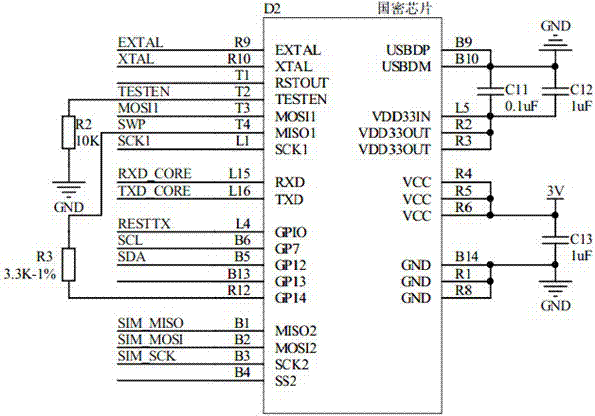
Patents
Literature
164results about How to "Ensure transaction security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Virtual account convenient application system based on mobile terminal and achieving method thereof
InactiveCN103268550AReduce operating costsAvoid abuseProtocol authorisationOperational costsComputer terminal
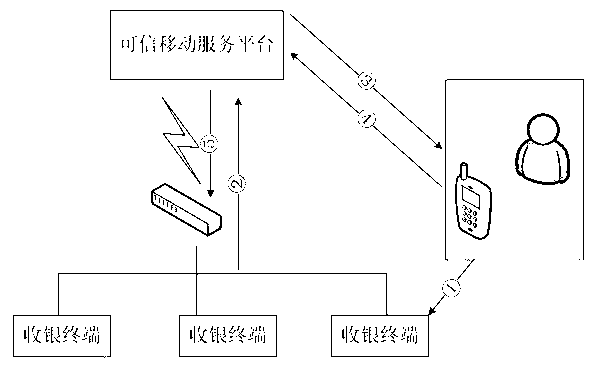
The invention discloses a virtual account convenient application system based on a mobile terminal and an achieving method thereof. The mobile terminal of a user serves as a carrier, and the mobile terminal is connected with a cash terminal and a reliable mobile service platform of a merchant through the internet or a communication network. Based on the binding relation of a cell phone account of the mobile terminal and a virtual account, the reliable mobile service platform utilizes cell phone hardware to serve as an important medium for identification to achieve a basis of identification verification and trading monitoring, and provides various consumption modes regarding mobile payment consumption movements of a series of virtual accounts for each user in various application places. With the development of popularization of intelligent cell phones and the mobile internet, by the adoption of the technical scheme of the virtual account convenient application system, transaction safety is ensured, manufacturing cost of a financial practical card is reduced, and abuse of a false card is thoroughly eradicated, operation cost of mobile payment is reduced, and safety and low cost of the virtual account convenient application system based on the mobile terminal further facilitate popularization.
Owner:JIANGSU PAYEGIS INFORMATION SECURITY TECH CO LTD
System and method for realizing electronic transaction risk control based on position scene identification
InactiveCN103745397APrevent fraudReduce personal property damageFinanceBuying/selling/leasing transactionsRisk ControlEmbedded security
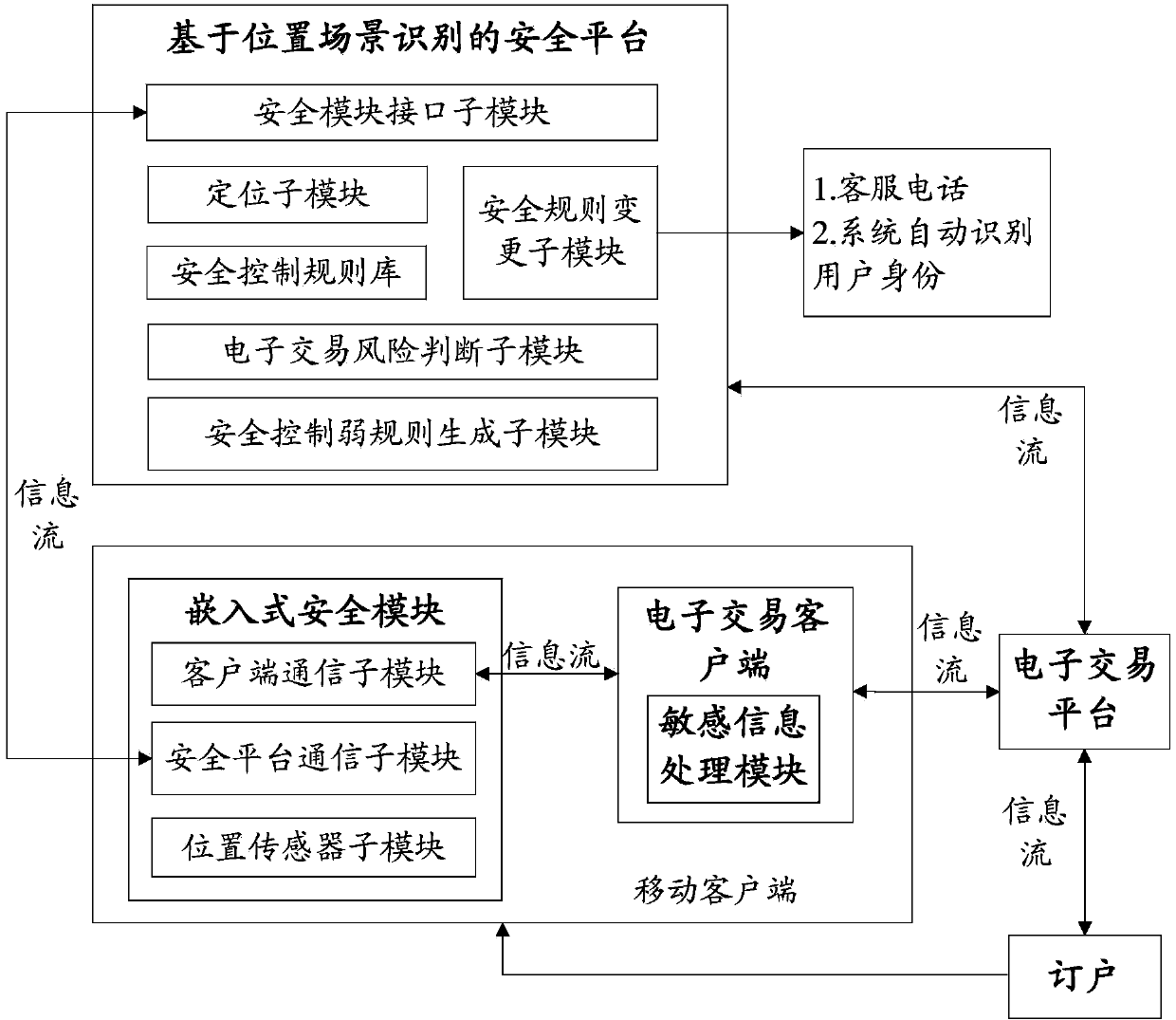
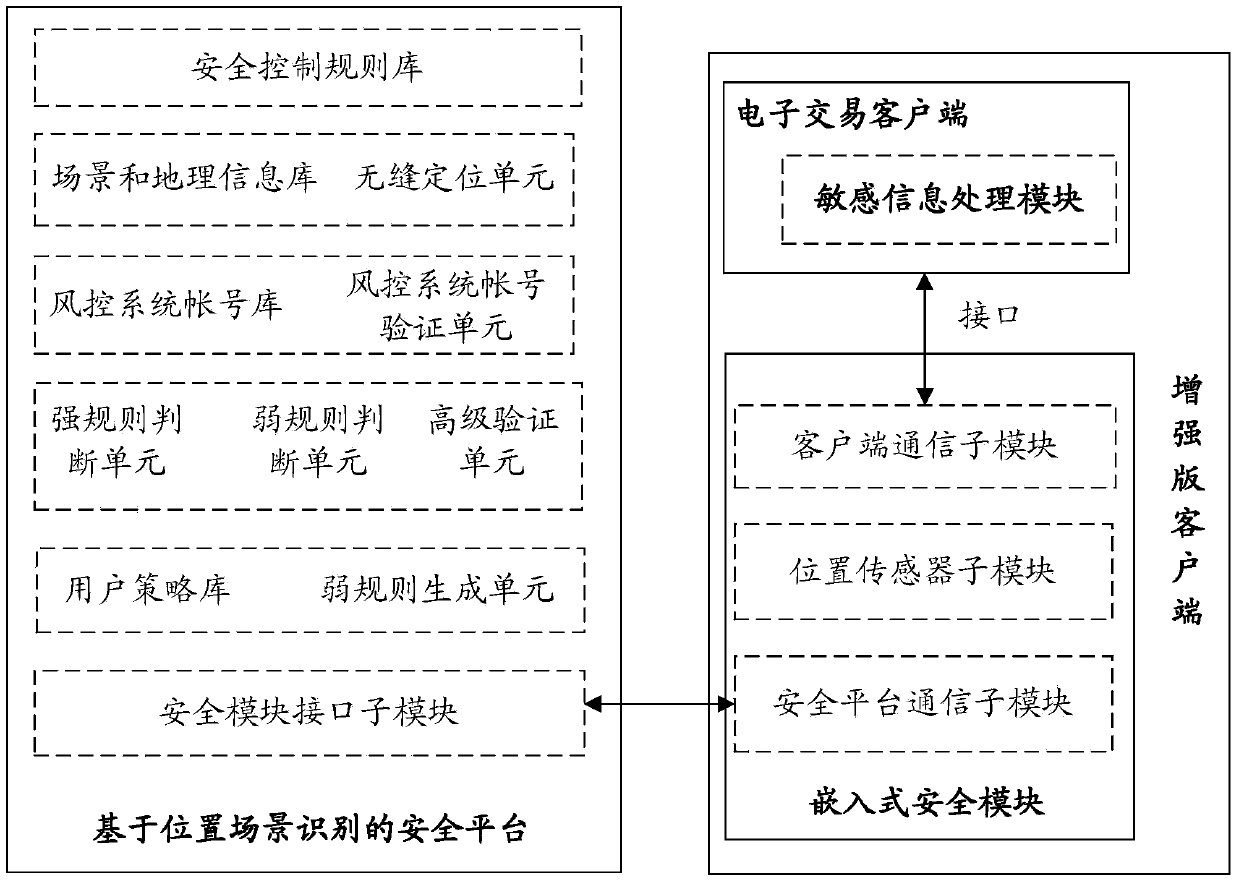
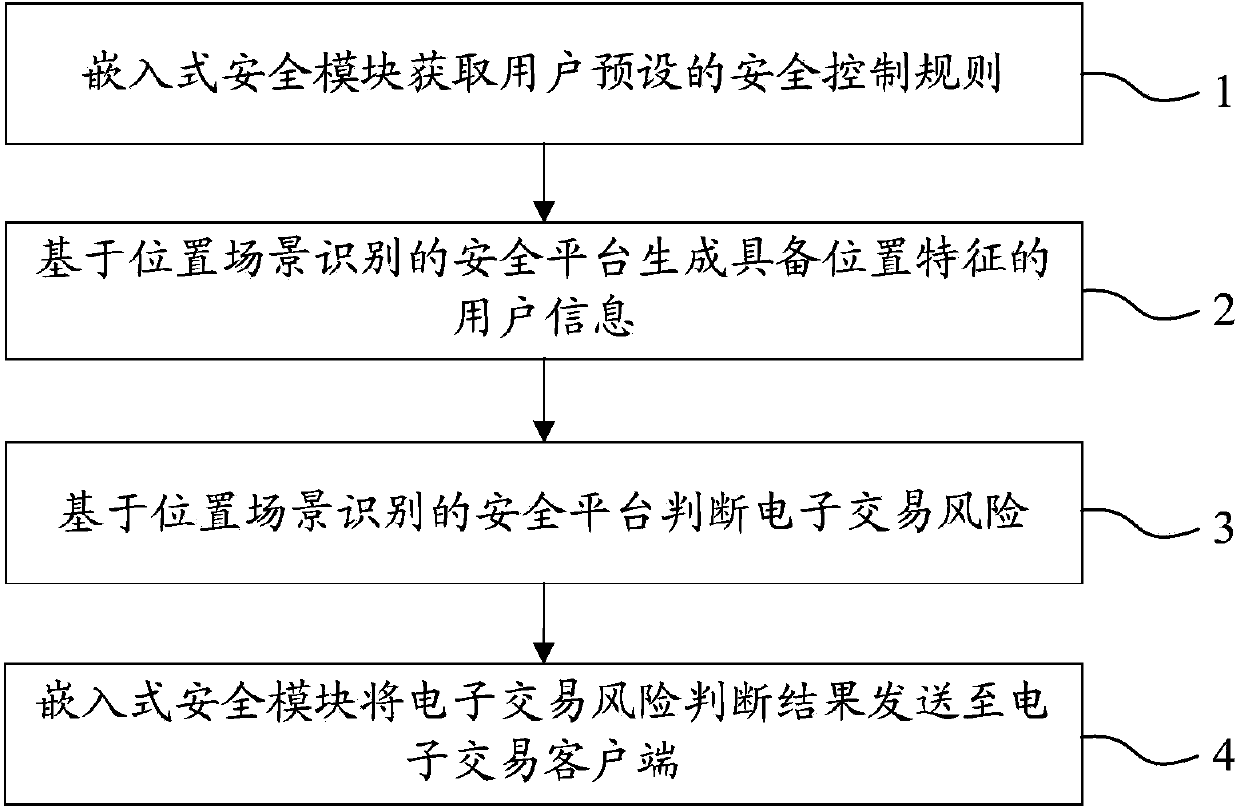
The invention relates to a system for realizing electronic transaction risk control based on position scene identification. The system comprises a position scene identification-based security platform and an embedded security module, wherein the position scene identification-based security platform comprises a security interface sub-module, a positioning sub-module, a security control rule library, a security rule change sub-module, an electronic transaction risk judging sub-module and a security control weak rule generation sub-module, which are communicated with the embedded security module. The invention further relates to a method for realizing electronic transaction risk control based on position scene identification through the system. By adopting the system and the method for realizing electronic transaction risk control based on position scene identification, risk control over the electronic transactions of a user can be realized by providing positioning service and identifying a user position scene, so that the security of an electronic transaction process is enhanced, and losses caused by transaction security problems are reduced. The method is easy, convenient, and wider in application range.
Owner:YINLIAN FINANCIAL INFORMATION SERVICE BEIJING CO LTD
Method for carrying out electronic identity recognition by utilizing two-dimensional code
InactiveCN103177297ARealize online managementConducive to the efficiency of pit stopsTicket-issuing apparatusReservationsElectronic taggingTerminal equipment
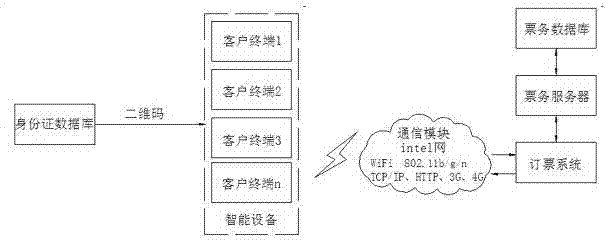
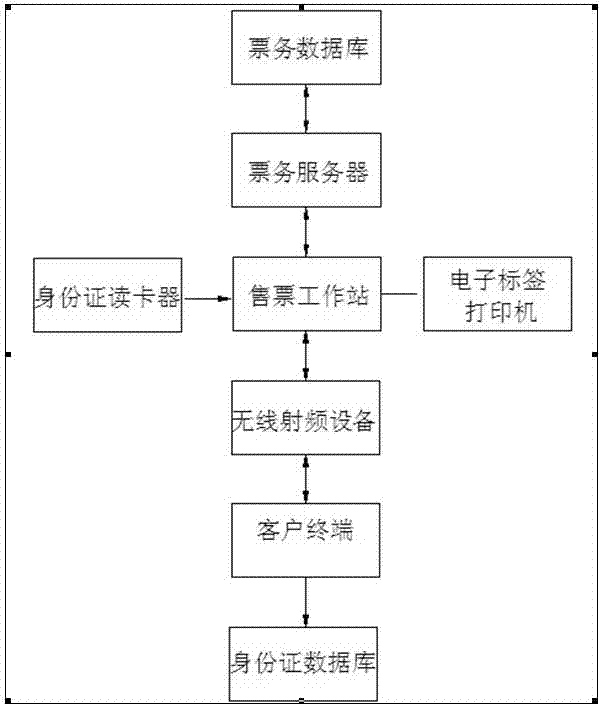
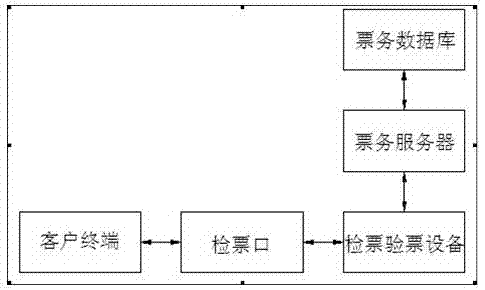
The invention relates to the field of identification, and particularly relates to a method for carrying out electronic identity recognition by utilizing two-dimensional codes. The method is characterized in that at least one client terminal, a ticket reservation system, a ticket business server, a ticket business database, a ticket selling workstation, an electronic tag printer, an identity card reader, a ticket checking entrance, wireless radio-frequency equipment and an identity card database are adopted in the method, wherein the client terminal refers to a passenger, namely a person who needs to purchase a ticket for taking a bus and acquires a two-dimensional code electronic tag through intelligent terminal equipment during ticket purchasing; the ticket reservation system refers to a network ticket reservation system; and the ticket selling workstation refers to the existing station ticket window and various agent ticket offices. The method for fast and conveniently carrying out the electronic identity recognition, which is provided by the invention, mainly aims at overcoming the defects of the existing paper ticket and solving the problem of difficult queuing during the ticket purchasing and can reduce the labor intensity of ticket checking personnel, improve the incoming efficiency of the passengers and realize the high security and the high antifalsification through the uniqueness of a second-generation identity card.
Owner:JINHUA INFORMATION DIGITAL TECH
Multi-module automatic trading system based on network distributed computing
InactiveCN106934716AReduce human errorSimplify Quantitative Modeling ProceduresFinanceRisk ControlTransaction management
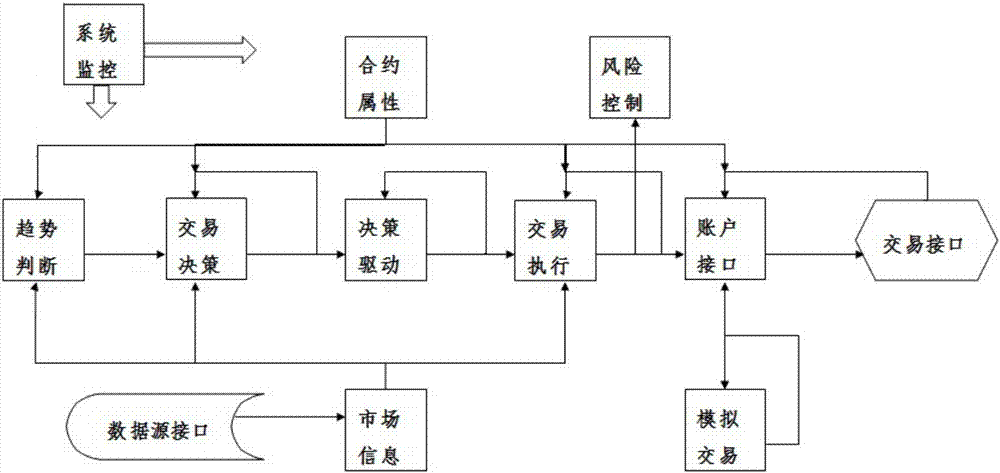
The invention discloses a multi-module automatic trading system based on network distributed computing. The system comprises a historical and real-time market data processing module, a real-time market probability distribution prediction module, a trading strategy design and development module, a trading strategy history backtracking and evaluating module, a trading strategy market access and transaction management module, a system monitoring and risk control module, and a transaction report and quantitative analysis module. The automatic trading system can face various types of quantitative traders, a quantitative modeling program is simplified, a quantitative trading threshold is reduced, the quantitative strategy test and evaluation efficiency is improved, and the transaction security is guaranteed. The automatic trading system can automatically and intelligently analyze market and trading trends, provide real-time price probability distribution prediction for market main transaction products, provide a transaction signal with low delay and a high success rate for a transaction strategy and thus generate a timely and accurate trading signal, an efficient tool and comprehensive and accurate data are provided to construct the strategy of a user, and back testing and optimization are carried out.
