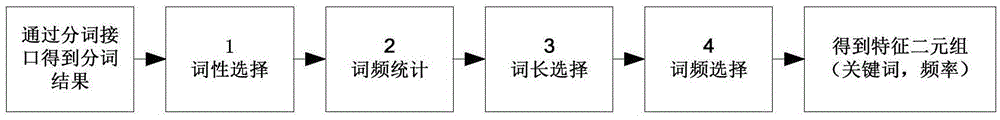
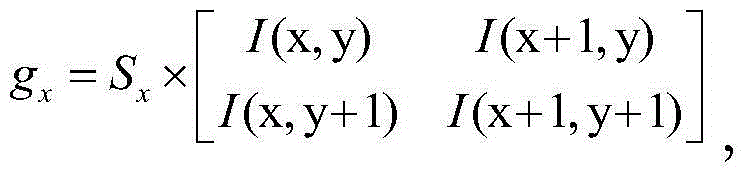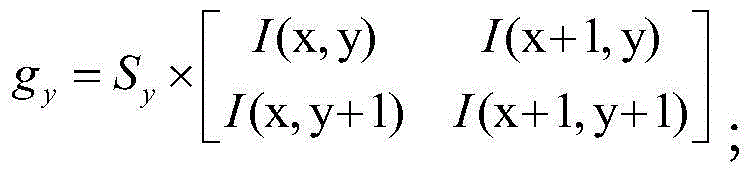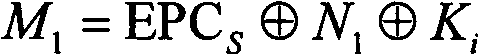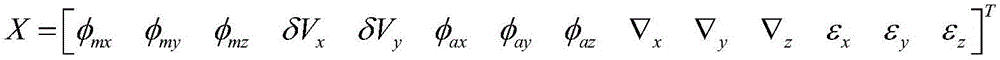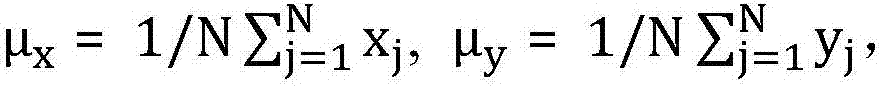Patents
Literature
95results about How to "Reduce computing needs" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
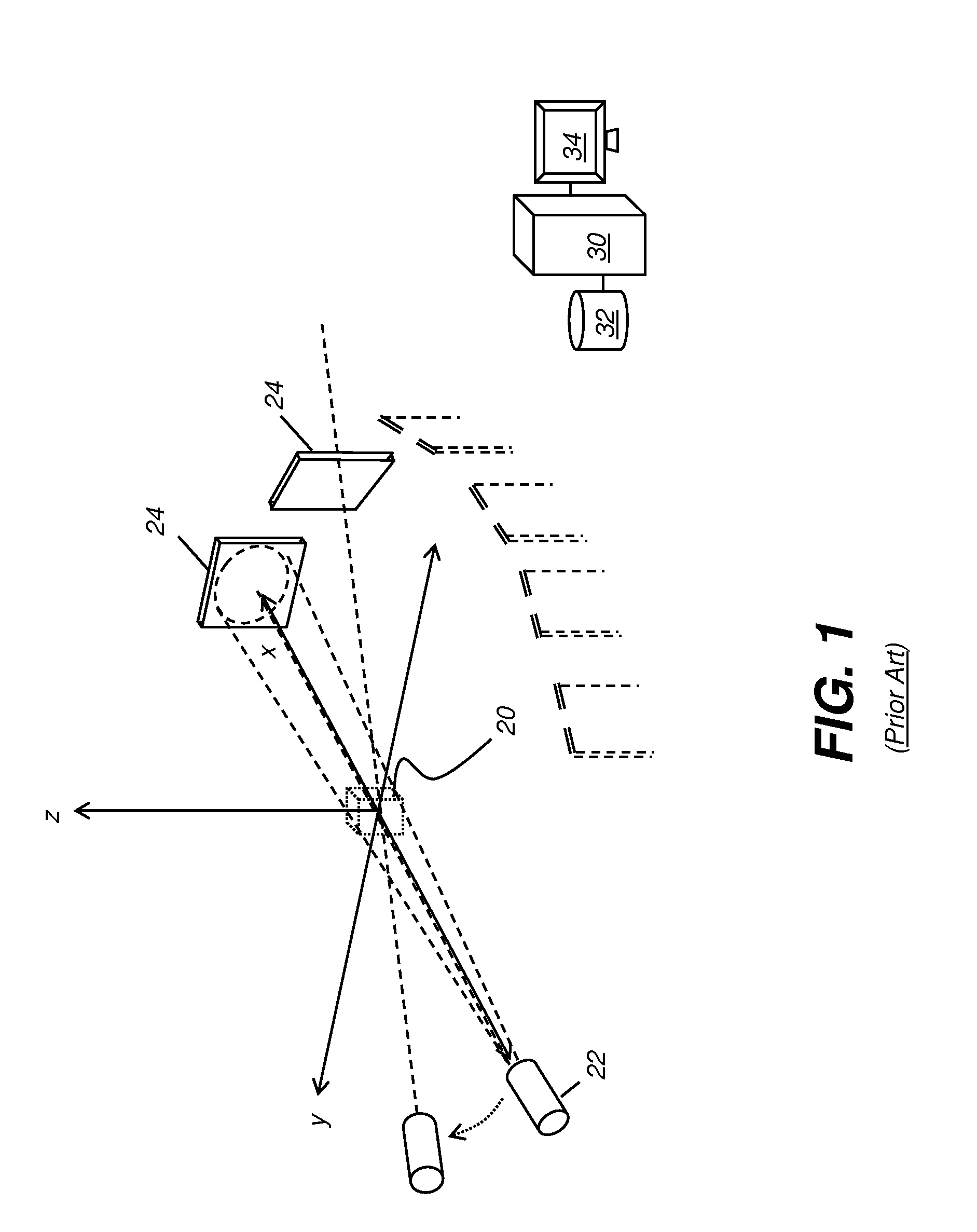
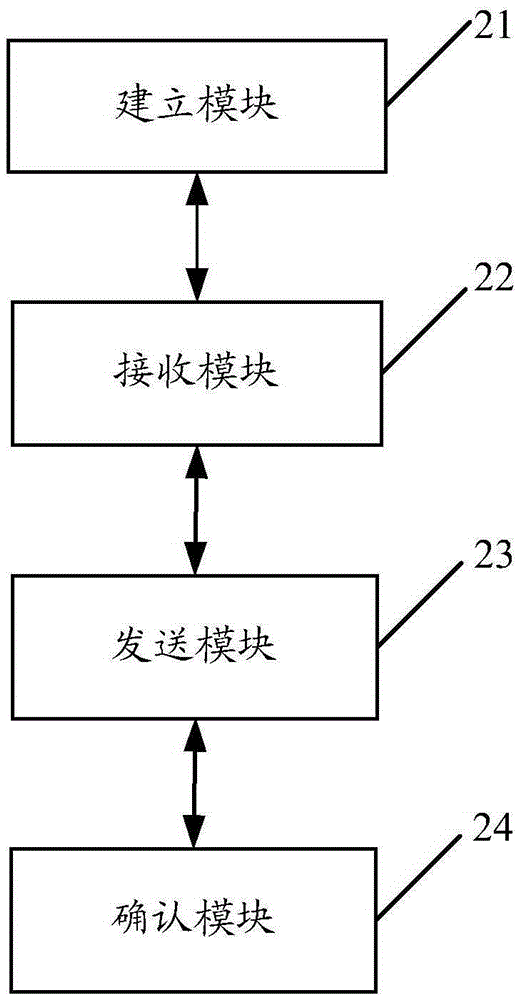
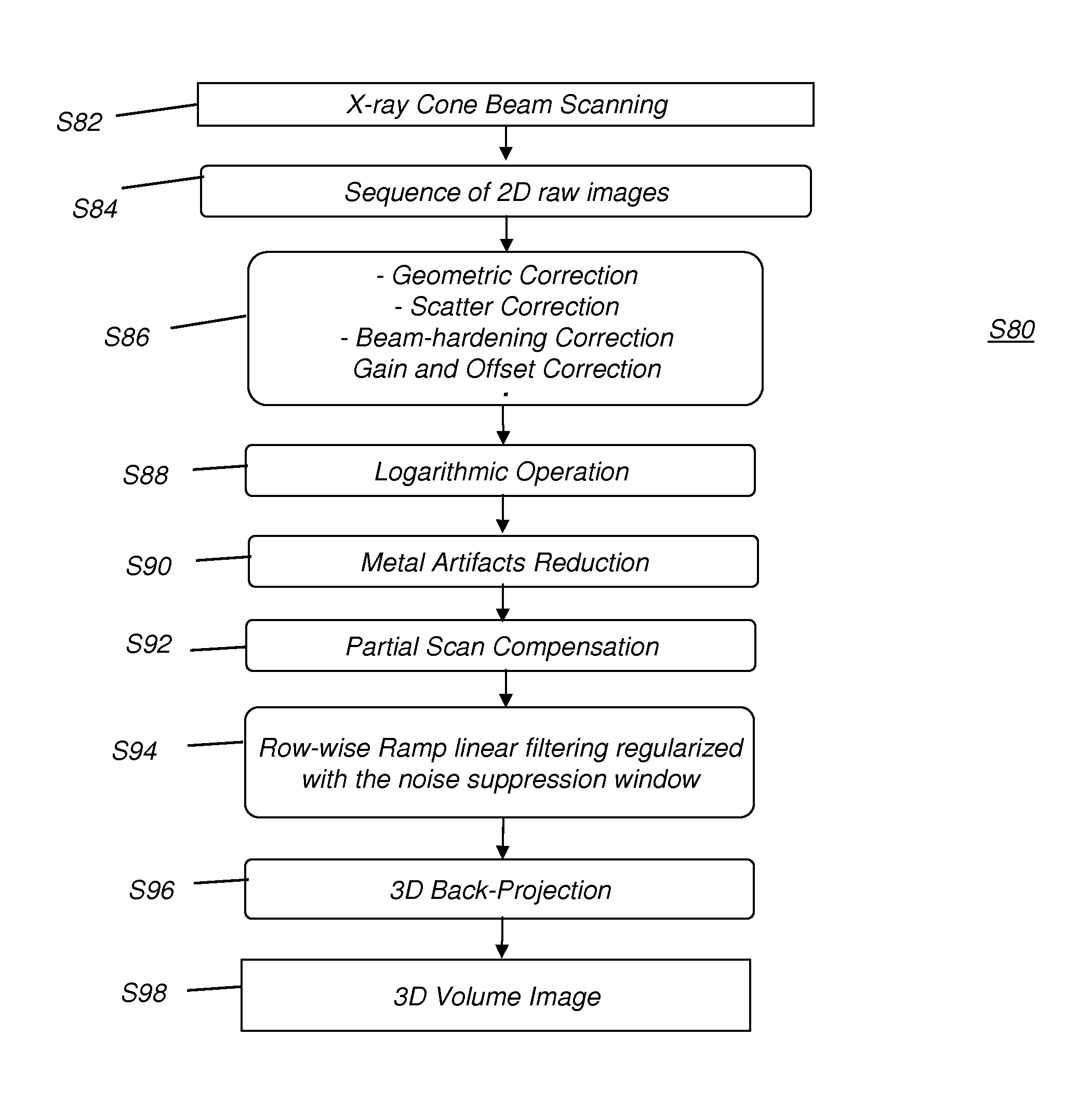
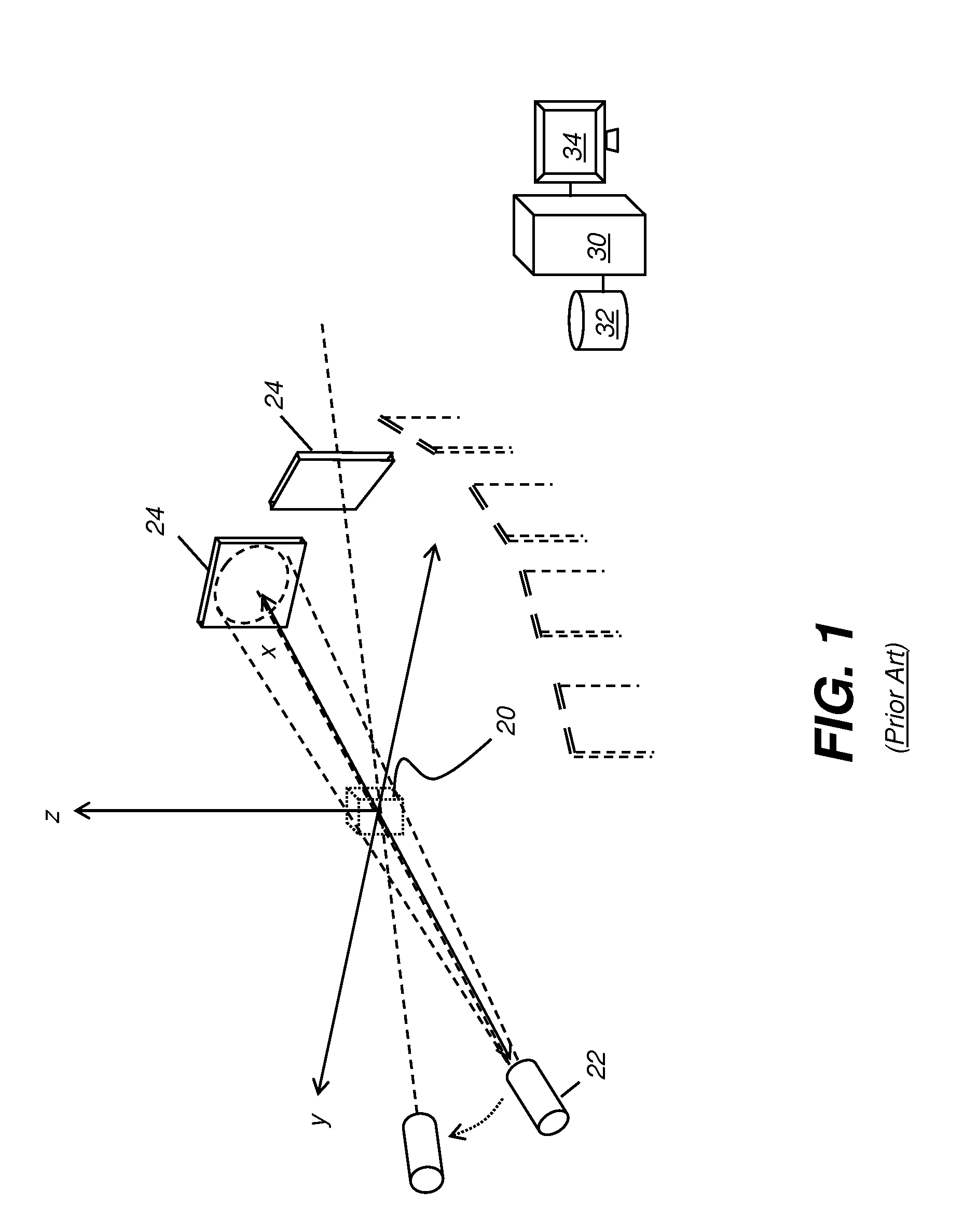
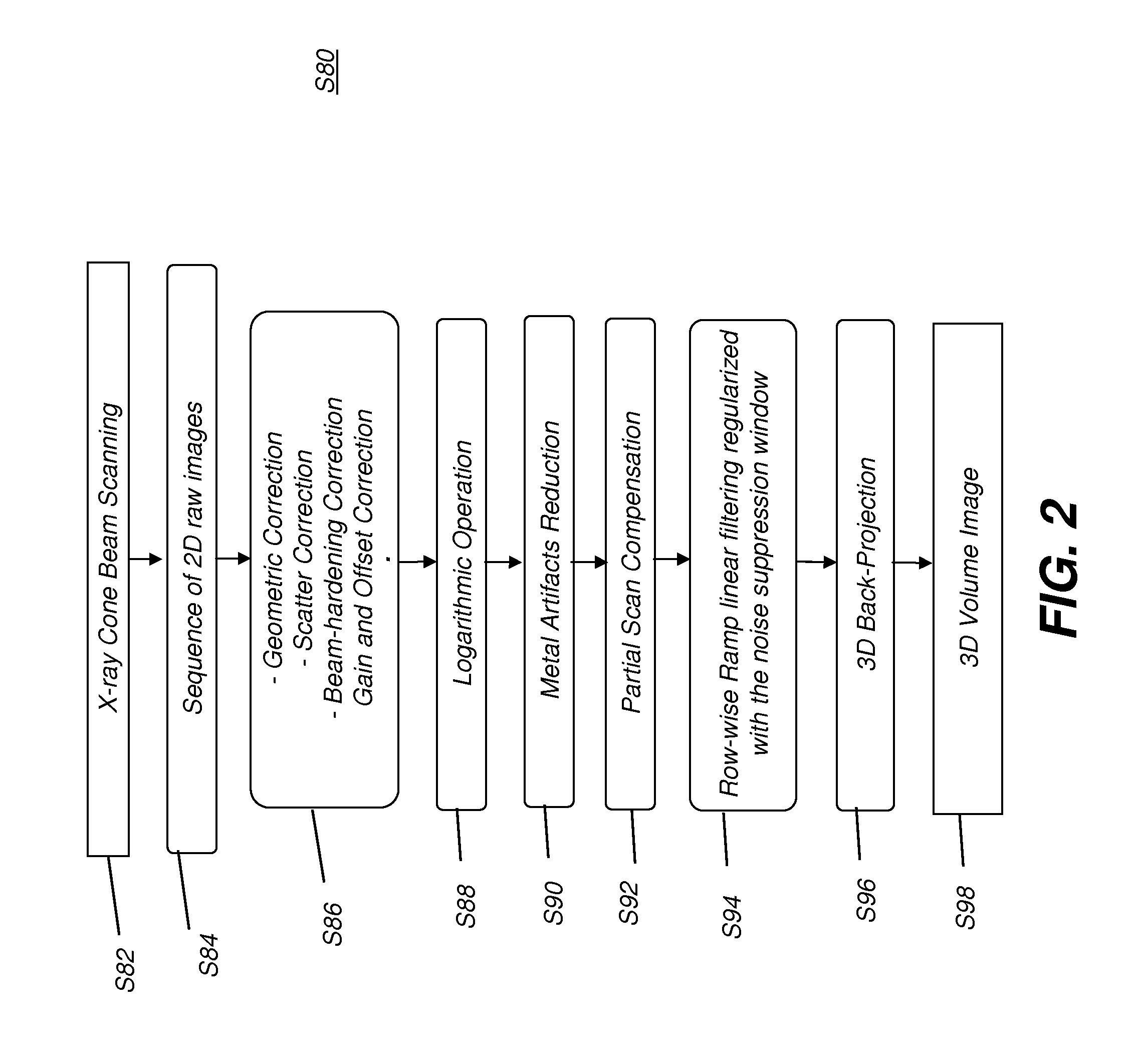
Metal artifacts reduction for cone beam ct
ActiveUS20130070991A1Reduce artifactsImprove processing efficiencyReconstruction from projectionCharacter and pattern recognitionMetal ArtifactRadiography
A method for suppressing metal artifacts in a radiographic image, the method executed at least in part on a computer, obtains at least one two-dimensional radiographic image of a subject, wherein the subject has one or more metal objects and identifies a material that forms the one or more metal objects and a radiation energy level used to generate the obtained image. The obtained radiographic image is segmented to identify boundaries of the metal object. A conditioned radiographic image is formed by replacing pixel values in the radiographic image that correspond to the one or more metal objects with compensating pixel values according to the identified material and the identified radiation energy level. The conditioned radiographic image is then displayed.
