Method and device for preventing information tampering
A technology for tampering and identifying information, which is applied to secure communication devices and key distribution, and can solve problems such as untrustworthy information obtained by the server.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
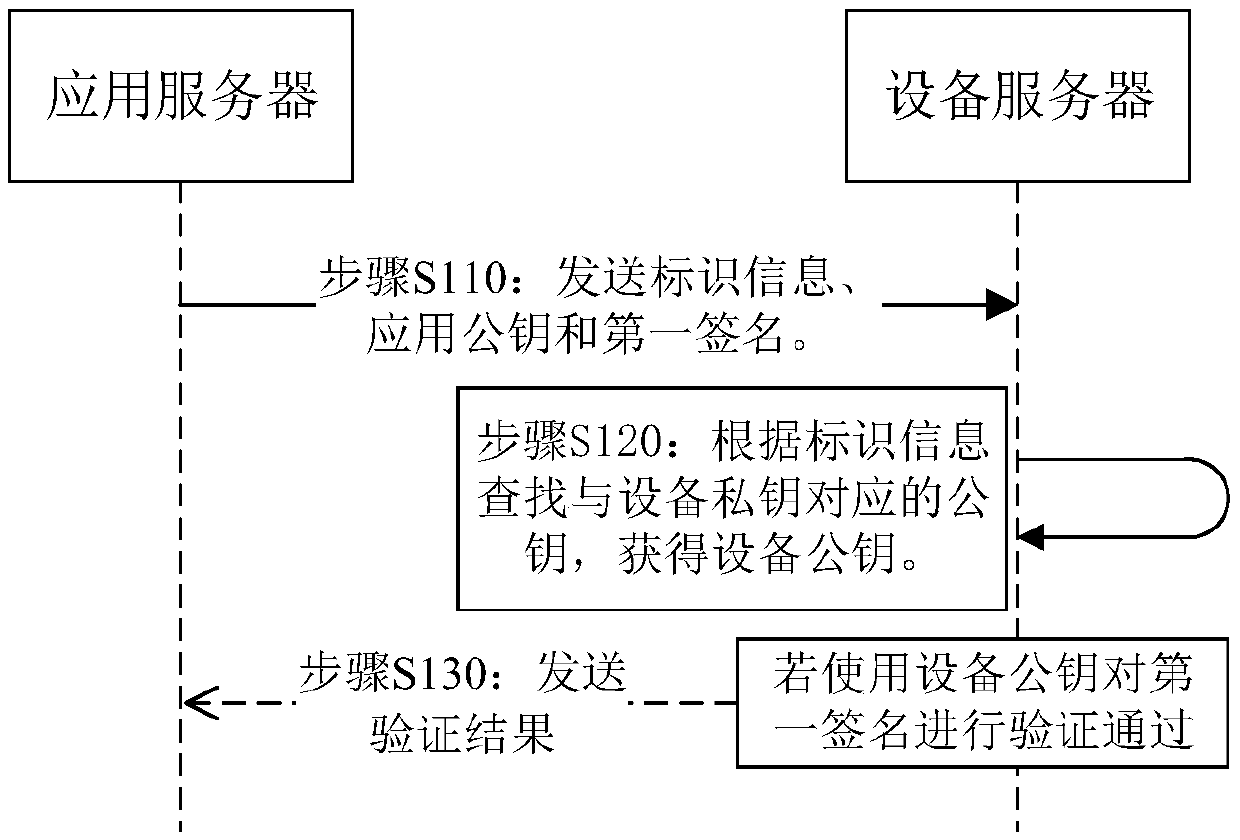
[0055] See figure 2 , figure 2 A sequence diagram of a method for preventing information tampering applied to a device server according to an embodiment of the present application is shown. A method for preventing information tampering provided by the embodiment of this application is applied to a device server, including:
[0056] Step S110: Receive the identification information, application public key and first signature sent by the application server.
[0057] The identification information is the identification information of the device terminal, the application public key is generated by the device terminal and sent to the application server, and the first signature is signed by the device terminal using the device private key in the trusted execution environment to the application public key Acquired, information stored in the TEE cannot be modified by untrusted applications. The identification information here includes: Media Access Control Address (Media Access C...
