Patents
Literature
1628 results about "Ancillary data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Ancillary data (commonly abbreviated as ANC data), in the context of television systems, refers to a means which by non-video information (such as audio, other forms of essence, and metadata) may be embedded within the serial digital interface. Ancillary data is standardized by SMPTE as SMPTE 291M: Ancillary Data Packet and Space Formatting.
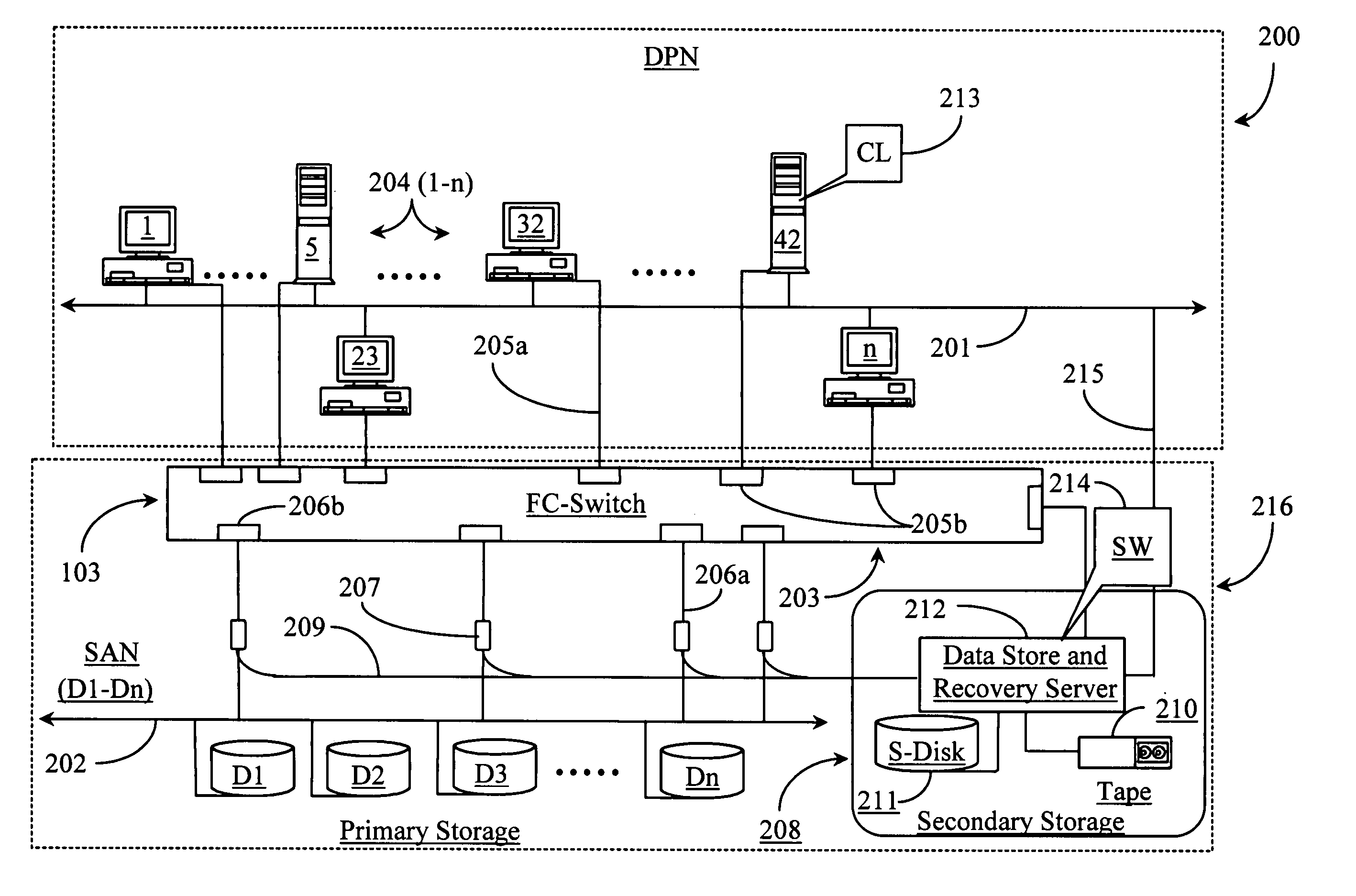
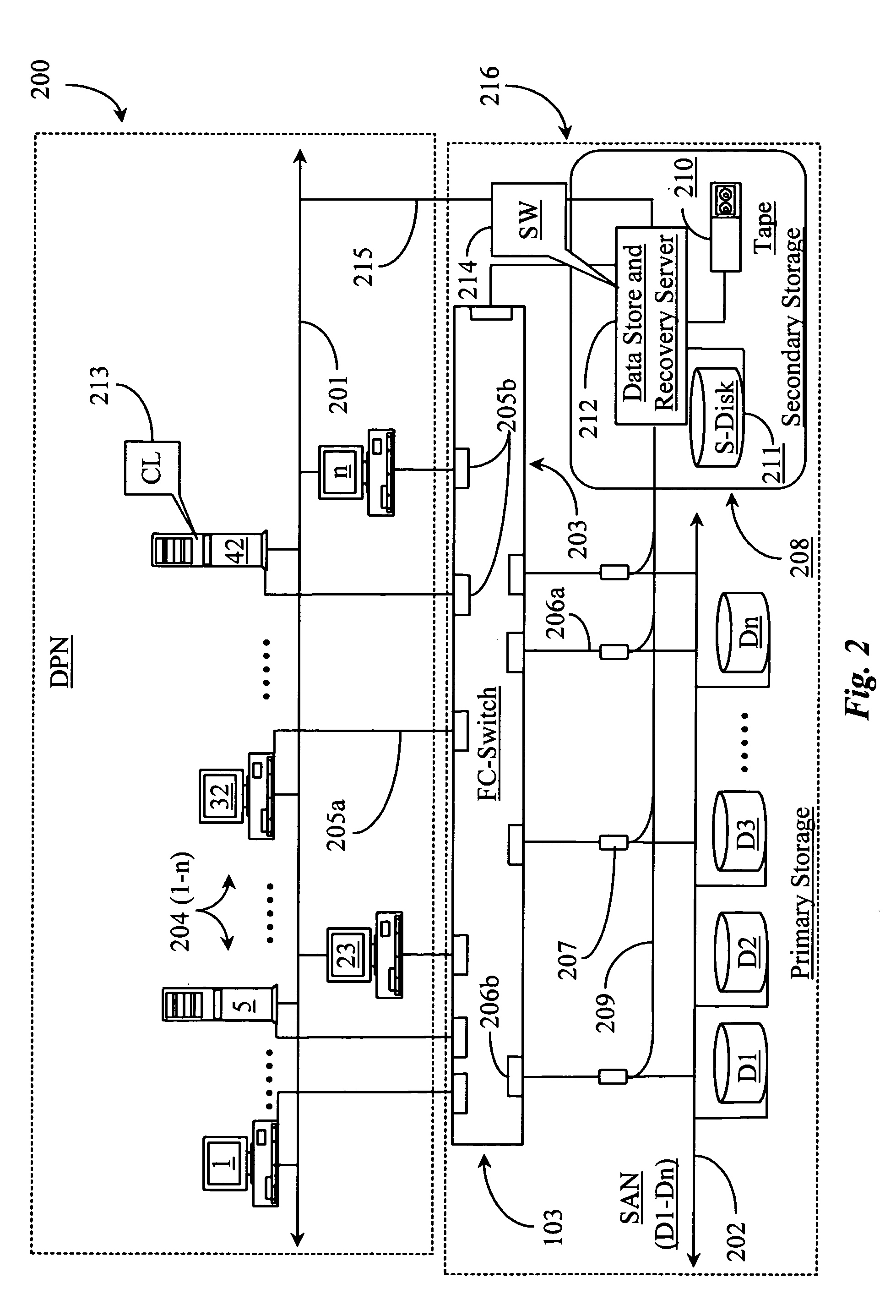
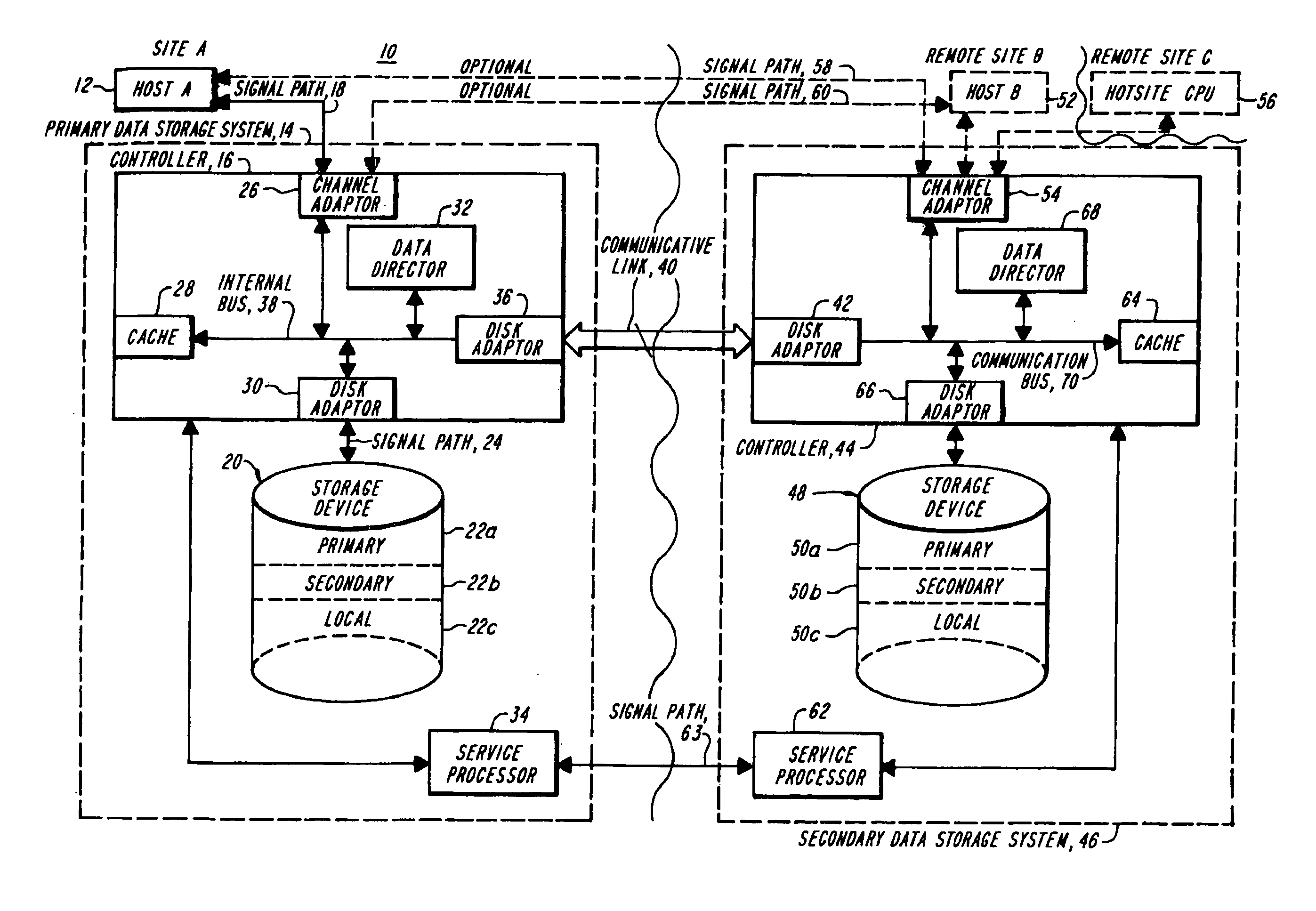
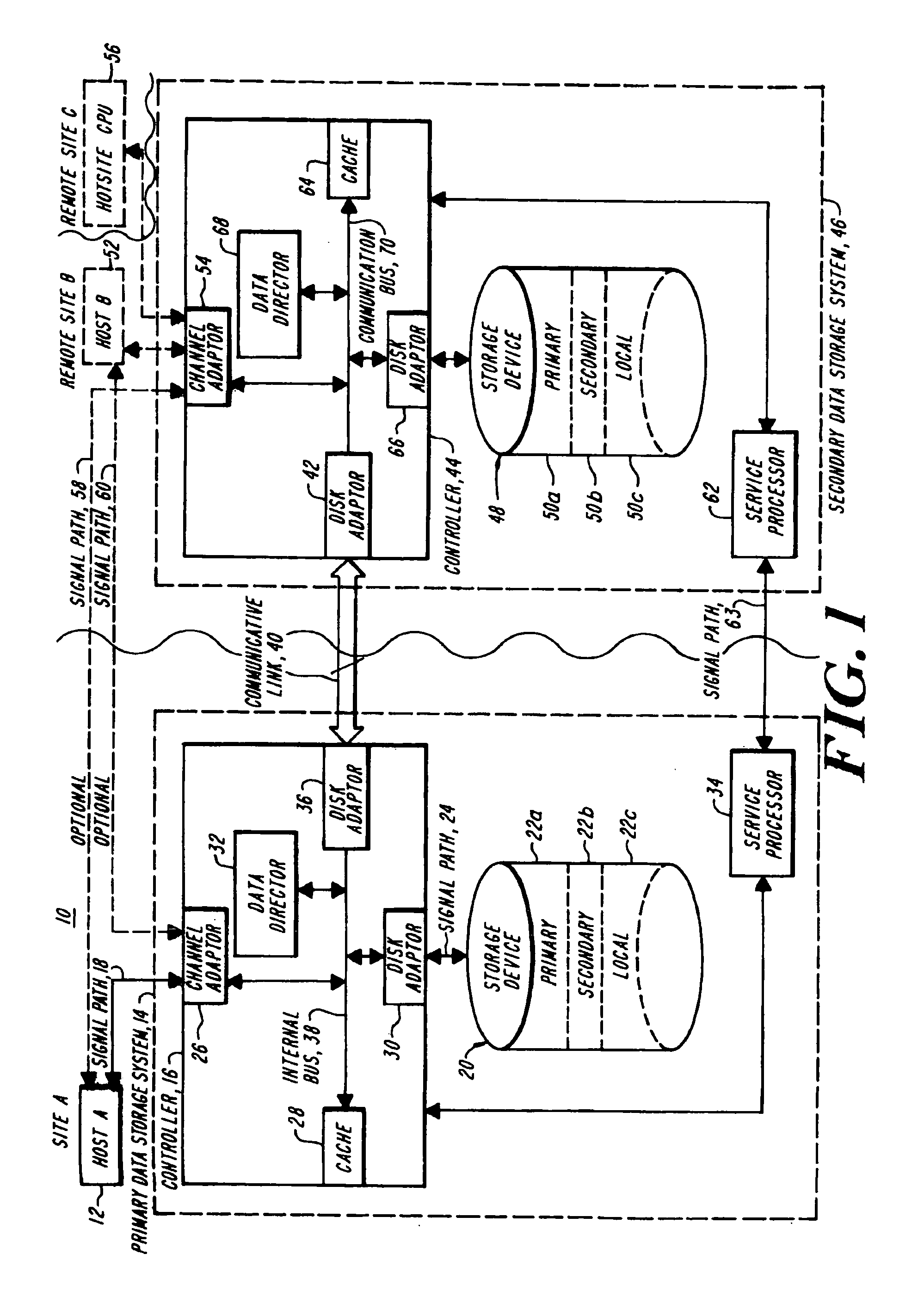
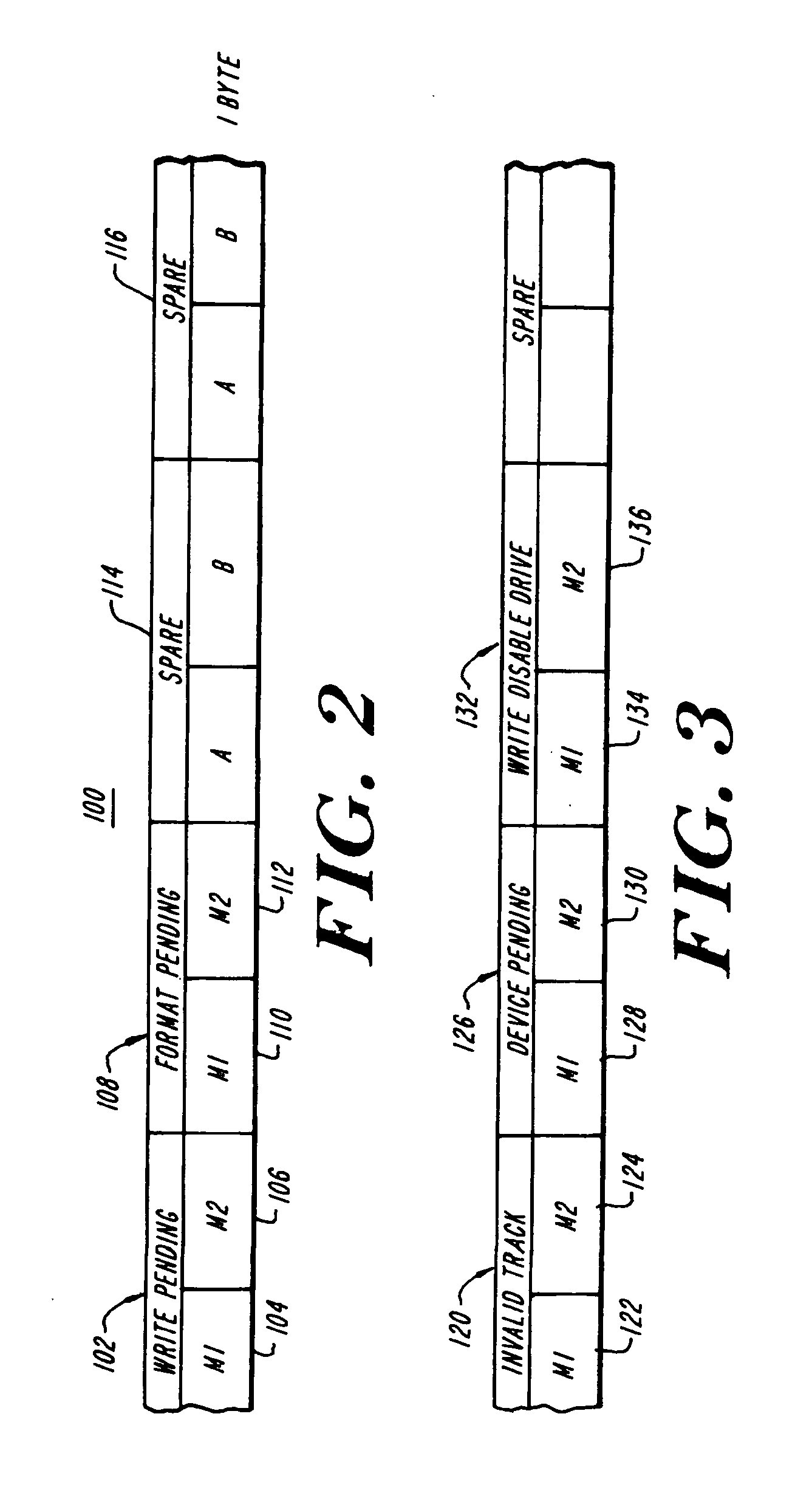
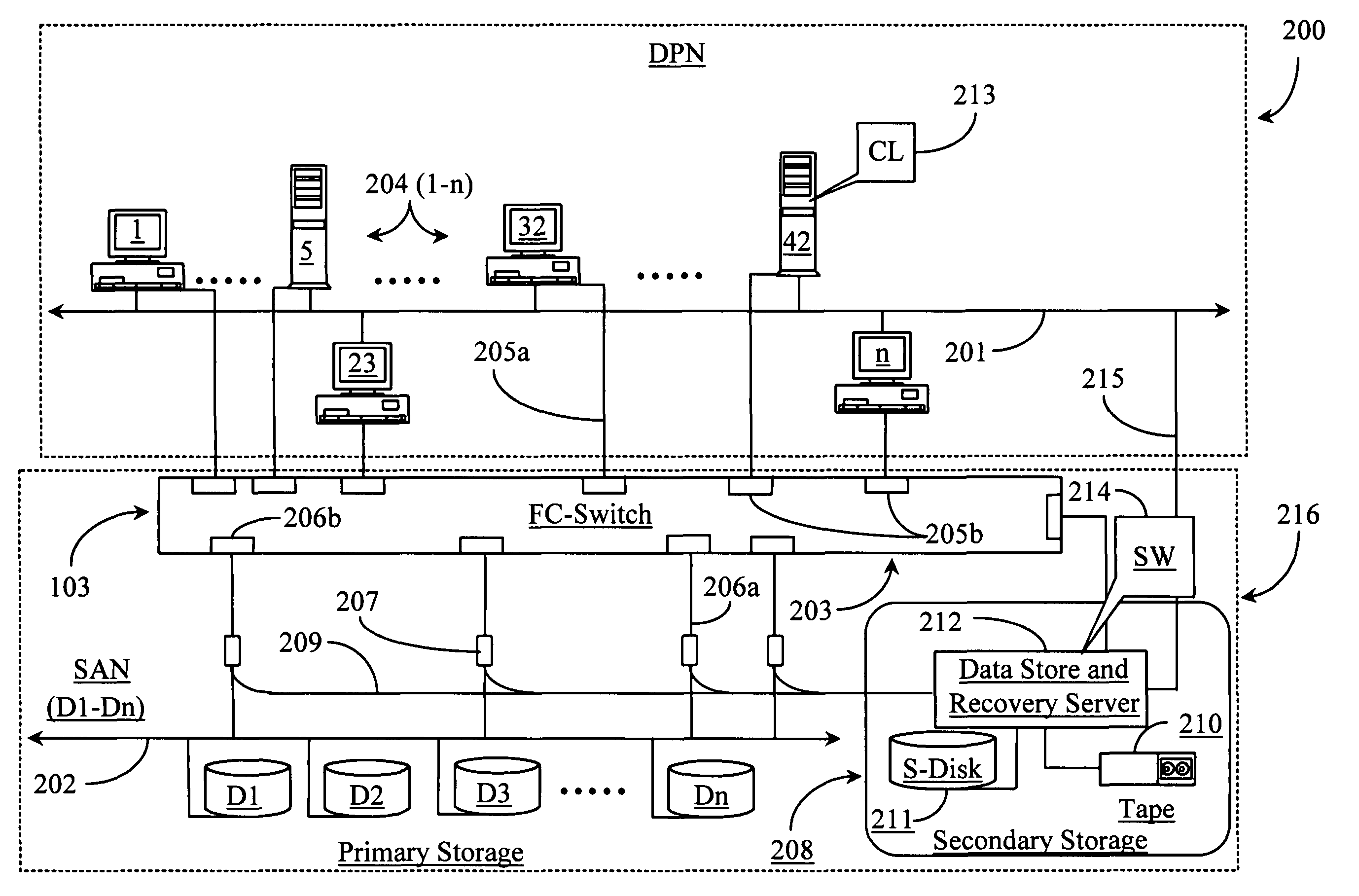
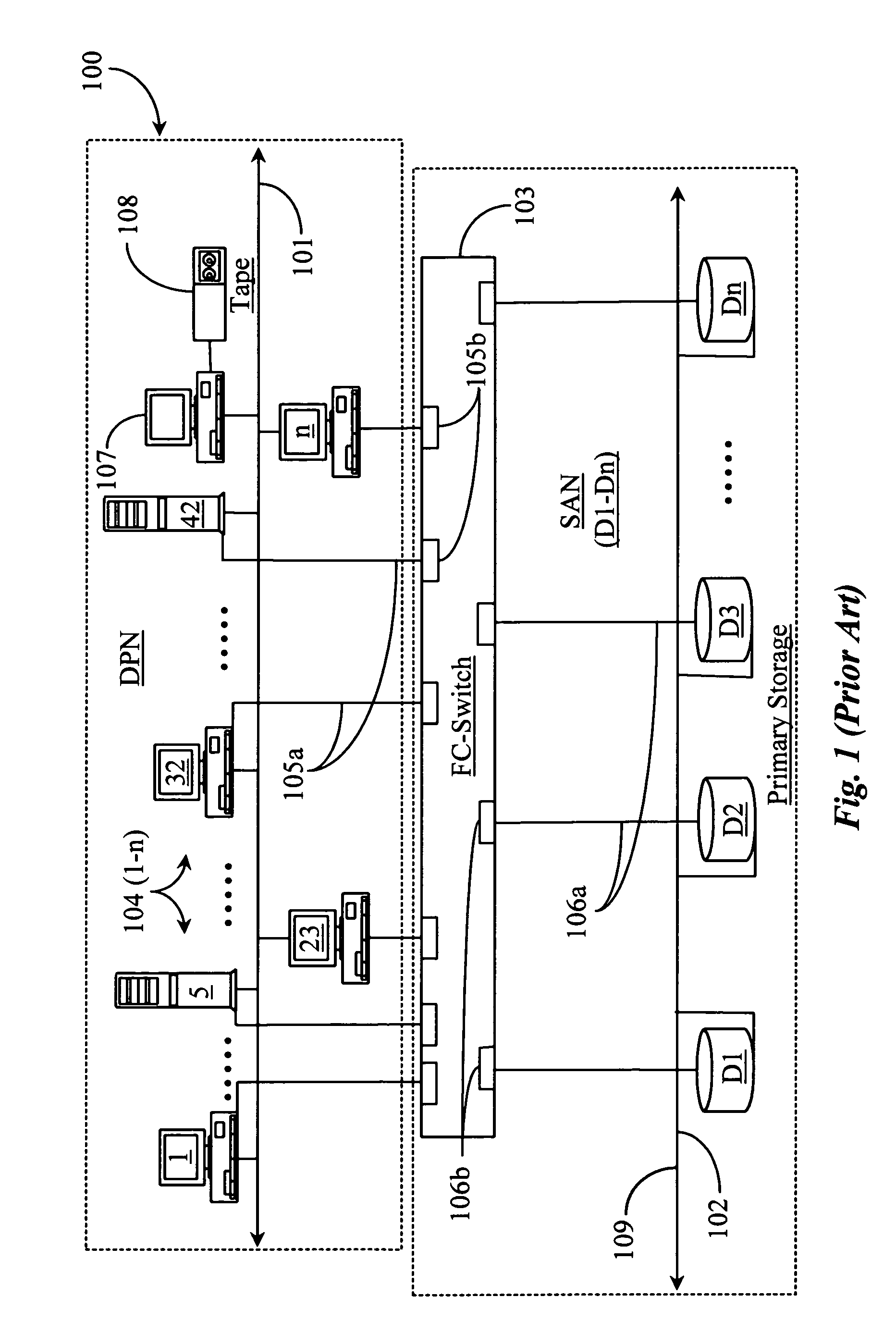
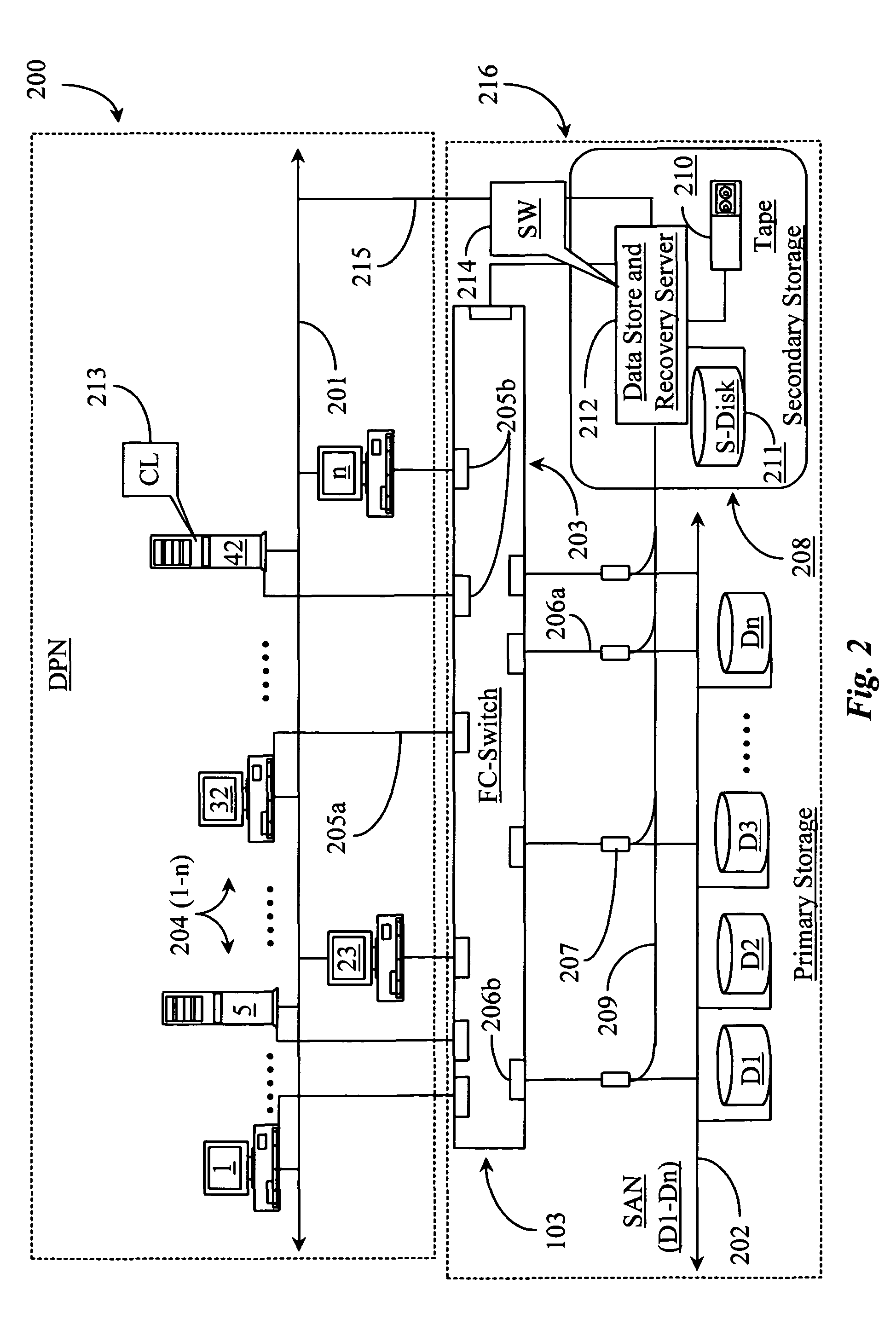
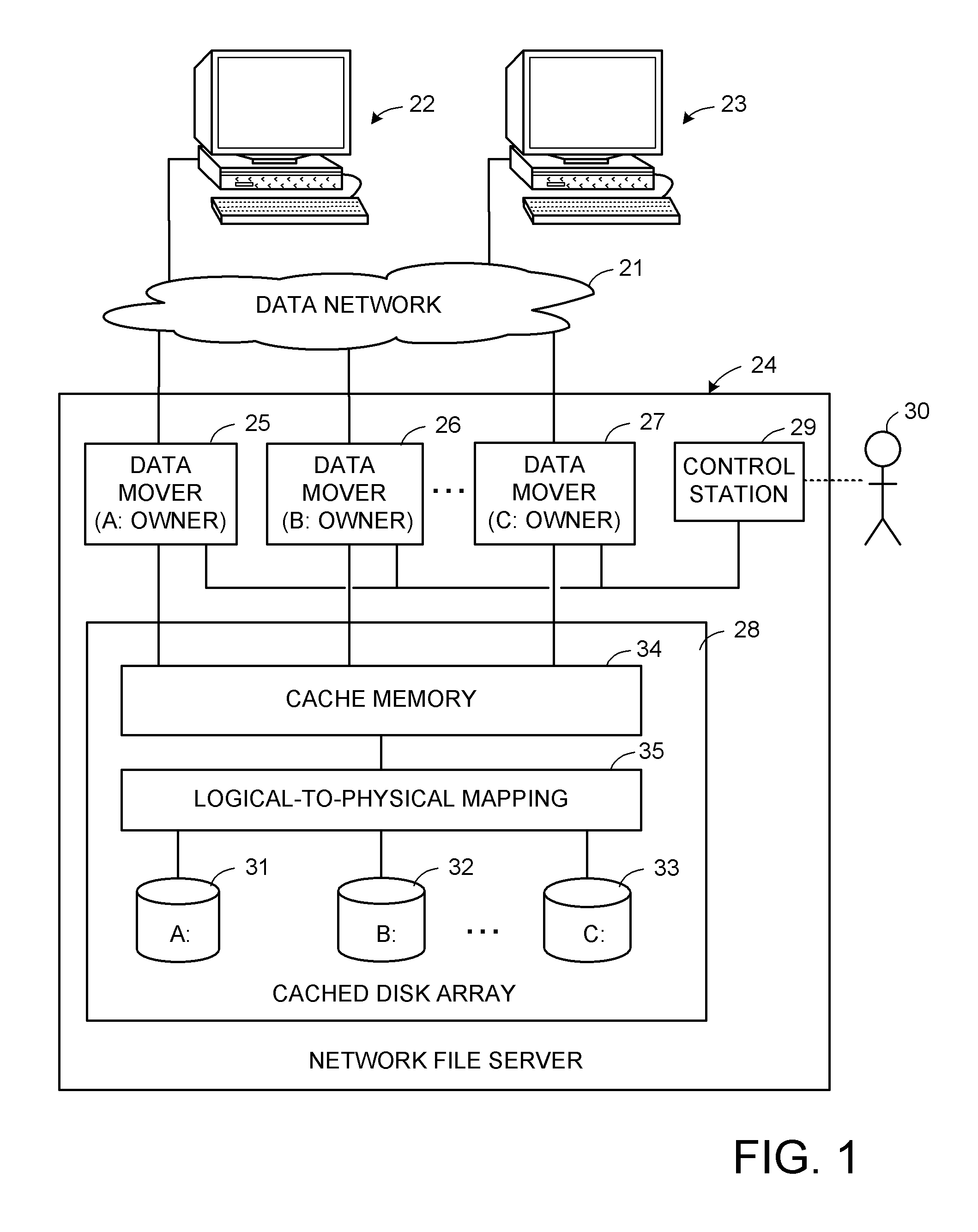
Methods and apparatus for accessing data from a primary data storage system for secondary storage
InactiveUS20060010227A1Error detection/correctionMultiple digital computer combinationsMachine instructionLogical view
A system for providing secondary data storage and recovery services for one or more networked host nodes includes a server application for facilitating data backup and recovery services; a first data storage medium accessible to the server application; a second data storage medium accessible to the server application; at least one client application for mapping write locations allocated by the first data storage medium to write locations represented in a logical view of the first data storage medium; and at least one machine instruction enabling direct read capability of the first data storage medium by the server application for purposes of subsequent time-based storage of the read data into the secondary data storage medium.