Owner:燧石科技(武汉)有限公司
Two-dimension code-based mobile terminal transaction encryption method
ActiveCN103714458ANot burdenedEnsure safetyUser identity/authority verificationBuying/selling/leasing transactionsPaymentRelevant information
The invention discloses a two-dimension code-based mobile terminal transaction encryption method and belongs to the network technical field. According to the two-dimension code-based mobile terminal transaction encryption method of the invention, based on the combination of a two-dimensional code technology and an existing mobile transaction protocol, related information can be encrypted through two-dimension codes in identity authentication of two transaction parties, order confirmation and payment, such that transaction security can be ensured. With the two-dimension code-based mobile terminal transaction encryption method of the invention adopted, safer and more reliable online transactions can be realized without too much burden brought to a mobile terminal device, and the safety, confidentiality and non-repudiation performance of the online transactions of the mobile terminal can be ensured.
Owner:JIANGSU UNIV
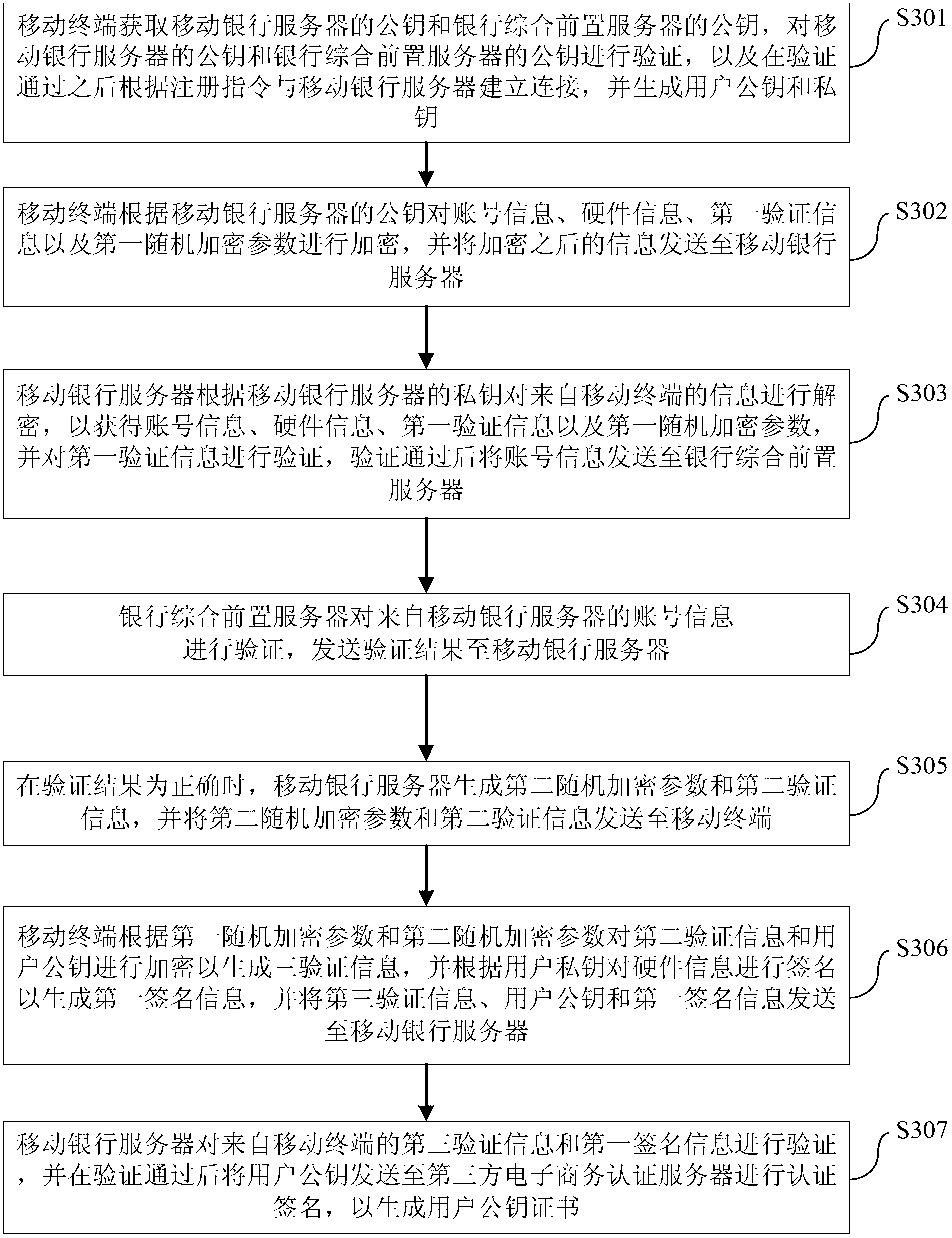
Method and system for key protection
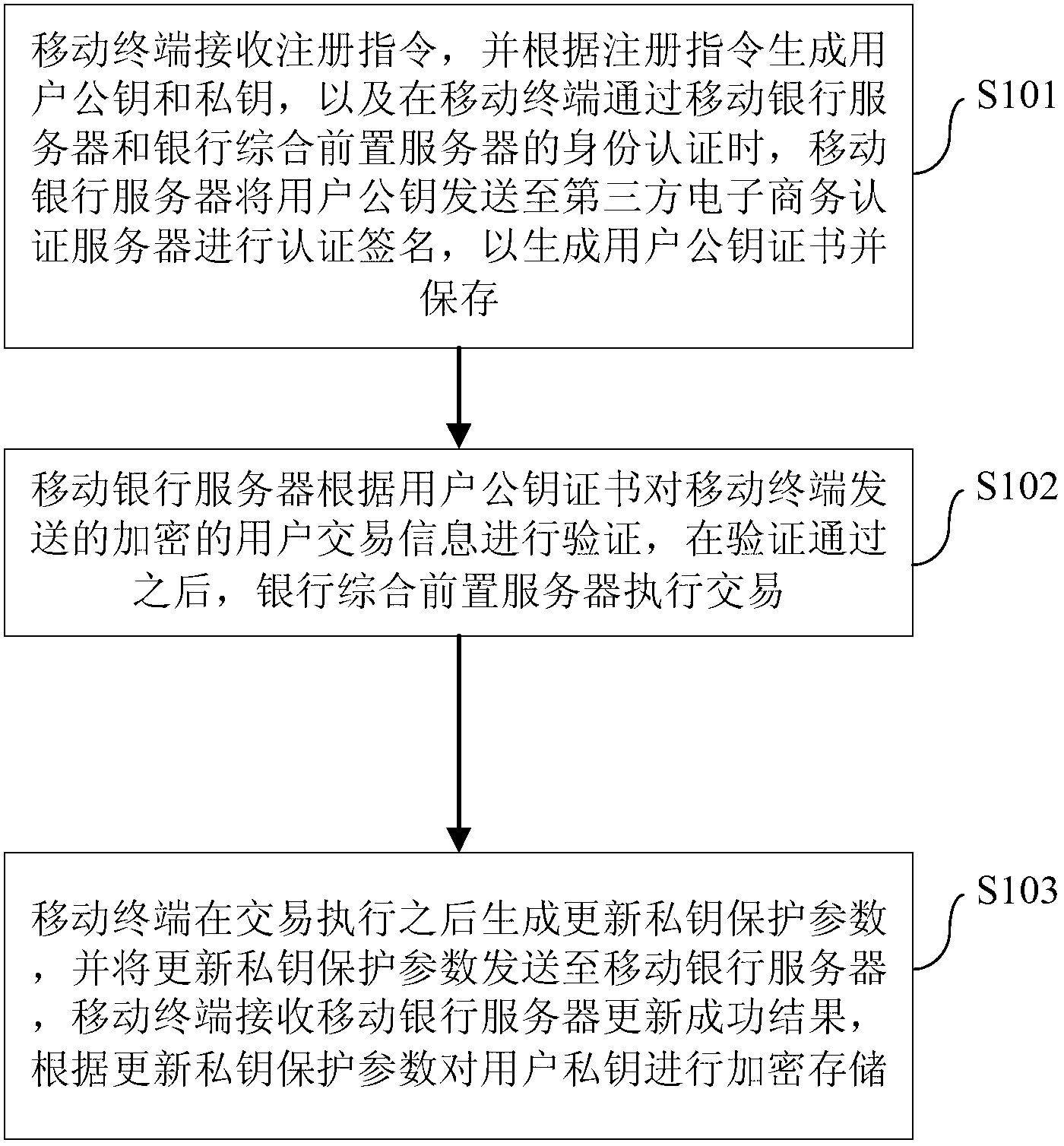
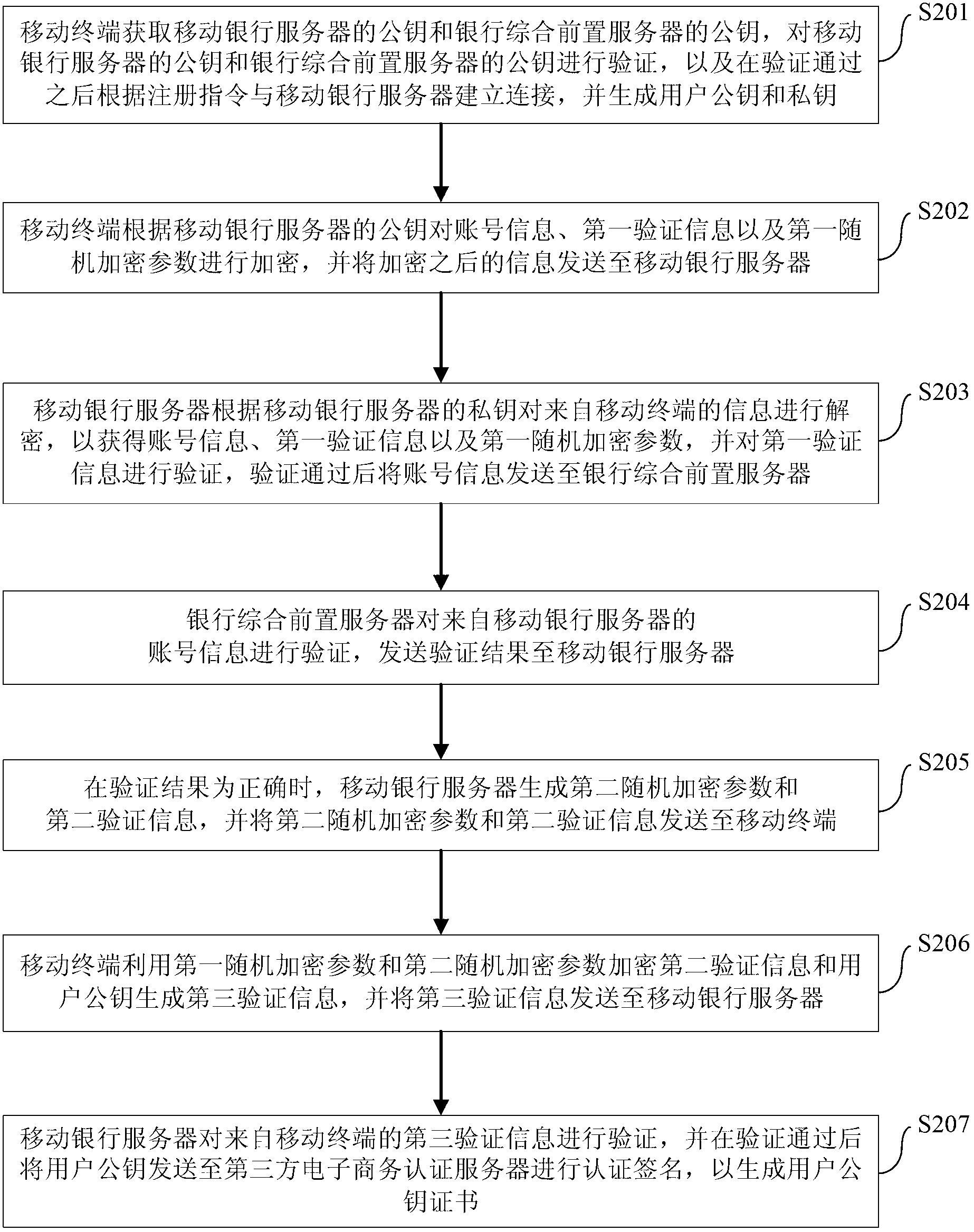
ActiveCN103067401AAvoid interactionEnsure safetyKey distribution for secure communicationFinanceThird partyE-commerce
The invention provides a method for key protection and a system for the key protection. The method for the key protection includes that a mobile terminal receives a registration instruction and generates a user public key and a user private key according to the registration instruction; when the mobile terminal is subjected to identification authentication by a mobile banking server and a bank comprehensive front server, the mobile banking server sends the user public key to a third-party e-commerce authentication server for certified signing so as to generate a user public key certificate and store the user public key certificate; the mobile banking server carries out an authentication process to encrypted user transaction information sent by the mobile terminal according to the user public key certificate, and when the authentication is passed, the bank comprehensive front server executes a transaction; and after the transaction is finished, the mobile terminal generates an updated private key protecting parameter and sends the updated private key protecting parameter to the mobile banking server, and then the mobile terminal receives an update success result from the mobile banking server and encrypts and stores the user private key according to the updated private key protecting parameter. The method for the key protection and the system for the key protection can increase attack difficulty and improve safety.
Owner:TENDYRON CORP
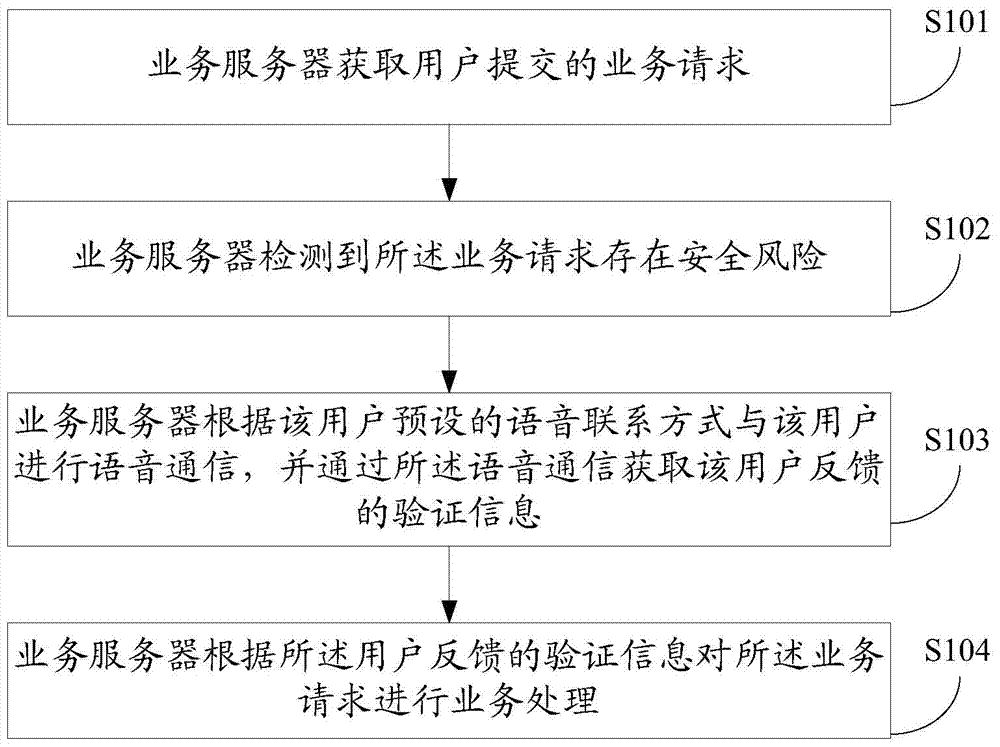
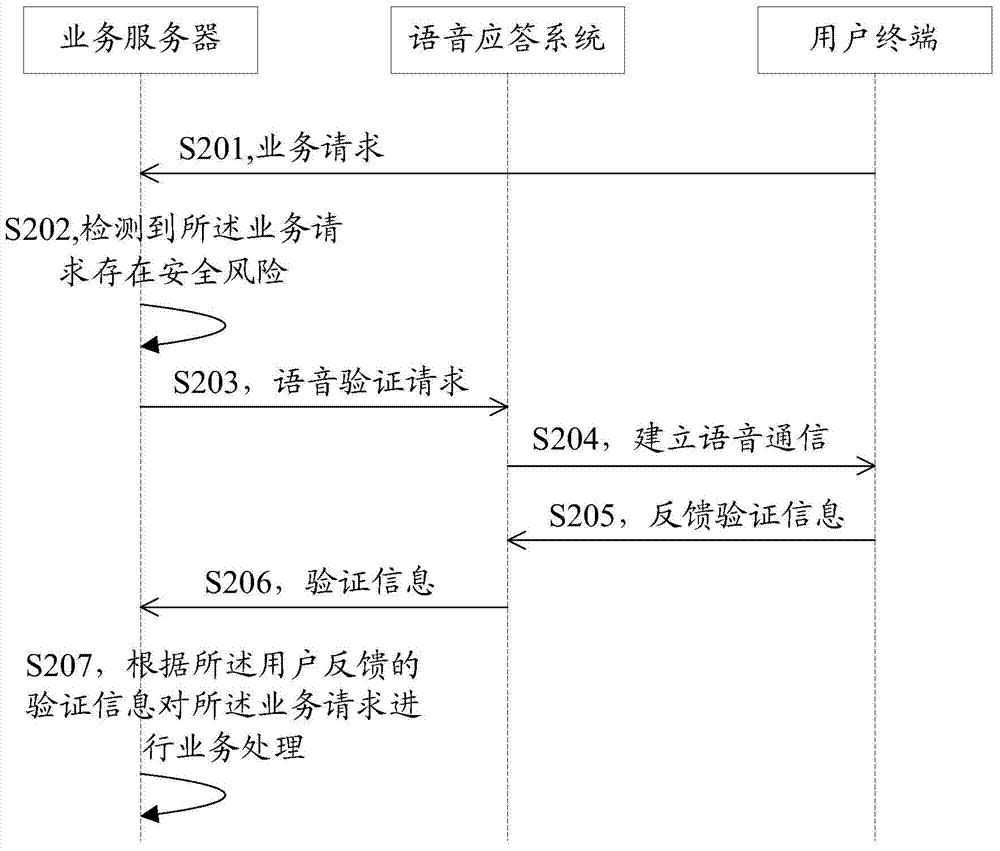
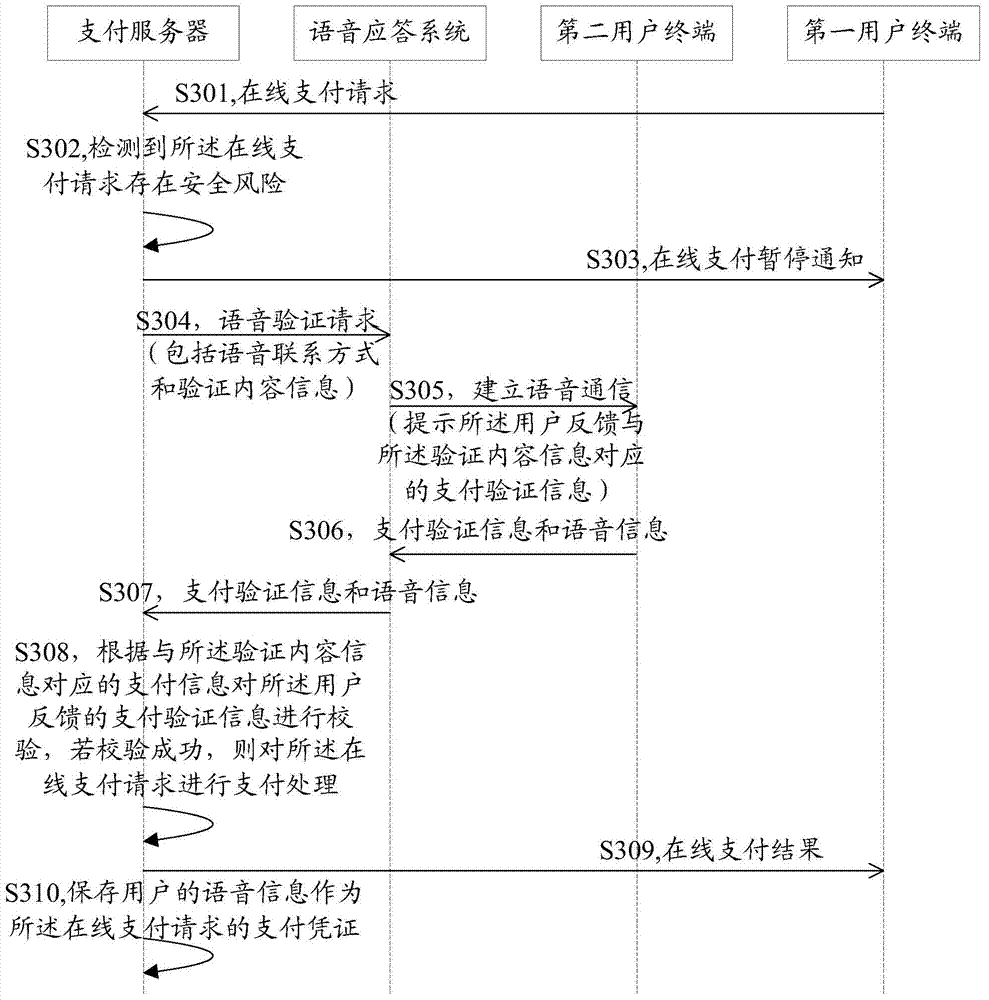
Safety verification method, service server and safety verification system
InactiveCN104753868AImprove experienceEnsure transaction securityPayment architectureBuying/selling/leasing transactionsSecurity levelVerification system
A server with processor (s) and memory receives a transaction request from a first device to perform a transaction with an account and determines a security level for the transaction. When the security level satisfies predetermined criterion, the server: instructs the first device to suspend the transaction and to display a first interface indicating the suspended transaction; and sends a confirmation request, to a second device associated with the account, for voice verification of the transaction. The server receives voice verification information from the second device that includes audio data provided by a user of the second device and determines whether the voice verification information matches stored account verification data corresponding to the account. When there is a match, the server: processes the transaction; and instructs the first device to complete the transaction and to replace display of the first interface with a second interface indicating the completed transaction.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Near field communication payment method authenticated by both sides of deal
InactiveCN103116844ARealize identificationAvoid card swipingUser identity/authority verificationPayment architectureBank accountComputer science
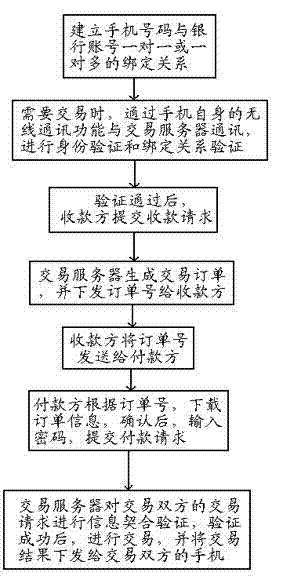
The invention discloses a near field communication payment method authenticated by both sides of the deal. The method includes steps that 1, a binding relationship of one-to-one and one-to-many of a cell phone number and a bank account is established; 2, identity authentication on both sides of the deal through a cell phone is performed when a near field communication deal is needed; 3, after authenticating, the payee inputs amount collected to the cell phone, submits a collection request to a deal server, and the deal server generates a trade order and sends the order number to the payee; 4, the payee chooses a payer to trade, and sends the order number to the payer by means of near field communication; 5, the payer downloads the order information from the deal server, identifies the order information, inputs a payment code to the cell phone, and submitting a payment request; 6, information verification is performed, the trade is carried on when the verification is successful, otherwise, the trade is not carried on. The method of identity authentication is high in safety and reliability and easy to achieve based on the uniqueness of the cell phone number and background server.
