User-level code and data security and credibility protection method and device based on TrustZone
A data security, user-level technology, applied in the direction of digital data authentication, platform integrity maintenance, etc., can solve untrustworthy and other problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
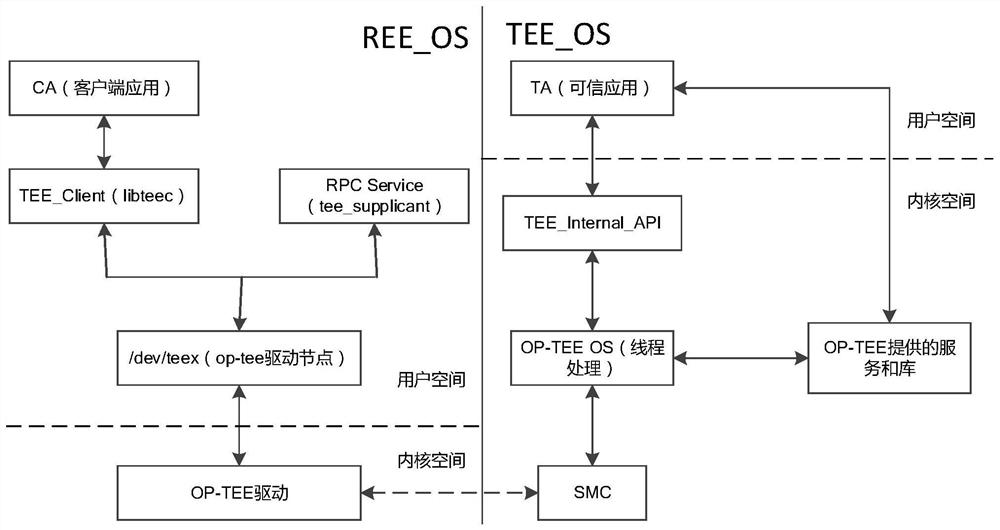
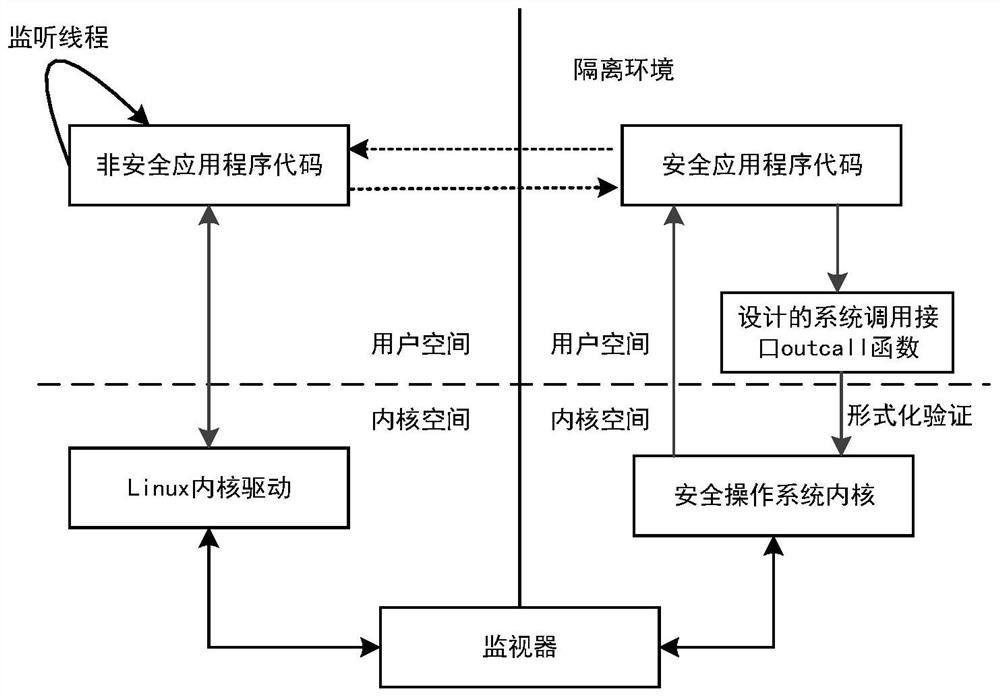
[0040] Such as image 3 and Figure 4 As shown, the user-level code and data security trusted protection method based on TrustZone in this embodiment includes the steps of calling the non-safe application code located in the general-purpose operating system by the secure application code located in the secure operating system:
[0041] A1) The safety application code invokes a dedicated system call interface to initiate a non-safe operation call request to the monitor through the driver program in the safety operating system;
[0042] A2) The monitor utilizes the safety monitoring mode to transfer the non-safety operation call request into the general-purpose operating system of the kernel state;
[0043] A3) The general-purpose operating system in the kernel state loads the target non-safe application code corresponding to the non-safe operation call request, and the target non-safe application code performs the corresponding non-safe operation, and returns the operation res...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com