Owner:MICROSOFT TECH LICENSING LLC
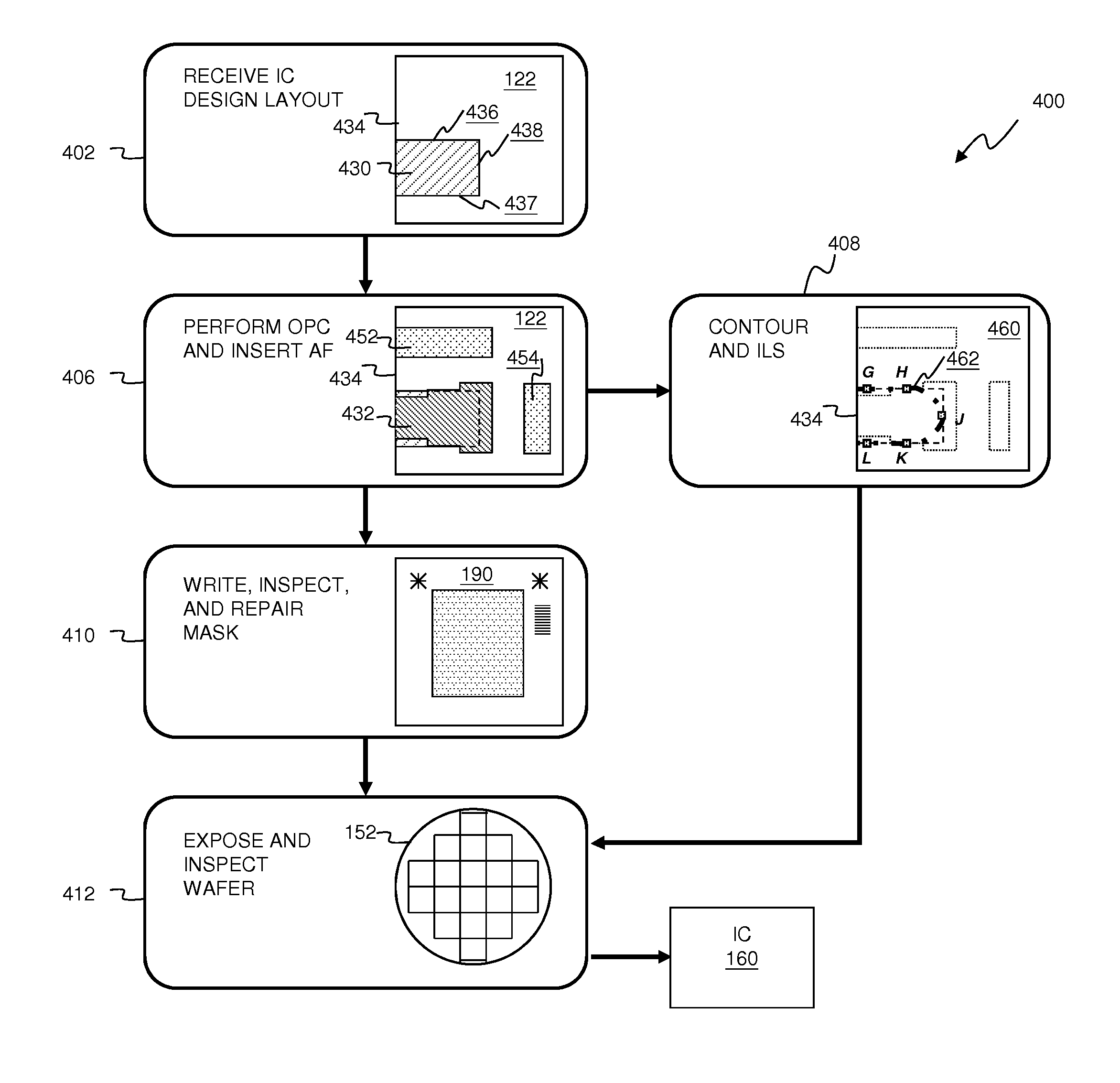
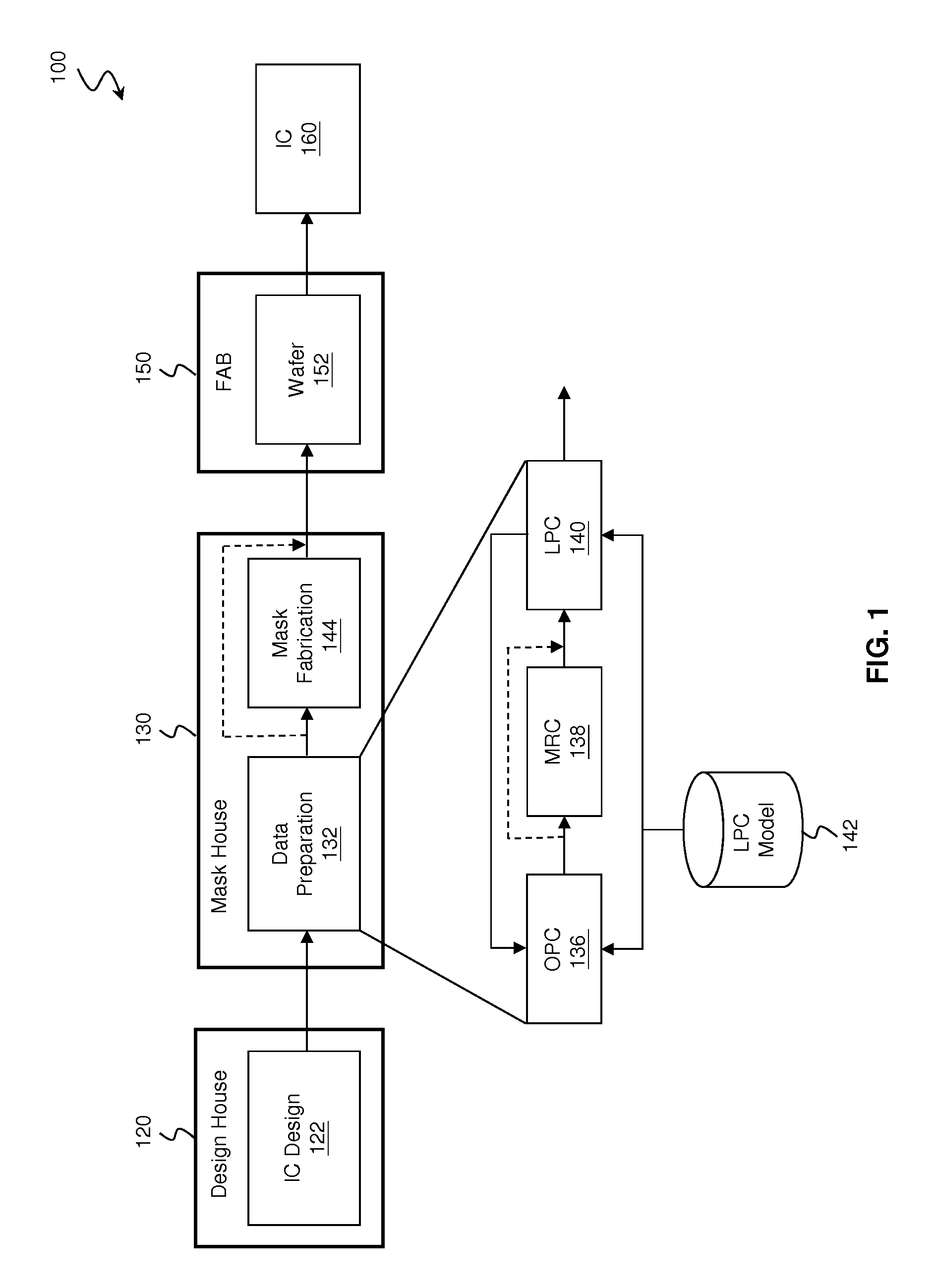
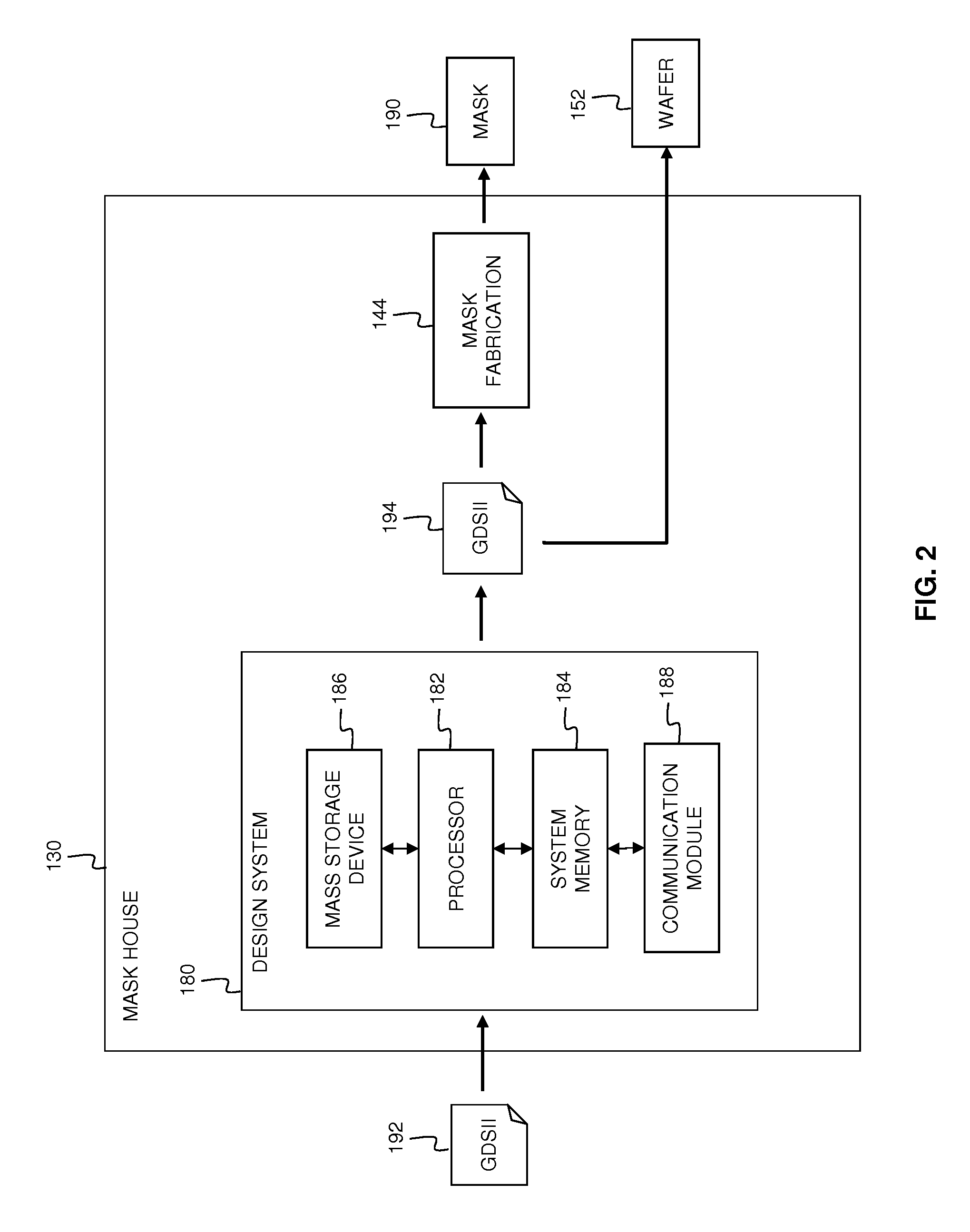
System and Method for Integrated Circuit Manufacturing
ActiveUS20150278429A1Photomechanical apparatusDesign optimisation/simulationMask inspectionIntegrated circuit manufacturing
Provided is an integrated circuit (IC) manufacturing method. The method includes receiving a design layout of an IC, the design layout having a main feature; performing a process correction to the main feature thereby generating a modified main feature; using a computer, generating a simulated contour of the modified main feature, the simulated contour having a plurality of points; generating a plurality of assistant data in computer readable format, wherein each assistant data includes at least one process performance factor associated with one of the points; and keeping the simulated contour and the assistant data for use by a further process stage, such as mask making, mask inspection, mask repairing, wafer direct writing, wafer inspection, and wafer repairing.
Owner:TAIWAN SEMICON MFG CO LTD
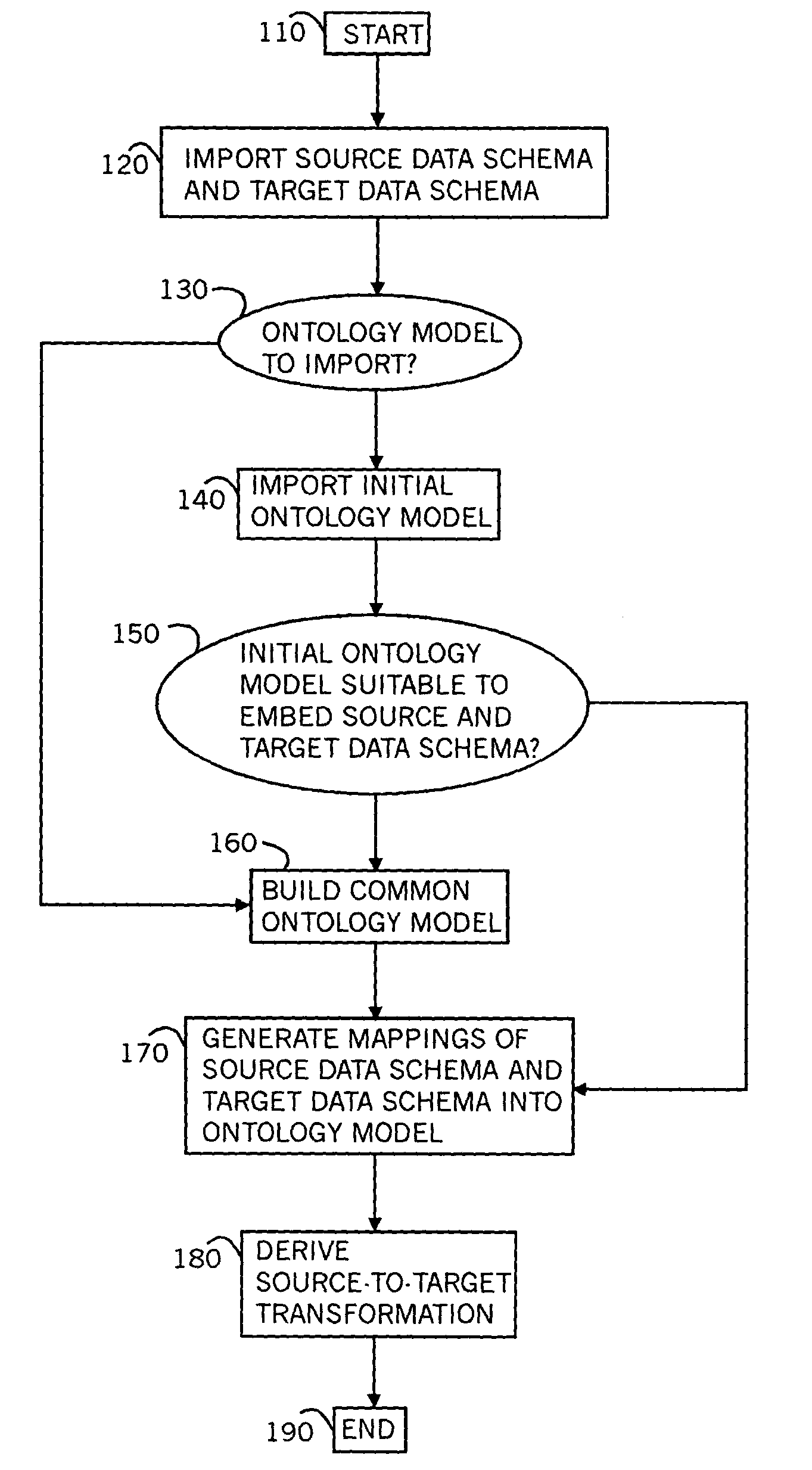
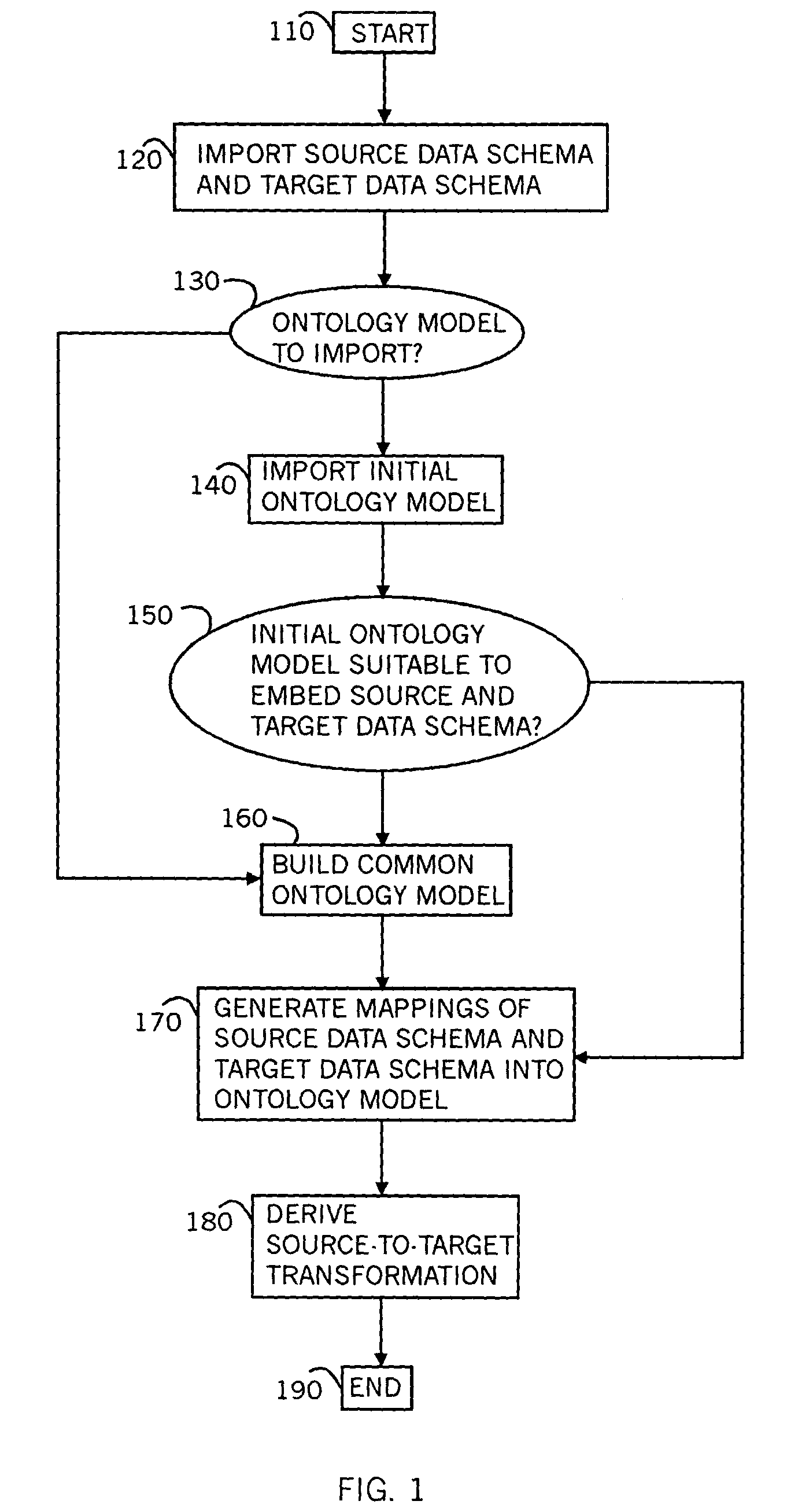
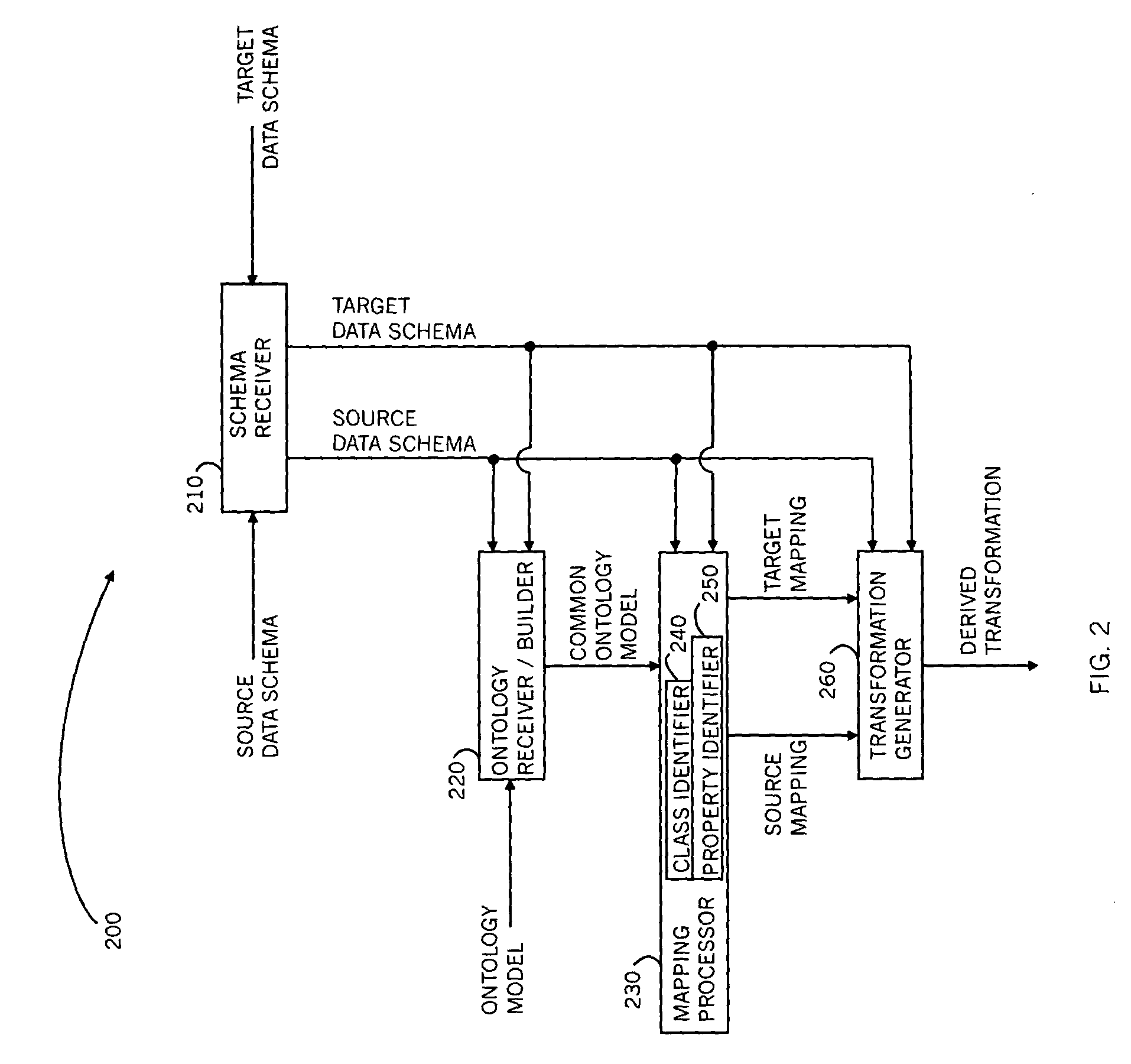
Method and system for mapping enterprise data assets to a semantic information model
A method for mapping data schemas into an ontology model, including providing an ontology model including classes and properties of classes, providing a data schema, identifying a primary data construct within the data schema, identifying a secondary data construct within the primary data construct, mapping the primary data construct to a corresponding class of the ontology model, and mapping the secondary data construct to a property of the corresponding class of the ontology model. A system and a computer readable storage medium are also described and claimed.
Owner:IBM CORP
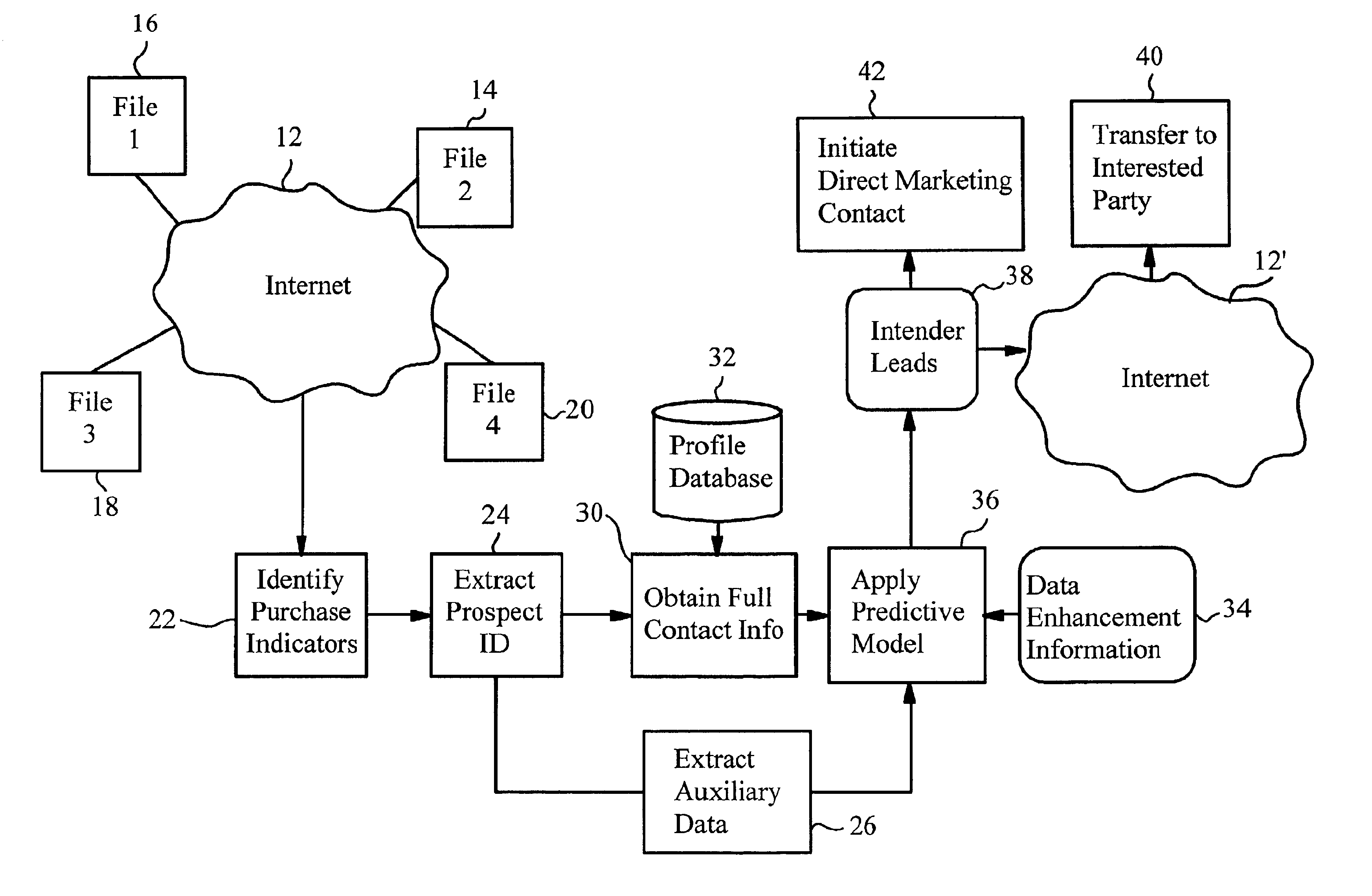
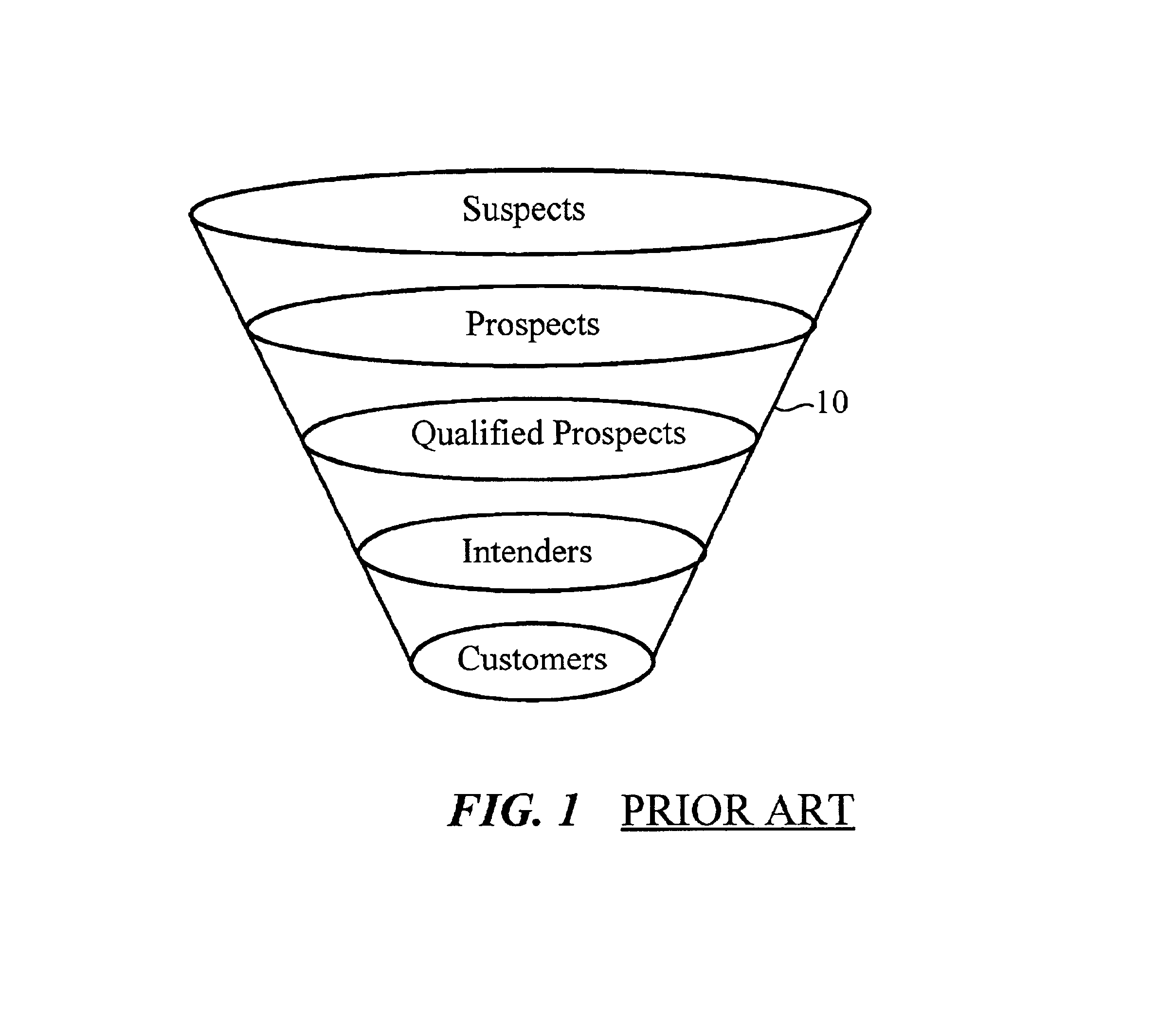
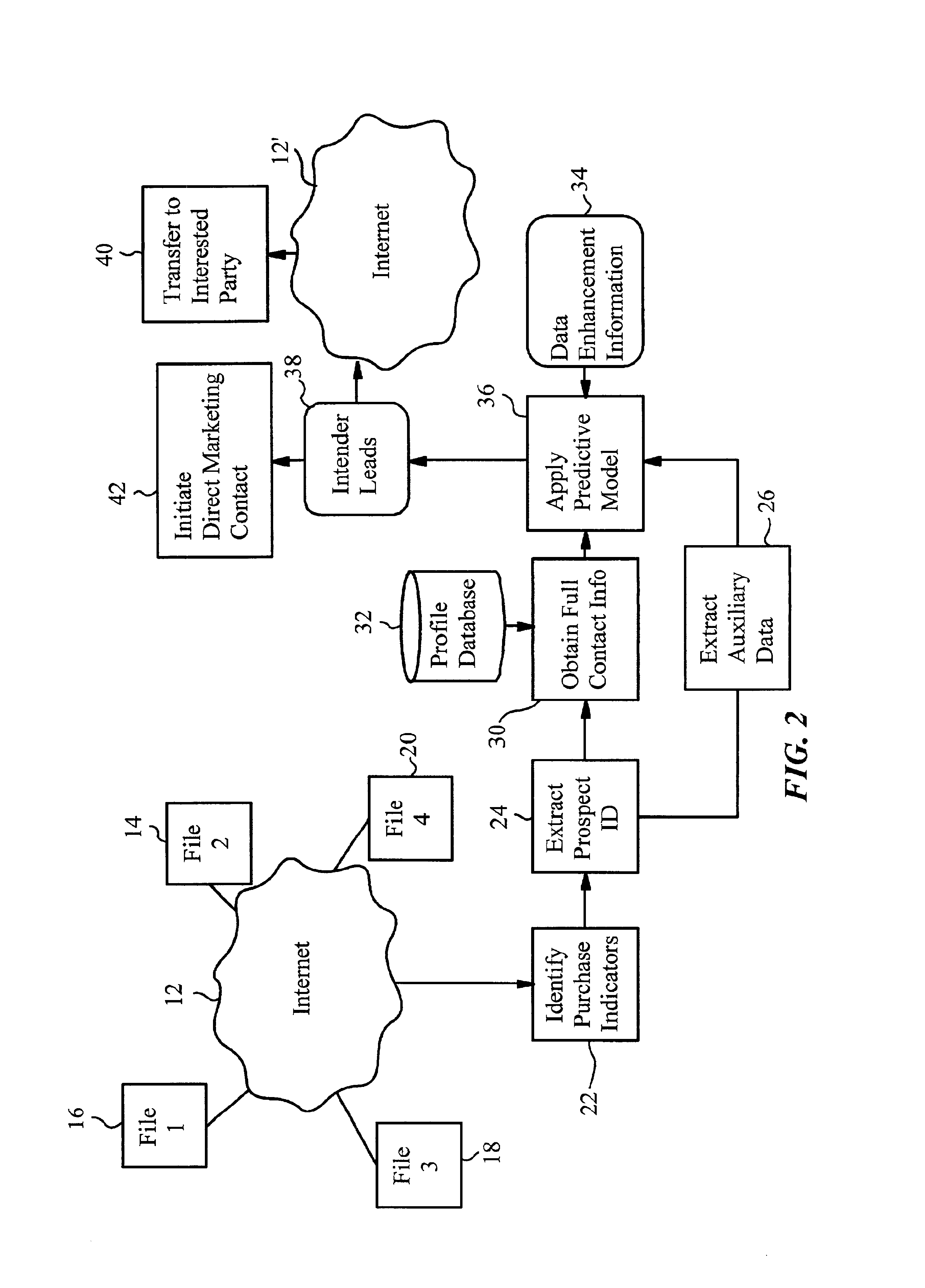
Internet-enabled lead generation
InactiveUS6868389B1Special data processing applicationsMarket data gatheringEmail addressThe Internet
A method of generating intender leads in a distributed computer system includes the steps of identifying purchase indicators and extracting prospect identifiers from the purchase indicators. Purchase indicators are pieces of data that represent a potential future purchase by a prospect. For example, an online classified advertisement selling an automobile is a purchase indicator for a potential future purchase of a new car by the old car seller. The prospect identifier, such as a telephone number or email address, uniquely identifies the prospect likely to make the future purchase. Preferably, the method also contains the steps of obtaining full contact information for the prospect from a profile database, applying a predictive model to the prospects to select intender leads, and transferring the intender leads to an interested party, such as a direct marketing service or sales force. An intender lead is a lead for a person intending to make a purchase of a particular product or service within a given time period. Only some of the prospects are actual intenders. Preferably, the method also includes the steps of extracting auxiliary data that is independent of the prospect from the purchase indicator, and obtaining data enhancement information about the prospect from data enhancement databases. The predictive model is preferably also applied to the data enhancement information and auxiliary data. The method is particularly well-suited for the Internet, which is a large source of publicly-available purchase indicators that is constantly updated. The intender leads are preferably transferred over the Internet, e.g. by email, so that they arrive at the sales force when they are still “hot.”
Owner:MEDIA DIRECT
Wafer fabrication data acquisition and management systems
InactiveUS6952656B1Improve data transfer performanceIncrease costResistance/reactance/impedenceComputer controlWafer fabricationData acquisition
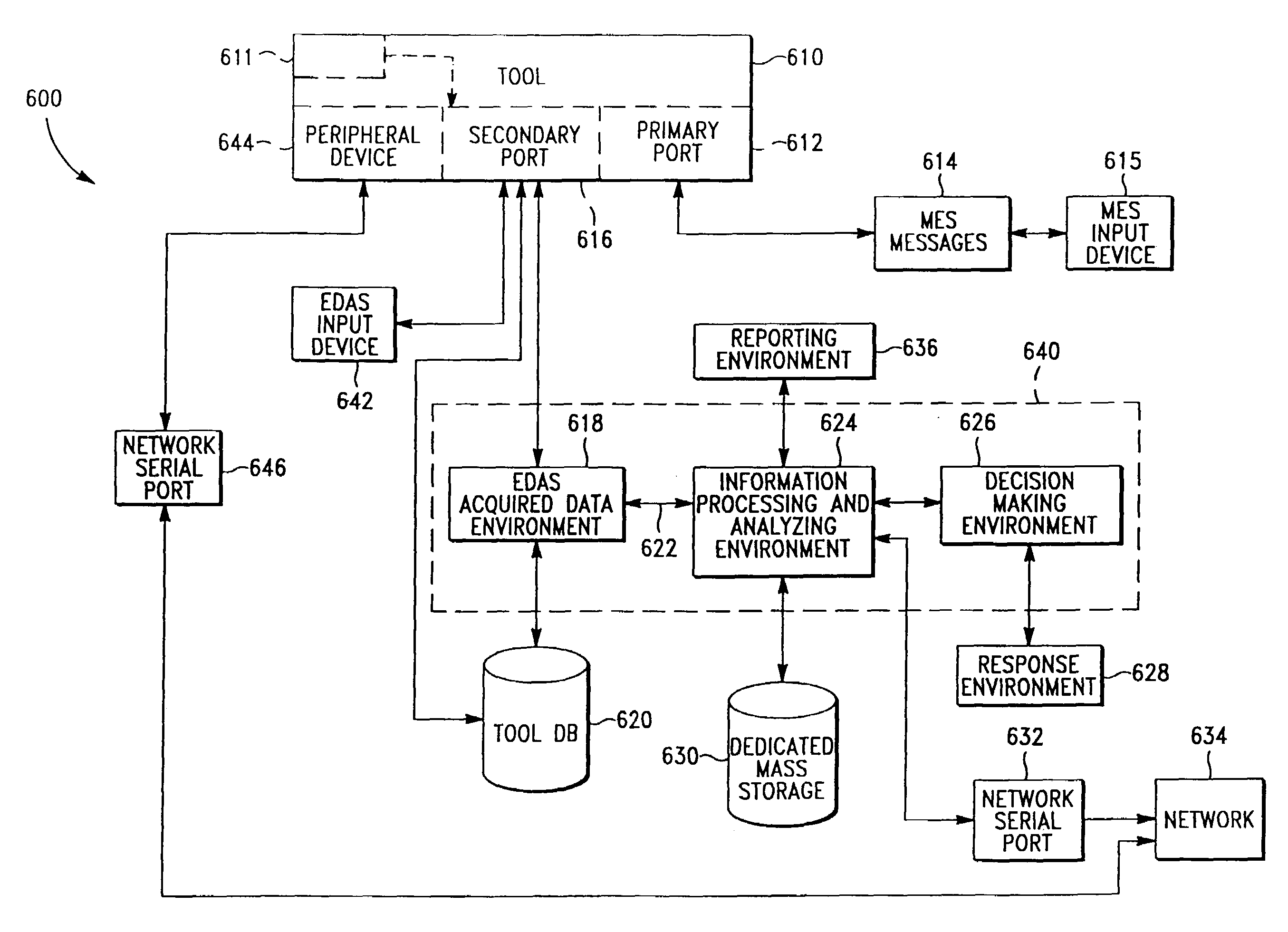
The present invention provides a semiconductor processing device (800) including a tool (802) having one or more sensors, a primary data communication port (804) and a secondary data communication port (806). A sensor data acquisition subsystem (808) acquires sensor data from the tool via the secondary port (806). The data acquisition subsystem (808) acquires MES operation messages via the primary port (804). Sensor data are communicated to a sensor processing unit (828) of a sensor data processing subsystem (810). The sensor processing unit (828) processes and analyzes the sensor data. Additionally, the processing unit (828) can be adapted for making product or processing related decisions, for example activating an alarm if the process is not operating within control limits. In another embodiment, the present invention provides a method and apparatus for processing data from a wafer fab facility (1000) including a plurality of tools (1004–1010) each having a primary data communication port (1012–1018) and a secondary data communication port (1042–1048).
Owner:APPLIED MATERIALS INC
Method and apparatus for regenerating a clock for auxiliary data transmitted over a serial link with video data
ActiveUS7088398B1Television system detailsPulse modulation television signal transmissionComputer hardwareCommunications system
Owner:KONINKLJIJKE PHILIPS NV
Associating data with images in imaging systems
InactiveUS20060041591A1Readily apparentDigital data processing detailsMetadata multimedia retrievalDatabaseManagement system
A reference to auxiliary data is steganographically encoded within a media signal. The auxiliary data is stored in a metadata database that maps the reference encoded in the media signal to its corresponding metadata. Various application programs and devices can access the metadata by extracting the reference from the media signal, and querying the database for metadata corresponding to the reference. The metadata database may be implemented in a network server to make metadata readily available to devices and applications distributed throughout a network. This steganographic link to metadata may be used to retrieve metadata across media management systems. In one configuration, for example, media management systems have metadata servers that maintain metadata for a collection of media signals. The metadata server is responsible for responding to requests for metadata associated with media titles in its collection. In the event that a metadata server does not have metadata associated with a particular media title, it forwards the reference extracted from the media signal to a metadata router, which in turn, re-directs the request to the appropriate metadata server.