Owner:李锦风 +2
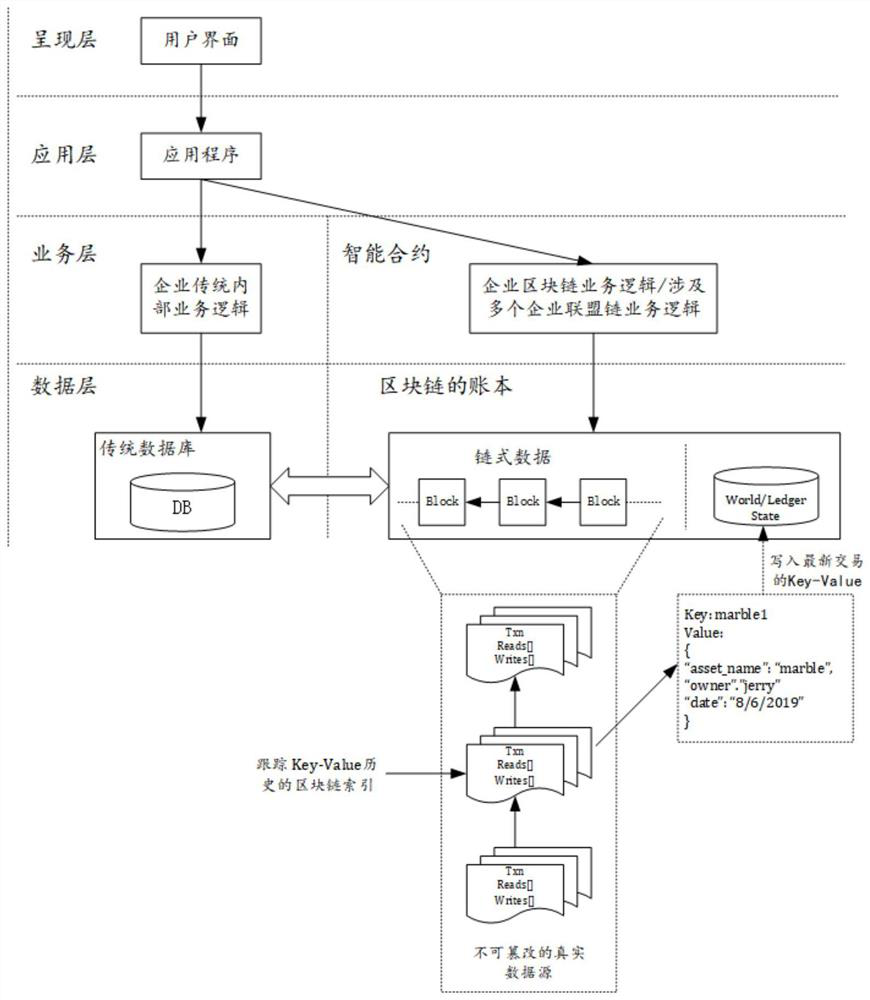
Data reconciliation method and system and computer readable storage medium
ActiveCN108074177AImprove reconciliation efficiencyEnsure transaction securityFinanceSmart contractMedication Reconciliation
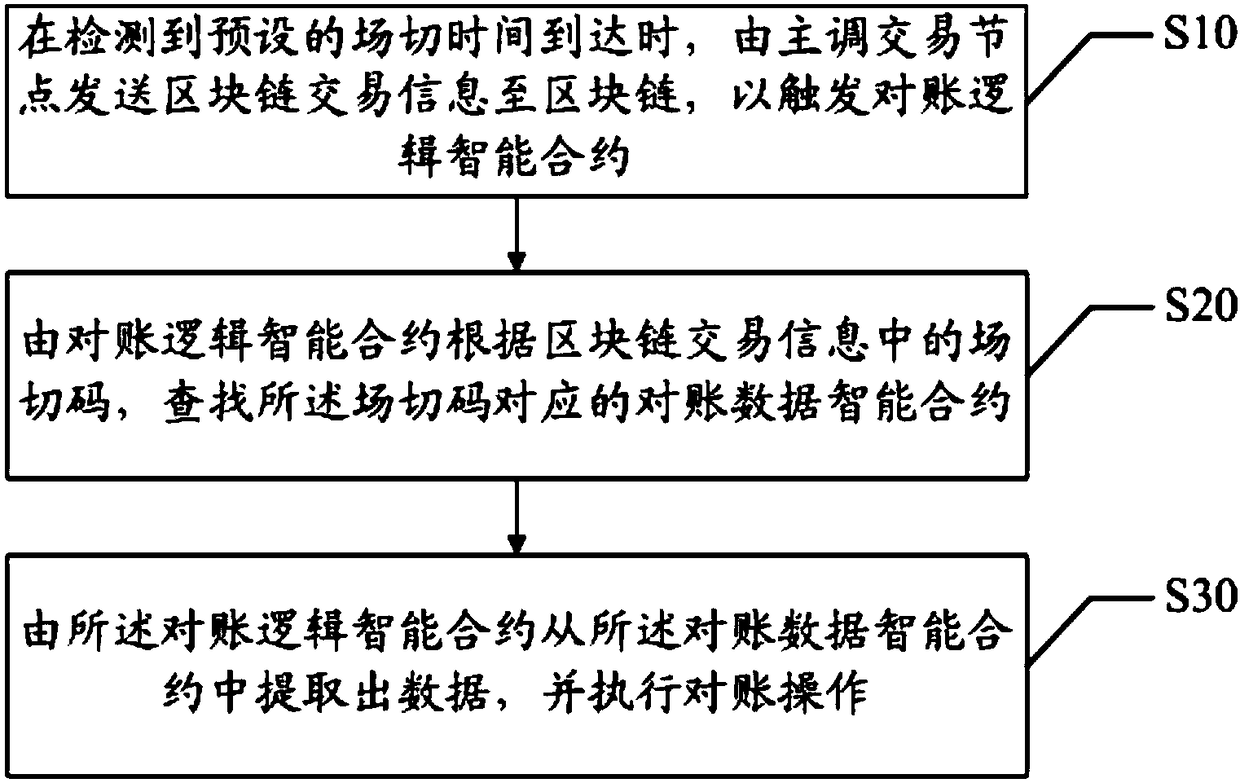
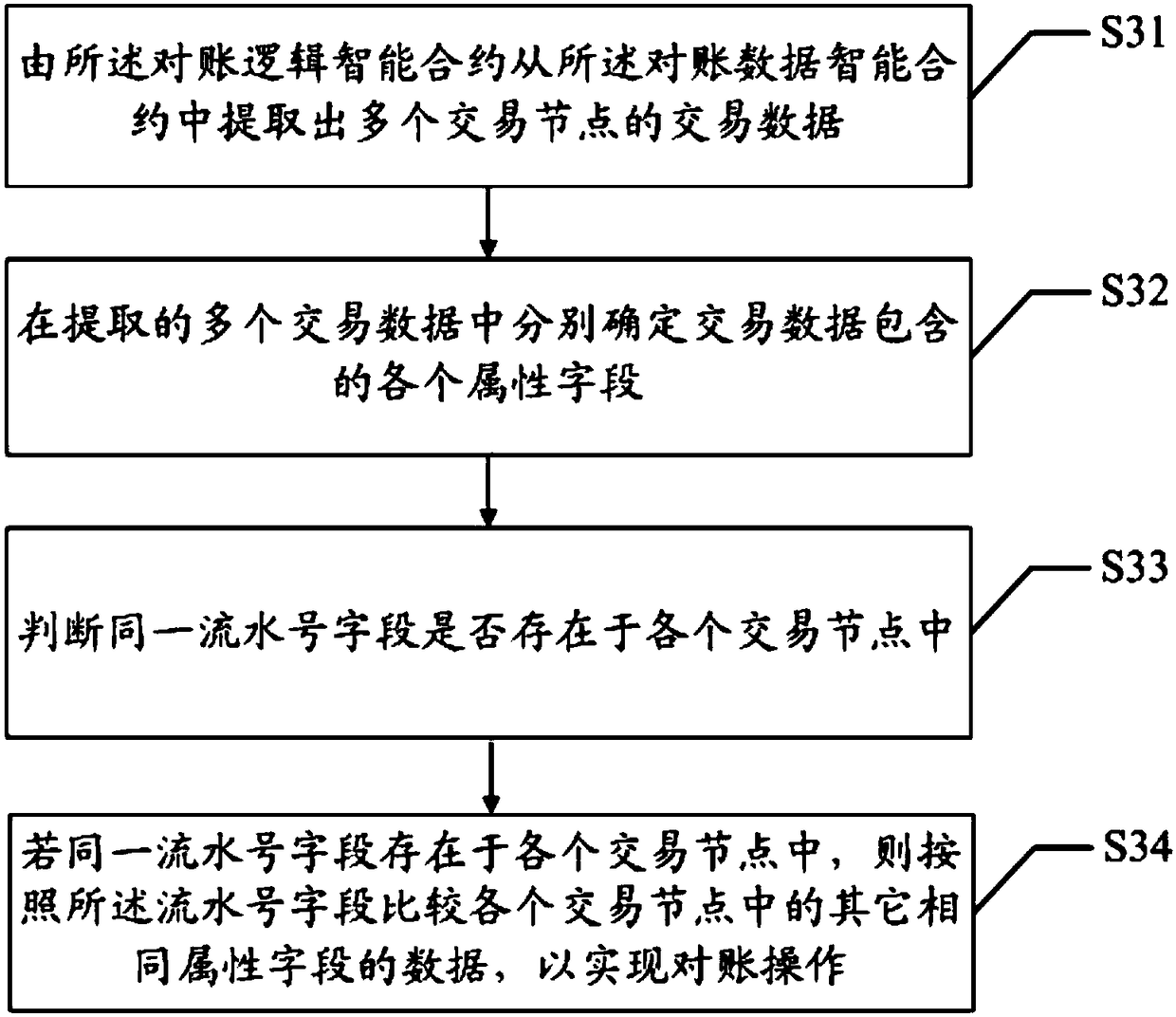
The invention discloses a data reconciliation method and system and a computer readable storage medium. The method comprises the following steps: when a preset filed switching time arrives, a main transaction node sends block chain trading information to a block chain to trigger a reconciliation logic smart contract; the reconciliation logic smart contract searches a reconciliation data smart contract corresponding to filed switching codes according to the filed switching codes in the block chain trading information; and the reconciliation logic smart contract extracts data from the reconciliation data smart contract and carries out data reconciliation. Data reconciliation safety and efficiency are improved.
Owner:WEBANK (CHINA)
Logistics management system based on Internet
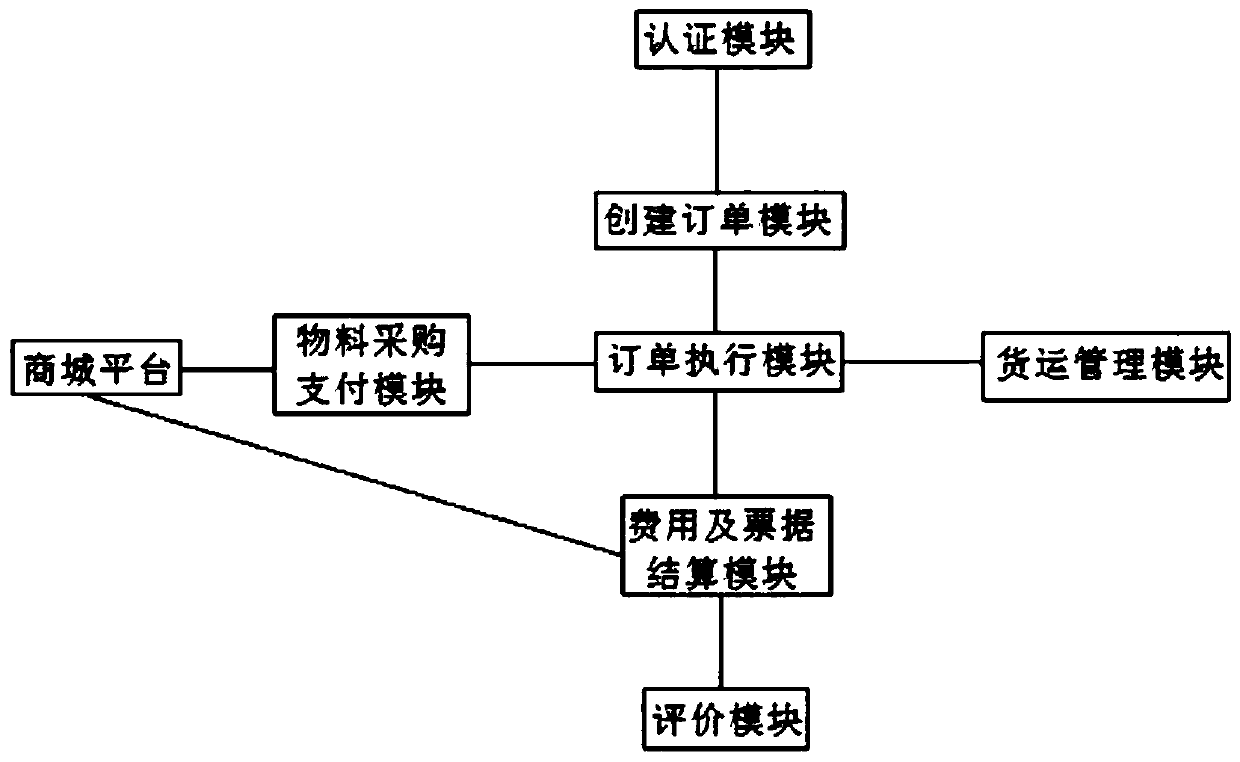
InactiveCN108681850AHigh speedImprove efficiencyElectronic credentialsLogisticsPaymentLogistics management
A logistics management system based on Internet according to the invention comprises a client and a server end. The server end comprises an authentication module, an order creating module, an order executing module, a freight management module, a cost and bill settling module, a material purchasing payment module and a shopping mall platform. The order creating module receives and processes, issues transportation request information and generates a logistics order. The material purchasing payment performs freezing or transferring on a resource-party fund account according to a logistics cost in the logistics order. The resource party or a carrier purchases the materials required for transportation on the shopping mall platform through a fund account. The order executing module performs transportation operation and cargo inspection and receiving by a consignee. The freight management module is used for tracking the cargo. The shopping mall platform performs combined settlement of the material total cost and bill with a material supplier through the cost and bill settling module and supplies a logistics cost invoice to a resource party. The logistics management system has advantagesof realizing high interaction experience, reducing logistics cost, providing benefit and ensuring benefit of each party.