no. 2 example
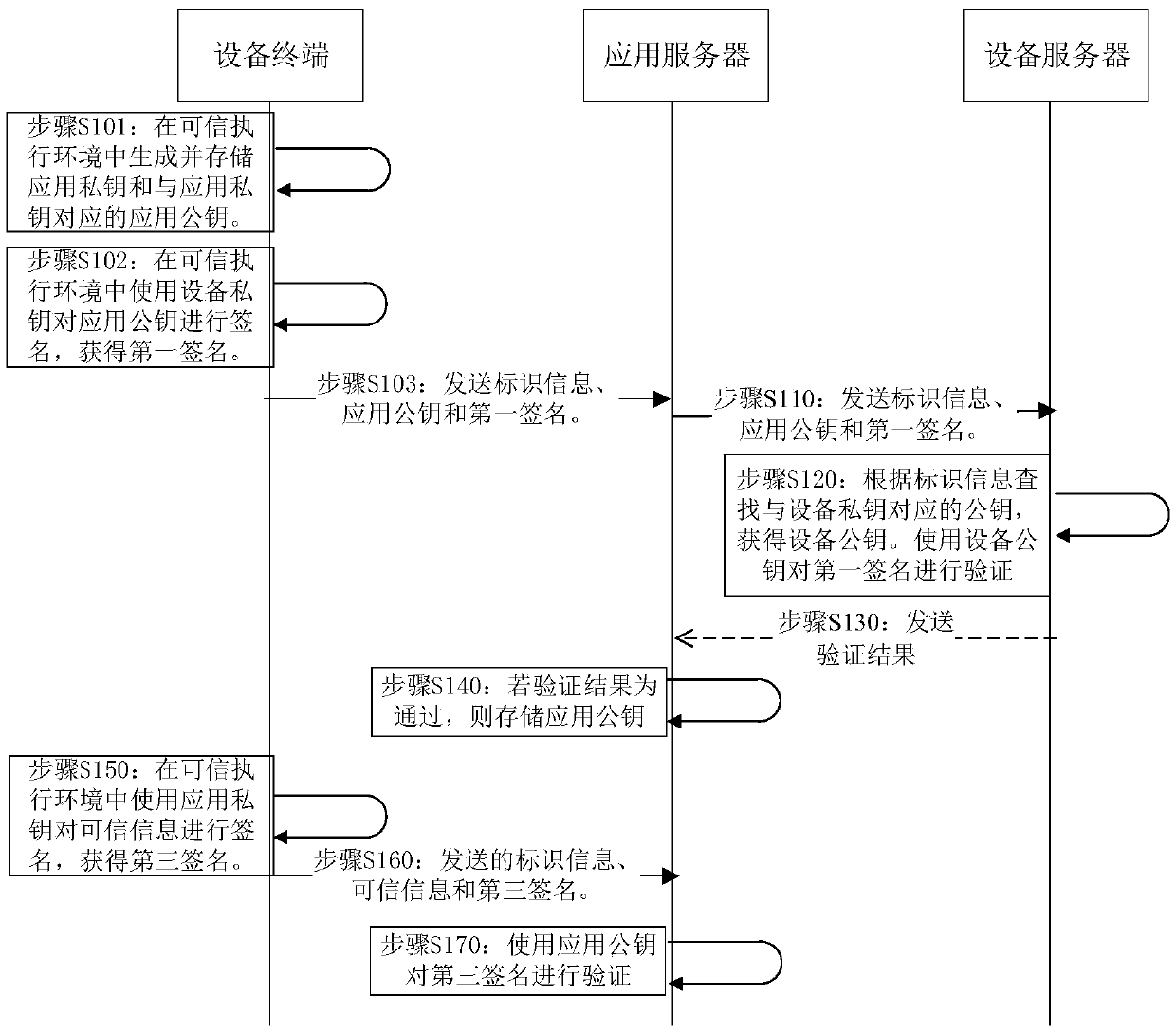
[0080] See Figure 4 , Figure 4 A sequence diagram of an interaction between a device terminal sending trusted information to a device server provided by the embodiment of the present application is shown.
[0081] Step S210: The device terminal obtains the information obtained by executing trusted operations in the trusted execution environment, and obtains trusted information.
[0082] Wherein, the trusted information is the information obtained by performing trusted operations in the trusted execution environment of the device terminal, where the trusted information may be geographic location information, for example: geographic location information obtained through a wireless module, and geographic location information includes: longitude , latitude, province / state and city, etc., or location information obtained by accessing the Global Positioning System or the Beidou Satellite System. Of course, other information may also be included, such as information about the dev...
Embodiment approach
[0088] In order to facilitate understanding, the following describes another implementation of the method for preventing information tampering provided by the embodiment of the present application. Another implementation of the method for preventing information tampering provided by the embodiment of the present application is specifically described as follows:
[0089] See Figure 5 , Figure 5 A schematic diagram of the connection of the information tampering prevention system provided by the embodiment of the present application is shown. The specific implementation mainly includes the following four steps:
[0090] 1. Preset device public-private key pair: Before the device leaves the factory, a pair of public-private key pair is generated at the production line stage. The device private key is stored in the RPMB partition on storage devices such as eMMC, and the device public key is imported to the device server. The device private key is managed by the key management T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com