Owner:DIGIMARC CORP +1
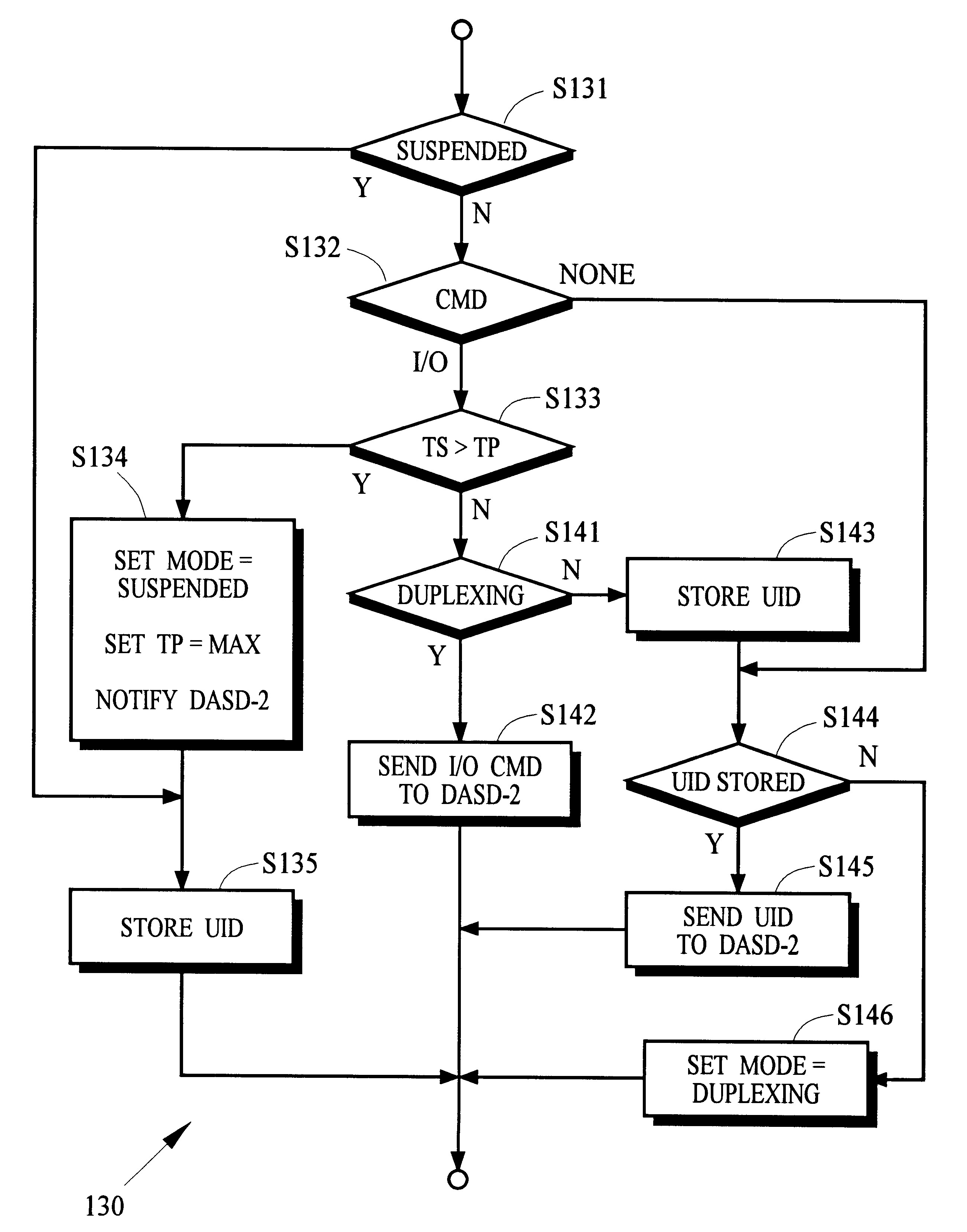
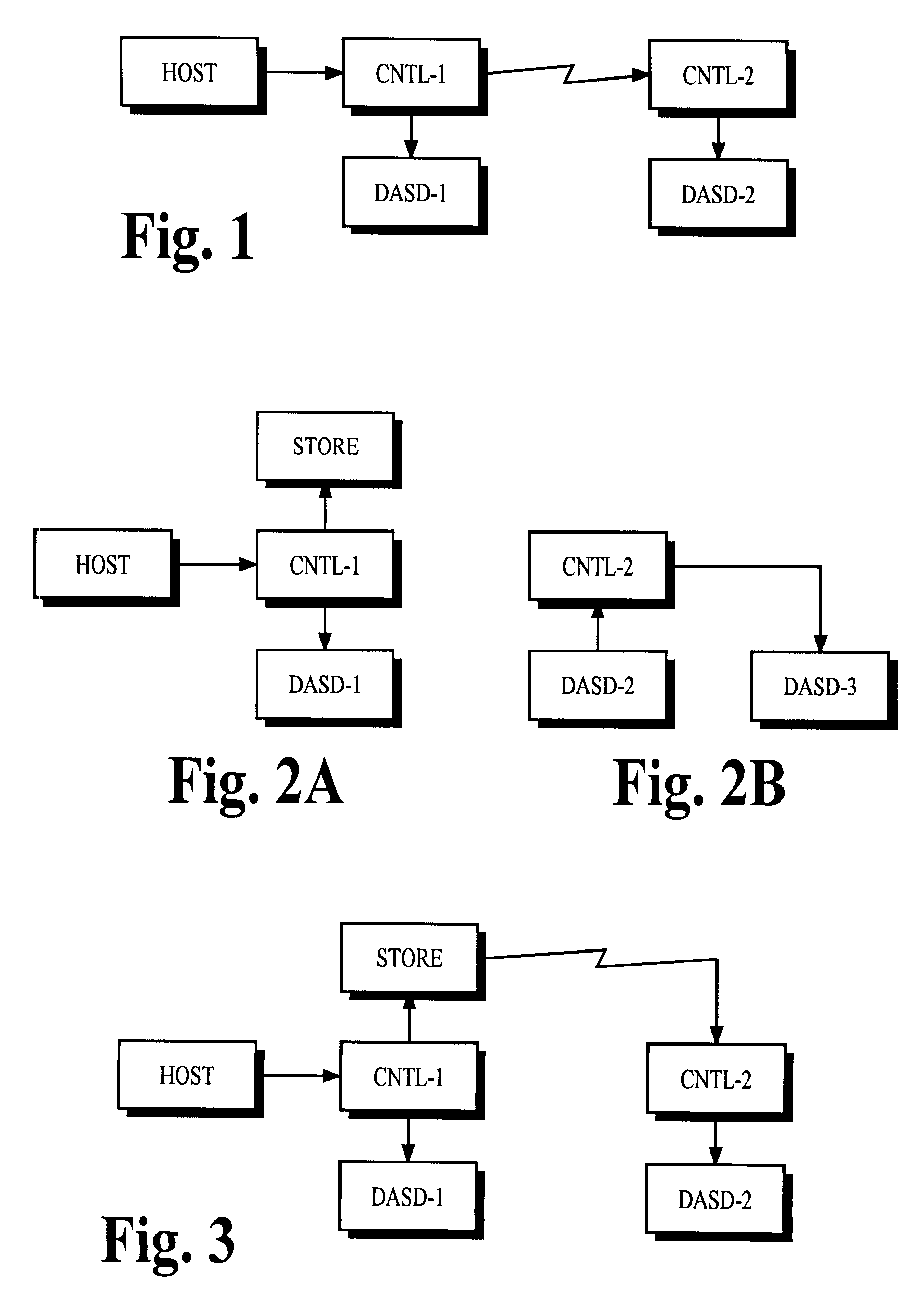
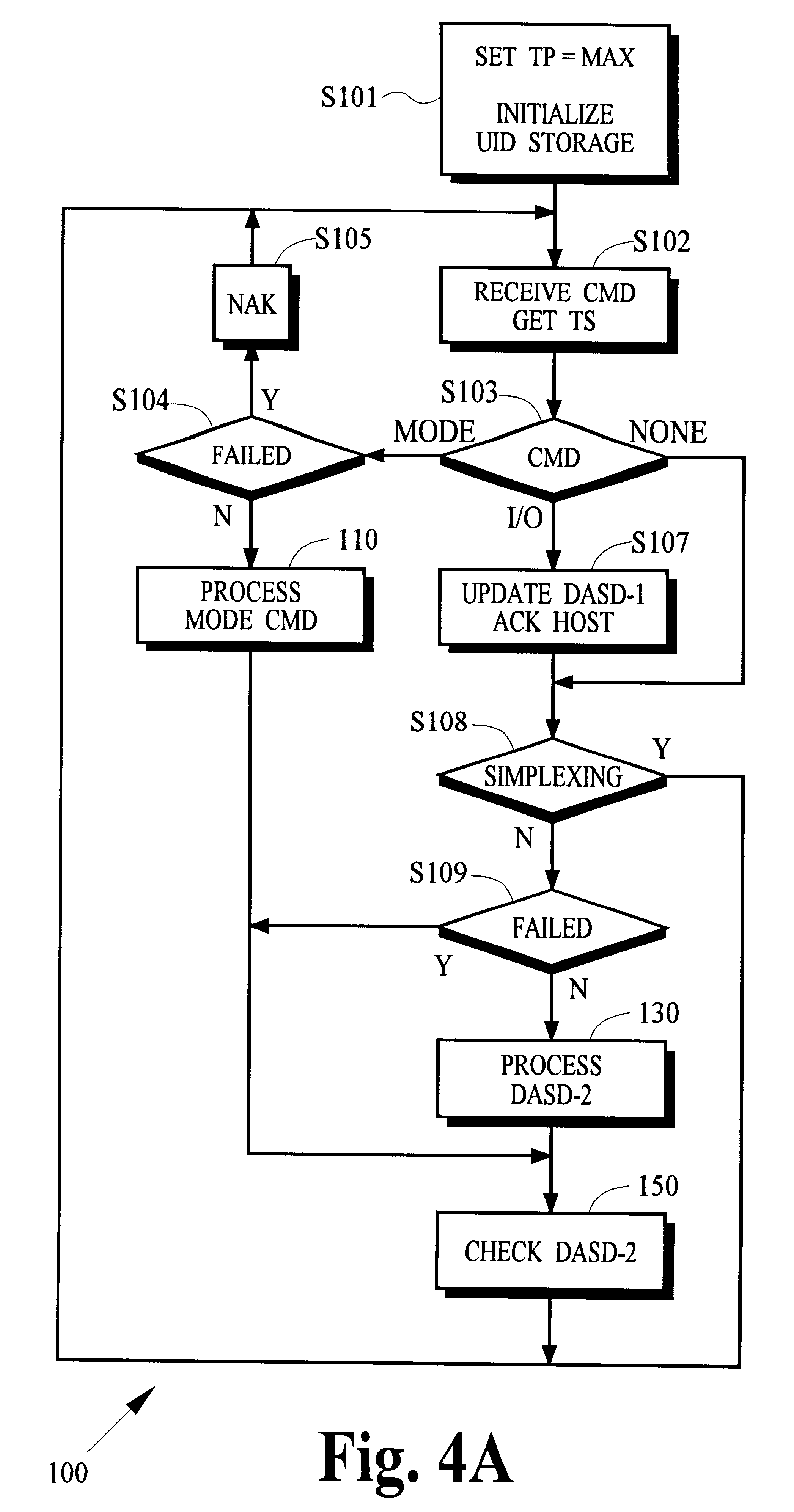
Remote data copy using a prospective suspend command
InactiveUS6539462B1Improve usabilityReducing resourceData processing applicationsInput/output to record carriersComputerized systemOperation mode
In a computer system, the controller of one or more primary data recording devices sends update information to the controller of one or more secondary data recording devices to maintain a remote copy of data stored on the primary data recording devices. The primary controller receives a command from a computer that specifies a prospective suspend time after which remote copy operation is to be suspended. After the suspend time passes, the primary controller stops sending the update information to the secondary controller and begins storing indicators of the updated information in cache memory. The primary controller may resume remote copy operation in response to a command received from the computer by first entering into a pending mode of operation in which cached indicators are used to identify update information that must be sent to the secondary controller to resynchronize the remote copy. When the information for all cached indicators has been sent, normal remote copy operation may be resumed.
Owner:HITACHI DATA SYST CORP
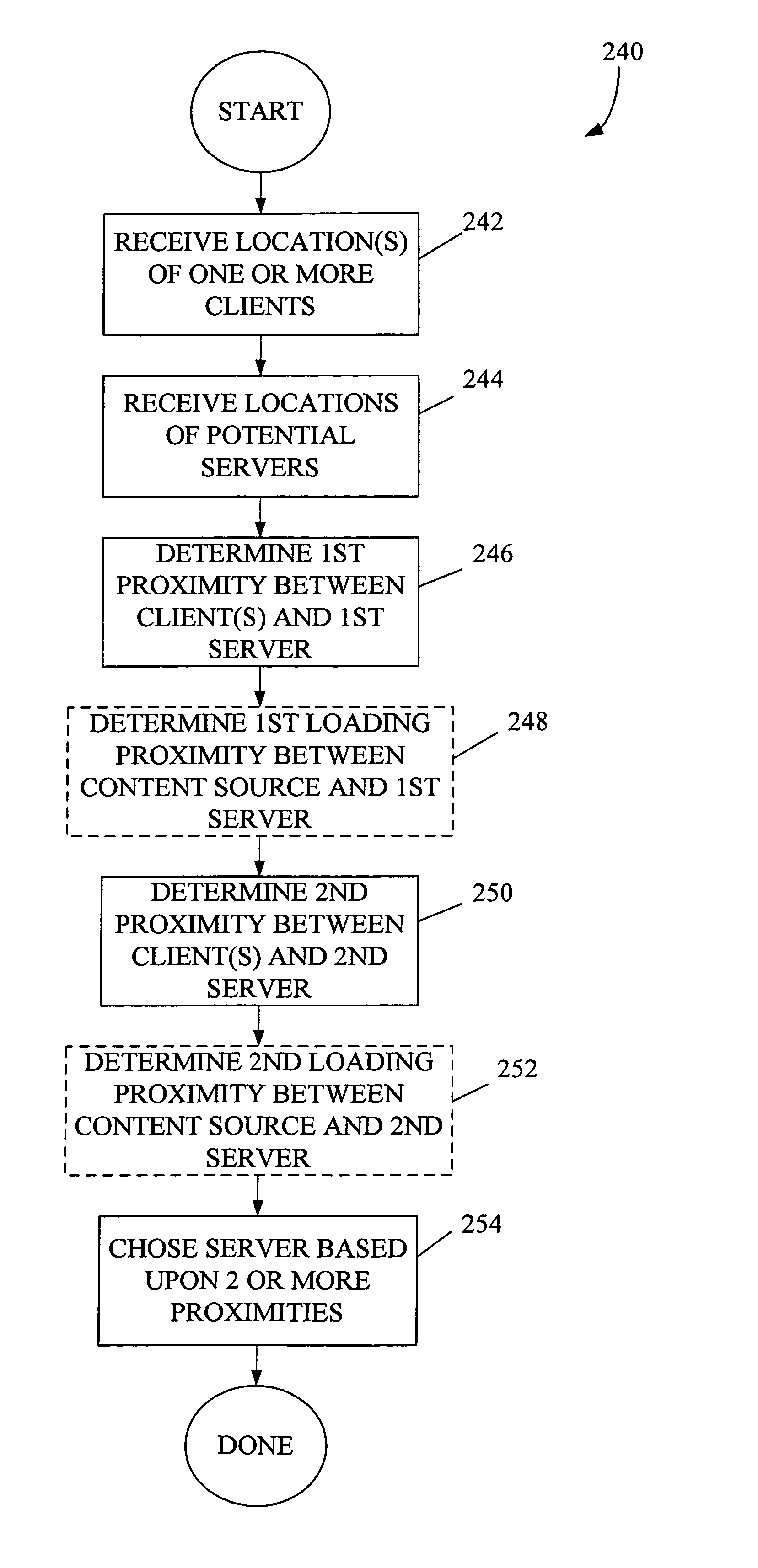
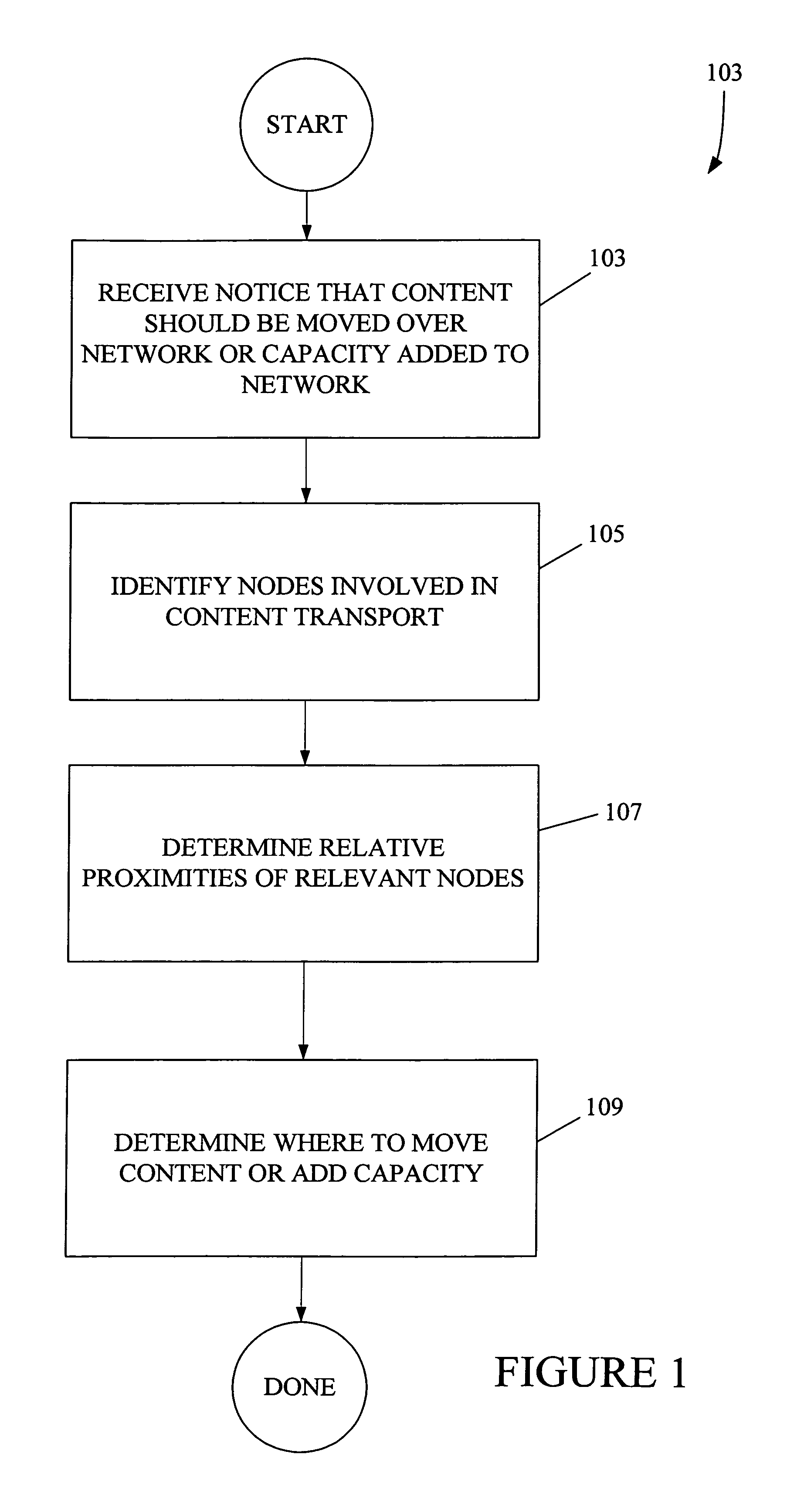
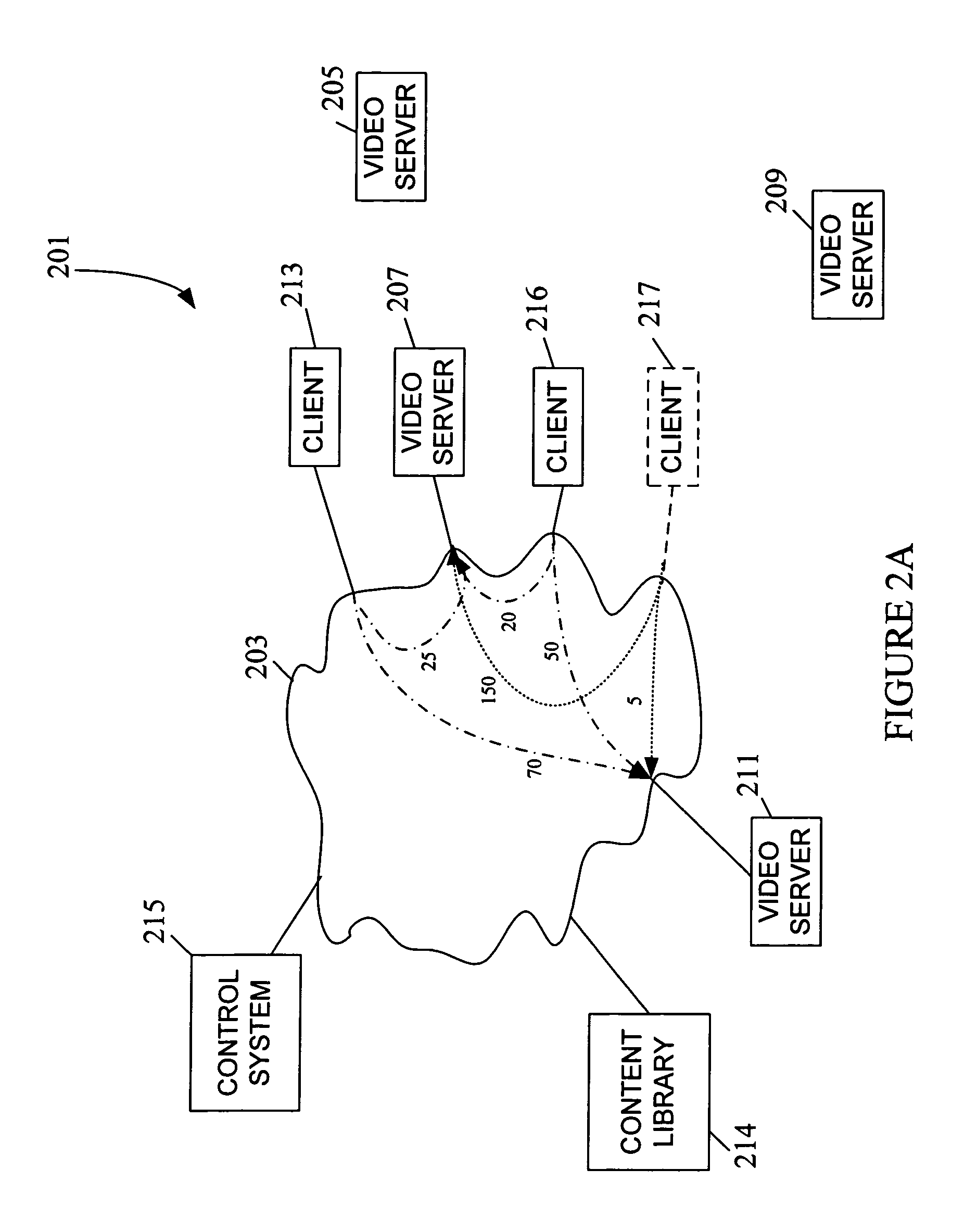
Proximity as an aid to caching and secondary serving of data
A proximity-based content control method “propagates” or positions content based upon “proximity” between various nodes on a network. The nodes between which the content is propagated include content libraries, servers, and clients. In one case, the relative proximities of two content servers to a particular client or group of clients determines which of these servers serves client requests. In another case, the method employs anticipatory loading of content from a library to a server based upon the server's proximity to a given client-base. Yet another application involves adding or removing server capacity to a network based upon proximity to clients. Another application applies proximity affects to cache release algorithms. A “content control system” calculates proximity dynamically and automatically decides whether to move content based upon the proximity calculation.
Owner:CISCO TECH INC
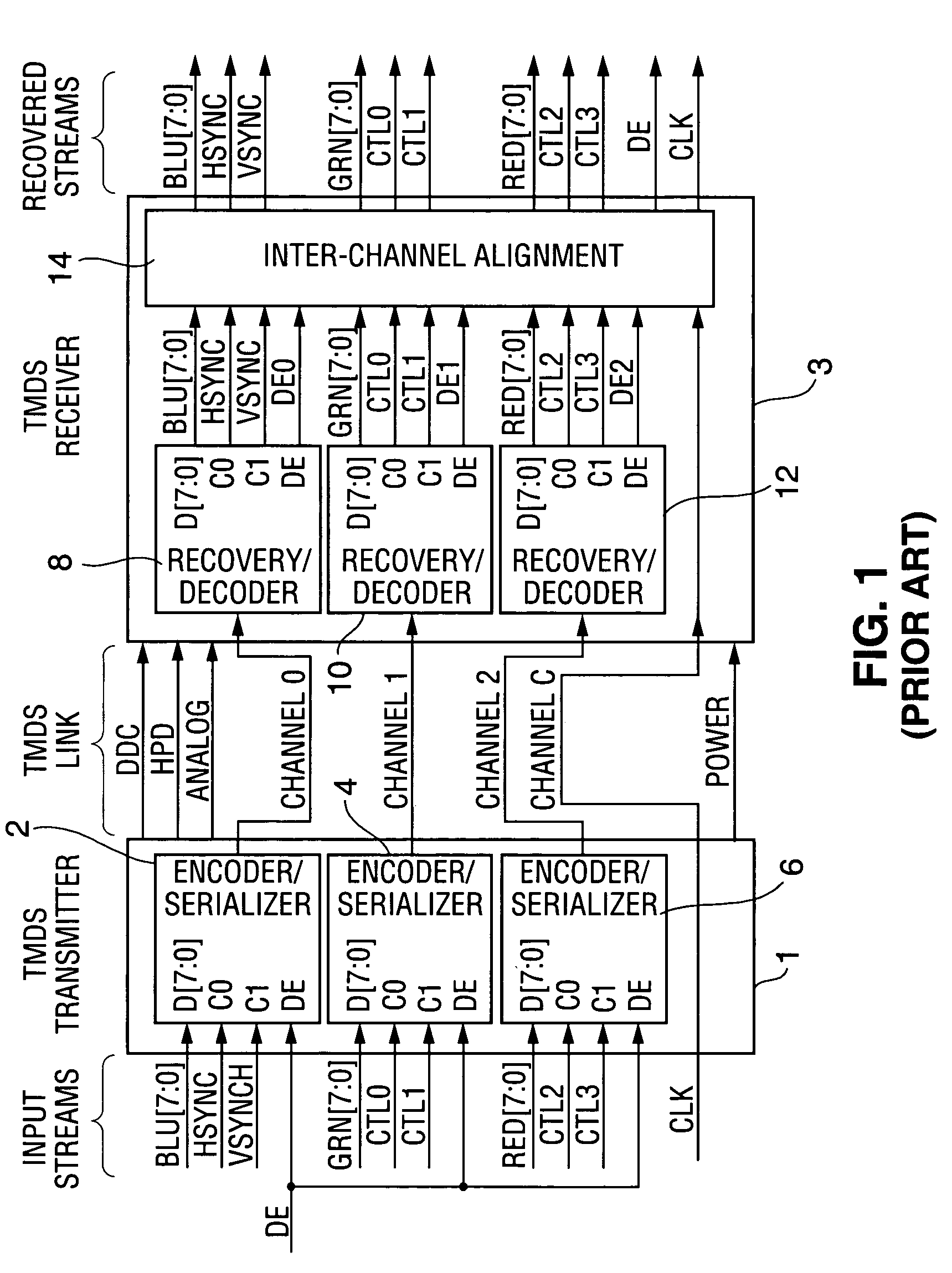
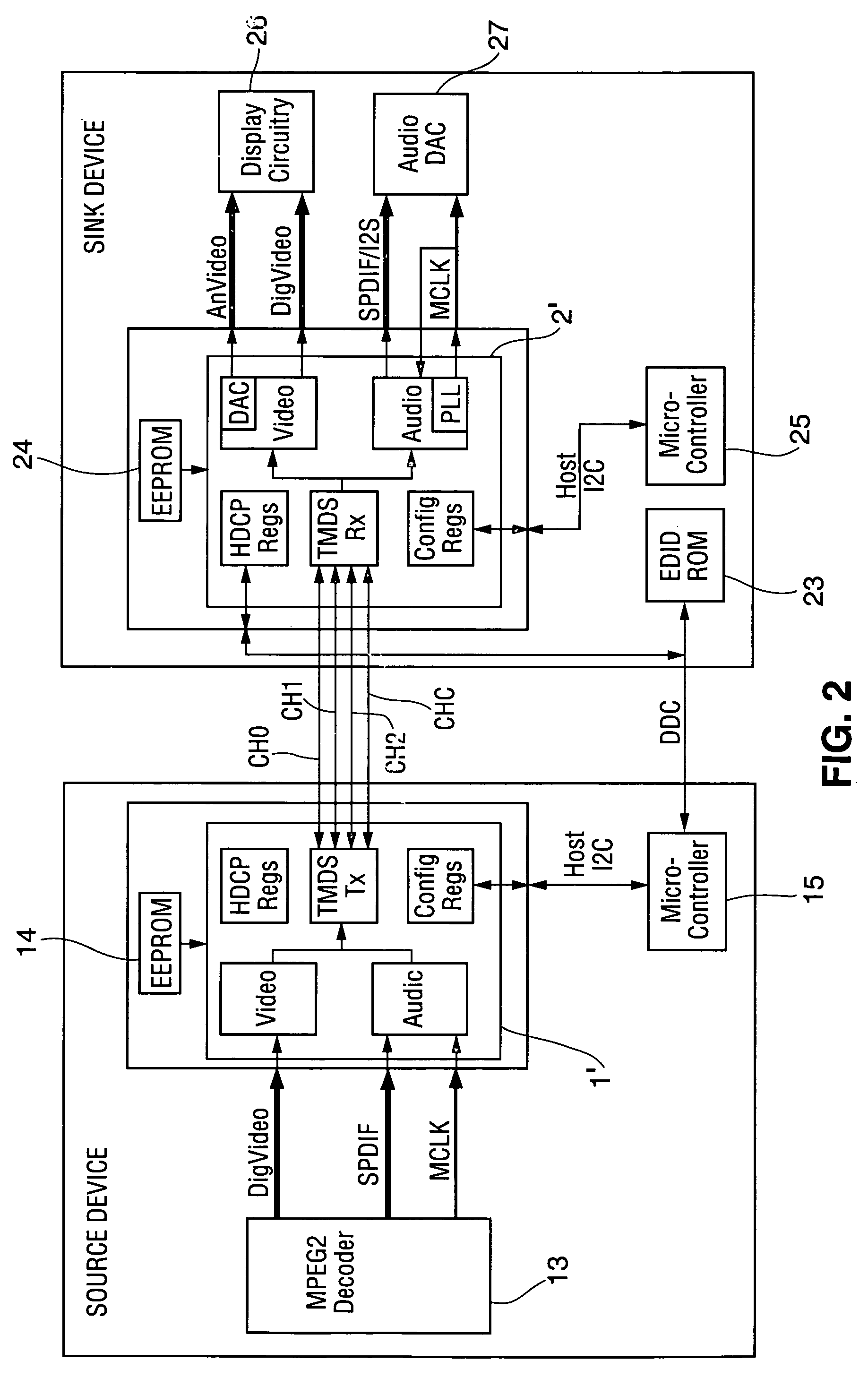
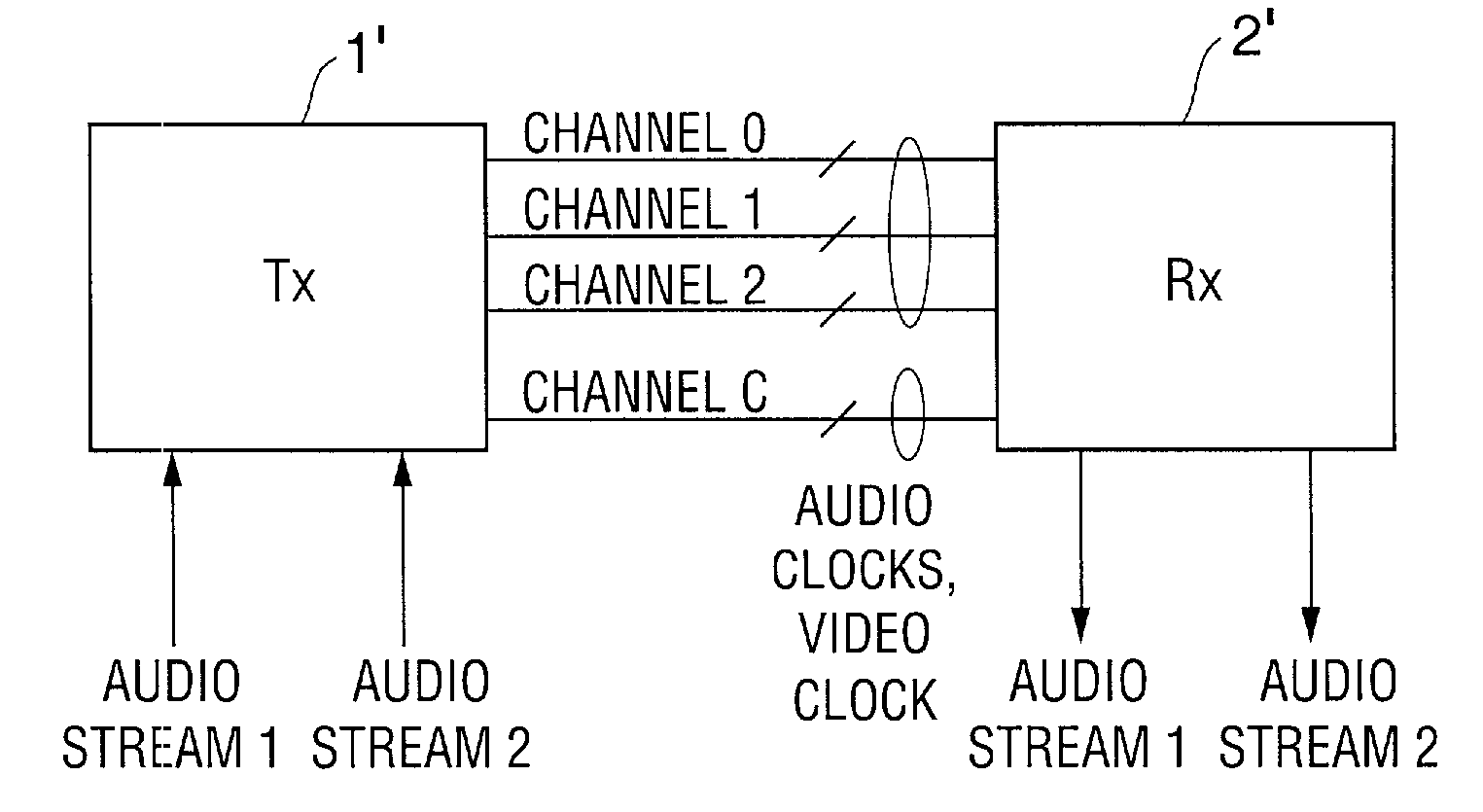
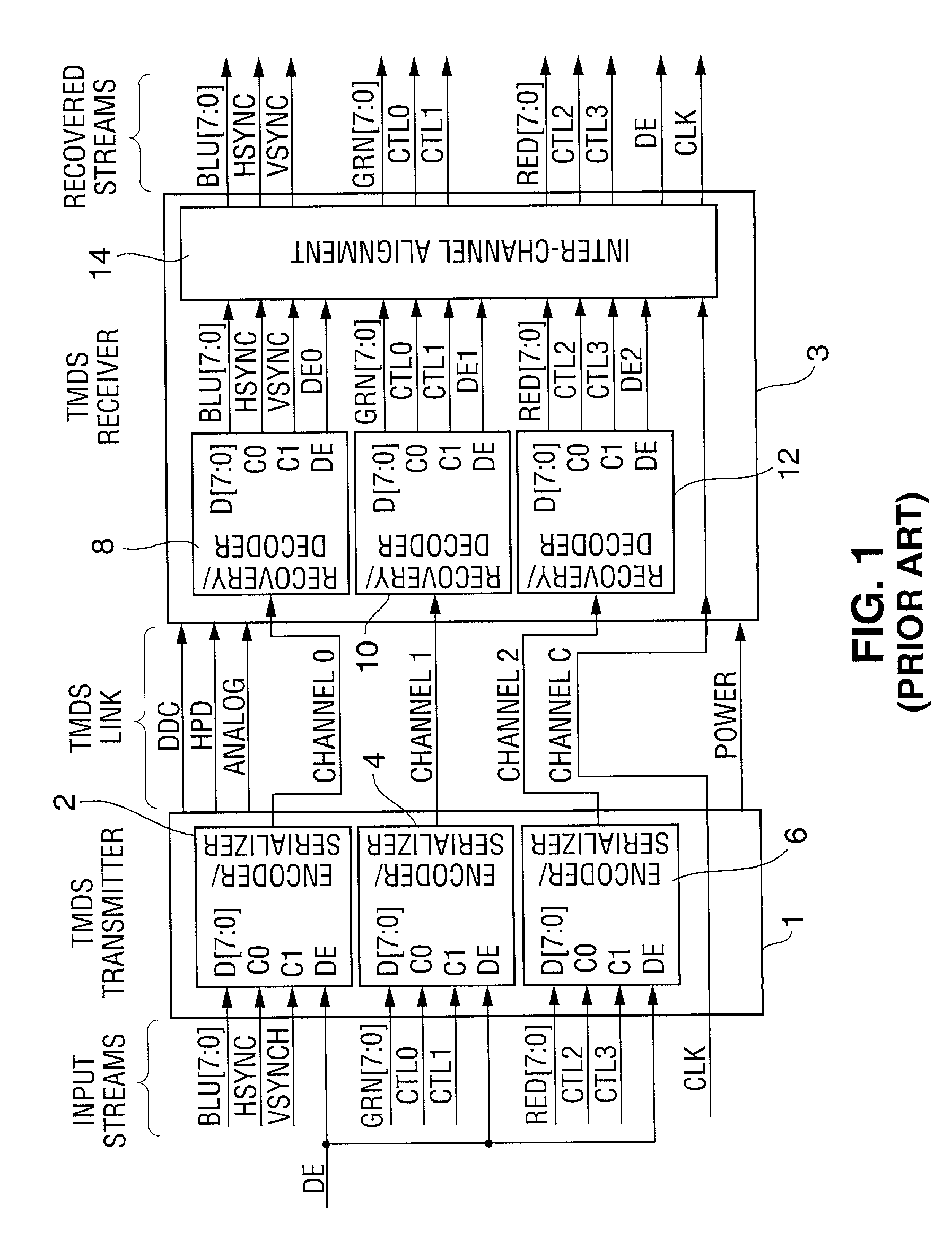
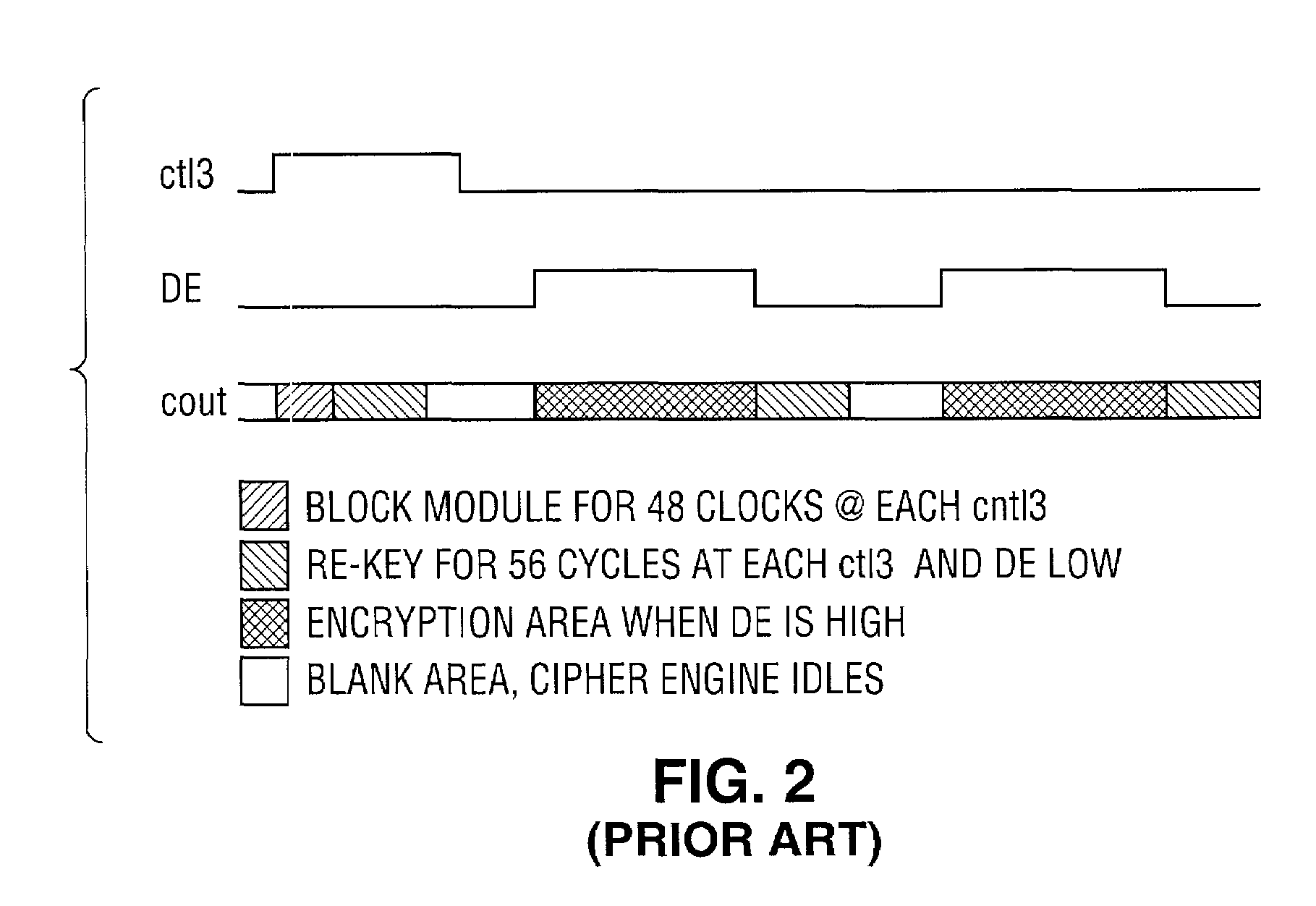
Method and apparatus for synchronizing auxiliary data and video data transmitted over a TMDS-like link
InactiveUS7295578B1Synchronisation information channelsPulse automatic controlData synchronizationCommunications system
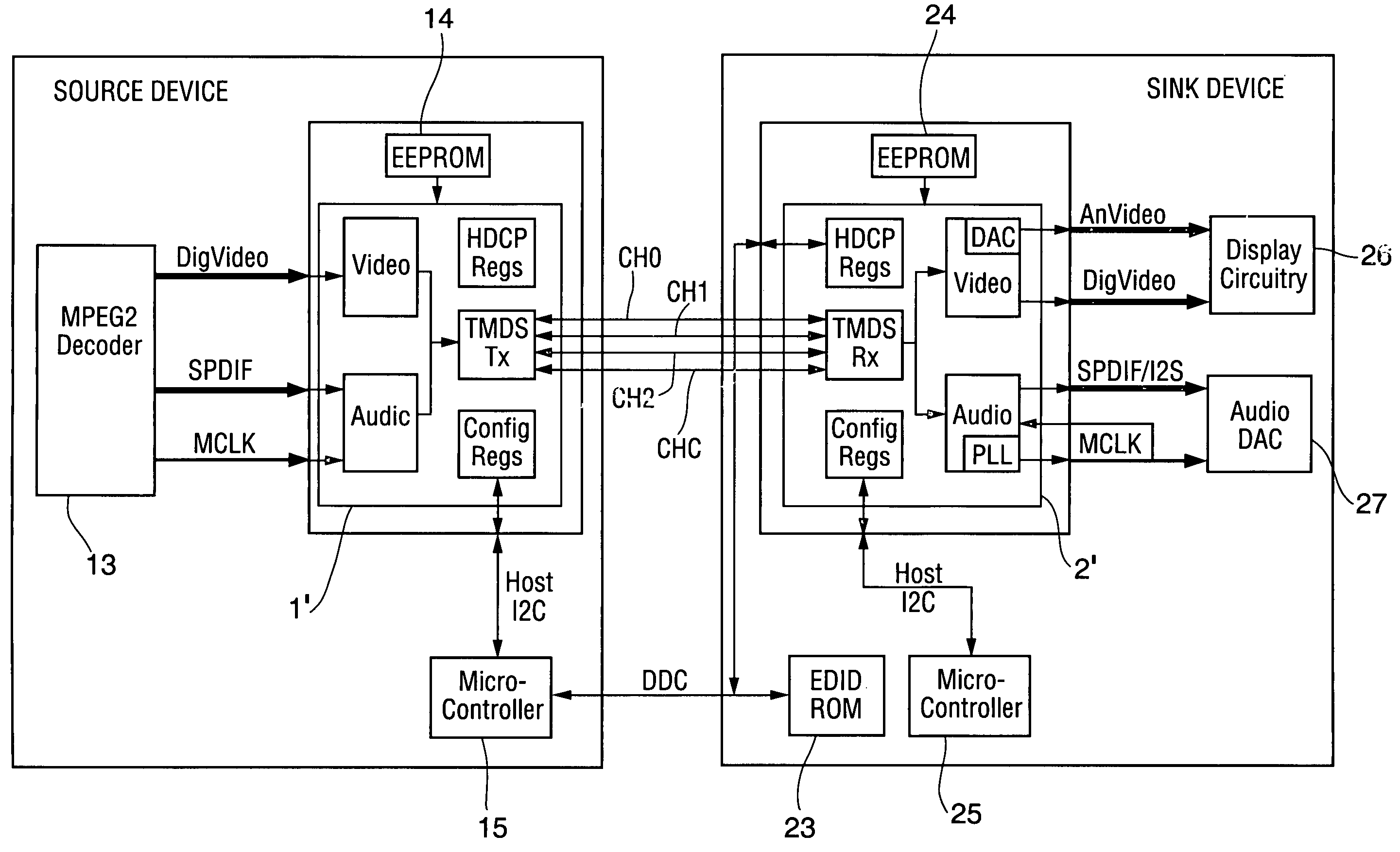
A communication system including a transmitter, a receiver, and a TMDS-like link, in which video data and auxiliary data are transmitted from the transmitter to the receiver, or in which video data are transmitted over the link from the transmitter to the receiver and auxiliary data are transmitted from the receiver to the transmitter (or from the transmitter to the receiver and also from receiver to the transmitter), a transmitter or receiver for use in such a system, and methods for sending auxiliary data and video data over such a link, synchronizing such auxiliary data with such video data, and generating clocks having frequency closely matching the rate at which the auxiliary data are transmitted. Typically, the auxiliary data include one or more streams of audio data. In some embodiments the transmitter transmits a video clock to the receiver over a video clock channel, at least one of the transmitter and receiver transmits at least one stream of auxiliary data to the other one of the transmitter and the receiver, and at least one of the transmitter and the receiver transmits over the video clock channel at least one auxiliary clock for the auxiliary data.