Owner:叶明宝
Information interaction method and system and smart key equipment
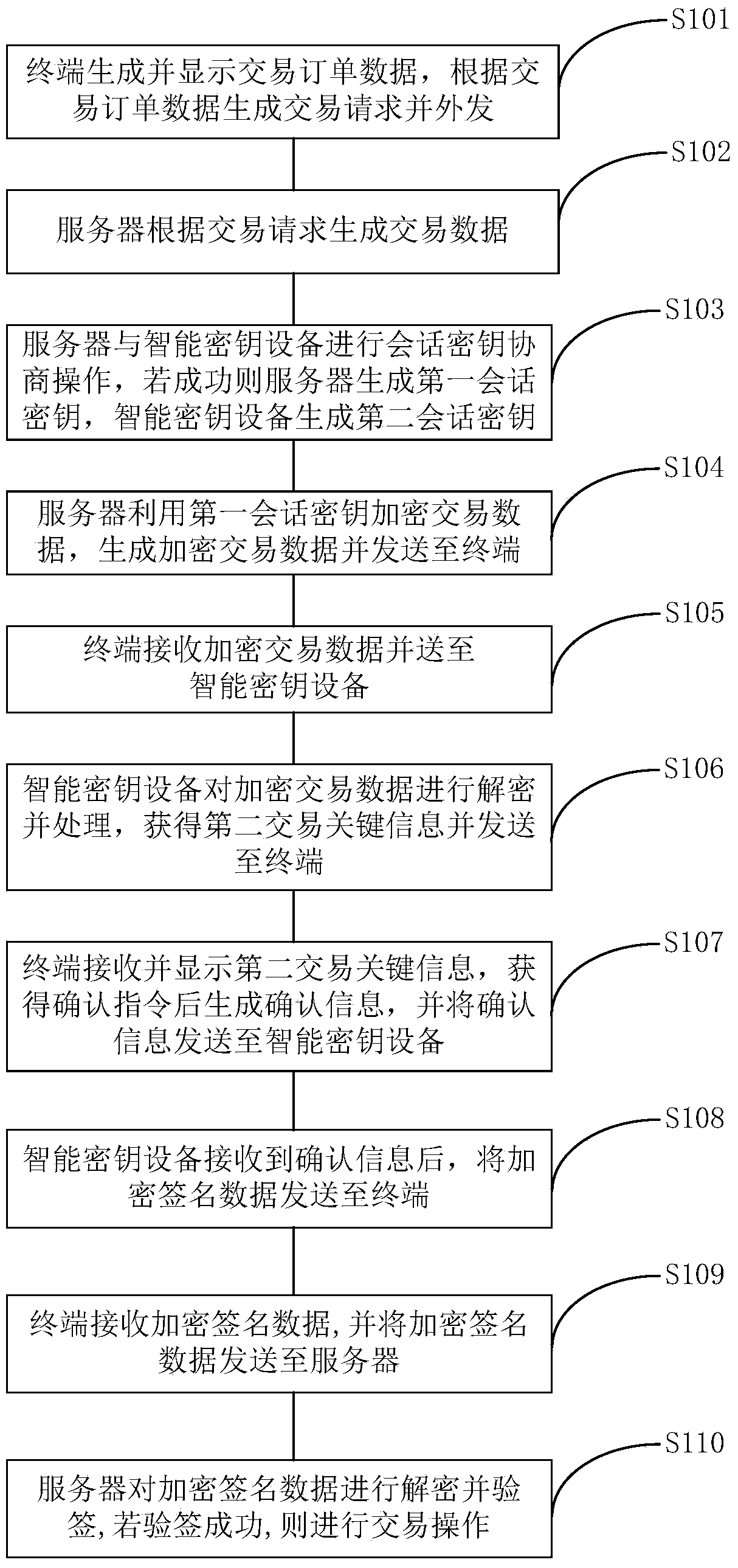
ActiveCN104243451AImprove portabilityReduce volumeFinanceUser identity/authority verificationTransaction dataComputer terminal
The invention provides an information interaction method and system and smart key equipment. The information interaction method comprises the steps that a terminal generates and displays transaction order data and generates and issues a transaction request; a server receives the transaction request and generates transaction data; the server and the smart key equipment conduct session key negotiation operation, and a first session key and a second session key are generated respectively; the server uses the first session key to encrypt the transaction data, generates the encrypted transaction data and sends the encrypted transaction data to the terminal; the terminal receives the encrypted transaction data and sends the encrypted transaction data to the smart key equipment; the smart key equipment uses the second session key for decryption to obtain the transaction data, processes the transaction data, obtains second transaction key information and sends the second transaction key information to the terminal; the terminal displays the second transaction key information, generates a confirmation information after obtaining confirmation instruction and sends the confirmation information to the smart key equipment; the smart key equipment sends encrypted signature data to the terminal, and the terminals receives the encrypted signature data and sends the encrypted signature data to the server; the server uses the first session key to decrypt the encrypted signature data, obtains the signature data and conducts attestation operation.
Owner:TENDYRON CORP
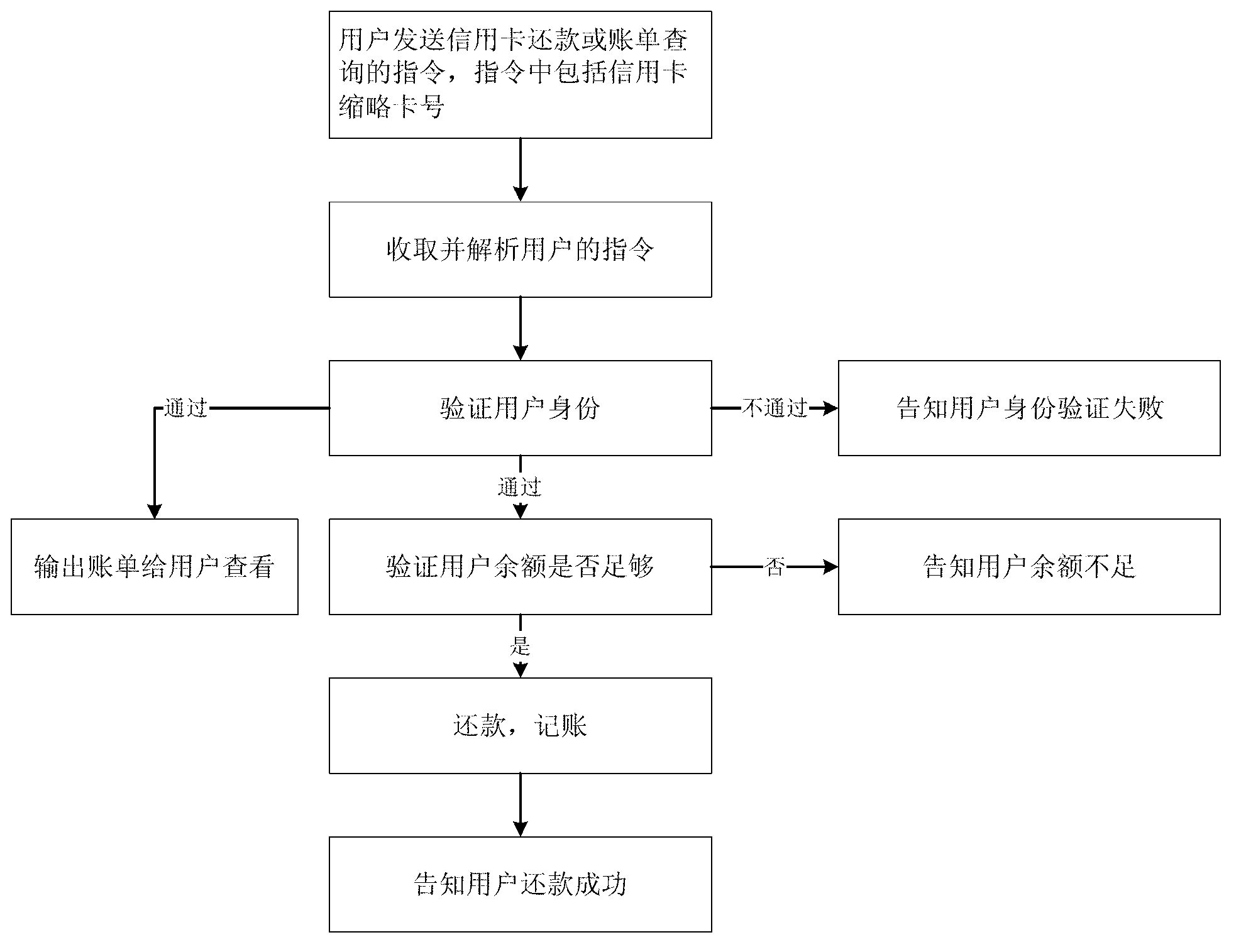
Payment method based on socializing platform
The invention discloses a payment method based on a socializing platform and belongs to the field of electronic commerce. The payment method based on the socializing platform is characterized in that when a user needs to pay, the user informs a payment module by an instruction. The payment module is connected with a trading system (a banking system or other payment systems) and a relative request is treated. The user needs to own an account of the socializing system and an account where money can be deducted (a bank car, a pre-payment car, a virtual account and the like). Two accounts are related and the account of the socializing platform and the account where money is deducted do not need opening on the same socializing platform or the same institution. In purchasing financial management products, directional payment is used, namely, cash is transferred from one account of the user to the other account. In purchasing, information of financial management products, a purchasing cash amount or portion and the like need inputting. A socializing identification (ID) of the opposite side and a transferring cash amount are input to finish cash transferring. In credit card repayment, an abbreviated account of the credit card is input to inquire an account and repayment. In paying fees, fee paying information is input to pay the fees. All communication is done with codes so as to ensure safety of trading.
Owner:VIVE&BEST INFORMATION SERVICE
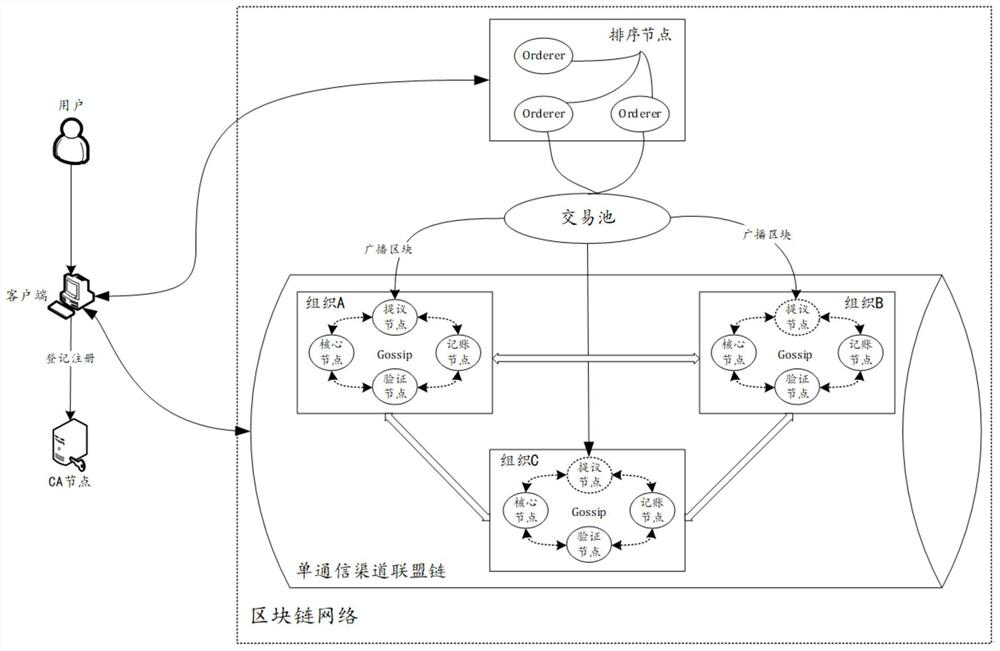
Energy storage system automatic demand response method based on block chain technology
InactiveCN109672202ARealize reasonable configurationAchieve constructionSingle network parallel feeding arrangementsAc network load balancingEngineeringSmart contract
The invention provides an energy source local area network energy storage system automatic demand response method based on a block chain technology. The method comprises the following steps of obtaining state information of the energy storage system connected into an energy source local area network; building an energy storage system charging and discharging model; building an electric automobileschedulable capability comprehensive evaluation system; using a real-time electricity price mechanism; setting charging and discharging electricity price orienting electric automobile users; finally developing a decentered automatic demand response criterion on the basis of the block chain technology; building an intelligent contract between two trading parties. By aiming at the energy source local area networks comprising an electric automobile cluster, a wind light power generation system and an energy storage battery, a distributive node network for charging and discharging by the user is built by the invention for pursuing point-to-point direct trading of mass users; reasonable configuration of inside resources of the system is realized; the autonomous supply and demand balance state is achieved.
Owner:ZHEJIANG UNIV OF TECH
A payment account secure transaction method and system based on block chain
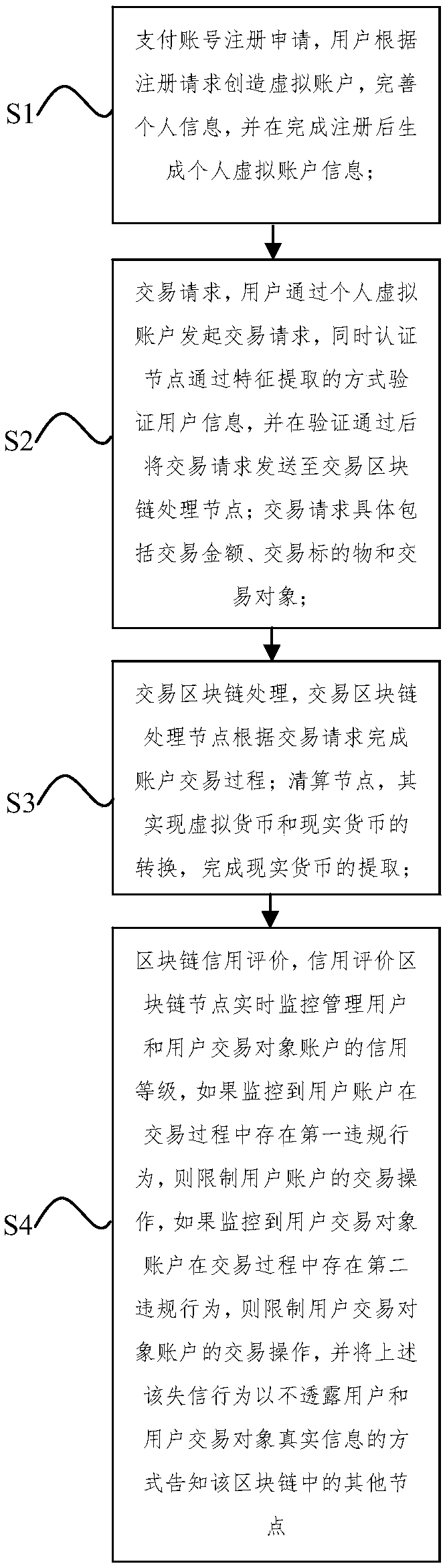
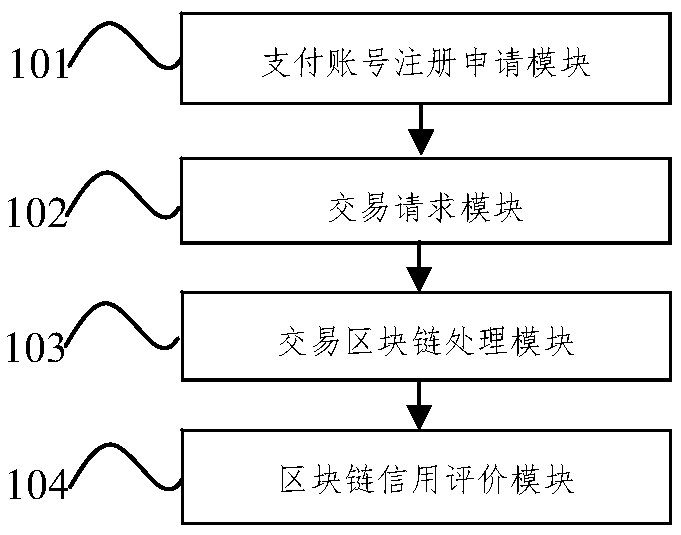
InactiveCN108985773AImprove securityConvenient transactionCurrency conversionProtocol authorisationRing signatureEncryption
The invention provides a payment account secure transaction method and system which improve the transaction security of a payment account through multiple protection means and will not leak the real information of users. The invention adopts the following technical scheme: a user applies for a payment account, an authentication node performs feature extraction on the user's personal information, after checking, the user is added to the payment account transaction block chain node and constrained by the intelligent contract, according to the specific process of payment account transaction, theuser pays or accepts the virtual currency, transmits the virtual currency through ring signature encryption, and extracts the real currency through the clearing node. A credit rating block chain nodeis set to monitor and manage account credit ratings of users and user transactions, if a first violation of a user account during a transaction is monitored, then, the transaction operation of the user account is restricted, and if the second violation behavior of the user transaction object account in the transaction process is monitored, the transaction operation of the user transaction object account is restricted, and other nodes in the block chain are informed of the above-mentioned dishonest behavior in a manner that the true information of the user and the user transaction object is notdisclosed.
