Method and device for identifying and processing malicious behaviors of OBD (On-Board Diagnostics) equipment
A behavior and equipment technology, applied in the direction of electrical digital data processing, computer security devices, instruments, etc., can solve problems such as hidden dangers of car owners, and achieve the effect of preventing paralysis and ensuring safety.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0022] Embodiment 1: a kind of method of identifying malicious behavior of OBD equipment and processing, a kind of method of identifying malicious behavior of OBD equipment and processing, comprising:
[0023] S1. Monitor the OBD data of the reaction action behavior in the OBD device diagnosis protocol;
[0024] S2. When the OBD data is obtained, store the OBD data, and notify the user that the action is about to be executed;
[0025] S3. The user judges whether the action can be executed. If it is judged to be executable, the stored OBD data is sent to the vehicle for execution; if it is judged to be unexecutable, the stored OBD data is cleared.
[0026] Wherein: the OBD data is at least one of the OBD data of the diagnostic protocol of the CAN application layer (ISO14229) and the diagnostic protocol of the K application layer (ISO14230): electronic control unit reset (0x11), safe entry (0x27), pass Identifier write data (0x2E); write memory by address (0x3D), clear diagnost...
Embodiment 2
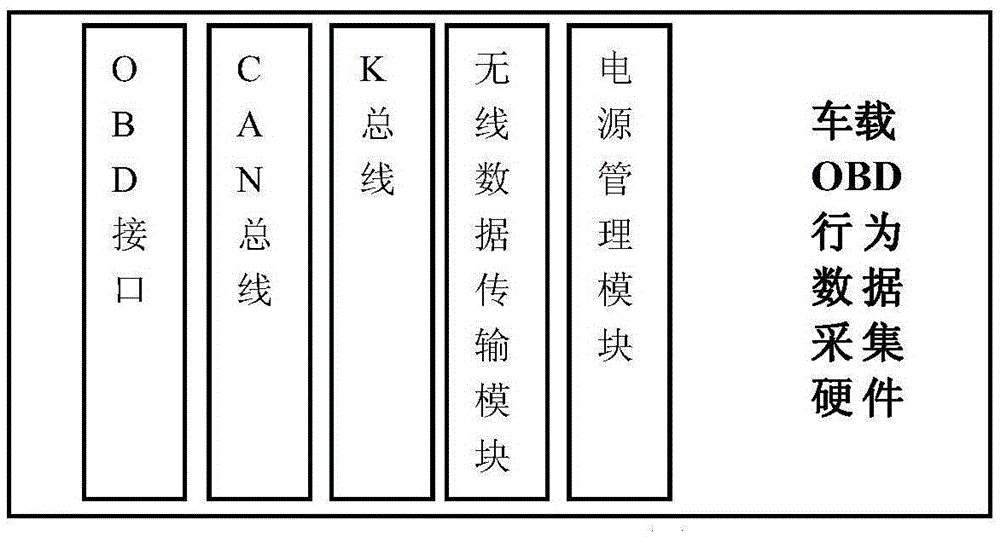
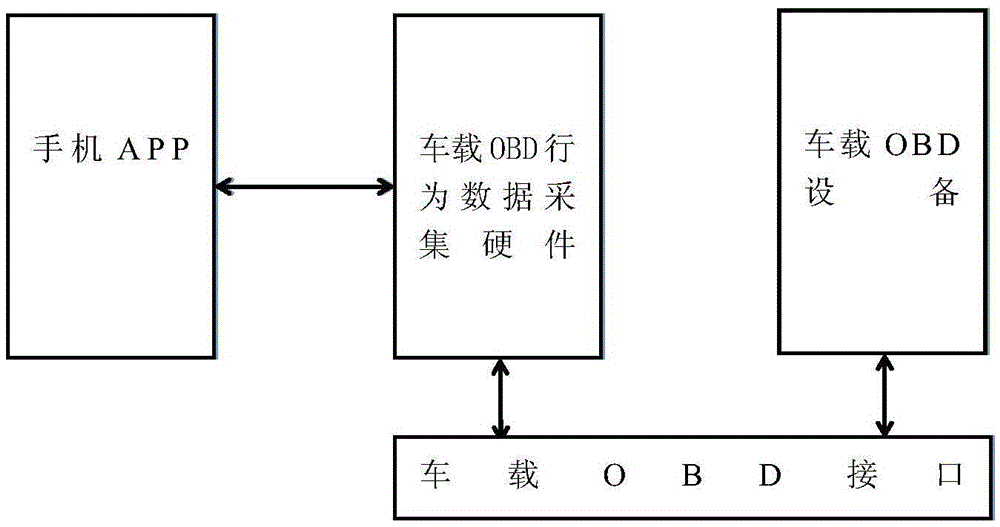
[0027] Embodiment 2: have the technical scheme identical with embodiment 1, more specifically, as figure 1 and figure 2 As shown, the OBD device is monitored by a system that monitors the behavior of the OBD device in real time. The system includes: a vehicle-mounted OBD device connected to the vehicle-mounted OBD interface, and an adapter line is added to the OBD interface, which is connected to the behavior data acquisition hardware of the vehicle-mounted OBD device. The vehicle-mounted OBD behavior The data acquisition hardware collects the interactive data between the vehicle-mounted OBD device and the CAN bus, sends the data to the data analysis terminal for analysis, and displays the behavior information obtained from the analysis.