Owner:LATTICE SEMICON CORP
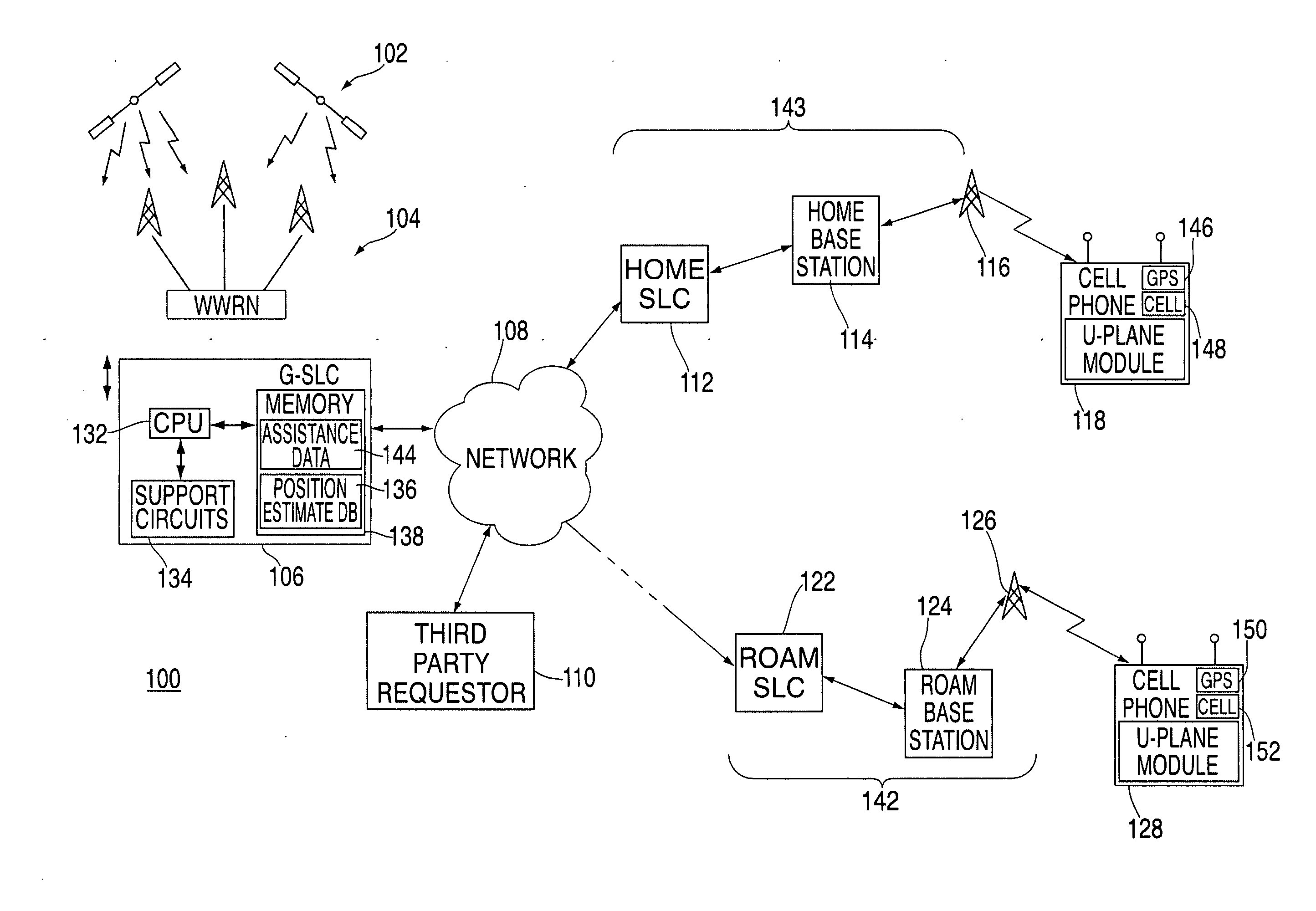
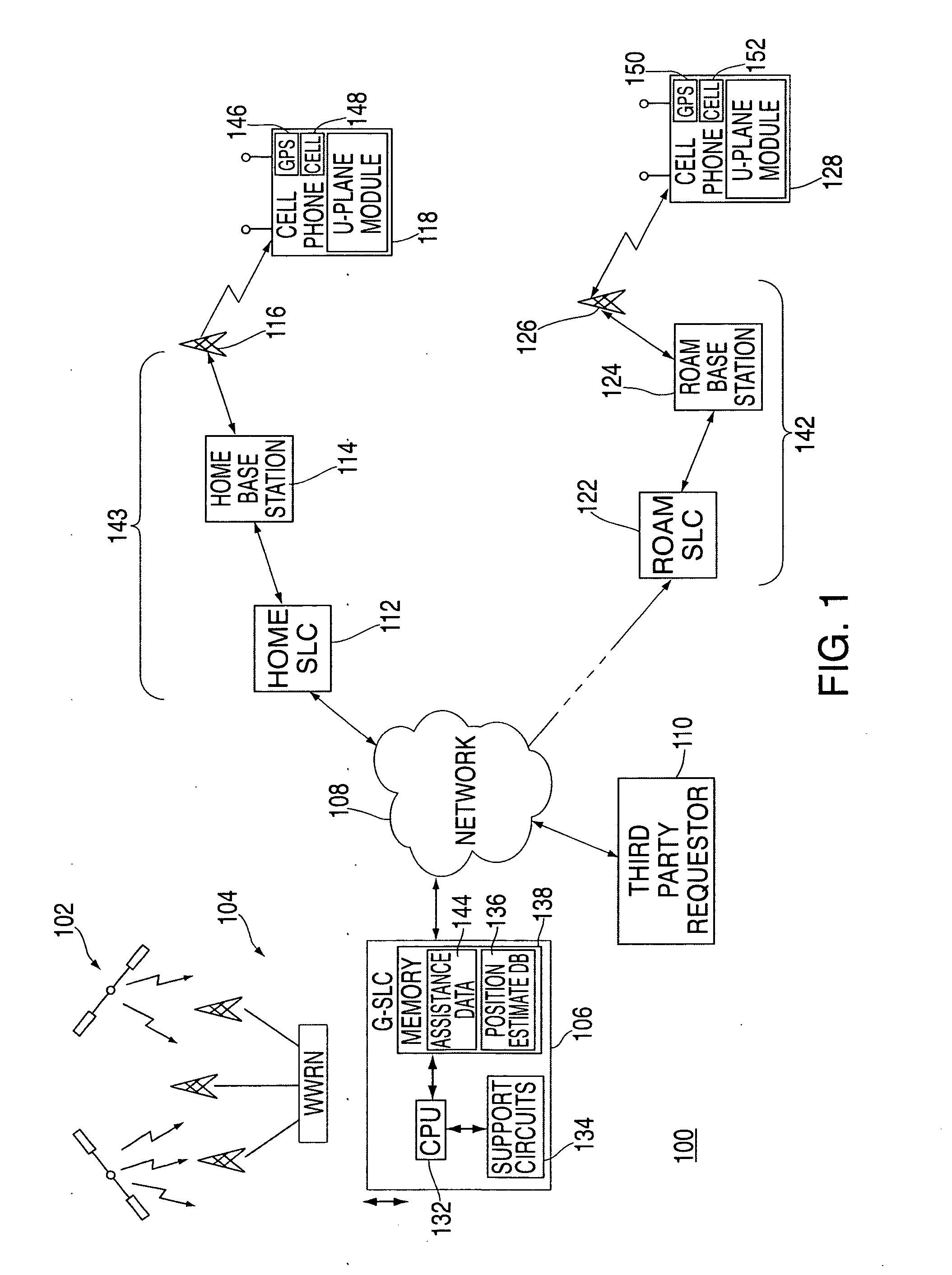
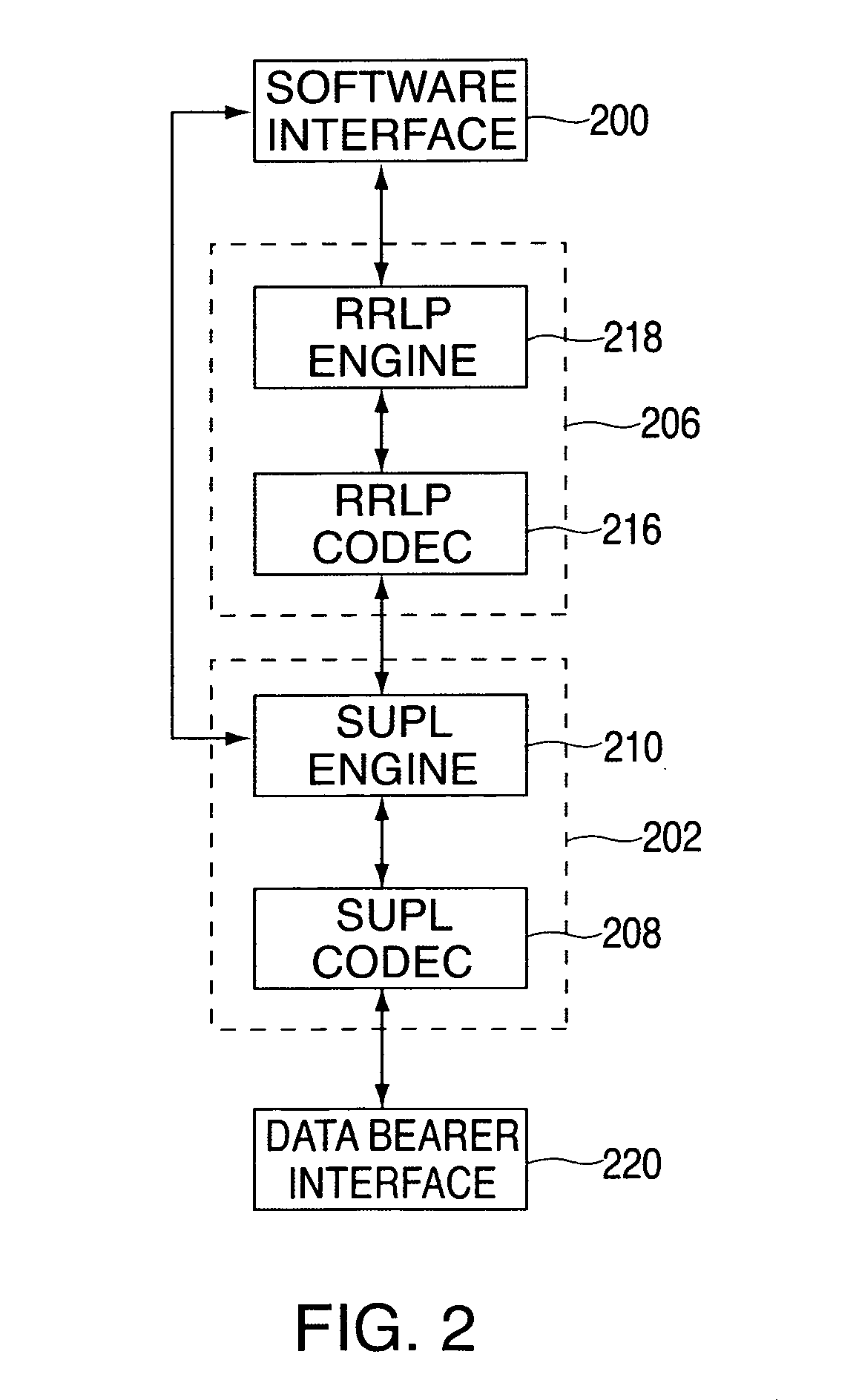
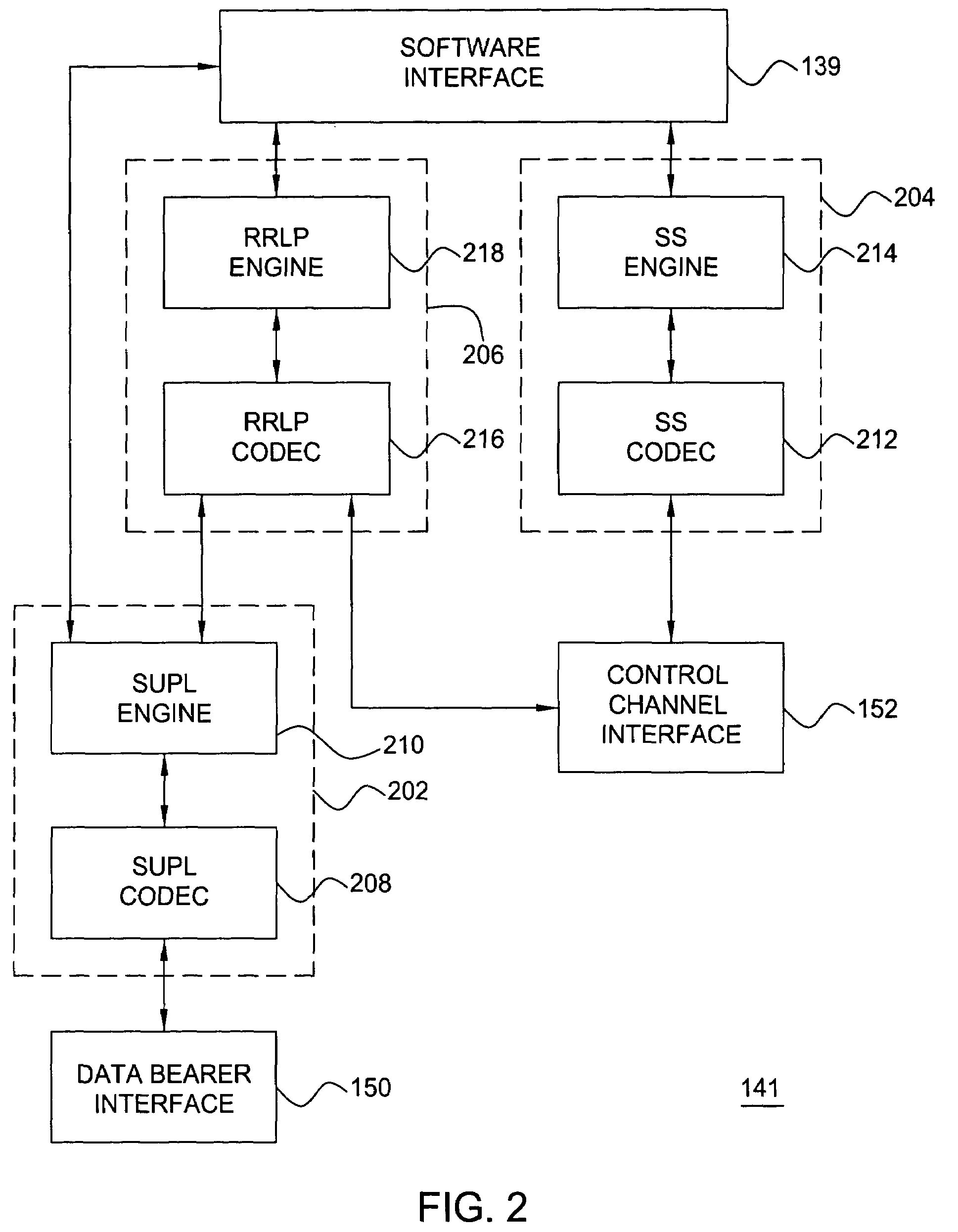
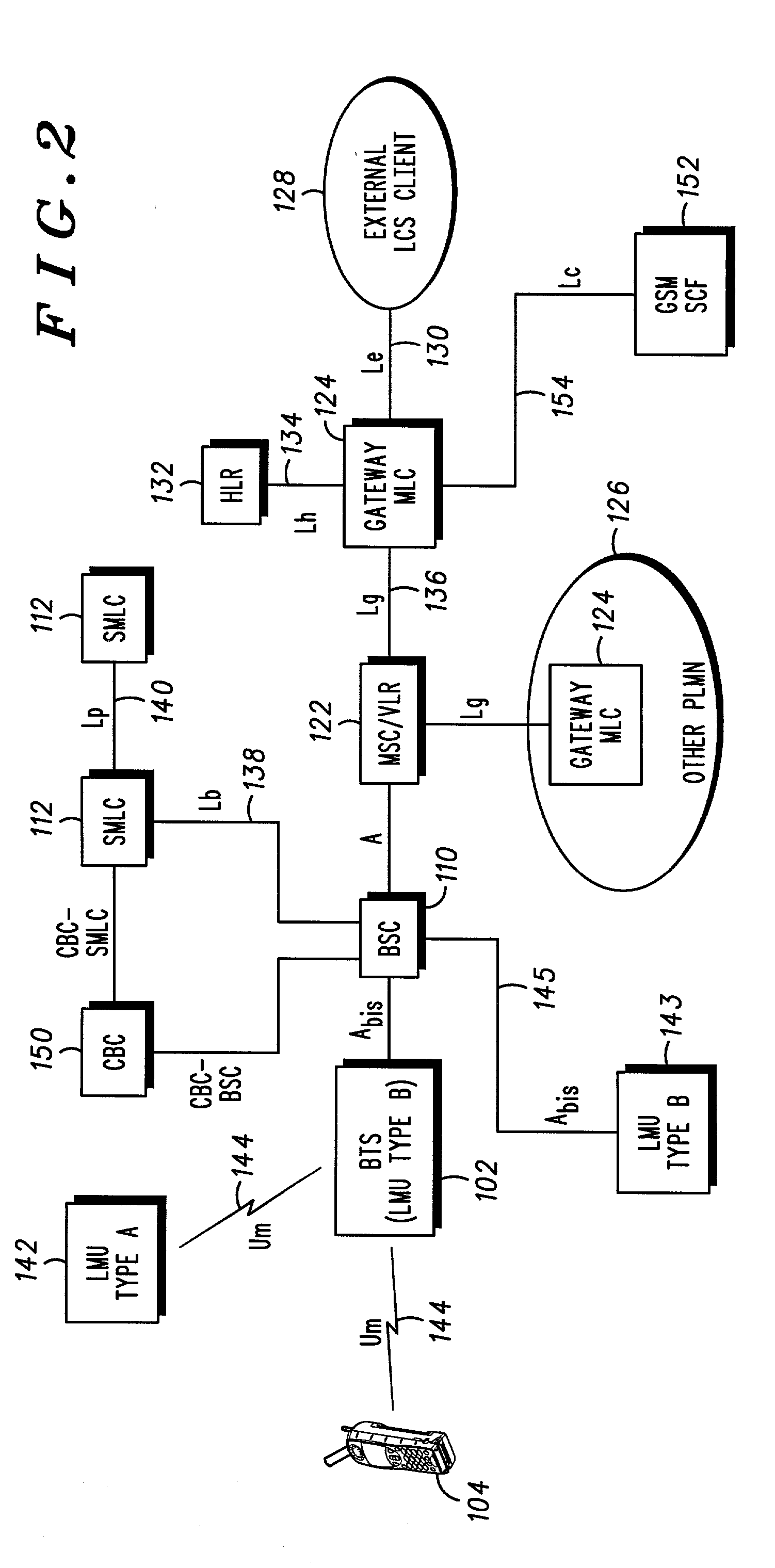
Method and apparatus for providing a global secure user plane location (SUPL) service
InactiveUS20070096981A1Avoid chargingPosition fixationServices signallingComputer networkSecure User Plane Location
A method and apparatus for providing assistance data for satellite positioning system receivers utilizing a secure user plane location (SUPL) service. In one embodiment, the assistance data is supplied by a global secure user plane location center that contains global assistance data.
Owner:AVAGO TECH INT SALES PTE LTD
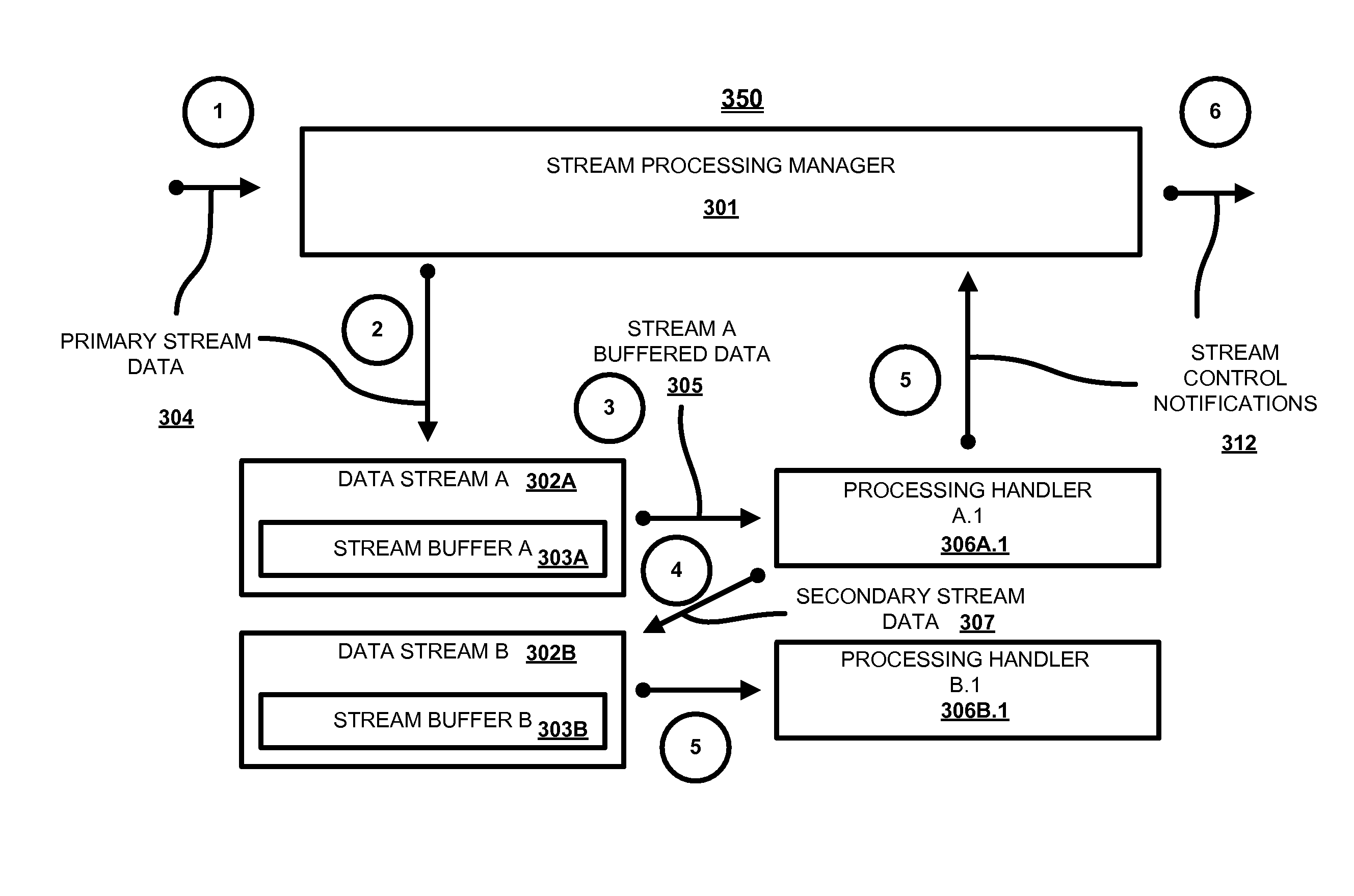
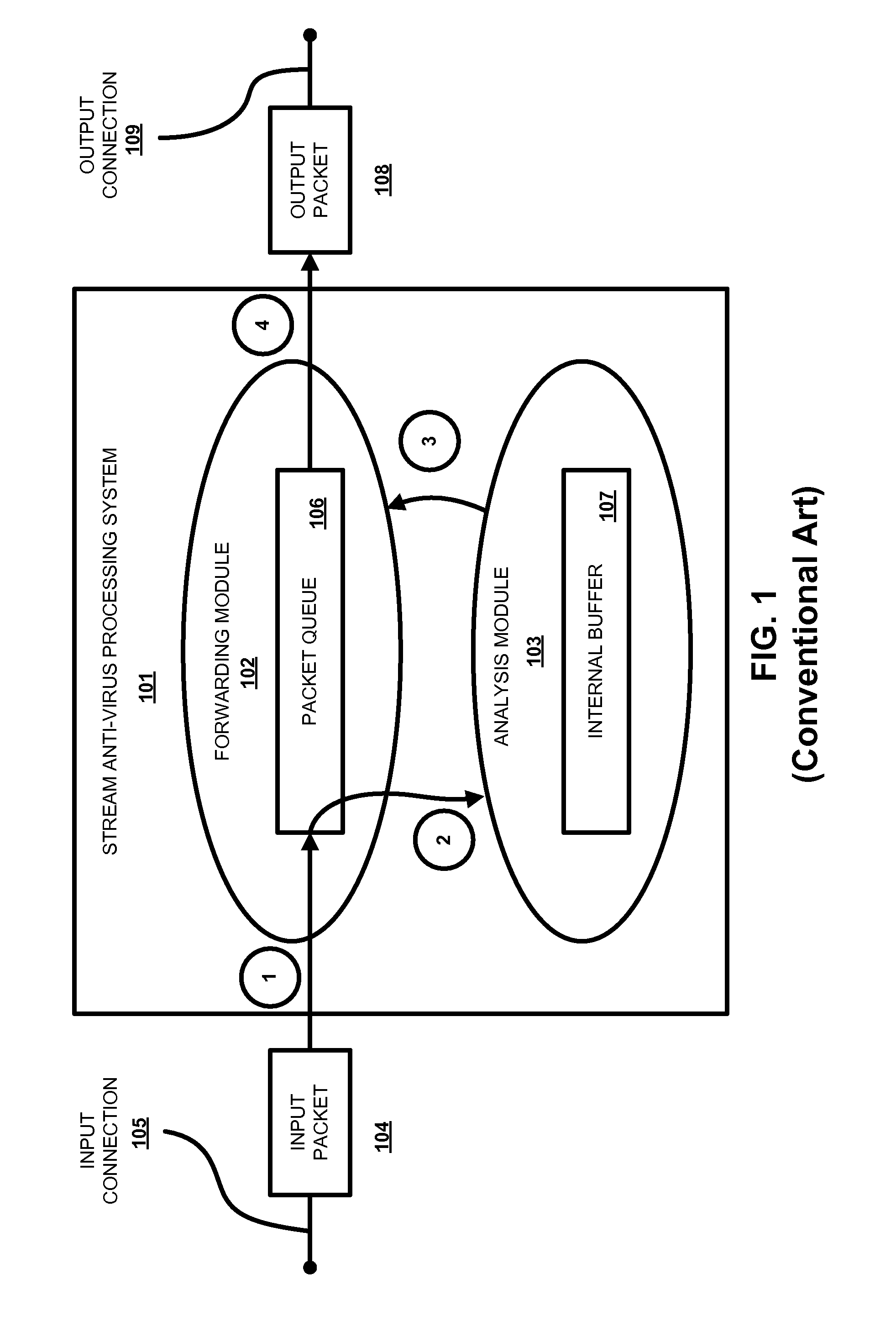
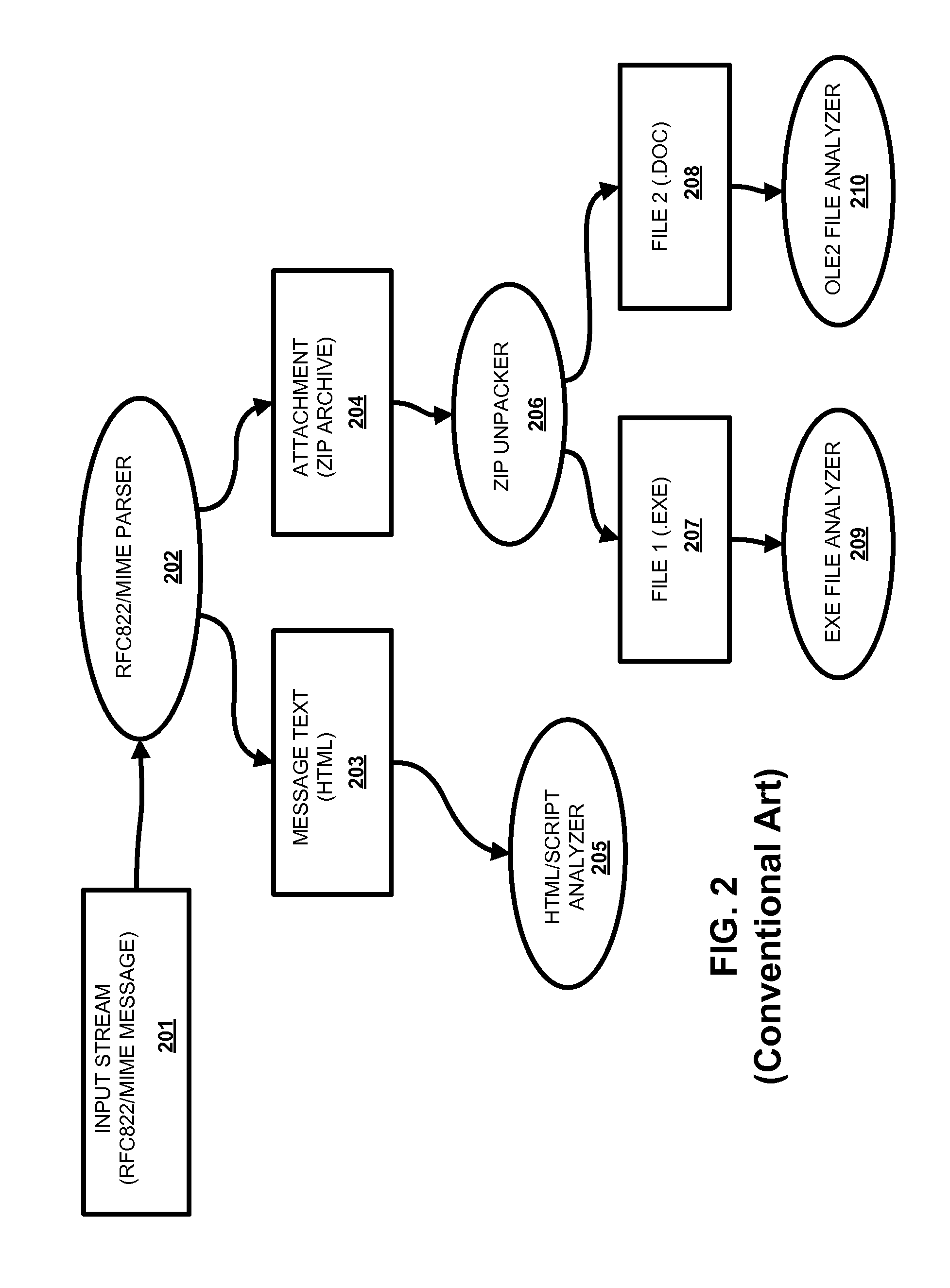
Rapid analysis of data stream for malware presence
ActiveUS8042184B1Quick analysisMemory loss protectionUnauthorized memory use protectionStreaming dataData stream
A system, method and computer program product for anti-malware processing of data stream that includes a plurality of logical data streams formed from a primary data stream; and a plurality of stream buffers, each buffering data of a corresponding logical data stream. A plurality of processing handlers each associated with one of the data streams, where the handlers are processing the data of the logical data stream buffered by its stream buffer. Each processing handler is associated with a particular functionality and at least one processing handler scans its logical data stream for malware presence. Each stream buffer has a configurable buffering policy. At least one of the processing handlers decompresses the data into one or more secondary streams. At least one of the processing handlers parses its logical data stream, creating one or more instances of secondary data streams. The scanning can be based on a signature search. At least one of the processing handlers parses its logical data stream to identify headers, wherein new secondary data streams are instantiated based on regions of interest in a future stream data at positions identified by the headers. The set of conditions is stored e.g., in a table, a list, and / or a registry.