Owner:HENGBAO
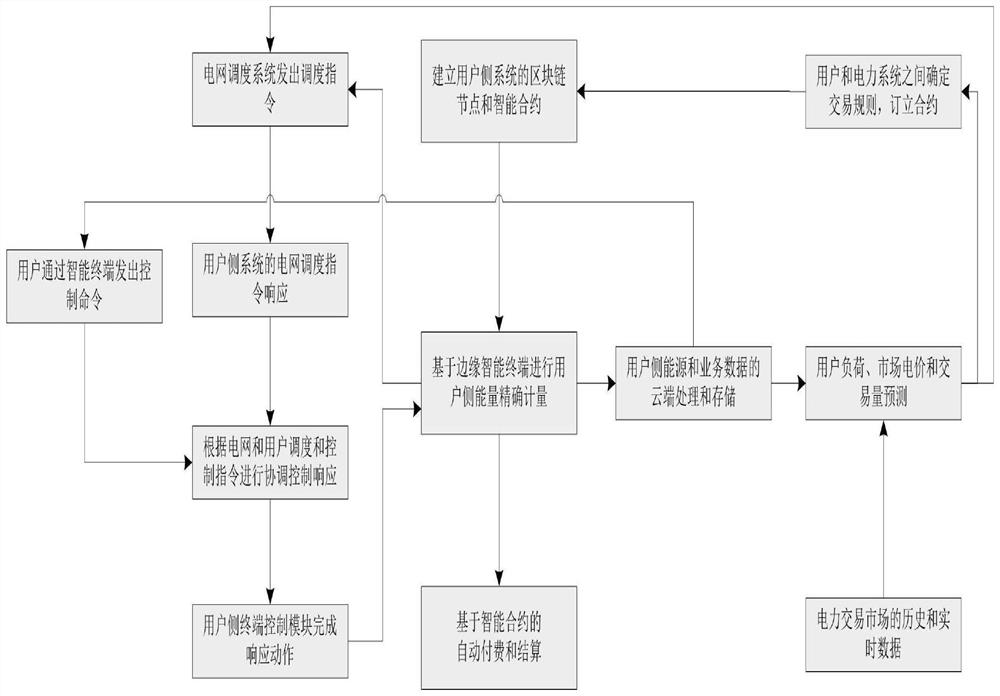
Edge-cloud collaborative user load prediction control and transaction system and implementation method thereof
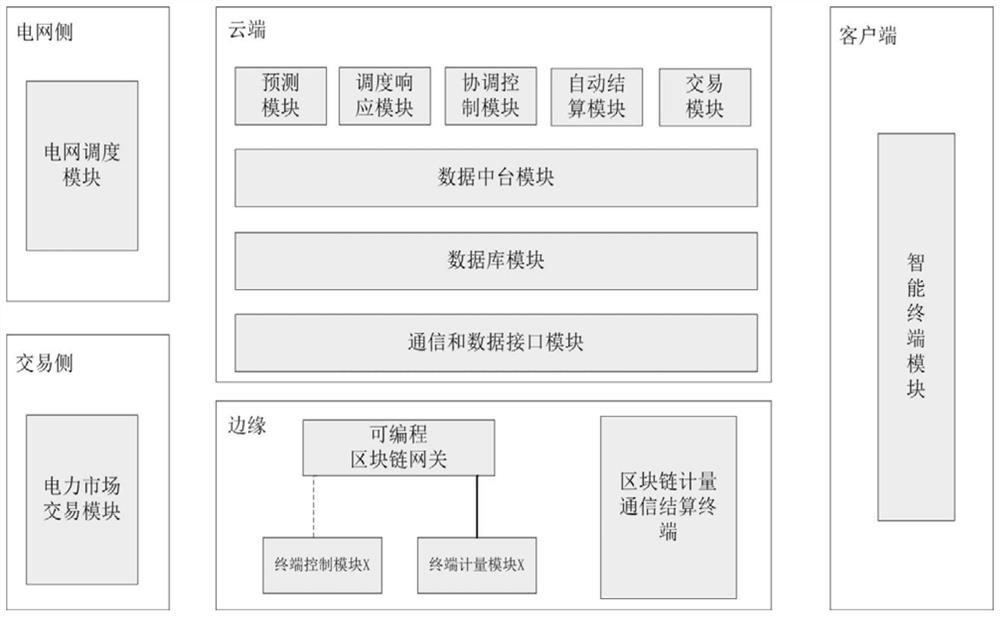
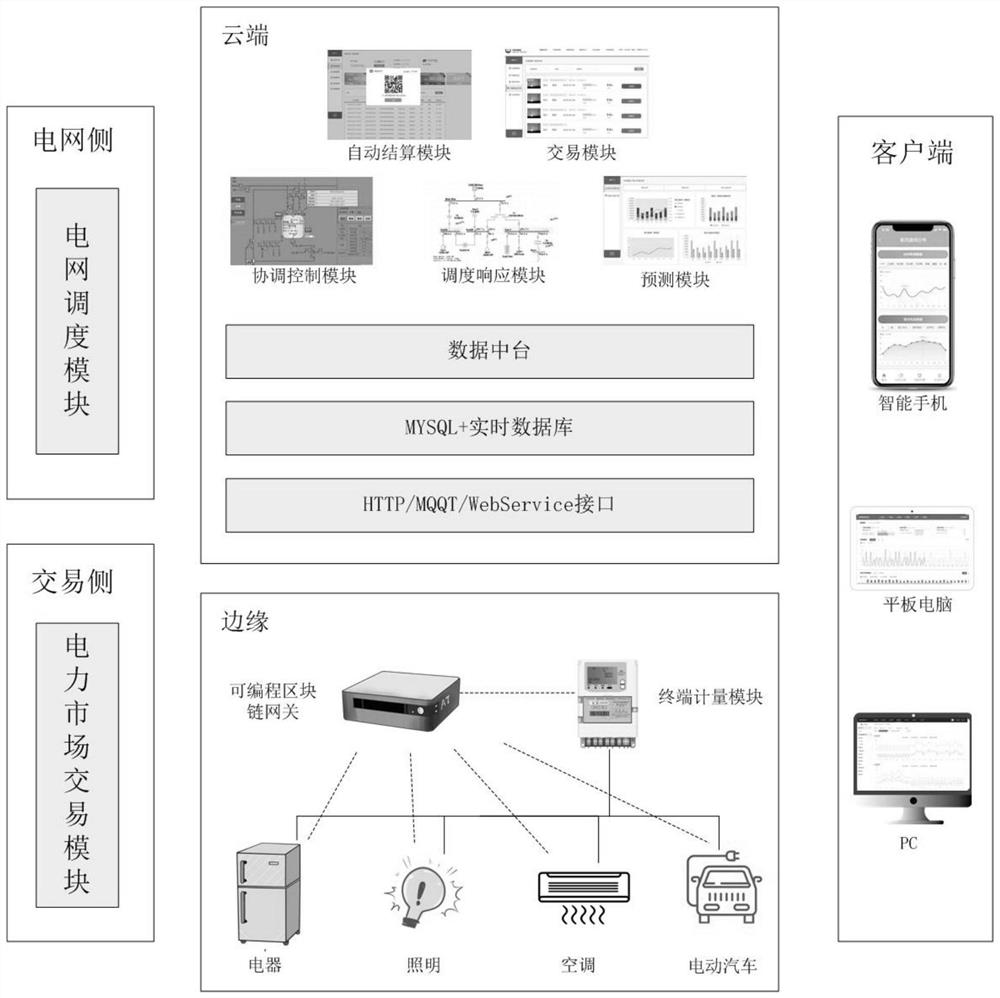
PendingCN111754023AReal-time grasp of operation statusEnsure data securityForecastingDigital data protectionData centerPower grid
The invention discloses an edge-cloud collaborative user load prediction control and transaction system and an implementation method thereof; the edge-cloud collaborative user load prediction controland transaction system comprises a cloud, an edge and a client, and the edge comprises a block chain metering communication settlement terminal, a programmable block chain gateway, a terminal controlmodule and a terminal metering module; the cloud comprises a communication and data interface module, a database module, a data center module, a prediction module, a scheduling response module, a coordination control module, a transaction module and an automatic settlement module; the Client comprises an intelligent terminal module. Interaction with the dispatching module on the power grid side and the electricity market transaction module on the transaction side can be achieved, power grid dispatching instruction response and electricity market transaction are supported, and the power grid issupported to master the accurate user system energy consumption condition. By converting a user system into predictable and controllable resources, power grid dispatching and user instructions can beaccurately and automatically responded. And the edge side block chain records the charging period to guarantee data security, and the smart contract transaction automation is realized.
Owner:GUANGDONG MINGYANG WIND POWER IND GRP CO LTD
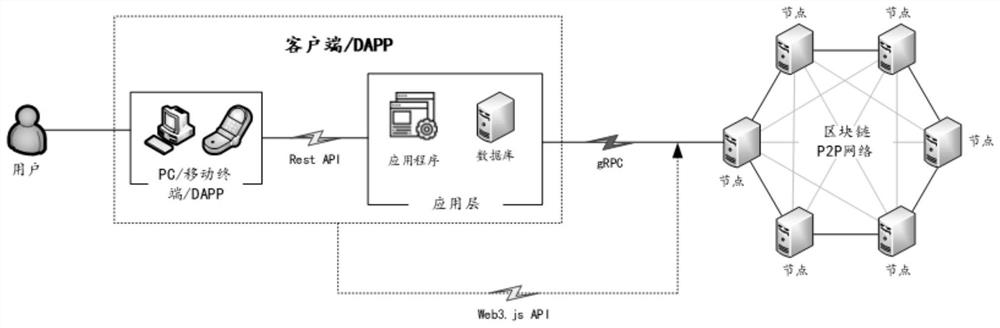
Multi-round voting type fault-tolerant sorting consensus mechanism and method based on block chain
PendingCN112541758AEnsure safetyImprove fault toleranceFinanceDigital data protectionComputer networkTransaction data
The invention discloses a multi-round voting type fault-tolerant sorting consensus mechanism and method based on a block chain. The mechanism comprises service nodes in the consensus and accounting process. Transaction initiation and sorting are carried out through the service nodes, legal transactions are obtained and then put into a transaction pool for transaction, and then multiple rounds of voting consensus is entered; multiple rounds of consensus verification and execution is performed on the transaction data through the service node in the voting consensus; and after the consensus is completed, the multichannel account book of the block chain is synchronously updated and accounted, the transaction with successful consensus is sent to the sorting node to sort out the block, the received block transaction is verified by the accounting node, the state database of the block transaction is updated after verification, a new block is added to the main chain, and then a new round of consensus verification and execution work is entered. According to the mechanism and method, achievement of global correct consensus can be guaranteed, fault tolerance is high, and the mechanism and methodare suitable for alliance chains with a large number of nodes. When a large number of verification nodes fail, the system stops working, so that the security of the blockchain is better guaranteed,and the double-fault problem is prevented.
Owner:鲁静
Mobile payment method and system based on two-dimension codes
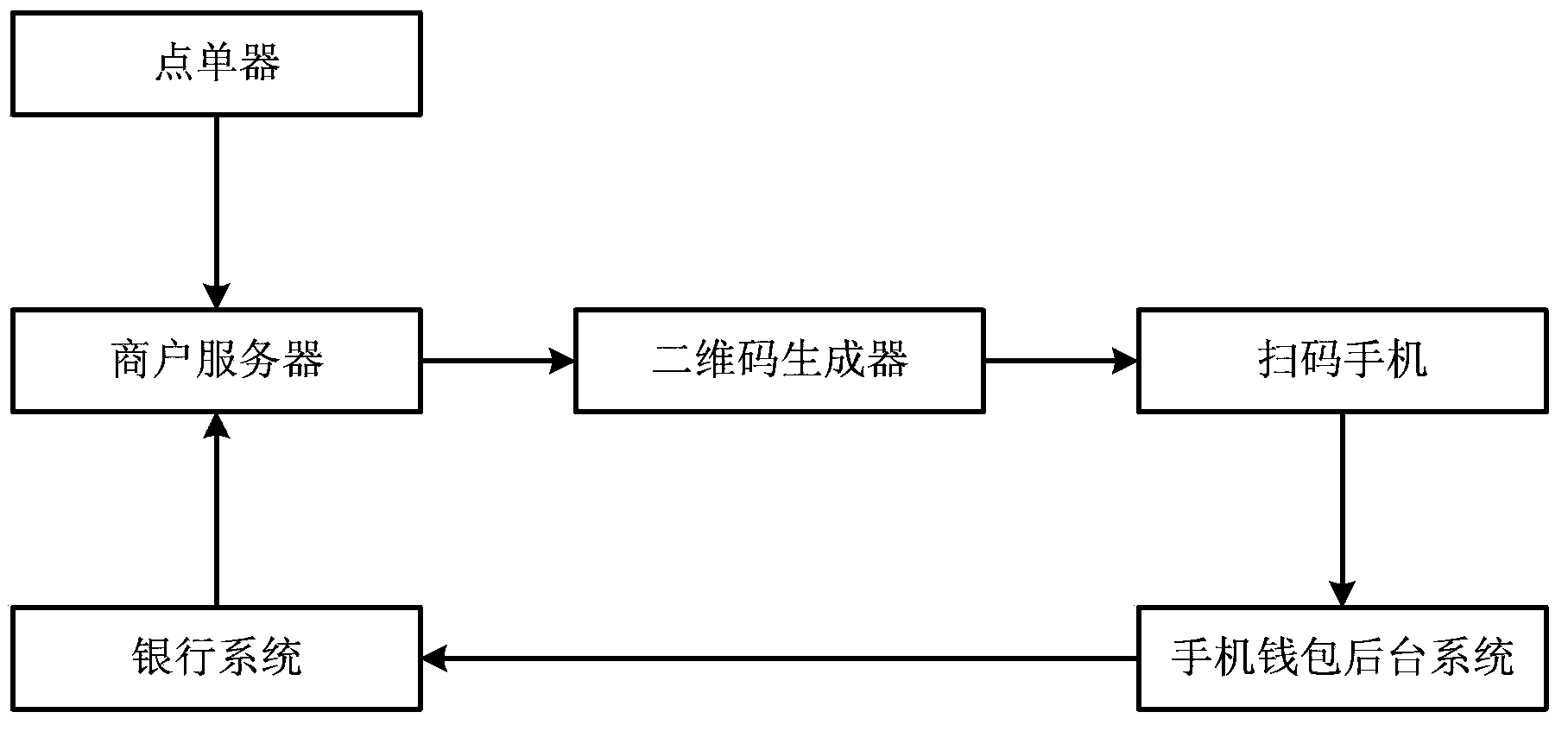
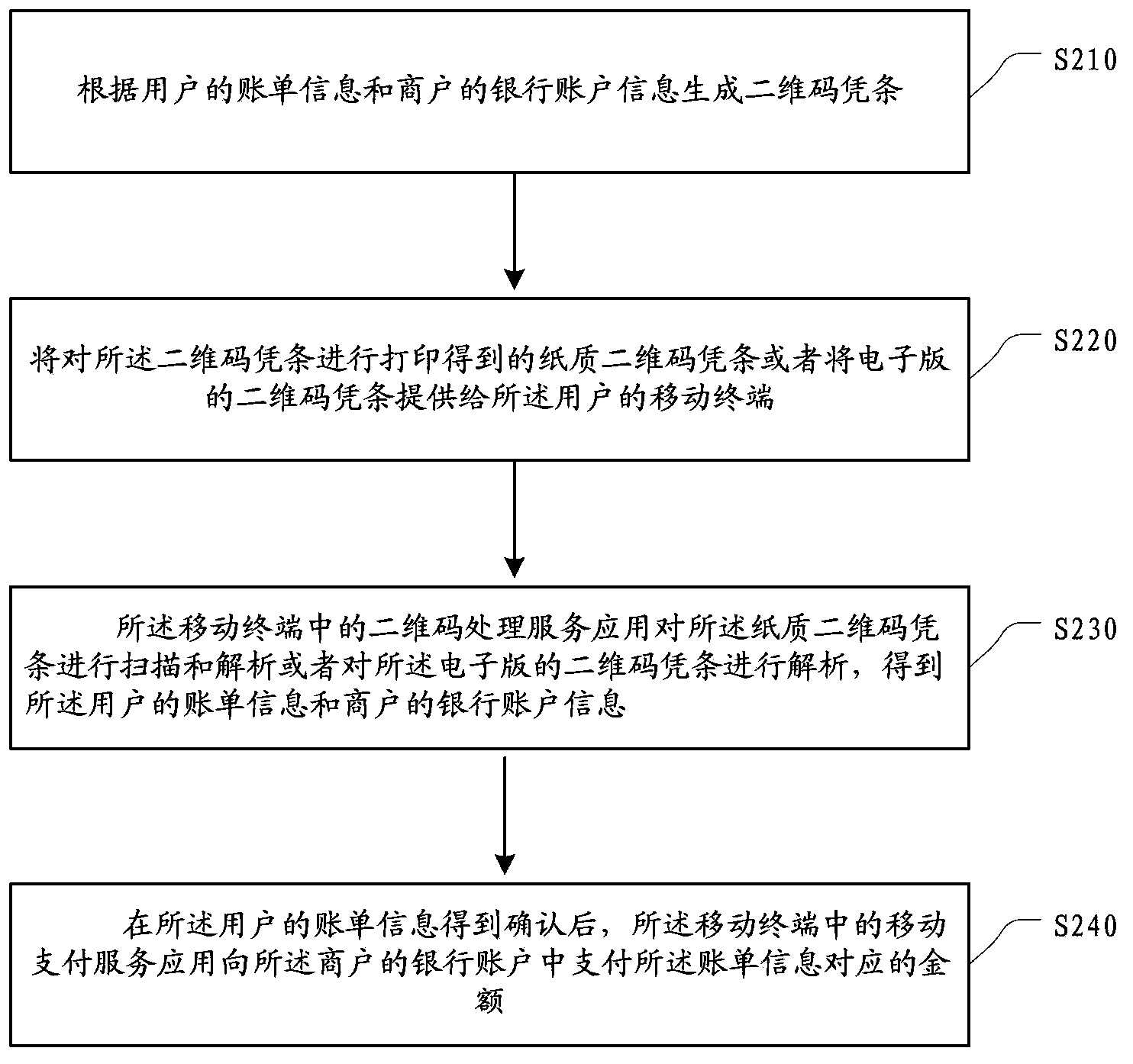
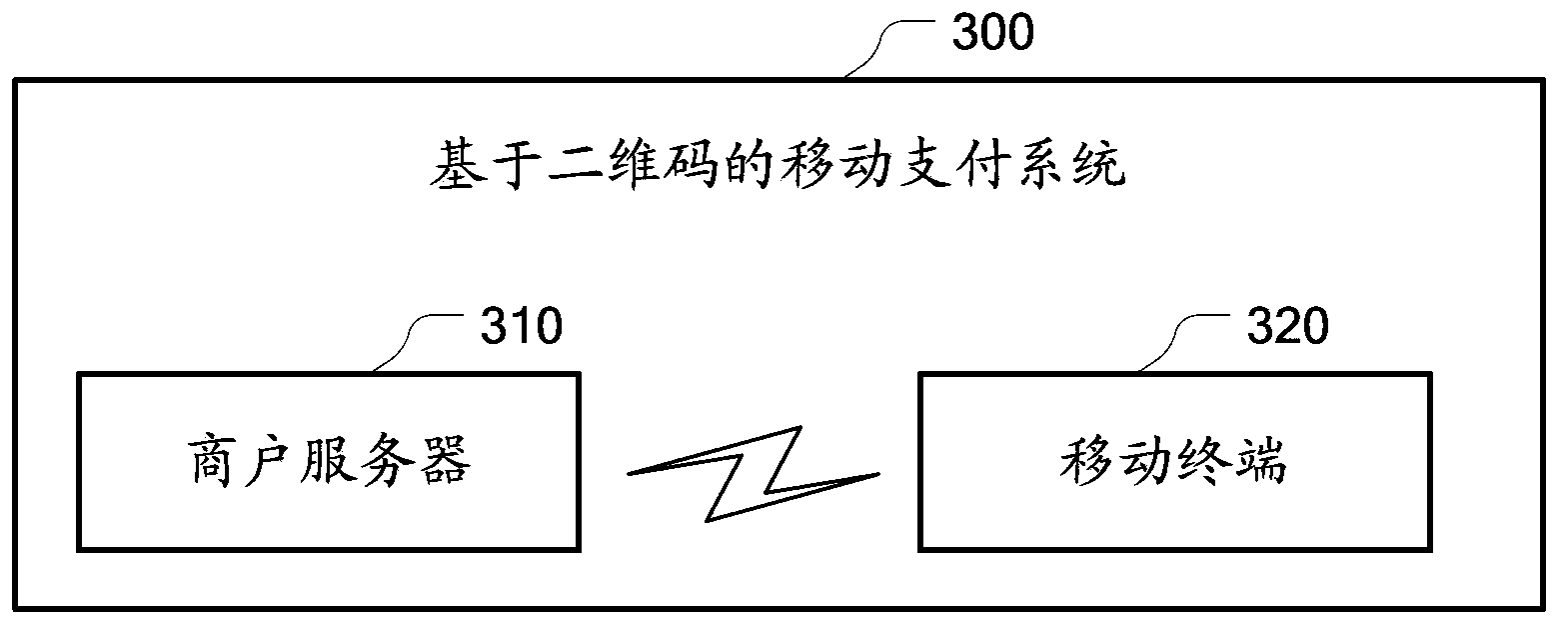
InactiveCN104281948AEnsure transaction securityThe operation process is simpleCryptography processingPayment architectureMobile paymentWhole systems
The embodiment of the invention provides a mobile payment method and system based on two-dimension codes. The method mainly comprises the steps of generating a two-dimension code slip according to bill information of a user and bank account information of a merchant, printing the two-dimension code slip to obtain a paper two-dimension code slip or providing the two-dimension code slip of an electronic edition to a mobile terminal of the user, utilizing a two-dimension code processing service application in the mobile terminal to scan and analyze the paper two-dimension code slip or analyze the two-dimension code slip of the electronic edition to obtain the bill information of the user and the bank account information of the merchant, and utilizing a mobile payment service application in the mobile terminal to pay money corresponding to the bill information to a band account of the merchant after the bill information of the user is confirmed. The mobile payment method and system based on the two-dimension codes enables the two-dimension code technology and the mobile payment technology to be combined and has the characteristics of short time and short reach, and therefore transaction security of the whole system is guaranteed. The user operation process is simple, and convenience of mobile payment is improved.
