Mobile authentication system based on intelligent mobile phone
A smart phone and authentication system technology, applied in the field of information security, can solve problems such as unimaginable consequences, impossibility of long-term use, and potential safety hazards, and achieve the effects of good scalability, cost savings, and high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be further elaborated below in conjunction with the accompanying drawings.
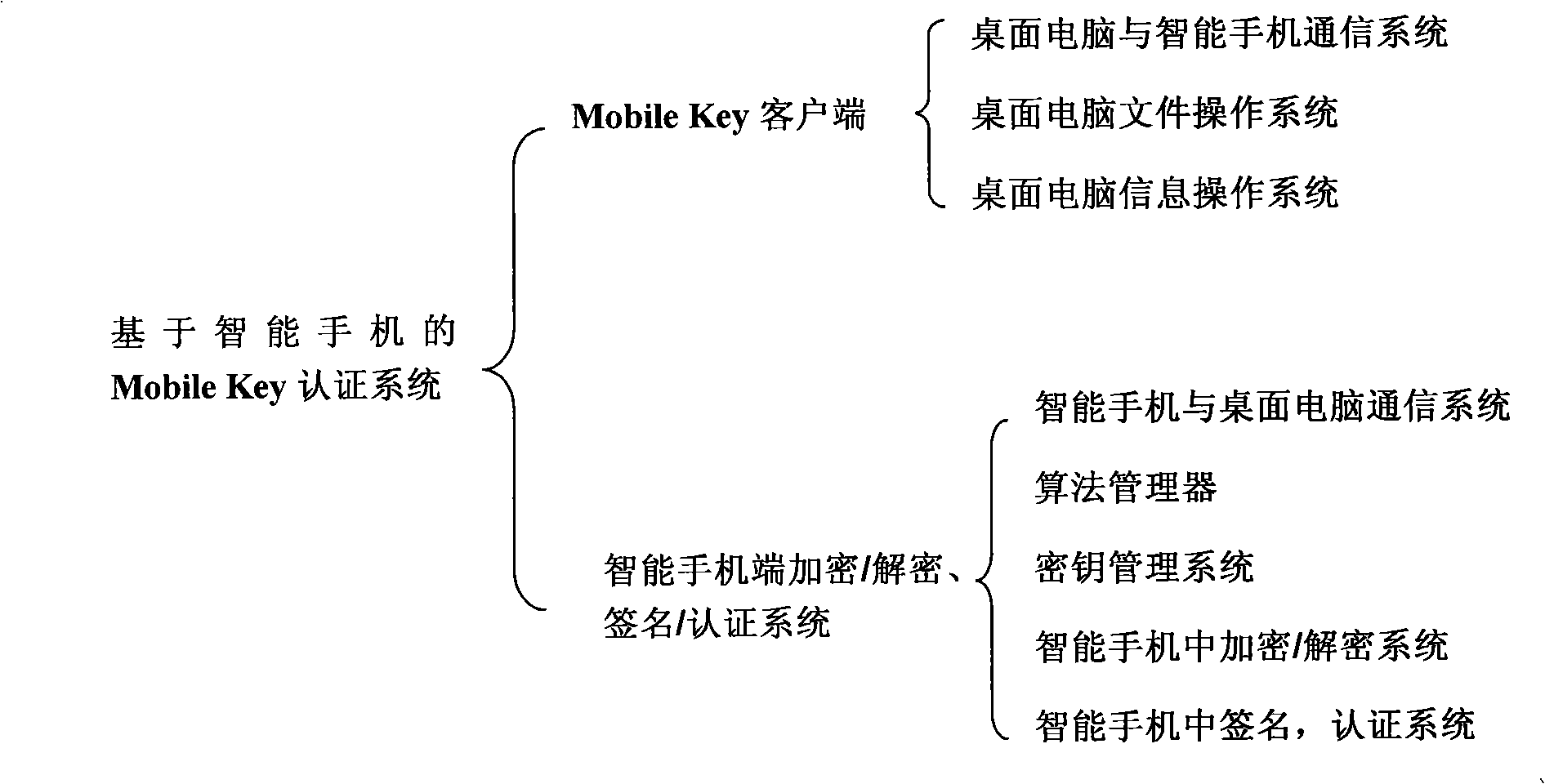
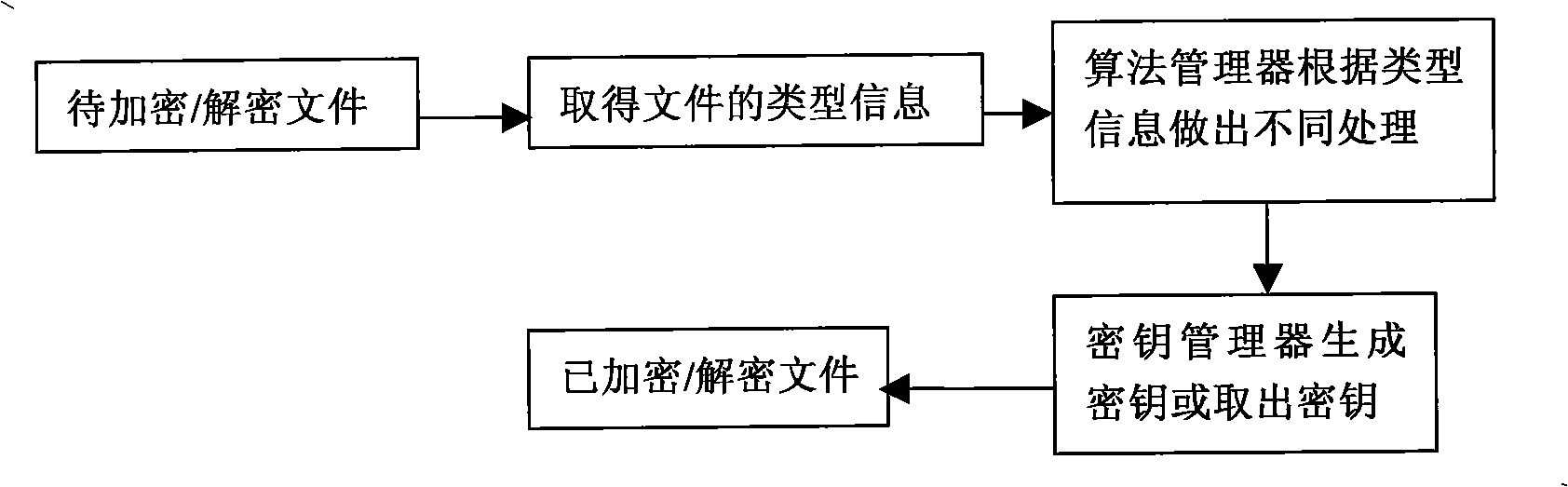
[0039] The purpose of this invention is to design and implement an authentication system MobileKey based on smart phones. The system overcomes the shortcomings of USB Key such as slow computing power, relatively