Patents
Literature
62results about How to "Avoid Malicious Modifications" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
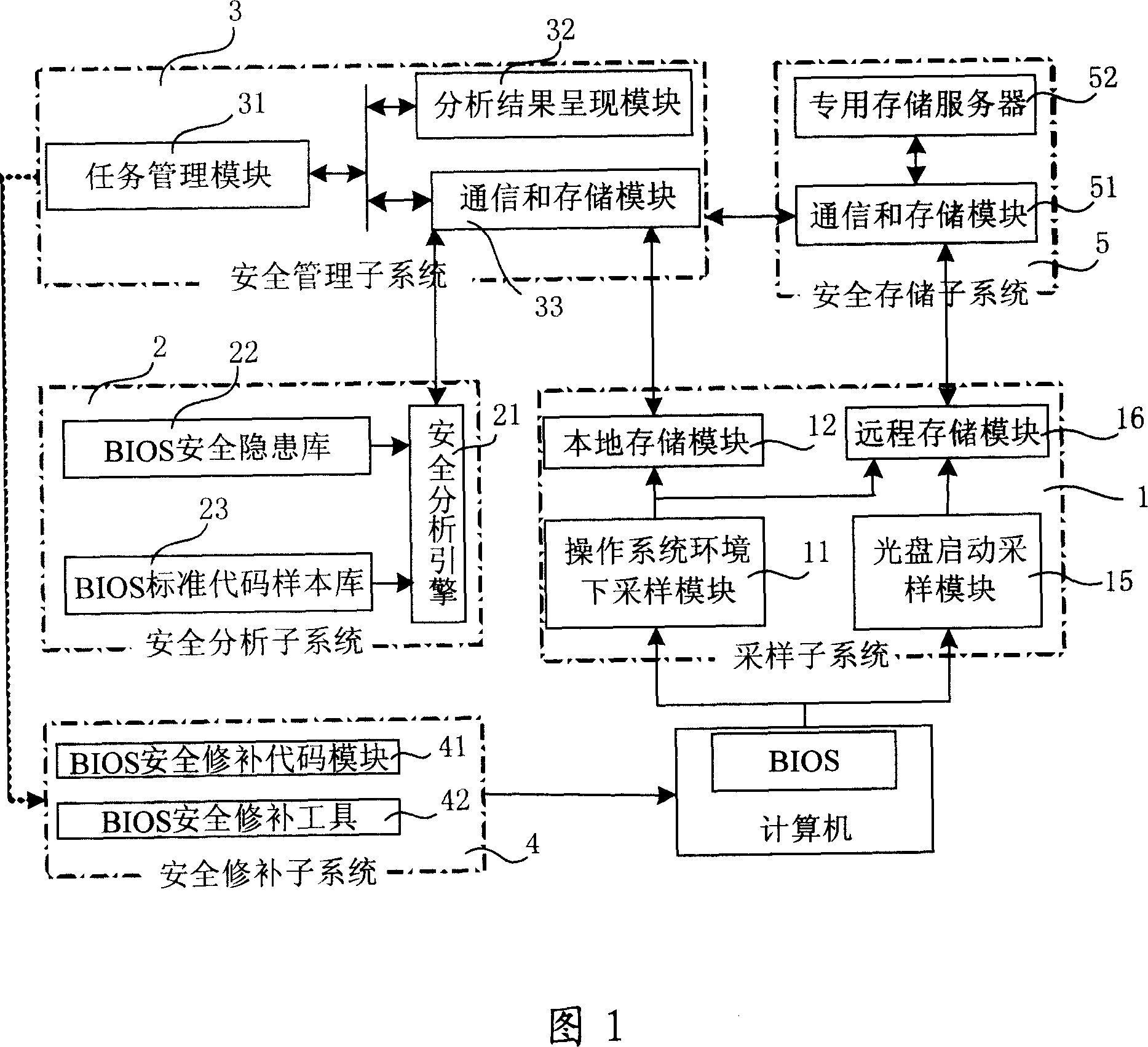
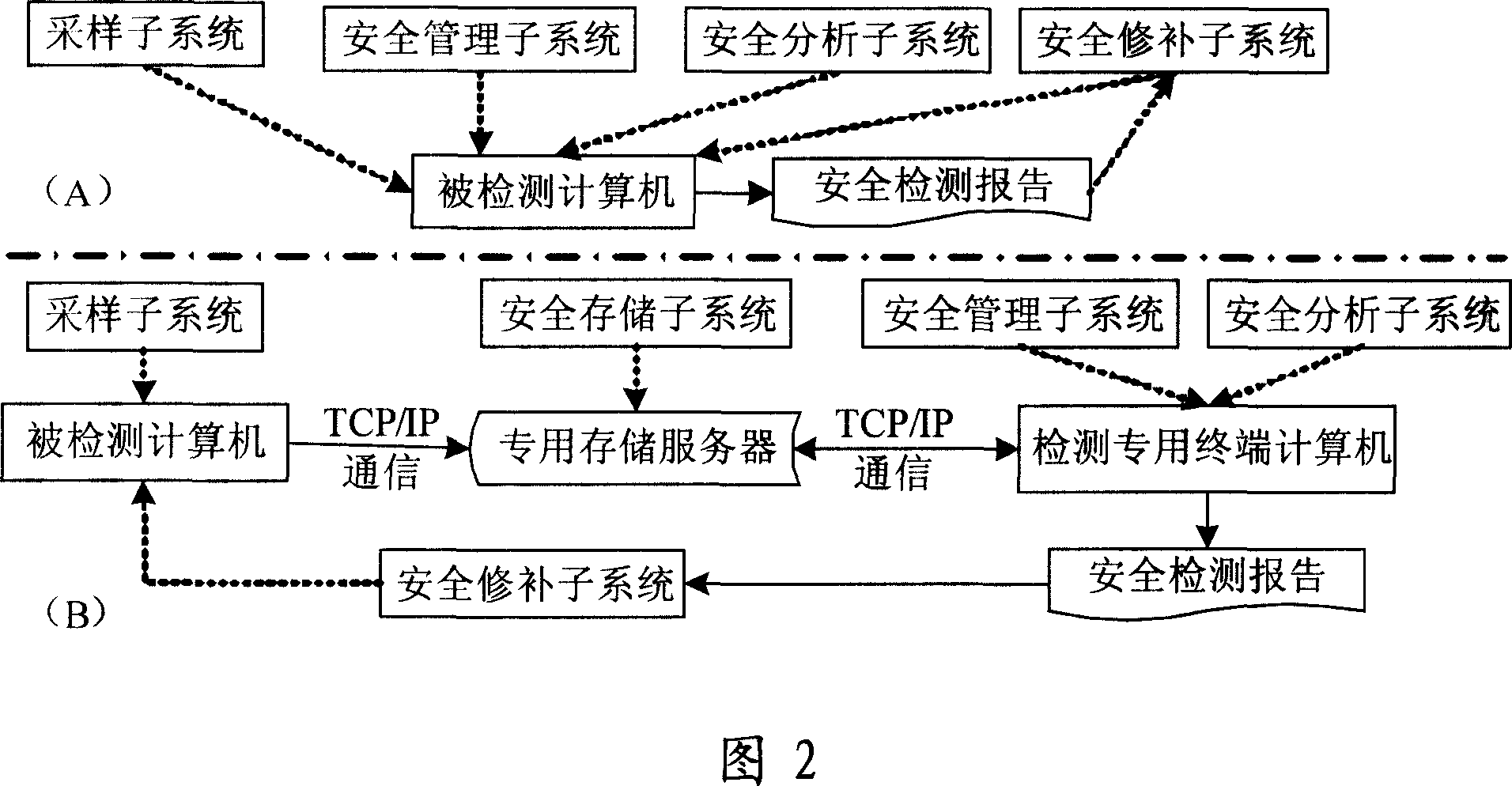
System and method for carrying out safety risk check to computer BIOS firmware
InactiveCN101079003AAvoid lossPrevent crashSoftware testing/debuggingRedundant operation error correctionEngineeringBIOS
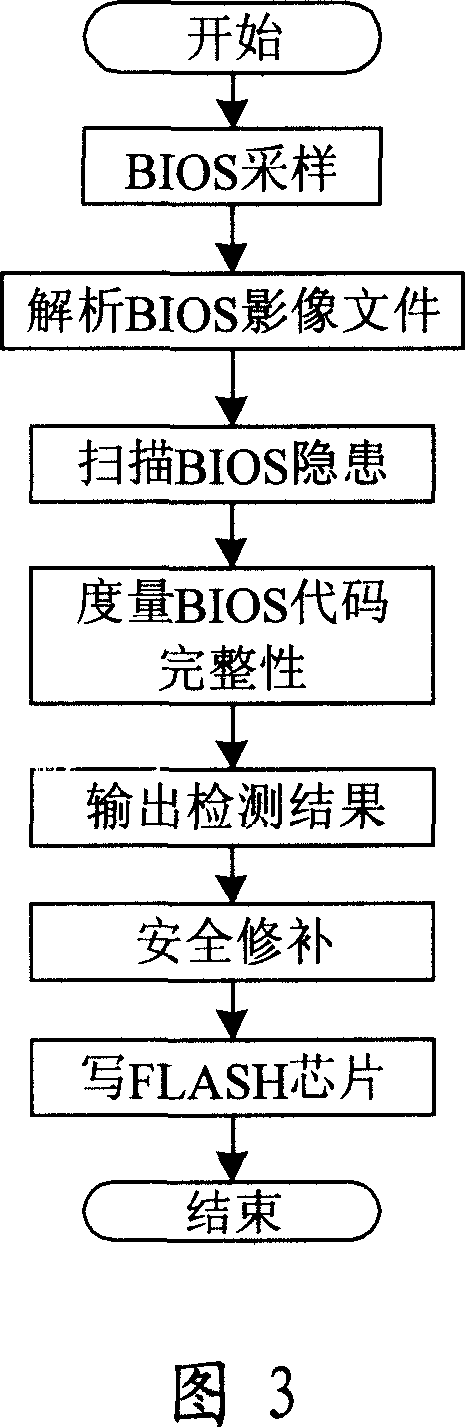
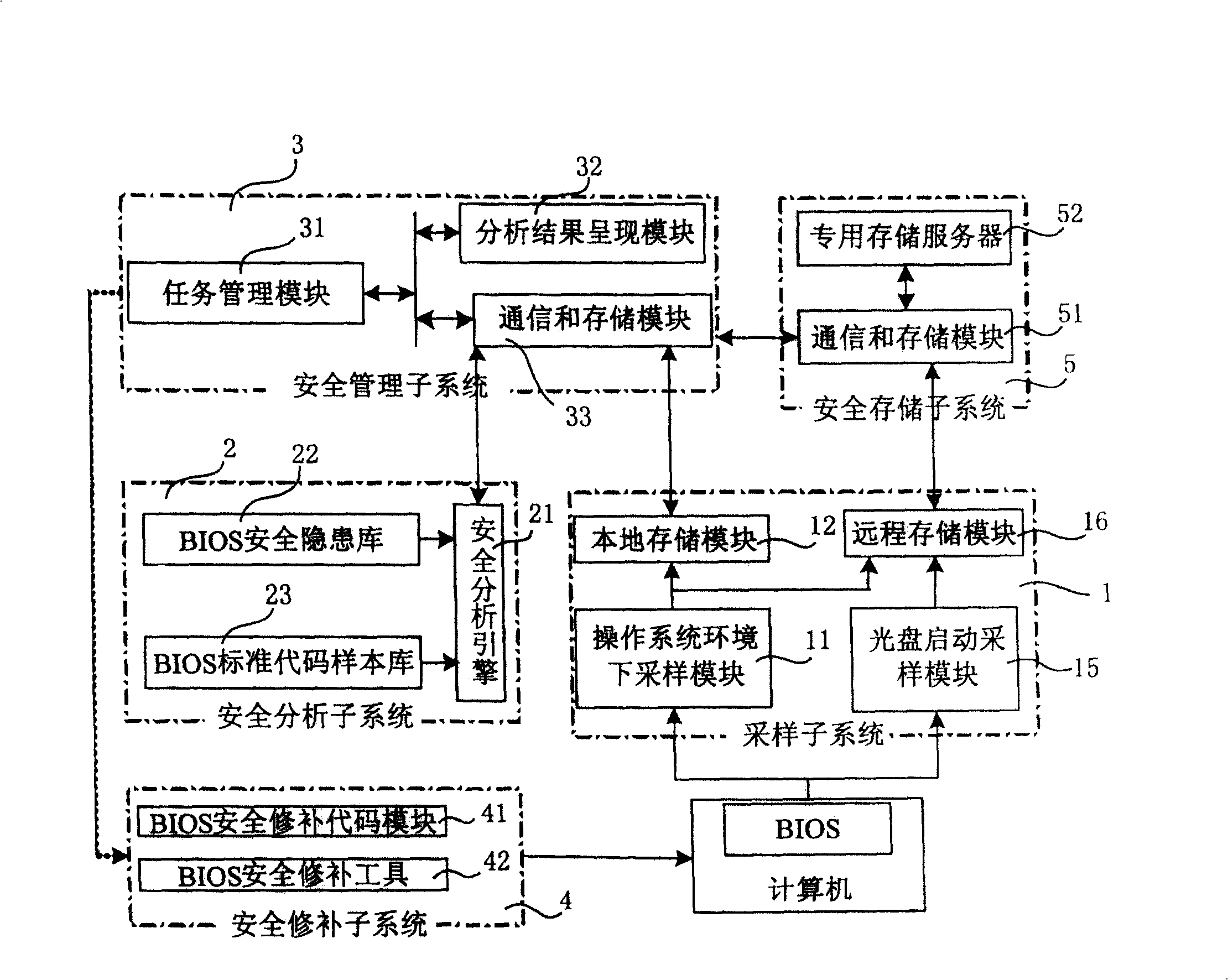
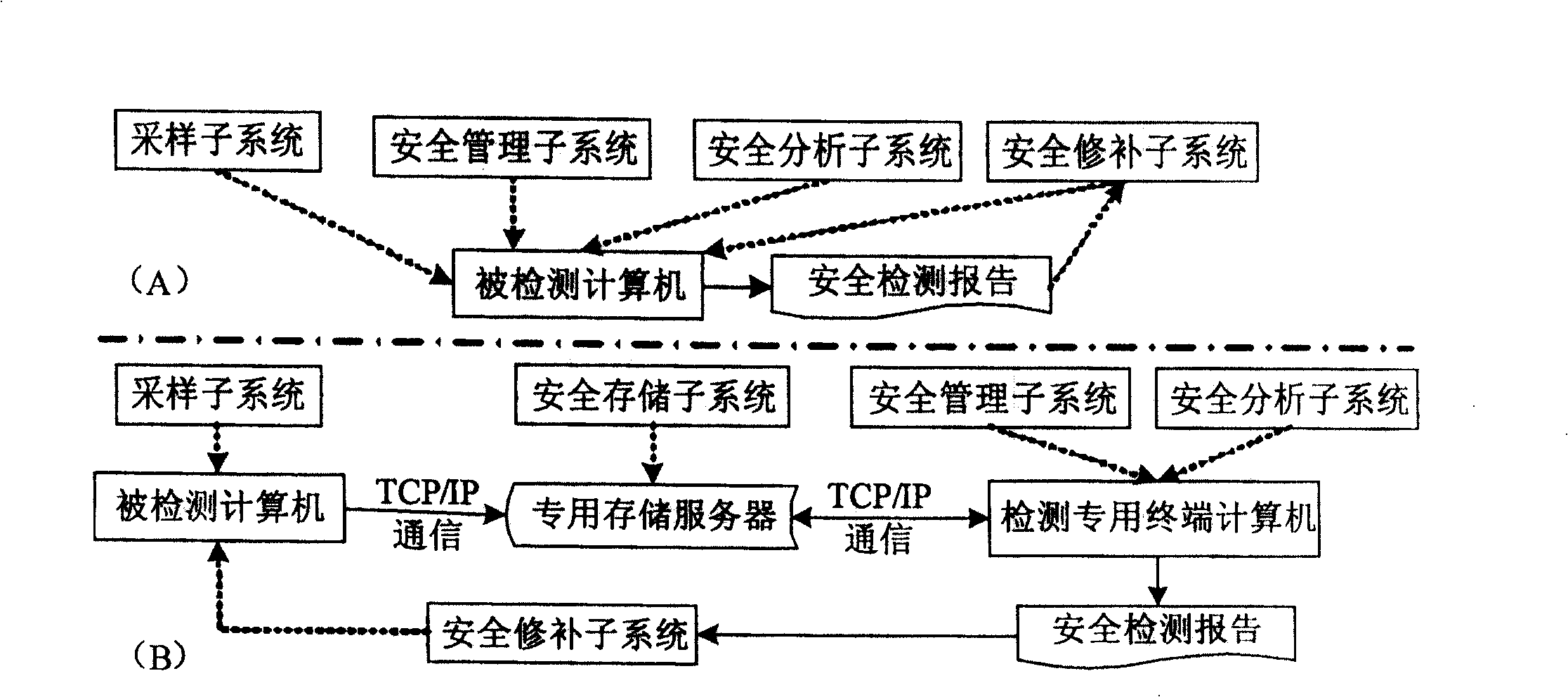
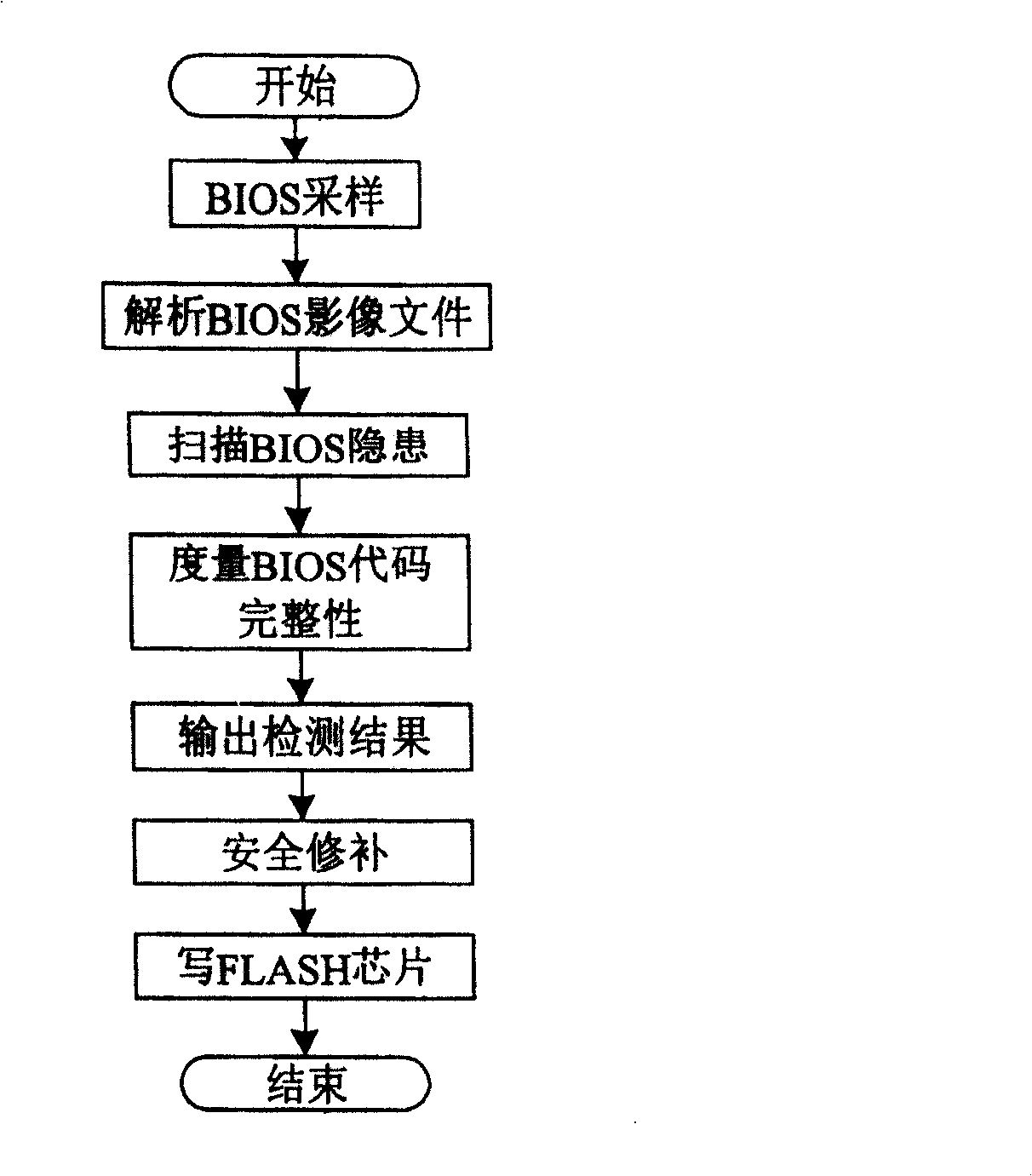
The invention discloses a system proceed safe test for computer BIOS firmware and method, which comprises the following steps: initializing; proceeding BIOS sampling; analyzing BIOS image file; scanning various hidden dangers of BIOS; measuring completeness integrity of BIOS code; outputting the testing effect; proceeding safe repair for BIOS. This invention can decrease, reduce and remove safety loophole and hidden danger of computer BIOS, which provides reliable terminal safety prevention and overall protection for computer and network.
