Method and system for obtaining user position
A user and subsystem technology, applied in the field of communication, can solve the problems of untrustworthiness, reduced IMS service security, and inability to satisfy, and achieve the effect of solving the untrustworthy location information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0030] Figure 4 It shows a flow chart of a method for acquiring a user location according to an embodiment of the present invention, and the method includes the following steps:
[0031] Step S404, when the IMS network element needs the location information of the UE, the IMS network element requests the location information of the UE from the PS network element;
[0032] When the UE registers with the IMS network element, or after the UE registers with the IMS network element, when the UE or the IMS network element initiates an IMS service, the IMS network element needs the location information of the terminal UE;
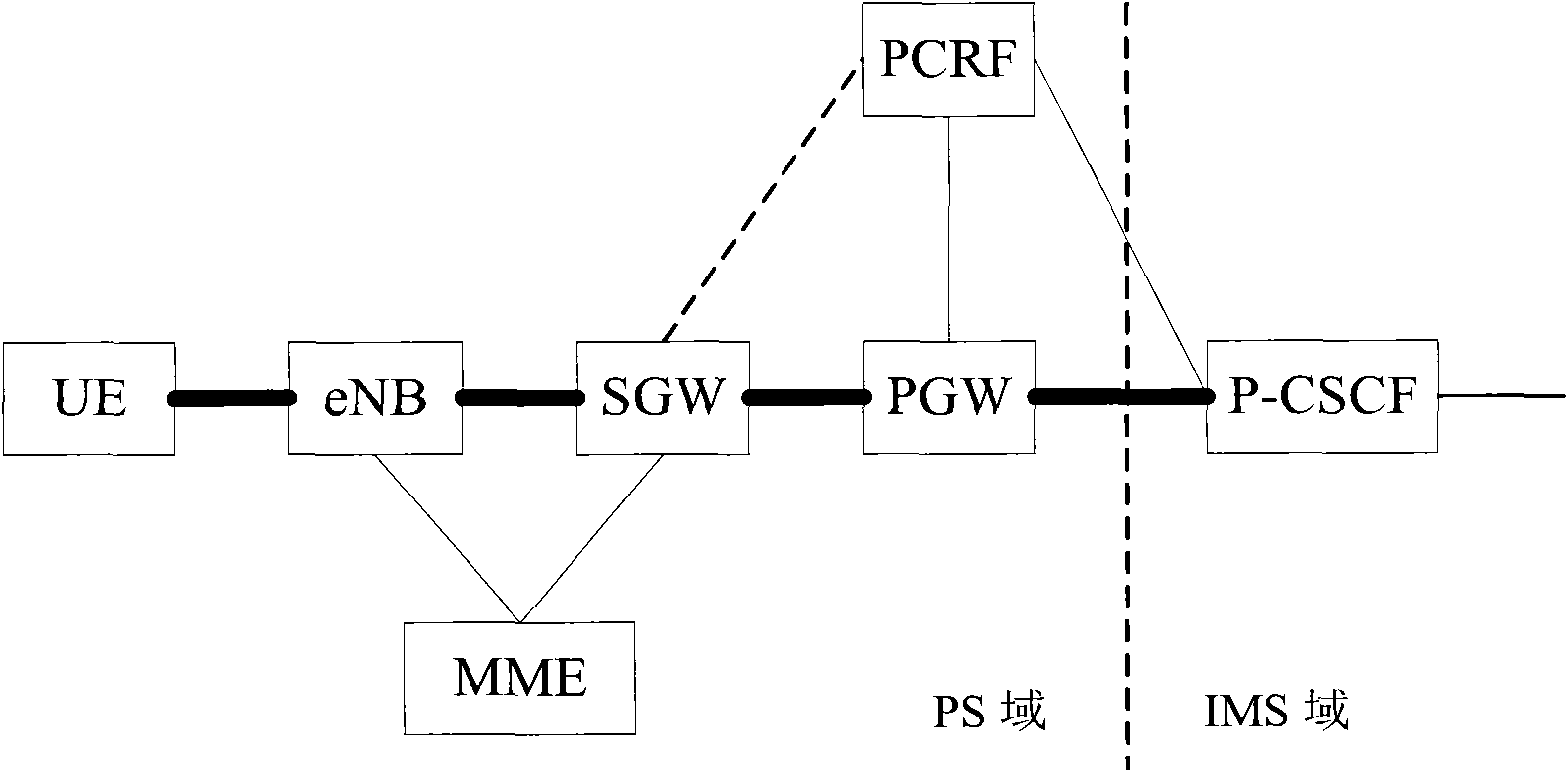
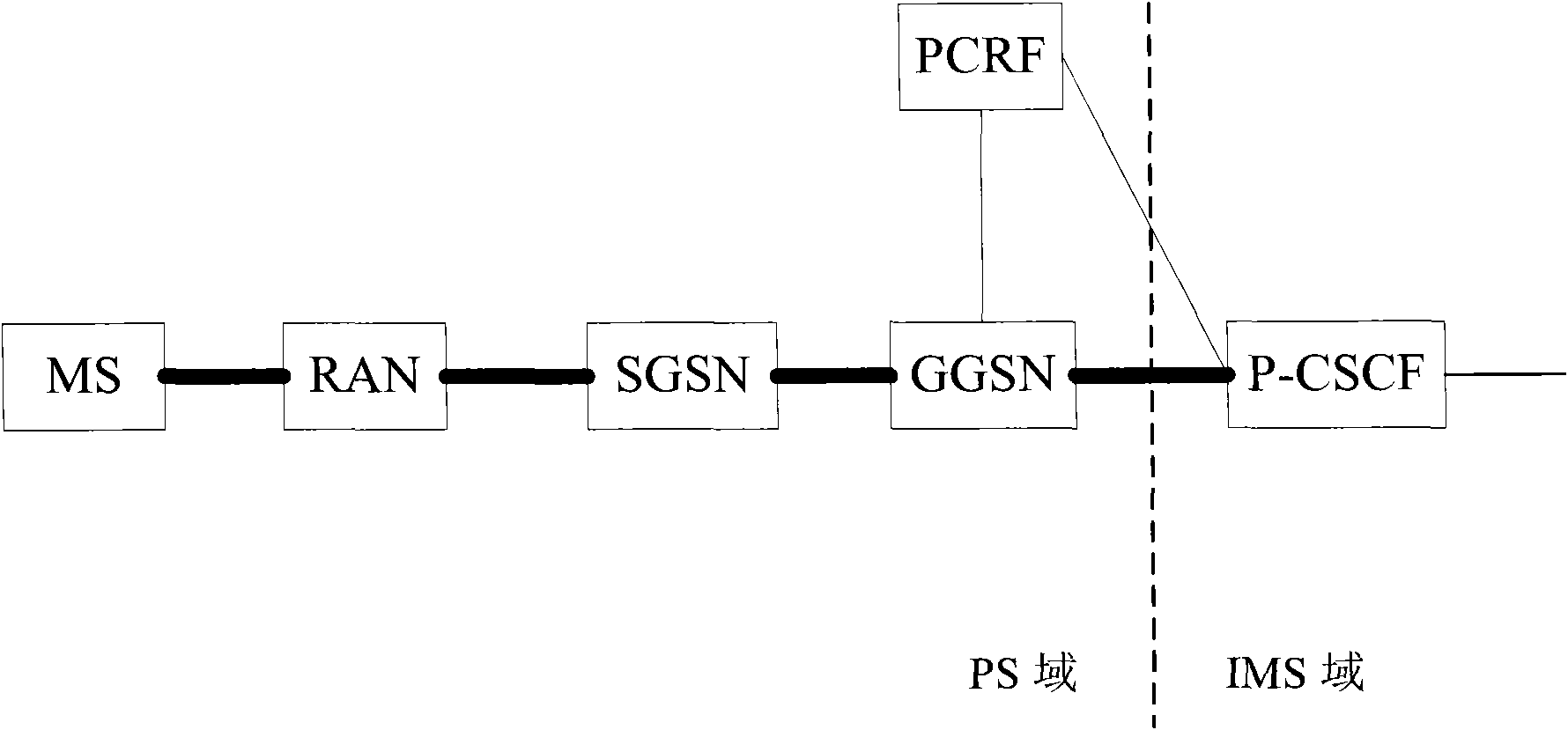
[0033] Among them, the IMS network element can be P-CSCF, and the PS network element includes PCRF, PGW, SGW, MME and eNB; UE establishes IP-CAN connection through EPS or GPRS, obtains IP address and IP address of P-CSCF, according to P - The IP address of the CSCF is registered on the P-CSCF;
[0034] According to the registration information of the UE and the...