low security, and inability to expand, and proposes a new technology called Mobile Key. Mobile Key is not only much stronger in computing power than USB Key, but also greatly improved in security. The important thing is to support the processing of large files. Mobile Key can be used in file encryption, decryption, digital signature, authentication, information disguise, information hiding and other fields.
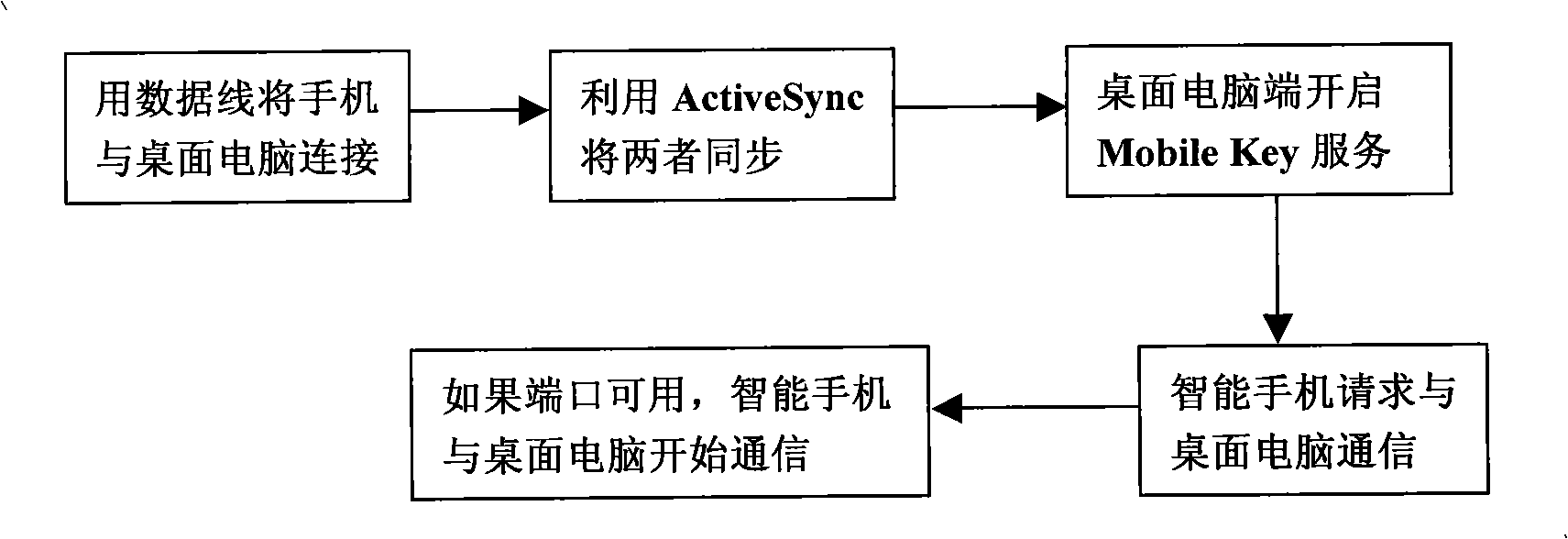
[0040] The Mobile Key system works like a print service in Windows. A smart phone is equivalent to a printer, and a Mobile Key application client is similar to a user who needs to use a printer. These clients must register with the Mobile Key service pro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com