Owner:BEIJING JINYUAN LONGMAI INFORMATION TECH
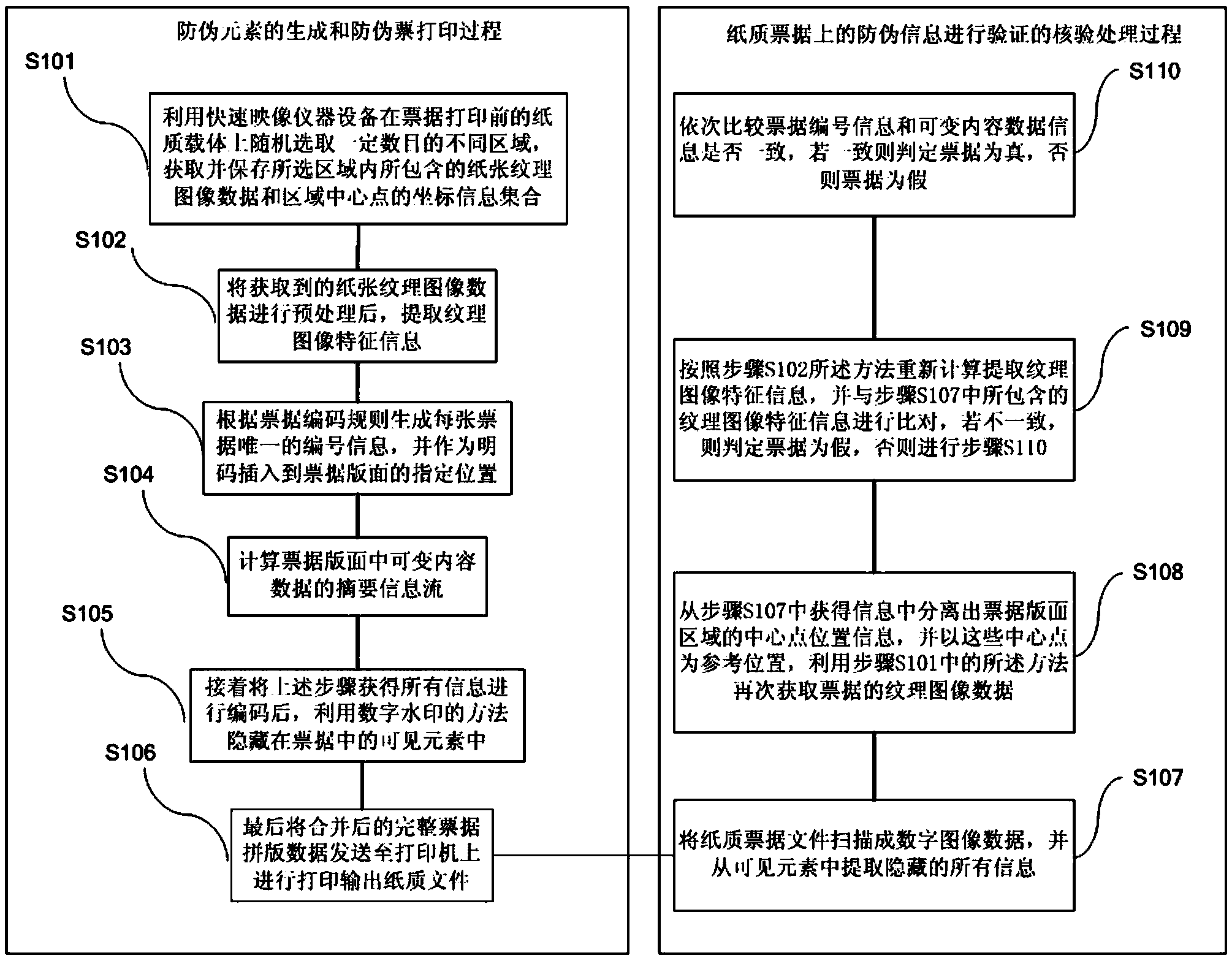
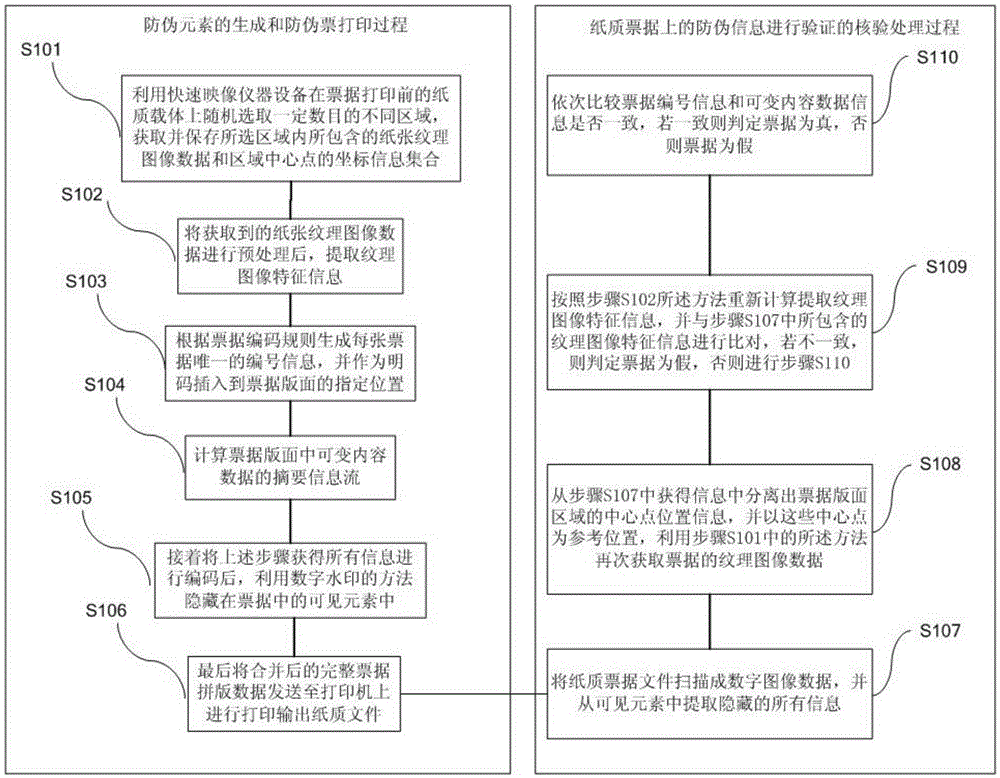
Bill anti-counterfeit method and device based on texture image characteristics
ActiveCN103761799AGreat practicabilityImage acquisition is simpleCharacter and pattern recognitionData informationComputer graphics (images)
The invention relates to a bill anti-counterfeit method and device based on texture image characteristics. The method comprises the steps of firstly utilizing a rapid image device for selecting a certain number of areas from a paper carrier before a bill is printed, obtaining paper texture image data and area central point position information, extracting texture image characteristic information, generating bill number information, calculating an abstract information flow of variable content data, encoding all the obtained information, hiding the information in visible elements of the bills, and finally printing and outputting the complete bill makeup data. In the verification process, a paper bill file is scanned to digital image data, all hidden information is extracted, and then whether the texture image characteristic information, the bill number information and the variable content data information are consistent or not is obtained in a comparing mode so as to judge bill authenticity. The anti-counterfeit technology meets the requirements of technical exclusivity, technical reliability, identification simplicity, identification uniqueness, anti-counterfeit timeliness and the like.
Owner:李晓妮
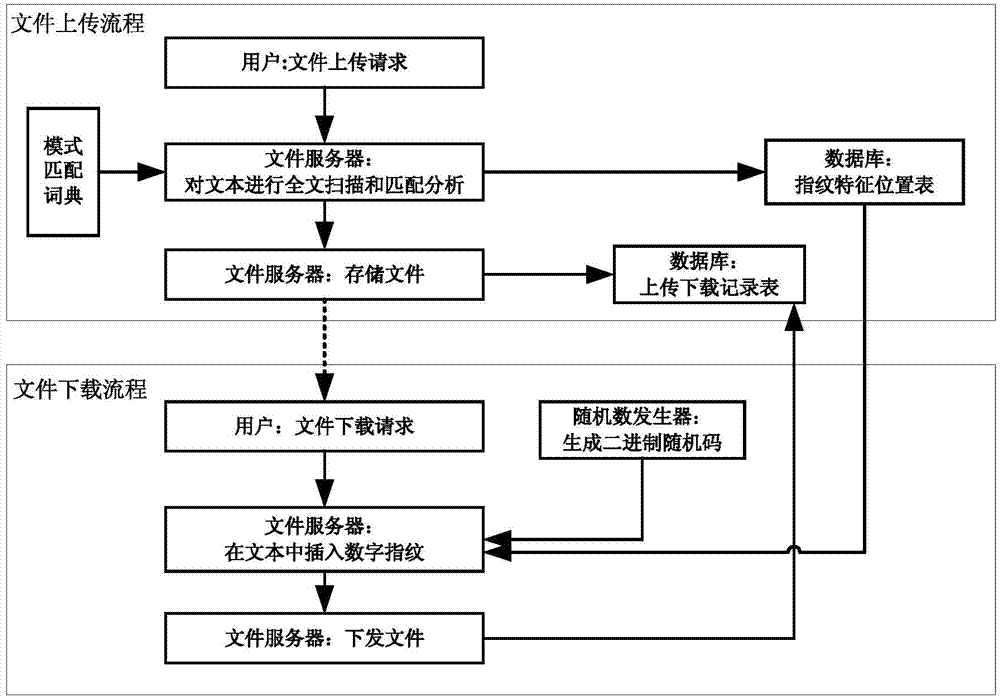
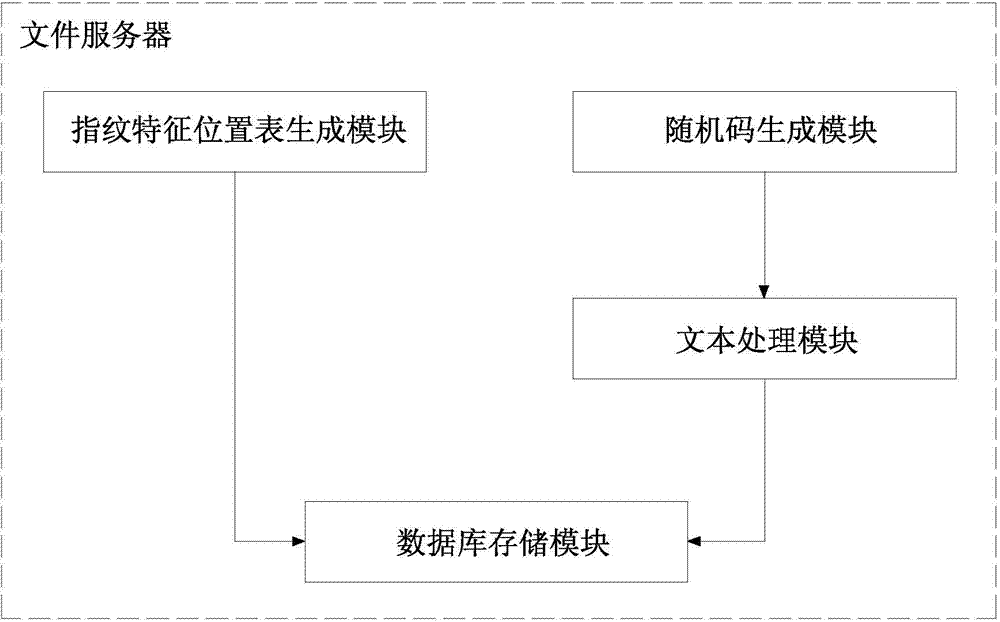
File security control and trace method and system based on digital fingerprints
InactiveCN104715168AImprove robustnessAvoid Malicious ModificationsProgram/content distribution protectionNatural language analysisFile server
The invention discloses a file security control and trace method and system based on digital fingerprints. The method includes the file uploading procedure and the file downloading procedure. In the file uploading procedure, when a user uploads files to a file server, the file server starts a natural language analysis program and conducts full-context scanning and matched analysis on file contexts, a position where the digital fingerprints can be inserted is found, a fingerprint feature position list is generated, the fingerprint feature position list and original files are stored in the file server together, the uploading and downloading record list is generated, and information uploaded this time is recorded. In the file downloading procedure, when the user sends a file downloading request to the file server, the file server generates binary random codes with the same length according to the length of the fingerprint feature position list, when the random code corresponding position is 1, the digital fingerprints are inserted in the contexts at the corresponding position, a new file is generated and sent to the user, and meanwhile the downloaded information is recorded in the uploading and downloading record list. By means of the method and system, the context files can be traced back, and the security of the context files is managed.
Owner:陈佳阳 +1
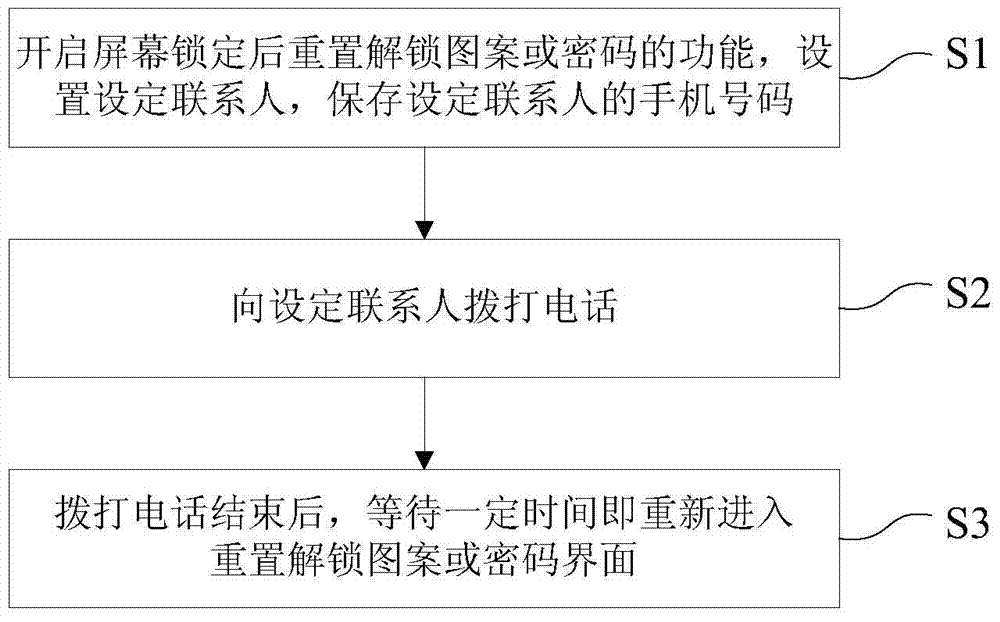
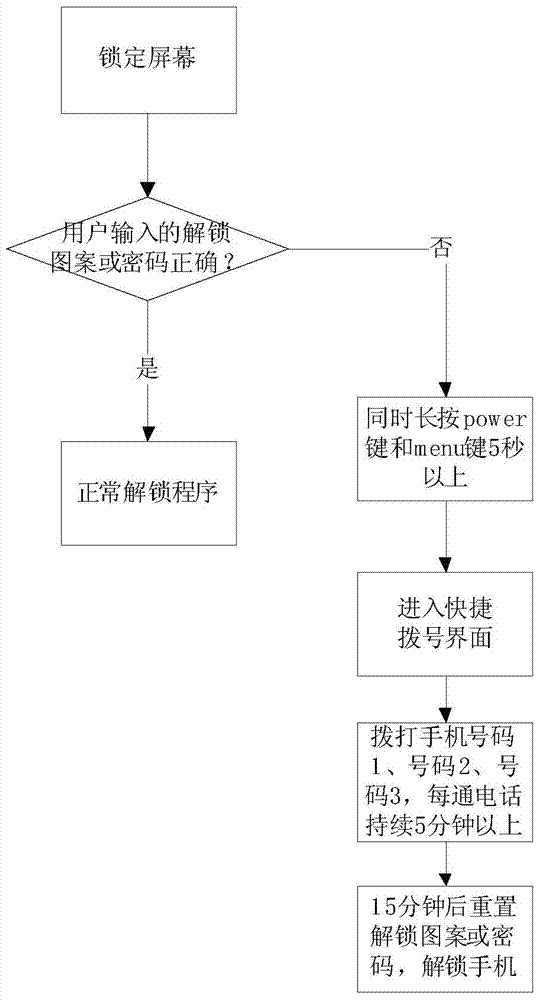
Set contact calling based method for unlocking mobile phone
InactiveCN103533180APrevent accidental lossAvoid Malicious ModificationsTelephone sets with user guidance/featuresIndividual dataConfidentiality
The invention provides a set contact calling based method for unlocking a mobile phone. The method at least comprises the steps as follows: a function of resetting of unlocking patterns or passwords after screen locking is enabled in system settings of the mobile phone, set contacts are set, and mobile phone numbers of the set contacts are saved; a call is made to each set contact; and after the calls are finished, a user can enter an unlocking pattern or password resetting interface again after the user waits for a certain time, and the user can finish unlocking pattern or password resetting and screen unlocking. According to the three set contact calling based method for resetting the passwords, the mobile phone can be unlocked on the premise that phone resetting is not required, so that personal data of the user can not be damaged, the confidentiality is high, and other persons are prevented from resetting the unlocking patterns or the passwords maliciously.
