Cloud Data Sharing Method Based on Block Chain to Realize Data Tampering Resistance and User Collusion
A data tampering and blockchain technology, applied in the field of cloud data sharing, can solve the problems of shared data tampering and complex system processing steps, and achieve the effect of solving untrustworthy problems and ensuring security and reliability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to make the present invention more comprehensible, preferred embodiments are described in detail below with accompanying drawings.
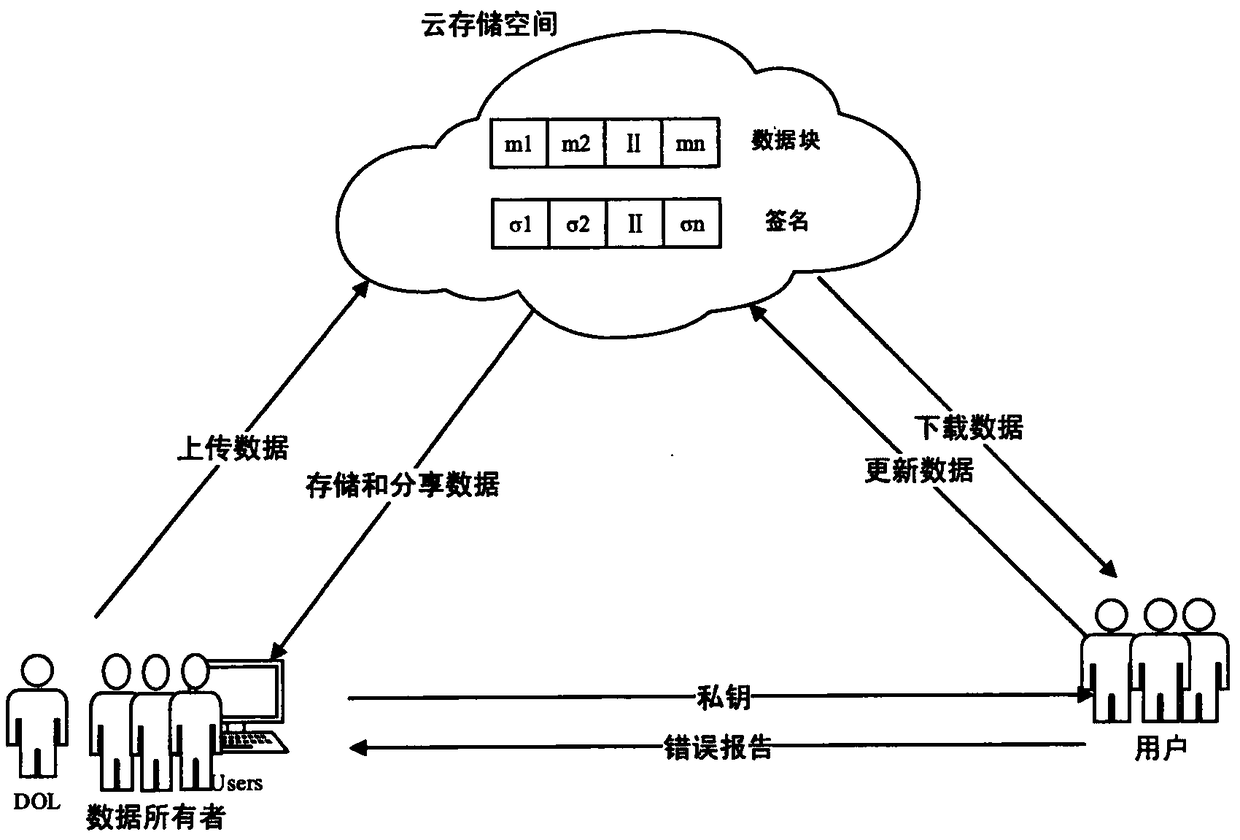
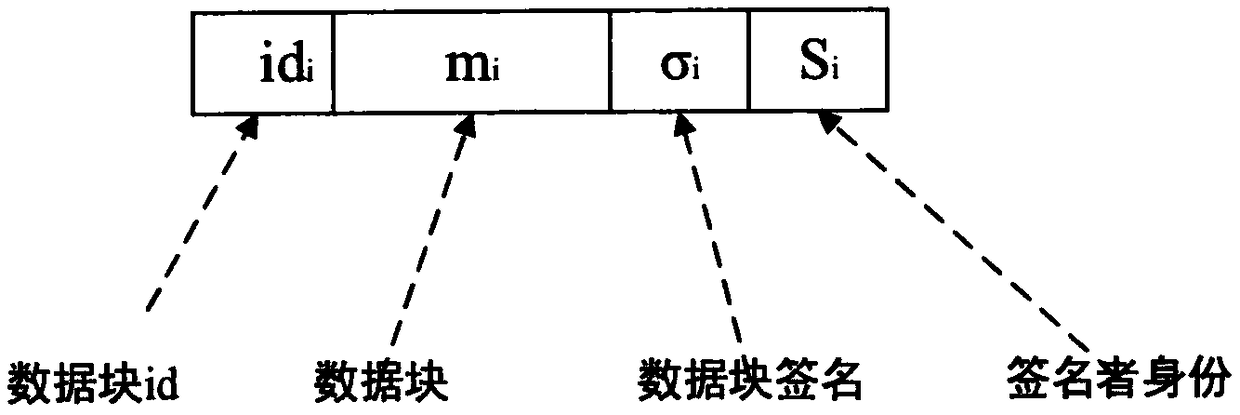
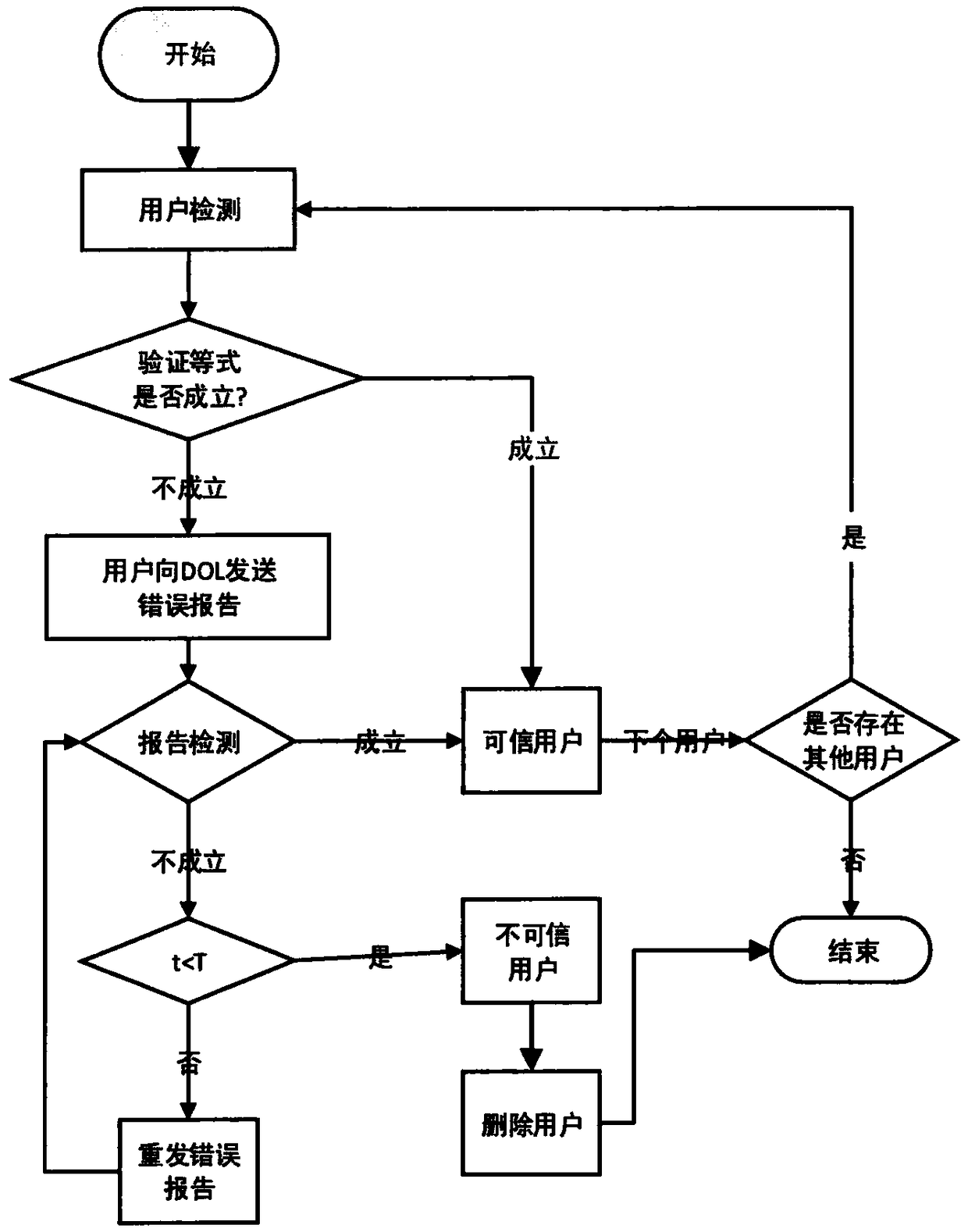
[0030] Such as figure 1 As shown, the model of this method is composed of three roles: data owner (data owner), cloud service provider (CSP), and user (user). (1) The data owner first encrypts the data, and then uploads it to the cloud server for sharing. The data owner consists of two roles: dedicated sharing and part-time sharing (user). That is, users in this scenario can also share all their own data. Among the data owners, a Data Owner Leader (Data Owner Leader, hereinafter referred to as DOL) is recommended according to the data sharing contribution rate, and is responsible for some work of data operation. In the scheme of the present invention, DOL is honest The role of the data sharer and responsible person. (2) The cloud service provider is responsible for the data storage of the data owner. The cloud service provider is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com