Owner:KASPERSKY LAB ZAO
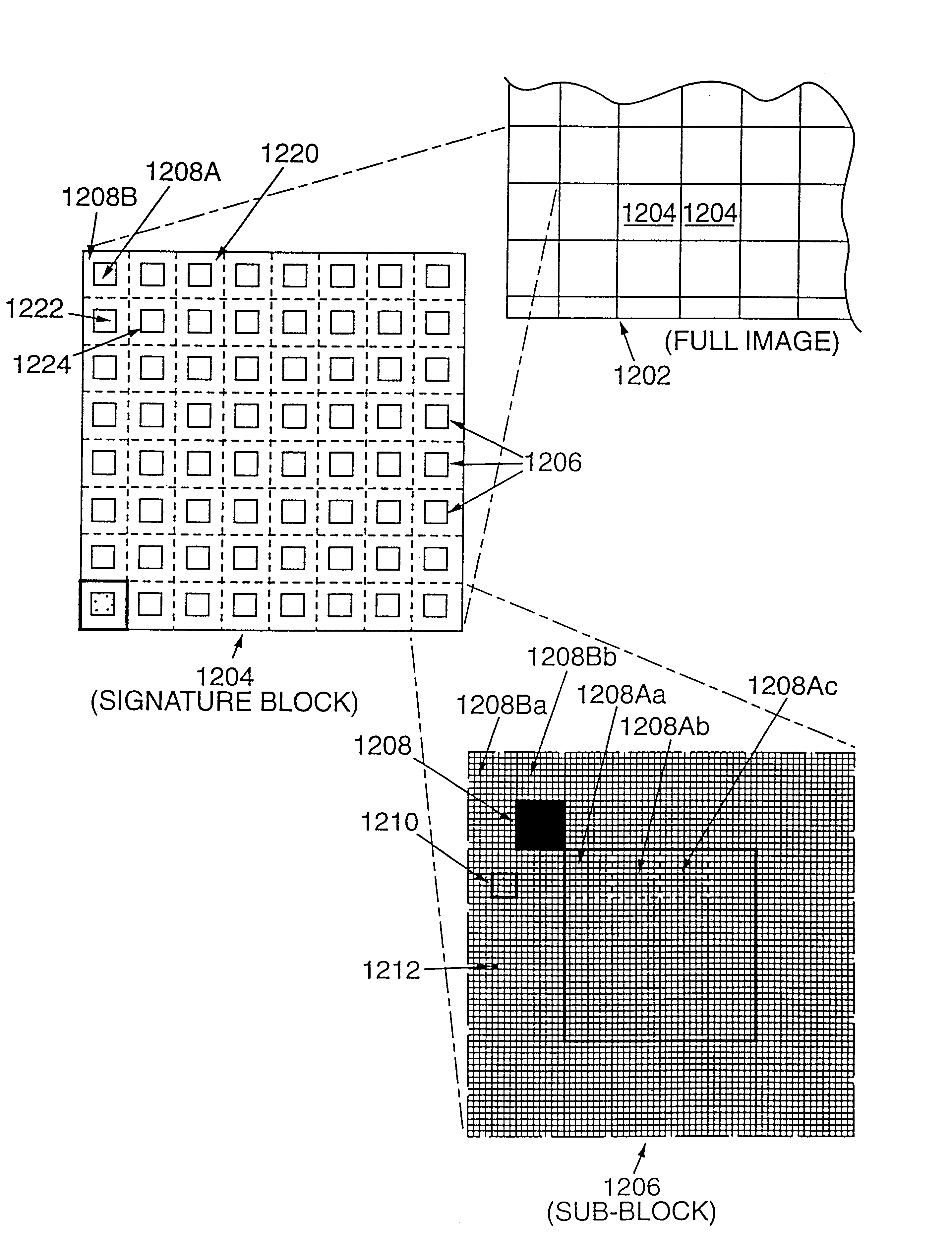
Tile-based digital watermarking techniques
InactiveUS6879701B1Television system detailsCoin-freed apparatusComputer graphics (images)Digital image
A tile-based arrangement is employed to effect watermarking of plural-bit auxiliary data into still or moving digital images. In a particular embodiment, the plural-bit auxiliary data is represented as a rectangular block of overlay data. This block is repetitively tiled, both vertically and horizontally, across the image, and combined with the image data to effect the encoding.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP)
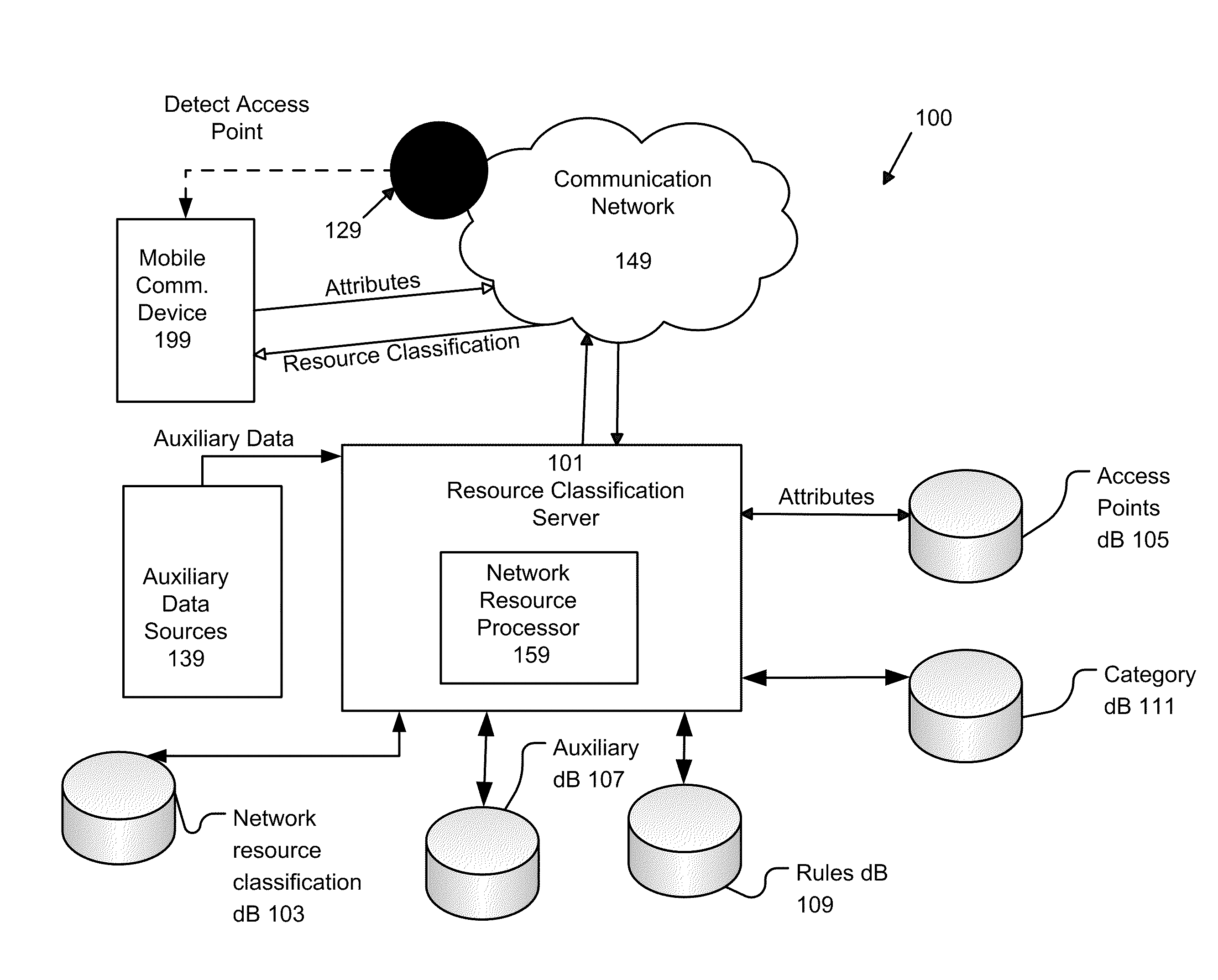
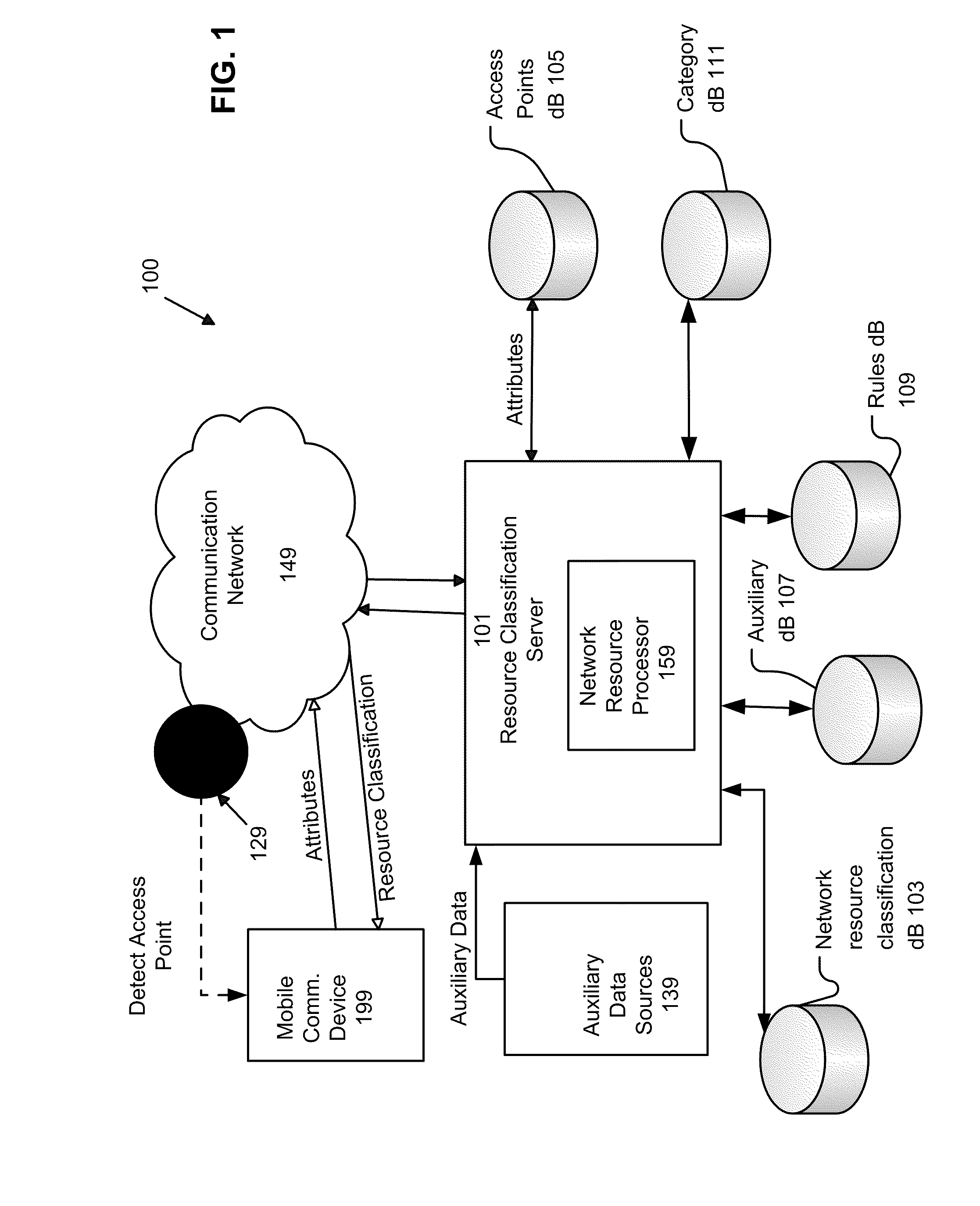
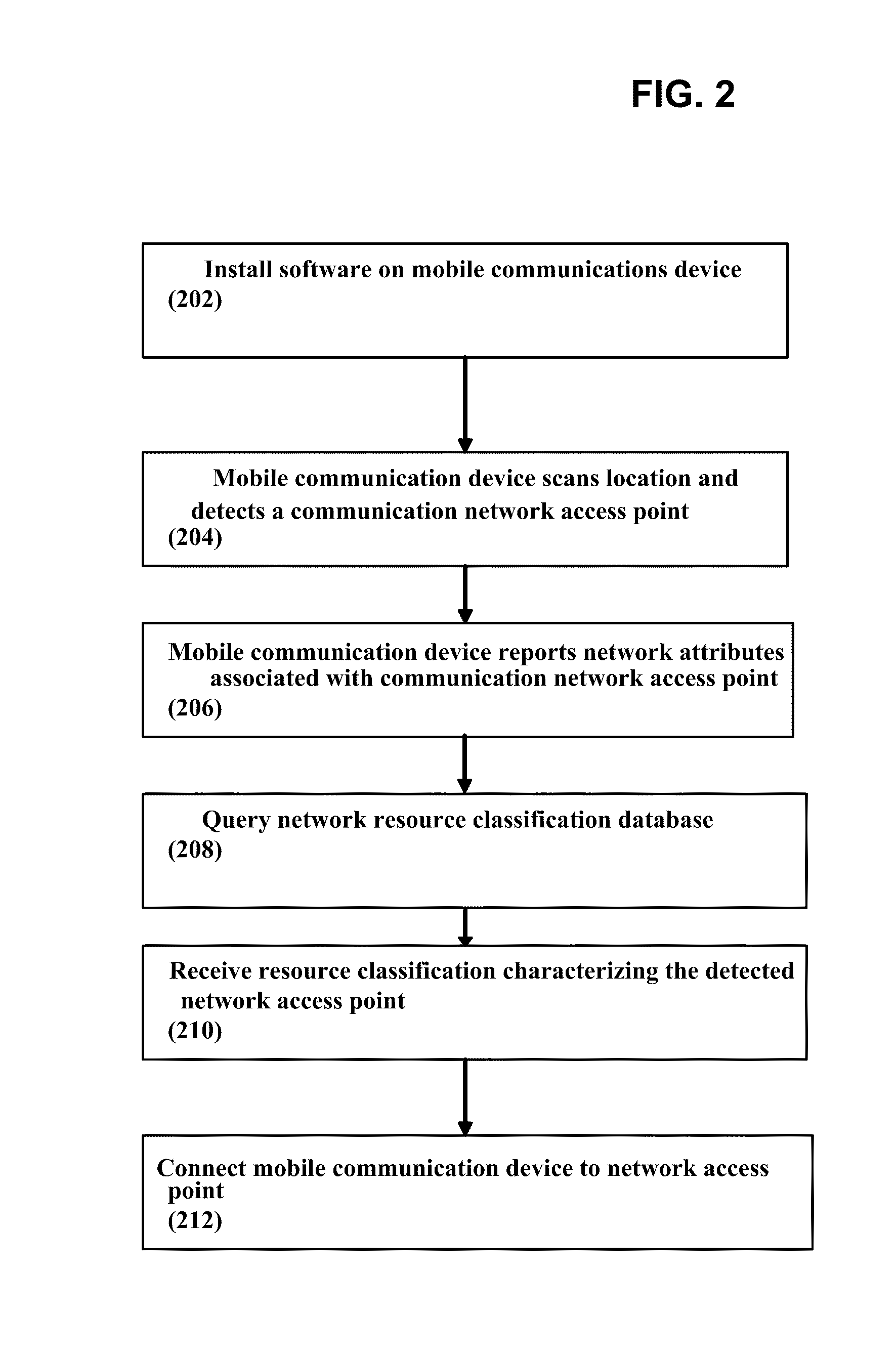
System and Method of Automatically Connecting a Mobile Communication Device to A Network Using a Communications Resource Database
ActiveUS20110159818A1Easy to useBridging the gapError preventionFrequency-division multiplex detailsNetwork access pointCommunication device
A system, method, and computer program product of automatically connecting a mobile communication device to a communication network using a network resource classification database includes detecting a communication network access point using the mobile communication device and reporting network attributes associated with the access point to a resource classification server. The server analyzes and stores the network attributes, determines auxiliary data related to the access point, and uses a rules database to determine a category identifier associated with the access point. The server creates a resource classification characterizing the access point based upon the network attributes, auxiliary data, and category identifier and the network attributes, auxiliary data, and / or category identifier data of other access points. The mobile communication device queries the server, receives a resource classification, and connects to an access point based upon the received resource classification.
Owner:WEFI
Remote data mirroring
InactiveUS20060005074A1Low costLess manpowerInput/output to record carriersData processing applicationsSelf adaptiveData store
Two data storage systems are interconnected by a data link for remote mirroring of data. Each volume of data is configured as local, primary in a remotely mirrored volume pair, or secondary in a remotely mirrored volume pair. Normally, a host computer directly accesses either a local or a primary volume, and data written to a primary volume is automatically sent over the link to a corresponding secondary volume. Each remotely mirrored volume pair can operate in a selected synchronization mode including synchronous, semi-synchronous, adaptive copy-remote write pending, and adaptive copy-disk. Direct write access to a secondary volume is denied if a “sync required” attribute is set for the volume and the volume is not synchronized.
Owner:EMC CORP
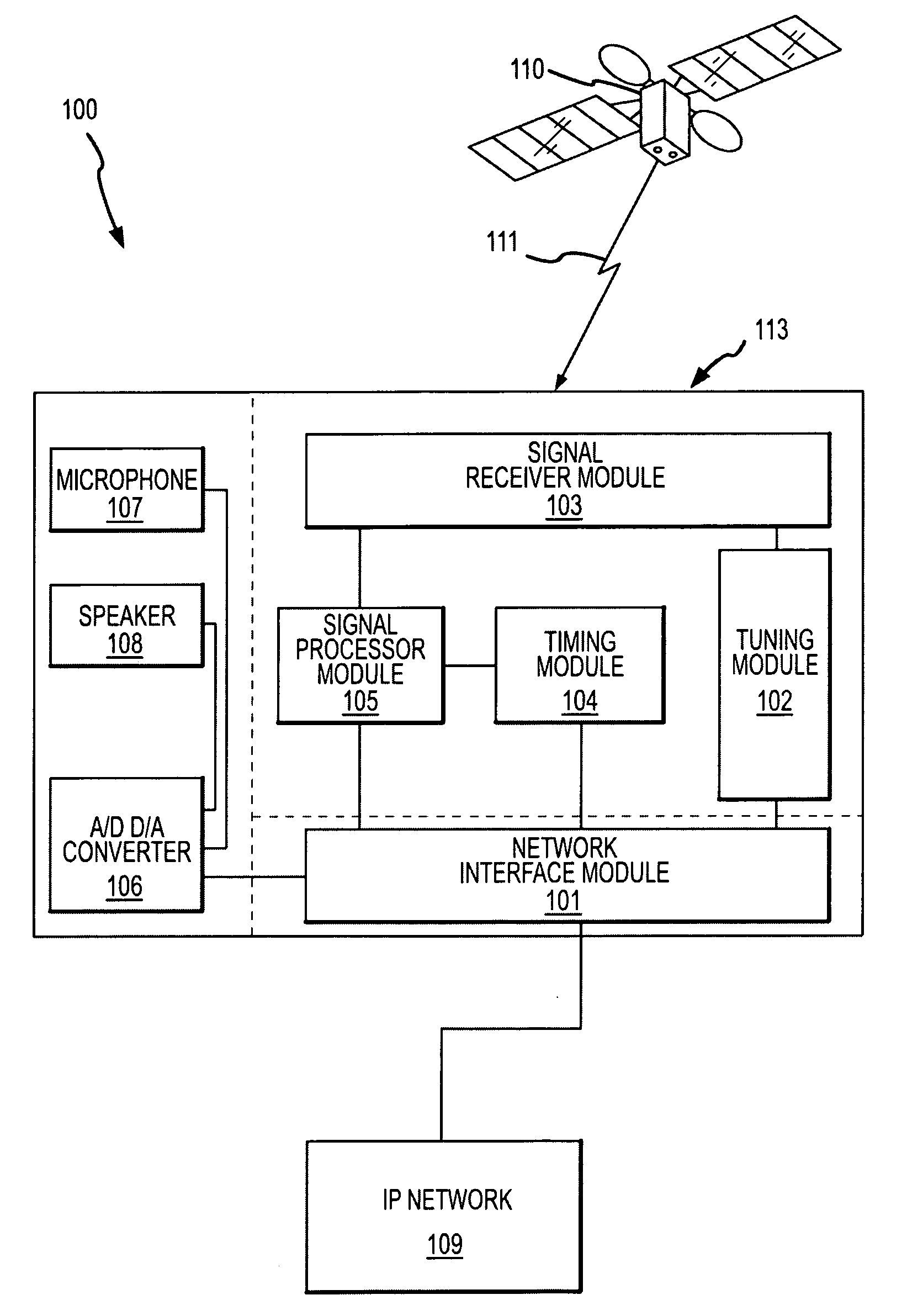
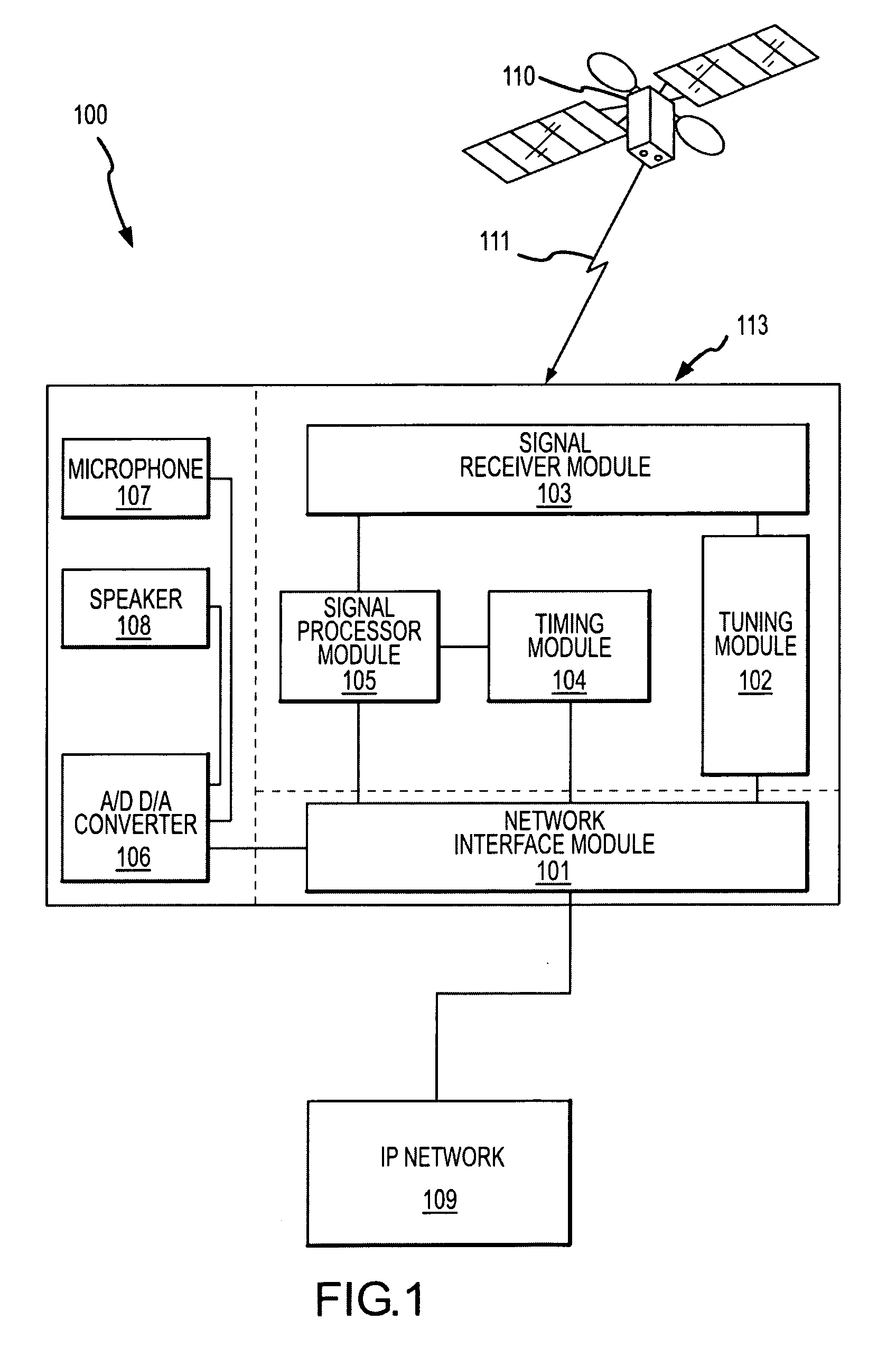
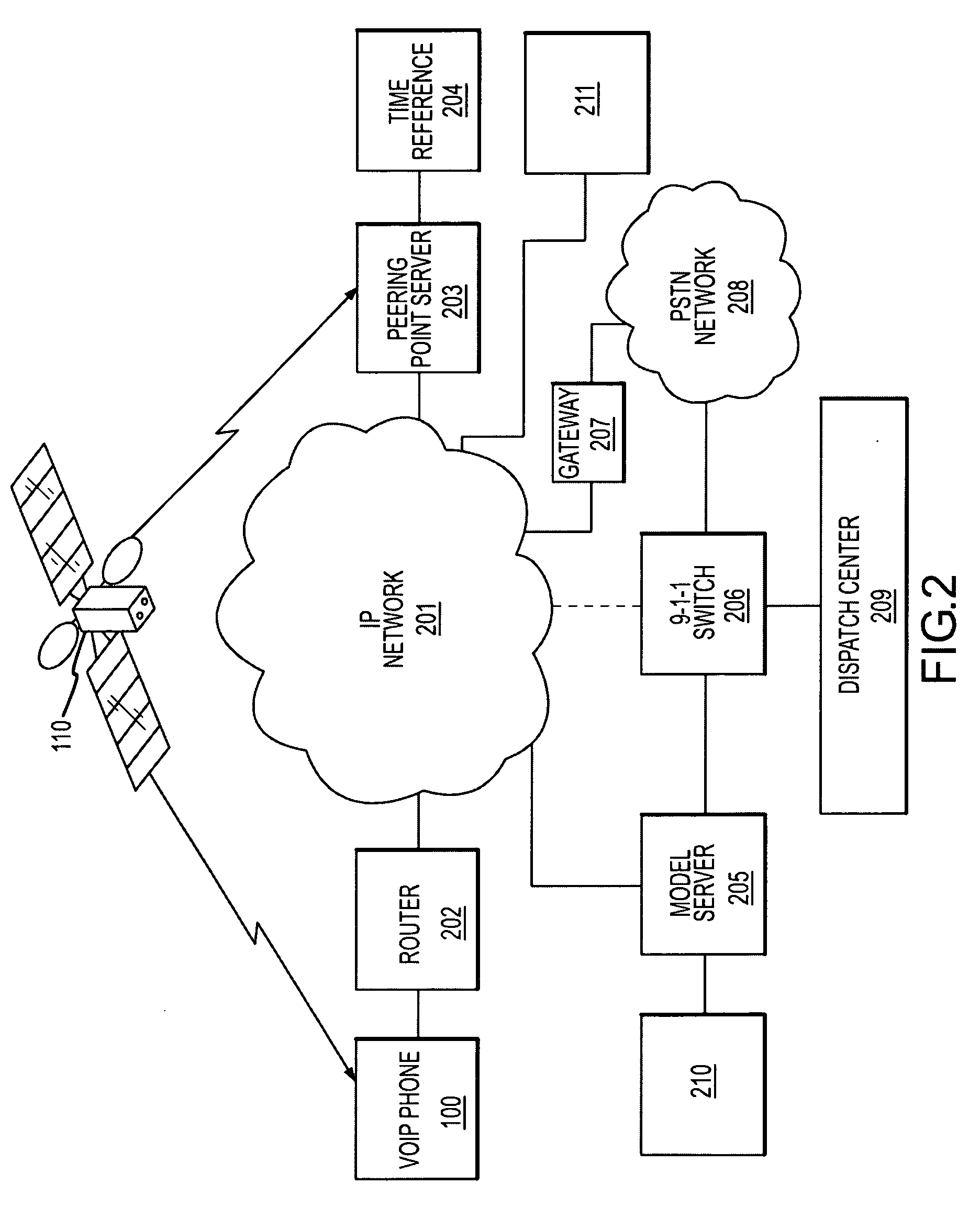
System and methods for IP and VoIP device location determination
ActiveUS20070030841A1Easy to movePrecise positioningPosition fixationData switching by path configurationGeolocationStandard methods
A method and system for precise position determination of general Internet Protocol (IP) network-connected devices. A method enables use of remote intelligence located at strategic network points to distribute relevant assistance data to IP devices with embedded receivers. Assistance is tailored to provide physical timing, frequency and real time signal status data using general broad band communication protocols. Relevant assistance data enables several complementary forms of signal processing gain critical to acquire and measure weakened or distorted in-building Global Navigation Satellite Services (GNSS) signals and to ultimately extract corresponding pseudo-range time components. A method to assemble sets of GNSS measurements that are observed over long periods of time while using standard satellite navigation methods, and once compiled, convert using standard methods each pseudo-range into usable path distances used to calculate a precise geographic position to a known degree of accuracy.
Owner:IPOSI
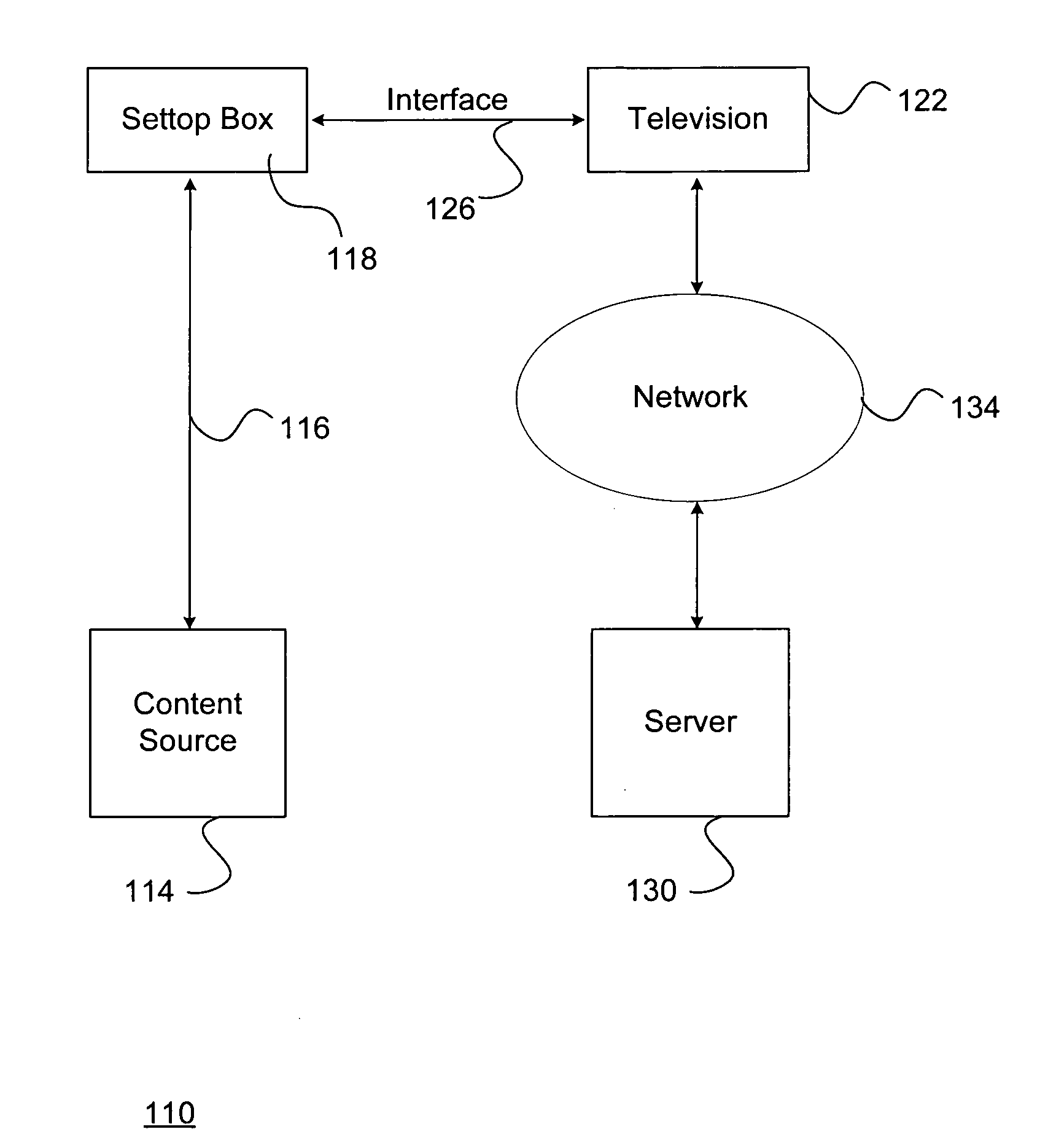
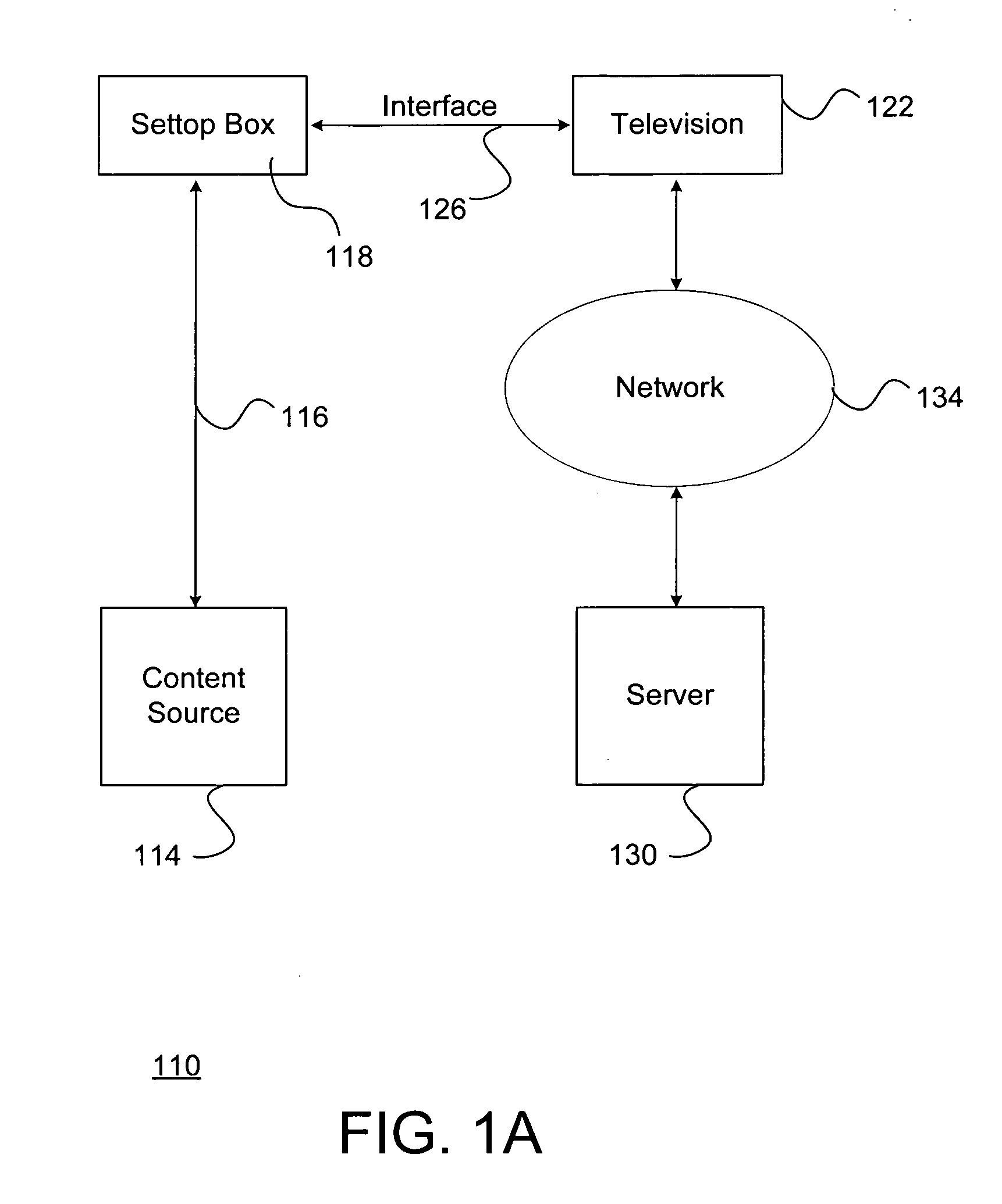
System and method for distributing auxiliary data embedded in video data
ActiveUS20110088075A1Television system detailsPicture reproducersMultiplexingComputer graphics (images)
A system and method for distributing auxiliary data embedded in video data includes a content source that embeds the auxiliary data into the video data. The content source then encodes the video data together with the auxiliary data to create a distribution multiplex including compressed video data. A decoder receives and decompresses the distribution multiplex to reproduce the video data with the auxiliary data embedded. A television or other device then detects and extracts the auxiliary data from the video data. The television or other device processes the auxiliary data to support a variety of possible interactive applications including displaying a synchronized widget on a display of the television.