Owner:CARESTREAM HEALTH INC
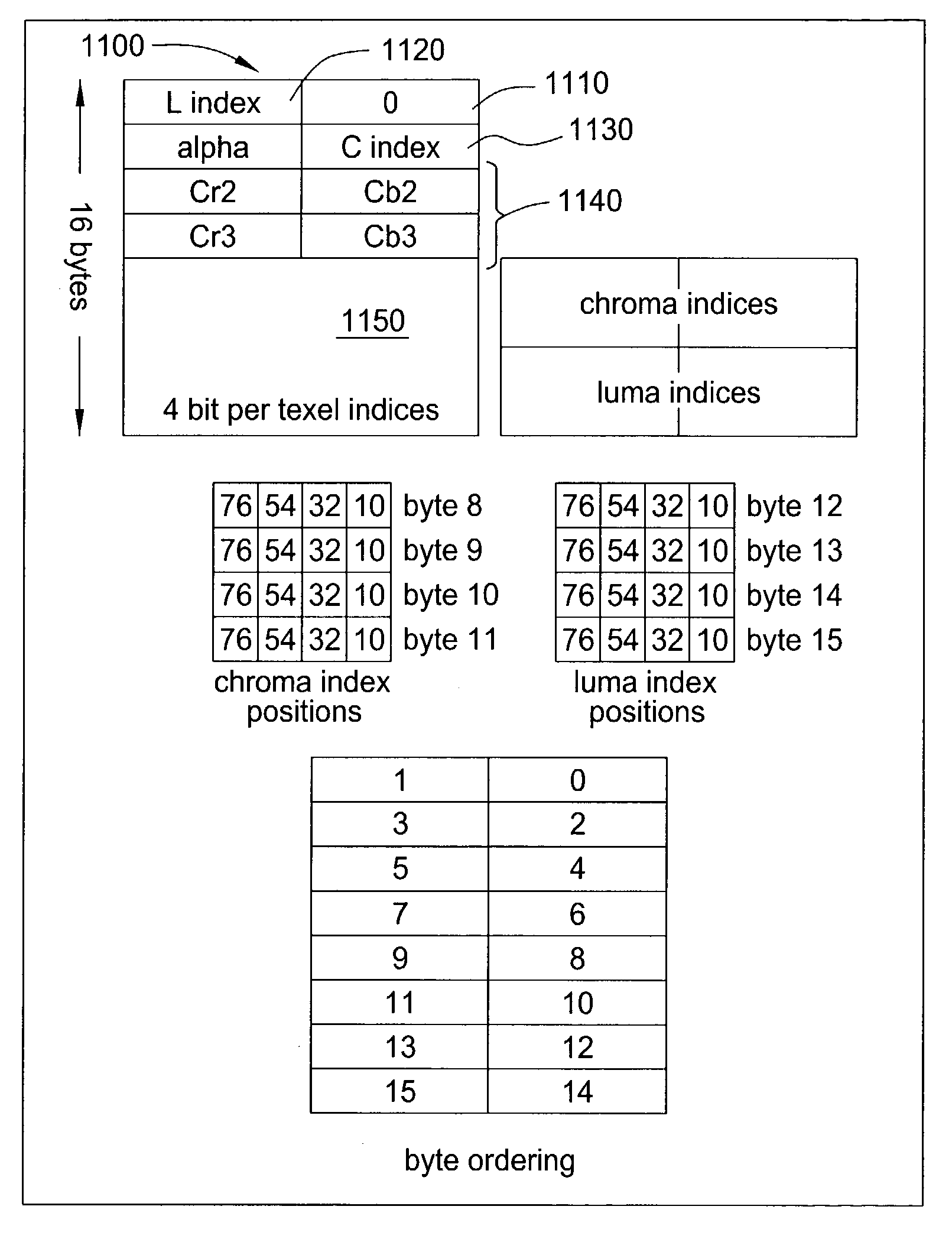
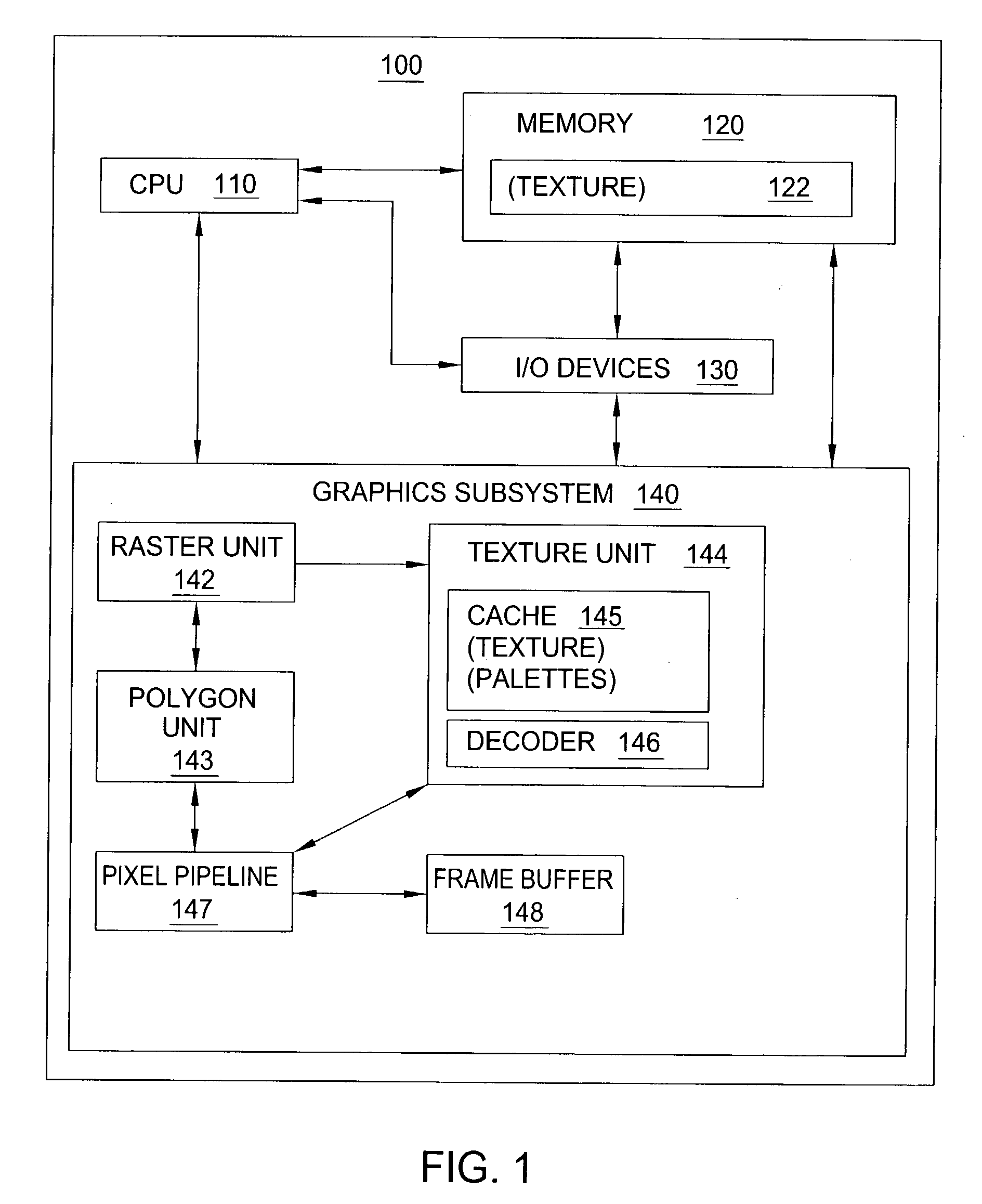
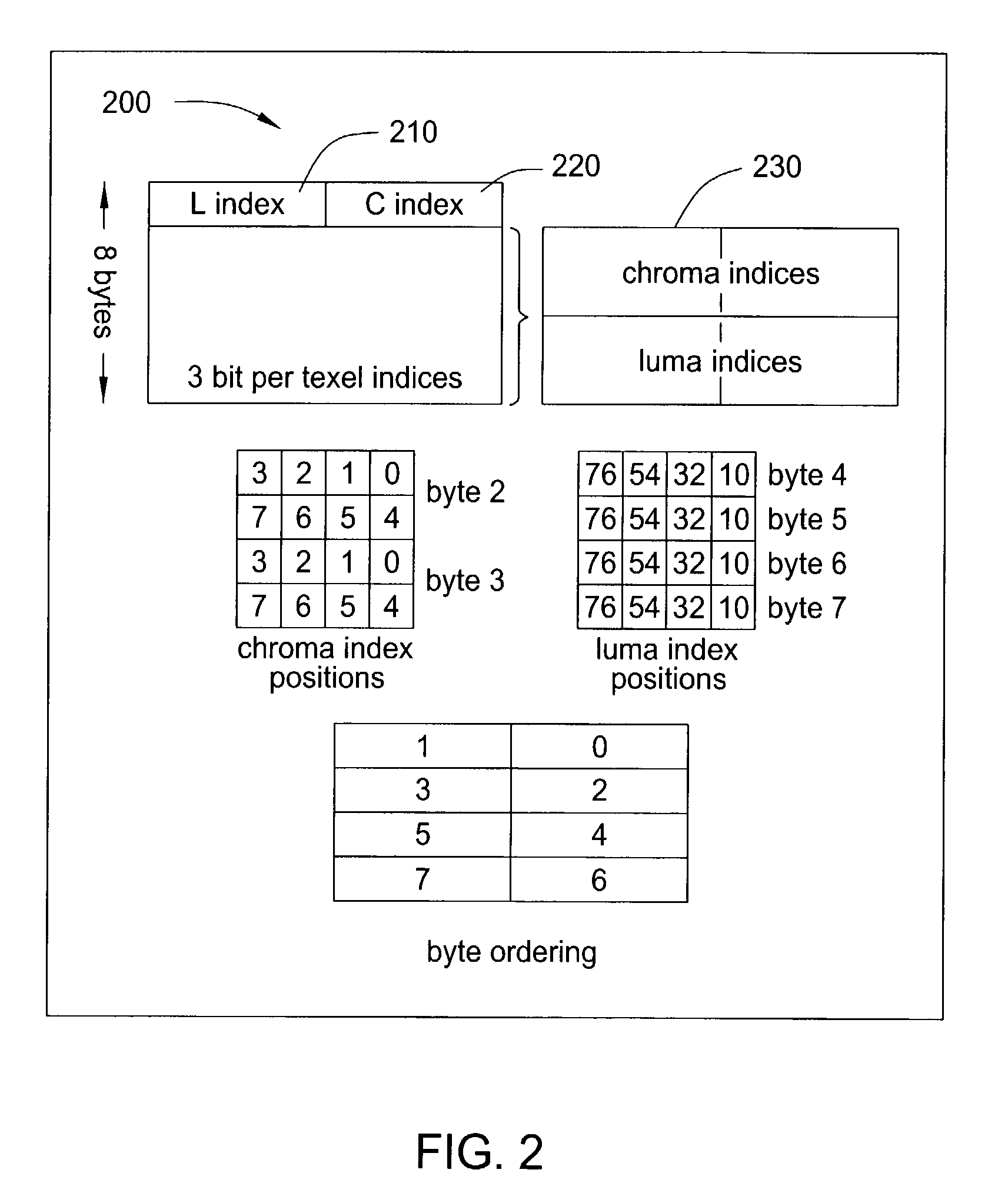
Method and apparatus for performing fixed blocksize compression for texture mapping
ActiveUS7171051B1Reduce computing needsAttenuation bandwidthCharacter and pattern recognitionImage codingPattern recognitionPresent method
Method and apparatus for providing texture and / or alpha compression. In one embodiment, the present invention incorporates stored palettes, e.g., a luminance palette and a chrominance palette such that, compressed texture data pertaining to a fixed blocksize is decoded and applied to the stored palettes to extract the texel data. In a second embodiment, the present method uses a plane to estimate the alpha value at each of the texels, and a three-bit correction factor to adjust the estimate to produce a final alpha value.
Owner:NVIDIA CORP
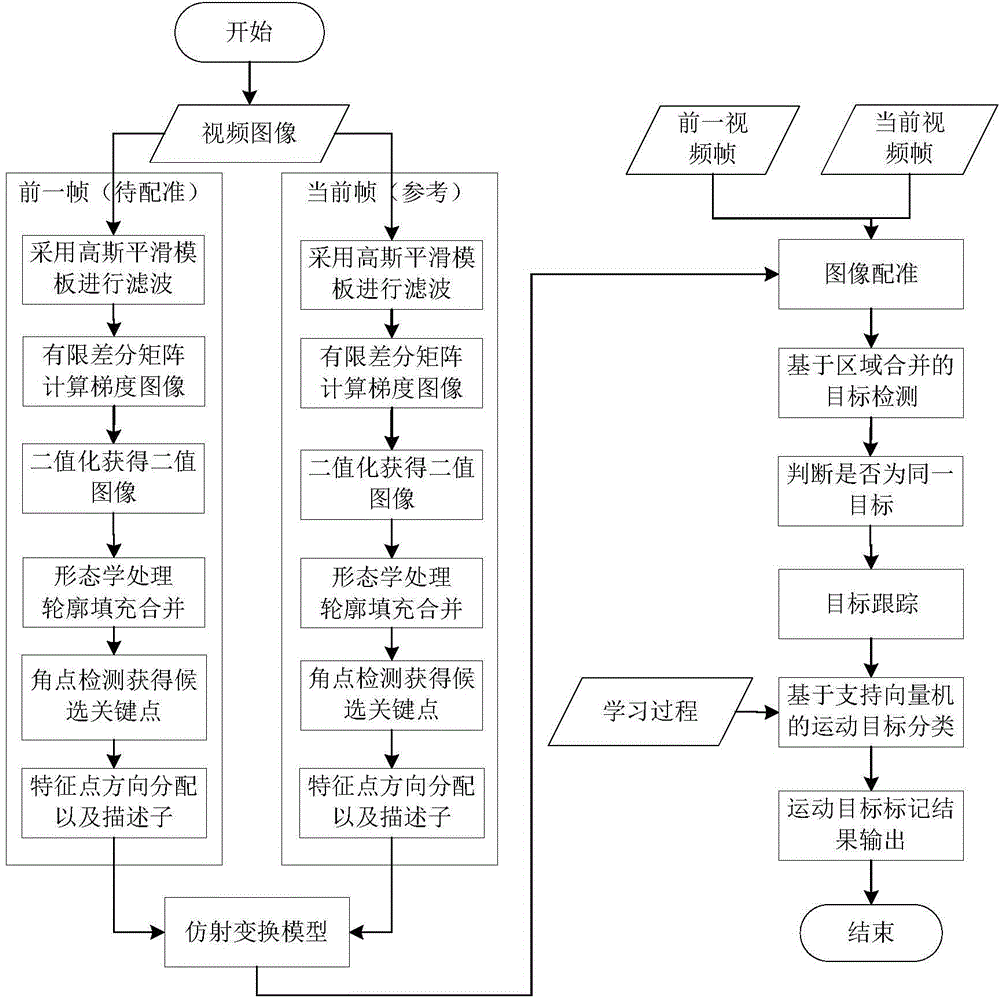
Intelligent transportation moving object detection tracking method
ActiveCN104658011AImprove time and efficiencyReduce computing needsImage analysisFrame differenceVideo sequence
The invention discloses an intelligent transportation moving object detection tracking method which is used for detecting and tracking a moving object in an intelligent transportation video. The intelligent transportation moving object detection tracking method comprises the following steps: considering objects with obvious edge characteristics such as guard bars in the middle part and on the two sides of a road in a video frame image; adopting a finite difference first-order partial derivative matrix to calculate the gradients of an input front video frame image and a back video frame image, and extracting a fine outline of an input image characteristic area; performing outline connection, area filling consolidation and morphological processing to obtain a preprocessed image; adopting an improved SIFT algorithm to extract key points from the preprocessed image, and only establishing a six-layered Gaussian pyramid for the preprocessed image, so as to ensure the situation that a few of key points can be detected when the image is changed in a small scale, meanwhile reduce redundant calculation requirement on establishing the pyramid, and improve the time efficiency of the algorithm; before frame difference, the image of the video sequence front frame and back frame is rectified by utilizing an affine transformation model obtained by the preprocessed image, so as to eliminate the influence of the video frame shift on performance detection.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
RFID (radio frequency identification) mutual authentication protocol method
ActiveCN103078741AReduce computing needsReduce storage requirementsUser identity/authority verificationCo-operative working arrangementsThree stageExclusive or
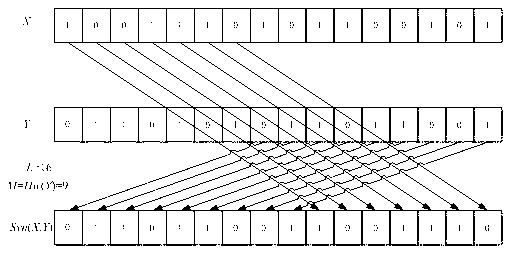
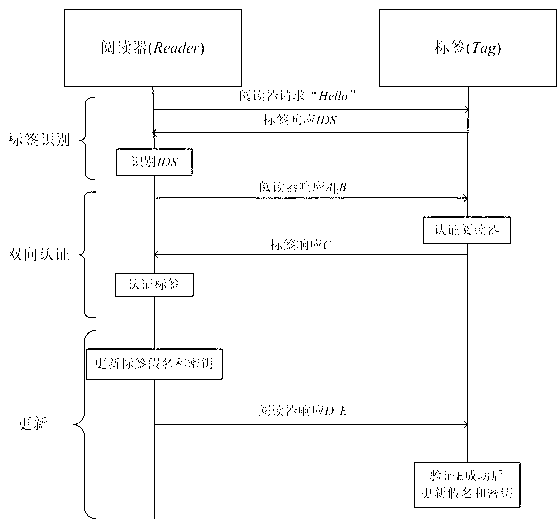
The invention relates to an RFID (radio frequency identification) mutual authentication protocol method, which comprises the following three stages: a tag identification stage, a mutual authentication stage and an update stage, wherein at the tag identification stage, a reader sends a request to a tag, and the tag returns an identification section (IDS) to the reader after receiving the request; at the mutual authentication stage, after the IDS is identified by the reader, an exclusive-or operation related to a digital synthetic operation is conducted to obtain A and B, A and B are sent to the tag, after the reader is identified by the tag through received A||B, related calculation is conducted to obtain C, C is sent to the reader, and the tag is identified by the reader; and at the update stage, after C is successfully identified by the reader, IDS and secret keys (K1 and K2) in C are updated, then D and E are calculated and sent to the tag, and after E is successfully identified by the tag, IDS and secret keys of E are updated. Only the simple digital synthetic or exclusive-or operation exists in the RFID mutual authentication protocol method. Therefore, the RFID mutual authentication protocol method has the beneficial effects that the calculation amount and storage space of the tag can be effectively reduced, various attacks such as impersonation, retransmission, tracking and denial of service can be resisted, and forward security is provided.
