RFID authentication method and RFID authentication system
A technology of radio frequency identification and authentication method, applied in the field of radio frequency identification, can solve the problems of security threats, limited computing power of tags and readers, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
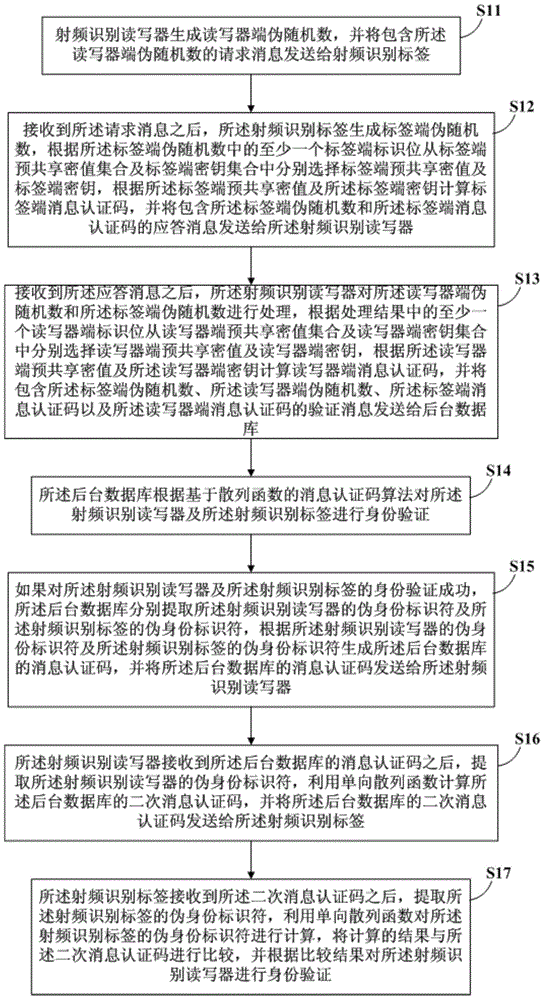
[0023] This embodiment provides a technical solution of the radio frequency identification authentication method. The radio frequency identification authentication method can be implemented by a radio frequency identification system. The radio frequency identification system includes: a radio frequency identification tag, a radio frequency identification reader and a background database. The radio frequency identification reader / writer is connected to the radio frequency identification tag and the background database respectively, and there is no communication connection between the radio frequency identification tag and the background database. In the above two communication connections, the connection between the RFID tag and the RFID reader is a wireless connection using RFID technology, so the communication connection is vulnerable to attacks; and the RFID read / write The connection between the RFID reader and the background database is a wired communication connection, whi...
no. 2 example
[0072] This embodiment provides another technical solution of the radio frequency identification authentication method. In this technical solution,
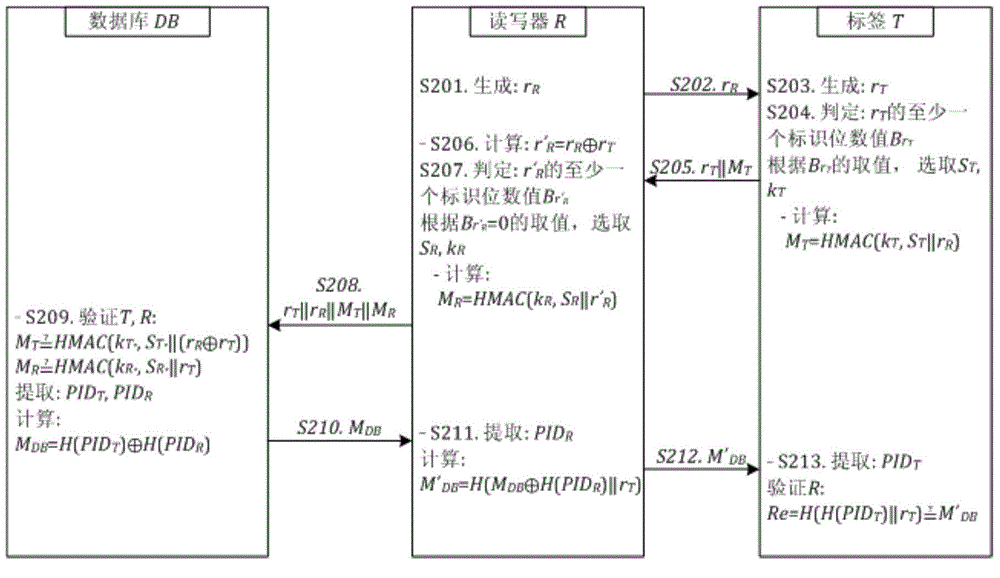
[0073] See figure 2 , The radio frequency identification authentication method includes:
[0074] S201, the radio frequency identification reader generates a pseudo-random number r at the reader R .
[0075] S202, the RFID reader sends the generated pseudo-random number r on the reader to the RFID tag R .
[0076] S203, the RFID tag generates a pseudo-random number r on the tag side T .
[0077] S204: According to the pseudo-random number r at the tag end T At least one tag end identification bit in B rT Select the label side key k T And the tag side share secret value S T .
[0078] Exemplarily, mark B at the tag end rT In the case of only one bit, if the pseudo-random number r T The last digit B rT The value of is 0, the radio frequency identification tag selects k T0 Is the label side key, and select S T0 Is the shared secret value at ...
no. 3 example
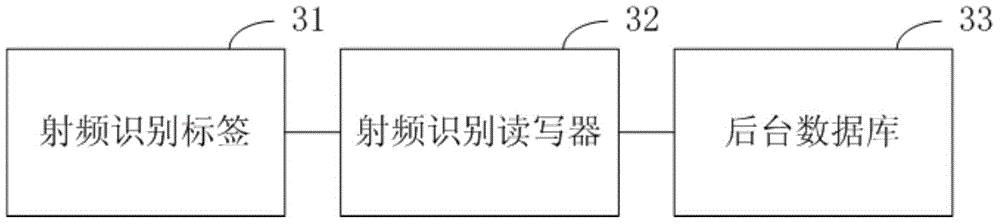
[0108] This embodiment provides a technical solution of the radio frequency identification authentication system. See image 3 In this technical solution, the radio frequency identification authentication system includes: a radio frequency identification tag 31, a radio frequency identification reader 32 and a background database 33.
[0109] The RFID tag 31 is used to generate a tag end pseudo-random number after receiving the request message, and pre-share the secret value set and the tag end key from the tag end according to at least one tag end identification bit in the tag end pseudo random number The tag-end pre-shared secret value and tag-end key are respectively selected in the set, and the tag-end message authentication code is calculated according to the tag-end pre-shared secret value and the tag-end key, and will include the tag-end pseudo-random number and The response message of the tag-side message authentication code is sent to the RFID reader 32, and after receiv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com