Owner:AEROSPACE INFORMATION
Method and system for preventing repeated payment
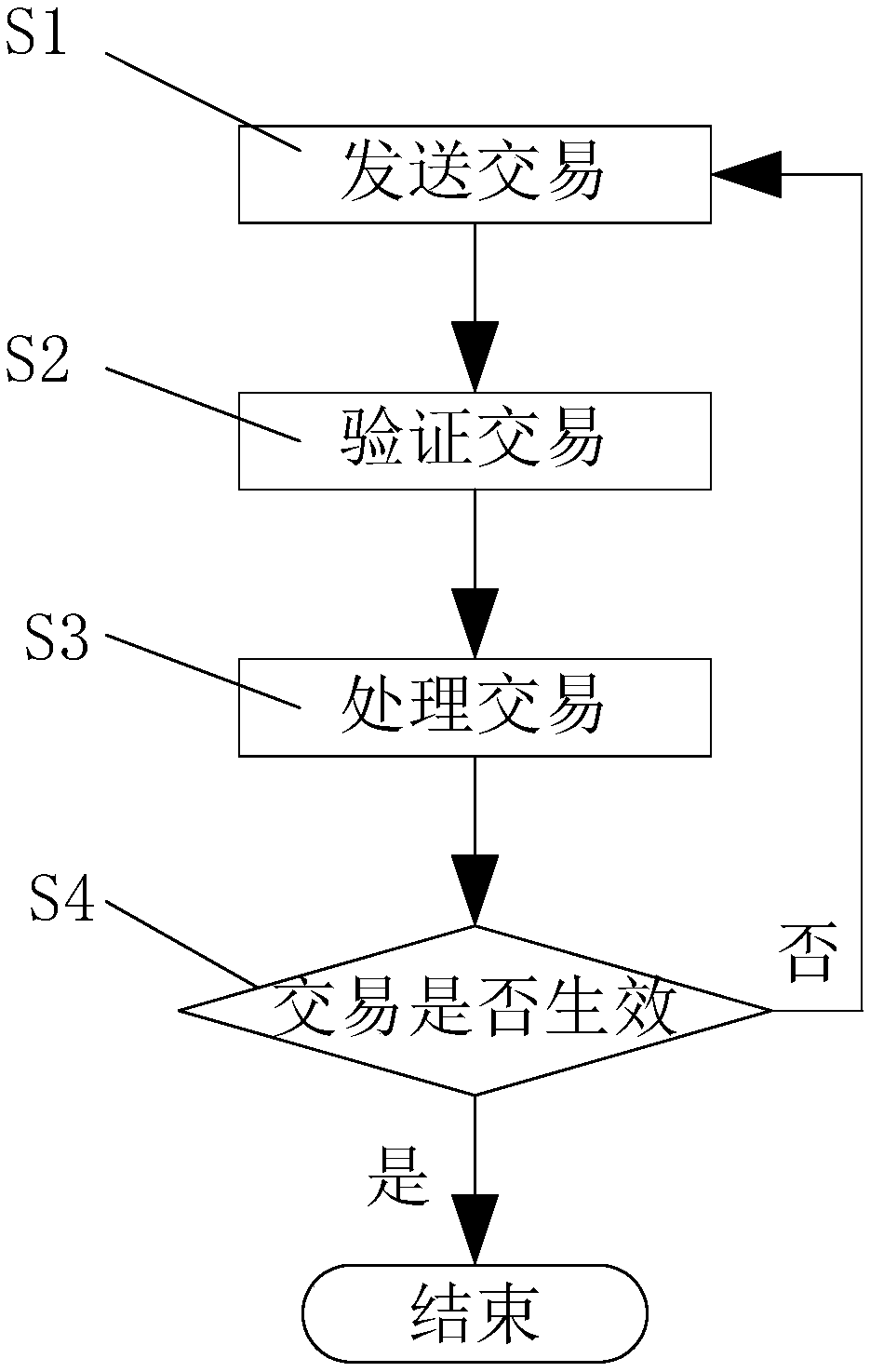
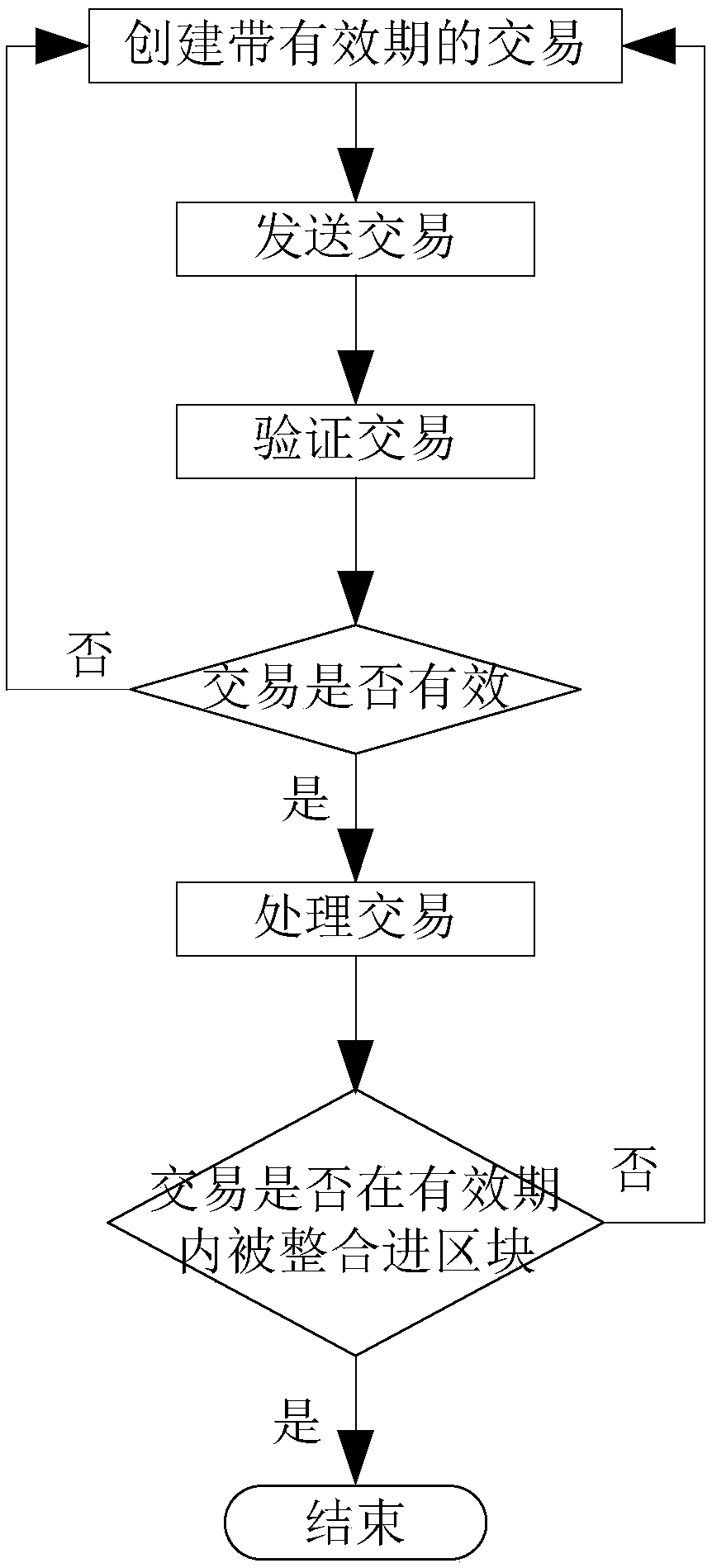
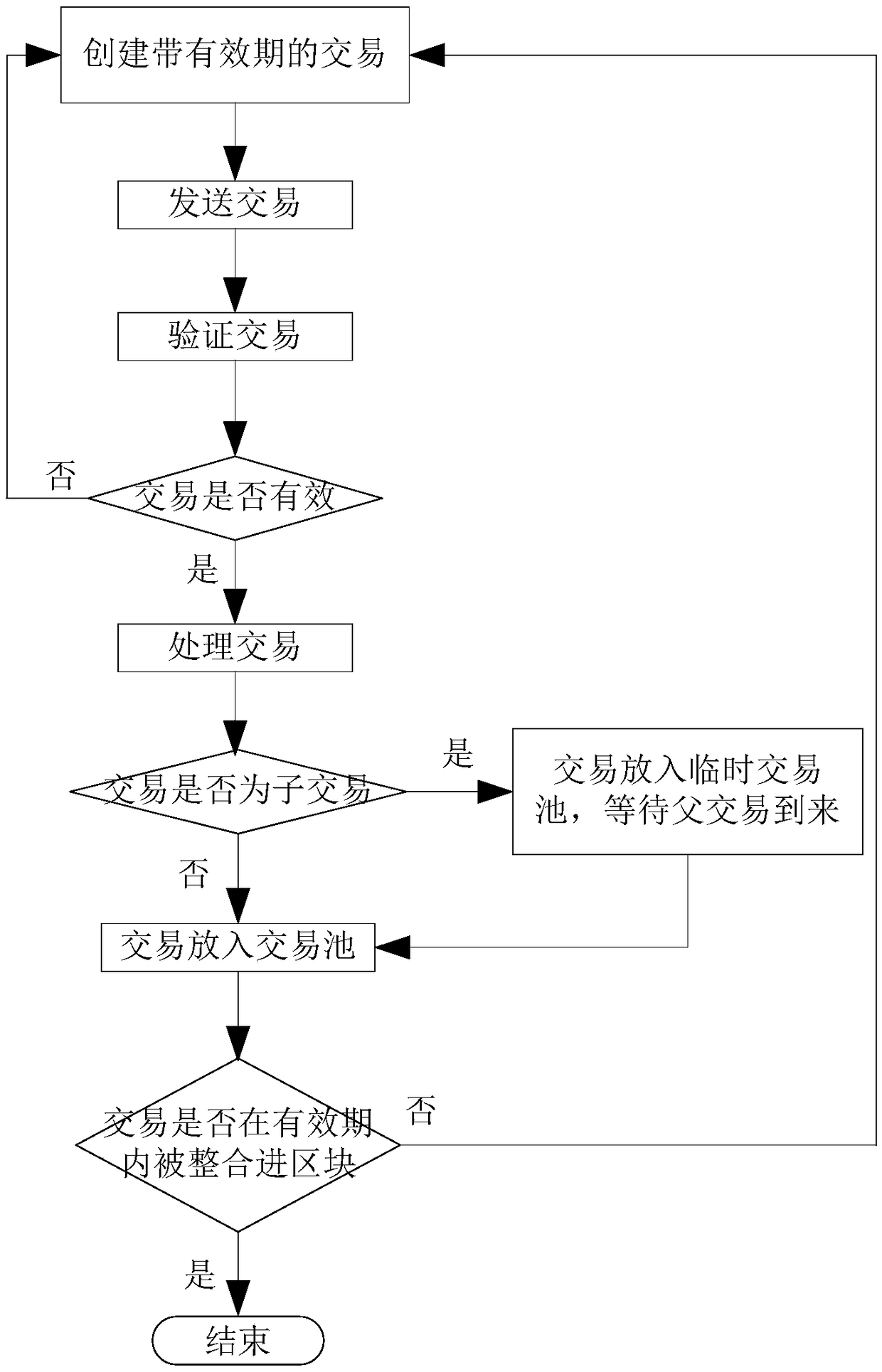
InactiveCN108876377AAvoid the possibility of double paymentEnsure transaction securityFinancePayment protocolsPaymentFinancial transaction
The invention discloses a method and a system for preventing repeated payment, and belongs to the technical field of blockchain. The method comprises the steps of: S1, sending a transaction: the transaction with a valid period is sent to a node of any blockchain network; S2, verifying the transaction: whether the transaction is valid is verified by the node; S3, processing the transaction: a transaction which is verified successfully is put into a pool of nodes and waits to be processed into a valid transaction or an invalid transaction; and S4, determining whether the transaction is valid: ifthe transaction is integrated into a block within the valid period, the transaction is valid and the transaction ends; and if the transaction has expired in the pool of nodes, the transaction is invalid, then S1 to S4 is repeated and the transaction does not end until the transaction is valid. The invention further includes a system, a device, and a storage medium. Specific to a case that repeated payment existing in an existing transaction mechanism, repeated payment can be prevented, so as to speed up effective time for a transaction and maintain stability of the blockchain system.
Owner:HANGZHOU FUZAMEI TECH CO LTD
E-bank safety certification method based on living fingerprint verification
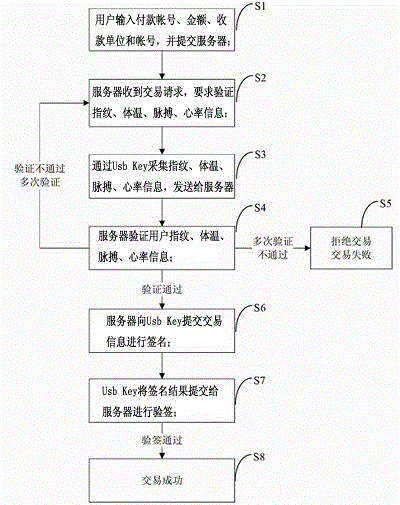
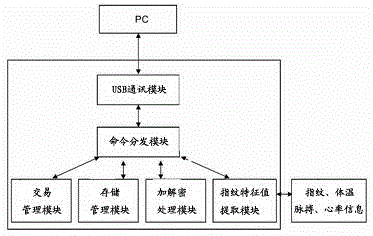
InactiveCN104134030AGuaranteed validityMonitor real-time body temperatureDigital data authenticationProtocol authorisationOperation safetyDatabase
The invention provides an E-bank safety certification method based on living fingerprint verification. According to the E-bank safety certification method based on living fingerprint verification, an E-bank terminal Ukey and an E-bank background identity authentication database are involved. A fingerprint collecting and identifying module, a body temperature sensor, a pulse sensor, a heart rate sensor and an information feature value extracting module are set in the E-bank terminal Ukey. A fingerprint information feature value comparison processing module is arranged in the E-bank background identity authentication database and is used for comparing the fingerprint feature value, extracted by the E-bank terminal Ukey, of a user with the fingerprint feature value, matched with the E-bank terminal Ukey and stored in the database, of the user in real time so that whether the user is an authorized user or not can be judged. By the adoption of the E-bank safety certification method based on living fingerprint verification, whether the user of the E-bank is a specific user of a corresponding account can be accurately determined, and operation safety of the E-bank and the security of the fund of the user are guaranteed.
Owner:中山市品匠电子科技有限公司
Security payment system based on wearable device and payment method
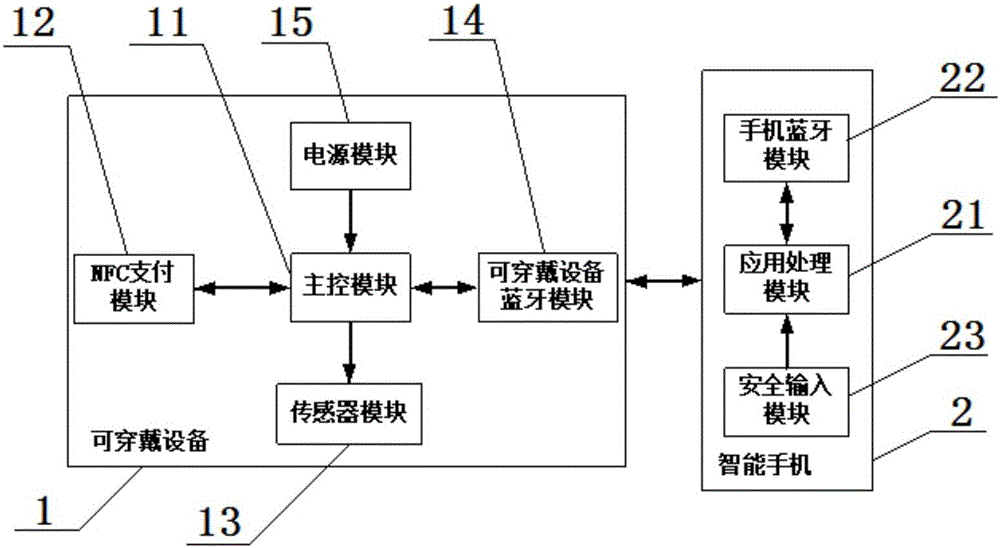
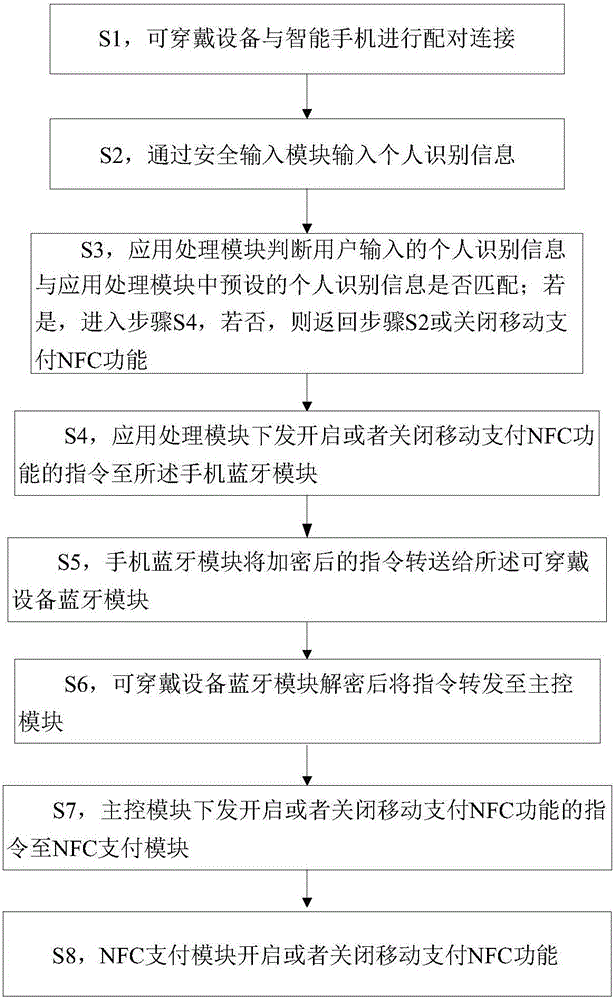
InactiveCN105956849AIncreased personal identity verification processEnsure transaction securityWireless commuication servicesShort range communication servicePersonal identity verificationMobile payment
The invention discloses a security payment system based on a wearable device and relates to the field of wearable equipment and mobile payment. The security payment system comprises a wearable device and a smart phone. The wearable device comprises a master control module, a NFC payment module, a sensor module, a wearable device Bluetooth module, and a power module. The smart phone comprises an application processing module, a phone Bluetooth module, and a safety input module. A user may flexibly activate or inactivate the mobile payment NFC function of the wearable device, may add a personal ID authentication process to guarantee transaction safety. The process that the user activates or inactivates the mobile payment NFC function of the wearable device is transferred via a Bluetooth protocol and an encryption mechanism strategy is used in Bluetooth transmission in order to guarantee that a user-set process is safe, reliable, and unduplicable. The invention discloses a payment method of the security payment system based on the wearable device.
Owner:WUHAN TIANYU JULIAN TECH CO LTD
Mobile information safety equipment and working method thereof
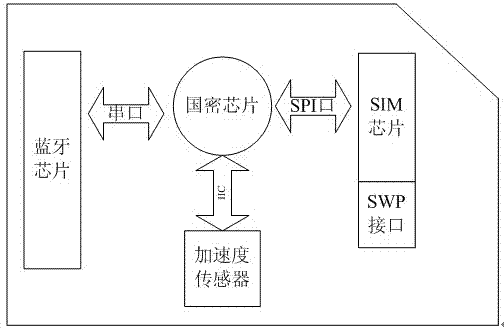
The invention discloses mobile information safety equipment. The equipment is arranged in an SIM (subscriber identity module) card of a mobile terminal and comprises a Bluetooth chip, a state secret chip and an acceleration sensor, wherein the Bluetooth chip is in data communication with a Bluetooth part in the mobile terminal; a Bluetooth communication channel of the equipment is provided; the state secret chip is in data communication with the mobile terminal through the Bluetooth communication channel; the acceleration sensor is used for controlling starting, stopping and operation confirmation of the state secret chip; the state secret chip is in data communication with an SIM chip through an interface and is communicated with an NFC (near field communication) module of the mobile terminal through an SWP (single wire protocol) interface; and an NFC communication channel of the equipment is provided. The invention also discloses a working method of the mobile information safety equipment. The mobile information safety equipment is mainly used for the field of mobile payment, is not required to be externally connected with equipment during payment, is safe and reliable and is convenient to use.