Owner:上海诚扬信息科技有限公司
RFID security authentication method based on EPC C-1G-2 standard
InactiveCN102497264AGuarantee forward securityReduce storage requirementsKey distribution for secure communicationUser identity/authority verificationRfid authenticationLow-performance equipment
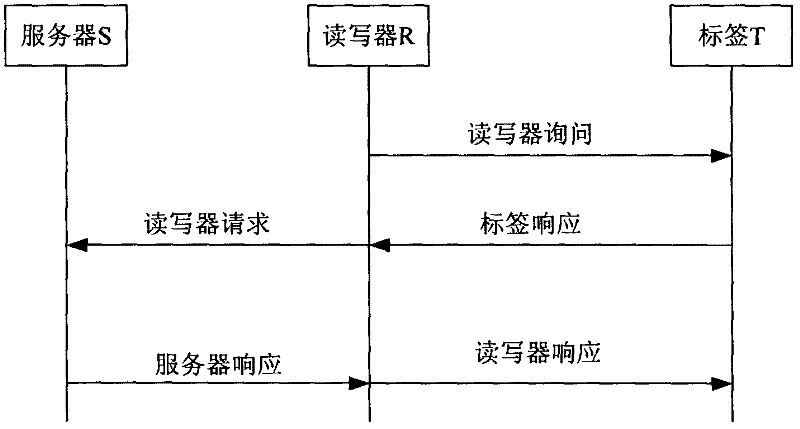
The invention discloses a RFID (Radio Frequency Identification) security authentication method based on an EPC (Electronic Product Code) C-1G-2 standard. The method is used for solving the technical problem of poor security of the existing RFID security authentication method based on the EPC C-1G-2 standard. A technical scheme is that a tag and a reader use cyclic redundancy check codes (CRC), a pseudo random number generator (PRNG) and bitwise exclusive OR operations, so that known security holes of the existing RFID authentication scheme are solved, tag tracking attacks are resisted effectively, and tag forward security is ensured. Moreover, the method meets the EPC C-1G-2 standard of the low-cost RFID tag, reduces demands on storage and calculation of the tag and can be well suitable for the requirement on application of low-performance equipment.
Owner:XIDIAN UNIV +1
Co-base installation-based transfer alignment accuracy quantitative evaluation method
ActiveCN105973268AAlignment Accuracy EvaluationAlignment assessmentMeasurement devicesComputation complexityAutocollimation
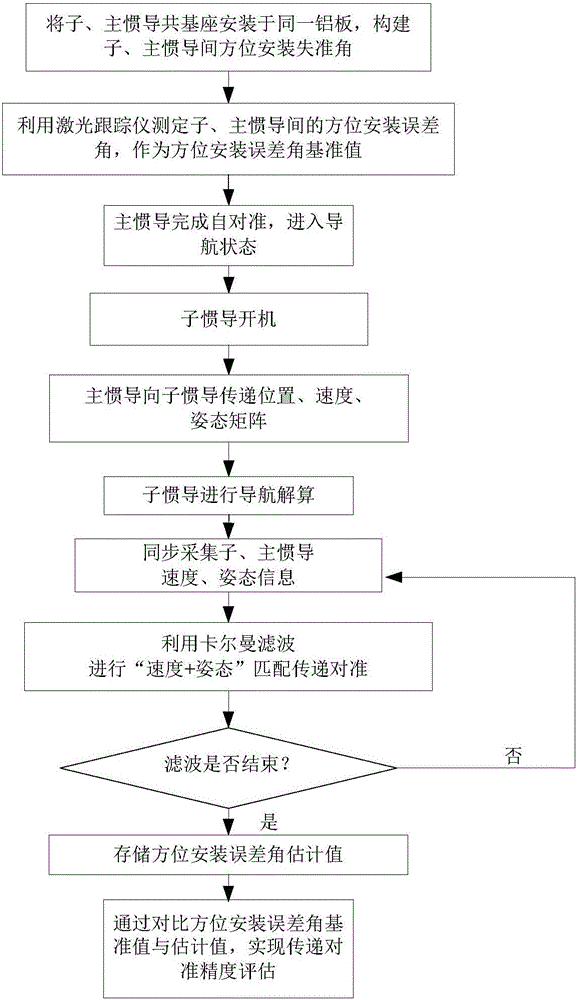
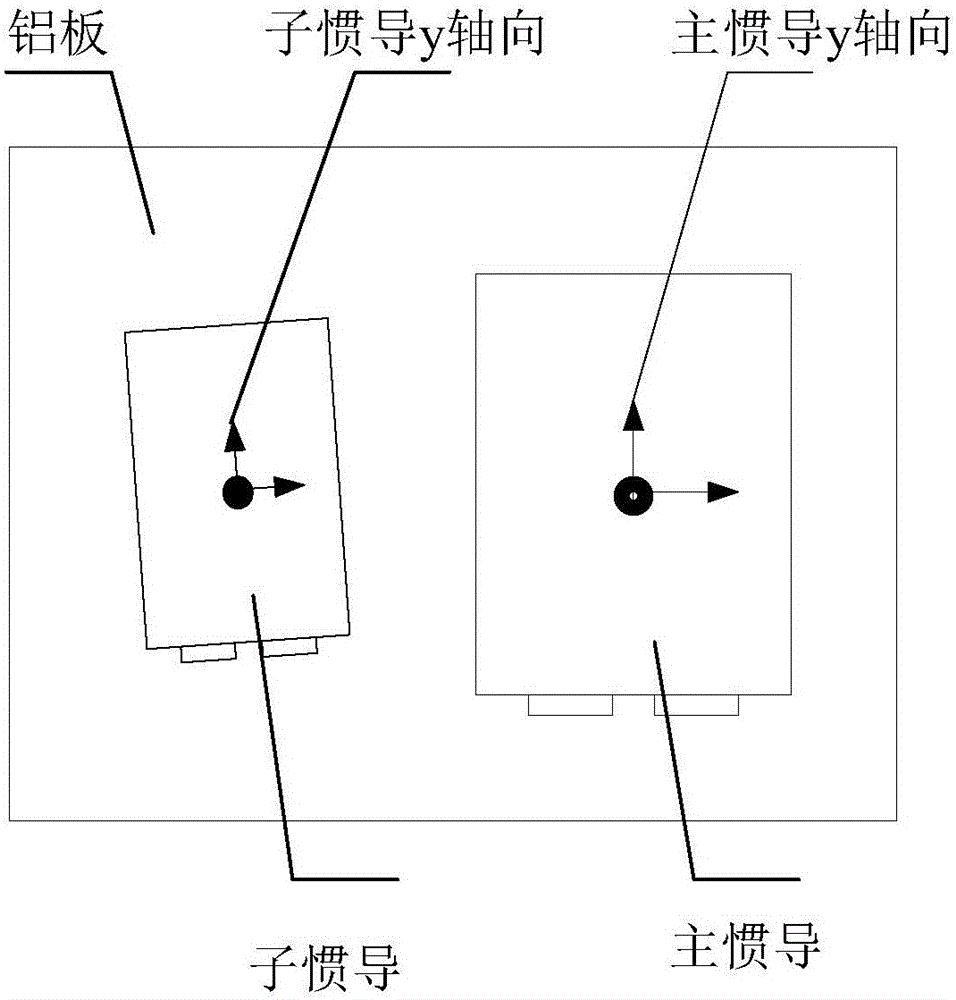
The invention belongs to the field of inertial navigation system performance assessment and relates to a co-base installation-based transfer alignment accuracy quantitative evaluation method aiming at strapdown inertial navitation system transfer alignment accuracy. The method comprises installing slave and main inertial navigation devices sharing a base on an aluminum plate, constructing slave and main inertial navigation device orientation installation misalignment angles, putting the aluminum plate with the slave and main inertial navigation devices on a high precision rotary table, guiding the y axis of the main inertial navigation device to point to the true north direction through an optical sighting telescope, measuring slave and main inertial navigation device y axis orientation installation error angles as orientation installation error angle reference values through a laser tracker and starting the main inertial navigation device to carry out autocollimation. The method can acquire alignment accuracy evaluation reference before transfer alignment and through comparison between the reference value and the evaluation value, alignment accuracy quantitative evaluation is realized. The method is free of slave inertial navigation device navigation calculation and smooth calculation after alignment, greatly reduces computation complexity and data storage demands and realizes repeated tests in short time.
Owner:HARBIN ENG UNIV
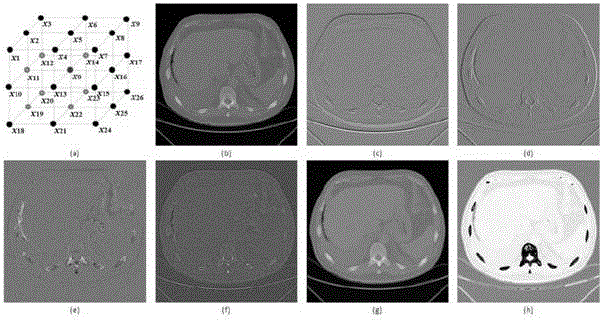
Removal method and system for bone tissue in 3D CT (Three Dimensional Computed Tomography) image
InactiveCN104616289AGuaranteed accurate extractionStrong descriptive abilityImage enhancementImage analysisFeature vectorComputed tomography
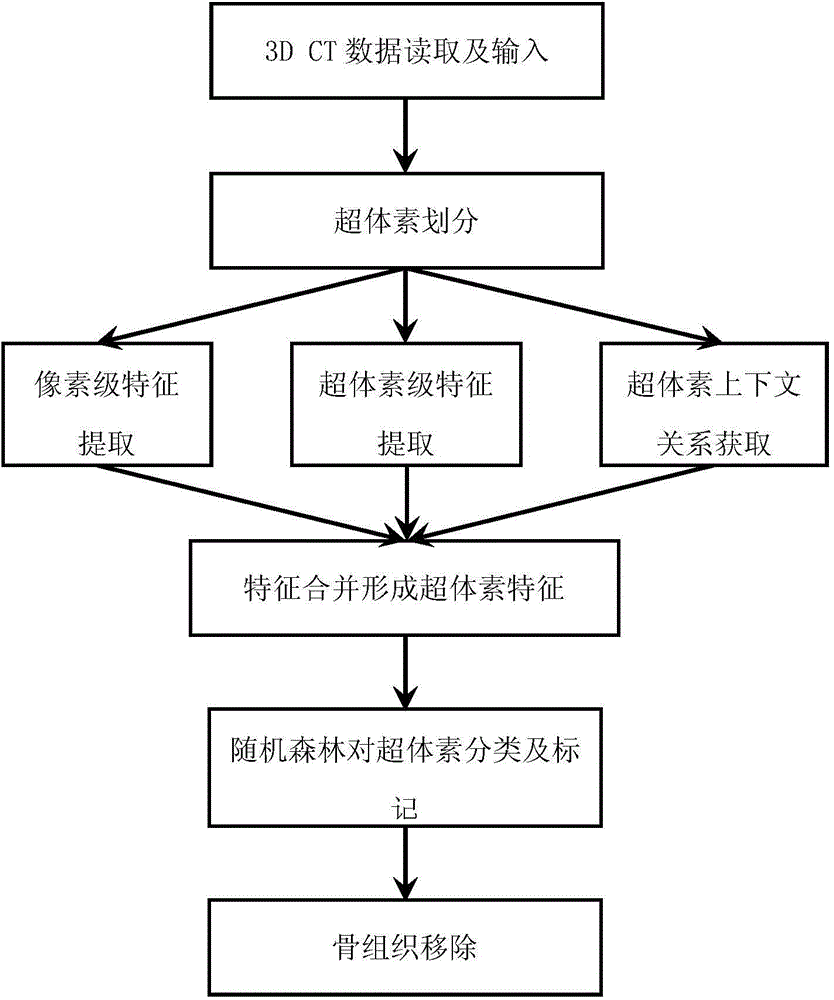
The invention discloses a removal method and system for a bone tissue in a 3D CT (Three Dimensional Computed Tomography) image. The method comprises the following steps: reading a 3D CT image data sequence and dividing the sequence by using a clustering method; describing each marked supervoxel from supervoxel level, pixel level and supervoxel neighborhood relation level respectively to obtain a characteristic vector for describing each supervoxel; constructing a supervoxel training set, training a classifier by using the characteristic vector corresponding to the supervoxel, then classifying the supervoxel by using the trained classifier and marking the category; if a certain supervoxel is marked as the bone tissue according to a supervoxel mark value, removing the supervoxel from the original CT data, and otherwise, remaining. The supervoxel obtained by dividing the 3D CT data is used as a basic operation unit, bone tissue templates on different parts are not required to be learnt and trained, and meanwhile the problem of inaccurate bone tissue extraction caused by mismatching of the templates is also avoided.
Owner:XIAN HWATECH MEDICAL INFORMATION TECH
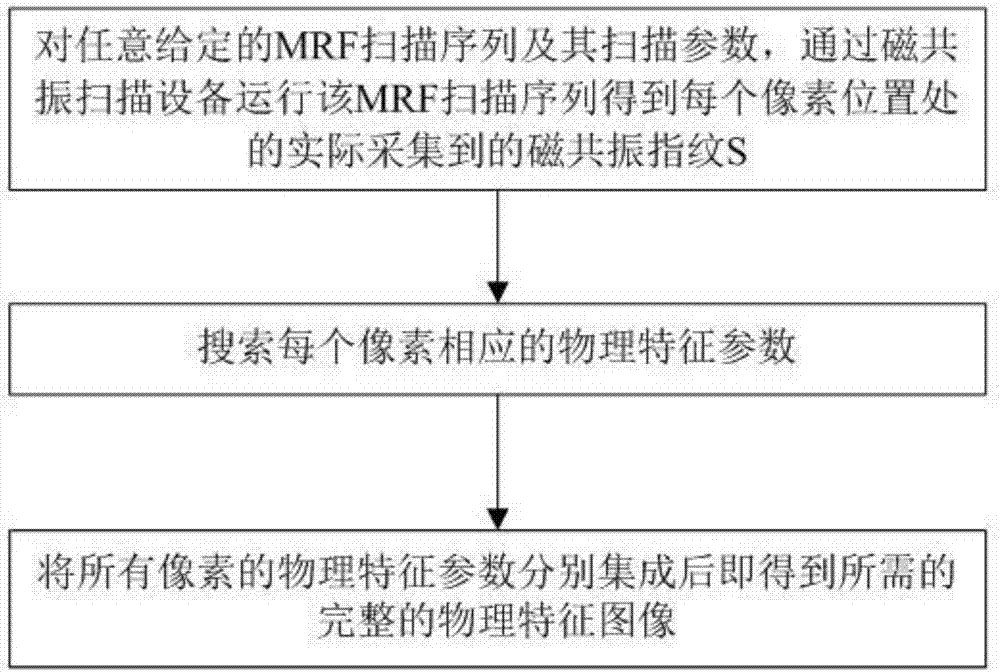
Magnetic resonance fingerprint imaging based quick dictionary search method
ActiveCN107194354AShorten the timeReduce complexityCharacter and pattern recognitionMeasurements using magnetic resonanceResonanceComputer science
The invention discloses a magnetic resonance fingerprint imaging based quick dictionary search method. The magnetic resonance fingerprint imaging based quick dictionary search method comprises the steps of S1, running an MRF scanning sequence for any given MRF scanning sequence and scanning parameters thereof by a magnetic resonance scanning device to obtain a magnetic resonance fingerprint S actually collected at each pixel position; S2, searching a physical characteristic parameter corresponding to each pixel, wherein the step of searching the physical characteristic parameter corresponding to one pixel comprises the sub-steps of matching the magnetic resonance fingerprint signal S of the pixel with the corresponding signal directory D and finding a matching item most proximal to the magnetic resonance fingerprint S of the pixel, and the most proximal matching item is the physical characteristic parameter of the pixel; and S3, integrating the physical characteristic parameters of all the pixels respectively to obtain a needed complete physical characteristic image. The magnetic resonance fingerprint imaging based quick dictionary search method can efficiently reduce the search calculation complexity, can reduce the calculation time and can improve the search efficiency.
