File security control and trace method and system based on digital fingerprints
A digital fingerprint, security management and control technology, applied in the field of information security management and control, can solve the problems of high deployment and maintenance costs, the inability of the DLP system to track the flow of documents, and the inability to achieve accurate traceability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
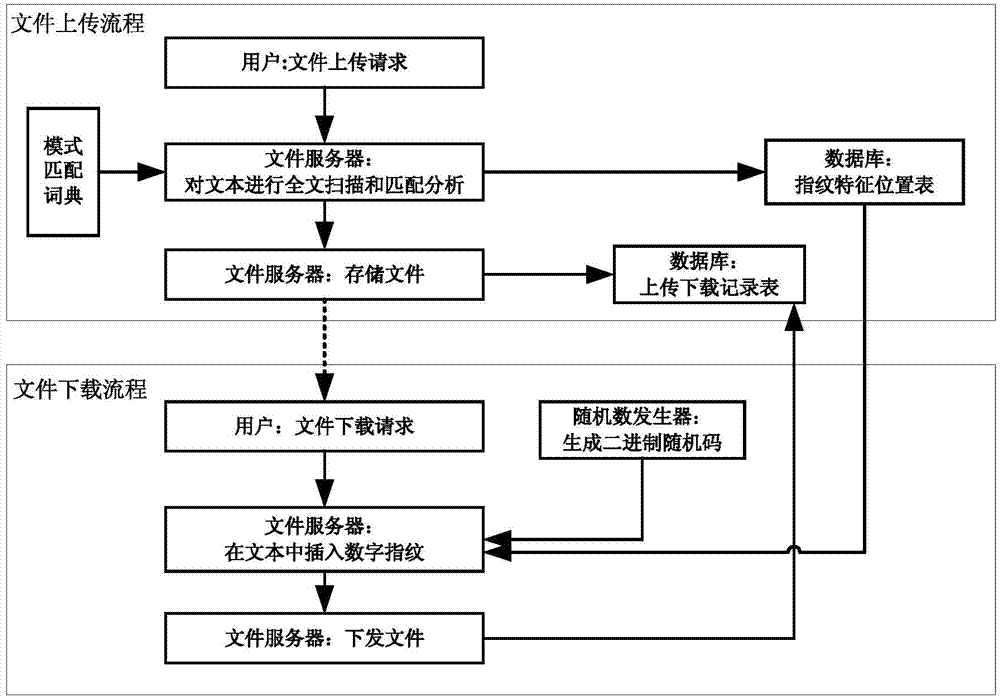
[0077] The digital fingerprint-based file security control and traceability method of this embodiment can realize traceability and security management of text files. It is a digital fingerprint algorithm based on natural language analysis and processing, including file upload process and file download process.
[0078] First of all, in order to facilitate understanding and gain a perceptual understanding, let me take an article as an example. This paragraph is a paragraph in the middle school textbook "Moonlight in the Lotus Pond". The original text is as follows:
[0079] on the surface of the winding andtwisting lotus pond floated an endless field of leaves. the leaves lay high in the water, rising up like the skirts of a dancing girl. Among the layers ofleaves white blossoms adorned the vista, some beguilingly open and othersbashfully holding their petals in their petals; just like bright pearls or starsin a blue sky, or like roses just emerging from their bath. beauty. a...
Embodiment 2
[0145] This embodiment mainly illustrates the scene where the method of the present invention can be applied. Since the inserted digital fingerprint does not affect the semantic expression of the document, this solution can be used except those official documents with legal effect, and its use scene will be very Broadly, as follows:
[0146] Company OA official document system: If a certain official document is only an internal official document and is not intended for external release, then a slight text watermark can be accepted while maintaining semantics; in this scenario, when employees view and download, the OA system will Through the file server of this solution, a copy is generated for employees, and this copy contains a certain amount of fingerprint information, so each employee bears the responsibility of keeping it confidential.
[0147] Company mailbox system: the attachments of the mailbox system are also stored by the file server. After the file server adopting t...
Embodiment 3
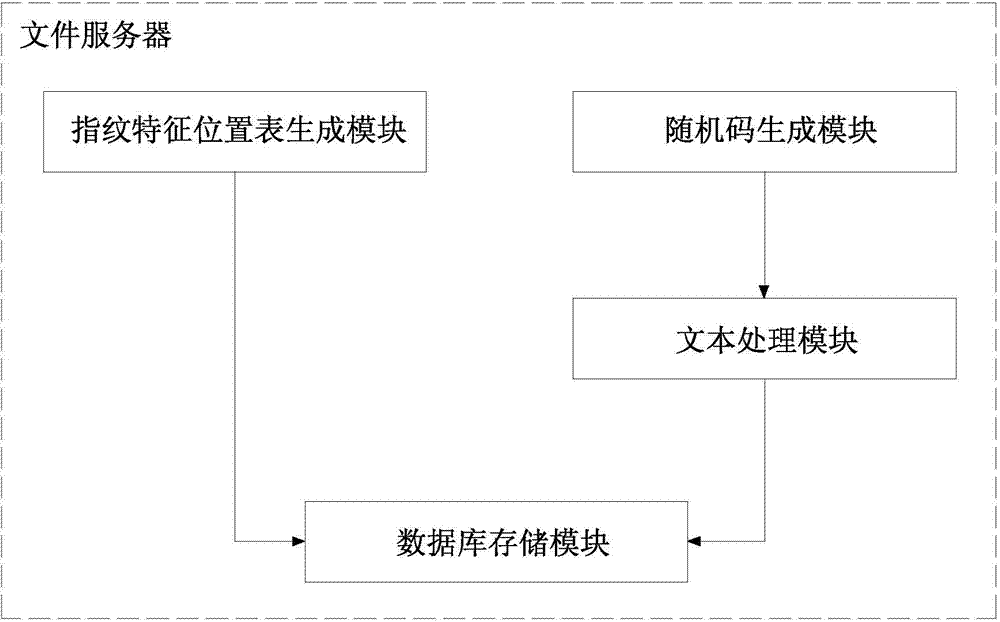
[0152] Such as figure 2 As shown, the digital fingerprint-based file security control and traceability system of this embodiment includes a file server, and the file server includes:
[0153] The fingerprint feature location table generation module is used to use the pattern matching dictionary to start the natural language analysis algorithm when the user uploads the file, scan and match the full text of the file text, find the position where the digital fingerprint can be inserted, and generate a fingerprint feature location table;
[0154] The random code generation module is used to generate a binary random code of the same length according to the length of the fingerprint feature location table when the user initiates a file download request;
[0155] Text processing module, if the corresponding bit of the generated random code is 0, it means that the bit is not modified; if the corresponding bit of the generated random code is 1, it means that the bit is in the correspon...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com