Owner:PHICOMM (SHANGHAI) CO LTD
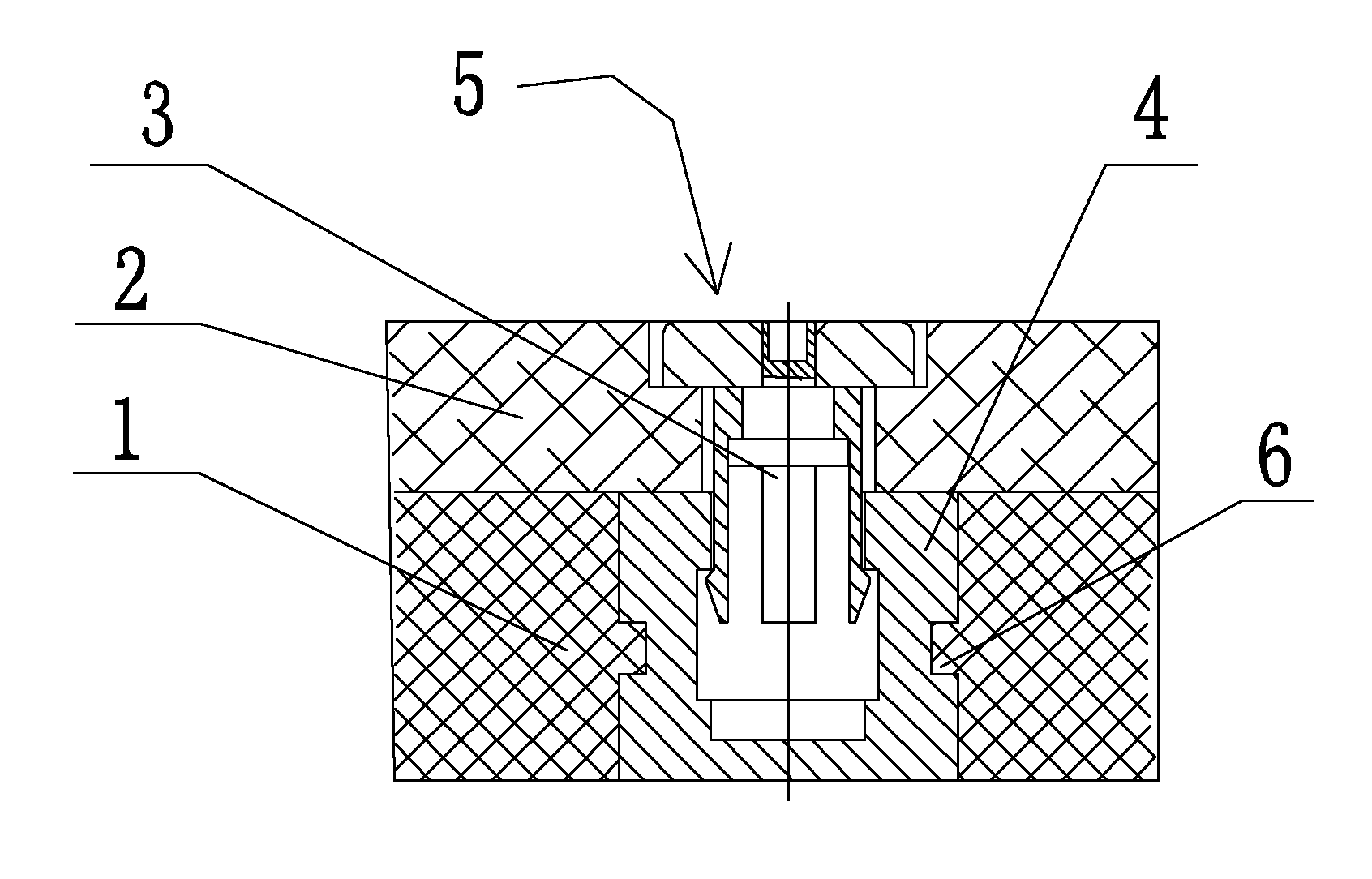
Electric energy meter single enclosure structure
InactiveCN102116780AAvoid Malicious ModificationsTimely replacementTime integral measurementElectricityCurrent electric
An electric energy meter single enclosure structure designed according to the invention solves the technical problems of complex operation and low efficiency in the current electric energy meter enclosure. The structure comprises an electric energy meter shell and a flip cover, wherein the flip cover is engaged with the upper part of the shell in a covering manner and is provided with a through hole thereon, a metal piece with a slot is embedded on a surface where the shell is corresponding to the through hole, the upper part of the slot is a reverse step structure with narrow outside and wide inside, a bolt with a buckle on the tail thereof penetrates through the through hole to be in clamping connection with the metal piece, and the buckle is buckled on the step surface of the slot, and the head of the bolt adopts a step-shaped structure and the step surface thereof abuts against a working surface of the flip cover. The electric energy meter single enclosure structure can prevent the electric energy meter from being modified viciously during the use of the electric energy meter, and the bolt clamping connection structure is not exposed so as not to be restored after being destroyed, the sign representing that the electric energy meter is destroyed can be easily found, the destroyed electric energy meter can be replaced in time, and the anti-electricity theft effect is excellent.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +1
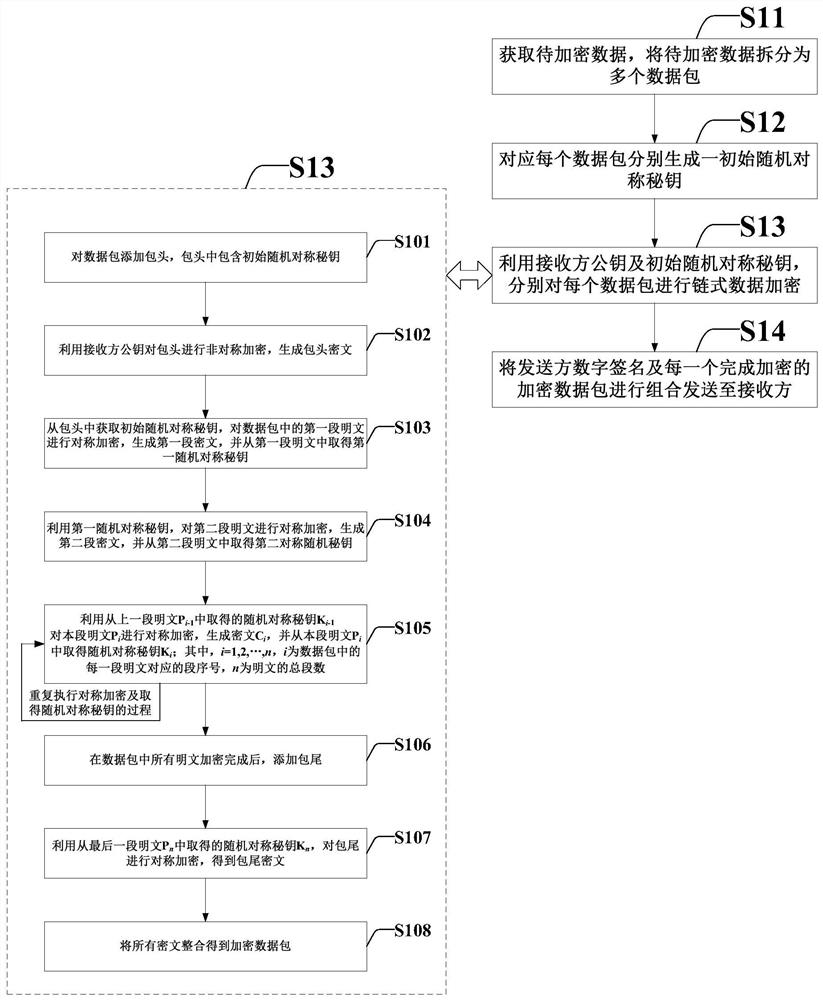
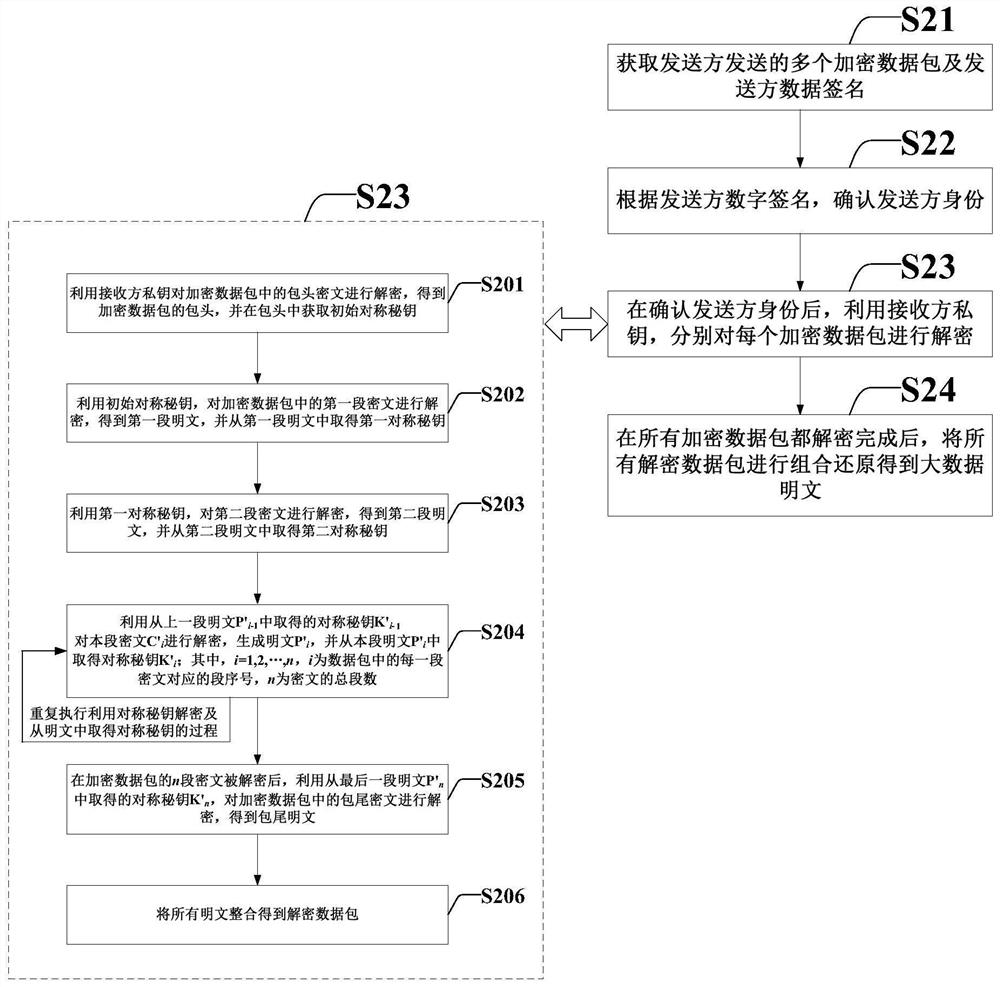
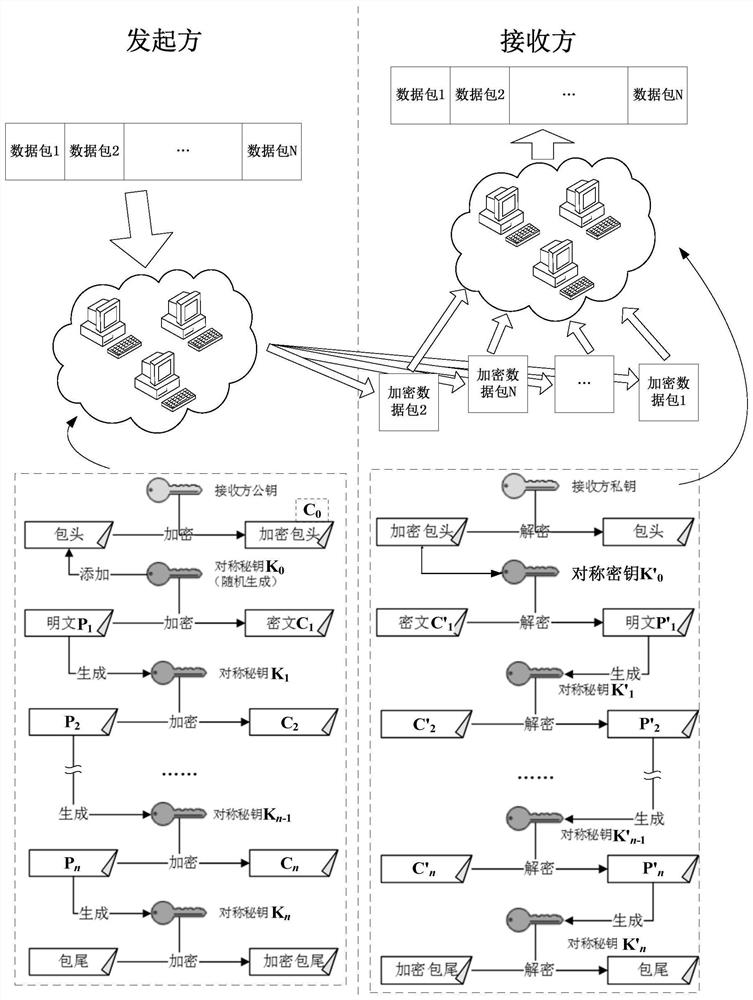
Chained data encryption method, chained data decryption method and corresponding systems
PendingCN111654511AFree from malicious modificationAvoid Malicious ModificationsMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesReal-time computingReceiver
The invention provides a chained data encryption method, a chained data decryption method and corresponding systems, and the chained data encryption method comprises the steps: obtaining to-be-encrypted data, and splitting the to-be-encrypted data into a plurality of data packets; generating an initial random symmetric key corresponding to each data packet; utilizing a public key of a receiver andthe initial random symmetric secret key to respectively carry out chain type data encryption on each data packet; and combining the digital signature of the sender and each encrypted data packet which is encrypted, and sending the combined data packet to a receiver. According to the scheme, in encryption and decryption operation of large-scale data, the processing efficiency can be greatly improved; on the premise that the system processing amount is not increased, the encryption effect is obviously enhanced, meanwhile, under the condition that an abstract algorithm is not increased, the datahas tamper resistance, multiple different encryption algorithms in a cloud platform can be effectively compatible, and the transformation cost is low.
Owner:BANK OF CHINA
An information processing method and system based on two-dimensional codes
InactiveCN106022428AConducive to transaction securityAvoid Malicious ModificationsRecord carriers used with machinesMarketingInformation processingComputer terminal
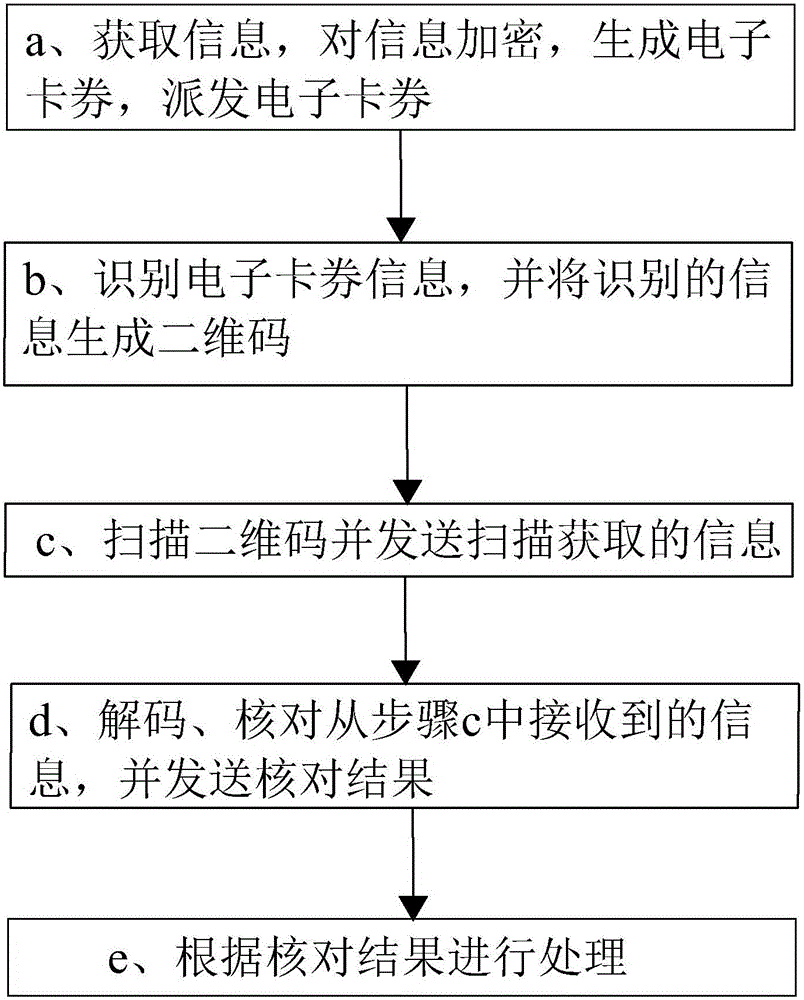
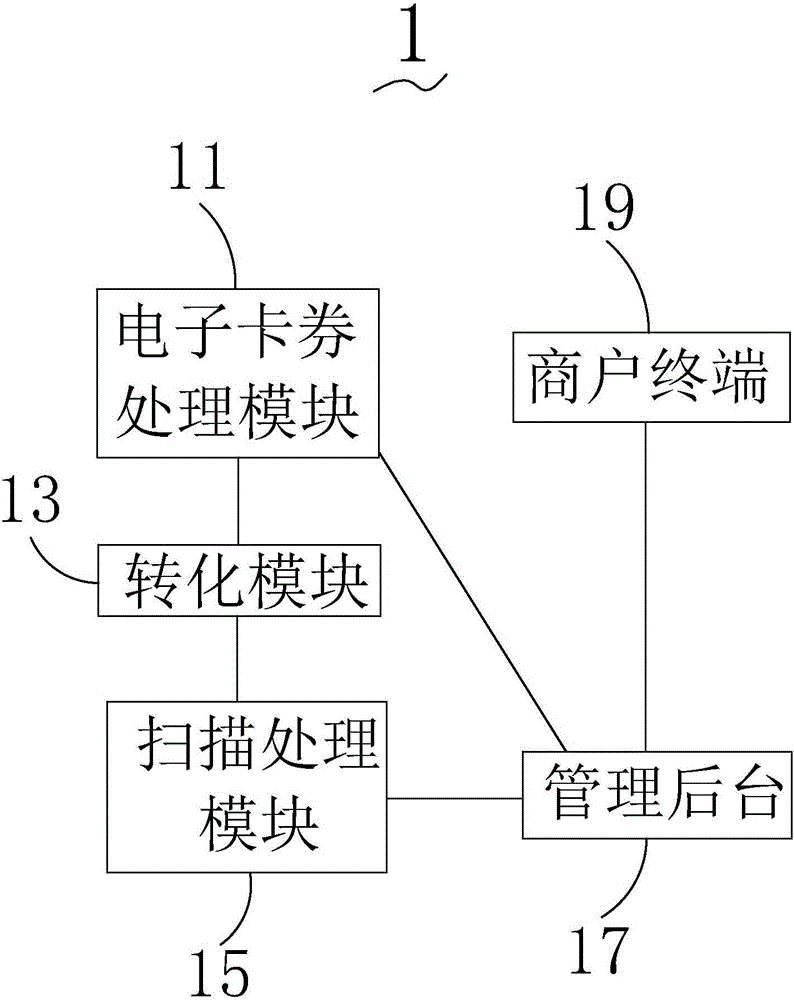
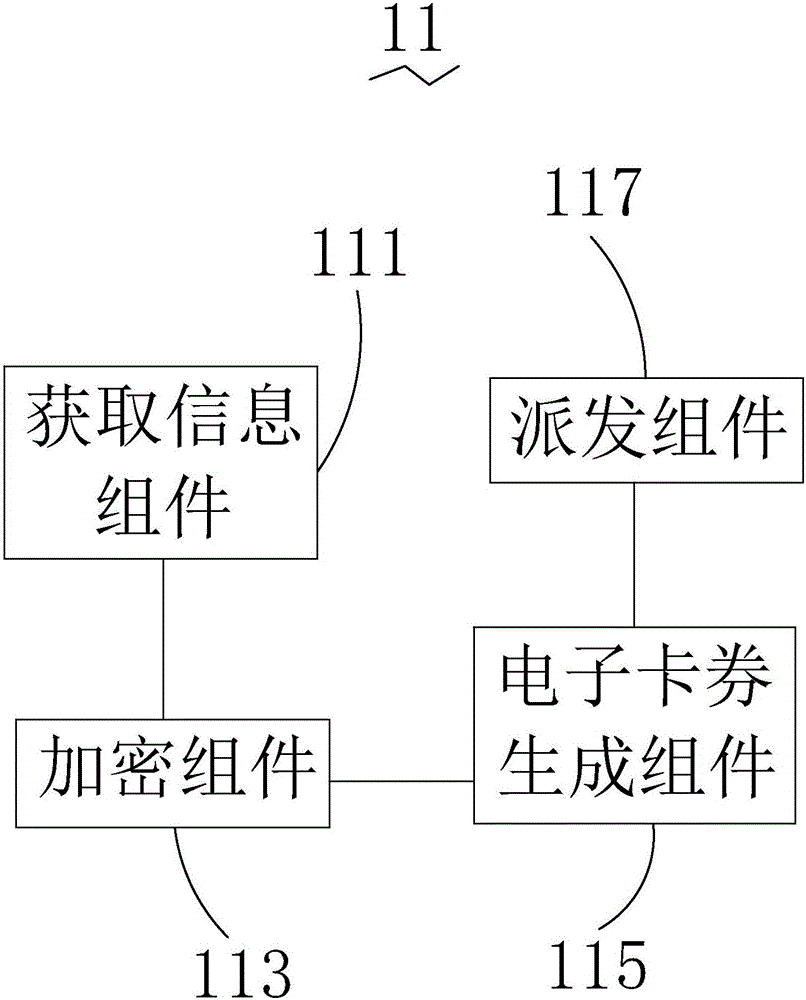
The invention provides an information processing method and system based on a two-dimensional code. The two-dimensional code-based information processing method includes: a. acquiring information, encrypting information, generating electronic coupons, and distributing electronic coupons; b. identifying electronic coupon information, and generating the identified information Two-dimensional code; c. Scanning the two-dimensional code and sending the scanned information; d. Decoding and checking the information received from step c, and sending the checking result; e. Processing according to the checking result. The two-dimensional code-based information processing system includes an electronic coupon processing module, a conversion module, a scanning processing module, a management background and a merchant terminal, which are sequentially connected, and the electronic coupon processing module is connected to the management background. The two-dimension code-based information processing method and system provided by the present invention have the advantages of facilitating the transaction security of merchants and consumers and facilitating the identification of coupon information.