Owner:HANGZHOU NORMAL UNIVERSITY
Water and fat separation method based on under-sampling k-space data
ActiveCN102779327AConvenience to mergeReduce the amount of calculationImage enhancementSystem matrixResonance
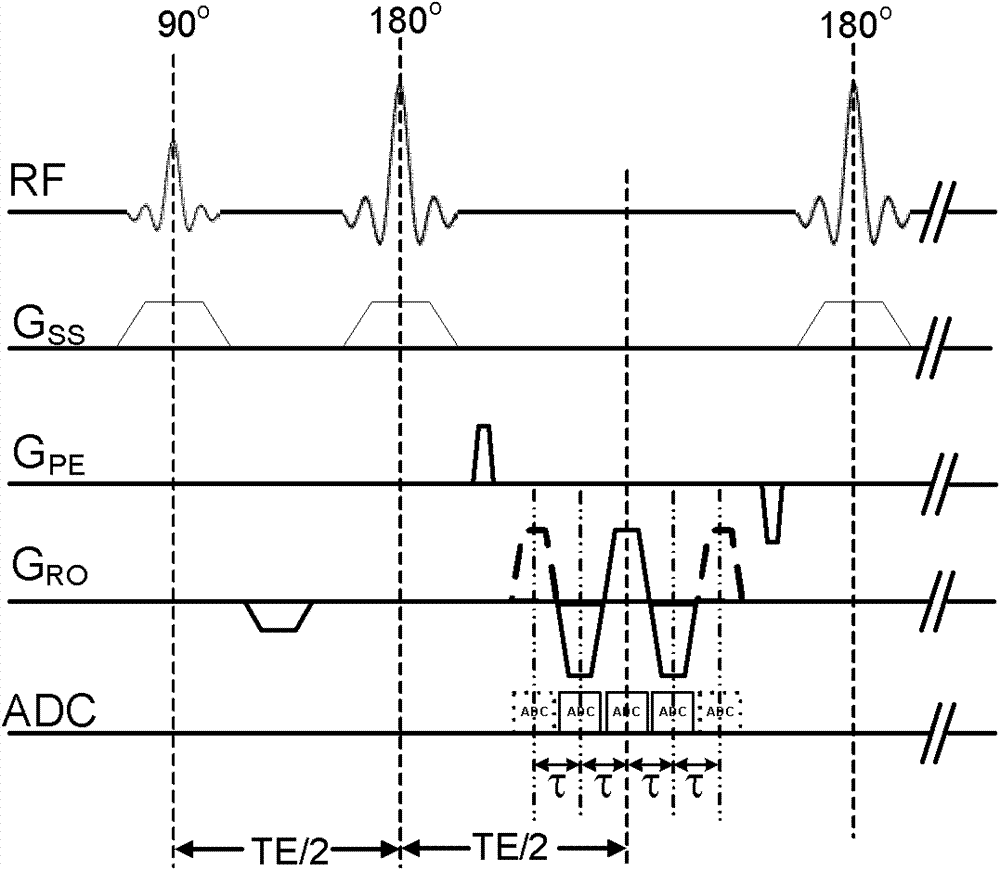
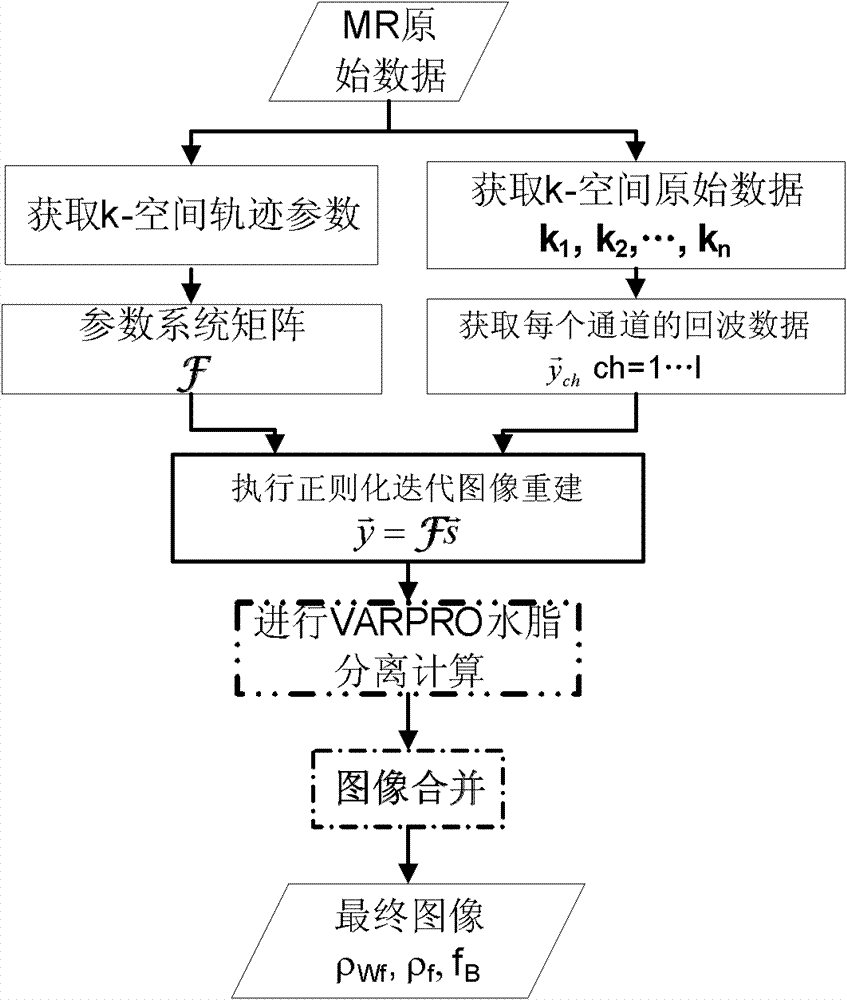
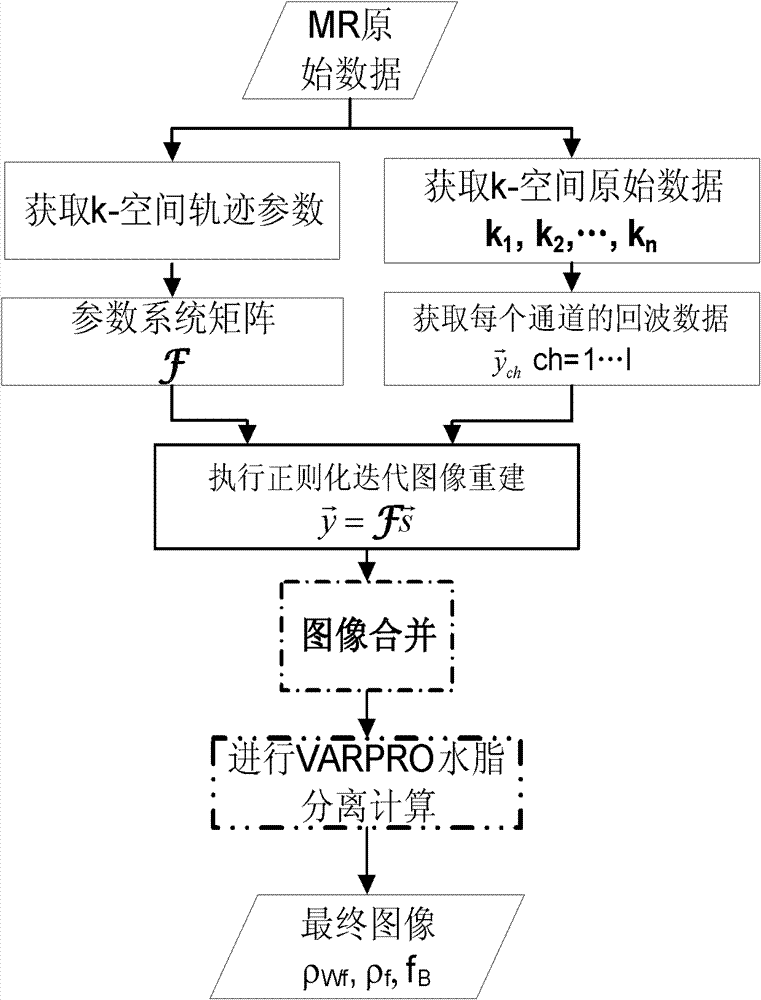
The invention discloses a water and fat separation method based on under-sampling k-space data. The method includes steps of, step one, respectively acquiring k-space trajectory parameters and k-space raw data according to magnetic resonance (MR) raw data; step two, selecting a parameter system matrix according to the k-space trajectory parameters; step three, acquiring echo data of each channel according to the k-space raw data; step four, executing regularization iteration image reconstruction by using the parameter system matrix and the echo data of each channel; and step five, subjecting reconstructed images to variable projection (VARPRO) water and fat separation calculating to obtain a final image. The water and fat separation method based on the under-sampling k-space data is applicable to more scanning tracks, and by means of a VARPRO water and fat separation algorithm, a phase diagram, a B0 field image, a water image and a fat image which are irrelevant to main magnetic field inhomogeneity are separated; the water and fat separation method based on the under-sampling k-space data has advantages of VARPRO iteration field image calculating and is insensitive to seed points; and the water and fat separation method based on the under-sampling k-space data is smaller in calculated amount and fewer in calculating requirements, image merging is easier to finish, and a system function which is capable of achieving parallel imaging can be introduced.
Owner:SHENZHEN UNITED IMAGING HEALTHCARE CO LTD
Intelligent speech recognition system and method
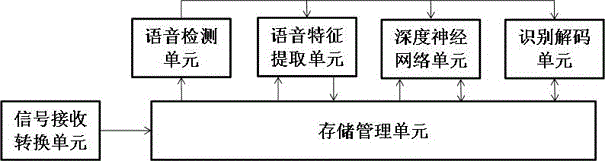
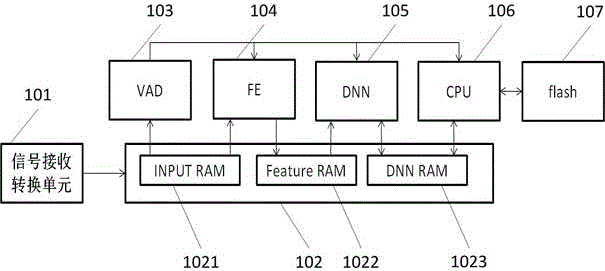
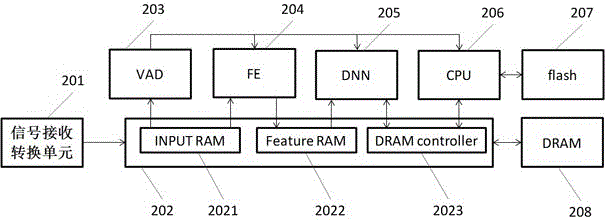
ActiveCN105976808AImprove computing powerReduce power consumptionSpeech recognitionEnergy efficient computingFeature extractionEngineering
The invention relates to the technical field of electronics, and particularly relates to an intelligent speech recognition system. The intelligent speech recognition system comprises a signal receiving and converting unit, a storage management unit, a speech detection unit, a speech feature extraction unit, a deep neural network unit and a recognizing and decoding unit. The invention further discloses an intelligent speech recognition method containing the intelligent speech recognition system. The system and the method provided by the invention significantly improve the calculation performance of a chip under the condition of the same chip area compared with a CPU or a GPU, and reduce the power consumption and the cost.
Owner:成都启英泰伦科技有限公司
Method and device for acquiring energy spectrum, and device for setting energy window
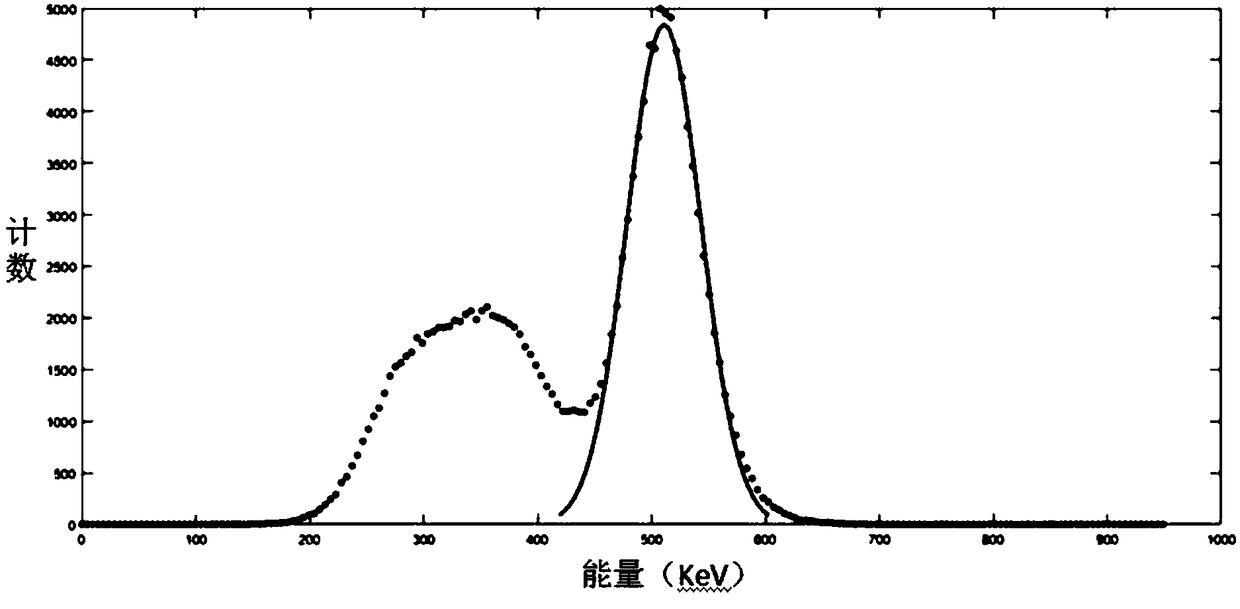
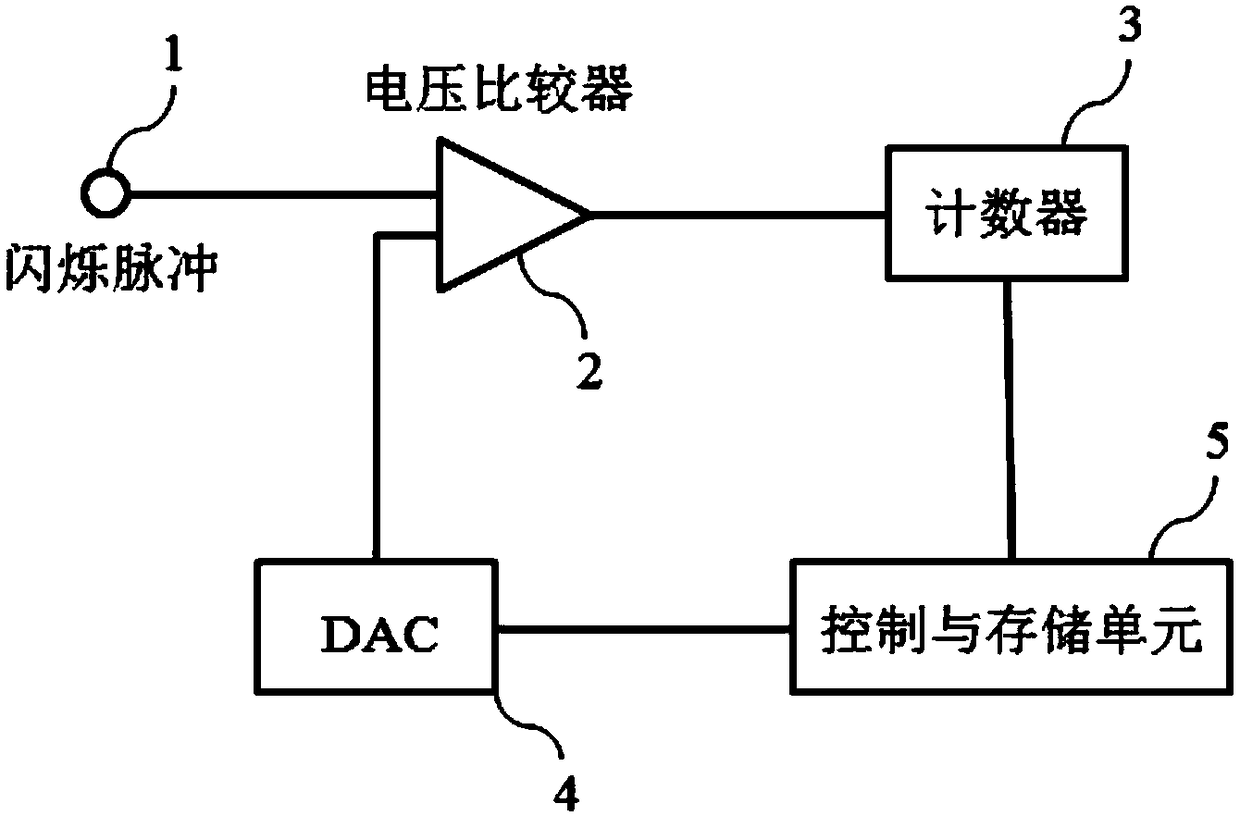
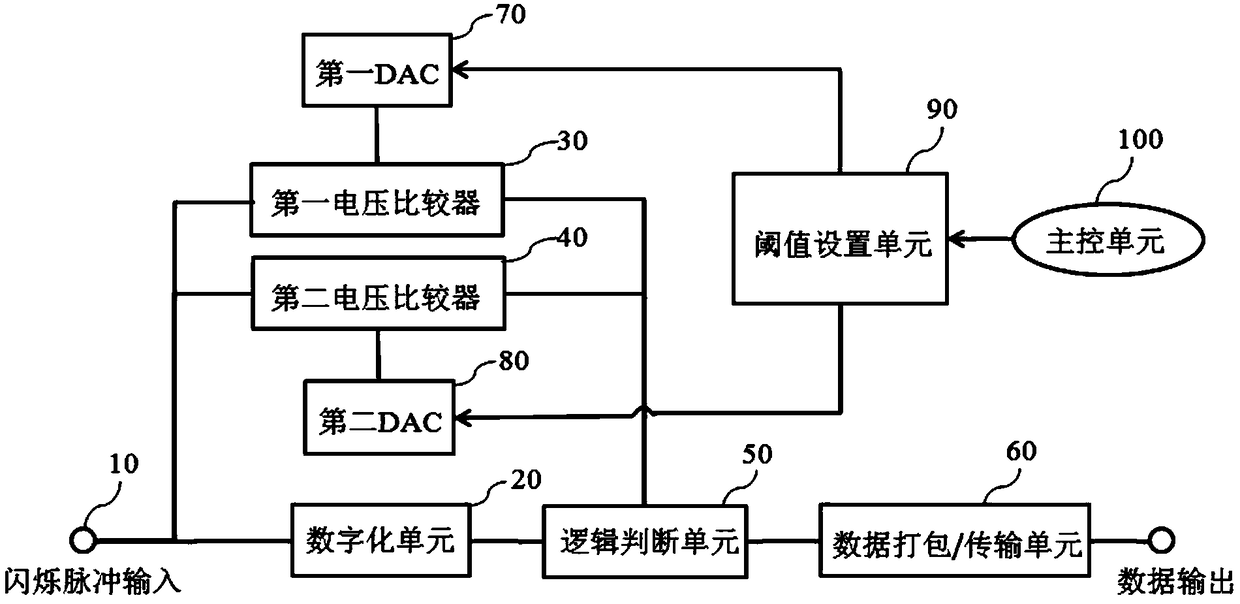
ActiveCN108169789AReduce usageHigh speed useX-ray spectral distribution measurementNuclear energy generationEnergy windowPulse number
The invention provides a method and device for acquiring an energy spectrum and a device for setting an energy window. A voltage comparator is in communication connection with a detector module and receives a flicker pulse signal sent by the detector module; a DAC (digital to analog converter) is in communication connection with the voltage comparator and transmits threshold information to the voltage comparator; the voltage comparator sends a flicker pulse signal that meets the threshold information to a counter; a control and storage unit is coupled to the counter and stores and records thecount information, and the control and storage unit is also connected to the DAC and stores and records the threshold information. The method comprises the following steps of: setting a threshold of the DAC and resetting the counter; using the counter to record the pulse number of flicker pulses whose amplitude exceeds the threshold within a T time period; setting the threshold of the DAC again, resetting the counter, and then recording the pulse number of flicker pulses whose amplitude exceeds the threshold within the T time period, and repeating the operation until the threshold is zero. Themethod and device for acquiring the energy spectrum and the device for setting the energy window can effectively reduce the cost and complexity of systems such as PET and SPET, and reduce the system's demand for computing resources and time.