Owner:SHANDONG ZHONGFU INFORMATION IND
Multi-modal USB key authentication method based on face recognition technology
InactiveCN104102868AGuaranteed validityImprove the performance of the comparisonUser identity/authority verificationDigital data authenticationPattern recognitionComputer module
The invention provides a multi-modal USB (Universal Serial Bus) key authentication method based on a face recognition technology. According to the method, a web bank terminal USB key and a web bank background identity authentication database are used; a face collection and recognition module, a body temperature sensor, a pulse sensor, a heart rate sensor and an information feature value extracting module are arranged in the web bank terminal USB key; and a face information feature value comparison and processing module is arranged in the web bank background identity authentication database and is used for carrying out real-time comparison on a face feature value, extracted by the web bank terminal USB key, of a user and a face feature value, matched with the web bank terminal USB key and stored in the database, of the user, so that whether the user is a permission user or not is judged. The authentication method has the advantages that whether a web bank user is a specified user of a corresponding account or not can be accurately determined, and the operation safety of the web bank and the fund security of the user can be guaranteed.
Owner:中山市品匠电子科技有限公司
Safe internet bank implementation method
InactiveCN103117854AEnsure transaction securityEnsure safetyUser identity/authority verificationPayment protocolsInternet privacyPassword
The invention provides a double dynamic password implementation method. Steps comprises that a user can preinstall a trade identifying code in a internet bank system before using the internet bank, wherein the trade identifying code is defined by the user; the user can login the internet bank system through the internet, the internet bank system sends a dynamic login password to the user after the internet bank receives a login requirement and the user inputs the received dynamic login password to the internet bank system though the internet; the internet bank system jumps out to prompt after the trade identifying password is inerrable, prompt content is the trade identifying code, wherein the trade identifying code is preinstalled by the user and the user click and confirm after the user check the trade identifying code inerrably; the internet bank system sends a dynamic trade password to the user after the internet bank system receives the information of confirming the trade identifying code; the user input the received dynamic trade password to the internet bank system through the internet and the user can login a internet bank transactional interface to trade successfully.
Owner:涂国坚
An information processing method and system based on two-dimensional codes
InactiveCN106022428AConducive to transaction securityAvoid Malicious ModificationsRecord carriers used with machinesMarketingInformation processingComputer terminal
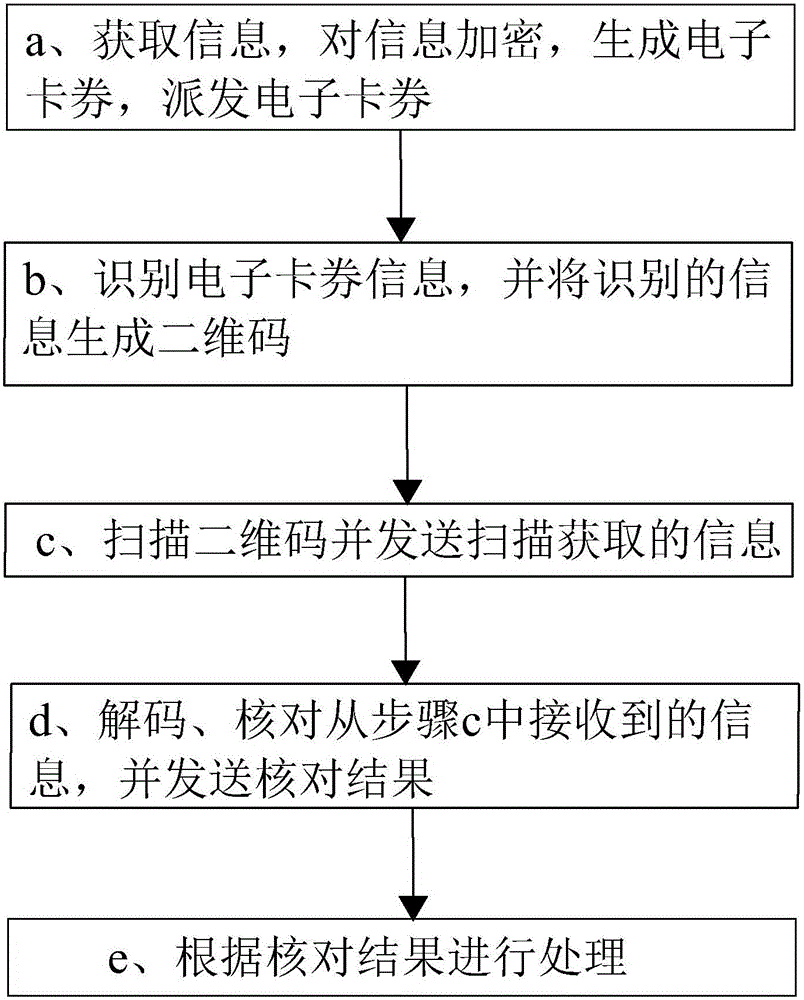
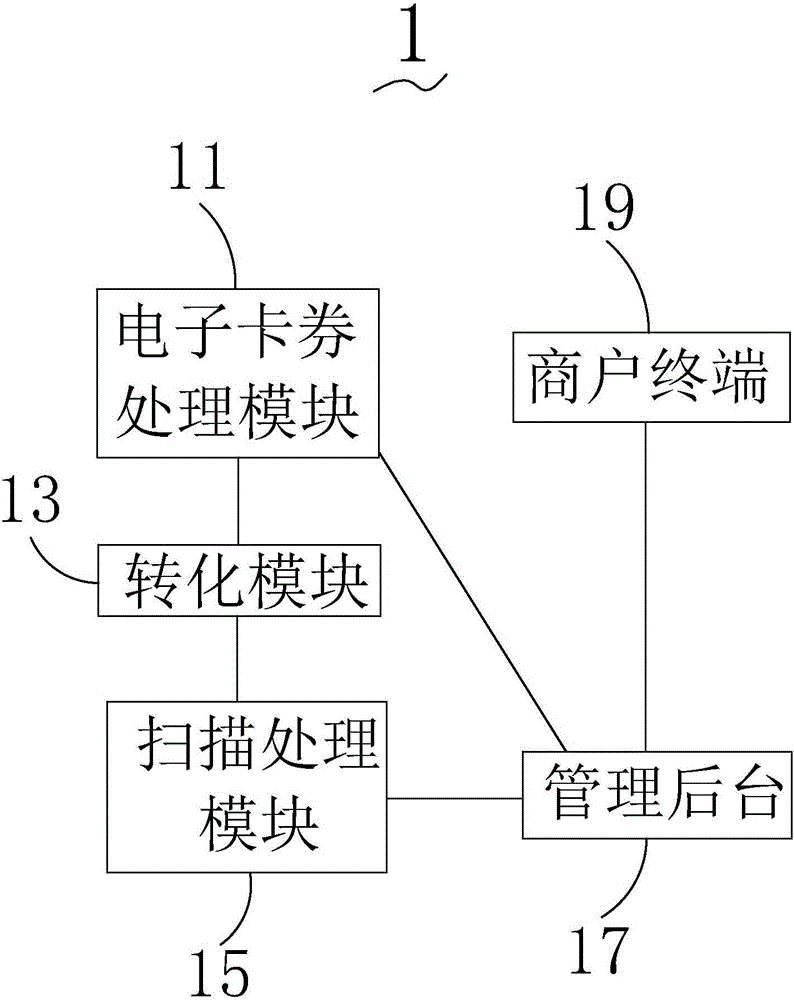
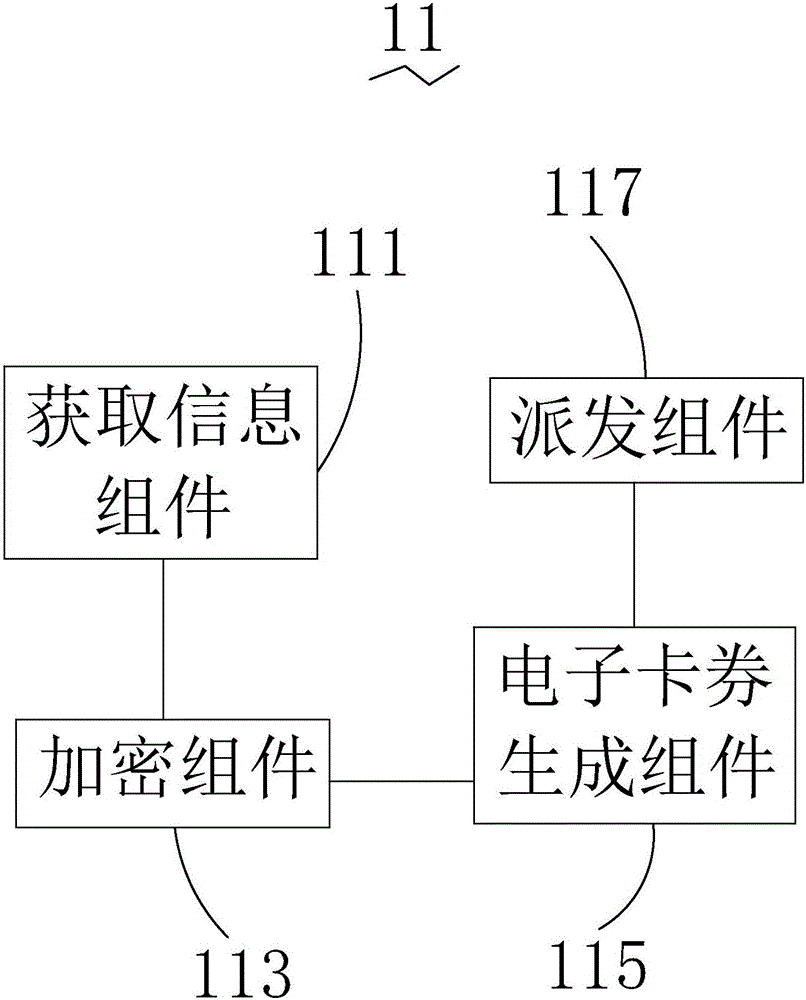
The invention provides an information processing method and system based on a two-dimensional code. The two-dimensional code-based information processing method includes: a. acquiring information, encrypting information, generating electronic coupons, and distributing electronic coupons; b. identifying electronic coupon information, and generating the identified information Two-dimensional code; c. Scanning the two-dimensional code and sending the scanned information; d. Decoding and checking the information received from step c, and sending the checking result; e. Processing according to the checking result. The two-dimensional code-based information processing system includes an electronic coupon processing module, a conversion module, a scanning processing module, a management background and a merchant terminal, which are sequentially connected, and the electronic coupon processing module is connected to the management background. The two-dimension code-based information processing method and system provided by the present invention have the advantages of facilitating the transaction security of merchants and consumers and facilitating the identification of coupon information.
Owner:YUNNEX TECH
Information interaction method and system and smart key equipment
ActiveCN104243162AImprove portabilityReduce volumeKey distribution for secure communicationUser identity/authority verificationTransaction dataComputer terminal
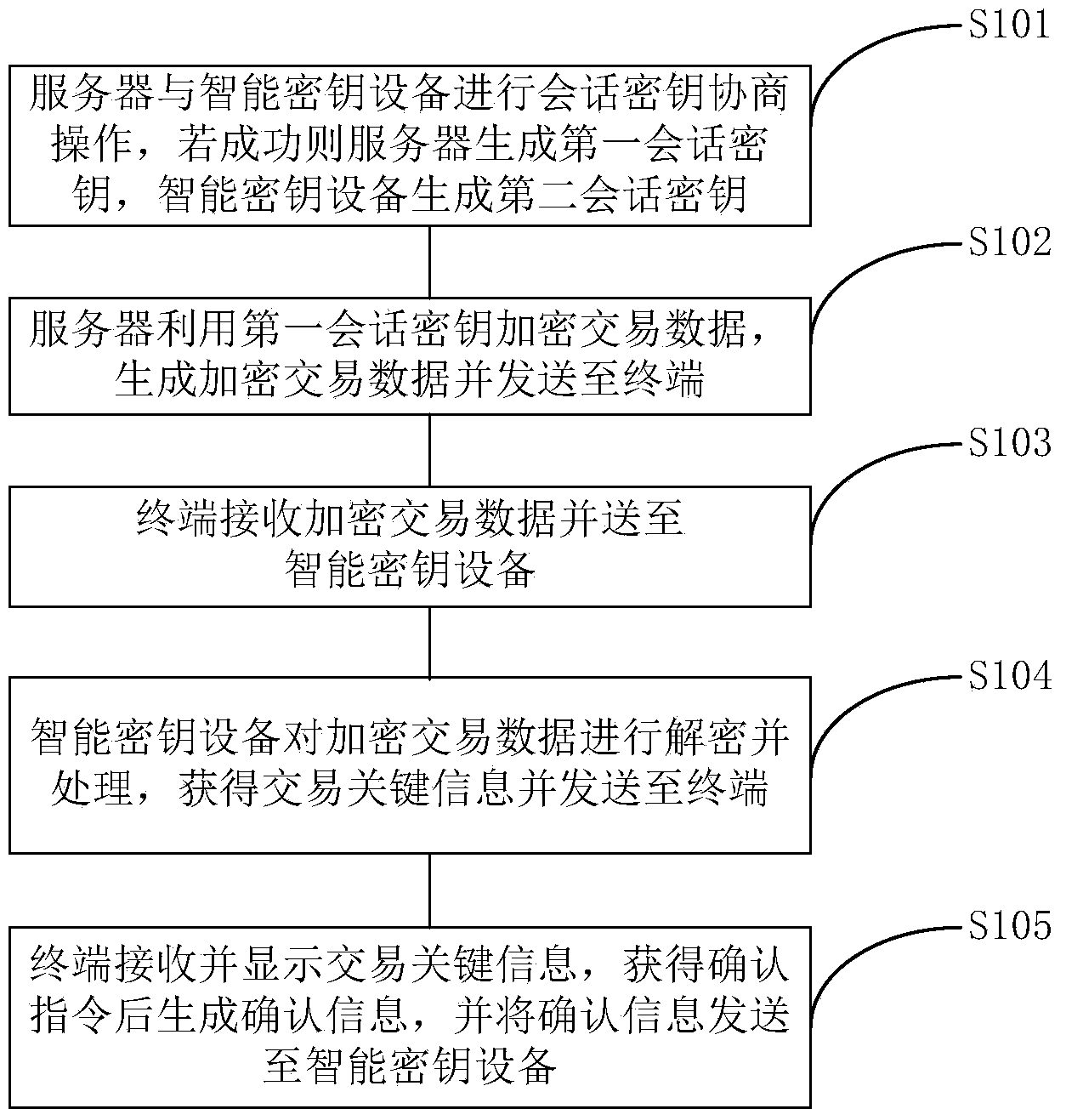
The invention provides an information interaction method and system and smart key equipment. The information interaction method comprises the steps that a server and the smart key equipment conduct session key negotiation operation, if the session key negotiation operation is successfully conducted, a first session key is generated by the server, a second session key is generated by the smart key equipment, and the first session key and the second session key are a key pair; the server uses the first session key to encrypt transaction data, generates the encrypted transaction data and sends the encrypted transaction data to a terminal; the terminal receives the encrypted transaction data and sends the encrypted transaction data to the smart key equipment; the smart key equipment receives the encrypted transaction data, uses the second session key for decrypting the encrypted transaction data, obtains the transaction data, processes the transaction data, obtains transaction key information and sends the transaction key information to the terminal; the terminal receives and displays the transaction key information, generates confirmation information after obtaining a confirmation instruction and sends the confirmation information to the smart key equipment.
Owner:TENDYRON CORP
Network payment system based on two-dimensional code
ActiveCN105894263AEasy to changeEnsure safetyPayment protocolsPoint-of-sale network systemsComputer hardwareFinancial transaction
The invention provides a network payment system based on a two-dimensional code, and the system comprises the two-dimensional code, code binding equipment, a management background, a consumer terminal, and a merchant terminal. The code binding equipment achieves the binding of the two-dimensional code and the merchant information, and the code binding equipment is connected with the management background. The management background is configured with a merchant ID for a merchant. The consumer terminal scans the bound two-dimensional code to carry out payment, and the merchant terminal displays the amount of successful transaction. The system does not need to change the two-dimensional code and does not damage the two-dimensional code when changing the money-receiving account information, and protects the safety of the fund of the merchant.