Owner:YUNNEX TECH
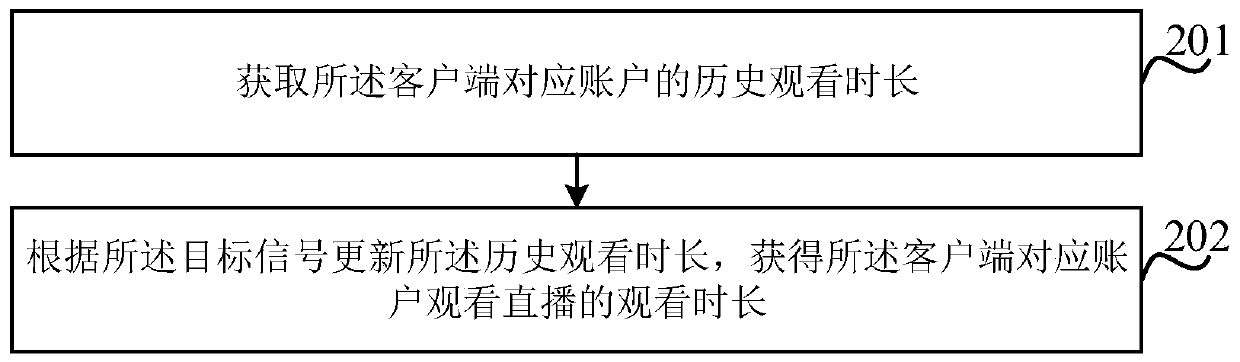
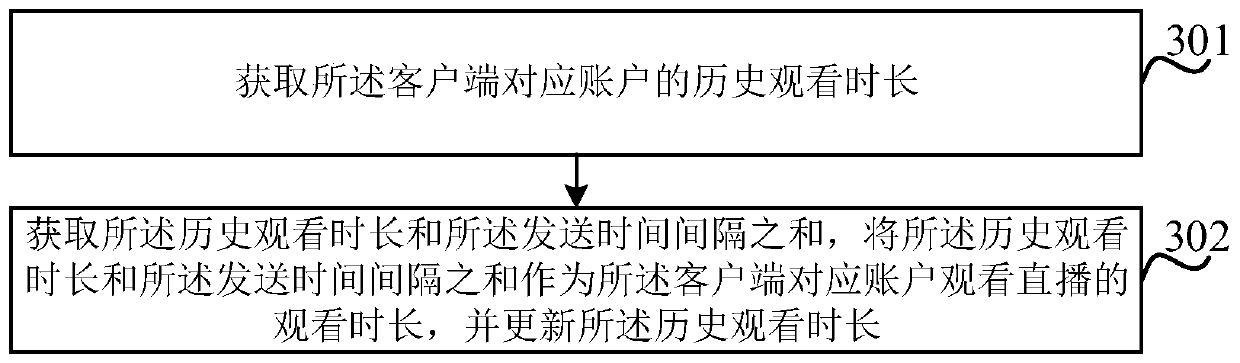
Method and device for obtaining watching duration, electronic equipment and storage medium
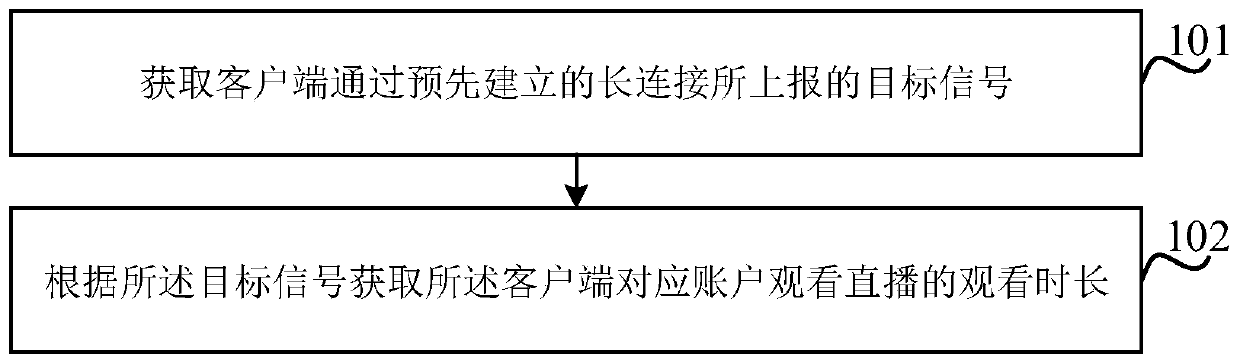
InactiveCN110446079AIncrease credibilityAvoid Malicious ModificationsTransmissionSelective content distributionTarget signalClient-side
The invention relates to a method and a device for obtaining watching duration, electronic equipment and a storage medium. The method comprises the following steps: acquiring a target signal reportedby a client through a pre-established long connection; and the account corresponding to the client acquires the watching duration of watching the live broadcast by the account corresponding to the client according to the target signal. According to the embodiment of the invention, when the user switches to different electronic devices to watch the live broadcast, the corresponding account is not changed, so that the server can accumulate the watching duration of the live broadcast watched by the account, and the continuity of watching duration statistics is ensured. Moreover, in the embodiment, the client only reports the target signal without counting the watching duration, so that the user can be prevented from maliciously modifying the watching duration, and the credibility of the watching duration obtained by the server is higher.
Owner:BEIJING DAJIA INTERNET INFORMATION TECH CO LTD
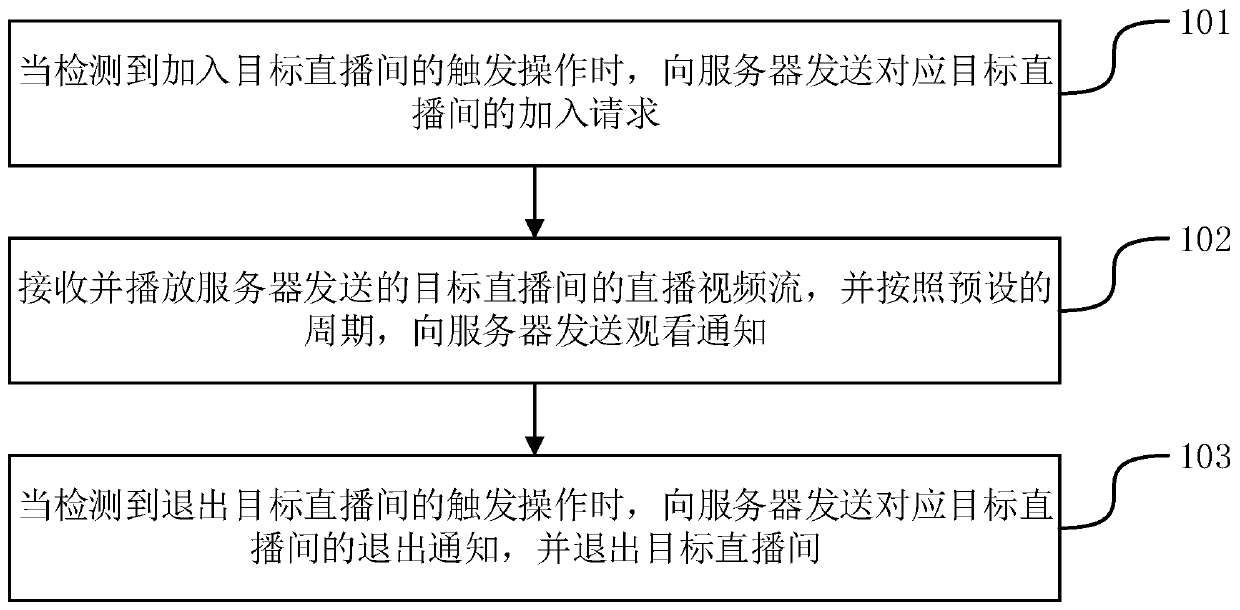
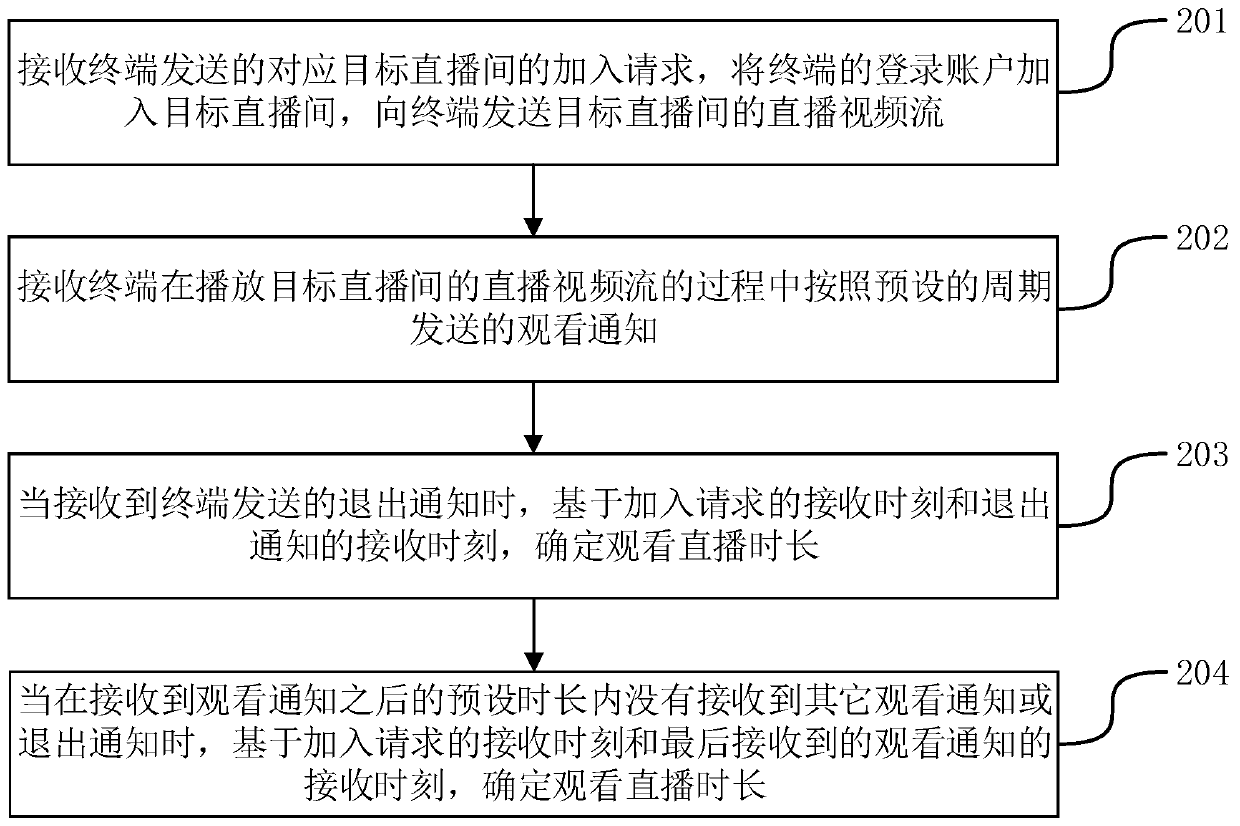
Method, device and system for determining watching live broadcast duration
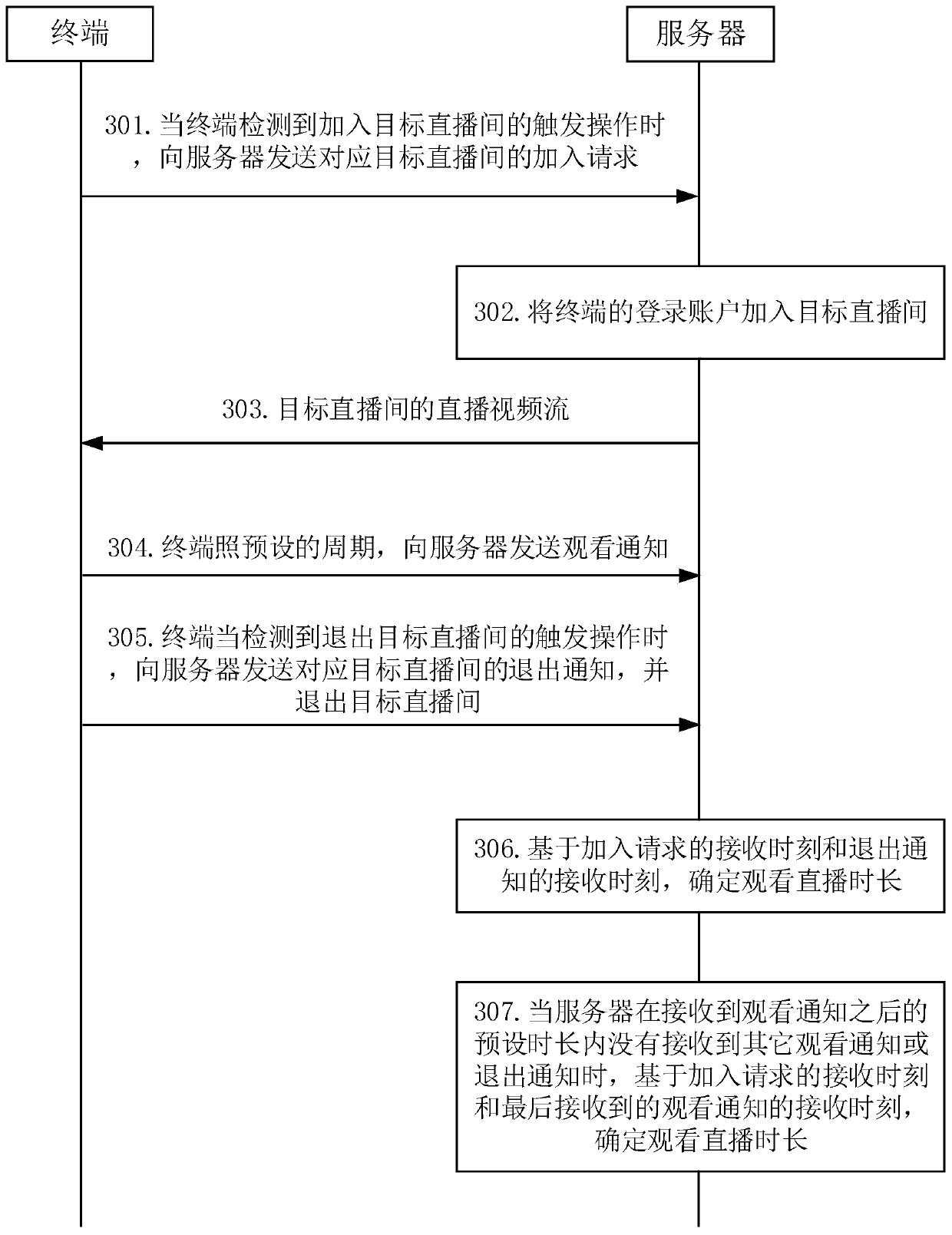
ActiveCN111107389AImprove accuracyAvoid Malicious ModificationsSelective content distributionTelecommunicationsThe Internet
The invention discloses a method, device and system for determining live broadcast watching duration, and belongs to the technical field of the Internet. The method comprises the following steps: receiving an adding request which is sent by a terminal and corresponds to a target live broadcast room, adding a login account of the terminal into the target live broadcast room, and sending a live broadcast video stream of the target live broadcast room to the terminal; receiving a watching notification sent by the terminal according to a preset period in the process of playing the live video stream of the target live broadcast room; when an exit notification sent by the terminal is received, determining live broadcast watching duration based on the receiving moment of the joining request and the receiving moment of the exit notification; and when other watching notifications or quitting notifications are not received within a preset duration after the watching notifications are received, determining the watching live broadcast duration based on the receiving moment of the joining request and the receiving moment of the finally received watching notifications. According to the invention, the accuracy of the live broadcast watching duration of the user recorded by the server can be improved.
Owner:GUANGZHOU KUGOU TECH
Method for protecting mirror image codes based on executable mirror image hiding and dll injection
ActiveCN105512548APrevent dynamic debuggingIncreased protectionComputer security arrangementsProcess functionComputer module
Provided is a method for protecting mirror image codes based on executable mirror image hiding and dll injection. The method comprises the following steps that 1, a target mirror image is decrypted in a memorizer; 2, a PE mirror image is loaded, wherein a dll file needed for a program is loaded, mirror image repositioning is executed, and finally OEP is executed; 3, whether an IAT of an exe module is hijacked or not is checked; 4, a Load Library and a Load Library Ex are actively hijacked, operation in the step 3 is executed on a dll mirror image of a load result, and if judgment is not abnormal, the step 5 is executed; 5, a Create Process function is hijacked, and a protection dll is injected while a subprocess is set up; 6, remote thread injection is carried out, a protected target process is injected in a Ring3 environment, and thread injection of a vicious loader is avoided; 7, a thread (THREAD_PRIORITY_BELOW_NORMAL) with low priority is built, endless loop check is carried out, whether the thread is loaded by a Debugger or not is checked, and checking is carried out once every second.
Owner:XIANGTAN UNIV
Autonomous behavior-based product marketing support system and method
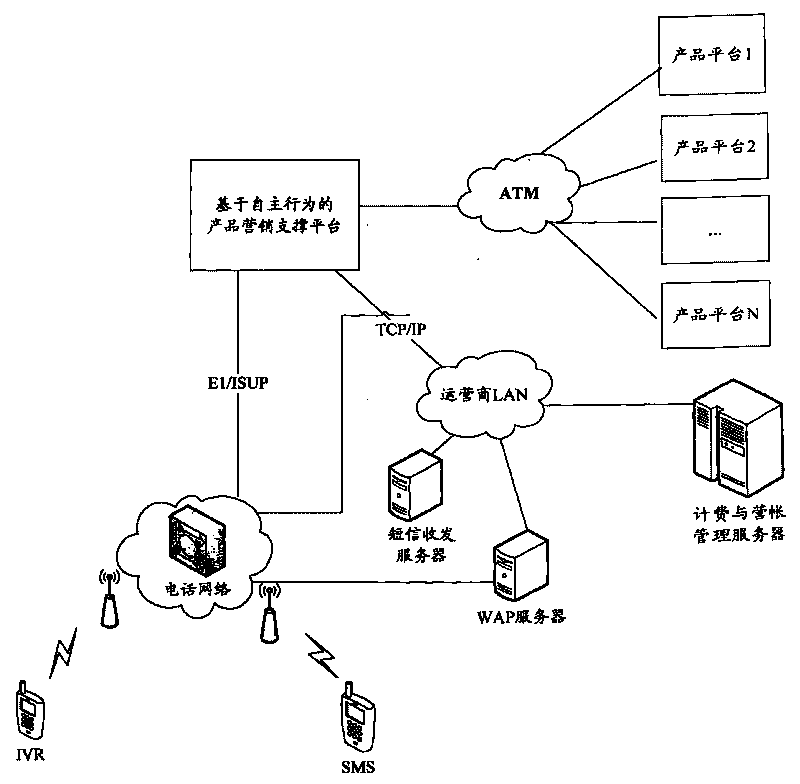
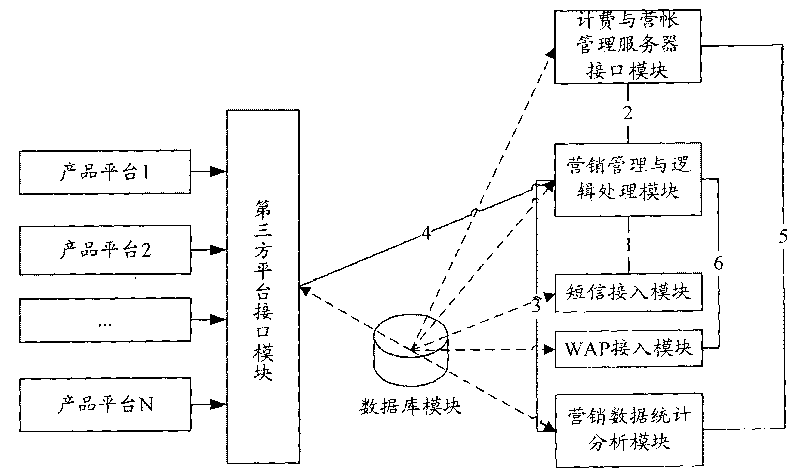
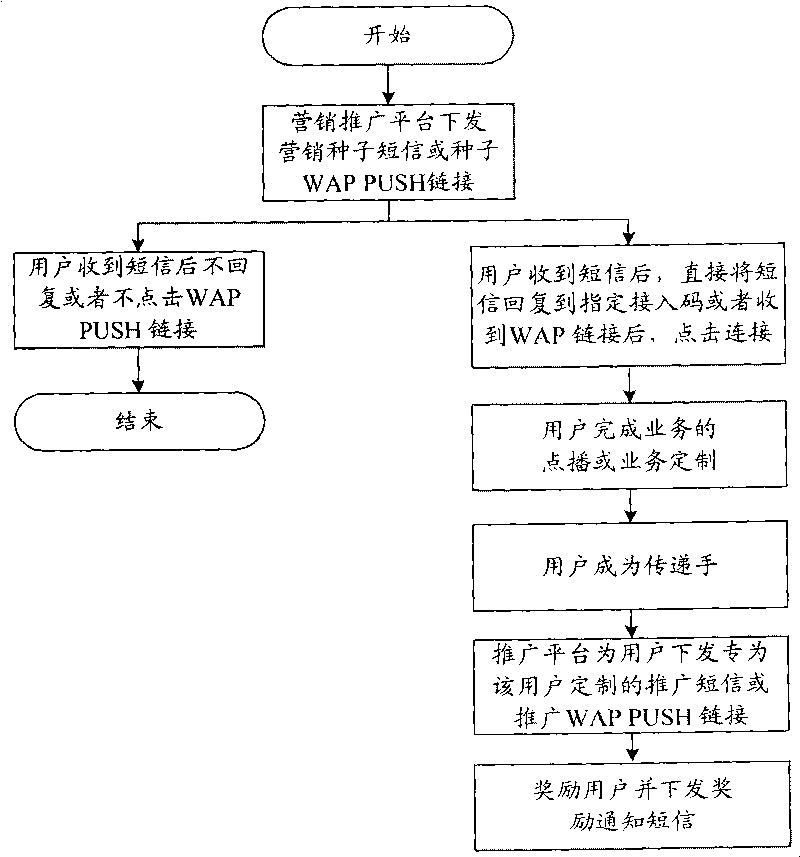
InactiveCN101741999AReduce complaint rateImprove trustSpecial service for subscribersWireless network protocolsReal-time marketingAutonomous behavior
The invention relates to an autonomous behavior-based product marketing support system and method, is a support system which can provide marketing management for a plurality of products at the same time and initiatively provides a novel product marketing mode which is suitable for ordinary users to participate extensively and has great influence. Except for relevant network elements and various product marketing platforms of an original telephone switching network, the product marketing support system is also provided with the autonomous behavior-based product marketing support platform. The system has the following main functions: mainly adopting user autonomous promotion in a short message or network mode to provide parallel support for multi-product and multi-region marketing; and meanwhile, ensuring that transmission or marketing tasks of each product or service are independent to realize noninterference among promotion and transmission tasks. Moreover, the marketing support system and method can strictly limit participating populations and regions and provide real-time marketing awards for participating users. Meanwhile, marketing personnel can learn personal marketing performance in real time, thereby furthest arousing the working enthusiasm of marketing personnel.