Owner:RAYMEASURE MEDICAL TECH CO LTD SUZHOU
Device and associated methodoloy for encoding and decoding of data for an erasure code
ActiveUS20180048333A1Reduce computing needsEfficiently solve multiple pixelsCode conversionError correction/detection by combining multiple code structuresComputer hardwareErasure code
Owner:ZEBWARE AB
Detector for determining a position of at least one object
ActiveUS20200348385A1Reduce possible numberReduce computing needsImage analysisDirection/deviation determining electromagnetic systemsLight beamReference image
Owner:TRINAMIX GMBH
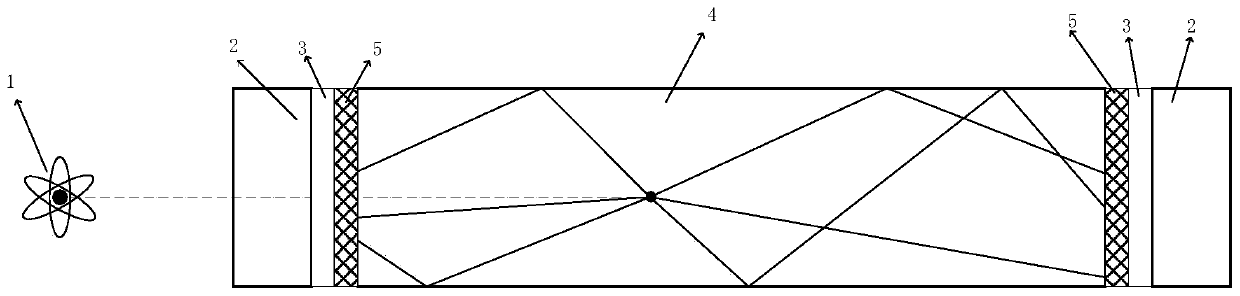
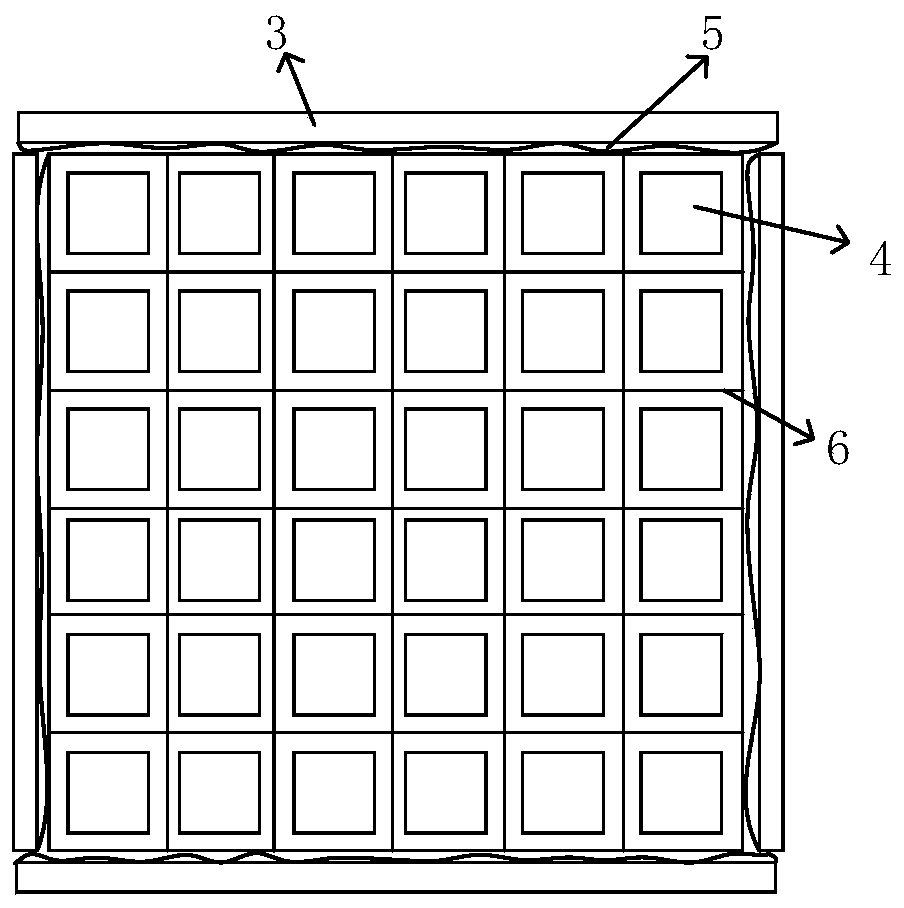
Positron imaging method and system of dual-readout PET detector
PendingCN110632641AHigh sensitivityImprove imaging effectComputerised tomographsTomographyAnalog-to-digital converterDigital converter
The invention discloses a positron imaging method and system of a dual-readout PET detector. According to the system, photoelectric devices are arranged at two ends of crystal bar for coupling and areused for acquiring optical signal data in the crystal to carry out scintillation pulse data coupling; measured amplitude height of the pulse and arrival time of the pulse in the photoelectric devicesare recorded; and a difference value of the pulse arrival time and the amplitude height of the pulse are calculated and the position of the deposition energy of the gamma photon in the crystal is estimated. In addition, the method comprises the following steps: digitalizing a scintillation pulse coupling signal acquired by a photoelectric detector through an analog-to-digital converter; calculating the position of a photon conversion interaction depth according to the ratio of signal amplitudes at two ends of the detector; and performing interaction effect depth information reconstruction according to the energy, time and position information of the obtained signal. According to the invention, the action depth of the photon in the crystal is accurately located and action depth informationis obtained; parallax error correction is carried out; the interaction depth effect is effectively reduced; and the PET imaging effect is improved.
Owner:南昌华亮光电有限责任公司
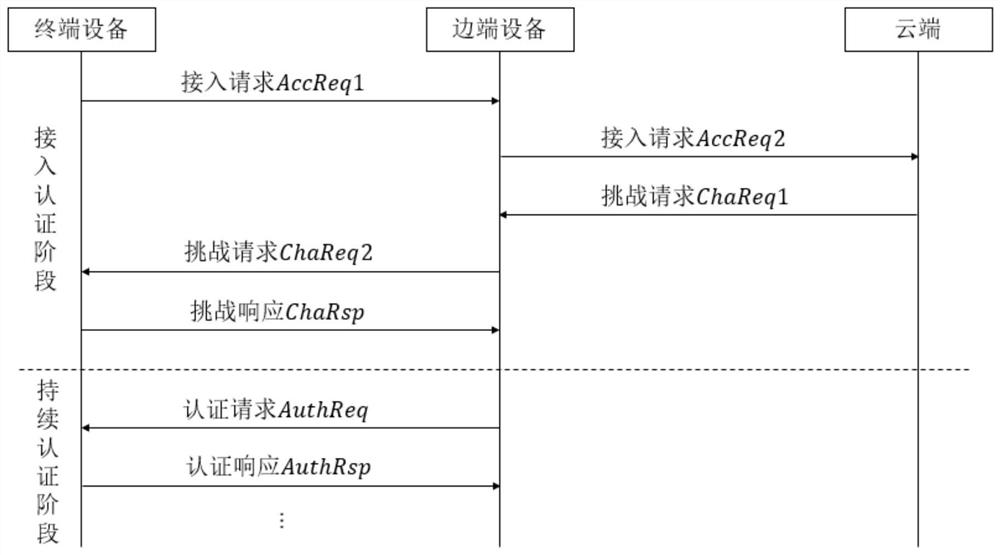
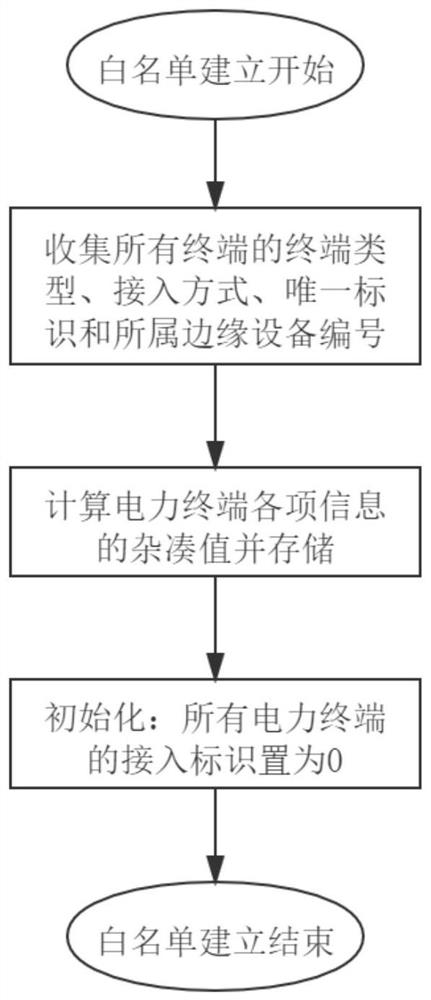
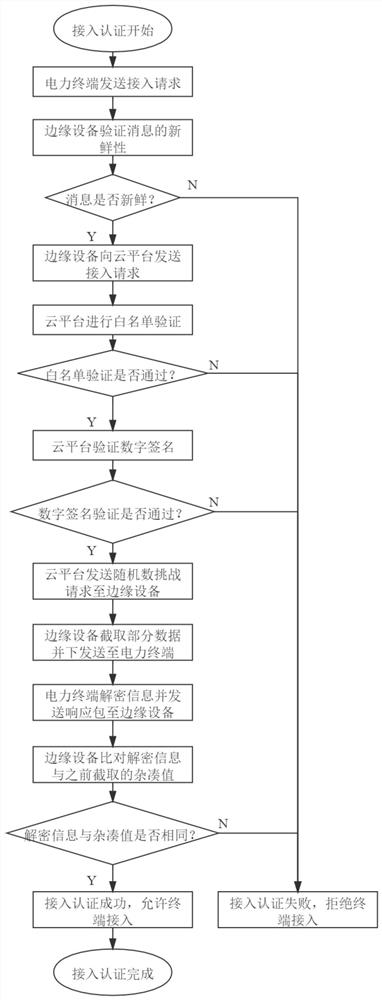
Power terminal cloud edge-end cooperative security access authentication method based on edge computing
ActiveCN113395166AReduce computing pressureReduce consumptionData processing applicationsEncryption apparatus with shift registers/memoriesDigital signatureEdge computing
The invention relates to access authentication of power terminal equipment, and aims to provide a power terminal cloud edge-end cooperative security access authentication method based on edge computing. The method comprises one-time authentication when the power terminal is accessed and continuous authentication after the power terminal is accessed, wherein the one-time authentication is jointly participated by the power terminal, the edge device and the cloud platform, and the continuous authentication is only participated by the power terminal and the edge device. According to the invention, a continuous authentication link is introduced to enhance security, and a lightweight identity authentication mechanism is realized by a password and non-password means. According to the method, mechanism design is carried out by using the white list, the digital signature and the challenge response, so that feasibility is guaranteed; in terms of security, one-time complex authentication is considered to fully ensure access security during access, and continuous simple authentication after access is used as a supplement to improve the security; and the advantages of edge calculation are fully played in conciseness, and a simple authentication mechanism is selected to reduce calculation pressure.
Owner:ZHEJIANG UNIV +1
Spectral shaping of multicarrier signals
InactiveCN102396173AReduce calculationSave battery resourcesModulated-carrier systemsOrthogonal multiplexFrequency spectrumFourier transform on finite groups
Owner:HUAWEI TECH CO LTD
Abnormal signal orientation method in pipeline
ActiveCN103032682AMeet the site installation conditionsReliable determination of the direction of propagationPipeline systemsSignal onElectrical polarity
The invention provides an abnormal signal orientation method in a pipeline. The method comprises the following steps of: acquiring and extracting output signals of two transmitters of a preset time length as first acquired data; performing normalization processing, mean adjustment and bipolar processing of the output signals on two frames of data of the first acquired data to obtain second acquired data; searching a signal maximum extreme value from the two frames of data of the second acquired data according polarity of the signal and performing trailing edge processing of an abnormal signal on the two frames of data of the second acquired data to obtain third acquired data; performing forward and backward bidirectional one-time linear interpolation of M-1 points on any path of signal for the third acquired data to form two interpolation sequences; and calculating cross correlation coefficient curves of the two sequences and another signal sequence respectively to obtain propagation direction of a pipeline leakage signal. According to the method, the propagation direction of the abnormal signal in the pipeline can be reliably determined.
Owner:BEIJING UNIV OF CHEM TECH
Valve internal leakage detecting method based on sonic wave sensors
ActiveCN104764564AImprove detection efficiencyReduce complexityFluid-tightness measurementAcoustic emissionAcoustic wave
The invention discloses a valve internal leakage detecting method based on sonic wave sensors. The method comprises the following steps that W point first sampling signals, detected by the valve upstream sonic wave sensor, of first sonic wave signals inside a pipeline and W point second sampling signals, detected by the valve downstream sonic wave sensor, of second sonic wave signals are obtained, wavelet packet decomposition is carried out on the first sampling signals and the second sampling signals through first preset dimension and second preset dimension, and first wavelet packet entropy of the first sampling signals and second wavelet packet entropy of the second sampling signals are calculated; whether internal leakage of a tested valve occurs or not is determined by comparing the first wavelet packet entropy with a first preset wavelet packet entropy threshold value and comparing the second wavelet packet entropy with a second preset wavelet packet entropy threshold value. By means of the method, a traditional high-frequency acoustic emission sensor is not needed, the high real-time performance requirement and the complexity degree of signal processing in judgment of internal leakage of the valve are greatly lowered, the computing workload and the memory demand quantity are greatly reduced, and engineering implementation is facilitated.
Owner:BEIJING UNIV OF CHEM TECH
Method and devices for a reduced repair and update erasure code
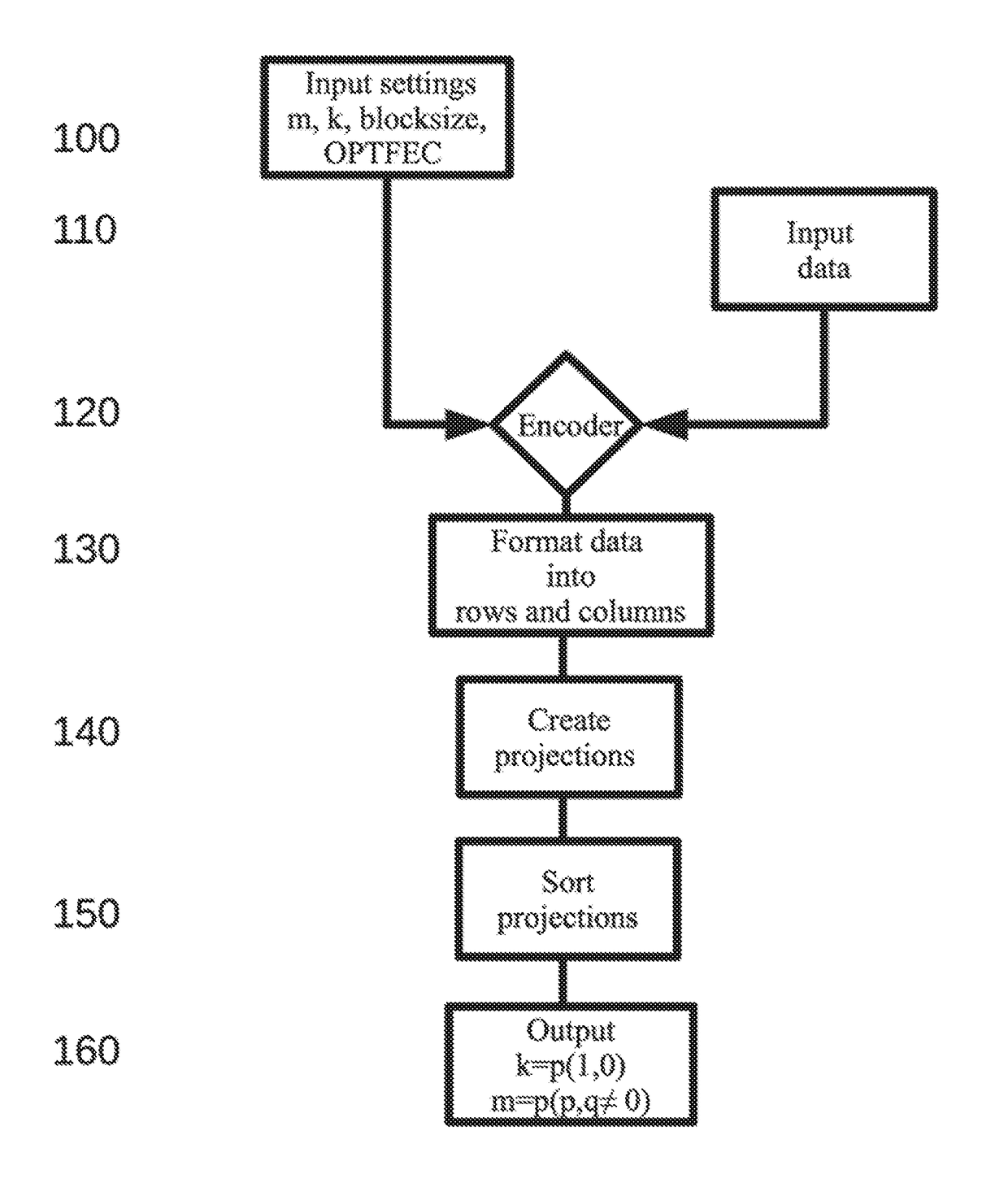
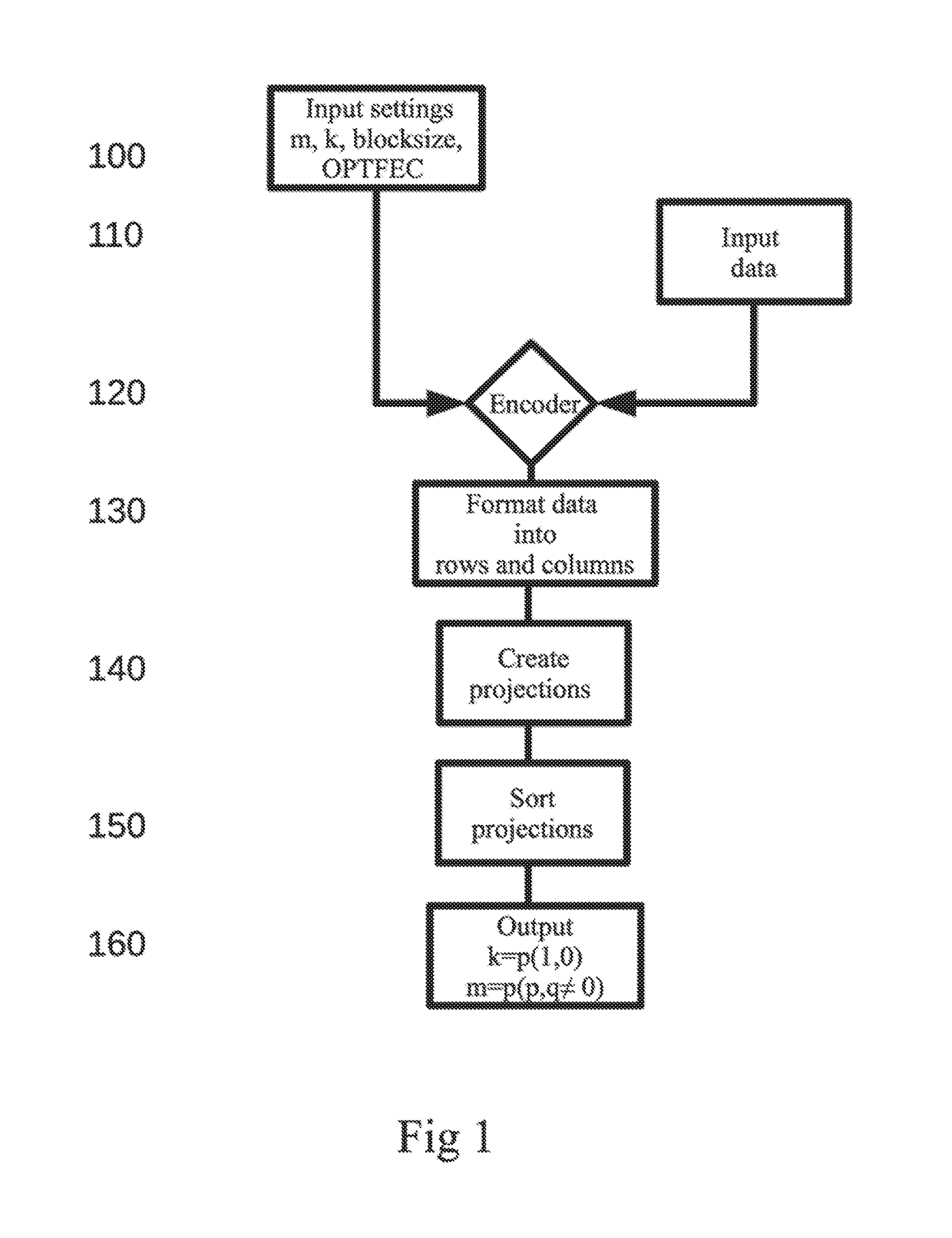
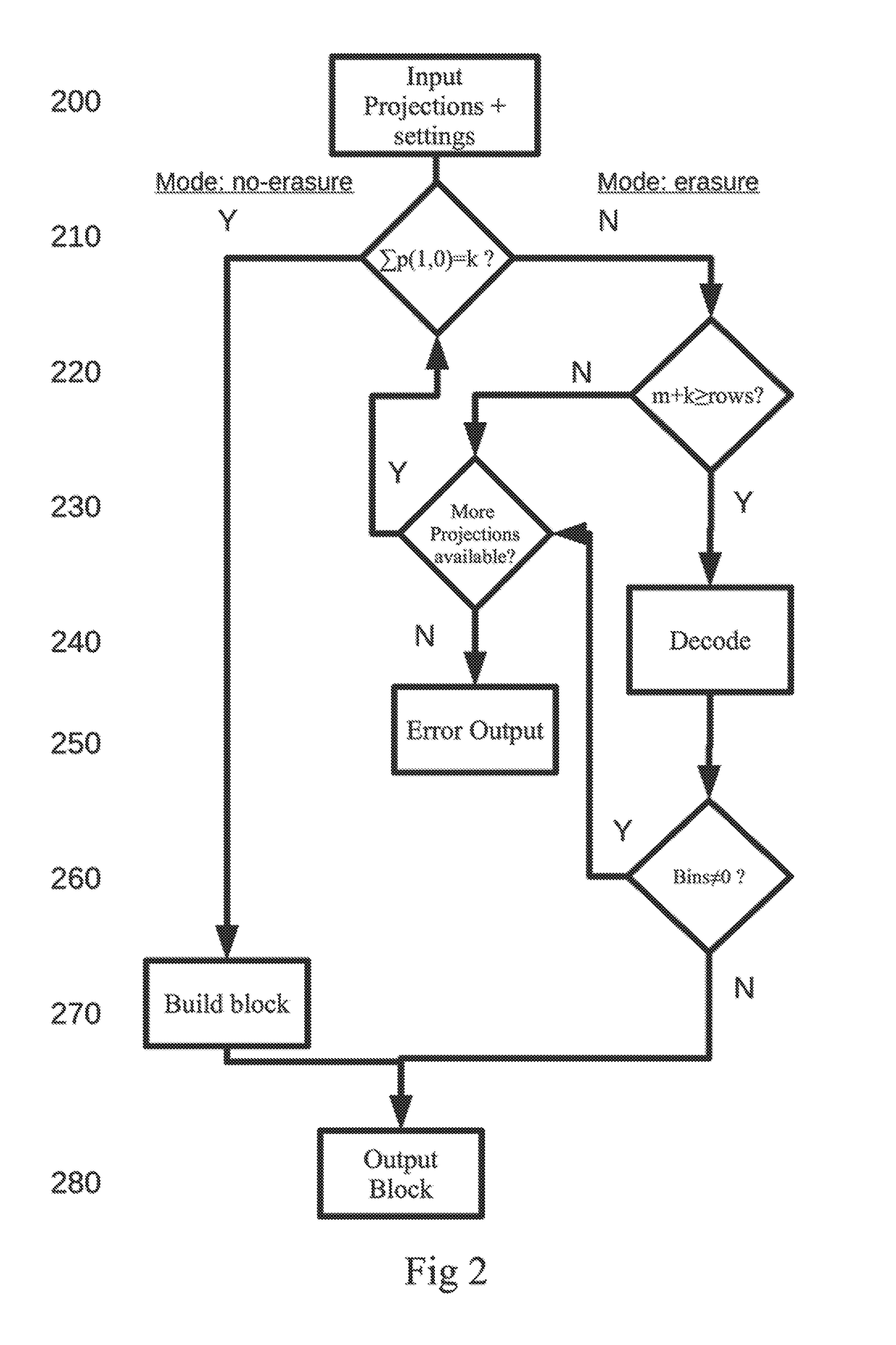
ActiveUS20190158120A1Reduce effortData blockError preventionCode conversionData projectionComputer hardware
An apparatus for generating encoded data includes processing circuitry configured to encode data using a Mojette transform (MT) based on generating encoded representations of data blocks. Generating the encoded representations of data blocks includes reading data in the form of a data block formatted according to specified settings to comprise rows and columns, creating a set of projections, and outputting the created set of projections to enable storage of the data in the form of the set of projections. The apparatus then transmits the encoded data over a network to another device. Additionally, creating the set of projections includes applying the Mojette transform on the data block, and creating a first number of projections based on mapping each row of the data block to a corresponding projection, wherein the first number of projections carries the same information as a corresponding row.