Owner:YUNNEX TECH
Payment method through a payment instrument and server and mobile terminal
InactiveCN103366273AImprove securityEnsure transaction securityProtocol authorisationTelecommunicationsComputer terminal
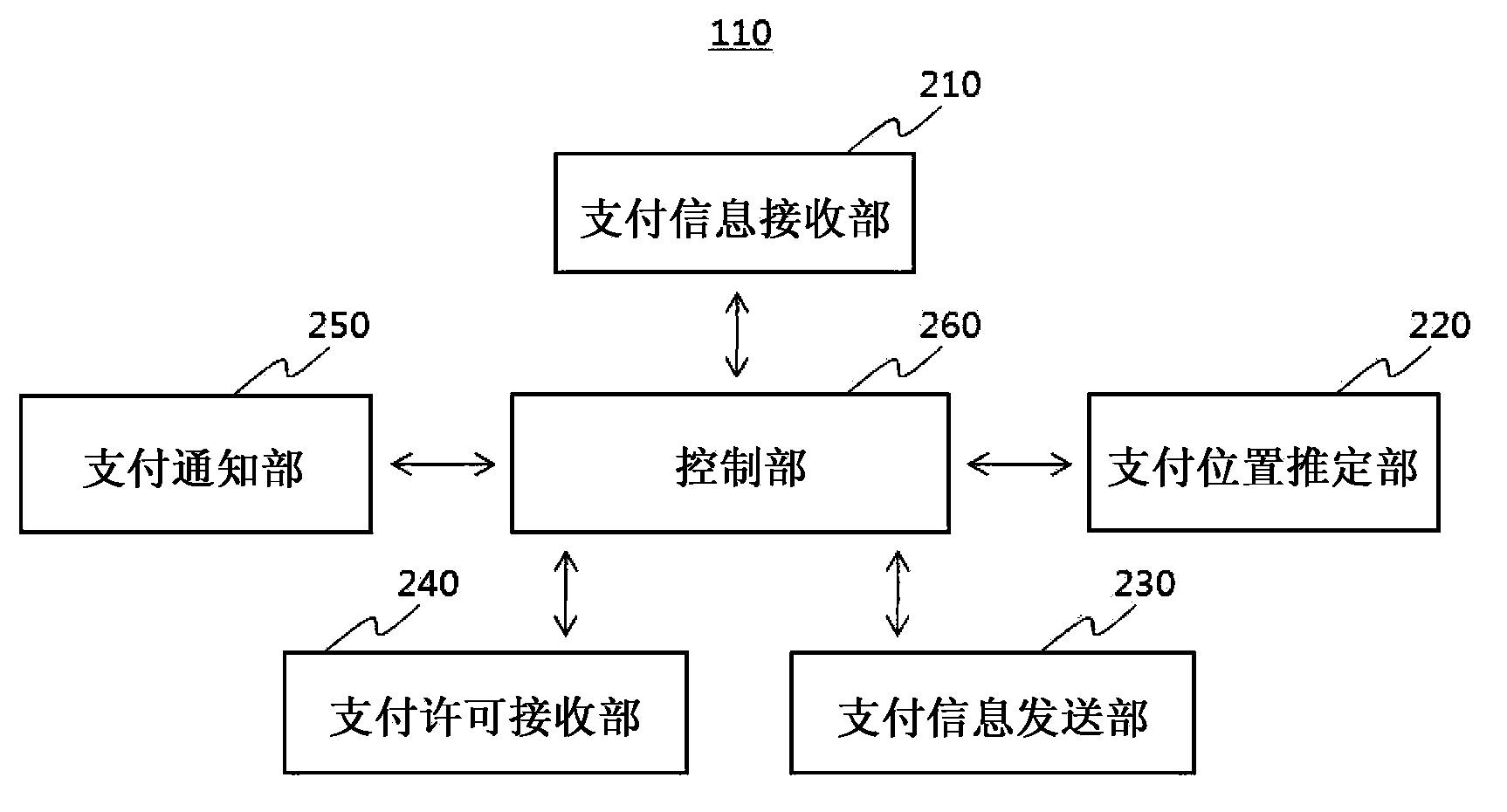
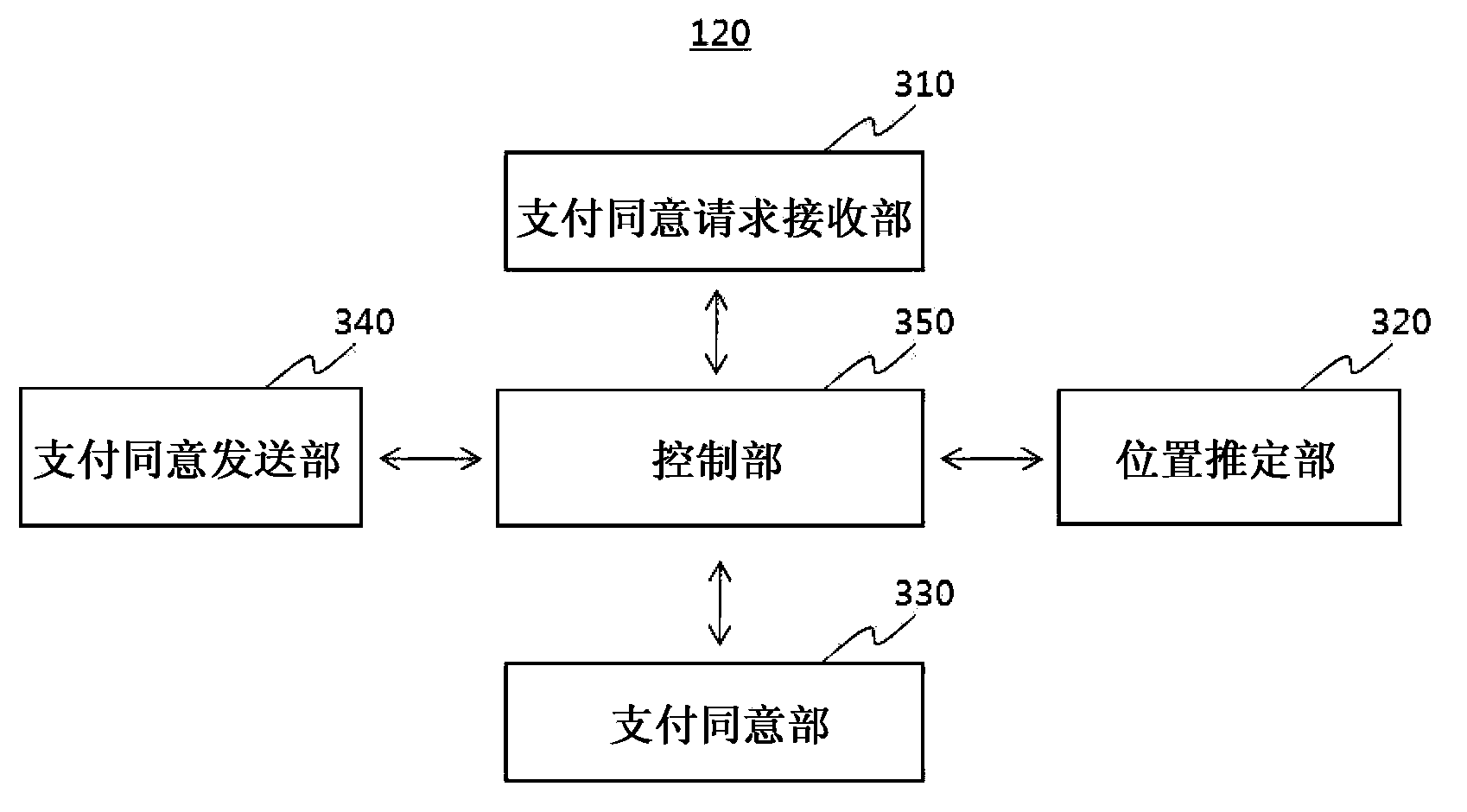
A payment method is performed through a payment server connectable to at least one mobile terminal and a payment terminal. The payment method includes: receiving payment information including a payment identification code and a payment location code from the payment terminal; estimating a payment location based on the payment location code; determining the at least one mobile terminal associated with the payment identification code; transmitting the estimated payment location to the at least one mobile terminal; and receiving a location-based approval or a payment rejection from a particular mobile terminal, the approval / rejection determined based on the estimated payment location and a location of a particular mobile terminal belonging to the at least one mobile terminal.
Owner:LG CNS
Information collection, transmission, processing system and method based on mobile phone short message
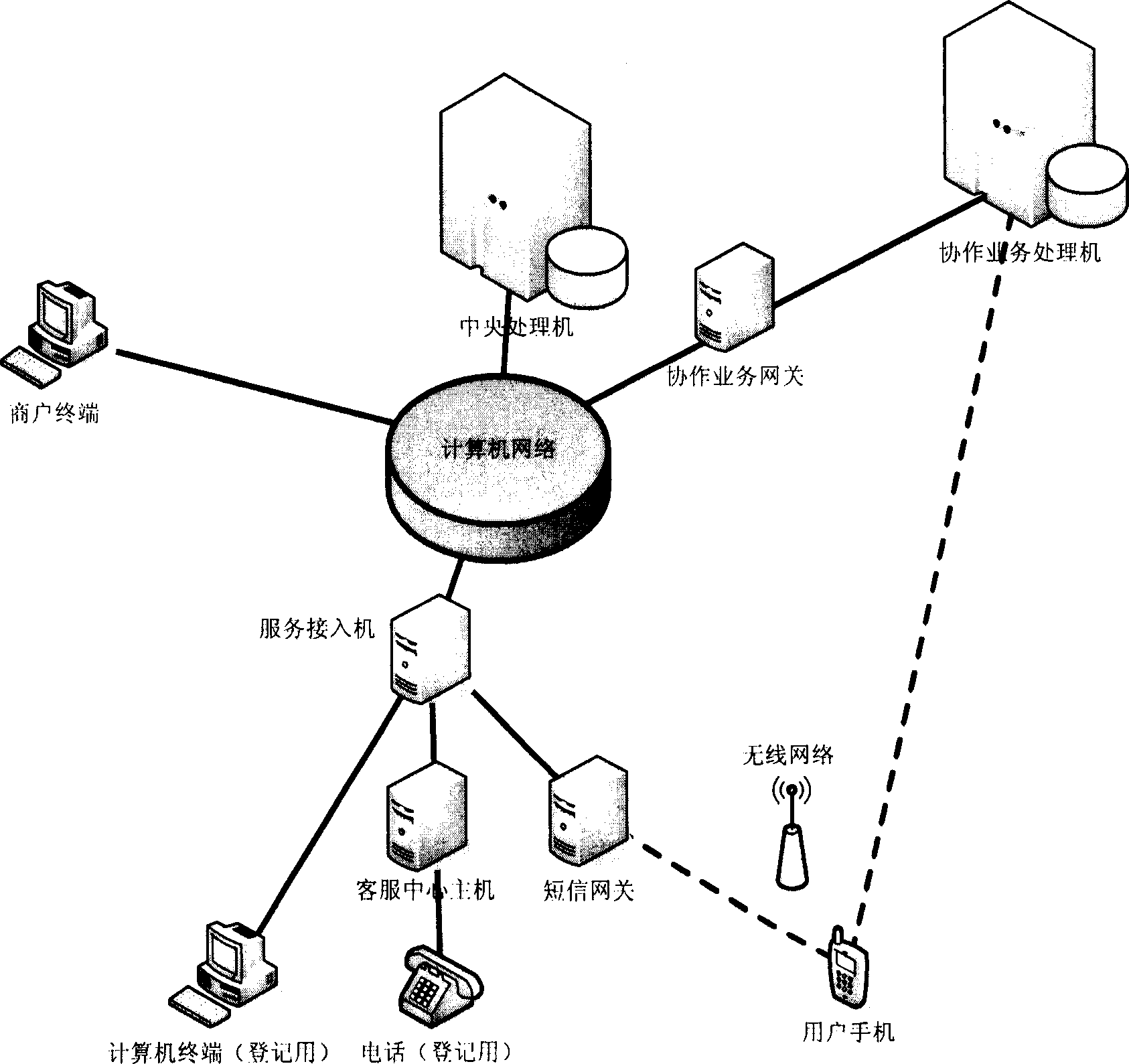
InactiveCN1794298ATrade anytimeReduce data volumeFinanceRadio/inductive link selection arrangementsHandling systemComputer science
This invention relates to a system and a method for information collection, transmission and process based on the short message of a cell phone to constitute a unified standard electronic trade system based on short messages of cell phones. Since this invented system and method transmits the bank account numbers and codes in the system by different routes and they cannot be interrupted on a same route at the same time, the bank account information of the user can be guaranteed safely.
Owner:BEIJING YIFUJINCHUAN TECH
Ordering processing method for mobile Internet online payment
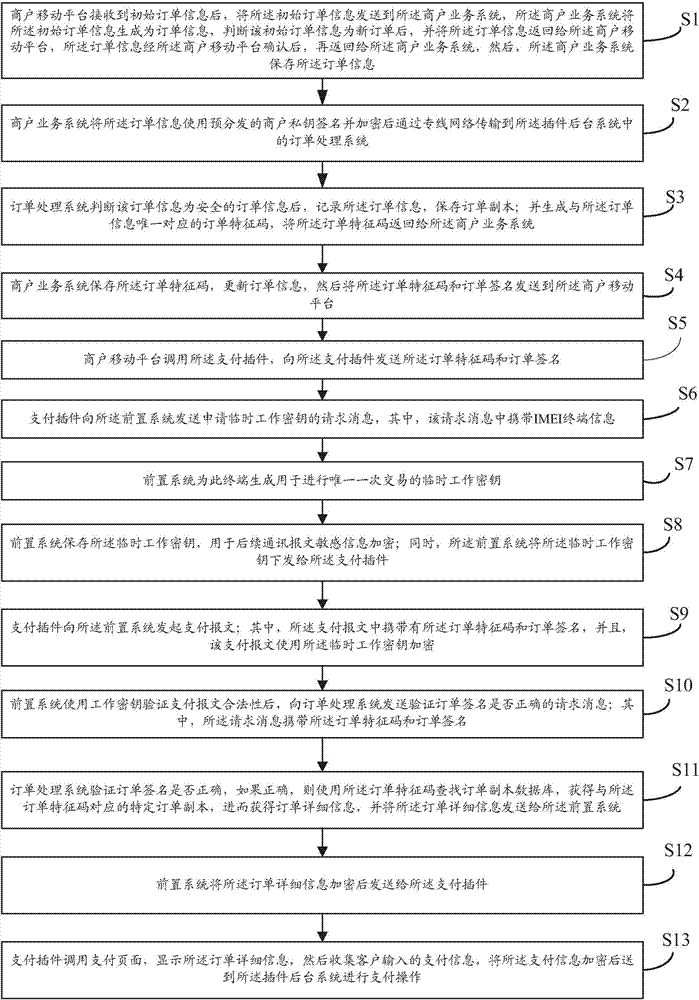
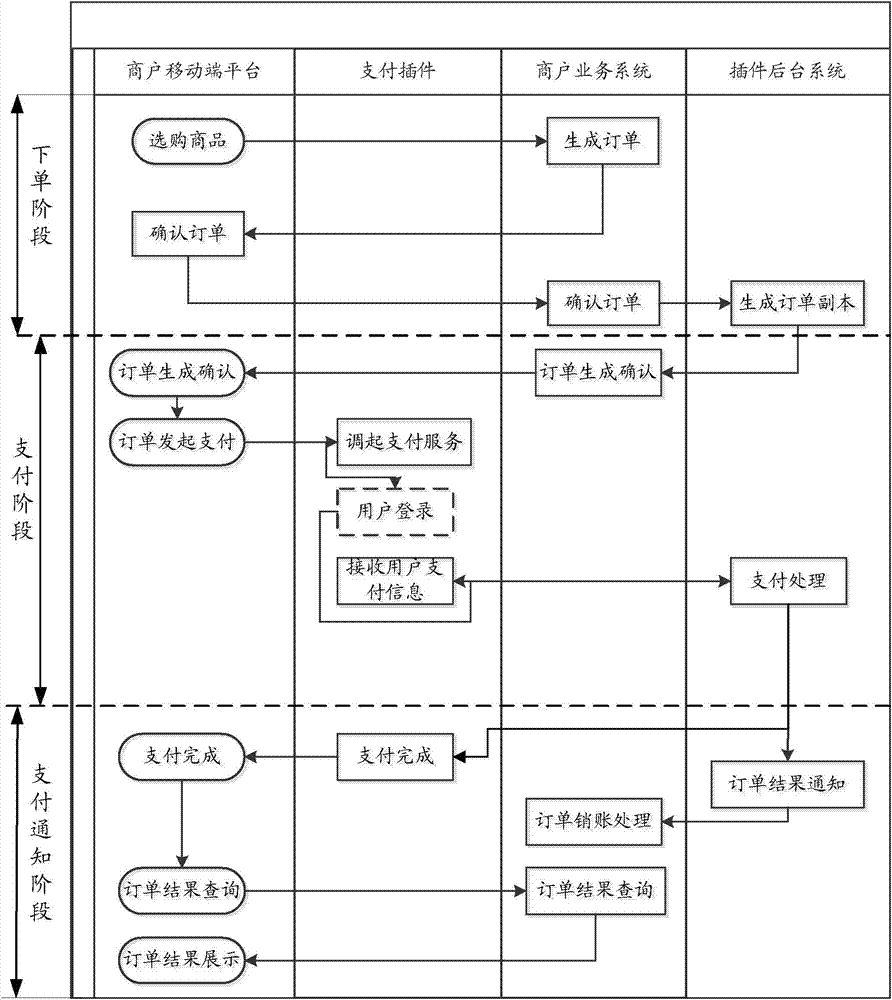
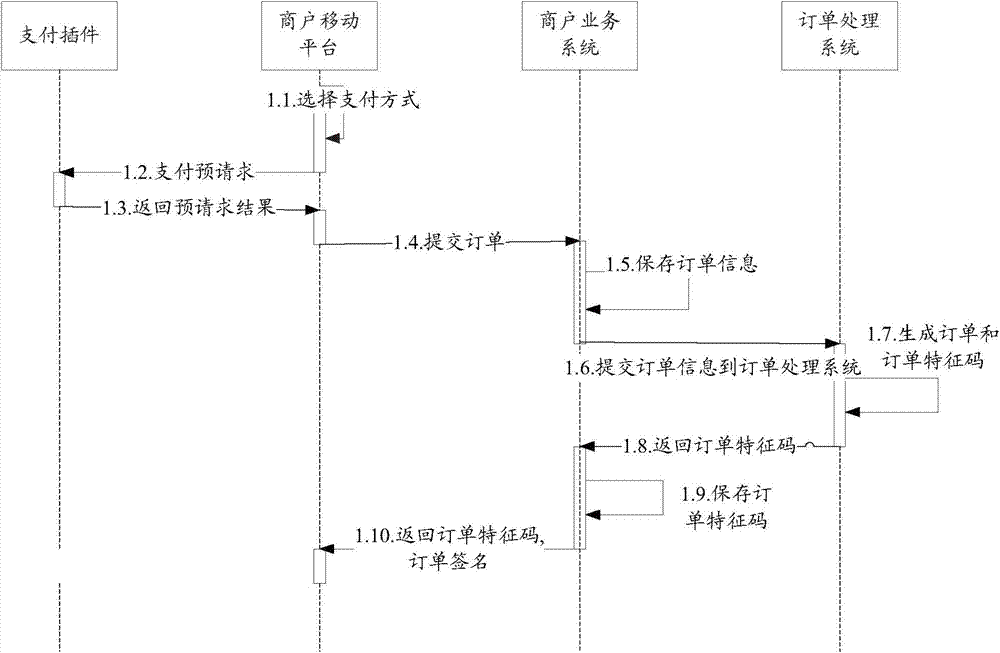
InactiveCN103761644AEnsure safetyEnsure transaction securityPayment architectureCommerceProcess systemsMerchant services
The invention provides an ordering processing method for mobile Internet online payment. According to the method, a payment plug-in is embedded in a merchant mobile platform; the merchant mobile platform is connected with a merchant service system, and the payment plug-in is connected with a plug-in background system. The merchant service system is a merchant background order processing system and is used for processing orders. The plug-in background system is an order processing system of a payment mechanism and comprises a payment front-end system, an order processing system body and a payment processing system. Order information needs to pass the merchant service system and then be transmitted to the order processing system of the background system, the order information can be transmitted back to the merchant service system after the order processing system generates order feature codes, and finally payment operation is carried out on a foreground by transmitting the order feature codes only. According to the ordering processing method, the order feature codes are used as confirmation factors, the possibilities of leakage of the order information and order phishing can be avoided, and safety of the order information can be guaranteed.
Owner:北京中科金财信息科技有限公司
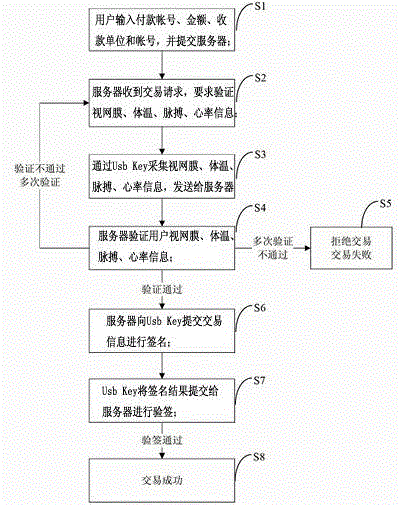
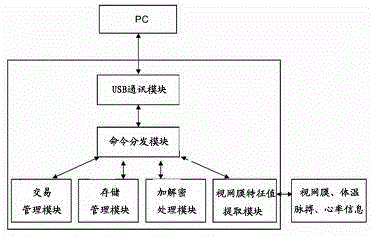
Multi-modal electronic bank payment settlement authentication method using retina verification
InactiveCN104102867AMonitor real-time body temperatureEnsure transaction securityUser identity/authority verificationDigital data authenticationPaymentComputer terminal
The invention relates to a multi-modal electronic bank payment settlement authentication method using retina verification. The method comprises the following steps that: an electronic bank terminal Ukey and an electronic bank background identity authentication database are adopted; a retina collection and recognition module, a body temperature sensor, a pulse sensor, a heart rate sensor and an information feature value extracting module are arranged in the electronic bank terminal Ukey; and a retina information feature value comparison and processing module is arranged in the electronic bank background identity authentication database and is used for carrying out real-time comparison on the retina feature value, extracted by the electronic bank terminal Ukey, of of an user and the retina feature value, matched with the electronic bank terminal Ukey and stored in the database, of the user, so that whether the user is a permission user or not is judged. The authentication method can be used for accurately determining whether the user of an electronic bank is a specified user of a corresponding account, so that the operation security of the electronic bank and the fund security of the user can be guaranteed.
Owner:ZHONGSHAN YIZHAN DECORATION ENGINEERING CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com