Owner:BEIJING DASCOM TECH +1
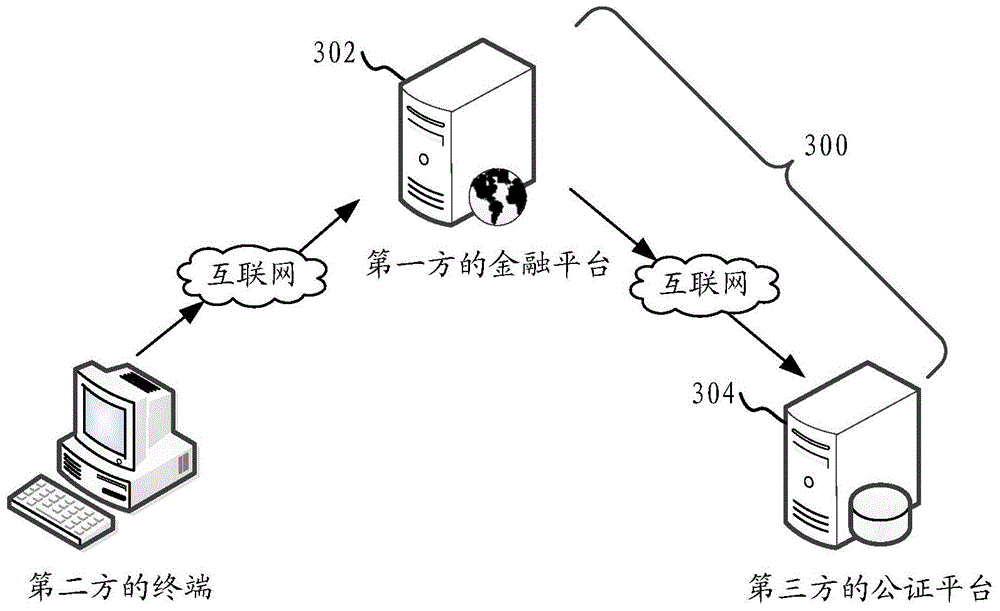
Finance platform data processing method and system
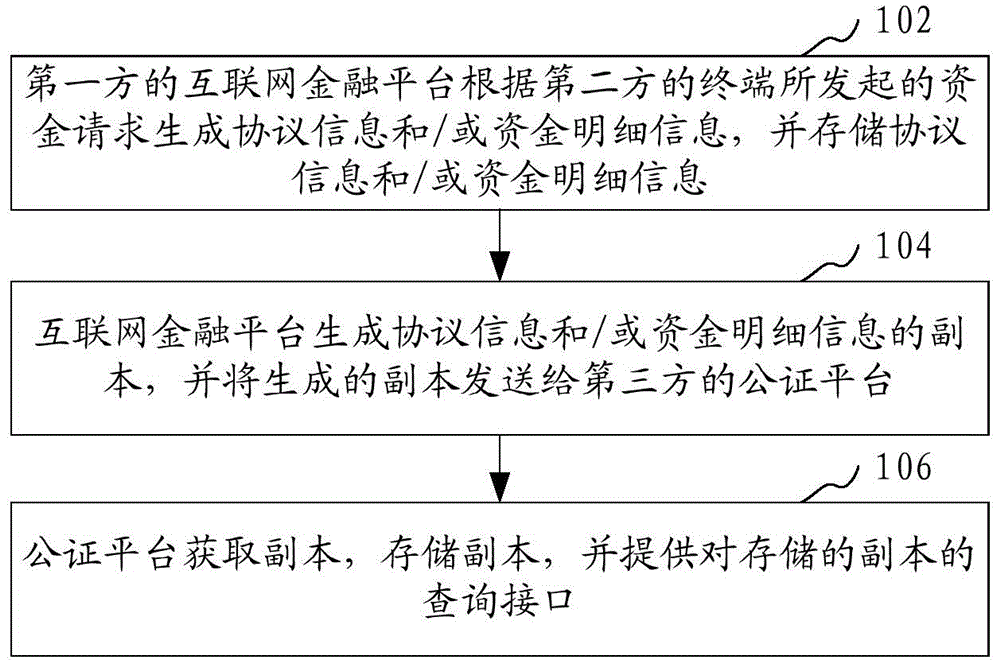
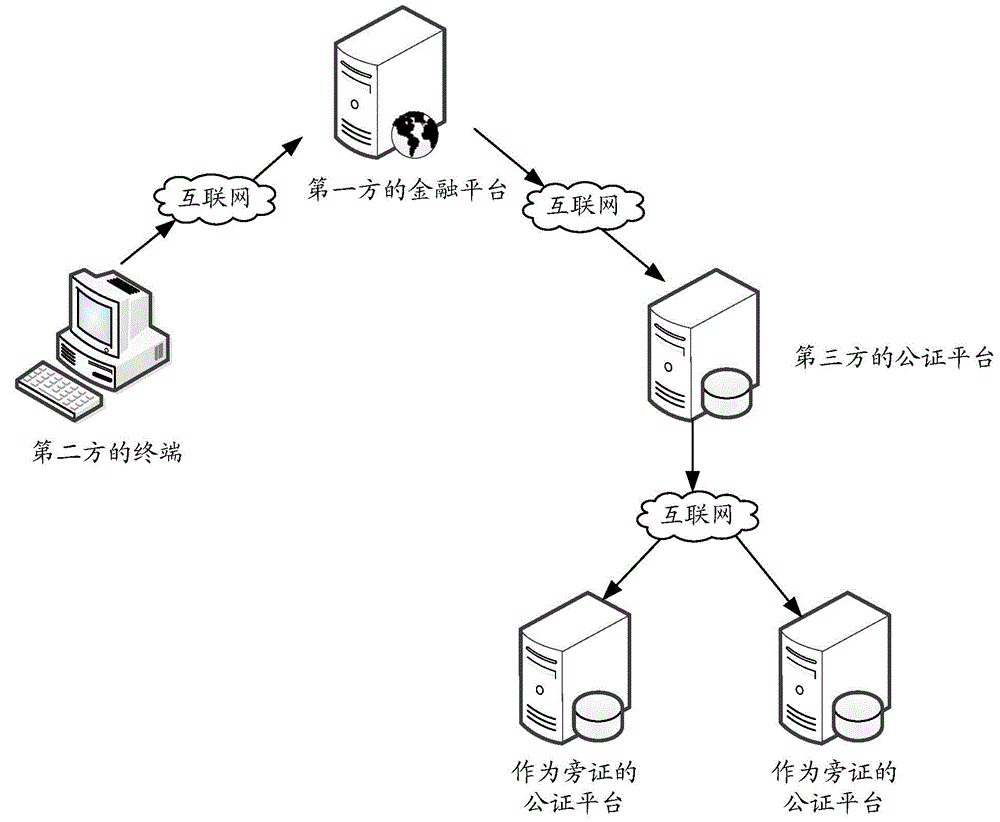
ActiveCN104917738AAvoid Malicious ModificationsAvoid safety hazardsFinanceInternal/peripheral component protectionData processing systemThird party
The present invention provides a financial platform data notarization method, and the method includes that: the financial platform generates protocol information and / or fund detail information according to a fund request initiated by a terminal, and stores the information and / or transmits the information to a storage platform for storage; the financial platform and / or storage platform generate / generates a copy of the protocol information and / or fund detail information, and transmit / transmits the generated copy and / or designated part of the copy and / or a copy set to a notary platform; the notary platform obtains and stores the copy and / or designated part of the copy and / or the copy set, and provides query interfaces to the stored copy and / or designated part of the copy and / or the copy set. By the financial platform data notarization method provided by the present invention, a user can query the copy of protocol information and / or fund detail information through the query interfaces at any time, and compare the copy with the original stored in the financial platform, in case that the protocol information and / or fund detail information are maliciously modified and lost. The present invention also provides a financial platform data notarization system.
Owner:陈衡
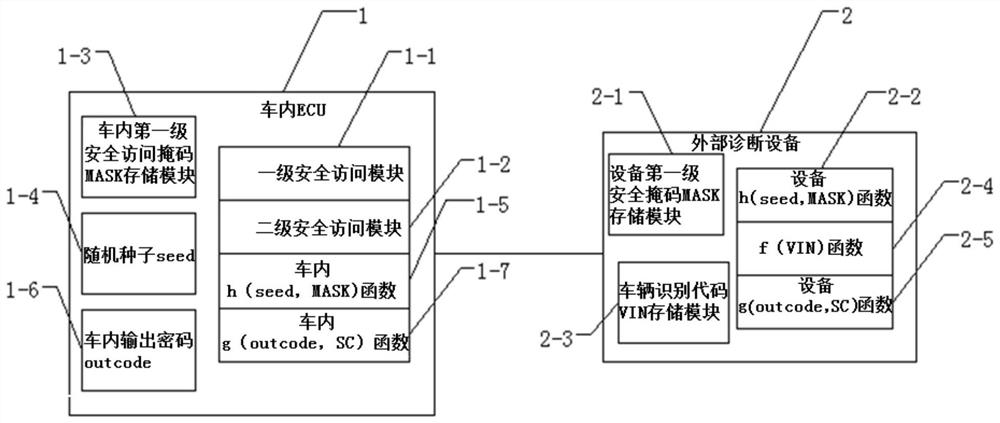
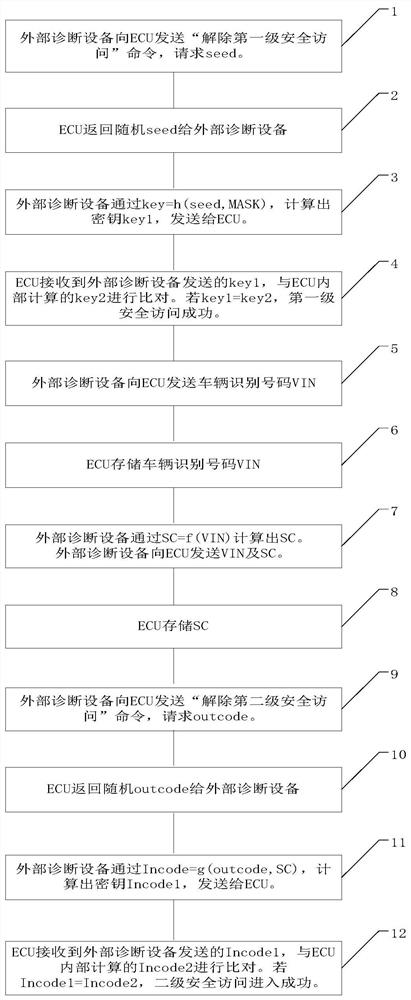
Two-stage safety access system of passenger vehicle and access method thereof
PendingCN112182663AAvoid Malicious ModificationsKey distribution for secure communicationUser identity/authority verificationComputer scienceDiagnostic equipment
The invention relates to a two-stage safety access system of a passenger vehicle. The system comprises a safety access system of an ECU in the vehicle and a safety access system of external diagnosisequipment. The external diagnosis equipment is physically connected with the in-vehicle ECU; after the external diagnosis equipment and the ECU in the vehicle judge that the first-stage safety accessis successful through the diagnosis command, the second-stage safety access can be carried out; and the ECU data in the vehicle is modified only after judging that the second-level security access issuccessful. According to the method, the important data of the controller in the passenger vehicle is protected by adopting a method of combining primary safety access and secondary safety access, sothat the internal data of the ECU of the passenger vehicle can be prevented from being maliciously modified.
Owner:FAW CAR CO LTD
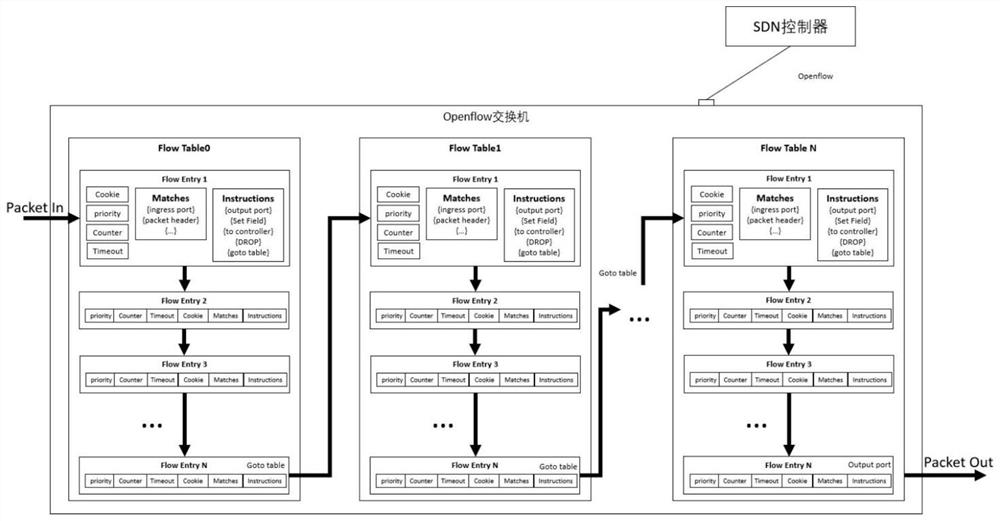
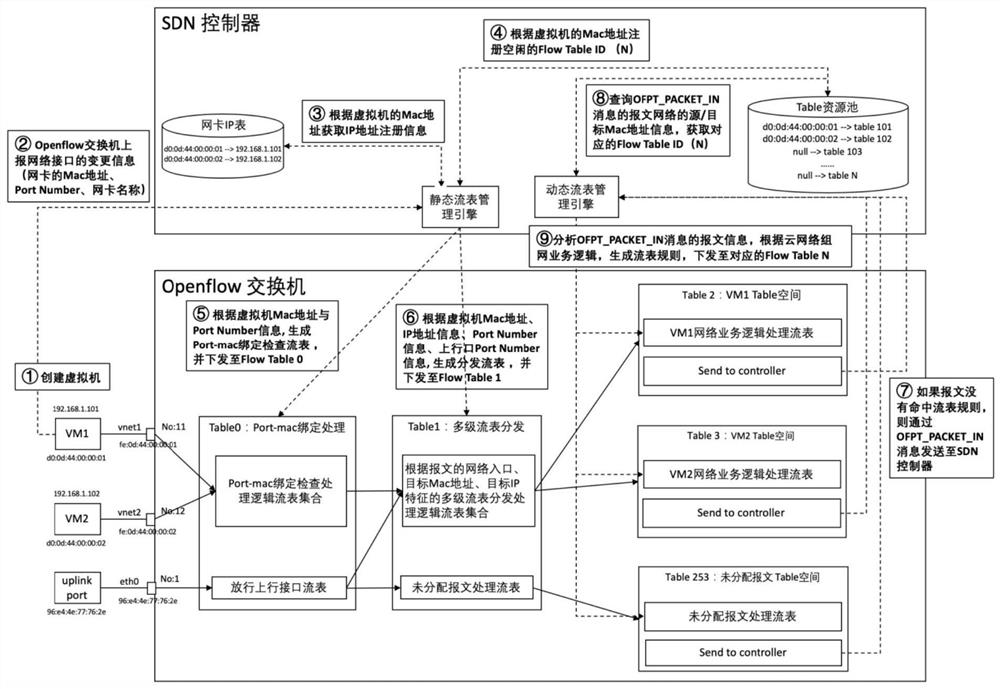
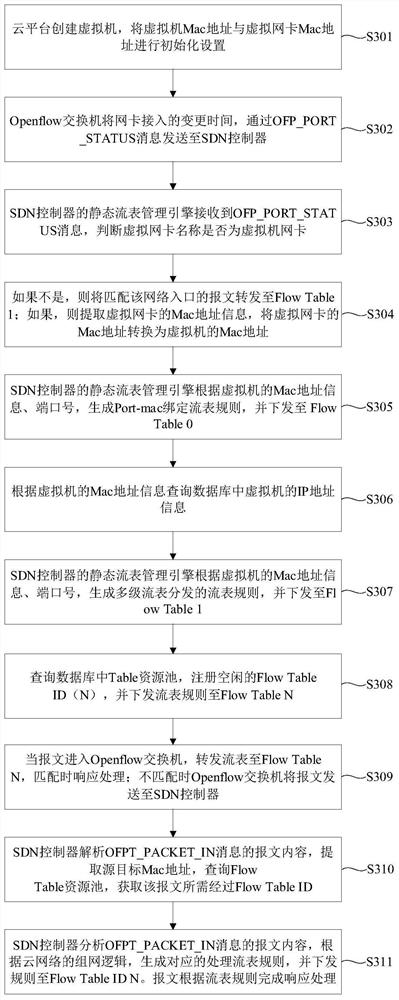
Multistage flow table management and control method and system for virtual machine
ActiveCN111726305AAvoid Malicious ModificationsQuick indexData switching networksSoftware simulation/interpretation/emulationAccess networkResource assignment
The invention discloses a multistage flow table management and control method and system for a virtual machine. The multistage flow table management and control method for the virtual machine comprises the following steps: generating a port-mac binding flow table rule, and issuing the port-mac binding flow table rule to a flow table 0; registering an idle flow table N, and issuing the port-mac binding flow table rule to the flow table N; generating a multi-level flow table distribution rule, and issuing the multi-level flow table distribution rule to the flow table 1; and when the message enters the Openflow switch, when it is determined that the message is sent by a virtual machine according to a port-mac binding flow table rule of a flow table 0, forwarding the flow table of the messageto a corresponding flow table N according to a multi-stage flow table distribution rule of a flow table 1. According to the management and control method and system provided by the invention, the flowtable of the Openflow switch and the Mac address of the virtual machine access network card are used as unique identifiers of virtual machine network resources; according to the method, rapid indexing and resource allocation of the SDN controller are realized, and the virtual machine Mac address is used as a key matching item for multistage flow table distribution, so that the effect of preventing the virtual machine from maliciously modifying the Mac address can be achieved.