Owner:ZEBWARE AB
Computer readable storage medium and code for adaptively learning information in a digital control system
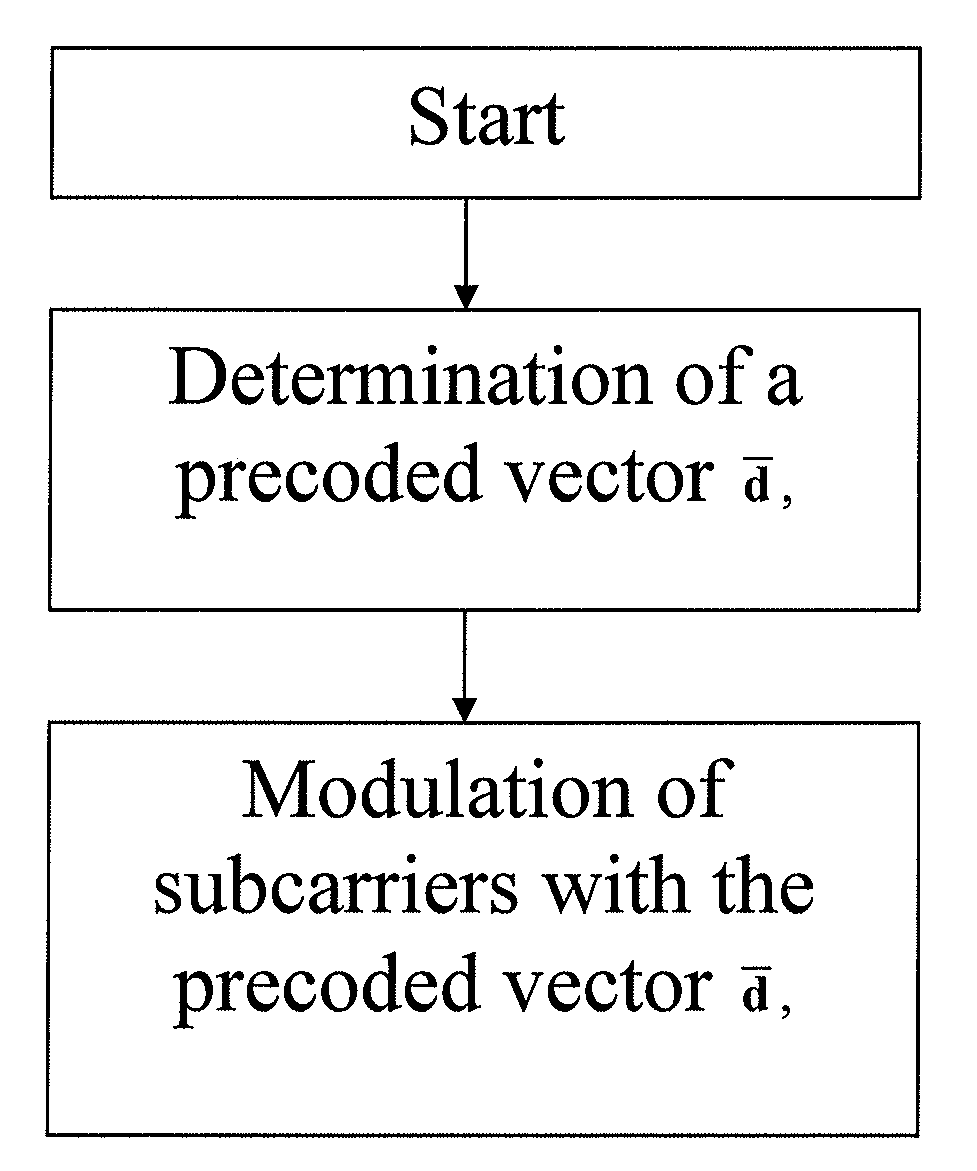
InactiveUS6895326B1Improve accuracyReduce computing needsAnalogue computers for vehiclesElectrical controlPattern recognitionAdaptive learning
Owner:FORD GLOBAL TECH LLC
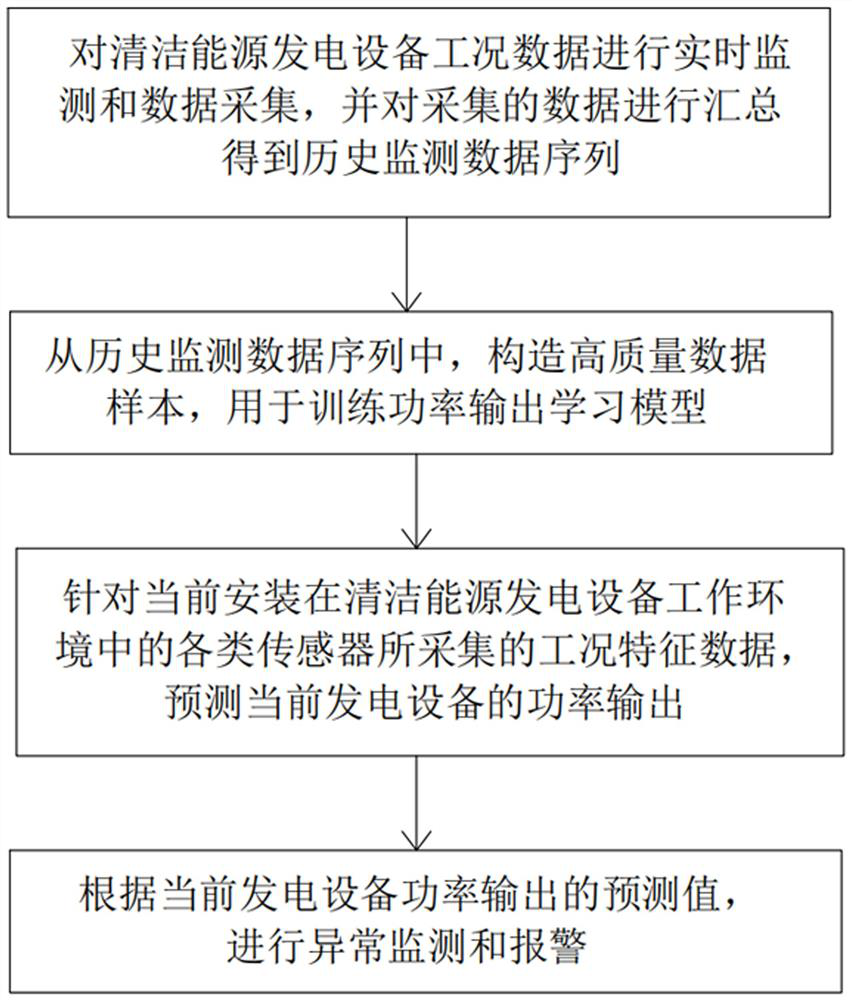
Clean energy generation power prediction method and system
PendingCN114021822AImprove power output prediction accuracyTake advantage ofGeneration forecast in ac networkElectric devicesQuality dataPredictive methods
The invention relates to the technical field of clean energy utilization, and discloses a clean energy generation power prediction method and system. The clean energy power generation power prediction method comprises the following steps: S1, carrying out real-time monitoring and data acquisition on working condition data of clean energy power generation equipment, and monitoring and acquiring power output data of the power generation equipment in real time through an electric energy meter installed in the clean energy power generation equipment; and S2, constructing a high-quality data sample from a historical monitoring data sequence and applying the high-quality data sample to training a power output machine learning model. According to the clean energy generation power prediction method and system, high-quality training sample extraction and abnormal data sample interference elimination can be carried out, corresponding prediction means can be adopted according to working condition characteristics of different conditions, and prediction precision is improved.
Owner:莫毓昌
Method and device for daily activity classification under low complexity, equipment and storage medium
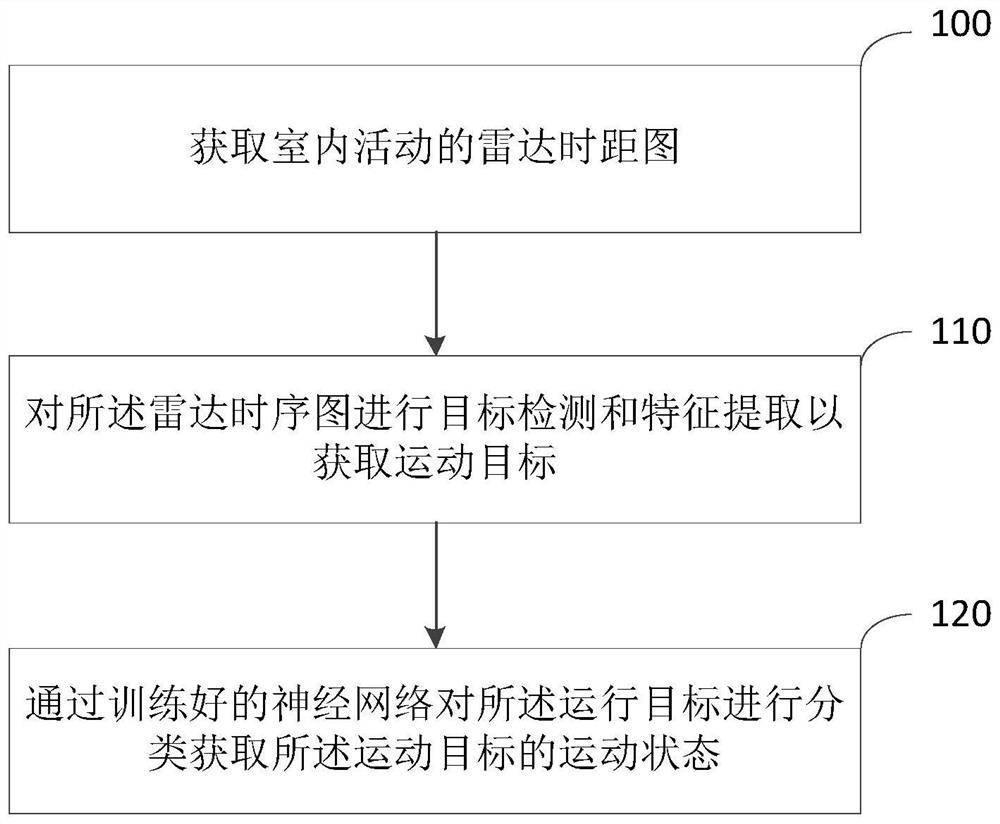
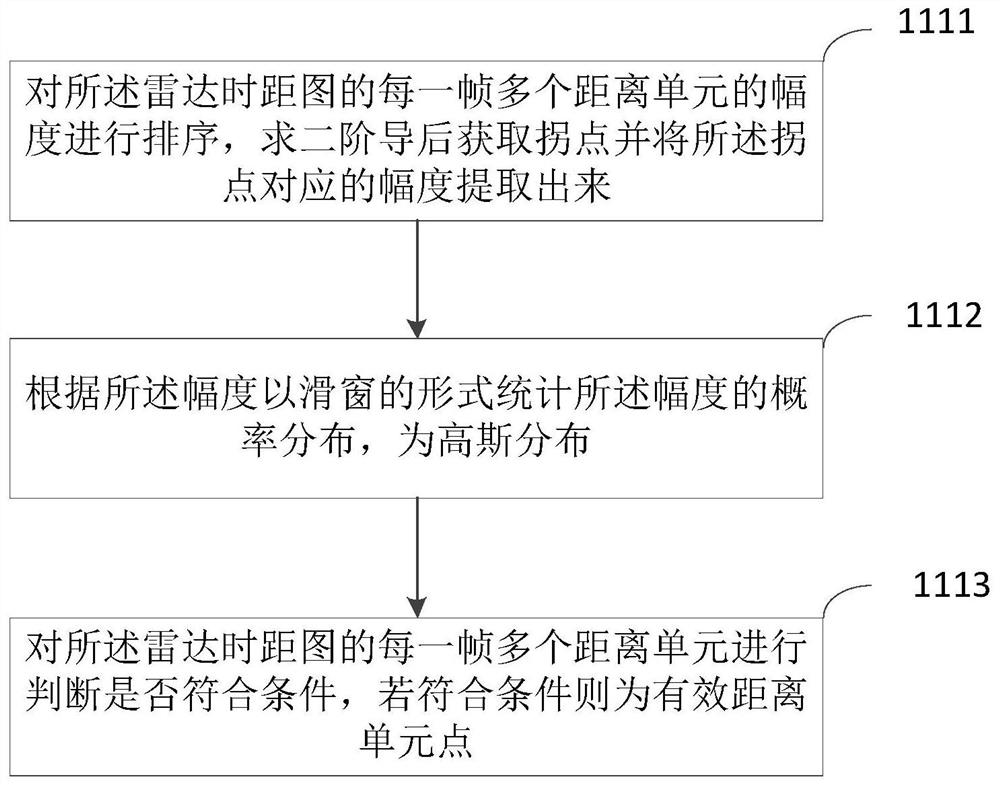
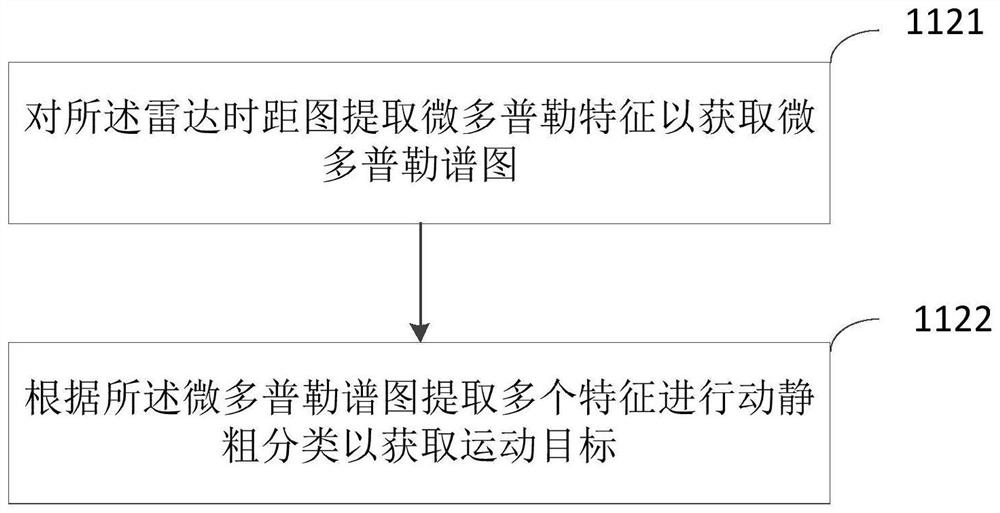
PendingCN112327286AReduce complexityReduce computing needsCharacter and pattern recognitionNeural architecturesActivity classificationHuman body
The embodiment of the invention discloses a method and device for daily activity classification under a low complexity, equipment and a storage medium. The method comprises the following steps: acquiring a radar time-distance map of indoor activity; performing target detection and feature extraction on the radar time interval graph to obtain a moving target; and classifying the operation targets through a trained neural network to obtain the motion state of the motion target. According to the method for daily activity classification under the low complexity, provided by the embodiment of the invention, human body activity identification is realized by using target detection, feature extraction and a lightweight neural network method, and the problems of excessive consumption of computing resources and no real-time performance for human body activity identification in the prior art are solved; and the effects of low complexity and small calculation requirement in daily activity detection are achieved.
