Method and system for modifying password of encryption lock
An encryption lock and password technology, applied in the field of encryption locks, can solve the problem that the initial password of the encryption lock is not controlled by the manufacturer
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
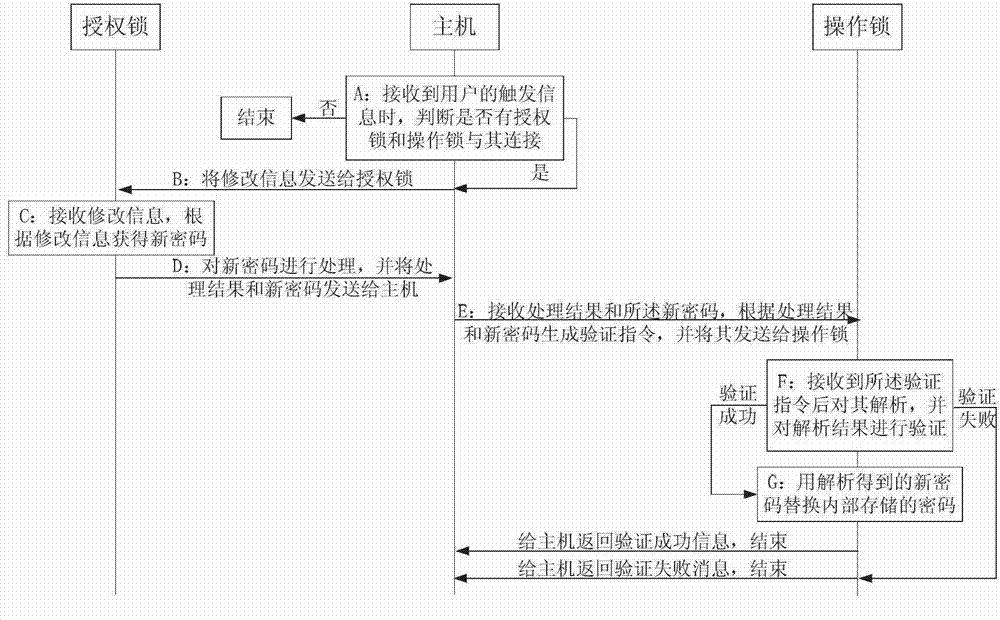
[0161] Embodiment 1 of the present invention provides a method for modifying the encryption lock password, such as figure 1 shown, including:
[0162] Step A: When the host receives the user's trigger information, it judges whether there is an authorization lock and an operation lock connected to it, and if yes, execute step B, otherwise end.
[0163] Step B: The host sends the modification information to the authorization lock;
[0164] The modification information in this embodiment is a new password or serial number.
[0165] In this embodiment, between step A and step B, it may also include:
[0166] Step a1: the host obtains a password list from the authorization lock, and outputs it;
[0167] Step a2: The host waits for the selection information input by the user, and judges whether the selection information is received within the preset time, if yes, continue, otherwise output an error message, and end;
[0168] The selection information in this embodiment includes ...
Embodiment 2
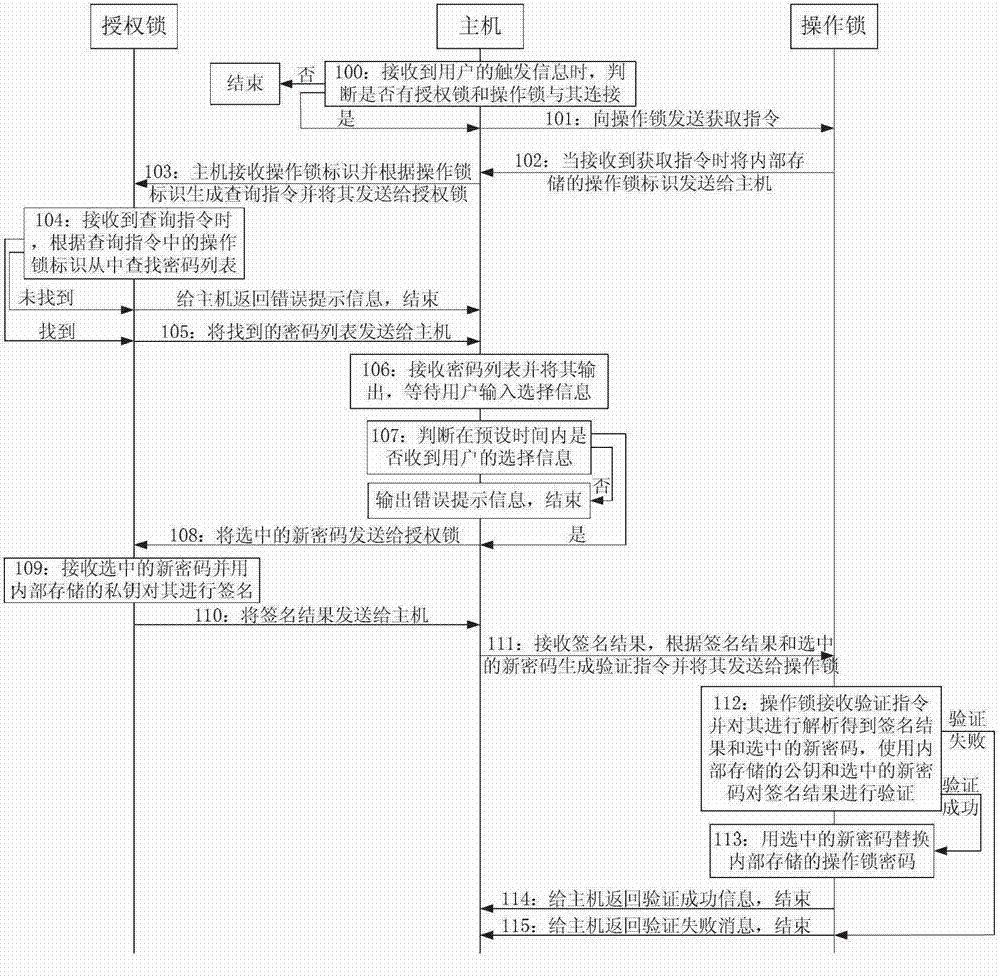
[0204] Embodiment 2 of the present invention provides a method for modifying the encryption lock password, such as figure 2 shown, including:
[0205] Step 100: When the host computer receives the trigger information from the user, it judges whether there is an authorization lock and an operation lock connected to it, if yes, execute step 101, otherwise end;