Owner:GUANGZHOU BINGO SOFTWARE
Data storage management method on blockchain
InactiveCN111427897AImprove securityAvoid Malicious ModificationsDatabase updatingDatabase distribution/replicationEngineeringData store
The invention discloses a data storage management method on a blockchain, and specifically relates to the technical field of block chains, and specifically comprises the steps that cloud servers matched with nodes in a block chain system are arranged, the number of the cloud servers is the same as that of the nodes in the block chain system, a single node is matched with a single cloud server, andthe cloud servers are not communicated with one another; in the blockchain system, a blockchain node is controlled to divide data uploaded by a terminal of the blockchain node into different data segments, and the data segments are manageable blocks; and after fragmentation is completed, the storage system encrypts each data fragment on the local system, and the control in the encryption processis controlled in the whole process of the content ownership of the data fragment, so that any person unexpected by a content owner cannot check and access the data in the data fragment. According to the method, different data management operations are performed through different verification modes and verification sequences, so that the security of data storage and management on the blockchain canbe improved.
Owner:安徽高山科技有限公司
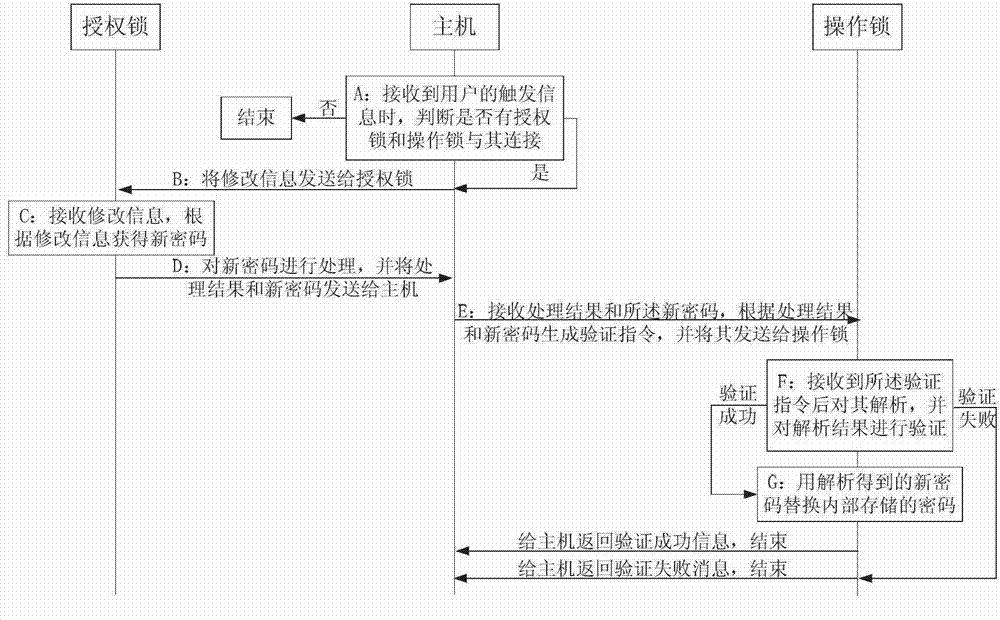
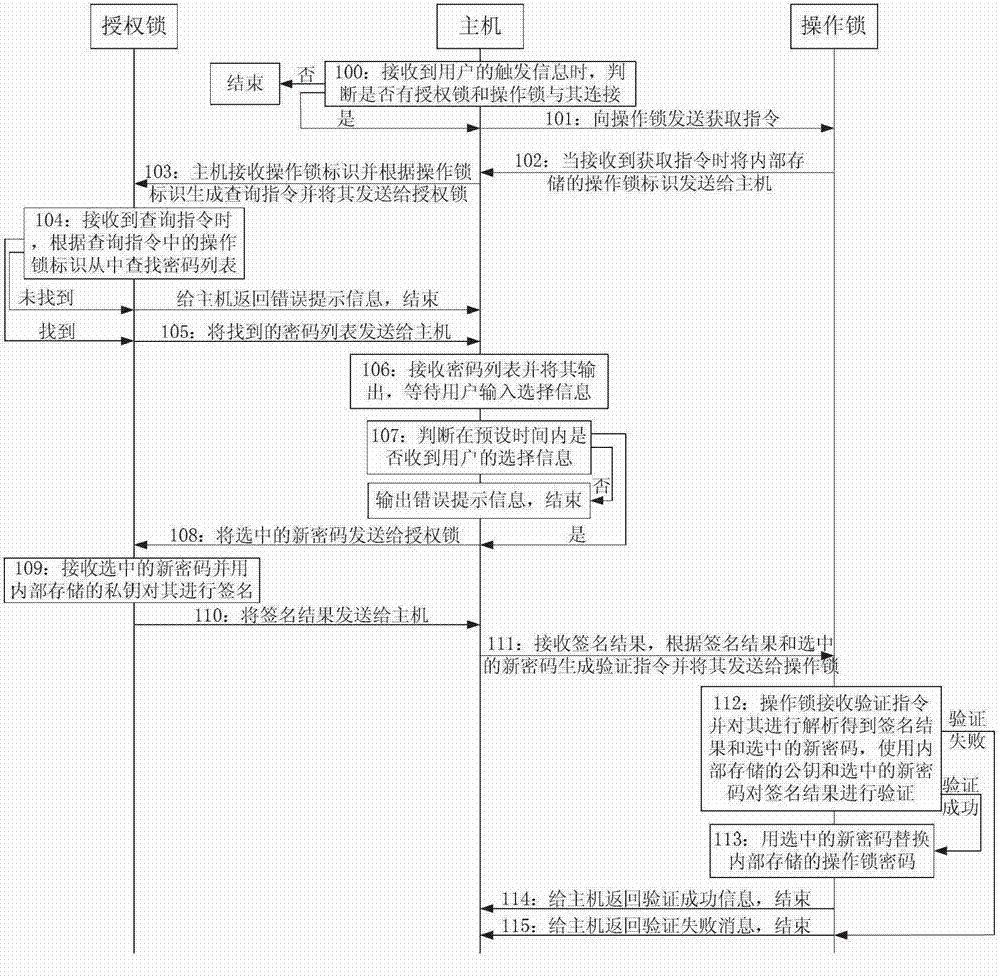
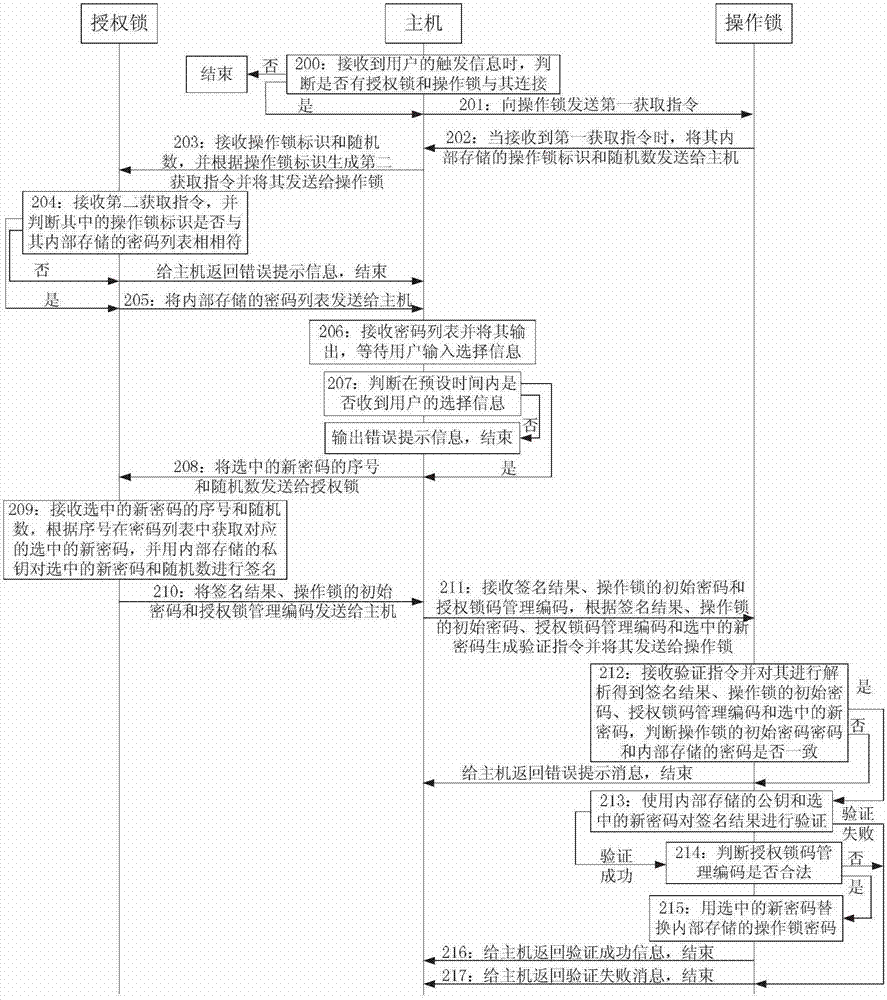
Method and system for modifying password of encryption lock
ActiveCN102902927AAvoid Malicious ModificationsThe modification process is safe and controllablePlatform integrity maintainancePasswordEncryption
The invention discloses a method and a system for modifying a password of an encryption lock. The method comprises the steps that: when the user trigger information is received, a host judges whether an authorized lock and an operation lock are connected with the host, if so, the host transmits the modification information to the authorized lock, otherwise, the operation is ended; the authorized lock receives the modification information and obtains a new password; the authorized lock processes the new password and transmits the processing result and the new password to the host; the host generates a verification instruction according to the processing result and the new password and transmits the verification instruction to the operation lock; the operation lock analyzes and verifies the received verification instruction, if verification instruction is verified to be qualified, the internally stored password is replaced by the analyzed new password, the modification success information returns to the host, and the operation is ended; otherwise the failure information returns to the host, and the operation is ended. According to the technical scheme, an agent or a developer can modify the password of the operation lock by utilizing the authorized lock, namely the password is modified under the control of a manufacturer, malicious modification is avoided, and the modification process is safe and controllable.
Owner:FEITIAN TECHNOLOGIES
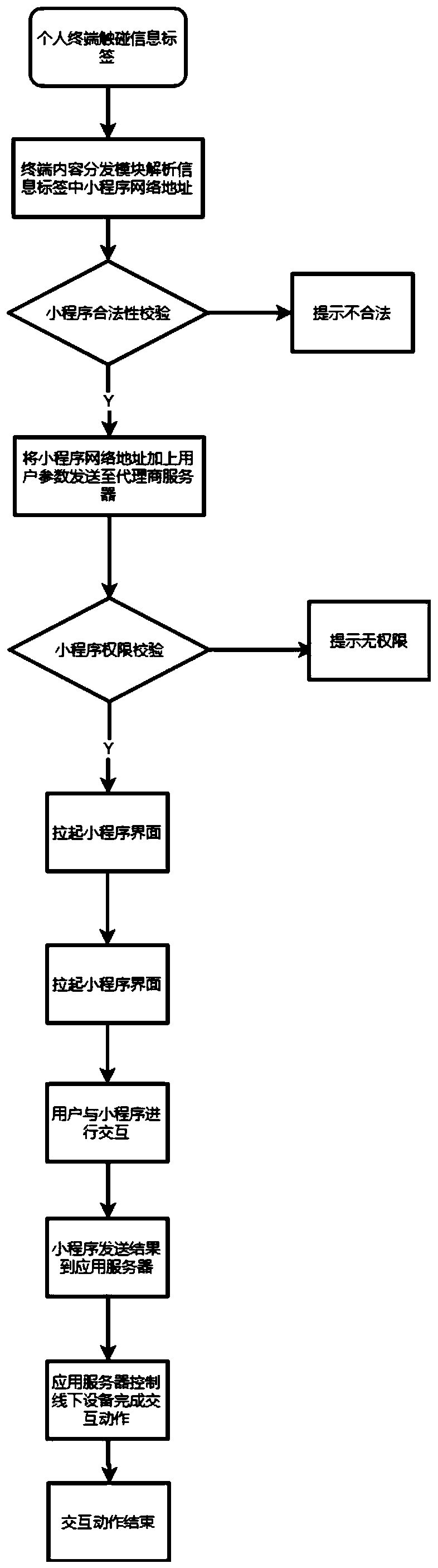
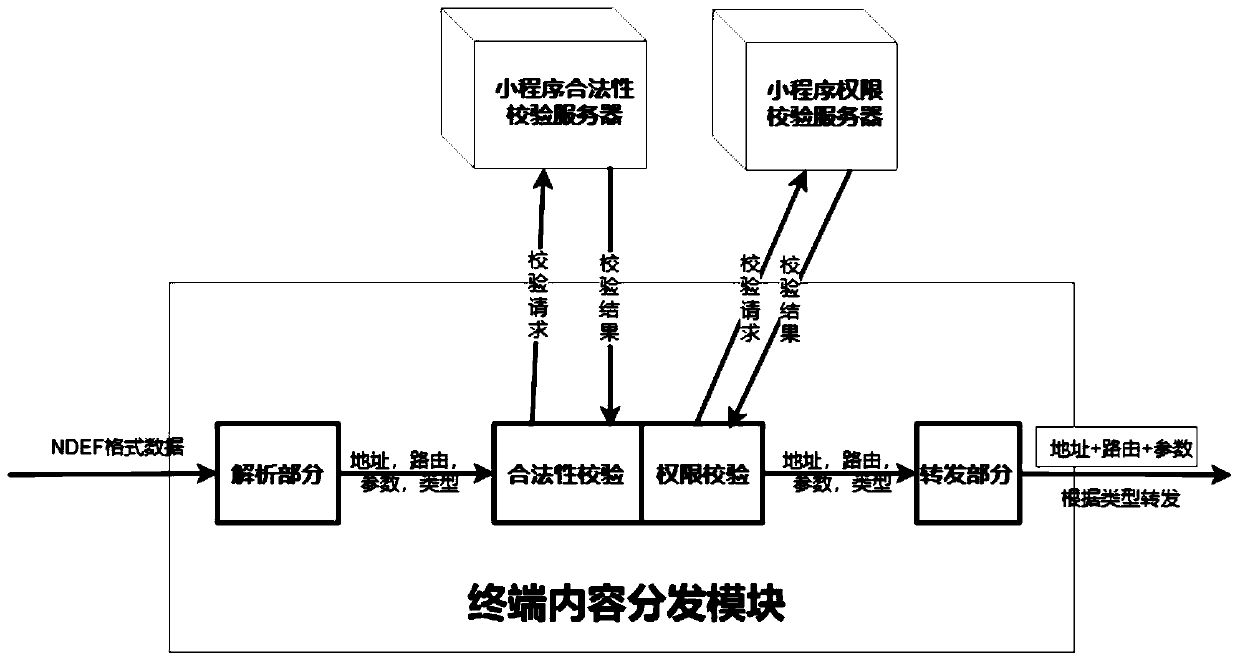
Mini-program touch type interaction mode based on NFC technology
ActiveCN110704123AHigh directnessAcquisition speed is fastComputer security arrangementsBootstrappingHuman–computer interactionComputer engineering
The invention discloses a applet touch type interaction mode based on an NFC (near field communication) technology, which comprises the following steps of: sealing corresponding information of an applet in an NFC label in advance, reading the information in the NFC label through an intelligent terminal, analyzing by an application program, and skipping to the applet according to the information toobtain a service. Compared with the traditional way of opening the applet by searching or scanning the two-dimensional code, the interaction mode can greatly shorten the operation waiting time of theuser, eliminate the learning cost of the user and improve the user experience.
Owner:EAST CHINA NORMAL UNIV
System for version completeness detection of network phone
PendingCN106411657AQuickly locate and verifyAvoid Malicious ModificationsData switching networksReal time displayFailure probability
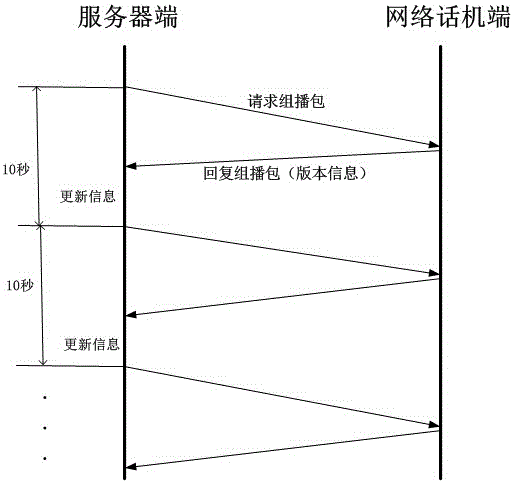
The present invention discloses a system for version completeness detection of a network phone. When large-scale network phone production is performed, the version and configuration upgrading correction and completeness are detected, a software program installed at a server is configured to detect the data exchanging with the phones in the local area network to collect the information of the versions, resource files and the like of all the phones in the local area network to perform comparison and analysis and display whether the versions of the phones are correct or not in real time so as to reduce the failure probability of the version and factory configuration upgrading when large-scale production is performed, quickly search and locate the network phones which are failed in upgrading, improve the qualified rate of the network phone production versions and reduce the labor cost.
Owner:南京汉隆科技有限公司
MIPS (Million Instructions Per Second) platform Web access strategy control method
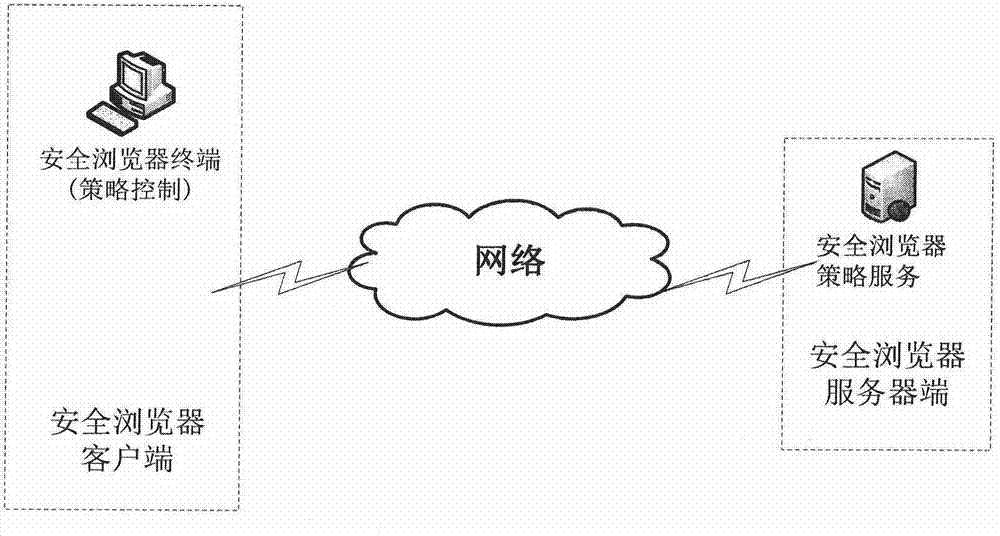
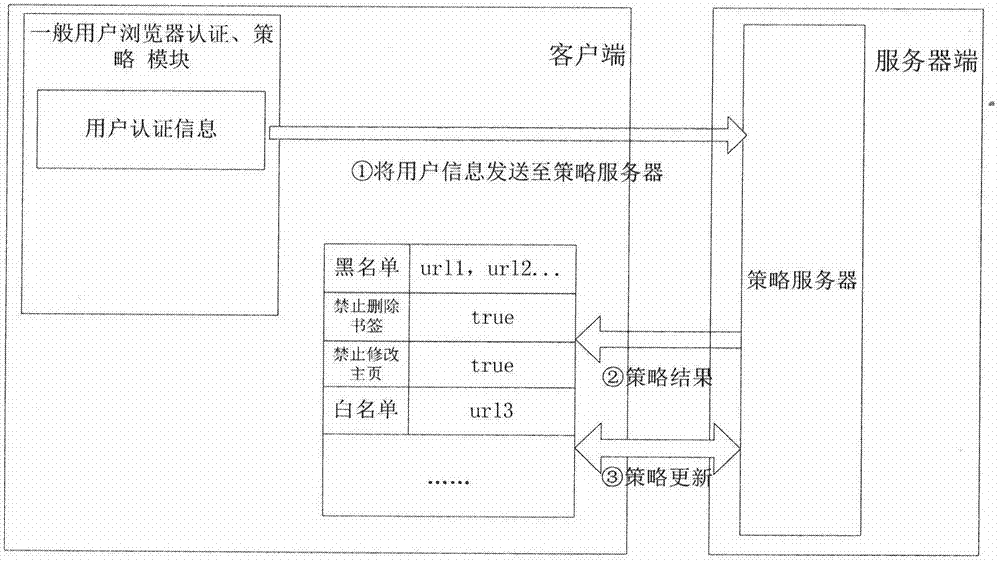
InactiveCN104506520AAvoid visitingAvoid Malicious ModificationsPlatform integrity maintainanceTransmissionInstructions per secondHome page
The invention discloses an MIPS (Million Instructions Per Second) platform Web access strategy control method. According to the MIPS platform Web access strategy control method, strategy setting of users of a client browser is uniformly managed and controlled in a centralized manner by a strategy server; the browser requests for the strategy server at certain time intervals; the strategy server manages strategy information of the users and returns the strategy information of the users to the client browser; the browser implements corresponding control according to the related strategy information. The MIPS platform Web access strategy control method has the advantages that control on an MIPS platform Web access strategy, functions of URL (Uniform Resource Locator) access blacklist control, URL access white list control and a forced home page address setting strategy, a function that whether a bookmark is editable, a function of installing a blacklist on an extension and functions of a download directory setting strategy, a plug-in URL white list, a plug-in URL blacklist and the like of the browser, are implemented, so that a local terminal can be protected and the users are prevented from accessing malicious websites, operating malicious plug-ins, installing malicious extensions, maliciously modifying a home page of the browser and the like.