Owner:SATURN LICENSING LLC
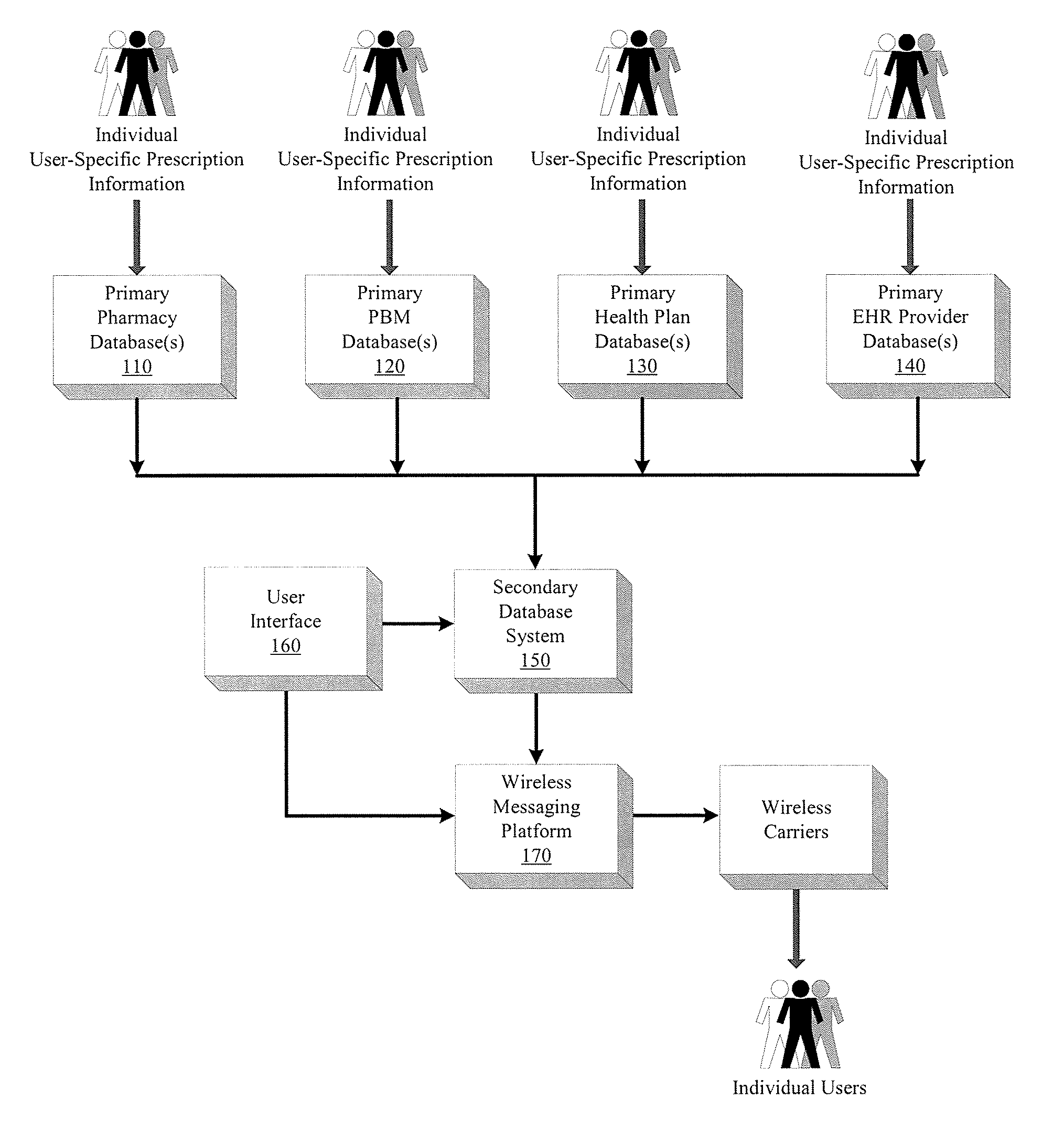
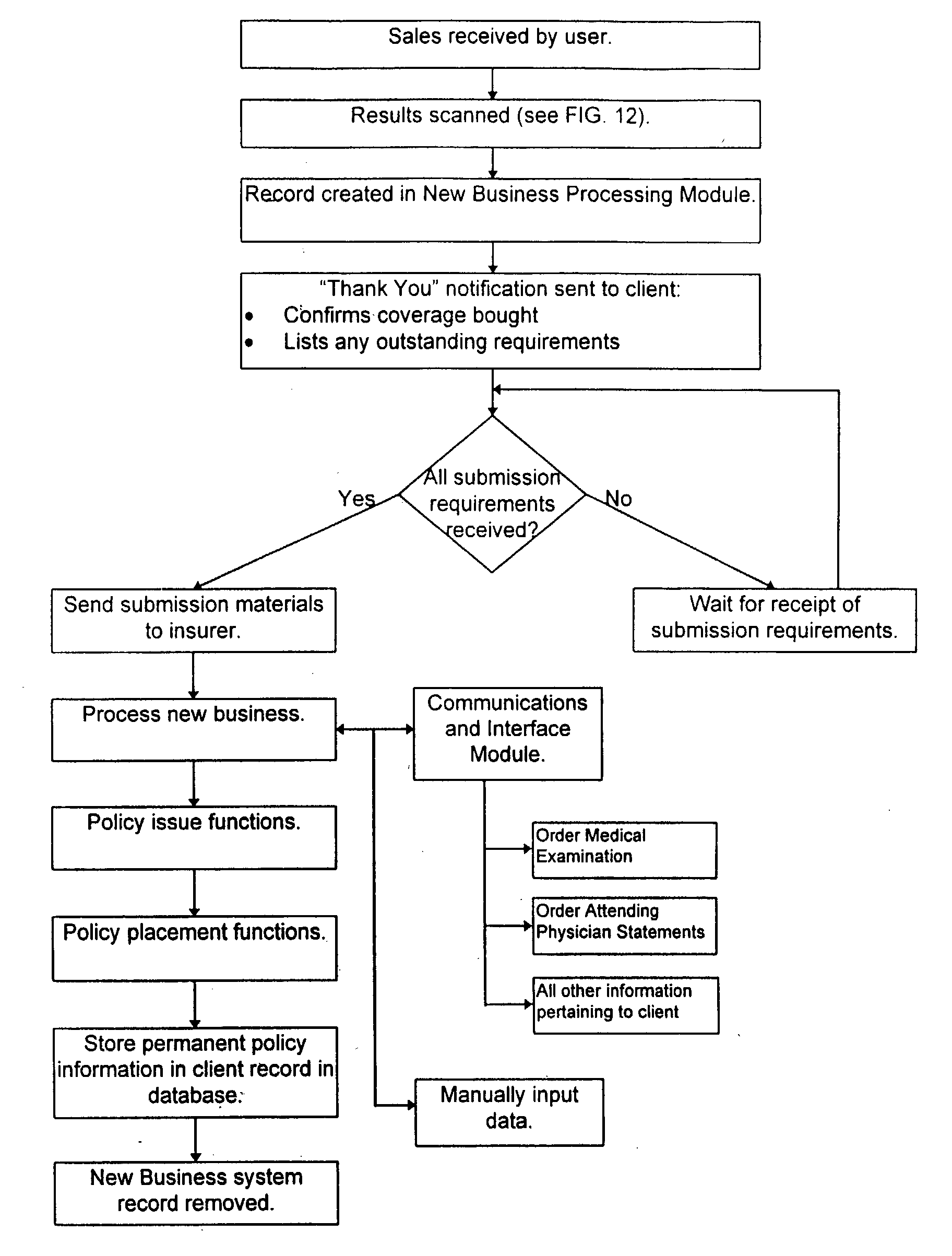
Integrated prescription management and compliance system
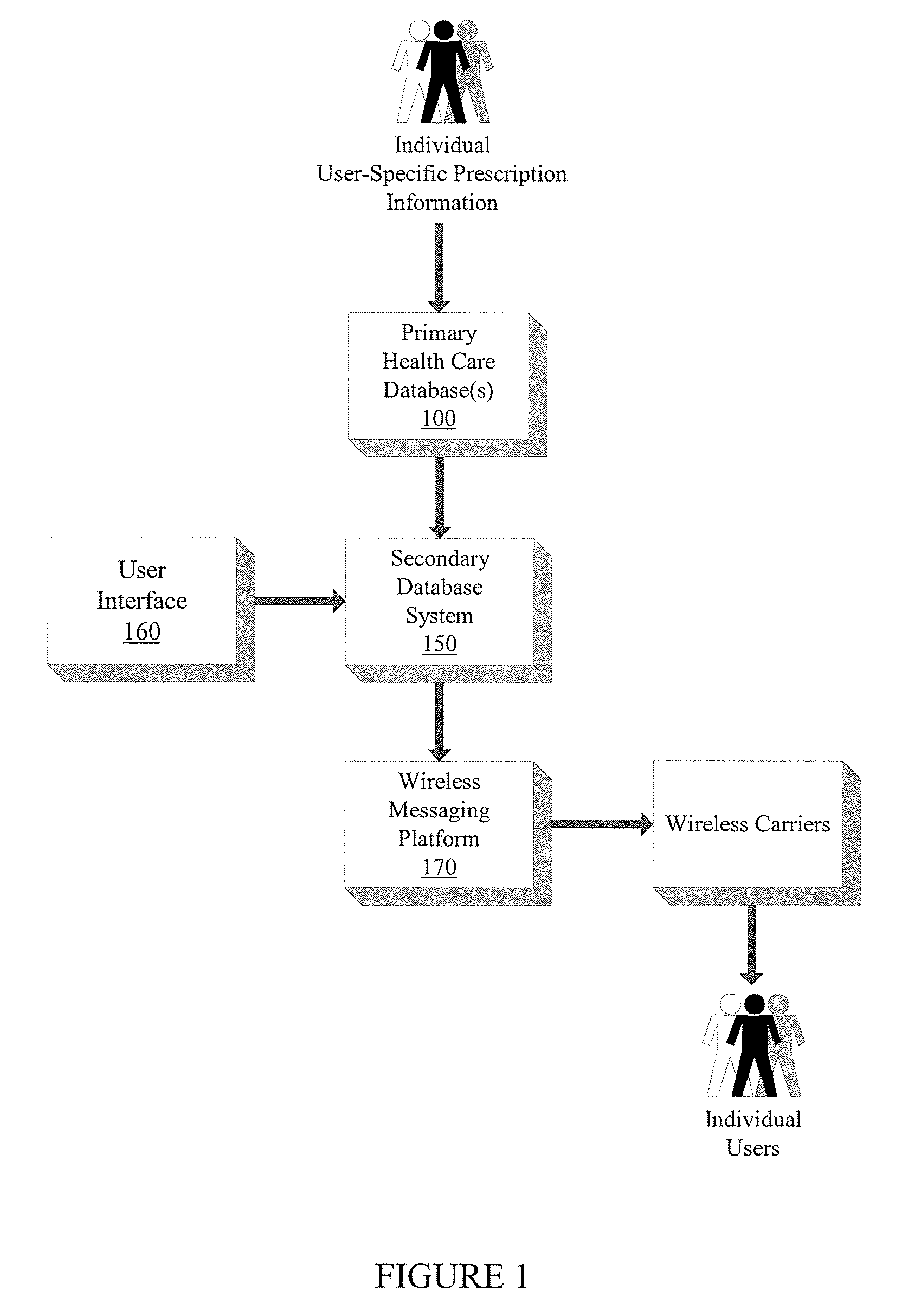
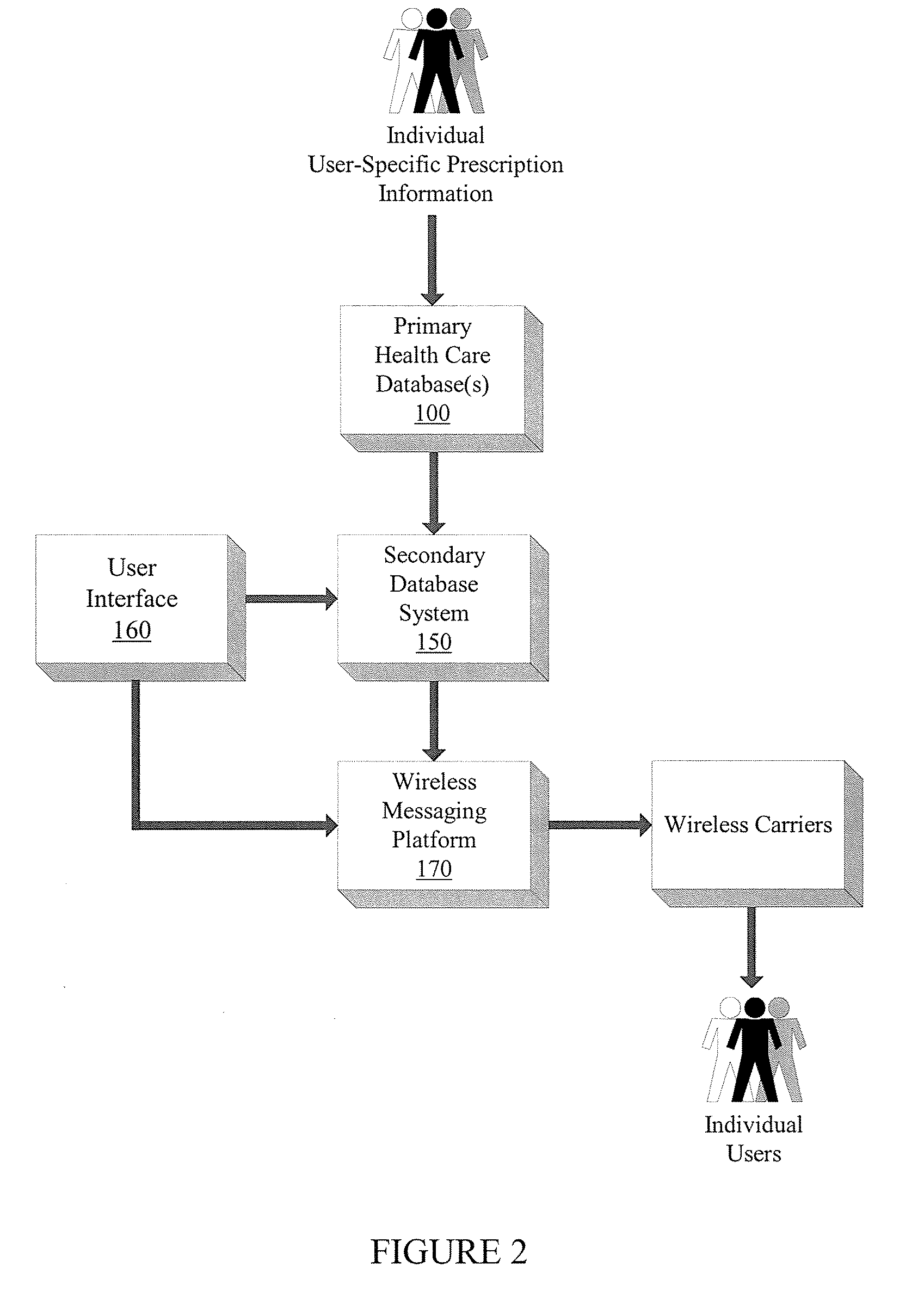
A system and method for prescription therapy management and compliance are provided. The system framework integrates primary databases from pharmacies, pharmacy benefit managers (PBMs), health plans, and EHR providers with a secondary database system, user interface, and wireless messaging platform, in order to extract and aggregate user-specific prescription data and make it available to users through a personalized account and as a part of a wireless prescription reminder service. The system helps users access, aggregate, manage, update, automate, and schedule the prescriptions they are currently taking. Users receive real-time wireless prescription dosing reminders based on their prescribed drug, dosage, and other indications, tailored to each individual's daily schedule. These wireless dosing reminders (i) include additional instructional content such as pill images, compliance tools, and Web or WAP drug links, (ii) are automatically scheduled and transmitted based on the user's prescription source data, in conjunction with selections indicated on their personal account, and (iii) are transmitted via SMS, EMS, MMS, WAP, email, and other formats to the user's mobile phone, PDA, or other wireless device. The integrated interface and secondary database system enable a number of additional system features which focus on compliance and management of the underlying source prescription data.
Owner:LAWLESS OLIVER CHARLES
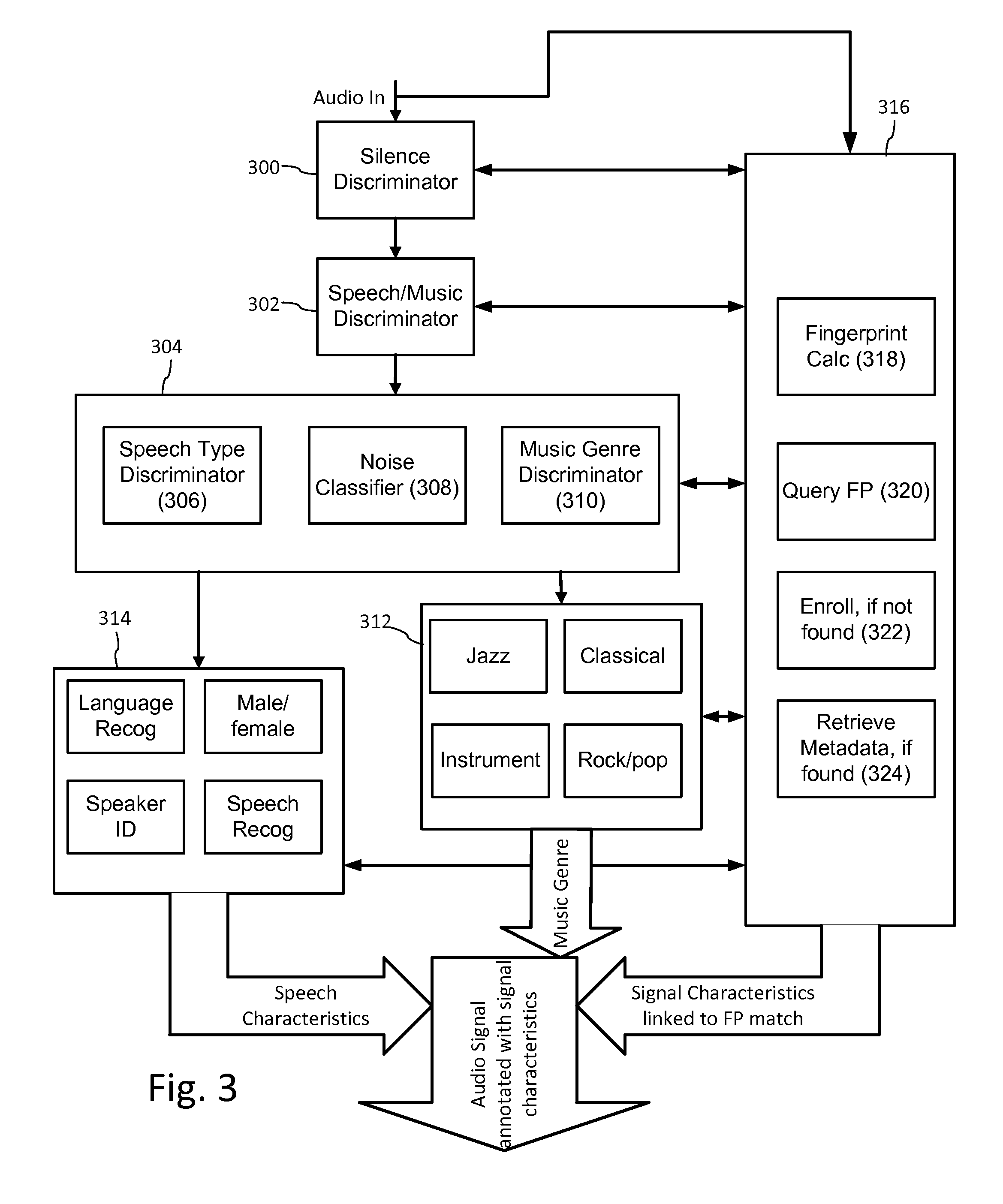
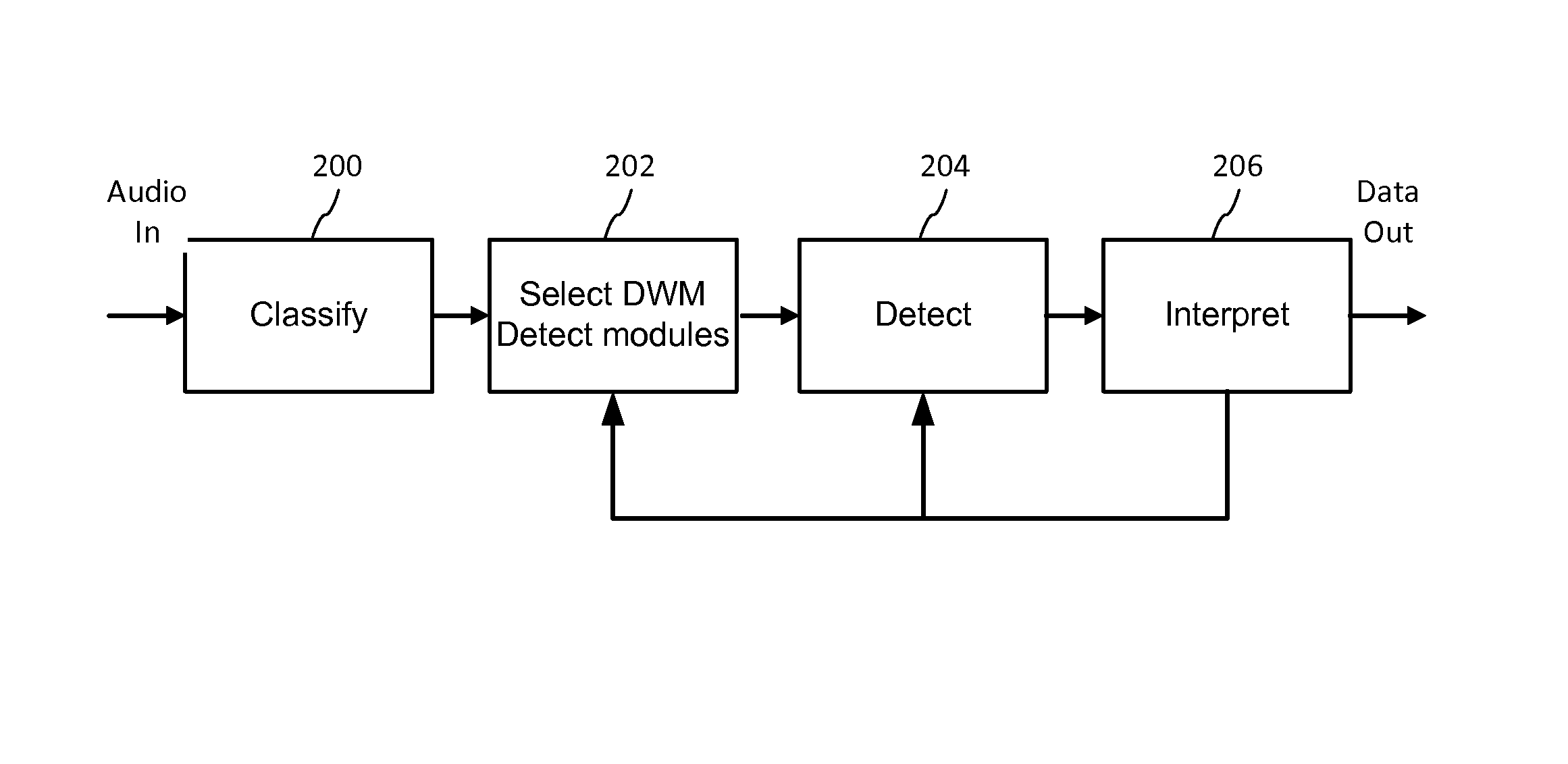
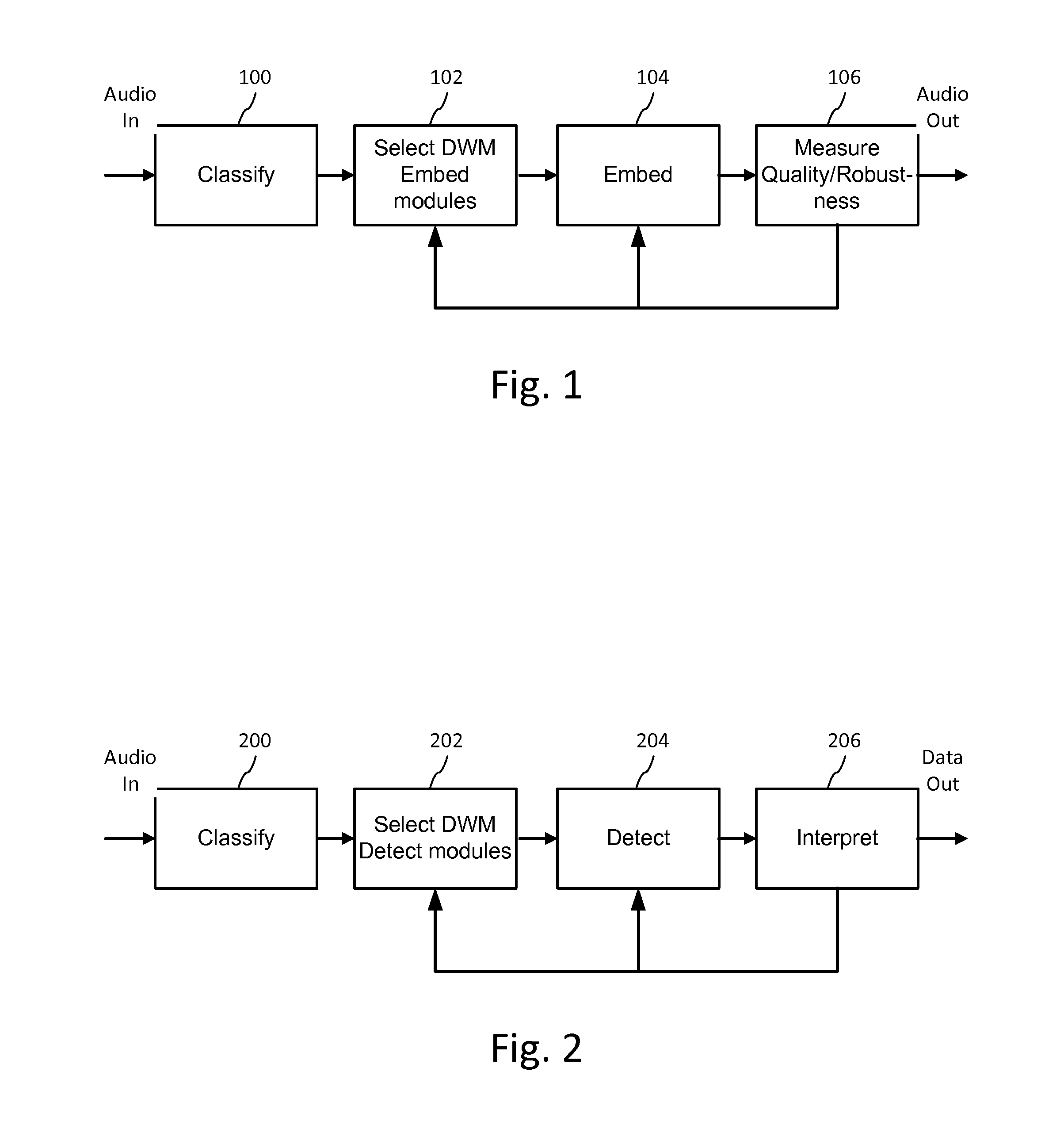
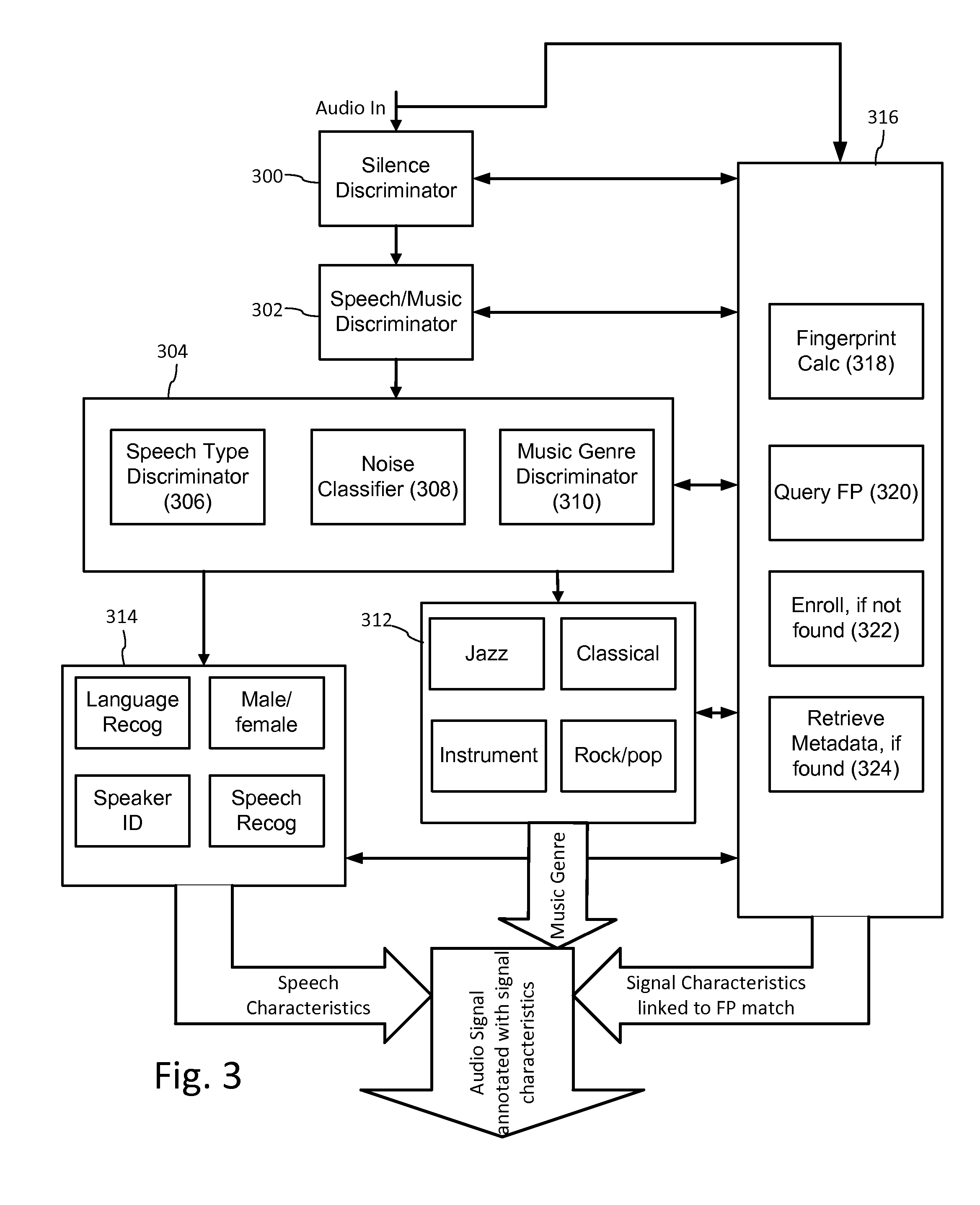
Multi-mode audio recognition and auxiliary data encoding and decoding
ActiveUS20140108020A1Improving communication over networkOptimize networkSpeech analysisData capacityFeature extraction
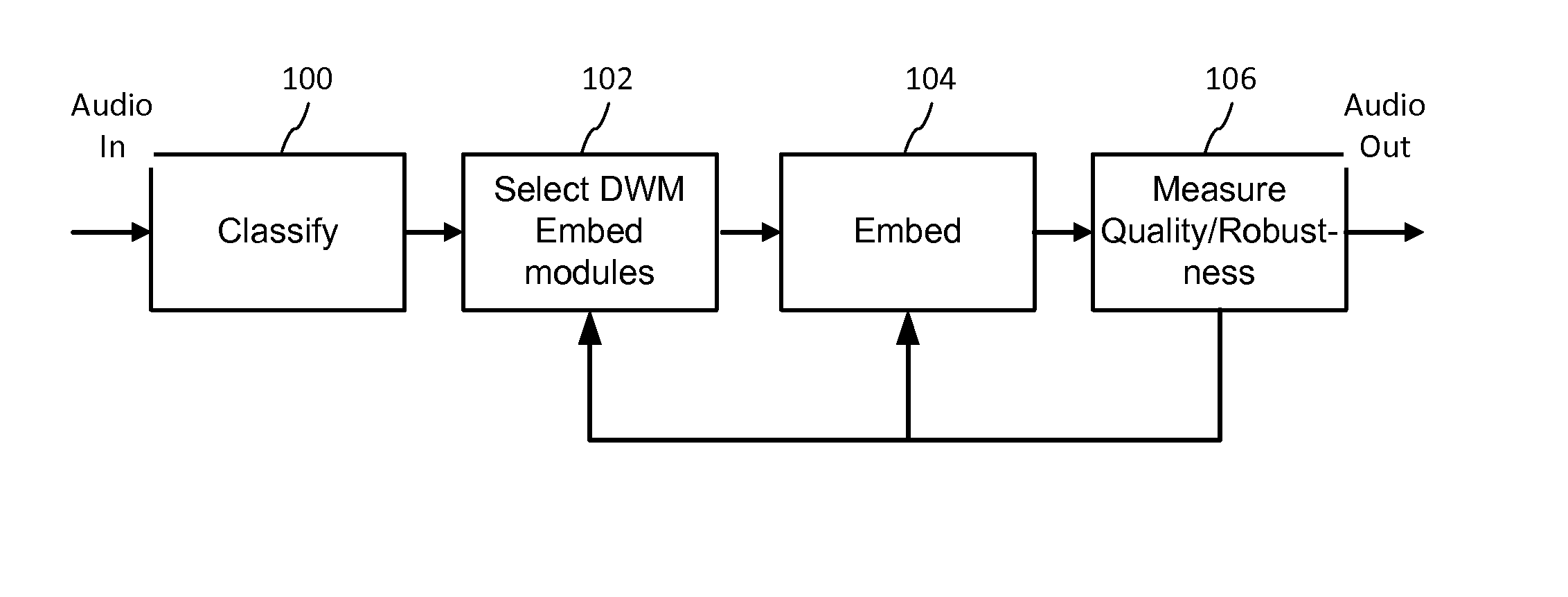
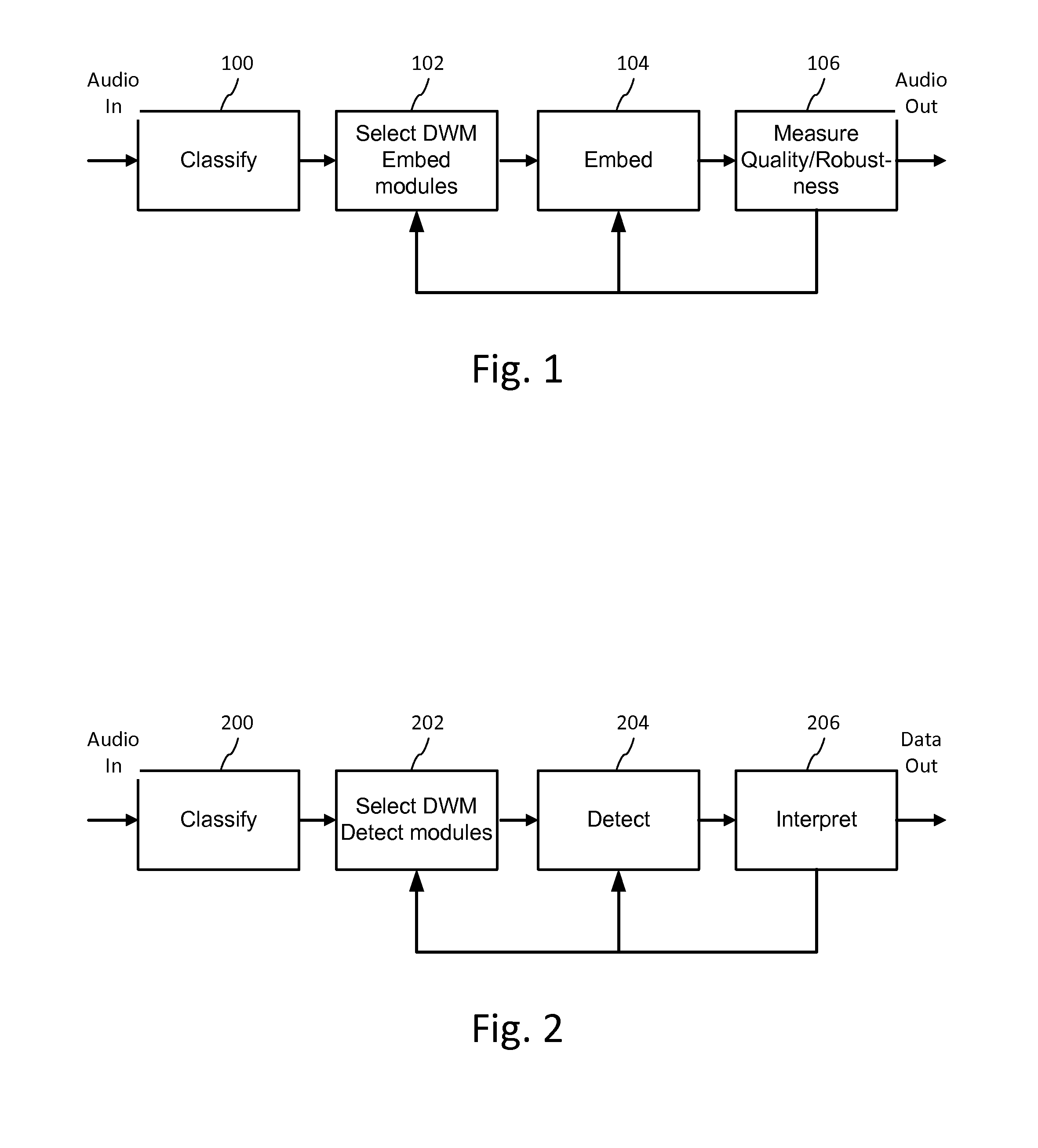
Audio signal processing enhances audio watermark embedding and detecting processes. Audio signal processes include audio classification and adapting watermark embedding and detecting based on classification. Advances in audio watermark design include adaptive watermark signal structure data protocols, perceptual models, and insertion methods. Perceptual and robustness evaluation is integrated into audio watermark embedding to optimize audio quality relative the original signal, and to optimize robustness or data capacity. These methods are applied to audio segments in audio embedder and detector configurations to support real time operation. Feature extraction and matching are also used to adapt audio watermark embedding and detecting.