[0206] In this embodiment, the host distinguishes the operation lock and the authorization lock through different interfaces; when the operation lock and the authorization lock are the same type of lock, it can also be distinguished by other identifications, such as user ID, UID, specific data files in the lock or specific executable programs, etc.;
[0207] Specifically, the trigger information is generated when the user starts the tool software;
[0208] Step 101: the host sends an acquisition command to the operation lock;
[0209] Step 102: When the operation lock receives the acquisition instruction, send the in...
Embodiment 3
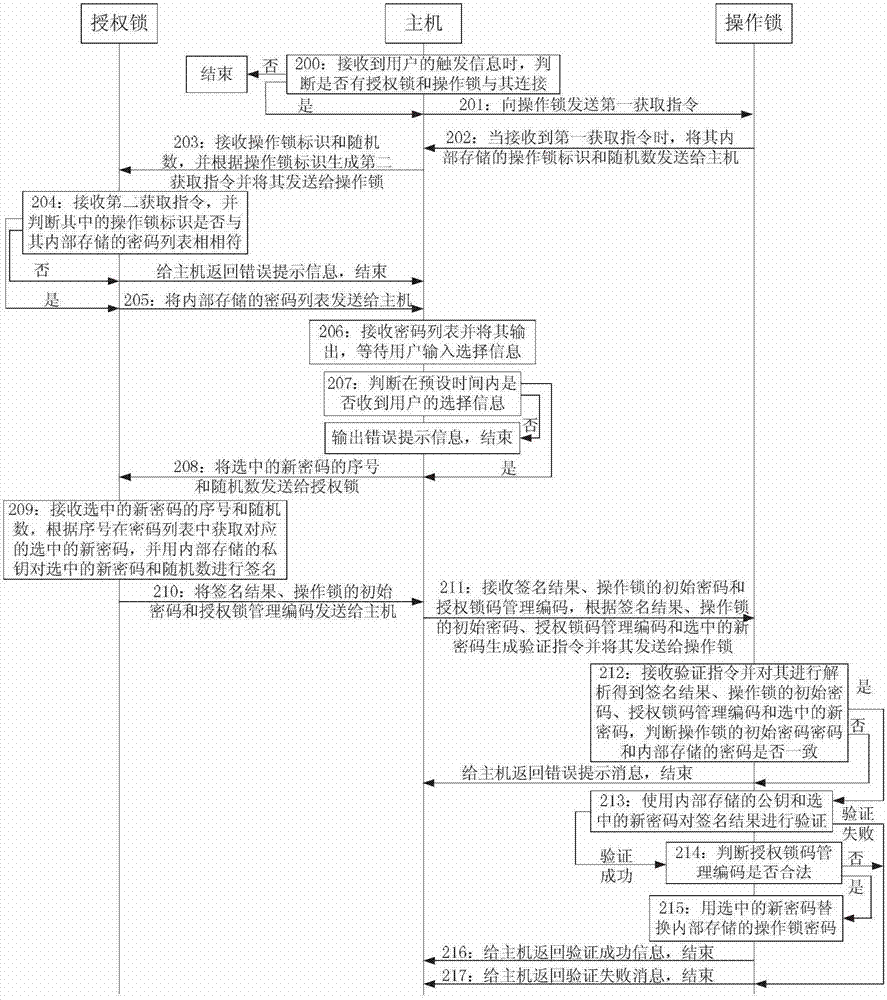
[0270] Embodiment 3 of the present invention provides a method for modifying the encryption lock password. In this embodiment, an authorized lock can only modify the initial password of a type of operation lock once, such as image 3 As shown, the method of the present embodiment includes:
[0271] Step 200: When the host receives the trigger information from the user, it judges whether there is an authorization lock and an operation lock connected to it, if yes, execute step 201, otherwise end;
[0272] In this embodiment, the host distinguishes the operation lock and the authorization lock through different interfaces; when the operation lock and the authorization lock are the same type of lock, the host can also distinguish through other identifications, such as user ID, UID, specific data files or Specific executable programs, etc.;
[0273] Specifically, the trigger information is generated when the user starts the tool software;
[0274] Step 201: the host sends a firs...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com