Owner:中软信息系统工程有限公司
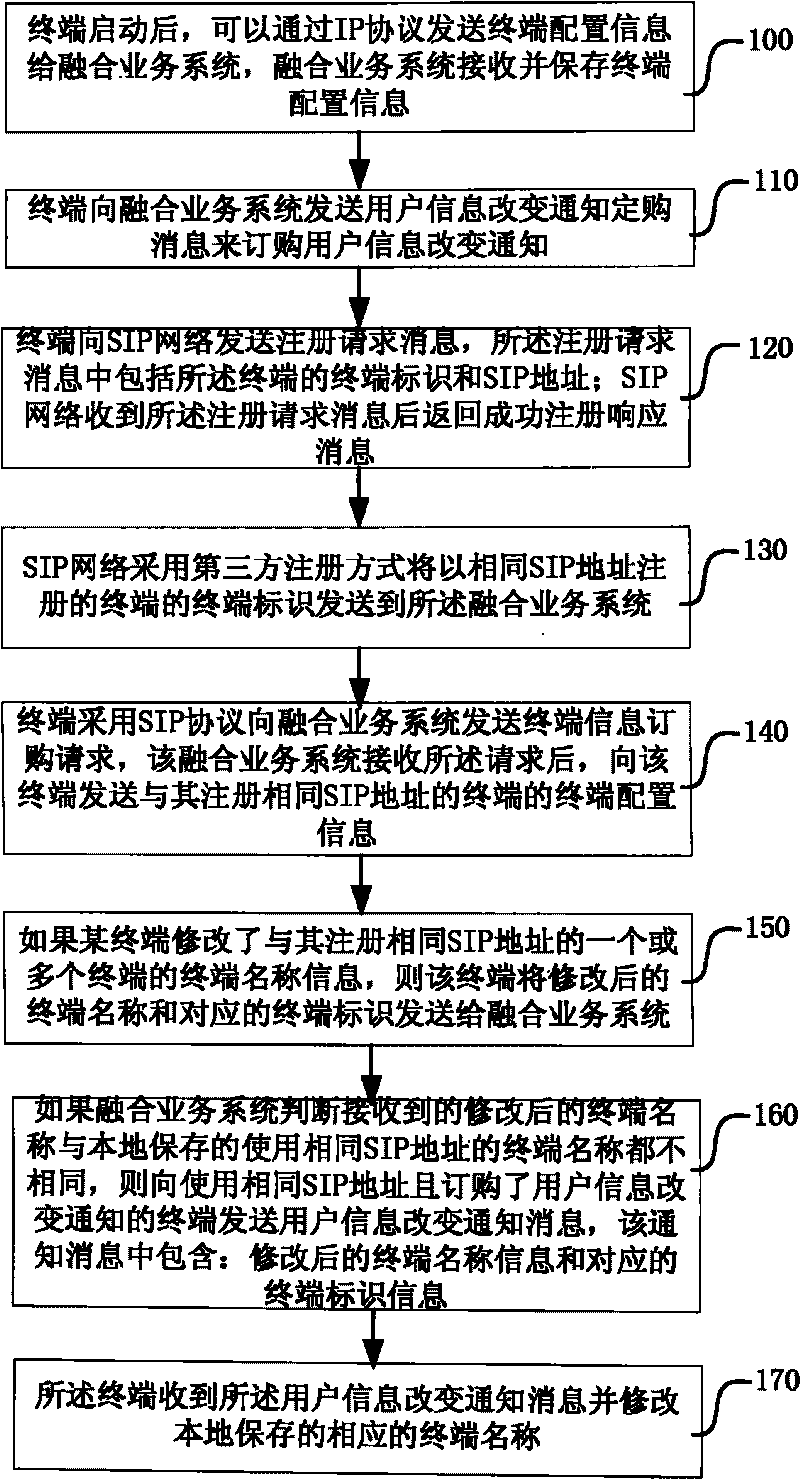
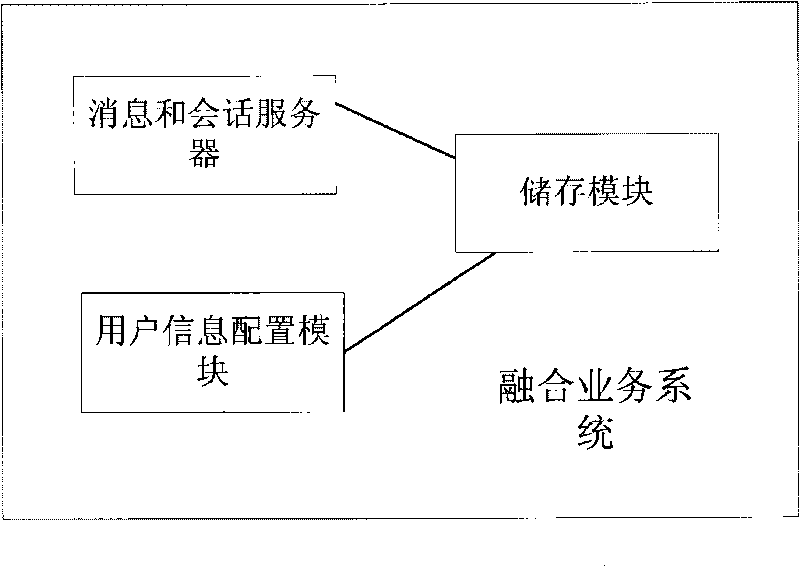
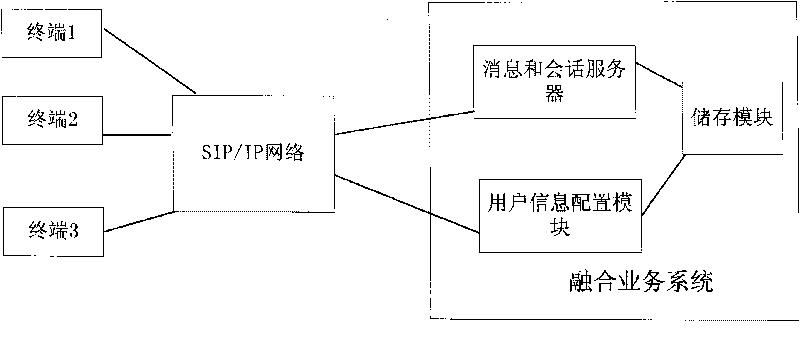
Terminal name changing method and fusion service system
The invention discloses a terminal name modifying method and a fusion service system. The method comprises the following steps that: after a terminal is successfully registered in an SIP network, the SIP network transmits a terminal identifier of the terminal to the fusion service system according to an SIP address of the terminal; if the terminal changes the terminal names of one or more locally stored terminals registered with the same SIP address, the SIP network transmits changed terminal names and corresponding terminal identifiers to the fusion service system; and the fusion service system loads the received modified terminal names and corresponding terminal identifiers in a notification message and transmits the notification message to the one or more terminals registered with the SIP address, and the terminals receiving the notification message change corresponding terminal names locally stored. The terminal name changing method and the fusion service system of the invention solve the problem that other terminals can change corresponding terminal names when a user can change the names of a local terminal or other terminals on one terminal under the condition of a plurality of terminals.
Owner:ZTE CORP
SaaS-based data management system
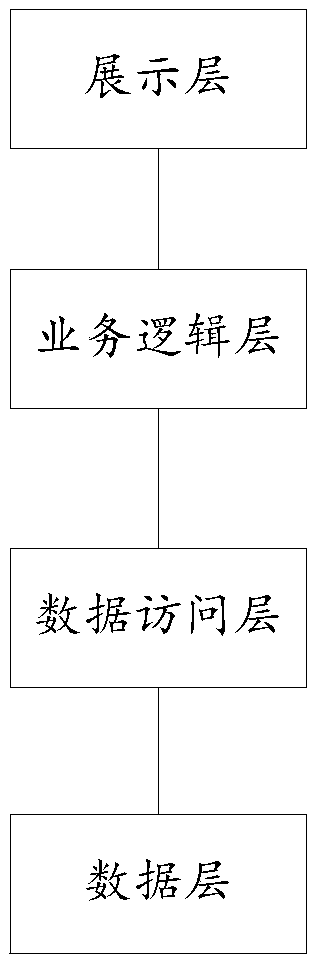
InactiveCN108768964AData Operation SecurityAvoid Malicious ModificationsUser identity/authority verificationData switching networksOriginal dataStructure of Management Information
The invention provides an SaaS-based data management system, comprising: a display layer, used for expressing a system structure and a visual form in view and text forms, and receiving an interactiveinstruction of the user; a business logic layer, used for performing interaction and corresponding business logic processing with the data access layer according to an operation instruction of the user, and implementing user instruction operations according to the interaction and corresponding logic processing; a data access layer, used for accessing the data layer according to the interactive instruction of the business logic layer, and reading and transmitting the data of the data layer; and a data layer, used for performing logical operation encapsulation on the non-initial data, and reading and transmitting the encapsulated non-original data through the data access layer. The invention is capable of avoiding data leakage regardless of transmission or storage, and ensuring the securityof the data.
Owner:江苏知更鸟科技服务有限公司
Intelligent lock authentication method, security chip, intelligent lock and management system thereof
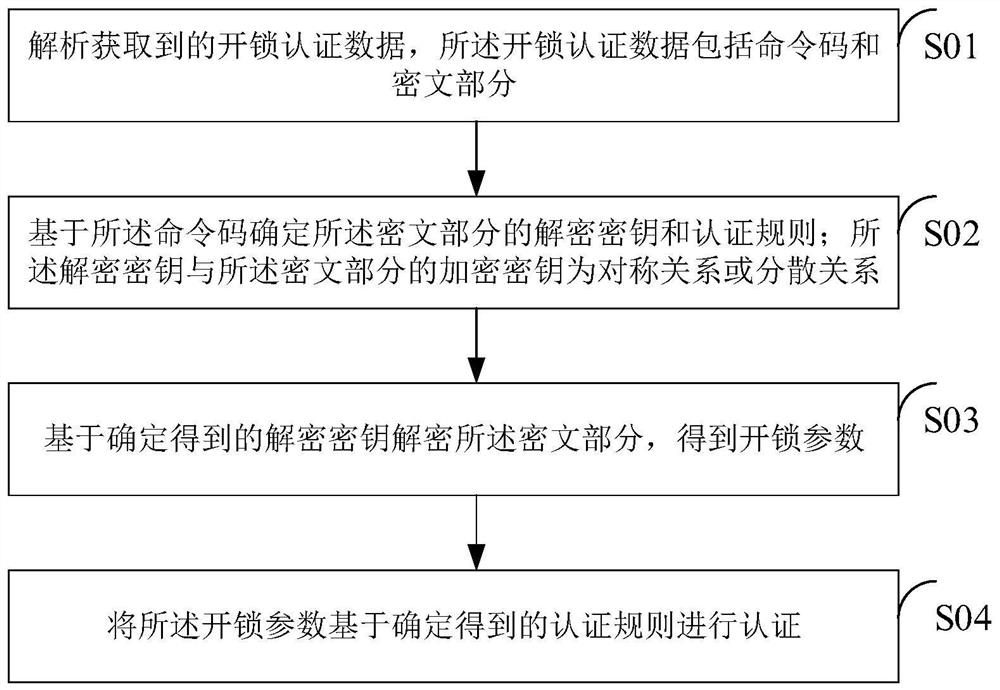
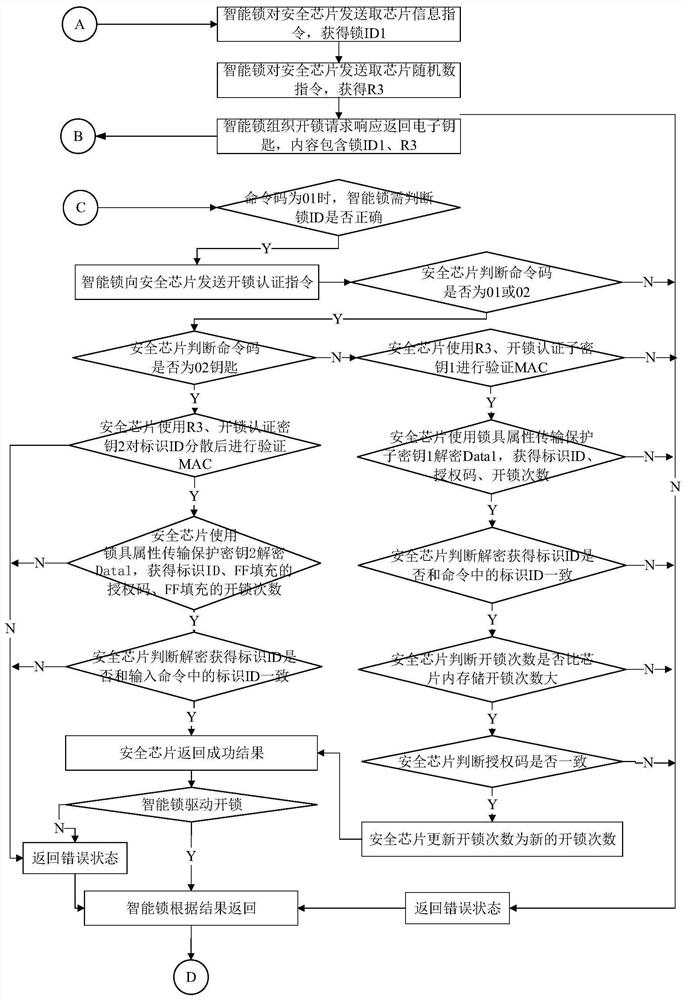
ActiveCN112598827AAvoid Malicious ModificationsImprove data securityUser identity/authority verificationIndividual entry/exit registersCiphertextEmbedded system
The embodiment of the invention relates to the technical field of safety, in particular to an intelligent lock authentication method, a safety chip, an intelligent lock and a management system thereof. The intelligent lock authentication method comprises the following steps: analyzing acquired unlocking authentication data, wherein the unlocking authentication data comprises a command code and a ciphertext part; determining a decryption key and an authentication rule of the ciphertext part based on the command code, wherein the decryption key and the encryption key of the ciphertext part are in a symmetric relationship or a dispersed relationship; decrypting the ciphertext part based on the determined decryption key to obtain an unlocking parameter; and authenticating the unlocking parameter based on the determined authentication rule. Meanwhile, the invention further provides a corresponding safety chip, an intelligent lock and a management system of the intelligent lock. According tothe embodiment provided by the invention, the data security of the security chip and the intelligent lock can be improved.