Owner:SHENZHEN UNIV
Audio signal processing based on object
ActiveCN106385660AReduce computing needsReduce bandwidth requirementsSpeech analysisStereophonic systemsSpeech recognitionAudio signal
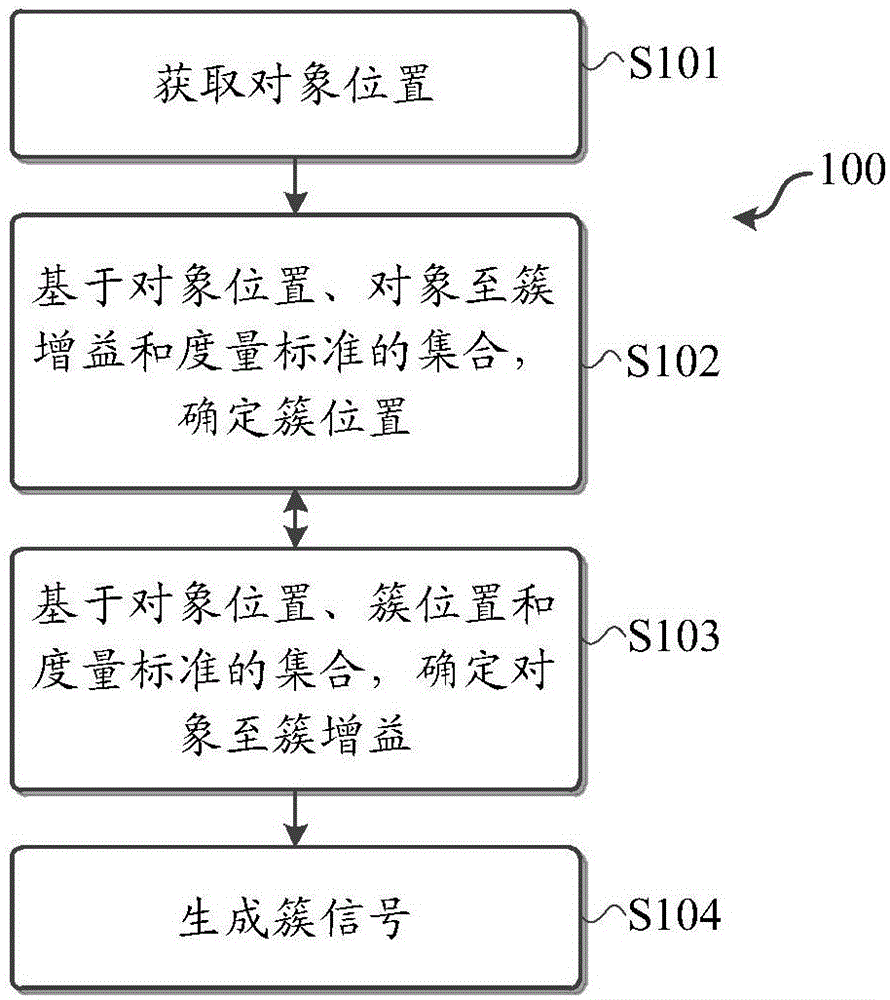
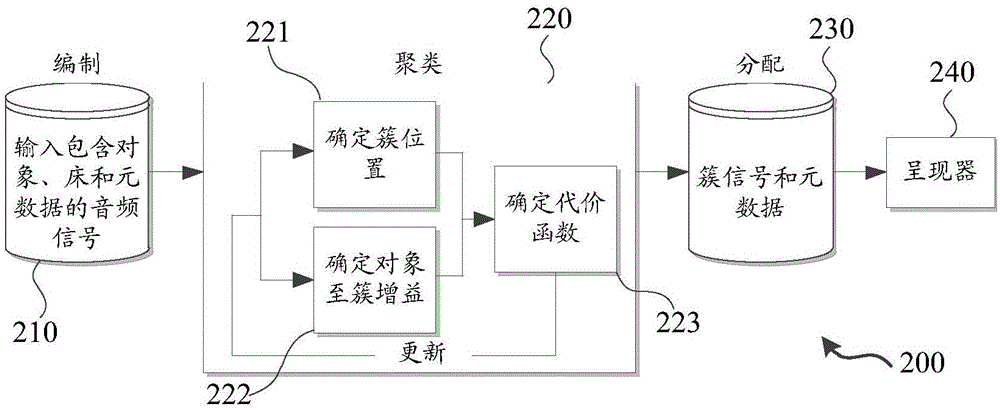
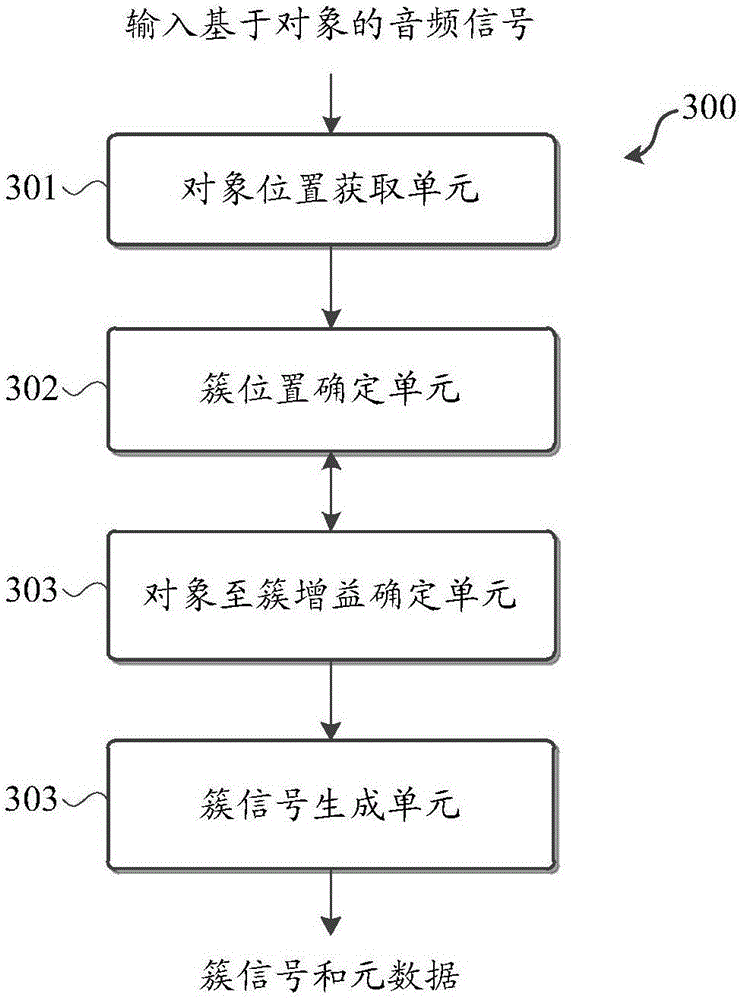
Embodiments of the invention relate to audio signal processing. An audio signal possesses a plurality of audio objects. The invention discloses a method of processing the audio signal. The method comprises the following steps of acquiring an object position aiming at each audio object; based on a set of the object position, a plurality of gains of objects to clusters and a measurement standard, determining cluster positions used for grouping the audio object into clusters, wherein the measurement standard indicates quality of the cluster positions and quality of the gains of objects to clusters; each cluster position in the cluster positions is a center of mass of a corresponding cluster; and one gain in the gains of objects to clusters defines a ratio of a corresponding audio object in one cluster. In the method, the set based on the object position, the cluster positions and the measurement standard is included and the gains of objects to clusters is determined; and based on the determined cluster positions and the gains of objects to clusters, a cluster signal is generated. The invention also discloses a corresponding system and a computer program product.
Owner:DOLBY LAB LICENSING CORP
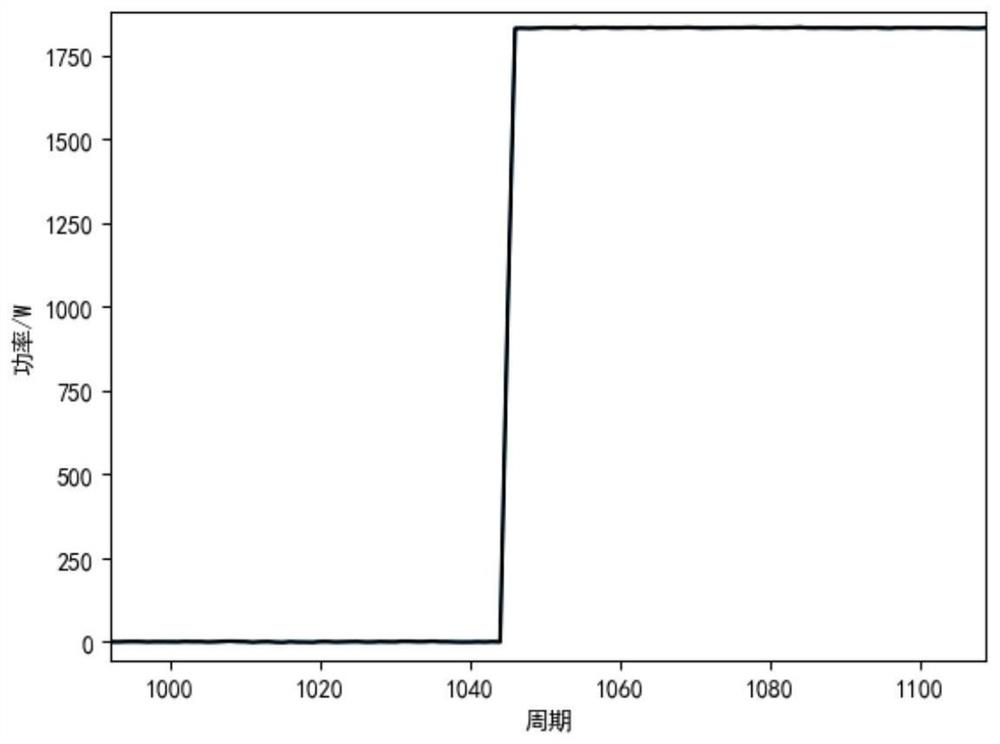
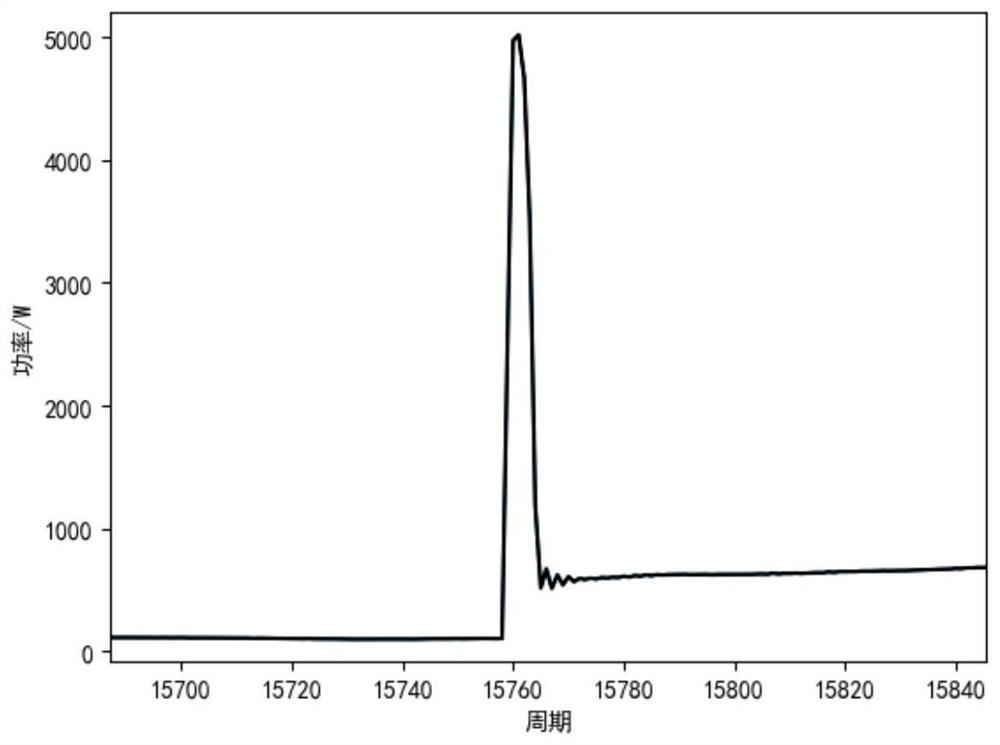
Non-invasive resident load sudden change event three-threshold detection method and system
ActiveCN112396007AImprove detection accuracyImprove fault toleranceData processing applicationsElectric devicesTransient stateComputer science
The invention discloses a non-invasive resident load sudden change event three-threshold detection method and system, and the method comprises the steps: firstly carrying out the high-sensitivity detection through employing low-threshold resident entrance side high-frequency sampling data, and detecting all possible load sudden change event segments; secondly, carrying out similar splicing on thedetected load sudden change event sections on a time scale according to a time threshold value, so as to completely obtain a sudden change whole process of various start-stop events such as a long start event and the like; and finally, judging the complete event set by using a high threshold, screening effective load mutation events, and filtering disturbance mutation generated by load fluctuation. According to the method, the input and removal moments of various types of loads are quickly and accurately positioned, the transient interval interception precision of the sudden load change eventis improved, and meanwhile, the method has outstanding advantages in the aspect of solving the slow-rise type sudden load change event detection.
Owner:STATE GRID JIANGSU ELECTRIC POWER CO LTD MARKETING SERVICE CENT +2
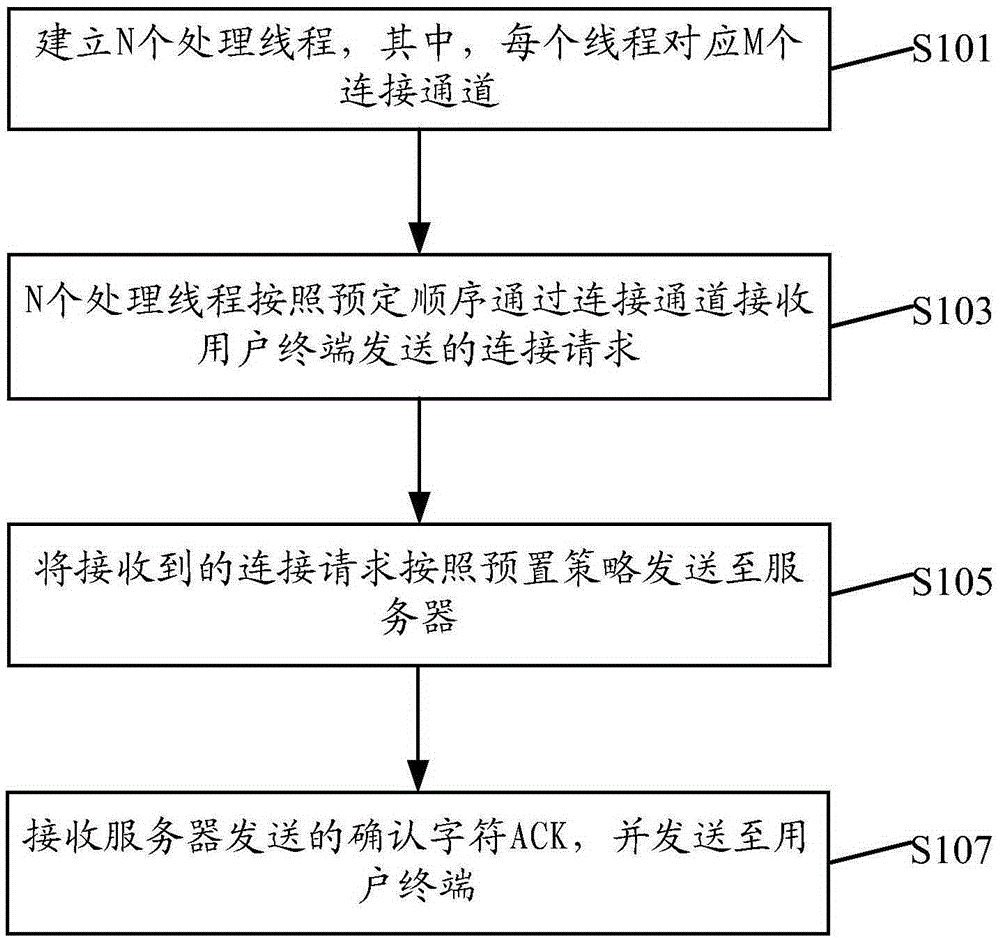
Load balancing method and device
InactiveCN105376334AReduce computing needsShield network topologyTransmissionCluster systemsDistributed computing
The invention provides a load balancing method and device. The method includes the following steps that: N processing threads are established, wherein each thread corresponds to M connection channels; the N processing threads receive connection requests sent by user terminals through the connection channels according to a predetermined order; the received connection requests are sent to a server according to load balancing strategies; and acknowledgement characters (ACK) sent by the server are received and are sent to the user terminals. With the load balancing method and device of the invention adopted, the connection requests received by each connection channel can be transmitted to the server according to corresponding load balancing strategies, and therefore, the computational requirements of the user terminals can be reduced, and requirements of load balancing for network topology in an cluster system can be lowered, and the scalability of clusters can be improved.
Owner:DAWNING INFORMATION IND BEIJING
Metal artifacts reduction for cone beam CT
ActiveUS9202296B2Reduce artifactsImprove processing efficiencyReconstruction from projectionCharacter and pattern recognitionMetal ArtifactComputer science
A method for suppressing metal artifacts in a radiographic image, the method executed at least in part on a computer, obtains at least one two-dimensional radiographic image of a subject, wherein the subject has one or more metal objects and identifies a material that forms the one or more metal objects and a radiation energy level used to generate the obtained image. The obtained radiographic image is segmented to identify boundaries of the metal object. A conditioned radiographic image is formed by replacing pixel values in the radiographic image that correspond to the one or more metal objects with compensating pixel values according to the identified material and the identified radiation energy level. The conditioned radiographic image is then displayed.
