Power terminal cloud edge-end cooperative security access authentication method based on edge computing
A power terminal and secure access technology, applied in the field of information security, can solve the problems of high communication bandwidth requirements, high computing consumption, and large computing requirements of deep learning methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] The present invention will be further described below in conjunction with the accompanying drawings.
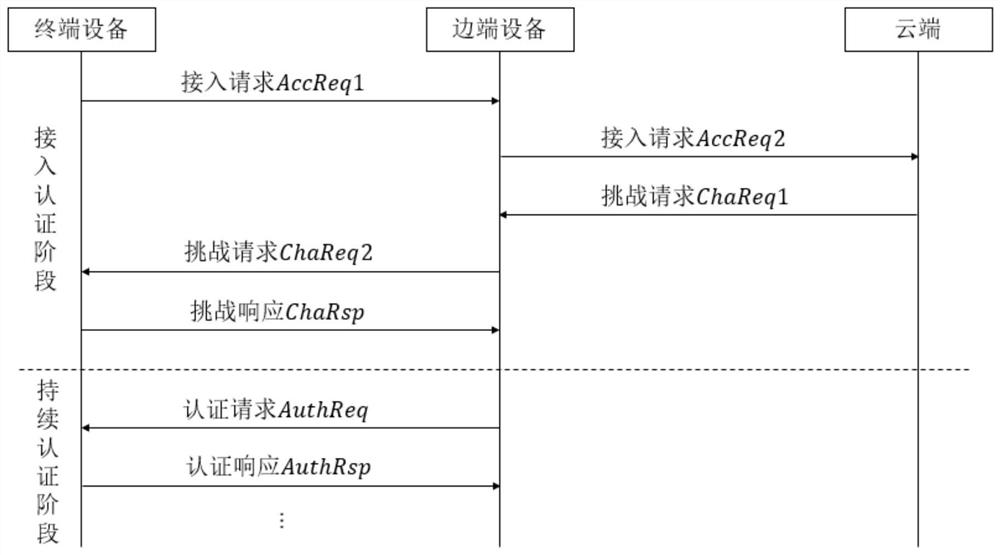
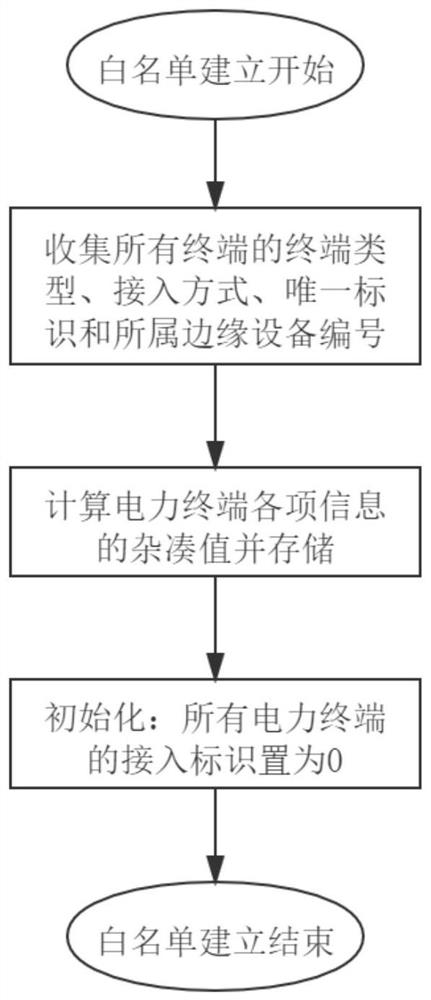
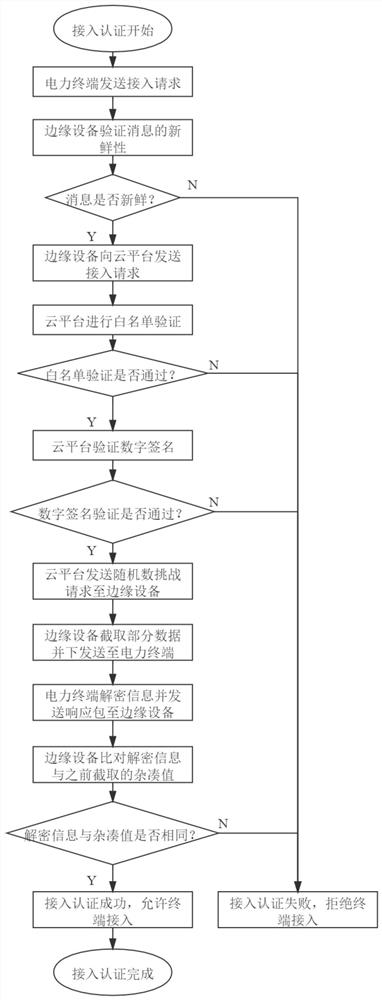
[0058] The traditional power distribution Internet of Things power terminal access is based on the "cloud-end" architecture, and with the access of massive terminals, the computing pressure on the cloud platform increases sharply, so edge devices are introduced to share the pressure on the cloud platform. The introduction of edge devices has changed the original communication architecture and evolved into a new "cloud-edge-end" architecture, while the traditional authentication mechanism is based on the "cloud-end" architecture design, so it is not suitable for the introduction of edge computing scenarios. The present invention aims at This situation proposes a new authentication mechanism, which fully considers the challenges and opportunities brought by edge devices, in order to overcome the difficulties brought by edge computing and give full play to its advantages. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com