Owner:BEIJING SMARTCHIP MICROELECTRONICS TECH COMPANY +3
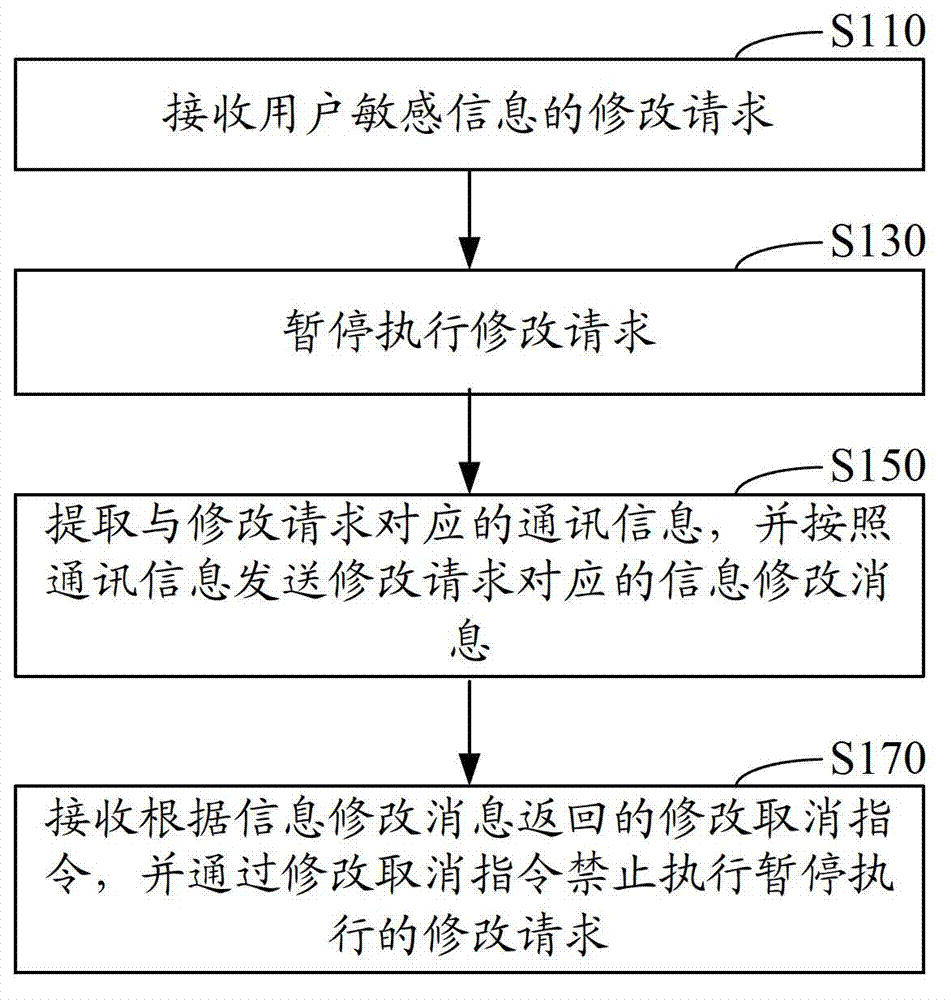
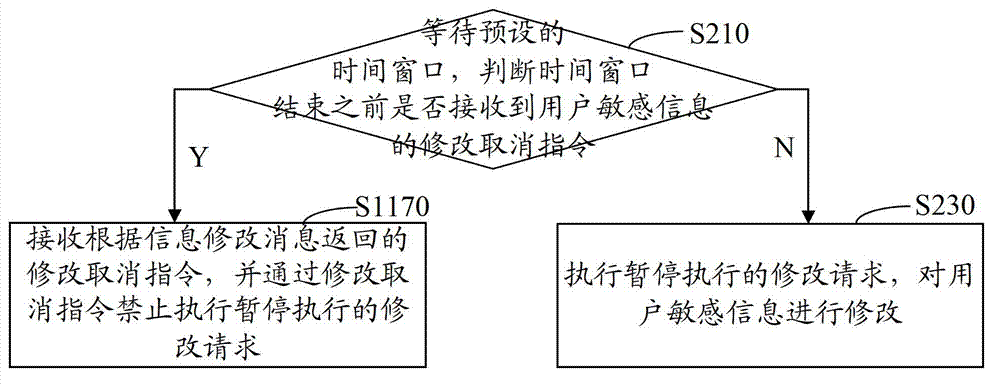
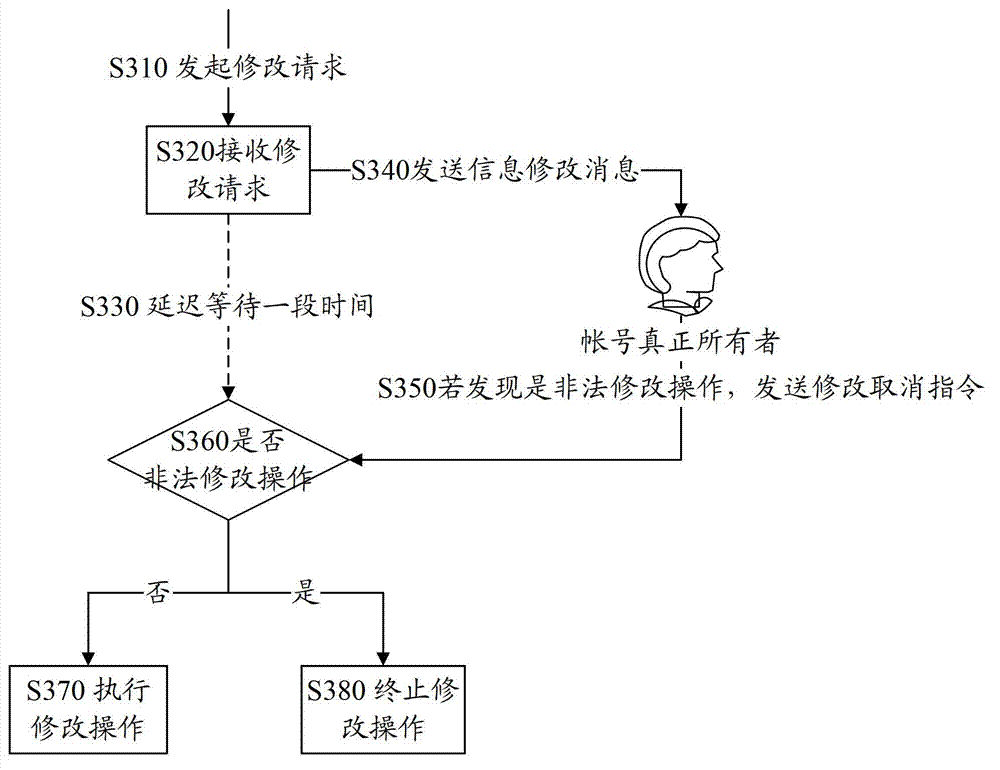
Method and system for controlling modification of user's sensitive information
The invention provides a method and a system for controlling modification of user's sensitive information. The method comprises the steps of receiving a modification request of the user's sensitive information; performing suspend execution on the modification request; extracting communication information corresponding to the modification request, and transmitting an information modification message corresponding to the modification request according to the communication information; receiving a modification cancel command returned according to the information modification message and forbidding execution of the modification request subjected to the suspend execution according to the modification cancel command. The system comprises a request receiving module, a suspend execution module, a processing module and a request forbidding module. By means of the method and the system for controlling modification of the user's sensitive information, labor cost is reduced, and malicious modification of the user's sensitive information is avoided.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Interaction method for online group members
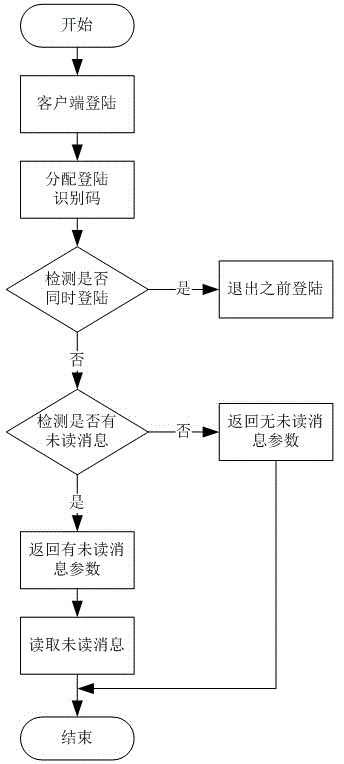
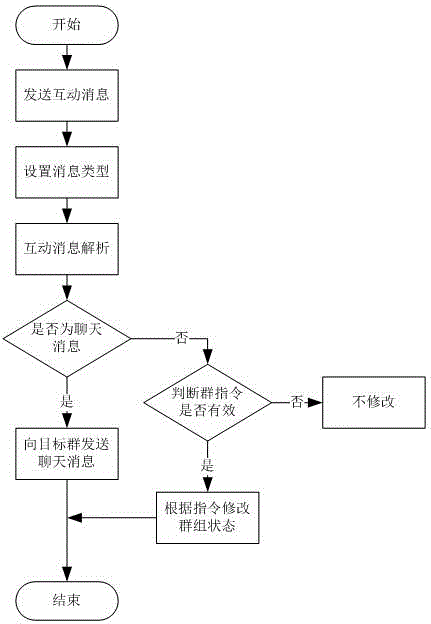
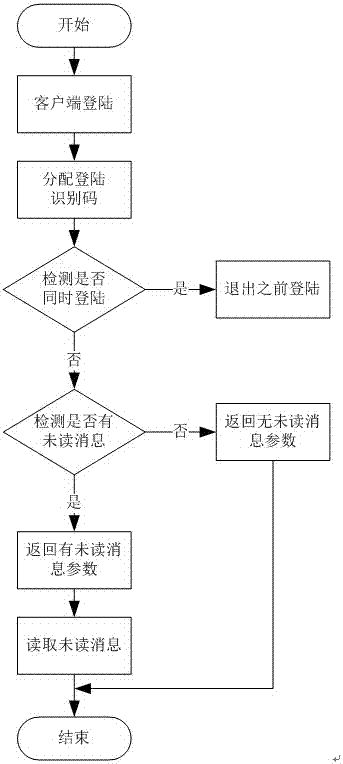
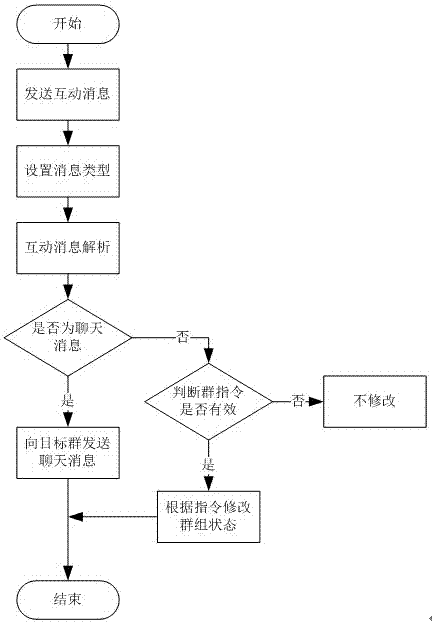
ActiveCN104901869AAvoid simultaneous loginEasy to manageData switching networksInformation typeMessage type
The invention provides an interaction method for online group members, comprising the steps as follows: managing login of group members, managing unread information, setting information type and analyzing interaction information, thereby performing effective management to the interaction information of group members so as to simplify the management of the interaction of the group members.
Owner:上海尚美嘉晋互联网科技有限公司
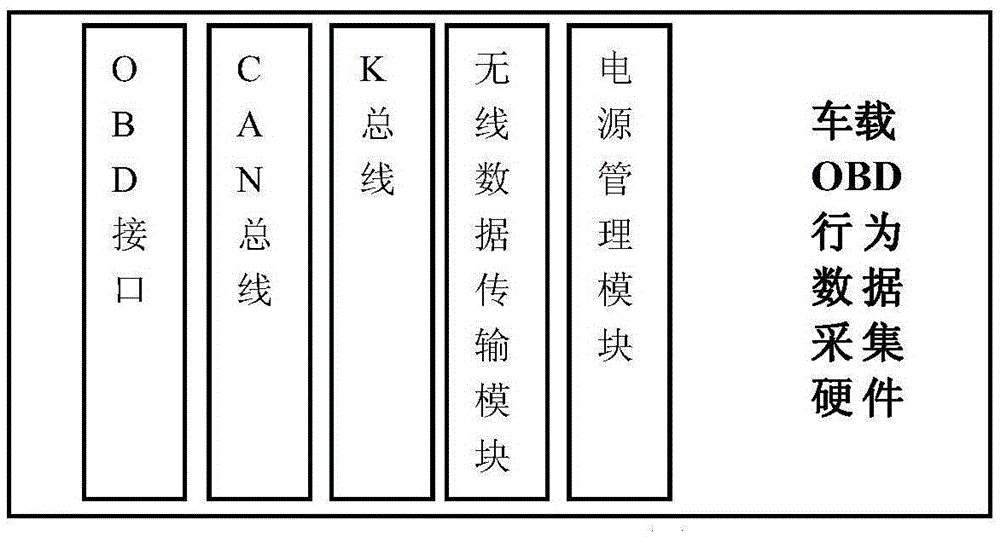
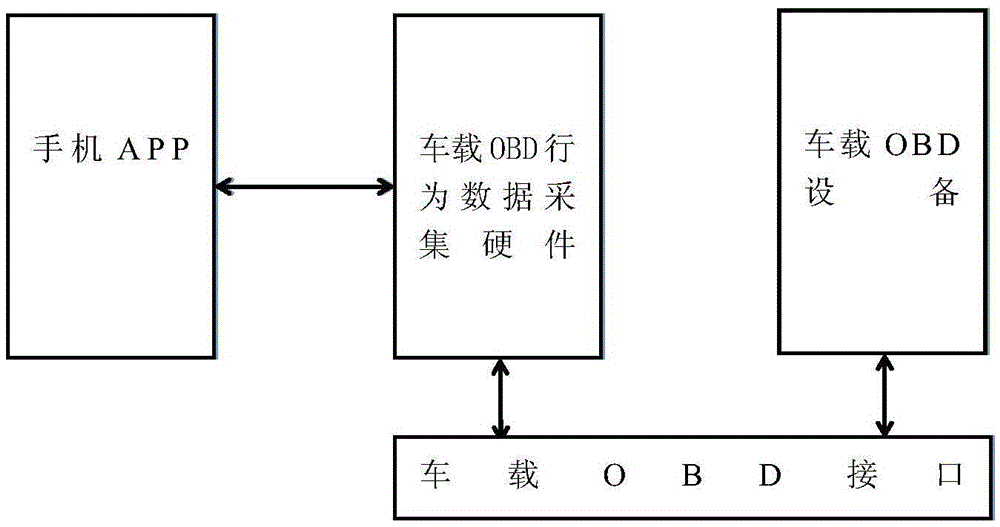
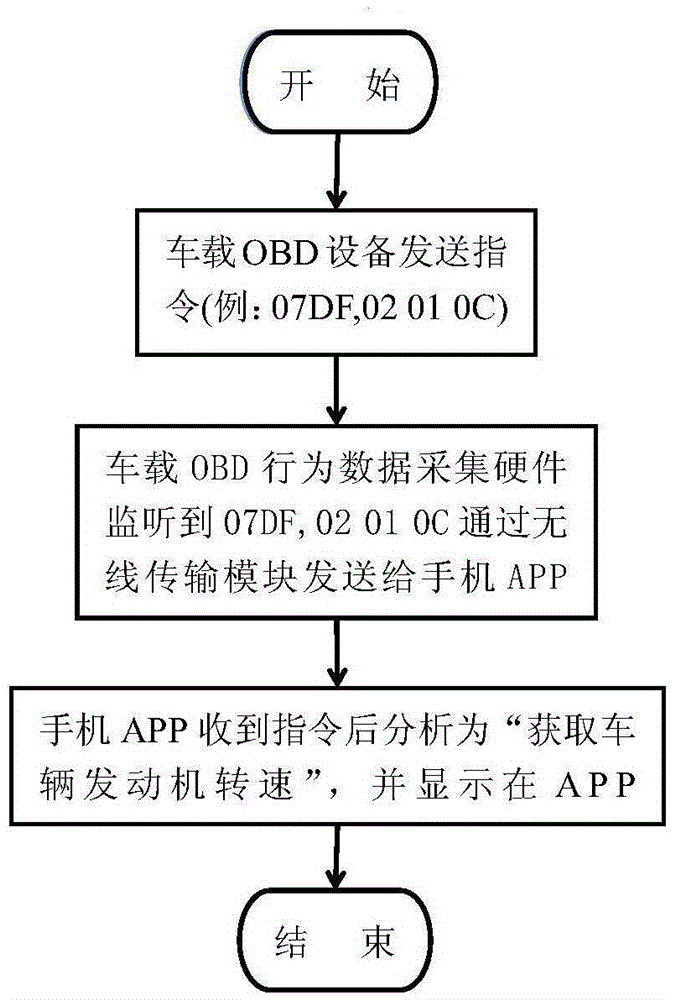
Method and device for identifying and processing malicious behaviors of OBD (On-Board Diagnostics) equipment
ActiveCN105631323AEnsure safetyAvoid paralysisPlatform integrity maintainanceData monitoringOn-board diagnostics
The invention discloses a method and a device for identifying and handling malicious behaviors of OBD (On-Board Diagnostics) equipment, belongs to the field of equipment data monitoring, and aims to inform a vehicle owner of malicious behaviors of the OBD equipment in a vehicle and judge whether operation is practical or not. The method is characterized by comprising the following steps: S1, monitoring OBD data of a response action behavior in an OBD equipment diagnostic protocol; S2, when the OBD data are acquired, storing the OBD data, and informing a user that the action behavior is to be executed; S3, judging whether the action behavior is executable or not by the user, transmitting the stored OBD data to the vehicle to be executed when the action behavior is judged to be executable, and clearing the stored OBD data when the action behavior is judged to be un-executable. The method and the device have the effect that an interface for the user to operate in the case of actual OBD malicious behaviors is provided, so that malicious modification of the vehicle of the user is prevented.
Owner:DALIAN ROILAND SCI & TECH CO LTD
A bill anti-counterfeiting method and device based on texture image features
ActiveCN103761799BBe uniqueGreat practicabilityCharacter and pattern recognitionPattern recognitionData information
The invention relates to a bill anti-counterfeit method and device based on texture image characteristics. The method comprises the steps of firstly utilizing a rapid image device for selecting a certain number of areas from a paper carrier before a bill is printed, obtaining paper texture image data and area central point position information, extracting texture image characteristic information, generating bill number information, calculating an abstract information flow of variable content data, encoding all the obtained information, hiding the information in visible elements of the bills, and finally printing and outputting the complete bill makeup data. In the verification process, a paper bill file is scanned to digital image data, all hidden information is extracted, and then whether the texture image characteristic information, the bill number information and the variable content data information are consistent or not is obtained in a comparing mode so as to judge bill authenticity. The anti-counterfeit technology meets the requirements of technical exclusivity, technical reliability, identification simplicity, identification uniqueness, anti-counterfeit timeliness and the like.
Owner:李晓妮
An online group member interaction method
ActiveCN104901869BAvoid Malicious ModificationsEasy to manageData switching networksMessage typeInteraction management
The invention provides an online group member interaction method, including group member login management, unread message management, message type setting and interactive message analysis, so as to effectively manage the interactive messages of group members and make group members Management of interactions is simplified.
Owner:上海尚美嘉晋互联网科技股份有限公司
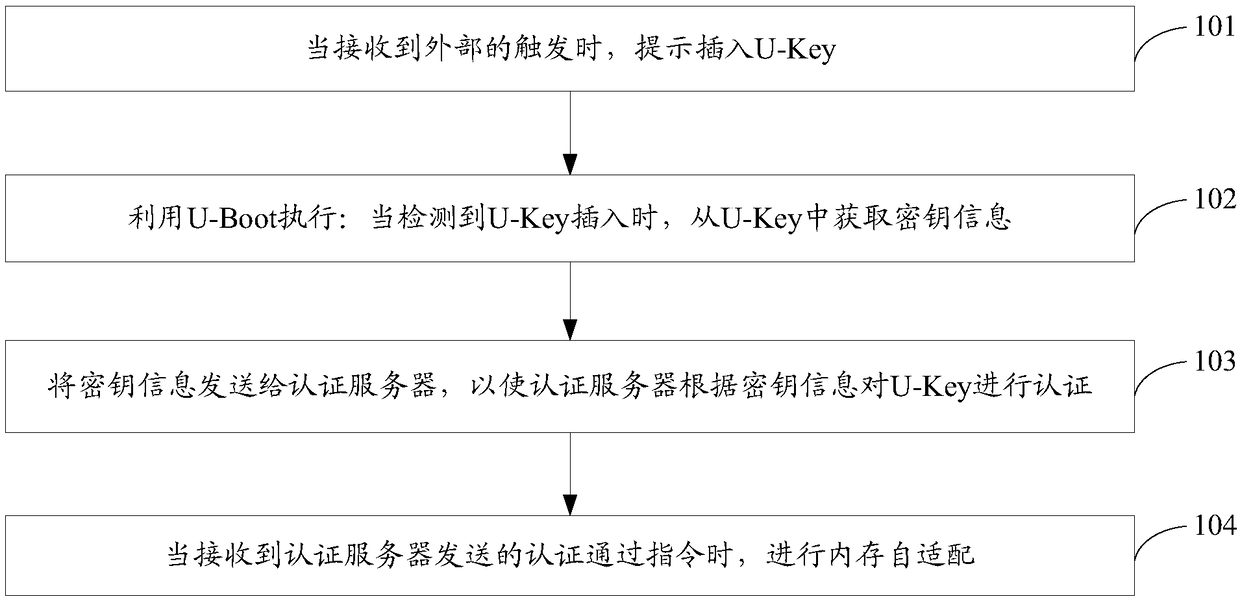
U-Boot-based memory self-adaptation method, device and system
InactiveCN108537044ASave configuration timeImprove securityResource allocationDigital data authenticationComputer hardwareAuthentication server
The invention provides a U-Boot-based memory self-adaption method, device and system. The method comprises the steps that when an external trigger is received, it is prompted that an encryption key U-Key needs to be inserted; U-Boot is used for performing that when it is detected that the U-Key is inserted, key information is acquired from the U-Key; the key information is transmitted to an authentication server, so that the authentication server authenticates the U-Key according to the key information; when an authentication pass instruction sent by the authentication server is received, memory self-adaptation is performed. The method can save memory parameter configuration time.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
System and method for carrying out safety risk check to computer BIOS firmware
InactiveCN100451987CEliminate security concernsAvoid Malicious ModificationsSoftware testing/debuggingRedundant operation error correctionEngineeringBIOS
The invention discloses a system proceed safe test for computer BIOS firmware and method, which comprises the following steps: initializing; proceeding BIOS sampling; analyzing BIOS image file; scanning various hidden dangers of BIOS; measuring completeness integrity of BIOS code; outputting the testing effect; proceeding safe repair for BIOS. This invention can decrease, reduce and remove safety loophole and hidden danger of computer BIOS, which provides reliable terminal safety prevention and overall protection for computer and network.
Owner:BEIJING JINYUAN LONGMAI INFORMATION TECH
Method of protecting image code based on hiding executable image and injecting dll
ActiveCN105512548BPrevent dynamic debuggingIncreased protectionComputer security arrangementsProcess functionComputer module
Provided is a method for protecting mirror image codes based on executable mirror image hiding and dll injection. The method comprises the following steps that 1, a target mirror image is decrypted in a memorizer; 2, a PE mirror image is loaded, wherein a dll file needed for a program is loaded, mirror image repositioning is executed, and finally OEP is executed; 3, whether an IAT of an exe module is hijacked or not is checked; 4, a Load Library and a Load Library Ex are actively hijacked, operation in the step 3 is executed on a dll mirror image of a load result, and if judgment is not abnormal, the step 5 is executed; 5, a Create Process function is hijacked, and a protection dll is injected while a subprocess is set up; 6, remote thread injection is carried out, a protected target process is injected in a Ring3 environment, and thread injection of a vicious loader is avoided; 7, a thread (THREAD_PRIORITY_BELOW_NORMAL) with low priority is built, endless loop check is carried out, whether the thread is loaded by a Debugger or not is checked, and checking is carried out once every second.
Owner:XIANGTAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com