Owner:CARESTREAM HEALTH INC
Detection tracking algorithm optimization method based on multi-core heterogeneous platform
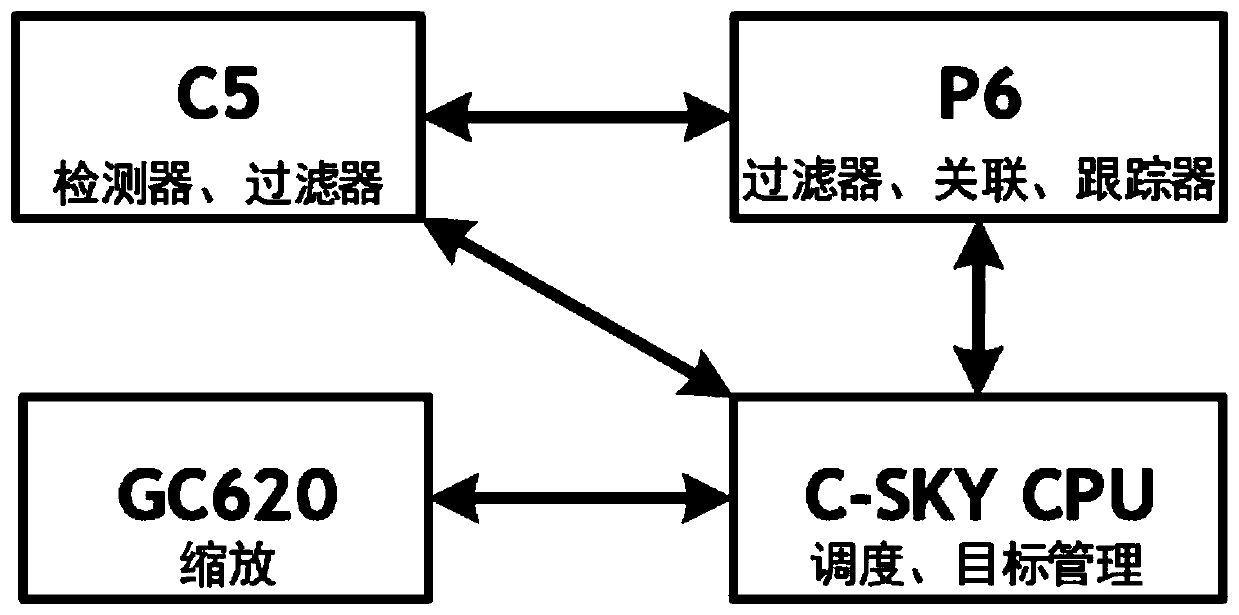
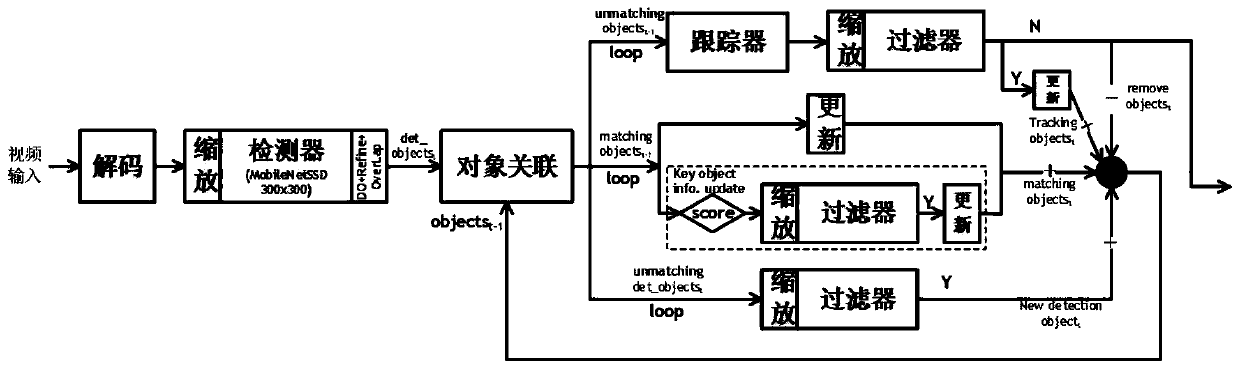
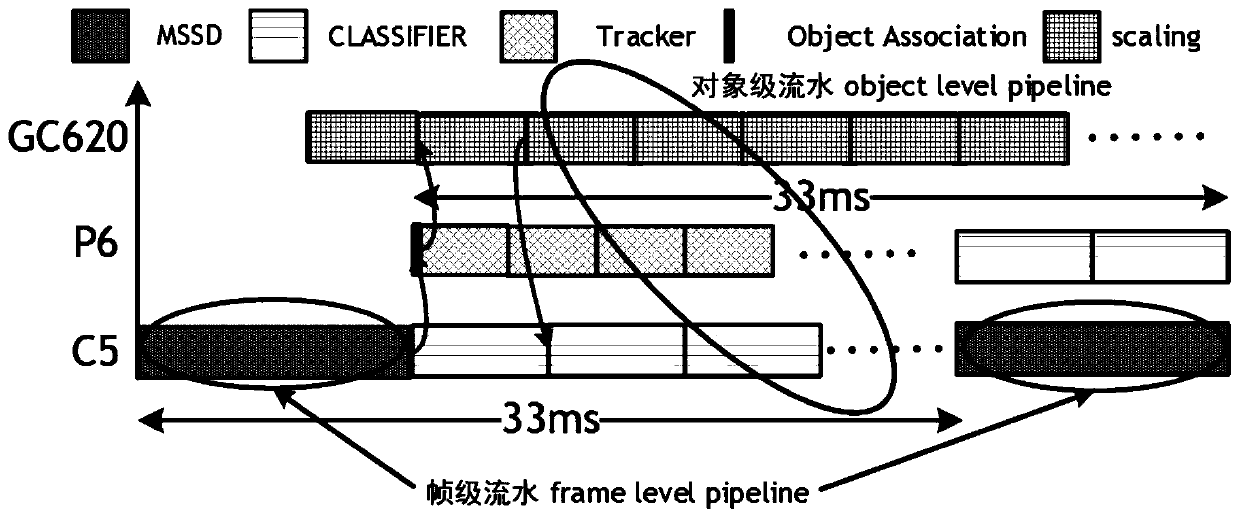
PendingCN110706256AImprove computing efficiencyReduce computing needsImage enhancementImage analysisImage resolutionGraphics accelerator
The invention provides a detection tracking algorithm optimization method based on a multi-core heterogeneous platform. The method comprises the following steps: firstly, zooming an input 1920 * 1080high-definition image into two output resolution images by adopting a GC620 graphic accelerator, namely a resolution of 300 * 300 and a resolution of 300 * 300 for detection of a detector; 2, zoomingto the resolution of 720 * 576 for tracking on the zoomed image by the tracker. By use of the frame-level pipeline of object detection and the object-level pipeline of target tracking, the calculationefficiency is improved. The cache object information is stored in the on-chip SRAM, so that the calculation efficiency is improved. A multi-core heterogeneous platform is used for carrying out distributed calculation on a filter module on C5 and P6, so that the calculation efficiency is improved. And meanwhile, by utilizing the KCF response value, the calculation requirement of the classificationfilter is further reduced.
Owner:杭州博雅鸿图视频技术有限公司
Data isolation exchange and security filtering method orienting electric power internet of things
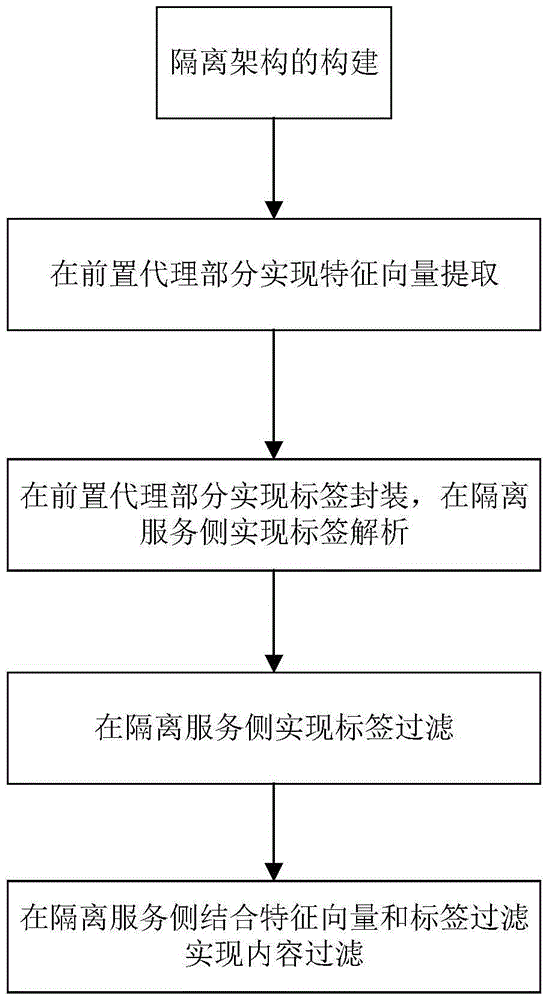
ActiveCN105491023APerfect isolationImprove isolation strengthTransmissionFeature vectorProtocol Application
The invention provides a data isolation exchange and security filtering method orienting electric power internet of things. The method comprises: (1) constructing an isolation framework based on a preposition agent and a special protocol; (2), carrying out feature vector extraction at the preposition agent part; (3), carrying out label package at the preposition agent part, carrying out label analysis at an isolation service side; (4), carrying out label filter at the isolation service side; (5), carrying content filter at the isolation service side combining the feature vector and the label filter. According to the invention, complete protocol isolation is realized through introducing the preposition agent and private application layer protocol, and the isolation intensity is greatly improved.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +1
Reducing object detection time by utilizing space localization of features
InactiveCN105009145AReduce computational complexityReduce computing needsCharacter and pattern recognitionSpatial positioningComputer graphics (images)
In one example, a method for exiting an object detection pipeline includes determining, while in the object detection pipeline, a number of features within a first tile of an image, wherein the image consists of a plurality of tiles, performing a matching procedure using at least a subset of the features within the first tile if the number of features within the first tile meets a threshold value, exiting the object detection pipeline if a result of the matching procedure indicates an object is recognized in the image, and presenting the result of the matching procedure.
Owner:QUALCOMM INC
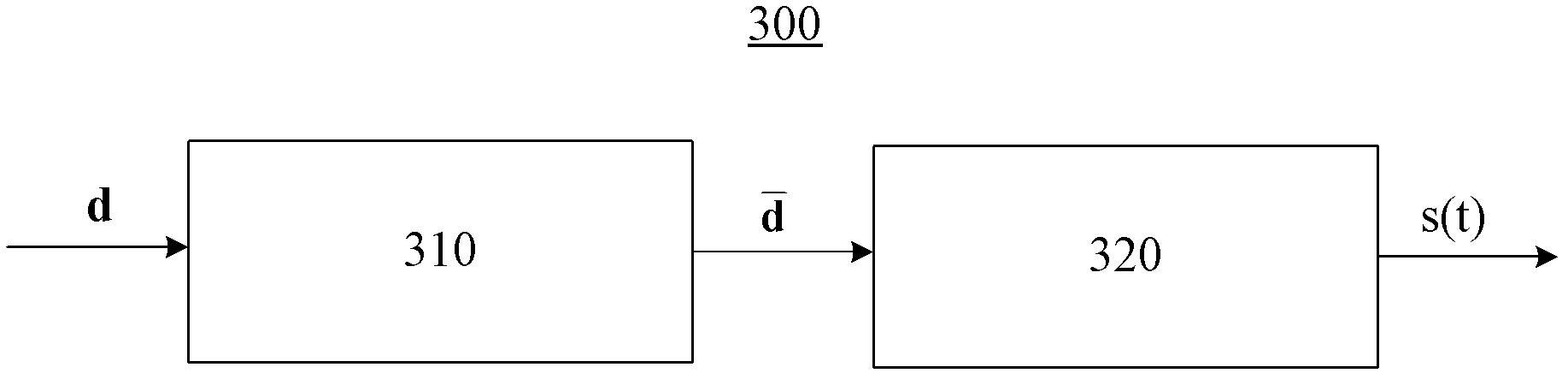
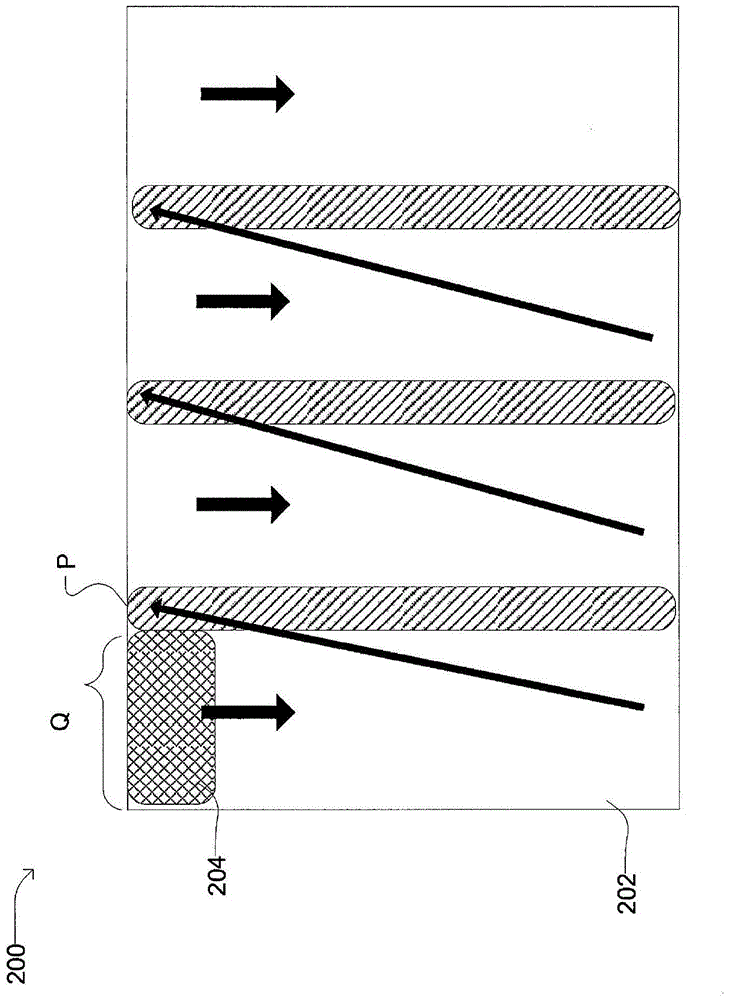
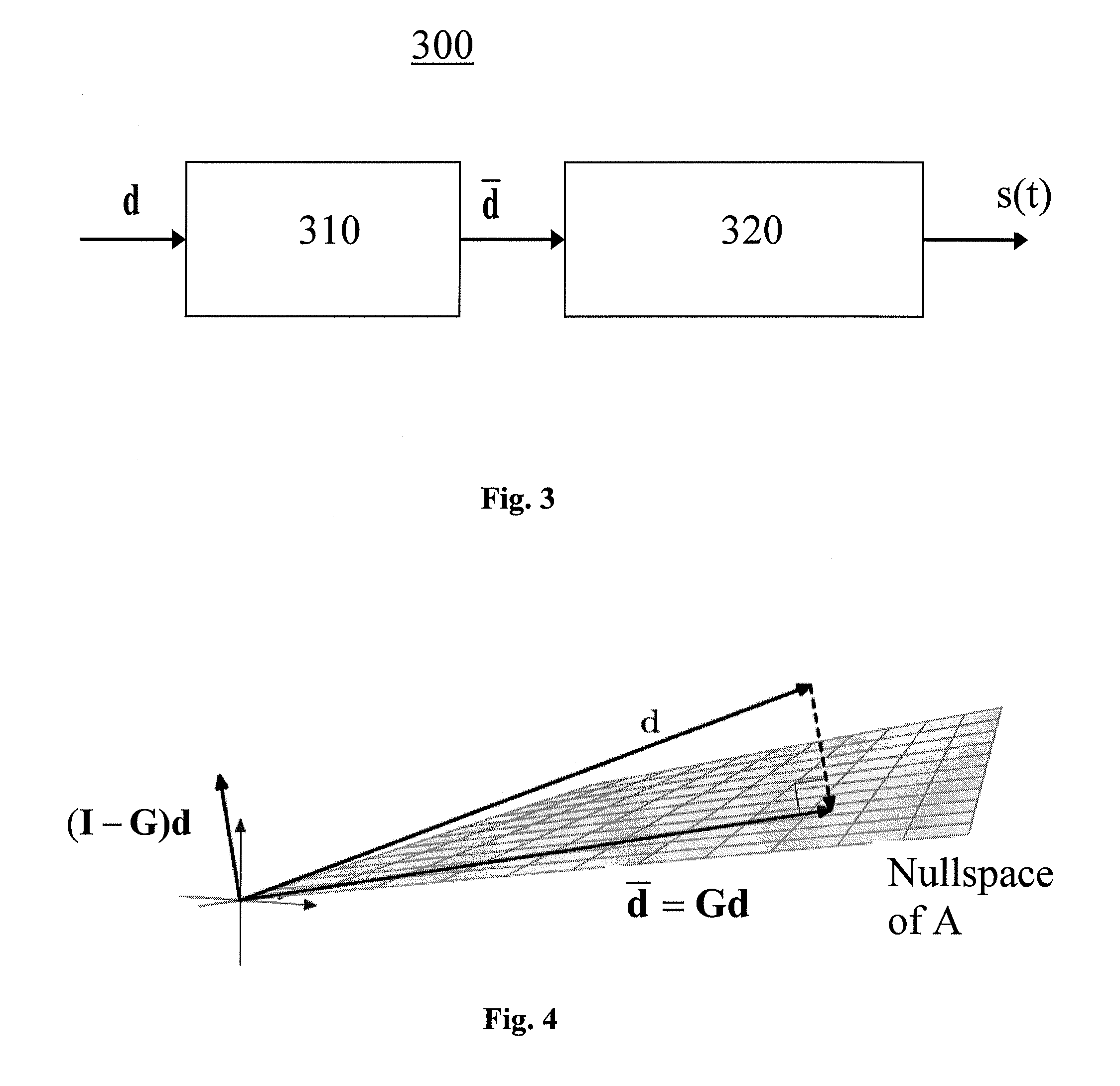
Spectral shaping of multicarrier signals
InactiveUS20120114073A1Low out-of-bandLow in-band emissionModulated-carrier systemsSecret communicationFrequency spectrumCarrier signal
A method for generating and transmitting a multicarrier signal representing data symbols, where the multicarrier signal is a linear combination of subcarriers, is disclosed, as well as a transmission entity. The generation and transmission is characterized bymodulation of base signals with the data symbols, wherein each one of the base signals is a weighted sum of the subcarriers, whereby each one of the subcarriers is weighted by an element of a weighting vector residing in a nullspace of a constraint matrix, whereinthe constraint matrix represents constraints limiting a magnitude of the multicarrier signal's Fourier transform at frequencies outside a designated bandwidth.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com