Owner:DIGIMARC CORP
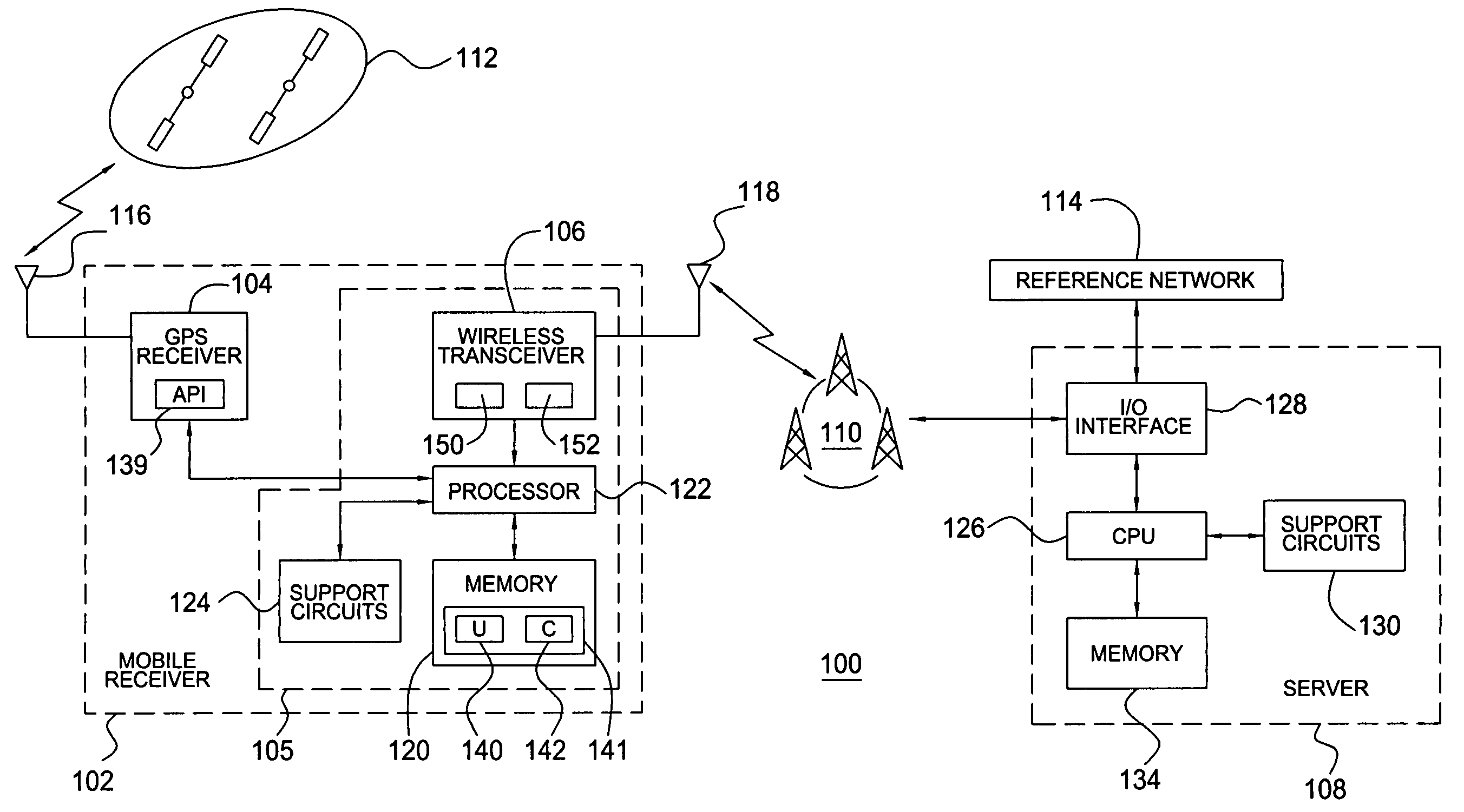
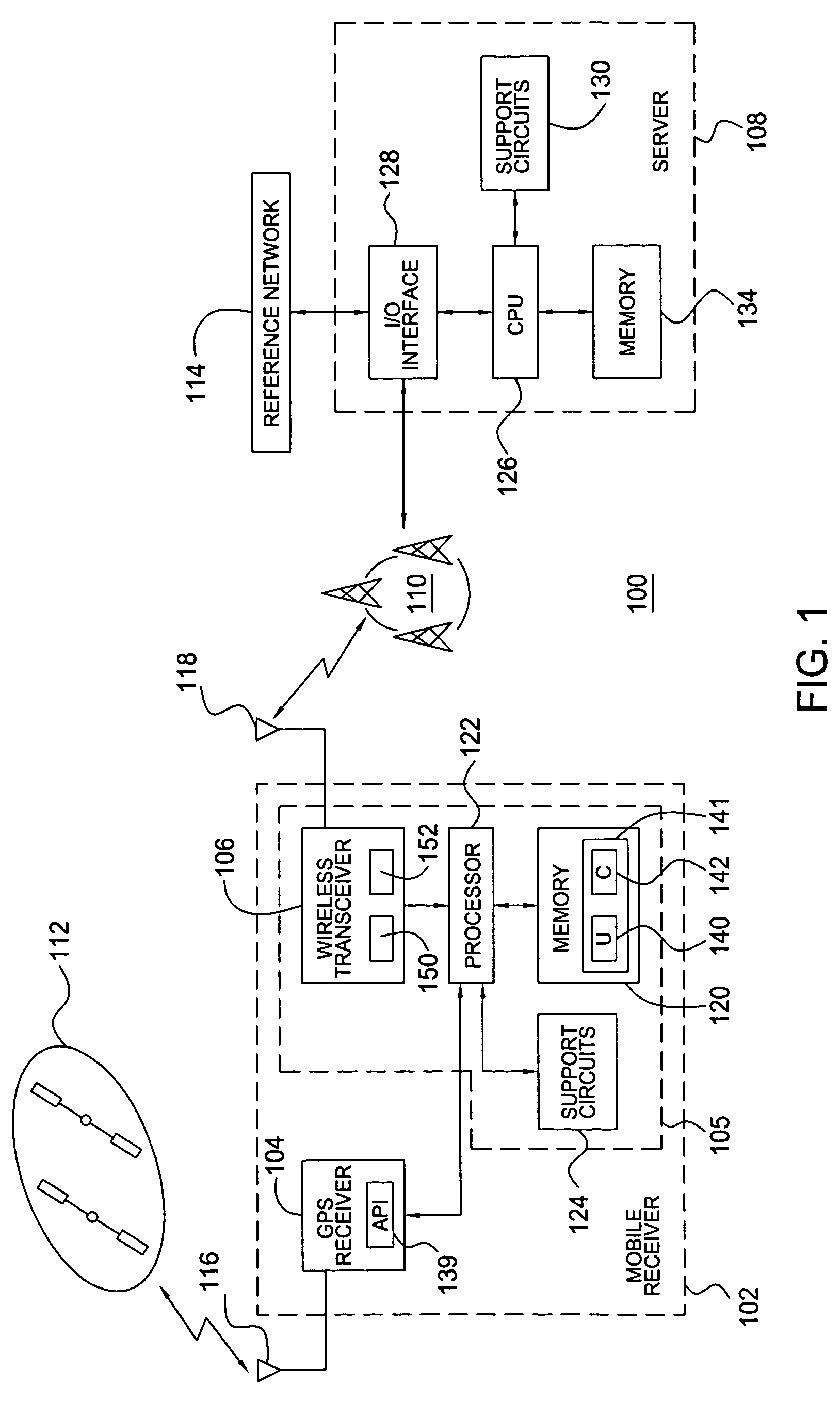
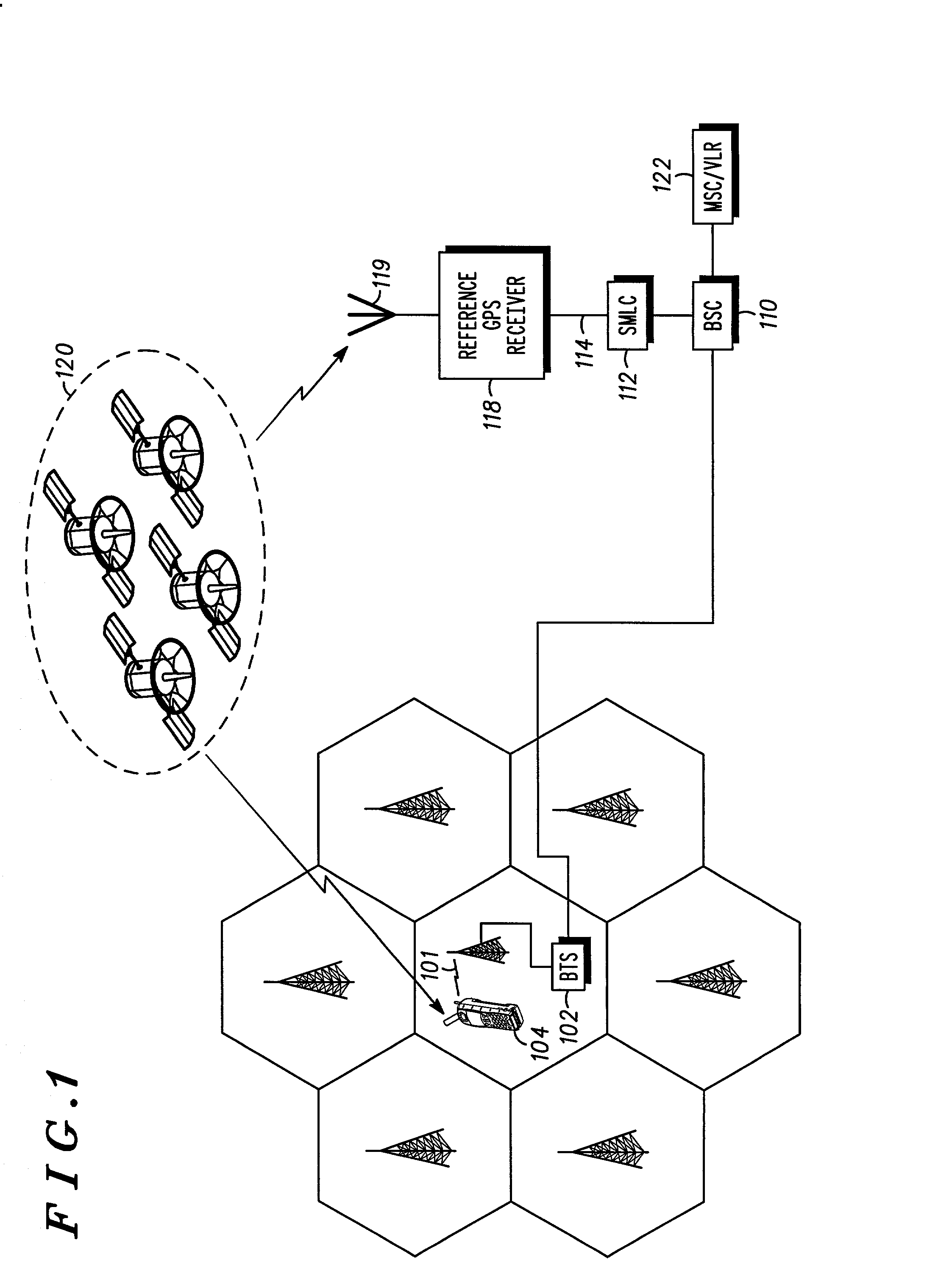
Method and apparatus for processing location service messages in a satellite position location system
Method and apparatus for processing location service messages in a satellite position location system is described. In one example, a mobile receiver includes a satellite signal receiver, wireless circuitry, and at least one module. The satellite signal receiver is configured to receive satellite positioning system signals, such as Global Positioning System (GPS) signals. The wireless circuitry is configured to communicate location service messages between the mobile receiver and a server through a cellular communication network. The location service messages may include any type of data related to A-GPS operation, such as assistance data, position data, request and response data, and the like. The at least one module is configured to provide a user-plane interface and a control-plane interface between the satellite signal receiver and the wireless transceiver. The at leat one module is capable of processing location service messages communicated using either the control-plane signaling or user-plane signaling mechanisms.
Owner:AVAGO TECH INT SALES PTE LTD
Multi-mode audio recognition and auxiliary data encoding and decoding
ActiveUS20140142958A1Improving communication over networkOptimize networkSpeech analysisData capacityFeature extraction
Audio signal processing enhances audio watermark embedding and detecting processes. Audio signal processes include audio classification and adapting watermark embedding and detecting based on classification. Advances in audio watermark design include adaptive watermark signal structure data protocols, perceptual models, and insertion methods. Perceptual and robustness evaluation is integrated into audio watermark embedding to optimize audio quality relative the original signal, and to optimize robustness or data capacity. These methods are applied to audio segments in audio embedder and detector configurations to support real time operation. Feature extraction and matching are also used to adapt audio watermark embedding and detecting.
Owner:DIGIMARC CORP
System, method, and computer program product for selecting and presenting financial products and services
InactiveUS20040030626A1Improve automationEffective volumeDiscounts/incentivesFinanceOutput deviceClient-side
An apparatus and method are provided which use client information from a client to automatically select and present financial products appropriate for the client. The apparatus according to one aspect of the invention comprises an input device for inputting client information relevant to a need by the client for the financial products, for inputting information about the financial products, for inputting ancillary data which excludes the client information and the financial products information, and for inputting decision criteria pertaining to selection from among the financial products. The apparatus further includes a storage device for storing the client information, the financial products information, the ancillary information, and the decision criteria. The apparatus still further includes decision making logic circuitry for using the client information, the financial products information, the ancillary information, and the decision criteria to select a subset of the financial products. It further includes an output device for preparing a client communication which identifies the subset of the financial products. The output device incorporates a portion of the client information and a portion of the financial products information into the client communication. The method according to one aspect of the invention comprises inputting client information relevant to a need by the client for the financial products, inputting information about the financial products, inputting ancillary data which excludes the client information and the financial products information, and inputting decision criteria pertaining to selection from among the financial products. The method also includes storing the client information, the financial products information, the ancillary information, and the decision criteria. This method further includes using the client information, the financial products information, the ancillary information, and the decision criteria to select a subset of the financial products. It further includes preparing a client communication which identifies the subset of the financial products. This client communication preparing step includes incorporating a portion of the client information and a portion of the financial products information into the client communication.
Owner:RPX CORP
Method and apparatus for assisted GPS
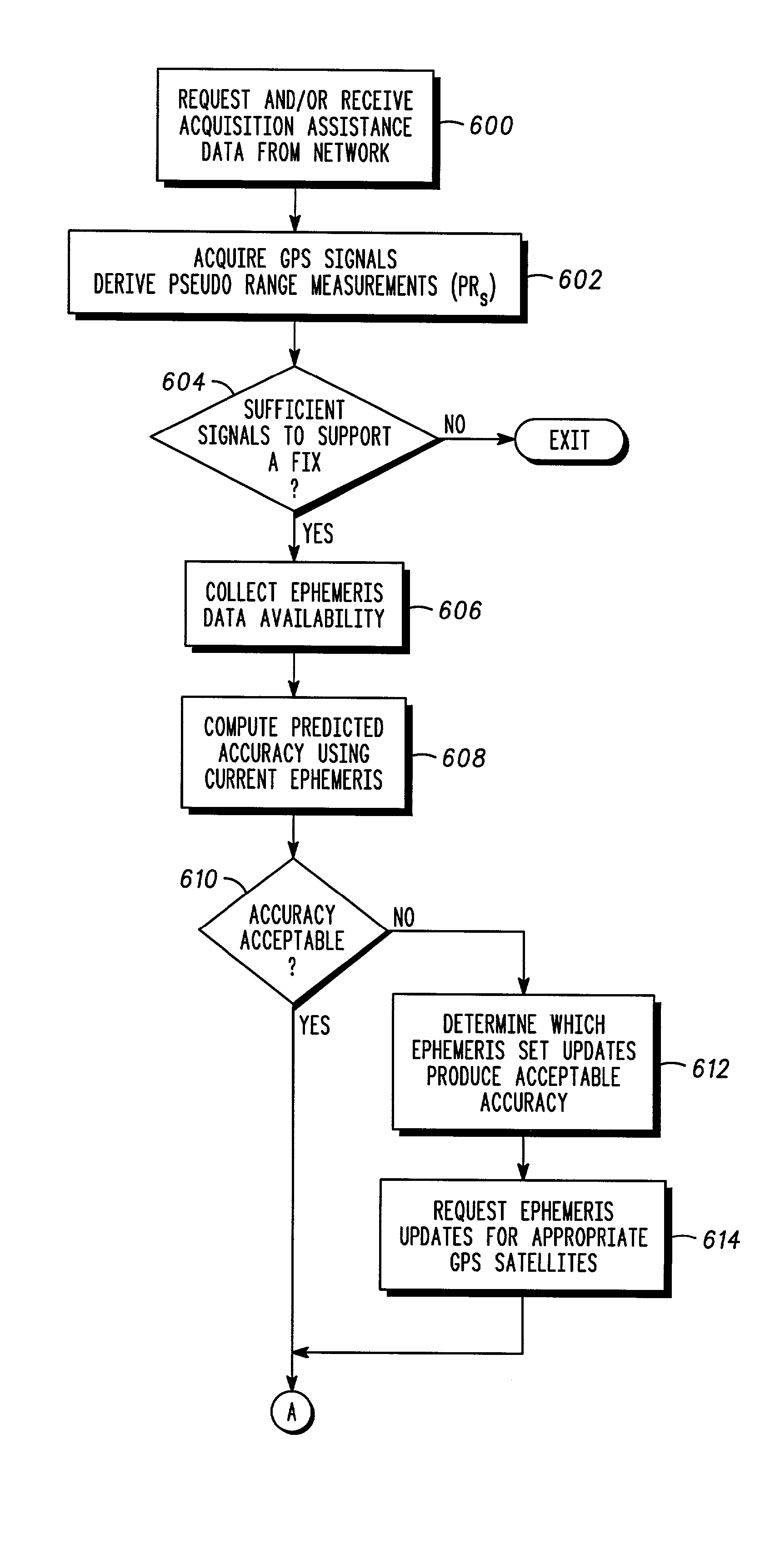
A cellular network protocol that maintains the reliability of assisted GPS based positioning is taught. An Integrity Monitor (IM) informs mobile stations, their users, or networks of measurement quality and it warns them of failing and failed GPS satellites by isolating them from the effects of these failures. Whenever an unhealthy satellite is detected, its corresponding assistance data will be excluded for delivery or for position determination. In other words, there are two specific aspects to the Integrity Monitor (IM). For DGPS users, it predicts the reliability or quality of the DGPS corrections. For all users, it isolates the mobile position calculation from the effects of GPS satellite failures. The UDRE parameter, nominally output by a reference DGPS receiver, is used to communicate the DGPS quality information, and DGPS corrections are simply excluded for failed satellites. For autonomous GPS users, a special integrity message is required and defined to communicate the satellite failure status information.
Owner:GOOGLE TECH HLDG LLC
Methods and apparatus for accessing data from a primary data storage system for secondary storage
InactiveUS8055745B2Error detection/correctionMultiple digital computer combinationsMachine instructionClient-side
A system for providing secondary data storage and recovery services for one or more networked host nodes includes a server application for facilitating data backup and recovery services; a first data storage medium accessible to the server application; a second data storage medium accessible to the server application; at least one client application for mapping write locations allocated by the first data storage medium to write locations represented in a logical view of the first data storage medium; and at least one machine instruction enabling direct read capability of the first data storage medium by the server application for purposes of subsequent time-based storage of the read data into the secondary data storage medium.
Owner:MICROSOFT TECH LICENSING LLC
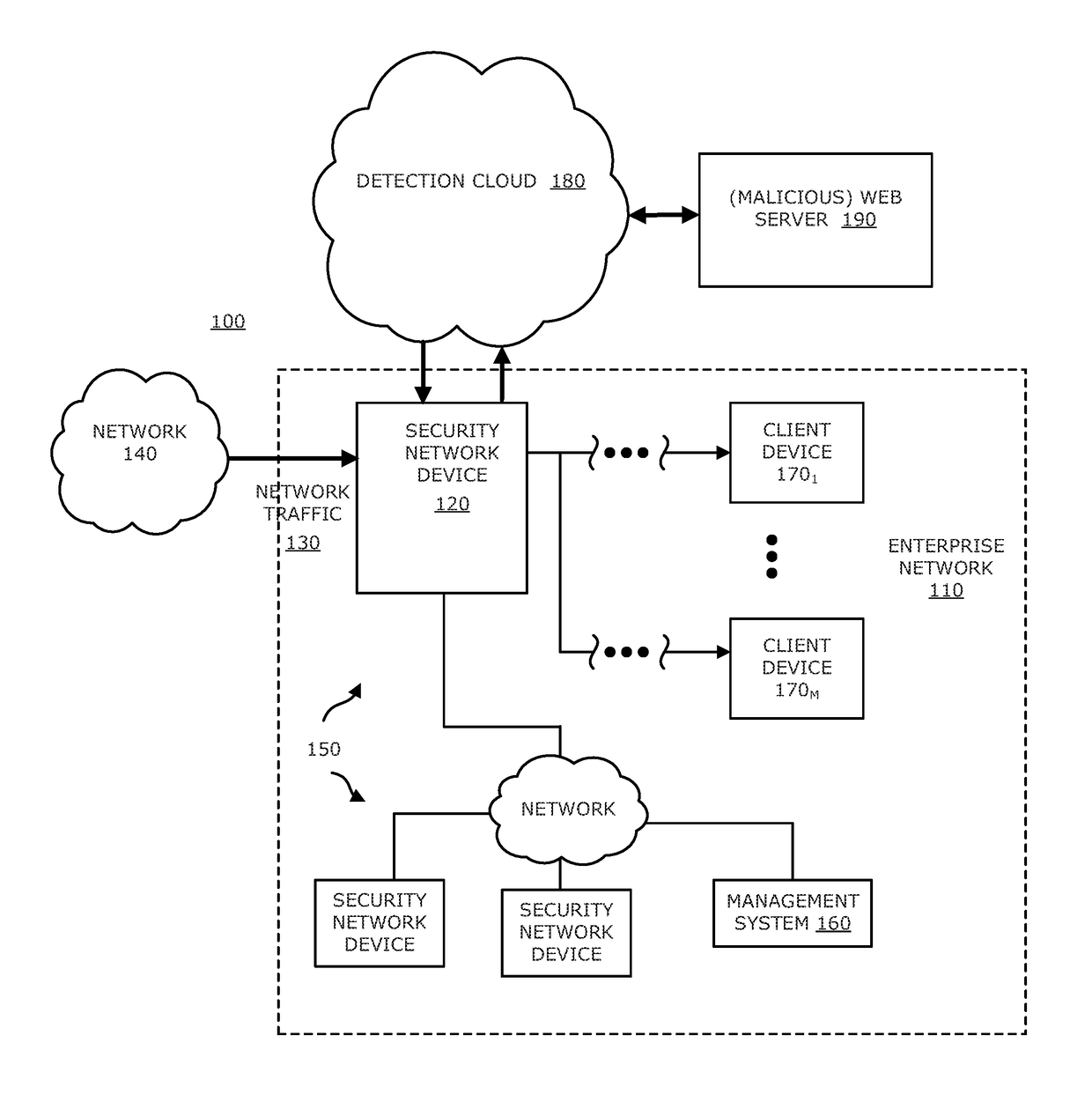
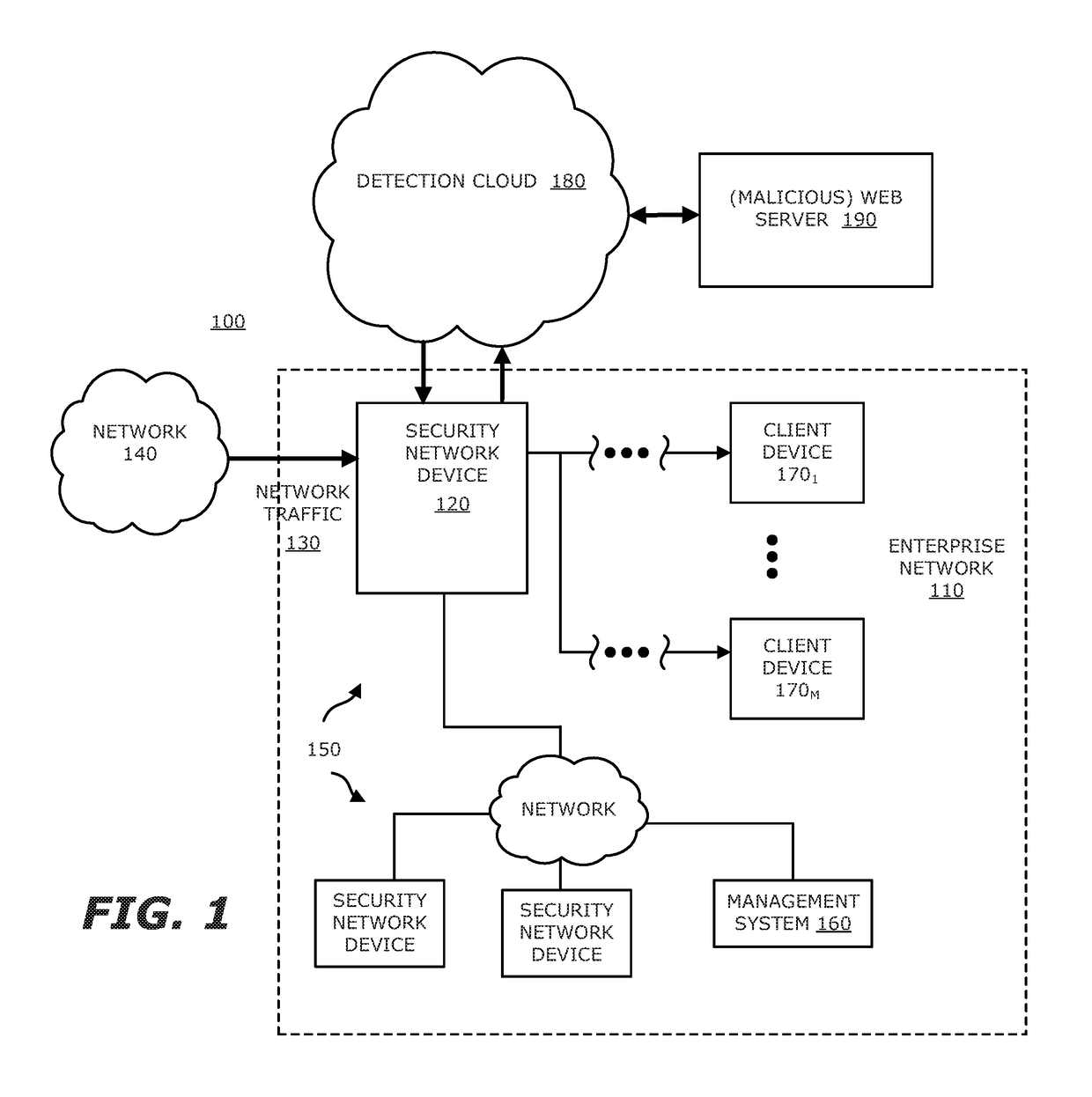
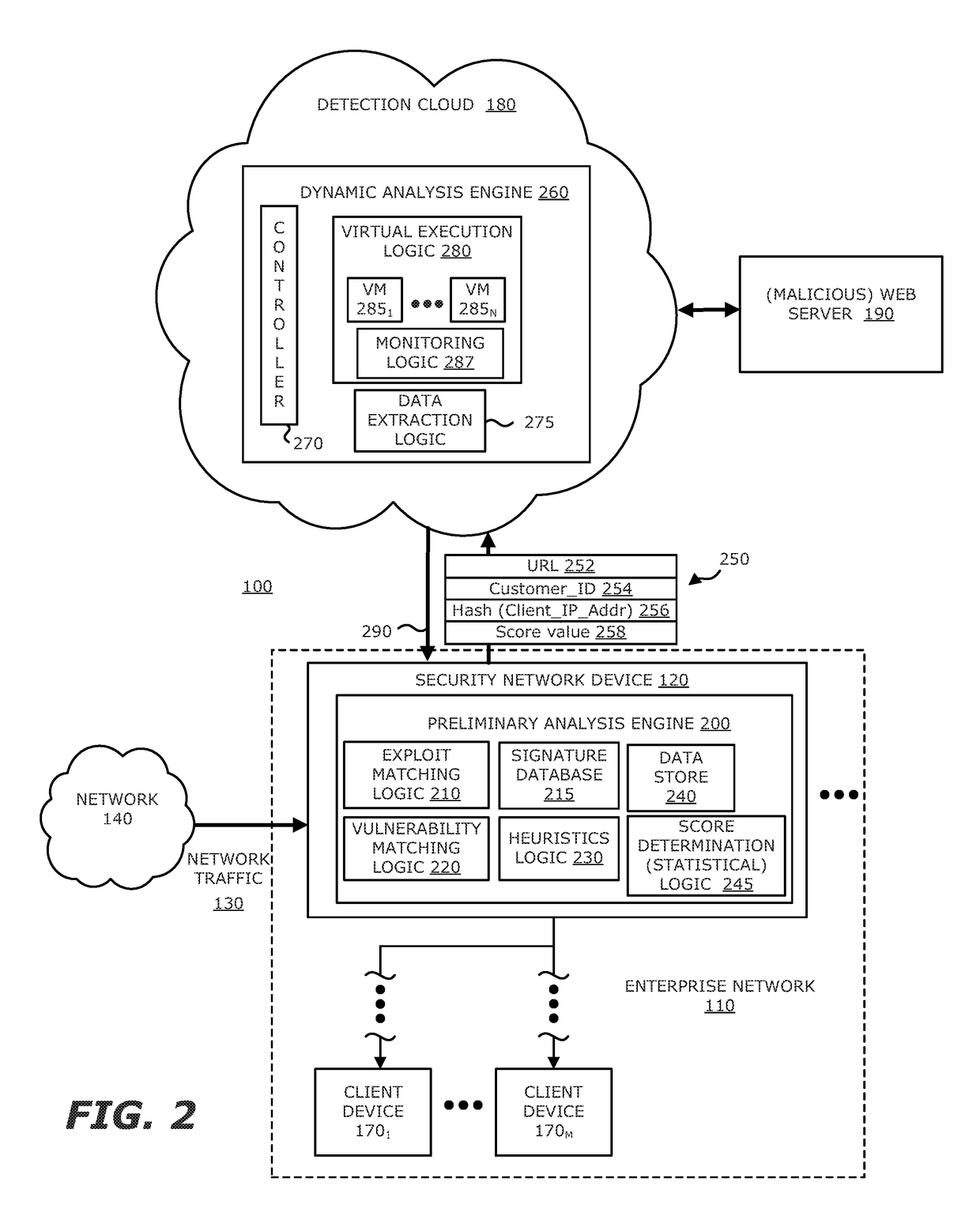
System, device and method for detecting a malicious attack based on direct communications between remotely hosted virtual machines and malicious web servers
ActiveUS9838408B1TransmissionSoftware simulation/interpretation/emulationTraffic capacityWeb service
In an embodiment, a system, device and method for detecting a malicious attack is described. Herein, the system includes a security network device that conducts an analysis on received network traffic to detect a suspicious object associated with the network traffic and determine an identifier associated with a source of the suspicious object. Information associated with the suspicious object and / or ancillary data, including information that identifies a return path for analysis results to a customer, are uploaded to a detection cloud. The detection cloud includes provisioning logic and one or more virtual machines that are provisioned by the provisioning logic in accordance with at least a portion of the ancillary data. The provisioning logic to customize functionality of the detection cloud for a specific customer.
Owner:FIREEYE SECURITY HLDG US LLC +1
Network-based malware detection
In an embodiment, a system, device and method for detecting a malicious attack is described. Herein, the system includes a security network device that conducts an analysis on received network traffic to detect a suspicious object associated with the network traffic and determine an identifier associated with a source of the suspicious object. Both information associated with the suspicious object and ancillary data, including information that identifies a return path for analysis results to a customer, are uploaded to a detection cloud. The detection cloud includes provisioning logic and one or more virtual machines that are provisioned by the provisioning logic in accordance with at least a portion of the ancillary data. The provisioning logic to customize functionality of the detection cloud for a specific customer.