[0028] The vehicle-mounted OBD device behavior data acquisition hardware includes a CAN bus circuit, a K bus circuit, and a wireless transmission module. The vehicle-mounted OBD device behavior data acquisition hardware monitors the vehicle...
Embodiment 3
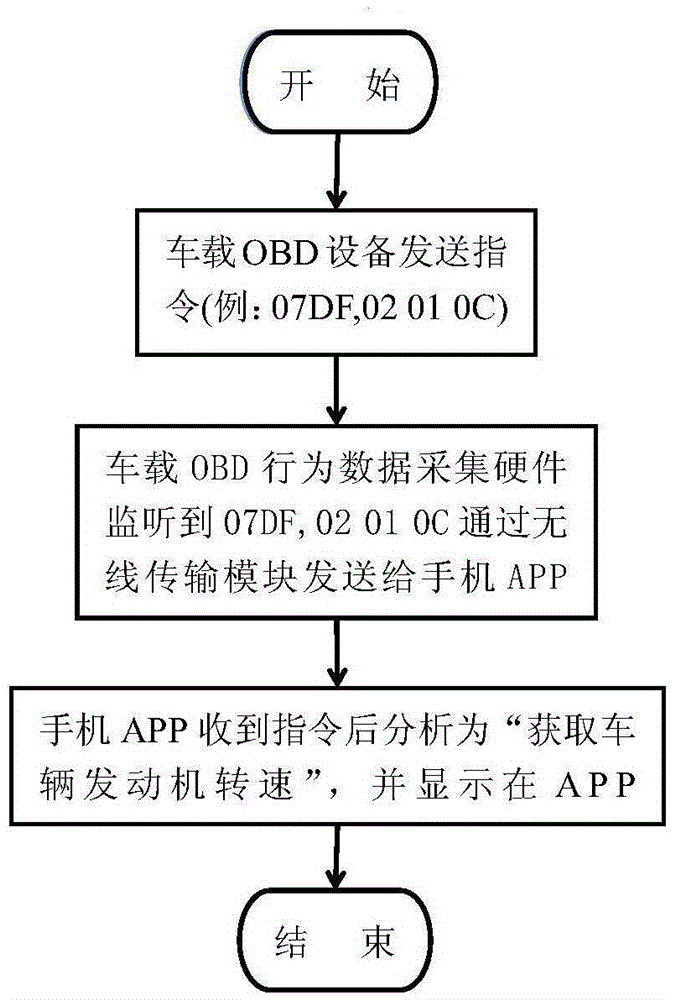
[0030] Embodiment 3: This embodiment has the same technical solution as Embodiment 2, and the method that the analysis terminal analyzes the received data into the behavior information of the vehicle-mounted OBD device is: as attached image 3 , the analysis is actually to analyze the instruction when the on-board OBD sends the instruction, and correspond the instruction to the behavior. The analysis of the instruction is carried out according to the international standard 14229 and 15031, of which 15031 specifies the meaning of some values, and Some of them are self-defined instructions for car manufacturers, but they all conform to international standards.
[0031] attached image 3 The analysis process of the OBD device's behavior "obtaining the vehicle engine speed" is given. The vehicle-mounted OBD device sends an instruction code, for example: 07DF, 02010C, and the data is monitored by the vehicle-mounted OBD device's behavior data acquisition hardware through the CAN bu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com