Embodiment 2
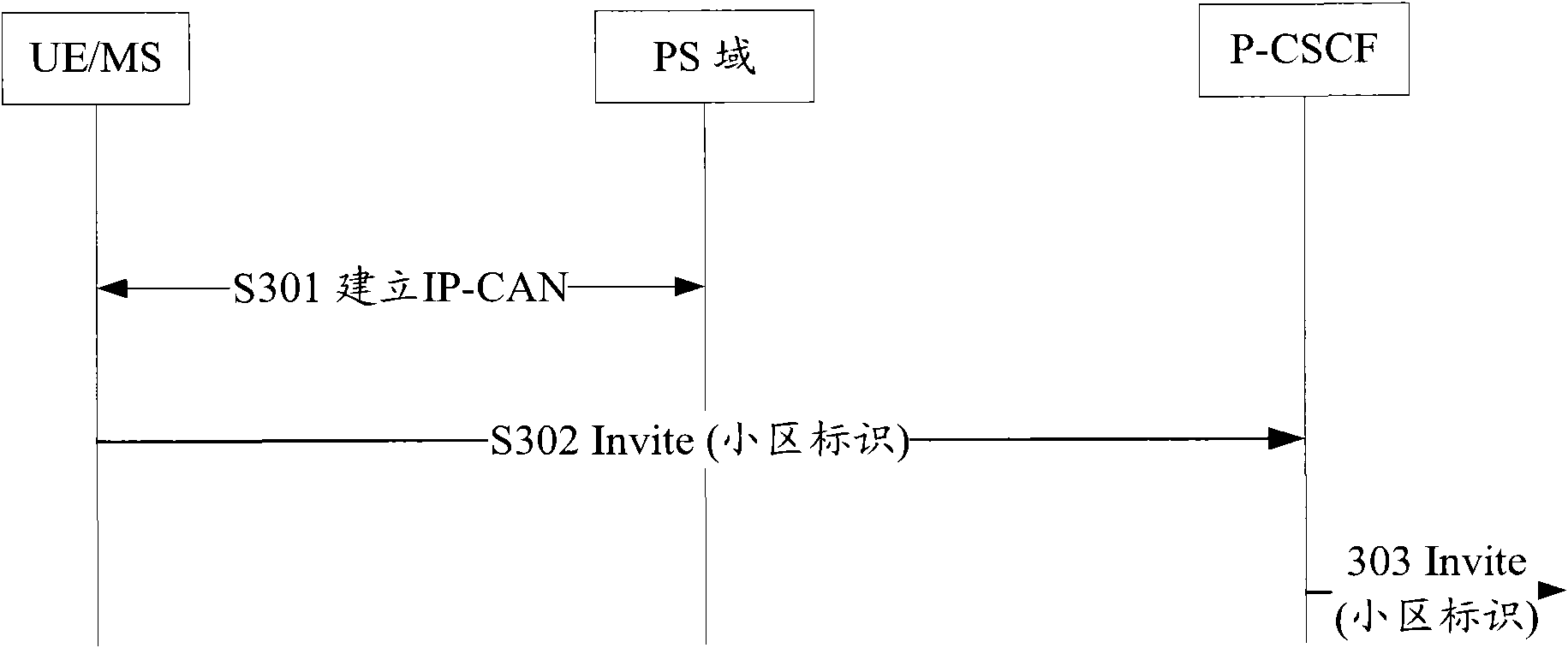
[0041] Figure 5 It is a flow chart of the UE initiates a service to the IMS domain through the EPS network, and the P-CSCF obtains the UE cell ID; the specific steps are as follows:
[0042] Step S501, the UE establishes an IP-CAN connection in the EPS, the EPS network assigns an IP address to the UE, and the UE obtains the IP address of the P-CSCF through DHCP (Dynamic Host Configuration Protocol) or DNS (Domain Name Server) query;
[0043] Step S502, the UE initiates an IMS service, and sends an invitation (Invite) to the P-CSCF, which contains service information and may include the cell identity of the UE;
[0044] Step S503, the P-CSCF judges that it is necessary to obtain the user's cell identity from the PCRF according to the content of the INVITE and the locally configured policy, and sends an Auth-Application Request (AA-Request for short) to the PCRF, which carries instructions or event triggers Device: Obtain the cell ID of the user. The specific reason may be th...
Embodiment 3
[0059] Figure 6 It shows a flow chart of UE handover between different cells within the eNB, and the eNB reporting the latest cell identity after the UE location changes to the MME. Specific steps are as follows:
[0060] In step S601, the UE moves between different cells inside the eNB and performs handover.
[0061] Step S602, the eNB reports the latest cell ID of the UE after the change to the MME according to the location change event trigger or location request type sent by the MME as location change report;
[0062] Step S603, the MME sends a location change notification to the SGW / PGW, which carries the latest cell identity of the UE;
[0063] In step S604, the PGW / SGW sends a location change confirmation to the MME to confirm receipt of the message in step S603;
[0064] Step S605, the PGW sends a credit control request to the PCRF, which carries the cell identity of the UE; when PMIPv6 is used between the PGW and the SGW, the SGW can send a credit control request ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com