Owner:FIREEYE SECURITY HLDG US LLC +1
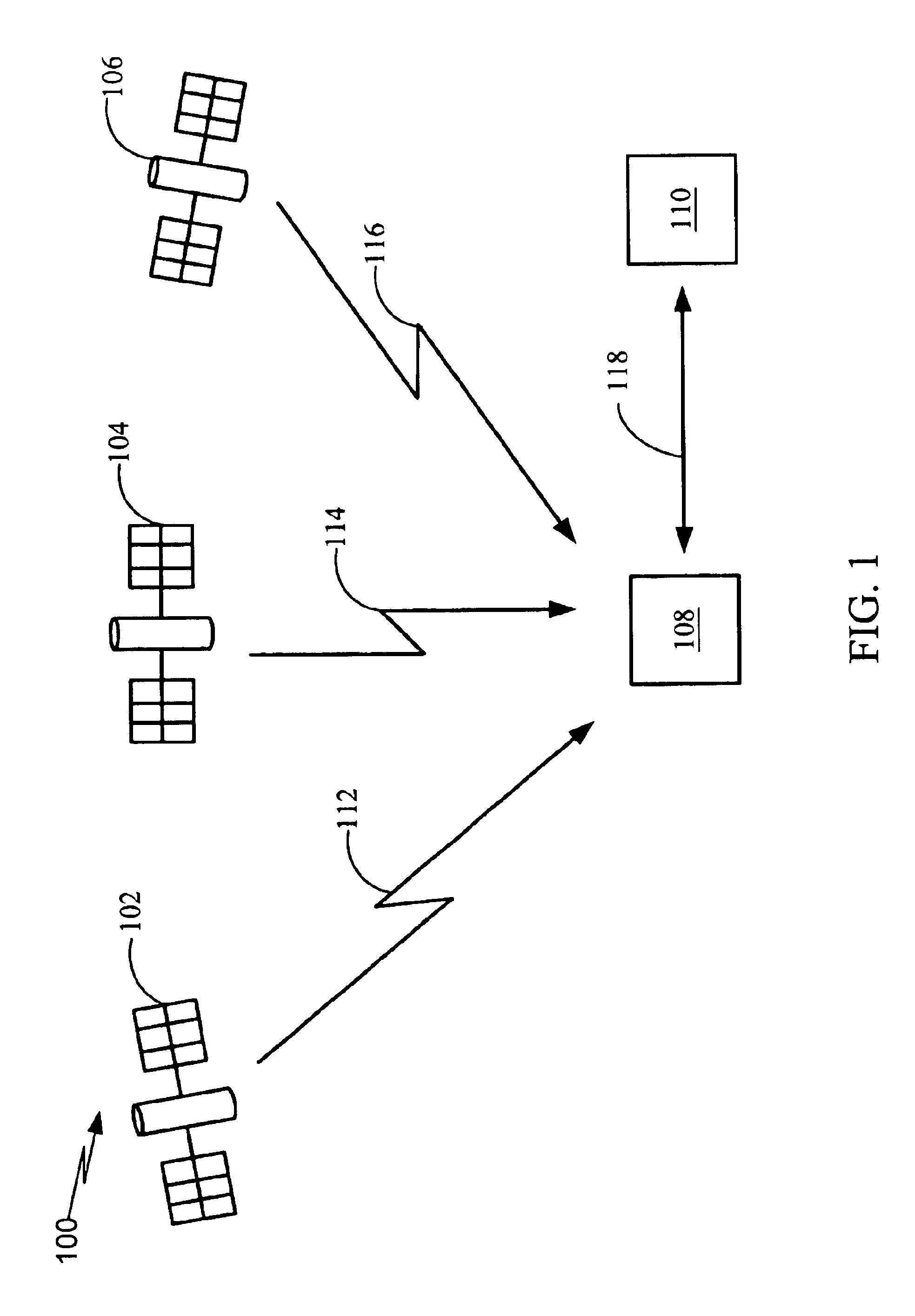
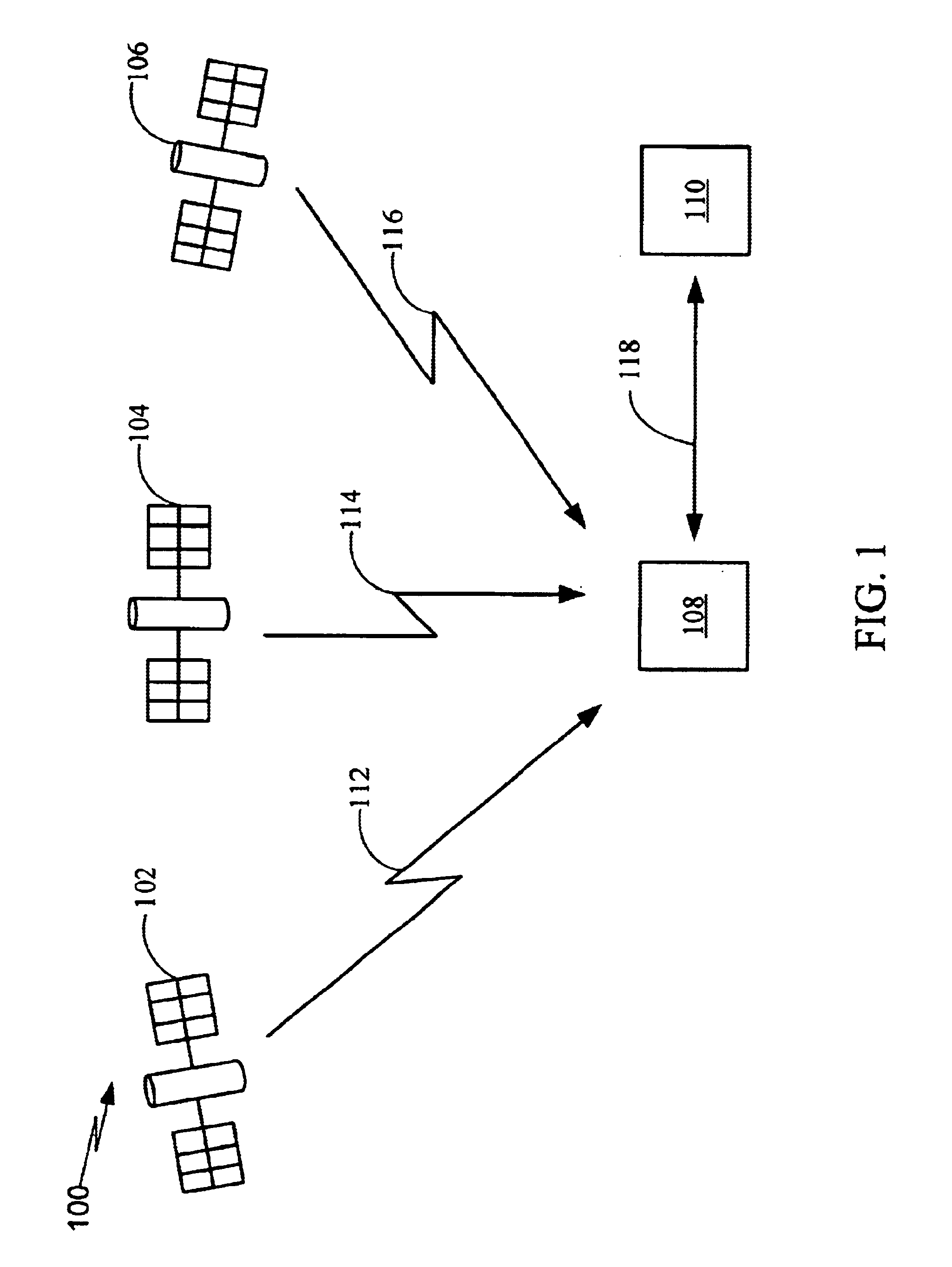
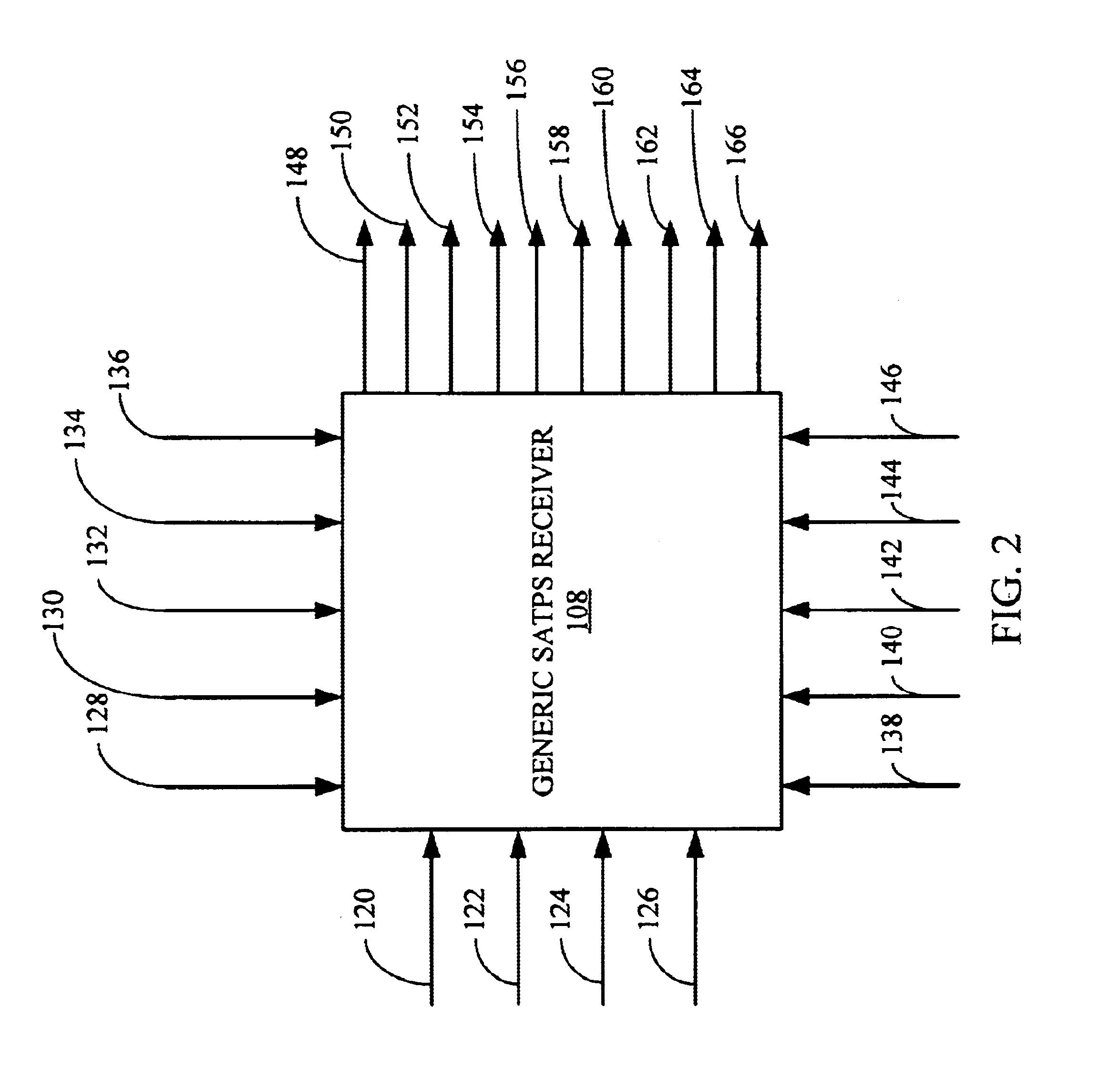
Generic satellite positioning system receivers with programmable inputs
Owner:SAMSUNG ELECTRONICS CO LTD
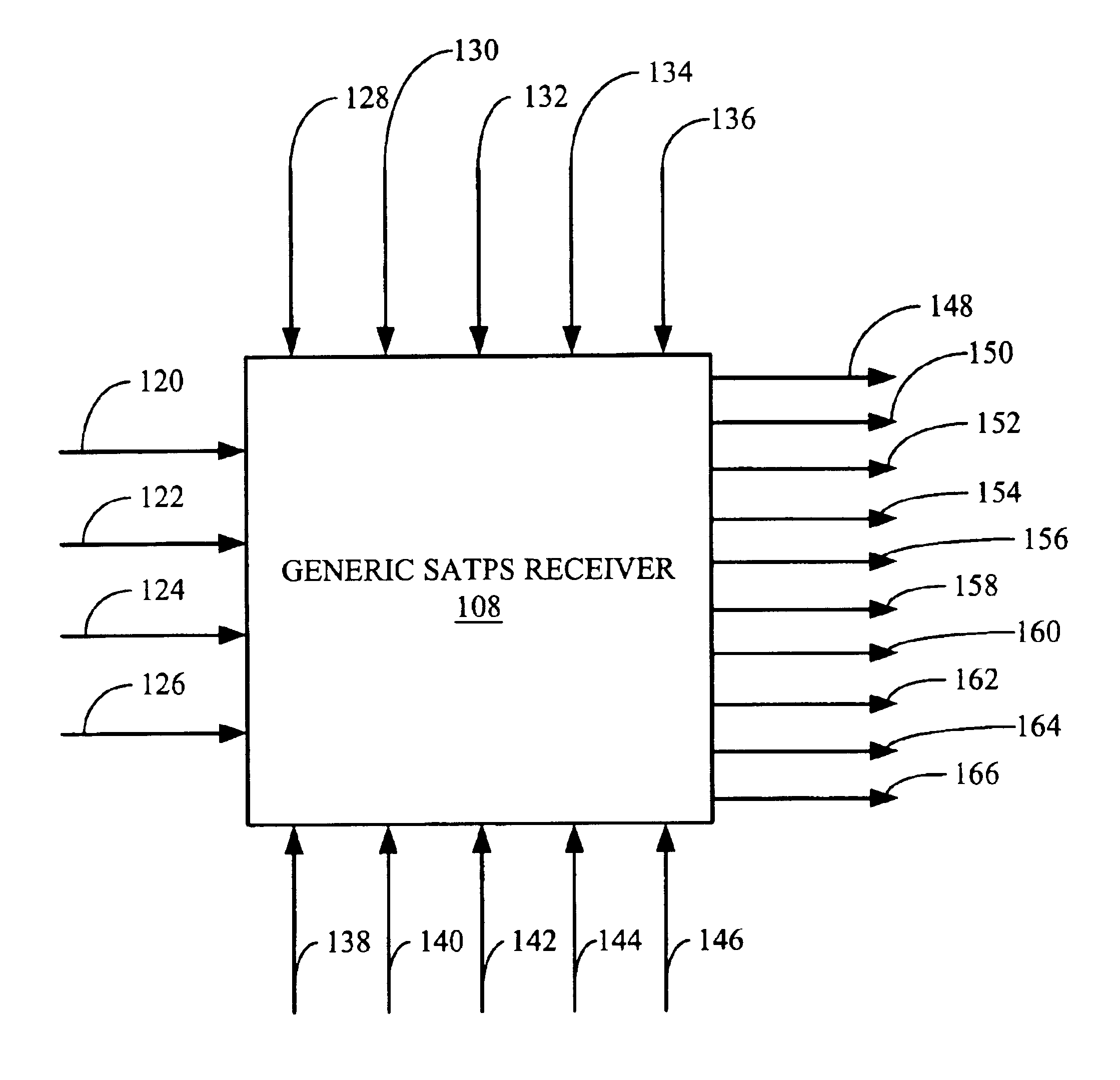
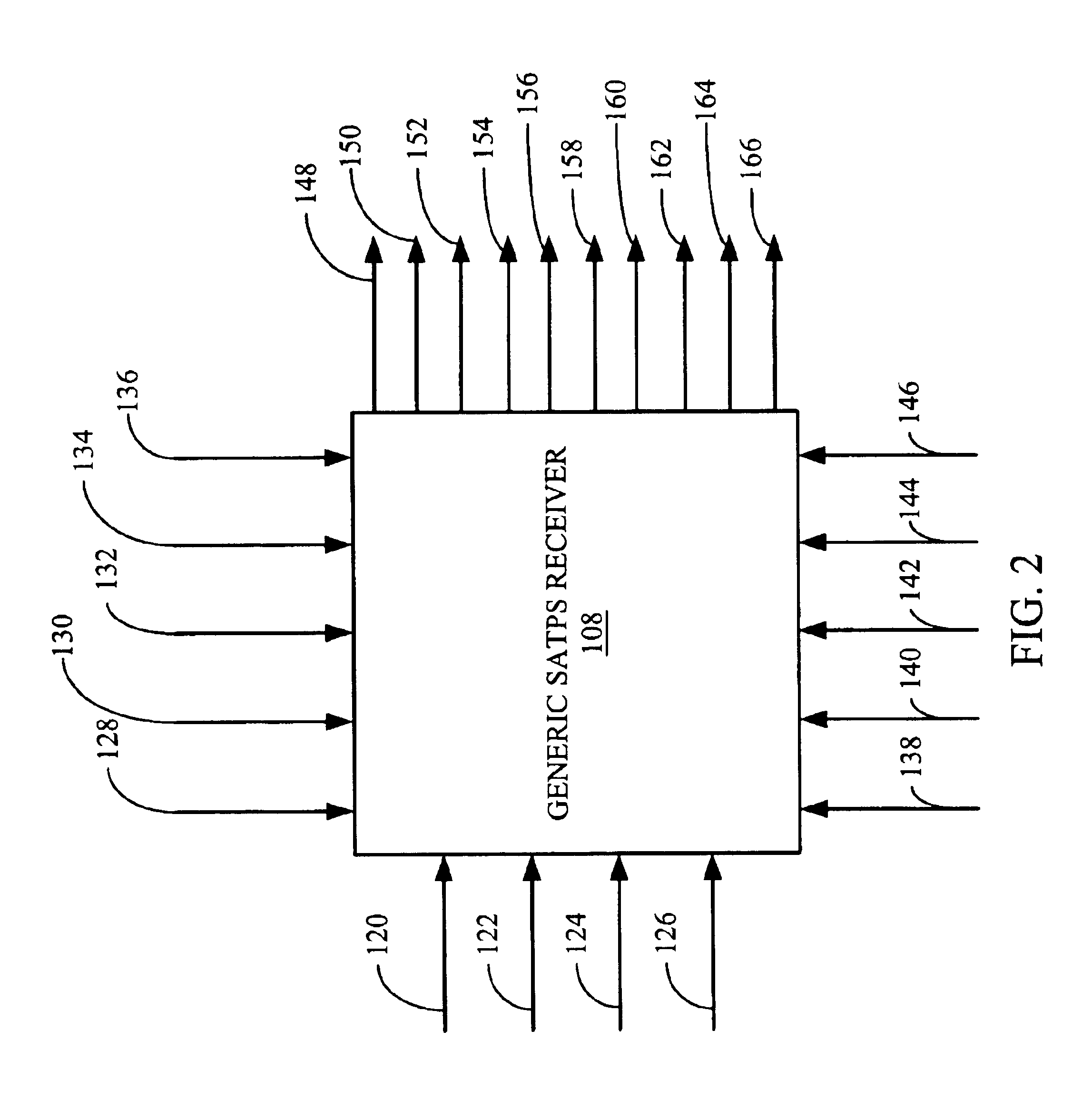
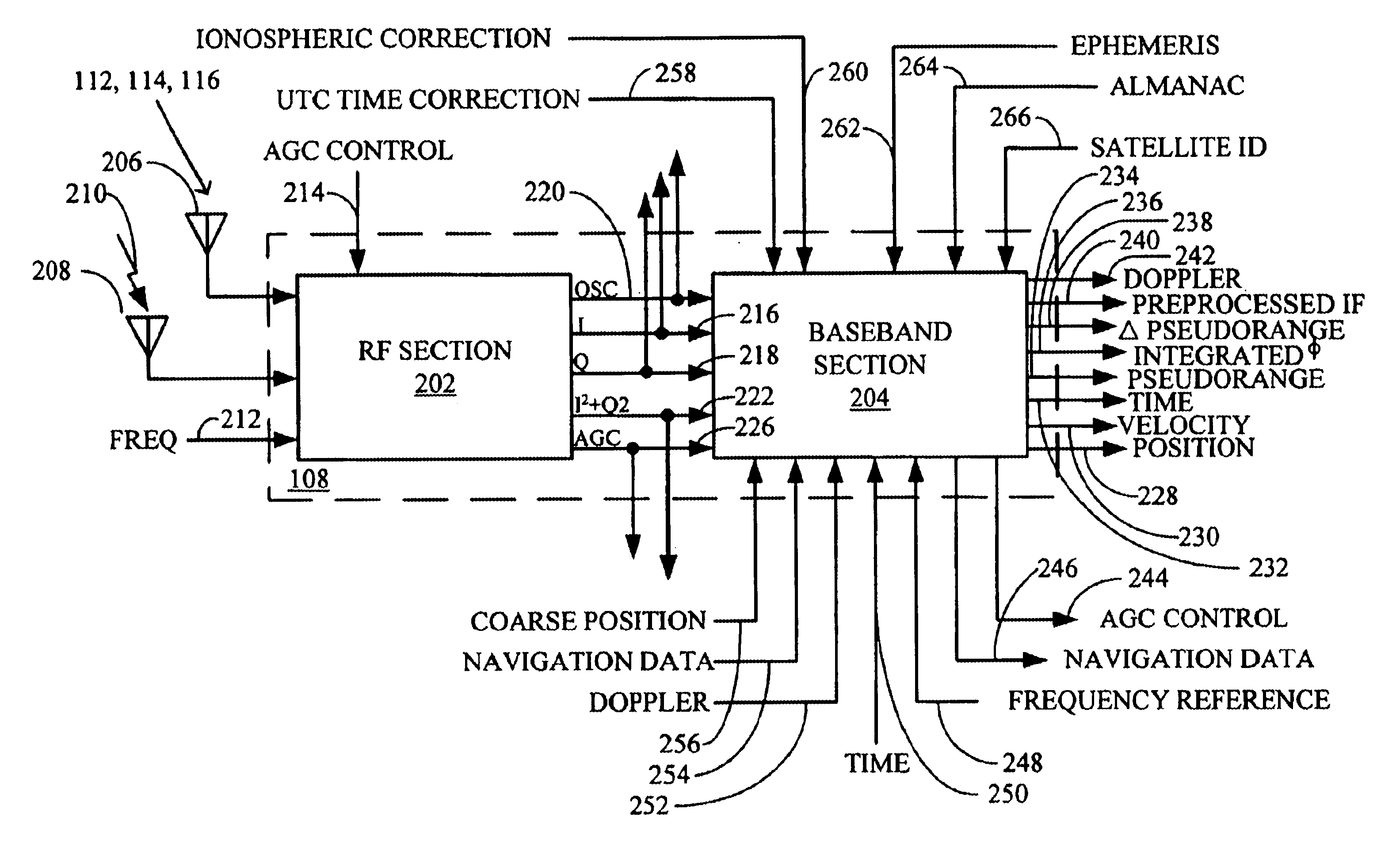
Generic satellite positioning system receivers with selective inputs and outputs
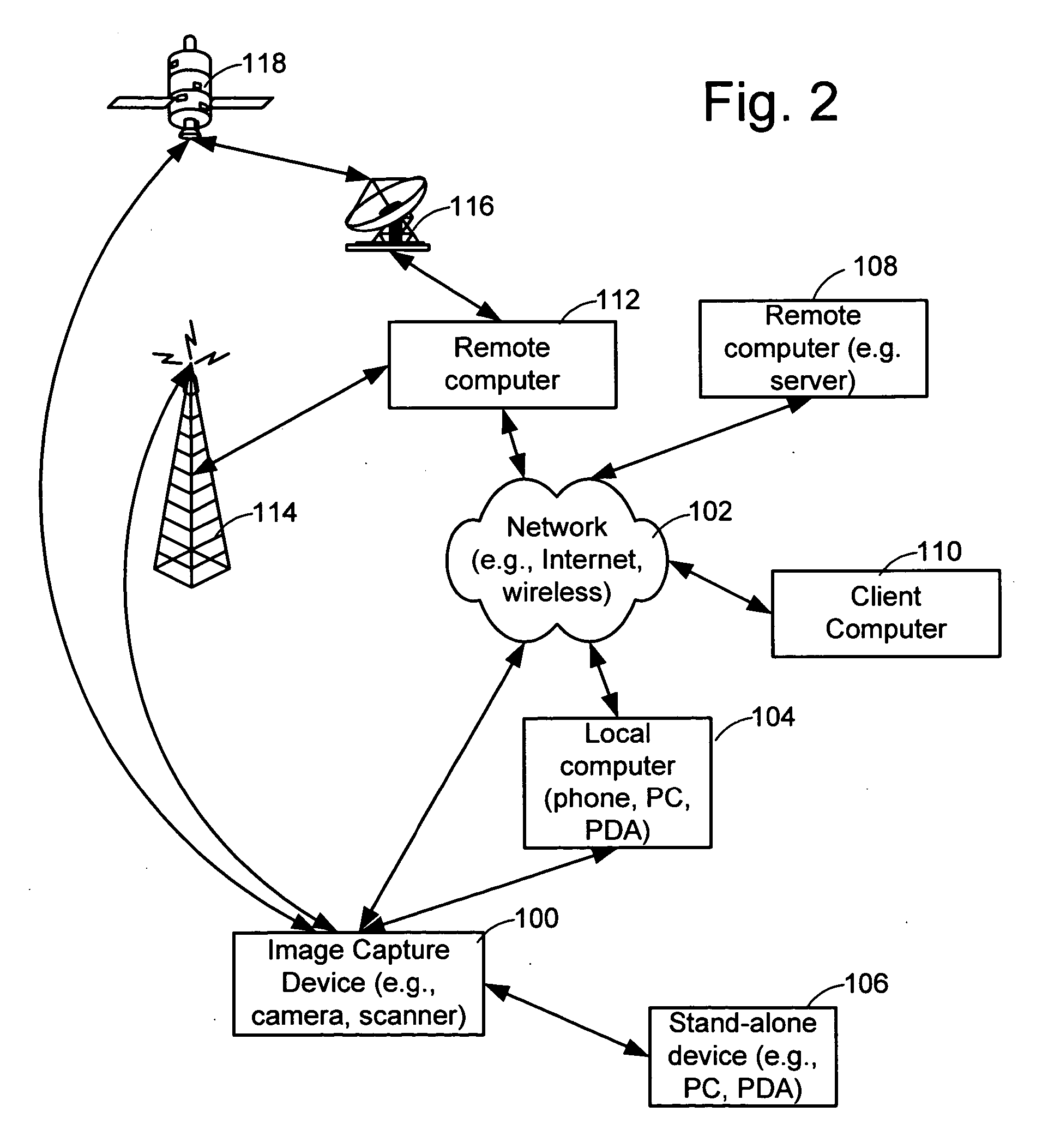
Generic SATPS receivers and methods for configuring generic SATPS receivers that include a plurality of outputs are provided. These configurable SATPS receivers are adapted to be utilized in at least one of a plurality of particular SATPS receiver applications, and can also include a plurality of input paths, and a means for generating selected ones of the plurality of possible outputs. Selected ones of the plurality of outputs are enabled / disabled based on at least one requirement of the particular receiver application to configure or program the generic SATPS receiver to function as a SATPS receiver used for a particular SATPS receiver application or operating environment. The selected ones of the plurality of outputs can be defined by and can be those utilized by the particular SATPS receiver application or operating environment. Thus, SATPS receivers are provided that can be used in multiple applications, that can accept multiple types of assistance data, and that have multiple types of outputs depending on the application and / or desires of the user. The SATPS receiver can be implemented in SATPS systems that include at least one satellite that provides SATPS information, a generic SATPS receiver, and a remote computer.
Owner:CSR TECH INC
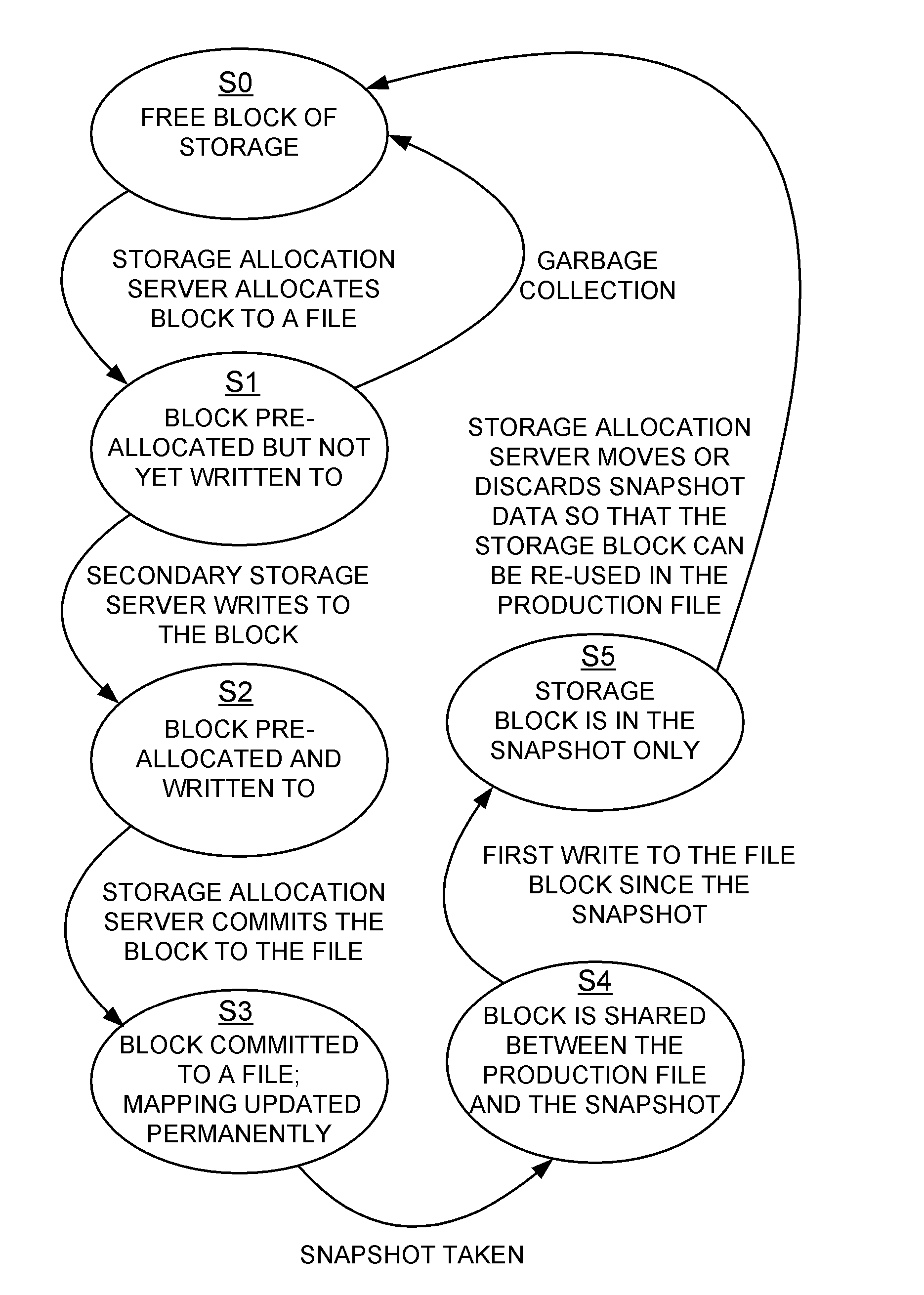
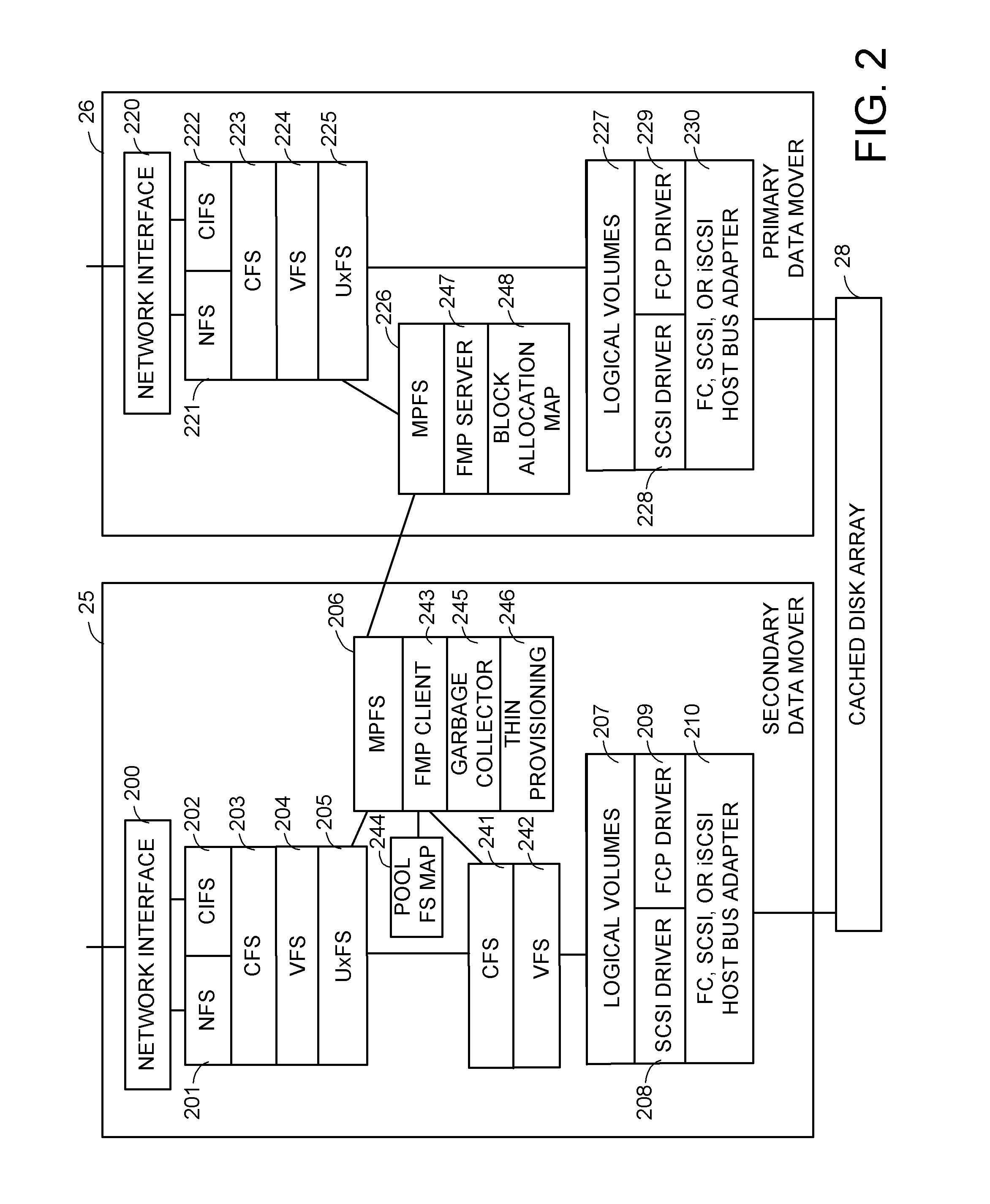
Distributed maintenance of snapshot copies by a primary processor managing metadata and a secondary processor providing read-write access to a production dataset
ActiveUS20070260830A1Degrades I/O performanceImprove I/O performanceMemory loss protectionDigital data processing detailsData setCoprocessor
A primary processor manages metadata of a production dataset and a snapshot copy, while a secondary processor provides concurrent read-write access to the primary dataset. The secondary processor determines when a first write is being made to a data block of the production dataset, and in this case sends a metadata change request to the primary data processor. The primary data processor commits the metadata change to the production dataset and maintains the snapshot copy while the secondary data processor continues to service other read-write requests. The secondary processor logs metadata changes so that the secondary processor may return a “write completed” message before the primary processor commits the metadata change. The primary data processor pre-allocates data storage blocks in such a way that the “write anywhere” method does not result in a gradual degradation in I / O performance.
Owner:EMC IP HLDG CO LLC
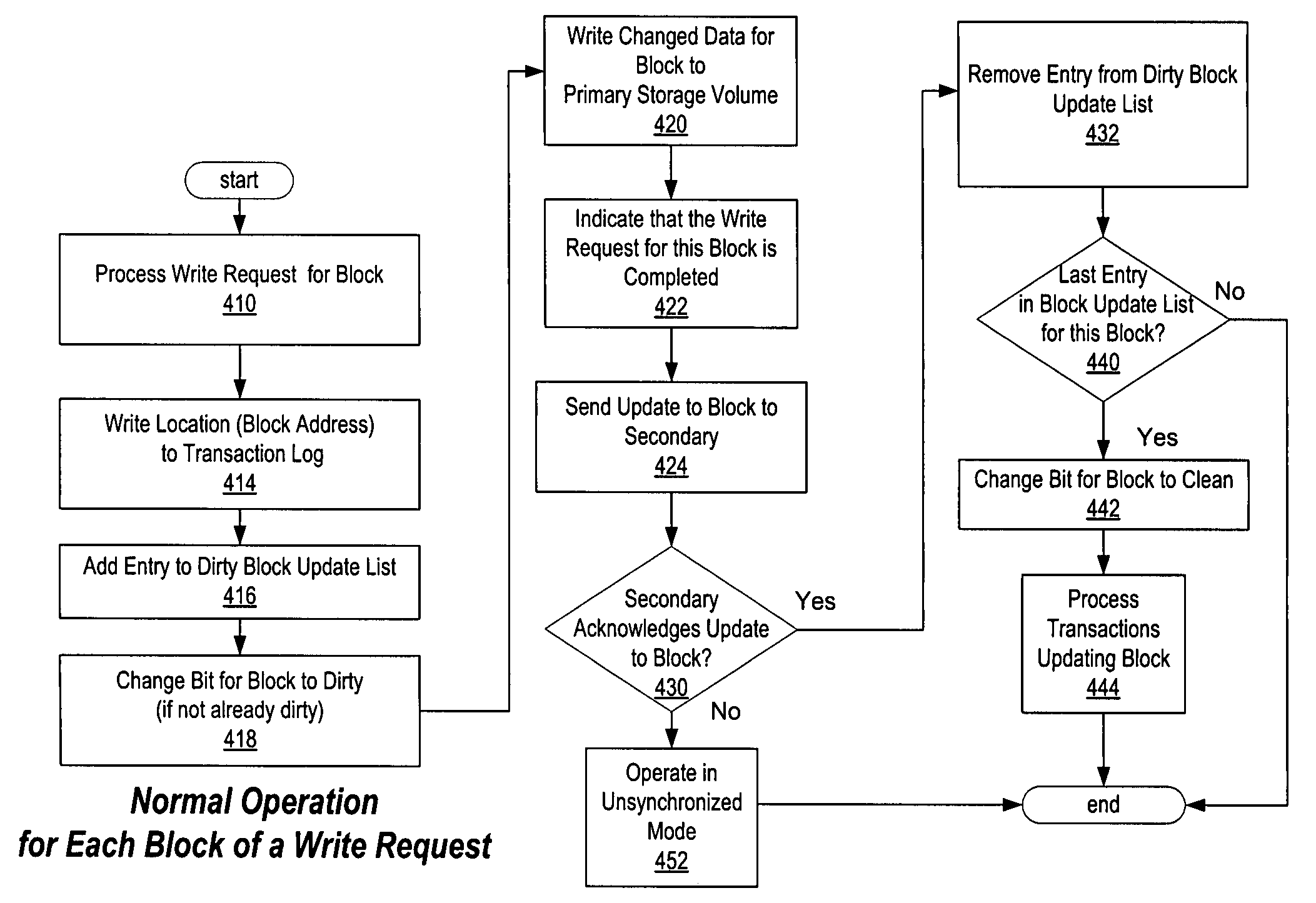
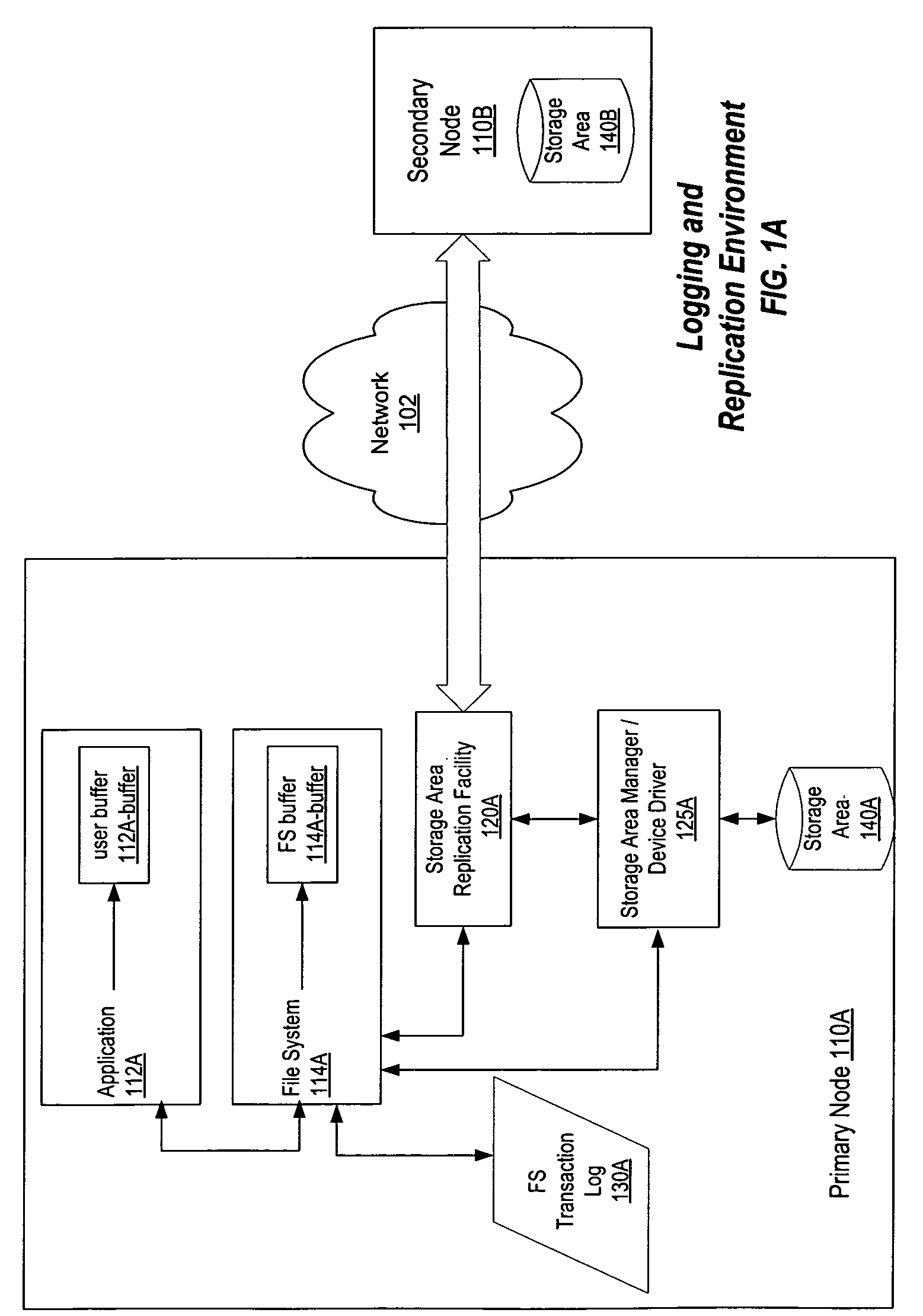
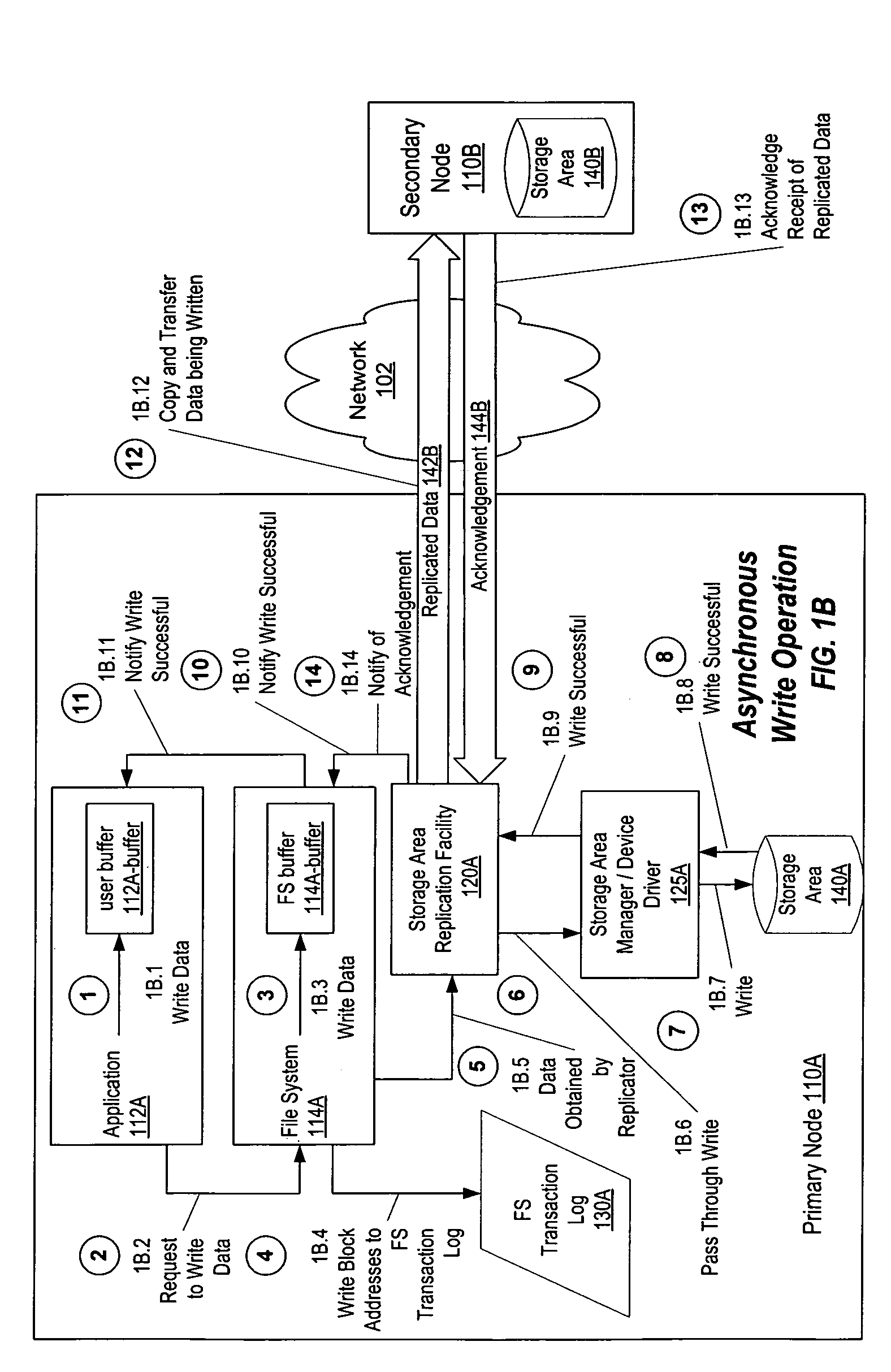
Coordinated dirty block tracking
InactiveUS7606841B1Data processing applicationsError detection/correctionFile systemNetwork connection
A method, system, computer system, and computer-readable medium to maintain consistent, up-to-date copies of primary data that enable quick resumption of operations upon failure of the primary node, the secondary node, and / or the network connecting nodes. The current status of individual storage locations is tracked, indicating whether data in each individual storage location is synchronized between a primary node and a secondary node. Transaction logging by a transaction-logging application, such as a file system or database system, is used to track individual storage locations updated with each transaction. Acknowledgements of these updates are tracked during replication to determine whether individual storage locations containing primary and secondary data are synchronized. This coordinated transaction logging and acknowledgement tracking enables write operations and replication to be performed efficiently while maintaining the information necessary to resynchronize only individual storage locations when primary and- secondary data become unsynchronized.
Owner:VERITAS TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com