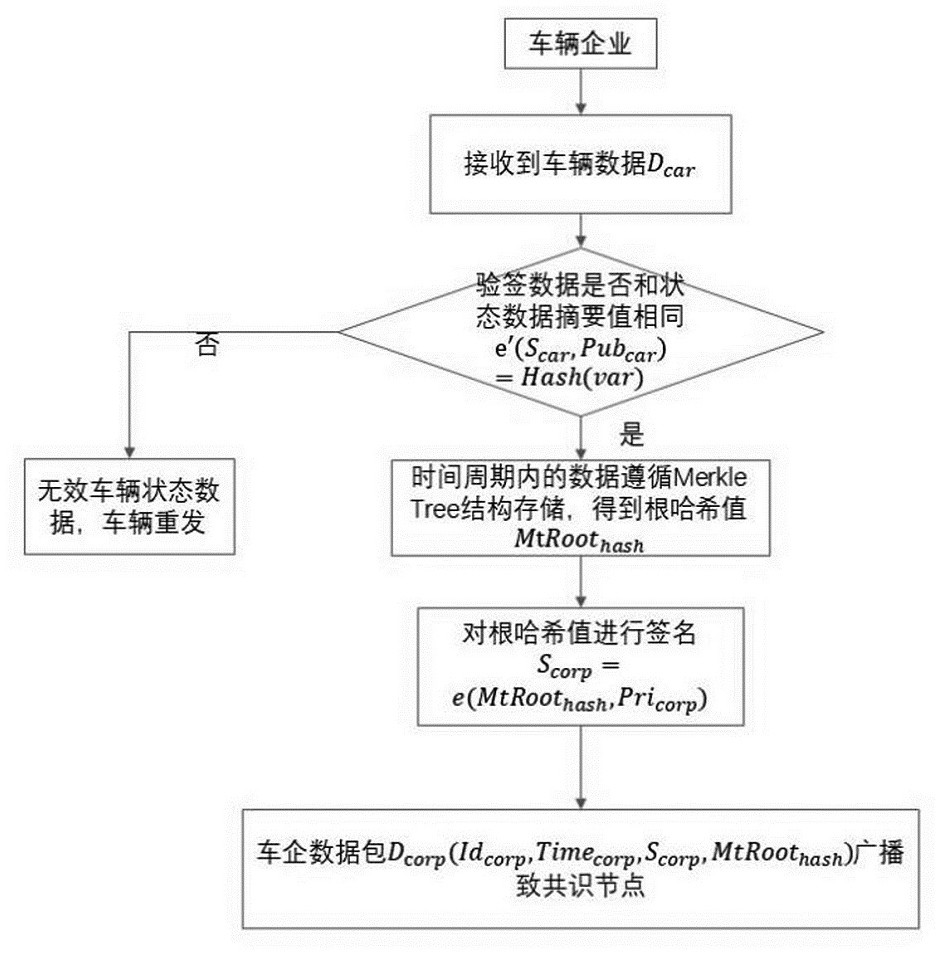
Method for proving credible state data of Internet of Vehicles
ActiveCN114844654AGuaranteed timelinessSolving tamper-evidentUser identity/authority verificationData packEngineering
The invention provides an Internet of Vehicles credible state data proving method, which comprises the steps of collecting vehicle state data, signing the vehicle state data, packaging and sending the vehicle state data to a data processing platform of a vehicle enterprise; the data processing platform verifies whether the vehicle state data meets a preset condition, constructs a Merkle Tree for the data meeting the preset condition, stores all hash operation paths in the Merkle Tree, and broadcasts a data packet containing a Merkle Tree root hash value and signature information to all consensus nodes; writing the block into the block chain by using a consensus algorithm; and querying whether the root hash value is in the Merkle Tree leaf node parameters of the corresponding block according to the abstract value of the root hash value in the block chain, and if so, proving that the data is credible.
Owner:湖南密码工程研究中心有限公司
Method and system for implementing ssh protocol based on post-quantum key exchange
ActiveCN108111301BSolve untrustworthyKey distribution for secure communicationUser identity/authority verificationKey exchangeAttack
The invention belongs to the field of information technology, and in particular relates to a method and a system for realizing the SSH protocol based on post-quantum key exchange. The method includes: the client and the server calculate the public-private key pair respectively; calculate the temporary session public key of the client, and send the client public key and the client temporary session public key to the server; the server authenticates the client; the calculation server Temporary session public key; calculate the server’s temporary session variable and temporary session error correction variable, and the initial seed of the server’s shared key; the server uses the post-quantum algorithm to generate the final server’s shared key for this session; Authentication; the client calculates the client temporary session variable and the initial seed of the client shared key through the server's identity authentication; the client uses the post-quantum algorithm to generate the final client shared key for this session. The method and its system can effectively resist quantum computer attacks and ensure network security.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com