Network electron evidence processing system and processing method
A technology of electronic evidence and processing system, applied in the field of computer information, which can solve the problems of user inconvenience and inability to adapt to the needs of the public
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
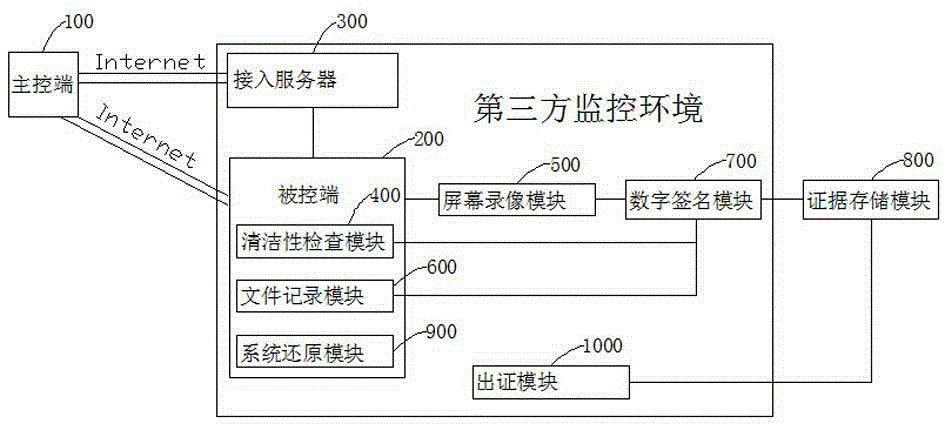
[0041] Example 1 like figure 1 As shown, a network electronic evidence processing system is disclosed, including a main control terminal 100, an access server 300, a controlled terminal 200 with the function of accessing the Internet, a cleanliness inspection module 400, a screen recording module 500, and a file recording module 600, A digital signature module 700 , an evidence storage module 800 , a system restoration module 900 , and a certification module 1000 .
[0042] Wherein the access server 300 responds to the login request sent by the user from the main control terminal 100 and performs user identity information verification; the controlled terminal 200 is connected to the access server 300 through the network and can be remotely controlled by the main control terminal 100; the cleanliness inspection module 400 It is used to carry out continuous cleanliness inspection on the controlled terminal 200 to form a corresponding cleanliness inspection report; the screen r...
Embodiment 2
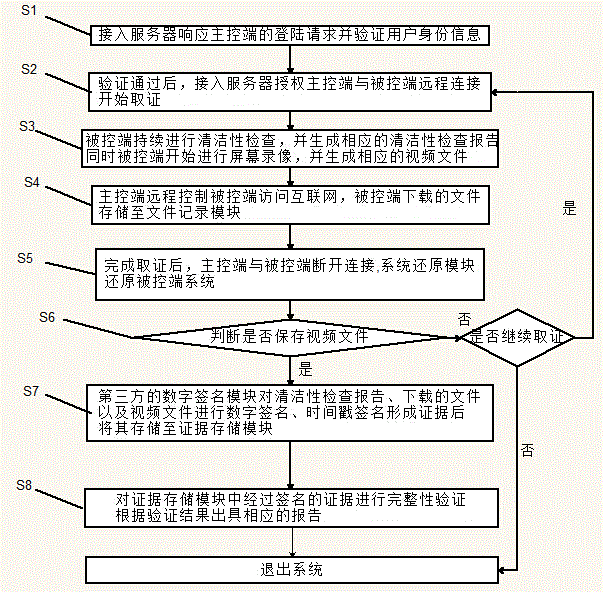
[0043] Example 2 like figure 2 As shown, a network electronic evidence processing method is disclosed, including three parts: obtaining evidence, storing evidence, and issuing evidence, and using the network evidence processing system disclosed in Embodiment 1, specifically including the following steps:
[0044] S1: The access server responds to the login request of the master control terminal and verifies the user identity information;
[0045] S2: After the verification is passed, the access server authorizes the remote connection between the control terminal and the controlled terminal, and starts to collect evidence;
[0046] S3: The controlled terminal continues to perform cleanliness inspection and generates a corresponding cleanliness inspection report. At the same time, the controlled terminal starts to record the screen and generate a corresponding video record file;
[0047] S4: The master control terminal remotely controls the controlled terminal to access the ...
Embodiment 3
[0052] Example 3 As a further solution of Embodiment 1, the master control terminal 100 is a computer with VNCviewer installed, the controlled terminal 200 is a computer with VNCserver installed, the access server 300 is a WEB server at the notary office, and the screen recording module 500 is inserted in another The acquisition card on each computer, the cleanliness inspection module 400, the file record module 600, and the system restore module 900 are all software systems installed on the controlled-end computer. As long as the controlled-end computer is on, the cleanliness inspection module 400 Continuously monitor and kill the system vulnerabilities and Trojan horse viruses of the controlled end in real time. The digital signature module 700 includes a digital signature server and a time stamp server with the private key certificate of the notary office. The digital signature module 700 also has data Encryption function, the evidence storage module 800 is a cloud storage...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com